Abstract
In recent years, industrial wireless networks (IWNs) have been transformed by the introduction of mobile nodes, and they now offer increased extensibility, mobility, and flexibility. Nevertheless, mobile nodes pose efficiency and reliability challenges. Efficient node deployment and management of channel interference directly affect network system performance, particularly for key node placement in clustered wireless networks. This study analyzes this system model, considering both industrial properties of wireless networks and their mobility. Then, static and mobile node coverage problems are unified and simplified to target coverage problems. We propose a novel strategy for the deployment of clustered heads in grouped industrial mobile wireless networks (IMWNs) based on the improved maximal clique model and the iterative computation of new candidate cluster head positions. The maximal cliques are obtained via a double-layer Tabu search. Each cluster head updates its new position via an improved virtual force while moving with full coverage to find the minimal inter-cluster interference. Finally, we develop a simulation environment. The simulation results, based on a performance comparison, show the efficacy of the proposed strategies and their superiority over current approaches.
Keywords: industrial wireless network, clustered network, maximal clique, deployment, reliability
1. Introduction
Wireless networks have attracted considerable attention due to their many advantages and industrial applications, such as industrial equipment monitoring and control order transmission. In the new Industry 4.0 architecture, or smart factory, the new manufacturing system must accomplish multi-layered and ubiquitous data communication, such as machine-to-machine (M2M), machine-to-user (M2U), and machine-to-cloud (M2C) server capability [1,2]. Recently, with the increased development of smart manufacturing, a growing number of mobility elements have been introduced into the current system. Because industrial mobile wireless networks (IMWNs) can save costs and accommodate flexible deployment, IMWNs are widely used in manufacturing systems [3,4]. Wireless networks play a key and increasing role in these systems; thus, efficient deployment of network nodes and anti-interference schemes are essential for the reliable operation of IMWNs.
With the progressing research of industrial wireless networks (IWNs), network structure design and optimization has become an area of considerable interest. Previous studies have determined that a clustered network framework has the following advantages [5,6,7]: (1) Since cluster heads are responsible for most of the communication and management tasks, a clustered network structure can reduce the communication load of other nodes in a network; thus, clustered networks are easy to centrally manage. (2) In a clustered sub-system, channel interference can be reduced by time division multiple access (TDMA). (3) A group network is beneficial to the entire network’s security and privacy because such a system can easily isolate a network virus or attack. Meanwhile, compared with traditional networks, wireless networks have the following new features. Firstly, IMWNs are adopted to gather important parameters (such as gas emission) or deliver control instruction and emergent information, so low communication latency and high communication stability are required [8,9]. Secondly, in industrial domains, wireless networks consist of equipment with limited forms of energy, such as batteries in harsh environments. If the wireless nodes consume high amounts of energy, networks face low network connectivity and lifetime [10,11]. Summary, IMWNs are different from traditional wireless networks in terms of their features and performance, such as their real-time operation, reliability, and low-energy consumption. Therefore, new manufacturing systems add challenges to IMWN key node deployment (in the form of access points, cluster heads, and group leaders, for example) and increase inter-cluster interference.
Overall, network deployment can be divided into target coverage, area coverage, and barrier coverage [12]. Previous work on network node deployment has concentrated on cases in which nodes are static and deterministic. Moreover, those research studies focused on the network connectivity, energy consumption or coverage ratio. Channel interference consists of inter-clustered, intra-clustered, and neighbor interference. Studies addressing anti-interference [13,14] have made use of time slots and MIMO (multiple-input multiple-output) technologies to reduce interference from different layers. Although these studies provide beneficial references on the topic, many deficiencies exist in the current state of research: (1) Most studies independently solve deployment or anti-interference. (2) Recent works have not considered industrial applications. In this study, we jointly develop optimal strategies for cluster head deployment and inter-cluster interference by considering the needs of industrial applications. The main contributions of the present study are summarized as follows:
-
(1)
Using the trajectory discretization method, static and mobile node coverage is simplified into a one-dimensional target coverage problem. From the perspective of a virtual cluster’s interior, we simplify the target coverage to a maximal clique problem by developing and analyzing a mathematical model.
-
(2)
We divide the problem into two stages. In the first stage, for full target coverage and improved real-time performance, a distributed double-layer Tabu search is employed to solve the optimal number and position of cluster heads. In the second stage, we use an improved virtual force and a virtual cluster head movement to redeploy the position of the cluster heads.
This paper is organized as follows. A brief literature review on network deployment and inter-cluster interference in wireless networks is presented in Section 2. Preliminary information and the system model are provided in Section 3. Section 4 details new methods for optimal coverage via two stages. Simulations, results, and analysis are presented in Section 5. Finally, the paper concludes with a summary in Section 6.
2. Related Works
In this section, previous works on network deployment and wireless network anti-interference methods is reviewed.
Network coverage, which is the key problem of network deployment, directly affects the performance of the entire network and has thus drawn attention from a large number of researchers. Based on the description above, the coverage consists of target, area, and barrier coverage. Target coverage is the basic problem into which all other coverage problems can be transformed. In [15,16,17,18,19], the authors employed heuristic and improved methods to optimize target coverage from the perspective of maximum network lifespan, network coverage ratio, and error-tolerance rates; the feasibility of the algorithms were independently verified via simulation experiments. However, these algorithms focus only on the target coverage of nodes in a static state; they do not consider the mobile situation. Therefore, in [20,21], to reduce the moving distance and minimal energy consumption, the authors provided a mathematical model and used strategies based on Hungarian and greedy algorithms. Hamid et al. [22] proposed a method for updating the new location of a mobile node for a minimum of coverage holes based on the configuration of Voronoi polygons and the virtual force. However, this and similar studies focused on the conventional, environment-sensing, node coverage problem and did not consider the specific application or actual demand of the industrial environment [23,24].
In industrial wireless network deployment research, another report [25] reviewed and discussed the applicability and limitation of different methods for target coverage in industrial applications; the simulation results demonstrated the method’s advantages and disadvantages via different evaluation indicators. The authors of [26] jointly optimized node deployment and dynamical sleep scheduling via a hybrid harmony search and genetic algorithms. Another study [27] decisively solved the connectivity problem that occurs when industrial wireless sensors are grouped, established a wireless network and inter-group connection system model, and optimized the deployment of nodes in the industrial environment. Industrial wireless network deployment studies have focused on single performance indexes of wireless networks in industrial environments, such as energy consumption, connectivity, or moving distance. However, the key indicators of IWNs, such as real-time stability, have been given less consideration.
As wireless network research has developed, an increasing number of studies have shown that grouped or clustered network frameworks have a strong advantage over network management, security, and other features [28]. However, inter-cluster interference becomes a bottleneck problem, particularly in single-radio-frequency systems. The authors of [29] divided M2M wireless communication interference into inter-cluster and intra-cluster interference and then employed a mixed integer nonlinear programming method to manage radio resources. The authors of [30,31] introduced an adaptive time-slot dynamic, self-management mechanism for increasing the inter-cluster interference; the simulation results verified the strategy. In addition, previous studies [32,33,34] have increased the reliability of clustered networks by adopting dynamic sleep, MIMO, and cognitive radio technologies. However, these methods require high-resolution time synchronization and neighbor node information; thus, they are not easily applied in the industrial domain.
3. Preliminaries
3.1. Network Model and Hypothesis
In industrial environments, smart manufacturing systems employ hybrid networks, including both static and mobile nodes, thus increasing mobility and flexibility. To facilitate modeling of this type of problem without losing generality, the present study introduces the following network assumptions. (1) Networks adopt a single wireless frequency radio band. (2) Network nodes work with omnidirectional antennas. (3) Mobile node paths remain unchanged. Based on these assumptions, we present the following clustered IMWN model.
Let A denote the industrial environment on a 2D plane. We assume that the industrial environmental interferences of environment are static, so a fixed effective communication range is used. Consider a set of n ≥ 1 static nodes in A, denoted by , with a communication range of . Each node has a unique ID number and a coordinate location . The main task of the static node is to sense key parameters from the physical world and then to transmit or receive the data to or from clustered heads. Let be the set of communication loads of static nodes Sc. A cluster is a sub-system. A finite number of cluster heads Z > 1 work in A. Let be the set of cluster heads. A cluster head api has the coordinate location , with an efficient communication range . Assume that IMWN A has m > 0 mobile nodes, denoted by , with the communication range . Let be the set of communication loads of static nodes SR. Meanwhile, for a better understanding of the problem, assume that t communication loads of wireless static and mobile nodes are fixed. Mobile nodes move along the path via vision, magnetic wires, ribbons, and so on. Let and be the set of paths and velocity, respectively.
3.2. Network Model and Hypothesis
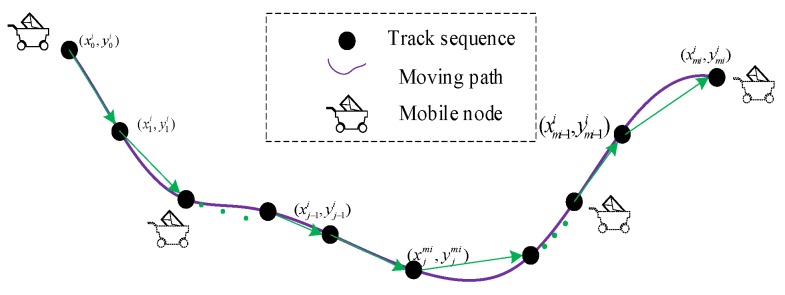
Discretization of the mobile node trajectory: Assume that mobile node communicates with cluster head APj over time t, as shown in Figure 1. Therefore, we obtain the mobile node moving a distance dm = vi × t during the period, and the coordinate location of changes from into . Thus, according to the rule, li can be divided into mi sections. In other words, we can use a series of discrete points to represent the moving path.
Figure 1.
Discrete and continuous moving paths.
Definition 1.
Communication trajectory sequence: The communication trajectory sequence Ti, of mobile nodes , along path li is the set that contains a series of moving positions over t. Namely, .
According to Definition 1, we can use a discrete point set T′ to express the set of paths L. Thus, the discrete point set T′ is
| (1) |
where . Through discretization and the use of Definition 1, the coverage of the moving trajectories is transformed into the covering of point sets T′.
Definition 2.
Full coverage: When all members si of S are covered by AP, then AP fully covers S. The symbol denotes full coverage.
Theorem 1.
The necessary condition for path L to be fully covered by cluster head AP is that point set T′ is fully covered by AP.
Proof.
If path L is covered by AP, then all points Pall are covered by AP, that is, . According to Definition 1, ; thus, point set T′ is fully covered by AP.
Starting from Definitions 1 and 2 and Theorem 1, we note that the problem of full coverage can be changed into a point set coverage problem. Let P′ denote the target point set, such that and . Similarly, let point set AP denote the cluster heads. We can obtain the Euclidean distance d between point and cluster head as follows:
| (2) |
We assume that . When d (pi, apj), i.e., the distance between point pi and the cluster head apj, is less than the effective coverage radius of cluster head R, then apj covers the target point pi. Let Covij(pi, apj) be the coverage function:
| (3) |
Definition 3.
Optimal cluster coverage problem (OCCP): We seek the minimum AP to fully cover the target point. Given the target point set P′ in A, we want the minimum number and location of AP that fully covers P′, for which the following function is minimized.
(4)
The problem described above is called the OCCP.
Wireless channel model: Assume that Pt is the transmission power of apj; then, the received power of the target point pi is described by the following:
| (5) |
Let Bi be the clustered neighbor set such that all cluster heads satisfy , and let ap0 be the corresponding cluster head of pi. Therefore, we can obtain the inter-cluster interference power Pinf_intercluster of target point pi as follows:
| (6) |
Then, the signal-to-noise ratio (SNR) of pi, in cluster ap0, is
| (7) |
In Equations (5) and (6), a(d0) is the path loss of wireless signals with the distance d0; is a path loss index such that in the industrial environment. In addition, let be the correlation function of the two cluster heads api and apj. The following function is described:
| (8) |
where and are the covered target point sets of api and apj, respectively.
According to Equations (5)–(7), when Pt is constant and the environment is determined, a decreasing Pinf_intercluster is the most effective way to increase SNR, which implies that dij is increasing. Therefore, we use the effective distance ol between cluster heads to represent the inter-cluster interference power. For cluster head node api, there are k cluster heads with a signal overlapping area, and the cluster head node api for all effective overlap distances is
| (9) |
The total effective overlapping distance, mapped by the inter-cluster interference signals of the whole network, can be expressed by
| (10) |
Definition 4.
Best communicated cover problem (BCCP): We seek the best location of AP with the minimum inter-cluster interference. Given the target points set P′ in A, we want the minimum inter-cluster interference of AP that fully covers P′, for which the OL function is minimized.
(11)
3.3. Maximal Communication Latency and Maximal Energy Consumption
In the section, we will analyze the proposal from communication latency, energy consumption, and number of inter-cluster interference targets.
Maximal communication latency (MCL): In a cluster, we will use the maximal communication latency to describe the communication real time in a cycle. Assume that in one cluster, there are target points and inter-cluster interference targets. We can get the MCL for the one cluster
| (12) |
where Vc is the communication rate, and Probj is the data recommunication probability for the j-th inter-cluster interference targets. Therefore, we can get the maximal communication latency by and . Consider the communication and channel energy consumption spent, we can obtain the maximal energy consumption (MEC), formulated as follows:
| (13) |
where are the energy consumption coefficients of communication and wireless channel, respectively.
4. Our System Model (Proposed Methods)
In this section, we present our algorithm. First, we employ a distributed double Tabu search method to solve the OCCP and to find the fully covered cluster head set AP and the associated coarse locations. Then, an improved virtual force and virtual motion strategy is adopted to find the best results of the BCCP based on the cluster head set AP.
4.1. Optimal Cluster Head Coverage Problem—Stage I
In industrial environments, coverage of all points is the main communication problem in industrial network data. From the view of a single cluster analysis, the relationship between points in the same cluster is the premise for solving the problem. In a cluster, any Euclidean distance dij of two points (vi, vj) meets the condition . If any two points meet the condition, we call the two points connected. As a result, we obtain the following theorems.
Theorem 2.
If the two-point Euclidean distance ≤2R denotes that two points are collected, then the target point set V in a cluster is a subset of the maximal clique C that includes >V.
Proof.
For a cluster radius of R, the Euclidean distance between any two points is less than 2R. That is, because, when dij ≤ 2R, the two points are connected. In other words, any two target points are connected. According to the definition of the maximum clique, we obtain . That is, V is a subset of the maximal clique C.
Theorem 3.
The OCCP is an NP-hard problem.
Proof.
According to Theorem 2, V is a subset of a maximal clique; thus, the OCCP should aim to find the maximal clique enumeration (MCE) of all target points of P′. MCE is an NP-hard problem. The OCCP is also an NP-hard problem.
According to Theorem 3, it is challenging to find an algorithm that obtains all possible maximal cliques of a graph in polynomial time; thus, an intelligent heuristic algorithm is used in this study.
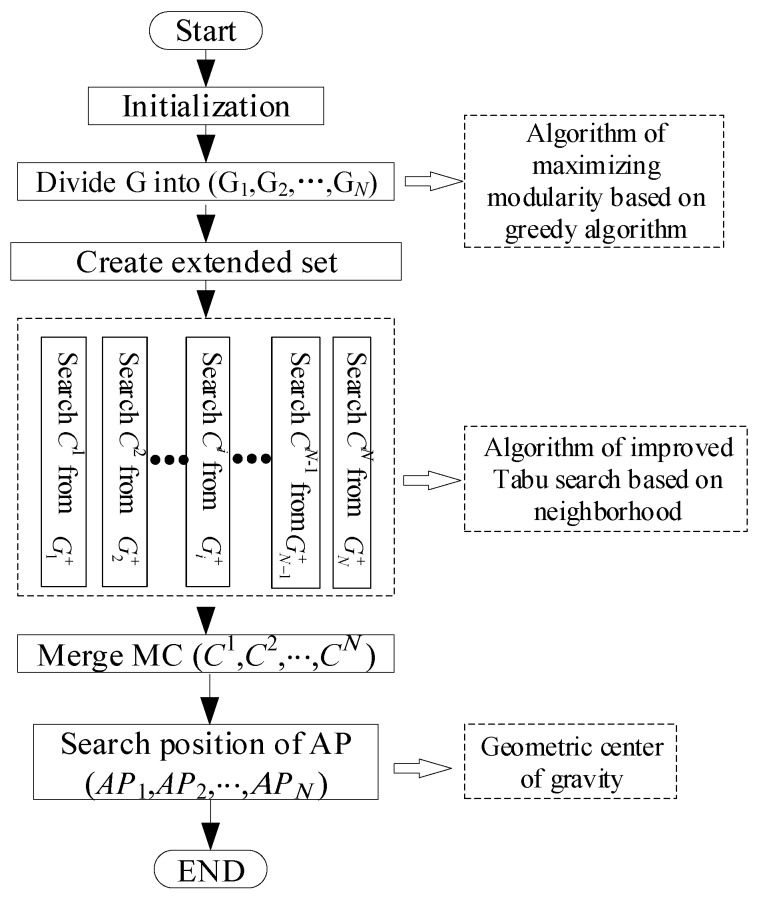
The distributed double Tabu search method: In industrial domains the algorithms provide not only efficiency but simplicity and easily operation, the Tabu search method has the above advantages and is fit to small-scale situations. Therefore, for solving the OCCP and MCE, an improved Tabu search method is adopted in the section. Given a deterministic graph G = {P′, E}, where P′ is the target point set and E is the set of links, let graph G be divided into f regions:
| (14) |
Different methods produce different effects; thus, we employ a complex network modularity Q to divide G:
| (15) |
where eii is the fractional link between community i and the total link G; ai is the fraction of ends of edges that are attached to vertices in community i.
In this study, a greedy algorithm (previously used to maximize the degree of modularity [35]) is used to divide G. The working principle is as follows: First, each target point is regarded as an independent module. Then, according to Equation (11), we compute the increment between the network modularity of any two modules Gi and Gj. Based on the greedy principle, we merge the two modules, which makes the maximum modularity increase and iterate the steps above stepwise until the number of modules is f. For a divided module Gi , let N(Gi) be the neighbor vertex set of Gi with .
Theorem 4.
Given a point v, which belongs to a maximal clique C, and the subgraph Gi, then contains C.
Proof.
A maximal clique C includes a vertex set that is denoted by C = {v, U}; U is the only remaining vertex set after deleting v because and, according to the clique, any members in u ∈ U are now linked with v. Thus, there are two cases: (1) u ∈ Gi and (2) u Gi and their neighbors Gi. In other words, u ∈ N(Gi). Therefore, contains C.
Let be the extended set of Gi and be the extended G. According to the earlier discussion and the properties of the maximal clique, as shown in Figure 2, we adopt the distributed computing method to find the results. We use the double Tabu method to find the results of with the Pi vertex in one subgraph, as shown in Algorithm 1. The method is explained as follows. First, we randomly select a point pi; then, we create the left vertex set of the target P_left = Pi, the maximal clique set Ci = {pi, pj}, pj ∈ N(pi), and the candidate select set Candi_set = N(pi) ∩ N(Pj). In addition, the Tabu list is given such that Tabu_set = {pi, pj}. We randomly select a target pont p_next from the Candi_set to join in Ci = {pi, pj, p_next}; then, we update Candi_set = − Cj until Candi_set = ø. Next, we record the Cj in and delete the member Ci from P_left. The vertex degree of the deleted member is less than |Ci| − 1. We repeat the above steps until P_left = ø.
| Algorithm 1: The double-layer Tabu search maximal clique (DTSMC). | |
|
Input: , Degree () and N() Output: |
|
| 1 | Initialization: randomly select the min degree vertex Current from , Tabu_first_set = ø, Tabu_second_set = ø, = ø, Ci = ø, p_next = ε, P_left = |
| 2 | for j = 1; j ≤ |P_left|; j++ do // Find maximal clique of subgraph |
| 3 | Candi_set = N(); |
| 4 | while |Candi_set| ≠ ø // Find the maximum clique at the current node |
| 5 | Randomly select a vertex p_next from Candi_set; |
| 6 | if p_next ∈ // Evaluate common neighbor nodes |
| 7 | Cj ← Cj ∪ {p_next }; |
| 8 | Tabu_second_set ← Tabu_second_set ∪ {p_next}; // Update second-level Tabu list |
| 9 | Candi_set ← − Cj; // |
| 10 | end if |
| 11 | end while |
| 12 | for k = 1, K = |Cj| |
| 13 | if degree() = |Cj| − 1 // Compute the node degree |
| 14 | P_left ← P_left/; // Update second-level candidate solution list |
| 15 | Tabu_firt_set = − P_left; // Update first-level Tabu list |
| 16 | end if |
| 17 | end for |
| 18 | = + Cj; |
| 19 | end for |
| 20 | Return //Return all maximal clique |
Figure 2.
The distributed parallel improved Tabu search algorithm.
Determine the cluster head number and locations: Using Algorithm 1, we can obtain the sub maximal clique set for each subgraph from ; then, we delete the same maximal clique, which is C = Merge{C1, C2, … }. Let C = {c1, c2, …, cz}, where each maximal clique represents a cluster head. However, to deal with communication load and obtain low communication latency, we need to determine the number of cluster heads. Consider ki as the number of coverage targets for ci () and , in accordance with the maximum allowable communication load for a cluster head. We can compute the i-th cluster head number and the total number of cluster heads in an entire IMWN, . The formulations are given by
| (16) |
| (17) |
where Dj is the communication load of the j-th static or mobile node. Dmax is the maximum allowable communication load for a cluster head, and works to round up to the value.
After the maximal cliques of target points P′ and the number of cluster heads are obtained, we determine the coarse location of each cluster head. First, we select the related number of targets for keeping commination load less than Dmax. We use the selected targets’ gravity center to compute the location of the cluster head. The formulations are given by
| (18) |
where denotes the coordinate location of the j-th target point position of APi, and |·| obtains the number of target points in one cluster. If there are multiple cluster heads in the same maximal clique, an orthogonal frequency or MIMO technologies are adopted.
4.2. Minimum Inter-Cluster Interference Problem—Stage II
From the discussion above, we know that any overlapping distances of cluster heads can express inter-cluster interference. Thus, in this section, we use an improved virtual force and virtual motion to solve the BCCP. In the traditional virtual force model, when the distance between two clusters api and apj is less than 2R, i.e., , then the virtual force is a repulsive force; otherwise, it is an attractive force. The model is not fitted to the minimal inter-cluster interference; when there are no target points in the overlap, for example, the above model is inefficient. Therefore, we use only the repulsive force to express the virtual force, and the function of inter-cluster correlation is introduced into the model. We use the following formulation to express the virtual force:
| (19) |
where the dij is the distance between the api and apj clusters. Then, the strength of the virtual force in the x- and y-axes can be expressed as follows:
| (20) |
where is the angle between the virtual force and the x-axis. Let be the neighboring cluster set of cluster heads api; we can then obtain the total virtual force of api in the industrial wireless network in A. We use the following equation to determine the total virtual force:
| (21) |
It is then straightforward to obtain the total virtual force of the entire network as follows:
| (22) |
According to the analysis above, we minimize the virtual force to solve the BCCP and ensure that all target points are fully covered:
| (23) |
A minimum inter-cluster interference strategy based on improved virtual force and motion: After obtaining the virtual force, we use the virtual motion of the cluster heads to reduce the virtual force. To obtain Equation (19), certain sub-problems must be solved: (1) moving the maximal distance din and (2) finding the stop motion condition. The normal line of the virtual force of api divides the members of api into right and left sections: and . The left section members (target points) restrict the moving distance by meeting . For any member , we use the following formulation to compute the of the member of pk in the cluster head api:
| (24) |
where dpf is the distance between the left node pj and the line of the virtual force; dop is the distance between the left node pj and the cluster head api. Equation (19) is used to compute the maximal distance din:
| (25) |
where dp is the set of for the remaining members of api and dmove_step is the iterative moving distance. After achieving the maximum moving distance din, we use the following method to update the new location of the cluster head () according the current position ():
| (26) |
where Fx and Fy are the virtual forces in the x- and y-axis, respectively, and FTH is the threshold value.
The details of the proposal are given in Algorithm 2 (VFM). The method is explained as follows. Suppose that there are Z clusters and that their position is APPosition. Then, NAP is an AP cluster head neighboring set. During each iteration h of Algorithm 2, we first compute the virtual force of each cluster (Line 3) and then determine din (Lines 5–10) and the new position of the cluster head (Lines 12–16). Line 18 involves moving the cluster head to a new position. Note that the positions are within the region A. When h achieves the max value, Max_interation, or , the iteration is stopped, and we return .
| Algorithm 2: The minimum inter-cluster interference strategy based on improved virtual force and motion. | |
|
Input: and NAP, , FTH Output: APPositon_new |
|
| 1 | Initialization: Max_interation; C; |
| 2 | While (h < Max_interation) |
| 3 | if |
| 4 | for j = 1; j ≤ |AP|; j++ do |
| 5 | Calculate the virtual force of apj according to Equations (15)–(18); |
| 6 | if > 0 |
| 7 | Calculate the maximum move distance dp according to Equation (20); |
| 8 | if dp > dmove_step // Ensure that the cluster head covers its target points |
| 9 | din ← dmove_step |
| 10 | else |
| 11 | din ← dp |
| 12 | end if |
| 13 | Update the new position of according to Equation (22) |
| 14 | if apposition_new ∈ A // Evaluate whether the new position is in A |
| 15 | apposition_new ← chposition_new |
| 16 | else |
| 17 | apposition_old ← the corresponding boundary value of A |
| 18 | end if |
| 19 | Move the cluster head to the new position |
| 20 | apposition_new ← chposition_new |
| 21 | end if |
| 22 | Compute the total virtual force of the entire network |
| 23 | end for |
| 24 | end if |
| 25 | end while |
| 26 | Return APPosition_new // Return the new position of the cluster heads |
5. Simulation Results
To evaluate the deployment algorithm of cluster heads of the IMWN, the deployment simulation environment is built in the simulation software. The performance of the algorithm is tested numerically. By comparing the algorithm with similar current approaches, the performance of each algorithm is evaluated via the following three aspects: (1) the cluster head number (CHN), (2) the location changes of CHs using VFM, and (3) the inter-cluster interference target point number.
5.1. Experimental Environment
The simulation settings are described as follows. The simulation area A is represented as A = 1000 m × 1000 m. The discrete path points and static nodes constitute the set of target points P′ such that the discrete path points constitute 20% of the total. The transmission range R of every target point is 50–100 m, and the traffic load of each node is 10. The number of target points within the simulation area A is 50–100. Using the algorithm proposed here, the average results are obtained by repeating the simulation 100 times, comparing the algorithm to the regular hexagon deployment [36] (RHD), random placement (RP) [37], and K-means (KM) [38] methods. Additionally, the other parameters of the proposed method are given as follows in Table 1. In the RHD method, we use communication range R as the hexagon side length; in the KM method, we use the increasing K value to cover all target points. Similarly, in the RP method and in our proposed method, the cluster heads are deployed until the all wireless nodes and target points are fully covered.
Table 1.
Parameters values used in the simulation.
| Parameter | Value | Description |
|---|---|---|
| R | 50, 100, 150, 200 | Communication radius |
| n | 50, 60, 70, 80, 90, 100 | Number of target points |
| FTH | 0 | Virtual force threshold |
| Di | 100 Mb | Communication load of wireless node |
| Dmax | 500 Mb | Maximum allowable communication load |
| 0.1 J/Mb | Coefficient of communication energy consumption | |
| 0.08 J/Mb | Coefficient of wireless channel energy consumption | |
| Prob | 20% | Data recommunication probability |
| Vc | 10 Mb/s | Communication rate |
| Dmove_step | 10, 20, 30 | Moving step length |
| Max_iterations | 100 | Number of iterations |
5.2. Results Analysis
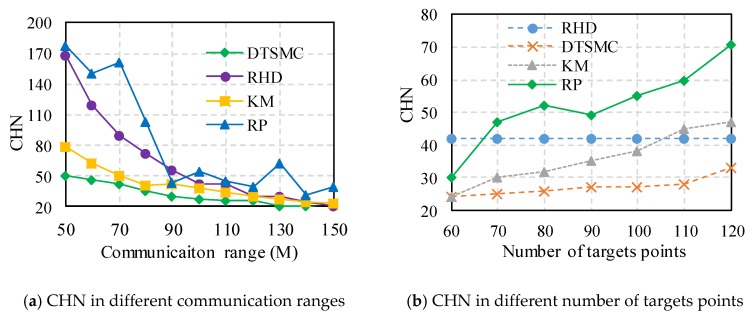
We use the number of cluster heads required to fully cover the target node as the optimization objective to assess the algorithms. Figure 3 shows the network deployment effect diagram using the proposed DTSMC with 50 target points and 14 cluster heads. The results show that the target points (green points) are fully covered by the cluster heads (red circle) as show in Figure 4a. The results also demonstrate the efficiency of the proposal. By keeping the number of target points (n = 100) (and their locations) unchanged and by increasing the communication radius from 50 to 150 m, the CHN curves vary in different ways (DTSMC, KM, RP, and RHD), as shown in Figure 3a. Generally, the CHN decreases as the communication radius R increases. When the communication radius is high, the cluster heads cover more area and more wireless nodes and target points. The CHN of the RP achieves a maximum value, and the RHD increases in value. The DTSMC also obtains the minimum CHN. Thus, the DTSM can achieve the best performance relative to the other algorithms in terms of CHN. When the communication radius is 100 m, the DRSMC can save 35%, 28%, and 50% CHN relative to RHD, KM, and RP, respectively.
Figure 3.
The results of CHN in different methods.
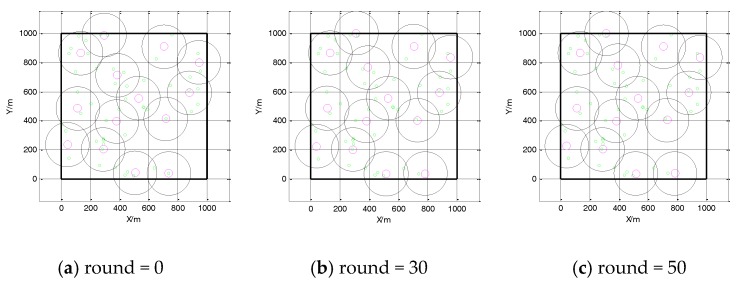
Figure 4.
Location changing in different iteration with virtual force and motion.
Similarly, Figure 3b shows the CHN figure with a communication radius R = 100 m and where the target points increase from 60 to 120. In general, the CHN for the remaining algorithms, excluding RHD, increases with the number of target points, and RHD remains unchanged. In the RHD (regular hexagon deployment) method, when the communication range is given, the number of cluster heads reaches a constant value. Therefore, when the number of target points increases, there are no changes to the CHN in RHD. Clearly, DTSMC requires that the smallest CHN be below several target points. When n is larger than 70, RP achieves the highest possible rising rate of CHN. If n is larger than 105, the CHN of KM is more than that of RPH. Whether the radius of communication increases or the number of target points increases, the proposed strategies can find the smallest CHN. In other words, our deployment strategy has an advantage in terms of the number of cluster heads and the performance with full coverage. The reasons are that in our proposal, by using a distribution Tabu search, it is easy to obtain optimal results.
The subfigures of Figure 4 show the changing snapshot locations of cluster heads such that R = 150 m and n = 50. The red circles are the centers of the cluster heads, the green circles are the target points, and the black circles are the cluster communication radii and the cluster ranges. Figure 4a shows the initial configuration, Figure 4b shows the configuration after 50 rounds, and Figure 4c shows the final deployment. At first, several inter-cluster interference target points exist. When the round is 23, the location of cluster heads will not change; if the round is more than 50, the number of inter-cluster interference target points decreases. It is shown that our proposal is convergent, and the cluster head deployment can enable full coverage for all target points. A comparison of Figure 4b with Figure 4c indicates that no difference exists in the location and deployment of cluster heads. Furthermore, the virtual force of the whole network achieves the minimum value, and the inter-cluster interference is the smallest final configuration. Moreover, Figure 4 shows the feasibility and convergence of the algorithms.
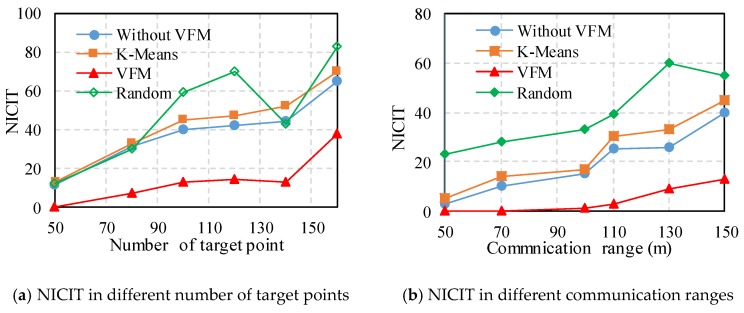
We use the number of inter-cluster interference targets (NICIT) to assess the reliability of the deployment and efficacy of the VFM. Figure 5a shows the NICIT curve resulting from four strategies (without VFM, KM, or RP) with n targets (such that n = 100) and with various communication radii from 50 to 100 m. The NICIT increases after the targets are added, and RP yields the worst effects. VFM provides the best performance, particularly if R is less than 140. When R is more than 90 m, the NICIT greatly increases for the remaining methods, except for VFM. The NICIT for R = 150 m, with different methods, is the number of target points from 50 to 150, as shown in Figure 5b. Generally, all NICIT values rise when n is added, as a result of more target points increasing the probability of inter-clutter interference. Similarly, VFM produces the best performance in terms of NICIT. Relative to KM, without VFM and RP, VFM reduces the NICIT values by 93%, 94%, and 94%, respectively. Moreover, our proposal can decrease the inter-cluster interference and increase the reliability of the IMWNs. Since our algorithm adopts the virtual force and motion on cluster heads to reduce inter-cluster interference, the presented strategy always obtains the lowest NICIT compared with other methods.
Figure 5.
The results of NICIT in different methods.
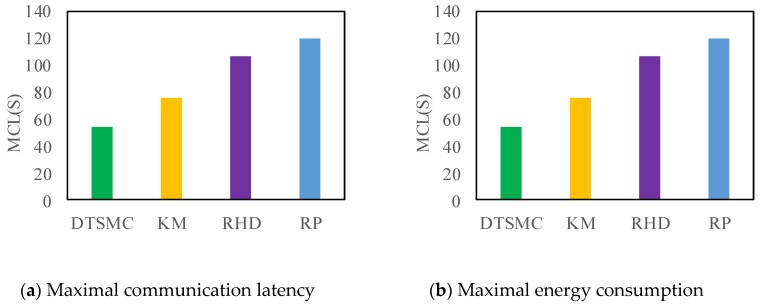
We use the MCL and MEC as evaluation criteria in one cycle for network communication latency and energy consumption. Figure 6 shows the MCL using the proposed DTSMC and other methods with 50 target points for full coverage. Figure 6a shows the results of MCL of all methods. The results demonstrate that the DTSMC has the lowest MCL. Namely, when n = 50 and R = 100 m, the DTSMC has low max communication latency and will perform better in real time. DRSMC can save MCL more than 5%, 10%, and 20% relative to RHD, KM, and RP, respectively. In the same way, Figure 6b demonstrates the MEC of the different strategies. The DTSMC shows the same trend; our proposal achieves the lowest MEC. The DTSMC, compared with other algorithms, consumes less energy. In sum, employing the maximal communication load limit during the cluster head deployment, DTSMC performs better in terms of MCL and MEC.
Figure 6.
The maximal communication latency (MCL) and maximal energy consumption (MEC) in different methods.
6. Conclusions
IMWNs form a significant basis for connecting a smart factory, an Industry 4.0 site, or other intelligent manufacturing systems. In clustered networks, full coverage and the reliable deployment of cluster heads are directly related to the performance of the entire system, such as real-time response and reliability, making such factors a topic of active research in academia and industry. Wireless node deployment is a hot topic for wireless networks, as previous work has not considered the properties of industrial applications, and the current approaches are not suitable for manufacturing systems. We employ an appropriate system model to simplify the static and mobile node coverage to target coverage. We divide the full target coverage into two stages: maximal cliques for full coverage and minimal inter-cluster interference. Then, we apply the optimal strategies by adopting a distributed double-layer Tabu search and improve the virtual force and motion. We developed a simulation of our proposal, and the results demonstrate that our strategies can reduce the number cluster heads and increase reliability by comparison to other traditional methods such as RHP, KM, and RP. Meanwhile, comparing results of the maximal communication latency and maximal energy consumption of IMWNs demonstrates that our methods can reduce energy consumption and increase real-time communication. In the future, we will study the changing communication range and loads. We also plan to apply the proposal to our prototype platform and other industrial applications.
Acknowledgments
This project was supported in part by grants from the Fundamental Research Funds for the Central Universities (Nos. 2015ZZ079, and x2jqD2170480), the National Basic Research Program of China (973 project, 2013CB035403), the Natural Science Foundation of Guangdong Province, China (Nos. 2015A030308002, and 2017B030311008), the Science and Technology Planning Project of Guangdong Province (No. 2015B010917001), and the National Natural Science Foundations of China (No. 51575194).
Author Contributions
Di Li and Chengliang Liu conceived and designed the experiments; Zhijie Dong and Yage Hu analyzed the data and performed the experiments; Xiaomin Li wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Wollschlaeger M., Sauter T., Jasperneite J. The Future of Industrial Communication: Automation Networks in the Era of the Internet of Things and Industry 4.0. IEEE Ind. Electron. Mag. 2017;11:17–27. doi: 10.1109/MIE.2017.2649104. [DOI] [Google Scholar]
- 2.Wan J., Xia M. Cloud-Assisted Cyber-Physical Systems for the Implementation of Industry 4.0. Mob. Netw. Appl. 2017;22:1157–1158. doi: 10.1007/s11036-017-0874-1. [DOI] [Google Scholar]
- 3.Li D., Li X., Wan J. A Cloud-Assisted Handover Optimization Strategy for Mobile Nodes in Industrial Wireless Networks. Comput. Netw. 2017;128:133–141. doi: 10.1016/j.comnet.2017.05.026. [DOI] [Google Scholar]
- 4.Zheng T., Gidlund M., Åkerberg J. WirArb: A New MAC Protocol for Time Critical Industrial Wireless Sensor Network Applications. IEEE Sens. J. 2016;16:2127–2139. doi: 10.1109/JSEN.2015.2504948. [DOI] [Google Scholar]
- 5.Jia D., Zhu H., Zou S., Hu F. Dynamic Cluster Head Selection Method for Wireless Sensor Network. IEEE Sens. J. 2016;16:2746–2754. doi: 10.1109/JSEN.2015.2512322. [DOI] [Google Scholar]
- 6.Wei D., Jin Y., Vural S., Moessner K., Tafazolli R. An Energy-Efficient Clustering Solution for Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2011;10:3973–3983. doi: 10.1109/TWC.2011.092011.110717. [DOI] [Google Scholar]
- 7.Hu S., Han J., Wei X., Chen Z. A multi-hop heterogeneous cluster-based optimization algorithm for wireless sensor networks. Wirel. Netw. 2015;21:57–65. doi: 10.1007/s11276-014-0769-z. [DOI] [Google Scholar]
- 8.Shu L., Mukherjee M., Hu L., Bergmann N., Zhu C. Geographic Routing in Duty-Cycled Industrial Wireless Sensor Networks with Radio Irregularity. IEEE Access. 2017;4:9043–9052. doi: 10.1109/ACCESS.2016.2638441. [DOI] [Google Scholar]
- 9.Shu L., Mukherjee M., Wu X. Toxic gas boundary area detection in large-scale petrochemical plants with industrial wireless sensor networks. IEEE Commun. Mag. 2016;54:22–28. doi: 10.1109/MCOM.2016.7588225. [DOI] [Google Scholar]
- 10.Wang J., Kim J.U., Shu L., Niu Y., Lee S. A Distance-based Energy Aware Routing algorithm for wireless sensor networks. Sensors. 2010;10:9493–9511. doi: 10.3390/s101009493. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Li X., Li D., Wan J., Liu C., Imran M. Adaptive Transmission Optimization in SDN-based Industrial Internet of Things with Edge Computing. IEEE Internet Things J. 2018 doi: 10.1109/JIOT.2018.2797187. [DOI] [Google Scholar]
- 12.Deif D.S., Gadallah Y. Classification of Wireless Sensor Networks Deployment Techniques. IEEE Commun. Surv. Tutor. 2014;16:834–855. doi: 10.1109/SURV.2013.091213.00018. [DOI] [Google Scholar]
- 13.Jiang Z., Zhou S., Niu Z. Optimal Antenna Cluster Size in Cell-Free Large-Scale Distributed Antenna Systems with Imperfect CSI and Intercluster Interference. IEEE Trans. Veh. Technol. 2015;64:2834–2845. [Google Scholar]
- 14.Chen S., Cheng R.S. Clustering for Interference Alignment in Multiuser Interference Network. IEEE Trans. Veh. Technol. 2014;63:2613–2624. doi: 10.1109/TVT.2013.2292897. [DOI] [Google Scholar]
- 15.Gu Y., Ji Y., Li J., Zhao B. Covering Targets in Sensor Networks: From Time Domain to Space Domain. IEEE Trans. Parallel Distrib. Syst. 2012;23:1643–1656. doi: 10.1109/TPDS.2012.99. [DOI] [Google Scholar]
- 16.Zorbas D., Glynos D., Kotzanikolaou P., Douligeris C. Solving coverage problems in wireless sensor networks using cover sets. Ad Hoc Netw. 2010;8:400–415. doi: 10.1016/j.adhoc.2009.10.003. [DOI] [Google Scholar]
- 17.Dimple M., Man J. Maximum coverage heuristics (MCH) for target coverage problem in Wireless Sensor Network; Proceedings of the 2014 IEEE International Advance Computing Conference (IACC); Gurgaon, India. 21–22 February 2014; pp. 300–305. [Google Scholar]
- 18.Lu Z., Li W.W., Pan M. Maximum Lifetime Scheduling for Target Coverage and Data Collection in Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2015;64:714–727. doi: 10.1109/TVT.2014.2322356. [DOI] [Google Scholar]
- 19.Willson J., Zhang Z., Wu W., Du D.Z. Fault-tolerant coverage with maximum lifetime in wireless sensor networks; Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM); Kowloon, Hong Kong. 26 April–1 May 2015; pp. 1364–1372. [Google Scholar]
- 20.Chen Z., Gao X., Wu F., Chen G. A PTAS to minimize mobile sensor movement for target coverage problem; Proceedings of the IEEE INFOCOM 2016—IEEE Conference on Computer Communications; San Francisco, CA, USA. 10–14 April 2016; pp. 1–9. [Google Scholar]
- 21.Liao Z., Wang J., Zhang S., Cao J., Min G. Minimizing Movement for Target Coverage and Network Connectivity in Mobile Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2015;26:1971–1983. doi: 10.1109/TPDS.2014.2333011. [DOI] [Google Scholar]
- 22.Mahboubi H., Aghdam A.G. Distributed Deployment Algorithms for Coverage Improvement in a Network of Wireless Mobile Sensors: Relocation by Virtual Force. IEEE Trans. Control Netw. Syst. 2016;4:736–748. doi: 10.1109/TCNS.2016.2547579. [DOI] [Google Scholar]
- 23.Ovsthus K., Kristensen L.M. An Industrial Perspective on Wireless Sensor Networks—A Survey of Requirements, Protocols, and Challenges. IEEE Commun. Surv. Tutor. 2014;16:1391–1412. [Google Scholar]
- 24.Li X., Li D., Wan J., Vasilakos A.V., Lai C.F., Wang S. A review of industrial wireless networks in the context of Industry 4.0. Wirel. Netw. 2015;23:1–19. doi: 10.1007/s11276-015-1133-7. [DOI] [Google Scholar]
- 25.Han G., Liu L., Jiang J., Shu L., Hancke G. Analysis of Energy-Efficient Connected Target Coverage Algorithms for Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2017;13:135–143. doi: 10.1109/TII.2015.2513767. [DOI] [Google Scholar]
- 26.Lin C.C., Deng D.J., Chen Z.Y., Chen K.C. Key design of driving industry 4.0: Joint energy-efficient deployment and scheduling in group-based industrial wireless sensor networks. IEEE Commun. Mag. 2016;54:46–52. doi: 10.1109/MCOM.2016.7588228. [DOI] [Google Scholar]
- 27.Gholami M., Brennan R.W. A Comparison of Alternative Distributed Dynamic Cluster Formation Techniques for Industrial Wireless Sensor Networks. Sensors. 2016;16:65. doi: 10.3390/s16010065. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28.Lee J.H., Kwon T., Song J.S. Group Connectivity Model for Industrial Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2010;57:1835–1844. [Google Scholar]
- 29.Hsieh H.Y., Juan T.C., Tsai Y.D., Huang H.C. Minimizing Radio Resource Usage for Machine-to-Machine Communications through Data-Centric Clustering. IEEE Trans. Mob. Comput. 2016;15:3072–3086. doi: 10.1109/TMC.2016.2528244. [DOI] [Google Scholar]
- 30.Wu T., Biswas S. Minimizing inter-cluster interference by self-reorganizing MAC allocation in sensor networks. Wirel. Netw. 2007;13:691–703. doi: 10.1007/s11276-006-8150-5. [DOI] [Google Scholar]
- 31.Al-Shawaqfeh M., Abu-El-Haija A., Rahman M.J.A. Collision avoidance slot allocation scheme for multi-cluster wireless sensor networks. Wirel. Netw. 2013;19:1187–1201. doi: 10.1007/s11276-012-0527-z. [DOI] [Google Scholar]
- 32.Luo H., Liao J., Sun Y. Efficient Sleep Scheduling for Avoiding Inter-Cluster Interference in Wireless Sensor Networks; Proceedings of the 2013 IEEE Ninth International Conference on Mobile Ad-hoc and Sensor Networks (MSN); Dalian, China. 11–13 December 2013; pp. 414–420. [Google Scholar]
- 33.Moon J.M., Cho D.H. Efficient Cell-Clustering Algorithm for Inter-Cluster Interference Mitigation in Network MIMO Systems. IEEE Commun. Lett. 2011;15:326–328. doi: 10.1109/LCOMM.2011.012511.101865. [DOI] [Google Scholar]
- 34.Zhang Z., Zhang W., Chao H.C., Lai C.F. Toward Belief Function Based Cooperative Sensing for Interference Resistant Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2016;12:2115–2126. doi: 10.1109/TII.2016.2558464. [DOI] [Google Scholar]
- 35.Newman M.E. Fast algorithm for detecting community structure in networks. 6 Pt 2Phys. Rev. E Stat. Nonlinear Soft Matter Phys. 2004;69:066133. doi: 10.1103/PhysRevE.69.066133. [DOI] [PubMed] [Google Scholar]
- 36.Wu P.F., Xiao F., Sha C., Huang H.P., Wang R.C., Xiong N.X. Node Scheduling Strategies for Achieving Full-View Area Coverage in Camera Sensor Networks. Sensors. 2017;17:1303. doi: 10.3390/s17061303. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 37.Vales-Alonso J., Alcaraz J.J. On the optimal random deployment of wireless sensor networks in non-homogeneous scenarios. Ad Hoc Netw. 2013;11:846–860. doi: 10.1016/j.adhoc.2012.10.001. [DOI] [Google Scholar]
- 38.Yu G.J., Yeh K.Y. A K-Means Based Small Cell Deployment Algorithm for Wireless Access Networks; Proceedings of the 2016 International Conference on Networking and Network Applications (NaNA); Hokkaido, Japan. 23–25 July 2016; pp. 393–398. [Google Scholar]