Significance
We examine near-repeat activity patterns of al-Qaeda, ISIS, and local insurgents, whereby a first terrorist attack temporarily increases the likelihood of a second one by the same group. We observe heightened near-repeat activity for all organizations in six geographic clusters and quantify the effect to persist within 20 km and 4 to 10 weeks after the first event. Near-reaction patterns, where two distinct groups react to each other’s activities, depend on the adversarial, neutral, or collaborative relationship between parties at the local level. We find no evidence of outbidding, whereas terrorist and state activities mutually reinforce one another. Our results may be useful for counterterrorism decision making and strategic resource allocation; near-repeat patterns may offer insight into local power structures.
Keywords: terrorist attacks, near-repeat activity, rivalries, social balance theory
Abstract
We study the spatiotemporal correlation of terrorist attacks by al-Qaeda, the Islamic State of Iraq and Syria (ISIS), and local insurgents, in six geographical areas identified via -means clustering applied to the Global Terrorism Database. All surveyed organizations exhibit near-repeat activity whereby a prior attack increases the likelihood of a subsequent one by the same group within 20 km and on average 4 (al-Qaeda) to 10 (ISIS) weeks. Near-response activity, whereby an attack by a given organization elicits further attacks from a different one, is found to depend on the adversarial, neutral, or collaborative relationship between the two. When in conflict, local insurgents respond quickly to attacks by global terror groups while global terror groups delay their responses to local insurgents, leading to an asymmetric dynamic. When neutral or allied, attacks by one group enhance the response likelihood of the other, regardless of hierarchy. These trends arise consistently in all clusters for which data are available. Government intervention and spillover effects are also discussed; we find no evidence of outbidding. Understanding the regional dynamics of terrorism may be greatly beneficial in policy making and intervention design.
Terrorist activities by al-Qaeda (AQ) and the Islamic State of Iraq and Syria (ISIS) have brought violence and destruction to the Middle East and the world (1). Many historical, political, and religious motivations lie behind this unrest and several complementary perspectives have been offered to explain it (2–5). Recent advances in data collection have allowed for the thorough updating of terrorist databases; being able to extract information from them may help gain additional insight and develop counterterrorism strategies.
This work examines the spatiotemporal correlation of terrorist attacks perpetrated worldwide by AQ and ISIS, focusing on the post-2014 era, when they began functioning as independent entities. On the local scale, the AQ/ISIS dynamics may be affected by independent militias or insurgents acting as rivals or allies to either. These groups are often entrenched in their communities and may be quite powerful, even eclipsing AQ or ISIS. Using near-repeat analysis (6–11) on data derived from the Global Terrorism Database (GTD), we analyze patterns of attack for three classes of terror groups (AQ, ISIS, and local militias) in six geographical clusters. The latter are identified through -means clustering without imposing any a priori geographical constraints, such as national borders. The constituency of each class varies across clusters: AQ or ISIS may have the most combatants in some; in others, local militias may be the most numerous. Despite cluster heterogeneity, our findings indicate universal near-repeat activity, whereby an attack by a given group temporarily raises the probability of further attacks by the same one within 20 km over 4 to 10 weeks. The variability depends on location and organization, but groups with fewer combatants are always found to display the longest period of enhanced near repeat. While insurgents are present in all clusters, AQ and ISIS may or may not be; where they do colocalize, one is numerically superior to the other and in conflict with insurgents. The two most numerous groups (insurgents and either AQ or ISIS) are regarded as major players; the minor, numerically inferior one between AQ and ISIS aligns with either of the major two. We also examine patterns of responding near repeat, in short near reaction, whereby an attack by a given group elicits a response from a different one. Insurgent activity intensifies after an attack by a major rival (either AQ or ISIS) while the latter suppresses its activity following insurgent attacks, leading to an asymmetric dynamic. Aligned groups, allies, or neutral parties united against a common enemy reinforce each other’s activities so that regardless of which one strikes first, the other will always intensify its attacks within 20 km. No evidence of outbidding is found, whereas terrorist activity increases in response to government action in all surveyed clusters. Our findings underline the importance of local geography and hierarchies in understanding terrorism.
Historical Background
AQ was founded by Osama bin Laden during the Soviet–Afghan War in the 1980s. Due to intense international pressure after the 9/11 attacks, AQ evolved into a decentralized “dune”-like organization (12): Its affiliates were encouraged to operate independently while still being part of its broader network. Among the myriad of players, ISIS rapidly emerged as a strong challenger to AQ’s lead. ISIS was originally established in Jordan by Abu Musa al-Zarqawi in the late 1990s under the name Jamaat al-Tawhid wal-Jihad (JTJ). In 2004 al-Zarqawi pledged allegiance to AQ and renamed JTJ al-Qaeda in Iraq (AQI). Instructed by AQ to establish a formal governing body, in early 2006 AQI merged with other insurgent groups to form the Mujahideen Shura Council (MSC) and later announced the creation of the Islamic State of Iraq (ISI), a centralized group aiming to occupy the northern Iraqi territories by the Syrian border. As the Syrian civil war intensified in 2013, ISI became ISIS and expanded into Syria without consulting AQ’s general command, creating tension with Jabhat al-Nusra (JN), a Syrian AQ affiliate. After repeated attempts to control its expansion, AQ disavowed ISIS on February 2, 2014. In the years since, AQ continued fostering local collaborations, including with al-Shabaab in Somalia and Boko Haram in Nigeria, while ISIS expanded beyond its Iraq/Syria base to control remote territories in Yemen, Afghanistan, and Pakistan. Given their more adversarial nature and efficient media usage, counterterror efforts focused on constraining ISIS, leading to concerns of indirectly strengthening AQ (13). Since imbalanced intervention may be ineffective (14), better understanding the interplay among groups may lead to strategies that do not inadvertently bolster any of them.
Materials and Methods
We examine the terrorist activities of AQ, ISIS, and local groups as listed by the GTD which cataloged global terrorist attacks between January 1, 1970 and December 31, 2017 (15). We mostly focus on the post-2014 era, when AQ disavowed ISIS.
Data Selection.
The GTD lists a maximum of three confirmed or suspected perpetrator groups per attack. We discard entries with unknown offenders (46% of the total). If at least one of the perpetrators is an AQ affiliate, the record is assigned to AQ and similarly for ISIS. If AQ and ISIS are responsible for the same attack, it is assigned to both. Finally, if neither is listed as the perpetrator, the record is assigned to the L class (local militias/insurgents). Affiliates were added to the AQ/ISIS classes only after their formal acceptance; since during 2004 to 2014 ISIS predecessors were recognized as AQ affiliates, their attacks within this period are assigned to both the AQ and ISIS classes. Full affiliate AQ/ISIS lists are in SI Appendix.
Cluster Analysis.
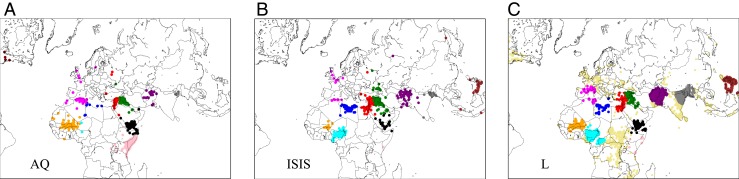
To examine the spatiotemporal distribution of AQ/ISIS attacks we first identify geographic areas where they colocalize, using -means clustering (16). The sole input here is attack location; no other constraints, such as state borders, are used (SI Appendix). We identify 12 clusters and determine the geographic centers and SDs of each. As shown in Fig. 1 A and B clusters are found to mostly coincide with geo-political boundaries, due to increased border security, attacks occurring in civic centers in the interior, or terrorist familiarity with terrain/culture. In some cases we observe spillover or domino effects, due to weak borders or historical/political precedents (17). The Afghan–Pakistan cluster arises due to militant groups residing between the two countries; the Syria cluster is found to include Lebanon due to the Syrian civil war spilling over to its neighbor; the Nigeria cluster includes small portions of neighboring Chad, Cameroon, and Niger, as Boko Haram attempted to evade government scrutiny; since AQ-affiliated al-Shabaab often launched attacks from Somalia into neighboring Kenya, the two form a unique cluster. Specific geographical conditions may thus allow terrorism to spread across borders. To add an L-class attack to one of the clusters identified above we calculate its distance from the center of the nearest AQ/ISIS cluster; if the distance is within three SDs from its center, the L-class attack is assigned to this cluster; otherwise it is discarded. The resulting distribution is shown in Fig 1C. The six clusters containing enough events to justify further analysis are listed in Table 1. We focus on them in the remainder of this work. Major and minor groups are labeled on the basis of their estimated number of combatants. The two major groups in Syria and Yemen are known rivals.
Fig. 1.
Color-coded geographic clusters of post-2001 AQ/ISIS attacks. Twelve clusters are identified via -means clustering for their attacks recorded in the GTD. Each cluster is labeled by the country with the majority of AQ/ISIS attacks: Iraq (green), Somalia (pink), Syria (red), Yemen (black), Nigeria (cyan), Pakistan/Afghanistan (purple), Libya (blue), Algeria/European Union (magenta), Mali (orange), Philippines (brown), Bangladesh (gray), and the United States (maroon). The above ordering follows the total number of AQ/ISIS attacks per cluster after the AQ-ISIS rift in 2014. Only the first six contain enough data for near-activity analysis. (A) AQ post-2014 activity in each cluster. (B) ISIS activity. Each solid circle represents one attack. (C) Post-2014 attacks perpetrated by local insurgent groups colocalizing with these 12 clusters using the same color codes, whereas attacks located outside the same 12 clusters are denoted by light yellow solid circles.
Table 1.
Active terrorist groups in six significant clusters and their relative strength as measured by estimated numbers of combatants
| Clusters | Major 1, no. of combatants | Major 2, no. of combatants | Minor, no. of combatants |
| Iraq | ISIS, 200,000 (35) | al-Naqshabandiya Army, 50,000 (36); PKK, 32,000 (37); Badr Brigades, 10,000 to 32,000 (38) | |
| Syria | ISIS, 200,000 (35) | The Islamic Front, 70,000 (39); Free Syrian Army, 40,000 to 50,000 (40); PKK, 32,000 (37) | AQ:JN, 5,000–10,000 (41) |
| Somalia | AQ:al-Shabaab, 7,000 to 9,000 (42) | ||
| Yemen | Houtis, 100,000 (43); Southern Movement, N/A | AQAP, 12,000 (44) | IS:Yemen Province, 300 (45) |
| Nigeria | IS:Boko Haram, 20,000 (46) | Fulani extremists, N/A | |
| Afghan-Pakistan | Taliban, 60,000 (47) | IS:Khorasan Chapter, 3,000 (48) |
Estimated numbers of combatants are shown; N/A indicates they are not available. Major 1 and Major 2 groups are known from journalistic reports to be in conflict. Only the most prominent groups of the L class are listed; attacks from smaller ones are also included in this study. References: Cockburn (35), Freeman (36), Tarihi (37), George (38), Hassan (39), Cockburn (40), Kareem (41), BBC News (42), Almasmari (43), Roggio (44), Aboudi (45), BBC News (46), Dawi (47), and Seldin (48).
Near-Repeat Analysis.
Terrorist events within each cluster are examined using near-repeat analysis tools developed in criminology (7–11). Near repetition within the “fixed-window” method is quantified by comparing the distribution of given data to a hypothetical distribution of random, independent events (9, 10). This is done by partitioning the given timespan into several windows of time ; within each window the time difference and the spatial distance between every pair of events are calculated. The time distribution for events occurring within a maximum distance is subsequently compiled from all windows. This data-derived distribution is then compared to the random-event hypothesis (REH)
| [1] |
Eq. 1 is the random probability distribution for finding a pair of events separated by a time interval within , assuming events are uniformly distributed. For example, if days, the probability of two events being separated by day is proportional to the number of pairs separated by 1 day in 1 week: Monday to Tuesday, Tuesday to Wednesday, through Saturday to Sunday, for a total of six possibilities. Conversely, there is only one possible pair of events separated by days, Monday to Sunday. is thus proportional to ; the normalization prefactor in Eq. 1 ensures that . Deviations from indicate a nonrandom likelihood for an event to repeat after a prescribed time . Contrasting observed distributions to is equivalent to performing a Knox ratio analysis (11, 18, 19). However, the latter requires sampling and Monte Carlo simulations to generate a randomized distribution for data comparison. Eq. 1 requires fewer assumptions and eliminates the need for simulations. We set weeks, guaranteeing all near-repeat effects are captured. February 2, 2014, the official AQ/ISIS rift date, is used as a starting point from which successive windows of periods are generated. To verify whether any biases were introduced, different values and start dates were used; results remained essentially unchanged. Same-day attacks are discarded, as it is not possible to determine whether they are part of a coordinated campaign or independent events (20).
Government Intervention.
Since government (G) activity is not part of the GTD, we utilize the Uppsala Conflict Data Program (UCDP) dyadic dataset (21) to obtain lists of state-sponsored counterterrorism events. These are then cross-listed with terrorist attacks from the GTD to study terrorist/counterterrorist interplay. Sufficient data exist only for Iraq, Somalia, and the Afghan–Pakistan clusters where government activities were targeted at ISIS, AQ, and the Taliban, respectively. We use post-2014 data for Iraq; post-2012 data for Somalia, when al-Shabaab joined AQ and the Federal Government of Somalia was established; and post-2003 data for the Afghan–Pakistan cluster, when the Taliban launched large-scale insurgencies against the Afghan government. There is not enough UCDP data for Nigeria or Syria (22); it is not possible to identify a legitimate government in Yemen due to the ongoing civil war.
Results
Al-Qaeda and ISIS Activities.
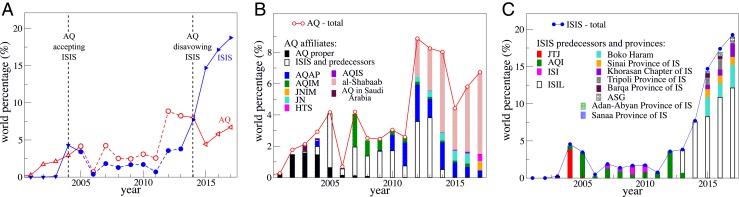
Terrorist attacks executed by AQ and ISIS between 2001 and 2017 are shown in Fig. 2A. Until 2011, AQ contributed to less than of global activity and the ISIS precursors even less. In 2012, AQ’s activities increased to roughly of world total, mostly fueled by ISIS and al-Shabaab as shown in Fig. 2B. After the 2014 AQ/ISIS rift the percentage of attacks by AQ proper stagnated, while ISIS’s activity grew rapidly, surpassing AQ to reach almost of world total in 2017. Fig. 2C shows that this increase is due to greater activity of ISIS proper, but also to the emergence of affiliate terrorist groups. AQ’s activities post-2014 are mostly due to al-Shabaab in Somalia. The distribution of terrorist attacks within the 12 geographical clusters identified in Fig. 1 is illustrated in Fig. 3A. In Iraq, AQ attacks mostly cease after the 2014 AQ/ISIS rift while concurrent AQ/ISIS activities persist in Syria and Yemen as also shown in the time-resolved plot in SI Appendix, Fig. S2. AQ is mostly absent in Nigeria, Libya, and the Philippines; ISIS is inactive in Somalia and in the United States. We also observe ISIS spreading from its Iraq base to neighboring countries through the terror “wave” in Fig. 3B. Here, the date of ISIS’s first attack in each cluster is plotted as a function of its distance from Iraq. The progressive spread of ISIS activities also emerges in SI Appendix, Fig. S3, where attacks are geo-spatially mapped over time. These findings are consistent with ISIS’s focus on expansion while AQ’s activities vary in a more random manner, consistent with its decentralized dune-like structure.
Fig. 2.
(A) AQ and ISIS terrorist activity as percentage of world total. Between 2004 and 2014 the AQ curve includes contributions from ISIS and its precursors. Pre-2004 data in the ISIS curve are due to JTJ, its first precursor; post-2014 data are attacks by ISIS operating independently from AQ. The limited activity in 2006 is most likely due to the great regional turmoil at the time, with the media (and the GTD) unable to identify attackers. Indeed, the total number of attacks in the Middle East increased from 2005 to 2006 but so did the number of incidents with unknown perpetrators. (B) Yearly AQ affiliate attacks. (C) Yearly ISIS affiliate attacks. Note the diverging trends after the 2014 AQ/ISIS rift.
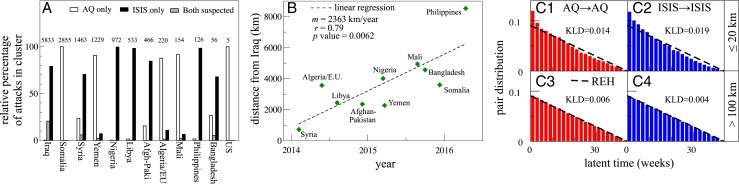
Fig. 3.
(A) Attack fractions per cluster attributable to AQ and ISIS, 2001 to 2017. (B) First ISIS attack dates per cluster vs. distance from Iraq post-2014. A linear regression yields a spread of roughly 2,400 km/y with correlation and a significant value of 0.006. (C) Near-repeat patterns for AQ AQ and ISIS ISIS worldwide, 2014 to 2017. Each bar contains data binned over 2 weeks. Deviations from the REH are estimated using KLD. (C1) The distribution of AQ AQ attacks separated by less than 20 km deviates from the REH over the first 4 weeks, indicating increased near-repeat likelihood. (C2) For ISIS ISIS attacks the enhanced repeat likelihood is over the first 10 weeks. (C3 and C4) AQ AQ and ISIS ISIS attacks separated by more than 100 km follow the REH, suggesting negligible correlation between repeat events.
Near-Repeat Activity.
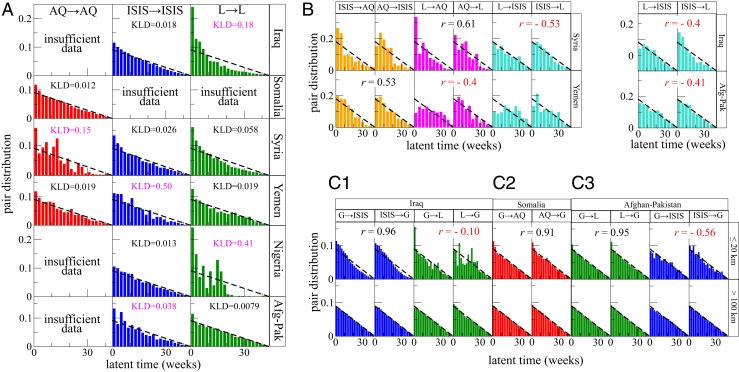
Near-repeat results are shown in Fig. 3C where we plot the latent time between every pair of AQ after AQ (i.e., AQ AQ) or ISIS after ISIS (i.e., ISIS ISIS) attacks separated by less than 20 km or more than 100 km, worldwide and post-2014. For comparison the REH distribution in Eq. 1 is also shown. We use the Kullback–Leibler divergence (KLD) (SI Appendix) to quantify the deviation of attack distributions from the REH. Fig. 3 C1 shows that during the first 4 weeks after an AQ attack, the probability for a near-repeat attack within 20 km is elevated with respect to the REH. ISIS exhibits an even longer period of elevated near-repeat probability within 20 km: 10 weeks, as shown in Fig. 3 C2. At distances beyond 100 km, near-repeat effects are negligible and the latent time distributions converge to the REH, as seen in Fig. 3 C3 and C4. Henceforth, we use 20 km as the maximal distance for near-repeat events. Only six of the clusters identified in Fig. 1 contain enough data for near-repeat analysis. Fig. 4A shows the resulting patterns after the 2014 AQ/ISIS rift. All panels show elevated near-repeat probability for at least 4 weeks. This period is extended for the minor group in a cluster, as identified in Table 1, which displays larger deviations from the REH, larger KLD values, and longer near-repeat periods compared to the major classes. The trend is consistent across clusters. For example, ISIS in Iraq and Syria, L (Taliban) in the Afghan–Pakistan region, L (Houthi and Southern Movement ethnopolitical rebels) in Yemen, and AQ (al-Shabaab) in Somalia are all major players and display enhanced repeat likelihood over 4 weeks. For ISIS (Boko Haram) in Nigeria the period is 6 weeks. In clusters where minor players are also present, they always display longer periods of enhanced near repeat compared to the major groups listed above. The longest period is 14 weeks for ISIS, the minor player in Yemen.
Fig. 4.
(A) Near-repeat patterns AQ AQ, ISIS ISIS, and L L, in six clusters post-2014. Each bar contains data binned over 2 weeks; all pairs of events are separated by less than 20 km. Heightened near-repeat likelihood is observed at least over the first 4 weeks in all panels. Near-repeat tendencies are more prominent for the minor classes, as indicated by their KLD values shown in magenta. (B) Near-reaction patterns A B, B A, where in clusters where their post-2014 activities overlap. The first class in each panel is the first to attack; the second one responds within 20 km after the given latent time. Each bar contains data binned over 4 weeks. The correlation coefficient between mirror panels is included for moderate correlation (). All known major rivals within each cluster show negative correlation. Panels showing positive correlation either are allies (AQ and L, Syria) or share ideology (AQ and ISIS, Yemen). (C1–C3) Terrorist/government (G) near-reaction patterns. In each cluster the correlation coefficient between G and the main class (ISIS in Iraq, AQ in Somalia, and L in the Afghan–Pakistan cluster) is shown in black. Each bar contains data binned over 2 weeks. Large values suggest strong interplay. (C1) In Iraq, ISIS intensifies its activity compared to the REH after G intervention over 4 months; G increases its activity over 4.5 months after ISIS attacks. The agile L class responds to the same G operations by intensifying its attacks over 2 weeks. No consistent patterns arise in L G as can be expected. (C2) In Somalia similar trends arise with enhanced AQ activity after G intervention (4 weeks); G also increases its activity in response to AQ (4 weeks). (C3) In the Afghan–Pakistan cluster near reaction is enhanced in the G L (4 weeks) and L G (6 weeks) panels where L is the Taliban. Although data are limited, we observe a delayed response from ISIS and an asymmetric G ISIS and ISIS G dynamic with , typical of near-repeat patterns involving transnational groups. Events separated by more than 100 km follow the REH. Panels with less than 100 data points are not analyzed due to insufficient data. The L classes are as listed in Table 1.
Near-Reaction Activity.
To analyze the post-2014 interplay among AQ, ISIS, and the L groups in each cluster we consider the latent time distribution for A B events where a class A attack is followed by a class B attack within 20 km for and A B. We do not expect symmetry between the A B and B A panels as power structures may be imbalanced. We omit Somalia, with no significant ISIS or L presence, and Nigeria where attacks by ISIS (Boko Haram) and l-class Fulani extremists display negligible overlap within 20 km. Fig. 4B shows data deviating significantly from the REH in all clusters, indicating enhanced or hindered near reaction. To interpret these results and determine whether the order in which the A,B classes strike and respond is relevant, we calculate the Shannon entropy contribution for each of the A B and B A datasets in Fig. 4B. The terms allow us to compare datapoints from Fig. 4B with the corresponding REH where as evaluated from Eq. 1. Finally, the correlation coefficient between the two derived datasets and is calculated. We find that within each cluster, only one of the A B, B A panels is marked by appreciable negative correlation (, in red). The respective classes are as follows: in Iraq, = ; in Syria, = ; in Yemen, = ; in Afghan–Pakistan, . The two parties involved are always either AQ or ISIS (global organizations) and the local l class and are always known to be in conflict. Table 1 indicates that in all cases the two above classes are also the largest in their clusters. Our finding of a negative correlation suggests that an l-class group responds promptly to an attack by AQ or ISIS while the latter’s response is delayed. If a third class is present, it is always the minor player listed in Table 1 and either collaborates (such as AQ and l-class rebels in Syria) or shares a similar ideology (such as AQ and ISIS in Yemen) with either of the two major ones. Fig. 4B shows that the minor party always correlates positively with the major player it aligns with. Correlations between the minor group and the other major player are not significant, indicating that the major player neglects its smaller adversary to focus on its main rival. These findings are consistent across surveyed clusters and emerge for pre-2014 data as well (SI Appendix).
Government Intervention.
We examine terrorist/state interplay in the Iraq, Somalia, and Afghan–Pakistan clusters in Fig. 4 C1–C3. In Iraq, the post-2014 G (UCDP data) ISIS (GTD data) and ISIS G near-reaction panels show both parties displaying enhanced near response within 20 km over several months. There are no data for government action explicitly aimed at the l class in Iraq; however, we can examine whether government operations directed at ISIS indirectly affect l-class activities. Thus, in Fig. 4 C1 we also study G L (GTD data) near-reaction activity. L responses spike for 2 weeks after G action, most likely as a short-lived immediate reaction to any nearby event, regardless of intended targets. No clear L G trends emerge, implying that government activity aimed at ISIS is not influenced by prior l-class activities. Similar trends are observed for the G AQ and AQ G post-2012 panels in Fig. 4 C2 for Somalia, where no l-class group is present, and in the G L and L G post-2003 panels in Fig. 4 C3 for the Afghan–Pakistan cluster (L here is the Taliban). We also include near reaction between the small ISIS group present in the Afghan–Pakistan cluster and government interventions aimed at the Taliban. Despite the small sample size of the ISIS attacks, the asymmetry between the G ISIS and ISIS G panels in Fig. 4 C3 is in agreement with earlier observations of delayed responses by global groups. Large correlation values in all clusters indicate strong interplay between terrorist and state actors, each aiming to signal their own supremacy. Except for Somalia, state operations persist slightly longer than terrorist activity.
Discussion
Near-repeat patterns, often observed in urban crime, also emerge for terrorist attacks by AQ, ISIS, and mostly all other contemporary insurgent groups, despite heterogeneous local conditions. The corresponding spatiotemporal scales (20 km and 4 to 10 weeks) are larger than for urban crime, where effects persist over a few hundred meters for 2 to 6 weeks (6, 9, 10). This may be due to terror attacks being more impactful in terms of damage, media coverage, and psychological effects; longer times may also be required to orchestrate repeat events. Spatial clustering reveals territorial effects. For example, AQ displays a longer period of elevated near repeat than ISIS in Syria, but the trend is reversed in Yemen. In both cases, the minor organization exhibits more prominent near-repeat activity than the major one, a consistent finding in this work. Why? We note that numerically inferior groups may need to act more frequently to maintain visibility, especially in the presence of more established organizations. This is in agreement with game-theoretic studies whereby sustained violence allows small groups of radicals to stay relevant and grow (23). Near-reaction patterns between major rivals in the same cluster show asymmetric behavior. Typically, one of the two global terrorist organizations (AQ or ISIS) is in conflict with local militias/insurgents which respond promptly to AQ or ISIS attacks. Conversely, the response of the global terror group is delayed in time. This asymmetric behavior may be due to local militias having the agility and need to respond quickly, whereas global terror groups may require longer decisional times. The remaining group, typically with the least number of combatants, tends to align itself with one of the major ones, executing copycat or supportive attacks. These aligned parties may be engaged in a leader–follower relationship, the minor party may be a supportive ally of the major one, or the two may be neutral, nonhostile entities united by the same ideology or intent against the same rival. The trend is consistent with social balance theory which posits that in a triadic relationship where two entities are already in conflict, the only balanced position the third one can adopt is to align itself with one and oppose the other (24). Recent studies on urban gangs confirm similar dynamics (25). This triadic pattern is manifest in Syria, where post-2014, AQ affiliate JN began supporting the l-class antigovernment rebels, leading to ISIS L rivalry/negative (r/n) correlation, AQ L aligned/positive (a/p) correlation, and weak AQ ISIS correlation. In Yemen, al-Qaeda in the Arabian Peninsula (AQAP) has been a longtime opponent to local insurgents, whereas ISIS established its provinces there in 2015. AQ and ISIS are rivals but both regard insurgent groups as their primary enemies, leading to AQ L r/n correlation, AQ ISIS a/p correlation, and weak ISIS L correlation. In the Afghan–Pakistan region, AQ has mainly assisted the Taliban; as ISIS attempted to gain territory, it engaged in open conflict with the Taliban. We thus observe ISIS L (Taliban) and ISIS AQ r/n correlation. There are not enough data to compare AQ and the Taliban. In Iraq, there is no AQ presence post-2014, so we observe only ISIS L (ethnoreligious militias) r/n correlation. We find no evidence of outbidding (26) in the form of escalating responses under provocation or when casualties are involved (SI Appendix), consistent with existing studies (27, 28). State and terrorist actions are strongly correlated, with long-term near-reaction deviations from the REH (SI Appendix). This indicates both parties prioritize overcoming the other and questions the immediate efficacy of state-sponsored military action. Interestingly the G ISIS panel in Iraq is the only one where ISIS does not show a delayed response, suggesting that when priorities or clear enemies arise, ISIS does have a fast reaction capability.
Conclusion
We studied the spatiotemporal patterns of terrorist attacks by AQ, ISIS, and local militias/insurgents by applying data-driven, unsupervised -means clustering to the GTD. While near-repeat/reaction patterns are observed in all clusters (29–31), the accompanying variations highlight the territorial aspects of terrorism (32) and the role played by local hierarchies, even when global terrorist groups are present. Near-repeat duration, intergroup dynamics, and government response depend more on a group’s relative size and on its local relation to other groups than on whether or not it is part of a transnational organization. Understanding the local aspects of terrorism may help policymakers better plan timing, permanence, and expectations of antiterrorism intervention. Our correlative observations can help shape statistically optimal resource allocation and logistics to more efficiently respond to future attacks. Possible extensions could include constructing poly-order chains of events to distinguish attack methods and weapon/target types to further refine the understanding of repeat activity and the design of response protocols (33, 34).
Supplementary Material
Acknowledgments
We acknowledge support from the Army Research Laboratory through grant ARL W911NF-16-2-0113 (to N.B.-A.), from the Army Research Office through grant ARO W911NF-16-1-0165 (to M.R.D), and from the National Science Foundation through grant DMS-1814090 (to M.R.D.). We thank V. Asal, A. Moghadam, and E. Miller for helpful discussions and the reviewers for valuable feedback. The views and conclusions contained in this document are those of the authors and should not be interpreted as representing the official policies, either expressed or implied, of the Army Research Laboratory or the US Government. The US Government is authorized to reproduce and distribute reprints for government purposes notwithstanding any copyright notation herein.
Footnotes
The authors declare no conflict of interest.
This article is a PNAS Direct Submission.
This article contains supporting information online at www.pnas.org/lookup/suppl/doi:10.1073/pnas.1904418116/-/DCSupplemental.
References
- 1.Watts C., Deciphering competition between al-Qa’ida and the Islamic State. CTC Sentinel 9, 1–6 (2016). [Google Scholar]
- 2.Hashim A. S., The Islamic State: From al–Qaeda affiliate to Caliphate. Middle East Policy 21, 69–83 (2014). [Google Scholar]
- 3.Zelin A. Y., The War between ISIS and Al-Qaeda for Supremacy of the Global Jihadist Movement (The Washington Institute for Near East Policy, Washington, DC, 2014). [Google Scholar]
- 4.Lassalle K., Ozkaya E., Akgul B., Light years ahead: Differences and similarities between al-Qaeda and Islamic State’s approach to the global jihad. Rev. Int. Law Polit. 12, 41–74 (2016). [Google Scholar]
- 5.Roul A., Fertile ground for al-Qa’ida and the Islamic State. CTC Rep. 9, 27–34 (2016). [Google Scholar]
- 6.Johnson S. D., et al. , Time patterns of risk: A cross national assessment of residential burglary victimization. J. Quant. Criminol. 3, 201–219 (2007). [Google Scholar]
- 7.Townsley M., Johnson S. D., Ratcliffe J. H., Space-time dynamics of insurgent activity in Iraq. Secur. J. 21, 139–146 (2008). [Google Scholar]
- 8.Johnson S. D., Braithwaite A., “Spatio-temporal modeling of insurgency in Iraq” in Reducing Terrorism through Situational Crime Prevention, Freilich J. D., Newman G. R., Eds. (Criminal Justice Press, Monsey, NY, 2009), pp. 9–32. [Google Scholar]
- 9.Short M. B., D’Orsogna M. R., Brantingham P. J., Tita G. E., Measuring and modeling repeat and near-repeat burglary effects. J. Quant. Criminol. 25, 325–339 (2009). [Google Scholar]
- 10.Short M. B., Brantingham P. J., Bertozzi A. L., Tita G. E., Dissipation and displacement of hotspots in reaction-diffusion models of crime. Proc. Natl. Acad. Sci. U.S.A. 107, 3961–3965 (2010). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Ornstein J. T., Hammond R. A., The burglary boost: A note on detecting contagion using the Knox test. J. Quant. Criminol. 33, 65–75 (2017). [Google Scholar]
- 12.Mishal S., Rosenthal M., Al Qaeda as a dune organization: Toward a typology of Islamic terrorist organizations. Stud. Confl. Terror. 28, 275–293 (2005). [Google Scholar]
- 13.Rollins J., Perspective, Global Presence, and Implications for U.S. Policy (Congressional Research Service, Washington, DC, 2011). [Google Scholar]
- 14.Gao J., Fang P., Liu F., Empirical scaling law connecting persistence and severity of global terrorism. Physica A 482, 74–86 (2017). [Google Scholar]
- 15.National Consortium for the Study of Terrorism and Responses to Terrorism (START) , Global Terrorism Database [Data file]. https://www.start.umd.edu/gtd. Accessed 1 February 2019.
- 16.MacQueen J., “Some methods for classification and analysis of multivariate observations” in Proceedings of the Fifth Berkeley Symposium on Mathematical Statistics and Probability, Le Cam L. M., Neyman J., Eds. (University of California Press, Berkeley, CA, 1967), vol. 1, pp. 281–297. [Google Scholar]
- 17.LaFree G., Xie M., Matanock A. M., The contagious diffusion of worldwide terrorism: Is it less common than we might think? Stud. Confl. Terror. 41, 261–280 (2018). [Google Scholar]
- 18.Knox G., Epidemiology of childhood leukaemia in Northumberland and Durham. Br. J. Prev. Soc. Med. 18, 17–24 (1964). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 19.Braithwaite A., Johnson S. D., Space-time modeling of insurgency and counterinsurgency in Iraq. J. Quant. Criminol. 28, 31–48 (2012). [Google Scholar]
- 20.Deloughery K., Simultaneous attacks by terrorist organisations. Perspect. Terrorism 7, 79–89 (2013). [Google Scholar]
- 21.Sundberg R., Melander E., Introducing the UCDP geo-referenced event dataset. J. Peace Res. 50, 523–532 (2013). [Google Scholar]
- 22.Högbladh S., UCDP GED Codebook version 19.1 (Department of Peace and Conflict Research, Uppsala University, Uppsala, Sweden, 2019).
- 23.Short M. B., McCalla S. G., D’Orsogna M. R., Modelling radicalization: How small violent fringe sects develop into large indoctrinated societies. R. Soc. Open Sci. 4, 170678 (2017). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Heider F., Attitudes and cognitive organization. J. Psychol. 21, 107–112 (1946). [DOI] [PubMed] [Google Scholar]
- 25.Nakamura K., Tita G., Krackhardt D., Violence in the balance: A structural analysis of how rivals, allies, and third-parties shape inter-gang violence. Global Crime, 10.1080/17440572.2019.1627879 (2019). [DOI] [Google Scholar]
- 26.Bloom M., Dying to Kill: The Allure of Suicide Terror (Columbia University Press, New York, NY, 2005). [Google Scholar]
- 27.Findley M. G., Young J. K., More combatant groups, more terror? Empirical tests of an outbidding logic . Terror. Polit. Violence 24, 706–721 (2012). [Google Scholar]
- 28.Hamming T. R., The Al Qaeda-Islamic State rivalry: Competition yes, but no competitive escalation. Terrorism Polit. Violence, 10.1080/09546553.2017.1342634 (2017). [DOI] [Google Scholar]
- 29.Lewis E., Mohler G., Brantingham P. J., Bertozzi A. L., Self-exciting point process models of civilian deaths in Iraq. Secur. J. 25, 244–264 (2012). [Google Scholar]
- 30.White G., Porter M. D., Mazerolle L., Terrorism risk, resilience and volatility: A comparison of terrorism patterns in three Southeast Asian countries. J. Quant. Criminol. 29, 295–320 (2013). [Google Scholar]
- 31.Tench S., Fry H., Gill P., Spatio-temporal patterns of IED usage by the provisional Irish Republican army. Eur. J. Appl. Math. 27, 377–402 (2016). [Google Scholar]
- 32.Braithwaite A., Li Q., Transnational terrorism hot spots: Identification and impact evaluation. Conflict Manag. Peace Sci. 24, 281–296 (2007). [Google Scholar]
- 33.Behlendorf B., LaFree G., Legault R., Microcycles of violence: Evidence from terrorist attacks by ETA and the FMLN. J. Quant. Criminol. 28, 49–75 (2012). [Google Scholar]
- 34.Haushofer J., Biletzki A., Kanwisher N., Both sides retaliate in the Israeli Palestinian conflict. Proc. Natl. Acad. Sci. U.S.A. 107, 17927–17932 (2010). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 35.Cockburn P., War with ISIS: Islamic militants have army of 200,000, claims senior Kurdish leader. The Independent, 16 November 2014. https://www.independent.co.uk/news/world/middle-east/war-with-isis-islamic-militants-have-army-of-200000-claims-kurdish-leader-9863418.html. Accessed 12 September 2019.
- 36.Freeman C., Izzat Ibrahim al-Douri: The King of Clubs is back, and he may yet prove to be Saddam Hussein’s trump card. The Telegraph, 18 May 2013. https://www.telegraph.co.uk/news/worldnews/middleeast/iraq/10065919/Izzat-Ibrahim-al-Douri-the-King-of-Clubs-is-back-and-he-may-yet-prove-to-be-Saddam-Husseins-trump-card.html. Accessed 12 September 2019.
- 37.Tarihi G., The PKK in numbers. Sabah, 29 December 2015. https://www.sabah.com.tr/galeri/turkiye/iste-pkkli-hainlerin-il-il-dagilimi/85. Accessed 12 September 2019.
- 38.George S., Breaking Badr. Foreign Policy, 6 November 2015. https://foreignpolicy.com/2014/11/06/breaking-badr/. Accessed 12 September 2019.
- 39.Hassan H., Front to back. Foreign Policy, 4 March 2014. https://foreignpolicy.com/2014/03/04/front-to-back/. Accessed 12 September 2019.
- 40.Cockburn P., West suspends aid for Islamist rebels in Syria, underlining their disillusionment with those forces opposed to President Bashar al-Assad. The Independent, 11 December 2013. https://www.independent.co.uk/news/world/middle-east/west-suspends-aid-for-islamist-rebels-in-syria-underlining-their-disillusionment-with-those-forces-8998891.html. Accessed 12 September 2019.
- 41.Schmitt E., Al Qaeda turns to Syria, with a plan to challenge ISIS. The New York Times, 15 May 2016. https://www.nytimes.com/2016/05/16/world/middleeast/al-qaeda-turns-to-syria-with-a-plan-to-challenge-isis.html. Accessed 12 September 2019.
- 42.Who are Somalia’s al-Shabab? BBC News, 22 December 2017. https://www.bbc.com/news/world-africa-15336689. Accessed 12 September 2019.
- 43.Almasmari H., Medics: Militants raid Yemen town, killing dozens. CNN, 27 November 2011. https://edition.cnn.com/2011/11/27/world/meast/yemen-clashes/index.html. Accessed 12 September 2019.
- 44.Roggio B., Al Qaeda prepares “an army of 12,000 fighters,” threatens security forces. FDD’s Long War Journal, 30 July 2010. https://www.longwarjournal.org/archives/2010/07/al_qaeda_prepares_an.php. Accessed 12 September 2019.
- 45.Aboudi S., In Yemen chaos, Islamic State grows to rival al Qaeda. Reuters, 30 June 2015. https://www.reuters.com/article/us-yemen-security-islamicstate-insight/in-yemen-chaos-islamic-state-grows-to-rival-al-qaeda-idUSKCN0PA1T920150630. Accessed 12 September 2019.
- 46.Boko Haram HQ Gwoza in Nigeria “retaken.” BBC News, 27 March 2015. https://www.bbc.com/news/world-africa-32087211. Accessed 12 September 2019.
- 47.Dawi A., Despite massive Taliban death toll no drop in insurgency. Voice of America, 6 March 2014. https://www.voanews.com/east-asia/despite-massive-taliban-death-toll-no-drop-insurgency. Accessed 12 September 2019.
- 48.Seldin J., Afghan officials: Islamic State fighters finding sanctuary in Afghanistan. Voice of America, 18 November 2017. https://www.voanews.com/east-asia-pacific/afghan-officials-islamic-state-fighters-finding-sanctuary-afghanistan. Accessed 12 September 2019.
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.