Abstract
With the evolution of communication technology and the exponential increase of mobile devices, the ubiquitous networking allows people to use our data and computing resources anytime and everywhere. However, numerous security concerns and complicated requirements arise as these ubiquitous networks are deployed throughout people’s lives. To meet the challenge, the user authentication schemes in ubiquitous networks should ensure the essential security properties for the preservation of the privacy with low computational cost. In 2017, Chaudhry et al. proposed a password-based authentication scheme for the roaming in ubiquitous networks to enhance the security. Unfortunately, we found that their scheme remains insecure in its protection of the user privacy. In this paper, we prove that Chaudhry et al.’s scheme is vulnerable to the stolen-mobile device and user impersonation attacks, and its drawbacks comprise the absence of the incorrect login-input detection, the incorrectness of the password change phase, and the absence of the revocation provision. Moreover, we suggest a possible way to fix the security flaw in Chaudhry et al’s scheme by using the biometric-based authentication for which the bio-hash is applied in the implementation of a three-factor authentication. We prove the security of the proposed scheme with the random oracle model and formally verify its security properties using a tool named ProVerif, and analyze it in terms of the computational and communication cost. The analysis result shows that the proposed scheme is suitable for resource-constrained ubiquitous environments.
Introduction
The development of communication technology provides efficient services based on sustainable infrastructures that improve the human quality of life. As smart devices such as smartphones, smart watches, and tablets become widely available, it has become possible to access various services and to allow people to utilize information anytime and anywhere. Also, the ubiquitous smart society, in which the combining of the data from smart devices and various sensors enables intelligent communication, is being built in the form of the smart city [1, 2].
In this smart city, the ubiquitous network provides useful information and resources for remote operations such as human-resource management and enterprise-resource management by connecting to a home agent (HA) through the roaming of a foreign agent (FA) while a citizen is moving [3, 4].
For a user mobile device to be able to remotely access the authority of various services via the HA, remote user authentication is required. In the remote authentication scheme, the user identifier is required to verify that the user is legitimate. This identifier such as an ID and password is associated with user privacy, and it can seriously affect the user security when they are leaked; therefore, the login and authentication requests of the user that are transmitted to the public channel with the identifier can be easily targeted by an attacker. Due to this issue, the user anonymity and untraceability should be maintained in the remote authentication process [5].
In addition, after the user login and authentication requests are accepted, the participants on the ubiquitous network must share the same session key for secure future communications. At this time, to establish a secure session key from an attacker’s spoofing attack that threatens the security of the participants, the key should not be directly distributed from one node to the other. The key agreement must be performed after a mutual authentication in which the participants identify each other’s legitimacy [6].
In recent years, authentication techniques [7–13] have been frequently proposed. A two-factor authentication scheme using the user ID and password is widely used. However, the password-based authentication scheme has the security issue that it is vulnerable to password-guessing attacks. A key technology to overcome this security issue is a biometric-based three-factor authentication method. Since biometric keys (irises, fingerprints, hand geometry, palm prints, etc.) represent unique human characteristics, they have the following advantages [14]: (1) Biometric keys cannot be lost or forgotten; (2) it is extremely difficult to forge or distribute biometric keys; (3) biometric keys maintain uniqueness; and (4) it is difficult to guess biometric keys. Thus, it is obvious that the biometric-based user authentication methods are more secure and reliable than the traditional password-based user authentication methods.
Combining password and biometric key makes it difficult to guess the user credentials. Because of this, three-factor authentication schemes that use the uniqueness of users have recently been proposed [15, 16]. However, there are some caveats to be noted when practically applying biometric-based authentication techniques. First, as mentioned, biometrics is a human characteristic, so it cannot be changed, unlike a password. Consequently, if it is leaked, it will cause serious privacy problems [17]. Therefore, the original biometric template or the feature-vector value of users should not be directly exported. To enhance the security, many biometric-based authentication schemes have been proposed using techniques for extracting user’s biometrics into a random value such as a bio-hash or a fuzzy-extractor [18–20].
Over the past few years, a number of authentication scheme have been proposed to support the roaming in ubiquitous networks. In 2004, Zhu and Ma [21] presented the first password-based authentication scheme for ubiquitous networks to protect the security of ubiquitous networks, but Lee et al. [22] then demonstrated that this scheme does not achieve a perfect backward secrecy and a mutual authentication, and also its failure to resist the forgery attack. To enhance the security of Zhu and Ma’s scheme [21], Lee et al. [22] proposed an improved password-based authentication scheme. In 2008, however, Wu et al. [23] proved that the schemes of both Zhu and Ma [21] and Lee et al. [22] do not preserve the user anonymity, and the latter scheme does not achieve a perfect backward secrecy; additionally, Wu et al. [23] proposed simple solutions to fix the drawbacks of the two schemes. In 2012, however, Mun et al. [24] showed that the scheme of Wu et al. [23] does not achieve the user anonymity and a perfect forward secrecy and they presented an enhanced password-based authentication scheme to overcome these weaknesses. Unfortunately, in 2014, Zhao et al. [25] then proved that the scheme of Mun et al. [24] is vulnerable to various attacks.
In 2011, He et al. [26] proposed a lightweight password-based authentication scheme, claiming that it satisfies the various security requirements for ubiquitous networks. In 2013, however, Jiang et al. [27] proved that He et al.’s scheme [26] does not prevent the off-line password guessing, server-spoofing, replay, and privileged-insider attacks, and they also presented an enhanced password-based authentication scheme to overcome these weaknesses. Wen et al. [28] subsequently showed that Jiang et al.’s scheme [27] is vulnerable to stolen-verifier, server-spoofing, replay, and denial-of-service attacks and its failure regarding the provision of the forward secrecy. In 2015, in a different study of Farash et al. [29], and Gope and Hwang [30], it was common that Wen et al.’s scheme [28] is insecure against the known attacks. Then, Farash et al. [29], and Gope and Hwang [30] independently introduced the improved password-based authentication schemes that prevent the various attacks. Nevertheless, Wu et al. [31] showed both schemes of Farash et al. [29], and Gope and Hwang [30] are vulnerable to various attacks. In addition, Chaudhry et al. [32] also found a number of security pitfalls in Farash et al.’s scheme [29] such as a user-anonymity violation and the disclosure of the secret parameters of the mobile node (MN) and the session key.
Contributions of the paper
Recently, Chaudhry et al. [32] proposed a privacy-preserving password-based authentication scheme for roaming in ubiquitous networks to solve the security issues of Farash et al.’s scheme [29]. They claimed that their scheme is secure against the various known attacks and is lightweight compared with the earlier scheme of Farash et al. [29]. However, We found that Chaudhry et al.’s scheme [32] is still vulnerable to several attacks; therefore, in this paper, we provide the proof that Chaudhry et al.’s scheme [32] is vulnerable to stolen-mobile devices and user impersonation attacks, and has drawbacks to the absence of the incorrect login-input detection, incorrect password change phase, and the absence of the revocation-process provision. To fix the security flaw of the scheme of Chaudhry et al. [32], we present an improved biometric-based authentication scheme for roaming in ubiquitous networks in this paper. In addition, to achieve the three-factor authentication that protects the user’s biometrics, a bio-hash technique is applied in the proposed scheme whenever the user imprints his/her biometrics on a mobile device. Furthermore, we perform formal and informal analyses to prove that the proposed scheme meets the various security requirements, and conduct the comparisons in terms of the computational and communication cost to show the efficiency of the proposed scheme.
Organization of the paper
The remainder of this paper is organized as follows. In Section 2, a number of preliminaries are introduced. A brief review of the scheme of Chaudhry et al. [32] is presented in Section 3, and a cryptanalysis of Chaudhry et al. [32]’s scheme is presented in Section 4. The proposed scheme is presented in Section 5. The proposed scheme is analyzed in terms of formal and informal security in Section 6. Data from the comparisons of the performance of the proposed scheme with other related works are presented in Section 7. The conclusion of this paper is provided in Section 8.
Preliminary knowledge
This section introduces the requisite basic knowledge for the attainment of an understanding of the authentication process in ubiquitous networks, adversarial models, security requirements, and bio-hash functions.
User authentication in ubiquitous networks
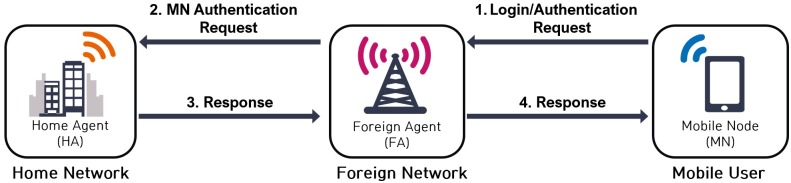
To enable the roaming service in ubiquitous networks, MN and FA perform a mutual authentication and share the session key with the support of the HA. The brief description of the user authentication process that is depicted in Fig 1 is as follows:
MN sends a login and authentication request message to FA while it visits foreign networks.
After it receives the request message from MN, FA transmits it to HA for the authentication of MN.
HA authenticates MN by checking the received message from FA, and it responds accordingly to FA.
FA sends a response to MN, and then both MN and FA authenticate each other.
Fig 1. User authentication process in ubiquitous networks.
Adversarial model
For the analysis of the security of Chaudhry et al. and the proposed scheme in this paper, we consider the adversarial model with following the capacity of adversary:
The adversary has full control over the public communication channel, which means that can eavesdrop, insert, delete, alter, or intercept any of the transmitted messages of the public channel.
If obtains a stolen or lost mobile device of a user in some way, he/she is able to extract the secret parameters from the device using side-channel attacks [33–36].
is capable of enumerating off-line all of the possible items in the Cartesian product within polynomial time, where and denote the dictionary spaces of the identity and password, respectively [37, 38].
Security requirements
Based on recent research efforts [6, 39–41], a biometrics-based authentication scheme for roaming in ubiquitous networks should meet the following security requirements against the adversarial model and the functional requirements to provide user-friendliness:
User anonymity: The scheme must ensure the user anonymity to preserve the privacy of MN, i.e., should not be able to discover the real identity of MN.
Unlinkability: To provide greater security for the user’s privacy, the scheme should ensure unlinkability, i.e., should not be able to trace the user’s actions.
Mutual authentication: The schemes should support mutual authentication to ensure the legitimacy of each participant, i.e., MN, FA, and HA are capable of authenticating each other in the authentication phase.
Session key agreement: When the scheme permits the establishment of a session key between each of the participants, the session key that is used to encrypt and decrypt messages in the future communications should be fresh and provide the forward secrecy.
Three-factor secrecy: To ensure the secrecy of the user’s private keys, the scheme should provide three-factor (e.g., identity, password, and biometrics) secrecy. The should not be able to extract one secret value from the remaining two factors.
Resilience to various attacks: The scheme should provide all major security goals and should be resistant to different types of the known attacks.
Bio-hash function
The biometrics provides a unique identification method to solve the security vulnerabilities of passwords, pins, and tokens that are easy to forget or can be stolen. The imprint biometric characteristics may be slightly different each time due to a variety of reasons such as the user’s dry or cracked skin, and the presence of dirt on the imprint sensor [42]. Therefore, high false rejection of genuine users that results in a denial of access often occur in the evaluation of biometric systems, and this consequently impacts on the usability of a system [43]. To resolve the problem of high false rejection instances, Jin et al. [44] proposed a two-factor authenticator in 2004 that is based on the iterated inner products between a tokenized pseudorandom number and the user-specific fingerprint features. To achieve this, a set of user-specific compact codes called the bio-hash code can be created. The bio-hash is a random mapping of biometric feature onto binary strings with user-specific tokenized pseudorandom numbers. In recent times, many authentication schemes using bio-hash have been proposed [45–47]. According to the recent bio-hash researches [48–51], the execution times of bio-hash are considered to be the same as the one-way hash function. In contrast, the execution time of the fuzzy extractor that is also generally used in biometric-system is considered to be the same as the elliptic-curve cryptography (ECC) [52]. Bio-hash is an effective technique for biometrics-based authentication schemes [53], and it is convenient mechanisms for small devices such as smart cards and mobile devices.
Review of Chaudhry et al.’s scheme
This section discusses Chaudhry et al.’s [32] user authentication scheme for roaming in ubiquitous networks. This scheme consists of the following three phases: (1) registration, (2) login and authentication, and (3) password change. All of the notations that are used in this paper are presented in Table 1.
Table 1. Notations.
| Values | Description |
|---|---|
| MNi | Mobile node |
| FAj | Foreign agent |
| HAk | Home agent |
| IDmi, IDfj, IDhk | Identities of MNi, FAj, HAk |
| PWmi | Password of MNi |
| BIOmi | Biometrics of MNi |
| Tx | Timestamp of x |
| nx | Random number of x |
| rx | Random nonce for a specific purpose |
| SKx | Session key of x |
| Ek(⋅), Dk(⋅) | Symmetric encryption/decryption |
| h(⋅) | Hash function |
| H(⋅) | Bio-hash function |
| || | Concatenation |
| ⊕ | XOR operation |
| KF,H | Pre-shared secret key between FAj and HAk |
| KH | Private key of HAk |
Registration phase
In the registration phase, MNi registers with HAk and the following operations are performed:
-
MNi → HAk: IDmi, h(PWmi||rA||IDmi)
MNi selects his/her identity IDmi and password PWmi, and generates rA. MNi then computes h(PWmi||rA||IDmi) and sends a registration request message 〈IDmi, h(PWmi||rA||IDmi)〉 to HAk via a secure channel.
-
HAk → MNi: PIDmi, Ami
HAk verifies whether MNi’s IDmi is valid. If it is valid, HAk computes the following equations:(1)
HAk then sends EIDmi and Ami to MNi via a secure channel.(2) MNi retains the secret parameters EIDmi, Ami and rA in the mobile device.
Login and authentication phase
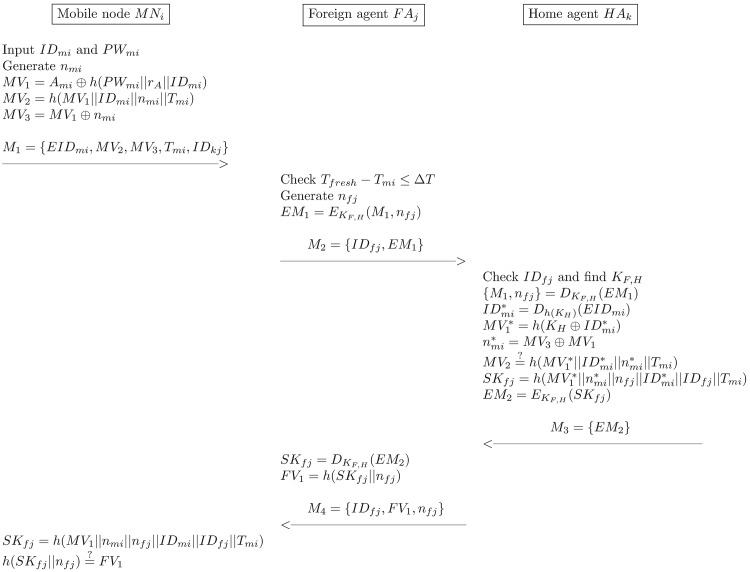
In this phase, MNi and FAj perform a mutual authentication to establish a session key with the support of MNi’s HAk. It is assumed that each pair of FAj and HAk share pre-shared key KF,H. The details of the login and authentication procedure, which are depicted in Fig 2 are as follows:
-
MNi → FAj: M1 = 〈PIDmi, MV2, MV3, Tmi, IDhk〉
MNi enters his/her IDmi and PWmi, generates the random number nmi, and computes the following equations:(3) (4)
MNi sends the login request message M1 = 〈EIDmi, MV2, MV3, Tmi, IDhk〉 to FAj via a public channel.(5) -
FAj → HAk: M2 = 〈IDfj, EM1)〉
FAj checks the freshness of Tmi. If it is fresh, FAj generates the random number nfj and computes as follows:
FAj then sends the message M2 = 〈IDfj, EM1)〉 to HAk.(6) -
HAk → FAj: M3 = 〈EM2)〉
HAk checks IDfj and finds its corresponding KF,H. To obtain M1 and nfj, HAk decrypts EM1 and computes the following equations:(7) (8) (9)
Then, HAk checks the validity of the following equation:(10)
If Eq (11) does not hold, this phase is terminated; otherwise, HAk computes as follows:(11) (12)
Lastly, HAk sends the message M3 = 〈EM2〉 to FAj.(13) -
FAj → MNi: M4 = 〈IDfj, FV1, nfj〉
To obtain SKfj, FAj decrypts the received message EM2 and computes as follows:(14)
Then, FAj sends the message M4 = 〈IDfj, FV1, nfj〉 to MNi.(15) - To check validity of the session key, MNi computes the following equations:
(16)
If Eq (17) does not hold, MNi terminates connection; otherwise, MNi accepts FAj as legal and authenticated.(17)
Fig 2. The login and authentication phase of Chaudhry et al.’scheme.
Password change phase
MNi inputs IDmi, a old password and a new password into his/her mobile device. The mobile device then computes the following equations:
| (18) |
| (19) |
Lastly, the mobile device replaces Ami with .
Cryptanalysis of Chaudhry et al.’s scheme
This section consists of the cryptanalysis of Chaudhry et al.’s scheme [32].
Stolen-mobile device attack
Under the previously explained adversarial model, it is assumed that somehow acquires MNi’s mobile device, extracts the secret parameters, and captures the login request message M1. Using the extracted parameters and the captured messages, can attempt to guess MNi’s identity and password until the correct identity and password are found.
In [33, 34, 37, 38, 54], the identity and password can be guessed simultaneously after the user’s device is stolen by ; therefore, it is prudent to consider off-line identity and password guessing attacks.
Based on [37], . The time complexity to determine a identity and password is linear to and because the more candidate data the attacker has, the more that matching operations are required to determine the desired value.
To demonstrate the vulnerability of Chaudhry et al.’s scheme [32] to the stolen-mobile device attack, the following scenario is used:
eavesdrops the previous login messages M1 = 〈EIDmi, MV2, MV3, Tmi〉, and compromises the secret parameters 〈Ami, EIDmi, rA〉 from the mobile device.
selects any of the identity and password candidates and .
computes .
compares .
If the comparison shows they are equal, successfully guesses the correct IDmi and PWmi. Otherwise, selects another identity and password, and repeats the steps 3 and 4 until he/she finds the correct identity and password.
In Chaudhry et al.’s scheme [32], the time complexity of the guessing attack process is , where Th is the execution time of the hash operation and TXOR is the execution time of the exclusive-or operation. Therefore, the time complexity of the guessing attack in Chaudhry et al.’s scheme is not negligible, and their scheme is consequently vulnerable to the stolen-mobile device attack.
User impersonation attack
This subsection presents a demonstration of the way that Chaudhry et al.’s scheme [32] allows to impersonate a legal user if obtains the MNi’s identity and password through a guessing attack, as presented in the previous subsection, as follows:
obtains the secret parameters 〈Ami, EIDmi, rA〉, correctly guessing the identity and password of MNi by completing the stolen-mobile device attack.
- The mobile device of generates the random number nai, and computes the following equation:
sends the login request message to FAj, where TA is the current timestamp of . - Because of the validation of , FAj and HAk successfully proceed the subsequent steps of the authentication phase. Lastly, FAj sends the message M4 = 〈IDfj, FV1, nfj〉 to MNi, but receives M4 and computes the following equations:
(20)
If Eq (21) holds, has successfully established a session key with FAj.(21)
Therefore, Chaudhry et al.’s scheme [32] is vulnerable to the user impersonation attack.
Absence of the incorrect login-input detection
The detection of the incorrect login inputs must be performed at the beginning of the login phase. However, Chaudhry et al.’s scheme [32] does not support the incorrect input detection during the login and authentication phase. In their scheme, the MNi sends the message M1 without verifying the correctness of the IDmi and PWmi. Even if MNi mistakenly enters the wrong and , the mobile device can still compute , and . As a result, an invalid form of the login request message, M1, is transmitted to HAk through FAj, thereby resulting in unnecessary computations and communication costs.
Incorrectness of the password change phase
Chaudhry et al.’s scheme [32] allows the user to change his/her password easily without any server assistance. However, in the password change phase, the mobile device does not check the accuracy of the old password when MNi enters the old and new passwords to replace the old password with a new password. If MNi enters the old password incorrectly, an incorrect MV1 is computed with Eq (18), and an incorrect is also computed with Eq (19). As a result, h(KH ⊕ IDmi) will be damaged beyond the possibility of a restoration, thereby causing HAk’s rejection of MNi in the future authentication phase.
No provision for revocation
The revocation of a stolen or lost mobile device is essential for the practical deployment of smart card-based authentication schemes [55]. If a legal MNi’s mobile device is lost or stolen, some kind of mechanism must be in place to prevent the misuse of the mobile device. To address this problem, the server needs to maintain the identity information that will serve as the basis for the detection of the invalid mobile device [56]. However, Chaudhry et al.’s scheme [32] scheme does not take this feature into consideration.
Proposed scheme
This section contains the proposal for the improved and anonymous biometrics-based authentication scheme for roaming in ubiquitous networks. The proposed scheme consists of the following three phases: (1) registration, (2) login and authentication, (3) password change, and (4) mobile-device revocation.
Registration phase
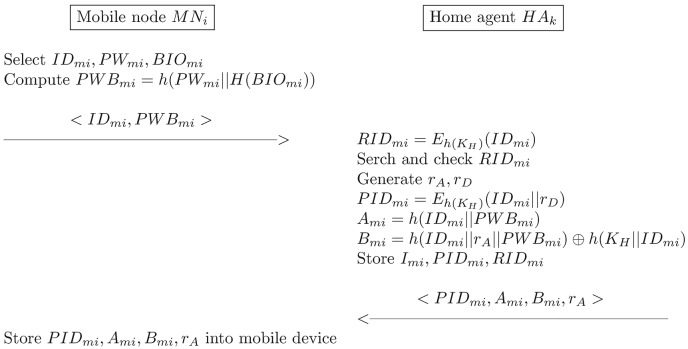
The registration phase for the mobile user MNi that are illustrated in Fig 3 involves the following operations:
-
MNi → HAk: IDmi, PWBmi
MNi selects his/her IDmi and PWmi and inputs BIOmi. MNi then computes the following equation:
MNi subsequently sends a registration request message 〈IDmi, PWBmi〉 to HAk via a secure channel.(22) -
HAk → MNi: PIDmi, Ami, Bmi, rA
HAk then verifies the identity of MNi and computes the following equation:
HAk searches RIDmi in the database to verify the presence of an already registered user with the same IDmi; if this is verified, HAk requests a new identity from MNi. Otherwise HAk gernerates rA and rD, and computes the following equations:(23) (24) (25)
If MNi is a new user, HAk sets Imi to zero, otherwise, Imi = Imi + 1. HAk then stores Imi, PIDmi, and RIDmi as a tuple in the database, and it sends 〈PIDmi, Ami, Bmi, rA〉 to MNi via a secure channel.(26) MNi stores all of the received parameters into the mobile device.
Fig 3. The registration phase of the proposed scheme.
Login and authentication phase
In this phase, MNi and FAj perform a mutual authentication to establish a session key with the support of MNi’s HAk. It is assumed here that each pair of FAj and HAk share the pre-shared key KF,H. The details of the login and authentication procedure that are illustrated in Fig 4 are as follows:
-
MNi → FAj: M1 = 〈PIDmi, MV2, MV3, IDhk〉
MNi enters his/her IDmi, PWmi, and BIOmi, and it then computes as follows:
HAk then checks the validity of:(27)
If Eq (28) does not hold, MNi terminates the user’s login request. Otherwise, MNi generates nmi and computes the following equations:(28) (29) (30)
MNi then sends the login request message M1 = 〈PIDmi, MV2, MV3, IDhk〉 to FAj.(31) -
FAj → HAk: M2 = 〈IDfj, FV2, FV3, M1〉
FAj generates the random number nfj and computes the following equations:(32) (33)
FAj sends the message M2 = 〈IDfj, FV2, FV3, M1〉 to HAk.(34) -
HAk checks IDfj to find its corresponding KF,H and computes the following equations:
(35) (36)
If Eq (37) does not hold, this phase is terminated; otherwise, HAk accepts FAj as legitimate. HAk then computes the following equations:(37) (38) (39) (40)
If Eq (41) does not hold, this phase is terminated; otherwise, HAk accepts MNi as legitimate. HAk then generates and computes the following equations:(41) (42) (43) (44)
HAk then replaces PIDmi with , and it then sends the message to FAj.(45) -
FAj computes the following equations:
(46)
If Eq (47) does not hold, FAj terminates the connection; otherwise, FAj computes the following equation:(47)
FAj then sends the message to MNi.(48) - MNi computes the following equations to check the validity of the session key:
(49) (50)
If Eq (51) does not hold, MNi terminates the connection; otherwise, MNi accepts FAj as legal and authenticated. That is, MNi, FAj and HAj have all successfully established the same session key, SK. Lastly, MNi replaces PIDmi with .(51)
Fig 4. The login and authentication phase of the proposed scheme.
Password change phase
In this phase, MNi changes its password on the mobile device without the help of the HA. The details of the password change phase that are illustrated in Fig 5 are as follows:
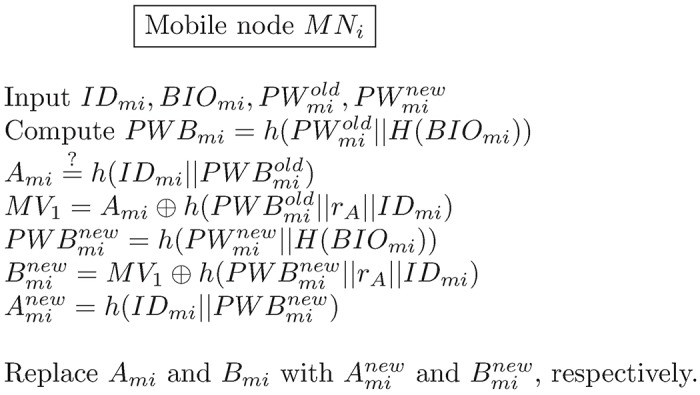
- MNi inputs IDmi, BIOmi, a old password and a new password into his/her mobile device. MNi then computes the following equations:
(52)
If Eq (57) does not hold, MNi terminates this phase; otherwise, MNi computes the following equations:(53) (54) (55) (56)
Finally, MNi replaces and with and , respectively.(57)
Fig 5. The password change phase of the proposed scheme.
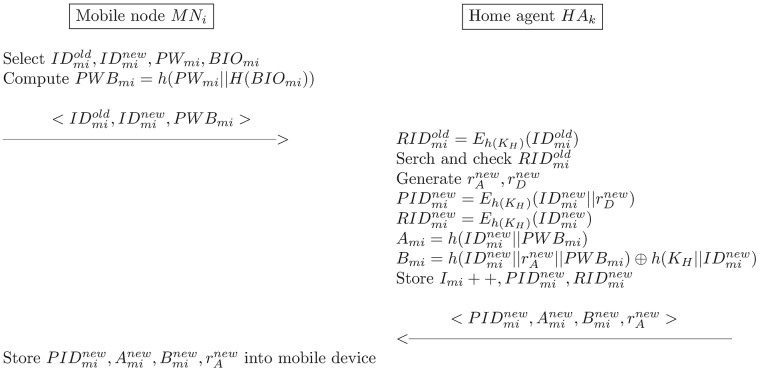
Mobile device revocation phase
To recover a stolen/lost mobile device or a long-term key of MNi, the mobile device revocation mechanism that is illustrated in Fig 6 is activated as follows:
-
If MNi wants to revoke and reissue a secret parameter, MNi selects an old identity and a new identity , inputs a new password and BIOmi into his/her mobile device. MNi then computes the following equation:
MNi subsequently sends a revocation request message to HAk via a secure channel.(58) -
HAk → MNi: Ami, Bmi
HAk then verifies the identity of MNi and computes the following equation:
HAk searches in the database to verify the presence of a registered user. If this is the case, HAk generates the new random nonces and , and computes the following equations:(59) (60) (61)
HAk updates Imi, PIDmi, and RIDmi with , and , respectively. It then sends to MNi via a secure channel.(62) Finally, MNi stores all of the received parameters into the mobile device.
Fig 6. The revocation phase of the proposed scheme.
Security analysis
In this section, a security analysis of the proposed scheme is performed using formal and informal verification methods. The formal analysis is conducted using automatic analysis tool named ProVerif and a random oracle model.
Formal verification using ProVerif
ProVerif is an automatic tool for analyzing cryptographic protocols according to the formal model (the so-called Dolev–Yao model). It supports a wide range of cryptographic primitives that are defined by rewrite rules or equations, as follows: asymmetric and symmetric en/decryption, digital signatures, and hash functions. This tool can prove the various security properties as follows: secrecy, authentication, and process equivalences of the protocol with unlimited sessions and message space [57].
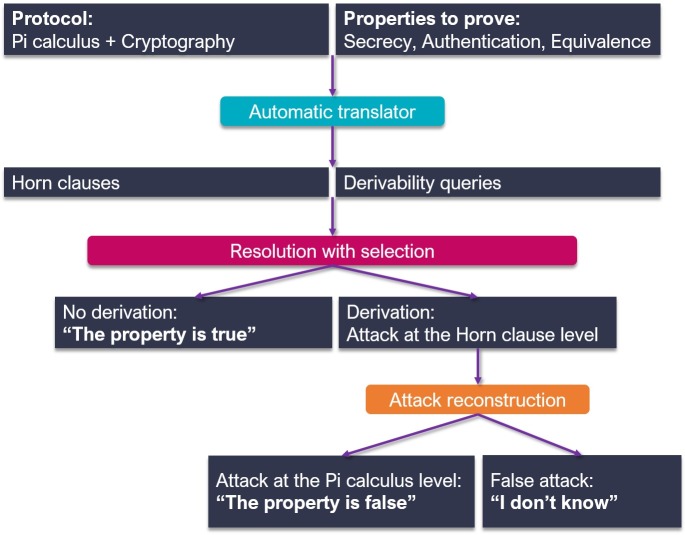
The verification structure of ProVerif is illustrated in Fig 7. First, ProVerif takes as its input a protocol description to perform a verification in a dialect of the applied pi calculus, which is an extension of the pi-calculus and is a language for describing and analyzing protocols.
Fig 7. Structure of ProVerif.
It also takes an input the security properties that are being proven here. It then automatically translates this protocol description into Horn clauses and the security properties into derivability queries on these clauses, and it determines whether a fact can be proved from these clauses using an algorithm that is based on a resolution with a free selection. If the fact is not derivable, the corresponding security properties are proved. If the fact is derivable, the protocol may be vulnerable to an attack against the corresponding security properties. Actually, the derivation either corresponds to a real attack or a false attack, since the problem of the protocol verifications for an unbounded number of sessions is not decidable.
Recently, many researchers [58–61] have used ProVerif to verify the security of the schemes for the key agreement and authentication. In this section, the security of the proposed scheme is proven using ProVerif, where the ProVerif code is introduced as a description of the proposed scheme, and the analysis results are then provided.
The definitions for the process of the proposed scheme are shown in Fig 8, wherein the following identifiers are used: “cha” denotes the private channel between the MNi and HAk; “chb” and “chc” denote the public channels between the MNi and FAj and the FAj and HAk, respectively; “IDmi”, “PWmi”, and “BIOmi” denote the private MN identity, password, and biometrics, respectively; “IDfj” and “IDhk” denote the public identity of FAj and HAk, respectively. “KH” denotes the HAk’s private key; “KFH” denotes the pre-shared key between the FAj and HAk; “SKfj” denotes a HAk-generated session key that is transmitted to the FAj; and “SKmi” denotes an MNi-generated session key. The constructors for the operations of the concatenation, symmetric cryptography, exclusive-or, one-way hash, and bio-hash are defined from the lines 18 to 22. In addition, the destructors for the symmetric decryption and exclusive-or operations are defined in the lines 23 and 24. In the lines 26 to 31, six events that indicate the start and end of each node are defined to verify the correspondence relations for the messages of each node.
Fig 8. ProVerif code for definitions.
Fig 9 shows the code for the entire MNi process. The MNi process of the registration phase is modeled in the lines 34 to 36. The MNi process of the login and authentication phase is modeled in the lines 37 to 50.
Fig 9. ProVerif code for entire MN process.
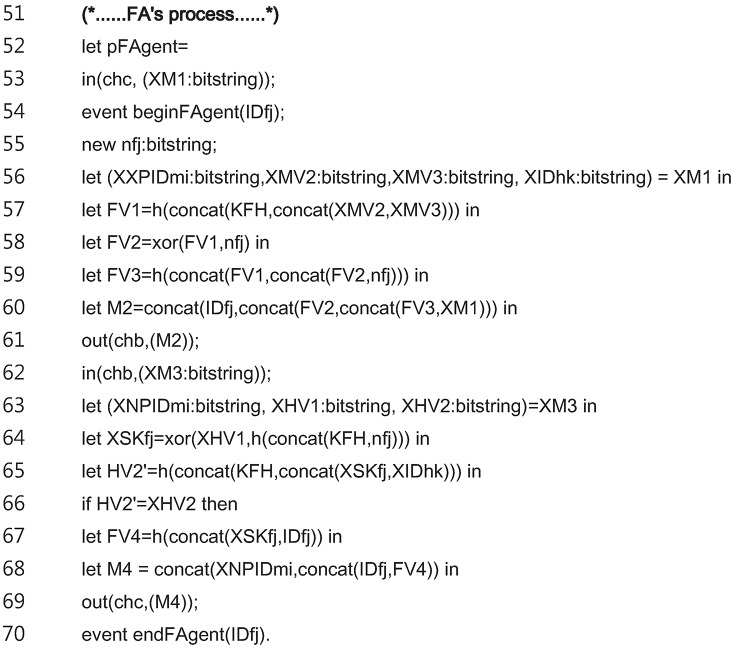
Fig 10 shows the code for the entire FAj process. The FAj process of the login and authentication phase is modeled in the lines 53 to 70.
Fig 10. ProVerif code for entire FA process.
Fig 11 shows the code for the entire HAk process. The HAk process of the registration phase is modeled in the lines 73 to 80. The HAk process of the login and authentication phase is modeled in the lines 81 to 101.
Fig 11. ProVerif code for entire HA process.
The code for the modeling of the adversary capabilities and the verifying of the interprocess equivalences is shown in Fig 12. The lines 103 to 104 prove that the session keys SKfj and SKmi are secret and unknown to the adversary. The lines 105 to 107 verify the internodal relationships to determine the execution of the proposed scheme in the correct order.
Fig 12. ProVerif code for adversary capabilities and verifying equivalences verification.
When the code that defines the elements that are needed to configure the protocol is run, ProVerif prints the results in the following format:
RESULT inj–event[Event] ==> inj–event[Event] is true: The event is proved; for example, the authentication of A to B or the others hold.
RESULT inj–event[Event] ==> inj–event[Event] is false: The event is not proved; that is, the authentication of A to B or the others does not hold
RESULT [Query] is true: The query is proved, so there is no attack. In this case, ProVerif displays no attack derivation and no attack trace.
RESULT [Query] is false: The query is false, as ProVerif has discovered an attack against the desired security property. The attack traces with the attack derivations, which represent the real attack, are displayed.
The execution of the ProVerif code for the verification of the security and the authentication of the proposed scheme produces the simulation result, as shown in Fig 13, thereby verifying the accuracy of the results for all of the events and queries. That is, the successful mutual authentication of the proposed scheme has been achieved as the mutual communication with all of the authentication factors among MNi, FAj, and HAk, as defined by the previously mentioned events. Furthermore, the session keys of the proposed scheme are secure against the adversary; therefore, the proposed scheme can be considered as secure against simulated attacks.
Fig 13. ProVerif simulation result of the proposed scheme.

Formal verification using the random oracle model
In this section, the formal security analysis of the proposed scheme is demonstrated using the random oracle model. For this, we define a hash function and symmetric cryptography as follows:
Definition 1. A hash function h: {0, 1}* → {0, 1}n is a one-way function that takes an input x ∈ {0, 1}* of an arbitrary length and outputs a bit string with a fixed-length h(x) ∈ {0, 1}n and it satisfies the following three security requirements:
It is computationally infeasible to find an input x such that y = h(x).
It is computationally infeasible to find another input x′ ≠ x such that the h(x′) = h(x).
It is computationally infeasible to find the inputs (x, x′), with x′ ≠ x, such that h(x′) = h(x).
Definition 2. A symmetric cryptography ∏ = (E, K, KSPC, MSPC) is a pair of algorithms that is associated with the finite sets, KSPC(k) and MSPC(k), {0, 1}*, for k ∈ N.
E, called the encryption algorithm, is a deterministic algorithm that takes a pair of the strings, a and x and produces y = Ea(x).
D, called the decryption algorithm, is a deterministic algorithm that takes a pair of the strings, a and y and outputs the string x = Da(y)
It is required here, for any k ∈ N, if a ∈ KSPC(k), x ∈ MSPC, any y = Ea(x), then Da(y) = x.
Theorem 1. Under the assumption that the one-way hash function and the symmetric cryptography closely behave like an oracle, then the proposed scheme is provably secure against for the protection of the identity IDmi of MNi, and the private key KH of HAk.
Reveal: Given the hash result y = h(x), this random oracle will unconditionally output the input x.
Extract: Given the cipher text C = EKx(P), this random oracle will unconditionally output the plain text P.
Proof. A method for the formal security proof that is similar to that used in [62–64] is applied in the proposed scheme. For the proof, it is assumed that is able to derive IDmi and KH. For this, runs the experimental algorithm that is shown in Algorithm 1, for the proposed improved and anonymous user authentication scheme, called IAUAS. The success probability of is defined by the following equation:
| (63) |
The advantage function for this experiment becomes as following equation:
| (64) |
in which the maximum is determined by all of with the execution time t and the number of queries qR and qE that are made to the Reveal and Extract oracles, respectively. If is able to invert the hash function and the symmetric cryptography that are provided in Definitions 1 and 2, can directly derive IDmi and KH. Consider the attack experiment that is shown in Algorithm 1. In this case, will discover the complete connections between all of the participants. However, it is computationally infeasible to invert the input from the given hash and encrypted values, i.e., , ∀ϵ > 0. Then, is obtained, because it depends on . Since is negligible, is also negligible. As a result, cannot compute the IDmi and KH and the proposed scheme is provably secure against for the deriving of them.
Algorithm 1: Algorithm
1. Eavesdrop login request message 〈PIDmi, MV2, MV3, IDhk〉 during the login and authentication phase.
2. Call the Reveal oracle. Let
3. Call the Extract oracle. Let
4. Computes
5. if then
6. Call the Reveal oracle. Let
7. if then
8. Compute
9. if then
10. Accept as the correct secret key KH of HAk
11. Accept as the correct secret key IDmi of MNi
12. return 1 (Success)
13. else
14. return 0
15. end if
16. else
17. return 0
18. end if
19. else
20. return 0
21. end if
Theorem 2. Under the assumption that the one-way hash function and the symmetric cryptography closely behave like an oracle, then the proposed scheme is provably secure against for the protection of IDmi, PWmi, and BIOmi of MNi, and the private key KH of HAk.
Proof. For this proof, it is assumed that is able to derive IDmi, PWmi, BIOmi and KH after extracting the secret parameters Ami, Bmi, and Cmi that are stored in the mobile device using side-channel attacks [33, 34, 65]. runs the experimental algorithm that is shown in Algorithm 2. The success of the probability of is defined as the following equation:
| (65) |
The advantage function for this experiment becomes as following equation:
| (66) |
in which the maximum is determined by all of with the execution time t2 and the number of queries qR and qE that are made to the Reveal and Extract oracles, respectively. If is able to invert the hash function and the symmetric cryptography, can directly derive IDmi, PWmi, BIOmi, and KH. Consider the attack experiment that is shown in Algorithm 2. It is computationally infeasible to invert the input from given hash and encrypted values, i.e., , ∀ϵ > 0). Then, is obtained, because it depends on . Since is negligible, is also negligible. As a result, cannot compute the IDmi, PWmi, BIOmi, and KH, and the proposed scheme is provably secure against for deriving them even if the mobile device is stolen by .
Algorithm 2: Algorithm
1. Extract the information {PIDmi, Ami, Bmi, rA, h(⋅), H(⋅)} that is stored in the mobile device through a physical monitoring of its power consumption.
2. Call the Reveal oracle. Let
3. Call the Reveal oracle. Let
4. Computes
5. if then
6. Accepts and as the correct PWmi and BIOmi of MNi
7. Call the Extract oracle. Let
8. if then
9. Compute
10. Compute
11. Call the Reveal oracle. Let
12. if then
13. Accepts as the correct IDi of user MNi
14. Compute
15. if then
16. Accept as the correct secret key KH of HAk
17. return 1 (Success)
18. else
19. return 0
20. end if
21. else
22. return 0
23. end if
24. else
25. return 0
26. end if
27. else
28. return 0
29. end if
Informal verification
In this section, we perform an informal security analysis of the proposed scheme to prove that it is secure against the various security threats. According to the adversarial model that is described in the preliminary knowledge section, can perform the following attacks to undermine the security of the proposed scheme.
has full control over the public communication channel, eavesdropping on the messages M1, M2, M3, and M4, and then inserting new values or removing a value.
If obtains a stolen or lost mobile device of a user in some way, he/she is able to extract the PIDmi, Ami, Bmi, and rA from the device using side-channel attacks [33, 34].
has the ability to make an offline guessing attack within a polynomial time and can try to threaten the privacy of the user by enumerating the eavesdropped messages and the extracted parameters.
Table 2 shows the analysis summary of the comparison of the proposed scheme with the related schemes [26–29, 32].
Table 2. Comparative summary: Security requirements.
| Property | Jiang et al. [27] | Wen et al. [28] | Farash et al. [29] | Gope and Hwang [30] | Wu et al. [31] | Chaudhry et al. [32] | Proposed scheme |
|---|---|---|---|---|---|---|---|
| SR1 | O | O | O | O | O | ||
| SR2 | O | O | O | O | O | O | O |
| SR3 | O | O | O | ||||
| SR4 | O | O | O | O | O | ||
| SR5 | O | O | O | O | O | O | O |
| SR6 | O | O | O | O | O | ||
| SR7 | O | O | O | O | |||
| SR8 | O | O | O | ||||
| SR9 | O | O | O | O | O | ||
| SR10 | O | O | O | O | O | O | O |
| SR11 | O | O | O | O | O | ||
| SR12 | O | O | O | O | |||
| SR13 | O | O | O | O | O | O | O |
| SR14 | O | O | |||||
| SR15 | O |
SR1: user anonymity; SR2: untraceability; SR3: resistance to stolen-mobile device or smart card attack; SR4: mutual authentication; SR5: session key agreement; SR6: resistance to impersonation attack; SR7: resistance to replay attack; SR8: local user verification process; SR9: resistance to stolen-verifier attack; SR10: resistance to privileged-insider attack; SR11: user-friendly password change; SR12: forward secrecy; SR13: resistance to foreign bypass attack; SR14: does not need time synchronization; SR15: provision of the revocation phase;
User anonymity
In the proposed scheme, the pseudo-identity PIDmi = Eh(KH)(IDmi||rD) that varies each session by rD is used. After MNi is authenticated by HAk in Eq (41), HAk replaces the existing PIDmi with a new using a new . Then, is transmitted to MNi that has been encrypted with HAk’s private key KH in Eq (42). Therefore, even if obtains PIDmi by eavesdropping the public messages or extracting the secret parameters stored in the mobile device, the proposed scheme guarantees the user anonymity because it is not possible for to know the real identity IDmi of MNi.
User untraceability
In the login and authentication phase, MNi sends PIDmi, MV2 and MV3 via a public channel. They contain nmi and rD, which are changed for each session. That is, cannot trace MNi’s actions in the proposed scheme because these parameters are computed each time with a different value. Therefore, the proposed scheme ensures the user untraceability.
Stolen-mobile device attack
With the proposed scheme, needs to know KH to guess IDmi and PWmi; however, KH is not stored in the mobile device directly, nor it is transmitted via the public channel as plaintext. Also, even if finds this value somehow, he/she still cannot guess PWmi without H(BIOmi) that is unique to only MNi. Therefore, the proposed scheme withstands the stolen-mobile device attack.
Mutual authentication
In the proposed scheme, MNi and FAj authenticate each other with the assistance of HAk. Only a legitimate MNi can compute MV1 that cannot compute because of PWBmi. Accordingly, HAk authenticates only the legitimate MNi using Eq (41). Also, only the legitimate HAk is authenticated by MNi through the verification of , as shown in Eq (51). Only FAj and HAk that share KF,H can verify each other using the same key to compute valid messages, and only they can compute and obtain a valid session key, SK. Therefore, the adversary or invalid participants cannot carry out the login and authentication phase. Furthermore, FAj authenticates HAk by performing Eq (47). After it receives M4, MNi can verify that using Eq (51) to authenticate FAj and to establish the session key, SK. Therefore, the proposed scheme achieves the mutual authentication.
Session key agreement
After the login and authentication process, FAj receives HV1 and obtains the session key SKfj from HAk, and MNi generates the session key SKmi. As a result, only the legitimate MNi and FAj establish the same session key SKmi = h(MV1||IDmi||IDfj||nmi) = SKfj. Therefore, the proposed scheme provides a secure session key agreement.
User impersonation attack
With the proposed scheme, the user impersonation attack is prevented by the mutual authentication, local user-verification process, and prevention of the stolen-mobile-device attack. Furthermore, the proposed scheme provides a secure session key agreement. Therefore, the proposed scheme ensures the prevention of the user impersonation attack.
Replay attack
might replay an old login request message M1 to FAj and receive the message M4 from FAj. However, still cannot compute the correct session key SK as he/she is not capable of computing IDmi and nmi without KH. Furthermore, cannot derive the session key, SK, without KF,H. Therefore, the proposed scheme is secure against the replay attack.
Local user verification process
With the proposed scheme, mobile devices verify the legality of the user. Only a user who enters the correct IDmi, PWmi, and BIOmi can pass the user-verification process, as given by Eq (28). In addition, since BIOmi of each individual user is unique, cannot attempt an illegal access.
Stolen-verifier attack
In the login and authentication phase of the proposed scheme, HAk does not store and receive any of the credentials of MNi such as PWmi and H(BIOmi). Furthermore, HAk retains RIDmi in the database; however, cannot know the real identity of MNi even if steals the user registration information from HAk’s database. Therefore, the proposed scheme withstands the stolen-verifier attack.
Privileged-insider attack
In the registration phase of the proposed scheme, MNi sends IDmi and PWBmi to HAk. Here, PWBmi contains H(BIOmi). The insider of HAk cannot derive MNi’s password PWmi. Therefore, he/she cannot try to impersonate MNi to access FAj. Furthermore, MNi can change his/her password, PWBmi, without the assistance of HAk in the password change phase. Since it is not possible for the insider to know the MNi’s password, PWmi, the proposed scheme resists the privileged-insider attack.
User-friendly password change
Generally, it is recommended that the performance of the password change process is without any server involvement, thereby providing a user-friendliness and an improvement of the computational efficiency. In the password change phase of the proposed scheme, the existing user password is self-verified in the user’s mobile device, and it is replaced by the new password only if it passes the verification process. Therefore, the proposed scheme supports an efficient password change phase.
Forward secrecy
In the proposed scheme, even though the generated session key between all of the participants can be compromised by , he/she cannot recover any earlier session keys because the session key SKmi = h(MV1||IDmi||IDfj||nmi) = SKfj is different each time. Consequently, a significant correlation was not found between the past, current, and future session keys. Therefore, the proposed scheme ensures the forward secrecy.
Foreign bypass attack
During the authentication phase of the proposed scheme, may try to construct the messages M1 and M2 using the parameters that are stored in a stolen mobile device and transmitted over a public channel to impersonate a legitimate FAj. However, cannot compute FV1, because KF,H is not public information. Thus, cannot construct a sufficient message to cheat HAk. Eventually, is unable to impersonate a valid FAj.
Does not need time synchronization
In many authentication schemes, timestamps are used to resist the replay attack. However, by using the timestamp in the authentication scheme, the clocks of MNi and HAk must be synchronized beforehand. In the synchronization process, there is the possibility that time synchronization error occurs; therefore, to prevent this problem, the proposed scheme only uses random-number-based authentication mechanism instead of timestamps.
Provision of the revocation phase
In the proposed scheme, if MNi’s mobile device is stolen/lost or a secret parameter/authentication factor is revealed, HAk can issues new secret parameters to MNi for the purpose of recovery. HAk retains RIDmi that is encrypted with the real identity of MNi, in the database. When HAk receives a revocation request with IDm i from MNi, HAk computes and compares it with the existing RIDmi that is stored in the database to verify that MNi is registered and legitimate. Therefore, the proposed scheme can cope with unexpected problems by supporting the revocation phase.
Performance analysis
In this section, we perform the comparisons of the computational and communication cost of the proposed scheme with the related schemes [27–32].
Comparisons of the computational costs
We consider four cryptographic operations: hash function Th, the symmetric en/decryption Ts, the ECC-based asymmetric en/decryption Te, and the modular exponent operation Tm were considered. The authors [66] measured the approximate execution time of each cryptographic operation on the following central processing unit (CPU): Intel(R) Core(TM)2T6570 2.1GHz, 4G memory, OS:Win7 32-bit, and Visual C++ 2008 software using the MIRACL C/C++ library. The authors considered the 1024-bit Rivest–Shamir–Adleman (RSA) algorithm, the 320-bit ECC algorithm, the 128-bit Advanced Encryption Standard (AES) algorithm, and the 160-bit Secure Hash Algorithm 1 (SHA-1) hash function, and the experiment the results are Tm ≈ 1.8269ms, Te ≈ 1.6003ms, Ts ≈ 0.1303ms, and Th ≈ 0.0004ms, respectively. The registration and password change phases were excluded from the comparison because the registration phase of the mobile node occurs only once and the password change phase can be executed only within MN. Therefore, only the login and authentication phase was considered in the comparison, because this phase frequently occurs during the intercommunication between participants when the mobile node accesses the ubiquitous networks and the roaming occurs.
Table 3 shows the comparative summary in terms of the computational costs of MN, FA, and HA, as well as the total cost of the different participants. The result of the proposed scheme is 0.2614ms, while the results of the schemes of Jiang et al., Wen et al., Farash et al., Gope and Hwang, Wu et al., and Chaudhry et al. are 3.6543ms, 7.3081ms, 0.5217ms, 3.6543ms, 6.9232ms, and 0.6519ms, respectively. The Table 3 highlights that the computational cost of the proposed scheme is lowest in comparison with the related schemes.
Table 3. Comparative summary: Computational cost.
| Jiang et al. [27] | Wen et al. [28] | Farash et al. [29] | Gope and Hwang [30] | Wu et al. [31] | Chaudhry et al. [32] | Proposed scheme | |
|---|---|---|---|---|---|---|---|
| MN | 3Th + 1Tm | 4Th + 1Tm | 6Th | 4Th + 1Tm | 8Th + 2Te | 5Th | 7Th |
| FA | 4Th | 4Th + 1Tm | 1Th + 2Ts | 4Th | 4Th + 1Ts + 2Te | 1Th + 2Ts | 4Th |
| HA | 5Th + 1Tm | 5Th + 2Tm | 5Th + 2Ts | 4Th + 1Tm | 8Th + 3Ts | 4Th + 3Ts | 9Th + 2Ts |
| Total | 12Th + 2Tm | 13Th + 4Tm | 12Th + 4Ts | 12Th + 2Tm | 20Th + 4Ts + 4Te | 10Th + 5Ts | 20Th + 2Ts |
| Time(ms) | 3.6543 | 7.3081 | 0.5217 | 3.6543 | 6.9232 | 0.6519 | 0.2614 |
Comparisons of the communication costs
For the communication costs, a comparison of the login and authentication phases that referred to [67, 68] was performed, and it is assumed that the lengths of the identity, random number, and timestamp are 128 bits, 64 bits, and 32 bits, respectively. The hash function and the symmetric-key encryption produce 160 bits and 256 bits, respectively. For the asymmetric-key encryption, the modular prime operation and the scalar multiplication operation on the elliptic curve produces 1024 bits and 320bits, respectively.
Table 4 provides the data of the comparisons of the communication costs of the login and authentication phases of the proposed scheme with the other existing schemes. The total communication cost of proposed scheme is 2976 bits, while the schemes of Jiang et al., Wen et al., Farash et al., Gope and Hwang, Wu et al., and Chaudhry et al. are 3200 bits, 3072 bits, 1696 bits, 3072 bits, 3936 bits, and 1824 bits, respectively. Although the total communication costs of the scheme of Farash et al. and Chaudhry et al. are less than that of the proposed scheme, their schemes are insecure, as previously mentioned. Therefore, the proposed scheme is a more practical option for the ubiquitous network environment.
Table 4. Comparative summary: Communication cost.
| Mssage | Jiang et al. [27] | Wen et al. [28] | Farash et al. [29] | Gope and Hwang [30] | Wu et al. [31] | Chaudhry et al. [32] | Proposed scheme |
|---|---|---|---|---|---|---|---|
| M1 | 1152 | 1152 | 608 | 1152 | 864 | 736 | 704 |
| M2 | 1504 | 1440 | 384 | 1440 | 1280 | 384 | 1152 |
| M3 | 320 | 320 | 256 | 320 | 736 | 256 | 576 |
| M4 | 224 | 160 | 448 | 160 | 1056 | 448 | 544 |
| Total (bits) | 3200 | 3072 | 1696 | 3072 | 3936 | 1824 | 2976 |
Conclusion
In this paper, Chaudhry et al.’s authentication scheme for roaming in ubiquitous networks is reviewed, and the scheme’s ongoing vulnerability to several attacks is proven; furthermore, the improved proposed scheme resolves the security issues of Chaudhry et al.’s scheme. To demonstrate the security of the proposed scheme, informal and formal analyses were performed using the random oracle model and the automated verification tool, ProVerif. Also, the performance evaluation that was conducted with related works shows that the proposed scheme is suitable for resource-constrained ubiquitous environments.
Data Availability
All relevant data are within the paper.
Funding Statement
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2010-0020210), http://www.nrf.re.kr/index.
References
- 1. Lambrechts J, Sinha S. Microsensing networks for sustainable cities. Smart sensors, measurement and instrumentation (ISSN 2194-8402). 2016;18. [Google Scholar]
- 2. Islam SR, Kwak D, Kabir MH, Hossain M, Kwak KS. The internet of things for health care: a comprehensive survey. IEEE Access. 2015;3:678–708. doi: 10.1109/ACCESS.2015.2437951 [Google Scholar]
- 3. Rabari C, Storper M. The digital skin of cities: urban theory and research in the age of the sensored and metered city, ubiquitous computing and big data. Cambridge Journal of Regions, Economy and Society. 2014;8(1):27–42. doi: 10.1093/cjres/rsu021 [Google Scholar]
- 4. Yeh CK, Lee WB. An Overall Cost-effective Authentication Technique for the Global Mobility Network. IJ Network Security. 2009;9(3):227–232. [Google Scholar]
- 5. Chaudhry SA, Farash MS, Naqvi H, Kumari S, Khan MK. An enhanced privacy preserving remote user authentication scheme with provable security. Security and Communication Networks. 2015;8(18):3782–3795. doi: 10.1002/sec.1299 [Google Scholar]
- 6.Mishra D. Efficient and secure two-factor dynamic ID-based password authentication scheme with provable security. Cryptologia. 2017; p. 1–30.
- 7. Choi Y, Lee Y, Moon J, Won D. Security enhanced multi-factor biometric authentication scheme using bio-hash function. PLoS ONE. 2017;12(5):e0176250 doi: 10.1371/journal.pone.0176250 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8. Lee Y, Kim S, Won D. Enhancement of two-factor authenticated key exchange protocols in public wireless LANs. Computers & electrical engineering. 2010;36(1):213–223. doi: 10.1016/j.compeleceng.2009.08.007 [Google Scholar]
- 9. Choo KKR, Nam J, Won D. A mechanical approach to derive identity-based protocols from Diffie–Hellman-based protocols. Information Sciences. 2014;281:182–200. doi: 10.1016/j.ins.2014.05.041 [Google Scholar]
- 10. Moon J, Choi Y, Jung J, Won D. An improvement of robust biometrics-based authentication and key agreement scheme for multi-server environments using smart cards. PLoS ONE. 2015;10(12):e0145263 doi: 10.1371/journal.pone.0145263 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11. Nam J, Choo KKR, Han S, Kim M, Paik J, Won D. Efficient and anonymous two-factor user authentication in wireless sensor networks: achieving user anonymity with lightweight sensor computation. PLoS ONE. 2015;10(4):e0116709 doi: 10.1371/journal.pone.0116709 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12. Kang D, Jung J, Mun J, Lee D, Choi Y, Won D. Efficient and robust user authentication scheme that achieve user anonymity with a Markov chain. Security and Communication Networks. 2016;9(11):1462–1476. doi: 10.1002/sec.1432 [Google Scholar]
- 13. Chaudhry SA, Naqvi H, Mahmood K, Ahmad HF, Khan MK. An improved remote user authentication scheme using elliptic curve cryptography. Wireless Personal Communications. 2017;96(4):5355–5373. doi: 10.1007/s11277-016-3745-3 [Google Scholar]
- 14. Chaturvedi A, Mishra D, Jangirala S, Mukhopadhyay S. A privacy preserving biometric-based three-factor remote user authenticated key agreement scheme. Journal of Information Security and Applications. 2017;32:15–26. doi: 10.1016/j.jisa.2016.11.002 [Google Scholar]
- 15. Mishra D, Mukhopadhyay S, Kumari S, Khan MK, Chaturvedi A. Security enhancement of a biometric based authentication scheme for telecare medicine information systems with nonce. Journal of medical systems. 2014;38(5):41 doi: 10.1007/s10916-014-0041-1 [DOI] [PubMed] [Google Scholar]
- 16. Srinivas J, Mishra D, Mukhopadhyay S, Kumari S. Provably secure biometric based authentication and key agreement protocol for wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing. 2017; p. 1–21. [Google Scholar]
- 17. Ignatenko T, Willems FM. Biometric systems: Privacy and secrecy aspects. IEEE Transactions on Information Forensics and Security. 2009;4(4):956–973. doi: 10.1109/TIFS.2009.2033228 [Google Scholar]
- 18. Wazid M, Das AK, Kumari S, Li X, Wu F. Provably secure biometric-based user authentication and key agreement scheme in cloud computing. Security and Communication Networks. 2016;9(17):4103–4119. doi: 10.1002/sec.1591 [Google Scholar]
- 19. Jung J, Kang D, Lee D, Won D. An improved and secure anonymous biometric-based user authentication with key agreement scheme for the integrated EPR information system. PLoS ONE. 2017;12(1):e0169414 doi: 10.1371/journal.pone.0169414 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20. Odelu V, Das AK, Kumari S, Huang X, Wazid M. Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Future Generation Computer Systems. 2017;68:74–88. doi: 10.1016/j.future.2016.09.009 [Google Scholar]
- 21. Zhu J, Ma J. A new authentication scheme with anonymity for wireless environments. IEEE Transactions on Consumer Electronics. 2004;50(1):231–235. doi: 10.1109/TCE.2004.1277867 [Google Scholar]
- 22. Lee CC, Hwang MS, Liao IE. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Transactions on Industrial Electronics. 2006;53(5):1683–1687. doi: 10.1109/TIE.2006.881998 [Google Scholar]
- 23. Wu CC, Lee WB, Tsaur WJ. A secure authentication scheme with anonymity for wireless communications. IEEE Communications Letters. 2008;12(10). [Google Scholar]
- 24. Mun H, Han K, Lee YS, Yeun CY, Choi HH. Enhanced secure anonymous authentication scheme for roaming service in global mobility networks. Mathematical and Computer Modelling. 2012;55(1):214–222. doi: 10.1016/j.mcm.2011.04.036 [Google Scholar]
- 25. Zhao D, Peng H, Li L, Yang Y. A secure and effective anonymous authentication scheme for roaming service in global mobility networks. Wireless Personal Communications. 2014;78(1):247–269. doi: 10.1007/s11277-014-1750-y [Google Scholar]
- 26. He D, Chan S, Chen C, Bu J, Fan R. Design and validation of an efficient authentication scheme with anonymity for roaming service in global mobility networks. Wireless Personal Communications. 2011;61(2):465–476. doi: 10.1007/s11277-010-0033-5 [Google Scholar]
- 27. Jiang Q, Ma J, Li G, Yang L. An enhanced authentication scheme with privacy preservation for roaming service in global mobility networks. Wireless Personal Communications. 2013;68(4):1477–1491. doi: 10.1007/s11277-012-0535-4 [Google Scholar]
- 28. Wen F, Susilo W, Yang G. A secure and effective anonymous user authentication scheme for roaming service in global mobility networks. Wireless personal communications. 2013;73(3):993–1004. doi: 10.1007/s11277-013-1243-4 [Google Scholar]
- 29. Farash MS, Chaudhry SA, Heydari M, Sadough S, Mohammad S, Kumari S, et al. A lightweight anonymous authentication scheme for consumer roaming in ubiquitous networks with provable security. International Journal of Communication Systems. 2017;30(4). doi: 10.1002/dac.3019 [Google Scholar]
- 30. Gope P, Hwang T. Enhanced secure mutual authentication and key agreement scheme preserving user anonymity in global mobile networks. Wireless Personal Communications. 2015;82(4):2231–2245. doi: 10.1007/s11277-015-2344-z [Google Scholar]
- 31. Wu F, Xu L, Kumari S, Li X, Khan MK, Das AK. An enhanced mutual authentication and key agreement scheme for mobile user roaming service in global mobility networks. Annals of Telecommunications. 2017;72(3-4):131–144. doi: 10.1007/s12243-016-0547-2 [Google Scholar]
- 32. Chaudhry SA, Albeshri A, Xiong N, Lee C, Shon T. A privacy preserving authentication scheme for roaming in ubiquitous networks. Cluster Computing. 2017;20(2):1223–1236. doi: 10.1007/s10586-017-0783-x [Google Scholar]
- 33. Jiang Q, Ma J, Yang C, Ma X, Shen J, Chaudhry SA. Efficient end-to-end authentication protocol for wearable health monitoring systems. Computers & Electrical Engineering. 2017;63:182–195. doi: 10.1016/j.compeleceng.2017.03.016 [Google Scholar]
- 34. Wu F, Xu L, Kumari S, Li X, Khan MK, Das AK. An enhanced mutual authentication and key agreement scheme for mobile user roaming service in global mobility networks. Annals of Telecommunications. 2016; p. 1–14. [Google Scholar]
- 35. Kumari S. Design flaws of an anonymous two-factor authenticated key agreement scheme for session initiation protocol using elliptic curve cryptography. Multimedia Tools and Applications. 2017;76(11):13581–13583. doi: 10.1007/s11042-016-3771-x [Google Scholar]
- 36. Kumari S, Khan MK, Li X. A more secure digital rights management authentication scheme based on smart card. Multimedia Tools and Applications. 2016;75(2):1135–1158. doi: 10.1007/s11042-014-2361-z [Google Scholar]
- 37.Wang D, Gu Q, Cheng H, Wang P. The request for better measurement: A comparative evaluation of two-factor authentication schemes. In: Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security. ACM; 2016. p. 475–486.
- 38. Jiang Q, Zeadally S, Ma J, He D. Lightweight Three-Factor Authentication and Key Agreement Protocol for Internet-Integrated Wireless Sensor Networks. IEEE Access. 2017;5:3376–3392. doi: 10.1109/ACCESS.2017.2673239 [Google Scholar]
- 39.Feng Q, He D, Zeadally S, Wang H. Anonymous biometrics-based authentication scheme with key distribution for mobile multi-server environment. Future Generation Computer Systems. 2017;.
- 40. Odelu V, Banerjee S, Das AK, Chattopadhyay S, Kumari S, Li X, et al. A secure anonymity preserving authentication scheme for roaming service in global mobility networks. Wireless Personal Communications. 2017;96(2):2351–2387. doi: 10.1007/s11277-017-4302-4 [Google Scholar]
- 41. Srinivas J, Mukhopadhyay S, Mishra D. A self-verifiable password based authentication scheme for multi-server architecture using smart card. Wireless Personal Communications. 2017;96(4):6273–6297. doi: 10.1007/s11277-017-4476-9 [Google Scholar]
- 42. Mishra D, Das AK, Mukhopadhyay S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Systems with Applications. 2014;41(18):8129–8143. doi: 10.1016/j.eswa.2014.07.004 [Google Scholar]
- 43. Srinivas J, Mukhopadhyay S, Mishra D. Secure and efficient user authentication scheme for multi-gateway wireless sensor networks. Ad Hoc Networks. 2017;54:147–169. doi: 10.1016/j.adhoc.2016.11.002 [Google Scholar]
- 44. Jin ATB, Ling DNC, Goh A. Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern recognition. 2004;37(11):2245–2255. doi: 10.1016/j.patcog.2004.04.011 [Google Scholar]
- 45. Chaudhry SA, Naqvi H, Farash MS, Shon T, Sher M. An improved and robust biometrics-based three factor authentication scheme for multiserver environments. The Journal of Supercomputing. 2015; p. 1–17. [Google Scholar]
- 46. Khan I, Chaudhry SA, Sher M, Khan JI, Khan MK. An anonymous and provably secure biometric-based authentication scheme using chaotic maps for accessing medical drop box data. The Journal of Supercomputing. 2016; p. 1–19. [Google Scholar]
- 47. Chaudhry SA, Naqvi H, Khan MK. An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimedia Tools and Applications. 2017; p. 1–22. [Google Scholar]
- 48. Mishra D, Vijayakumar P, Sureshkumar V, Amin R, Islam SH, Gope P. Efficient authentication protocol for secure multimedia communications in IoT-enabled wireless sensor networks. Multimedia Tools and Applications. 2017; p. 1–31. [Google Scholar]
- 49. Amin R, Biswas G. A novel user authentication and key agreement protocol for accessing multi-medical server usable in tmis. Journal of medical systems. 2015;39(3):33 doi: 10.1007/s10916-015-0217-3 [DOI] [PubMed] [Google Scholar]
- 50. Amin R, Biswas G. A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. Journal of medical systems. 2015;39(8):78 doi: 10.1007/s10916-015-0258-7 [DOI] [PubMed] [Google Scholar]
- 51. Moon J, Choi Y, Kim J, Won D. An improvement of robust and efficient biometrics based password authentication scheme for telecare medicine information systems using extended chaotic maps. Journal of medical systems. 2016;40(3):70 doi: 10.1007/s10916-015-0422-0 [DOI] [PubMed] [Google Scholar]
- 52. Jung J, Moon J, Lee D, Won D. Efficient and Security Enhanced Anonymous Authentication with Key Agreement Scheme in Wireless Sensor Networks. Sensors. 2017;17(3):644 doi: 10.3390/s17030644 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 53. Kumari S, Li X, Wu F, Das AK, Choo KKR, Shen J. Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Future Generation Computer Systems. 2017;68:320–330. doi: 10.1016/j.future.2016.10.004 [Google Scholar]
- 54. Jiang Q, Khan MK, Lu X, Ma J, He D. A privacy preserving three-factor authentication protocol for e-Health clouds. The Journal of Supercomputing. 2016;72(10):3826–3849. doi: 10.1007/s11227-015-1610-x [Google Scholar]
- 55. Mishra D, Chaturvedi A, Mukhopadhyay S. Design of a lightweight two-factor authentication scheme with smart card revocation. Journal of Information Security and Applications. 2015;23:44–53. doi: 10.1016/j.jisa.2015.06.001 [Google Scholar]
- 56. Jiang Q, Ma J, Wei F. On the security of a privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Systems Journal. 2016;. doi: 10.1109/JSYST.2016.2574719 [Google Scholar]
- 57. Blanchet B, et al. Modeling and Verifying Security Protocols with the Applied Pi Calculus and ProVerif. Foundations and Trends® in Privacy and Security. 2016;1(1-2):1–135. doi: 10.1561/3300000004 [Google Scholar]
- 58. Karuppiah M, Kumari S, Li X, Wu F, Das AK, Khan MK, et al. A Dynamic ID-Based Generic Framework for Anonymous Authentication Scheme for Roaming Service in Global Mobility Networks. Wireless Personal Communications. 2016; p. 1–25. [Google Scholar]
- 59. Wu F, Xu L, Kumari S, Li X, Shen J, Choo KKR, et al. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. Journal of Network and Computer Applications. 2016;. [Google Scholar]
- 60. Kumari S, Chaudhry SA, Wu F, Li X, Farash MS, Khan MK. An improved smart card based authentication scheme for session initiation protocol. Peer-to-Peer Networking and Applications. 2017;10(1):92–105. doi: 10.1007/s12083-015-0409-0 [Google Scholar]
- 61. Chaudhry SA, Khan I, Irshad A, Ashraf MU, Khan MK, Ahmad HF. A provably secure anonymous authentication scheme for Session Initiation Protocol. Security and Communication Networks. 2016;. doi: 10.1002/sec.1672 [Google Scholar]
- 62. Lu Y, Li L, Yang X, Yang Y. Robust biometrics based authentication and key agreement scheme for multi-server environments using smart cards. PLoS ONE. 2015;10(5):e0126323 doi: 10.1371/journal.pone.0126323 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 63. Das AK. A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications. Networking Science. 2013;2(1-2):12–27. doi: 10.1007/s13119-012-0009-8 [Google Scholar]
- 64. Das AK, Paul NR, Tripathy L. Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Information Sciences. 2012;209:80–92. doi: 10.1016/j.ins.2012.04.036 [Google Scholar]
- 65. Kumari S, Khan MK, Li X, Wu F. Design of a user anonymous password authentication scheme without smart card. International Journal of Communication Systems. 2016;29(3):441–458. doi: 10.1002/dac.2853 [Google Scholar]
- 66. Xu L, Wu F. Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. Journal of medical systems. 2015;39(2):10 doi: 10.1007/s10916-014-0179-x [DOI] [PubMed] [Google Scholar]
- 67. Reddy AG, Das AK, Odelu V, Yoo KY. An enhanced biometric based authentication with key-agreement protocol for multi-server architecture based on elliptic curve cryptography. PLoS ONE. 2016;11(5):e0154308 doi: 10.1371/journal.pone.0154308 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 68. Kumari S, Khan MK, Atiquzzaman M. User authentication schemes for wireless sensor networks: A review. Ad Hoc Networks. 2015;27:159–194. doi: 10.1016/j.adhoc.2014.11.018 [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
All relevant data are within the paper.