Abstract
In this paper, we evaluate the secrecy performance of multi-hop cognitive wireless sensor networks (WSNs). In the secondary network, a source transmits its data to a destination via the multi-hop relaying model using the transmit antenna selection (TAS)/selection combining (SC) technique at each hop, in the presence of an eavesdropper who wants to receive the data illegally. The secondary transmitters, including the source and intermediate relays, have to harvest energy from radio-frequency signals of a power beacon for transmitting the source data. Moreover, their transmit power must be adjusted to satisfy the quality of service (QoS) of the primary network. Under the joint impact of hardware imperfection and interference constraint, expressions for the transmit power for the secondary transmitters are derived. We also derive exact and asymptotic expressions of secrecy outage probability (SOP) and probability of non-zero secrecy capacity (PNSC) for the proposed protocol over Rayleigh fading channel. The derivations are then verified by Monte Carlo simulations.
Keywords: multi-hop wireless sensor networks, physical-layer security, transmit antenna selection, selection combining, cognitive radio, energy harvesting, hardware impairments
1. Introduction
Security is one of the important issues in wireless sensor networks (WSNs) due to the broadcast nature of wireless medium. Conventionally, encryption/decryption algorithms that generate public/private keys are used to guarantee security [1,2]. Recently, a security framework for the physical layer, called the wiretap channel or physical-layer security (PLS) [3,4,5,6,7], has been introduced as a potential solution. In PLS, the difference between the channel capacity of the data link and the channel capacity of the eavesdropping link, named secrecy capacity, is commonly used to evaluate secrecy performance such as average secrecy capacity (ASC), secrecy outage probability (SOP), and probability of non-zero secrecy capacity (PNSC). Hence, to enhance the secrecy performance, the quality of the data and eavesdropping links should be increased and decreased, respectively. To enhance the channel capacity of the data links, diversity transmit and receive methods [8,9,10] can be used. In [8], the transmit antenna selection (TAS) technique is employed at a multi-antenna base station (BS) to maximize the instantaneous signal-to-noise ratios (SNRs) obtained between BS and intended users. References [9,10] considered MIMO secure communication systems, where the transmitter uses the TAS technique, while the legitimate receiver and eavesdropper can use selection combining (SC) or maximal ratio combining (MRC) for reception. In [11,12,13,14,15], cooperative relaying strategies were proposed to improve secrecy performance via increasing the channel capacity for the data links. Moreover, to avoid the eavesdropper combining the data with MRC, a randomize-and-forward (RF) strategy [16] can be employed, where the source and relays generate different code-books to confuse the eavesdropper. For significantly degrading the eavesdropping channels, cooperative jamming (CJ) methods were reported in [17,18,19]. The basic idea of the CJ method is that jammer nodes are employed to generate artificial noises on the eavesdropper. In addition, the legitimate receivers have to cooperate with the jammers to remove the interference appeared in their received signals. However, the implementation of this technique can be a difficult work due to the requirement of high synchronization between the nodes.
Recently, wireless energy harvesting (EH) [20,21] has emerged as a potential solution to prolong the lifetime of WSNs. In wireless EH, the energy-constrained devices can harvest energy from radio frequency signals generated by ambient nodes. In [21], EH amplify-and-forward (AF) relaying protocols were proposed and analyzed, where the relay node harvests energy from the source for transmitting the source data to the destination. The authors of [22] considered both AF and decode-and-forward (DF) relaying schemes employed a hybrid power splitting (PS) and time switching (TS) EH relay. In [23,24,25], power beacons (PBs) are deployed in the networks to charge energy for wireless devices. The PB-aided wireless power transfer models are suitable for large-scale WSNs or wireless ad-hoc networks. Moreover, to avoid causing the co-channel interference to the receivers, channels used for harvesting energy from the wireless signals of PBs are different from those used for the data transmission. In [23,24,25], the authors studied the performance of secondary networks in PB-assisted underlay cognitive radio (PB-UCR), where the transmit power of secondary users was limited by both the harvested energy and the maximum interference levels required by primary users. In [26], a secure communication scenario in cognitive sensor radio networks with an EH eavesdropper was introduced. Reference [27] proposed various path-selection protocols in multi-path multi-hop relaying networks in the presence of active eavesdroppers. Moreover, in [27], all of the terminals whose transceiver hardware is low-cost suffered from hardware imperfection due to phase noise, I/Q imbalance (IQI), amplifier nonlinearities, etc. [28,29,30].
This paper deals with multi-hop secure communication networks in PB-UCR under impact of hardware impairments. In [31], the authors first evaluated the secrecy capacity in the presence of IQI for OFDMA communication systems. Reference [32] proposed a secure massive MIMO system with a passive multiple-antenna eavesdropper and hardware noises. The results in [31,32] showed that the hardware impairments significantly impact of the secrecy performance. Next, unlike [27], our scheme considers the PB-URC networks using the MIMO-based TAS/SC relaying technique. In [33,34,35], cooperative multi-hop full-duplex relaying networks were proposed to enhance the end-to-end secrecy performance. However, it is too difficult to apply these schemes into WSNs due to the complexity of full-duplex operation. References [36,37,38] introduced simple multi-hop secure relaying scenarios in which all of the nodes are equipped with a single antenna. In [39], PLS in downlink MIMO multi-hop heterogeneous cellular networks were investigated. In particular, the data transmission between base stations and mobile users is realized via direct or multi-hop mode. In [40], a multi-hop multicasting secure transmission protocol with multi-antenna DF relays in the presence of multiple eavesdroppers was proposed and analyzed. However, in [36,37,38,39,40], the authors did not consider the cognitive environment as well as the wireless EH technique.
To the best of our knowledge, there is no published work related to multi-hop secure transmission in PB-UCR under the impact of hardware noises. In the proposed protocol, a secondary source transmits its data to a secondary destination using the multi-hop mode in the presence of a secondary eavesdropper. To support the reliable communication at each hop, the TAS/SC technique is used to forward the source data. Operating on the underlay spectrum sharing method, the transmit power of the secondary source and relay nodes must be adjusted to satisfy the required QoS of the primary network. Moreover, the secondary transmitters have to harvest energy from PB deployed in the secondary network for the data transmission. The main contribution of this paper can be summarized as follows:
We propose a simple multi-hop MIMO relaying protocol using the TAS/SC technique for PB-UCR WSNs. The proposed protocol can obtain energy efficiency and spectrum usage efficiency, enhance the reliability of data transmission, and improve the secrecy performance.
In almost published works related to EH and UCR (see [23,24,25]), the transmitters adjust their transmit power following the instantaneous channel state information. As a result, the transmit power is a random variable (RV), which is not feasible. In this paper, the secondary source and relay nodes are assumed to transmit the source data at fixed transmit power levels. In addition, we derive an exact closed-form expression of the average transmit power of the secondary transmitters under the joint impacts of the energy harvested, the interference constraint, and the maximum transmit power level.
We investigate the impact of hardware impairments on the end-to-end SOP and PNSC of the proposed scheme. Indeed, the obtained results presented that the hardware imperfection has a significant impact on the secrecy performance. Moreover, the analytical results showed that different values of the hardware impairment levels of the data and eavesdropping links lead to different secrecy performance trend. Finally, it is worth noting that the proposed scheme is a generalized case of the existing schemes in which the transceiver hardware is assumed to be perfect [11,41,42,43].
We derive new exact and asymptotic expressions of the end-to-end SOP and PNSC over Rayleigh fading channels, which are then verified by Monte Carlo simulations.
The rest of this paper is organized as follows. The system model of the considered protocol is described in Section 2. In Section 3, the expressions of SOP are derived. The simulation results are shown in Section 4. Finally, this paper is concluded in Section 5.
2. System Model
Figure 1 illustrates the system model of the proposed scheme, in which a secondary source wants to transmit its data to a destination via intermediate nodes denoted by , …, . The data transmission between and is realized via K orthogonal time slots, exploiting the TAS/SC technique. In particular, at the -th hop, the node selects an antenna to transmit the source data to the node , which uses the SC technique to combine the signals received from , where . We assume that all of the nodes including the source, the destination and the relays are equipped with antennas. The transmitter has to harvest energy from wireless signals of a single-antenna power beacon (PB) deployed in the secondary network. Moreover, must adjust the transmit power to satisfy a maximal interference threshold () required by a single-antenna primary user (PU). Also in the secondary network, there exists an -antenna eavesdropper (E) who uses the SC technique to decode the source data obtained at each hop. Similar to [16], the secondary transmitters randomly generate code-book to confuse the eavesdropper.
Figure 1.
System model of the proposed scheme.
Comment 1: Due to the size limitation and complexity constraint, it is assumed that all of the receivers can only use the SC combiner for decoding the data. In addition, the secrecy performance of the proposed protocol is same with that of the corresponding one with multiple non-colluding single-antenna eavesdroppers [44,45]. Finally, in the case where the eavesdropper can employ the MRC technique, the expressions derived in this paper can be used as bound expressions of the secrecy performance.
Let us denote as the channel gain of the link, where . Assume that all of the channels are Rayleigh fading; hence the channel gain is an exponential RV. The cumulative distribution function (CDF) and probability density function (PDF) of can be expressed, respectively, as
| (1) |
where is parameter of the exponential RV , i.e., , where is expected operator and is variance of X. To take path-loss into account, we can model as [46], where is the distance between X and Y, and is the path-loss exponent.
We denote as the channel gain between the m-th antenna of and Y, where . Assume that RVs are independent and identical, i.e., for all m. Also, let and as channel gain between X and the n-th antenna of , and that between X and the p-th antenna of E, respectively, where and . Similarly, and are independent and identically distributed (i.i.d.) RVs, i.e., and for all n and p.
Let denote the total transmission time between and , and hence the time allocated for each time slot is given as . Considering the -th hop; a duration of is used for to harvest energy, and the remaining duration, i.e., , is spent for the data transmission between and , where . Then, the amount of energy that can harvest is given by
| (2) |
where is energy conversion efficiency, and is transmit power of PB.
From (2), we can formulate the transmit power that can use in the data transmission phase by
| (3) |
where and . Using (Equation (A.7) [25]), we can write the CDF of as
| (4) |
Considering the data transmission between the transmitter A and the receiver B; under the impact of the hardware impairments, the instantaneous SNR received at B can be expressed as in [30,33,34,47,48]:
| (5) |
where , is transmit power of the transmitter A, is channel gain between A and B, is the variance of additive white Gaussian noise (AWGN), and are constants characterizing the level of the hardware impairments at A and B, respectively, and is the total hardware impairment level. The values of , , , which depend on the structure of the transceiver hardware at A and B, can be determined by practical experiments.
Moreover, in the URC network, if uses the m-th antenna to transmit the data, the transmit power must satisfy the interference constraint required by PU as in [25,49]:
| (6) |
where is total hardware impairment level at and PU (see [25,49]).
Let denote the maximum transmit power of each antenna; by combining (3) and (6), the transmit power of the m-th antenna at can be formulated by
| (7) |
where
We can observe from (7) that when , then is a RV, which is not feasible (although this assumption was widely used in many published literature, e.g., [23,24,25] and references therein). In practice, the transmit power should be fixed at pre-determined levels. Indeed, assume that there are fixed levels denoted by with . For example, is the lowest level, and is the highest one. Now, by combining with (7), we can write the expression of as
| (8) |
Now, we consider the data transmission between and . Employing the TAS/SC technique, the transmit antenna at and the receive antenna at are selected by the following strategy (see [9]):
| (9) |
where b and c are the selected antennas at and , respectively, and . Since are i.i.d. RVs, CDF of can be obtained by
| (10) |
With the presence of hardware impairments, the channel capacity of the link is calculated as
| (11) |
where is the total hardware impairment level at and , which is assumed to be the same for all values of k.
Let us consider the eavesdropping link at the -th hop; the channel capacity of the link can be obtained by
| (12) |
where is the total hardware impairment level at and E. In addition, since E uses the SC combiner, the channel gain can be written as
| (13) |
where . In addition, CDF of can be expressed by
| (14) |
From (14), we obtain PDF of as
| (15) |
Next, from (11) and (12), the secrecy capacity at the -th hop is obtained by
| (16) |
With the random-and-forward strategy, the end-to-end secrecy capacity of the proposed protocol is given as in [37]:
| (17) |
3. Performance Analysis
In this section, we analyze the average transmit power of the secondary transmitters and the secrecy performance of the proposed protocol in terms of SOP and PNSC.
3.1. Average Transmit Power of the Secondary Transmitters
From (8), the average transmit power of can be given by the following formula:
| (18) |
where is an expectation operator. To calculate , we attempt to find CDF of . Setting , the CDF of is obtained by
| (19) |
Substituting and (4) into (19) yields
| (20) |
Therefore, the average transmit power of is written by
| (21) |
3.2. Secrecy Outage Probability (SOP)
The end-to-end SOP of the proposed protocol can be calculated by
| (22) |
where is a predetermined outage threshold, and is the secrecy outage probability at the k-th hop. Using (8) and (16), we can formulate by
| (23) |
where .
It is noted from (23) that the secrecy outage event is only considered in the cases where the transmit power is higher than zero, i.e., and .
For the probability in (23), it can be calculated by
| (24) |
Next, let us consider the SOP conditioned on as marked in (23); we have
| (25) |
where
| (26) |
We can observe from (25) that if (or ), always equals 1 for all values of k and v.
In the following, we derive the exact expressions of as given in Lemmas 1–3 below.
Lemma 1.
When and , the exact expression of SOP can be given as
(27)
Proof.
At first, when and , we can rewrite as
(28) By substituting the CDF of in (10), and the PDF of in (15) into (28), after some manipulations, we arrive at
(29) By changing variable , we have
(30) With , we can rewrite (30) as
(31) where
(32) We finish the proof of Lemma 1 here. We note that the integrals in (27) can be easily calculated by computer software such as Matlab or Mathematica. ☐
Comment 2: We can observe from (27) that the exact expression of is still in integral form, which does not provide any insights into the system performance. Therefore, our next objective is to find an asymptotic expression at high transmit SNR as given in Corollary 1 below.
Corollary 1.
When and , we can approximate at high transmit SNR by a closed-form expression as
(33)
Proof.
At high transmit SNR, we can approximate (25) in this case as follows:
(34)
Comment 3: Combining (22), (23), (27), and (33), we obtain exact and asymptotic formulas of the end-to-end SOP when and . Equation (33) implies that at high transmit SNR only depends on , and . Moreover, (and the end-to-end SOP) increases when increases.
Lemma 2.
When and , an exact expression of can be given as
(35)
Proof.
Similar to (28), in this case can be written by
(36) With the same manner as deriving in (28), we can obtain (35). ☐
Corollary 2.
At high transmit SNR, in (35) can be approximated by
(37)
Proof.
Similar to the proof of Corollary 1, we have
(38)
Comment 4: Combining (22), (23), (35), and (37), we obtain exact and asymptotic expressions of the end-to-end SOP when and . Equation (37) also shows that at high transmit SNR, (and the end-to-end SOP) decreases as increases.
Lemma 3.
When and , is given by an exact closed-form expression as
(39)
Proof.
In this case, we have
(40) Substituting CDF of in (10), and PDF of in (15) into (40), after some manipulations, we can obtain (39), and finish the proof. ☐
Corollary 3.
When and , can be approximated by
(41)
Proof.
In this case, we have the following approximation:
(42) ☐
Substituting CDF of , and PDF of into (42), after some manipulations, we can obtain (41).
Comment 5: Equation (41) shows that , as well as the end-to-end SOP at high transmit SNR, do not depend on . It is worth noting that this paper considers a generalized system model where the hardware impairment levels on the data links and eavesdropping links can be different or the same. Moreover, we can observe from Lemmas 1–3 that the secrecy outage probability of the proposed protocol is only expressed by an exact closed-form formula when .
3.3. Probability of Non-Zero Secrecy Capacity (PNSC)
In this subsection, we analyze the end-to-end PNSC of the proposed protocol, which can be formulated by
| (43) |
where is the probability of non-zero secrecy capacity at the k-th hop.
Lemma 4.
The exact expressions of can be given by
(44) where is calculated as in (24), and
(45)
Proof.
Similar to (23), we can formulate as
(46) Next, by substituting , into in (27), (35), and (39), we can obtain (45). ☐
Comment 6: Similar to [37], the end-to-end PNSC can be obtained with three different cases, i.e., , , and . Moreover, when , we obtain the exact closed-form expression of the end-to-end PNSC. Finally, with , the end-to-end PNSC value does not depend on the transmit SNR as well as the hardware impairment levels.
4. Simulation Results
In this section, we present Monte Carlo simulations to verify the theoretical results obtained in Section 3 by using MATLAB 2014a. For Monte Carlo experiments, we perform – independent trials, and in each trial, the Rayleigh channel coefficients for all of the links are generated to obtain the end-to-end secrecy performance. For the theoretical results, the expressions derived in Section 3 are used to present them.
In the simulation environment, a two-dimensional Oxy plane is considered, where the primary user (PU), the power beacon (PB), the secondary eavesdropper (E), and the secondary node () are located at , , , and , respectively, where . In all of the simulations, we fix the path-loss exponent by 3, the number of transmit power levels by 8, the variance of Gaussian noises by 1, and the block time () by 1. Moreover, we assume that , and the total hardware impairment level equals 0. It is noted from figures that simulation results (Sim) are presented by markers, while the theoretical results including exact ones (Exact) and asymptotic ones (Asym) are presented by solid and dash lines, respectively.
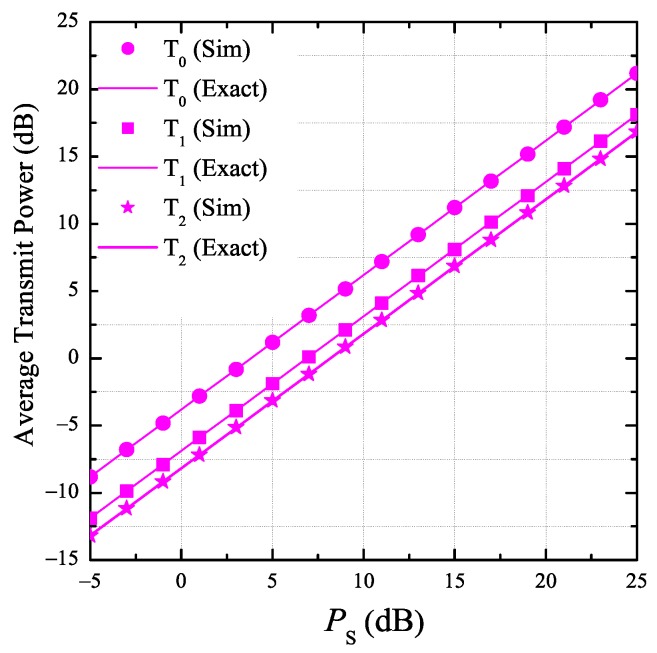
In Figure 2, we present the average transmit power of the secondary transmitters as a function of . In this simulation, the number of hops (K) is 3, the number of antennas at the node equals 3, the energy conversion efficiency by 0.25, and the fraction of time spent for the EH phase is 0.25. In addition, the co-ordinates of PB and PU are and , respectively. We can observe from Figure 2 that the average transmit power of the source () is highest because the Euclidean distance between and PU is farthest. We also see that the average transmit power of , , and linearly increases as increases. It is worth noting that the simulation results match very well with the theoretical ones, which validates our derivations.
Figure 2.
Average transmit power of the secondary transmitters as a function of when , , , , , , , and .
Figure 3 investigates the impact of the positions of PU and PB on the average transmit power of the secondary transmitters. Particularly, we change from 0.1 to 0.9, and is calculated by . Moreover, we fix the values of and by 0.3 and –0.5, respectively. It can be seen from Figure 3 that the average transmit power of , , and varies with different positions of PB and PU. For example, when , the positions of PB and PU are (0.1, 0.3) and (0.9, –0.5), respectively. In this case, the average transmit power of is lowest because this node is nearest to PU. For another example, , the distances between and PU, and between and PU are the same, and hence the average transmit power of and is almost the same. For the nodes and , we see that there exist positions of PB and PU at which their average transmit power is lowest. However, the average transmit power of always decreases as increases.
Figure 3.
Average transmit power of the secondary transmitters as a function of when dB, , , , , , , and .
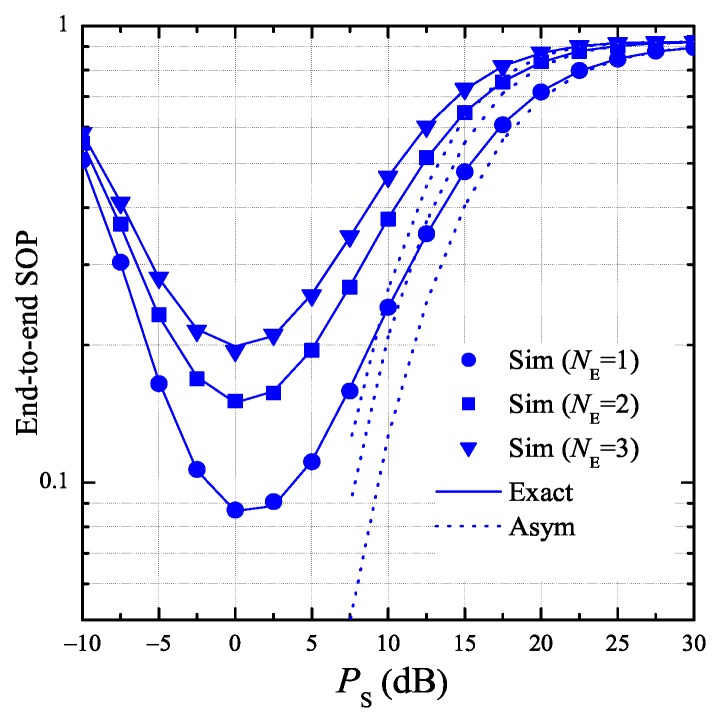
Figure 4 presents the end-to-end SOP as a function of with different number of antennas at E. In this simulation, the total hardware impairment levels of the data and eavesdropping links are given as and , respectively, and hence the conditions in Lemma 1 are satisfied, i.e., and . It can be seen from this figure that simulation results match very well with theoretical ones. Moreover, we see that the exact end-to-end SOP converges to the approximate one at high values, which verifies the derived expressions obtained in Lemma 1 and Corollary 1. As proved in Corollary 1, the end-to-end SOP at high regime increases with the increasing of . In addition, Figure 4 shows that there exists an optimal value of at which the SOP value is lowest. Finally, we can see that the secrecy performance of the proposed protocol is worse with higher number of antennas at E.
Figure 4.
End-to-end secrecy outage probability as a function of when , , , , , , , , , , , , and .
In Figure 5, we present the end-to-end SOP as a function of with various number of hops . In this figure, we assume that the transceiver hardware of the authorized nodes is better than that of the eavesdropper, i.e., and , which satisfy the conditions in Lemma 2, i.e., and . It is seen from Figure 5 that the end-to-end SOP rapidly decreases as increases. Moreover, the secrecy performance significantly enhances with higher number of hops. Finally, the simulation results again validate the theoretical results obtained from Lemma 2 and Corollary 2.
Figure 5.
End-to-end secrecy outage probability as a function of when , , , , , , , , , , , , and .
In Figure 6, we consider the cases where or . As proved in Lemma 3 and Corollary 3, we can see from Figure 6 that the exact end-to-end SOP rapidly converges to the asymptotic one which does not depend on . It is also seen that the hardware impairment levels and significantly impact on the secrecy performance. In this figure, the value of SOP is lowest when the transceiver hardware of the authorized nodes and the eavesdropper is perfect, i.e., .
Figure 6.
End-to-end secrecy outage probability as a function of when , , , , , , , , , , , and .
Figure 7 presents the SOP performance of the proposed protocol as a function of the fraction of time spent for the EH process . As illustrated in this figure, the end-to-end SOP increases with higher value of . Moreover, when is very small, the probability in (23) () converges to zero, and hence the end-to-end SOP also goes to zero. Next, similar to Figure 5, the secrecy performance significantly enhances when the hardware impairment level of the data links is lower than that of the eavesdropping links .
Figure 7.
End-to-end secrecy outage probability as a function of when dB, , , , , , , , , , , and .
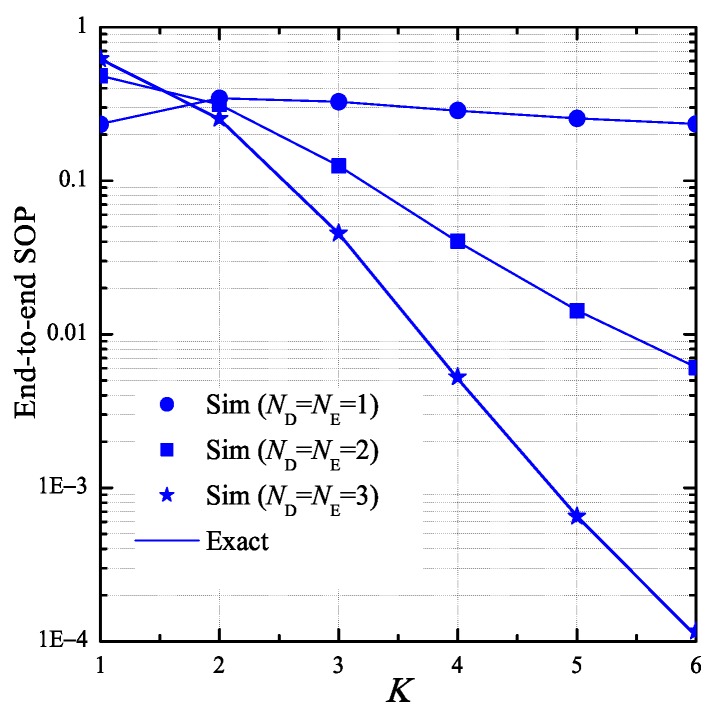
In Figure 8, we investigate the impact of the number of hops on the end-to-end SOP. In this simulation, we assume that the number of antennas at the and E nodes is same, i.e., , and the transceiver hardware of these nodes is perfect, i.e., . As we can see, the values of SOP almost decrease as increasing the number of hops. However, in the case that , the end-to-end SOP is highest when the number of hops equals 2. When , it is seen that the SOP performance in case that is best. Moreover, the value of SOP in this case rapidly decreases with the increasing of K.
Figure 8.
End-to-end secrecy outage probability as a function of K when dB, , , , , , , , , , , and .
In Figure 9, we present the end-to-end PNSC as a function of with various values of as is fixed by 0.05. As observed, the PNSC performance is better with the decreasing of . Moreover, as , the value of PNSC increases (decreases) with higher value of , and in the case that , this value does not depend on . It is worth noting that the simulation and theoretical results match very well with each other, which validates the formulas derived in Lemma 4.
Figure 9.
End-to-end probability of non-zero secrecy capacity as a function of when , , , , , , , , , , , and .
Figure 10 presents the end-to-end PNSC as a function of with different number of hops (K). As shown in this figure, the PNSC performance significantly decreases when the hardware impairment level of the data link increases. Moreover, at high values, the end-to-end PNSC is worse with high number of hops.
Figure 10.
End-to-end probability of non-zero secrecy capacity as a function of when , , , , , , , , , , , and .
5. Conclusions
This paper proposed and evaluated the secrecy performance of the TAS/SC-based multi-hop harvest-to-transmit cognitive WSNs under the joint impact of the interference constraint, the limited-energy source, and the hardware impairments. The main contribution of this paper is to derive new exact and asymptotic expressions of the end-to-end SOP and PNSC over Rayleigh fading channel, which can be used to design and optimize the performance of the considered networks, with any hardware impairment levels, as well as other system parameters, in the practical considerations. The interesting results obtained in this paper can be listed as follows:
The hardware impairments have a significant impact on the secrecy performance. Particularly, when the transceiver hardware of the authorized nodes is better than that of the eavesdropper, the proposed protocol obtains high secrecy performance. Otherwise, the SOP and PNSC performance is significantly degraded.
The secrecy performance of the proposed protocol can be enhanced with higher number of antennas equipped at the authorized nodes.
By optimally designing the number of hops and the fraction of time spent for the energy harvesting phase, the secrecy performance of the proposed protocol can be significantly improved.
Acknowledgments
This work was supported by the grant SGS reg. No. SP2019/41 conducted at VSB Technical University of Ostrava, Czech Republic, and partially was funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.317.
Author Contributions
The main contributions of P.T.T. (Phu Tran Tin) and P.M.N. were to create the main ideas and execute performance evaluation by extensive simulations, while T.T.D., P.T.T. (Phuong T. Tran) and M.V. worked as the advisers of P.T.T. (Phu Tran Tin) and P.M.N. to discuss, create, and advise the main ideas and performance evaluations together.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Ledwaba L.P.I., Hancke G.P., Venter H.S., Isaac S.J. Performance Costs of Software Cryptography in Securing New-Generation Internet of Energy Endpoint Devices. IEEE Access. 2018;6:9303–9323. doi: 10.1109/ACCESS.2018.2793301. [DOI] [Google Scholar]
- 2.Liu Z., Choo K.-K.R., Grossschadl J. Securing Edge Devices in the Post-Quantum Internet of Things Using Lattice-Based Cryptography. IEEE Commun. Mag. 2018;56:158–162. doi: 10.1109/MCOM.2018.1700330. [DOI] [Google Scholar]
- 3.Wyner A.D. The Wire-tap Channel. Bell Syst. Tech. J. 1975;54:1355–1387. doi: 10.1002/j.1538-7305.1975.tb02040.x. [DOI] [Google Scholar]
- 4.Csiszar I., Korner J. Broadcast Channels With Confidential Messages. IEEE Trans. Inf. Theory. 1978;24:339–348. doi: 10.1109/TIT.1978.1055892. [DOI] [Google Scholar]
- 5.Gopala P.K., Lai L., Gamal H.E. On the secrecy capacity of fading channels. IEEE Trans. Inf. Theory. 2008;54:4687–4698. doi: 10.1109/TIT.2008.928990. [DOI] [Google Scholar]
- 6.Li Z., Jing T., Ma L., Huo Y., Qian J. Worst-Case Cooperative Jamming for Secure Communications in CIoT Networks. Sensors. 2016;16:339. doi: 10.3390/s16030339. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Tang X., Cai Y., Yang W., Yang W., Chen D., Hu J. Secure Transmission of Cooperative Zero-Forcing Jamming for Two-User SWIPT Sensor Networks. Sensors. 2018;18:331. doi: 10.3390/s18020331. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Yang M., Zhang B., Huang Y., Yang N., Guo D., Gao B. Secure Multiuser Communications in Wireless Sensor Networks with TAS and Cooperative Jamming. Sensors. 2016;16:1908. doi: 10.3390/s16111908. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Yang N., Yeoh P.L., Elkashlan M., Schober R., Collings I.B. Transmit Antenna Selection for Security Enhancement in MIMO Wiretap Channels. IEEE Trans. Commun. 2013;61:144–154. doi: 10.1109/TCOMM.2012.12.110670. [DOI] [Google Scholar]
- 10.Xiong J., Tang Y., Ma D., Xiao P., Wong K.-K. Secrecy Performance Analysis for TAS-MRC System with Imperfect Feedback. IEEE Trans. Inf. Forensics Secur. 2015;10:1617–1629. doi: 10.1109/TIFS.2015.2421358. [DOI] [Google Scholar]
- 11.Krikidis I. Opportunistic Relay Selection For Cooperative Networks with Secrecy Constraints. IET Commun. 2010;4:1787–1791. doi: 10.1049/iet-com.2009.0634. [DOI] [Google Scholar]
- 12.Liu Y., Wang L., Tran T.D., Elkashlan M., Duong T.Q. Relay Selection for Security Enhancement in Cognitive Relay Networks. IEEE Wirel. Commun. Lett. 2015;4:46–49. doi: 10.1109/LWC.2014.2365808. [DOI] [Google Scholar]
- 13.Duy T.T., Duong T.Q., Thanh T.L., Bao V.N.Q. Secrecy Performance Analysis with Relay Selection Methods under Impact of Co-channel Interference. IET Commun. 2015;9:1427–1435. doi: 10.1049/iet-com.2014.1128. [DOI] [Google Scholar]
- 14.Zhong B., Zhang Z. Secure Full-Duplex Two-Way Relaying Networks With Optimal Relay Selection. IEEE Commun. Lett. 2017;21:1123–1126. doi: 10.1109/LCOMM.2017.2655050. [DOI] [Google Scholar]
- 15.Kuhestani A., Mohammadi A., Mohammadi M. Joint Relay Selection and Power Allocation in Large-Scale MIMO Systems With Untrusted Relays and Passive Eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2018;13:341–355. doi: 10.1109/TIFS.2017.2750102. [DOI] [Google Scholar]
- 16.Mo J., Tao M., Liu Y. Relay Placement for Physical Layer Security: A Secure Connection Perspective. IEEE Commun. Lett. 2012;16:878–881. [Google Scholar]
- 17.Hu L., Wen H., Wu B., Pan F., Liao R.-F., Song H., Tang J., Wang X. Cooperative Jamming for Physical Layer Security Enhancement in Internet of Things. IEEE Internet Things J. 2018;5:219–228. doi: 10.1109/JIOT.2017.2778185. [DOI] [Google Scholar]
- 18.Ma H., Cheng J., Wang X., Ma P. Robust MISO Beamforming with Cooperative Jamming for Secure Transmission From Perspectives of QoS and Secrecy Rate. IEEE Trans. Commun. 2018;66:767–780. doi: 10.1109/TCOMM.2017.2765637. [DOI] [Google Scholar]
- 19.Zhang G., Xu J., Wu Q., Cui M., Li X., Lin F. Wireless Powered Cooperative Jamming for Secure OFDM System. IEEE Trans. Veh. Technol. 2018;67:1331–1346. doi: 10.1109/TVT.2017.2756877. [DOI] [Google Scholar]
- 20.Zhou X., Zhang R., Ho C.-K. Wireless information and power transfer: Architecture design and rate-energy tradeoff. IEEE Trans. Commun. 2013;61:4754–4767. doi: 10.1109/TCOMM.2013.13.120855. [DOI] [Google Scholar]
- 21.Nasir A.A., Zhou X., Durrani S., Kennedy R.A. Relaying protocols for wireless energy harvesting and information processing. IEEE Trans. Wirel. Commun. 2013;12:3622–3636. doi: 10.1109/TWC.2013.062413.122042. [DOI] [Google Scholar]
- 22.Atapattu S., Evans J. Optimal Energy Harvesting Protocols for Wireless Relay Networks. IEEE Trans. Wirel. Commun. 2016;15:5789–5803. doi: 10.1109/TWC.2016.2569097. [DOI] [Google Scholar]
- 23.Xu C., Zheng M., Liang W., Yu H., Liang Y.-C. Outage Performance of Underlay Multihop Cognitive Relay Networks with Energy Harvesting. IEEE Commun. Lett. 2016;20:1148–1151. doi: 10.1109/LCOMM.2016.2547985. [DOI] [Google Scholar]
- 24.Xu C., Zheng M., Liang W., Yu H., Liang Y.-C. End-to-end Throughput Maximization for Underlay Multi-hop Cognitive Radio Networks with RF Energy Harvesting. IEEE Trans. Wirel. Commun. 2017;16:3561–3572. doi: 10.1109/TWC.2017.2684125. [DOI] [Google Scholar]
- 25.Hieu T.D., Duy T.T., Dung L.T., Choi S.G. Performance Evaluation of Relay Selection Schemes in Beacon-Assisted Dual-hop Cognitive Radio Wireless Sensor Networks under Impact of Hardware Noises. Sensors. 2018;18:1843. doi: 10.3390/s18061843. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Sun A., Liang T., Li B. Secrecy Performance Analysis of Cognitive Sensor Radio Networks with an EH-Based Eavesdropper. Sensors. 2017;17:1026. doi: 10.3390/s17051026. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 27.Hieu T.D., Duy T.T., Kim B.-S. Performance Enhancement for Multi-hop Harvest-to-Transmit WSNs with Path-Selection Methods in Presence of Eavesdroppers and Hardware Noises. IEEE Sens. J. 2018;18:5173–5186. doi: 10.1109/JSEN.2018.2829145. [DOI] [Google Scholar]
- 28.Mokhtar M., Gomaa A., Al-Dhahir N. OFDM AF relaying under I/Q imbalance: Performance analysis and baseband compensation. IEEE Trans. Commun. 2013;61:1304–1313. doi: 10.1109/TCOMM.2013.020813.120576. [DOI] [Google Scholar]
- 29.Björnson E., Matthaiou M., Debbah M. A new look at dual-hop relaying: Performance limits with hardware impairments. IEEE Trans. Commun. 2013;61:4512–4525. doi: 10.1109/TCOMM.2013.100913.130282. [DOI] [Google Scholar]
- 30.Solanki S., Upadhyay P.K., da Costa D.B., Bithas P.S., Kanatas A.G., Dias U.S. Joint Impact of RF Hardware Impairments and Channel Estimation Errors in Spectrum Sharing Multiple-Relay Networks. IEEE Trans. Commun. 2018;66:3809–3824. doi: 10.1109/TCOMM.2018.2832623. [DOI] [Google Scholar]
- 31.Boulogeorgos A.A., Karas D.S., Karagiannidis G.K. How much does I/Q Imbalance affect secrecy capacity? IEEE Commun. Lett. 2016;20:1305–1308. doi: 10.1109/LCOMM.2016.2558561. [DOI] [Google Scholar]
- 32.Zhu J., Ng D.W.K., Wang N., Schober R., Bhargava V.K. Analysis and Design of Secure Massive MIMO Systems in the Presence of Hardware Impairments. IEEE Trans. Wirel. Commun. 2017;16:2001–2016. doi: 10.1109/TWC.2017.2659724. [DOI] [Google Scholar]
- 33.Lee J.-H. Full-Duplex Relay for Enhancing Physical Layer Security in Multi-Hop Relaying Systems. IEEE Commun. Lett. 2015;19:525–528. doi: 10.1109/LCOMM.2015.2401551. [DOI] [Google Scholar]
- 34.Lee J.-H., Sohn I., Kim Y.-H. Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors. 2016;16:1726. doi: 10.3390/s16101726. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 35.Tian F., Chen X., Liu S., Yuan X., Li D., Zhang X., Yang Z. Secrecy Rate Optimization in Wireless Multi-Hop Full Duplex Networks. IEEE Access. 2018;6:5695–5704. doi: 10.1109/ACCESS.2018.2794739. [DOI] [Google Scholar]
- 36.Alotaibi E.R., Hamdi K.A. Secure Relaying in Multihop Communication Systems. IEEE Commun. Lett. 2016;20:1120–1123. doi: 10.1109/LCOMM.2016.2550025. [DOI] [Google Scholar]
- 37.Tin P.T., Hung D.T., Duy T.T., Voznak M. Analysis of Probability of Non-zero Secrecy Capacity for Multi-hop Networks in Presence of Hardware Impairments over Nakagami-m Fading Channels. Radio Eng. 2016;25:774–782. [Google Scholar]
- 38.Yao J., Liu Y. Secrecy Rate Maximization with Outage Constraint in Multihop Relaying Networks. IEEE Commun. Lett. 2018;22:304–307. doi: 10.1109/LCOMM.2017.2768513. [DOI] [Google Scholar]
- 39.Qi X., Huang K., Zhong Z., Kang X., Zhong Z. Physical layer security of multi-hop aided downlink MIMO heterogeneous cellular networks. Chin. Commun. 2016;13:120–130. doi: 10.1109/CC.2016.7833466. [DOI] [Google Scholar]
- 40.Lee J.-H. Confidential Multicasting Assisted by Multi-Hop Multi-Antenna DF Relays in the Presence of Multiple Eavesdroppers. IEEE Trans. Commun. 2016;64:4295–4304. doi: 10.1109/TCOMM.2016.2600676. [DOI] [Google Scholar]
- 41.Dong L., Han Z., Petropulu A.P., Poor H.V. Improving wireless physical layer security via cooperating relays. IEEE Trans. Signal Process. 2010;58:1875–1888. doi: 10.1109/TSP.2009.2038412. [DOI] [Google Scholar]
- 42.Bao V.N.Q., Trung N.L., Debbah M. Relay selection scheme for dual-hop networks under security constraints with multiple eavesdroppers. IEEE Trans. Wirel. Commun. 2013;12:6076–6085. doi: 10.1109/TWC.2013.110813.121671. [DOI] [Google Scholar]
- 43.Vo V.N., Tran D.-D., Chakchai S.-I., Tran H. Secrecy Performance Analysis for Fixed-Gain Energy Harvesting in an Internet of Things with Untrusted Relays. IEEE Access. 2018;6:48247–48258. [Google Scholar]
- 44.Huang Y., Zhang P., Wu Q., Wang J. Secrecy Performance of Wireless Powered Communication Networks with Multiple Eavesdroppers and Outdated CSI. IEEE Access. 2018;6:33774–33788. doi: 10.1109/ACCESS.2018.2835832. [DOI] [Google Scholar]
- 45.Lee K., Choi H.-H. Secure Analog Network Coding with Wireless Energy Harvesting under Multiple Eavesdroppers. IEEE Access. 2018;6:76289–76301. doi: 10.1109/ACCESS.2018.2884010. [DOI] [Google Scholar]
- 46.Laneman J.N., Tse D.N., Wornell G.W. Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Trans. Inf. Theory. 2004;50:3062–3080. doi: 10.1109/TIT.2004.838089. [DOI] [Google Scholar]
- 47.Matthaiou M., Papadogiannis A. Two-way relaying under the presence of relay transceiver hardware impairments. IEEE Commun. Lett. 2013;17:1136–1139. doi: 10.1109/LCOMM.2013.042313.130191. [DOI] [Google Scholar]
- 48.Duy T.T., Duong Q.T., da Costa D.B., Bao V.N.Q., Elkashlan M. Proactive Relay Selection with Joint Impact of Hardware Impairment and Co-channel Interference. IEEE Trans. Commun. 2015;63:1594–1606. doi: 10.1109/TCOMM.2015.2396517. [DOI] [Google Scholar]
- 49.Sharma P.K., Upadhyay P.K. Cognitive relaying with transceiver hardware impairments under interference constraints. IEEE Commun. Lett. 2016;20:820–823. doi: 10.1109/LCOMM.2016.2533500. [DOI] [Google Scholar]