Abstract
The recent innovations in information and communication technologies have appreciably changed the panorama of health information system (HIS). These advances provide new means to process, handle, and share medical images and also augment the medical image security issues in terms of confidentiality, reliability, and integrity. Digital watermarking has emerged as new era that offers acceptable solutions to the security issues in HIS. Texture is a significant feature to detect the embedding sites in an image, which further leads to substantial improvement in the robustness. However, considering the perspective of digital watermarking, this feature has received meager attention in the reported literature. This paper exploits the texture property of an image and presents a novel hybrid texture-quantization-based approach for reversible multiple watermarking. The watermarked image quality has been accessed by peak signal to noise ratio (PSNR), structural similarity measure (SSIM), and universal image quality index (UIQI), and the obtained results are superior to the state-of-the-art methods. The algorithm has been evaluated on a variety of medical imaging modalities (CT, MRA, MRI, US) and robustness has been verified, considering various image processing attacks including JPEG compression. The proposed scheme offers additional security using repetitive embedding of BCH encoded watermarks and ADM encrypted ECG signal. Experimental results achieved a maximum of 22,616 bits hiding capacity with PSNR of 53.64 dB.
Keywords: Medical image authentication, Multiple watermarking, Medical data protection, Wavelet transforms, Texture feature, Quantization
Introduction
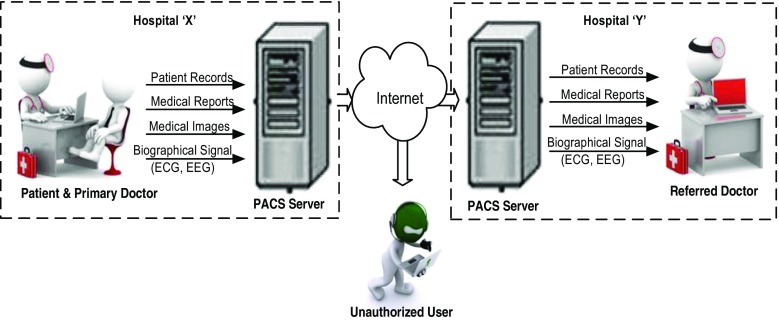
The recent advancements in information and communication technology have changed the landscape of health information system (HIS). A typical HIS (as depicted in Fig. 1) collects vast amount of medical data from the health sectors (say hospital “X”) and converts the data into information for health-related decision making (say at hospital “Y”). The internet and the picture archiving and communication system (PACS) are the key elements of HIS as they provide the necessary connection link to the physicians for determining appropriate diagnostic procedure in consultation with the global experts/referred doctors. The use of open networks for the exchange of databases and information between hospitals at global platforms imposes various challenges in the HIS. The sensitive information of the patients and the doctors is widely distributed on the open network and is likely to be hacked by an unauthorized user/intruder. It is essential to address this crucial issues and develop algorithms to ensure security, confidentiality, and integrity and avoid copyright forgery of the patient’s credentials [1–3]. HIS is thus emerging as the most emerging field of research demanding complementary and/or alternative solutions to address the challenges.
Fig. 1.
General block diagram for a typical HIS
Digital watermarking is one of the promising solutions widely offered by the researchers in making the HIS very effective. Digital watermarking hides the appropriate secret information in the image without hampering the perceptual quality of the image, and hence is considered as one of the prospective solutions to the aforesaid problems of security and has been therefore attracting the attention of wide research community. Various spatial domain watermarking techniques that focus on pixel modification are evaluated to hide the patient’s credentials [4–8] for authentication. However, these algorithms were fragile, which are further modified using discrete cosine transform (DCT)-based scheme [9]. A multiple watermarking approach was reported in [10, 11] for the first time to address the issue of security in HIS and has brought revolution in the domain of multiple medical image watermarking. Quantization-based approach presented in [12] to verify and analyze the signal integrity for EEG monitoring application is also an encouraging contribution by the researchers. Researchers have also explored frequency domain techniques using DCT [13] and discrete wavelet transform (DWT) [14–18] to achieve reduction in the storage and transmission overheads, tamper proofing, and authentication. These methods though effective, are not reversible and therefore are not very popular from the perspective of HIS. The development in HIS domain is therefore still at an infant stage demanding further research.
Existing research trend in watermarking involves interleaving of the sensitive information (credentials of the patients, diagnostic reports, patient ID, tag, label, physician’s signature, digital signature, biographical signal, image ID, and patient history) by modifying the pixel values of the host medical image [4]. The process of interleaving/embedding introduces possibility of distortion in the medical images. It is therefore vital to develop reversible algorithms which extract the embedded contents and recover the original medical image for appropriate diagnosis [19].
Reversible watermarking techniques, also referred as invertible or lossless data hiding schemes have thus emerged as a dire need in HIS. Literature reports popular algorithms to implement reversible watermarking algorithms, which include histogram modification, difference expansion, data compression, expansion-based, predication error-based, and quantization-based techniques [20, 21]. Reversible approaches using genetic algorithm and integer wavelet transform to hide multiple watermarks in the medical images [19, 22] present encouraging results; however, both the studies report low PSNR value with limited tamper detection. These reported methods need further experimentation to validate the robustness against various attacks. Other popular reversible methods include integer wavelet transform-based histogram shifting approach [23] and dual layer watermarking using digital envelop-CRC code [4] to insert the patient’s metadata into the medical images. These algorithms are reported to successfully recover the watermarked image using reversible techniques but have attained limited success in terms of the hiding capacity, robustness, and imperceptibility. Moreover, the hiding capacity is not evaluated by considering various patient credentials. A multiple watermark incorporating such details will add significant value in the development of HIS.
It is worth mentioning that most of the state-of-the-art methods are limited to only irreversible watermarking, and it is essential to make them reversible which are the need of HIS. It is necessary that the reversible techniques should strike the balance in hiding capacity and imperceptibility and should be analyzed for the robustness against intentional and unintentional attacks. It is also crucial to validate the presented approach using a concrete dataset of medical images.
A novel reversible watermarking approach is presented in this research paper. The proposed algorithm uses texture as a feature, which is very popular in the literature for various applications in the domains of image classification, pattern recognition, and many others; however, it has received meager attention and is not explored fully from the perspective of HIS. The proposed, novel hybrid approach based on combination of texture and quantization is exploited to hide patient credentials as multiple watermarks in the medical images. The texture feature is initially extracted after application of DWT and these coefficients are further quantized. The hybrid texture-quantization-based approach is the key significant contribution of this research which enhances the confidentiality, reliability and ensures the integrity of patients’ credentials interleaved in the medical images. Moreover, a tracking key is further used to make the proposed algorithm reversible. The use of multiple watermarks in selected texture to address the security challenges of HIS and the assignment of the tracking key to embed and retrieve the content from selected texture coefficient are the major contributions of this research in coping with the demands of existing HIS. The next section describes the proposed novel scheme, and the experimental results are presented in “Experimental Results.” “Discussion” details the comparison with the popular methods reported in the literature. The paper concludes summarizing the novel finding and contributions.
Proposed Scheme
This paper presents a novel hybrid texture-quantization approach to interleave multiple watermarking in medical images for data authentication, confidentiality protection, and proficient information recovery. The proposed approach and algorithms for the embedding phase and the extraction phase are detailed in this section.
Hybrid Texture-Quantization-Based Approach
Generally, transform domain techniques are superior to the spatial as they increase the robustness and preserve the imperceptibility of watermarked images. Wavelet analysis is a very popular transform domain technique in the research community due to its property of spatial and frequency localization which helps in analyzing the textured areas and edges [24, 25]. Its dyadic scaling decomposition is similar to signal processing of human visual system. DWT thus helps to adapt distortion induced by watermarking or quantization to the masking properties of human eye [26]. Similar to HVS, DWT splits the image in multiple frequency bands and processes them individually [27]. A typical demonstration considering CT image modality, where DWT (invertible and orthogonal Haar DWT) is used to decompose the CT image to be watermarked into seven sub-bands, is depicted in Fig. 2a, b. Figure 2c indicates the selection of the sub-bands for interleaving various credentials. The credentials considered in the experimentation of the proposed approach are as detailed:
Caption (patient’s history, diagnostic reports in the form of text),
An ECG signal (important diagnostic tool for many critical diseases),
The signature (doctor’s digital signature or identification code), and
An index (ICD-10 diagnostic codes) for securing patient data, bandwidth reduction, and origin authentication and to facilitate the retrieval of an image, respectively.
Fig. 2.

a Medical image (CT Modality). b Two-level Haar DWT of CT image. c Selection of sub-bands for interleaving different watermarks
Texture is a function of spatial variation in pixel intensities. It is a significant feature commonly used for detection of embedding site. Wavelet analysis is particularly useful for texture perception because it provides scale-dependent texture properties of the image [28]. In the proposed approach, texture features of the sub-bands are obtained to generate the texture feature matrix or texture map. The use of texture map enhances the security of the patient’s credentials watermarked in the medical image.
Texture primitives have two prominent characteristics: coarseness and directionality [24]. The algorithm uses statistical texture analysis approach to derive the prominent texture features. Texture information of an image at different resolution and scale is obtained from wavelet decompose sub-bands (HH, LH, HL). The size of texture matrix is the same as the size of sub-bands. Texture primitive is a continuous set of pixels having some tonal or regional property. It is represented by its average intensity, maximum and minimum intensity, size, or shape [29].The spatial relationship of texture primitives is obtained by combining its energy with variance of the equivalent coefficients in the lowest sub-band matrix (LL) as represented in Eq. (1) [30]
| 1 |
Images pixels are highly correlated in non-texture region, hence Eq. (1) helps to obtain the texture features of the image superimposed on the background for each sub-band. The difference between two neighboring pixels is compared with predefined threshold to so extract prominent texture areas in the medical images. Pixels with high energy are selected for multiple watermark hiding. Such pixels have relatively less impact on imperceptibility of the host medical image. Moreover, it also increases the robustness of the proposed algorithm as recovery of data is difficult for hackers or unauthorized users.
Figure 3a represents the texture feature and texture map of original CT image represented in Fig. 2a. Figure 3b depicts the prominent edges whose values are higher than the background pixels. It is imperative to select the sub-band and the corresponding patient credential to be watermarked so as to optimize the trade-off among capacity, robustness, and imperceptibility. This is achieved by calculating energy of the sub-bands. Figure 2c depicts the sub-band selection for hiding the four watermarks. The energy is calculated for each sub-band as it gives significant information of robustness of each decomposition level. The energy is calculated using the following Eq. (2):
| 2 |
where, k signifies the approximation and the detail sub-bands at each decomposition levels and J k are the sub band coefficients with dimensions N k M k.
Fig. 3.
a Texture feature of CT image. b Texture map of CT image
The energy distribution of CT test image depicted in Fig. 2a in its approximation and detail sub-bands obtained by 2-level DWT is represented in Table 1. It is observed that most of the energy is concentrated in the high decomposition levels, so robustness of watermark is achieved in ascending levels and hiding capacity reduces accordingly. All sub-bands excluding LL sub-band are used for data hiding as LL sub-band has most impact on image reconstruction quality [20].
Table 1.
Energy of approximation and detail images of two level wavelet decomposition
| Sub-band | Level 1 | Level 2 |
|---|---|---|
| Approximation | – | 337.4605 |
| Horizontal details | 4.3460 | 12.2253 |
| Vertical details | 4.7951 | 15.9863 |
| Diagonal details | 1.2830 | 5.7287 |
The watermarks are embedded in the wavelet coefficients selected by texture map. Wavelet coefficients are real numbers and which are mapped to binary using quantization function Q (f). The quantization procedure involves defining a function f that indicates the entire range of DWT coefficients which gets divided into steps of Δ, where Δ is quantization parameter (real positive number). In the proposed scheme, Δ = 2L where L is decomposition level.
| 3 |
The quantized coefficient will be either 0 or 1 as represented in Eq. (3). This quantized value is compared with watermark to either add or subtract an appropriate constant from original wavelet coefficient to obtain a new coefficient value. It is likely to get same value for multiple coefficients due to addition and subtraction of the same constant. This fact arises ambiguity while reconstruction of original image. So, it is imperative to assign a tracking key to preserve the information of change in the sign of original coefficient. The assignment of the tracking key plays a vital role to recover the original coefficients and thus makes the proposed algorithm reversible. The processing of embedding and the extracting of the multiple watermarks, and the corresponding algorithms are explained in the next section.
Embedding Algorithm
The proposed scheme initially extracts the texture features from the original medical image using DWT transform. The wavelet coefficients and the texture map are quantized using the quantization key. Tracker key is generated which is later used for the recovery process. Figure 4 elaborates the interleaving approach.
Fig. 4.
Embedding process
Extraction Algorithm
The extraction scheme of multiple watermarks is outlined in Fig. 5. It comprises of decomposition of the watermarked image using 2-level Haar wavelet transform, texture feature extraction, quantization, and tracking key-based approach to regain the original image.
Fig. 5.
Extraction process
Experimental Results
The test set considered for validation of the results in this research consists of 40 images of size 512 × 512 pixels from each modality (CT, MRA, MRI, US). Signature of 128 bits is randomly generated which is sufficient to claim the uniqueness for conveying identification code. Index of 546 bits comprises of special keywords and helps to retrieve image using database query. Caption of 910 bits in the form of electronic patient record is obtained by ASCII to binary conversion of text files.
In critical cases related to heart diseases, biographic signals like ECG and EEG play a vital role in the diagnosis and deciding the line of treatment [13, 31]. These biographic signals usually need high storage size in the range of 22–85 kB and it utilizes huge bandwidth while sending from one location to other along with patient reports and medical images [31]. In such scenarios, it will obviously be beneficial to include biographic signal as one of the credentials for watermarking and save the memory storage and transmission overheads. Considering the importance of ECG in practical HIS, the proposed technique explores the possibility to embed patient’s real ECG records in his/her medical image. The proposed algorithm embeds the ECG signal of 2000 bits. Predicative coding technique, adaptive delta modulation (ADM) is used for ECG signal encryption and compression. ADM encrypts and compresses the ECG signal which is of 16 bits to 1 bit. Our earlier research details the analysis of signal encryption and hiding approach for ECG signal [32].
It is necessary to increase the robustness of the embedded data regardless of image modification due to intentional or unintentional attacks. Error correcting code is a natural choice in order to correct the possible error bits and thus ensures robustness and security [14]. BCH codes are a large class of cyclic codes which include both binary and non-binary alphabets. Binary BCH codes can be constructed with parameters (n, k, l), where n is the length of the code word, k is the length of partition, and l is the number of bit errors this BCH code can correct [33, 34]. In a proposed approach, BCH is implemented to add security and to boost the robustness for three watermarks: signature, index, and caption. BCH encoding scheme (n, k, l) is used to enhance error correction capacity. As depicted in Table 2, suitable BCH scheme for given watermarks is selected which divides the entire length of watermark into partitions of length k. Thus, in order to encode 128 bits of signature, (31, 16, and 3) BCH scheme is used which splits the signature into 8 equal parts and each part generates 31 output bits with 3-bit error correction capacity. Thus, a total number of 248 bits are generated for the signature.
Table 2.
BCH encoding schemes for each type of watermark
| Type of watermark | Number of bits | BCH scheme | Iterations | Total number of embedded bits |
|---|---|---|---|---|
| Caption | 910 | (255,91,25) | 10 | 2550 |
| Index | 546 | (255,91,25) | 6 | 1530 |
| Signature | 128 | (31,16,3) | 8 | 248 |
The quantitative assessment of watermarked image is evaluated by PSNR, MSSIM, and UIQI which are popular measures to compute imperceptibility, similarity, and visual quality degradation between original and watermarked images, respectively [35]. PSNR offers an overall efficient numerical appraise of image distortion which conveys significant information in medical applications.
Table 3 presents the achieved PSNR, MSSIM, and UIQI values of the watermarked images, for different medical image modalities which confirm the preservation of imperceptibility of interleaved medical image. Figure 6 represents the results of the proposed scheme on few test cases of the database created for the experimentation. Figure 6a–e depicts the original images to be watermarked. Figure 6a1–e1 represents the corresponding watermarked images. The results report no major visual difference between original and watermarked image and thus, the imperceptibility of the watermarked image is preserved.
Table 3.
Performance measure in terms of PSNR, MSSIM, and UIQI
| Image modality | PSNR | MSSIM | UIQI |
|---|---|---|---|
| CT | 58.66 | 0.9998 | 0.9853 |
| MRI | 58.61 | 0.9997 | 0.9973 |
| MRA | 58.63 | 0.9977 | 0.9970 |
| US | 58.66 | 0.9991 | 0.9789 |
Fig. 6.

Original images a–e and their corresponding watermarked images a1–e1
Figure 7a, b depicts the plot of MSSIM and UIQI values of watermarked image respectively considering various modalities and more samples from the data set of 40 images. The obtained values of MSSIM and UIQI are approximately equal to 1 and thus validate the similarity of the watermarked and the original images. High value of PSNR ensures imperceptibility and no visual disparity between the watermarked and the original images.
Fig. 7.
a Plot of MSSIM. b Plot of UIQI. Values for medical image modalities
Figure 8a, b illustrates statistical pixel distribution, evaluated by plotting the histogram of original and watermarked image, respectively. It reveals similar probability distribution of original and watermarked image.
Fig. 8.
a Histogram of original CT image. b Histogram of watermarked CT image
The performance of the algorithm is also tested with JPEG compression attacks. Table 4 presents comparative evaluations of the distortion produced by embedding patient’s credentials using our scheme and the distortions induced by JPEG image compression with different quality factors in terms of PSNR for CT modality. It is remarkable to mention that watermarked image adds less distortion than the JPEG compression with quality factor 95. The adequate perceptual quality of the watermarked images combined with high PSNR shows the transparency of the proposed scheme.
Table 4.
Performance of watermarked and JPEG images in terms of PSNR for CT modality
| Type of image processing | Quality factor | PSNR(dB) |
|---|---|---|
| JPEG compressed original image |
Quality factor 95 | 51.23 |
| Quality factor 90 | 47.08 | |
| Quality factor 85 | 44.44 | |
| Quality factor 80 | 43.41 | |
| Watermarked image | – | 58.65 |
The scheme is further tested for possible common attacks while sending the images like: rotation (30°), sharpening, blurring, Gaussian noise, and salt and paper noise (0.02) and results are shown in Fig. 9. The system resists the blurring and sharpening attacks as compared to rotation and Gaussian noise.
Fig. 9.
a, b, c, d PSNR of medical images (CT, MRA, MRI, US) after rotating, sharpening, blurring, and Gaussian attack
Discussion
This research presents a novel reversible watermarking approach which exploits texture feature to hide patient credentials as multiple watermarks in the medical images. The presented scheme embeds four types of watermarks (patient diagnosis detail, ECG signal, doctor’s digital signature, and diagnostic code) into medical images. Multiple watermarking augments security of sensitive data, provides data authentication, and allows efficient image retrieval. The use of BCH encoding scheme for caption, index, and signature further enhances the security and robustness. Considering the necessity and importance of ECG (in critical cases) to decide the line of treatment, the proposed algorithm incorporates ECG signal as one of the patient’s credentials. Predictive coding technique, adaptive delta modulation is applied to encrypt the ECG signal, which is further interleaved and finally retrieved using the proposed invertible algorithm.
The experimental results reveal the effectiveness of the scheme in terms of imperceptibility and robustness. The experimental results claim successful retrieval of the original image using the proposed reversible algorithm with high value of PSNR (> 58 dB), MSSIM (~ 1), and UIQI (~ 1) along with improved hiding capacity. The algorithm is tested for various attacks like rotation, blurring, sharpening, and presented reversible algorithm sustains these attacks while maintaining good imperceptibility. Transparency of the proposed scheme is higher as the distortion introduced by watermarking is less than the distortion introduced by JPEG compression with quality factors of up to 95. It is necessary to compare the state-of-the-art methods. Table 5 compares the finding and contributions in this research with the most popular approaches reported in the literature [4, 20, 22, 31, 36–38].
Table 5.
Comparison with state-of-the-art methods
| Parameter | Tan et al. [4] | Khan et al. [20] | Arsalin et al. [22] | Das et al. [36] | Maity et al. [37] | Deng et al. [38] | Nambaksh et al. [31] | Proposed |
|---|---|---|---|---|---|---|---|---|
| Watermarking approach | Reversible | Reversible | Reversible | Irreversible | Reversible | Reversible | Irreversible | Reversible |
| Robustness check with attacks | No | No | No | Few attacks | No | No | No | Seven attacks |
| Robustness with JPEG compression | No | No | No | Yes | No | No | Yes | Yes |
| PSNR (in decibel) | Less than 40 | Greater than 45 | Greater than 40 | Less than 40 | Greater than 40 | Greater than 45 | Greater than 45 | Greater than 50 |
| SSIM | No | No | 0.98 | 0.773 | 0.93 | No | 0.93 | 0.99 |
| UIQI | No | No | No | No | No | No | 0.96 | 0.98 |
| Hiding capacity | High | High | High | Less | High | Moderate | Moderate | High |
| Watermark single/multiple | Single | Single | Single | Multiple | Single | Multiple | Multiple | Multiple |
| Data security schemes (eg., CRC, RSA, hash function, or BCH) | CRC scheme | No | No | BCH scheme | No | No | No | BCH scheme |
| Similarity check between extracted watermark and original watermark | No | No | No | No | No | No | No | Yes |
It is necessary to emphasize that the texture-based approach reported in [31] is irreversible, limited to dual watermarking, is inefficient to calculate prominent texture features for said hiding capacity, and is restricted to PET images only. The algorithm presented in this research is reversible and incorporates multiple watermarks. Moreover, it modifies the threshold finding calculation reported in [31] to accommodate all the modalities and still achieves relatively higher PSNR. Robustness of the proposed scheme is validated considering various attacks. The contributions of this research are superior to the state-of-the-art methods and therefore are important considering practical deployment of the system.
Conclusion
Developments in HIS are still at an infant stage and demand further exhaustive research to ensure the security, authentication, and integrity of the confidential data (patient credentials) transmitted in an open access network. Developing such reversible algorithms with multiple watermarking, which preserve the quality of the medical image for the appropriate diagnosis, is an imperative demand in HIS. This research presents a novel hybrid texture-quantization-based reversible approach for multiple watermarking. Experimental results achieved maximum of 22,616 bits of hiding capacity with PSNR of 53.64 dB and are superior to the state-of-the-art methods. Similar assessment of original and watermarked images using parameters of MSSIM and UIQI confirms the preservation of the imperceptibility. The experimental results also prove the higher quality watermarked images can be achieved as compared to JPEG compressed images up to quality factor of 95%. The comparison of the novel texture-based reversible approach presented in this research with the earlier reported findings and contribution prove the efficacy of our approach. The substantial improvement in robustness, authenticity, hiding capacity, and confidentiality obtained using the reversible approach are major contributions of this research in coping with the demands and developments of existing HIS.
Contributor Information
Mousami Turuk, Phone: 020-24371101, Email: mpturuk@pict.edu.
Ashwin Dhande, Phone: 020-24371101, Email: apdhande@pict.edu.
References
- 1.Wilson P, Leitner C, Moussalli A: Mapping the potential of eHealth: empowering the citizen through eHealth tools and services. Research Report presented at the eHealth Conference, Cork, Ireland. European Institute of Public Administration, Maastricht, 2004, p 52
- 2.Giakoumaki A, Perakis K, Tagaris A, Koutsouris D: Digital watermarking in telemedicine applications-towards enhanced data security and accessibility. In: Engineering in Medicine and Biology Society. EMBS'06. 28th Annual International Conference of the IEEE. IEEE, New York, 2006, pp 6328–6311 [DOI] [PubMed]
- 3.Nyeem H, Boles W, Boyd C. A review of medical image watermarking requirements for teleradiology. J Digit Imaging. 2013;26(2):326–343. doi: 10.1007/s10278-012-9527-x. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Tan CK, Ng JC, Xu X, Poh CL, Guan YL, Sheah K. Security protection of DICOM medical images using dual-layer reversible watermarking with tamper detection capability. J Digit Imaging. 2011;24(3):528–540. doi: 10.1007/s10278-010-9295-4. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Chao HM, Hsu CM, Miaou SG. A data-hiding technique with authentication, integration, and confidentiality for electronic patient records. IEEE Trans Inf Technol Biomed. 2002;6(1):46–53. doi: 10.1109/4233.992161. [DOI] [PubMed] [Google Scholar]
- 6.Miaou SG, Hsu CM, Tsai YS, Chao HM: A secure data hiding technique with heterogeneous data-combining capability for electronic patient records. In: Engineering in Medicine and Biology Society. Proceedings of the 22nd Annual International Conference of the IEEE. IEEE, Chicago, 2000, vol. 1, pp 280–283
- 7.Zain JM, Fauzi AR: Medical image watermarking with tamper detection and recovery. In: Engineering in Medicine and Biology Society. EMBS'06. 28th Annual International Conference of the IEEE. IEEE, New York, 2006, 3270–3273 [DOI] [PubMed]
- 8.Acharya U, Rajendra DA, Subbanna Bhat P, Niranjan UC. Compact storage of medical images with patient information. IEEE Trans Inf Technol Biomed. 2001;5(4):320–323. doi: 10.1109/4233.966107. [DOI] [PubMed] [Google Scholar]
- 9.Osborne D, Abbott D, Sorell M, Rogers D: Multiple embedding using robust watermarks for wireless medical images. In: Proceedings of the 3rd International conference on Mobile and ubiquitous multimedia. ACM, New York, 2004, pp 245–250
- 10.Coatrieux G, Sankur B, Maitre H. Strict integrity control of biomedical images. Proc SPIE. 2001;4314:229–240. doi: 10.1117/12.435403. [DOI] [Google Scholar]
- 11.Coatrieux G, Maitre H, Sankur B, Rolland Y, Collorec R: Relevance of watermarking in medical imaging. In: Proceedings IEEE EMBS International Conference on Information Technology Applications in Biomedicine, 2000, pp 250–255
- 12.Kong X, Feng R. Watermarking medical signals for telemedicine. IEEE Trans Inf Technol Biomed. 2001;5(3):195–201. doi: 10.1109/4233.945290. [DOI] [PubMed] [Google Scholar]
- 13.Nayak J, Subbanna Bhat P, Acharya R, Niranjan UC. Simultaneous storage of medical images in the spatial and frequency domain: a comparative study. Biomed Eng. 2004;3(1):17. doi: 10.1186/1475-925X-3-17. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Giakoumaki A, Pavlopoulos S, Koutsouris D. Secure and efficient health data management through multiple watermarking on medical images. Med Biol Eng Comput. 2006;44(8):619. doi: 10.1007/s11517-006-0081-x. [DOI] [PubMed] [Google Scholar]
- 15.Nambakhsh S, Ahmadian A, Ghavami M, Dilmaghani RS, Karimi-Fard S: A novel blind watermarking of ECG signals on medical images using EZW algorithm. In: Engineering in Medicine and Biology Society. EMBS'06. 28th Annual International Conference of the IEEE. IEEE, New York, 2006, 3274–3277 [DOI] [PubMed]
- 16.Deepa K, Hatzinakos D. Digital watermarking for telltale tamper proofing and authentication. Proc IEEE. 1999;87(7):1167–1180. doi: 10.1109/5.771070. [DOI] [Google Scholar]
- 17.Xie R, Wu K, Zhu S: An improved semi-fragile digital watermarking scheme for image authentication. In: IEEE International Workshop on Anti-counterfeiting, Security, Identification. IEEE, Xiamen, 262–265,2007
- 18.Ko L-T, Jwu-E C, Shieh Y-S, Scalia M, Sung T-Y. A novel fractional-discrete-cosine-transform-based reversible watermarking for healthcare information management systems. Math Probl Eng. 2012;2012:8. [Google Scholar]
- 19.Irany BM, Guo XC, Hatzinakos D: A high capacity reversible multiple watermarking scheme for medical images. In: 17th International Conference on Digital Signal Processing (DSP). 2011, pp 1–6
- 20.Khan A, Malik SA. A high capacity reversible watermarking approach for authenticating images: exploiting down-sampling, histogram processing, and block selection. Inf Sci. 2014;256:162–183. doi: 10.1016/j.ins.2013.07.035. [DOI] [Google Scholar]
- 21.Khan A, Siddiqa A, Munib S, Malik SA. A recent survey of reversible watermarking techniques. Inf Sci. 2014;279:251–272. doi: 10.1016/j.ins.2014.03.118. [DOI] [Google Scholar]
- 22.Arsalan M, Ambreen S, Malik AK. Intelligent reversible watermarking in integer wavelet domain for medical images. J Syst Softw. 2012;85(4):883–894. doi: 10.1016/j.jss.2011.11.005. [DOI] [Google Scholar]
- 23.Gu Q, Gao T: A novel reversible watermarking scheme based on block energy difference for medical images. In: Soft Computing and Intelligent Systems (SCIS) and International Symposium on Advanced Intelligent Systems (ISIS), Joint 6th International Conference. IEEE, Kobe, 2012, pp 232–237
- 24.Van Gool L, Dewaele V, Oosterlinck A. Texture analysis anno 1983. Comput Vis Graph Image Process. 1985;29(3):336–357. doi: 10.1016/0734-189X(85)90130-6. [DOI] [Google Scholar]
- 25.Wang H-JM, Su P-C, Kuo C-CJ. Wavelet-based digital image watermarking. Optics Express. 1998;3(12):491–496. doi: 10.1364/OE.3.000491. [DOI] [PubMed] [Google Scholar]
- 26.Meerwald P, Uhl A: Survey of wavelet-domain watermarking algorithms. Photonics West 2001-Electronic Imaging, 505–516,2001
- 27.Saini K, Dewal ML, Rohit MK: Segmentation of mitral regurgitant jet using the combination of wavelet and watershed transformation. In: IEEE 8th International Colloquium on Signal Processing and its Applications (CSPA). IEEE, Melaka, 2012, 74–79
- 28.Ni R, Ruan Q, Cheng H-D. Secure semi-blind watermarking based on iteration mapping and image features. Pattern Recogn. 2005;38(3):357–368. doi: 10.1016/j.patcog.2004.08.006. [DOI] [Google Scholar]
- 29.Sonka M, Hlavac V, Boyle R: Image processing, analysis, and machine vision. Third Edition, Cengage Learning, 2014
- 30.Lewis AS, Knowles G. Image compression using the 2-D wavelet transform. IEEE Trans Image Process. 1992;1(2):244–250. doi: 10.1109/83.136601. [DOI] [PubMed] [Google Scholar]
- 31.Nambakhsh M-S, Ahmadian A, Zaidi H. A contextual based double watermarking of PET images by patient ID and ECG signal. Comput Methods Prog Biomed. 2011;104(3):418–425. doi: 10.1016/j.cmpb.2010.08.016. [DOI] [PubMed] [Google Scholar]
- 32.Turuk M, Dhande A: Interleaving Scheme for Medical Image Authentication. Emerging Research in Computing, Information, Communication and Applications Springer Singapore, 2016, pp 669–681
- 33.Wang W. Applying BCH error correcting code in digital watermark. Advances in electronic commerce, web application and communication. Berlin Heidelberg: Springer; 2012. pp. 405–410. [Google Scholar]
- 34.Zinger S, Jin Z, Maître H, Sankur B: Optimization of watermarking performances using error correcting codes and repetition. In: Communications and Multimedia Security Issues of the New Century. Springer, Boston, 2001, pp 229–240
- 35.Wang Z, Bovik AC, Sheikh HR, Simoncelli EP. Image quality assessment from error visibility to structural similarity. IEEE Trans Image Process. 2004;13(4):600–612. doi: 10.1109/TIP.2003.819861. [DOI] [PubMed] [Google Scholar]
- 36.Das S, Kundu MK. Effective management of medical information through a novel blind watermarking technique. J Med Syst. 2012;36(5):3339–3351. doi: 10.1007/s10916-012-9827-1. [DOI] [PubMed] [Google Scholar]
- 37.Maity HK, Maity SP. Joint robust and reversible watermarking for medical images. Proc Technol. 2012;6:275–282. doi: 10.1016/j.protcy.2012.10.033. [DOI] [Google Scholar]
- 38.Deng X, Chen Z, Zeng F, Zhang Y, Mao Y. Authentication and recovery of medical diagnostic image using dual reversible digital watermarking. J Nanosci Nanotechnol. 2013;13(3):2099–2107. doi: 10.1166/jnn.2013.6872. [DOI] [PubMed] [Google Scholar]