Abstract
We present a self-contained proof of a uniform bound on multi-point correlations of trigonometric functions of a class of Gaussian random fields. It corresponds to a special case of the general situation considered in Hairer and Xu (large-scale limit of interface fluctuation models. ArXiv e-prints arXiv:1802.08192, 2018), but with improved estimates. As a consequence, we establish convergence of a class of Gaussian fields composite with more general functions. These bounds and convergences are useful ingredients to establish weak universalities of several singular stochastic PDEs.
Keywords: Multi-point correlation function, Trigonometric polynomial, Gaussian random fields
Introduction
Motivation from Weak Universalities
The study of singular stochastic PDEs has received much attention recently, and powerful theories are being developed to enhance the general understanding of this area. We refer to the excellent surveys [8, 11] and references therein for recent breakthroughs in the field.
One of the motivations to study singular SPDEs is that many of them are expected to be universal objects in crossover regimes of their respective universality classes, a phenomenon known as weak universality. One well-known example is the KPZ equation [14], formally given by
where is the one-dimensional space-time white noise. The equation is only formal since it involves the square of a distribution. Nevertheless, the solution can be rigorously constructed in a few different ways, including the Cole–Hopf transform [1], pathwise solutions via rough paths/regularity structures [3, 9, 10] or paracontrolled distributions [6], or the notion of energy solution through a martingale problem [4, 7].
The KPZ equation is expected to be the universal model for weakly asymmetric interface growth at large scales. In [12], the authors considered continuous microscopic models of the type
| 1.1 |
for any even polynomial F and smooth stationary Gaussian random field . The main result in [12] is that there exists such that the rescaled and re-centered height function
converges to the solution of the KPZ equation with
| 1.2 |
where and P is the heat kernel. Hairer and Xu [13] extended the result to arbitrary even functions F with sufficient regularity and polynomial growth. Similar results have also been obtained in [5] for models at stationarity.
To see why the convergence holds with given by (1.2), we write down the equation for :
where approximates the space-time white noise at scale . Let , then is stationary Gaussian with finite variance. In addition, by analogy with the standard KPZ equation, it is reasonable to expect that the remainder is almost bounded. Hence, one can Taylor expand the nonlinearity around and formally get
One then needs to show the convergence of the objects , , as well as their products, which arise from the local expansion of . Furthermore, such convergences need to be established in the optimal regularity space, which requires one to pth obtain moment bounds of these stochastic objects for arbitrarily large pth.
At least formally, by chaos expanding and taking , one can see that
| 1.3 |
where is given in (1.2) and is the limit of . This is because all terms starting from the 4-th chaos vanish termwise as , and only the second chaos component survives in the limit.
When F is even polynomial, this heuristic indeed gives a direct proof of the convergence of the term in (1.3). However, when F is not polynomial, the actual proof of the convergence becomes much subtler. The main obstacle is that expands into an infinite chaos series. If we brutally control their high moments termwise as in the polynomial case, then in order for these termwise moment bounds to be summable, we need to impose very strong conditions on F (namely, its Fourier transform being compactly supported), which is clearly too restrictive.
Instead, in [13], the authors expanded in terms of Fourier transform, developed a procedure in obtaining pointwise correlation bounds on trigonometric functions of Gaussians, and deduced the desired convergence from those bounds.
Similar universality results are also present in the dynamical model. The weak universality of equation for a large class of symmetric phase coexistence models with polynomial potential was established in [13] for Gaussian noise and then extended in [17] to non-Gaussian noise. The extension beyond polynomial potential (even with Gaussian noise) has the same difficulties as in the KPZ case discussed above. In the recent work [2], the authors developed different methods based on Malliavin calculus to control similar objects. The methods developed in [2, 13] to treat general nonlinearities are both robust enough to cover both KPZ and equations as well as other similar situations.
In this article, we follow the ideas developed in [13] and prove a uniform bound in a special case considered in there. This special case is technically simpler to explain, but is also illustrative enough to reveal the main idea of the proof for the more general case. Furthermore, we obtain a better bound in this special case, thus yielding convergence results for functions F with lower regularity.
Main Statements
Fix a scaling on , and let . The metric induced by is
Since the scaling is fixed throughout the article, we simply write |x| instead of . For any Gaussian random field X, any function with at most exponential growth, and any integer , we write
where denotes the n-th Wick power of X, and is the coefficient of in the chaos expansion of F(X). In other words, is F(X) with the first chaos removed. We refer to [16, Chapter 1] for more details on chaos expansion of random variables. We have the following bound.
Theorem 1.1
Let , and be a class of centered Gaussian random fields satisfying
| 1.4 |
for some and for all and all . Then, for every and , there exists depending on these parameters and only such that
| 1.5 |
for all , and .
Theorem 1.1 is the main technical ingredient to establish that if approximates a certain Gaussian random field , then a large class of nonlinear functions of , after proper rescaling and re-centering, converges to certain Wick powers of . We first give the assumption on the random field .
Assumption 1.2
is a stationary Gaussian random field with correlation1
where G satisfies the bounds
for some and all . In addition, there exists a locally integrable function g such that
| 1.6 |
in for every bounded subset of .
For and open subset , we define the norm on distributions on by
Our assumption on the function is the following.
Assumption 1.3
There exists such that the Fourier transform of F satisfies
where .
For every and , let
The main convergence theorem is the following.
Theorem 1.4
Let and F satisfy the above assumptions, and g be the limiting function of as in Assumption 1.2. Let be a mollifier on and . For every integer m, define
| 1.7 |
where is a Gaussian measure on with variance
| 1.8 |
Then, for every and every sufficiently small , we have
as almost surely in . Here, is the m-th Wick power of .
We will first prove the main bound (1.5) in Theorem 1.1 and then establish the convergence in Theorem1.4 by Fourier expanding F and applying (1.5) to . Note that although the bound in Theorem 1.1 holds for every integer m, the convergence in Theorem 1.4 requires . This can be easily seen from the fact that if , then would have divergent covariance and hence not well defined.
Example 1.5
One typical example of the random field satisfying Assumption 1.2 is , where is the white noise on , , and is the differential operator given by
This is the fractional Gaussian field. In this case, the convolution kernel K of is homogeneous (in the scaling ) of order in the sense that
for all . Hence, for g, G as in Assumption 1.2, we have the expression
The same is true when is given the parabolic scaling and is the heat operator.
In the case of standard Euclidean scaling , is simply the standard fractional Gaussian field . We refer to the survey [15] for more details on fractional Gaussian fields.
Example 1.6
As for the function F, all functions with polynomial growth fall in Assumption 1.3. More precisely, if for some , and there exist such that
for all , then F satisfies Assumption 1.3.
Example 1.7
One very interesting example of the microscopic model (1.1) is with . It is almost linear, but one still expects its large-scale behavior to be nonlinear as described by the KPZ equation. This function F even not , but we still have
which clearly satisfies Assumption 1.3. Hence, as a consequence of Theorem 1.1, if where is the space-time white noise with one space dimension, and P is the heat kernel, then we have
for some depending on the mollifier. This is the first step toward establishing convergence to the KPZ equation for the microscopic model of the form (1.1) with .
Remarks and Possible Generalizations
Theorem 1.1 is a special case of [13, Theorem 6.4] in that it allows only one frequency variable rather than multiple ones. On the other hand, it is also more general since it allows subtraction of Wiener chaos up to any order. Furthermore, the bound (1.5) is completely independent of , while the corresponding one in [13] is polynomial in . As a consequence of this improvement, the condition on F for the convergence in Theorem 1.4 to hold is weaker.
The main technical difference that results in this improvement, as we shall see later in Sect. 2, is that in the clustering procedure, we are able to take the clustering distance L being independent of rather than being quadratic in as in [13].
We shall note that the convergence results in this article are not sufficient to establish weak universality in general situations. These would require convergence of the products of the objects considered in Theorem 1.4, with possible subtraction of extra chaos components after taking product. The convergence of these products requires a more general bound than Theorem 1.1 and [13, Theorem 6.2]. We leave them to future work.
Proof of Theorem 1.1
This section is devoted to the proof of Theorem 1.1. Assumptions 1.2 and 1.3 on and F are irrelevant here. We fix , and let be a family of Gaussian random fields with correlation functions satisfying (1.4). The following preliminary bounds on the correlation function will be used throughout the section.
Proposition 2.1
Let . If , then
| 2.1 |
The bound is uniform over all and all pairs of points satisfying the above constraint. As a consequence, we have
| 2.2 |
for all and all .
Proof
The first bound follows from
where we have used the assumption in the second inequality. As for the second one, it suffices to notice
and then apply (2.1).
In what follows, we keep our notations same as in [13, Section 6]. For every finite set , let be the set of multi-indices on . For -tuple of Gaussian random variables and , we write  . Similarly, we write and . In general, we use standard letters for scalars and boldface ones to denote tuples.
. Similarly, we write and . In general, we use standard letters for scalars and boldface ones to denote tuples.
Fix and . Let . We also fix and arbitrary. Write . All the constants C below depend on , K, m, and r only unless otherwise mentioned. We seek bounds that are uniform in , , and . We also write for simplicity since the bounds will be independent of .
Clustering and the First Bound
Let be a fixed large constant whose value, depending on , K, m, and r only, will be specified later. Let be an equivalence relation on [K] such that if there exists and with and such that
for all . We let denote the partition of [K] into clusters obtained in this way. In other words, j and belong to the same cluster if and only if starting from , one can reach by performing jumps with sizes at most onto connecting points in .
We distinguish two cases depending on whether contains singletons or not. We first prove (1.5) when has no singleton; that is, every cluster in has at least two elements. In this case, we write down the explicit expression
| 2.3 |
Since , the coefficients are uniformly bounded in . We then plug the expansion (2.3) into the left-hand side of (1.5). The Gaussianity of the ’s and boundedness of the coefficients of the removed chaos imply
| 2.4 |
for some C independent of , , and . It then remains to show that the right-hand side of (1.5) is bounded by a constant from below. For this, we use the assumption that contains no singletons.
Let be arbitrary, and we label its elements by . Since has no singleton set, we necessarily have . By clustering, any two points in are at most away from each other. Hence, the assumption (1.4) implies (recalling that )
for every two points . which implies
where we identified with . Multiplying the above bound over all and using Wick’s formula and positivity of the correlations, we obtain
| 2.5 |
This is the place where we use for every , for otherwise the middle term above would contain the variance of a single random variable and the second inequality in (2.5) would be wrong. Combining (2.4) and (2.5), we obtain
| 2.6 |
which matches the right-hand side of (1.5). Since L (to be chosen later) is also independent of , , and , this concludes the case when contains no singleton. The rest of the section is devoted to establishing (1.5) when at least one cluster in is singleton.
Expansion
Given the collection of points and the clustering above, let
be the set of singletons in , and let . We write for simplicity if is a singleton set in .
For and , we write and for their restrictions to , and  . Splitting the left-hand side of (1.5) into sub-products within clusters and chaos expanding each sub-product, we can rewrite it as
. Splitting the left-hand side of (1.5) into sub-products within clusters and chaos expanding each sub-product, we can rewrite it as
| 2.7 |
Here, is the coefficient of in the chaos expansion of and has the expression
| 2.8 |
Note the product involving the expectation on the right-hand side of (2.7) is 0 if is odd. But we still sum over all integers N since this simplifies the notations later. The following lemma gives control on the coefficients .
Lemma 2.2
There exists depending on K, m, r, and only such that
| 2.9 |
for all , where we recall . As a consequence, we have
| 2.10 |
Furthermore, if , then we have
| 2.11 |
All the bounds are uniform in and , and in the location of subject to whether contains a singleton or not.
Proof
We express the right-hand side of (2.8) in a way that is convenient to estimate. For this, we introduce variables . Let denote the restriction of to , and write and . Using the identity
where if , we can rewrite the right-hand side of (2.8) as
When distributing r derivatives of each into the two terms in the parenthesis, the differentiation of the first term () yields an additional factor which is at most for some fixed constant C, while the second term is uniformly bounded both in and since ’s all have bounded variance. This gives (2.9). The bound (2.10) follows from (2.9) and the multinomial theorem.
Finally, in order to obtain (2.11) when , it suffices to note that for , we have
if , and is 0 otherwise. Since , we gain an additional Gaussian factor for every , and hence in total. The bound (2.11) then follows from relaxing it to .
Representative Point
For , the corresponding term in the expectation on the right-hand side of (2.7) is a Wick product of multiple Gaussian random variables. We aim to reduce it to the Wick product of a single variable by choosing a representative point from each cluster.
For every , choose arbitrary. The choice for is unique if is singleton. We have the following proposition.
Proposition 2.3
There exists such that
| 2.12 |
for every and every choice of .
Proof
If is odd, then both sides of (2.12) are 0, so we only need to consider the situation when is even.
In this case, the left-hand side is the sum of products of pairwise expectations for j and belonging to different clusters. The right-hand side (without the factor ) is the same except that each instance of for is replaced by . It then suffices to control the effects of such replacements.
Let be two different clusters in , and use and to denote and , respectively. For every and , according to the clustering, we have
which implies
Hence, by (2.1), we deduce that
This is the effect of one such replacement. The claim then follows since there are pairwise expectations in each product in the sum. It also means we can take in (2.12).
From now on, we restrict ourselves to the situation when , and recall the notation . We need to split the product on the right-hand side of (2.7) into sub-products in and in . For this, we introduce multi-indices and and write and . We then have the following proposition.
Proposition 2.4
Suppose . Then, the left-hand side of (1.5) can be controlled by
| 2.13 |
Proof
We start with the expression (2.7). Note that for , whenever , so we can relax the expression to
where both the sum and supremum are taken over with the further restriction that for all . The claim follows immediately by applying Lemma 2.2 and Proposition 2.3 to the right-hand side above and noting the range of the sum and supremum.
Graphic Representation
It remains to control the term involving the expectation on the right-hand side of (2.13). Since all ’s are Gaussian, it can be written as a sum over products of pairwise expectations. The number of terms in each product (and hence the total power) can be arbitrarily large since N will be summed over all integers. Following [13], we introduce graphic notations to describe these objects.
Given a set , we write for the set of all subsets of with exactly two elements. A (generalized) graph is a triple . Here, is the set of vertices, and is the set of edges with multiplicities. More precisely, each edge has multiplicity . We do not allow self-loops, so for all . Finally, is a function that assigns a value to each pair of vertices.
Given a graph , we define the degree of a point and of , respectively, by
The value of is defined by
In what follows, we always take fixed (so is the clusters in ), and . We also fix the representative points chosen for each . Hence, the only variable in our graph is the multiplicity of the edges. Recall the decomposition into singletons and clusters with at least two points. We introduce the following definition to characterize the pairings that appear in the expectation term on the right-hand side of (2.13).
Definition 2.5
For each and , the set consists of graphs with and R specified above, and such that for all , for all , and for all other .
Let be the set of graphs such that both of the following hold:
for some and with the restriction that for every and for each .
If for some , then there exists such that .
Remark 2.6
The first requirement for above is equivalent to that for all , for all , and is 0 for all other points. The second requirement says that if has a nonzero degree, then all its edges must be connected to a single point for some . We will see later that the definition of corresponds to “minimal graphs” after the reduction procedure in the next subsection.
Remark 2.7
The clustering depends on the choice of L, and hence so do the definitions of and . On the other hand, these are just intermediate steps and our final bound (1.5) does not involve clustering at all. Furthermore, the choice of L later [in (2.18)] is also independent of the location of . Hence, we omit the dependence of the clustering on L here for notational simplicity.
Reduction
We now start to control the right-hand side of (2.13). If is odd, then the term with the expectation is 0. So we only need to deal with the case when is even.
In that case, the number of different pairings contributing to the expectation in (2.13) is at most , so with Definition 2.5, we have
| 2.14 |
Comparing the above bound and the right-hand side of (2.13), we see that we need to control for with arbitrarily large and . We first bound it by values of the graphs in , which is done via a reduction procedure. After that, we enhance the graphs in to match the right-hand side of (1.5) to conclude the proof.
We start with the reduction step. This is where we need to choose the clustering distance L sufficiently large, which will ensure the uniform in bound after summing over and . We first give the following proposition, which reduces graphs in to those in .
Proposition 2.8
There exists depending on only such that
for every pair and every . The constant C does not depend on the choice of L, though the clusters and the definitions of and do.
Proof
Fix , , and arbitrary. It suffices to show that if , then we can find a with , and strictly such that
| 2.15 |
One can then iterate this bound until the graph is reduced to some to conclude the proposition. This necessarily happens since each time the total degree of the graph decreases strictly. Here, the inequality on and means the inequality in each component.
To see the existence of such a when , we consider the two situations where either one of the two conditions for in Definition 2.5 is violated. We first consider the violation of Condition 1. Since , failure of Condition 1 means there exists such that . We fix this j, and there are two possibilities in this situation.
Case 1. There exist such that and . In this case, we let be the graph obtained from by performing the following operations:
The only point whose degree has been changed in this operation is (reduced by 2). Hence, we have with and . To see the bound (2.15), we note that by definition of , is at least away from both and . Hence, by (2.2), we have
In graphic notation, this means
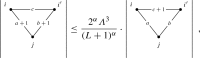 |
where we have omitted x and simply write the indices to denote vertices. Since all the other parts of the graph remain unchanged, this operation gives a desired with (2.15).
Case 2.
If for the that violates Condition 1, all its edges are connected to another point , then we necessarily have . Thus, we let be the graph obtained from by reducing by two. Then, with but this time . Since , we also have the bound
which is also of the form (2.15). This completes the treatment of the violation of Condition 1.
We now turn to the situation when Condition 2 is violated. This means there exists such that
either is connected to two other different points and ;
or is connected to for some .
For (a), we perform exactly the same operation as Case 1 in the above situation. This will give rise to a graph in with , and for all other , and satisfying (2.15). For (b), we simply reduce by 1, which results a graph in with and the desired bound (2.15).
Since the above cases have covered all the possibilities for , we have completed the proof of the proposition.
The following proposition is then a simple consequence.
Proposition 2.9
There exist and depending on , K, m, and r only such that for every , every location , and every , we have the bound
| 2.16 |
Remark 2.10
The bound is completely independent of and , and its dependence on the location of is via only. Also note that the clustering, and hence , depends on the choice of L.
Proof of Proposition 2.9
Note that graphs in have degree , so by Proposition 2.8, there exists such that
for all and . Combining it with Proposition 2.4 and (2.14), we get
| 2.17 |
for some constant . One can choose L sufficiently large depending on and only such that
| 2.18 |
This guarantees that the exponential term is uniformly bounded in . Since depends on , K, m, and r only, so does L. Finally, is also uniformly bounded since graphs in have degrees at most . This completes the proof.
Remark 2.11
The reason why we need to choose L large is to ensure the exponential and hence the whole right-hand side of (2.17) being uniformly bounded in . As we see now, the Gaussian factor in (2.11) allows us to choose such L being independent of . Together with the enhancement procedure in Sect. 2.6, this ensures the bounds in Proposition 2.9 and hence in Theorem 1.1 are completely independent of .
Without the Gaussian factor, one would need to take L quadratic in to make the exponential in (2.17) bounded, and the enhancement procedure in below would produce a bound that is polynomial in with its degree depending on m and K.
Enhancement and Conclusion of the Proof
From now on, we fix the choice of L in (2.18). We need to control the right-hand side of (2.16) by that of (1.5). To achieve this, we enhance every to a graph where for every , which matches the pairing occurring in the desired upper bound. The enhancement procedure will also be performed in such a way that is an upper bound for up to some proportionality constant, which is uniform in , , and subject to . This will lead to bound (1.5). The procedure is similar to the one used to obtain (2.6) when .
Fix arbitrary, so in particular, for some and . By the definition of , for all . For every , we have , and all of them are connected to one single for some if . All other points in have degree 0. To construct , we add new edges to vertices in and also move around existing edges, but keep unchanged for all throughout the procedure. We do this cluster by cluster and write for simplicity.
Fix arbitrary. To perform the enhancement operation for , we let be such that is the unique singleton point connected to if . This also includes , in which case s could be arbitrary. We distinguish several situations depending on the number of points in .
Case 1. . Let denote the other point in . By definition of , we have . We then perform the following operations. We move of the edges between and to connecting and and add edges between and . By clustering, we have and . Hence, Proposition 2.1 gives the bounds
where L as chosen in (2.18) is independent of , , and . So in graphic notation, the above operation gives
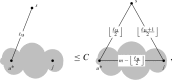 |
where the gray area indicates the cluster , and we have omitted drawing the remaining or edges from . We also drop and simply use the graph itself to denote its value. Then, or is unchanged in the procedure. Furthermore, we have and after the operation. This also includes the situation .
Case 2. . Let i, j denote the two other points in . We then perform the operation
 |
We see is unchanged. One can also check that or , and . So we have the correct degrees of the vertices as well as the desired bound.
Case 3. . We denote the other points in the cluster by . For of them, say , we perform the same operation as in Sect. 2.1 by cyclically connecting them with edges of multiplicities . This yields the bound
For the remaining points and , we perform the same operation as in Case 1 above. This again raises the degrees of all points in to m or with a desired bound.
Every cluster falls into one of the above three cases. The graph is obtained by performing the above operations to all . It is clear from the bounds in the above three situations that there exists such that
It is also straightforward to check that in , we have for all , and hence it represents one of the pairings from the expectation
Hence, we deduce there exists such that
| 2.19 |
for all , , and , and this is true for all . Combining (2.19) and Proposition 2.9, we obtain the bound (1.5) in the case .
Since the bound when has already been established in (2.6), we have thus completed the proof of Theorem 1.1.
Convergence of the Fields—Proof of Theorem 1.4
We are now ready to prove Theorem 1.4. For notational simplicity, we write to denote that , where the constant C depends only on the parameter(s) in the subscripts of the symbol (and in this case ).
In order to apply the bound in Theorem 1.1, we use the convention for such that
But this only appears in intermediate steps, and the final statement does not depend on the definition of . For every , every , and every , we let
Recall that , where is the rescaled mollifier. Also recall the form of in (1.7). We first give the convergence criterion.
Proposition 3.1
Let and . If for every compact and every , we have
| 3.1 |
as , then in for every .
The proof of the proposition is standard Kolmogorov’s criterion, and so it remains to prove (3.1). By stationarity, we can simply restrict to the case in (3.1). Writing as well as , we need to show for all small that
| 3.2 |
as , uniformly over and smooth supported in a ball of radius 1 such that . The rest of the section is devoted to the proof of (3.2).
Since is stationary, so is . Hence, has stationary Gaussian distribution with
| 3.3 |
where G is the correlation function of as in Assumption 1.2. The coefficient of the m-th term in the chaos expansion of is given by
We split the difference into three parts by
| 3.4 |
and we show that each of them satisfies a bound of the form of (3.2).
The latter two terms are simpler. For the second one, we notice that ensures is well defined, and for all sufficiently small , we have
uniformly over . Also, since is uniformly bounded in , it then follows immediately that
as , uniformly over and in the range required in Proposition 3.1.
For the third term, it suffices to notice that assumption (1.6) on G guarantees that , where and are given by (3.3) and (1.8). Hence, we immediately have . The desired bound of the form (3.2) then follows immediately from the boundedness of in .
We now turn to the first term on the right-hand side of (3.4), which requires the use of the bound in Theorem 1.1. We first note that the covariance of has the form
where denotes the forward convolution in the sense that . Assumption 1.2 on G guarantees that satisfies the assumption (1.4) in Theorem 1.1 with some . Since , and is precisely the m-th coefficient in the chaos expansion of , we have
| 3.5 |
We leave aside the factor and focus on for a moment. Fourier expanding F and changing the order of integration, we get the identity
where
| 3.6 |
and the subscript on the inner product indicates that the testing is taken with respect to the Fourier variable . We now omit the subscripts in for simplicity. Recall that . Multiplying by a partition of unity subordinate to the intervals and separating these terms, we get the bound
where is as in Assumption 1.3. Now, taking 2n-th moments on both sides and using triangle inequality, we get
| 3.7 |
There are two suprema inside the expectation. The first supremum is taken over elements, so we can move it out of at the cost of a constant multiple depending on M and n only. The second one is taken over an interval, so we need the following lemma to interchange it with the expectation.
Lemma 3.2
Suppose f is a random function on an interval . For every , there exists C depending on p and only such that
Proof
Fix arbitrary. By fundamental theorem of calculus and Hölder’s inequality, we have
Raising both sides to p-th power, we get
where C depends on p and . The assertion then follows by taking expectation on both sides and noting that
This completes the proof of the lemma.
Using Lemma 3.2 to interchange the expectation and supremum, we have
where the supremum over r is taken over to include the one additional derivative required in the interchange. Plugging it back into the right-hand side of (3.7), we obtain
| 3.8 |
It then remains to control the quantity . Recalling the expression of in (3.6), we have
where we used the shorthand notation . We now apply Theorem 1.1 to the expectation part above, so that we get
Plugging it into the integral on the right-hand side above and using the identity
we get
| 3.9 |
In particular, the bound is uniform in both and . We have the following lemma controlling the right-hand side above.
Lemma 3.3
For every integer and every sufficiently small , we have
uniformly over .
Proof
Since is Gaussian, by equivalence of moments, the left-hand side above can be controlled by
so we only need to bound the second moment. By Wick’s formula, we have
Since , we have
for all . For all sufficiently small such that , the singularity on the right-hand side above is integrable, so we have
The proof is complete by taking square roots on both sides and replacing by .
Now, combining (3.8), (3.9) and Lemma 3.3, and using Assumption 1.3 on F, we get
Substituting the above bound back to (3.5), we deduce that
which is the desired bound. The proof of Theorem 1.4 is thus complete.
Acknowledgements
The author acknowledges the support from the Engineering and Physical Sciences Research Council through the fellowship EP/N021568/1. I also thank the anonymous referee for carefully reading the draft version of the article and providing helpful suggestions on improving the presentation.
Footnotes
References
- 1.Bertini L, Giacomin G. Stochastic burgers and KPZ equations from particle systems. Commun. Math. Phys. 1997;183(3):571–607. doi: 10.1007/s002200050044. [DOI] [Google Scholar]
- 2.Furlan, M., Gubinelli, M.: Weak universality for a class of 3D stochastic reaction-diffusion models. ArXiv e-prints (2017). arXiv:1708.03118
- 3.Friz PK, Hairer M. A Course on Rough Paths. Universitext. With an Introduction to Regularity Structures. Cham: Springer; 2014. [Google Scholar]
- 4.Goncalves P, Jara M. Nonlinear fluctuations of weakly asymmetric interacting particle systems. Arch. Rational Mech. Anal. 2014;212(2):597–644. doi: 10.1007/s00205-013-0693-x. [DOI] [Google Scholar]
- 5.Gubinelli, M., Perkowski, N.: The Hairer–Quastel universality result at stationarity. In: Stochastic analysis on large scale interacting systems, RIMS Kôkyûroku Bessatsu, vol. B59, pp. 101–115. Research Institute for Mathematical Sciences (RIMS), Kyoto (2016)
- 6.Gubinelli M, Perkowski N. KPZ reloaded. Commun. Math. Phys. 2017;349(1):165–269. doi: 10.1007/s00220-016-2788-3. [DOI] [Google Scholar]
- 7.Gubinelli M, Perkowski N. Energy solutions of KPZ are unique. J. Am. Math. Soc. 2018;312:427–471. doi: 10.1090/jams/889. [DOI] [Google Scholar]
- 8.Gubinelli M. A panorama of singular SPDEs. Proc. Int. Cong. Math. 2018;2:2277–2304. [Google Scholar]
- 9.Hairer M. Solving the KPZ equation. Ann. Math. 2013;1782:559–664. doi: 10.4007/annals.2013.178.2.4. [DOI] [Google Scholar]
- 10.Hairer M. A theory of regularity structures. Invent. Math. 1982;2014:269–504. doi: 10.1007/s00222-014-0505-4. [DOI] [Google Scholar]
- 11.Hairer M. Renormalisation of parabolic stochastic PDEs. Jpn. J. Math. 2018;13(2):187–233. doi: 10.1007/s11537-018-1742-x. [DOI] [Google Scholar]
- 12.Hairer, M., Quastel, J.: A class of growth models rescaling to KPZ. ArXiv e-prints (2015). arxiv:1512.07845
- 13.Hairer, M., Xu, W.: Large-scale limit of interface fluctuation models. Ann Probab. ArXiv e-prints (2018). arXiv:1802.08192
- 14.Kardar M, Parisi G, Zhang Y-C. Dynamical scaling of growing interfaces. Phys. Rev. Lett. 1986;56:889–892. doi: 10.1103/PhysRevLett.56.889. [DOI] [PubMed] [Google Scholar]
- 15.Lodhia A, Sheffield S, Sun X, Watson S. Fractional Gaussian fields: a survey. Probab. Surv. 2016;13:1–56. doi: 10.1214/14-PS243. [DOI] [Google Scholar]
- 16.Nualart D. The Malliavin Calculus and Related Topics. Probability and its Applications (New York) 2. Berlin: Springer; 2006. [Google Scholar]
- 17.Shen H, Xu W. Weak universality of dynamical : non-Gaussian noise. Stoch. Partial Differ. Equ. Anal. Comput. 2018;62:211–254. [Google Scholar]


