Abstract
Vehicular ad hoc networks (VANETs) are the key enabling technology for intelligent transportation systems. Carrier-sense multiple access with collision avoidance (CSMA/CA) is the de facto media access standard for inter-vehicular communications, but its performance degrades in high-density networks. Time-division multiple access (TDMA)-based protocols fill this gap to a certain extent, but encounter inefficient clock synchronization and lack of prioritized message delivery. Therefore, we propose a priority-based direction-aware media access control (PDMAC) as a novel protocol for intra-cluster and inter-cluster clock synchronization. Furthermore, PDMAC pioneers a three-tier priority assignment technique to enhance warning messages delivery by taking into account the direction component, message type, and severity level on each tier. Analytical and simulation results validate the improved performance of PDMAC in terms of clock synchronization, channel utilization, message loss rate, end-to-end delays, and network throughput, as compared with eminent VANET MAC protocols.
Keywords: clock synchronization, media access control protocol, time-division multiple access, vehicular ad hoc networks, warning message dissemination
1. Introduction
1.1. Motivation and Objectives
Vehicular ad hoc networks (VANETs) enable communication among high-speed vehicles (hereafter, nodes) in an intelligent transportation system (ITS) [1]. ITSs have several applications (e.g., smart cities, infotainment, route and travel time estimation, and accident prevention) [2]. However, accident prevention attracts more attention due to the over million deaths and 20–50 million critical injuries caused by road accidents each year around the globe [3].
To evade road accidents, cooperative collision avoidance (CCA) schemes compute collision probabilities at regular intervals among nodes and encapsulate them in warning messages along with appropriate preventive measures [4]. These messages are transmitted either through a vehicle-to-vehicle (V2V) or a vehicle-to-infrastructure (V2I) communication model. A V2V model establishes communication among nodes directly, while a V2I model employs road-side units (RSUs) for message transmission and has increased deployment and maintenance costs [5,6]. In this regard, cluster-based approaches effectively manage the nodes and prevent broadcast floods by restricting the broadcast domain to the individual clusters, thereby minimizing the communication overhead [1,7].
Besides the identification of a possible collision among nodes, reliable and in-time delivery of warning messages is also critical in CCA schemes [8]. This is because preventive measures can only be effective if the nodes find ample time to take these measures. Issues related to the warning message dissemination are addressed both at network and media access control (MAC) layers. Network layer protocols seek to find the best route to reach a certain destination node in a multi-hop environment [5,9], whereas protocols at the MAC layer ensure message delivery over a single link while preventing channel access collisions. This paper focuses on the MAC layer, where communications over a shared medium remain critical.
Toward that end, carrier-sense multiple access with collision avoidance (CSMA/CA) is considered as the de facto media access standard for inter-vehicular communication at the MAC layer [10]. However, it experiences performance degradation in the face of high node density [11]. This demands efficient channel utilization and message delivery at the MAC layer. The protocols that adopt time-division multiple access (TDMA) fill this gap to a certain extent. However, as a result of frequent topological changes in VANETs due to high-speed nodes moving in opposite directions, TDMA-based protocols also experience performance degradation in terms of increased end-to-end delays and message losses, which adversely impact the network throughput. One of the major reasons for this is the lack of consideration of the direction component during the relay selection process on bi-directional highways.
Moreover, clock synchronization is another issue in TDMA-based protocols [12,13]. The existing literature focuses only on the intra-cluster clock synchronization. However, it is not necessary that a path only comprises nodes from a single cluster; rather, relay services of nodes from other clusters are also frequently acquired in VANETs. In such cases, time slot reservations become challenging for messages generated by nodes from different clusters. This is because local clocks of nodes in different clusters may bear different clock times, which result in inefficient time slot reservation, utilization, and release, thus producing channel collisions at a large scale. To overcome this issue, the need for inter-cluster clock synchronization becomes critical in addition to intra-cluster clock synchronization.
Furthermore, since warning messages are time-sensitive, CCA schemes require the prioritized delivery of warning messages. A promising approach in this regard is to assign higher priority to warning messages over non-warning messages (A non-warning message refers to any message other than the warning message, which can be used to communicate route identification, traffic density information, etc. [14,15].) (see, e.g., [16]). However, treating all warning messages with equal priority limits the performance of this approach because the probability of collision among nodes may not remain the same all the time. This adversely affects the delivery of warning messages with high probability of collision, especially in dense networks.
The objective of this paper is to address the aforementioned challenges of TDMA-based MAC protocols by presenting a novel protocol that enables reliable and in-time delivery of time-critical warning messages in VANETs. This will provide ample time for nodes to implement preventive measures, thereby reducing the number of road accidents.
1.2. Novelty and Contributions
We propose a priority-based direction-aware media access control (PDMAC) protocol which makes the following contributions:
PDMAC introduces inter-cluster clock synchronization in addition to intra-cluster clock synchronization, using a V2V model on bi-directional highways. We show that this leads to fast clock synchronization with reduced communication overhead and improved channel utilization.
- PDMAC introduces a three-tier priority assignment technique to ensure prioritized delivery of time-sensitive warning messages, as follows.
- The first tier takes into account the direction of nodes for selecting relays. This helps to reduce the message loss rate and end-to-end delays, and improves the network throughput.
- The second tier prioritizes the time-critical warning messages over non-warning messages.
- The third tier further prioritizes warning message on the basis of different severity levels, where a severity level is proportional to the probability of collision among nodes. Such a prioritized transmission helps to enhance the delivery ratio of warning messages, thereby providing better collision avoidance among nodes.
To the best of our knowledge, PDMAC is a pioneering approach to employ a three-tier priority assignment and exploit inter-cluster clock synchronization besides intra-cluster clock synchronization.
1.3. Paper Organization
The rest of the paper is organized as follows. Section 2 reviews state-of-the-art MAC protocols in VANETs. Section 3 details the proposed PDMAC protocol. Section 4 evaluates the performance of the proposed protocol. Finally, Section 5 concludes the paper with future research directions. Table 1 lists the notations used in this paper.
Table 1.
List of notations.
| Notation | Description |
|---|---|
| Message forwarding from left to right node | |
| Acknowledgment in response to | |
| Set of free time slots | |
| Best forwarder intermediary relay node | |
| Identity | |
| Range of speeds for nodes | |
| C | Set of member nodes in a cluster |
| Set of cluster heads | |
| A randomly selected CH for clock synchronization | |
| Identity of | |
| Identity of the cluster head | |
| D | Destination node |
| Time slot on the frame to transmit messages | |
| Acceptance/rejection field of relay service | |
| Final distance between nodes | |
| Hamming distance function | |
| Direction component | |
| L1-norm distance between nodes | |
| Minimum function | |
| N | Set of all nodes |
| A non-warning message | |
| R | Set of intermediary relay nodes |
| Rand(.) | Random selection function |
| Request message | |
| Response message | |
| Collision probability among nodes | |
| S | Source node |
| Severity level of a warning message | |
| Message type | |
| T | Local clock time of a node |
| Node’s timer validation field | |
| W | A warning message |
2. Related Work
In dynamic networks like VANETS, TDMA-based protocols perform better than CSMA/CA with respect to message delivery rate [11]. However, inefficient clock synchronization limits the performance of TDMA-based protocols [13]. In this regard, the authors in [17] present an intra-cluster clock synchronization technique, referred to as the CSRDS protocol in this paper. CSRDS introduces an approximate agreement approach to avoid Global Positioning System (GPS)-based clock synchronization. Similar intra-cluster clock synchronization techniques have also been presented [12,18,19]. However, unless the local clocks of all the nodes in a network are synchronized to a commonly shared clock through inter-cluster clock synchronization, the time slot reservation, its utilization, and release on successful or unsuccessful delivery of messages always remain inefficient. Distributed multi-channel MAC (DMCMAC) [14] synchronizes its local clock with the GPS. However, in such an approach the clocks remain unsynchronized when GPS is not available (e.g., inside tunnels). Another clock synchronization protocol proposed in [20] employs epoch time to evaluate and synchronize the local current round-time. However, time slot shifting correction is a major limitation of this work.
The lack of prioritized message transmission is another issue in TDMA-based protocols. Prediction-based TDMA MAC (PTMAC) [21] detects packet collisions on the channels. Similarly, optimal cooperative ad hoc-MAC (OCA-MAC) [22] considers relay and destination nodes with available time slots to compute an optimal path. Moreover, VANET adaptive TDMA-MAC (VAT-MAC) [23] optimizes frame length by predicting the number of nodes in the network. Furthermore, the authors in [24,25,26] allocate disjoint sets of time slots that minimize the channel collisions. However, the availability of such disjoint sets at all times is unrealistic. In addition, the authors in [27,28] propose hybrid protocols that combine the functionality of CSMA with TDMA to enhance message delivery ratio, but face performance degradation as the network density increases.
Similarly, TDMA-aware routing protocol for multi-hop communication (TRPM) [29] enables reliable long-distance communication. It selects a relay based on a delay-tolerant MAC (DTMAC) scheduling scheme, which exhibits the problem of channel access collisions [30]. Furthermore, the work in [31] presents a novel software-defined network (SDN)-based protocol for warning messages dissemination and introduces the concept of open flow switch. However, the selection of an SDN controller in VANETs is a challenging task due to its highly dynamic topology. The authors in [32,33] propose adaptive techniques for time slot reservation, which improve channel access. However, the warning messages delivery ratio deteriorates due to non-prioritized slot allocation. Similarly, cluster-based MAC (CB-MAC) [34] avoids the use of request to send (RTS) and clear to send (CTS) messages in order to minimize the warning messages communication overhead. However, the lack of such essential handshake messages may result in access collisions at a large scale. Moreover, mobility-aware collision avoidance MAC (MoMAC) [35] proposes an even distribution of time slots among road lanes, which is unrealistic and may result in time slot wastage in real traffic.
The work in [36] presents the triggered control channel interval (CCHI) multi-channel MAC (TCM-MAC) protocol, which allocates variable time slots to messages for their transmission. The authors in [37] propose the use of variable transmission power to enhance message delivery ratio. RSU-assisted multi-channel protocol [38] employs RSUs for time interval optimization and message tracking. However, the deployment and maintenance costs of RSUs is a limitation. The work in [14] proposes an adaptive DMCMAC protocol, which divides the number of time slots on the frames in accordance with the number of messages to be transmitted on the network in order to enhance channel access. However, treating the warning and non-warning messages with equal priority degrades the performance of this protocol, especially when the number of non-warning messages is higher than that of the warning messages. The work in [39] takes the congestion level into account in order to prioritize messages. However, this approach also treats both warning and non-warning messages with the same priority. The authors in [16,40,41] propose TDMA-based MAC protocols that prioritize warning messages over non-warning messages. This improves the delivery rate of time-sensitive warning messages to a certain extent. However, these protocols do not differentiate between warning messages of different severity levels. Thus, there is a need to further prioritize warning messages based on the severity level, which can be determined from the probability of collision among nodes.
From the literature survey, we found that the existing TDMA-based MAC protocols provide timely and reliable delivery of warning messages in VANETs, mainly by using intra-cluster clock synchronization approaches. However, it is not necessary that a path only comprises nodes from a single cluster, as relay services of nodes from other clusters are also frequently acquired in VANETs. Nevertheless, the existing approaches lack inter-cluster clock synchronization, and thus these approaches fail when time slot reservations are carried out for nodes belonging to different clusters. Moreover, the current literature on MAC protocols for VANETs does not take into account the direction component of nodes, and thus cannot cater to bi-directional highways where high-speed nodes move in opposite directions, causing frequent topological changes. Furthermore, the current body of literature provides MAC protocols that are capable of prioritizing warning messages over non-warning messages. However, these protocols lack the ability to differentiate between warning messages of different severity. To address the aforementioned challenges, we propose a novel solution called PDMAC, which is described in the following section.
3. Priority-Based Direction-Aware Media Access Control (PDMAC) Protocol
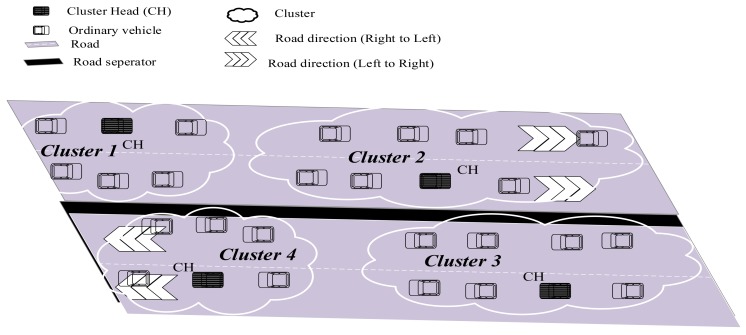
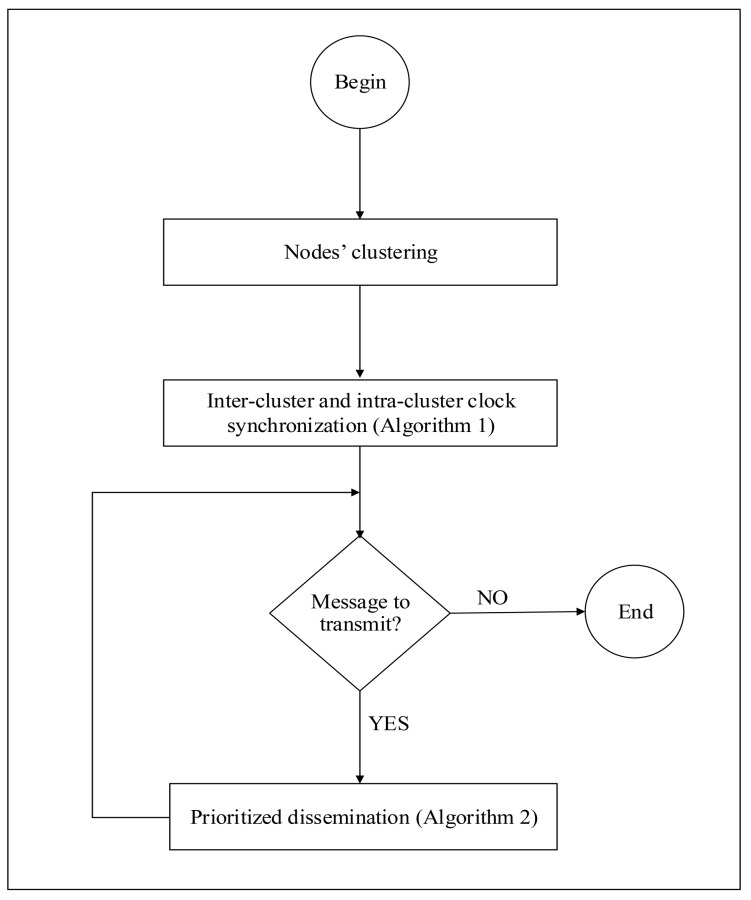
This section presents our proposed PDMAC protocol for V2V warning message dissemination on bi-directional highways, as depicted in Figure 1. The methodology of PDMAC is to start with nodes’ clustering to enable enhanced node manageability and to restrict the broadcast domains (see Section 3.1). This is followed by the clock synchronization of nodes, which is critical for time slot reservation (see Section 3.2). Here, we introduce a local clock synchronization technique that is composed of two phases, namely, inter-cluster and intra-cluster clock synchronizations. We then present the proposed three-tier priority assignment technique to enhance the delivery rate of time-sensitive warning messages (see Section 3.3). Finally, we present the time complexity of PDMAC (see Section 3.4). An overview of the proposed solution is presented in Figure 2.
Figure 1.
A bi-directional highway traffic scenario.
Figure 2.
Overview of the proposed priority-based direction-aware media access control (PDMAC) protocol.
3.1. Node Clustering
In TDMA-based MAC protocols, clock synchronization is one of the most important factors for message transmission. Since each node uses a specific time slot () to transmit its message, it becomes inevitable to synchronize the local clocks of all nodes on the network. In this regard, cluster-based approaches are promising, as the limited broadcast domain due to clustering reduces the communication overhead and prevents broadcast floods to a significant extent [1,7,18,19]. In all such approaches, clustering is performed as soon as a node joins the highway. Once a node is a member or cluster head (CH) of a cluster, it can transmit messages. This allows nodes to timely transmit warning messages in critical situations without having to perform clustering each time before sending a message. Thus, clustering is not performed just before a critical event, such as an incipient collision, and it does not have any adverse effect in critical situations. Rather, enhanced node manageability results in improved performance due to clustering [4].
PDMAC clusters nodes on the network by using a VANET-specific variant of the k-medoids algorithm, proposed in our previous work [4]. However, in [4] clustering is performed at the application layer with the aim of avoiding road accidents, whereas in this paper we use clustering for warning message dissemination at the MAC layer. The process of clustering in PDMAC initiates as soon as a node enters the highway. Here, we have two types of nodes: cluster heads (CHs) and ordinary vehicles (OVs). A CH manages a cluster and keeps the record of all its member nodes. Conversely, an OV represents any node other than the CH. However, the status of an OV changes to member node as soon as it joins a certain cluster.
3.2. Clock Synchronization
On successful completion of node clustering, the process of clock synchronization is initiated. The local clocks of nodes are synchronized to a commonly shared clock in the following two phases.
3.2.1. Inter-Cluster Clock Synchronization
To synchronize the local clocks of all nodes on the network, PDMAC introduces a single-bit field—namely, the node’s timer validation bit ()—in the message header. This field indicates whether or not the timer is synchronized with the other network nodes. If = 1, the node’s timer is considered to be synchronized and, hence, valid. Conversely, if = 0, the clock is required to be synchronized and remains invalid to all other nodes on the network. PDMAC keeps the default as 0 to make clock synchronization mandatory for all the nodes on their entry to the highway.
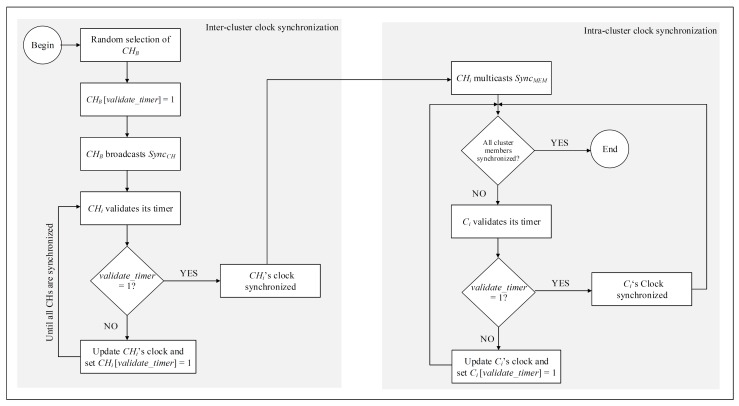
The clock synchronization process (Algorithm 1) starts after the completion of the clustering process, that is, when all nodes in the network are clustered and a CH for each cluster is elected using the k-medoids algorithm (see Section 3.1). The set of all CHs in the network, which are elected by means of the k-medoids algorithm, is denoted as . The first phase of Algorithm 1 synchronizes the clocks of . For this inter-cluster clock synchronization, a CH is arbitrarily chosen from , and is denoted as . The rest of the CHs then synchronize their local clocks with the commonly shared clock of as follows.
broadcasts a CH’s clock synchronization message (), which is acknowledged by all reachable CHs. It must be noted that OVs do not update their clocks on reception of and are only used as relay nodes to forward this message to the CHs. The for is set to 1, so that all other CHs can synchronize their timer to this randomly chosen CH. A CH with an unsynchronized timer changes its local time to that of . As soon as a CH synchronizes its local clock, its is set to 1 and in this way all the CHs are synchronized to a common local clock. Here, it is not mandatory for each new CH to synchronize its clock with only. Any CH with a validated clock can validate other CHs as soon as it receives a request for clock synchronization.
3.2.2. Intra-Cluster Clock Synchronization
On completion of the first phase, the process of intra-cluster local clock synchronization initiates. Here, each CH multicasts a member clock synchronization message () to its member nodes for the communication of its local clock time. If the of a node is 0, the member updates its local clock time () with respect to its corresponding CH and flips its to 1, which indicates that the node’s timer is now synchronized. However, in the case of a node with = 1, no further synchronization action is required. Moreover, a validated node does not need to synchronize its timer again if it is elected as a CH in the future.
The proposed inter-cluster and intra-cluster clock synchronization technique is presented in Algorithm 1. The algorithm takes N, , and C as input, where N represents the set of all nodes, is the set of cluster heads, and C represents the set of member nodes in each cluster. The output of this algorithm includes synchronized local clocks of all the nodes on the network. After clock synchronization, nodes can perform prioritized message dissemination, the procedure for which is detailed in the following section. Figure 3 presents the procedural flowchart of Algorithm 1.
Figure 3.
Procedural flowchart of the clock synchronization algorithm.
3.3. Prioritized Warning Message Dissemination
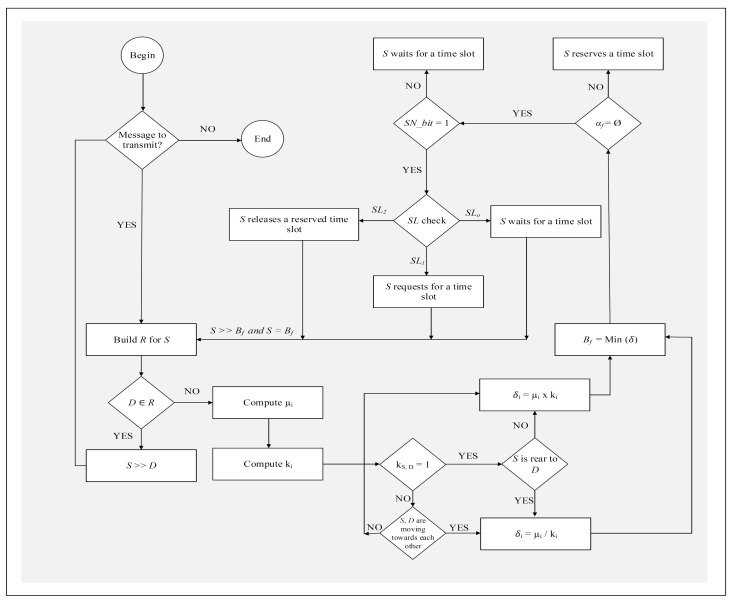
In PDMAC, when a source node (S) intends to transmit a warning message (W) to a certain destination (D) and these nodes lie within communication range of each other, S disseminates the message straightaway by reserving all available time slots in its frame to itself. Otherwise, S requests its neighboring nodes to provide relay services. Neighbors include all the nodes that lie within the communication range of S, and a suitable intermediary node (The terms intermediary node and forwarder are used interchangeably in this paper to refer to a relay node.) among the neighbors is selected to relay the message from S to D. To find a suitable relay node, S broadcasts a request message () to its neighbors. An message includes the following fields: Source Identity (), Destination Identity (), Source Direction Information (), Destination Direction Information (), Message Type (), and warning message Severity Level (). Each neighbor responds to S with an acknowledgment message () that includes Relay node Identity (), Relay node Direction Information (), set of free time slots (), and time slot to be assigned (). S selects the best forwarder () and sends a response message () to it only. An message includes the best forwarder Identity () and relay services acceptance/rejection decision (). To accept the relay services of a node, is set to 1. Furthermore, and use the control channel (CCH), whereas the utilizes the service channels (SCHs). PDMAC implements a three-tier priority assignment process to enhance the delivery of warning messages, which is detailed in the following subsections.
| Algorithm 1 Clock synchronization. |
|
Input:N, , and C Output: Synchronized time for all CHs and member nodes Begin: Set N[] as OFF Inter-cluster Clock Synchronization: ⟵ Rand() Set [] as ON broadcasts For i = 1 To sizeof() If [] = OFF Then ⟵ Set [] as ON Else No clock synchronization is required End If End For Intra-cluster Clock Synchronization: For j = 1 To sizeof() multicasts to its member nodes For i = 1 To sizeof(C) sends to If [] = OFF Then ⟵ Set [] as ON Else No clock synchronization is required End If End For End For End |
3.3.1. Tier 1—Direction-Based Relay Selection
The high-speed mobility of nodes in opposite directions on highways causes frequent topological changes in the form of route breakages and reconstructions, which result in network partitions [42]. Therefore, it becomes necessary to consider the movement direction of nodes during the selection of relays. Toward this end, PDMAC first computes the L1-norm distance () between each of the possible relays () and destination node (D), using the technique proposed in [5]. The protocol then considers the direction component () by using the Hamming distance function () and the technique proposed in [5]. The outcome of is 1 if is moving in the direction of D, and it will be 0 if the direction of is opposite to D. The final distance () between each and D is computed in terms of and . In the case where = 1, and D is in front of S, is computed as
| (1) |
Furthermore, when S is in front of D having = 1, is computed as
| (2) |
Similarly, for = 0 with S and D moving towards each other, (1) is used to compute . Alternatively, if = 0 and S and D are moving away from each other, (2) is used. Finally, a minimum function () identifies the among the available set of intermediary relay nodes (R), which assigns highest priority to the relay closest in distance to D and having direction towards it. On successful completion of the aforementioned process, PDMAC updates the relay identification field () of the message header by adding the Node Identity () of the selected .
3.3.2. Tier 2—Priority on the Basis of Message Type
Unlike non-warning messages, warning messages are time-critical and delays during their transmission may result in collisions among nodes at a large scale [12]. So, Tier-2 priority assignment in the proposed PDMAC protocol is to differentiate between warning and non-warning messages and to assign a higher priority to warning messages. PDMAC introduces a single-bit field in the message header, namely, message type (), to identify the type of a certain message. For warning messages, is set to 1, whereas remains 0 in case of non-warning messages.
The proposed -based Tier-2 priority assignment seeks to improve the delivery of warning messages to a certain extent. However, further prioritization of warning messages is essential because assigning equal priority to warning messages of low- as well as high-severity events degrades the performance of a CCA scheme, as discussed in Section 2. The severity levels of different critical events may be different. Thus, a warning message of a higher-severity event (e.g., an incipient road accident) should receive a higher priority. To address this issue, we propose a Tier-3 priority assignment in the following subsection which further prioritizes the warning messages based on their severity levels.
3.3.3. Tier 3—Priority on the Basis of Severity Levels
The third tier of priority assignment in PDMAC is to determine the priority of warning messages based on the severity of a critical event (e.g., an incipient collision among nodes). In this tier, warning messages are differentiated from each other based on their severity levels measured on the basis of the probability of collision among nodes. However, computing the collision probability is generally the task of an application layer protocol. In this regard, our previous work [4] proposes a technique to compute the collision probability based on relative speeds, relative distances, and the direction of nodes. It then determines the safe speed for nodes to evade a collision. The collision probability along with the safe speed is communicated to the rear node, which then adopts the safe speed to avoid the collision. However, since this paper concerns the MAC layer, for the sake of determining the priority of warning messages on the basis of severity level, we assume that the collision probability is available to PDMAC from the application layer protocol. PDMAC employs this collision probability to determine the Severity Level () of a certain warning message according to Table 2.
Table 2.
Severity levels of warning messages.
| Severity Level (SL) | SL Value | Range of Collision Probability () |
|---|---|---|
| 00 | <⩽ | |
| 01 | <⩽ | |
| 10 | <⩽ | |
| 11 |
Warning messages are classified into three levels, namely, , , and , as shown in Table 2. Here, represents a warning message with the lowest collision probability, whereas refers to the one with the highest collision probability. Moreover, for non-warning messages (s) with , the probability of collision always remains 0. This implements the third-tier priority in reservation, for which PDMAC introduces a 2-bit field in the message header.
In case of a warning message that belongs to the category, S waits for a free , which keeps this type of warning message on the lowest priority. increases the priority level, such that S can request to release a occupied by a non-warning message or a warning message of lower priority. If none of these options are available, then warning messages also wait for a to become available, as it is not obligatory upon other nodes to respond and release their occupied . Finally, if an level warning message does not find any free , it is mandatory for non-warning messages and lower-priority warning messages to release their allotted for it. This ensures reliable and in-time delivery of highly critical warning messages. It is worth mentioning here that an level warning message also behaves like or messages in a case where all are occupied by the warning messages of similar Tier-3 priority, which is extremely rare.
Our proposed three-tier priority assignment technique is presented in Algorithm 2. The algorithm takes S, D, R, , and W as inputs, where R represents the set of intermediary relay nodes, is the set of free , and W refers to a warning message. The output of the algorithm includes the selection of and the reservation of to transmit W. Figure 4 presents the flowchart of the three-tier priority assignment process of Algorithm 2.
Figure 4.
Procedural flowchart of the prioritized warning message dissemination algorithm.
| Algorithm 2 Prioritized warning message dissemination. |
|
Input:S, D, R, , and W Output: selection and time slot reservation for warning message dissemination Begin: Repeat If D∈R Then SD Else For i = 1 To sizeof(R) ⟵ + ⟵ If = 1 Then If S = Rear & D = Front node Then ⟵ Else ⟵ End If Else If S, D move towards each other Then ⟵ Else ⟵ End If End If End For ⟵ Min() If = Then If W[SN_bit] = 1 ℓ⟵W[severity_bits] Switch(ℓ) Case: 00 S waits for a free Case: 01 S requests to release a Case: 10 S releases already reserved by a non-warning or a lower priority warning message. End Switch Else S waits for a free End If Else S reserves a from End If S S⟵ End If Until = D End |
3.4. Time Complexity
Time complexity refers to the number of steps carried out for the dissemination of a message from S to D. In our proposed PDMAC protocol, Algorithm 1 is composed of two major sections, where the first is responsible for inter-cluster clock synchronization and the second section performs intra-cluster clock synchronization. The first section contains a single loop, whereas the second section is composed of two loops that are dependent upon each other (i.e., there is an inner-loop and an outer-loop). Hence, the worst-case time complexity of Algorithm 1 becomes , where N refers to the number of nodes. In a similar manner, the worst-case time complexity of Algorithm 2 remains . Since Algorithms 1 and 2 constitute the proposed PDMAC protocol, the overall worst-case complexity of PDMAC becomes .
4. Performance Evaluation
This section evaluates the performance of our proposed PDMAC protocol in comparison with DMCMAC [14], CSRDS [17], and IEEE 802.11p (CSMA/CA). Simulations were performed using the VANET Toolbox [43], which is a reliable and widely used vehicular network simulator with support for MAC layer [44,45,46,47]. Table 3 lists the simulation parameters along with their configurations, which are commonly used for evaluating TDMA-based vehicular MAC protocols in the state-of-the-art [4,5,14,41]. All simulations were based on the scenario depicted in Figure 1, where the number of nodes was varied from 0 to 550, unless otherwise specified. The synchronization interval for each protocol was taken as 100 ms. Moreover, nodes were categorized into different density levels, namely, sparse, medium, and dense, in order to normalize the number of nodes in accordance with the classification of real-life traffic with respect to node density proposed in [5]. A sparse network consisted of a maximum of 200 nodes, a medium network ranged between 201 to 400 nodes, and a dense network consisted of more than 400 nodes. Performance evaluation metrics included clock synchronization, channel utilization, message loss rate, end-to-end delay, and throughput, which are commonly used in the state-of-the-art to evaluate MAC protocols in VANETs [22,33,34,48]. Analytical results, obtained on MATLAB R2018a, were used to validate the simulation results for the proposed PDMAC protocol. Each result presented was averaged over 20 replicated simulation runs by keeping all parameters fixed and changing the random seed values.
Table 3.
Simulation parameters.
| Parameter | Value |
|---|---|
| Simulation area | 5000 m |
| Type of road traffic | Bi-directional highway |
| Cluster size | Variable |
| Speed of nodes | 0–42 m/s |
| Regular acceleration, deceleration | 1–6 m/s |
| Number of nodes | 0–550 |
| Transmission range | 150 m, 300 m |
| Number of channels | 1 control channel (CCH) and 6 SCH |
| Synchronization interval | 100 ms |
| Data transmission rate | 12 Mbps |
| Simulation time | 300 s |
4.1. Clock Synchronization
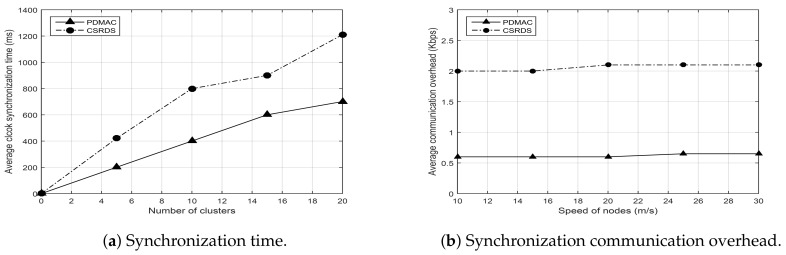
Clock synchronization is crucial in TDMA-based protocols because time slot reservation by all nodes must occur with respect to a commonly shared clock. In a case where the clocks are unsynchronized, nodes find it difficult to reserve slots for the transmission of their messages. PDMAC addresses this issue by proposing a novel clock synchronization technique using Algorithm 1, as detailed in Section 3.2. Results depicted in Figure 5a validate the improved performance of PDMAC, where it outperformed CSRDS in terms of average synchronization time in a scenario with a variable number of clusters ranging from 0 to 20, with each cluster consisting of 5 nodes.
Figure 5.
Clock synchronization.
Moreover, we considered another scenario, with 100 nodes having variable speeds ranging from 10 to 30 m/s, to evaluate the performance of PDMAC and CSRDS for communication overhead generated during clock synchronization. Toward this end, Figure 5b presents the results where PDMAC, due to its lightweight and messages, retained its superior performance.
4.2. Channel Utilization
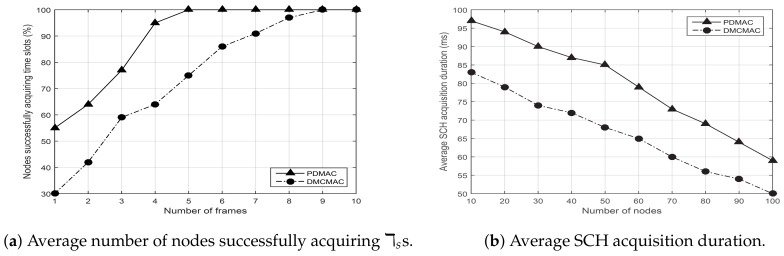
The priority-based dissemination of warning messages in CCA schemes is critical. In this regard, warning messages are given higher priority during channel access. We considered a scenario with 20 nodes and variable number of frames ranging from 1 to 10. While each node transmitted warning messages, we evaluated the performance of PDMAC and DMCMAC in terms of successful time slot acquisition. Since the efficiency improved for all the protocols as the number of frames increased, similar behavior by both the protocols can be observed in the results demonstrated in Figure 6a. However, PDMAC exhibited improved performance compared to DMCMAC because of its three-tier priority-based slot reservation process.
Figure 6.
Channel utilization. DMCMAC: distributed multi-channel media access control; SCH: service channel.
Moreover, we considered another scenario with the number of nodes ranging from 10 to 100. As frame collisions remained proportional to the number of nodes, SCH acquisition duration also experienced performance degradation. Results depicted in Figure 6b show the same behavior for PDMAC and DMCMAC. Furthermore, due to priority-based warning messages dissemination in PDMAC, messages acquired longer SCH duration than DMCMAC, thereby providing improved warning messages delivery.
4.3. Message Loss Rate
The rate of message loss ( ) is computed as [5]
| (3) |
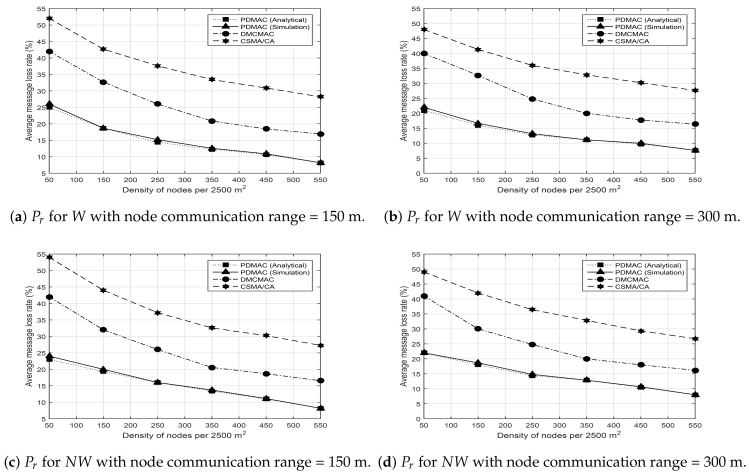
where denotes a single dropped message and represents the total number of messages transmitted across the network. The selection of is a critical decision during warning message transmission. Due to the high-speed mobility of nodes in opposite directions, frequent route changes are observed in VANETs even during the transmission of a single message, thereby producing frequent network partitions. The probability of such network partitions reduces with increasing node density because network connectivity improves with the increased number of nodes. Results shown in Figure 7a–d depict the same behavior for all the protocols.
Figure 7.
Average message loss rate. CSMA/CA: carrier-sense multiple access with collision avoidance.
Moreover, Figure 7a,b depicts the results of message loss rate, for warning messages only, with node communication ranges of 150 and 300 m, respectively. Here, all the protocols provided better efficiency as the communication range increased. However, the performance of PDMAC was considerably better than DMCMAC and CSMA/CA in both cases. DMCMAC exhibited better performance than CSMA/CA and provided an adaptive reservation, where the number of on the frames remained proportional to the number of messages. However, DMCMAC treats both warning and non-warning messages with equal priority. Here, a higher ratio of non-warning messages in the network increases the drop rate of warning messages. Conversely, the proposed PDMAC protocol employs a three-tier priority-based reservation, which effectively reduces the drop rate of warning messages.
Furthermore, DMCMAC and CSMA/CA do not take into account the direction component during relay selection. Here, the probability of a network partition increases when a relay node bears an opposite direction to the destination node, which ultimately results in an increased message loss rate [5]. To address this, PDMAC takes into account the direction component and the distance between the relay and destination nodes in order to select a suitable relay. This ensures reliable and in-time message dissemination. The results presented in Figure 7c,d validate this claim, where PDMAC outperformed DMCMAC and CSMA/CA by achieving reduced message loss rate during the transmission of non-warning messages for nodes with communication ranges of 150 and 300 m, respectively.
4.4. End-to-End Delay
This metric computes the end-to-end delay () observed during the transmission of each message as [5]
| (4) |
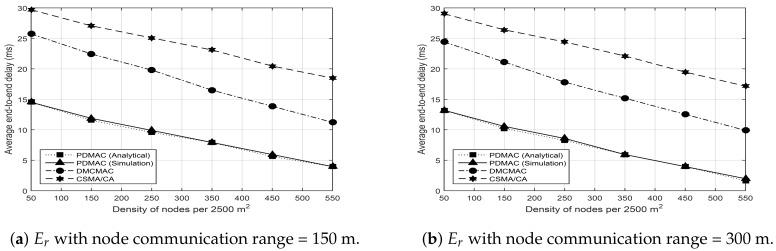
where refers to the delay experienced in transmitting an ith message, and represents the total number of messages successfully received at the destination. Since DMCMAC and CSMA/CA do not consider the direction component, relays selected by these protocols may bear opposite directions to the destination nodes. Due to the opposite directions of nodes, the number of relays increases on the route, which leads to an increased number of send and receive operations. As these operations are costly in terms of time during communication [49], increased end-to-end delays are experienced by DMCMAC and CSMA/CA. Furthermore, the adaptive feature of DMCMAC allocates to all the messages. The number of on the frame remains proportional to the number of messages. Thus, the duration of each also increases or decreases accordingly. This implies that an increased traffic load on the network shortens the duration on the frame in DMCMAC, which results in increased end-to-end delay. Conversely, PDMAC takes the direction component into account and the prioritized dissemination of messages to resolve the aforementioned issues. For these reasons, PDMAC outperforms DMCMAC and CSMA/CA, as shown in the results of Figure 8a,b.
Figure 8.
Average end-to-end delay.
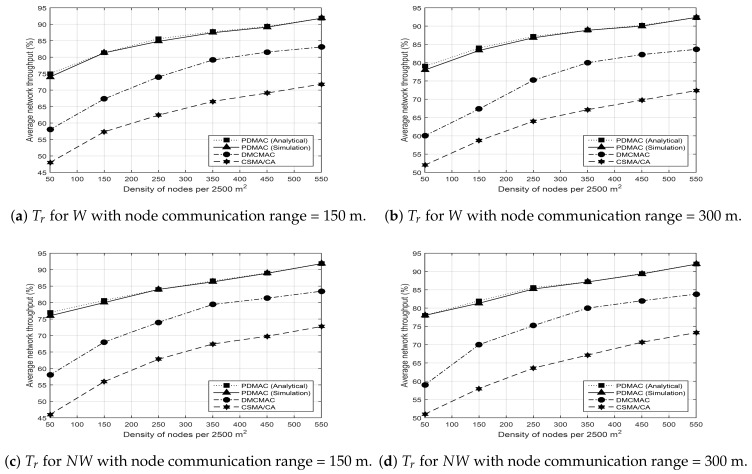
4.5. Throughput
The final metric for performance evaluation refers to the achieved network throughput (), which is computed as [5]
| (5) |
where symbolizes the successful reception of the ith message at a destination node, and represents the total number of messages originated from all source nodes. The network throughput remains inversely proportional to the message loss rate and end-to-end delay observed during message transmissions. The results presented in Figure 9a,b validate the improved throughput in the case of PDMAC, in comparison to DMCMAC and CSMA/CA, due to our novel three-tier priority assignment technique. Similarly, PDMAC also retained its superiority over DMCMAC and CSMA/CA in the results shown in Figure 9c,d.
Figure 9.
Average network throughput.
4.6. Critical Discussion
In VANETs, the performance of CSMA/CA degrades with the increase in network density. Conversely, TDMA-based protocols, which divide each frame into a set of time slots to enable simultaneous message transmission, are considered more suitable for dynamic networks like VANETs. However, inefficient clock synchronization and lack of message prioritization limit the efficiency of TDMA-based protocols. So, we propose a protocol, called PDMAC, for robust inter-cluster and intra-cluster clock synchronization and better channel utilization. Furthermore, PDMAC pioneers the use of a three-tier priority-based warning message dissemination, which ensures reliability and in-time delivery.
Simulation results presented in the previous sections demonstrate the robust nature of PDMAC, which was validated further by analytical results. The results demonstrate reduced average clock synchronization time and communication overhead for PDMAC by 286 ms and Kbps, respectively, in comparison to CSRDS. Considering channel utilization, compared with DMCMAC, PDMAC demonstrated 15% and 14% enhanced performance in successful time slot reservation and SCH acquisition duration, respectively. Moreover, for average message loss rate, end-to-end delay and network throughput, PDMAC demonstrated an improved efficiency by %, 10 ms, and 12%, respectively, over DMCMAC; and 21%, ms, and 22%, respectively, over CSMA/CA.
The proposed PDMAC protocol can be incorporated in intelligent transportation systems to enable a safe driving environment through in-time and reliable warning messages dissemination. This will provide significant time for vehicles to adopt the communicated preventive measures, thereby minimizing road accidents. To that end, our future work will evaluate PDMAC in tandem with our previously proposed application layer protocol [4], network layer protocol [5], and secure message dissemination [2], to study their combined effect on vehicle accident prevention. The limitation of PDMAC, however, is that it is designed for warning messages dissemination on bi-directional highways and cannot cater for road intersections in urban environments. We also intend to address this limitation in our future work.
5. Conclusions
We proposed a cluster-based V2V MAC protocol called PDMAC for prioritized warning messages delivery in VANETs to evade road accidents on bi-directional highways. PDMAC introduces inter-cluster clock synchronization alongside intra-cluster synchronization, which leads to reduced communication overhead and improved channel utilization. Additionally, PDMAC pioneers the use of a three-tier priority assignment to ensure reliable and in-time delivery of warning messages by taking into account the direction component of nodes, message type, and severity level on each tier. Simulation and analytical results reveal that, as compared to eminent vehicular MAC protocols, PDMAC enables reduced message loss rate and end-to-end delays, and increased network throughput. Our future work includes the extension of PDMAC to cater to urban VANET environments.
Author Contributions
All authors have read and agreed to the published version of the manuscript. Conceptualization, G.A.; Data curation, G.A. and S.B.; Formal analysis, G.A. and S.B.; Funding acquisition, T.B.; Methodology, G.A., S.H., T.B. and F.M.; Project administration, F.M.; Resources, T.B.; Software, Z.H.A. and S.H.; Supervision, Z.H.A. and S.H.; Validation, T.B.; Writing—review & editing, T.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Cooper C., Franklin D., Ros M., Safaei F., Abolhasan M. A comparative survey of VANET clustering techniques. IEEE Commun. Surv. Tutor. 2016;19:657–681. doi: 10.1109/COMST.2016.2611524. [DOI] [Google Scholar]
- 2.Haider S., Abbas G., Abbas Z.H., Fazal M. LWE-CPPA: A scheme for secure delivery of warning messages in VANETs. Int. J. Ad Hoc Ubiquitous Comput. 2019 in press. [Google Scholar]
- 3.Halim Z., Kalsoom R., Bashir S., Abbas G. Artificial intelligence techniques for driving safety and vehicle crash prediction. Artif. Intell. Rev. 2016;46:351–387. doi: 10.1007/s10462-016-9467-9. [DOI] [Google Scholar]
- 4.Haider S., Abbas G., Abbas Z.H., Boudjit S., Halim Z. P-DACCA: A probabilistic direction-aware cooperative collision avoidance scheme for VANETs. Future Gener. Comput. Syst. 2019;103:1–17. doi: 10.1016/j.future.2019.09.054. [DOI] [Google Scholar]
- 5.Haider S., Abbas G., Abbas Z.H., Baker T. DABFS: A robust routing protocol for warning messages dissemination in VANETs. Comput. Commun. 2019;147:21–34. doi: 10.1016/j.comcom.2019.08.011. [DOI] [Google Scholar]
- 6.Al-Sultan S., Al-Doori M.M., Al-Bayatti A.H., Zedan H. A comprehensive survey on vehicular ad hoc network. J. Netw. Comput. Appl. 2014;37:380–392. doi: 10.1016/j.jnca.2013.02.036. [DOI] [Google Scholar]
- 7.Eze E., Zhang S., Liu E., Eze J., Muhammad S. Reliable and enhanced cooperative cross-layer medium access control scheme for vehicular communication. IET Netw. 2018;7:200–209. doi: 10.1049/iet-net.2017.0232. [DOI] [Google Scholar]
- 8.Taleb T., Benslimane A., Letaief K.B. Toward an effective risk-conscious and collaborative vehicular collision avoidance system. IEEE Trans. Veh. Technol. 2010;59:1474–1486. doi: 10.1109/TVT.2010.2040639. [DOI] [Google Scholar]
- 9.Baker T., García-Campos J.M., Reina D.G., Toral S., Tawfik H., Al-Jumeily D., Hussain A. GreeAODV: An energy efficient routing protocol for vehicular ad hoc networks; Proceedings of the 14th International Conference on Intelligent Computing (ICIC 2018); Wuhan, China. 15–18 August 2018; pp. 670–681. [Google Scholar]
- 10.Salem F., Elhillali Y., Nisar S. Efficient modelling of IEEE 802.11p MAC output process for V2X interworking enhancement. IET Netw. 2018;7:210–219. doi: 10.1049/iet-net.2017.0228. [DOI] [Google Scholar]
- 11.Bazzi A., Campolo C., Masini B.M., Molinaro A., Zanella A., Berthet A.O. Enhancing cooperative driving in IEEE 802.11 vehicular networks through full-duplex radios. IEEE Trans. Wirel. Commun. 2018;17:2402–2416. doi: 10.1109/TWC.2018.2794967. [DOI] [Google Scholar]
- 12.Singh R., Mann K.S. Improved TDMA protocol for channel sensing in vehicular ad hoc network using time lay; Proceedings of the 2nd International Conference on Communication, Computing and Networking (ICCCN 2018); Chandigarh, India. 29–30 March 2018; pp. 303–311. [Google Scholar]
- 13.Hasan K.F., Wang C., Feng Y., Tian Y.C. Time synchronization in vehicular ad-hoc networks: A survey on theory and practice. Veh. Commun. 2018;14:39–51. doi: 10.1016/j.vehcom.2018.09.001. [DOI] [Google Scholar]
- 14.Lin Z., Tang Y. Distributed multi-channel MAC protocol for VANET: An adaptive frame structure scheme. IEEE Access. 2019;7:12868–12878. doi: 10.1109/ACCESS.2019.2892820. [DOI] [Google Scholar]
- 15.Böhmländer D., Dirndorfer T., Al-Bayatti A.H., Brandmeier T. Context-aware system for pre-triggering irreversible vehicle safety actuators. Accid. Anal. Prev. 2017;103:72–84. doi: 10.1016/j.aap.2017.02.015. [DOI] [PubMed] [Google Scholar]
- 16.Shao C., Leng S., Zhang Y., Fu H. A multi-priority supported medium access control in vehicular ad hoc networks. Comput. Commun. 2014;39:11–21. doi: 10.1016/j.comcom.2013.11.002. [DOI] [Google Scholar]
- 17.Hussein S., Krings A., Azadmanesh A. VANET clock synchronization for resilient DSRC safety applications; Proceedings of the 2017 Resilience Week (RWS); Wilmington, DE, USA. 18–22 September 2017; pp. 57–63. [Google Scholar]
- 18.Wang S., Pervez A., Nekovee M. Converging time synchronization algorithm for highly dynamic vehicular ad hoc networks (VANETs); Proceedings of the 2010 7th International Symposium on Communication Systems, Networks & Digital Signal Processing (CSNDSP 2010); Newcastle upon Tyne, UK. 21–23 July 2010; pp. 443–448. [Google Scholar]
- 19.Chaurasia B.K., Alam M.I., Prakash A., Tomar R.S., Verma S. MPMAC: Clustering based MAC protocol for VANETs. Wirel. Pers. Commun. 2019;108:409–436. doi: 10.1007/s11277-019-06409-8. [DOI] [Google Scholar]
- 20.Pinto L., Almeida L. A robust approach to TDMA synchronization in aerial networks. Sensors. 2018;18:4497. doi: 10.3390/s18124497. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21.Jiang X., Du D.H. PTMAC: A prediction-based TDMA MAC protocol for reducing packet collisions in VANET. IEEE Trans. Veh. Technol. 2016;65:9209–9223. doi: 10.1109/TVT.2016.2519442. [DOI] [Google Scholar]
- 22.Liu Y., Zhou H., Huang J. OCA-MAC: A cooperative TDMA-based MAC protocol for vehicular ad hoc networks. Sensors. 2019;19:2691. doi: 10.3390/s19122691. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Cao S., Lee V.C. A novel adaptive TDMA-based MAC protocol for VANETs. IEEE Commun. Lett. 2018;22:614–617. doi: 10.1109/LCOMM.2017.2785378. [DOI] [Google Scholar]
- 24.Omar H.A., Zhuang W., Li L. VeMAC: A TDMA-based MAC protocol for reliable broadcast in VANETs. IEEE Trans. Mob. Comput. 2012;12:1724–1736. doi: 10.1109/TMC.2012.142. [DOI] [Google Scholar]
- 25.Haq A.U., Liu K., Latif M.B. A location-and mobility-aware clustering-based TDMA MAC protocol for vehicular Ad-hoc networks; Proceedings of the 2019 28th Wireless and Optical Communications Conference (WOCC); Beijing, China. 9–10 May 2019; pp. 1–5. [Google Scholar]
- 26.El-Gawad M.A.A., Elsharief M., Kim H. A cooperative V2X MAC protocol for vehicular networks. EURASIP J. Wirel. Commun. Netw. 2019;2019:65. doi: 10.1186/s13638-019-1382-8. [DOI] [Google Scholar]
- 27.Huang J., Li Q., Zhong S., Liu L., Zhong P., Wang J., Ye J. Synthesizing existing CSMA and TDMA based MAC protocols for VANETs. Sensors. 2017;17:338. doi: 10.3390/s17020338. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28.Nguyen V., Anh Khoa T., Zin Oo T., H Tran N., Seon Hong C., Huh E.N. Time slot utilization for efficient multi-channel MAC protocol in VANETs. Sensors. 2018;18:3028. doi: 10.3390/s18093028. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29.Hadded M., Muhlethaler P., Laouiti A., Saidane L.A. TDMA-aware routing protocol for multi-hop communications in vehicular ad hoc networks; Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC); San Francisco, CA, USA. 19–22 March 2017; pp. 1–6. [Google Scholar]
- 30.Boukhalfa F., Hadded M., Muhlethaler P., Shagdar O. An active signaling mechanism to reduce access collisions in a distributed TDMA based MAC protocol for vehicular networks; Proceedings of the 33rd International Conference on Advanced Information Networking and Applications (AINA 2019); Matsue, Japan. 27–29 March 2019; pp. 286–300. [Google Scholar]
- 31.Luo G., Li J., Zhang L., Yuan Q., Liu Z., Yang F. sdnMAC: A software-defined network inspired MAC protocol for cooperative safety in VANETs. IEEE Trans. Intell. Transp. Syst. 2018;19:2011–2024. doi: 10.1109/TITS.2017.2736887. [DOI] [Google Scholar]
- 32.Xu Z., Wang M., Wu Y., Lin X. Adaptive multichannel MAC protocol based on SD-TDMA mechanism for the vehicular ad hoc network. IET Commun. 2018;12:1509–1516. doi: 10.1049/iet-com.2017.1072. [DOI] [Google Scholar]
- 33.Pal R., Gupta N., Prakash A., Tripathi R. Adaptive mobility and range based clustering dependent MAC protocol for vehicular ad Hoc networks. Wirel. Pers. Commun. 2018;98:1155–1170. doi: 10.1007/s11277-017-4913-9. [DOI] [Google Scholar]
- 34.Shah A.S., Ilhan H., Tureli U. CB-MAC: A novel cluster-based MAC protocol for VANETs. IET Intell. Transp. Syst. 2018;13:587–595. doi: 10.1049/iet-its.2018.5267. [DOI] [Google Scholar]
- 35.Lyu F., Zhu H., Zhou H., Qian L., Xu W., Li M., Shen X. MoMAC: Mobility-aware and collision-avoidance MAC for safety applications in VANETs. IEEE Trans. Veh. Technol. 2018;67:10590–10602. doi: 10.1109/TVT.2018.2866496. [DOI] [Google Scholar]
- 36.Pal R., Prakash A., Tripathi R. Triggered CCHI multichannel MAC protocol for vehicular ad hoc networks. Veh. Commun. 2018;12:14–22. doi: 10.1016/j.vehcom.2018.01.007. [DOI] [Google Scholar]
- 37.Li S., Liu Y., Wang J. An efficient broadcast scheme for safety-related services in distributed TDMA-based VANETs. IEEE Commun. Lett. 2019;23:1432–1436. doi: 10.1109/LCOMM.2019.2923412. [DOI] [Google Scholar]
- 38.Nguyen V., Khanh T.T., Oo T.Z., Tran N.H., Huh E.N., Hong C.S. A cooperative and reliable RSU-assisted IEEE 802.11p-based multi-channel MAC protocol for VANETs. IEEE Access. 2019;7:107576–107590. doi: 10.1109/ACCESS.2019.2933241. [DOI] [Google Scholar]
- 39.Taherkhani N., Pierre S. Prioritizing and scheduling messages for congestion control in vehicular ad hoc networks. Comput. Netw. 2016;108:15–28. doi: 10.1016/j.comnet.2016.06.027. [DOI] [Google Scholar]
- 40.Chu J.H., Feng K.T., Lin J.S. Prioritized optimal channel allocation schemes for multi-channel vehicular networks. IEEE Trans. Mob. Comput. 2014;14:1463–1474. doi: 10.1109/TMC.2014.2359658. [DOI] [Google Scholar]
- 41.Campolo C., Molinaro A., Vinel A., Zhang Y. Modeling prioritized broadcasting in multichannel vehicular networks. IEEE Trans. Veh. Technol. 2011;61:687–701. doi: 10.1109/TVT.2011.2181440. [DOI] [Google Scholar]
- 42.Rana K.K., Tripathi S., Raw R.S. Analytical analysis of improved directional location added routing protocol for VANETs. Wirel. Pers. Commun. 2018;98:2403–2426. doi: 10.1007/s11277-017-4980-y. [DOI] [Google Scholar]
- 43.Wang L. VANET Toolbox: A Vehicular Network Simulator Based on DES. [(accessed on 17 September 2019)];2019 Available online: https://www.mathworks.com/matlabcentral/fileexchange/68437-vanet-toolbox-a-vehicular-network-simulator-based-on-des.
- 44.Wang L., Iida R., Wyglinski A.M. Vehicular network simulation environment via discrete event system modeling. IEEE Access. 2019;7:87246–87264. doi: 10.1109/ACCESS.2019.2922766. [DOI] [Google Scholar]
- 45.Lisboa A.C., De Souza F.H., Ribeiro C.M., Maia C.A., Saldanha R.R., Castro F.L., Vieira D.A. On modelling and simulating Open Pit mine through stochastic timed Petri nets. IEEE Access. 2019;7:112821–112835. doi: 10.1109/ACCESS.2019.2934718. [DOI] [Google Scholar]
- 46.Wang L., Iida R.F., Wyglinski A.M. Coordinated lane changing using V2V communications; Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall); Chicago, IL, USA. 27–30 August 2018; pp. 1–5. [Google Scholar]
- 47.Wang L., Iida R.F., Wyglinski A.M. Performance analysis of multichannel EDCA-based V2V communications via discrete event system; Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall); Honolulu, HI, USA. 22–25 September 2019; pp. 1–5. [Google Scholar]
- 48.Alodadi K., Al-Bayatti A.H., Alalwan N. Cooperative volunteer protocol to detect non-line of sight nodes in vehicular ad hoc networks. Veh. Commun. 2017;9:72–82. doi: 10.1016/j.vehcom.2017.03.001. [DOI] [Google Scholar]
- 49.Ullah U., Khan A., Altowaijri S.M., Ali I., Rahman A.U., Kumar V., Ali M., Mahmood H. Cooperative and delay minimization routing schemes for dense underwater wireless sensor networks. Symmetry. 2019;11:195. doi: 10.3390/sym11020195. [DOI] [Google Scholar]