Abstract
We propose an enhanced discrimination measurement for tripartite 3-dimensional entangled states in order to improve the discernible number of orthogonal entangled states. The scheme suggests 3-dimensional Bell state measurement by exploiting composite two 3-dimensional state measurement setups. The setup relies on state-of-the-art techniques, a multi-port interferometer and nondestructive photon number measurements that are used for the post-selection of suitable ensembles. With this scheme, the sifted signal rate of measurement-device-independent quantum key distribution using 3-dimensional quantum states is improved by up to a factor of three compared with that of the best existing setup.
Introduction
Quantum cryptography is a mature research field that exploits the principles of quantum mechanics to ensure its information theoretical security. The core protocol of quantum cryptography is quantum key distribution (QKD), which is the process of generating a secret key that is shared between two distant parties, called Alice and Bob. These parties are assumed to be exposed to a potential malicious eavesdropper, conventionally called Eve. Since the proposal of the first QKD protocols1,2, many efforts have been made to improve the security of QKD based on quantum principles3–6. Various types of QKD have also been experimentally demonstrated to date7–10.
The earliest proposal for QKD used 2-dimensional quantum states, called qubits11. After this proposal, significant efforts were made to increase the key rate of QKD protocols. For example, protocols involving high-dimensional quantum states, called qudits, were introduced. It is well known that higher-dimensional quantum states can carry more information per quantum. In fact, there have been many theoretical proposals of the exploitation of qudits in various types of quantum information processing, such as non-locality testing12–16 and quantum teleportation17,18. High-dimensional quantum states have been experimentally demonstrated in various quantum systems, energy-time eigenstates19,20, multipath-entangled states21–24, and quantized orbital angular momentum (OAM) modes of photons25,26.
Furthermore, applying high-dimensional states in QKD is known to increase the efficiency of key distribution under a potential attack by Eve in the ideal case27–30. The results show that QKD based on qudits can achieve a higher key rate and a higher upper bound on the allowed error rate than the original QKD protocol can. Such protocols have been demonstrated using various photon degrees of freedom, such as energy-time states31–34 and OAM modes35–37.
Along another branch of investigation, the security of the original QKD system has been scrutinized in more detail. Device-independent QKD (DI-QKD) has been proposed to extend the notion of ultimate security in the device attack scenario38–44. In this protocol, Alice and Bob can generate a secret key without any a priori assumptions regarding device performance. This scheme is designed to protect the key from side-channel attack when the measurement device is not very reliable. In this case, the security of the protocol is guaranteed only by nonlocal correlations as identified by the Clauser-Horne-Shimony-Holt (CHSH) inequality45. However, the DI-QKD protocol is not easy to be implemented in practice since it requires a loophole-free Bell test experiment, which poses high technological demands46–50.
To compensate for this practical difficulty, a measurement-device-independent QKD (MDI-QKD) protocol was proposed in 201251. This protocol can be more easily implemented than DI-QKD can because the MDI-QKD procedure does not rely on entanglement. In MDI-QKD, an untrusted third party, called Charlie, maintains quantum state detectors separately from Alice and Bob. After Alice and Bob send quantum states, e.g. single photon states, to Charlie, he performs a Bell state measurement (BSM) on the incoming photons to generate the correlation between Alice and Bob. In this protocol, Charlie acts as a referee to build up the necessary correlation. Due to the selective construction of the correlation, an eavesdropper who attacks the detector cannot obtain exact information about the secret key. For this reason, MDI-QKD possesses unbounded security against any detector attacks. Using MDI-QKD, most side-channel attacks made possible by detector imperfections can be resisted52.
However, MDI-QKD suffers from a low secret key rate. When the BSM in MDI-QKD is performed using linear optical elements, the success probability of the setup is only 50%53. In the original QKD protocol, the secret key can be extracted when Alice and Bob use the same encoding basis, which is true for half of the generated ensembles on average. However, in MDI-QKD, Alice and Bob can share information only when they use the same encoding basis and the BSM is successful, meaning that 75% of their trials must be discarded. This shortcoming makes this key distribution scheme quite inefficient.
To increase the key rate, aversion of MDI-QKD using high-dimensional quantum states was recently studied54,55, and a performance increase was demonstrated for MDI-QKD using 3-dimensional quantum states, called qutrits, instead of qubits54. However, the practicality of this scheme is still questionable. This is because a generalized BSM of a bipartite high-dimensional maximally entangled state cannot be implemented using only linear optical elements56,57. For the implementation of high-dimensional entangled state discrimination, multi-mode quantum scissors58 and a linear optical setup for multipartite high-dimensional entangled state discrimination59 have been proposed, although their success probabilities are still not sufficient for the implementation of efficient high-dimensional MDI-QKD.
In the present work, we propose an efficient discrimination setup for tripartite entangled qutrit states to enhance the discernible number of orthogonal entangled states. The setup relies on state-of-the-art techniques, a multi-port interferometer called a tritter60, and nondestructive photon number measurements61,62. The generation of multipartite high-dimensional entangled photonic states has not been well studied even now, and such states have been experimentally demonstrated only very recently26,59,63,64. With the technologies listed above, we construct a setup that can discriminate subsets of tripartite entangled qutrit states and show that qutrit MDI-QKD can be implemented using this setup. Moreover, we generalize the measurement to d-dimensional d-photon entangled state discrimination measurement and analyse the secret key rate of high-dimensional MDI-QKD using the generalized setup.
This article is organized as follows. We present a schematic description of the tripartite entangled qutrit state discrimination setup and the set of entangled states that the setup can discriminate. We also present schematic descriptions of the teleportation process and MDI-QKD using qutrit states with the setup we propose. We analyse the security of the MDI-QKD protocol using qutrit states as well. We generalize the proposed setup to a setup for d-dimensional d-photon entangled state discrimination and analyse the secret key rate of high-dimensional MDI-QKD. The efficiency of the proposed MDI-QKD setup when experimental factors are considered is described as well.
Results
Tripartite entangled qutrit state discrimination setup
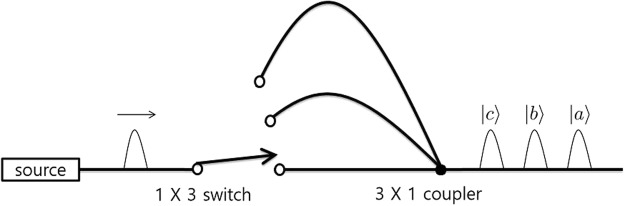
Before we introduce the discrimination setup, we describe the physical system we are considering and introduce the related notation. We consider 3-dimensional photonic states, where |a〉, |b〉, and |c〉 denote 3-dimensional orthonormal states. Such 3-dimensional quantum states can be realized by exploiting various degrees of freedom, such as, high-dimensional time-bin states20,31 and OAM modes of single photons25,26. As an example, Fig. 1 shows a schematic setup for generating 3-dimensional time-bin states31. The source generates a single photon and the photon is injected into a delay line. The delay lines have different lengths, and the user can choose into which of the delay lines the photon is injected. |a〉, |b〉, and |c〉 denote the photonic time-bin states when the photon passes though the shortest, intermediate, and longest delay lines, respectively.
Figure 1.
A schematic diagram of the time-bin qutrit generating source31. The diagram is based on a figure from our previous work54. In this setup, the photon injection time to the output port is controlled by three different delay lines and a photonic path switch. |a〉, |b〉, and |c〉 denote the time states when the photon passes through the shortest, intermediate, and longest delay lines, respectively.
With regard to the qutrit states, we will focus on tripartite entangled states. To realize interference among three photons, we use a multi-port interferometer called a tritter60. The tritter we consider has three input ports and three output ports. We consider the three-path operation described in Eq. (1):
| 1 |
where is a photon creation operator on path y and is a three-dimensional discrete Fourier transformation defined in terms of ω, which, in turn, is defined as ω = exp(2πi/3). The input and output ports are distinguished by the subscripted numbers 0, 1, and 2 and 3, 4, and 5, respectively.
In our notation, a single photon that is time-bin mode x in the port labelled y is represented by . We consider nine states, as given in Eq. (2):
| 2 |
where i ∈ {0, 1, 2}, ω is defined in Eq. (1), and we omit (mod 3) in the subscripts on the right-hand side. In the states described in Eq. (2), the three photons are in different time-bin modes, |a〉, |b〉, and |c〉. The tripartite entangled qutrit states |Ψ0〉, |Ψ1〉, and |Ψ2〉 are the quantum states in which each photon exists in a separate input port, and the other states are those in which two photons of different time-bin modes exist in one port and the other photon is in another port. The orthogonality of the nine tripartite entangled qutrit states is easily provable.
A schematic diagram of the entire tripartite entangled qutrit state discrimination setup is shown in Fig. 2. Before photons that are in one of the states described in Eq. (2) are injected into the tritter, nondestructive photon number measurements are performed on each input port for post-selection. The details of the post-selection process will be described later. Subsequently, the photons enter the tritter, and the tritter performs the operation on the photons. After interference, we perform a qutrit state discrimination measurement on each output port. Since we are using the time-bin modes of single photons, the states can be discriminated by measuring the arrival times of the photons at on-off detectors65,66 or by using ultrafast optical switches67. We obtain a certain combination of clicked detectors when one of our input states described in Eq. (2) is injected into the entire setup, yielding an output state as shown in Eq. (14); the combination of clicked detectors for each state is given in Eq. (3):
| 3 |
where i ∈ {0, 1, 2} and Dxy denotes a click of the detector corresponding to the single-photon state |yx〉. Each possible detection listed in Eq.(3) has an equal probability of 1/6. Since we are using on-off detectors, we cannot discriminate phase differences among the three states. This means that we can infer groups of entangled states from the measurement results, but we cannot discriminate exact entangled states. To discriminate the exact state, we post-select only those trials in which all three photons exist in different input ports by means of nondestructive photon number measurements. In a nondestructive measurement, the absorption of the photons during the measurement is ideally avoided, and the other degrees of freedom of the photons also remain unaffected. Nondestructive measurements of the photon number state can be successfully realized using nonlinear effects68,69 or an atom-cavity system70,71. The remaining states after post-selection are |Ψ0〉, |Ψ1〉, and |Ψ2〉, which can be exactly discriminated from the combinations of clicked detectors given in Eq. (3). The nondestructive photon number measurements do not affect other degrees of freedom of the photons in the case that all photons are distributed in different ports, so the interference pattern among the three photons in the tritter is the same when there is no nondestructive photon number measurement. We note that it is sufficient to use a nondestructive photon number parity measurement instead of a full nondestructive photon number measurement. If nondestructive photon number parity measurements on the input ports indicate an odd photon number, then it is guarantee that all of the photons are in different input ports.
Figure 2.
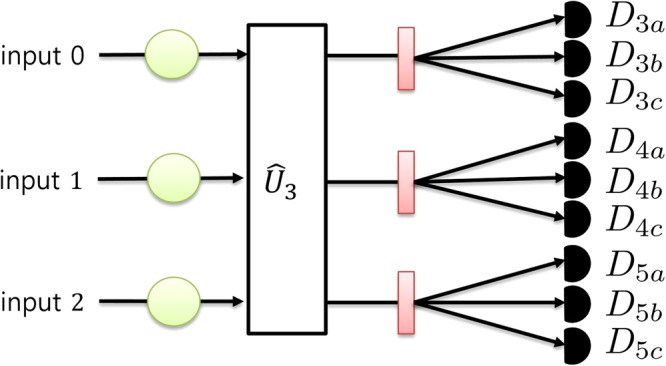
A schematic diagram of the measurement setup. denotes the tritter setup described in the Methods section; the pink rectangular boxes represent state discrimination elements, which correspond to polarization beam splitters in polarization qubit experiments; the black semicircles denote on-off detectors; and the green circles on the input ports denote nondestructive measurement devices for detecting the parity of the photon number. Dxy denotes a detector corresponding to a single photon state |yx〉.
Path-encoded qutrit teleportation
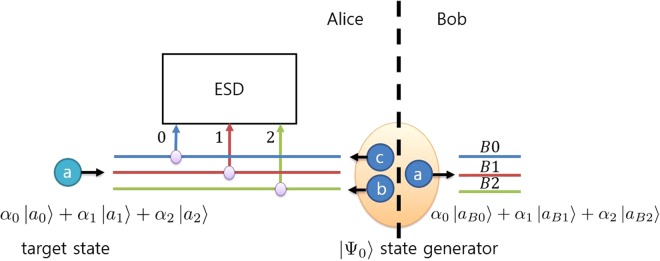
In this section, we show that a qutrit state teleportation protocol can be implemented with the proposed tripartite entangled qutrit state discrimination setup. The protocol is very similar to the previously studied teleportation protocol using linear optical elements59. Figure 3 shows a schematic diagram of the qutrit teleportation protocol. The target state that we want to teleport is a path-encoded qutrit state, and its time-bin mode is |a〉. The target state can be written as shown in Eq. (4):
| 4 |
where αi is an arbitrary complex number satisfying the normalization condition, . One user, called Alice, possesses the target state. She wants to send that state to the other user, called Bob. To teleport the state, Alice and Bob share a photonic entangled state |Ψ0〉. Previous studies have investigated the generation of multipartite photonic entangled states by means of an array of nonlinear crystals64 and by means of tritter and nondestructive photon number measurements59. Alice has the target state and two photons generated from |Ψ0〉 in time-bin states |b〉 and |c〉, and Bob has a photon generated from |Ψ0〉 in time-bin state |a〉. Then, the entire system can be written as described in Eq. (5):
| 5 |
where we omit (mod 3) in the subscripts. Alice applies the tripartite entangled qutrit state discrimination operation to her three photons. The entire system can be rewritten in the basis of Alice’s measurement, as shown in Eq. (6):
| 6 |
where ω = exp(2πi/3) and we omit (mod 3) in all subscripts except those of Ψ. After Alice’s measurement, Alice sends the result of the measurement to Bob. Bob can recover the initial target state by performing a unitary operation on his state corresponding to Alice’s result. The operation that Bob should perform for each possible result is specified in Table 1. The operations that Bob needs to perform are two path rotating operations, which are described in Eq. (7):
| 7 |
Figure 3.
A schematic diagram of 3-dimensional path-encoded state teleportation. The purple circles represent 2 × 1 couplers, fiber optical devices combining two paths into one path. ESD is the tripartite entangled qutrit state discrimination setup, and the numbers 0, 1, and 2 denote the ports. The blue circles represent photons, and the letters on the circles denote the time-bin states of the photons. The numbers 0, 1, and 2 correspond to the input ports connected to ESD, and B0, B1, and B2 denote the ports of the result states. Alice and Bob share the entangled state |Ψ0〉 (orange circle), where Alice has the photons in time-bin states b and c and Bob has the photon in time-bin state a. Teleportation can be performed using the result of Alice’s tripartite ESD measurement and Bob’s corresponding unitary operation. The details of the scheme are described in the text.
Table 1.
Bob’s unitary operations for qutrit teleportation corresponding to the result of Alice’s entangled state discrimination measurement. The definition of each unitary operator is given in Eq. (7).
| Alice’s ESD result | Ψ0 | Ψ1 | Ψ2 |
| Bob’s operation | — |
The unitary operators and can be implemented with phase shifters on Bob’s photonic paths B0, B1, and B2. For instance, to realize , the phase shifters should simultaneously apply no phase shift on B0, a phase shift of ω2 on B1, and a phase shift of ω on B2. After the unitary operation, Bob’s photonic path state is as described in Eq. (8):
| 8 |
This state is the same as the initial target state that is given in Eq. (4).
Measurement-device-independent quantum key distribution using qutrits
In this section, we study the conceptual implementation of MDI-QKD using qutrit states. MDI-QKD is proposed to prevent side-channel attacks against imperfect measurement devices51. In MDI-QKD, Alice and Bob, who want to share a secret key, send their encoded photonic states to an untrusted third party, Charlie. Charlie then performs a BSM to measure the correlation of the photons and announces the result. Alice (Bob) can infer the state that Bob (Alice) sent to Charlie from the announced result and her (his) own encoded state. Since the measurement setup detects only the correlation of the photons, an eavesdropper Eve cannot obtain the information that Alice and Bob share by attacking the measurement setup. It has been proven that QKD with high-dimensional quantum states has a higher secret key rate than that of traditional qubit QKD27–30, and there are also studies that have shown that MDI-QKD with high-dimensional states has some advantages compared with qubit MDI-QKD54,55. The procedure for MDI-QKD using qutrit states was introduced in our previous work54. Since the proposed setup is designed to discriminate tripartite entangled qutrit states, the quantum states in which Alice and Bob encode their information must be different from those used in the original protocol in order to exploit the setup. Here, we will show that MDI-QKD can be implemented with our proposed setup.
In the original MDI-QKD protocol, Alice and Bob use two encoding bases at each site. As an extension of that protocol, our protocol also uses two encoding bases, a path-encoding basis and one of its mutually unbiased bases (MUBs). The condition for the two bases to be MUBs in three-dimensional Hilbert space, , should be satisfied for all i, j ∈ {0, 1, 2}, where {0, 1, 2} and are orthonormal bases. In our physical system, {|x0〉, |x1〉, |x2〉} is a path-encoding basis, and is one of its MUBs, as defined in Eq. (9):
| 9 |
The states in the MUB can be generated with the tritter operation . For example, state can be generated by inputting the photonic state |x〉 into input port 0 of the tritter depicted in the methods section.
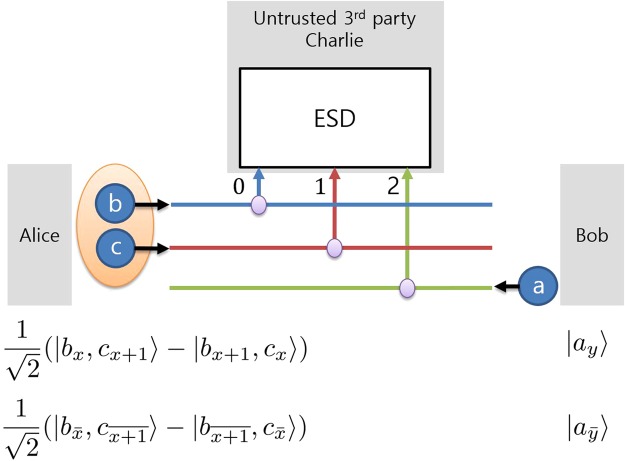
A description of MDI-QKD using qutrit states is given as follows. Since the measurement setup projects an incoming state onto tripartite entangled states, the total number of encoded photonic states that Alice and Bob send to Charlie should be three. We assume that Alice sends two photonic states and that Bob sends one photonic state as shown in Fig. 4. First, Alice randomly chooses encoding information from among the ordinary numbers 1, 2 and 3 and the bar numbers, , and . After that, Alice generates the corresponding bipartite path entangled state. If Alice chooses a number x, Alice generates the state . Bob chooses a number y from among the numbers Alice used and generates the state ay. Alice and Bob send their states to Charlie; then, Charlie performs tripartite entangled qutrit state discrimination on the incoming photons and announces the result through a public channel. Subsequently, Alice and Bob discard trials in which their encoding bases were different after a basis comparison through a public channel. The remaining data become the sifted key, and Alice and Bob can synchronize their information by performing the appropriate post-processing as described in our previous work54.
Figure 4.
A schematic diagram of MDI-QKD using qutrits. The purple circles represent 2 × 1 couplers, ESD denotes the entengled state discrimination measurement setup, and the numbers 0,1, and 2 denote three paths. Subscripts x and y in the states of Alice and Bob represent the labels of the paths on which the photons exist, meaning that x, y ∈ {0, 1, 2} and we omit (mod 3) in the subscripts. The photons in the large orange circle are in an entangled state. Alice generates a bipartite path-entangled photon pair in time-bin states b and c on paths x and x + 1 and sends them to an untrusted third party, Charlie. Bob generates a photon in state a on path y and also sends it to Charlie.The details of the states are described in the text.
To evaluate the usefulness of the proposed protocol, a security analysis of this protocol is necessary. Such an analysis can be performed through an inspection of the equivalent protocol using the entanglement distillation process (EDP)3,5,6. If the two parties, Alice and Bob, share the maximally entangled state generated via the EDP, then an eavesdropper cannot establish correlations between her state and the states of Alice and Bob72. In this sense, if Alice and Bob share a maximally entangled state, then they are assured that their protocol is secure against eavesdroppers. Thus, the security of the proposed protocol can be analysed with respect to the number of maximally entangled states generated via the EDP.
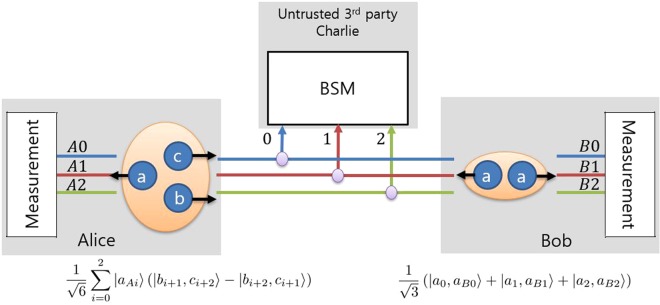
A schematic diagram of the equivalent protocol that exploits the maximally entangled state is shown in Fig. 5. In this protocol, we assume that Alice has a tripartite qutrit path-entangled state generator and that Bob has a bipartite qutrit path entangled state generator. Implementations of multipartite high-dimensional path-entangled states using linear optical elements and nondestructive photon number parity measurements59 and using overlapping paths of photon pairs created in different crystals64 have recently been proposed. The generation of bipartite high-dimensional path-entangled states using nonlinear crystals has previously been studied and demonstrated22,23. With regard to the states, Alice keeps the state that is in time-bin mode a and sends the other photons to Charlie by using state discrimination elements, and Bob also keep one photon and sends the other to Charlie. Then the whole system can be described as written in Eq. (10):
| 10 |
Figure 5.
A schematic diagram of MDI-QKD using entangled qutrit states for security analysis. Alice prepares tripartite entangled qutrits and sends two of them, in states b and c, to Charlie using state discrimination elements. Bob prepares bipartite maximally path-entangled qutrits with both photons in state a and sends one of them to Charlie. Charlie performs tripartite entangled qutrit state discrimination (ESD) on the incoming photons and announces the result. By means of a unitary operation applied to Bob’s state, Alice and Bob can share bipartite maximally entangled qutrits.
The entire system can be rewritten as given in Eq. (11):
| 11 |
In Eq. (11), the state |Ψ〉 represents the tripartite state that Alice and Bob sent to Charlie for the entangled state discrimination measurement. The bipartite states in the square brackets denote the path-entangled qutrit state that Alice and Bob share. With the proposed setup, the states |Ψ0〉, |Ψ1〉, and |Ψ2〉 can be exactly discriminated. The other states cannot be exactly discriminated, so Alice and Bob should discard any trials in which Charlie’s announced result is not one of |Ψ0〉, |Ψ1〉, and |Ψ2〉. After sifting, Bob performs a unitary operation on his state based on Charlie’s result; then, the final state Alice and Bob share is the maximally entangled state when there is no error. Alice and Bob privately choose their measurement bases from between the photon path measurement and the corresponding MUB measurement and perform their measurements. The measurement results of Alice and Bob are strongly correlated only when Alice and Bob choose the same basis, so they discard any trial in which different bases are used after a basis comparison step conducted through public communication. The remaining data are correlated, so these data can be used as a secret key. Then, the security analysis of the MDI-QKD protocol using entangled qutrit states becomes equivalent to that of the QKD protocol using 3-dimensional maximally entangled states, which has already been studied28,29,54. According to the results, the secret key rate per sifted signal of the protocol, r3,can be evaluated as shown in Eq. (12):
| 12 |
where H(x) is the Shannon entropy, defined as , and Q denotes the state error rate in the path-encoding basis. Each sifted signal is the result of a trial in which Alice and Bob generated the |Ψ0〉 state and chose the same measurement basis. The error rate can be obtained as follows (number of signals that contain errors)/(number of sifted signals). An error corresponds to a case in which Alice and Bob share |Ψx〉 such that x ≠ 0 at the end of the protocol.
d-dimensional d-photon state discrimination setup and its efficiency
We investigate applications of a d-dimensional generalized setup and their efficiency. With the generalized setup and states, the qutrit teleportation scheme and qutrit MDI-QKD scheme described in previous sections can be extended to the teleportation of arbitrary d-dimensional path-encoded states and d-dimensional MDI-QKD, respectively. For instance, the steps of the d-dimensional MDI-QKD protocol are very similar to those of the qutrit MDI-QKD protocol, except that Alice and Bob should prepare d-dimensional information instead of 3-dimensional information and Alice and Bob use the states Ai and 0j to encode their information, where Ai is defined in the Methods section and i, j ∈ {0, 1, 2, …, d − 1}. The security proof for d-dimensional QKD using maximally entangled states has already been studied28,29. Using the results, the secret key rate per sifted signal of d-dimensional QKD can be written as given in Eq. (13):
| 13 |
where Q is the state error rate. As previously mentioned, MDI-QKD has the disadvantage of a lower secret key rate than that of the original BB84 protocol since Alice and Bob must discard more trials in MDI-QKD than in BB84 because of the success probability of the BSM. Here, we investigate the secret key rate per total signal of d-dimensional MDI-QKD. The secret key rate per total signal R is obtained from (sifted signal rate) × (secret key rate per sifted signal), where the sifted signal rate contains the probability that the d-dimensional d-photon entangled state discrimination succeeds and that Alice and Bob chose the same basis. In d-dimensional MDI-QKD, the number of possible combinations that Charlie can receive is d2 since Alice and Bob each use d different orthonormal states. Among the possible combinations, only the states in which all photons exist in different ports are post-selected by means of nondestructive photon number measurements. They are projected onto {|Φi〉 |Φi||i = 0, 1, 2, …, d − 1}, and all other states are discarded. Thus, the success probability of d-dimensional d-photon entangled state discrimination is 1/d in the ideal situation in which we ignore all experimental factors and there is no eavesdropper. With this probability, the secret key rate per total signal of d-dimensional MDI-QKD can be calculated as rd/(2d), where the 2 in the denominator comes from the probability that Alice and Bob choose the same basis. The secret key rates per total signal of d-dimensional MDI-QKD with various values of d are shown in Fig. 6. It is already known that high-dimensional QKD is more robust against state error than qubit QKD is27–30, this phenomenon is also reflected in this plot. In the case of no error, when Q = 0, only MDI-QKD using qutrit states has a higher key rate than that of the original qubit MDI-QKD protocol. The expression for the secret key rate per total signal when Q = 0 is . In this expression, the denominator increases linearly with the number of dimensions while the numerator increases logarithmically, so the secret key rate decreases in the high-dimensional case. From the plot, we can identify that qutrit MDI-QKD has the highest secret key rate per total signal when 0 ≤ Q ≤ 0.0294. This means that qutrits are best high-dimensional quantum states for MDI-QKD in the low-error range.
Figure 6.
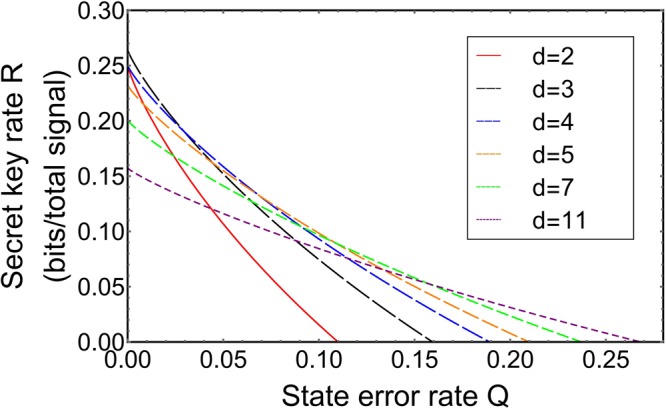
The secret key rate per total signal of d-dimensional MDI-QKD in the ideal situation. Since the number of states that can be discriminated via generalized d-dimensional d-photon entangled state discrimination is d among the d2 possible states considered, the success probability of entangled state discrimination is 1/d if all experimental factors are ignored. The secret key rate per total signal, R, can be obtained as follows: (secret key rate per sifted signal, r) × (probability that a trial produces a sifted signal). The plot shows that only MDI-QKD using 3-dimensional quantum states has a higher secret key rate than that of the original MDI-QKD protocol at Q = 0, the zero-error case.
In real experiments, our proposed setup can fail even if the input state is one of {|Φi〉i = 1, 2, …, d − 1} since the setup involves nondestructive photon number measurements and the success probability of such measurements is not 100%. The generalized d-dimensional d-photon entangled state discrimination setup involves d nondestructive photon number measurements, so the efficiency of this setup is exponentially affected by the success probability of these measurements. To investigate its usefulness, we compare the generalized setup with a “Bell filter” that consists only of linear optical elements59. The Bell filter can discriminate |Ψ0〉 regardless of dimensionality, so the sifted signal rate of d-dimensional MDI-QKD using the Bell filter is always 1/d2, where we ignore the probability that Alice and Bob choose the same basis since it is the same for all considered protocols. For the generalized setup we propose, the sifted signal rate is 1/d × (η)d, where η is the success probability of each nondestructive photon number measurement. For the sifted signal rates of the two setups to be the same, η should be η = (1/d)(1/d); examples of the value of η are 0.693, 0.707, and 0.725 for 3, 4, and 5 dimensions, respectively. Since the efficiency of nondestructive photon number measurements using an atom-cavity system was reported to be 0.66 in 201370, the success probability of the proposed setup is lower than that of a Bell filter with current technology, even though the proposed setup can discriminate more states than the Bell filter can.
Discussion
We investigated a tripartite entangled qutrit state discrimination setup and its applications, especially teleportation and MDI-QKD. We showed that the proposed setup can discriminate three tripartite entangled qutrit states. We showed that the setup can be generalized to d-dimensional d-photon entangled state discrimination and that the secret key rate per total signal of d-dimensional MDI-QKD using the generalized setup is highest when qutrit states are used. We considered the efficiency of the nondestructive photon number measurements performed in the setup and calculated the efficiency bound of the proposed setup for which the sifted signal rate becomes higher than that of a Bell filter that consists of linear optical elements59. Since the success probability of the nondestructive photon number measurements using an atom-cavity system is 66%70, the proposed setup is not as efficient as a Bell filter with current technology. However, we expect that the proposed setup will be more efficient with future technologies.
Methods
Tritter operation in the proposed setup
A schematic diagram of the tritter that corresponds to the unitary operator is shown in Fig. 7. The tritter contains only linear optical elements: two 50:50 beam splitters, one beam splitter whose reflectivity is 1/3 and several phase shifters. When the input states is one of the state described in Eq. (2), the output state after the tritter operation can be easily obtained from the input-output relation of the tritter given in Eq. (1); the possible states are given in Eq. (14):
| 14 |
where i ∈ {0, 1, 2}, the value of a subscript j in Eq. (14) is equal to as 3 + [j (mod 3)] if a number in the subscript is larger than 5, and an unimportant global phase is ignored. The results for the discrimination setup (Eq. (3)) are obtained directly from Eq. (14).
Figure 7.
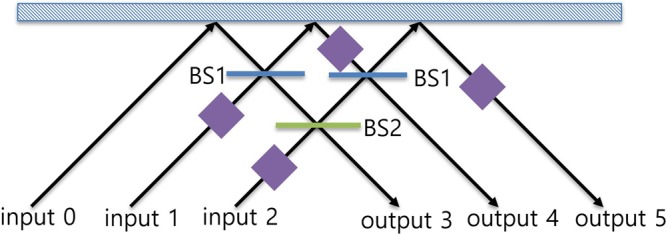
A schematic diagram of the tritter setup for realizing the unitary operator described in Eq. (1). The blue box represents a mirror, each BS1 (blue line) represents a 50:50 beam splitter, BS2 (green line) represents a beam splitter whose reflectivity is 1/3, and the purple squares represent phase shifters.
d-dimensional d-photon state discrimination setup
Our proposed setup can be easily generalized to a setup for d-dimensional d-photon entangled state discrimination. For d-dimensional d-photon entangled state discrimination, we need to generalize the three-path operation in Eq. (1) to a d-path operation, which is described by a d × d discrete Fourier transform operation , as shown in Eq. (15):
| 15 |
where χ = exp(2πi/d). The unitary operation can be realized by means of a tritter with d inputs and d outputs. As an extension of the tripartite entangled qutrit state discrimination setup, the d-dimensional d-photon entangled state discrimination setup consists of a d-input d-output tritter, d nondestructive photon number measurements, and d2 on-off detectors. One of the states that the generalized setup can discriminate is very similar to the state that can be discriminated by means of the existing setup59, this state is given in Eq. (16):
| 16 |
where
| 17 |
and |vac〉 means the vacuum state. Let us recall that in our notation, is the photon creation operator whose orthonormal mode is x and whose path label is y; thus, it can be rewritten as . If we extend the state with respect to the first row, then the state is rewritten as shown in Eq. (18):
| 18 |
where
| 19 |
and Λ0i is the (d − 1) × (d − 1) submatrix obtained by omitting the (i + 1)th column and first row of Λ. Similar to the case of tripartite entangled qutrit state discrimination, all states that the generalized setup can discriminate are orthogonal to |Φ0〉 with a phase factor χ; these states can be described as given in Eq. (20):
| 20 |
where i ∈ {0, 1, 2, 3, …, d − 1}. These d states can be discriminated from the combinations of clicked detectors in the generalized setup after post-selection using nondestructive photon number measurements.
Acknowledgements
We acknowledge the financial support from the National Security Research Institute (NSRI). W. Son acknowledges the support provided by KIAS through the Open KIAS Program.
Author Contributions
Y.J. designed and analysed the protocols. K.B. contributed to the analysis. W.S. supervised the whole project. All authors reviewed the manuscript.
Competing Interests
Y. Jo was funded by the Agency for Defense Development (ADD). K. Bae and W. Son were funded by The National Security Research Institute (NSRI). W. Son received a salary from Sogang University. W. Son also acknowledges the University of Oxford and KIAS for their visitorship programme.
Footnotes
Publisher’s note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Bennett, C. H. & Brassard, G., Quantum cryptography: Public key distribution and coin tossing. in Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing (IEEE Press, New York, 1984), 175.
- 2.Ekert A. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991;67:661. doi: 10.1103/PhysRevLett.67.661. [DOI] [PubMed] [Google Scholar]
- 3.Deutsch D, et al. Quantum Privacy Amplification and the Security of Quantum Cryptography over Noisy Channels. Phys. Rev. Lett. 1996;77:2818. doi: 10.1103/PhysRevLett.77.2818. [DOI] [PubMed] [Google Scholar]
- 4.Mayers D. Unconditional security in quantum cryptography. J. Assoc. Comput. Mach. 2001;48:351. doi: 10.1145/382780.382781. [DOI] [Google Scholar]
- 5.Shor P, Preskill J. Simple Proof of Security of the BB84 Quantum Key Distribution Protocol. Phys. Rev. Lett. 2000;85:441. doi: 10.1103/PhysRevLett.85.441. [DOI] [PubMed] [Google Scholar]
- 6.Devetak I, Winter A. Distillation of secret key and entanglement from quantum states. Proc. R. Soc. Lond. A. 2005;461:207. doi: 10.1098/rspa.2004.1372. [DOI] [Google Scholar]
- 7.Breguet J, Muller A, Gisin N. Quantum Cryptography with Polarized Photons in Optical Fibres. J. Mod. Opt. 1994;41:2405–2412. doi: 10.1080/09500349414552251. [DOI] [Google Scholar]
- 8.Muller A, Zbinden H, Gisin N. Underwater quantum coding. Nature. 1995;378:449. doi: 10.1038/378449a0. [DOI] [Google Scholar]
- 9.Muller A, et al. “Plug and play” systems for quantum cryptography. Appl. Phys. Lett. 1997;70:793. doi: 10.1063/1.118224. [DOI] [Google Scholar]
- 10.Naik D, Peterson C, White A, Berglund A, Kwiat P. Entangled state quantum cryptography: eavesdropping on the Ekert protocol. Phys. Rev. Lett. 2000;84:4733. doi: 10.1103/PhysRevLett.84.4733. [DOI] [PubMed] [Google Scholar]
- 11.Schumacher B. Quantum coding. Phys. Rev. A. 1995;51:2738. doi: 10.1103/PhysRevA.51.2738. [DOI] [PubMed] [Google Scholar]
- 12.Collins D, Gisin N, Linden N, Massar S, Popescu S. Bell inequalities for arbitrarily high-dimensional systems. Phys. Rev. Lett. 2002;88:040404. doi: 10.1103/PhysRevLett.88.040404. [DOI] [PubMed] [Google Scholar]
- 13.Son W, Lee J, Kim MS. D-Outcome Measurement for a NonlocalityTest. J. Phys. A: Math. Gen. 2004;37:11897. doi: 10.1088/0305-4470/37/49/009. [DOI] [Google Scholar]
- 14.Bae G, Son W. Axiomatic approach for the functional bound of multipartite high dimensional correlation. Curr. Appl. Phys. 2016;16:378. doi: 10.1016/j.cap.2015.12.005. [DOI] [Google Scholar]
- 15.Bae G, Son W. Analytic evaluation of the high-order quantum correlation for non-locality. J. Korean Phys. Soc. 2016;69:1625. doi: 10.3938/jkps.69.1625. [DOI] [Google Scholar]
- 16.Salavrakos A, et al. Bell Inequalities Tailored to Maximally Entangled States. Phys. Rev. Lett. 2017;119:040402. doi: 10.1103/PhysRevLett.119.040402. [DOI] [PubMed] [Google Scholar]
- 17.Braunstein S, D’Ariano G, Milburn G, Sacchi M. Universal Teleportation with a Twist. Phys. Rev. Lett. 2000;84:3486. doi: 10.1103/PhysRevLett.84.3486. [DOI] [PubMed] [Google Scholar]
- 18.Son W, Lee J, Kim MS, Park YJ. Conclusive teleportation of a d -dimensional unknown state. Phys. Rev. A. 2001;64:064304. doi: 10.1103/PhysRevA.64.064304. [DOI] [Google Scholar]
- 19.Thew R, Acín A, Zbinden H, Gisin N. Bell-Type Test of Energy-Time Entangled Qutrits. Phys. Rev. Lett. 2004;93:010503. doi: 10.1103/PhysRevLett.93.010503. [DOI] [Google Scholar]
- 20.Ali-Khan I, Howell J. Experimental demonstration of high two-photon time-energy entanglement. Phys. Rev. A. 2006;73:031801. doi: 10.1103/PhysRevA.73.031801. [DOI] [Google Scholar]
- 21.Schaeff C, et al. Scalable fiber integrated source for higher-dimensional path-entangled photonic quNits. Opt. Express. 2012;20:16145. doi: 10.1364/OE.20.016145. [DOI] [Google Scholar]
- 22.Rossi A, Vallone G, Chiuri A, Martini F, Mataloni P. Multipath Entanglement of Two Photons. Phys. Rev. Lett. 2009;102:153902. doi: 10.1103/PhysRevLett.102.153902. [DOI] [PubMed] [Google Scholar]
- 23.Lee H, Choi S, Park H. Experimental Demonstration of Four-Dimensional Photonic Spatial Entanglement between Multi-core Optical Fibres. Sci. Rep. 2017;7:4302. doi: 10.1038/s41598-017-04444-8. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Wang J, et al. Science. 2018. Multidimensional quantum entanglement with large-scale integrated optics; pp. 285–291. [DOI] [PubMed] [Google Scholar]
- 25.Leach J, Padgett M, Barnett S, Franke-Arnold S, Courtial J. Measuring the Orbital Angular Momentum of a Single Photon. Phys. Rev. Lett. 2002;88:257901. doi: 10.1103/PhysRevLett.88.257901. [DOI] [PubMed] [Google Scholar]
- 26.Malik M, et al. Multi-photon entanglement in high dimensions. Nat. Photon. 2016;10:248. doi: 10.1038/nphoton.2016.12. [DOI] [Google Scholar]
- 27.Cerf N, Bourennane M, Karlsson A, Gisin N. Security of Quantum Key Distribution Using d-Level Systems. Phys. Rev. Lett. 2002;88:127902. doi: 10.1103/PhysRevLett.88.127902. [DOI] [PubMed] [Google Scholar]
- 28.Durt T, Kaszlikowski D, Chen J, Kwek L. Security of quantum key distributions with entangled qudits. Phys. Rev. A. 2004;69:032313. doi: 10.1103/PhysRevA.69.032313. [DOI] [Google Scholar]
- 29.Ferenczi A, Lütkenhaus N. Symmetries in quantum key distribution and the connection between optimal attacks and optimal cloning. Phys. Rev. A. 2012;85:052310. doi: 10.1103/PhysRevA.85.052310. [DOI] [Google Scholar]
- 30.Coles P, Metodiev E, Lütkenhaus N. Numerical approach for unstructured quantum key distribution. Nat. Commun. 2016;7:11712. doi: 10.1038/ncomms11712. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.Bechmann-Pasquinucci H, Tittel W. Quantum cryptography using larger alphabets. Phys. Rev. A. 2000;61:062308. doi: 10.1103/PhysRevA.61.062308. [DOI] [Google Scholar]
- 32.Ali-Khan I, Broadbent C, Howell J. Large-alphabet quantum key distribution using energy-time entangled bipartite states. Phys. Rev. Lett. 2007;98:060503. doi: 10.1103/PhysRevLett.98.060503. [DOI] [PubMed] [Google Scholar]
- 33.Mower J, et al. High-dimensional quantum key distribution using dispersive optics. Phys. Rev. A. 2013;87:062322. doi: 10.1103/PhysRevA.87.062322. [DOI] [Google Scholar]
- 34.Nunn J, et al. Large-alphabet time-frequency entangled quantum key distribution by means of time-to-frequency conversion. Opt. Express. 2013;21:15959. doi: 10.1364/OE.21.015959. [DOI] [PubMed] [Google Scholar]
- 35.Gröblacher S, Jennewein T, Vaziri A, Weihs G, Zeilinger A. Experimental quantum cryptography with qutrits. N. J. Phys. 2006;8:75. doi: 10.1088/1367-2630/8/5/075. [DOI] [Google Scholar]
- 36.Mirhosseini M, et al. High-dimensional quantum cryptography with twisted light. N. J. Phys. 2015;17:033033. doi: 10.1088/1367-2630/17/3/033033. [DOI] [Google Scholar]
- 37.Sit A, et al. High-dimensional intracity quantum cryptography with structured photons. Optica. 2017;4:1006. doi: 10.1364/OPTICA.4.001006. [DOI] [Google Scholar]
- 38.Acín A, Gisin N, Masanes L. From Bell’s Theorem to Secure Quantum Key Distribution. Phys. Rev. Lett. 2006;97:120405. doi: 10.1103/PhysRevLett.97.120405. [DOI] [PubMed] [Google Scholar]
- 39.Acín A, et al. Device-Independent Security of Quantum Cryptography against Collective Attacks. Phys. Rev. Lett. 2007;98:230501. doi: 10.1103/PhysRevLett.98.230501. [DOI] [PubMed] [Google Scholar]
- 40.Pironio S, et al. Device-independent quantum key distribution secure against collective attacks. N. J. Phys. 2009;11:103037. doi: 10.1088/1367-2630/11/4/045021. [DOI] [Google Scholar]
- 41.Hänggi, E. & Renner, R. Device-Independent Quantum Key Distribution with Commuting Measurements. arXiv:1009.1833 (2010).
- 42.Masanes L, Pironio S, Acín A. Secure device-independent quantum key distribution with causally independent measurement devices. Nat. Commun. 2011;2:238. doi: 10.1038/ncomms1244. [DOI] [PubMed] [Google Scholar]
- 43.Lim CCW, Portmann C, Tomamichel M, Renner R, Gisin N. Device-Independent Quantum Key Distribution with Local BellTest. Phys. Rev. X. 2013;3:031006. [Google Scholar]
- 44.Vazirani U, Vidick T. Fully Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2014;113:140501. doi: 10.1103/PhysRevLett.113.140501. [DOI] [PubMed] [Google Scholar]
- 45.Clauser J, Horne M, Shimony A, Holt R. Proposed Experiment to Test Local Hidden-Variable Theories. Phys. Rev. Lett. 1969;23:880. doi: 10.1103/PhysRevLett.23.880. [DOI] [Google Scholar]
- 46.Giustina M, et al. Bell violation using entangled photons without the fair-sampling assumption. Nature. 2013;497:227. doi: 10.1038/nature12012. [DOI] [PubMed] [Google Scholar]
- 47.Christensen B, et al. Detection-Loophole-Free Test of Quantum Nonlocality, and Applications. Phys. Rev. Lett. 2013;111:130406. doi: 10.1103/PhysRevLett.111.130406. [DOI] [PubMed] [Google Scholar]
- 48.Larsson J, et al. Bell-inequality violation with entangled photons, free of the coincidence-time loophole. Phys. Rev. A. 2014;90:032107. doi: 10.1103/PhysRevA.90.032107. [DOI] [Google Scholar]
- 49.Hensen B, et al. Loophole-free Bell inequality violation using electron spins separated by 1.3 kilometres. Nature. 2015;526:682. doi: 10.1038/nature15759. [DOI] [PubMed] [Google Scholar]
- 50.Rosenfeld W, et al. Event-Ready Bell Test Using Entangled Atoms Simultaneously Closing Detection and Locality Loopholes. Phys. Rev. Lett. 2017;199:010402. doi: 10.1103/PhysRevLett.119.010402. [DOI] [PubMed] [Google Scholar]
- 51.Lo H, Curty M, Qi B. Measurement-Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2012;108:130503. doi: 10.1103/PhysRevLett.108.130503. [DOI] [PubMed] [Google Scholar]
- 52.Lo H, Curty M, Tamaki K. Secure quantum key distribution. Nat. Photon. 2014;8:595. doi: 10.1038/nphoton.2014.149. [DOI] [Google Scholar]
- 53.Lütkenhaus N, Calsamiglia J, Suominen K-A. Bell measurements for teleportation. Phys. Rev. A. 1999;59:3295. doi: 10.1103/PhysRevA.59.3295. [DOI] [Google Scholar]
- 54.Jo Y, Son W. Key-rate enhancement using qutrit states for quantum key distribution with askew aligned sources. Phys. Rev. A. 2016;94:052316. doi: 10.1103/PhysRevA.94.052316. [DOI] [Google Scholar]
- 55.Hwang W, Su H, Bae J. N-dimensional measurement-device-independent quantum key distribution with N + 1 un-characterized sources: zero quantum-bit-error-rate case. Sci. Rep. 2016;6:30036. doi: 10.1038/srep30036. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 56.Dušek M. Discrimination of the Bell states of qudits by means of linear optics. Opt. Commun. 2001;199:161. doi: 10.1016/S0030-4018(01)01565-6. [DOI] [Google Scholar]
- 57.Calsamiglia J. Generalized measurements by linear elements. Phys. Rev. A. 2002;65:030301(R). doi: 10.1103/PhysRevA.65.030301. [DOI] [Google Scholar]
- 58.Goyal S, Konrad T. Teleporting photonic qudits using multimode quantum scissors. Sci. Rep. 2013;3:3548. doi: 10.1038/srep03548. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 59.Goyal S, Boukama-Dzoussi P, Ghosh S, Roux F, Konrad T. Qudit-Teleportation for photons with linear optics. Sci. Rep. 2014;4:4543. doi: 10.1038/srep04543. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 60.Reck M, Zeilinger A, Bernstein H, Bertani P. Experimental realization of any discrete unitary operator. Phys. Rev. Lett. 1994;73:58. doi: 10.1103/PhysRevLett.73.58. [DOI] [PubMed] [Google Scholar]
- 61.Imoto N, Watkins S, Sasaki Y. A nonlinear optical-fiber interferometer for nondemolitional measurement of photon number. Opt. Commun. 1987;61:159. doi: 10.1016/0030-4018(87)90240-9. [DOI] [Google Scholar]
- 62.Nogues G, et al. Seeing a single photon without destroying it. Nature. 1999;400:239. doi: 10.1038/22275. [DOI] [Google Scholar]
- 63.Krenn M, Malik M, Fickler R, Lapkiewicz R, Zeilinger A. Automated Search for new Quantum Experiments. Phys. Rev. Lett. 2016;116:090405. doi: 10.1103/PhysRevLett.116.090405. [DOI] [PubMed] [Google Scholar]
- 64.Krenn M, Hochrainer A, Lahiri M, Zeilinger A. Entanglement by Path Identity. Phys. Rev. Lett. 2017;118:080401. doi: 10.1103/PhysRevLett.118.080401. [DOI] [PubMed] [Google Scholar]
- 65.Marcikic I, et al. Distribution of Time-Bin Entangled Qubits over 50 km of Optical Fiber. Phys. Rev. Lett. 2004;93:180502. doi: 10.1103/PhysRevLett.93.180502. [DOI] [PubMed] [Google Scholar]
- 66.Donohue J, Agnew M, Lavoie J, Resch K. Coherent Ultrafast Measurement of Time-Bin Encoded Photons. Phys. Rev. Lett. 2013;111:153602. doi: 10.1103/PhysRevLett.111.153602. [DOI] [PubMed] [Google Scholar]
- 67.Volz T, et al. Ultrafast all-optical switching by single photons. Nat. Photon. 2012;6:605. doi: 10.1038/nphoton.2012.181. [DOI] [Google Scholar]
- 68.Sathyamoorthy S, et al. Quantum Nondemolition Detection of a Propagating Microwave Photon. Phys. Rev. Lett. 2014;112:093601. doi: 10.1103/PhysRevLett.112.093601. [DOI] [PubMed] [Google Scholar]
- 69.Xia K, Johnsson M, Knight P, Twamley J. Cavity-Free Scheme for Nondestructive Detection of a Single Optical Photon. Phys. Rev. Lett. 2016;116:023601. doi: 10.1103/PhysRevLett.116.023601. [DOI] [PubMed] [Google Scholar]
- 70.Reiserer A, Ritter S, Rempe G. Nondestructive Detection of an Optical Photon. Science. 2013;342:1349. doi: 10.1126/science.1246164. [DOI] [PubMed] [Google Scholar]
- 71.O’Brien C, Zhong T, Faraon A, Simon C. Nondestructive photon detection using a single rare-earth ion coupled to a photonic cavity. Phys. Rev. A. 2016;94:043807. doi: 10.1103/PhysRevA.94.043807. [DOI] [Google Scholar]
- 72.Coffman V, Kundu J, Wootters W. Distributed entanglement. Phys. Rev. A. 2000;61:052306. doi: 10.1103/PhysRevA.61.052306. [DOI] [Google Scholar]