Abstract
Background
Electroencephalogram (EEG) signals of a brain contain a unique pattern for each person and the potential for biometric applications. Authentication and security is a very important issue in our life and brainwave-based authentication is an addition to biometric authentication systems, which has many advantages over others. In this paper, we study the performance of a single channel brainwave-based authentication systems and select optimum channels based on mental activities.
Methods
In this study, we used a dataset with five mental activities with seven subjects (325 samples). The EEG based authentication system includes three pre-processing steps, feature extraction, and classification. Features for Subject Authentication, are obtained from discrete Fourier transform, discrete wavelet transform, autoregressive modeling, and entropy features. Then these features are classified using the Neural Network, Bayesian network and Support Vector Machine.
Results
We achieved accuracy in the range of 97–98% mean accuracy with Neural Network classifier for single-channel authentication system with optimum electrode placement for mental activity. We also analyzed the authentication system independently from the type of mental activity and chose channel O2 as the optimum channel with an accuracy of 95%.
Conclusions
Channel optimization can obtain higher performance by reducing the number of EEG channels and defined the optimum electrode placement for different mental activities.
Keywords: Authentication, Electroencephalogram (EEG), Biometric, Single-channel, Signal processing, Security
At a glance commentary
Scientific background on the subject
Authentication and security have great importance in various life fields. Electroencephalogram (EEG) contains a unique pattern for each person and the potential for biometric applications and cannot be faked or duplicated.
What this study adds to the field
Authentication systems should make a balance between user-friendliness and security. Most of these systems used 32, 64 or more channels that are high-cost and bounded mobility of the users. Single-channel systems could provide user-friendliness and selecting channels placement based on mental activities could provide security with increasing accuracy.
Each system needs types of authentication for providing its security. The traditional form of authentication, like using passwords, PINs are losing attraction because they are vulnerable to falsification as it is possible to forge or steal. Biometric-based ways which are referred to ways that use personal biological features like iris pattern, fingerprint is being used much more in new usages. Recently, attention has been drawn to the use of electrical medical signals for biometric applications. Examples of these signals are the Electroencephalographic Signal (EEG) [1] and Electrocardiogram (ECG) [2].
One of the effective ways for authentication purpose is Electroencephalogram (EEG) recordings. EEG is the electrical activity of the brain which is recorded by measuring the voltage fluctuations on the scalp surface with simple placement of the electrodes on the skin [3]. It is measured by placing electrodes on several locations on the scalp. The uniqueness of EEG is the main advantage of using it; the electrical activities and brain signals are different for each person and cannot be faked or duplicated [4], [5]. Performing a behavioral activity or task in an emergency will result in a change in the brain signals due to emotional stress [6]. This property also makes EEG more secure because it's difficult to obtain them under force and threat [4]. There are other advantages of EEG over other biometric-based features i.e. they aren't visual and can't be stolen by others. Also, one important advantage over other biometrics is that the person must be alive during the process of recording signals. EEG signals are very dependent on person's mood so even if the mental activity is the same the result is different for different persons [1].
EEG-based methods for authentication are getting popular these days. In 1980, EEG signals have been used for the first time for automatic user recognition [7]. Palaniappan et al. proposed a two-stage threshold method to verify five subjects on 6 channels based on the features of autoregressive coefficients (AR), channel spectral powers and inter-hemispheric channel spectral power differences (IHPD), inter-hemispheric channel linear complexity (IHLC), and non-linear complexity. False reject error (FRE) for this method was in the range of 0–1.5% [8]. He et al. introduced a system with 4 subjects based on Multi-variate autoregressive (mAR) features, naïve Bayes classifier and obtained half total rate (HTER) of 6.7% [9].
Marcel et al. implemented a statistical framework with a Gaussian mixture model (GMM) and maximum a posteriori (MAP) estimation. These were used for authenticating 9 subjects, achieving HTER as low as 6.6% [4]. Yeom et al. used 10 subjects and got an accuracy of 86.1% using the visual stimuli related to the face of individuals [10]. Garima Bajwa et al. used EEG signals for authenticating using the same database that uses in this paper. They used discrete Fourier transform and discrete wavelet transform for feature extraction process and Bayesian network and Support Vector Machine classifiers. Finally obtained 98.46% mean accuracy, by combining the extracted features from Fourier transform and Wavelet transform [6]. Ying Zeng et al. combine two kinds of biometric trait, face and EEG an authentication method based on Hierarchical Discriminant Component Analysis and Genetic Algorithm is proposed to build a subject-specific model with optimized fewer channels. The averaged authentication accuracy of 94.26%. For a 30-day averaged time interval, their method can still reach the averaged accuracy of 88.88% [11]. Thomas et al. used band power features extracted from alpha, beta and gamma bands. During online authentication, recorded test EEG pattern is matched with the template that generated during enrollment and degree of matching in terms of its correlation coefficient predicts the genuineness of the claimant, and achieves an average recognition rate of 88.33% using 14 EEG channels and 6 subjects [12].
Most of these works have done for clinical purposes or used high-density EEG systems with access to 32, 64, 128, or even more channels of EEG data. These type of systems can provide good space-time resolution of brain activities but they are high-cost and also they bound mobility of the user in real-life scenarios. Only a few studies with high performance have reported for single channel EEG authentication systems. Koike-Akino et al. achieved an accuracy of 96.7% by joint classification of multiple epochs [13]. Recently Chuang et al. did another research using single channel EEG data on 15 subjects and accuracy of their authentication system in verification mode was more than 99% [14].
Authentication systems should make a balance between user-friendliness and security in practical applications [14]. In this paper, we introduced a single channel authentication system with high accuracy. The system is based on different mental activities and uses different machine learning algorithms for classification with the decreased error for practical applications.
Most of the current authentication systems are based on multi-channel or less reliability in user recognitions. authentication systems should make a balance between user-friendliness and security in practical applications [14]. In this paper, we introduced a single-channel authentication system with high accuracy. The system is based on different mental activities and uses different machine learning algorithms for classification with the decreased error for practical applications.
Materials and methods
Experimental data
Dataset used in this work has been gathered by Keirn and Aunon [15]. This set contains EEG signals which have been recorded from seven subjects with five different mental tasks. Tasks have been chosen in consideration of hemispheric brainwave asymmetry.
Above mentioned five tasks are described as follows:
-
1.
Baseline Task: The subjects were asked not to do any mental task and rest with very few movements and not to think of anything.
-
2.
Letter Task: subjects were instructed to compose a letter to a friend or a relative without spelling the words (no vocalizing).
-
3.
Math Task: A picture of some multiplication problems has been shown to the subjects. For example, it can be 78 × 49. Subjects were asked to solve it without any physical movement or vocalizing the answer.
-
4.
Geometric Figure Rotation: subjects were taught to visualize a particular 3-D geometric figure which is spinning around an axis.
-
5.
Visual Counting: subjects were asked to imagine a blackboard and think that multiple numbers were written on it sequentially.
Signals were recorded from six channels, C3, C4, P3, P4, O1, O2 and placing the electrodes was done using the 10–20 standard system. Sampling rate of data recording was 250 HZ. Blinking was detected by two electrodes which have been placed below and above the subject's left eye. All tasks were done with the subject's eyes open.
First subject was a left-handed person with age 48 and the other one was a right-handed 39 years old person. Both were an employee of the university. Subjects 3–7 were right-handed university students with age 20–30. All subjects were male except subject 5.
All 5 trials of a task were done on the same day. The duration of each task was 10 seconds and subjects returned in another day for doing the next tasks. Subjects 2 and 7 completed one session consist of five trials, subject 5 did three sessions and all others did them 2 sessions.
Preprocessing
In this step, a bandpass filter (0.1–64 Hz) was applied on recorded signals in order to reduce noise effects. Also for getting a better result and using data in its best performance, each record was divided into 10 segments and each segment was 1 second with 250 samples. In this way, feature extraction methods were applied on each 1 second segment and the feature vector of each trial was obtained combining all the features of the 10 segments.
Feature extraction
Fourier Transform and power spectrum density
Fourier Transform is one of the non-parametric feature extraction techniques for EEG signals [1] and signal power spectrum is one of the most common signal representations in the frequency domain. Hence the spectrum estimation is one of the most commonly discussed issues in defining and extracting the features of the signals [1].
EEG signals are divided into five standard sub-bands, Delta (1–4 Hz), Theta (4–8 Hz), Alpha (8–12 Hz), Beta (12–30 Hz) and Gamma (30–44 Hz) frequencies. In this paper, time domain signals were converted to the frequency domain using Fast Fourier Transform (FFT), which is an efficient algorithm for calculating DFT. FFT was applied to all channels to obtain the frequency spectrum. Then, by averaging this value on the EEG standard bands, five features were obtained for each channel and also the power of each frequency band from 1 to 44 Hz was calculated.
Wavelet transform
In this paper, Discrete Wavelet Transforms (DWT) from the Daubechies family of wavelets (Daubechies's versions of "db8") have been used to extract the features. The signal decomposition into its details and approximate coefficients was achieved by applying a series of high-pass and low-pass filters to the signal. Unlike the FFT, DWT displays a time-frequency representation of the signal and helps in analyzing signals which suffer from discontinuity or severe changes [6].
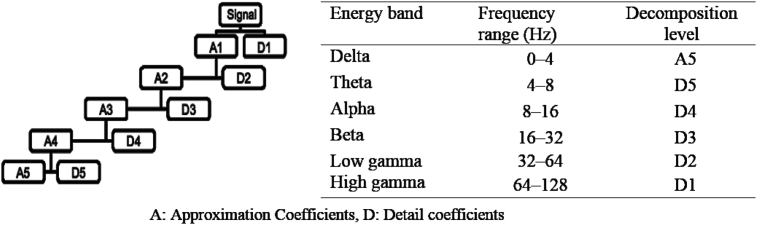
[Fig. 1] shows the Wavelet decomposition tree at five levels and relationship between the EEG standard bands and the Wavelet decomposition tree.
Fig. 1.
Relationship between the EEG standard bands and the Wavelet decomposition tree [6].
For the purpose of deriving features by DWT, instead of using all the coefficients at each decomposition level, the mean of the absolute value of the coefficients, average power of wavelet coefficients, the standard deviation of coefficients and Shannon entropy of coefficients were extracted from the wavelet coefficients at each subband.
Autoregressive modeling
In autoregressive modeling, the amount of signal in each moment was defined by a linear combination of the white noise and signal's amount in previous moments.
The mathematical expression x [k] was modeled Eq. (1).
| (1) |
In Eq. (1) e [k] is Gaussian white noise. Coefficients of this linear combination (αi) are parameters of the model. These coefficients are directly considered as features [16]. In this paper, p was selected as 10.
Log energy entropy
Log Energy Entropy can clearly illustrate the complexity of the signal in time and show the spectral feature of the signal.
If represent the distribution of energy in N samples of the spectrum in each frequency band. Probability distribution function denoted by and defined as Eq. (2)
| (2) |
The log energy entropy of E is obtained from Eq. (3), [17].
| (3) |
Sample entropy
Sample entropy is a revised version of the approximate entropy and is less sensitive to noise and can be applied for short-length time series of data. Sample entropy can be defined as the negative logarithm of the probability of two sequences that are similar in m points. The condition which must be considered is that they remain similar at the next point, where self-matches are not included in calculating the probability. This similarity is calculated by considering tolerance as . To calculate sample entropy, the time series is expressed in an m-dimensional space with vectors of length m as Eq. (4):
| (4) |
For vectors in length of m, is the probability of sharing two sequences in m points, which is obtained by counting the average number of vectors with Euclidean distance less than (In this paper the value of r is set to 0.1). The same procedure is repeated by incrementing the vector and calculating the probability of for same as calculating the [18] Eq. (5) shows the exact definition:
| (5) |
Classification
Support Vector Machine (SVM)
Support Vector machine is one of the best and popular machine learning techniques for accuracy prediction [19]. The main idea behind the SVM is the assumption that the classes are separated linearly and they can create hyper-plain that can separate the classes. In cases where the data is not linearly separable non-linear mathematical functions are used which are known as kernel functions. In this case, data are mapped to a higher-dimensional space to be linearly separable [20]. One of the problems which can be mentioned about SVM is that it is still unclear how the kernel and its parameters are determined. The choice of a suitable kernel and its parameters depend on the nature of the data and is determined empirically [19].
Bayesian network
Naive Bayesian classifier is one of the most effective classifiers. This classifier learns from the conditional probability of Ai as a training dataset attribute, given the class label C. Bayes rule is applied in order to do the classification. The rule is applied to compute the probability of C given the particular instance of A1, A2,…, An and then predicting the class with the highest posterior probability. Simplification of This computation is possible using a strong independence assumption: all the training dataset attribute (Ai)are conditionally independent given the value of the class C [21].
Neural network
Neural networks are composed of interconnecting artificial neurons and modeling the brain of human. Various neural network architecture has been introduced for different functions, one of the most popular architecture is the feedforward network. Feedforward network is commonly known for its ability in pattern recognition, predicting and fitting nonlinear function [22].
Results
In the authentication systems, first the EEG signals are recorded for all subjects and tasks, and after the pre-processing step, the appropriate features are extracted. The combined feature vector for one of the ten segments of one trail of the single electrode for each subject had 85 features, containing (44 + 5) FFT features, 24 DWT features, one Log Energy entropy feature, one sample entropy feature and 10 autoregressive coefficients. Given that each ten-second trail of the signal is divided into ten one-second parts, the feature vector for each trail will be 850 feature.
In this paper polynomial kernel function for SVM classifier is used with Polynomial Order = 1 with 70% training data and 30% test data, and for training step of feedforward neural network classifier two sets of data are required.
-
•
Input data: represents the extracted features of the signal
-
•
Target data: defines the desired output of the neural network (labels of feature vectors that represent the signal class and the person whose signal is recorded.)
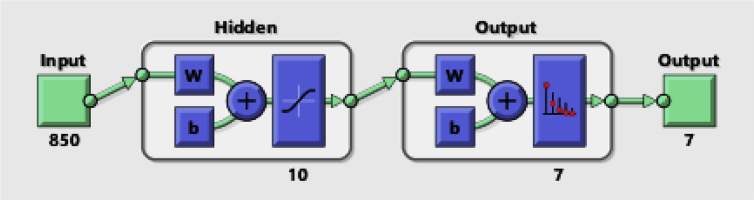
Network setup that gives the best performance is in form of 70% training data, 10% validation and 20% testing data. 1 hidden layer with 10 neurons is used to obtain the best cross entropy in the neural network training GUI. The architecture of the neural network is shown in [Fig. 2]. In this study, the number of outputs (number of subjects) is 7 and the number of inputs is 850 (number of extracted features). The transfer function for hidden layer is tan-sigmoid and activation function for output layer is softmax.
Fig. 2.
Architecture of the neural network.
Training parameters for Neural Network are shown in [Table 1]. Training stops when any of the parameters are fulfilled.
Table 1.
Neural network training parameters.
| Maximum number of epochs | 1000 |
|---|---|
| Minimum performance gradient | 0.000001 |
| Performance goal | 0 |
| Maximum validation failures | 100 |
In the classification step, k-fold cross validation has been used with k = 5. Also, to evaluate the results of the classification, two criteria of accuracy and f-score Measures were derived from the confusion matrix to evaluate the performance of the models using the flowing metrics:
| (6) |
| (7) |
| (8) |
| (9) |
TP: True Positive, TN: True Negative, FP: False Positive, FN: False Negative.
Another important criterion used to determine the efficiency of a classifier is the AUC criterion. The area under the curve or AUC is equal to the probability that a classifier will rank a randomly chosen positive instance higher than a randomly chosen negative one [23].
Accuracy and F-score for all electrodes and tasks are calculated as single-channel. The results are averaged and are shown in [Table 2].
Table 2.
Mean and standard deviation of accuracy and F-score for 6 electrodes and all tasks.
| Classifier | Accuracy (%) |
Mean F-score |
||
|---|---|---|---|---|
| Average | Standard deviation | Average | Standard deviation | |
| SVM | 84.49 | 5.37 | 0.79 | 7.18 |
| Bayesian network | 85.97 | 5.91 | 0.85 | 6.04 |
| Neural network | 92.89 | 4.41 | 0.88 | 5.90 |
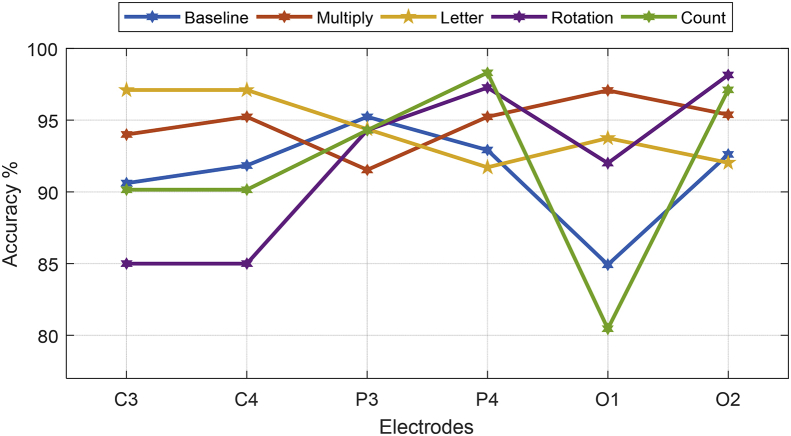
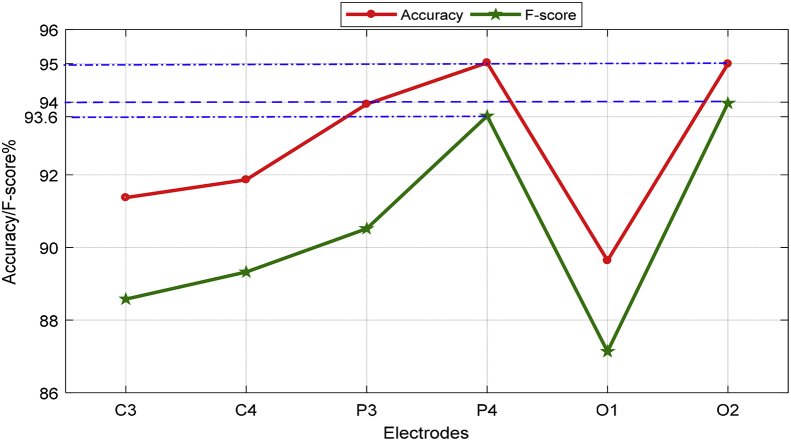
In [Fig. 3] accuracy for all 6 channels and for all of the mental tasks and in [Fig. 4] mean of accuracy and f-score for all mental tasks and all 6 channels are shown.
Fig. 3.
Accuracy for all 6 channels and for all of the mental tasks.
Fig. 4.
Mean accuracy and mean f-score for all 6 channels independent of mental tasks.
In this database, each electrode in a specific task shows optimum accuracy according to recorded tasks. Therefore for each task, a specific channel is set as an optimum channel. Results are shown in [Table 3].
Table 3.
Accuracy, F-score and AUC of the subject classification using a Neural network for different tasks and mental activity.
| optimum channel | Accuracy | F-score | AUC | |
|---|---|---|---|---|
| Baseline | P3 | 97.1 | 0.97 | 0.98 |
| Multiply | O1 | 97.07 | 0.98 | 0.99 |
| Letter | C4 | 97.1 | 0.97 | 0.98 |
| Rotation | O2 | 98.15 | 0.98 | 1 |
| Count | P4 | 98.3 | 0.98 | 0.99 |
Discussion
Since EEG signals have a significantly low spatial resolution, therefore they are dominant for different tasks and mental activities over specific areas of the brain rather than others. Selecting the appropriate channel with high accuracy for different tasks is an important part of authentication systems. Different classifiers in the classification of EEG signals and EEG based authentication systems are used, three classifiers (SVM, Bayes network, neural network) are used in this paper order to obtain the optimum classifier. According to the results of [Table 2] higher values of accuracy and F-score is recorded for neural network classifier so this classifier is selected to continue the discussion.
According to [Table 3] and comparing the classification accuracy for various tasks shows that task 1 is more precise, which emphasizes the use of specific brain activity signals for security applications and authentication. To design a single channel authentication system with mental tasks independency for this dataset, a channel with maximum accuracy and f-score must be chosen. According to the results of [Fig. 2, Fig. 3] each different mental task, according to its essence, enables different part of brain and O2 is chosen as the best electrode for single channel system.
Usually, the EEG biometric authentication system is evaluated in two modes:
-
•
Identification mode: classification one to many comparison (user identified or not)
-
•
Verification mode: classification one to one comparison (true/false)
The mean accuracy of our single channel authentication systems for all channels independent of mental tasks based on identification mode was 95% and when we used a selected channel based on mental activity, mean accuracy was 97.54%. For the first time, we can achieve high accuracy for this data set in single channel mode.
In Ref. [13] Experimental results show that an identification accuracy of 72% can be achieved using only a single epoch and 96.7% by joint classification of multiple epochs. Our method uses only a single epoch for classification and Maximum accuracy in our paper is 98.3% for count mental activity and P4. In Ref. [14] two modes of identification and verification are used. In verification mode, they used methods based on the similarity between EEG signals achieved 99% accuracy.
In identification mode, they used classification algorithm machine learning. They used k-nearest neighborhood classifier with k = 5 and achieved a 22% success rate. Nonetheless, a 22% success rate still falls far below levels acceptable for practical user identification systems.
According to the results presented in Ref. [6], the mean accuracy for 6-channel authentication was 98.46%. Based on the results of the proposed method, we were able to use a single-channel instead of a six-channel system with acceptable decreasing in accuracy, which is cost effective to use in practical applications.
EEG signals are being affected by a person's mood like stress happiness and etc. Stress is a mental condition that affects brain electrical activity to be different from the normal state [24]. Performing a mental activity under stress will also result in a change in the EEG patterns. Many common methods to estimate the mental stress are based on features extracted from different signals, including electrocardiogram, blood pressure, skin temperature, galvanic skin response [25]and EEG signals [26], [27]. With the increasing availability of devices and methods for detecting stress, and implementing a new biofeedback methodology for personalized stress management devices with low power-cost and low complexity [28], the problem of EEG based authentication system with stress can be solved.
Conclusion
In this paper, we studied the performance of single channel brainwave-based authentication systems and selected channels placement based on mental activities. We used different feature extracting methods and by splitting each trail of the signals into ten parts, we used the signals in an optimal way. We examined the performance of different classifiers to get the least error and achieve 97.54% mean accuracy with neural network classifier for single-channel authentication systems with optimum electrode placement. We also analyzed the authentication system individually, without considering the type of mental activity, and chose channel O2 as the optimum channel with an accuracy of 95%.
Conflicts of interest
The authors states that there is no conflict of interest.
Acknowledgements
We would like to acknowledge the assistance of Dr. Charles Anderson of Colorado State University, USA, for maintaining a repository of the 1989 Keirn and Aunon dataset and making them available for experimentation.
Footnotes
Peer review under responsibility of Chang Gung University.
References
- 1.Abo-Zahhad M., Ahmed S.M., Abbas S.N. State-of-the-art methods and future perspectives for personal recognition based on electroencephalogram signals. IET Biom. 2015;4:179–190. [Google Scholar]
- 2.Pirbhulal S., Zhang H., Wu W., Mukhopadhyay S.C., Zhang Y.T. Heart-beats based biometric random binary sequences generation to secure wireless body sensor networks. IEEE Trans Biomed Eng. 2018;65:2751–2759. doi: 10.1109/TBME.2018.2815155. [DOI] [PubMed] [Google Scholar]
- 3.Maiorana E., Hine G.E., La Rocca D., Campisi P. IEEE Sixth Int’l Conf. Biometrics: Theory, Applications and Systems (BTAS) 2013. On the vulnerability of an EEG-based biometric system to hill-climbing attacks algorithms' comparison and possible countermeasures; pp. 1–6. [Google Scholar]
- 4.Marcel S., Millan Jdel R. Person authentication using brainwaves (EEG) and maximum a posteriori model adaptation. IEEE Trans Pattern Anal Mach Intell. 2007;29:743–752. doi: 10.1109/TPAMI.2007.1012. [DOI] [PubMed] [Google Scholar]
- 5.Palaniappan R., Mandic D.P. EEG based biometric framework for automatic identity verification. J VLSI Signal Process. 2007;49:243–250. [Google Scholar]
- 6.Bajwa G., Dantu R. Neurokey: towards a new paradigm of cancelable biometrics-based key generation using electroencephalograms. Comput Secur. 2016;62:95–113. [Google Scholar]
- 7.Campisi P., La Rocca D. Brain waves for automatic biometric-based user recognition. IEEE Trans Inf Forensics Secur. 2014;9:782–800. [Google Scholar]
- 8.Palaniappan R. Two-stage biometric authentication method using thought activity brain waves. Int J Neural Syst. 2008;18:59–66. doi: 10.1142/S0129065708001373. [DOI] [PubMed] [Google Scholar]
- 9.He C., Lv X., Wang Z.J. IEEE; Taipei, Taiwan: 2009. Hashing the mAR coefficients from EEG data for person authentication. Acoustics, speech and signal processing: 2009 IEEE International Conference on acoustics, speech and signal processing; pp. 1445–1448. [Google Scholar]
- 10.Yeom S.K., Suk H.I., Lee S.W. Person authentication from neural activity of face-specific visual self-representation. Pattern Recogn. 2013;46:1159–1169. [Google Scholar]
- 11.Zeng Y., Wu Q., Yang K., Tong L., Yan B., Shu J. EEG-based identity authentication framework using face rapid serial visual presentation with optimized channels. Sensors. 2019;19:6. doi: 10.3390/s19010006. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Thomas K.P., Vinod A.P., Robinson N. Proceedings of the 2017 International conference on cryptography, security and privacy. 2017. Online biometric authentication using subject-specific band power features of eeg; pp. 136–141. [Google Scholar]
- 13.Koike-Akino T., Mahajan R., Marks T.K., Wang Y., Watanabe S., Tuzel O. 2016 IEEE 38th Annual International conference of the engineering in medicine and biology society. IEEE; 2016. High-accuracy user identification using EEG biometrics. EMBC; pp. 854–858. [DOI] [PubMed] [Google Scholar]
- 14.Chuang J., Nguyen H., Wang C., Johnson B. International conference on financial cryptography and data security. Springer; 2013. I think, therefore i am: usability and security of authentication using brainwaves; pp. 1–16. [Google Scholar]
- 15.Bao X., Wang J., Hu J. International Conference on New Trends in Information and Service Science. IEEE; 2009. Method of individual identification based on electroencephalogram analysis; pp. 390–393. [Google Scholar]
- 16.Bao X., Wang J., Hu J. International conference on new trends in information and service science 2009. IEEE; 2009. Method of individual identification based on electroencephalogram analysis. NISS'09; pp. 390–393. [Google Scholar]
- 17.Aydın S., Saraoğlu H.M., Kara S. Log energy entropy-based EEG classification with multilayer neural networks in seizure. Ann Biomed Eng. 2009;37:2626–2630. doi: 10.1007/s10439-009-9795-x. [DOI] [PubMed] [Google Scholar]
- 18.Song Y., Lio P. A new approach for epileptic seizure detection: sample entropy based feature extraction and extreme learning machine. J Biomed Sci Eng. 2010;3:556–567. [Google Scholar]
- 19.Sasikala S., Geetha S. A novel memetic algorithm for discovering knowledge in binary and multi class predictions based on support vector machine. Appl Soft Comput. 2016;49:407–422. [Google Scholar]
- 20.Han J., Kamber M., Pei J. 3rd ed. Morgan Kaufmann; Burlington: 2011. Data mining: concepts and techniques. [Google Scholar]
- 21.Friedman N., Geiger D., Goldszmidt M. Bayesian network classifiers. Mach Learn. 1997;29:131–163. [Google Scholar]
- 22.Cheong L.C., Sudirman R., Hussin S.S. Feature extraction of EEG signal using wavelet transform for autism classification. J Eng Appl Sci ARPN. 2015;10:8533–8540. [Google Scholar]
- 23.Fawcett T. An introduction to ROC analysis. Pattern Recogn Lett. 2006;27:861–874. [Google Scholar]
- 24.Gaikwad P., Paithane A.N. International conference on computing methodologies and communication (ICCMC) IEEE; 2017. Novel approach for stress recognition using EEG signal by SVM classifier; pp. 967–971. [Google Scholar]
- 25.Wu W., Pirbhulal S., Zhang H., Mukhopadhyay S.C. Quantitative assessment for self-tracking of acute stress based on triangulation principle in a wearable sensor system. IEEE J Biomed Heal Informatics. 2018;23:703–713. doi: 10.1109/JBHI.2018.2832069. [DOI] [PubMed] [Google Scholar]
- 26.Alonso J.F., Romero S., Ballester M.R., Antonijoan R.M., Mañanas M.A. Stress assessment based on EEG univariate features and functional connectivity measures. Physiol Meas. 2015;36:1351–1365. doi: 10.1088/0967-3334/36/7/1351. [DOI] [PubMed] [Google Scholar]
- 27.Al-shargie F., Tang T.B., Badruddin N., Kiguchi M. Towards multilevel mental stress assessment using SVM with ECOC: an EEG approach. Med Biol Eng Comput. 2018;56:125–136. doi: 10.1007/s11517-017-1733-8. [DOI] [PubMed] [Google Scholar]
- 28.Wu W., Zhang H., Pirbhulal S., Mukhopadhyay S.C., Zhang Y.T. Assessment of biofeedback training for emotion management through wearable textile physiological monitoring system. IEEE Sens J. 2015;15:7087–7095. [Google Scholar]