Abstract
If two quantum players at a nonlocal game G achieve a superclassical score, then their measurement outcomes must be at least partially random from the perspective of any third player. This is the basis for device-independent quantum cryptography. In this paper we address a related question: does a superclassical score at G guarantee that one player has created randomness from the perspective of the other player? We show that for complete-support games, the answer is yes: even if the second player is given the first player’s input at the conclusion of the game, he cannot perfectly recover her output. Thus some amount of local randomness (i.e., randomness possessed by only one player) is always obtained when randomness is certified from nonlocal games with quantum strategies. This is in contrast to non-signaling game strategies, which may produce global randomness without any local randomness. We discuss potential implications for cryptographic protocols between mistrustful parties.
INTRODUCTION
When two quantum parties Alice and Bob play a non-local game G and achieve a score that exceeds the best classical score ωc(G), their outputs must be at least partially random. In other words, all Bell inequality violations certify the existence of randomness. This fact is at the center of protocols for device-independent quantum cryptography, where untrusted devices are used to per- form cryptographic procedures. In particular, this notion of certification is the basis for device-independent randomness expansion, where a small random seed is converted into a much larger uniformly random output by repeating Bell violations [1–12].
A natural question arises: is new randomness also generated by one player from the perspective of the other player? Specifically, if X denotes Alice’s outputs, Z denotes the post-measurement state that Bob has at the conclusion of the game, and F denotes all side information (including Alice’s input), is there a certified lower bound for the conditional entropy H(X | ZF)? Besides helping us understand the nature of certified randomness, this particular kind of randomness (local randomness) has applications in mutually mistrustful cryptographic settings, where Alice and Bob are cooperating but have different interests.
Quantifying local randomness (i.e., randomness that is only known to one player) is challenging because many of the known tools do not apply. Lower bounds for the total randomness (i.e, randomness from the perspective of an outside adversary) have been computed as a function of the degree of the Bell violation (see Figure 2 in [2]) but are not directly useful for certifying local randomness. One of the central challenges is that we are measuring randomness from the perspective of an active, rather than passive, adversary: Bob’s guess at Alice’s output occurs after Bob has carried out his part of the strategy for G. Current tools for device-independent randomness expansion are not designed to address the case where the adversary is a participant in the nonlocal game.
Does the generation of certified randomness always involve the generation of local certified randomness? The answer is not obvious: for example, in the non-signaling setting, Alice and Bob could share a PR-box1 which generates 1 bit of certified randomness per use, but no new local randomness – Bob could perfectly guess Alice’s output from his own if he were given Alice’s input.
Motivated by the above, we prove the following result in this paper (see Theorem 14 for a formal statement).
Theorem 1 (Informal)
For any complete-support game2 G, there is a constant CG > 0 such that the following holds. Suppose Alice and Bob use a strategy for G which achieves a score that is δ above the best classical score (with δ > 0). Then, at the conclusion of the strategy and given Alice’s input, Bob can guess her output with probability at most (1 − δ2/CG).
We note that similar problems have been studied in the literature in settings different from ours. There has been other work examining the scenario where a third party tries to guess Alice’s output after a game (e.g., [13], [14], [15]), and single-round games have appeared where Bob is sometimes given only Alice’s input, and asked to produce her output (e.g., [16], [17], [18]). (We believe the novelty of our scenario in comparison to these papers is that we consider the randomness of Alice’s output after Bob has performed his part of a quantum strategy, and thus has potentially lost information due to measurement.) Two recent papers also address randomness between multiple players, under assumptions about imperfect storage [19, 20].
In addition to the above, we prove a structural theorem for quantum strategies that allow perfect guessing by Bob. Not only do such strategies not achieve Bell inequalities, but they are also essentially classical in the following sense. Let D,E denote the quantum systems possessed by Alice and Bob, respectively
Theorem 2 (Informal)
Suppose that Alice’s and Bob’s strategy is such that if the game G is played and then Bob is given Alice’s input, he can perfectly guess her output. Then, there is an isometry mapping Bob’s system to E1 ⊗ E2 such that Bob’s strategy for G involves only E1, and all of Alice’s observables commute with the reduced state on DE1.
(See Theorem 5 and Corollary 7 for a formal statement.) Thus, in the case of perfect guessing, the strategy is equivalent to one in which Alice’s measurements have no effect on the shared state.
Structure of the paper
We begin with the case of perfect guessing. We formalize the concept of an essentially classical strategy, using a definition of equivalence between strategies which is similar to definitions used in results on quantum rigidity. We then give the proof of Theorem 2. It is known that two sets of mutually commuting measurements on a finite-dimensional space can be expressed as the pullback of bipartite measurements. This fact is used along with matrix algebra arguments to show the necessary splitting of Bob’s system into E1 ⊗ E2.
Then we proceed with the proof of Theorem 1. It has been observed by previous work (e.g., [16], [21]) that if a measurement {Pi} on a system D from bipartite state ρDE are highly predictable via measurements on E, then the measurement does not disturb the reduced state by much: Σi PiρDPi ~ ρD. In this paper we give a simplified proof of that fact (Proposition 11). The interesting consequence for our purpose is that if Alice’s measurements are highly predictable to Bob, then Alice can copy out her measurement outcomes in advance, thus making her strategy approximately classical. We take this a step further, and show that if Bob first performs his own measurement on E the resulting classical-quantum correlation is also approximately preserved by Alice’s measurements (which is not necessarily true of the original entangled state ρAB). This is sufficient to show that an approximately-guessable strategy yields an approximately classical strategy.
The subtleties in the proof are in establishing the error terms that arise when Alice copies out multiple measures from her side of the state. We note that the proof crucially requires that the game G has complete support. An interesting further avenue is to explore how local randomness may break down if the condition is not satisfied.
In section we discuss the implications of our result.
PRELIMINARIES
For any finite-dimensional Hilbert space V, let L(V) denote the vector space of linear automorphisms of V. For any M, N ∈ L(V), we let 〈M, N〉 denote Tr[M*N]. If S ⊆ V is a subspace of V, let PS ∈ L(V) denote orthogonal projection onto V.
Throughout this paper we fix four disjoint finite sets 𝒜, ℬ, 𝒳, 𝒴, which denote, respectively, the first player’s input alphabet, the second player’s input alphabet, the first player’s output alphabet, and the second player’s output alphabet. A 2-player (input-output) correlation is a vector of nonnegative reals, indexed by a, b, x, y ∈ 𝒜 × ℬ × 𝒳 × 𝒴 satisfying for all pairs (a, b), and satisfying the condition that the quantities
| (1) |
are independent of b and a, respectively (no-signaling).
A 2-player game is a pair (q, H) where
| (2) |
is a probability distribution and
| (3) |
is a function. If q(a, b) ≠ 0 for all a ∈ 𝒜 and b ∈ ℬ, the game is said to have a complete support. The expected score associated to such a game for a 2-player correlation is
| (4) |
We will extend notation by writing q(a) = Σb q(a, b), q(b) = Σa q(a, b), and q(a | b) = q(a, b)/q(b) (if q(b) ≠ 0).
A 2-player strategy is a 5-tuple
| (5) |
such that D, E are finite dimensional Hilbert spaces, is a family of 𝒳-valued positive operator valued measures (POVMs) on D (indexed by 𝒜), is a family of 𝒴-valued positive operator valued measures on E, and γ is a density operator on D ⊗ E. The second player states of Γ are defined by
| (6) |
(These states are, more explicitly, the subnormalized states of Bob’s system that arise after both Alice and Bob have performed their measurements.) Define by the same expression with replaced by the identity operator. (These represent the pre-measurement states of the second-player.) Define for any a.
We say that the strategy Γ achieves the 2-player correlation if for all a, b, x, y. If a 2-player correlation can be achieved by a 2-player strategy then we say that it is a quantum correlation.
If is a convex combination of product distributions (i.e., distributions of the form where and then we say that is a classical correlation. Note that if the underlying state of a quantum strategy is separable (i.e., it is a convex combination of bipartite product states) then the correlation it achieves is classical. The maximum expected score that can be achieved for a game G by a classical correlation is denoted ωc(G).
PERFECT GUESSING
We first address the case of perfect guessing — that is, the case when the second-player states that remain after the game is played are perfectly distinguishable by Bob. It turns out that this condition will imply some strong structural conditions on the strategy used by Alice and Bob, and it will imply in particular that Alice’s and Bob’s score at the game G cannot be better than that of any classical strategy.
Congruent strategies
It is necessary to identify pairs of strategies that are essentially the same from an operational standpoint. We use a definition that is similar to definitions from quantum self-testing (e.g., Definition 2.13 in [22]).
A unitary embedding from a 2-player strategy
| (7) |
to another 2-player strategy
| (8) |
is a pair of unitary embeddings i : D ↪ D̅ and j : E ↪ Ē such that γ̅ = (i ⊗ j)γ(i ⊗ j)*, , and .
Additionally, if Γ is such that D = D1 ⊗ D2, and for all a, x, then we will call the strategy given by
| (9) |
a partial trace of Γ. We can similarly define a partial trace on the second subspace E if it is a tensor product space.
We will say that two strategies Γ and Γ′ are congruent if there exists a sequence of strategies Γ = Γ1, …, Γn = Γ′ such that for each i ∈ {1, …, n − 1}, either Γi+1 is a partial trace of Γi, or vice versa, or there is a unitary embedding of Γi into Γi+1, or vice versa. This is an equivalence relation. Intuitively, two strategies are congruent if one can be constructed from the other by adding or dropping irrelevant information. Note that if two strategies are congruent then they achieve the same correlation.
Essentially classical strategies
We are ready to define the key concept in this section and to state formally our main theorem.
Definition 3
A quantum strategy (5) is said to be essentially classical if it is congruent to one where γ commutes with for all x and a.
Note that if the above condition holds, then applying the measurement map
| (10) |
to the system D leaves the state γ of DE unchanged.
We are interested in strategies after the application of which Bob can predict Alice’s output given her input. This is formalized as follows. If χ1, …, χn are positive semidefinite operators on some finite dimensional Hilbert space V, then we say that {χ1, …, χn} is perfectly distinguishable if χi and χj have orthogonal support for any i ≠ j. This is equivalent to the condition that there exists a projective measurement on V which perfectly identifies the state from the set {χ1, …, χn}.
Definition 4
A quantum strategy (5) allows perfect guessing (by Bob) if for any a, b, y, is perfectly distinguishable.
Theorem 5 (Main Theorem)
If a strategy for a complete-support game allows perfect guessing, then it is essentially classical.
(We note that the converse of the statement is not true. This is because even in a classical strategy, Alice’s output may depend on some local randomness, which Bob cannot perfectly predict.)
Before giving the proof of this result, we note the following proposition, which taken together with Theorem 5 implies that any strategy that permits perfect guessing yields a classical correlation.
Proposition 6
The correlation achieved by an essentially classical strategy must be classical.
Proof
We need only to consider the case that γ commutes with for all a, x. For each a ∈ 𝒜, let Va = ℂ𝒳, and let Φa : L(D) → L(Va ⊗ D) be the nondestructive measurement defined by
| (11) |
Note that by the commutativity assumption, such operation leaves the state of DE unchanged.
Since the measurements do not disturb the state of DE, Alice can copy out all of her measurement outcomes in advance. Without loss of generality, assume 𝒜 = {1, 2, …, n}. Let Λ ∈ L(V1 ⊗ … ⊗ Vn ⊗ D ⊗ E) be the state that arises from applying the superoperators Φ1, …, Φn, in order, to γ. For any a ∈ {1, …, n}, the reduced state ΛVaE is precisely the same as the result of taking the state γ, applying the measurement to D, and recording the result in Va. Alice and Bob can therefore generate the correlation from the marginal state ΛV1…VnE alone (if Alice possesses V1, …, Vn and Bob possesses E). Since this state is classical on Alice’s side, and therefore separable, the result follows.
Corollary 7
If a strategy for a complete-support game allows perfect guessing, the correlation achieved must be classical.
Proving Theorem 5
The proof will proceed as follows. First, we show that Alice’s measurements induce projective measurements on Bob’s system. Next, we argue that Qa commutes with Bob’s own measurement for any b. This allows us to isometrically decompose Bob’s system into two subsystems E1 ⊗ E2, such that Sb acts trivially on E2, while E2 alone can be used to predict x given a. The latter property allows us to arrive at the conclusion that Ra commutes with γDE1.
We will need the following lemma, which is well-known and commonly attributed to Tsirelson. We will only sketch the proof, and more details can be found in Appendix A of [23]. The lemma asserts that for families of positive semidefinite operators {Mj}, {Nk} on a finite-dimensional space V, commutativity (i.e., the condition that Mj, Nk commute for and j, k) implies bipartiteness (i.e., the condition that {Mj} and {Nk} can be obtained as pullbacks via a map V → V1 ⊗ V2 of operators on V1 and V2, respectively).
Lemma 8
Let {Mj}, {Nk} be positive semidefinite operators on a finite-dimensional Hilbert space V such that MjNk = NkMj for all j, k. Then, there exists a unitary embedding i : V ↪ V1 ⊗ V2 and and positive semidefinite operators on V1 and N̅k on V2 such that Mj = i* (M̅j ⊗ 𝕀)i and Nk = i*(𝕀 ⊗ N̅k)i for all j, k, ℓ, m.
Proof sketch
Via the theory of von Neumann algebras, there exists an isomorphism
| (12) |
under which
| (13) |
| (14) |
Let V1 = ⊕ℓVℓ, V2 = ⊕ℓWℓ, and let .
Proof of Theorem 5
Express Γ as in (5). Without loss of generality, we may assume that Supp ρ = E. By the assumption that Γ allows perfect guessing, for any a, the second-player states must be perfectly distinguishable (since otherwise the post-measurement states would not be). Therefore, we can find projective measurements on E such that
| (15) |
Note that for any fixed a, if Alice and Bob were to prepare the state γDE and Alice were to measure with and Bob were to measure with , their outcomes would be the same.
We have that the states
| (16) |
| (17) |
have orthogonal support for any x ≠ x′. Since Supp ρ = E, we have c𝕀 ≤ ρ for some c > 0. Therefore,
| (18) |
which implies, using the cyclicity of the trace function,
| (19) |
Therefore, the measurements and commute for any a, b. (This is clear from writing out the matrix in block form under the subspaces determined by the projections .)
By Lemma 8, we can find a unitary embedding i : E ↪ E1 ⊗ E2 and POVMs on E1, E2 such that and . With
| (20) |
the strategy Γ embeds into the strategy
For any fixed a, the state γ̅ is such that applying the measurement to the system D and the measurement to the system E2 always yields the same outcome. In particular, if we let
| (21) |
then will always be equal to 1 if x = x′ and equal to 0 otherwise. Therefore commutes with the operators , and thus also with their sum .
Thus if we trace out the strategy Γ′ over the system E2, we obtain a strategy (congruent to the original strategy Γ) in which Alice’s measurement operators commute with the shared state.
APPROXIMATE GUESSING
Next we address the case where the second-player states are not necessarily perfectly distinguishable as x varies, but are approximately distinguishable. (Thus, if Bob were given Alice’s input after the game was played and asked to guess her output, he could do so with probability close to 1.) We begin by quantizing “approximate” distinguishability.
Definition 9
Let denote a finite set of positive semidefinite operators on a finite dimensional Hilbert space V. Then, let
| (22) |
where the maximum is taken over all POVMs on V.
Note that if Σi Tr(ρi) = 1, and each ρi is nonzero, then this quantity has the following interpretation: if Alice gives Bob a state from the set {ρi/Tr(ρi)} at random according to the distribution (Tr(ρi))i, then Dist{ρi} is the optimal probability that Bob can correctly guess the state. This quantity is well-studied (see, e.g., [24]).
When we discussed perfect distinguishability, we made use of measurements that commuted with a given state. In the current section we will need an approximate version of such commutativity, and thus we make the following definition.
Definition 10
Let Φ: L(V) → L(V) denote a completely positive trace-preserving map over a finite-dimensional Hilbert space V. Let β ∈ L(V) denote a density operator on V. Then we say that Φ is ε-commutative with β if
| (23) |
Note that this relation obeys a natural triangle inequality: if Φ1 is ε1-commutative with β, and Φ2 is ε2-commutative with β, then
The following known proposition will be an important building block. We give a proof that is a significant simplification of a method from Lemma 29 in [21]. (See also Lemma 2 in [16] for a related result.)
Proposition 11
Let Λ ∈ L (A⊗B) be a density operator and a projective measurement on A such that the induced states satisfy
| (24) |
Then, the superoperator X ↦ Σi Fi X Fi is -commutative with ΛA ≔ TrBΛ.
Proof
Let α = ΛA. By assumption, there exists a POVM {Gi} on B such that
| (25) |
By standard arguments, we can assume without loss of generality that {Gi} is a projective measurement and that Λ is pure.3
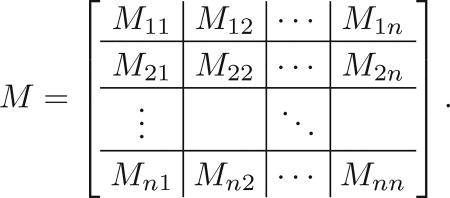
There is a linear map M : ℂs → ℂr such that TrAΛ = M* M and α = TrBΛ = M M*. Upon choosing an appropriate basis for A and B, we can write M with a block form determined by the spans of {Fi} and {Gj}:
 |
(26) |
Let
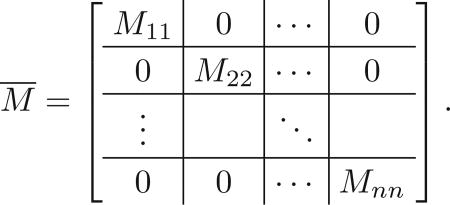 |
(27) |
Note that the probability of obtaining outcome Fi for the measurement on A and outcome Gj for the measurement on B is given by the quantity , and the probability that the outcomes of the measurements disagree is exactly . We have
| (28) |
Additionally, we can compare to the post-measurement state Σi FiαFi. The latter quantity is given by
 |
and therefore the difference is equal to
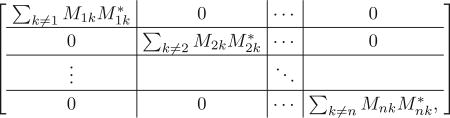 |
which is a positive semidefinite operator whose trace is exactly . Thus,
| (29) |
Therefore we have the following, using the Cauchy-Schwarz inequality:
as desired.
The previous proposition showed that if a measurement by Alice is highly predictable to Bob, then it does not disturb Alice’s marginal state by much. The next corollary asserts Alice’s measurement must also approximately preserve any existing classical correlation that Bob has with Alice’s state.
Corollary 12
Let Λ ∈ L(A ⊗ B ⊗ C) be a density operator which is classical on C. (That is, Λ = Σk Λk ⊗ |ck〉 〈ck| for some orthonormal basis {c1, …, ck} ⊆ C.) Suppose that is a projective measurement on A such that the induced states satisfy
| (30) |
Then, the superoperator X ↦ Σi (Fi ⊗ I)X (Fi ⊗ I) is -commutative with ΛAC.
Proof
Let C̅ be a Hilbert space which is isomorphic to C, and let Λ̅ ∈ L (A ⊗ B ⊗ C ⊗ C̅) be the state that arises from Λ by copying out along the standard basis: . This copying leaves the state ABC unaffected, so assumption (30) still applies. Thus by Proposition 11, the operator X ↦ Σi (Fi ⊗ I)X (Fi ⊗ I) is -commutative with ΛAC̅, and the same holds for the isomorphic state ΛAC.
Now we prove a preliminary version of our main result. We assume that the states are highly distinguishable on average, and then deduce that Alice’s and Bob’s correlation must be approximately classical.
Proposition 13
Let
| (31) |
be a two-player strategy. Let
| (32) |
Then, there exists a classical correlation such that
| (33) |
Proof
We can assume without loss of generality that the measurements are all projective. We begin with the same strategy as in the proof of Proposition 6. For each a ∈ 𝒜, let Va = ℂ𝒳, and let Φa : L(D) → L(Va ⊗ D) be the nondestructive measurement defined by
| (34) |
Let and let . Likewise let Wb = ℂ𝒴 for each b ∈ ℬ, let Ψb : L(E) → L(Wb ⊗ E) be the nondestructive measurement defined by
| (35) |
Let and .
Assume without loss of generality that 𝒜 = {1, 2, …, n}. Let Λ ∈ L(V1 ⊗ … ⊗ Vn ⊗ D ⊗ E) be the state that arises from applying the superoperators Φ1 ⊗ IE, …, Φn ⊗ IE, in order, to γ. Let be the correlation that arises from Alice and Bob sharing the reduced state ΛV1…VnE, Alice obtaining her output on input a from the register Va, and Bob obtaining his output from his prescribed measurements to E. Since the state ΛV1…VnE is a separable state over the bipartition (V1 … Vn | E), the correlation is classical.
Let
| (36) |
If Alice and Bob share the measured state (ID ⊗ Ψb)(γ) partitioned as (D | EWb), then the probability that Bob can guess Alice’s outcome when she measures with is given by (1 − δab). By Corollary 12, the operator is -commutative with .
We wish to compare and . For any a, b the probability vector describes the joint distribution of the registers VaWb under the density operator
| (37) |
which by the previous paragraph is within trace-distance from the distribution described by :
| (38) |
Thus we have the following, in which we use the Cauchy-Schwarz inequality:
| (39) |
| (40) |
| (41) |
| (42) |
| (43) |
| (44) |
| (45) |
| (46) |
which simplifies to the desired bound.
Proposition 13 is useful for addressing any game (q, H) where the distribution q is uniform (i.e., q(a, b) = 1/(|𝒜||ℬ|).) We prove the following theorem which applies to more general games.
Theorem 14
Let G = (q, H) be a complete-support game and let
| (47) |
be a two-player strategy. Let
| (48) |
Then, the score achieved by Γ exceeds the best classical score ωc(G) by at most , where
| (49) |
Proof
Define and δab as in Proposition 13. We have the following (again using the Cauchy-Schwartz inequality):
| (50) |
| (51) |
| (52) |
| (53) |
| (54) |
| (55) |
| (56) |
| (57) |
| (58) |
Note that for any probability vectors t = (t1, …, tm) and s = (s1, …, sm) and any arbitrary vector (u1, …, um) ∈ [0, 1]m, we have
| (59) |
Applying this fact to the probability vectors and and the vector (H(a, b, x, y))abxy implies that the difference between the score achieved by and the score achieved by is no more than half the quantity (58), which yields the desired result.
DISCUSSION
When two players achieve a superclassical score at a nonlocal game, their outputs must be at least partially unpredictable to an outside party, even if that party knows the inputs that were given. This fact is one of the bases for randomness expansion from untrusted devices [1], where a user referees a nonlocal game repeatedly with 2 or more untrusted players (or, equivalently, 2 or more untrusted quantum devices) to expand a small uniformly random seed S into a large output string T that is uniform conditioned on S. The players can exhibit arbitrary quantum behavior, but it is assumed that they are prevented from communicating with the adversary. At the center of some of the discussions of randomness expansion (e.g., [2]) is the fact that the min-entropy of the outputs of the players can be lower bounded by an increasing function of the score achieved at the game.
In this paper we have proven an analogous result for the case where one player in a game wishes to generate randomness that is unknown to the other player — in other words, we have achieved (one-shot) blind randomness expansion. (The second party, Bob, is “blind” to the randomness generated by Alice.) We have also proven a general rate curve for any game G, which relates the score achieve at G to the predictability of Alice’s output from the perspective of Bob – specifically, if G is a complete support game and Alice and Bob achieve score w, then Bob’s probability of guessing her output given her input is at most
where CG denotes the constant defined in equation (49).
A possible next step would be to prove a multi-shot version of Theorem 14, e.g., a proof that Alice’s outputs across multiple rounds have high smooth min-entropy from Bob’s perspective. With the use of a quantum-proof randomness extractor (e.g., [25]) this would imply that Alice has the ability to generate uniformly random bits, known only to her, through interactions with Bob. In the device-independent setting, this would mean that one device could be be reused in multiple iterations of randomness expansion without affecting the security guarantee, and in particular would decrease the minimum number of quantum devices needed to perform unbounded randomness expansion from four (as in [9, 26]) down to three.
The recent entropy accumulation theorem [11] proves lower bounds on smooth min-entropy in various scenarios where a Bell inequality is violated. It will be interesting to see if it can be generalized to cover blind randomness expansion as well. (The current results apply under a Markov assumption which is not satisfied in our case.)
A corollary of our result is that, for any complete-support game G, the range of scores that certify randomness against a third party are exactly the same as the range of scores that certify randomness for one player against the second — in both cases, any superclassical score is adequate. We point out, however, that the certified min-entropy can be different. A simple example of this is the Magic Square game, where Alice and Bob are given inputs a, b ∈ {1, 2, 3} respectively, and must produce outputs (x1, x2, x3), (y1, y2, y3) ∈ {0, 1}3 respectively which satisfy
| (60) |
| (61) |
| (62) |
Self-testing [27] for the Magic Square game implies that if Alice and Bob achieve a perfect score, Alice’s output contains two bits of perfect randomness from the perspective of a third party, but only one perfect bit of randomness from the perspective of Bob. Optimizing the relationship between the game score and min-entropy in the blind scenario is an open problem.
A potentially useful aspect of Corollary 7 is that it contains a notion of certified erasure of information. For the example of the Magic Square game mentioned above, if Bob were asked before his turn to guess Alice’s output given her input, he could do this perfectly. (The optimal strategy for the Magic Square game uses a maximally entangled state and projective measurements, so each party’s measurement outcomes can be perfectly guessed by the other player.) Contrary to this, when Bob is compelled to carry out his part of the strategy before Alice’s input is revealed, he loses the ability to perfectly guess Alice’s output. Requiring a superclassical score from Alice and Bob amounts to forcing Bob to erase information. Different variants of certified erasure are a topic of current study [19, 20, 28]. An interesting research avenue is to determine the minimal assumptions under which certified erasure is possible.
Finally, we note that the scenario in which the second player tries to guess the first player’s output after computing his own output fits the general framework of sequential nonlocal correlations [29]. In [30] such correlations are used for ordinary (non-blind) randomness expansion. A next step is to explore how our techniques could be applied to more general sequential nonlocal games.
Acknowledgments
We are indebted to Laura Mancinska for discussions that helped us to prove our robust result (Theorem 14). The first author also thanks Jedrzej Kaniewski, Marcin Pawlowski and Stefano Pironio for helpful information. This research was supported in part by US NSF Awards 1500095, 1216729, 1526928, and 1318070.
Footnotes
That is, the unique 2-part non-signaling resource whose input bits a, b and output bits x, y always satisfy x ⊕ y = a ∧ b
That is, a game in which each input pair occurs with nonzero probability.
We can construct an enlargement B ⊆ B̅ such that PBḠiPB = Gi for some projective measurement {Ḡi} on B̅, and we can construct an additional Hilbert space E and a pure state Λ̅ ∈ L(A ⊗ B ⊗ E) such that TrEΛ̅ = Λ. The joint probability distribution of the measurements {Fi} and {Ḡ i ⊗ IE} on Λ̅ are the same as those of {Fi} and {Gi} on Λ.
References
- 1.Colbeck R. Ph.D. thesis. University of Cambridge; 2006. arXiv:0911.3814. [Google Scholar]
- 2.Pironio S, Acín A, Massar S, Boyer de la Giroday A, Matsukevich DN, Maunz P, Olmschenk S, Hayes D, Luo L, Manning TA, et al. Nature. 2010;464:1021. doi: 10.1038/nature09008. [DOI] [PubMed] [Google Scholar]
- 3.Colbeck R, Kent A. Journal of Physics A: Mathematical and Theoretical. 2011;44:095305. URL http://stacks.iop.org/1751-8121/44/i=9/a=095305. [Google Scholar]
- 4.Vazirani UV, Vidick T. In: Karloff HJ, Pitassi T, editors. Proceedings of the 44th Symposium on Theory of Computing Conference, STOC 2012; New York, NY, USA. May 19–22, 2012; ACM; 2012. pp. 61–76. URL http://dl.acm.org/citation.cfm?id=2213977. [Google Scholar]
- 5.Pironio S, Massar S. Phys. Rev. A. 2013;87:012336. URL http://link.aps.org/doi/10.1103/PhysRevA.87.012336. [Google Scholar]
- 6.Fehr S, Gelles R, Schaffner C. Phys. Rev. A. 2013;87:012335. URL http://link.aps.org/doi/10.1103/PhysRevA.87.012335. [Google Scholar]
- 7.Coudron M, Vidick T, Yuen H. Proceedings of APPROX 2013 and RANDOM 2013. Springer; 2013. pp. 468–483. vol. 8096 of Lecture Notes in Computer Science. [Google Scholar]
- 8.Coudron M, Yuen H. Proceedings of the 46th Annual ACM Symposium on Theory of Computing; 2014. pp. 427–436. [Google Scholar]
- 9.Miller CA, Shi Y. J. ACM. Vol. 63. 2016. p. 33:1. URL http://doi.acm.org/10.1145/2885493. [Google Scholar]
- 10.Miller CA, Shi Y. Universal security for randomness expansion from the spot-checking protocol. 2015 arXiv:1411.6608. [Google Scholar]
- 11.Dupuis F, Fawzi O, Renner R. 2016 arXiv:1607.01796. [Google Scholar]
- 12.Arnon-Friedman R, Renner R, Vidick T. 2016 doi: 10.1038/s41467-017-02307-4. arXiv:1607.01797. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 13.Pawlowski M. Physical Review A. 2010;82:032313. [Google Scholar]
- 14.Kempe J, Kobayashi H, Matsumoto K, Toner B, Vidick T. SIAM Journal on Computing. 2011;40(848) http://dx.doi.org/10.1137/090751293, URL http://dx.doi.org/10.1137/090751293. [Google Scholar]
- 15.Acín A, Cavalcanti D, Passaro E, Pironio S, Skrzypczyk P. Phys. Rev. A. 2016;93:012319. URL https://link.aps.org/doi/10.1103/PhysRevA.93.012319. [Google Scholar]
- 16.Mančinska L. In: Computing with New Resources: Essays Dedicated to Jozef Gruska on the Occasion of His 80th Birthday. Calude CS, Freivalds R, Kazuo I, editors. Springer International Publishing; 2014. pp. 200–207. [Google Scholar]
- 17.Vazirani U, Vidick T. Phys. Rev. Lett. 2014;113:140501. doi: 10.1103/PhysRevLett.113.140501. URL http://link.aps.org/doi/10.1103/PhysRevLett.113.140501. [DOI] [PubMed] [Google Scholar]
- 18.Vidick T. Proceedings - Annual IEEE Symposium on Foundations of Computer Science (FOCS); 2013. pp. 766–755. [Google Scholar]
- 19.Kaniewski J, Wehner S. New Journal of Physics. 2016;18 [Google Scholar]
- 20.Riberio J, Thinh LP, Kaniewski J, Helsen J, Wehner S. Device-independence for two-party cryptography and position verification. 2016 arXiv:1606.08750. [Google Scholar]
- 21.Vidick T. Ph.D. thesis. University of California; Berkeley: 2011. The complexity of entangled games. [Google Scholar]
- 22.McKague M. Theory of Computing. 2016;12:1. [Google Scholar]
- 23.Doherty AC, Liang Y-C, Toner B, Wehner S. 2008 arXiv:0803.4373. [Google Scholar]
- 24.Spehner D. Journal of Mathematical Physics. 2014;55:075211. http://dx.doi.org/10.1063/1.4885832, URL http://dx.doi.org/10.1063/1.4885832. [Google Scholar]
- 25.De A, Portmann C, Vidick T, Renner R. SIAM J. Comput. 2012;41:915. URL http://dx.doi.org/10.1137/100813683. [Google Scholar]
- 26.Chung K-M, Wu X, Shi Y. arXiv:1402.4797, presented at QIP 2014 2014 [Google Scholar]
- 27.Wu X, Bancal J-D, McKague M, Scarani V. Phys. Rev. A. 2016;93:062121. URL http://link.aps.org/doi/10.1103/PhysRevA.93.062121. [Google Scholar]
- 28.Unruh D. J. ACM. Vol. 62. 2015. p. 49:1. URL http://doi.acm.org/10.1145/2817206. [Google Scholar]
- 29.Gallego R, Wurflinger LE, Chaves R, Acin A, Navascues M. New Journal of Physics. 2014;16 [Google Scholar]
- 30.Curchod FJ, Johansson M, Augusiak R, Hoban MJ, Wittek P, Acín A. Phys. Rev. A. 2017;95:020102. URL https://link.aps.org/doi/10.1103/PhysRevA.95.020102. [Google Scholar]


