Abstract
In this paper, the secrecy performance of the two-user simultaneous wireless information and power transfer (SWIPT) sensor networks is studied and a novel secure transmission scheme of cooperative zero-forcing (ZF) jamming is proposed. The two sensors opportunistically conduct the SWIPT and cooperative ZF jamming, respectively, where the energy required for jamming the eavesdropper is provided by the SWIPT operation so as to keep the energy balance at the sensors in the long run. By deriving the exact closed-form expressions of the secrecy outage probability and the secrecy throughout, we provide an effective approach to precisely assess the impacts of key parameters on the secrecy performance of the system. It has been shown that the secrecy outage probability is a monotonically increasing function of the growth of secrecy rate (), and a monotonically decreasing function of the increase of the transmit signal-to-noise ratio (), and energy conversion efficiency (). Furthermore, the secrecy throughput could be enhanced when increases, which becomes especially obvious when a large is provided. Moreover, the existence of an optimum maximizing the secrecy throughput is depicted, which also grows with the increase of . Simulations are provided for the validation of the analysis.
Keywords: physical layer security, zero-forcing jamming, secrecy outage probability, secrecy throughput, wireless sensor networks
1. Introduction
Because of the broadcast nature of wireless medium, it is a critical issue to secure the transmission in the design of wireless sensor networks [1]. The security is conventionally tackled through higher layer techniques, e.g., cryptographic protocols, which, however, could not guarantee the required security level alone for the large-scale wireless sensor networks due to the significant increase in the complexity of key distribution and management [2]. In contrast to conventional cryptographic approaches conducted at higher layers, the physical layer security (PLS) tries to secure the wireless networks against eavesdropping by exploiting the inherent channel randomness at the physical layer. Hence, PLS has been widely regarded as an effective supplementary protocol for wireless communications and, thus, has gained much attention in research communities [3,4,5].
The main idea of PLS is that, by making and enlarging the capacity differences between the legitimate channels and the wiretapping channels, the information could be transmitted at a predefined secrecy rate so that only the authorized receiver can decode the data while the eavesdropper could not [6]. Various advanced techniques have been proposed to further enhance the potential benefits of PLS, such as antenna selection [7], cooperative relaying [8], cooperative jamming [9], etc. Generally speaking, the security of wireless transmission could be significantly increased if jamming signals could be carefully exploited in the legitimate network. As a consequence, the cooperative jamming has been widely applied in the PLS research in numerous systems, such as single-input-multiple-output (SIMO) networks [10], two-way relay scenarios [11], multiple-input-multiple-output (MIMO) wiretap-channel settings [12], etc.
More recently, the simultaneous wireless information and power transfer (SWIPT) has become an appealing technique in wireless communications due to its great potential in tackling the energy bottleneck issue, especially in some energy-constrained cases [13,14,15]. Authors in [16] investigated the safeguarding approach for SWIPT systems with both the eavesdropper and the friendly jammer harvesting energy from the wireless signals, and the optimal power allocation strategy based on the Lagrange method was then proposed. In [17], a cooperative jamming aided robust secure transmission for SWIPT multiple-input-single-output (MISO) networks was presented, where the objective of the source and the jammer was to maximize the secrecy rate and also supply wireless power to the energy receiver and the destination. However, an additional jammer must be deployed in literature [16,17], which is practically costly in the construction and upgrading of current wireless systems, especially in the wireless sensor networks.
There has been some research investigating the security issue of scenarios where no additional jammer is available and the user harvests the energy and also acts as the jammer itself [18,19,20]. Work [18] studied the secrecy performance of full-duplex SWIPT networks, where the two-antenna user received information and energy with one of its antennae by applying the power-splitting SWIPT protocol, and sent the jamming signal to confuse the eavesdropper with the other antenna. Under a similar system of deployment, the security of the time-switching SWIPT protocol was examined in [19], where the secrecy outage performance and the secrecy energy efficiency were formulated. The author in [20] extended the research in the cognitive networks, where the energy collected by the receiving antenna via the power-splitting SWIPT protocol was used for producing jamming signals by the transmitting antenna. However, the shortage of [18,19,20] is obvious. On the one hand, an effective self-interference cancellation (SIC) method at the users is required to guarantee the validity of the secure schemes, as the users in this literature all work in the full-duplex mode. On the other hand, both the power-splitting and the time-switching approaches applied in these literature will definitely increase the complexity of realization significantly. As a result, the practical value of these schemes in wireless sensor networks is greatly limited.
Motivated by the above observations, we present a novel secure transmission scheme for the proposed two-user SWIPT sensor networks where the two sensors conduct the cooperative zero-forcing (ZF) jamming opportunistically and mutually with the harvested energy. We note that the proposed two-user cooperative pair model is rather practical because each sensor in actual sensor networks can choose another sensor nearby to form this pair and then conduct cooperative jamming in turn. It is also highlighted that the sensors are generally energy-constrained, which again reveals the advantage of the proposed cooperative jamming scheme because it does not consume any energy of the sensors in the long run due to the SWIPT operation. Furthermore, neither the full-duplex and SIC techniques nor the power-splitting and time-switching methods are needed in the proposed scheme, which is of great benefit in practical realization. The remainder of the work is organized as follows: Section 2 characterizes the system model and presents the secure transmission scheme. In Section 3, the exact secrecy analysis of the proposed scheme is carried out. Section 4 conducts the simulations and gives the discussions. Finally, Section 5 summarizes the whole paper.
Notation: Throughout this paper, the boldface uppercase letters are used to denote matrices or vectors. and are denoted as the transpose operation and the conjugate transpose operation, respectively. and represent the cumulative distribution function (CDF) and the probability density function (PDF) of random variable , respectively. denotes the expectation operation.
2. System Model
2.1. System Description
We consider a downlink SWIPT sensor network as illustrated in Figure 1, which consists of a source node S, a pair of two sensor nodes and , and an eavesdropper E. All nodes are equipped with a single antenna, except for the two sensors, which both have only two antennae without having to increase too much complexity of realization [19,20]. In addition, we assume that the channel state information (CSI) of the legitimate links is available, while the CSI of the eavesdropping link is not known by the legitimate nodes. This is a typical passive eavesdropping scenario which is more practical than active eavesdropping [21] and has been widely used in existing literature (see [22,23,24] and the references therein). It is also assumed that all the channels between two nodes experience quasi-static Rayleigh fading, such that the channel coefficients keep constant during a packet time but vary independently from one packet time to another. Furthermore, all the channels of and are assumed to be independent and identically distributed (i.i.d), respectively.
Figure 1.
System model.
2.2. Secure Transmission
At each slot, the specific antenna of a certain sensor that maximizes the instantaneous transmission channel capacity is chosen for information receiving (IR). At the same time, the remaining antenna of the selected sensor will be assigned for energy harvesting (EH). In addition, the jamming operation is introduced in order to enhance the security of the transmission. More specifically, the cooperative ZF jamming is applied in this paper by the other sensor, so that the IR process is not interfered.
Without loss of generality, we assume that the is selected in a certain slot, namely
| (1) |
where , and represents the channel coefficient between S and the j-th antenna of i-th sensor. At the same time, the antenna is allocated for collecting energy, and the other sensor is assigned to produce ZF jamming signals in order to increase the security of the transmission. As described above, we can summarize the working mode of all the antennae when is determined, which is shown in Table 1 for the better readability.
Table 1.
Working mode of the sensors and antennas .
| Sensor | Antenna | Working Mode |
|---|---|---|
| Information receiving | ||
| Energy harvesting | ||
| Zero-forcing jamming | ||
As a result, the signals for IR and EH can be given by Labels (2) and (3), respectively,
| (2) |
| (3) |
where and represent the transmit power of S and the jamming power of sensors, , represent the channel coefficient vectors from to and , respectively. and denote the information-bearing signal and the jamming signal, is the additive white Gaussian noise (AWGN) at node a with , . Without loss of generality, the noise power spectral density is assumed the same everywhere within the network and is denoted as , and is the normalized vector of the jamming operation.
Now, we will focus on the derivation of . As pointed out previously, the jamming operation is introduced to increase the security of the transmission. Therefore, three purposes are expected to be achieved by this jamming operation. Firstly, the jamming operation will not affect the receiving performance of the legitimate information receiver. Secondly, the interference received at the eavesdropper should be maximized, so that the eavesdropper is confused as much as possible. Thirdly, the interference received at the legitimate energy receiver should be maximized, so that the legitimate energy receiver could collect as much energy as possible from the jamming signal. Mathematically, the above three ideas can be achieved by Equations (4)–(6), respectively,
| (4) |
| (5) |
| (6) |
where represents the channel coefficient vector from to E. In addition, recall that the jamming vector is normalized, hence we have
| (7) |
Unfortunately, due to the passive eavesdropping assumption, the eavesdropper’s CSI, , is unavailable at the legitimate network, thus it is not possible to maximize the confusing effect to the eavesdropper. As a result, we will try to find an appropriate so that Labels (4), (6), and (7) are all satisfied, namely
| (8) |
According to [25,26], the solution of Label (8) can be given by
| (9) |
where is the projection idempotent matrix with rank 1, which is given by
| (10) |
It is easy to see from Labels (9) and (10) that is chosen from the null space of the channel direction of so that the information receiving process is not interfered [27,28].
As can be observed, the CSI knowledge is required for both the selection process and ZF jamming operation. Now, we will elaborate on how this knowledge is obtained. As shown in Figure 2, each time slot could be divided into two parts, namely the pilot duration and the transmission duration. In order to select the best antenna for IR, the antenna () will send pilot signals during its pilot duration , which can be exploited for channel estimation by S and the other sensor, which acts as a jammer. Hence, S is able to obtain the knowledge of for user/antenna selection, and the sensor that acts as jammer can derive the knowledge of and to construct the ZF jamming vector.
Figure 2.
Time slot structure for user/antenna selection.
According to Labels (2) and (8), the receiving signal-to-noise ratio (SNR) for information receiving is given by
| (11) |
At the same time, the amount of collected energy is expressed as
| (12) |
and denoting . According to (Lemma 2 [25]), (Lemma 2 [26]), (Equation (30) [27]), (Equation (52) [28]), the CDF of is a chi-square random variable with degrees of freedom, namely U ~ , where represents the number of ZF antennae. In this paper, we have . Hence, U ~ , which degenerates into exponentially distributed random variables, namely we have
| (13) |
where represents the average channel gain of link , . Specifically, represents the average channel gain between the two sensors. By using the above result, Equation (12) can be readily calculated as (We note that little energy can be harvested from the AWGN in practice, hence is neglected in this paper [14,29].)
| (14) |
where is the energy conversion efficiency. Hence, in order to keep the energy balance at the sensors in the long run, the jamming power can be chosen as (We note that an energy outage would occur by adopting the approach in this paper. Although the probability to occur this can be proven to be very low by the simulations when an appropriate initial energy can be provided, it still should be considered for accurate analysis. In fact, by modeling battery as an energy queue would be a good method to give out the accurate analysis, which however is beyond the scope of this paper and is left for the research in the future.)
| (15) |
It is readily to know that Label (15) yields to
| (16) |
Similarly, the receiving signal at E is expressed as
| (17) |
Thus, the receiving signal-to-interference-plus-noise ratio (SINR) at E is given by
| (18) |
3. Secrecy Performance Analysis
In this section, we focus our attention on the secrecy performance of the proposed scheme. Before delving into the details, we present the preliminary of the following two lemmas.
Lemma 1.
The CDF and the PDF of are given by
(19)
(20)
Proof.
According to Label (11) and referring to [5], Equation (19) is readily obtained. By taking the derivation operation, the PDF of is derived as
(21) By using the binomial theorem (Equation (1.111) [30]) in Label (21), the result in Label (20) is readily obtained. ☐
Lemma 2.
The CDF and PDF of are given by
(22)
(23)
Proof.
Mathematically, the CDF of can be manipulated as , which can be rewritten as Label (24) according to Label (18)
(24) where . As shown in Label (8), is a normalized vector, i.e., . Thus, is a unitary transformation of . In addition, it is obvious that is independent of , and the two elements of , namely and are both Gaussian variables. In other words, we have . Therefore, and can be concluded. Hence, , which means that is also an exponentially distributed random variables with the mean of . We note that V has the same distribution with and , and this has verified the conclusion that the unitary transformation does not change the distribution of the transformed variables. As a result, we have
(25) In addition, the CDF of is given by
(26) Substituting Labels (25) and (26) into Label (24) and after some calculations, the CDF of is easily obtained as in Label (22). By taking the derivation operation in Label (22), we finally derive the result in Label (23). ☐
3.1. Secrecy Outage Probability
The secrecy outage probability is defined as the probability that the instantaneous secrecy capacity falls below a predefined secrecy rate (The design of falls into the construction of the wiretap coding, which has been elaborated abundantly in the literature [31,32], and thus is omitted in this paper.), which can be equivalently expressed as [5,28]
| (27) |
where .
Theorem 1.
The secrecy outage probability for the proposed system is given by
(28) where
(29)
(30)
Proof.
Replacing x with in Label (19), we derive
(31) With the help of binomial theorem, Label (31) can be rewritten as
(32) By substituting Labels (23) and (32) into Label (27), and letting , we obtain
(33) where
(34)
(35) By using (Equation (3.353.3) [30]), Label (34) leads to Label (29). Similarly, by using (Equation (3.352.4) [30]), Label (35) results in Label (30). ☐
3.2. Secrecy Throughput
The secrecy throughput can be defined as the secrecy rate multiplied by the probability of a reliable and secure transmission, which is mathematically written as [33]
| (36) |
By substituting the result in Theorem 1 into Label (36), the secrecy throughput can be easily deduced.
4. Simulation Results and Discussion
In this section, some representative simulations are provided to examine the impacts of the system parameters on the cooperative zero-forcing jamming scheme for the two-user SWIPT networks. The transmit SNR is defined as . As can be readily observed, the theoretical results are in exact agreement with the simulations, validating the correctness of the analysis. Without loss of generality, we set .
Figure 3 illustrates the secrecy outage probability versus the secrecy rate with different and . As it is shown, the secrecy outage probability monotonically increases with the growth of . In addition, we see from Figure 3 that larger and both lead to a better secrecy outage performance. It is not difficult for comprehension because a larger secrecy rate is much harder to support for a given channel condition, thus leading to a greater secrecy outage. In addition, a larger indicates a greater amount of harvested energy and a better receiving SNR performance at the receiver. In other words, by increasing , the receiving SNR performance at the receiver is promoted while the receiving SNR performance at the eavesdropper becomes poor because a larger jamming power could be provided. Furthermore, although it is not a benefit to the receiver by increasing , it still improves the amount of harvested energy, and thus can confuse the eavesdropper better. Therefore, increasing and both contribute to a better secrecy outage performance.
Figure 3.
vs. with different and . dB, dB, dB, dB.
Figure 4 plots the secrecy outage probability versus the transmit SNR for various . As can be seen, the secrecy outage probability is a monotonically increasing function with , which coincides with the finding in Figure 3. In addition, a lower secrecy outage probability is observed when a larger is provided, regardless of the value of . As a matter of fact, the changing of will have two effects on the performance. On the one hand, increasing will benefit the receiving performance of both the receiver’s and the eavesdropper’s. One the other hand, the performance of the eavesdropper will be degraded by the jamming operation while the performance of the information receiver will not. We note that, when a larger is provided, the confusing effect to the eavesdropper will become better because more energy will be harvested, so that the user can jam the eavesdropper at a greater power. Overall, the receiving performance of the information receiver is much more improved than that of the eavesdropper. Therefore, the secrecy outage probability becomes a decreasing function with .
Figure 4.
vs. with various . dB, dB, dB, dB, .
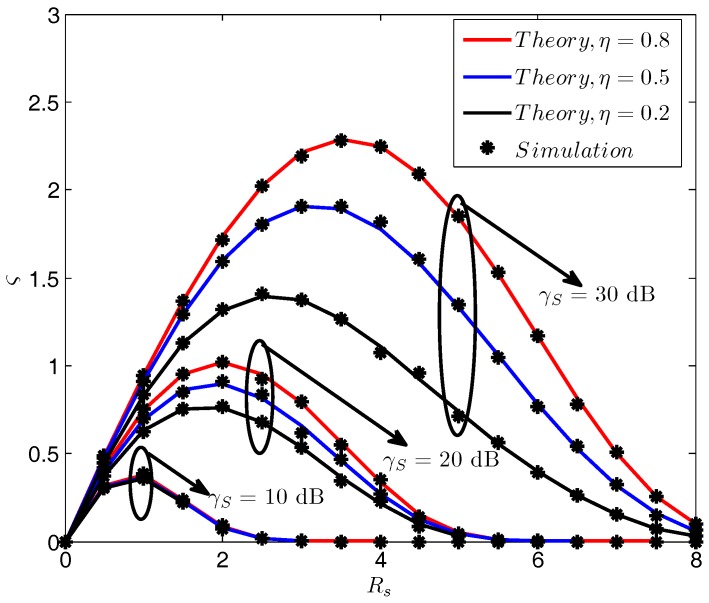
Figure 5 compares the secrecy throughput versus the secrecy rate with different and . It is shown that the secrecy throughput improves significantly when a larger is provided. Moreover, it is also beneficial to boost the secrecy throughput if could be increased. In addition, this is especially useful in the high SNR region, as the enhancement of secrecy throughput is much more notable when is large. Furthermore, it is noted that the variation tendency of the secrecy throughput in each line indicates the existence of an optimum which can maximize the secrecy throughput. This phenomenon is comprehensible. On the one hand, increasing will directly contribute to the enhancement of secrecy throughput, as more secrecy message is transmitted. On the other hand, a larger secrecy rate will also lead to a greater secrecy outage probability, which will result in the decline of the secrecy throughput. As a result, an optimum that maximizes the secrecy throughput is observed.
Figure 5.
vs. with different and . dB, dB, dB, dB, dB.
5. Conclusions
This paper presented a novel secure transmission scheme for the two-user SWIPT sensor networks where the cooperative zero-forcing jamming was conducted to confuse the eavesdropper. It is highlighted that the cooperative jamming does not require any energy of the sensors due to the SWIPT operation, and thus can be well applied to the energy-constrained wireless sensor networks. The exact closed-form expressions of the secrecy outage probability and the secrecy throughout were derived, which depicted the impacts of the system parameters on the system secrecy performance intuitively. The results illustrated that the secrecy outage probability monotonically increases with the growth of , and monotonically decreases with the increase of and . Moreover, the secrecy throughput could be further boosted if increases, which is especially notable when is large enough. In addition, it was indicated that an optimum value of maximizing the secrecy throughput exists, which also grows with the increase of . All of the findings are of great importance in guiding the secure design of practical wireless sensor networks.
Acknowledgments
This work was supported by the National Natural Science Foundation of China under Grant Nos. 61771487, 61471393, and 61371122. The authors would like to extend their gratitude to the anonymous reviewers for their valuable and constructive comments, which have largely improved and clarified this paper.
Author Contributions
Xuanxuan Tang, Yueming Cai, Wendong Yang and Weiwei Yang conceived of the main proposal of the secure transmission schemes, conducted system modeling, and derived analysis and numerical simulation of the proposed schemes. Xuanxuan Tang and Yueming Cai wrote the manuscript. Dechuan Chen and Junquan Hu provided considerable comments and technique review of the proposed scheme and contributed to the revision of the paper. Yueming Cai read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Zheng J., Cai Y., Shen X., Zheng Z., Yang W. Green energy optimization in energy harvesting wireless sensor networks. IEEE Commun. Mag. 2015;53:150–157. doi: 10.1109/MCOM.2015.7321985. [DOI] [Google Scholar]
- 2.Hu J., Yang W., Yang N., Zhou X., Cai Y. On-off-based secure transmission design with outdated channel state information. IEEE Trans. Veh. Technol. 2016;65:6075–6088. doi: 10.1109/TVT.2015.2477427. [DOI] [Google Scholar]
- 3.Mukherjee A., Fakoorian S.A.A., Huang J., Swindlehurst A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014;16:1550–1573. doi: 10.1109/SURV.2014.012314.00178. [DOI] [Google Scholar]
- 4.Yang N., Wang L., Geraci G., Elkashlan M., Yuan J., Renzo M.D. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015;53:20–27. doi: 10.1109/MCOM.2015.7081071. [DOI] [Google Scholar]
- 5.Tang X., Cai Y., Huang Y., Duong T.Q., Yang W., Yang W. Secrecy outage analysis of buffer-aided cooperative MIMO relaying systems. IEEE Trans. Veh. Technol. 2017 doi: 10.1109/TVT.2017.2695500. [DOI] [Google Scholar]
- 6.Chen G., Gong Y., Xiao P., Chambers J.A. Physical layer network security in the full-duplex relay system. IEEE Trans. Inf. Forensics Secur. 2015;10:574–583. doi: 10.1109/TIFS.2015.2390136. [DOI] [Google Scholar]
- 7.Hu J., Cai Y., Yang N., Yang W. A new secure transmission scheme with outdated antenna selection. IEEE Trans. Inf. Forensics Secur. 2015;10:2435–2446. doi: 10.1109/TIFS.2015.2464703. [DOI] [Google Scholar]
- 8.Zou Y., Wang X., Shen W. Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE J. Sel. Areas Commun. 2013;31:2099–2111. doi: 10.1109/JSAC.2013.131011. [DOI] [Google Scholar]
- 9.Yang M.Q., Zhang B.N., Huang Y.Z., Yang N., Guo D.X., Gao B. Secure multiuser communications in wireless sensor networks with TAS and cooperative jamming. Sensors. 2016;16:1908. doi: 10.3390/s16111908. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Wang C., Wang H.M., Xia X.G., Liu C. Uncoordinated jammer selection for securing SIMOME wiretap channels: A stochastic geometry approach. IEEE Trans. Wirel. Commun. 2015;14:2596–2612. doi: 10.1109/TWC.2015.2389821. [DOI] [Google Scholar]
- 11.Zhang R., Song L., Han Z., Jiao B. Physical layer security for two-way untrusted relaying with friendly jammers. IEEE Trans. Veh. Technol. 2012;61:3693–3704. doi: 10.1109/TVT.2012.2209692. [DOI] [Google Scholar]
- 12.Yun S., Park J., Im S., Ha J. On the secrecy rate of artificial noise assisted MIMOME channels with full-duplex receiver; Proceedings of the IEEE Wireless Communications and Networking Conference; San Francisco, CA, USA. 19–22 March 2017; pp. 1–6. [Google Scholar]
- 13.Liu H., Kim K.J., Kwak K.S., Poor H.V. Power splitting-based SWIPT with decode-and-forward full-duplex relaying. IEEE Trans. Wirel. Commun. 2016;15:7561–7577. doi: 10.1109/TWC.2016.2604801. [DOI] [Google Scholar]
- 14.Zhou X. Training-based SWIPT: Optimal power splitting at the receiver. IEEE Trans. Veh. Technol. 2015;64:4377–4382. doi: 10.1109/TVT.2014.2364196. [DOI] [Google Scholar]
- 15.Krikidis I., Timotheou S., Nikolaou S., Zheng G., Ng D.W.K., Schober R. Simultaneous wireless information and power transfer in modern communication systems. IEEE Commun. Mag. 2014;52:104–110. doi: 10.1109/MCOM.2014.6957150. [DOI] [Google Scholar]
- 16.Liu M., Liu Y. Power allocation for secure SWIPT systems with wireless-powered cooperative jamming. IEEE Commun. Lett. 2017;21:1353–1356. doi: 10.1109/LCOMM.2017.2672660. [DOI] [Google Scholar]
- 17.Zhang Q., Huang X., Li Q., Qin J. Cooperative jamming aided robust secure transmission for wireless information and power transfer in MISO channels. IEEE Trans. Commun. 2015;63:906–915. doi: 10.1109/TCOMM.2015.2405063. [DOI] [Google Scholar]
- 18.Tang X., Yang W., Cai Y., Yang W., Cao K., Yuan P. Secrecy analysis of full-duplex power-splitting SWIPT networks with artificial noise; Proceedings of the International Workshop on Computer Science and Engineering; Beijing, China. 25–27 June 2017; pp. 950–955. [Google Scholar]
- 19.Yang W., Mou W., Xu X., Yang W., Cai Y. Energy efficiency analysis and enhancement for secure transmission in SWIPT systems exploiting full duplex techniques. IET Commun. 2016;10:1712–1720. doi: 10.1049/iet-com.2015.1147. [DOI] [Google Scholar]
- 20.Zhang J., Pan G., Wang H.M. On physical-layer security in underlay cognitive radio networks with full-duplex wireless-powered secondary system. IEEE Access. 2016;4:3887–3893. doi: 10.1109/ACCESS.2016.2591782. [DOI] [Google Scholar]
- 21.Zhou X., Maham B., Hjorungnes A. Pilot contamination for active eavesdropping. IEEE Trans. Wirel. Commun. 2012;11:903–907. doi: 10.1109/TWC.2012.020712.111298. [DOI] [Google Scholar]
- 22.Wang H.M., Zheng T., Mu P. Secure MISO wiretap channels with multi-antenna passive eavesdropper via artificial fast fading; Proceedings of the IEEE International Conference on Communications; Sydney, NSW, Australia. 10–14 June 2014; pp. 5396–5401. [Google Scholar]
- 23.Hu J., Yang N., Zhou X., Yang W., Cai Y. A versatile secure transmission strategy in the presence of outdated CSI. IEEE Trans. Veh. Technol. 2016;65:10084–10090. doi: 10.1109/TVT.2016.2550032. [DOI] [Google Scholar]
- 24.Bi Y., Chen H. Accumulate and jam: Towards secure communication via a wireless-powered full-duplex jammer. IEEE J. Sel. Top. Signal Process. 2016;10:1538–1550. doi: 10.1109/JSTSP.2016.2600523. [DOI] [Google Scholar]
- 25.Afana A., Asghari V., Ghrayeb A., Affes S. On the performance of cooperative relaying spectrum-sharing systems with collaborative distributed beamforming. IEEE Trans. Commun. 2014;62:857–871. doi: 10.1109/TCOMM.2014.032014.130399. [DOI] [Google Scholar]
- 26.Afana A., Asghari V., Ghrayeb A., Affes S. Cooperative relaying in spectrum-sharing systems with beamforming and interference constraints; Proceedings of the 2012 IEEE 13th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC); Cesme, Turkey. 17–20 June 2012; pp. 429–433. [Google Scholar]
- 27.Zhang T., Cai Y., Huang Y., Duong T.Q., Yang W. Secure full-duplex spectrum-sharing wiretap networks with different antenna reception schemes. IEEE Trans. Commun. 2017;65:335–346. doi: 10.1109/TCOMM.2016.2625257. [DOI] [Google Scholar]
- 28.Zhang T., Huang Y., Cai Y., Zhong C., Yang W., Karagiannidis G. Secure multi-antenna cognitive wiretap networks. IEEE Trans. Veh. Technol. 2017;66:4059–4072. doi: 10.1109/TVT.2016.2609396. [DOI] [Google Scholar]
- 29.Zeng Y., Zhang R. Full-duplex wireless-powered relay with self-energy recycling. IEEE Wirel. Commun. Lett. 2015;4:201–204. doi: 10.1109/LWC.2015.2396516. [DOI] [Google Scholar]
- 30.Gradshteyn I.S., Ryzhik I.M. Table of Integrals, Series, and Products. 7th ed. Elsevier/Academic Press; Amsterdam, The Netherlands: 2007. [Google Scholar]
- 31.Xu X., Yang W., Cai Y., Jin S. On the secure spectral-energy efficiency tradeoff in random cognitive radio networks. IEEE J. Sel. Areas Commun. 2016;34:2706–2722. doi: 10.1109/JSAC.2016.2605901. [DOI] [Google Scholar]
- 32.Yan S., Yang N., Geraci G., Malaney R., Yuan J. Optimization of code rates in SISOME wiretap channels. IEEE Trans. Wirel. Commun. 2015;14:6377–6388. doi: 10.1109/TWC.2015.2453260. [DOI] [Google Scholar]
- 33.Wang L., Cai Y., Zou Y., Yang W., Hanzo L. Joint relay and jammer selection improves the physical layer security in the face of CSI feedback delays. IEEE Trans. Veh. Technol. 2016;65:6259–6274. doi: 10.1109/TVT.2015.2478029. [DOI] [Google Scholar]