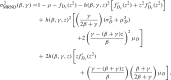Abstract
A Markovian Susceptible Infectious Recovered (SIR) model is considered for the spread of an epidemic on a configuration model network, in which susceptible individuals may take preventive measures by dropping edges to infectious neighbours. An effective degree formulation of the model is used in conjunction with the theory of density dependent population processes to obtain a law of large numbers and a functional central limit theorem for the epidemic as the population size , assuming that the degrees of individuals are bounded. A central limit theorem is conjectured for the final size of the epidemic. The results are obtained for both the Molloy–Reed (in which the degrees of individuals are deterministic) and Newman–Strogatz–Watts (in which the degrees of individuals are independent and identically distributed) versions of the configuration model. The two versions yield the same limiting deterministic model but the asymptotic variances in the central limit theorems are greater in the Newman–Strogatz–Watts version. The basic reproduction number and the process of susceptible individuals in the limiting deterministic model, for the model with dropping of edges, are the same as for a corresponding SIR model without dropping of edges but an increased recovery rate, though, when , the probability of a major outbreak is greater in the model with dropping of edges. The results are specialised to the model without dropping of edges to yield conjectured central limit theorems for the final size of Markovian SIR epidemics on configuration-model networks, and for the size of the giant components of those networks. The theory is illustrated by numerical studies, which demonstrate that the asymptotic approximations are good, even for moderate N.
Keywords: SIR epidemic, Configuration model, Social distancing, Density dependent population process, Effective degree, Final size
Introduction
In understanding the transmission dynamics in a population, one of the most important modelling components is the contact process. In this work we consider a form of self-initiated social distancing in response to an epidemic while at the same time taking into account the underlying contact network structure of the population. The resulting network is sometimes referred to as an adaptive network, e.g. Gross et al. (2006), Shaw and Schwartz (2008), Zanette and Risau-Gusmán (2008) and Tunc and Shaw (2014). Behavioural dynamics in infectious disease models can come in many different forms. Much of the literature that combines behavioural changes with network models uses agent-based simulations, as in the works cited above, although analytical advances have also been made (e.g. Britton et al. (2016) and Jacobsen et al. (2018)). Our work takes the model introduced in Britton et al. (2016) as its starting point. Britton et al. (2016) consider a broader class of models but restrict the analysis to the initial phase of the epidemic. In the current paper we analyse the time evolution and the final size of the epidemic. We model an SIR (Susceptible Infectious Recovered) infection on a configuration network that is static in the absence of infection. A susceptible individual breaks off its connection to an infectious neighbour upon learning of that neighbour’s infectious status. This occurs at a constant rate, independently per neighbour. One can think of this mechanism as being governed by infectious individuals informing their neighbours. Whereas infectious and recovered neighbours do not take any action upon being informed, susceptible neighbours want to avoid becoming infected and therefore cease contact with the infectious individual. We use the term ‘preventive dropping of edges’ to indicate this type of behaviour. Details of the model formulation are presented in Sect. 2.
To some extent, from the point of view of a susceptible neighbour of an infectious individual, it does not matter whether the infectious individual recovers or informs and dissolves the connection. Either way, it means that the susceptible neighbour can no longer acquire infection from this individual. In Sect. 5 we see that this is true when dealing with the asymptotic mean (deterministic) process, in that the number of susceptibles in the deterministic process for the model with dropping of edges coincides with that for the model without dropping of edges but with an increased recovery rate. In Sect. 8 we also see that this is not true for the stochastic process, in particular, the probability of a major outbreak differs (Theorem 8.1). Indeed, we cannot expect the two stochastic processes to coincide since informing neighbours happens independently of one another, while recovery affects all neighbours simultaneously.
In Sect. 3 we analyse the preventive dropping model throughout the epidemic outbreak, by using a so-called effective degree construction (cf. Ball and Neal 2008). Using such a construction, conditional on a major outbreak, by using techniques from Ethier and Kurtz (1986), we show under the assumption of bounded degrees that, as the population size N tends to infinity, the fractions of the population that are susceptible, infective and recovered satisfy a law of large numbers (LLN) over any finite time interval (more specifically that they converge almost surely to a limiting deterministic process), together with an associated functional central limit theorem (CLT) which describes fluctuations of the stochastic epidemic process about the limiting deterministic epidemic.
The population consists of N individuals that make up a network, which is formed using the configuaration model. The configuration model was introduced by Bollobás (1980), see Bollobás (2001) for further references, and comes in two versions: either (i) the degrees of individuals are prescribed deterministically, the Molloy–Reed (MR) random graph (Molloy and Reed 1995), or (ii) the degrees of individuals are assumed to be independent and identically distributed, the Newman–Strogatz–Watts (NSW) random graph (Newman et al. 2001). We treat both the MR and the NSW versions. If the limiting distribution of the degrees in the MR construction agrees with the degree distribution of the NSW random graph, the two versions give the same LLN, as we show in Theorem 3.1. However, the two versions differ regarding the variance in the CLTs, since (for finite N) there is greater variability in the degrees of the individuals in the NSW model than in the MR model. The functional CLT for the epidemic on an MR random graph is given in Theorem 3.2. By making a random time transformation, in Sect. 4, we conjecture a CLT for the final outcome of the epidemic on an MR random graph; see Conjecture 4.1. Corresponding results for the epidemic on an NSW random graph are discussed in Sect. 7; see Theorem 7.2 and Conjecture 7.1. To prove the latter results we require a version of the functional CLT in Ethier and Kurtz (1986) which allows for asymptotically random initial conditions; see Theorem 7.1.
The asymptotic variance–covariance matrix in the CLT in Proposition 4.1 is far from explicit. In order to obtain a nearly-explicit expression for the limiting variance of the final size, it is necessary to solve (partially) a time-transformed limiting deterministic process, which is more amenable to analysis than the corresponding deterministic process in real time. This is done in Sect. 5.1 and linked to the solution of the real-time process in Sect. 5.1.2. These results are used in Sects. 6 and 7 to obtain almost fully explicit expressions for the asymptotic variance of the final size of epidemics on MR and NSW random graphs, respectively, see Proposition 6.1 and Conjecture 7.1. In Sect. 5.2, we connect our analysis of the deterministic effective degree model to results derived using other deterministic approaches (cf. Volz (2008), Leung and Diekmann (2016) for related models), leading to a simple proof that the process of susceptible individuals in the limiting deterministic model for the epidemic with preventive dropping of edges is identical to that in the corresponding deterministic model without dropping of edges but with an increased recovery rate (see Remark 5.3).
Note that in the absence of behaviour change, we are in the setting of a Markov SIR epidemic on a configuration model network, which we consider in Sect. 9. This model has been analysed in several papers, e.g. Newman (2002), Kenah and Robins (2007), Lindquist et al. (2011) and Miller (2011). Our results further improve understanding of this well-studied model, particularly in terms of the asymptotic variance of the final size in Conjecture 9.1. Moreover, our work yields conjectured CLTs for the size of the giant component in MR and NSW configuration model random graphs; see Conjecture 9.2.
In Sect. 10, we illustrate our results with some numerical studies. In particular, we demonstrate that the asymptotic results generally give a good approximation for moderate population sizes, investigate the impact of the dropping of edges on properties of epidemics and do some comparison of the behaviour of the epidemic on MR and NSW type random graphs. Some brief concluding comments are given in Sect. 11.
Finally, we would like to make a note on the structure of the paper. Clearly, this paper does not readily lend itself to a quick superficial read, owing to its length and some of the technicalities and details involved in obtaining our results. However, we have tried to help the reader by formulating our main results in terms of propositions, theorems and well-motivated conjectures. The more technical aspects can be found in the appendices for the interested reader, which consequently constitute a significant part of the paper.
The stochastic SIR network epidemic model with preventive dropping
In this section we define the stochastic SIR network epidemic model with preventive dropping. This model is a special case of the network epidemic model with preventive rewiring defined in Britton et al. (2016), namely where there is no latent period and where the fraction of dropped edges that are replaced by new edges is set to zero.
The population consists of N individuals, labelled , that make up a network. The network is formed using the configuration model, which, as described in Sect. 1, comes in two versions, namely MR and NSW random graphs. Let D be a random variable which describes the degree of a typical individual and . Let and denote the mean and variance of D, respectively, both of which are assumed to be finite.
-
(i)
In the MR model, the degrees are prescribed. More specifically, for , let denote the degrees of the individuals when the population size is N. Note that these are deterministic. Let be the empirical distribution of , where the Kronecker delta is 1 if and 0 otherwise. It is assumed that .
-
(ii)
In the NSW model, the degrees of the N individuals are independent and identically distributed copies of D. A sequence of networks, indexed by N, may be constructed from a sequence of independent and identically distributed copies of D by using the first N random variables for the network on N individuals.
In both models the network is formed by attaching a number of stubs (i.e. half-edges) to each individual, according to its degree (so, for example, in the NSW model, stubs are attached to individual i, for ), and then pairing up these stubs uniformly at random to form the network. If is odd, there is a left-over stub, which is ignored. The network may have some ‘defects’, specifically self-loops and multiple edges between pairs of individuals, but provided , which we assume, such defects become sparse in the network as ; see Durrett (2007), Theorem 3.1.2.
A Markovian SIR epidemic is defined on the network of N individuals as follows. Each individual is at any point in time either susceptible, infective or recovered (and immune to further infection). An infective individual infects each of its susceptible neighbours at the points of independent Poisson processes, each having rate . An infectious individual recovers and becomes immune at rate (implying that the duration of the infectious period follows an exponential distribution having mean ). Finally, susceptible individuals that have infectious neighbours drop such connections, independently, at rate (an equivalent description to be used later is that the infective ‘warns’ its neighbours independently at rate , and warned susceptible individuals drop the corresponding edge). All infectious periods, infecting processes and edge-dropping processes are mutually independent. The epidemic is initiated at time by one or more individuals being infectious and all other individuals being susceptible. More precise initial conditions are given when they are required. The epidemic continues until there is no infectious individual. Then the epidemic stops and the result is that some of the individuals have been infected (and later recovered) and the rest of the population remains susceptible and hence have not been infected during the outbreak.
The parameters of the model are the degree distribution , including its mean and variance , the infection rate , the recovery rate and the dropping rate .
It was shown in Britton et al. (2016) that the basic reproduction number for the model is given by
| 2.1 |
see also Sect. 8. Note that the first factor in (2.1) is the probability that an infective infects a given susceptible neighbour before either the infective recovers or the neighbour drops its edge to that infective. The second factor is the expected number of susceptible neighbours for infected individuals during the early stages of an outbreak initiated by few infectives. Owing to the way the network is constructed, the degree of a typical neighbour of a typical individual has the size-biased distribution , , and hence mean . In the early stages of an outbreak, a typical infective has all susceptible neighbours except for one, namely its infector.
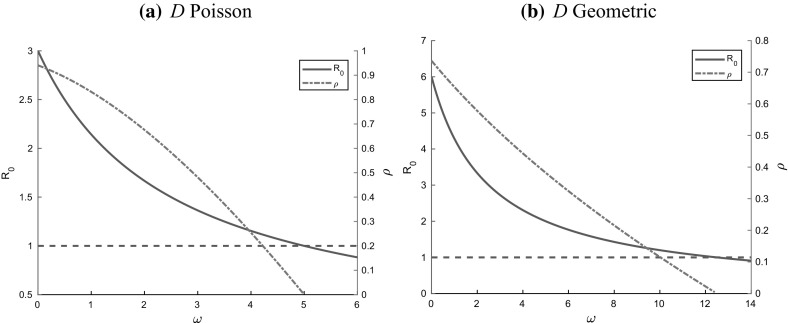
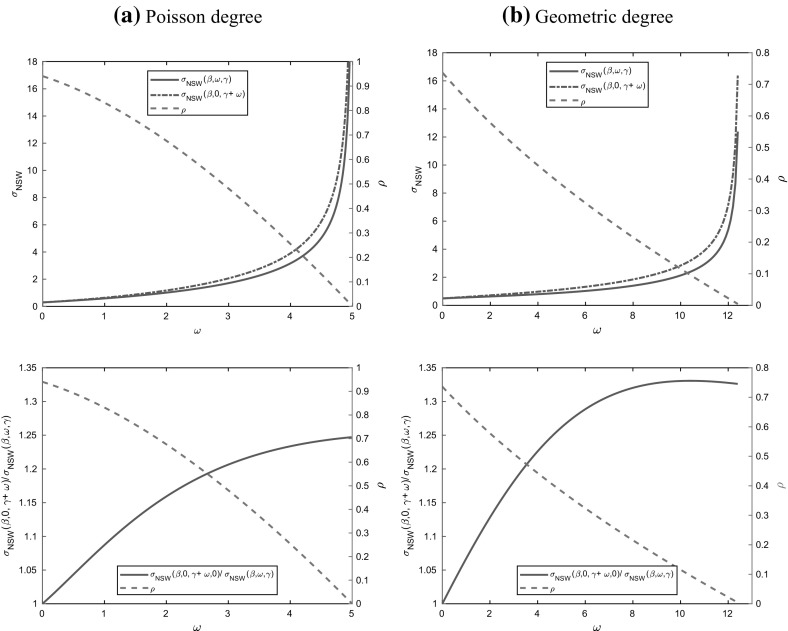
Note that for the dropping model is the same as for a Markovian SIR epidemic on a configuration model network without dropping of edges but with an increased recovery rate ; see also Remark 5.3 and Sect. 8, where we discuss this modified model with increased recovery rate and its relation to the dropping model. Furthermore, from (2.1) we find that is a monotonically decreasing function of , i.e. dropping edges always decreases the epidemic threshold parameter ; see also Fig. 5 in Sect. 10.4. For epidemics initiated by few infectives, this paper is concerned mainly with the case where , since only then is there a possibility for a major outbreak to take place.
Fig. 5.
Plots of and showing the impact of increasing the dropping rate from zero. Other parameters are , , and a, b
Effective degree formulation
In this section we analyse the stochastic SIR network epidemic model with preventive dropping that is described in Sect. 2. We do so by extending the ‘effective degree’ construction of an SIR epidemic on a configuration model network, introduced in Ball and Neal (2008), to incorporate dropping of edges. This allows us to prove a LLN and a functional CLT for the epidemic process (Theorems 3.1 and 3.2). Our proofs rely on the results of Ethier and Kurtz (1986) (see also Kurtz (1970, 1971)), and we adopt mostly the notation used in their work for ease of reference.
In the effective degree formulation the network is constructed as the epidemic progresses. The process starts with some individuals infective and the remaining individuals susceptible, but with none of the stubs paired up. For , the effective degree of individual i is initially in the MR graph and in the NSW graph. Infected individuals behave in the following fashion. An infective, i say, transmits infection down its unpaired stubs at points of independent Poisson processes, each having rate . When i transmits infection down a stub, that stub is paired with a stub (attached to individual j, say) chosen uniformly at random from all other unpaired stubs to form an edge. If then the effective degrees of both i and j are reduced by 1, otherwise the effective degree of i is reduced by 2. If individual j is susceptible then it becomes infective. If individual j is infective or recovered then nothing happens, apart from the edge being formed. The infective i also independently sends warning messages down its unpaired stubs at points of independent Poisson processes, each having rate . When i sends a warning message down a stub, that stub is paired with a stub (attached to individual j, say) chosen uniformly at random from all other unpaired stubs. If individual j is susceptible then the stub from individual i and the stub from individual j are deleted, corresponding to dropping of an edge in the original model. If individual j is infective or recovered then the two stubs are paired to form an edge. In all three cases, the effective degrees of i and j are reduced as above. Individual i recovers independently at rate , keeping all, if any, of its unpaired stubs. Note that in the formulation in Ball and Neal (2008), when an infective recovers, its unpaired stubs, if any, are paired immediately; however, that is not necessary and indeed complicates analysis of the model.
Note also that we now use the equivalent formulation of the process for dropping edges of Sect. 2, where dropping is driven by infectives rather than by susceptibles, although it is clear that the two formulations are probabilistically equivalent. The change is required for the effective degree formulation to model dropping of edges correctly.
Before proceeding we introduce some notation. For and , let and be respectively the numbers of susceptibles and infectives having effective degree i at time t. We refer to such individuals as type-i susceptibles and type-i infectives. For , let be the number of unpaired stubs attached to recovered individuals at time t. (Note that it is not necessary to keep track of the effective degrees of recovered individuals since only the total number of unpaired stubs attached to recovered individuals, and not the effective degrees of the individuals involved, is required in the above effective degree formulation.) Let , and . (Unless stated to the contrary, vectors are row vectors in this paper.) Let denote the state space of . Define unit vectors and on H, where, for example, has a one in the ith ‘susceptible component’ and zeros elsewhere, and has a one in the ‘recovered component’ and zeros elsewhere. Let denote a typical element of H, and let and . Thus and are the total number of stubs attached to susceptibles, infectives and recovered individuals, respectively, when .
The process is a continuous-time Markov chain with the following transition intensities, where an intensity is zero if , since then there is only one stub remaining.
For ,
-
(i)type-i infective infects a type-j susceptible
-
(ii)type-i infective ‘infects’ a type-j infective, so an edge is formed
-
(iii)type-i infective warns a type-j susceptible, so an edge is dropped
-
(iv)type-i infective ‘warns’ a type-j infective, so an edge is formed
For ,
-
(v)type-i infective ‘infects’ a recovered individual, so an edge is formed
-
(vi)type-i infective ‘warns’ a recovered individual, so an edge is formed
For ,
-
(vii)type-i infective recovers
Remark 3.1
(Comments on the intensities) Note that although the above intensities are all independent of N, we index them by N since that is required so that is a density dependent population process, see (3.6) and (3.7) below. Note also that the intensities in (ii) and (iv) above need to be modified slightly if to include the possibility that an infective ‘infects’ or ‘warns’ itself. For example, the intensity for a type-i infective ‘infecting’ itself is given by , so this should be subtracted from the intensity in (ii) when and included instead in a new transition, (ii’) say. It is easily verified that that as , so the modifications may be absorbed into the O(1 / N) term in (3.6) below and ignoring such transitions does not affect the LLNs and CLTs in the paper.
We now introduce notation for the jumps of . Note that the transitions in (ii) and (iv) above are identical, as are the transitions in (v) and (vi), so there are five types of jumps. For , let
| 3.1 |
| 3.2 |
| 3.3 |
for , let
| 3.4 |
and, for , let
| 3.5 |
Then, excluding self-infection and self-warning (see Remark 3.1), the set of possible jumps of from a typical state is , where
Let and , and . Further, let , and . For , let . For any , the intensities of the jumps of admit the form
| 3.6 |
with the functions given by
| 3.7 |
Remark 3.2
(Applying the theory of Ethier and Kurtz) The theory of density dependent population processes in Ethier and Kurtz (1986), Chapter 11, is for a class of continuous-time Markov chains whose state space is a subset of for some . Thus to use this theory we need to assume that there is a maximum degree, i.e. that , where . Then, for any , provided the sample paths of remain within , is a density dependent population process; see Appendix B for details. We conjecture that our results continue to hold when the condition is relaxed, provided suitable conditions are imposed on (i) the distribution of D and (ii), for epidemics on MR random graphs, the convergence of the empirical distribution of prescribed degrees.
The key theorems in Ethier and Kurtz (1986), Chapter 11, have their origin in Kurtz (1970, 1971). However, the proofs in Ethier and Kurtz (1986) are different from those in the earlier papers and the LLN is stronger in that it concerns almost sure convergence rather than convergence in probability. In Ethier and Kurtz (1986), the processes corresponding to are defined on the same probability space by using a single set of independent unit-rate Poisson processes indexed by the possible jumps .
A LLN and a functional CLT for density dependent population processes having countable state space are proved in Barbour and Luczak (2012a, b). They do not apply immediately to as the jumps of are unbounded, though that can be overcome by replacing by , where is the number of recovered individuals having effective degree i at time t. We do not consider here sufficient conditions for the theorems in Barbour and Luczak (2012a, b) to be satisfied in the present setting, since is satisfied for real-life epidemics. We note that LLNs for the Markov SIR epidemic () on an MR random graph with unbounded degree are given in Decreusefond et al. (2012) and Janson et al. (2014), and a functional CLT for the Markov SI epidemic () on an MR random graph with unbounded degree is given in KhudaBukhsh et al. (2017). It seems likely that similar techniques used in the first two of those papers will apply to the present model. LLNs for the Markov SIR epidemic () on an MR random graph with bounded degree are given in Bohman and Picollelli (2012) and Barbour and Reinert (2013), the latter for epidemics started by a trace of infection. Indeed our model (assuming bounded degrees) fits into the framework of Barbour and Reinert (2013), Sect 3.2.
Following Ethier and Kurtz (1986), define the drift function by
Substituting from (3.7) yields (see Appendix A for details)
| 3.8 |
Consider a sequence of epidemics indexed by N, each having . Suppose that and as , where and denotes almost sure convergence. Note that for epidemics on NSW random graphs is random and, depending on how the initial infectives are chosen, may also be random. The above almost sure convergence is reasonable for such epidemics since in an NSW random graph, the fraction of vertices of any given degree satisfies the strong law of large numbers. For epidemics on MR random graphs it is often more natural for to be non-random, in which case and as . Let and . The following result holds for epidemics on both MR and NSW random graphs.
Theorem 3.1
(LLN for epidemic on network with dropping)
Suppose that and . Then, for any ,
where is given by the solution of the following system of ordinary differential equations (ODEs) with initial condition :
| 3.9 |
| 3.10 |
| 3.11 |
where
| 3.12 |
and .
Proof
See Appendix B.
Remark 3.3
(Solving the ODEs (3.9)–(3.11)) The solution of the system of ODEs (3.9)–(3.11) is considered in Sect. 5. Note that under the conditions of Theorem 3.1 the system of ODEs (3.9)–(3.11) is finite, so existence and uniqueness of a solution follow from standard results. We do not consider existence and uniqueness of solutions to ODEs (3.9)–(3.11) when the degrees are unbounded but acknowledge that further justification and some regularity conditions will be required. A similar comment applies to the time-transformed system of ODEs (4.3)–(4.5) in Sect. 4.
For the epidemic on an MR random graph, a functional CLT for the fluctuations of about its deterministic limit is also available using Ethier and Kurtz (1986), Theorem 11.2.3, as we formulate in Theorem 3.2. See Sect. 7 for discussion of a corresponding CLT for the epidemic on an NSW random graph.
Write as and let denote the matrix of first partial derivatives of . For , let be the solution of the matrix ODE
| 3.13 |
where I denotes the identity matrix of appropriate dimension. Let
where denotes transpose. Note that is the coefficient matrix of the time-inhomogeneous linear drift of the limiting Gaussian process in Theorem 3.2 below and enables a representation of in terms of an Itô integral with respect to a time-inhomogeneous Brownian motion; see (7.1) in Sect. 7.
Theorem 3.2
(Functional CLT for epidemic on MR graph with dropping)
Suppose that and, for ,
| 3.14 |
where is constant. Then
| 3.15 |
where denotes weak convergence and is a zero-mean Gaussian process with and covariance function given by
Proof
See Appendix B, where a complete definition of is given.
Remark 3.4
(Computing the asymptotic variance) Theorem 3.2 yields immediately that
| 3.16 |
It follows from (3.13) and (3.16) that satisfies the ODE
| 3.17 |
with initial condition . Thus, provided , can be computed by numerically solving the ODEs (3.9)–(3.11) and (3.17) simultaneously.
Final outcome of epidemic on MR random graph
We conjecture a CLT for the final outcome of the epidemic with preventive dropping on an MR random graph (see Conjecture 4.1). In order to do so, we consider a random time-transformation of the real-time process.
For , let and be respectively the numbers of susceptible and infectious stubs at time t. Let , so the final number of susceptibles of different types is given by . For , let , so . Recall the definition of following (3.8). For , we derive a CLT for ; see Proposition 4.1. Assuming that Proposition 4.1 holds also when leads immediately to a CLT (Conjecture 4.1) for , and hence for the total number of individuals that are ultimately infected by the epidemic, since the latter is given by . A key step in deriving these CLTs is to consider the following random time-scale transformation of ; cf. Ethier and Kurtz (1986), page 467, and Janson et al. (2014), Section 3, where similar transformations are used to derive a CLT for the final size of the so-called general stochastic epidemic and a LLN for the Markovian SIR epidemic on an MR random graph, respectively.
For , let
and let . For , let and
Then is also a density dependent population process, having the same set of jumps as , and intensity functions given by
| 4.1 |
Note that when is in state , the clock in runs at rate times faster than the clock in , so the intensities in (4.1) are obtained by multiplying the corresponding intensities in (3.7) by . The drift function associated with is (cf. (3.8))
| 4.2 |
Let be the solution of the following system of ODEs, with initial condition :
| 4.3 |
| 4.4 |
| 4.5 |
where and , with and . The solution of this system is considered in Sect. 5.1.1. Let . It is shown in Appendix C that , i.e. the duration of the limiting time-changed deterministic epidemic is finite, unless .
We consider the same sequence of epidemics as for Proposition 3.1 in Sect. 3. Again, using Ethier and Kurtz (1986), Theorem 11.2.1, as , converges almost surely over any finite time interval , with , to (see Appendix B for further details of this and of the functional CLT given at (4.6)). Suppose further that the initial conditions satisfy (3.14) and . Then it follows using Ethier and Kurtz (1986), Theorem 11.2.3, that, for any ,
| 4.6 |
where is a zero-mean Gaussian process with and variance given by
| 4.7 |
where
| 4.8 |
and, for , is the solution of the matrix ODE
| 4.9 |
For , let . Further, for , let
| 4.10 |
so both and are decreasing with , and . We show in Appendix C that ; it is clearly finite if . Let , so
For fixed , application of Ethier and Kurtz (1986), Theorem 11.4.2, yields
| 4.11 |
where denotes inner vector product and denotes convergence in distribution. This result requires that
| 4.12 |
which we show in Appendix C. Condition (4.12) ensures that is a proper crossing time. Note that
where
| 4.13 |
and denotes outer vector product.
The following proposition follows immediately from (4.11) on noting that and , where .
Proposition 4.1
(CLT for ‘final’ outcome of epidemic on MR graph with dropping) Suppose that and (3.14) is satisfied. Then
| 4.14 |
where
and denotes a multivariate normal distribution (of appropriate dimension) with mean vector and variance–covariance matrix .
Remark 4.1
(Extending Proposition 4.1to) We are primarily interested in the case when . The difficulty in extending Proposition 4.1 to include is that to apply Ethier and Kurtz (1986), Theorem 11.4.2, we need the weak convergence at (4.6) to hold for some . Thus we need to extend the process so that it is defined beyond time . Now for (see (5.11) in Sect. 5.1.1), so we need to extend the state space of so that can be negative. However, this cannot be done so that the conditions of the LLN and CLT theorems in Ethier and Kurtz (1986) are satisified. In particular, in any neighbourhood of , the intensity functions are not bounded and the drift function is not Lipschitz continuous.
In work done while this paper was under review, the first author has found a way of overcoming this problem; see Ball (2018) which is in the setting of an SIR epidemic (without dropping of edges) with an arbitrary but specified infectious period distribution on configuration model networks. The theorems proved in Ball (2018) provide further (very strong) support for Conjecture 4.1 below, which assumes that Proposition 4.1 extends in the obvious way to include , and for subsequent conjectures which are contingent on Conjecture 4.1. Note that the final outcome of the epidemic is given by and the corresponding determinsitic outcome is .
We use the term final outcome to refer to that of the effective degree formulation, in which the degrees of susceptibles can change owing to dropping of edges. This is sufficient to determine the final size of an epidemic. If the final numbers of susceptibles of various original degrees are required, the effective degree formulation can be extended to keep track of both the original and effective degrees of suceptibles.
Conjecture 4.1
(CLT for final outcome of epidemic on MR graph with dropping) Suppose that and (3.14) is satisfied. Then
| 4.15 |
where
with B given by (4.13) with .
Remark 4.2
(LLN for final outcome of SIR epidemic with preventive dropping) Conjecture 4.1 implies that as , where denotes convergence in probability, i.e. the final outcome of the epidemic on an MR random graph obeys a weak LLN. The same conjecture holds also for the epidemic on an NSW random graph, using the theory in Sect. 7. Note that and an expression for is given in Eq. (5.26) in Sect. 5.3.
Remark 4.3
(Explicit expression for asymptotic variance of final size) Note that , and hence , can be computed numerically as described for in Remark 3.4. However, as detailed in Sect. 6 for the case , it is possible to derive an almost fully explicit expression, as a function of , for the asymptotic variance of the ‘final’ number of susceptibles. Moreover, the expression is fully explicit when , i.e. when there is no dropping of edges, so the model reduces to a standard Markov SIR epidemic on an MR configuration model network.
Deterministic temporal behaviour and final size
In Sect. 5.1 we study the deterministic temporal behaviour of the effective degree model, described by the system of ODEs (3.9)–(3.11) given in Theorem 3.1, by considering first the corresponding time-transformed system (4.3)–(4.5). The resulting (partial) solution of this system is required to calculate the asymptotic variance of the final size in Sects. 6 and 7. Furthermore, the results of this section are used in Appendix C to prove that the conditions and (4.12), required for the application of Ethier and Kurtz (1986), Theorem 11.4.2, are satisfied. In Sect. 5.2, we connect the analysis of (4.3)–(4.5) to other approaches taken in the literature for the deterministic analysis of epidemics on configuration model networks. Finally, in Sect. 5.3, we give a characterization of the deterministic final size of the epidemic and consider the final size of epidemics initiated by a trace of infection in Proposition 5.1. We do not consider existence and uniqueness of solutions of the determinstic model when (see Remark 3.3) but indicate where further justification is required for a proof.
Temporal behaviour
Time-transformed process
Consider the system of ODEs given by (4.3)–(4.5), with initial condition , and . In this section we obtain explicit expressions for , , and other variables pertaining to the fraction of susceptible, infectious, and recovered individuals in the population in the time-transformed process, while in Sect. 5.1.2 we connect these to corresponding variables in the real-time process.
Observe that the evolution of is decoupled from the rest of the system. To solve (4.3), let denote a transient continuous-time Markov chain describing the evolution of a single susceptible individual, whose stubs are independently dropped at rate and independently infected at rate . For , let X(t) be the number of stubs attached to the individual at time t, if it is still susceptible, otherwise let . Let , for and . By deriving the forward equation for it is easily seen that, for , ).
It is straightforward to calculate , since stubs disappear (by dropping or infection) independently, the probability that a given initial stub has disappeared by time t is and, given that a stub has disappeared, the probability its disappearance was caused by dropping is . Thus,
| 5.1 |
whence, for ,
| 5.2 |
where
| 5.3 |
and denotes the ith derivative of . It then follows that
| 5.4 |
where
| 5.5 |
Differentiating (5.4) yields
| 5.6 |
Note that and, using a similar argument to the derivation of (5.4),
| 5.7 |
Multiplying (4.4) by i and summing over yields
| 5.8 |
(This requires justifying and further conditions if . A similar comment applies to equations contingent on (5.8), such as (5.11).) Adding (5.6), (5.8) and (4.5) gives
which, together with the initial condition , yields
| 5.9 |
Substituting (5.9) into (4.5) yields
whence
| 5.10 |
Thus
| 5.11 |
Remark 5.1
(Fractions of susceptible, infectious, and recovered individuals) Although the above results are useful for analysing the final outcome of the epidemic, of greater practical interest is the evolution of the fractions of the population that are susceptible, infective and recovered individuals, which in the time-transformed process are given by and , respectively. Summing (5.2) over and using a similar argument to the derivation of (5.4) yields
| 5.12 |
Turning to , summing (4.4) over and using (5.4) yields
| 5.13 |
Let and
Then (5.13) has solution
| 5.14 |
We do not have a closed-form expression for the integral in (5.14), though it is straightforward to calculate numerically using the ODE (5.13). Finally, note that .
Real-time process
Turning to the system of ODEs (3.9)–(3.11), which describe the limiting evolution of the epidemic as the population size , let
| 5.15 |
where is given by (3.12). Then and it follows that, for ,
| 5.16 |
connecting the original process to the time-transformed process. Hence, , so (5.11) and (5.9) imply that is determined by
| 5.17 |
together with . The ODE (5.17) does not seem to admit an explicit solution, although it is straightforward to solve numerically.
Connection to other approaches
In this section we consider other deterministic formulations of the preventive dropping model and make the connection to the effective degree approach (ODE system (3.9)–(3.11)). Our focus is on the deterministic variable that is defined as follows:
| 5.18 |
Here, is the probability that an individual escapes infection from a given neighbour, up to at least t units of time after the neighbour became infected. In the Markovian SIR case with dropping of edges, this probability equals
| 5.19 |
Indeed, there are three competing events: transmission, ending of the infectious period, and informing the susceptible neighbour, that occur at rates , , and , respectively. We see immediately from the renewal equation for , obtained by substituting (5.19) into (5.18), that one can also interpret dropping of edges as an increased recovery rate for the deterministic mean temporal behaviour since only appears as part of the sum (see Remark 5.3 in Sect. 5.3). This aspect of the mean temporal behaviour may not be immediately clear from the system (3.9)–(3.11).
The variable can be interpreted as the probability that along a randomly chosen edge between two individuals, i and j say, there is no transmission from j to i before time t, given that no transmission occurred from individual i to j. The variable formed the basis for the edge-based compartmental models of Volz, Miller and co-workers (see e.g. Kiss et al. (2017) and references therein). Closely related to edge-based compartmental models is the binding site formulation presented in Leung and Diekmann (2016), where the relation to edge-based compartmental models is also explained. We use the binding site formulation in this section to state the renewal equation for the variable , restricting ourselves to the Markovian SIR epidemic (in Leung and Diekmann (2016) is used instead of ). In principle, the renewal Eq. (5.18) is far more general and allows for randomness in infectiousness beyond the Markovian setting, see Leung and Diekmann (2016) for details. Note that in the above works, the derivation of the equations describing the evolution of is heuristic. Those equations are proved for the Markov SIR epidemic on a configuration model network, in the sense of a large population limit, in Decreusefond et al. (2012) and Janson et al. (2014); see also Barbour and Reinert (2013).
The variable relates to the effective degree formulation as follows:
| 5.20 |
where the functions and from the effective degree formulation are defined at (5.5) and (5.15), respectively. Indeed, Eq. (5.20) is expected from the interpretation of : is the probability that the susceptible individual is informed by the infection status of a given neighbour before being infected by that neighbour, so the stub disappears through dropping, while is the probability that there is no dropping and the given stub has not disappeared at time (where accounts for the time-transformation, see (5.16)). One can check that (5.20) holds true by first transforming the renewal Eq. (5.18) into an ODE for by differentiating (and using (5.19)):
| 5.21 |
with initial condition . Next, differentiating the right-hand-side of (5.20), and using (5.17), we find that satisfies the ODE (5.21). Furthermore, the initial condition implies that .
Finally, the Malthusian parameter r, the basic reproduction number and the final size of the epidemic are easily derived from the single renewal equation (5.18). Here we only state the expressions and refer to Leung and Diekmann (2016), Section 2.5, for details. In the limit of the Euler–Lotka characteristic equation is
| 5.22 |
The Malthusian parameter r is the unique real root of (5.22) and a simple calculation yields
| 5.23 |
agreeing with Britton et al. (2016), equation (3). The basic reproduction number is obtained from (5.22) by evaluating the right hand side at , yielding the same expression as (2.1). The final size is discussed in Remark 5.2.
Final size
Recall that defined at (4.10) satisfies . In particular, using (5.11), satisfies
| 5.24 |
For later use, we rewrite (5.24) as
| 5.25 |
where and . Further, using (5.12) yields that the final proportion of the population that remains uninfected is given by
| 5.26 |
We let denote the fraction of the population ultimately infected in the limiting deterministic epidemic.
Let . Then in the limit as , i.e. for epidemics started by a trace of infection (or, more precisely, a trace of infected stubs), the final susceptible fraction is given by (5.26), where satisfies
| 5.27 |
We can now formulate the characterization for the final size of the epidemic. We illustrate the dependence of on the dropping rate in Sect. 10.4.
Proposition 5.1
(Deterministic final size) Suppose that .
- Suppose that . Then the fraction of the population that is ultimately infected in the deterministic epidemic is given by
where s is the unique solution in [0, 1) of5.28 5.29 - Suppose . Then in the limit as , the fraction of the population that is ultimately infected in the limiting deterministic epidemic is given by
where s is the unique solution in [0, 1) of5.30 5.31
Proof
(a) Suppose that . Let , so . It then follows from (5.25) and (5.26) that s satisfies (5.29) and is given by (5.28). Let and . Then and , since . Thus (5.29) has a unique solution in [0, 1) as is convex on [0, 1], since .
(b) Letting in (5.28) and (5.29) shows that is given by (5.30), where s satisfies (5.31). Let be as in (a) and . Then and , since . Further, is a convex function, so it follows that (5.31) has a solution in [0, 1) if and only if and moreover that solution is unique. Now and , so if and only if .
Remark 5.2
(Connection to the renewal Eq. (5.18)) Proposition 5.1(b) can also be derived by taking the limit in (5.18):
| 5.32 |
using (5.19), so satisfies (5.31). Then, using (5.12) and (5.16), one obtains that the proportion of the population that ultimately is susceptible agrees with (5.30).
Remark 5.3
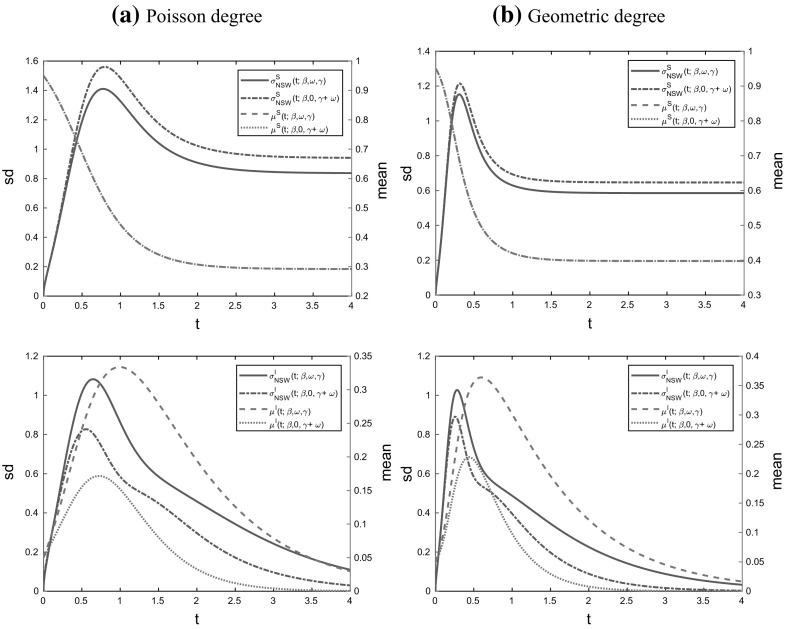
(Increased recovery rate and no dropping) Observe that Eq. (5.18) for and (5.19) for together imply immediately that the process of susceptibles in the deterministic model with recovery rate and dropping rate depends on only through their sum , since and only appear in (5.19) through the sum . Furthermore, (5.20) relates the variable of the binding site formulation to the effective degree formulation through and defined at (5.5) and (5.15), respectively. Thus the LLN limit describing the evolution of susceptibles classified by their effective degree for the model with dropping is the same as that for the model without dropping (i.e. the standard Markov SIR epidemic on a configuration model network) but with the recovery rate increased to . In particular, this implies that the deterministic final size of the two models are the same, as is apparent immediately from Proposition 5.1. This invariance also holds for the basic reproduction number and Mathusian parameter r, as is clear from the formulae in Eqs. (2.1) and (5.23), respectively. Note however that the LLN limit describing the infectives is not the same for these two models, since infectives recover more quickly in the model with increased recovery rate. Thus (as illustrated in Fig. 9 in Sect. 10.6) at any time there are more infectives in the deterministic model with dropping than in the corresponding model with increased recovery rate and no dropping. We revisit the model with increased recovery rate and no dropping in Sect. 8, where we focus on the probability of a major outbreak in the stochastic model with few initial infectives.
Fig. 9.
Scaled asymptotic means and standard deviations of the number of susceptible and infectious individuals through time (in the upper and lower plots, respectively), comparing the model with dropping to that with increased recovery rate. Model parameters are as in Fig. 7, except that . (Note that in the upper plots the two quantities are exactly equal)
Asymptotic variance of final size of epidemic on an MR random graph
Recall that denotes the number of susceptibles remaining at the end of the epidemic on an MR random graph. Thus denotes the final size of the epidemic. Note that, in an obvious notation, . Let and . Then, assuming the truth of Conjecture 4.1 for , the asymptotic variance of is given by
| 6.1 |
Suppose that and let z be the unique solution in [0, 1) of (5.25); cf. Proposition 5.1(a). The following proposition gives an almost fully explicit expression for the asymptotic variance .
Proposition 6.1
(Asymptotic variance of final size of epidemic on MR graph with dropping) Suppose that and . Then,
| 6.2 |
with
| 6.3 |
| 6.4 |
| 6.5 |
| 6.6 |
| 6.7 |
and .
Proof
The proof is rather long so only an outline is given here, with detailed calculations deferred to appendices. Let
| 6.8 |
where B is given by (4.13) with . Then, using (4.7) and (4.8),
| 6.9 |
The rest of the proof involves showing that the right-hand side of (6.9) yields the expression (6.2) for .
Recall that and note that is a scalar. It then follows that
| 6.10 |
where
| 6.11 |
Evaluation of (6.11) requires , which we now determine.
Let . Observe that , where , so using (4.2),
| 6.12 |
| 6.13 |
using , (5.7) and (5.9). Also, using (4.2), , so
| 6.14 |
where
| 6.15 |
Note from (4.2) that takes the partitioned form
| 6.16 |
It follows from (4.9) that has the partitioned form
Thus, using (6.8) and (6.14), we have
We show in Appendix D that
see (D.5), (D.26), (D.15) and (D.14), respectively. Hence,
| 6.17 |
where
| 6.18 |
| 6.19 |
| 6.20 |
with
We can now calculate using (6.11), (6.17) and (4.1), and hence obtain using (6.10). The details are lengthy and are given in Appendix E.
Recall from Sect. 5.3 that if then , where z is the unique solution in [0, 1) of (5.25), and if and then , where z is the unique solution in [0, 1) of (5.25) with replaced by ; cf. Proposition 5.1.
Conjecture 6.1
(CLT for of final size of epidemic on MR graph with dropping)
Remark 6.1
(Proving Conjecture 6.1) Part (a) of Conjecture 6.1 follows immediately from Conjecture 4.1 and Proposition 6.1; see Remark 4.1 for how Conjecture 4.1 might be proved. Part (b) of Conjecture 6.1 is concerned with epidemics started by a trace of infection, i.e. with . Similar CLTs for the final size of a wide range of SIR epidemics (e.g. von Bahr and Martin-Löf (1980), Scalia-Tomba (1985) and Ball and Neal (2003)) suggest that letting in the CLT with yields the correct CLT when for epidemics that become established and lead to a major outbreak. This is proved for the SIR epidemic without dropping of edges on configuration model networks in Ball (2018); see Remark 4.1. A similar proof should hold for the present model with dropping of edges.
Remark 6.2
(The condition) The condition in Proposition 6.1 and Conjecture 6.1 is required to ensure that ; recall from Sect. 5.3 that . Note from (5.28) that implies , so the LLN and functional CLT in Ethier and Kurtz (1986), Chapter 11, hold for both the original and random time-scale transformed processes and provided there is a maximum degree; see Appendix B. Further, as explained in Appendix C, if then if and only if . Now if and only if . Thus unless there is no recovery of infectives, no droping of edges and the limiting fraction of degree-1 susceptibles is 0. The same conclusion holds when .
Extension to iid degrees: epidemics on an NSW random graph
In this section we assume that the underlying network is constructed from a sequence of independent and identically distributed copies of the random variable D, which describes the degree of a typical individual. The random variables are used to construct a network of N individuals, yielding a realisation of NSW random graph. The almost sure convergence results described in Theorem 3.1 (and the corresponding time-transformed almost sure convergence result of Sect. 4) still hold for the present model, as noted previously, but the functional CLT and the CLT for the final size (Theorem 3.2 and Conjecture 6.1) need modifying, as the variability in the empirical degree distribution of the random network (and hence in the initial conditions for the effective degree process ) is of the same order of magnitude as that of the process itself. The modified results for epidemics on an NSW random graph are presented in Theorem 7.2 and Conjecture 7.1. In order to prove and motivate, respectively, these results we need a version of the functional CLT (Theorem 11.2.3) in Ethier and Kurtz (1986) that allows for asymptotically random initial conditions; see Theorem 7.1 below, which may be of more general interest beyond the present paper. Like the above-mentioned Theorem 11.2.3, Theorem 7.1 assumes a finite-dimensional state space, which for our application amounts to assuming that .
The limiting Gaussian process in Theorem 3.2 admits the Itô integral representation
| 7.1 |
where is a time-inhomogeneous Brownian motion (see Ethier and Kurtz (1986), Theorem 11.2.3, page 458) and . (To aid connection with Ethier and Kurtz (1986), and are now column vectors.) In Ethier and Kurtz (1986), Theorem 11.2.3, is nonrandom. In Theorem 7.1 below, we allow to be random.
Theorem 7.1
(Functional CLT for process with asymptotically random initial conditions) Suppose that the conditions of Ethier and Kurtz (1986), Theorem 11.2.3, are satisfied except that as , where . Then
| 7.2 |
where is a zero-mean Gaussian process with covariance function given, for , by
| 7.3 |
Proof
It is easily seen that the proof of Ethier and Kurtz (1986), Theorem 11.2.3, continues to hold in this more general setting. In particular, the limiting process satisfies (7.1), where now , so is a zero-mean Gaussian process. Further, the time-inhomogeneous Brownian motion arises as the weak limit, as , of the (suitably centred and scaled) Poisson processes used to construct realisations of , and hence is independent of . The covariance function in (7.3) then follows immediately from (7.1).
Remark 7.1
(Computing the asymptotic variance) Setting in (7.3) and differentiating as in Remark 3.4 shows that satisfies the ODE (3.17) but now with initial condition .
Remark 7.2
(Non-Gaussian limiting initial conditions) The covariance function (7.3) also holds when is non-Gaussian, provided and , though of course is no longer Gaussian.
Theorem 7.2
(Functional CLT for epidemic on NSW graph with dropping)
Suppose that as . Then the same functional CLT holds as in the MR graph situation (Theorem 3.2), but with the covariance function of changed in accordance with Eq. (7.3) and Remark 7.1 to reflect the randomness in the initial conditions.
Proof
The details of the proof, applying Theorem 7.1, are exactly the same as those in Appendix B where Theorem 11.2.3 of Ethier and Kurtz (1986) is applied to prove Theorem 3.2.
Remark 7.3
(The asymptotic variance matrix) Note that in Theorem 7.2 depends on how the initial infectives are chosen from the population. An example and some discussion can be found in Sect. 10.1. Also note that Theorem 7.2 as presented allows for the possibility of some initially recovered individuals in the population. This is to simplify the presentation of the theorem; the assumption of no initially recovered individuals implies that , from which it follows that and the last row and column of have all entries 0.
Next, we use Theorem 7.1 to conjecture a CLT for the final size of the epidemic on an NSW random graph. For , let denote a random variable with distribution given by the empirical distribution of , so
| 7.4 |
For , let be the final size of the epidemic on an NSW configuration model random graph having N vertices. We consider epidemics initiated by a trace of infection and assume that the variability in the initial conditions is owing entirely to the variability in .
Conjecture 7.1
(CLT for final size of epidemic on NSW graph with dropping)
Suppose that , , and . Then, in the event of a major outbreak,
| 7.5 |
where
| 7.6 |
with given by (6.2) (replacing by D in (6.3)–(6.7)) and
| 7.7 |
We now give the argument leading to this conjecture. Suppose, for the time being, that and consider the random time-scale transformed process , defined in Sect. 4, but now for the epidemic on an NSW network. Using (4.6) and Theorem 7.1, for any ,
where is a zero-mean Gaussian process with variance–covariance matrix at time t given by
| 7.8 |
is given by (4.7) and , with being defined as in Theorem 7.1. Then arguing as in the derivation of Proposition 4.1 yields, for any ,
| 7.9 |
where
| 7.10 |
We now assume that (7.9) extends to the case , so (7.5) holds with
cf. (6.1). Thus, using (7.8) and (7.10),
| 7.11 |
where
| 7.12 |
using (6.14).
We now assume that the above extends in the obvious way to and calculate the resulting asymptotic variance . Write
| 7.13 |
Then
| 7.14 |
where and are the deterministic ‘number’ of susceptible individuals and infectious half-edges, given by (5.26) and (5.11), respectively, but with (random) initial conditions induced by the NSW random graph on N vertices.
Recall the function and the random variable , defined at (5.5) and (7.4), respectively. It follows from (5.26) that
| 7.15 |
and, from (5.11), that
| 7.16 |
Let . Note, for example, that , so and is asymptotically normally distributed by the CLT for independent and identically distributed random variables. This and similar elementary calculations show that
| 7.17 |
| 7.18 |
| 7.19 |
| 7.20 |
| 7.21 |
| 7.22 |
Recall that , and (see (5.25) and Proposition 5.1(b)). Setting in (5.27) then gives (cf. (5.25))
| 7.23 |
Then, using (7.15) and (7.17),
| 7.24 |
using (7.15), (7.16), (7.20) and (7.22)
| 7.25 |
and
| 7.26 |
It follows from (5.4), (6.13), (6.15) (all with replaced by D) and (7.23), that
| 7.27 |
so
| 7.28 |
Note that , where is given by (6.3) with replaced by D. Substituting (7.24), (7.25) and (7.26) into (7.14), and invoking (7.23) and (7.28), yields (7.7) after a little algebra.
Remark 7.4
(Proving Conjecture 7.1) The two remaining steps required to prove Conjecture 7.1 are to justify (i) that (7.9) holds when and (ii) letting to obtain a CLT in the event of a major outbreak; cf. Remarks 4.1 and 6.1 which discuss these steps, respectively, for an epidemic on a MR random graph. As for epidemics on MR random graphs, the proofs in Ball (2018) for the SIR epidemic without dropping of edges on an NSW random graph should extend to the model with dropping of edges.
Remark 7.5
(Conjecture 7.1with) It is possible to extend Conjecture 7.1 to consider also the case and obtain an analogous result to Conjecture 6.1(a). The asymptotic variance is given by (7.11) and (7.12) but now depends on how the initial infectives are chosen.
Increased recovery rate instead of dropping edges
Recall the equivalent formulation of the model with dropping in which an infectious individual sends out warnings to each neighbour independently at rate , and susceptible individuals who receive such a warning immediately drop the corresponding edge. Consider a different but related model where, instead of sending out warnings to each neighbour at rate independently, one single warning (at rate ) is used for all neighbours simultaneously (and all of them immediately drop the edges). The effect of this change is that edge droppings become dependent. However, from the point of view of a given susceptible neighbour the probability that it drops its edge to a given infective is unchanged. Thus, for a given susceptible, such a warning (where all susceptible neighbours drop their edges) has the same effect as if its infective neighbour recovered. Hence, we consider a model without dropping, but with recovery rate instead of . We use and to refer to the two models, where the first component refers to the recovery rate and the second component to the dropping rate.
The above reasoning suggests that the dropping model should in some ways resemble this modified model. In fact, we have seen already in Sect. 5.3 (Remark 5.3) that, as , the scaled process of susceptibles in the two epidemics converge to the same LLN limit, and the same LLN holds for the final fraction getting infected. However, the two models are stochastically different, even for the process of susceptibles. The underlying reason for this difference is that independent warning signals makes the total number of infections less variable compared to having one warning signal to all susceptible neighbours. Consequently, the probability of a major outbreak is greater in the dropping model than in the modified model, as we prove in Theorem 8.1 below. Furthermore, we expect that the decrease in variability of the number of infections made by an infective decreases the limiting variance of both the whole process of susceptibles and the final size in the event of a major outbreak compared to the modified model. This is illustrated by the numerical results in Sect. 10.6.
Consider the beginning of an outbreak and an infectious individual having k susceptible neighbours. Let be the number of these k neighbours that the infectious individual infects in the dropping model and define similarly for the modified model. We compute the distributions of these two offspring random variables.
In the model we first condition on the infectious period I, which has an distribution, i.e. an exponential distribution with rate and hence mean . Given the duration of the infectious period , the infectious individual infects each of its k susceptible neighbours independently, and a given neighbour is infected if and only if there is an infectious contact before t and the edge has not been dropped before then. Thus, conditional upon , the probability that the given neighbour is infected is
Given , the number of neighbours infected follows a binomial distribution with parameters k and the probability above. Hence, if we relax the conditioning, it follows that has the mixed-Binomial distribution
| 8.1 |
Setting and yields immediately that
| 8.2 |
It is not hard to show that
| 8.3 |
and that .
Suppose that the epidemic is initiated by a single individual, chosen uniformly at random from the entire population, becoming infective. Then the number of susceptible neighbours of the initial infective is distributed according to D and, during the early stages of an outbreak in a large population, the number of susceptible neighbours of a subsequently infected individual is distributed as (see Sect. 2). These results hold for both models. It follows that the early stages of the dropping model in a large population can be approximated, on a generation basis, by a Galton–Watson branching process having offspring distribution that is a mixture of , , with mixing probabilities in the initial generation and mixing probabilities in all subsequent generations, where . (Note that , , is the probability mass function of .) A similar approximation holds for the modified model, except is replaced by . These approximations can be made rigorous in the limit as the population size by using a coupling argument, as in e.g. Ball and Sirl (2012). In the limit as , the probability of a major outbreak in the epidemic model is given by the probability that the corresponding approximating branching process does not go extinct.
The following lemma, proved in Appendix F, is required for the proof of Theorem 8.1 below, which shows that the probability of a major outbreak is greater in the dropping model than in the corresponding modified model. First, some more notation is required. For let , , denote the probability-generating function (PGF) of , the number of neighbours that an infectious individual with k susceptible neighbours infects in the early stages of the dropping model, and define similarly for the modified model. Let . Then, for the dropping model, the approximating branching process has offspring PGF in the first generation and offspring PGF in all subsequent generations, with analogous results holding for the model.
Lemma 1
Suppose that and . Then, for ,
| 8.4 |
with strict inequality for all when .
Theorem 8.1
(Probability of a major outbreak)
The basic reproduction number for both the dropping and modified models is given by (2.1).
- Suppose that and the epidemic is initiated by a single infective individual, chosen uniformly at random from the population. Then the probability of a major outbreak for the dropping model is strictly greater than the probability of a major outbreak for the modified model, i.e.
8.5
Proof
The basic reproduction number is given by the offspring mean of a typical (i.e. non-initial generation) infective, so for both models, using (8.3),
which proves part (a).
Turning to part (b), suppose that . Then, using standard branching process theory gives that, for the dropping model, the probability of a major outbreak is given by , where is the unique solution in [0, 1) of ; cf. Kenah and Robins (2007) and Ball and Sirl (2013). Analogously, for the modified model, , where is the unique solution in [0, 1) of .
Note that if then , so implies that . It then follows immediately from Lemma 1 that and for all . Hence, since and the derivative of both and at is , it follows that , whence , as is strictly increasing on [0, 1]. Thus we obtain our statement (8.5).
Remark 8.1
(Other choices for initial infectives) Theorem 8.1 is easily extended to other assumptions concerning initial infectives; for example, to an epidemic initiated by infective individuals chosen uniformly at random from the population, or to an epidemic initiated by an infective of a specified degree.
No dropping of edges
We use the results from this paper to analyse the Markovian SIR epidemic on a configuration model network in Sect. 9.1 and the giant component of a configuration model network in Sect. 9.2. Note that in the case that there is no dropping of edges, i.e. , we are in the setting of a Markovian SIR epidemic on a configuration model network. We treat the asymptotic variance of the final size for this model in Conjecture 9.1. If additionally, there is no recovery, i.e. , then in the event of a major outbreak, all individuals in the giant component eventually get infected. By using this we can apply the results from this paper to make statements about the size of the giant component in configuration model random graphs, see Conjecture 9.2.
SIR epidemic on configuration network
When , the model reduces to the Markov SIR epidemic on a configuration model network. The formulae for the asymptotic variance of the final size for the epidemic on MR and NSW random networks simplify and become fully explicit given z, defined below.
Recall that . If , then setting in Proposition 5.1(a) shows that , where z is the unique solution in [0, 1) of
| 9.1 |
If , so the epidemic is started by a trace of infection, and then, using Proposition 5.1(b), , where z is the unique solution in [0, 1) of (9.1) with replaced by .
Let and denote the final size of the epidemic, with no dropping of edges, on an MR and NSW configuration model random network, respectively, each having N vertices. Let and denote the asymptotic variance of the final size for the epidemic on an MR and an NSW configuration model random network, respectively. The following conjecture gives fully explicit formulae for and as functions of z, which are derived in Appendix G.
Conjecture 9.1
(CLT for final size of epidemic on configuration model networks)
- For the epidemic on an NSW network, suppose that , , and . Then, in the event of a major outbreak,
where9.5
and is given by (9.4), with replaced by D.9.6
Remark 9.1
(Proof of Conjecture 9.1) Although only conjectured here, Conjecture 9.1 (and hence also Conjecture 9.2 below) follow as a special case of Ball (2018), Theorems 2.1 and 2.2.
Remark 9.2
(Epidemics on NSW random network with) As for the model with dropping, Conjecture 9.1(b) can be extended to include the case ; the asymptotic variance then depends on how the initial infectives are chosen (cf. Remark 7.5).
Configuration model giant component
If then the epidemic ultimately infects all individuals in all components of the random network that contain at least one initial infective. Thus, under suitable conditions, in the limit as , setting in Conjecture 9.1(a)(ii) and (b) leads to CLTs for the size of the largest connected (i.e. giant) component in MR and NSW configuration model random graphs, respectively.
Let and note that, setting in the formula for , if and only if . The above configuration model random graphs possess a giant component if and only if , see e.g. Durrett (2007), Theorem 3.1.3. Suppose that . Setting and in (9.1) shows that z is now given by the unique solution in [0, 1) of
| 9.7 |
and the asymptotic fraction of vertices in the giant components of the above configuration model random graphs is given by .
Let and denote respectively the size of the giant component in an MR and an NSW random graph on N vertices. Setting in Conjecture 9.1 (a)(ii) and (b) yields the following conjecture.
Conjecture 9.2
(CLT for the size of the giant component)
Suppose that , and . Then,
- for an MR random graph,
where9.8 9.9 - for an NSW random graph,
where9.10 9.11
It is easily verified that the expressions (9.9) and (9.11) for the asymptotic variances and coincide with those first obtained by Ball and Neal (2017) using a completely different method; a CLT was conjectured in that paper and subsequently proved for an MR random graph in Barbour and Röllin (2019), and for both MR and NSW random graphs by Janson (2018). The results proved in these three papers allow for unbounded degrees under suitable conditions.
Numerical examples
In this section we give numerical results which exemplify some of the limit theorems and support some of the conjectures presented in the paper and give examples of using those limiting results for approximation. Such approximations follow from our asymptotic results in exactly the same way as the approximate distribution of the sum of independent and identically distributed random variables follows from the classical CLT. For example, we can use Eq. (3.15) in Theorem 3.2 to say that, for large N, the distribution of is approximately that of , from which approximations for the mean and variance of follow immediately from the corresponding properties of the Gaussian process . We also explore numerically some aspects of the behaviour of the model we have analysed, using the asymptotic results we have derived. In our numerical examples relating to the temporal evolution of the epidemic we look only at the mean and variance of the number of infective individuals in the population, we do not investigate any other quantities of interest or explicitly investigate the covariance/correlation structure in any way.
In this section we use the notation or to denote that the network degree distribution follows a standard Poisson or Geometric distribution with mass functions () or (), respectively. In particular we shall use repeatedly in our examples the distributions and . These distributions both have mean 5 and their standard deviations are and respectively.
First, however, we discuss some of the issues that arise in relation to the numerical implementation of our analytical results.
Implementation
The numerical implementation of our asymptotic results concerning epidemic final size (the formulae laid out in Propositions 5.1 and 6.1 and Conjecture 7.1) is straightforward, involving root-finding, numerical integration and derivatives up to order 3 of the degree distribution PGF . For the degree distributions we use, we have when and when , with both formulae being valid for . In the final size examples we always use the version of these results with , i.e. we work under the asymptotic regime where the epidemic starts with a trace of infection. The results concerning the evolution of the epidemic through time (Theorems 3.1, 3.2 and 7.2) warrant discussion of some issues that arise.
An obvious first issue is initial conditions and for the system of ODEs given by (3.9)–(3.11) together with the variance/covariance-related matrix ODE (3.17) (see also Remark 7.3). In an MR network we take the initial infectives to comprise a fixed number of individuals, with numbers of individuals of the various degrees chosen in the same proportions as they are present in the whole population. In an NSW network we choose the required number of initial infectives uniformly at random from the population. Ideally we might want the initial conditions to represent a large outbreak initiated by few initial infectives; this is a rather more complex situation and could be addressed using the results of Ball and House (2017).
Let be the proportion of individuals initially infected in the limit as . It is straightforward to show that and similarly that and (cf. the paragraph immediately before Theorem 3.1; with a NSW network these limits hold almost surely). Turning to , in the case of an MR network we have chosen the initial conditions so that there is no variability; i.e. all elements of are zero. With an NSW network there is variability in the initial conditions; to characterise it we let be the number of initially infected individuals (or assume that is a function of N such that ) and use the notation for the (i, j)-th element of the submatrix of corresponding to the susceptible elements (cf. the partitioning in (7.13)), so for example . We find that the following elements of are non-zero: for all i, and ; and for all , and . Derivations can be found in Appendix H.
After solving the ODE systems numerically we can calculate the asymptotic means and variances for other quantities of interest, for example to approximate , the number of infected individuals at time t, we use
The final ODE-related issue is choosing the value of M, the maximum degree, to use when the degree distribution does not have finite support. (This amounts to setting for all and .) The upper bound M needs to be large enough that the approximation is accurate but not so large that the systems of ODEs are impractical to solve numerically (the number of ODEs grows like ). To decide on an appropriate value for M we compare plots of the asymptotic means and variances of I(t) (i.e. the solid lines in the lower plots of Fig. 1), increasing M until there is no observable difference in these plots. We also compare the predicted relative ‘final’ size from the numerical ODE solution to the asymptotic final size predicted by Proposition 5.1. For the degree distributions we find that is sufficient when and when .
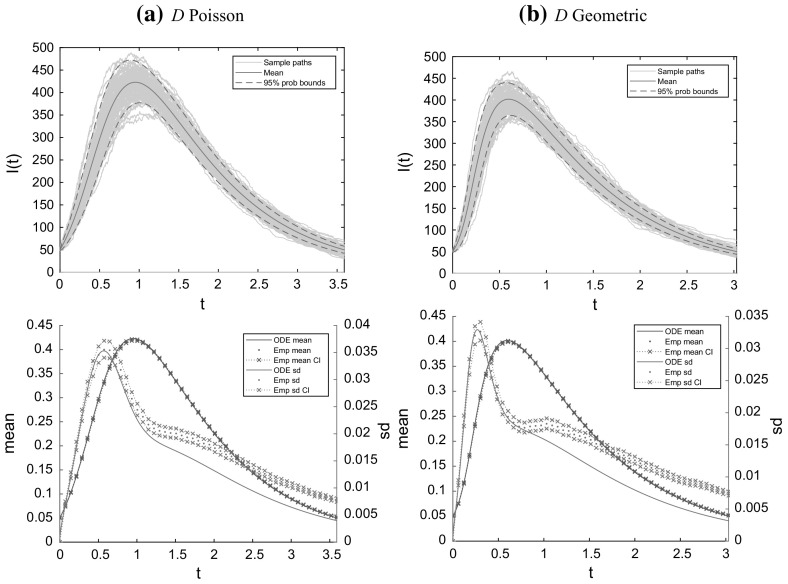
Fig. 1.
Demonstration of approximation implied by Theorem 7.2, for a and b. The upper plots show 100 simulated sample paths of the number of infectives against time t, together with the mean and central 95% probability bands for predicted by the functional CLT. The lower plots show asymptotic values and estimates from 1000 simulations of the scaled mean and standard deviation of the number of infectives through time. Other parameters are , , , , (All plots are truncated at the time when the proportion of individuals that are infective drops below 0.05)
Simulation of the epidemic process is relatively straightforward. Given a sequence of degrees (either [MR] a specified sequence or [NSW] independent realisations from the distribution ) we (i) generate the network, (ii) choose initial infectives, (iii) spread the epidemic on the network. There is therefore randomness in each simulation deriving not just from the evolution of the epidemic, but also the graph construction and, in the case of an NSW graph, the degree sequence. When we calculate confidence intervals (CIs) for quantities associated with simulations of the temporal evolution of the epidemic they are calculated independently for each time point; i.e. they are not confidence bands for the process. Endpoints of CIs for standard deviations are calculated as the square roots of the endpoints of standard symmetric (in terms of probability) CIs for the variance.
Convergence and approximation of temporal properties
First we demonstrate numerically some of the limit theorems from earlier sections, showing both how the convergence is realised and thus how these limit theorems can be used for approximation. We give examples only with an NSW graph construction, but much the same observations apply in the MR graph scenario.
In Fig. 1 we demonstrate using Theorem 7.2 for approximation of the temporal evolution of the epidemic, comparing simulated trajectories of the prevalence (for ) versus time t of the model with predictions from the functional central limit theorem, for a Poisson and a Geometric degree distribution. The upper plots show the simulated trajectories together with the mean and a central 95% probability band predicted by the CLT; they suggest that the approximation is fairly good. The lower plots compare the mean and standard deviation of the prevalence through time with the LLN and CLT based asymptotic predictions.
In Fig. 2 we investigate the convergence of the distribution of to its limit at three time points , and . The times are chosen so that is close to the time of peak prevalence and and are when prevalence is increasing and decreasing, respectively, at a level roughly half that of the peak prevalence. (Effectively we are examining the upper-right plot of Fig. 1 in detail at these three time points.) In this figure we have used a geometric degree distribution, but very similar conclusions are obtained using different distributions. This convergence is further investigated/demonstrated in Fig. 3, where, separately for each of the same three time points, we plot the Kolmogorov distance between the empirical and asymptotic distributions of the number of infectives against population size N.
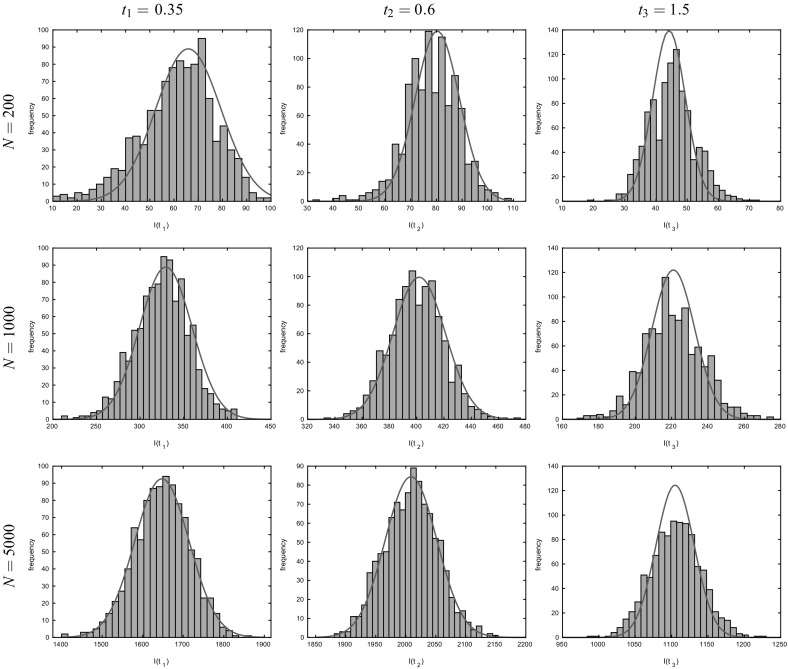
Fig. 2.
Demonstration of convergence described by Theorem 7.2, for . Histograms of (based on 1000 simulated trajectories) and normal approximation for three fixed time points , , and 3 population sizes , , . Other parameters are , , ,
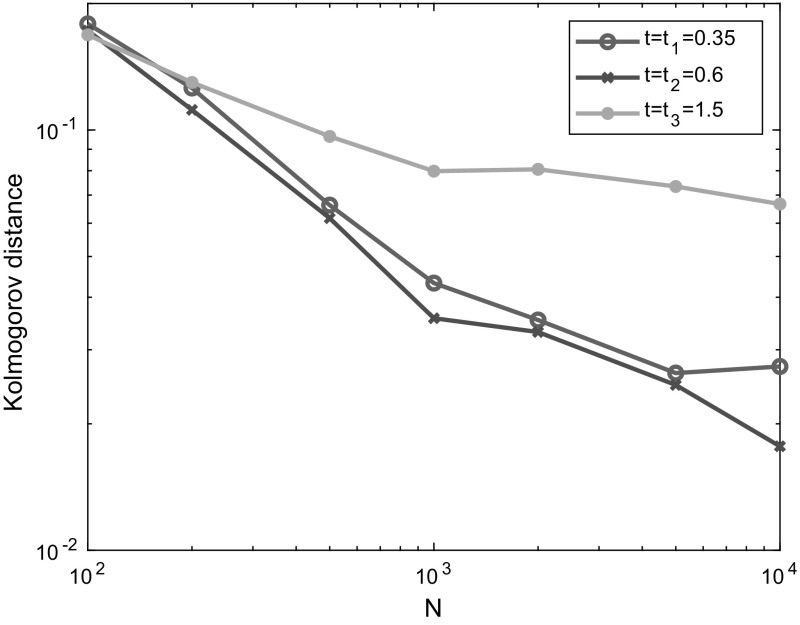
Fig. 3.
Demonstration of convergence described by Theorem 7.2, for . The distribution of (based on 5000 simulated trajectories) and its normal approximation are compared using the Kolmogorov distance at three fixed time points , , for population sizes . Other parameters are , , ,
Broadly speaking, Fig. 1 and similar plots for other population sizes, together with Figs. 2 and 3 and similar plots for other degree distributions, show that the predicted convergence is apparent, but seems slower for the later times. Even for quite small population sizes in the low hundreds, the asymptotic approximation to the mean behaviour of the epidemic is excellent. With smaller population sizes of a few hundred the approximation of the variability seems quite good in the early phase of epidemic growth, begins to worsen at or slightly before the time of peak prevalence and consistently underestimates the variability of after that. As the population size increases, the approximation for the standard deviation improves but not as quickly as one might hope: the agreement between asymptotic and empirical distributions seems to improve fairly slowly as N increases from 200 to 5000. Thus we can be very confident in using an LLN-based approximation for nearly any population size; but CLT-based approximations must be used with some caution, particularly at and after the time of peak prevalence. For these later times, a CLT-based approximation seems to systematically underestimate the variability in the number of infectives in the population. On a slightly more theoretical note, the plausibly linear (though also decidely noisy) behaviour of the plots in Fig. 3 is consistent with these Kolmogorov distances tending to 0 as . Consistent with the observations above, this convergence is at roughly the same rate for the time points in the early growth phase and near peak prevalence but much more slowly for the later time point in the phase where the infection is dying out.
Approximation of epidemic final size
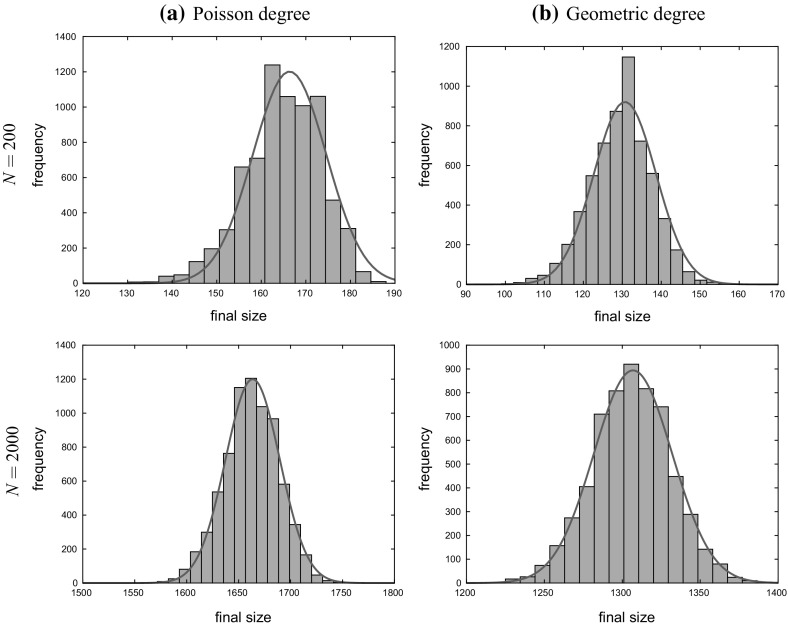
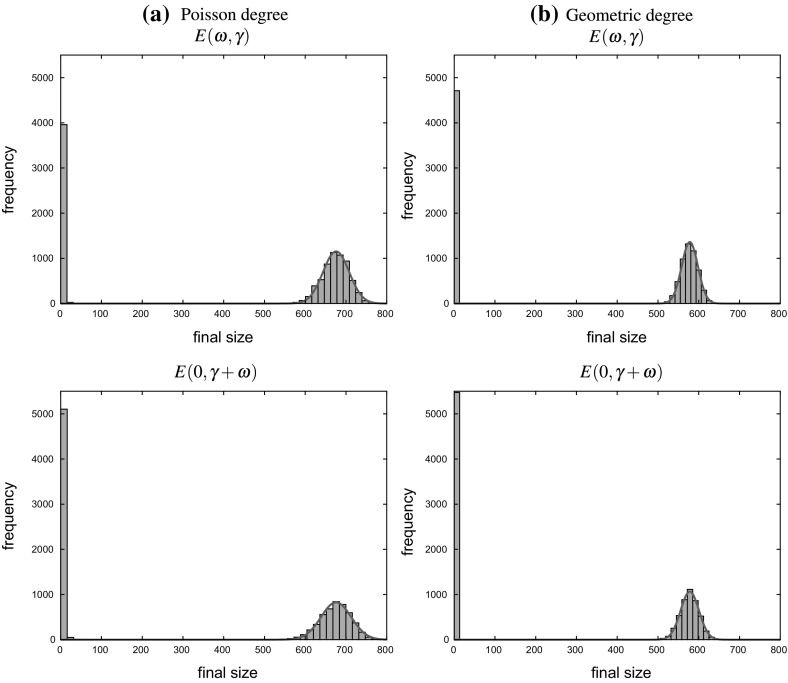
In Fig. 4 we demonstrate approximation results for the final size of major outbreaks in our epidemic model on an NSW graph (Conjecture 7.1). Again we see that the approximation is quite reasonable for relatively small population sizes in the low hundreds and becomes very good indeed for population sizes in the thousands.
Fig. 4.
Histograms (based on 10,000 simulations) and normal approximation of the final size distribution of major outbreaks for epidemics on graphs with a, b and varying populations sizes . Other parameter values are , and
The effect of dropping
Next we investigate the behaviour of our model in respect of the introduction of the dropping mechanism. Starting with an epidemic without dropping we examine the behaviour of and (the fraction of the population that is ultimately infected in the limiting determinstic model—see Sect. 5.3) as the dropping rate is increased from 0 (no dropping) to a value which brings the model below threshold. Figure 5 does this for two ‘starting’ models, one with a Poisson and one with a geometric degree distribution, both well above threshold with with comfortably above 0.5. (Recall that and are independent of whether the network is MR or NSW.) In both cases we see that increasing reduces the virulence and severity of the epidemic as measured by and . Perhaps noteworthy is that one of the plots of the mean final size is concave and the other convex.
The effect of random graph model on variances
We now demonstrate the effect of the random graph model (MR or NSW) on the variability of the final size of large outbreaks in our epidemic model. Figure 6 compares how the asymptotic scaled standard deviations for the final size of a major outbreak (i.e. and in Proposition 6.1 and Conjecture 7.1 ) behave as dropping is included into a baseline model with no dropping. The upper plots show that these standard deviations can change quite dramatically with ; the lower plots show that the extra variability in the NSW network model can result in substantially more variability in the epidemic final size. As might be anticipated, this effect is more pronounced for the geometric compared to the Poisson case, i.e. when the degree distribution is more variable.
Fig. 6.
Comparison of the scaled asymptotic standard deviations of the final size of a large outbreak in the MR and NSW models, as the dropping rate is increased from zero. In a the degree distribution is and in b; other parameters are , , . The upper plots show the actual scaled asymptotic standard deviations and and the lower plots show their ratio; all plots also show the relative final size for reference
Increased recovery rate instead of dropping
Lastly we investigate the relationship between our model and the related model with increased recovery rate instead of dropping, as discussed in Sect. 8. We focus mainly on the claims about relative variability in the two models with dropping and with increased recovery rate, though the results we present also illustrate Theorem 8.1, which gives an ordering of the major outbreak probabilities in the two models. Again we focus on the NSW graph model; similar conclusions (with less variability) are obtained with the MR graph model.
Figure 7 compares the final size distribution of the model with dropping to that of the model with increased recovery rate; again for two different degree distributions. The histograms and the normal approximation of the distribution of the size of a major outbreak confirm that the model with dropping does have a smaller variance in the size of major outbreaks and a larger chance of a major outbreak. Table 1 summarises the plots in Fig. 7. Here we see quite clearly that the major outbreak probabilities and the variances of the final size distributions are ordered as predicted by Theorem 8.1 and the argument involving differing dependence structures in Sect. 8. Differences between the two degree distributions are not very marked.
Fig. 7.
Histograms of 10,000 simulated final sizes for the epidemics and , with overlaid asymptotic approximations. Parameters are , , , , and the underlying graphs are of NSW type with a, b
Table 1.
Numerical summary of Fig. 7, using a final size of 0.15N to separate minor from major outbreaks
| Quantity | D Poisson, Model | D Geometric, Model | |||||
|---|---|---|---|---|---|---|---|
| Asymptotic | Estimate | 95% CI | Asymptotic | Estimate | 95% CI | ||
| Prob. of major outbreak | – | 0.601 | (0.592, 0.611) | – | 0.529 | (0.519, 0.539) | |
| Mean of major outbreak final size | 675.8 | 673.5 | (672.6, 674.3) | 578.0 | 576.8 | (576.3, 577.4) | |
| St. dev. of major outbreak final size | 32.0 | 32.4 | (31.8, 33.0) | 20.0 | 20.3 | (19.9, 20.6) | |
| D Poisson, Model | D Geometric, Model | ||||||
| Asymptotic | Estimate | 95% CI | Asymptotic | Estimate | 95% CI | ||
| Prob. of major outbreak | – | 0.483 | (0.474, 0.493) | – | 0.453 | (0.443, 0.463) | |
| Mean of major outbreak final size | 675.8 | 672.6 | (671.6, 673.7) | 578.0 | 577.2 | (576.5, 577.8) | |
| St. dev. of major outbreak final size | 37.1 | 38.3 | (37.6, 39.1) | 22.6 | 22.4 | (21.9, 22.8) | |
Figure 8 shows how the discrepancy in these variabilities generally increases with the dropping rate. Interestingly, we see that with the (more variable) geometric degree distribution the relative discrepancy increases with for most values of ; but decreases slightly with when is sufficiently large that the size of large outbreaks gets close to zero and the variability is quite large.
Fig. 8.
Scaled asymptotic standard deviations of the final size of a large outbreak in the models and for increasing dropping rate , starting from the ‘base model’ with , , and . The underlying graphs are of the NSW type with a, b. The upper plots show the standard deviations and the lower plot their ratio; all plots also show the relative final size for reference
Figure 9 shows how the asymptotic quantities relating to the mean and standard deviation of and compare through time for these models. In the model with dropping we denote the asymptotic mean proportion infected by and the asymptotic scaled standard deviation of by ; we let and denote the corresponding quantities for the number of susceptibles . Note that the absolute scale of the standard deviations here is not directly meaningful (to approximate the standard deviation in a population of size N these limiting quantities should be multiplied by ); it is the relative values that are of interest here. Firstly, the upper plots confirm our assertions about the relative numbers of susceptibles in the two models: that the mean (LLN) behaviour of the two models is the same but the model with dropping exhibits less variability (cf. the final size behaviour in Fig. 7 and Table 1). In the lower plots the behaviour of the individual models and is broadly in keeping with that observed in Fig. 1, however the differences between the two models are quite stark. Even though the two models have the same final size they achieve this through very different temporal behaviour: in the model individuals are infectious for less time but during that time infect others at a higher rate.
Concluding comments
The current paper is concerned with a model for an epidemic taking place on a network in which susceptible individuals may drop their connections to infectious individuals as a preventive measure. A consequence of the behavioural dynamics is that the network changes in time, and the way the network changes depends on the epidemic process taking place on it (sometimes referred to as an adaptive network). We derive limiting properties of the epidemic process assuming a large outbreak in a large community: the LLN and functional CLT for the epidemic process, as well as conjecture a LLN and CLT for the final number getting infected. We also give a version of the functional CLT in Ethier and Kurtz (1986), Chapter 11, which allows for asymptotically random initial conditions (Theorem 7.1). Although it is a simple extension of Ethier and Kurtz (1986), Theorem 11.2.3, we have not seen the result previously in the literature and it (especially the covariance formula (7.3)) clearly has interest and applications well beyond the present setting. Furthermore, from the analysis of the dropping model we also obtain results for the Markovian SIR epidemic on a configuration model and for the configuration model giant component. In particular, we conjecture CLTs, with essentially fully explicit expressions for the asymptotic variances, for the final size of such epidemics on both MR and NSW random graphs, and for the size of the giant components of those graphs.
The above LLN and functional CLT are proved under the assumption of bounded degrees. As noted in Remark 4.1, the arguments in Ball (2018) should yield proofs of the final-size LLN and CLTs under this assumption. Rigorous extension of these results to networks with unbounded degrees is a natural mathematical next step, though bounded degrees are clearly sufficient for most biological purposes.
The simulations in Sects. 10.2 and 10.3 show that the limiting approximations kick in for moderate population sizes. Further, from the numerical investigations, dropping of edges seems to have the greatest preventive effect when the basic reproduction number is not too large, more specifically when it is close to the epidemic threshold value of one. In fact, if is moderate in the absence of dropping of edges, a fairly small dropping rate can make the epidemic sub-critical implying that large outbreaks are no longer possible in the large population limit.
This paper is inspired by the model in Britton et al. (2016), who study only the initial stages of an outbreak. In the current paper, in order to make progress in the analysis of the complete outbreak, we assume that edges can only be dropped, in contrast to Britton et al. (2016), which allows for some of the dropped edges to rewire to other individuals. It would of course be of interest to study limiting properties of this more general dropping/rewiring model. However, the effective degree approach does not apply immediately in a rigorous fashion to this setting, and rigorous analysis of the non-initial stages of the model including rewiring is left as an open problem. The model with rewiring is considered further in Leung et al. (2018), where it is demonstrated that such rewiring of edges, although always beneficial to the susceptible individual, can have an adverse effect at the population level. Other possible forms of social distancing include reducing contacts rather than dropping edges completely (e.g. Viljoen et al. (2014) and Zhang et al. (2014)) or only temporarily dropping the edge (e.g. Althouse and Hébert-Dufresne (2014)).
Another extension of the current model would be to allow the network to change in time also for reasons other than the epidemic process. One could for example consider some type of dynamic network model as the base network model (e.g. one of the dynamic network models of Leung and Diekmann (2016)), and increase the dropping rate indirectly by decreasing the rate of creation of new edges and/or increasing the rewiring rate between susceptible-infectious pairs of individuals, see e.g. Reniers and Armbruster (2012) for a simulation study where partnership dissolution rates depend on the HIV status of the couple. Obviously, rigorous analysis of such models will be appreciably harder, if indeed possible.
Finally, we note that we have restricted ourselves to the Markovian setting throughout this paper. As always, this assumption is not realistic and is made for mathematical convenience. In the setting of this paper, it is possible to generalize some of our results to include non-exponentially distributed infectious periods. Using a susceptibility set argument, as in e.g. Ball and Sirl (2013), Section 2.1.2, we can prove results for the deterministic final size similar to Proposition 5.1(b). Specifically, if the infectious period follows a random variable I, the deterministic final size is the same as that for a standard SIR epidemic on a configuration model network in which the infectious period is distributed as , where W is independent of I and has an exponential distribution with rate . Recently, Sherborne et al. (2018) have extended edge-based compartmental models of epidemics on networks to allow for non-Markovian transmission and recovery processes, and that methodology should enable the limiting deterministic model for our model with dropping of edges and non-exponentially distributed infectious periods to be determined, as can be done using the binding site formulation of Leung and Diekmann (2016). It seems likely that our effective degree approach, together with LLN and functional CLT theorems in Wang (1975, 1977) for age and density dependent population processes, can be used to put such deterministic models in a fully rigorous asymptotic framework and provide an associated functional CLT.
Acknowledgements
This work was partially supported by a grant from the Simons Foundation and was carried out as a result of the authors’ visit to the Isaac Newton Institute for Mathematical Sciences during the programme Theoretical Foundations for Statistical Network Analysis in 2016 (EPSRC Grant Number EP/K032208/1). KYL was supported by the Swedish Research Council (VR) Grant Number 2015-05015. This work was also supported by a Grant from the Knut and Alice Wallenberg Foundation, which enabled FB to be a guest professor at the Department of Mathematics, Stockholm University. We thank Phil Pollett for some helpful discussions relating to Theorem 7.1 and the reviewers for their constructive comments which have improved the presentation of the paper.
A Derivation of drift function
In this appendix we derive the expression (3.8) for . First note that (3.1) and (3.7) yield
| A.1 |
| A.2 |
| A.3 |
Similarly, (3.4) and (3.7) yield
| A.4 |
| A.5 |
B Application of theorems for density dependent population processes
In this appendix we show that the conditions of the Theorems 11.2.2 and 11.2.3 in Ethier and Kurtz (1986), Chapter 11, concerning density dependent population processes are satisfied when there is a maximum degree, say, and . (Recall that is the fraction of the population that is ultimately infected by the limiting deterministic model.) Thus, for ,
so has dimension . The limiting deterministic process is , where, for ,
The domain of the intensity functions is
The proofs of the theorems in Ethier and Kurtz (1986), Chapter 11, make it clear that the conditions need only hold in some small neighbourhood of . Thus, since , there exists , so that can be replaced by , where . It follows that the density dependent condition (3.6) is satisfied for all sample paths of such that remains within , which is sufficient for the proofs in Ethier and Kurtz (1986).
Considering first the LLN for , the conditions of Ethier and Kurtz (1986), Theorem 11.2.1, are satisfied if (i) ; (ii) the drift function F is Lipschitz continuous on ; and (iii) . It is easily seen from (3.7) that (i) is satisfied, since is finite and for all . It follows from (3.8) that the partial derivatives are uniformly bounded on , since for all , so (ii) is satisfied. Finally, it is easily seen from the proof in Ethier and Kurtz (1986) that the result still holds if the convergence in (iii) holds almost surely, thus the LLN for , stated in Sect. 3, holds for epidemics on both MR and NSW random graphs.
Turning to the functional CLT (3.15), where to be more explict denotes weak convergence in the space of right-continuous functions having limits from the left (i.e. càdlàg functions), endowed with the Skorohod metric, the conditions of Ethier and Kurtz (1986), Theorem 11.2.3, are satisfied if, in addition to (i)–(iii), (iv) ; (v) the intensity functions and the partial derivatives are continuous on ; and (vi) , where is constant. Now (iv) is satisfied, for similar reasons to (i). It is easily seen from (3.7) and (3.8) that (v) is satisified, and (vi) follows from (3.14). Thus (3.15) is proved.
Consider now the random time-scale transformed process introduced in Sect. 4. The limiting determinstic process is now , where
For any , there exists such that for all . Let . The proofs that the conditions of Ethier and Kurtz (1986), Theorems 11.2.1 and 11.2.3, are satisfied for the transformed process are analagous to those above, except is replaced by . Note that the denominator in the intensity functions given at (4.1) (and hence in the drift function given at (4.2)) is , where for the untransformed process it is .
C Properties of
In this appendix we prove that (i) and (ii) (4.12) holds for all . Recalling the definition of at (4.10), it follows that is the smallest positive solution of with given by (5.11) (Clearly, for .) Also, it follows from (5.9), (6.12), and that
Let and recall that . Then,
| C.1 |
and from (5.11), if follows that satisfies
| C.2 |
For , let
| C.3 |
so satisfies . Now and . (Recall the definition of at (5.3).) Further, unless , then , so since A(z) is continuous, and (and hence also ) is finite. For , note that satisfies . Thus, and as , so and . If and , then it is easily verified using the convexity of that , so .
We show now that for . Differentiating (C.3) and recalling that yields
Suppose, for contradiction, that . Then, recalling (C.1), , whence for , since is increasing on [0, 1]. It follows from (C.2) that . Thus,
But , since, using (5.3), . Thus, , which is a contradiction as . Hence , as required.
Finally, suppose that the epidemic is started by a trace of infection, so , and that . Then, Proposition 5.1(b) shows that (C.2) (with replaced by D and ) has a (unique) solution, , in [0, 1) if and only if . Moreover, unless .
Further, the above proof is easily modified to show that .
D Calculations pertaining to
Expanding (4.9) in partitioned form yields, using (6.16),
| D.1 |
and, for and ,
| D.2 |
where and .
It follows from (4.2) that
Thus, letting denote the (i, j)th element of , it follows from (D.1) that, for ,
| D.3 |
with the initial condition . For fixed j, apart from the initial condition, satisfies the same system of ODEs as that given at (4.3) for , and it follows from (5.1) that, for ,
| D.4 |
so
| D.5 |
where is defined at (5.5).
From (4.2), the coefficient of in is
so
Hence
so
| D.6 |
where with . Similar calculations show that
| D.7 |
| D.8 |
| D.9 |
| D.10 |
| D.11 |
Setting in (D.2) and using (D.6)–(D.8) yields, for ,
| D.12 |
Setting in (D.2) and using (D.9)–(D.11) yields, for ,
| D.13 |
Setting in (D.12) and (D.13), and recalling that and are both identically zero, yields
with initial condition
This linear system of two ODEs has solution, for ,
| D.14 |
Similarly, setting in (D.12) and (D.13) yields
with initial condition
and solution, for ,
| D.15 |
Setting in (D.12) and (D.13) yields
| D.16 |
| D.17 |
with initial condition
| D.18 |
Further, using (D.4), for ,
| D.19 |
| D.20 |
Note that (D.16)–(D.20) imply that, for ,
| D.21 |
so we consider the case when .
Let
Then,
| D.22 |
with
| D.23 |
Substituting (D.23) into (D.22) yields, after using (D.19) and (D.20), that, for ,
| D.24 |
where
and, recalling (5.5), . Integrating by parts,
so
Also,
It then follows using (D.24) and (D.21) that, for ,
| D.25 |
| D.26 |
E Calculation of
Recall (6.10) for , where are given by (6.11). We first obtain closed-form expressions for the integrands in the definitions of , then evaluate the integrals as a function of and finally show that the expression for reduces to that given in Proposition 6.1.
E.1 Integrands
We determine the integrands for in reverse order.
E.1.1 Integral for
For , it follows from (3.5), (6.17) and (6.19) that
so, using (4.1) and recalling (5.9) for ,
where . Thus, using (6.11),
| E.1 |
E.1.2 Integral for
For , it follows from (3.4), (6.17) and (6.19) that
so, using (4.1),
Thus, using (6.11),
| E.2 |
E.1.3 Integral for
For , it follows from (3.3), (6.17) and (6.20) that
where . Hence, using (4.1),
and, using (6.11),
| E.3 |
E.1.4 Integral for
For , it follows from (3.2) and (6.17) that
so, using (4.1),
and, using (6.11),
| E.4 |
E.1.5 Integral for
For , it follows from (3.1), (6.17) and (6.20) that
so, using (4.1),
and, using (6.11),
| E.5 |
E.2 Evaluation of integrals
Recall that . Then adding (E.2)–(E.5) gives,
| E.6 |
where
| E.7 |
| E.8 |
| E.9 |
| E.10 |
| E.11 |
| E.12 |
| E.13 |
Recalling (5.9), (5.10) and (6.18) allows us to evaluate immediately and :
| E.14 |
| E.15 |
| E.16 |
For , let denote a falling factorial, with the convention that . To calculate and , observe first using (5.2) that, for and ,
| E.17 |
and that
Thus, using (E.17) with and ,
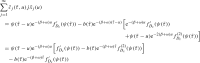 |
and
Hence, recalling (6.18),
| E.18 |
where
| E.19 |
Turning to and , note that
| E.20 |
so
where
Let
| E.21 |
Then, since and , it follows using (E.17) that
whence
| E.22 |
Further, (E.20) implies
so
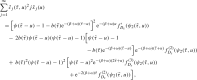 |
E.23 |
To calculate the integral in (E.1) for , let
| E.24 |
and note that
Multiplying (4.4) by and summing over yields, after recalling (5.9) and invoking (E.17) with and , that
so
since . Thus,
as . Using (E.24) gives and differentiating (5.3) twice yields . Thus, . Further, , so and using (E.1),
| E.25 |
E.3 Expression for
We now use (6.10), (E.6) and (E.25) to obtain an expression for .
Let . Then, since is the unique solution in of (5.24), z is the unique solution in [0, 1) of (5.25). Recall that . It then follows from (6.13) that
whence, using and (5.4)
| E.26 |
using (5.25), so defined at (6.3). For future reference, note that (E.26) implies
| E.27 |
| E.28 |
Adding (E.14) and (E.15) yields, after substituting ,
| E.29 |
using (5.25). Substituting for from (E.19) and rearranging then gives
| E.30 |
Adding (E.29) and (E.30) yields after a little algebra that
| E.31 |
Adding (E.16) and (E.25) yields
Substituting from (E.28) and noting that yields, after a little algebra, that
| E.32 |
Adding (E.31) and (E.32), and comparing with (6.2), shows that
| E.33 |
with and given by (6.4)–(6.7). Making the substitution in the integrals in (E.11) and (E.13), using the expressions (E.22) and (E.23) for the respective integrands, shows that
| E.34 |
The expression (6.2) for then follows using (6.10) and (E.6).
F Proof of Lemma 1
For , let and . Thus, for example, is the number of neighbours an infective, say, with k susceptible neighbours fails to infect in the dropping model. For , let denote a falling factorial, with the convention that . Further let , where , be the rth factorial moment of and define analogously for the modified model. Note that for all . We prove first that
| F.1 |
with strict inequality for , and then consider the Taylor expansions of and about to prove Lemma 1.
To determine the factorial moment , fix , give the k neighbours of the labels and let be the set of neighbours that are not infected by . Then, for any , depends on B only through its size |B|, so is a symmetric sampling procedure (Martin-Löf 1986). It follows from Lemma 1 in that paper that , where is the probability that no one in any fixed set of r neighbours of is infected by , with . Similarly, in an obvious notation, . To prove (F.1), we assume without loss of generality that , since otherwise time can be rescaled linearly so that . Note that , so using (8.1),
since . A similar but simpler argument using (8.2) yields
Thus for all k, r if and only if
| F.2 |
, which we now show.
First note that both sides of (F.2) equal 1 when . Suppose . Then
where
Now , so , as noted (in a different notation) after (8.2). For ,
where
Thus, for , proving (F.1).
Turning to Lemma 1 note that for and , , where is the PGF of . Similarly, in an obvious notation, . Now, for ,
with strict inequality if . Thus, for all , again with strict inequality if , proving Lemma 1 for . The lemma holds trivially when since . Finally, note that and, similarly, , so (F.1) implies the lemma holds also when .
G Derivation of asymptotic variances in Conjecture 9.1
In this appendix we derive the expressions for and given in Conjecture 9.1 by setting in Conjectures 6.1 and 7.1. We consider first the epidemic on an MR random network.
From (E.11) and (E.34), , since . We derive a closed-form expression for when . Note that now , so using (5.5) and (E.21), and . Substituting these into (E.22) yields
| G.1 |
For , let
Integrating by parts, for ,
| G.2 |
so, setting ,
| G.3 |
Substituting (G.1) into (E.13), and using (G.3) and (G.2) with yields
| G.4 |
Recall that and . Setting in (E.28) gives
Substituting these into (G.4) and using (9.1) yields
Setting in (6.2) and recalling that now then yields
| G.5 |
Setting in (7.27) shows that , where is defined at (9.4). Further ; see immediately after (9.1). The expression (9.3) for then follows immediately from (G.5).
Turning to the epidemic on an NSW random network, setting in (7.7) and noting that then , yields
| G.6 |
Setting in (7.6) shows that is given by the sum of the right-hand sides of (G.5), with replaced by D, and (G.6). The expression (9.6) for now follows since and .
H ODE initial conditions for the epidemic on an NSW graph
In this appendix we derive the initial conditions that are given in Sect. 10.1. We assume that the number of initial infectives is (or that is any function of N such that ) and that these individuals are chosen uniformly from the population. Since there is nothing special about the labelling of the individuals in the population we can assume that individuals are initially infected.
First consider the term . Writing as a sum of indicator variables, we use the independence of different individuals’ degrees to find that
so
for all i. Considering infectives instead, essentially the same arguments establish that
For the covariances we use the same independence and to find that, for ,
so that we have
The same calculations for yield
for . Next, for all i, j,
by independence of individuals (there are no terms with since the indices take values in disjoint sets). Thus
Finally, we have , so all (co)variances involving it are zero and remain so when divided by N, whence for all i we have
Footnotes
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Frank Ball, Phone: +44-(0)115-9514969, Email: frank.ball@nottingham.ac.uk.
Tom Britton, Email: tom.britton@math.su.se.
Ka Yin Leung, Email: kayin.leung@math.su.se.
David Sirl, Phone: +44-(0)115-9513896, Email: david.sirl@nottingham.ac.uk.
References
- Althouse B, Hébert-Dufresne L. Epidemic cycles driven by host behaviour. J R Soc Interface. 2014;11:20140,575. doi: 10.1098/rsif.2014.0575. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Ball F (2018) Central limit theorems for SIR epidemics and percolation on configuration model random graphs. arXiv:1812.03105v1
- Ball F, House T. Heterogeneous network epidemics: real-time growth, variance and extinction of infection. J Math Biol. 2017;75(3):577–619. doi: 10.1007/s00285-016-1092-3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Ball F, Neal P. The great circle epidemic model. Stoch Process Appl. 2003;107(2):233–268. [Google Scholar]
- Ball F, Neal P. Network epidemic models with two levels of mixing. Math Biosci. 2008;212(1):69–87. doi: 10.1016/j.mbs.2008.01.001. [DOI] [PubMed] [Google Scholar]
- Ball F, Neal P. The asymptotic variance of the giant component of configuration model random graphs. Ann Appl Probab. 2017;27(2):1057–1092. [Google Scholar]
- Ball F, Sirl D. An SIR epidemic model on a population with random network and household structure, and several types of individuals. Adv Appl Probab. 2012;44(1):63–86. [Google Scholar]
- Ball F, Sirl D. Acquaintance vaccination in an epidemic on a random graph with specified degree distribution. J Appl Probab. 2013;50(4):1147–1168. [Google Scholar]
- Barbour A, Reinert G. Approximating the epidemic curve. Electron J Probab. 2013;18(54):1–30. [Google Scholar]
- Barbour AD, Luczak MJ. A law of large numbers approximation for Markov population processes with countably many types. Probab Theory Relat Fields. 2012;153(3–4):725–757. [Google Scholar]
- Barbour AD, Luczak MJ. Central limit approximations for Markov population processes with countably many types. Electron J Probab. 2012;17(90):1–16. [Google Scholar]
- Barbour AD, Röllin A. Central limit theorems in the configuration model. Ann Appl Probab. 2019;29(2):1046–1069. [Google Scholar]
- Bohman T, Picollelli M. SIR epidemics on random graphs with a fixed degree sequence. Random Struct Algorithms. 2012;41(2):179–214. [Google Scholar]
- Bollobás B. A probabilistic proof of an asymptotic formula for the number of labelled regular graphs. Eur J Comb. 1980;1(4):311–316. [Google Scholar]
- Bollobás B. Random graphs. New York: Academic Press; 2001. [Google Scholar]
- Britton T, Juher D, Saldaña J. A network epidemic model with preventive rewiring: comparative analysis of the initial phase. Bull Math Biol. 2016;78(12):2427–2454. doi: 10.1007/s11538-016-0227-4. [DOI] [PubMed] [Google Scholar]
- Decreusefond L, Dhersin JS, Moyal P, Tran VC. Large graph limit for an SIR process in random network with heterogeneous connectivity. Ann Appl Probab. 2012;22(2):541–575. [Google Scholar]
- Durrett R. Random graph dynamics. Cambridge: Cambridge University Press; 2007. [Google Scholar]
- Ethier SN, Kurtz TG. Markov processes: characterization and convergence. Hoboken: Wiley; 1986. [Google Scholar]
- Gross T, D’Lima CJD, Blasius B. Epidemic dynamics on an adaptive network. Phys Rev Lett. 2006;96:208,701. doi: 10.1103/PhysRevLett.96.208701. [DOI] [PubMed] [Google Scholar]
- Jacobsen KA, Burch MG, Tien JH, Rempala GA. The large graph limit of a stochastic epidemic on a dynamic multilayer network. J Biol Dyn. 2018;12(1):746–788. doi: 10.1080/17513758.2018.1515993. [DOI] [PubMed] [Google Scholar]
- Janson S (2018) Asymptotic normality in random graphs with given vertex degrees. arXiv:1812.08063v1
- Janson S, Luczak M, Windridge P. Law of large numbers for the SIR epidemic on a random graph with given degrees. Random Struct Algorithms. 2014;45(4):726–763. [Google Scholar]
- Kenah E, Robins JM. Second look at the spread of epidemics on networks. Phys Rev E. 2007;76:036,113. doi: 10.1103/PhysRevE.76.036113. [DOI] [PMC free article] [PubMed] [Google Scholar]
- KhudaBukhsh WR, Woroszylo C, Rempala GA, Koeppl H (2017) Functional central limit theorem for susceptible-infected process on configuration model graphs. arXiv:1703.06328v1
- Kiss IZ, Miller JC, Simon P. Mathematics of epidemics on networks: from exact to approximate models. Berlin: Springer; 2017. [Google Scholar]
- Kurtz TG. Solutions of ordinary differential equations as limits of pure jump Markov processes. J Appl Probab. 1970;7(1):49–58. [Google Scholar]
- Kurtz TG. Limit theorems for sequences of jump Markov processes approximating ordinary differential equations. J Appl Probab. 1971;8(2):344–356. [Google Scholar]
- Leung K, Ball F, Sirl D, Britton T. Individual preventive social distancing during an epidemic may have negative population-level outcomes. J R Soc Interface. 2018;15:20180,296. doi: 10.1098/rsif.2018.0296. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Leung K, Diekmann O. Dangerous connections: on binding site models of infectious disease dynamics. J Math Biol. 2016;74(3):619–671. doi: 10.1007/s00285-016-1037-x. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Lindquist J, Ma J, van den Driessche P, Willeboordse FH. Effective degree network disease models. J Math Biol. 2011;62(2):143–164. doi: 10.1007/s00285-010-0331-2. [DOI] [PubMed] [Google Scholar]
- Martin-Löf A. Symmetric sampling procedures, general epidemic processes and their threshold limit theorems. J Appl Probab. 1986;23(2):265–282. [Google Scholar]
- Miller JC. A note on a paper by Erik Volz: SIR dynamics in random networks. J Math Biol. 2011;62(3):349–358. doi: 10.1007/s00285-010-0337-9. [DOI] [PubMed] [Google Scholar]
- Molloy M, Reed B. A critical point for random graphs with a given degree sequence. Random Struct Algorithms. 1995;6(2–3):161–179. [Google Scholar]
- Newman M. Spread of epidemics on networks. Phys Rev E. 2002;66:016,128. [Google Scholar]
- Newman M, Strogratz S, Watts D. Random graphs with arbitrary degree distributions and their applications. Phys Rev E. 2001;64:026,118. doi: 10.1103/PhysRevE.64.026118. [DOI] [PubMed] [Google Scholar]
- Reniers G, Armbruster B. HIV status awareness, partnership dissolution and HIV transmission in generalized epidemics. PLoS ONE. 2012;7(12):e50,669. doi: 10.1371/journal.pone.0050669. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Scalia-Tomba GP. Asymptotic final size distribution for some chain-binomial models. Adv Appl Probab. 1985;17(3):477–495. [Google Scholar]
- Shaw L, Schwartz IB. Fluctuating epidemics on adaptive networks. Phys Rev E. 2008;77:066,101. doi: 10.1103/PhysRevE.77.066101. [DOI] [PubMed] [Google Scholar]
- Sherborne N, Miller JC, Blyuss KB, Kiss IZ. Mean-field models for non-Markovian epidemics on networks. J Math Biol. 2018;76(3):755–778. doi: 10.1007/s00285-017-1155-0. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Tunc I, Shaw LB. Effects of community structure on epidemic spread in an adaptive network. Phys Rev E. 2014;90:022,801. doi: 10.1103/PhysRevE.90.022801. [DOI] [PubMed] [Google Scholar]
- Viljoen T, Spoelstra J, Hemerik L, Molenaar J. Modelling the impact of HIV on the populations of South Africa and Botswana. Acta Biotheoret. 2014;62(1):91–108. doi: 10.1007/s10441-014-9210-3. [DOI] [PubMed] [Google Scholar]
- Volz EM. SIR dynamics in random networks with heterogeneous connectivity. J Math Biol. 2008;56(3):293–310. doi: 10.1007/s00285-007-0116-4. [DOI] [PMC free article] [PubMed] [Google Scholar]
- von Bahr B, Martin-Löf A. Threshold limit theorems for some epidemic processes. Adv Appl Probab. 1980;12(2):319–349. [Google Scholar]
- Wang FJS. Limit theorems for age and density dependent stochastic population processes. J Math Biol. 1975;2(4):373–400. [Google Scholar]
- Wang FJS. A central limit theorem for age- and density-dependent population processes. Stoch Process Appl. 1977;5(2):173–193. [Google Scholar]
- Zanette DH, Risau-Gusmán S. Infection spreading in a population with evolving contacts. J Biol Phys. 2008;34(1–2):135–148. doi: 10.1007/s10867-008-9060-9. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Zhang HF, Xie JR, Tang M, Lai YC. Suppression of epidemic spreading in complex networks by local information based behavioral responses. Chaos Interdiscip J Nonlinear Sci. 2014;24:043,106. doi: 10.1063/1.4896333. [DOI] [PMC free article] [PubMed] [Google Scholar]