Abstract
Stable matching problems with lower quotas are fundamental in academic hiring and ensuring operability of rural hospitals. Only few tractable (polynomial-time solvable) cases of stable matching with lower quotas have been identified; most such problems are -hard and also hard to approximate (Hamada et al. in Algorithmica 74(1):440–465, 2016). We therefore consider stable matching problems with lower quotas under a relaxed notion of tractability, namely fixed-parameter tractability. By cloning hospitals we focus on the case when all hospitals have upper quota equal to 1, which generalizes the setting of “arranged marriages” first considered by Knuth (Mariages stables et leurs relations avec d’autres problèmes combinatoires, Les Presses de l’Université de Montréal, Montreal, 1976). We investigate how a set of natural parameters, namely the maximum length of preference lists for men and women, the number of distinguished men and women, and the number of blocking pairs allowed determine the computational tractability of this problem. Our main result is a complete complexity trichotomy: for each choice of parameters we either provide a polynomial-time algorithm, or an -hardness proof and fixed-parameter algorithm, or -hardness proof and -hardness proof. As corollary, we negatively answer a question by Hamada et al. (Algorithmica 74(1):440–465, 2016) by showing fixed-parameter intractability parameterized by optimal solution size. We also classify all cases of one-sided constraints where only women may be distinguished.
Keywords: Stable marriage, Lower quotas, Fixed-parameter algorithms
Introduction
The Stable Marriage (SM) problem is a fundamental problem first studied by Gale and Shapley [19]. An instance of SM consists of a set of men, a set of women, and a preference list for each person ordering members of the opposite sex. We aim to find a stable matching, i.e., a matching for which there exists no pair of a man and a woman who prefer each other to their partners given by the matching; such a pair is called a blocking pair. Gale and Shapley proved [19] that any instance of SM admits at least one stable matching, and gave a polynomial-time algorithm, known as the Gale–Shapley algorithm, to find one. Gale and Shapley also considered the many-to-one extension of SM, known as the Hospitals/Residents (HR) problem. In HR, the two sets and that correspond to men and women in the SM problem are residents and hospitals, respectively. Each hospital has an upper quota on the number of residents in that it can accept. For HR it still holds true that a stable matching always exists, and can be found efficiently.
An extension of HR that is motivated by several real-world applications is the Hospitals/Residents with Lower Quota (HRLQ) problem, where hospitals declare both lower and upper quotas which bound the number of residents they can accept; as before, residents rank hospitals and vice versa. Now it is no longer true that a stable assignment always exists. The possible non-existence of stable assignments motivates the design of algorithms that find an assignment with a minimum number of blocking pairs; this is the task of the HRLQ problem. Indeed, the HRLQ problem and its variants have recently gained quite some interest from the algorithmic community [4, 8, 16, 22, 24, 26, 30, 40, 44, 45]. In his book, Manlove [36, Chapter 5.2] devotes an entire chapter to the algorithmics of different versions of the HRLQ problem.
The reason for this high interest in HRLQ is explained by its importance in several real-world matching markets [17, 18, 42] such as school admission systems, centralized assignment of residents to hospitals, or of cadets to military branches. Lower quotas are a common feature of such admission systems. Their purpose is often to remedy the effects of under-staffing that are explained by the well-known Rural Hospitals Theorem [20]: as an example, governments usually want to assign at least a small number of medical residents to each rural hospital to guarantee a minimum service level. Minimum quotas are also discussed in controlled school choice programs [13, 33, 43] where students are divided into a small number of types, and schools set lower bounds for each type. Such models can represent various forms of affirmative actions taken by schools to, e.g., admit a certain number of minority students [13]. Another example is the German university admission system for admitting students to highly oversubscribed subjects, where a certain percentage of study places is assigned according to high school grades or waiting time [43]. But lower quotas may also arise due to financial considerations: for instance, a business course with too few (tuition-paying) attendees may not be profitable. Certain aspects of airline preferences for seat upgrade allocations can be also modelled by lower quotas [33].
Much of the algorithmic research found that the HRLQ problem (in its different variants) is -hard, and thus considered intractable. A common approach then to identify tractable (polynomial-time solvable) cases of HRLQ; this avenue has lead to several beautiful algorithms [16, 26, 45]. However, restricting to polynomial-time solvability necessarily means (if ) that some original features of HRLQ must be restricted more or less, which may be undesirable in the application. Another approach aimed at addressing the intractability of HRLQ was the design of approximation algorithms. Unfortunately, it turns out that non-trivial approximation algorithms for HRLQ are highly unlikely to exist: Hamada et al. [24] showed that, unless , no algorithm with approximation guarantee can exist for any (which they complement by an algorithm with approximation guarantee ). In light of their strong inapproximability bounds, Hamada et al. explicitly suggested to consider a more relaxed notion of tractability for HRLQ, namely, fixed-parameter tractability. They particularly asked whether HRLQ is fixed-parameter tractable parameterized by the minimum number b of blocking pairs over all matchings meeting all lower and upper quota requirements.
In this paper we follow this avenue, and study the fixed-parameter tractability of HRLQ. It allows us to provide a fine-grained analysis of HRLQ, and the design of efficient algorithms for -hard variants of HRLQ for small parameter values. Our main focus will be the case of HRLQ when each hospital has unit upper quota. The reason is that by the frequently applied method of “cloning” hospitals, stable instances of HRLQ reduce to the case where each hospital has unit upper quota—and thus we can reduce stable instances of HRLQ to the SM setting with lower quotas. In fact, this is equivalent to the special case of SM where only a subset of women (or, equivalently, men) are distinguished by having also a unit lower quota. From now on, we refer to HRLQ with unit upper quotas as SMC (where C means that we have to cover the women/men who have a unit lower quota), to the special case of SMC with one-sided covering constraints, linking SMC and HRLQ, as SMC-1. So formally, in SMC a set of women and a set of men are distinguished, and a feasible matching is one where each person in gets matched. By the Rural Hospitals Theorem [20] we know that the set of unmatched men and women is the same in all stable matchings, so clearly, feasible stable matchings may not exist. Thus, we define the task in SMC as finding a feasible matching with a minimum number of blocking pairs.
Apart from the recent interest in HRLQ, its reduction SMC also serves as a “modern version” of a classical problem first introduced by Donald Knuth. Knuth [31] considered SM with “arranged marriages”, which are a set of man-woman pairs that must be matched with each other. He showed that the Gale–Shapley algorithm can be extended to decide the existence of a stable matching still in time for n-person instances, but in case of absence of a stable matching, minimizing the number of blocking pairs is -hard. Now in SMC, one does not prescribe any more which woman has to marry which man, but only requires certain women and men to marry without dictating their partner. There is a natural Turing reduction from SMC to the variant considered by Knuth. Coarse analysis into polynomial-time solvable and -hard cases has been studied by several researchers [1].
Another motivation for studying the SMC problem comes from the following scenario that we dub Control for Stable Marriage. Consider a two-sided market where each participant of the market expresses its preferences over members of the other party, and some central agent (e.g., a government) performs the task of finding a stable matching in the market. It might happen that this central agency wishes to apply a certain control on the stable matching produced: it may favour some participants by trying to assign them a partner in the resulting matching. Such a behaviour might be either malicious (e.g., the central agency may accept bribes and thus favour certain participants) or beneficial (e.g., it may favour those who are at disadvantage, like handicapped or minority participants). However, there might not be a stable matching that covers all participants the agency wants to favour; thus arises the need to produce a matching that is as stable as possible among those that fulfil our constraints—the most natural aim in such a case is to minimize the number of blocking pairs in the produced matching, which yields exactly the SMC problem. Similar control problems have been extensively studied in the area of social choice for voting systems [7, Chapter 7] and recently also for fair division scenarios [2], but have not yet been considered in connection to stable matchings.
Our Results
We provide an extensive algorithmic analysis of the SMC problem and its special case SMC-1. In our analysis, we examine how different aspects of the input influence the tractability of these problems. To this end, we apply the framework of parameterized complexity, which deals with computationally hard problems and focuses on how certain parameters of a problem instance influence its tractability; for background, we refer to the book by Cygan et al. [11]. We aim to design so-called fixed-parameter algorithms, which perform well in practice if the value of the parameter on hand is small (for the precise definitions, see Sect. 2).
The parameters we consider are
the number b of blocking pairs allowed,
the number of women with covering constraint,
the number of men with covering constraint,
the maximum length of women’s preference lists, and
the maximum length of men’s preference lists.
The choice of each of these parameters is motivated by the aforementioned applications. For instance, we seek matchings where ideally no blocking pairs at all or at least only few of them appear, to ensure stability of the matching and happiness of those getting matched. The number of women/men with covering constraints corresponds, for instance, to the number of rural hospitals for which a minimum quota specifically must be enforced, which we can expect to be small among the set of all hospitals accepting medical residents. Finally, preference lists of hospitals and residents can be expected to be small, as each hospital might not rank many more candidates than the number of positions it has to fill, whereas residents might rank only their top choices of hospitals.
We investigate in detail how these parameters influence the complexity of the SMC problem. A parameterized restriction of SMC with respect to the set means a (possibly parameterized) special case of SMC where each element of S is either restricted to be some constant integer, or regarded as a parameter, or left unbounded. Intuitively, these different choices for the elements of S correspond to their expected “range” in applications, from very small to mid-range to large (compared to the size of the entire system). By considering all combinations, we can flexibly model the whole range of applications mentioned above. We can even cover some cases of master lists, where all men’s preference lists are restrictions of the exact same total order over the women, and likewise all women’s preference lists are restrictions of the exact same total order over the men.
Theorem 1
Any parameterized restriction of SMC with respect to is in , or -hard and fixed-parameter tractable, or -hard and -hard with the given parameterization,1 and is covered by one of the results shown in Table 1.
Table 1.
Summary of our results for Stable Marriage with Covering Constraints
| Constants | Parameters | Complexity |
|---|---|---|
| , | in (Gale–Shapley algorithm) | |
| in (Theorem 7) | ||
| in (Theorem 7) | ||
| in (Theorem 8) | ||
| in (Observation 2) | ||
| b | in (Observation 1) | |
| -hard (Theorem 9) | ||
| -hard (Theorem 10) | ||
| -hard (Theorem 2) | ||
| -hard (Theorem 5) | ||
| (Theorem 11) | ||
| b | (Corollary 3) | |
| (Theorem 12) |
Here, denotes the maximum length of the preference list of any distinguished person
In particular, SMC is -hard parameterized by , even if there are no distinguished men (i.e., ), there is a master list over men as well as one over women, , and each distinguished woman finds only a single man acceptable.
We give a decision diagram in Sect. 7 to show that the presented results indeed cover all restrictions of SMC with respect to . Table 1 summarizes our results on the complexity of SMC. Note that some results are implied directly by the symmetrical roles of men and women in SMC, and thus are not stated explicitly. Here and later, we assume for simplicity that and .
As a special case, we answer a question by Hamada et al. [24] who gave an exponential-time algorithm that in time decides for a given instance I of HRLQ whether it admits a feasible matching with at most b blocking pairs;2 the authors asked whether HRLQ is fixed-parameter tractable parameterized by b. As shown by Theorem 1, SMC-1 and therefore also HRLQ is -hard when parameterized by b, already in a very restricted setting. Thus, the answer to the question by Hamada et al. [24] is negative: SMC-1, and hence HRLQ, admits no fixed-parameter algorithm with parameter b unless .
Related Work
There is a dynamically growing literature on matching markets with lower quotas [4, 8, 16–18, 22, 24, 26, 30, 40, 44, 45]. These papers study several variants of HRLQ, adapting the general model to the various particularities of practical problems. However, there are only a few papers which consider the problem of minimizing the number of blocking pairs [17, 24]. The most closely related work to ours is the paper by Hamada et al. [24]: they prove that the HRLQ problem is -hard and give strong inapproximability results; they also consider the SMC-1 problem directly and propose an time algorithm for it.
A different line of research connected to SMC is the problem of arranged marriages, an early extension of SM suggested by Knuth [31]. Here, a set of man-woman pairs is distinguished, and we seek a stable matching that contains as a subset. Thus, as opposed to SMC, we not only require that each distinguished person is assigned some partner, but instead prescribe its partner exactly. Initial work on arranged marriages [23, 31] was extended by Dias et al. [12] to consider also forbidden marriages, and was further generalized by Fleiner et al. [15] and Cseh and Manlove [10]. Despite the similar flavour of the studied problems, none of these papers have a direct consequence on the complexity of SMC.
Our work also fits into the line of research that addresses computationally hard problems in the area of stable matchings by focusing on instances with bounded preference lists [6, 27, 29, 32, 41] or by applying the more flexible approach of parameterized complexity [1, 3, 5, 37, 38].
Organization After the preliminaries in Sect. 2, we start with the main intractability result in Sect. 3, which answers Hamada et al.’s question. This result shows -hardness of SMC parameterized by even when and . Thus, we explore three directions to achieve tractability: (i) to lower b to be a constant, (ii) to lower to be a constant, or (iii) to lower either or to 2. We cover the cases (i) and (ii) in Sect. 5, and case (iii) in Sect. 6. In addition, Sect. 4 provides polynomial-time approximation results for HRLQ and SMC, used also in the polynomial-time algorithms of Sect. 5.
Preliminaries
An instance I of the Stable Marriage (SM) problem consists of a set of men and a set of women. Each person has a preference list L(x) that strictly orders the members of the other party acceptable for x. We thus write L(x) as a vector , denoting that is (strictly) preferred by x over for each i and j with . A matching M for I is a set of man-woman pairs appearing in each other’s preference lists such that each person is contained in at most one pair of M; some persons may be left unmatched by M. For each person x we denote by M(x) the person assigned by M to x. For a matching M, a man m and a woman w included in each other’s preference lists form a blocking pair if (i) m is either unmatched or prefers w to M(m), and (ii) w is either unmatched or prefers m to M(w). In the Stable Marriage with Covering Constraints (SMC) problem, we are given additional subsets and of distinguished people that must be matched; a matching M is feasible if it matches everybody in . The objective of SMC is to find a feasible matching for I with minimum number of blocking pairs. If only people from one gender are distinguished, then without loss of generality, we assume these to be women; this special case will be denoted by SMC-1.
The many-to-one extension of SMC-1 is the Hospitals/Residents with Lower Quotas (HRLQ) problem whose input consists of a set of residents and a set of hospitals that have ordered preferences over the acceptable members of the other party. Each hospital has a quota lower bound and a quota upper bound , which bound the number of residents that can be assigned to h from below and above. One seeks an assignment M that maps a subset of the residents to hospitals that respects acceptability and is feasible, that is, for each hospital h. Here, M(h) is the set of residents assigned to some by M. We say that a hospital h is under-subscribed if . For an assignment M of an instance of HRLQ, a pair of a resident r and a hospital h is blocking if (i) r is unassigned or prefers h to the hospital assigned to r by M, and (ii) h is under-subscribed or prefers r to one of the residents in M(h). The task in HRLQ is to find a feasible assignment with minimum number of blocking pairs.
Some instances of SMC may admit a master list over women, which is a total ordering of all women, such that for each man , the preference list L(m) is the restriction of to those women that m finds acceptable. Similarly, we consider master lists over men.
With each instance I of SMC (or HRLQ) we can naturally associate a bipartite graph whose vertex partitions correspond to and (or and , respectively), and there is an edge between a man and a woman (or between a resident and a hospital , respectively) if they appear in each other’s preference lists. We may refer to entities of I as vertices, or a pair of entities as edges, without mentioning explicitly. For a graph G, we denote its vertex set by V(G) and its edge set by E(G); furthermore, let denote the degree of vertex in G. A pathP in G is a series of vertices that contains each vertex at most once, with an edge of G connecting any two consecutive vertices of P. With a slight abuse of the notation, we will often identify paths with their edge sets; we will write to express that is a subpath of P. A matching in G is a set of edges such that no vertex in G is adjacent to more than one edges of M; note that a matching in an instance I of SMC indeed corresponds to a matching in the graph . For a matching M in G, a path P is called M-alternating, if among any two consecutive edges along P exactly one belongs to M. We will use a few other notions from the theory of matchings about the symmetric difference of matchings, see e.g., the book by Lovász and Plummer [35] for an introduction to this topic.
Parameterized complexity The framework of parameterized complexity deals with computationally hard problems, examining their complexity in a more detailed way than classical complexity theory. In a parameterized problem problem , each input instance I is associated with an integer k called the parameter. An algorithm which decides instances I of in time for some computable function f is called a fixed-parameter algorithm. Note that the dependence of the polynomial in the run time is constant, but the dependence on the parameter k can be arbitrary (and is typically exponential). However, if the parameter of a given instance is small, then such an algorithm can be useful in practice even if the overall size of the instance is large.
The class of problems admitting fixed-parameter algorithms is denoted by . To argue that a problem is not in , parameterized complexity provides a hardness theory. For two parameterized problems and , a parameterized reduction from to is a function f, computable by a fixed-parameter algorithm, that maps each instance of to an instance of such that (i) is a “yes”-instance of if and only if is a “yes”-instance of , and (ii) for some function g. The basic class of parameterized intractability is : proving a problem to be -hard is strong evidence that . Given some problem that is known to be -hard, a parameterized reduction from to some parameterized problem implies -hardness of as well.
For more on parameterized complexity, we refer the reader to the book by Cygan et al. [11].
Strong Parameterized Intractability of SMC
This section provides parameterized intractability and inapproximability results for SMC showing the hardness of finding feasible matchings with minimum number of blocking pairs. Namely, we prove SMC-1 to be -hard parameterized by the number b of blocking pairs we aim for plus the number of distinguished women, even in a very restricted setting.
Theorem 2
SMC-1 is -hard parameterized by , even if there is a master list over men as well as one over women, all preference lists are of length at most 3, and for each woman .
Before proving Theorem 2, let us quickly state a simple but useful claim.
Proposition 1
Let and be two matchings in an instance of SMC. Let (with ) be a maximal path in the symmetric differenc of and , denoted by . Then
P contains an edge that blocks either or , and
if is such that prefers to , then contains an edge that blocks either or .
Proof
We call a person a leftist if either , or and prefers to . Similarly, we call a rightist if either , or and prefers to . Observe that any person on P is either a leftist or a rightist. Moreover, the path P, and under the conditions of (b) also the path , must contain an edge such that x is a leftist and y is a rightist. Let be the matching that does not contain (where ). Then both x and y prefer being matched to each other as opposed to their situation in (where they may or may not be matched), proving both (a) and (b).
Proof of Theorem 2
We give a reduction from the -hard Multicolored Clique parameterized by the size of the solution [14]. Let G be the input graph, with its vertex set partitioned into k sets ; the task is to find a clique of size k in G containing exactly one vertex from each of the sets . We let denote those edges that run between and for some . We fix an ordering on the vertices and edges of G that places vertices of before vertices of whenever (the ordering on the edges of G can be chosen arbitrarily). We will write to denote the vertex following x in this ordering, and we let and denote the first and last vertices in , respectively. Similarly, we write for the edge following , and we let and denote the first and last edges in , respectively. We will also write and for the predecessor of x or , respectively. Also, we denote the h-th neighbor of some vertex x as n(x, h). For simplicity, we assume that G has no isolated vertices.
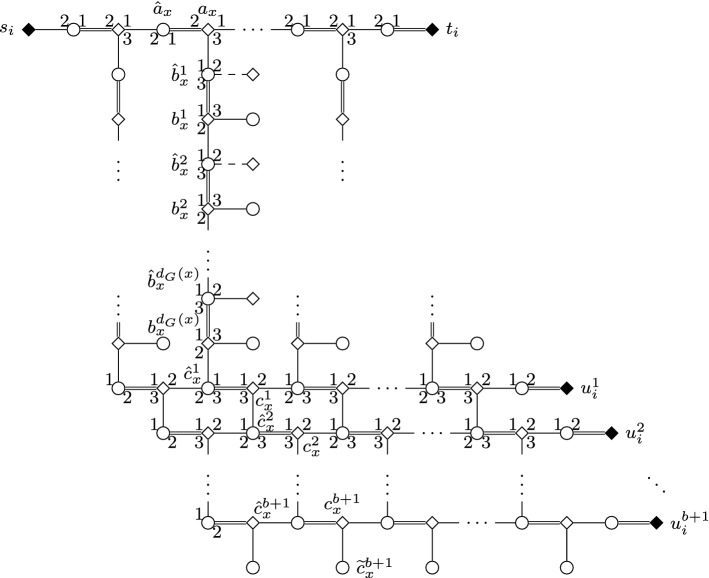
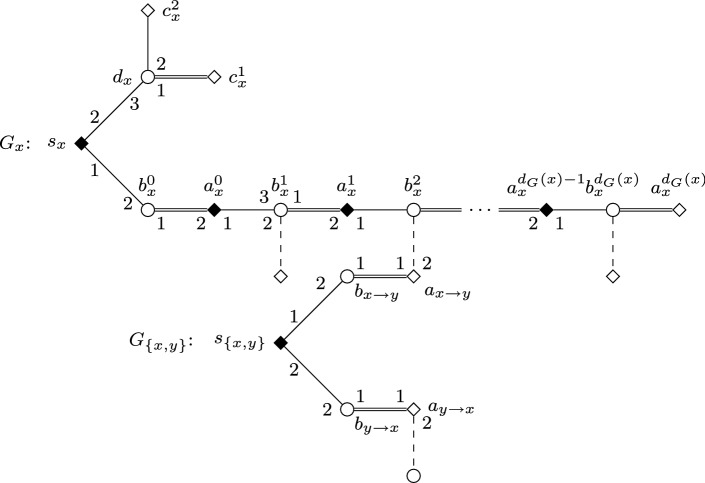
We construct an instance I of SMC as follows; see Figs. 1 and 2 for an illustration.
Fig. 1.
Node selecting gadget in the proof of Theorem 2. Throughout the paper, we use squares for women, circles for men; distinguished persons are denoted by filled squares/circles. The numbering of edges incident to some vertex (or, sometimes, arrows between edges) indicate preferences. Double edges denote edges of the stable matching , and dashed edges are those leaving some gadget
Fig. 2.
Edge selecting gadget in the reduction of Theorem 2
We set the number of blocking pairs allowed for I to be . Together with the instance I, we will define a stable (but not feasible) matching for I as well. If a woman w of I is matched by , we will denote the man by . Some women will need “dummy” partners in their preference lists: we denote the dummy of w by . The dummy will always appear as the last item on w’s preference list, and its preference list will always be .
For each i and j with , we construct an edge selecting gadget that involves women and , together with women , , and for each edge . All women in are matched by except for , and contains the man for each of these women w, together with additional dummies for each with x preceding y.
For each , we also construct a node selecting gadget involving women , and , together with women , , and for each . The men in include for each woman w of except for , and additional dummies and for each .
We define the following sets of women:
To define the set of women in I with covering constraint we let ; note . To finish the definition of I, we define the precise structure of these gadgets as well as the connections between them by the preference lists shown in Tables 2 and 3; when not stated otherwise, indices take all possible values. For simplicity, we write , , and for any vertex .
Table 2.
Preference lists of women and men in node selecting gadgets
| where , | |
| where , | |
| where , | |
| where , , | |
| where and , | |
| where , | |
| where , | |
| where , | |
| where , | |
| where , | |
| where , , and | |
| where , , and | |
| where , | |
| where , | |
| where , | |
| where , | |
| for any dummy woman . |
Table 3.
Preference lists of women and men in edge selecting gadgets
| where and x precedes y, | |
| where and x precedes y, | |
| where and x precedes y in V(G), | |
| where and x precedes y in V(G), | |
| where , | |
| where , | |
| where , | |
| where x precedes y in V(G), | |
| where x precedes y in V(G), | |
| where , | |
| for any dummy woman . |
Let us define a master list over all women as follows. The first women in are those in T, in any ordering. They are followed by women in A, ordered according to the reversed ordering over V(G), that is, precedes exactly if y precedes x. Next follow women of , ordered according to the reversed ordering over E(G). Next come women in . To order them, we first order those in B by putting before in if and only if x precedes y or and , then for each edge with x preceding y, and we insert just before , and we insert just before , thus determining the ordering of . After women in come women of C, with preceding exactly if or and x precedes y. We finish the definition of the master list by putting all women in at the end of in an arbitrary order.
The master list over men is derived from by letting precede whenever precedes in , and adding all dummies at the end in an arbitrary order. It is easy to check that the preference lists given in Tables 2 and 3 are indeed compatible with these master lists. This completes the construction of the instance.
We are going to prove that the constructed instance I admits a feasible assignment with at most b blocking pairs if and only if there is a clique of size k in the graph G.
“”: Suppose there is a feasible matching M of men to women with at most b blocking pairs. Let be the symmetric difference . Notice that for each woman , the difference must contain exactly one maximal path containing s as its endpoint, since the women in S must be matched in M, but are unmatched in . Similarly, no path of can contain a woman in , because these women are matched by to their only possible partners, and they must be matched by M as well, since is contained in . We call a maximal path P in with an endpoint s in S an improving path. We say that Pstarts at s and ends at its other endpoint, and we refer to the path starting at (or ) as (or , respectively).
We define the cost of some path P of as the number of blocking pairs for M involving a woman w that appears on P. By Proposition 1, each improving path contains at least one edge that is blocking for M, because no edge can block . Therefore, each path in has cost at least 1.
As there are exactly improving paths (as all women in S must be matched by M), we get a minimum cost of . Note also that the total cost of all paths in cannot exceed . Claim 1 is therefore crucial.
Claim 1
The following holds for any improving path P of :
P cannot end at a dummy for some .
P contains an edge for some that blocks M.
If P is not disjoint from for some i, then P has cost at least 2.
Proof of Claim 1
To prove (a), suppose for contradiction that P ends at , where . Clearly, P must contain at least one woman from each of the sets , . Fix h, and let us consider the last for which is incident to an edge of . Let if , or otherwise let . Then the edge yields a blocking pair in M, as , and thus prefers to w. This reasoning gives us different blocking pairs for M, one for each index h, contradicting our assumption on M.
To prove (b), let us consider the case when for some i; the argument goes the same way for the case where for some i and j. If P ends at for some , then forms a blocking pair with in M. If P does not end at a woman in A, then it must contain the edge for some x, in which case is again blocking in M, showing (b).
To see (c), first observe that if P is not disjoint from , then P ends in , simply because of its property that it contains edges from M and in an alternating fashion. Therefore, the last woman w on P must be in . If for some , then the edge is blocking M, as cannot get its first choice in M (and cannot be on P, as that would imply that is on P, contradicting the choice of w). If, by contrast, for some , then P must end at w by (a), and then c forms a blocking pair with the third man in its preference list (for whom c is the first choice). In either case, w is involved in a blocking pair, which together with the blocking pair guaranteed by (b) implies that P has cost at least 2.
This completes the proof of Claim 1.
Claim 1 proves that for each the improving path has cost at least 2. Since all the remaining improving paths have cost at least 1, and the total cost of these paths must be at most , we get that any path (or ) must have cost exactly 2 (or 1, respectively). Furthermore, it also follows that no other path of can enter or start in , for any i, as that would imply that the number of blocking pairs for M is more than b. In addition, it is not hard to see that does not contain any cycle, because all cycles in the graph underlying I contain two consecutive edges not in . Hence, it follows that the only connected component in that is not disjoint from is .
To deal with the possible courses the path may take in the graph for some , let denote the vertex in for which is the blocking edge guaranteed by statement (b) of Claim 1. Observe that either ends at or contains the edge . In either case, we say that selects from ; clearly, there can be only one vertex in selected by .
Consider now for some . Recall that has cost 1. Therefore, statement (b) of Claim 1 proves that the only blocking edge incident to some woman on must be for some . We say that selects the edge ; without loss of generality, let us assume that x precedes y. By statement (c) of Claim 1, we also know that cannot leave , which means that it can only have cost 1 if it ends at . In particular, it contains the edges and . Observe that the edge where h is such that cannot be blocking in M (as this would indicate a cost of 2 for ), yielding that must be matched to in M. By the arguments of the previous paragraph, this means that must contain the subpath . Hence, we obtain that x must be selected by . Similarly, from the fact that the edge where is not blocking in M we get that y must be selected by .
Thus, we obtain that if an edge is selected by for some i and j, then its endpoints must be selected by and . As this must hold for each pair of indices with , we obtain that there must be edges in G whose endpoints are among the k selected vertices. This can only happen if these edges are the edges of a clique of size k.
“”: Suppose now that G has a clique of size k formed by the vertices , with for each . Instead of directly defining the required matching M that is feasible and admits at most b blocking pairs, we give as the union of paths for , and paths for , defined as follows.
We set as the path
Similarly, we define
It is straightforward to verify that the blocking pairs for M are then the k edges , , the k edges , and the edges , . The feasibility of M is trivial; this completes the proof of Theorem 2.
A fundamental hypothesis about the complexity of -hard problems is the Exponential Time Hypothesis (ETH), which stipulates that algorithms solving all Satisfiability instances in subexponential time cannot exist [28]. Assuming ETH, the fundamental Clique problem parameterized by solution size k was shown not to admit any algorithm giving the correct answer in time for all n-vertex instances and any computable function f [9, Thm. 5.4]. The known reduction from Clique to Multicolored Clique does not change the parameter [14]. Finally, in the proof of Theorem 2, an instance of Multicolored Clique with solution size k is reduced to an instance of SMC-1 with parameter .
Corollary 1
Assuming ETH, SMC-1 cannot be solved in time for any computable function , even if there is a master list over men and over women, all preference lists have length at most 3, and each woman in finds only a single man acceptable.
Polynomial-Time Approximation
Here we first provide a polynomial-time algorithm that yields an approximation for HRLQ with factor , where is the maximum length of residents’ preference lists and is the total sum of all lower quotas. Then we use this result to propose an exact polynomial-time algorithm for HRLQ for the case where both and are constant. Recall that in HRLQ, our objective is to find an assignment that satisfies all quota lower and upper bounds and minimizes the number of blocking pairs.
Theorem 3
Let I be an instance of HRLQ. Let denote the maximum length of residents’ preference lists, and let denote the sum of lower quota bounds taken over all hospitals in I. There is an algorithm that in polynomial time either outputs a feasible assignment for I with at most blocking pairs, involving only residents, or concludes that no feasible assignment exists.
Proof
Let denote the set of hospitals with positive lower quotas. We start by finding an assignment that assigns residents to each hospital , and has the following property:  Such an assignment can be obtained as follows. We start from an arbitrary assignment M that assigns residents to each (if no such assignment exists, then we can stop and reject); such an assignment, if existent, can be found in polynomial time by an algorithm of Hopcroft and Karp [25]. Then we greedily re-assign residents to hospitals of , one-by-one: at each step, we take a hospital , and if there exists a resident r not assigned to any other hospital in that h prefers to the least preferred resident in M(h), then we replace with r in M(h). If this step cannot be applied anymore, then we arrive at an assignment with the desired property ().
Such an assignment can be obtained as follows. We start from an arbitrary assignment M that assigns residents to each (if no such assignment exists, then we can stop and reject); such an assignment, if existent, can be found in polynomial time by an algorithm of Hopcroft and Karp [25]. Then we greedily re-assign residents to hospitals of , one-by-one: at each step, we take a hospital , and if there exists a resident r not assigned to any other hospital in that h prefers to the least preferred resident in M(h), then we replace with r in M(h). If this step cannot be applied anymore, then we arrive at an assignment with the desired property ().
Given , we reduce the upper quotas of each hospital by , set all lower quotas to 0, and delete all residents in . We then find a stable assignment in the resulting instance ; note that is an instance of HR, so we can find in polynomial time [19]. Finally, we output . Clearly, is feasible. Also, any blocking pair that admits must involve either a hospital from or a resident from by the stability of with respect to . Observe that if some is involved in some blocking pair of , then we must have . To see this, recall that each resident that is preferred by h to its least preferred resident in must be in because of property (), and furthermore, h is under-subscribed in (within I) if and only if h is under-subscribed in (within ). Therefore, we can conclude that each blocking pair for must involve some resident in ; observe that . Since each resident in is incident to at most edges not in , we also have that admits at most blocking pairs.
If both and are constant, then Theorem 3 implies that HRLQ becomes polynomial-time solvable. Indeed, we can use the following simple strategy, depending on the number b of blocking pairs allowed: if , then we apply Theorem 3 directly; if , then we use the algorithm by Hamada et al. [24] running in time which is polynomial, since b is upper-bounded by a constant.
Corollary 2
If both the maximum length of residents’ preference lists and the total sum of all lower quotas is constant, then HRLQ is polynomial-time solvable.
Another application of Theorem 3 is an approximation algorithm that works regardless of whether or is a constant. In fact, the algorithm of Theorem 3 can be turned into a -factor approximation algorithm as follows. First, we find a stable assignment for I in polynomial time using the extension of the Gale–Shapley algorithm for the Hospitals/Residents problem. If is not feasible, then by the Rural Hospitals Theorem [20], we know that any feasible assignment for I must admit at least one blocking pair; hence, the algorithm presented in Theorem 3 clearly yields an approximation with (multiplicative and also additive) factor .
To close this section, we also state an analogue of Theorem 3 that deals with SMC: it can handle covering constraints on both sides, but assumes that all quota upper bounds are 1.
Theorem 4
There is an algorithm that in polynomial time either outputs a feasible matching for an instance I of SMC with at most blocking pairs, or concludes that I admits no feasible matching.
Proof
The proof uses the same ideas as those used in our proof for Theorem 3, so the reader may skip the proof below, which we only include for completeness.
We start by finding an arbitrary matching M that covers each distinguished person (if no such matching exists, then we can stop and reject); such a matching, if existent, can be found in polynomial time by standard flow techniques. We assume, without loss of generality, that each edge in M is incident to some distinguished person. Let us define , and let be the set of those persons whose partner M(x) is also in .
We proceed by modifying M into a matching that covers and has the following property: ![]() Such an assignment can be obtained as follows. We greedily assign partners to the men and women in , one-by-one: at each step, we take a person , and if x forms a blocking pair (with respect to the current matching) with some y that is not the partner of a distinguished person, then we replace the partner of x with y: we add the edge to the matching, and delete all the other edges incident to x or y. Observe that the obtained matching is still feasible. If this step cannot be applied anymore, then we arrive at a matching with the desired property (); note also that each edge in is incident to some distinguished person.
Such an assignment can be obtained as follows. We greedily assign partners to the men and women in , one-by-one: at each step, we take a person , and if x forms a blocking pair (with respect to the current matching) with some y that is not the partner of a distinguished person, then we replace the partner of x with y: we add the edge to the matching, and delete all the other edges incident to x or y. Observe that the obtained matching is still feasible. If this step cannot be applied anymore, then we arrive at a matching with the desired property (); note also that each edge in is incident to some distinguished person.
Given , we delete all men and women covered by . We then find a stable matching in the resulting instance ; note that is an instance of Stable Marriage, so we can find in polynomial time [19]. Finally, we output . Clearly, is feasible. Also, any blocking pair that admits must involve a person covered by due to the stability of with respect to .
We claim that any blocking pair involves a person whose partner by is distinguished, so either or . We can assume that x is covered by (because this holds for at least one of x and y). To see the claim, first note that if x is not distinguished, then must be distinguished, because each edge of contains a distinguished person. Second, if , then either (in which case ) or because of property (). Therefore, we can conclude that each blocking pair for must involve the partner of some distinguished resident. The partners of distinguished women can be incident to at most blocking pairs, and similarly, the partners of distinguished men can be incident to at most blocking pairs, proving the theorem.
SMC with Bounded Number of Distinguished Persons or Blocking Pairs
In Theorem 2 we proved -hardness of SMC-1 for the case where , with parameter . Here we investigate those instances of SMC and SMC-1 where the length of preference lists may be unbounded, but either b, or the number of distinguished persons is constant.
First, if the number b of blocking pairs allowed is constant, then SMC can be solved by simply running the extended Gale–Shapley algorithm after guessing and deleting all blocking pairs. This complements the result by Hamada et al. [24].
Observation 1
SMC can be solved in time , where b denotes the number of blocking pairs allowed in the input instance I.
In Theorem 5 we prove hardness of SMC-1 even if only one woman must be covered. If we require preferences to follow master lists, then a slightly weaker version of Theorem 5, where , still holds.
Theorem 5
SMC-1 is -hard parameterized by , even if , , and .
Proof
We present a reduction based on the one from Multicolored Clique given in the proof of Theorem 2. Given some graph G and an integer k as inputs, we are going to re-use the instance I constructed in the proof of Theorem 2. Recall that I has a feasible matching with at most blocking pairs if and only if G has a clique of size k. Recall also that the set of women that must be covered in I is ; here we denote this set by . We define a modified instance of SMC as follows. For each , we create a forcing gadget which apart from w contains the newly introduced women and men . We also add the distinguished woman s, who must be covered in , and the unique man t in L(s). See Fig. 3 for an illustration.
Fig. 3.
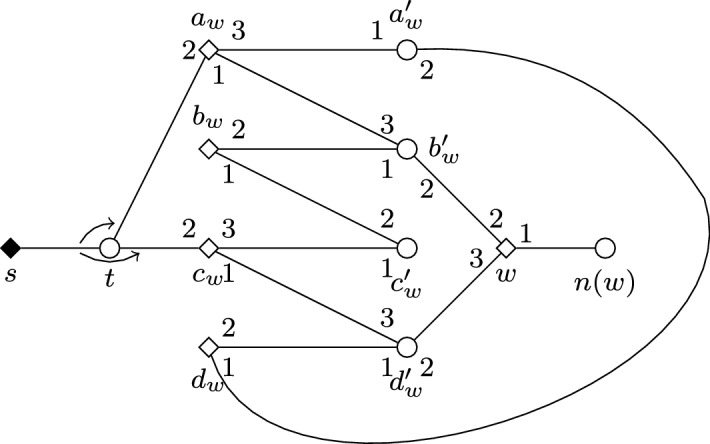
Illustration depicting the forcing gadget in the proof of Theorem 5
Let n(w) denote the unique man acceptable for some in I. Additionally, we let , and we write [Y] for an arbitrarily fixed ordering of the elements of Y. The preferences of the newly introduced men and women, as well as the modified preferences of those agents that find them acceptable, is given below. Here, again, indices take all possible values, and w can be any woman in . We let contain all other women and men defined in I, having the same preferences as in I.
We will show that has a feasible matching with at most b blocking pairs if and only if I has such a matching; this clearly proves the theorem.
First observe that any feasible matching for contains the edge . Thus, if some woman y in Y is not matched by to her first choice, then is blocking in . Consider now for some . It is straightforward to check that if , then there are at least two blocking pairs incident to a woman in . Indeed, assume first that is the only blocking pair in ; this quickly implies and , which in turn leads to blocking , a contradiction. Second, assume that does not block ; from this follows and we have that is a blocking pair for . Now either is blocking (in which case our claim holds), or we get , which implies that blocks , again a contradiction.
Now, let be the women in that must be covered in I, i.e., . Consider the number of blocking pairs for that involve a woman either in the gadget or in a gadget for some . On the one hand, if some is not matched by to n(w), then because of the blocking pairs in . On the other hand, if each is matched by to n(w), then using the arguments of the proof for Theorem 2, we again know because of the blocking pairs in . Also, can only be achieved if (i) , as otherwise would be blocking for , in addition to the two blocking pairs in , and (ii) for each , as otherwise we would have (so as to avoid having four blocking pairs due to women in and ), implying at least one blocking pair in in addition to those in .
Analogously, let denote the number of blocking pairs for that involve a woman either in the gadget or in a gadget for some . Then either , or we know that for both women ; in this case, from the proof of Theorem 2 we get . However, supposing that has at most blocking pairs, it follows that and must hold for each and each i, j with , respectively.
Along the same lines as in the proof of Theorem 2, it can also be verified that for each pair of indices i, j can only be achieved if contains a path in each gadget . From for each we get that such a path contains at least one blocking pair. This implies , as otherwise we would end up with because of the blocking pairs incident to women of .
Altogether, we have proved that for each . Hence, the restriction of to I yields a feasible matching for I that admits at most b blocking pairs.
For the other direction, suppose that I has a feasible matching M. Then it is easy to see that adding the edges , , , and for each together with the edge to M yields a feasible matching for that contains exactly the same number of blocking pairs in as M does in I.
Theorem 6
SMC-1 is -hard parameterized by , even if there is a master list over men as well as one over women, , , and for each .
Proof
The proof is very similar to the one for Theorem 5, so we will only sketch it. Again, we are going to re-use the instance I constructed in the proof of Theorem 2, and construct a modified instance of SMC, adding only two new women and and two men and to I. We append and , in this order, to the master list over women, and similarly, we append and to the master list over men. We define the women to be covered in as and .
Again, we denote the set of women to be covered in I by , and we denote by n(w) the unique man acceptable for some in I. The preferences of the newly introduced men and women, as well as the modified preferences of those agents that find them acceptable, is given below (here, denotes the ordering of given by the master list). We let contain all other women and men defined in I, having the same preferences as in I.
Arguing analogously as before in the proof of Theorem 5, one can show that has a feasible matching with at most b blocking pairs if and only if I has such a matching; this suffices to prove the theorem.
To contrast our intractability results, we show next that if each of the four parameters , , , and is constant, then SMC becomes polynomial-time solvable. Our algorithm relies on the observation that in this case, the number of blocking pairs in an optimal solution is at most by Theorem 4. Note that for instances of SMC-1, Theorem 7 yields a polynomial-time algorithm already if both and are constant.
Theorem 7
SMC can be solved in time .
Proof
By Theorem 4, there is a matching with at most blocking pairs. Hence, if the number b of blocking pairs allowed is at least , then we can simply run the algorithm of Theorem 4. Otherwise, we can use Observation 1, which gives us the required run time.
Importantly, restricting only three of the values , , , and to be constant does not yield tractability for SMC, showing that Theorem 7 is tight in this sense. Indeed, Theorem 5 implies immediately that restricting the maximum length of the preference lists on only one side still results in a hard problem: SMC remains -hard with parameter , even if , , and . On the other hand, Theorem 2 shows that the problem remains hard even if and .
SMC with Preference Lists of Length at Most Two
In this section we investigate the computational complexity of SMC where the maximum length of preference lists is bounded by 2 on one side. This restriction leads to important tractable special cases: we obtain both polynomial-time algorithms and fixed-parameter tractability results for various parameterizations.
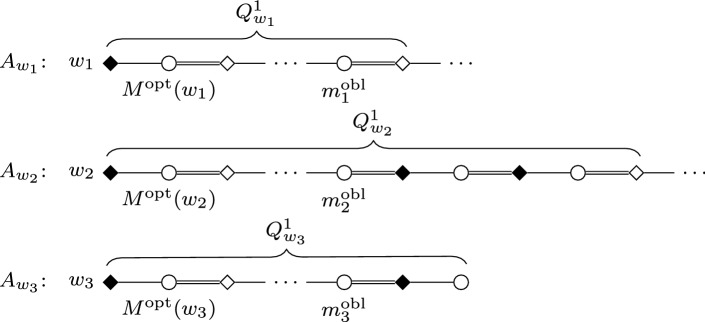
Let I be an instance of SMC with underlying graph G. Let be a stable matching in I, and let and denote the set of distinguished men and women, respectively, unmatched by . Furthermore, let and denote the set of all men and women, respectively, unmatched by . A path P in G is called an augmenting path, if is a matching, and either both endpoints of P are in , or one endpoint of P is in , and its other endpoint is not distinguished. This definition ensures that for an augmenting path P, the set of distinguished men and women that are matched in strictly contains the set of distinguished men and women matched in .3 We will call an augmenting path Pmasculine or feminine if it contains a man in or a woman in , respectively; if P is both masculine and feminine, then we call it neutral. If P is not neutral, then we say that it starts at the (unique) person from it contains, and ends at its other endpoint.
Covering Constraints on One Side
Here we deal with the SMC-1 problem where only women need to be covered. We first give a polynomial-time algorithm for SMC-1 when each man finds at most two women acceptable, and then show -hardness of SMC-1 for instances where each woman finds at most two men acceptable. We start by considering the special case of SMC-1 where .
Theorem 8
There is a polynomial-time algorithm for the special case ofSMC-1 where each man finds at most two women acceptable.
High-Level Description The main observation behind Theorem 8 is that if , then any two augmenting paths starting from different women in are almost disjoint, namely they can only intersect at their endpoints. Thus, we can modify the stable matching by selecting augmenting paths starting from each woman in in an almost independent fashion: intuitively, we simply need to take care not to choose paths sharing an endpoint—a task which can be managed by finding a bipartite matching in an appropriately defined auxiliary graph. To ensure that the number of blocking pairs in the output is minimized, we will assign costs to the augmenting paths. Roughly speaking, the cost of an augmenting path P determines the number of blocking pairs introduced when modifying along P (though certain special edges need not be counted); hence, our problem reduces to finding a bipartite matching with minimum weight in the auxiliary graph.
To present the algorithm of Theorem 8 in detail, we start with the following properties of augmenting paths which are easy to prove using that :
Proposition 2
Suppose . Let and be augmenting paths starting at women and , respectively.
If , then and are either vertex-disjoint, or they both end at some , with .
If there is an edge of G (with and ) connecting and , then and or must end at m.
If and P is the maximal common subpath of and starting at , then either , or and both end at some and .
With a set P of edges (typically a set of augmenting paths) where is a matching, we associate a cost, which is the number of blocking pairs that admits. A pair for some and is special, if and w is the second (less preferred) woman in L(m). As it turns out, such edges can be ignored during certain steps of the algorithm; thus, we define the special cost of P as the number of non-special blocking pairs in .
Lemma 1
For vertex-disjoint augmenting paths and with cost and , respectively, the cost of is at most . Further, if the cost of is less than , then the following holds for : there is a special edge with ending at m and w appearing on ; moreover, is blocking in , but not in .
Proof
First observe that if some edge has a common vertex with only one of the paths and , say , then is blocking in if and only if it is blocking in .
Consider now the case when connects and . By Proposition 2, this implies that one of the paths, say , ends at (and w lies on ). Clearly, is not blocking in , by the stability of . If, on the one hand, w is the first choice of m, then is blocking in exactly if it is blocking in . If, on the other hand, is special, then it cannot be blocking in , but it might be blocking in . Putting all these facts together, the lemma follows immediately.
We are ready to provide the algorithm, in a sequence of four steps.
Step 1: Computing all augmenting paths By Proposition 2, if we delete from the union of all augmenting paths starting at some , then we obtain a tree. Furthermore, these trees are mutually vertex-disjoint for different starting vertices of . This allows us to compute all augmenting paths in linear time, e.g., by an appropriately modified version of a depth-first search algorithm (so that only augmenting paths are considered). During this process, we can also compute the special cost of each augmenting path in a straightforward way.
Step 2: Constructing an auxiliary graph Using the results of the computation of Step 1, we construct an edge-weighted single bipartite graph as follows. To define the vertices of we set and , so for each woman we create a corresponding new vertex . The edge set E contains an edge for each , as well as an edge whenever , and there exists an augmenting path with endpoints w and m. We define the weight of an edge as the minimum special cost of any augmenting path starting at w and not ending in , and we define the weight of an edge with and as the minimum special cost of any augmenting path with endpoints w and m.
Step 3: Computing a minimum weight matching We compute a matching in covering U and having minimum weight; this can be done in polynomial time by, e.g., the Hungarian method [34]. Observe that the matching corresponds to a set of augmenting paths that are mutually vertex-disjoint by Proposition 2. Recall that the special cost of is the weight of the edge in incident to w.
Step 4: Eliminating blocking special edges In this step, we modify iteratively. We start by setting . At each iteration we modify as follows. We check whether there exists a special edge that is blocking in . If yes, then notice that is not matched in , because is special and thus . Let P be the path of containing . We modify by truncating P to its subpath between its starting vertex and , and appending to it the edge . This way, becomes an edge of the matching . The iteration stops when there is no special edge blocking . Note that once a special edge ceases to be blocking in , it cannot become blocking again during this process, so the algorithm performs at most iterations. For each , let denote the augmenting path in covering w at the end of Step 4; we define and output the matching .
This completes the description of the algorithm; we now provide its analysis.
Lemma 2
is a feasible matching for I, and the number of blocking pairs for is at most the weight of .
Proof
Consider the situation when the iteration in Step 4 deals with a special edge blocking in . Notice that since is the second woman in (by the definition of a special edge), and since is blocking in , we know that is unmatched in , that is, does not lie on any of the augmenting paths in . From this follows that the augmenting paths in , and hence in , remain mutually vertex-disjoint. Therefore, is indeed a matching. As it covers , and no augmenting path ends at a woman in , matching is feasible.
Clearly, Step 4 ensures that there are no blocking special edges in . Note that when the algorithm modifies for some , at most one new blocking pair may arise with respect to , and from the stability of M and Proposition 2 it follows that such an edge must be a special edge (incident to the man at which ends before its modification). This means that Step 4 gets rid of all blocking special edges without introducing any non-special blocking edges. Hence, we obtain that the cost of is at most the special cost of , for each . By Lemma 1, the number of blocking pairs that admits is at most the sum of the costs of all augmenting paths in ; this finishes the proof.
To show that our algorithm is correct and is optimal, by Lemma 2 it suffices to prove that the weight of is at most the number of blocking pairs in , where denotes an optimal solution in I. To this end, we are going to define a matching covering in whose weight is at most the number of blocking pairs in .
Clearly, contains an augmenting path covering w for each . If some ends at a man , then clearly no other path in can end at m. So let us take the matching in that includes all pairs where ends at for some . Also, we put into if does not end at a man of . Note that is indeed a matching.
It remains to show that the weight of is at most the number of blocking pairs in . By definition, the weight of is at most the sum of the special costs of the paths for every . By Lemma 1, any non-special blocking pair in remains a blocking pair in , and hence in as well. Hence, there is a matching in with weight at most the number of blocking pairs in an optimal solution, implying the correctness of our algorithm. As the algorithm runs in polynomial time, Theorem 8 follows.
By contrast to Theorem 8, if men may have preference lists of length 3, then SMC-1 (and hence SMC) is -hard even if each woman finds at most two men acceptable.
Theorem 9
SMC-1 is -hard even if and .
Proof
We give a reduction from the -hard Vertex Cover problem, asking whether the input graph G has a vertex cover of size at most k. We order the vertices of G arbitrarily, and denote the h-th neighbor of some vertex x by n(x, h) for any .
Let us construct an instance I of SMC as follows; see Fig. 4 for an illustration. For each vertex we construct a node gadget which contains women , , and , and men , and . For each edge we also construct an edge gadget involving women , and , and men and . Furthermore, there are two edges in the underlying graph connecting to and , namely and where and .
Fig. 4.
Illustration of a node gadget and an edge gadget constructed in the proof of Theorem 9. Double edges denote edges of a stable matching for I, and dashed edges are those leaving some gadget. The example depicted assumes
The preference lists of I are given in Table 4. Let the set of women with covering constraints be
and set the number of blocking pairs allowed to be . We are going to prove that I admits a feasible matching with at most blocking pairs if and only if there is a vertex cover of size k in the graph G.
Table 4.
Preference lists of women and men in the proof of Theorem 9
| where and , | |
| where , | |
| where , | |
| where x precedes y, | |
| where . |
When not stated otherwise, indices take all possible values
“”: Let M be a feasible matching with at most blocking pairs. We say that the cost of some gadget (or ) is the number of edges blocking M which are incident to some man of (or , respectively.) We will prove that the set S of vertices x for which has cost at least 2 is a vertex cover of G.
First, let us consider some x for which . In this case, both and form a blocking pair for M with , implying . Second, let us consider some x with . Since each with must be matched by M (because it is contained in ), we obtain for each such h. Hence, and form a blocking pair for M. Moreover, if the woman is unmatched in M for some y, then is also a blocking pair in M (where ), and implies a cost of at least 2 for . Therefore, we can observe that if , then must be matched by M to for each neighbor y of x in G.
However, for any , M must match either to or to (because is contained in ), which means that or . This proves that S is indeed a vertex cover for G. Moreover, the number of vertices in S can be at most k, since each with has cost at least 2, each with has cost at least 1, and the total cost of all gadgets cannot exceed our budget .
“”: Given a vertex cover S of size at most k for G, we define a matching M with the desired properties. Namely, for each we set and for each . In this case, are unmatched by M, both forming a blocking pair with . By contrast, all of the men get their first choices.
Next, for each we set , , and for each . Note that is unmatched by M, and thus forms a blocking pair with . Observe also that is not contained in any blocking pair.
Finally, for some , let us assume (since S is a vertex cover, it contains x or y). We set and . Note that gets her first choice, so it cannot be involved in a blocking pair. Although is unmatched by M, we know that it cannot form a blocking pair with where , because and hence is assigned her first choice by M. Thus, no man or woman of some edge gadget participates in a blocking pair, and therefore we obtain that the total number of blocking pairs for M is exactly .
Since M is feasible, the theorem follows.
Covering Constraints on Both Sides
Let us now investigate the complexity of SMC with covering constraints both for men and women. If we restrict the maximum length of preference lists on both sides to be at most 2, SMC becomes linear-time solvable. To see this, observe that by , the underlying graph G must be a collection of paths and cycles. Thus, we can process the connected components of G one by one. Applying dynamic programming on each component K, we can determine the minimum number of blocking pairs for any matching that is feasible for K, together with a matching for K that admits blocking pairs. If K is a path, then this can be done in a straightforward manner, traversing the edges of K one by one in linear time. If K is a cycle, then we can pick any edge e of K, guess whether it is contained in , or blocks , or neither of the two; we can then process the remainder of K (which is a path) taking into account our guess for e. To compute the minimum number of blocking pairs that a feasible matching admits in our instance, we can simply sum up the values over each connected component K of G. Hence, we arrive at the following.
Observation 2
Instances of SMC with are linear-time solvable.
Recall that the case where and is -hard by Theorem 9, even if there are no distinguished men to be covered. However, switching the roles of men and women in Theorem 8, we obtain that if there are no women to be covered, then guarantees polynomial-time solvability for SMC. This raises the natural question whether SMC with can be solved efficiently if the number of distinguished women is bounded. Next we show that this is unlikely, as the problem turns out to be -hard for .
Theorem 10
SMC is -hard, even if , and there is only one man m with .
Proof
We present a reduction from the following special case of Exact-3-Cover. We are given a set , a family of subsets of U, each having size 3, such that each element of U occurs in at most three sets of . The task is to decide whether there exists a collection of n/3 sets in whose union covers U; such a collection of subsets is called an exact cover for U. This problem is -complete [21, GT2]. We construct an equivalent instance I of SMC as follows.
The set of women in I contains the women , , , , and for each , women x and y, as well as two women for each element contained in for each . The men defined in I are , , , , and for each , a man for each , a man for each element contained in for each , plus one additional man . (The pairs form a stable matching in I.) The only distinguished woman in I is x, and the set of distinguished men is . The preferences of each person are as shown in Table 5. Note that since each subset contains three elements, and each element is contained in at most three subsets from , we get that all men except for have a preference list of length at most 3, as promised. To finish the construction, we set the number of allowed blocking pairs to be .
Table 5.
Preference lists of women and men in the proof of Theorem 10
| for , | |
| for the unique that satisfies , | |
| for and , | |
| where , | |
| where and is some fixed ordering of |
We denote by the index i for which is the h-th element in . When not stated otherwise, indices take all possible values
We claim that I admits a feasible matching with at most b blocking pairs if and only if is a “yes”-instance of Exact-3-Cover.
“”: Suppose that M is a feasible matching for I with at most b blocking pairs. Clearly, as x is distinguished, M must contain the edge . Thus, is blocking in M. Second, since is distinguished for each , we get that M matches either to or to , which in turn implies that either or blocks M, leading to m additional blocking pairs for M. Third, consider now any man , : as is distinguished, we know for some j such that contains . In this case, is also a blocking pair for M, yielding n blocking pairs of such form. Thus, if denotes the number of blocking pairs among the edges for indices i and j with , then we get . This adds up to blocking pairs so far.
Let us define the set of those edges that are incident to , , , or , but not to for some ; note that these sets are pairwise disjoint, and none of them contains any of the (possibly) blocking edges mentioned in the previous paragraph.
Let k be the number of indices j for which contains no blocking pairs for M; we call such indices (and the subsets corresponding to them) selected. The non-selected indices clearly correspond to at least blocking pairs for M (each contained in for some j).
Suppose now that j is selected. Then, since is not blocking, we get , since prefers to its partner x. This implies that , as otherwise would be blocking in M. Similarly, from this we obtain . Moreover, for each , to ensure that does not block M where is the h-th element of , we must have . Hence, must be blocking in M. Since this holds for each and each selected j, we get .
Summing up the blocking pairs identified so far, we know that M admits at least blocking pairs. Using that this must be upper-bounded by , it is easy to show that only is possible. This yields that there exist exactly n/3 selected indices, and for all such indices j all the edges for which are blocking with respect to M. Moreover, we also must have , as otherwise the number of blocking pairs would exceed b.
However, observe that for each , there must exist some j with for which the pair is blocking in M (because is distinguished), implying that for each there must exist some selected that contains . Since there are exactly n/3 selected sets in , we get that they form an exact covering of U.
“”: Suppose that is a “yes”-instance of Exact-3-Cover. Let J be the set of indices describing a solution, meaning that the subsets with form an exact covering of U; clearly, . We define as the unique index j in J for which . We define a feasible matching M for I with exactly b blocking pairs as follows (indices take all possible values, if not stated otherwise).
It is easy to check that M indeed is feasible, and the blocking pairs it admits are exactly the pairs , for each , for each , for each , and for each . This proves the lemma.
Contrasting Theorem 10, we establish fixed-parameter tractability of the case with three different parameterizations. Considering our five parameters, the relevant cases (whose tractability or intractability does not follow from our results obtained so far) are as follows, assuming throughout. Since letting the number b of blocking pairs and the number of distinguished women to be unbounded (while assuming ) results in -hardness by Theorem 9, in order to obtain fixed-parameter tractability, we need to take either b or as a parameter. However, taking only as a parameter is not likely to result in tractability, as the case is still -hard by Theorem 10. Thus we need to take either or as an additional parameter. Altogether, this results in the following parameterizations of the SMC problem, each case subject to the assumption :
taking b as the parameter,
taking as the parameter, and
taking as the parameter.
We show fixed-parameter tractability for each three of these parameterizations. The first two parameterizations can be dealt with an algorithm whose properties are stated in Theorem 11 (see also Corollary 3), while the third parameterization will be considered by Theorem 12.
Theorem 11
There is a fixed-parameter algorithm for the special case of SMC where each woman finds at most two men acceptable (i.e., ), parameterized by the number of distinguished men and women left unmatched by some stable matching.
Let denote an optimal solution for our instance I such that contains the minimum number of edges; recall that is a fixed stable matching for I. Without loss of generality, we can further assume that there does not exist another optimal solution such that (i) has the same number of common edges with as , and (ii) for each man m, either or m prefers to .4 Indeed, as long as such a “superior” matching exists, we can simply pick that instead of , until this is no longer possible. This way, we eventually end up with an optimal matching that satisfies our requirement.
We denote by b the number of blocking pairs in .
High-Level Description Let us remark first that simply guessing the optimal partners for each woman in and then using the polynomial-time algorithm presented in Sect. 6.1 (after exchanging the roles of men and women) does not work, since that algorithm heavily relies on the assumption that we start with a stable matching. In fact, the main difficulty to overcome is that feminine and masculine augmenting paths may “interact” in the sense that certain blocking pairs introduced by a feminine augmenting path can be “eliminated” (i.e., made non-blocking again) by an appropriately chosen masculine path. Therefore, we apply the following strategy. In Phase I, we find all feminine paths (as well as all cycles) in , and in Phase II we proceed with choosing the masculine paths carefully. Note that in Phase I it does not suffice to find a cheapest set of feminine augmenting paths, since we may not be able to eliminate as many blocking pairs afterwards as it is possible after an optimal choice of feminine paths. Instead, we need to find the exact feminine augmenting paths (and cycles) present in ; this can be accomplished by guessing certain properties of .
In Phase II, the main obstacle is that we do not know which blocking edges should be eliminated in an optimal solution, nor can we guess these edges efficiently. We deal with this problem by guessing the sets of those men in whose augmenting paths in contribute to the elimination of a blocking pair; this information allows us to find these masculine paths. Finally, we apply the algorithm of Theorem 8.
For the detailed description of our algorithm, we need a couple of simple observations and some additional notation. We begin with the following implications of the fact that each woman finds at most two men acceptable.
Proposition 3
Suppose . Let and be two augmenting paths.
If and start at some through the same edge, then one of them is a subpath of the other.
If and start at different women and , respectively, and and are not disjoint, then the set of their common vertices induces a suffix of either or (or both); their first common vertex is a man.
If and are disjoint and e is an edge incident to both, then one of the paths starts or ends at a women w, and e connects w with a man on the other path.
Observations (a) and (b) of Proposition 3 immediately suggest that feminine paths are easy to find, since once we decide which edge to start with, all possible augmenting paths lead in the same direction; the only difficulty arises in deciding when to stop. Observation (c) describes the limited ways in which two augmenting path can interact; we next look closer at such interactions.
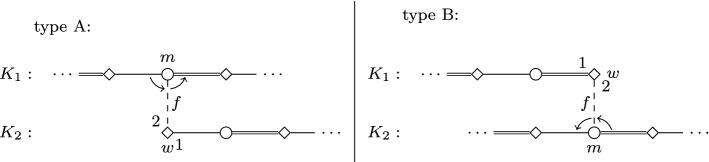
We say that an edge of G (with and ) is dependent if it connects two different connected components and of and, in addition, it holds that admits more blocking pairs than . We will say that f, and with a slight abuse of the notation, also relies on . We say that
f has type A, if w is the endpoint of (which is a path), f connects w with a man m on that prefers to w, and w to , and w is unmatched by and prefers to m;
f has type B, if w is the endpoint of (which is a path), unmatched by , and f connects w with a man m on that prefers to w, and w to .
See Fig. 5 for an illustration of the above definitions.
Fig. 5.
Illustration of a dependent edge f, running between two connected components and of where relies on . Double lines here denote edges of , single lines denote edges of , and f is drawn with a dashed line
Lemma 3
Let be the set of connected components of , and let and . Then any edge f that is blocking in but is not blocking in connects K with a connected component of H, is a dependent edge relying on K, and has either type A or type B.
Proof
Let f be an edge that blocks but does not block . Since is stable, f must have an endpoint in a connected component of H, because it blocks . However, as it ceases to be blocking in , it also must have an endpoint in K. Let w and m be the woman and the man connected by f, respectively. We distinguish now between two cases.
First, let us assume that w is contained in K. Since m is not contained in K, and w can only be connected to two men, it follows that the degree of w in K is at most (and hence exactly) 1. Since each connected component of is either a cycle or a path, this implies that K is a path with w being one of its endpoints.
Since f blocks and the partner of m under is , we know that m prefers w to . But as is stable, m must prefer to w.
Notice now that w is unmatched either in or in . However, as f blocks (where w is matched as in ) but does not block (where w is matched as in ), it must be the case that w is matched by but is unmatched in . Further, as f is not blocking in even though m prefers w to , we get that w prefers to m. This proves that f has type A.
Second, let us assume that w is contained in a connected component of H. As in the previous case, we quickly get that must be a path, with w being an endpoint of . Since f blocks , we know that w is matched by but is unmatched by . The stability of implies also that w prefers to m.
Regarding m, the fact that f blocks implies that m prefers w to . However, since f ceases to be blocking in , we get that m prefers to w. This proves that f has type B.
We are now ready to present our algorithm, which is a branching algorithm: throughout its course, we make several “guesses” for which all possibilities have to be explored. When certain guesses turn out to be trivially wrong, such guesses are discarded, and we might not explicitly mention this in the algorithm. (In Step 1, we describe such issues in detail for illustration, but later we omit them.) Phases I and II consist of Steps 1-5 and Steps 6-8, respectively.
Step 1: Guessing the first edges of feminine augmenting paths First, for each with , we guess the edge of incident to w. This results in at most possibilities, all of which must be explored. Naturally, we discard those guesses where the edges , , do not form a matching. From now on we assume that we know for each .
Additionally, we delete those edges for which and w prefers to m. Such edges are neither needed in , nor can they block any matching that contains all the edges , , guessed in this step.
Before proceeding to Step 2, we state an important lemma about augmenting paths.
Lemma 4
Each connected component of that is not a cycle is an augmenting path. Further, assume that Step 1 has already been performed, and and are connected components of such that relies on via a dependent edge f. Then
if f has type A, then is a masculine path and not a feminine path;
if f has type B, then is a feminine path and not a masculine path, and is either a cycle or a feminine path.
Proof
We begin by proving the first sentence of the lemma. Let us first suppose that Q is a connected component of that is not a cycle (thus is a path) but is not an augmenting path. The feasibility of implies that if Q has a distinguished person p as its endpoint, then p must be unmatched by . This means that Q can only be non-augmenting if neither of its endpoints is distinguished. This implies that is a feasible matching. Recall that b is the number of blocking pairs admits. If admits at most b blocking pairs as well, then this contradicts the choice of , because there are strictly less edges in than in .
Hence, admits at least blocking pairs. Since Q is a maximal path in and is stable, Proposition 1 implies that there must be an edge along Q that blocks . Obviously, there is no edge on Q that blocks , since is stable. Hence, modifying by switching the edges of and along Qdecreases the number of blocking edges among the edges ofQ. However, the same operation increases the total number of blocking pairs (from b to at least ), thus we get that there must exist at least two edges that become blocking only as a result of this switch along Q. In other words, there exist at least two edges that are blocking in but are not blocking in . By Lemma 3 we obtain that these edges must be dependent edges relying on Q.5 By the definition of a type A edge, at most one type A edge can rely on Q (as only one endpoint of Q can be a woman unmatched by , and this woman may be incident to at most one edge outside Q), so we get that at least one of these dependent edges relying on Q must have type B.
Let us call the man endpoint of a type B dependent edge a joiner; by the previous paragraph, Q contains at least one joiner. Our aim is to fix an “outer-most” joiner m on Q. However, for technical reasons we also have to take into account a special case where some man lying on Q, called the looper for Q, fulfils the following properties: (i) one endpoint of Q is a woman that is adjacent to in G but prefers to , and (ii) prefers to but prefers to .6 Now, we choose a man m that is either a joiner or the looper for Q so that the following holds: if m splits Q into two subpaths and with containing , then contains neither joiners nor the looper for Q.
Case for a Joiner First, let us assume that m is a joiner. In this case, there might be several women who form a dependent edge of type B with m, so let w denote the one that is most preferred by m. Let f be the edge , and let P be the path of that has w as its endpoint. We illustrate these concepts in Fig. 6.
Fig. 6.

The joiner m splits Q into subpaths and . Here and in later figures, double lines denote edges of . Single lines denote edges of , and dashed lines are for dependent edges
We claim that is an optimal solution. Observe that can be obtained from by deleting Q and substituting P by the path where the plus sign means concatenation. Let x denote the endpoint of that is not m. First, is clearly feasible, since x is not distinguished (by our assumption that Q is non-augmenting). Next, suppose that some edge e is blocking in but is not blocking in . It is easy to see that by our choice of w, e cannot be incident to w or m. As only vertices in are matched differently in as in , we obtain that one endpoint of e must lie on . Using the stability of , we also get that the other endpoint of e must lie either on a connected component of other than Q or on . In the former case, Lemma 3 implies7 that e is a dependent edge. By our choice of m, e cannot be of type B, hence by Lemma 3, e must have type A, and thus it is incident to x which must be a woman not covered by . In the latter case, supposing that the man endpoint of e lies on we quickly get that it must be the looper for Q. To see this, first note that the only woman that can be adjacent to on must be the common endpoint of and Q (by ); let denote this woman. Second, since e blocks but it does not block , we know that prefers to , but prefers to . Third, since prefers to , the stability of implies that is matched by and prefers to . Hence, is indeed the looper for Q, contradicting our choice of m. Thus, we know that it must be the woman endpoint of e that lies on . Since the two endpoints of are and x, by we obtain that the woman endpoint of e lying on can only be x, which therefore must be a woman not covered by . In either case, we can conclude that there can only exist at most one such edge e (because x has degree at most 2 in G). So the number of edges that are blocking in but not blocking in is at most one.
Furthermore, since f is a dependent edge of type B, by definition we know that m prefers to , and hence, y must prefer to m (as otherwise would be blocking in , which is not possible). Note that, in particular, exists and contains at least two edges. By Proposition 1, must contain at least one edge that blocks , and this edge is not blocking in , simply because any edge of that blocks but be an edge contained in and hence in . Thus, the number of edges blocking cannot be more than b. Hence, is an optimal solution such that there are less edges in than in , a contradiction. This proves the first statement of the lemma for the case of m being a joiner.
Case for a Looper Let us now assume that is the looper for Q. In this case let f be the edge connecting to the woman endpoint of Q that is matched by ; it is easy to see that is the endpoint of as well. See Fig. 7 for an illustration. Let us again define . As in the previous case, it is immediate that is feasible. Arguing similarly as before and using that does not contain any joiners, we get that any edge that blocks but does not block can only be a type A dependent edge incident to the (woman) endpoint x of that is not . Hence, there can be at most one edge blocking but not . From this point on, we can use the same reasoning as in the previous case to arrive at the conclusion that is an optimal solution that has more edges common with than , a contradiction. This proves the first statement of our lemma.
Fig. 7.
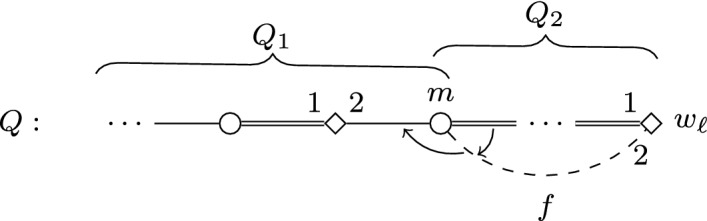
The looper m of Q splits Q into subpaths and
Let us prove (b) now. Suppose that and are two connected components of such that relies on via an edge of type B. By the definition of a type B edge, we know that is a path with an endpoint that is a woman covered by , so its other endpoint is either a woman not covered by , or a man covered by . Thus, cannot be a masculine path, so by the first statement of the lemma, it is feminine. It remains to show that if is a path, then it is feminine. Assume for contradiction that is a non-feminine path Q in and some other path P in relies on Q via a type B edge f. In this case we can argue exactly as above to show that there must exist an optimal matching (defined the same way as we did while proving the first statement of the lemma) for which contains less edges than , a contradiction.
To show (a), suppose that and are two connected components of such that relies on via an edge of type A. By the definition of a type A edge, the woman endpoint w of f is unmatched in , and is a path that has w as an endpoint. Also, m is the second choice of w and is the first choice of w. Hence is not possible, as in that case the edge f would have been deleted in Step 1 of the algorithm. Furthermore, since is an -alternating path with an endpoint in , the other endpoint of cannot be a woman in . Hence, is not a feminine augmenting path. Since we already know that is an augmenting path, (a) follows.
By Lemma 4, each connected component in that is a path must be an augmenting path; we let denote the augmenting path in that contains some as an endpoint.
Consider now any woman . Let us define a candidate path for w as an augmenting path that starts through the edge . Observe that itself is a candidate path for w. Furthermore, although we cannot determine directly, Proposition 3 implies that there exists a unique maximal candidate path for w that contains as a subpath. We can compute easily: starting from the edge , we can build by adding edges of and edges not in in an alternating manner, always appending a new edge to the last vertex of the current subpath of . Observe that after an addition of an edge of , the resulting subpath of ends at a woman, and thus implies that there exists at most one edge that we can add to our path. This shows the uniqueness of .
Step 2: Finding cycles in We make one more guess for each by guessing whether relies on some cycle of or not; this again yields possibilities. If relies on some cycle C, then by Proposition 3, both and C can be found in time as follows. We compute the longest possible candidate path for w. Since relies on cycle C, the last person on must be a woman x incident to an edge for which m is already on . Then the subpath of between m and x together with the edge form the cycle C. For an illustration, see Fig. 8.
Fig. 8.
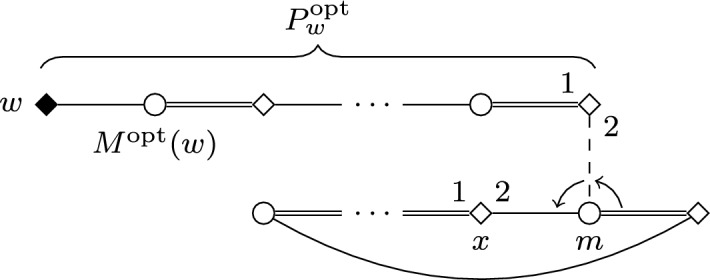
Step 2 of the algorithm for Theorem 11, for finding cycles in
Lemma 5
Assuming that the guesses made by the algorithm are correct, all cycles in and all paths relying on some cycle in are found in Step 2.
Proof
Let C be a cycle in . By the stability of , no edge of C blocks the matching . Since has more edges in common with than does, we know by the choice of that there must be an edge incident to C that is blocking in but is not blocking in . By Lemma 3, such an edge must be a dependent edge e relying on C. This proves that there are no cycles in without augmenting paths relying on them.
By Lemma 4 we know that dependent edges of type A rely on (masculine) paths,8 so e must have type B. From this, Lemma 4 yields that all paths relying on a cycle must be feminine paths. Hence, Step 2 indeed finds all paths that rely on some cycle, together with the cycles that these paths rely upon, which (as pointed out above) means that Step 2 finds all cycles of , proving our claim.
Step 3: Finding neutral paths In this step, for each we guess whether w lies on a neutral path in , yielding at most possibilities. Clearly, if w lies on a neutral path, then by Proposition 3, is the maximal candidate path starting with the edge , that is, .
Step 4: Finding feminine paths relying on other feminine paths In this step, we find all feminine paths that rely on some other feminine path; note that feminine paths that do not depend on other feminine paths will be taken care of by Step 5.
In Step 4, we first guess for each whether relies on another feminine path, and if so, we also guess on which one. This means at most possibilities for each , a total of possibilities.
Supposing that, according to our guesses, relies on for some w and y in , we can find easily as follows. Consider the maximal candidate paths and for w and y, respectively. We know that and are disjoint, but supposing that our guesses were made correctly, Lemma 4 implies that they are connected by a dependent edge f of type B relying on . Hence, contains , followed by the dependent edge f connecting and , followed possibly by a suffix of . Thus, by Proposition 3, and must share the man endpoint m of f as their first common vertex, and they coincide after m. Therefore, can be obtained by deleting all edges incident to or occurring after m on . This way, f and can be found in time.
Notice that this method only enables us to locate but not ; we only know that must contain the man m incident to f, but we do not know where ends. To remind us that contains m, we store m as an obligatory man for y.
Step 5: Finding all remaining feminine paths In this step, we find all feminine paths that rely neither on a cycle, nor on another feminine path. To do so, we will use a surprisingly simple method. Intuitively, it makes sense to construct augmenting paths to be as short as possible, since the longer such a path gets, the more opportunities arise for a blocking pair to appear along the way. This intuition is almost entirely correct, if no other path (or cycle) relies on the augmenting path we are looking for: it turns out that is either indeed the shortest possible, or if this is not the case, then we can “get rid of” only one blocking pair by constructing a longer augmenting path—and this, too, we can keep as short as it is possible, by stopping whenever we encounter a decrease in the number of blocking pairs along the augmenting path. In the case when some other path relies on , we need to be somewhat more careful, and take into account the obligatory men defined in Step 4.
After this high-level explanation, let us define Step 5 formally. Let be the set of those women for which has not been found yet (that is, where is not neutral, and it does not rely on any other path or cycle in ). Let us fix any woman . With any candidate path Q for w, we associate a matching ; we can think of as the matching that results from replacing with Q in the symmetrical difference of and the solution. Let us state a few useful properties of candidate paths and their associated matchings.
Proposition 4
The following holds for any candidate path Q for w:
is a matching.
is a feasible matching.
- Q must be one of the following two forms:
-
(i)Q ends at a man in , in which case , or
-
(ii)Q ends at a non-distinguished woman.
-
(i)
Proof
Recall that the definition of an augmenting path (see the beginning of Sect. 6) directly requires that be a matching, proving (a). This immediately implies that if Q ends at a man, then this man cannot be matched by , from which and thus follows. Using again the definition of an augmenting path, we get that the last person on Q is not distinguished (because is not neutral by Step 3), showing (c).
To see that is a matching, let denote the union of all connected components of except for . Then is a matching. But as is vertex-disjoint from Q, from (a) we get that must be a matching too. The properties of Q described in (c) show also that is feasible.
Now, we define two candidate paths for w as follows:
First, we let be the shortest candidate path for w that contains all obligatory men for w. In particular, if there are no obligatory men for w, then is the shortest candidate path for w; see Fig. 9 for an illustration.
Second, let be the shortest candidate path containing such that admits less blocking pairs than . Such a path, however, may not exist, in which case we leave undefined.
Fig. 9.
An example of the paths for three women , as defined in Step 5. The man for each is the last obligatory man for on the maximal augmenting path . In cases where there is no obligatory man for , one can identify with to get an appropriate figure
Lemma 6
If does not rely on any other path or cycle in , then either or .
Proof
First observe that for any , if the guesses made by the algorithm are correct, then contains as a subpath. To see this, recall that if the guesses made in Step 4 of the algorithm are correct, then indeed must contain all obligatory men for w. Since is a candidate path for w, it indeed must contain .
Next, suppose that , and consider the matching . By Proposition 4, is a feasible matching, and implies that ends at a non-distinguished woman x.
Claim 2
Let Q be a candidate path for w such that . If e is an edge blocking in but not blocking in , then e is adjacent to x.
Proof of Claim 2
Suppose for contradiction that e is not incident to x. First note that e must be adjacent to a person in , as all other persons (except for x) have the same partner in as in . Second, as is stable, at least one endpoint of e must be matched differently in than in . Thus, e must connect a person in either (i) with a connected component of , denoting the union of all connected components of except for , or (ii) with .
In case (i), e must be blocking in (as e blocks ). As e is not blocking in , it is not blocking in either (because any person in has the same partner in as in , except possibly for the last person on Q who might be left unmatched in ). Therefore, Lemma 3 implies that e is a dependent edge relying on . By Lemma 4, only feminine paths may rely on . However, in Step 4 we have stored the man endpoint of all edges that connect with a feminine path relying on as an obligatory man, so assuming correct guesses in Step 4, e must have an obligatory man as its endpoint. But contains all the obligatory men for w, which contradicts our assumption of case (i).
In case (ii), let and be the woman and man endpoint of e, respectively; we assumed . By , can only be adjacent to both and if either , or Q and also ends at . In the former case, , yielding . As e blocks , prefers w to ; however, w is not matched in , so this means that e blocks as well, a contradiction. In the latter case, lies on , yielding . As e blocks , prefers to ; however, is not matched by , so this means that e blocks as well, a contradiction. Hence the claim follows.
Let denote the number of blocking pairs with respect to that are incident to a man or woman on .
Claim 3
If Q is a candidate path for w such that , and c is the number of blocking pairs with respect to that are incident to a man or woman on Q, then .
Proof of Claim 3
By Claim 2, can only happen if both edges incident to x are blocking in , and none of them is blocking in . However, this cannot happen, as we are going to show now. Let and be the two men in x’s preference list; note that contains but not . If both and are blocking in , then prefers x to , and either prefers x to or is unmatched by . Therefore the stability of implies that x prefers to , as otherwise would block . But this shows that is a blocking pair in and thus in as well, proving our claim.
Now, let denote the number of blocking pairs with respect to that are incident to a man or woman on . By our assumption , we get , as otherwise would also be an optimal solution which would contradict our choice of (as contains less edges than ). Hence, Claim 3 implies .
By the definition of , we know that , and Proposition 4 yields that is a feasible solution. The definition of and Claim 3 together imply that the number of blocking pairs with respect to that are incident to a man or woman on is exactly . Hence, is an optimal solution. Therefore, cannot contain less edges than , because assuming otherwise would contradict our choice of . From this, follows.
According to Lemma 6, we can find all remaining feminine paths in by guessing for each whether equals or . This means at most guesses; the computations needed for each guess take linear time.
Step 6: Computing elimination paths. Let be the union of cycles, feminine and neutral paths found in Steps 1 to 5. When searching for masculine paths, we will have to deal with edges that might be type A dependent edges in the optimum solution. We call an edge volatile if it connects a woman in with her second choice. The importance of this definition is shown by the following two lemmas.
Lemma 7
Let f be an edge that is blocking in , but not blocking in . Then f is volatile, its woman endpoint is contained on a non-feminine path of , and its man-endpoint is contained in .
Proof
Observe that since f does not block , there must exists a connected component Q of not in such that f does not block . Clearly, Q is a masculine but not feminine augmenting path by the definition of . Lemma 3 then implies that f is a dependent edge relying on Q, and Lemma 4 yields also that f has type A and Q is masculine and not feminine. The remaining statements follow from the definition of a type A edge.
Lemma 8
If f is a volatile edge incident to some non-feminine path in , then f is not blocking in .
Proof
Recall that is an optimal solution for which has as few edges as possible, and there does not exist another optimal solution such that (i) has the same number of common edges with as , and (ii) for each man m, either or m prefers to .
Suppose for the sake of contradiction, that f is a volatile edge incident to a masculine path in for some , and f blocks . Let m and w be the man and woman connected by f.
Since m is the second choice of w and f is blocking in , we know that does not cover w. However, any woman on a masculine augmenting path is matched by with a man adjacent to her on this path, so w does not lie on . Therefore, m lies on .
Define P as the subpath of from x to m plus the edge f. Consider now ; is a matching because . Clearly, is feasible, since is not a neutral path.
Claim 4
If is an edge that blocks but does not block , then ends at a woman y, and is a volatile edge incident to y.
Proof of Claim 4
Let and be the woman and man connected by . The only persons that are matched differently in than in are those in ; recall that with . Since both m and w are better off in than in , and blocks but not , we get that one endpoint of must be in .
Suppose first that . Then and since blocks , we know that prefers to . But is stable, so prefers to , and in particular is matched by . As blocks , we get that . Hence, as (because but ), it must be the case that and is on a connected component of , denoting the union of all connected components of other than . This implies that is blocking in as well. Since is not blocking in , Lemma 3 implies that must be a dependent edge relying on . Note that since , cannot be of type A (by the definition of a type A edge), so it must be of type B. However, Lemma 4 tells us that a type B edge relies either on a cycle or on a feminine path, but as is neither of the two, we arrive at a contradiction.
Thus, we get . Observe that is not possible, because it would imply contradicting the assumption that blocks (note that m prefers w to because f blocks ). From this we obtain that cannot be contained in : we have by definition, and is also not possible, since in that case would imply . Thus, by we know that , and since blocks but not , we also get that must be the second choice of . Hence is volatile, proving our claim.
By Claim 4, there can be at most one edge that is blocking in but not in . Since f is an edge that blocks but not , we get that is an optimal matching. Moreover, either has more common edges with than , or m is the last man on , in which case every man has the same partner in as in except for m who is better off in than in . This contradicts our choice of .
For any volatile edge f we can decide in linear time if there exists a masculine augmenting path disjoint from that contains the woman endpoint w of f, but not f itself. Indeed, we can build such a path starting from w by taking edges not in and edges in in an alternating manner; by and since we need to start with an edge different from f, we always have at most one possibility to pick our next edge. This process may or may not result in a masculine augmenting path, but if it does, then the path is unique, proving the following claim.
Proposition 5
Let f be a volatile edge. If there exists a masculine augmenting path disjoint from that contains the woman endpoint w of f but not f itself, then this path is unique; we denote it by .
Let f be a volatile edge that is blocking in . We say that a set of masculine augmenting paths eliminates f if (i) exists and , and (ii) for any path , if there is a volatile blocking edge in , then exists and is contained in . We refer to the (inclusion-wise) minimal set of masculine paths eliminating f as the elimination paths for f, and denote it by . Further, we refer to the starting vertices of these paths as the elimination set for f. The next lemma illuminates the role of elimination paths.
Lemma 9
If f is an edge blocking in but not blocking in , then contains all paths in .
Proof
By Lemma 7, the woman endpoint w of f lies on a masculine path. By Proposition 5, this path can only be , and thus must be contained in . For an inductive reasoning, assume that Q is a masculine path in that is contained in and is a volatile edge that is blocking in . We claim that is contained in , which by induction proves our lemma.
To see our claim, note that by Lemma 8, cannot be blocking in . Since the woman endpoint of is unmatched by , it can only be blocking in if its man endpoint lies on Q. Thus, since is not blocking in (but is blocking in ), it must be the case that its woman endpoint lies on a masculine path in . Since such a path can only be by Proposition 5, we get that and the lemma follows.
Step 7: Guessing relevant elimination sets in We call an edge relevant in , if it is a volatile edge blocking , but it does not block . By Lemma 9, if f is a relevant edge in , then must contain all paths in . Since there may be several volatile edges blocking in , we cannot determine the relevant ones among them by simply guessing them. Instead, we only guess the elimination sets for all relevant edges. Clearly, these sets must be pairwise disjoint subsets of , so guessing them results in at most possibilities. Let us denote by the guessed elimination sets.
Step 8: Computing cheapest elimination paths For each set with that, according to our guesses made in Step 7, forms the elimination set for a volatile edge relevant in , we determine some volatile edge f incident to that is blocking in and whose elimination set is exactly . Namely, we pick an edge f among all such edges in a way that the number of blocking pairs in is as small as possible. Let be the volatile edge chosen this way, and let .
Step 9: Computing remaining masculine paths We define as the set of distinguished men that are neither covered by nor contained in any of the sets . For each such m we are going to compute an augmenting path disjoint from such that the number of edges that block but not is minimized. We set .
To compute , we use the algorithm of Theorem 8 with some modifications.
Step 9.1 We compute all augmenting paths that start at a man and are disjoint from . For each such augmenting path P we define a set C(P) containing those edges that block but not , and are either non-volatile or have a woman endpoint in ; we define the contributing cost of P as |C(P)|.
Step 9.2 We construct the auxiliary graph as follows: we set and . The edge set E contains an edge for each , as well as an edge whenever , and there exists an augmenting path disjoint from with endpoints m and w. We define the weight of an edge as the minimum contributing cost of any augmenting path starting at m and not ending in , and we define the weight of an edge with and as the minimum contributing cost of any augmenting path with endpoints m and w, disjoint from .
Step 9.3 We compute a minimum weight matching in covering U the same way as in the algorithm of Theorem 8; let denote the set of augmenting paths corresponding to the edges of the matching . Note that the paths in are pairwise disjoint, by the construction of and because is a matching in .
Step 9.4 We eliminate all volatile edges that block but not and are not incident to . We modify iteratively. We start by setting . At each iteration we modify as follows. We check whether there exists a volatile edge with that is not incident to , and blocks but not . If yes, then notice that is not matched in , because is the second choice for . Let P be the path of containing . We modify by truncating P to its subpath between its starting vertex and , and appending to it the edge . This way, becomes an edge of the matching . The iteration stops when there is no volatile edge disjoint from blocking but not . Note that once a volatile edge ceases to be blocking in , it cannot become blocking again during this process, so the algorithm performs at most iterations. For each , let denote the augmenting path in covering m at the end of this step; we set .
Step 9.5 Finally, we output the matching .
It is straightforward to verify that the number of guesses made are bounded by a function of , and all computations in a branch can be performed in time polynomial in the size |I| of the instance, yielding a fixed-parameter algorithm with parameter . It remains to prove the correctness of the proposed algorithm.
To this end, we first prove a simple observation.
Proposition 6
Suppose . Let M be a matching and the set of connected components in . Let also and be two disjoint subsets of . Then there is no edge that blocks both and
Proof
Suppose that e blocks both and ; by the stability of , e connects a person in with a person in . Since e blocks , we know that prefers to its situation in . Since e blocks , we also get that prefers to its situation in . This contradicts the stability of .
Next, let us prove that Step 9 works as promised.
Lemma 10
For each let be an augmenting path disjoint from and starting at m, and let . Then the number of edges that block but not is at most the number of edges that block but not .
Proof
Let be the number of edges that block but not . Then Claim 5 implies that there can be at most edges in .
Claim 5
If e is an edge such that for some , then e blocks but not .
Proof
Let and be the man and woman connected by e. By it does not block , so we only need to show that e blocks . Suppose for contradiction that e does not block . Then it must clearly be adjacent to some path , . By we know that is the endpoint of one of these paths, , and since e blocks but not we also get that must be the less preferred choice of ; this yields that e is volatile. However, as e is not incident to (because it connects and ), this contradicts .
Let and be two distinct men in ; we will show . Assuming otherwise, let e be an edge in . Then e does not block but blocks both and . Hence e connects with , and thus blocks and as well, contradicting Proposition 6. Thus,
Then, by the definition of edge-weights in , we get that there exists a matching in with weight at most that covers . Thus, the matching computed by the algorithm in Step 9.3 has weight at most as well, yielding that the set of augmenting path corresponding to this matching is such that , that is, their total contribution cost is at most . From this, Claim 6 below implies that there can be at most edges that block but not .
Claim 6
If an edge e blocks but not , then for some .
Proof
Let and be the man and woman connected by e. Clearly, e is adjacent to some path in .
First, suppose that e is adjacent to only one path where . Then e must block as well. In that case, to prove we only need to show that either is in or is e is non-volatile. Suppose for contradiction that e is volatile and is not in . However, as a result of Step 9.4, there can be no volatile edge that blocks , unless it is incident to . Hence, we must have that is in , and since e blocks , we get that prefers to its partner in , which is the same partner he has in . However, this yields that e blocks as well: since and is not in , she is unmatched in . Hence, we arrive at a contradiction, proving .
Second, suppose that e connects two paths and where and are distinct men in . By , we know that is an endpoint of one of these paths; without loss of generality, we may assume that is an endpoint of . Since is a masculine augmenting path, we get . Now, we know that e blocks , so it must also block , because is unmatched in and has the same partner in as in . Again, e cannot be volatile as a result of Step 9.4, yielding that e is contained in .
This proves the optimality of as stated by the lemma.
Next we state the following useful lemma.
Lemma 11
Let f be a volatile edge blocking in , Q an elimination path in , and a non-feminine augmenting path not contained in , disjoint from . Let e be an edge. Then e blocks if and only if it blocks or .
Proof
First observe that the statement of the lemma is obviously true for any edge e that is incident to at most one of Q and . So suppose that e connects Q with . Since both Q and are masculine augmenting paths and , by Proposition 3 we know that e connects the woman endpoint w of one of these paths with a man m on the other path; moreover, w must be unmatched by as it is the endpoint of a masculine augmenting path. Let be the path (either Q or ) that contains w, and let be the one containing m. By and the stability of , e cannot be blocking in .
Now, if e blocks , then it blocks as well, since m prefers w to its partner in and w is unmatched in .
It remains to show that if e blocks , then it also blocks . Supposing otherwise, it must be the case that (i) m prefers w to its partner in , but (ii) w prefers its partner in to m. Consequently, e is a volatile edge.9 We distinguish two cases.
Case (A). Then must be the unique masculine augmenting path containing the woman endpoint of e but not e itself, that is, . Hence, since e is a volatile edge blocking and , by the definition of elimination paths we get as well, a contradiction.
Case (B). Then contains the man endpoint of e. However, again by the definition of elimination paths, as Q is a path of , the man endpoint of e must be contained either in (if ) or another path of that triggered the addition of Q into ; both possibilities contradict our conditions on .
Now we are ready to show that our algorithm is correct.
Proof of Theorem 11
To prove the correctness of the proposed algorithm, we first show that if all our guesses are true, then the paths and cycles in are exactly the feminine paths and the cycles of . The correctness of Step 2 is stated by Lemma 5. From the description of our algorithm, it should be clear that the correctness of Steps 3 and 4 follows directly from Proposition 3 and Lemma 4. Lemma 6 guarantees the correctness of Step 5, which proves that in Steps 1–5 the algorithm indeed finds all cycles and feminine paths of .
Next, let us argue that is indeed a matching. For this, apart from the correctness of Steps 1–5, we need that the masculine paths in are disjoint from . Further, we also need that paths in are disjoint from all remaining masculine paths. To see this, observe that any path P in ends at a woman which is connected by a volatile edge (not on P) to either or to another path in . Hence, w cannot lie on any masculine path other than P by Proposition 5. Thus, is a matching. Its feasibility is implied by the correctness of Steps 1–5, and the definition of augmenting paths.
It remains to argue that admits at most as many blocking pairs as . First, Lemma 7 implies that all edges blocking in are either relevant volatile edges in , or they are also blocking in . Furthermore, if is a relevant volatile edge with elimination set for some , then by Lemma 9 we know that all elimination paths in must be contained in . As is the set of feminine augmenting paths and cycles of , in Step 8 the algorithm is bound to find some volatile edge (though not necessarily ) that is blocking in and whose elimination set is . Furthermore, by our choice of , there are at most as many blocking pairs in as there are in .
Let the contribution of a volatile edge e, denoted by C(e), be the set of edges that block but not ; we extend this notion to any set E of volatile edges with pairwise disjoint elimination sets by defining the contribution C(E) of E as the set of edges that block but not . By our choice of , we know .
We are going to show
which implies that has at most as many blocking pairs as does. To prove this, it suffices to prove the following claim.
Claim 7
Let be a set of volatile edges with pairwise disjoint elimination sets, . Then .
Proof
We need to prove that any edge e blocks but not if and only if it blocks exactly one of and but not . So let us assume that e does not block .
Notice that if e is incident to only one of and , then our claim is immediate. So suppose that e connects a path with a path . Observe that it suffices to show that e blocks if and only if it blocks exactly one of and , because e cannot be incident to any connected component of other than Q and . Now the claim follows directly from Lemma 11 and Proposition 6.
It remains to consider the blocking pairs contributed by the paths .
Claim 8
If e is an edge that blocks but not , then e blocks but not .
Proof
Recall that by definition and , so if e does not have an endpoint in , then the claim follows immediately.
So suppose that e is incident to a path for some . As e blocks but not , the other endpoint of e must be contained in a path for some . Since Q and are the only connected components of that e is adjacent to, the condition of our claim yields that e blocks , and we need to show that e blocks but not . To see this, first notice that by Proposition 6, edge e cannot block , because Q and are disjoint. Second, as e blocks , Lemma 11 implies that it must block as well, proving our claim.
Let be the number of those edges that block but not . Then Claim 8 implies that there are at most edges that block but not . Since Steps 9.1–9.4 calculate a set of augmenting paths that minimizes the number of edges that block but not , we know that there are at most such edges. This in turn shows that there can be at most edges that block but not , as implied by Claim 9. This proves the optimality of .
Claim 9
If e is an edge that blocks but not , then e blocks but not .
Proof
Since and , we have that if e does not have an endpoint in , then the claim follows immediately.
So suppose that e is incident to a path for some . As e blocks but not , the other endpoint of e must be contained in a path for some . Since Q and are the only connected components of that e is adjacent to, the condition of our claim yields that e blocks but not , and we only need to show that e blocks , which is directly implied by Lemma 11, proving our claim.
This finishes our proof of correctness for Theorem 11.
As each augmenting path contains at least one edge that blocks , the number of blocking pairs admitted by is at least . Thus, we get Corollary 3.
Corollary 3
The special case of SMC where each woman finds at most two men acceptable (i.e., ) is fixed-parameter tractable for parameter b.
It remains to deal with the third among the parameterizations we have to consider. So let us turn our attention to the complexity of the SMC with where we take as the parameter.
Theorem 12
There is a fixed-parameter algorithm for the special case of SMC where each woman finds at most two men acceptable (i.e., ), and the parameter is , the number of distinguished women plus the maximum length of men’s preference lists.
It turns out that Theorem 12 can be proved by a modified version of the algorithm described above to prove Theorem 11. In fact, we start with applying Steps 1 to 6. However, we can no longer apply Step 7, because now can be unbounded, and thus guessing the elimination sets would not yield a fixed-parameter tractable algorithm. To circumvent this problem, we rely on an observation stated by Lemma 12 which shows that “almost all” volatile edges that are blocking in are relevant edges, and thus have to be eliminated. This allows us to efficiently guess the set of relevant volatile edges, leading us to a fixed-parameter tractable algorithm. Hence, instead of guessing only the elimination sets (that is, the man endpoints of the elimination paths) we can now guess the exact set of edges that the optimal solution eliminates, so in fact the modified algorithm can be viewed as a more simple approach.
Let denote the set of all volatile blocking edges in , and let for some man m. We say that is loose, if
both and assign a partner to m,
m prefers to w, and w to , and
is not distinguished.
Lemma 12
All loose edges in are relevant, and at most edges in are not loose.
Proof
First suppose that for some man m is loose. Since is volatile, we have that m is the less preferred man acceptable to w, and since is blocking in , we know that w is unmatched in .
For the sake of contradiction, let us suppose that is not relevant, meaning that it is still blocking in . In this case, w must be unmatched in too. We define a matching obtained from by modifying only the partner of m to be and, i.e., . Observe that is indeed a matching, because w was unmatched in . It is also feasible, because only becomes unmatched by this modification, and is not distinguished (by the definition of a loose edge). Furthermore, while is not blocking in , the only edge that might be blocking in but not in is the edge adjacent to but not to m, if existent (because both m and w are better off in than in ). Hence, is also an optimal matching. It should also be clear that it has the same number of common edges with as . Note also that each man has the same partner in as in except for m who is better off in than in . This contradicts our choice of , proving that must indeed be relevant.
To prove the second part of the lemma, let us consider any edge with . Again, w must be unmatched in the matching , since otherwise would not block it (because m is the less preferred man in w’s preference list). By contrast, cannot block , which can be explained in three different ways, giving rise to the following three cases:
Case A: ,
Case B: , but exists and is preferred by w to m, or
Case C: , but exists and is preferred by m to w.
In Case A, by , the edge must be contained in an augmenting path of , with w being an endpoint (since w is not matched in ). In Case B, matches w to its first choice, say x, so the edge must be contained in an augmenting path of , with w being an endpoint. Thus, in both cases we know that w is an endpoint of a feminine augmenting path of . However, Cases A and B exclude each other, because in Case A the augmenting path ending at w contains the edge connecting w to her second choice, while in Case B it connects w to her first choice. Since there are at most feminine augmenting paths, it follows that the number of such edges where the conditions of Cases A or B hold is at most .
In Case C, let us first observe that m gets matched in . Indeed, if this were not the case, then m would be the man endpoint of a feminine augmenting path, with the last edge contained in ; however, this is not possible (simply because feminine paths start with women and with edges not in ). Because is a collection of connected components of , with m contained in , it is clear that the partner of m in is the same as his partner in . Thus, exists, and since blocks , we know that m prefers w to . Therefore, either is a loose edge, or is distinguished; in the latter case, we say that belongs to this distinguished woman.
Now, observe that all edges belonging to some woman are adjacent to , and is adjacent to at least two edges not belonging to z: namely, the edges and . Hence, at most edges may belong to z, implying that there are at most edges in total belonging to distinguished women. Taking into account all three cases, we get that there are at most edges in that are not loose.
Let us now describe our algorithm proving Theorem 12 in detail. This algorithm starts with Steps 1 to 6 (as given for Theorem 11), and then applies Steps and below. The last step of our algorithm is Step 9 from the algorithm for Theorem 11.
Step: Guessing the relevant edges To determine which edges among those volatile edges that block are relevant, we first compute the set of all loose edges in . Notice that when checking some edge , we already know : since m lies on a path or cycle of , it gets matched in to the same woman as in . Therefore, checking whether is loose is straightforward.
After determining all loose edges (which are all relevant by Lemma 12), we guess the remaining set of relevant edges in . By Lemma 12, this yields at most possibilities, and in the branch where our guess is correct, we obtain the set of all relevant volatile edges blocking in .
Step: Computing cheapest elimination path This step is a simplification of Step 8 of the algorithm for Theorem 11. By Lemma 9, for each the elimination paths in (determined in Step 6) are all contained in ; let .
Step: Computing remaining masculine paths Let denote the set of distinguished men in not covered by any of the elimination paths in . For each we compute an augmenting path disjoint from such that the number of edges that block but not is minimized, where is the union of all paths , . We accomplish this with the exact same method as in Step 9 of the algorithm for Theorem 11. Finally, we output the matching .
Note that the number of guesses made in Steps 1 to 6 are bounded by a function of , and the guesses made in Step result in at most possibilities. Since all computations in a branch can be performed in time polynomial in the size |I| of the instance, we obtain a fixed-parameter algorithm with parameter . It remains to prove its correctness.
Proof of Theorem 12
The proof is a straightforward adaptation of our proof for Theorem 11. The only difference is that instead of finding some elimination paths that eliminate the necessary number of relevant volatile edges blocking in , our algorithm now directly finds all of the relevant edges among those volatile edges that block , together with the corresponding elimination paths; this is a consequence of Lemma 12 and the definition of Step . As Step can also be viewed as a simplification of Step 8 as defined for the algorithm for Theorem 11, it can be verified that the exact same arguments that prove the correctness of Step 8 in our algorithm for Theorem 11 also imply the correctness of Step for our algorithm for Theorem 12 in a straightforward manner.
Discussion
We provided a systematic study of the computational complexity of Stable Marriage with Covering Constraints. Our main result is a complete computational complexity trichotomy into polynomial-time solvable cases, -hard and fixed-parameter tractable cases, and -hard and -hard cases, for all possible combinations of five natural parameters:
: the number of distinguished men,
: the number of distinguished women,
: the maximum length of preference lists for men,
: the maximum length of preference lists for women, and
b: the number of blocking pairs allowed.
As a special case, we solved a problem by Hamada et al. [24].
Figure 10 provides a decision diagram showing that our results indeed fully determine the computational complexity of SMC with respect to the set of possible parameters. Going through this decision diagram should convince the reader that any parameterized restriction of SMC with respect to the set S is classified as either polynomial-time solvable () or -hard, and in the latter case, either fixed-parameter tractable (), or -hard with the given parameterization (if any). In particular, when we provide parameterized results, this means that the parameterized restriction of SMC in question is -hard without parameterization.
Fig. 10.
Decision diagram for determining the complexity of SMC. We remark that if a certain restriction of SMC where one of the values is a constant k proves to be -hard or -hard with some parameterization, then it is easy to see that the same hardness result also holds for the case where (and all other assumptions are the same). We refer to the “reflection” of a result by adding the postfix ‘R’ to its name (so Theorem xR denotes the reflection of Theorem x); here by reflection we mean the statement obtained by switching the roles of men and women
Given the strong polynomial-time inapproximability bounds, as well as the parameterized intractability results of this paper, we pose as an open question whether fixed-parameter approximation algorithms can beat either of these obstacles for solving SMC.
Another challenge for future research is to investigate possible adaptations of the proposed algorithms to the Hospitals/Residents model (note that, naturally, all our hardness results for SMC-1 apply to the HRLQ problem), or to a setting where ties are allowed in the preference lists.
Acknowledgements
Open Access funding provided by Projekt DEAL. We thank the anonymous reviewers for their remarks which greatly helped to improve the paper; we are grateful for their patience and their rigorous reading of earlier drafts.
Footnotes
Restrictions without any parameters are simply classified as polynomial-time solvable or -hard.
Hamada et al. claim only a run time , but their algorithm can easily be implemented to run in time .
We remark that our concept of an augmenting path is analogous, but not identical, to the standard notion of an augmenting path in general matching theory. According to the standard definition, an augmenting path for a given matching M is an M-alternating path such that is a matching containing more edges than M. In our case, however, instead of increasing the number of edges in the matching, we aim for a path which can be used to increase the number of distinguished men and women that are matched.
Note that there may be optimal solutions that are incomparable to in the sense that they are preferred by some of the men while not preferred by some other men, but the existence of such a matching is of no importance to us: we can pick any optimal matching that fulfils our requirement above.
Formally, we need to apply Lemma 3 with setting H to contain all connected component of except for Q, and setting K as Q.
Note that there cannot exist two loopers for Q, because only one woman endpoint of Q can be matched by and such a woman can only be connected to at most one man on Q other than its partner in .
Again, we need to apply Lemma 3 with setting H to contain all connected component of except for Q, and setting K as Q.
We remark that it is still possible that C itself relies on a masculine path via a dependent edge of type A, but such edges do not play a role in Step 2.
This case is analogous with e being a type A edge; however, the paths Q and here need not be paths of .
A preliminary version of the results presented in here appeared at the Proceedings of the 10th International Symposium on Algorithmic Game Theory [39]. Research of M. Mnich supported by ERC Starting Grant 306465 (BeyondWorstCase) and DFG Grant MN 59/4-1. Research of I. Schlotter supported by the Hungarian National Research Fund (OTKA Grants Nos. K-108383 and K-108947).
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Matthias Mnich, Email: matthias.mnich@tuhh.de.
Ildikó Schlotter, Email: ildi@cs.bme.hu.
References
- 1.Arulselvan A, Cseh Á, Groß M, Manlove DF, Matuschke J. Matchings with lower quotas: algorithms and complexity. Algorithmica. 2018;8(1):185–208. doi: 10.1007/s00453-016-0252-6. [DOI] [Google Scholar]
- 2.Aziz, H., Schlotter, I., Walsh, T.: Control of fair division. In: IJCAI 2016, pp. 67–73. IJCAI/AAAI Press (2016)
- 3.Aziz, H., Seedig, H.G., von Wedel, J.K.: On the susceptibility of the deferred acceptance algorithm. In: AAMAS 2015, pp. 939–947 (2015)
- 4.Biró P, Fleiner T, Irving RW, Manlove DF. The college admissions problem with lower and common quotas. Theor. Comput. Sci. 2010;411(34–36):3136–3153. doi: 10.1016/j.tcs.2010.05.005. [DOI] [Google Scholar]
- 5.Biró P, Irving RW, Schlotter I. Stable matching with couples: an empirical study. ACM J. Exp. Algorithmics. 2011;16:1.2:1.1–1.2:1.27. [Google Scholar]
- 6.Biró P, Manlove DF, McDermid EJ. “Almost stable” matchings in the roommates problem with bounded preference lists. Theor. Comput. Sci. 2012;432:10–20. doi: 10.1016/j.tcs.2012.01.022. [DOI] [Google Scholar]
- 7.Brandt F, Conitzer V, Endriss U, Lang J, Procaccia AD. Handbook of Computational Social Choice. New York: Cambridge University Press; 2016. [Google Scholar]
- 8.Cechlárová K, Fleiner T. Pareto optimal matchings with lower quotas. Math. Soc. Sci. 2017;88(C):3–10. doi: 10.1016/j.mathsocsci.2017.03.007. [DOI] [Google Scholar]
- 9.Chen, J., Huang, X., Kanj, I.A., Xia, G.: Linear FPT reductions and computational lower bounds. In: STOC 2004, pp. 212–221 (2004)
- 10.Cseh Á, Manlove DF. Stable marriage and roommates problems with restricted edges: complexity and approximability. Discrete Optim. 2016;20:62–89. doi: 10.1016/j.disopt.2016.03.002. [DOI] [Google Scholar]
- 11.Cygan M, Fomin FV, Kowalik Ł, Lokshtanov D, Marx D, Pilipczuk M, Pilipczuk M, Saurabh S. Parameterized Algorithms. Cham: Springer; 2015. [Google Scholar]
- 12.Dias VM, da Fonseca GD, de Figueiredo CM, Szwarcfiter JL. The stable marriage problem with restricted pairs. Theor. Comput. Sci. 2003;306(1–3):391–405. doi: 10.1016/S0304-3975(03)00319-0. [DOI] [Google Scholar]
- 13.Ehlers L, Hafalir IE, Yenmez MB, Yildirim MA. School choice with controlled choice constraints: hard bounds versus soft bounds. J. Econ. Theory. 2014;153:648–683. doi: 10.1016/j.jet.2014.03.004. [DOI] [Google Scholar]
- 14.Fellows MR, Hermelin D, Rosamond F, Vialette S. On the parameterized complexity of multiple-interval graph problems. Theor. Comput. Sci. 2009;410(1):53–61. doi: 10.1016/j.tcs.2008.09.065. [DOI] [Google Scholar]
- 15.Fleiner T, Irving RW, Manlove DF. Efficient algorithms for generalised stable marriage and roommates problems. Theor. Comput. Sci. 2007;381:162–176. doi: 10.1016/j.tcs.2007.04.029. [DOI] [Google Scholar]
- 16.Fleiner T, Kamiyama N. A matroid approach to stable matchings with lower quotas. Math. Oper. Res. 2016;41(2):734–744. doi: 10.1287/moor.2015.0751. [DOI] [Google Scholar]
- 17.Fragiadakis D, Iwasaki A, Troyan P, Ueda S, Yokoo M. Strategyproof matching with minimum quotas. ACM Trans. Econ. Comput. 2016;4(1):6:1–6:40. doi: 10.1145/2841226. [DOI] [Google Scholar]
- 18.Fragiadakis D, Troyan P. Improving matching under hard distributional constraints. Theor. Econ. 2017;12:863–908. doi: 10.3982/TE2195. [DOI] [Google Scholar]
- 19.Gale D, Shapley LS. College admissions and the stability of marriage. Am. Math. Mon. 1962;69(1):9–15. doi: 10.1080/00029890.1962.11989827. [DOI] [Google Scholar]
- 20.Gale D, Sotomayor M. Some remarks on the stable matching problem. Discrete Appl. Math. 1985;11(3):223–232. doi: 10.1016/0166-218X(85)90074-5. [DOI] [Google Scholar]
- 21.Garey M, Johnson DS. Computers and Intractability: A Guide to the Theory of -Completeness. New York: W. H. Freeman and Co.; 1979. [Google Scholar]
- 22.Goto M, Iwasaki A, Kawasaki Y, Kurata R, Yasuda Y, Yokoo M. Strategyproof matching with regional minimum and maximum quotas. Artif. Intell. 2016;235:40–57. doi: 10.1016/j.artint.2016.02.002. [DOI] [Google Scholar]
- 23.Gusfield D, Irving RW. The Stable Marriage Problem: Structure and Algorithms. Cambridge: MIT Press; 1989. [Google Scholar]
- 24.Hamada K, Iwama K, Miyazaki S. The hospitals/residents problem with lower quotas. Algorithmica. 2016;74(1):440–465. doi: 10.1007/s00453-014-9951-z. [DOI] [Google Scholar]
- 25.Hopcroft JE, Karp RM. An algorithm for maximum matchings in bipartite graphs. SIAM J. Comput. 1973;2(4):225–231. doi: 10.1137/0202019. [DOI] [Google Scholar]
- 26.Huang, C.C.: Classified stable matching. In: SODA 2010, pp. 1235–1253 (2010)
- 27.Immorlica, N., Mahdian, M.: Marriage, honesty, and stability. In: SODA 2005, pp. 53–62 (2005)
- 28.Impagliazzo R, Paturi R, Zane F. Which problems have strongly exponential complexity? J. Comput. Syst. Sci. 2001;63(4):512–530. doi: 10.1006/jcss.2001.1774. [DOI] [Google Scholar]
- 29.Irving RW, Manlove D, O’Malley G. Stable marriage with ties and bounded length preference lists. J. Discrete Algorithms. 2009;7:213–219. doi: 10.1016/j.jda.2008.09.003. [DOI] [Google Scholar]
- 30.Kamiyama N. A note on the serial dictatorship with project closures. Oper. Res. Lett. 2013;41(5):559–561. doi: 10.1016/j.orl.2013.07.006. [DOI] [Google Scholar]
- 31.Knuth DE. Mariages stables et leurs relations avec d’autres problèmes combinatoires. Montreal: Les Presses de l’Université de Montréal; 1976. [Google Scholar]
- 32.Kojima F, Pathak PA, Roth AE. Matching with couples: stability and incentives in large markets. Q. J. Econ. 2013;128(4):1585–1632. doi: 10.1093/qje/qjt019. [DOI] [Google Scholar]
- 33.Kominers SD, Sönmez T. Matching with slot-specific priorities: theory. Theor. Econ. 2016;11(2):683–710. doi: 10.3982/TE1839. [DOI] [Google Scholar]
- 34.Kuhn HW. The Hungarian method for the assignment problem. Nav. Res. Logist. Q. 1955;2:83–97. doi: 10.1002/nav.3800020109. [DOI] [Google Scholar]
- 35.Lovász L, Plummer M. Matching Theory. Amsterdam: North-Holland; 2009. [Google Scholar]
- 36.Manlove DF. Algorithmics of Matching Under Preferences. Singapore: World Scientific Publishing; 2013. [Google Scholar]
- 37.Marx D, Schlotter I. Parameterized complexity and local search approaches for the stable marriage problem with ties. Algorithmica. 2010;58(1):170–187. doi: 10.1007/s00453-009-9326-z. [DOI] [Google Scholar]
- 38.Marx D, Schlotter I. Stable assignment with couples: parameterized complexity and local search. Discrete Optim. 2011;8:25–40. doi: 10.1016/j.disopt.2010.07.004. [DOI] [Google Scholar]
- 39.Mnich Matthias, Schlotter Ildikó. Algorithmic Game Theory. Cham: Springer International Publishing; 2017. Stable Marriage with Covering Constraints–A Complete Computational Trichotomy; pp. 320–332. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 40.Monte D, Tumennasan N. Matching with quorums. Econ. Lett. 2013;120(1):14–17. doi: 10.1016/j.econlet.2013.03.007. [DOI] [Google Scholar]
- 41.Roth AE, Peranson E. The redesign of the matching market for American physicians: some engineering aspects of economic design. Am. Econ. Rev. 1999;89:748–780. doi: 10.1257/aer.89.4.748. [DOI] [PubMed] [Google Scholar]
- 42.Veskioja, T.: Stable marriage problem and college admission. Ph.D. thesis, Department of Informatics, Tallinn University of Technology (2005)
- 43.Westkamp A. An analysis of the German university admissions system. Econ. Theory. 2013;53(3):561–589. doi: 10.1007/s00199-012-0704-4. [DOI] [Google Scholar]
- 44.Yokoi, Y.: Envy-free matchings with lower quotas. In: ISAAC 2017, Leibniz International Proceedings in Informatics, vol. 92, pp. 67:1–67:12 (2017)
- 45.Yokoi Y. A generalized polymatroid approach to stable matchings with lower quotas. Math. Oper. Res. 2017;42:238–255. doi: 10.1287/moor.2016.0802. [DOI] [Google Scholar]