Abstract
Smart manufacturing combines advanced manufacturing capabilities and digital technologies throughout the product lifecycle. These technologies can provide decision-making support to manufacturers through improved monitoring, analysis, modeling, and simulation that generate more and better intelligence about manufacturing systems. However, challenges and barriers have impeded the adoption of smart manufacturing technologies. To begin to address this need, this paper defines requirements for data-driven decision making in manufacturing based on a generalized description of decision making. Using these requirements, we then focus on identifying key barriers that prevent the development and use of data-driven decision making in industry as well as examples of technologies and standards that have the potential to overcome these barriers. The goal of this research is to promote a common understanding among the manufacturing community that can enable standardization efforts and innovation needed to continue adoption and use of smart manufacturing technologies.
Keywords: Smart manufacturing, Data-driven decision making, Standardization, Systems integration
INTRODUCTION
Manufacturing has increasingly relied on software systems to improve productivity and manage operations. Modern manufacturing equipment can often support networking and monitoring as well as reporting performance metrics to varying degrees. Even older, legacy equipment can be retrofitted to provide similar capabilities. New technologies have been proposed to enable better performance monitoring and control for manufacturing systems, including visualization tools and advanced analytical capabilities to support scheduling, performance monitoring, and anomaly detection. Such technologies have been driven by demands for increased flexibility and resource efficiency. Other business drivers include smaller customer orders and tighter delivery dates [1] and greater responsiveness to sustainability concerns [2]. As new capabilities have been introduced into manufacturing systems to respond to these and other technology drivers, more complexity has been added to manufacturing operations, which in turn has forced the use of new and better technologies for system design and management.
The term “smart manufacturing” has been adopted to refer to manufacturing systems that combine advanced manufacturing capabilities and digital technologies throughout the product lifecycle. Such systems are characterized by improvements in the following capabilities [3]:
Communication with other systems across a network
Collection and response to operational data
Support for decision making
Increased specialization to accommodate advanced Materials
Moreover, each component of a smart manufacturing system may contain all of these capabilities for a particular function and thus can be considered a smart manufacturing system in itself.
Smart manufacturing incorporates many of the historical manufacturing paradigms that have been the focus of researchers’ and practitioners’ efforts to improve manufacturing practices. Examples of these paradigms include lean, flexible, agile, sustainable, digital, and cloud manufacturing. Smart manufacturing can enable aspects of these paradigms for all manufacturers from small businesses to large enterprises [4],[5]. One critical aspect of these systems is the use of data and information to make informed decisions. An example technology area that reflects this characteristic is the Industrial Internet of Things (IIoT) based on the Internet of Things (IoT) concept. In the IoT, many commonly used items are networked and may be equipped with computers capable of collecting and processing data and responding to external events, which essentially makes them “smart.” The IIoT extends this idea to manufacturing where the items are the sensors, devices, equipment, and systems found within manufacturing facilities. Thus, whereas the IoT connects mainly consumer devices, the IIoT connects devices typically found in an industrial setting. By networking these items, manufacturers can have access to wide swaths of data and information to support decision making.
There is wide agreement that innovations, such as smart manufacturing and the IIoT, can provide important benefits to manufacturers. For example, an Industry Week survey found that 88% of surveyed manufacturers believe that the IIoT is an important trend and 63% also believe that it is critical to their success [6]. This trend was also found by a recent Accenture survey of manufacturers [7]. However, the majority of respondents – 66% in the Industry Week survey and 71–93% in the Accenture survey – also do not have a specific and comprehensive strategy to deploy and use the technology [6],[7]. A similar industry study from LNS Research found that only 13% of surveyed companies were moving forward with the IIoT today [8], and some industry experts estimate that only 5% of manufacturing machines are currently being digitally monitored [9]. These survey results should come as no surprise given that the IIoT and many smart manufacturing technologies are in the early phases of market adoption where compelling use cases and education are essential for success. The goal of this paper is to begin to meet this need by understanding the requirements for manufacturers to leverage smart manufacturing technology to support decision making.
BACKGROUND
We can think of a general data-driven decision-making process as being composed of seven basic activities that occur once the purpose or goal of the decision is well understood as shown in Figure 1 [10]. The first activity, “Scope,” refers to defining the boundaries and key performance indicators (KPIs) and metrics needed to address the goal of the decision. “Identify” determines the data and information needed to support the calculation of KPIs and metrics within the boundaries of analysis. “Collect” requires using tools and methods to gather the identified data and information from the system of interest, while “Transmit” requires using tools and methods to move the collected data and information from the system of interest to where it may be analyzed. “Analyze” is the calculation of the identified KPIs and metrics from the collected data and information using appropriate methodologies. “Share” refers to accessing previously generated data, knowledge, and resources to reduce the cost, expertise, time, and training needed to generate new intelligence through analysis. Finally, “Retrieve” is the storing and accessing of generated intelligence quickly and accurately without losing knowledge to support future decisions.
Figure 1.
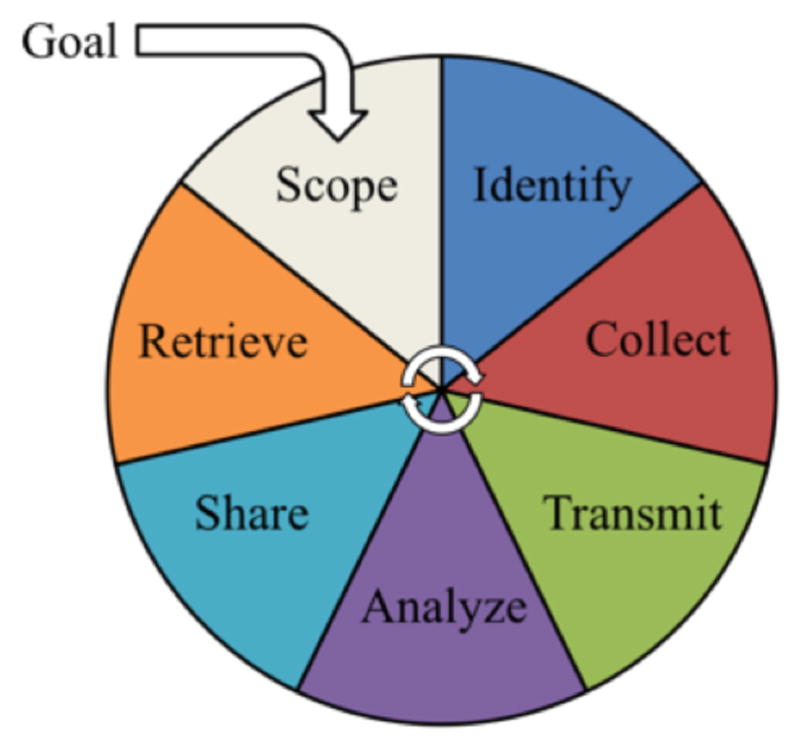
Generalized data-driven decision-making process [10].
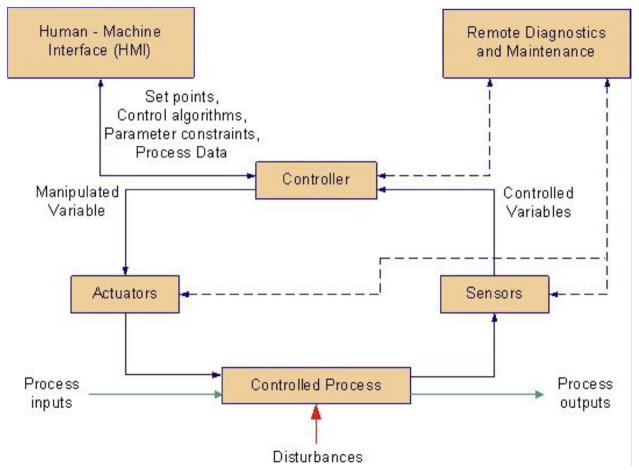
One of the primary purposes of much of the smart manufacturing technology on the market is to improve on the general data-driven decision-making process described previously [10]. Enabling technologies and standards have been established to support solutions that help manufacturers use data in new and valuable ways. One example is in the area of process monitoring and control systems, which are widely used throughout manufacturing industries [11]. At the heart of these systems are control-feedback loops. As shown in Figure 2, a control-feedback loop includes the following devices:
Figure 2.
Industrial Control Systems operation [11].
A controlled process; e.g., machining.
Actuators that act upon the environment; e.g., a pump to deliver coolant to the machine tool frame.
Sensors that measure physical properties of the process and convert measurements into outputs that a controller can interpret; e.g., a sensor to measure the temperature of the machine tool frame.
A controller that adjusts actuators based on sensor input; e.g., the controller may activate a coolant pump if the measured temperature of the machine tool frame exceeds a certain value.
The control-feedback mechanism shown in Figure 2 is influenced by disturbances to the process environment as well as by human interaction through a human-machine interface (HMI). In addition, the controller and sensors may receive input from remote diagnostics and maintenance tools.
The devices controlling a process in a smart manufacturing system may also be “smart.” For example, a smart sensor has the ability to perform computations on process measurement data before passing the data to the controller. The HMI and diagnostics and maintenance tools may adopt modern information technologies and Internet protocols. As a consequence, today’s smart manufacturing systems increasingly resemble traditional IT systems. Hence, they share some of the same potential weaknesses and vulnerabilities.
Other examples exist in process monitoring and control. These systems in manufacturing require data interoperability to capture often disparate data and information streams that exist within manufacturing systems. MTConnect is an example of a manufacturing data exchange standard that enables data-driven decision making. It is an open-source standard designed for data and information flowing from shop-floor devices, equipment, and applications [12]. There are several commercial solutions that have been created using the MTConnect standard, such as System Insights VIMANA, TechSolve ShopViz, and FORCAM Force [9],[13]. These and other solutions and standards available to manufacturers have allowed them to monitor shop-floor operations using dashboards that report appropriate KPIs and metrics. Despite the potential value provided by technologies and standards for process monitoring and control and decision making in general, manufacturers remain hesitant to adopt these solutions because of the inherent implementation challenges and potential security liabilities they pose.
Understanding how to integrate and deploy new technology is not trivial for a manufacturer or technology vendor. To benefit from these advances, manufacturers often require technical insight just to navigate the breadth and type of technologies now available to improve their systems [1],[14]. Preliminary technology development and validation also occur in research environments, which may not contain the implementation barriers that often exist in production environments [10]. For example, sensors can operate differently when installed in real production environments and may require interfaces to function with older equipment. Wireless networks may function differently in different environments based on existing sources of interference and the demands placed on the network. In addition, different components of a manufacturing system are connected by a wide range of interfaces with different levels of technological maturity and openness as well as different functional scopes [10].
Collaboration between manufacturers and solution providers will help assure that smart manufacturing technologies work well together. In this way, stakeholders can identify problem areas in deployment that may have been missed when developing smart solutions. Best practices for using solutions can emerge as will opportunities for standards. Additionally, the collective knowledge may expose systemic problems that were not identified in isolated performance testing. The sharing of this expertise can enable successful deployment and more widespread adoption of smart manufacturing technologies and can benefit the entire manufacturing community if made public. Ultimately, pooling the knowledge of many can create a resource that will benefit all and allow the community to discover trends and opportunities that would otherwise be missed.
Helu et al. [10] proposed the development of a collective knowledgebase to identify implementation barriers and solutions for deploying smart manufacturing technology. This paper expands that concept by identifying common activities for and barriers to data-driven decision making in manufacturing. This work forms an outline for when, where, and how new technologies offer the potential to help manufacturers make better decisions. It also provides an initial framework on which to build a base of experience when using these technologies and understanding the risks involved therein.
FRAMEWORK APPROACH
The software community has developed a large body of work that addresses how to assure the performance of software systems. This work serves as a useful template to address performance assurance for data-driven decision making in manufacturing. A foundation for our approach is the Common Weakness Enumeration (CWE). The CWE is based on a model of collaboration where problems with software infrastructures are collected and documented [15]. It is a critical component of a cybersecurity strategy that collects the experience of many software system users and distills learned shortcomings into a form that can benefit others. It categorizes reported issues, tracks the frequency of these issues, and provides documented solutions. The CWE forms a basis for addressing deficiencies in cyberdefense for many organizations.
Based on Helu et al. [10], we propose to apply the CWE model of collaborative experience to aid the deployment of smart manufacturing technologies for data-driven decision making. Using collaboration to find and share critical success stories, enable more rapid deployment of the technologies, and identify opportunities for improvements requires an organized means of enumerating common activities for and barriers to data-driven decision making in manufacturing. To organize such an approach and identify relevant content areas, we leverage a similar approach from the security community: the Cybersecurity Framework [17].
As cybersecurity has become an increasingly critical concern, considerable focus has been given to developing a comprehensive set of tools and guidelines that can educate various stakeholders in an organization about the intricacies of cybersecurity. The Cybersecurity Framework is one result of these efforts that was developed for critical infrastructure organizations to better manage and reduce cybersecurity risks [17]. The Cybersecurity Framework provides a way for organizations to describe their current security posture and target state and to communicate and assess progress toward meeting goals. It is organized in a hierarchical fashion, which allows for high-level as well as detailed descriptions of security activities. Thus, the Cybersecurity Framework has a broad base of users. It can facilitate communication not only between different categories of stakeholders but also between different levels of management within an organization, e.g., between a chief executive and cybersecurity professionals responsible for implementation. In addition, the Cybersecurity Framework links desired security outcomes to specific sections of standards, guidelines, and best practices, which offers guidance on how to achieve desired cybersecurity outcomes.
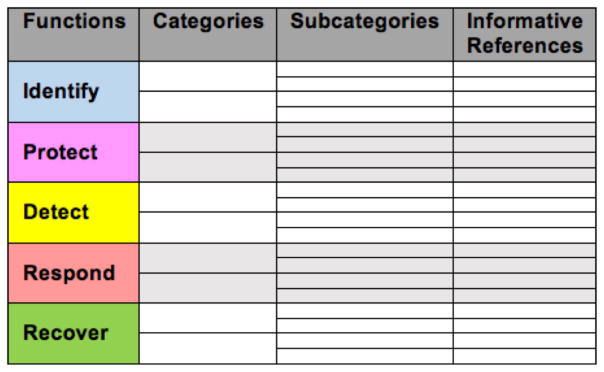
A major component of the Cybersecurity Framework is the Framework Core, which is a taxonomy of cybersecurity activities common across critical infrastructure sectors [17]. The highest level of the Framework Core consists of the following five functions denoting basic cybersecurity activities: Identify, Protect, Detect, Respond, and Recover. Each of these functions is subdivided into categories, which are high-level outcomes tied to a particular requirement or activity. Each category in turn contains a set of subcategories, which are specific lower-level outcomes that support the category’s higher-level outcome. Each subcategory points to informative references providing guidance for achieving the subcategory’s outcome. Figure 3 provides a high-level structure of the Framework Core.
Figure 3.
Cybersecurity Framework Core [17].
Because it provides a structure that enables capabilities similar to the ones we are interested in, we adapted the approach of the Cybersecurity Framework when defining the functional areas and categories of activities to be accomplished for data-driven decision making in manufacturing. Two especially attractive capabilities are the utility of the Cybersecurity Framework as a communication tool and its approach of linking goals to actionable guidance. The decision-making process described previously consists of seven functional areas. For each of those areas, we describe the categories of activities and subactivities required to achieve the function. We also provide examples of the barriers to successful implementation of the listed activities and the enabling solutions that are available to address these barriers. Note that these descriptions are not meant to be exhaustive. They are meant to provide a framework for others to contribute towards a collaborative, community-developed knowledgebase.
In our approach, we take advantage of instances where the requirements of cybersecurity and decision making in manufacturing are well aligned. For example, consider the Framework Core “Identify” function, which has been defined as: “Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities” [17]. This definition is similar to that of the Identify function in our proposed knowledgebase since both involve establishing an understanding of physical and human resources, business environment, capabilities, intellectual property, information, policies, and risk management strategy. Another example is the “Asset Management” category in the Framework Core Identify function. The high-level outcome for this category is defined as: “The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to business objectives and the organization’s risk strategy” [17]. Again, the definition is applicable to both cybersecurity and decision making in manufacturing.
In addition to overlap between the requirements of cybersecurity and decision making in manufacturing, our work relied on literature and industry experience as appropriate to generate a fuller perspective on the requirements and barriers to data-driven decision making in manufacturing. The result of our work was documented in a spreadsheet resource that can serve as the foundation of a larger knowledgebase. The content of this spreadsheet is discussed in the next two sections of this paper.
REQUIREMENTS FOR DECISION MAKING
Deploying data-driven decision-making technologies into manufacturing systems creates a system-of-systems integration challenge. The first and most important step in navigating this challenge is to identify the requirements of the systems through a variety of methods including literature reviews and pilot studies. These requirements serve as a foundation for realizing critical manufacturing needs (current and future) that can be effectively measured and ranked against other drivers. Similar to the Cybersecurity Framework, requirements are understood through the activities that they must support. They are captured within each function as a set of categories of activities which are then broken down into sub-activities as described previously. We can then identify barriers and enabling technologies to accomplish each subactivity listed.
Table 1 provides an example of our approach for one category of activities in the Analyze function: “Select appropriate analysis algorithms to assess data to satisfy the goal of the analysis.” This example illustrates the subactivities involved to perform any general manufacturing analysis. Manufacturing analyses are conducted to maintain the efficiency and effectiveness of manufacturing operations and to serve as a foundation for continuous improvement. A critical aspect of manufacturing analysis is the selection of appropriate algorithms and their implementation. Table 1 also inclues the barriers that influence how a company decides on a specific analysis solution. Collecting the information on the different barriers that a manufacturer will face provides an opportunity for understanding and prioritizing the trade-offs that must be balanced, such as cost, data storage, measurement uncertainty, reliability, response time, extensibility, openness, and required expertise. In addition, an understanding of barriers begins the process of identifying solutions. The remainder of this section describes some of the key categories of activities for each of the seven functions that compose data-driven decision making.
Table 1.
Subcategory of activites required to select algorithms for data analysis.
| Subcategory of Activities | Barriers to Implementation |
|---|---|
| Identify algorithms (or describe algorithm requirements if there are no known algorithms) | Explicit cost: Implementations costs money. Implicit cost: Even free implementations can involve expensive installation, maintenance, integration, tracking bug patches, finding support. |
| Choices are overwhelming, many algorithms have subtle differences that are not at first important. Algorithms may have different implementations. | |
| Select parameters | May not be possible to identify optimal parameters; Heuristics and/or extensive experimentation likely to be necessary. |
| Describe time performance Requirements | Performance is often hard (or impossible) to quantify; performance may take too long |
| Describe memory performance requirements | |
| Describe the uncertainty Requirements | Lack of common practices for quantifying manufacturing uncertainty |
| Describe reliability Requirements | Many algorithms trade off reliability for speed as most optimal algorithms are exponential (really, NP-complete). |
| Determine degree of opacity/transparency (and possibly justify lack thereof) | Some solutions are black boxes. Even ostensibly transparent algorithms (i.e., neural networks) come with no explanation. |
| Describe extensibility (or lack thereof) | Some algorithms cannot be readily extended. |
| Identify and justify proprietary, commercial, patented, secret algorithms. | Some algorithms are proprietary, patented, etc. which restrict usage, distribution, etc. |
| Determine required expertise | Expensive/difficult to find/become expert |
Function #1: Scope
The scope sets the stage for establishing or identifying the requirements for a problem space to which smart manufacturing technology will be applied. A properly scoped work effort can ensure a company’s success or failure. Too large a scope and the company may never achieve significant progress toward improving its smart manufacturing capabilities while too small a scope may result in mediocre results and poor marks by management. By first determining the appropriate focus, key system requirements, associated technologies, and significant barriers for deploying new technologies, companies can most effectively direct their efforts for maximum impact. Communications has a significant role in how one defines the scope as all manufacturing activities must be coordinated with internal and external stakeholders. This includes issues such as personnel knowing their roles and how to interact and coordinate with stakeholders. The categories of activities involved in setting the scope are as follows:
Analysis of the scope to understand the business environment, including the organization’s mission, objectives, stakeholders, and activities
Communication with stakeholders to understand interactions and dependencies
Function #2: Identify
Identifying key systems and data is an essential first step for planning and implementing new technologies for smart manufacturing. The requirements should have a direct and defined correlation to the smart manufacturing goals that map to business drivers and support the efforts that will have been made clear in the scoping activities. In this category, one identifies specific analysis needs in terms of manufacturing processes, associated resources, and data sources and flows. The identified processes and data, such as energy and material utilization, will support the goals designated in the scope:
Manage assets so as to understand the data, people, devices, systems, and facilities involved
Understand the operational environment, including the material and information flows to and from assets
Understand data collection capabilities of different assets
Understand the relationship between scope and data needs
Specify data collection requirements for specific analysis activities
Function #3: Collect
Data from decision-support and analysis applications, some developed internally and some commercial, need to be collected and key input/output parameters and other relevant information captured. Many newer manufacturing resources now support continuous monitoring, detect and communicate key events, and provide essential and reliable data collection. Older systems can be retrofitted to collect various types of performance information but instructions for doing so do not exist.
Data can be collected for a variety of purposes. For example, detailed data collection may be used for a thorough analysis of a manufacturing process for process improvements. This type of collection may involve modeling the physics of the process and supports offline analysis. The analysis is often relatively complex and requires significant computation. Conversely data can be collected to support real-time control of systems. This type of data collection involves carefully identified performance indicators that can be used to determine a need for adjustments in the system’s operation. Frequently, there is a relationship between these two types of data since detailed analysis is often conducted to plan for operational control.
Data can be collected through several means. Reviews of external studies (industry, academia, and government) can be used to collect comparable data sets to those operations within an organizaiton. The most applicable results can be obtained through collecting data internally within the enterprise. Internal data collection is a larger undertaking and is the focus of the activities for this function. Categories of activities in this area include:
Continuous monitoring
Detection and communication of performance problems
Collection methods
Function #4: Transmit
Transmitting data requires the physical movement of data from the data source to the point where the analysis occurs. For example, companies can move data from machine tools on the shop floor to an enterprise database that is accessible to engineers using MTConnect. This supports close to real-time analysis of shop-floor control and performance. Smart manufacturing is prefaced on automated dissemination of data ensuring proper delivery and requires methods beyond the use of portable digital-storage devices, such as thumb-drives. The transmission of data involves activities in a number of areas to ensure that the data arrives where it is needed in a usable and reliable manner. These activities fall into the following categories:
Data availability and timeliness
Data integrity in terms of both semantics and completeness
Data tracability
Infrastructure maintenance
Cybersecurity
Integration into manufacturing operations
Function #5: Analyze
A hallmark of smart manufacturing is that detailed analyses of manufacturing systems are being made more readily available in terms of speed, accuracy, and general accessibility of analysis applications. Categories of activities that support these capabilities include:
Identification of analysis techniques appropriate to the problem
Preparation of data for the analysis
Visualization methods
Validation and verification
Companies have made great progress in analyzing various aspects of manufacturing to better produce products. Key drivers continue to be cost, on-time product delivery, and asset utilization. Computing power and networking capabilities are making complex analysis using real-time data available for manufacturing systems during operations.
Function #6: Share
Smart manufacturing is defined by the ability to communicate data, information, and knowledge throughout the enterprise. To get maximum utility from an analysis, it is essential that information collected be stored in formats that promote sharing between the company’s various analysis applications, between the analysis applications and the operations, and with a variety of stakeholders. For example, planning simulations run by manufacturing engineers will need to send results to the factory floor. The ability to share data provides the opportunity for companies to undertake activities such as storing data and information for reuse, identifying storage technology, and defining resource registries. Categories of activities in this area include:
Planning for data and content reuse
Implementing data-sharing environments, including systems, policies, and procedures
Protecting sharable resources
Function #7: Retrieve
Due to the various types and formats of data being stored, having an optimal way to retrieve the data is important. Retrieval effectiveness will include identifying the right information, withdrawing the data at the right time, and providing it to the right user in the right format for its use. The categories of activities in the retrieve function are:
Ensuring accessibility of data resources
Presentation of data
Search and query of data through formal methods
Managing traceability of data
Common Requirements and Enabling Technologies
There are a number of requirements and enabling technologies that are common across the seven functions reviewed in this section. These examples reflect the interdependency of the functions and how complementary efforts better ensure that problems be addressed by taking a systems-level perspective. One example area is asset management. This is an important consideration whether tracking manufacturing equipment and tools, networking infrastructure, or deploying custom applications and software tools to meet production needs. A second area is information and data formats. This directly correlates to integration and interoperability challenges that cross all functions and remain a major cause for productivity issues. A third area is data availability and integrity. This area is now receiving needed attention in efforts to develop common practices for verification and validation of manufacturing data, such as the new ASME Subcommittee on Verification and Validation (V&V) for Manufacturing [16].
BARRIERS AND ENABLING TECHNOLOGIES
There are many significant barriers that can challenge manufacturers when addressing the requirements described previously. While some barriers can be easily addressed once properly understood, others may have conflicting goals that hinder effective resolution. However, recognizing these challenging barriers may be useful in creating new opportunities for appropriate standards and technology development.
Examples of significant barriers to achieve each decision-making function follow. Space does not permit us to be comprehensive, so instead we provide some example barriers that are often common for many manufacturers. We also describe potential solutions to these barriers where possible.
Function #1: Scope
Scoping requires that an organization’s mission, objectives, stakeholders, and activities are understood and clearly identified, communicated, and prioritized. One of the greatest challenges in scoping is addressing the multiple viewpoints that are involved in an analysis. Often a superficial understanding that rests on semantic misunderstandings prevails. The misunderstanding may not be clear until much further in the decision-making process, which may create faulty assumptions and wasted efforts.
Scoping challenges often occur when trying to deploy strategic objectives as operational improvements [18]. While many may understand a strategic objective such as cutting costs, it can be difficult to see the larger perspective where cost cutting in one area may increase costs in other areas or in the future. Identifying the operational areas to target for improvement is part of the scoping challenge. A number of technologies and standards for documenting processes can be employed to gain a clear understanding of the systems, software, and people involved in an analysis. However, the practice of using these technologies may be inconsistent. Good measures of the impact of different processes on the larger system can also help in scoping an analysis problem, but obtaining such measures can be difficult.
Conflicting goals are often created because of scoping challenges. As an example specific to manufacturing operations, consider a company embarking on an energy savings undertaking. Looking at energy use and energy saving potentials in isolation would very likely affect overall productivity. Whereas looking at productivity in isolation may overlook energy saving potentials. An instance of this phenomenon is seen in strategies being developed to control machine downtime so as to maximize productivity and minimize energy use to the extent possible.
Function #2: Identify
Identification barriers can arise from a number of issues most important of which is perhaps the complexity of manufacturing operations. Asset management, a key activity, is crucial to being able to identify appropriate systems and information for an analysis. For example, an analysis focused on discovering a particular type of environmental impact or a security vulnerability will be dependent on identifying the equipment that could potentially be involved. Asset management should address changes to any system in a timely manner to enable the identification of the resources needed for an analysis. Often asset management has been a very manual process. New technologies are allowing for more automated and accurate asset management. However, many cultural, procedural, and technical barriers can exist when deploying these technologies.
Many analyses require detailed information on the flows of material, energy, and information within the manufacturing enterprise, as well as the capabilities of various assets in terms of manufacturing performance and sensing and data reporting. This information is necessary for planning detailed analysis. For example, to understand energy consumption in a manufacturing facility, it can be useful to know what systems already monitor energy use and the level of detail at which this monitoring occurs to determine the need for additional sensors.
Another challenge is understanding the amount of data needed to support analysis. For example, the frequency of data collection from a sensor and the reliability of the sensor data can depend on several downstream considerations, such as the effectiveness of analytics, the impact of data transmission on network bandwidth, the amount of available data storage, and the affordability of solutions. In addition, as more data is collected, the means by which data is presented becomes another barrier to its utility.
Decreased costs, increased adoption of recognized standards, and improved technology can be helpful in addressing these barriers. For example, standards, such as ISO 22400 [19] for manufacturing operations management, can help identify data that needs to be collected for analysis.
Function #3: Collect
Connecting devices, applications, and machines to the network, making the devices and their information recognized and accessible to approved users, and protecting the devices from unauthorized access are some of the challenges manufacturers face. Data collection can be impeded or prevented entirely by a variety of barriers. For example, a machine tool can often be a “black box” that accepts commands but rarely provides rich data in response. It can be difficult for operators to know when actual process parameters (e.g., cutting speed, feed) meet the nominal process parameters requested. Other data may be “hidden” by the controller and inaccessible even to trained practitioners. Sometimes manufacturers can add sensors to capture this information, but it can be difficult to integrate these sensors without interfering with the operation of the machine and potentially voiding warrantees. Even if certain components are physically accessible, there may be no practical interface to provide access to data. Sometimes a vendor may intentionally hide information or limit export capability to lock customers into a proprietary tool [20]. Vendors can also be forced to develop solutions that are intentionally different to avoid infringing on patents. Since patents and patent overlap can be very complex, dangers of patent infringement are a particularly challenging barrier [21] and can apply to other functional areas as well.
Function #4: Transmit
While some data transmission is straightforward, much of it is difficult and will remain so for a variety of reasons. As an example, security requirements and practices stand as a barrier to transmission. Current security practices include isolating machines from a network if the machines present a significant risk to being accessed inappropriately. This is often the case for machine tools, many of which use outdated operating systems that are no longer supported by vendors. Even when machines are on a network, other barriers may be present, such as requiring protection by manual interaction for access (e.g., multifactor authentication) that intentionally cannot be automated.
Other barriers to transmission relate to the physical environment in a manufacturing facility. For instance, wireless signals do not always operate as efficiently as designed due to interference from the shop floor. Furthermore, as manufacturing becomes more reliant on timely access to data, infrastructure maintenance takes on greater importance.
Function #5: Analyze
Analysis faces many barriers including availability of the appropriate data and the ease of use of analysis applications. Changing analysis algorithms may require data that was previously thought to be valueless and discarded [22]. Some analysis can be used in real time while others require more processing time than is available in real time. While the later are still valuable, understanding how to integrate them into a system is still challenging. Some algorithms may be proprietary and patented, which can restrict use or make them too expensive. Some algorithms are based on heuristics without guarantees of performance, runtime, or space consumption limiting the applicability. Finally, some black-box-type algorithms (such as neural networks) provide no easy way to assess their performance, which can make their use unreliable. For more advanced analysis techniques, such as machine learning, reliable educational material on when and how to use them during operations is often lacking.
Function #6: Share
Barriers related to sharing range from policy to technology. On the policy side, deciding what can be shared and with whom is challenging. Too much sharing can create the risk of revealing trade secrets, while too little sharing may cause an organization to deal with duplication of efforts, people working at cross purposes, and missed opportunities. Another challenge is deciding what data, information, and metrics are most likely to be of benefit to the recipient since extra information may result in wasted processing effort. On the technology side having a common strategy for sharing results is important. Many solution providers are now offering cloud-based platforms for facilitating sharing but these do not necessarily address the complex archiving needs of an enterprise whose business depends on detailed engineering capabilities [23],[24]. Furthermore, tracability of products back to the specific processes used in their production is growing more important.
Another important barrier is understanding what partners within the supply chain can be trusted with what data. Partners may have other data or relationships that can use data in a way that is not expected. For example, access to inventory levels intended to give supply partners better preparation for ramping up manufacturing can be used by those same suppliers to negotiate more competitively. Some data can be sanitized, but figuring out what or how much sanitization is necessary can be time consuming and must be potentially revisited before each sharing event.
Function #7: Retrieve
Barriers to retrival limit the ability to find the right information at the right time. Challenges exist in addressing context-based methods for searching and managing the traceability of data. There are few methods to organize content in ways that are intuitive to practitioners, and few common practices for maintaining data provenance. For example, when data information resides in a variety of formats, some being proprietary, it can be difficult to bring them into a common analytic framework for further analysis. Difficulties arise in connecting data from different sources in terms of semantics as well as temporally. In addition, tracing the lineage of the data used in an analysis is important for authoritative purposes as well as understanding potential sources of error. Long-term archiving of data may be appropriate so that analysis can be repeated in the future. In addition, any translation of data is likely to result in some loss of content. For example, when creating visualizations for human consumption, details of the analysis are often not directly available.
Examples of Solutions to Overcome Barriers
Three types of solutions that address most barriers are standards, reference data, and technology. For example, dealing with multiple formats or multiple interfaces can be addressed with a standard. Similarly, technology advancements can provide solutions to some barriers. For example, improved modeling tools and methods allow for more effective and efficient simulations. Lastly, reference data can be helpful to implementors by saving them from the effort of exploring these ideas anew.
Admittedly, all of these approaches are limited to the degree by which they can surmount barriers and sometimes they can present new barriers themselves. While standards can be helpful, their development often takes considerable time and effort, and there is always the risk that the standard may not be adopted. Numerous organizations have evolved with different approaches to standards building as a result [5]. Still standards can themselves become a barrier. For example, there is no point to seek standardization for a technology that will have a relatively limited lifespan, especially when the time needed for a standard development effort exceeds the life of the technology. Indeed, premature standards can inadvertently lock users into inferior solutions.
An alternative to standards are “best practices,” where a group of companies or an industry sector agrees to a common set of implementation guidelines for a standard. Because the agreed-to best practices are not part of the “official” standard, they can be more easily modified in response to technological change or business drivers. An example of a best-practices effort in support of manufacturing is the CAx Implementor Forum, which is a group of Computer Aided Design software vendors, users, and solution providers who publish guidance for implementing ISO 10303-242. ISO 10303-242 is a standard for the representation and exchange of digital 3D design data with annotations that provides product and manufacturing information needed for fabrication 25,26. Another best-practices example is the MTConnect C++ Agent, which has been provided to enable implementation of the communications protocols of the standard [27].
Similarly, technology can also offer further challenges as well as solutions. When solutions work, they may come with trade-offs and often sacrifice flexibility due to a lack of interoperability between competing vendor solutions.
Wireless technology is an example of several of these issues. Wireless was a technological advance over wired connections that allowed mobile solutions as well as easier placement of sensors and controllers. Very quickly after its introduction, standards were offered to address incompatibility issues and proprietary lock-in. However, there are currently many incompatible wireless standards including some with proprietary implementations, such as IEEE 802.15.1 (Bluetooth Classic), Bluetooth Low Energy, IEEE 802.11 (WLAN), and IEEE 802.15.4 (ZigBee, WirelessHART, ISA 100) [28].
SUMMARY
The successful deployment and use of data-driven decision-making and other smart manufacturing technologies will depend on educating manufacturers and technology developers about the best ways to leverage the value of these solutions. Manufacturers need support to navigate the breadth of solutions in the market, and technology developers must understand the most compelling use cases to ensure that their solutions meet the needs of industry. The first step towards assuring the performance of smart manufacturing technologies is to develop a means for the manufacturing community to pool its knowledge and collaborate to identify problems and collect solutions and best practices. Helu et al. [10] proposed a collective knowledgebase to provide a means of achieving this goal. We have extended the idea in this paper by describing a framework to organize the content of the knowledgebase and by identifying some common activities for and barriers to data-driven decision making in manufacturing.
While the proposed framework has focused on data-driven decision making, it may be used for other aspects of smart manufacturing technology, such as increased specialization to accommodate advanced materials, increased use of model-based engineering [29],[30], and increased deployment of collaborative robotic systems. Future work will focus on expanding the content in the framework as well as providing more depth to the initial content generated for this research. We hope to engage the larger manufacturing community in this effort to ensure its comprehensiveness and accuracy. Bringing together experts, though, requires an effective operational model for the knowledgebase, which is another goal of future work. If successful, we believe that the knowledgebase can spur innovation by identifying high impact areas for standards and technologies that help deliver on the promise of smart manufacturing and ensure the success of manufacturing.
Acknowledgments
ACKNOWLEDGMENTS AND DISCLAIMER
The authors would like to acknowledge Kiwook Jung and Swee Leong for their support in completing this research. Certain commercial systems are identified in this paper. Such identification does not imply recommendation or endorsement by the National Institute of Standards and Technology. Nor does it imply that the products identified are necessarily the best available for the purpose.
Contributor Information
Moneer Helu, National Institute of Standards and Technology, Gaithersburg, Maryland, USA.
Don Libes, National Institute of Standards and Technology, Gaithersburg, Maryland, USA.
Joshua Lubell, National Institute of Standards and Technology, Gaithersburg, Maryland, USA.
Kevin Lyons, National Institute of Standards and Technology, Gaithersburg, Maryland, USA.
KC Morris, National Institute of Standards and Technology, Gaithersburg, Maryland, USA.
References
- 1.Davidson M, Goodwin G. 2013–2014 Manufacturing Metrics that Really Matter Summary Report. LNS Research; 2014. [accessed 05/12/2016]. http://www.lnsresearch.com/research-library/research-articles/2013-2014-manufacturing-metrics-that-really-matter-summary-report. [Google Scholar]
- 2.Hopkins MS, Kruschwitz N, Haanaes K, Kong MT, Arthur D, Reeves M. MIT Sloan Management Review. Spring; 2011. New Sustainability Study: The ‘Embracers’ Seize Advantage. [Google Scholar]
- 3.AMP2.0 Steering Committee. [accessed 05/12/2016];Report to the President: Accelerating U.S. Advanced Manufacturing. 2014 https://www.whitehouse.gov/sites/default/files/microsites/ostp/PCAST/amp20_report_final.pdf.
- 4.Lu Y, Morris K, Frechette S. Standards Landscape and Directions for Smart Manufacturing Systems. 2015 IEEE International Conference on Automation Science and Engineering (CASE); Gothenburg, Sweden. 2015. pp. 998–1005. [Google Scholar]
- 5.Lu Y, Morris K, Frechette S. NIST Technical Note 8107. National Institute of Standards and Technology; Gaithersburg, MD: 2016. Current Standards Landscape for Smart Manufacturing Systems. [Google Scholar]
- 6.O’Marah K, Manenti P. The Internet of Things Will Make Manufacturing Smarter. [accessed 05/12/2015];Industry Week. 2014 http://www.industryweek.com/manufacturing-smarter.
- 7.Accenture. [accessed 02/15/2016];CEO Briefing 2015: From Productivity to Outcomes: Using the Internet of Things to drive future business strategies. 2015 https://www.accenture.com/t20150527T211103__w__/fr-fr/_acnmedia/Accenture/Conversion-Assets/DotCom/Documents/Local/fr-fr/PDF_5/Accenture-CEO-Briefing-2015-Productivity-Outcomes-Internet-Things.pdf.
- 8.Littlefield M, Goodwin G. The Industrial Internet of Things and Big Data Analytics: A Coming Manufacturing Revolution. LNS Research; 2015. [accessed 05/12/2016]. http://www.lnsresearch.com/research-library/research-articles/the-industrial-internet-of-things-and-big-data-analytics-a-coming-manufacturing-revolution. [Google Scholar]
- 9.Waurzyniak P. Manufacturing Engineering. 2015. Oct, Why Manufacturing Needs Real-Time Data Collection; pp. 53–61. [Google Scholar]
- 10.Helu M, Morris K, Jung K, Lyons K, Leong S. Identifying Performance Assurance Challenges for Smart Manufacturing. Manufacturing Letters. 2015;6:1–4. doi: 10.1016/j.mfglet.2015.11.001. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Stouffer K, Pillitteri V, Lightman S, Abrams M, Hahn A. NIST Special Publication 800–82r2. National Institute of Standards and Technology; Gaithersburg, MD: 2015. Guide to Industrial Control Systems (ICS) Security. [Google Scholar]
- 12.MTConnect Institute. [accessed 05/12/2016];MTConnect v. 1.3.1. 2015 http://www.mtconnect.org/standard/
- 13.Albert M. MT Connect: Two Shops Share Their Experience. Modern Machine Shop; 2012. Aug, [accessed 05/12/2016]. http://www.mmsonline.com/articles/mt-connect-two-shops-share-their-experience. [Google Scholar]
- 14.Helu M, Weiss B. The Current State of Sensing, Health Management, and Control for Small-to-Medium-Sized Manufacturers. Proceedings of the ASME 2016 International Manufacturing Science and Engineering Conference; Blacksburg, VA. 2016. to appear. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.MITRE Corporation. [accessed 05/12/2016];Common Weakness Enumeration. 2015 https://cwe.mitre.org/
- 16.ASME. [accessed 05/12/2015];Committee Page: V&V 50 Verification and Validation of Computational Modeling for Advanced Manufacturing. 2016 https://cstools.asme.org/csconnect/CommitteePages.cfm?Committee=101978604.
- 17.National Institute of Standards and Technology. [accessed 05/12/2016];Framework for Improving Critical Infrastructure Cybersecurity: Version 1.0. 2014 http://www.nist.gov/cyberframework/upload/cybersecurity-framework-021214-final.pdf.
- 18.Jung K, Morris KC, Lyons KW, Leong S, Cho H. Mapping Strategic Goals and Operational Performance Metrics for Smart Manufacturing Systems. Procedia Computer Science. 2015;44:184–193. [Google Scholar]
- 19.ISO, 2014, “Automation systems and integration – Key performance indicators (KPIs) for manufacturing operations management – Part 2: Definitions and descriptions,” ISO 22400-2:2014.
- 20.Commission of the European Communities. C(2004)900 final. Brussels, Belgium: 2004. Commission Decision of 24.03.2004 relating to a proceeding under Article 82 of the EC Treaty. [Google Scholar]
- 21.Shapiro C. Navigating the Patent Thicket: Cross Licenses, Patent Pools, and Standard Setting. In: Jaffe AB, et al., editors. Innovation Policy and the Economy. Vol. 1. MIT Press; Cambridge, MA: pp. 119–150. [Google Scholar]
- 22.Libes D, Shin S, Woo J. Considerations and Recommendations for Data Availability for Data Analytics for Manufacturing. 2015 IEEE International Conference on Big Data (Big Data); Santa Clara, CA. 2015. pp. 68–75. [Google Scholar]
- 23.Barbau R, Lubell J, Rachuri S, Foufou S. Towards a Reference Architecture for Archival Systems: Use Case With Product Data. ASME Journal of Computational Information Science in Engineering. 2014 Apr 28;14(3):031005. [Google Scholar]
- 24.ISO, 2012, “Space data and information transfer systems – Open archival information system (OAIS) – Reference model,” ISO 14721:2012.
- 25.PDES, Inc. and ProSTEP iViP. [accessed 05/06/2016];CAx Implementor Forum. n.d https://cax-if.org/index.html.
- 26.Lipman R, Lubell J. Conformance Checking of PMI Representation in CAD Model STEP Data Exchange Files. Computer-Aided Design. 2015;66:14–23. [Google Scholar]
- 27.MTConnect User’s Portal. [accessed 05/12/2016];MTConnect C++ Agent. 2015 http://mtcup.org/wiki/C%2B%2B_Agent.
- 28.Andersson M. Wireless Technologies for Industrial Applications, Version 2.2. connectBlue; 2013. [accessed 05/12/2016]. http://www.connectblue.com/fileadmin/Connectblue/Web2006/Documents/White_papers/Industrial_Bluetooth.pdf. [Google Scholar]
- 29.Lubell J, Chen K, Horst J, Frechette S, Huang P. NIST Technical Note 1753. Gaithersburg, MD: 2012. Model Based Enterprise/Technical Data Package Summit Report. [Google Scholar]
- 30.Hedberg T, Jr, Lubell J, Fischer L, Maggiano L, Barnard Feeney A. Testing the Digital Thread in Support of Model-Based Manufacturing and Inspection. Journal of Computational and Information Science in Engineering. 2016 Mar 8;16(2):021001. doi: 10.1115/1.4032697. [DOI] [PMC free article] [PubMed] [Google Scholar]