Abstract
Different from the traditional healthcare field, Medical Cyber Physical Systems (MCPS) rely more on wireless wearable devices and medical applications to provide better medical services. The secure storage and sharing of medical data are facing great challenges. Blockchain technology with decentralization, security, credibility and tamper-proof is an effective way to solve this problem. However, capacity limitation is one of the main reasons affecting the improvement of blockchain performance. Certificateless aggregation signature schemes can greatly tackle the difficulty of blockchain expansion. In this paper, we describe a two-layer system model in which medical records are stored off-blockchain and shared on-blockchain. Furthermore, a multi-trapdoor hash function is proposed. Based on the proposed multi-trapdoor hash function, we present a certificateless aggregate signature scheme for blockchain-based MCPS. The purpose is to realize the authentication of related medical staffs, medical equipment, and medical apps, ensure the integrity of medical records, and support the secure storage and sharing of medical information. The proposed scheme is highly computationally efficient because it does not use bilinear maps and exponential operations. Many certificateless aggregate signature schemes without bilinear maps in Internet of things (IoT) have been proposed in recent years, but they are not applied to the medical field, and they do not consider the security requirements of medical data. The proposed scheme in this paper has high computing and storage efficiency, while meeting the security requirements in MCPS.
Keywords: blockchain, privacy protection, certificateless aggregate signature, trapdoor hash function, MCPS
1. Introduction
In the big data era, with the development of Internet of Things, smart healthcare provides people with more convenient and high-quality healthcare services [1]. The Medical Cyber Physical System (MCPS) [2] is a special type of Cyber Physical System (CPS) based on the application background of the smart healthcare field, which consists of physical space and cyber space. Physical space includes wearable devices, medical diagnostic equipment, and user space consisting of doctors, nurses, etc. Cyber space is the nerve center of MCPS. It receives sensing information from physical space through a network transmission system. Then cyber space identifies, stores, analyzes, processes, and generates feedback control information. Finally, it sends control information to physical space through a network transmission system.
MCPS continuously collects the patient’s physical signs data through various wearable devices and medical devices, so that the patient’s physical condition can be better detected [3]. In order to provide patients with a more accurate and timely diagnosis, different medical institutions need to share a large amount of physical data collected by the sensors and healthcare staff [4]. At the same time, patient privacy should be protected. Thus, blockchain is needed to utilize peer-to-peer network and cryptography technology to achieve tamper proof, unforgeable, non-repudiation, and verifiable medical records. The combination of MCPS and blockchain [5] promotes the sharing of medical services and resources [6]. However, the block capacity limit is one of the main factors that affects the performance improvement of blockchain.
MCPS controls the embedded medical equipment through a wireless network, which senses and monitors the patient’s physical data in real time. When the patient has an abnormal situation, the medical equipment sends the early warning information to the medical institution in time. Once MCPS is under cyberattacks, such as data inconsistency, unauthorized access, and data breaches [7], patients’ lives and health will be seriously threatened. In practice, medical institutions need to check the accuracy and integrity of shared and sensed medical data before making medical diagnoses. The medical data, which is collected from wearable devices, medical equipment, medical apps, and healthcare staff needs the responsible healthcare provider to sign on it. A large number of signatures and verifications result in high time and space overheads. At the same time, considering the capacity limitation of the blockchain, the certificateless aggregate signature is an effective method because of its compression characteristics. In recent years, some certificateless aggregate signature schemes [8,9,10] have been proposed. However, the performance of these schemes is not ideal because they use more time-consuming bilinear maps. At the same security level, the Elliptic Curve Cryptography (ECC) is more efficient than bilinear maps [11]. Therefore, with the characteristics of low computation, low storage, high reliability, privacy protection, and timeliness, the certificateless aggregate signature scheme based on ECC is suitable for blockchain-based MCPS.
The contributions of this paper are as follows:
A two-layer storage model in which medical data is stored off-blockchain and shared on-blockchain is proposed. The model meets security and privacy requirements of MCPS.
Based on ECC, we present the multi-trapdoor hash function, which is secure and efficient to construct the certificateless aggregate signature scheme.
The certificateless aggregate signature scheme based on the multi-trapdoor hash function is proposed in this paper. It can reduce the computation cost of wearable medical devices and miners.
The rest of this paper is organized as follows. Related works are discussed in Section 2. The necessary preliminaries are presented in Section 3. Section 4 presents a multi-trapdoor hash function. In Section 5, we describe the certificateless aggregate signature scheme. A security discussion of the proposed scheme is given in Section 6. Then, we make an efficiency analysis in Section 7. Finally, the conclusion is offered in Section 8.
2. Related Work
2.1. Blockchain
Blockchain is a decentralized, anonymous, untrusted, tamper proof, and traceable distributed data storage technology [5]. With the development of the medical industry, health data is growing exponentially. How to effectively store, share, and manage medical data involving a large number of patients’ privacy has become an obstacle to the development of the healthcare industry. Due to the characteristics of blockchain [12], such as non-tamperability, traceability, and multi private key authorization management, it is possible to share medical data securely among different institutions [13]. According to the difference of open objects, blockchain can be divided into Public Blockchain, Private Blockchain, and Consortium Blockchain. These three types of blockchains are compared in Table 1. In the special field of MCPS, medical data contains both a large amount of private information and has the need to be shared between different institutions, therefore the Consortium Blockchain is more suitable for the secure storage and sharing of medical data.
Table 1.
The comparison of three types of blockchains.
| Blockchain Type | Public Blockchain | Private Blockchain | Consortium Blockchain |
|---|---|---|---|
| Open objects | All | Individuals or inside company | Authorized companies or organizations |
| Consensus mechanism | PoW, PoS, DPoS | PBFT | PBFT, Raft |
| Centralization | Decentralization | Centralization | Partial centralization |
| Typical application | Bitcoin, Ethereum | Overstock | Hyperledger, R3CEV |
| Characteristics | Self-building of trust | Traceability | Improvement of efficiency |
Xue et al. [14] divided the existing medical institutions into medical institution federate servers (MIPS) and audit federate servers (AFS) according to their credit scores. Through the improved consensus mechanism, the medical data sharing model based on blockchain was realized. In the untrusted environment, Xia et al. [15] designed a sensitive medical data sharing model between cloud service providers based on blockchain through a smart contract and access control mechanism. The security requirements of medical records on integrity, confidentiality, and traceability can be realized by digital signature technology in the blockchain-based medical data sharing system.
In recent years, researchers have conducted in-depth research around blockchain-based multi-signatures [16], aggregate signatures [17,18], ring signatures [19], and homomorphic signatures [20]. Among them, aggregate signatures are favored for their advantages, such as fast computing speed, small storage space, and bandwidth saving. Moreover, some scholars have carried out in-depth research on the combination of quantum computing and the security of blockchain [21]. Gao et al. [21] proposed a lattice-based signature scheme and presented a cryptocurrency scheme based on post-quantum blockchain, which could resist quantum computing attacks.
2.2. Certificateless Aggregate Signature
In order to solve the management problems of certificate distribution and storage in the traditional PKI-based (Public Key Infrastructure) public key cryptosystem, Shamir proposed the identity-based public key cryptosystem (ID-PKC) in 1984 [22]. In ID-PKC, the public key is denoted by user information, such as mailbox, address, telephone number, etc. The private key is provided by the key generation center (KGC), a third-party trusted organization. Different from traditional public key cryptosystems, users cannot generate their own private key. For KGC, the user’s private key is known, and KGC can decrypt ciphertext and forge identity at will. Therefore, ID-PKC has the defect of key escrow [23], which is only applicable to the environment with low security requirements.
To solve this problem, Al-Riyami and Paterson proposed the notion of certificateless public key cryptography (CL-PKC) in 2003 [24]. Unlike ID-PKC, the private key in CL-PKC consists of a partial private key generated by KGC and the secret value selected by the user. KGC only knows partial private key but cannot get the secret key. It can effectively solve the key escrow problem [25]. Moreover, the public key in CL-PKC does not need certificate verification, so the problem of public key authentication is solved. CL-PKC has neither the certificate management problem nor the key escrow problem. Its calculation efficiency is higher than traditional public key cryptosystems, and its security is higher than ID-PKC. Therefore, it is suitable for application scenarios with higher requirements for computing, storage efficiency, and security.
Boneh et al. first proposed the concept of aggregate signature [26] on EUROCRYPT 2003, which greatly promoted the development of digital signature cryptography. Aggregate signature [26] is suitable for compressing many signatures generated by many different users to many different messages into one short signature, and simplifying the verification of multiple signatures into one verification. Aggregation signature greatly improves storage efficiency and verification time.
In recent years, certificateless aggregate signatures (CLAS) have attracted many scholars’ research interests because of the advantages of both a certificateless public key cryptosystem and aggregate signatures. Based on different theoretical foundations, scholars have proposed corresponding certificateless aggregate signature schemes. For example, most researchers proposed certificateless aggregate signature schemes based on bilinear maps [8,9,10]. For the first time, Gong et al. [9] proposed two certificateless identity-based aggregate signature schemes (denoted as CAS-1 and CAS-2 in [9]). In these two schemes, the aggregation verification of CAS-1 used 2n + 1 pairing operations on an elliptic curve. CAS-2 used n + 2 pairing operations and n scalar point multiplication operations on elliptic curves. It is clear that the verification efficiency was very low. Xiong et al. designed a more efficient certificateless aggregate signature scheme [8]. The verification of this scheme used only three pairing operations and 2n scalar multiplication operations. The efficiency of the scheme was not related to the number of signers. Moreover, it did not require a synchronized clock. As such, this scheme was more efficient than the Gong’s scheme [9]. However, He et al. [27] and Zhang [10] et al. pointed out that Xiong et al.’s scheme was not secure. He et al. [27] proved that Xiong et al.’s scheme was not resistant to forge attacks from Ⅱ adversary. Zhang et al. proved that Xiong et al.’s scheme could not resist coalition attacks from the honest-but-curious KGC, malicious-but-passive KGC, and inside signers.
Some scholars did not use bilinear pairs to construct certificateless aggregate signatures. Zhou et al. proposed two certificateless aggregate signature schemes without bilinear maps [28]. Based on the Elliptic Curve Discrete Logarithm Problem (ECDLP), the schemes both used 2n + 1 scalar multiplication operations. The difference is that CLAS-2 provides a shorter constant-level signature length than CLAS-1. Cui et al. [29] proposed a certificateless aggregate signature scheme based on ECC and applied it to vehicular ad hoc networks (VANETs) communication. The verification of this scheme used n scalar multiplications. Since the computational overhead of bilinear pairs is significantly higher than that of scalar multiplication under ECC [11], Zhou’s scheme and Cui’s scheme had higher computational efficiency.
In recent years, with the development of blockchain technology, more and more scholars have focused on the research of the aggregation signature algorithm based on blockchain [17,18,30]. Gao et al. [18] designed a fair and efficient multi-party contract signing scheme based on blockchain by conducting a certificateless aggregation verifiable encryption signature scheme. Wang et al. [30] realized the full anonymous blockchain by homomorphic encryption, and aggregate signature technology, which effectively protected the privacy of the user’s identity and the transaction amount. Neither of these schemes [18,30] is computationally efficient because they both used bilinear maps. Based on the gamma signature proposed by Yao et al. [31], Zhao [17] constructed an aggregate signature scheme without bilinear maps. By applying Zhao’s scheme [17] to Bitcoin, it could be found that both computation and storage overhead have decreased to some extent, however the length of this aggregate signature scheme increased with the number of signers. Due to their low computing or communication efficiency, these schemes [17,18,30] were not suitable for wearable medical devices with limited computing and storage resources. On the other hand, these schemes [17,18,30] did not focus on the security requirements of MCPS, such as timeliness and privacy protection.
Some scholars focused on the research of digital signatures in blockchain-based Internet of things (IoT) applications [32,33]. In order to reduce the time cost of transmitting authentication information from blockchain nodes to IoT devices, Danzi et al. [32] proposed a repeat-authenticate scheme. In which blockchain information that consists of a copy of the block header and the signatures of blockchain nodes is multicasted. Kaga et al. [33] proposed a biometrics-based fuzzy signature scheme and applied it into the IoT blockchain system. This scheme achieved the verification of a creator of a transaction. These two schemes payed more attention to authentication of transaction creators or blocks in IoT scenario. However, they did not focus on the effective storage of a large number of digital signatures and the privacy protection of medical data in MCPS scenario. When a patient goes to the hospital, a great deal of medical records will be generated. The digital signatures of these medical records will occupy a large amount of block space, which will seriously affect the performance of the blockchain. At the same time, medical data involves personal privacy, and it is necessary to protect the private data.
The blockchain-based schemes mentioned above are compared in Table 2. From Table 2, we can conclude that none of these solutions [17,18,30,32,33] provide both high computing and communication efficiency. Furthermore, nowadays, certificateless aggregate signatures based on blockchain have not been widely used in MCPS. In this paper, we combine ECC and the multi-trapdoor hash function to propose a certificateless aggregate signature scheme and apply it to secure storage and sharing of MCPS. The proposed scheme provides high computing efficiency and low space occupation, which is suitable for blockchain-based MCPS scenario with limited blockchain capacity and low computing power wearable devices.
Table 2.
The comparison of relevant blockchain-based schemes.
3. Preliminaries
3.1. Elliptic Curve Discrete Logarithm
Let p, q be two large prime numbers, Fp be a finite field determined by p, and E(Fp) be an elliptic curve over Fp, which is defined by the equation: y2 = x3 + ax + b mod p, where a, b∈Fp and 4a3 + 27b2 ≠ 0. If the additive group G consists of the infinity point O and all points on E(Fp), P is a generator of group G with the order q, we have the following definition.
Definition 1
(Elliptic curve discrete logarithm problem (ECDLP) [34]). Given Q = mP and , the task of ECDLP is to find the integer m, where 0 ≤ m ≤ q − 1.
3.2. Trapdoor Hash Function
The trapdoor hash function is also called the chameleon function [35]. Different from general hash functions, it has a hash/trapdoor key (HaK, TrK). The hash key (HaK) is public, while the trapdoor key (TrK) is private. The trapdoor hash function uses some special information to generate a fixed hash value, and its collision resistance depends on the user’s knowledge of trapdoor information (TrK) [36]. That is, without knowing the trapdoor key TrK, the trapdoor hash function is collision resistant. However, when the hash/trapdoor key is known, the trapdoor collision can be computed [37]. This property of the trapdoor hash function is suitable to construct various digital signature schemes [36,37,38,39].
The trapdoor hash function consists of the following four algorithms [37]:
ParG: Inputs security parameter k, outputs system parameter params;
KeyG: Inputs params, outputs hash/trapdoor key <HaK, TrK>;
HashG: Inputs params, message m and auxiliary parameter r, outputs trapdoor value THHaK(m, r);
TrapColG: Inputs params, <HaK, TrK>, m, r, and new message m’(≠ m), outputs r’ and HaK’ such that ;
According to the number of trapdoor information (TrK), trapdoor hash functions include the single trapdoor hash function [35], the double trapdoor hash function [39], and the multi-trapdoor hash function [37,38]. A double trapdoor hash function usually has two pairs of hash/trapdoor keys, named long-term hash/trapdoor key and temporary hash/trapdoor key. Double trapdoor hash function protects the long-term trapdoor key from being leaked by sacrificing the temporary trapdoor key. The multi-trapdoor hash function has multiple hash/trapdoor keys, which combines multiple collisions generated by multiple entities to conduct a single collision. As a result, the multi-trapdoor hash function has the advantage of computing efficiency as well as storage space and bandwidth saving. In this paper, we build a certificateless aggregate signature scheme based on the multi-trapdoor hash function, with which a blockchain- based MCPS data storage and sharing model is proposed.
3.3. Certificateless Aggregate Signature
3.3.1. Definition of Certificateless Aggregate Signature
A certificateless aggregate signature consists of the following six algorithms [40]:
Setup: Inputs the security parameter k, KGC outputs the system public parameter Kpub and system master key λ.
Partial-Private-Key-Gen: Inputs k, Kpub, λ, and user’s identity IDi, KGC outputs the partial private key θi and sends it to the user IDi through a secure channel.
User-Key-Gen: Inputs k, the user IDi outputs secret/public key pair (αi, Xi).
Sign: Inputs k, IDi, (αi, Xi), and message mi, the user IDi outputs a signature σi.
Agg-Sign-Gen: Inputs k, , , the aggregator outputs the aggregate signature σ on .
Agg-Ver-Gen: Inputs k, , σ, , and public key sets , if the verification is correct, the verifier outputs 1, otherwise, the verifier outputs 0.
3.3.2. Security Models of Certificateless Aggregate Signature
According to different capabilities, two types of adversaries are considered in certificateless aggregate signature schemes [9]. In addition, certificateless aggregate signature schemes should be existentially unforgeable under these adversaries, Ⅰ and Ⅱ.
Ⅰ adversary cannot get the system master key, but they can replace the public keys of legitimate users. Usually, Ⅰ adversary acts as malicious KGC.
Ⅱ adversary can obtain the system master key, however they cannot replace the public keys of legitimate users. Ⅱ adversary is often regarded as malicious inside signers.
For these types of adversaries, we define the following two games:
(1) Game Ⅰ:
Setup: Challenger inputs security parameters k, generates system parameter pars and system master key , sends pars to adversary Ⅰ, and keeps secretly.
Query: Ⅰ adaptively performs the following oracle queries:
Hash queries: Ⅰ sends a hash oracle query for all hash values in the scheme, and challenger returns the corresponding value.
Partial-Key-Gen query: When Ⅰ makes a partial private key query on the user IDi, the challenger runs the partial private key generation algorithm to generate the corresponding partial private key and returns it to Ⅰ.
Secret-Key-Gen query: When Ⅰ makes a secret key query on the user IDi, the challenger runs the secret key generation algorithm to generate the corresponding secret key and returns it to Ⅰ.
Public-Key-Gen query: When Ⅰ makes a public key query on the user IDi, the challenger runs the public key generation algorithm to generate the corresponding public key and returns it to Ⅰ.
Public-Key-Replacement query: When Ⅰ queries user IDi for public key replacement, replaces the corresponding public key of user IDi with a randomly selected and saves it.
Signature queries: Inputs message , user IDi and corresponding private key and status information , runs the signature algorithm to generate the corresponding signature and returns it to Ⅰ.
Forge: After the above polynomial bounded queries, outputs the forged aggregate signature σ* = (ω*, D*). The adversary wins the game if and only if:
Forged signature σ* is a valid signature.
Ⅰ cannot query at least one of n users for partial private key.
(2) Game Ⅱ:
Setup: Challenger inputs security parameters k, generates system parameter pars and system master key , sends pars and to adversary Ⅱ.
Query: In this stage, adversary Ⅱ adaptively performs the polynomial bounded oracle queries which are similar to Game Ⅰ. The difference is that Ⅱ does not perform the public key replacement query and partial private key query.
Forge: outputs the forged aggregate signature σ* = (ω*, D*). The adversary Ⅱ wins the game if and only if:
Forged signature σ* is a valid signature.
Ⅱ cannot query at least one of n users for secret value.
3.4. System Model
In this paper, a two-layer system model is used to describe the secure storage and sharing of medical records in MCPS. As shown in Figure 1, the off-blockchain layer completes the acquisition, aggregation, and storage of medical data. In our proposed system model, every doctor, nurse, medical device, and medical app has a pseudonym, partial private key, secret value, and public key. The pseudonym is distributed by the Registry Center, and partial private keys are allocated by the KGC. Doctors, nurses, medical equipment, and medical apps are noted as data acquisition units (DAU). The medical record of a patient consists of several medical record items (MRI). Each MRI is signed by the DAU who is responsible for it. A patient’s diagnosis and treatment process corresponds to a Central Hospital. When a patient goes to different Central Hospitals, it corresponds to different treatment processes. Each DAU encrypts the collected MRIs with the public key of the Central Hospital, and calculates the hash value of MRIs it is responsible for as digital digest. The DAU’s private key is used to individually sign on the digest information. Then, the encrypted MRIs, digest information, and individual signatures are sent to the Central Hospital. The Central Hospital verifies the correctness of the individual signature. If it is correct, the encrypted original medical data is stored in the Medical Cloud. Finally, the Central Hospital combines the individual signatures into an aggregate signature, and sends the digest, aggregate signature, access control, and location index of the original MRIs to the Medical Blockchain.
Figure 1.
System model.
The on-blockchain layer completes the sharing of medical data. Figure 2 shows that each transaction of the Medical Chain contains a digest of the Pi’s MRIs, an aggregate signature, access control, and a specific location index of the original medical data stored in the Medical Cloud. Each block contains a hash value linked to the previous block. This hash value can be used to retrieve the block. The Medical Chain uses time stamps to ensure that the blocks are linked in time. The latest generated blocks are broadcast to the entire network. The nodes receiving the information verify the correctness according to the consensus algorithm. If it is correct, they pass the information to other nodes. After most nodes verify the correctness, the miner adds the block into the main chain to form the permanent storage and sharing of medical records. The patient is the owner of medical data, who grants an entity (doctor, institution, researcher, etc.) access to original medical records through access control protocol. When an entity gains access, they look up on the Medical Chain, obtains the position index of medical data in cloud, then they can access the original medical records.
Figure 2.
Medical Chain model.
In the above model, one block contains multiple transactions, and one transaction relates to all medical records of one medical treatment process of a patient. By using blockchain to store the digest and aggregate signature, the unforgeability of DAU’s service and the integrity of medical data can be guaranteed. Meanwhile, the block capacity limitation can be greatly eased. On the other hand, the encrypted original medical data is stored in the cloud, which is retrieved through the data location index on the blockchain. The access rights of entities are managed through the access control on the blockchain. Therefore, the secure storage and sharing of medical data in MCPS is realized.
3.5. Security Requirements
The following security requirements are important for medical data in MCPS:
Non-repudiation: Medical data is the record of treatment process, which has the function of legal evidence. Any modification of a medical record should be non-repudiation;
Integrity: As an important record of the patient’s treatment, medical data should be guaranteed to be accurate, which means it cannot be tampered by anyone in any way. In other words, any data tampering can be detected;
Privacy: Medical data involves patient’s personal privacy, which should be kept confidential. It could not be allowed to be disclosed at will, only the authorized users can access it;
Traceability: When medical disputes occur between doctors and patients, medical data should be traceable as legal evidence;
Timeliness: Time factor is one of the key points in the whole treatment process. It is necessary to make effective time judgment on each sensitive link in the treatment process, so as to ensure the authenticity and effectiveness of medical data.
Among these security requirements, tamper-proofing, data integrity, and privacy protection are crucial issues in MCPS [4]. It is necessary to use relevant technical means, such as identity authentication, blockchain technology, digital signatures, to achieve secure storage and sharing of medical information.
3.6. System Framework
The certificateless aggregate signature scheme based on the trapdoor hash function proposed in this paper consists of the following algorithms:
Setup: The algorithm is completed by KGC. Inputs security parameter k, outputs master key λ, system parameter pars.
Pseudonym-Gen: The algorithm generates pseudonyms for each entity by Registry Center. Inputs the real identity of each DAUi or patient Pj (denoted as and ), outputs its pseudonym or .
DAUi Key-Gen: DAUi generates its secret value-public key pair and sends to KGC through the secure channel. After receiving DAUi’s pseudonym , system parameters pars, public key and master key λ, KGC outputs the DAUi’s partial private key . The public key (long-term hash key) of the DAUi is , the long-term trapdoor key is , and the private key is .
Hash-Gen: In this algorithm, the trapdoor hash value of DAUi is generated. Inputs system parameter pars, original message si, DAUi’s hash key , auxiliary parameter ui, outputs DAUi’s trapdoor hash value .
Individual-Sign: In this algorithm, DAUi generates its individual signature. Inputs system parameter pars, digest of MRIs in the charge of DAUi (denoted as ), status information Ωi of DAUi, trapdoor key , hash key , and outputs DAUi’s individual signature .
Individual-Verify: The Central Hospital verifies the correctness of individual signature. Inputs DAUi’s individual signature , hash key , check the correctness of . If correct, accepts and outputs 1, otherwise, rejects and outputs 0.
Aggregate-Sign: The Central Hospital produces aggregate signature. The Central Hospital aggregates the verified individual signatures into a single short signature .
Aggregate-Verify: The algorithm is responsible for verifying the correctness of the aggregate signature by miner nodes. Inputs aggregate signature , all related DAUi’s trapdoor keys , verifies the correctness of . If correct, accepts and outputs 1, otherwise, rejects and outputs 0.
4. The Proposed Multi-Trapdoor Hash Function
The proposed multi-trapdoor hash function based on ECC is presented in this section.
ParG: Suppose the security parameter k, KGC selects large prime numbers p, q and elliptic curves over finite fields , . Given G is a cyclic subgroup of E(Fp), P is a q-order generator of G, KGC takes secure hash function: . KGC outputs the system parameter pars = (G, P, q, W).
KeyG: Each DAUi selects randomly trapdoor key and computes hash key: , then outputs .
-
HashG: Each DAUi randomly selects the auxiliary parameter ui, computes trapdoor hash value:Finally, the Central Hospital calculates multi-trapdoor hash value:
- TrapColG: Each DAUi randomly selects temporary trapdoor key and computes temporary hash key . The collision parameter is given as
Trapdoor collision is one of the properties of trapdoor hash functions [37]. Given hash keys (), trapdoor keys (), message/auxiliary parameter pair , and new message , collision parameter is given by which satisfies
That is
From the above proof process, we can conclude that the owner of the trapdoor key can compute the trapdoor collision based on the given input. The proposed multi-trapdoor hash function aggregates multiple trapdoor collisions into one trapdoor collision, which improves the calculation efficiency. On the other hand, people who do not know the trapdoor key cannot calculate the trapdoor collision. Therefore, the proposed multi-trapdoor hash function is secure and efficient to construct the certificateless aggregate signature scheme.
5. The Proposed Certificateless Aggregate Signature Scheme
The proposed certificateless aggregate signature scheme based on the multiple trapdoor hash function is presented in this section. We introduce an attribute-based signature [41] and state the information, so that the requirements for medical data in blockchain-based MCPS can be better satisfied.
5.1. Setup
In this subsection, KGC will generate the system parameter and send it to data acquisition units DAUi, patients Pj, and Central Hospitals. Suppose the security parameter k, KGC selects large prime numbers p, q and elliptic curves over finite fields , . Given G is a cyclic subgroup of E(Fp), P is a q-order generator of G, KGC takes seven secure hash functions: , , , , , , . KGC randomly selects as the system master key. Then, the public key is . Finally, KGC outputs the system parameter pars = (G, P, q, Kpub, W1, W2, W3, W4, W5, W6, H).
5.2. Pseudonym-Gen
In this phase, the Registry Center calculates the pseudonyms for DAUi and Pj according to their real identities. The pseudonym system [42] is used to provide conditional privacy protection for doctors, nurses, patients, medical devices, etc. When relevant organizations need to know their real identity, the Registry Center can index their real identity. The Registry Center performs the following procedure to generate pseudonyms for DAUi and Pj.
The Registry Center accepts DAUi’s real identity and calculates its pseudo identity . After selecting a random , DAUi calculates , , and sends to the Registry Center through the secure channel. The Registry Center calculates , and outputs pseudonym .
The Registry Center accepts Pj’s real identity and calculates its pseudo identity . After selecting a random , Pj calculates , , and sends to the Registry Center through the secure channel. The Registry Center calculates , and outputs pseudonym .
At the same time, the Registry Center builds an index table between the real identities of DAUi (Pj) and their pseudonyms, such as , , so that when relevant organizations need to know the real identities of DAUi or Pj, the Registry Center could return their real identities.
5.3. DAUi Key-Gen
In this stage, DAUi completes secret value/public parameter pair generation and sends the public parameter to KGC. With the received public parameter, KGC computes partial private key/partial public key pair. These two key pairs constitute the public keys and private keys of DAUi. Because the keys of DAUi are obtained by two entities (KGC and DAU), it is effective to protect the security of the keys.
DAUi randomly selects the secret value , calculates as the public parameter. Then, DAUi sends the public parameter to the KGC and the Central Hospital.
It then inputs the pseudonym and public parameters of DAUi, KGC randomly selects as the secret value, calculates and DAUi’s partial private key , then sends and to DAUi through the secure channel. DAUi verifies the correctness of partial private key by checking whether the equation is valid.
DAUi’s public and private keys are: , . The partial private key and pseudonym effectively protect DAUi’s identity information. It plays a role of privacy protection.
5.4. Hash-Gen
In this section, each DAUi generates its own trapdoor hash value and sends it to the Central Hospital. Then, the Central Hospital combines all verified trapdoor hash values into a single value. Based on the trapdoor hash value, the trapdoor collision can be calculated, which can be used to achieve the individual signature.
Firstly, it inputs system parameter pars, original message si, DAUi’s hash key (public parameter), DAUi randomly selects auxiliary parameter ui, and calculates trapdoor hash value . Where the original message si depends on the attribute value of DAUi. That is to say, if DAUi is a doctor or a nurse, then si is composed of the ID of the hospital where he or she works, his or her working department, and position titles, etc.; if DAUi is a medical equipment or app, then si is composed of DAUi’s pseudonym , its manufacturer, categories, the affiliated institutions (hospitals, communities, scientific research institutions, etc.), etc. Using a series of attributes related to the signer to determine their identity can effectively protect the privacy of the signer, such as phone number, home address, email, etc.
When a patient Pj starts data interaction with a DAUi, the trapdoor hash value Ti of DAUi is calculated in advance and sent to the Central Hospital. When the treatment of Pj is completed (assuming that Pj generates n MRIs with n DAUis), the Central Hospital aggregates the trapdoor hash value T of all the DAUis responsible for Pj’s MRIs, and sends T to each DAUi, which interacts with Pj.
5.5. Individual-Sign
In this subsection, each DAUi that provides medical services to the patient Pj completes an individual signature on the medical data for which it is responsible. We define the state information of DAUi as Ωi, that is, the pseudonym of Pj associated with this DAUi. Only the individual signatures with the same Ωi (that is, for the same patient) can be aggregated.
DAUi selects the latest timestamp ti and calculates , . The latest timestamp ensures the timeliness of data collection and resists replay attacks. DAUi randomly selects temporary trapdoor key , and calculates the temporary hash key and the trapdoor hash value . represents the digest of Pj’s MRI, which is in the charge of DAUi during this treatment. According to trapdoor collision (that is ), it calculates collision parameter , , . DAUi’s individual signature for patient Pj is . DAUi sends to the Central Hospital.
5.6. Individual-Verify
In this stage, the Central Hospital achieves the verification of DAUi’s individual signature. When the Central Hospital receives DAUi’s individual signature and new auxiliary parameter , the Central Hospital performs the following steps:
Compute and
Check whether holds or not. If it holds, the Central Hospital accepts and then stores the encrypted original medical data in the Medical Cloud.
Since , , , we obtain
5.7. Aggregate-Sign
In this phase, the Central Hospital aggregates the accepted individual signatures for medical data from the same patient. The Central Hospital checks the status information Ωi of each DAUi whose individual signature is accepted. For individual signatures with the same Ωi, the Central Hospital calculates , D, and the aggregate signature . Then, the Central Hospital forms a transaction by Pj’s MRI digest, aggregation signature, access control, and the specific location of the original medical data in the Medical Cloud. Finally, a transaction request is sent to the Medical Chain.
5.8. Aggregate-Verify
After the miner receives the message, the aggregate signature is verified through the consensus mechanism. If the equation DP holds, the information is broadcast to other nodes in the network. The other nodes start consensus verification of the transaction and broadcast on the network. After the verification is successful, the transaction is added to the block.
6. Security Discussion
6.1. Correctness Proof
The correctness proof of the aggregate is verified as follows:
6.2. Security Proof
Theorem 1.
In the random oracle model, the proposed certificateless aggregate signature scheme is existentially unforgeable against adaptive chosen-message attacks under the assumption that the ECDLP problem is hard.
This theorem is obtained by combining Lemmas 1 and 2.
Lemma 1.
Given anⅠtype adversarymakes at mostSign queries,Partial-Key-Gen queries,Partial-Key-Gen queries within a period t in the random oracle model, and wins the game with an non-negligible probability ε, that is, successfully forging the signature of the proposed scheme. Then, an algorithmcan be performed in polynomial time, and solve an instance of ECDLP with probability (supposing the number of aggregate signatures is n).
Proof.
Suppose is a solution of ECDLP and as an instance of ECDLP, the goal of the algorithm is to compute x. Suppose makes Sign queries on identities, and generates aggregate signatures at the challenge stage, selects as the target victim, and the probability of the selection is . We set up a game between adversary and challenger , and the detailed interaction process is as follows:
Setup: Given , challenger inputs security parameters k, generates system parameter pars = (G, P, q, Kpub, W1, W2, W3, W4, W5, W6, H), and sends pars to adversary . needs to maintain nine lists , whose initial values are empty.
Query: adaptively performs the following oracle queries.
W4 hash query: When makes a W4 hash query with parameter , checks whether existing or not, if so, sends to . Otherwise, selects a random . If the list does not include the tuple (*, *, *, ), sends to and saves into the hash list .
W5 hash query: When makes a W5 hash query with parameter , checks whether existing or not, if so, sends to . Otherwise, selects a random . If the list does not include the tuple (*, *, ), sends to and saves into the hash list .
W6 hash query: When makes a W6 hash query with parameter , checks whether existing or not, if so, sends to . Otherwise, selects a random . If the list does not include the tuple (*, *, *, ), sends to and saves into the hash list .
H hash query: When makes an H hash query with parameter , checks whether existing or not, if so, sends to . Otherwise, then selects a random . If the list does not include the tuple (*, *, *, ), sends to and saves into the hash list .
- -
If LP includes the tuple , sends to .- -
If LP does not include the tuple and , selects a random , computes , sends to and saves into the hash list . If list does not include corresponding tuple, then adds tuple into .- -
If LP does not include the tuple and , randomly selects , lets ( is a known random number to ), then saves into the hash list and sends to If list does not include corresponding tuple, then adds tuple into .Secret-Key-Gen query: Suppose that the query is on a pseudo identity .
If the list includes , sends to Otherwise, selects a random and computes . Then makes a Partial-Key-Gen query by and adds into list . sends to and adds into list .
Public-Key-Gen query: Suppose that the query is on a pseudo identity .
If the list includes , sends to Otherwise, selects a random and computes . Then makes a Partial- Key query by and adds into list . sends to and adds into list .
Public-Key-Replacement query: can select a new public key to replace the original public key of any legitimate DAUi.
Sends Ti to and saves into the hash list .
Then, generates individual signature and sends it to .
Otherwise, outputs failure and halts.
Then, generates aggregate signature (ω, D) and sends it to .
Otherwise, if , outputs failure and halts.
- -
If the corresponding tuple of is included in list LPK and , calculates , and verifies whether the equation holds or not, if so, returns 1 to , otherwise, returns 0 to .- -
If the corresponding tuple of is included in list LPK and , returns 1 to when the list LH includes the tuple , otherwise, returns 0 to- -
If the corresponding tuple of is not included in list LPK, returns 1 to when the list LH includes the tuple , otherwise, returns 0 toForge: After the above polynomial bounded queries, outputs the aggregate signature σ* = (ω*, D*) of , in which at least one does not make Partial-Key-Gen query and Secret-Key-Gen query, and at least one message does not make Sign query.
If all the satisfies , then outputs failure and halts. Otherwise, if one satisfies , then queries the corresponding tuples of in the lists LPK, LSK, LH and checks whether the equation DP holds or not:
- -
If the equation holds, outputs x as the efficient solution to the ECDLP.
- -
Otherwise, cannot solve the discrete logarithmic problem, because:
If queries all with Partial-Key-Gen and Secret-Key-Gen, will terminate the simulation. Suppose that
Event E1 represents that at least a does not make Partial-Key-Gen query and Secret-Key-Gen query.
Event E2 represents that does not terminate at the Sign-query stage.
Event E3 represents that does not terminate at the challenge stage.
The probability of solving the ECDLP by algorithm is as follows:
The probability that does not terminate during the whole simulation is at least
Since , when is large enough, tends to , so the probability that does not terminate during the simulation is at least
In summary, if is not terminated during the simulation, and breaks the unforgeability of the proposed scheme with a non-negligible probability , can successfully solve ECDLP with a non-negligible probability:
□
Lemma 2.
Given anⅡtype adversarymakes at mostSign queries,Partial-Key-Gen queries,Partial-Key-Gen queries within a period t in the random oracle model, and wins the game with an non-negligible probability ε, that is, successfully forging the signature of the proposed scheme. Then, an algorithmcan be performed in polynomial time, and solve an instance of ECDLP with probability (supposing the number of aggregate signatures is n).
Proof.
Suppose is a solution of ECDLP and as an instance of ECDLP. The goal of the algorithm is to compute x. selects as the target victim, and the probability of the selection is . We set up a game between adversary and challenger , and the detailed interaction process is as follows:
Setup: Challenger inputs security parameters k, generates system parameter pars, and sends pars = (G, P, q, Kpub, W1, W2, W3, W4, W5, W6, H) to adversary . needs to maintain nine lists , whose initial values are empty.
Query: Adversary makes the same queries as that of W4 hash, W5 hash, W6 hash, H hash, Secret-Key-Gen, Public-Key-Gen, Hash-Gen, Sign query, Aggregate-Sign query in Lemma 1.
- -
If the tuple is included in the list LP, sends to .- -
If the tuple is not included in the list LP and , selects a random , computes , sends to and saves into the list . Then adds tuple into .- -
If the tuple is not included in the list LP and , randomly selects , lets , then saves into the hash list and sends to Then adds tuple into .
- -
If the corresponding tuple of is included in list LPK and , calculates , and verifies whether the equation holds or not, if so, returns 1 to , otherwise, returns 0 to .- -
If the corresponding tuple of is included in list LPK and , returns 1 to when the list LH includes the tuple , otherwise, returns 0 toForge: After the above polynomial bounded queries, outputs the aggregate signature σ* = (ω*, D*) of , in which at least one does not perform the Partial-Key-Gen query and Secret-Key-Gen query, and at least one message, does not make Sign query.
If all the satisfy , then outputs failure and halts. Otherwise, if one satisfies , then queries the corresponding tuples of in the lists LPK, LSK, LH, and checks whether the equation DP holds or not:
- -
If the equation holds, outputs x as the solution to the ECDLP.
- -
Otherwise, cannot solve the discrete logarithmic problem, because:
It can be seen from the proof of Lemma 1 that the probability that does not terminate during the simulation is at least
Therefore, if is not terminated during the simulation, and breaks the unforgeability of the proposed scheme with a non-negligible probability, can successfully solve ECDLP with a non-negligible probability:
□
6.3. Security Analysis
Message authentication: As Theorem 1 states, no polynomial adversary could forge a valid message under the assumption that the ECDLP problem is hard. Therefore, the Central Hospital verifies the validity and integrity of the message by checking whether the equation holds or not, where and . Thus, the proposed scheme for MCPS provides message authentication.
Identity privacy protection: The pseudonym proposed in this paper is divided into two types: the pseudonym of DAUs and the pseudonym of patients . and are generated by combining the randomly chosen secret value or and the system master key . No adversary could compute the real identity from the pseudonym without knowing the secret or and . Thus, the pseudonym proposed in this paper can protect the identity privacy of DAUs and patients.
Resistance to replay attack: Whenever DAUi makes an individual signature, it chooses a latest timestamp . The Central Hospital will check the freshness of the timestamp in order to detect the replay attacks.
Resistance to modification attack: According to Theorem 1, the Central Hospital can protect the integrity of message . Therefore, any modification on the message will be detected by checking whether the equation holds or not.
Resistance to spam attack [17]: Because of natural compression property of the aggregate signature, the proposed signature scheme can combine n individual signature into one short signature. The length of the aggregate signature will not increase with the increase of the number of signers. Therefore, in the blockchain-based MCPS, more transactions can be added into a block. However, the attacker has to send more transactions to congest the network. It will spend more transaction fee which will increase the cost of spam attacks.
7. Efficiency Analysis
Certificateless aggregate signatures can be classified into pairing-based certificateless aggregate signatures and ECC-based certificateless aggregate signatures. In this paper, we adopt the same efficiency evaluation method as reference [11,29], in which the simulations are conducted on an Intel I7 3.4 GHz, 4 GB machine with Windows 7. Pairing-based aggregate signature schemes can be simulated on the bilinear pairing . is an additive group generated with the order on the type A elliptic curve , where and are 512-bit and 160-bit prime number, respectively [11]. For ECC-based aggregate signature schemes, the simulation can be conducted over the non-singular elliptic curve . is an additive group generated on E with the order , where , are two 160-bit prime numbers, respectively. The above mentioned bilinear pairing and elliptic curve constructed in the experiments are on the same security level of 80 bits. As shown in Table 3 and Table 4, the running time of these encryption operations has been presented.
Table 3.
| Encryption Operation | Description | Time (ms) |
|---|---|---|
| The bilinear pair operation | 4.2110 | |
| The scalar multiplication in the bilinear pair | 1.7090 | |
| The bilinear pair-to-midpoint addition | 0.0071 | |
| The hash-to-point operation in bilinear pair | 4.4060 | |
| The scalar multiplication in elliptic curve | 0.4420 | |
| The point addition operation in elliptic curve | 0.0018 | |
| The general hash operation | 0.0001 |
Table 4.
| Symbol | Description | Length (bytes) |
|---|---|---|
| |G1| | The size of elements in group | 128 |
| |G| | The size of elements in group | 40 |
| |q| | The size of the elements in | 20 |
The computation cost and communication cost are two important factors to evaluate certificateless aggregate signature schemes. In this section, the efficiency analysis is divided into two parts. First, we compare the proposed scheme with related certificateless aggregate signature schemes. Second, we compare the proposed scheme with related aggregate signature schemes based on blockchains.
1. The efficiency analysis of certificateless aggregate signature schemes
Table 5 compares the computation cost of the proposed scheme and related certificateless aggregate signature schemes [9,29].
-
-
In the individual sign algorithm, DAUi needs three scalar multiplications in the elliptic curve and two general hash operations to generate individual signature. The computation cost of our scheme in individual signature is smaller than related certificateless aggregate signature schemes [9,29].
-
-
In the individual-verify algorithm, the Central Hospital needs three scalar multiplications, three point addition operations in the elliptic curve, and two general hash operations to verify the DAUi’s individual signature. The computation cost of our scheme in individual verification is smaller than that of Gong et al.’s scheme [9], but slightly higher than that of Cui et al.’s scheme [29].
-
-
As shown in Figure 3, in the aggregate verify algorithm, the Central Hospital needs (2n+1) scalar multiplications, (2n + 1) point addition operations in the elliptic curve, and 2n general hash operations to verify the aggregate signature. The computation cost of our scheme in aggregate verification is smaller than Gong et al.’s scheme [9], but slightly higher than that in Cui et al.’s scheme [29].
Table 5.
The comparison of computation cost.
Figure 3.
The comparison of aggregate verification time.
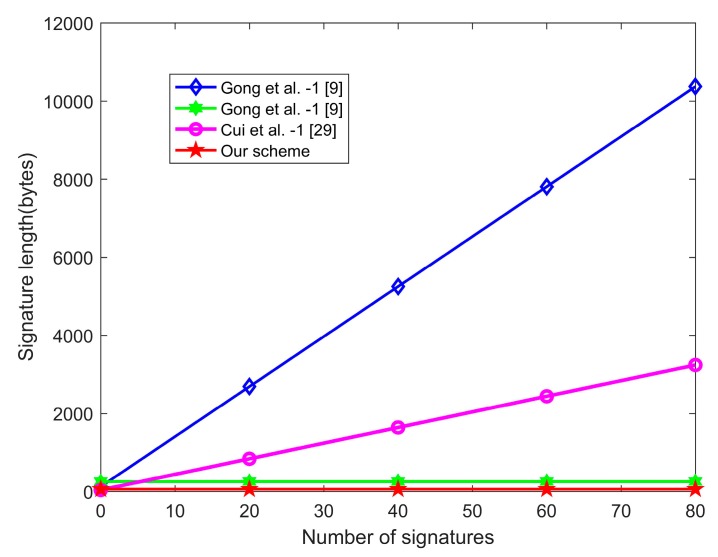
Table 6 shows the communication cost of our scheme and related certificateless aggregate signature schemes. In the proposed scheme, the aggregate signature length, such as that of CAS-2 in [9], is a constant, which does not increase with the number of individual signatures.
Table 6.
The comparison of communication cost.
From Figure 4, we can see that the communication cost of the proposed scheme is obviously smaller than that of CAS-1 [9] and Cui et al.’s scheme [29], and slightly smaller than that of CAS-2 [9].
Figure 4.
The comparison of signature length.
2. The comparison of certificateless aggregate signatures based on blockchain
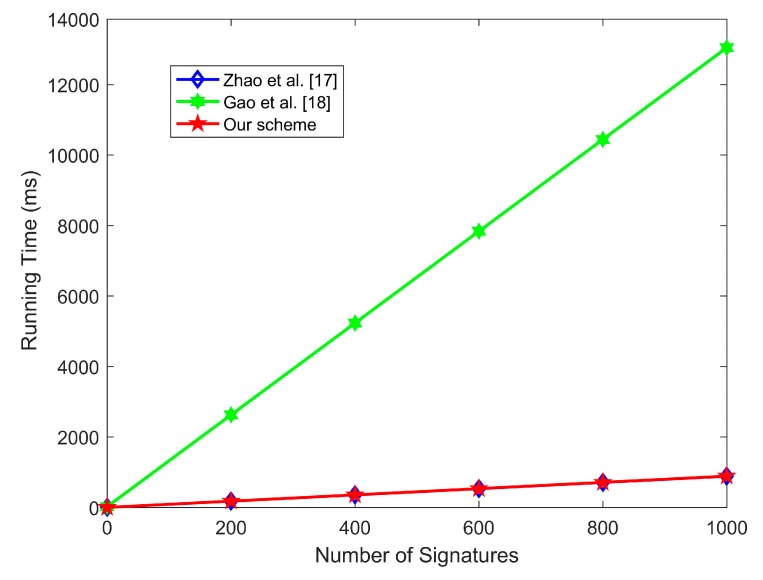
In this subsection, we compare the computation cost and communication cost of the proposed scheme with two most recently proposed certificateless aggregate signature schemes based on blockchain [17,18]. As shown in Table 7 and Figure 5, in the individual sign algorithm and aggregate verify algorithm, the computation cost of the proposed scheme is lower than that of Gao et al.’s scheme [18], but it is close to Zhao et al.’s scheme [17]. In the individual verify algorithm, the computation cost of the proposed scheme is lower than Gao et al.’s scheme [18] but slightly higher than that of Zhao et al.’s scheme [17].
Table 7.
Computation cost of schemes based on blockchain.
Figure 5.
The aggregate verification cost of schemes based on blockchain.
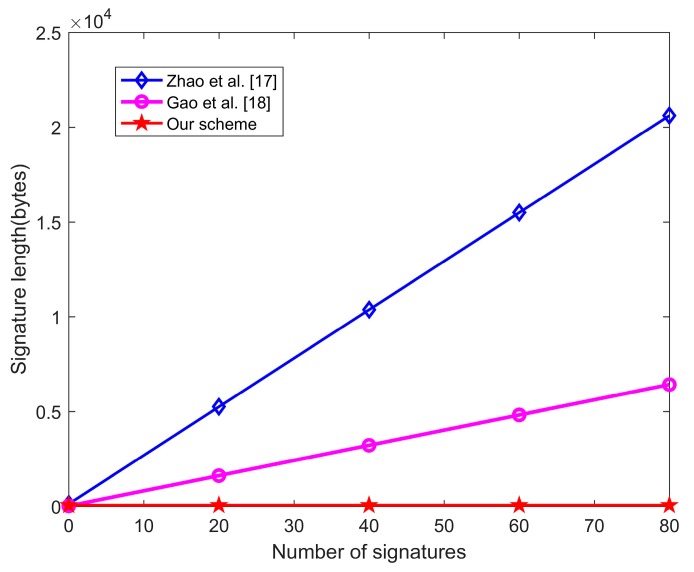
As shown in Table 8 and Figure 6, the aggregate signature length of the two most recently proposed certificateless aggregate signature schemes [17,18] based on blockchain is correlated to the individual signature number. However, the aggregate signature length of our scheme is , which is a constant and is obviously lower than the other two schemes [17,18]. That is to say, the storage capacity of the aggregate signature does not increase with the increase of the DAUi’s in each transaction, which can effectively improve the storage efficiency of each block.
Table 8.
Communication cost of schemes based on blockchain.
Figure 6.
The signature length of schemes based on blockchain.
8. Conclusions
In this paper, a certificateless aggregate signature scheme based on blockchain is proposed, which can be used for secure storage and sharing of medical data in MCPS. To improve performance, the function of trapdoor collision calculation in trapdoor hash function is included in our proposed scheme. The security analysis presents that the proposed scheme is existentially unforgeable against adaptive chosen-message attacks, which is resistant to replay attack and modification attack. The proposed scheme provides message authentication and identity privacy protection, which satisfies the security requirements of MCPS. Compared with pairing-based schemes, the scheme proposed in this paper is based on ECC with better computational efficiency, and the computational cost of our scheme is lower. More importantly, the aggregate signature length of the proposed scheme is independent of the number of signers, which can effectively increase the number of transactions stored in each block. Therefore, the proposed scheme can alleviate the capacity limitation of blockchain and prevent spam attacks to a certain extent.
In the future work, we will focus on the lattice-based digital signature algorithm and combine it with blockchain to improve the security of blockchain. More importantly, we will apply our research to practice and obtain measurement results from practical implementation.
Acknowledgments
The authors thank for the help of reviewers and editors.
Author Contributions
Conceptualization: P.Q. and L.S.; methodology: H.S.; validation: Y.H.; formal analysis: P.Q. and Y.H.; investigation: H.S. and L.S.; security analysis: D.X.; writing—original draft preparation: H.S.; writing—review and editing: D.X. and F.C.; project administration: F.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (nos. 61972438, and 61801004); the Natural Science Foundation of Anhui Province (no. 1808085QF211); the Natural Science Foundation of Universities of Anhui Province (nos. KJ2019A0702 and KJ2019A0704); Anhui Key Laboratory of Network and Information Security (no. AHNIS2020003).
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Yang Y., Zheng X.H., Guo W.Z., Liu X.M., Chang V. Privacy-preserving Smart IoT-based Healthcare Big Data Storage and Self-adaptive Access Control System. Inf. Sci. 2019;479:567–592. doi: 10.1016/j.ins.2018.02.005. [DOI] [Google Scholar]
- 2.Lee I., Sokolsky O. Medical Cyber Physical Systems; Proceedings of the CPS Demystified Session, DAC 2010; Anaheim, CA, USA. 17 June 2010; pp. 743–748. [Google Scholar]
- 3.Zhang X.J., Zhao J., Mu L.M., Tang Y., Xu C.X. Identity-based Proxy-oriented Outsourcing with Public Auditing in Cloud-based Medical Cyber–physical Systems. Pervasive Mob. Comput. 2019;56:18–28. doi: 10.1016/j.pmcj.2019.03.004. [DOI] [Google Scholar]
- 4.Yi C., Ding S., Xu Z., Zheng H.D., Yang S.L. Blockchain-based Medical Records Secure Storage and Medical Service Framework. J. Med. Syst. 2019;43:5–13. doi: 10.1007/s10916-018-1121-4. [DOI] [PubMed] [Google Scholar]
- 5.Liu A.D., Du X.H., Wang N., Li S.Z. Research Progress of Blockchain Technology and Its Application in Information Security. J. Softw. 2018;29:270–293. (In Chinese) [Google Scholar]
- 6.Tsai W., Yu L., Wang R., Liu N., Deng E. Blockchain Application Development Techniques. J. Softw. 2017;28:1474–1487. (In Chinese) [Google Scholar]
- 7.Sengupta J., Ruj S., Das Bit S. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020;149:102481–102500. doi: 10.1016/j.jnca.2019.102481. [DOI] [Google Scholar]
- 8.Xiong H., Guan Z., Chen Z., Li F. An Efficient Certificateless Aggregate Signature with Constant Pairing Computations. Inf. Sci. 2013;219:225–235. doi: 10.1016/j.ins.2012.07.004. [DOI] [Google Scholar]
- 9.Gong Z., Long Y., Hong X., Chen K. Two Certificateless Aggregate Signatures from Bilinear Maps; Proceedings of the 8th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD 2007); Qingdao, China. 30 July–1 August 2007; pp. 2093–2106. [Google Scholar]
- 10.Zhang F., Shen L., Ge W. Notes on the Security of Certificateless Aggregate Signature Schemes. Inf. Sci. 2014;287:32–37. doi: 10.1016/j.ins.2014.07.019. [DOI] [Google Scholar]
- 11.He D.B., Zeadally S., Xu B.W., Huang X.Y. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensic Secur. 2015;10:2681–2691. doi: 10.1109/TIFS.2015.2473820. [DOI] [Google Scholar]
- 12.Suciu G., Nădrag C., Istrate C., Vulpe A., Ditu M.C., Subea O. Comparative Analysis of Distributed Ledger Technologies; Proceedings of the 6th Global Wireless Summit (GWS 2018); Chiang Rai, Thailand. 25–28 November 2018; pp. 370–373. [Google Scholar]
- 13.Fan K., Wang S., Ren Y.H., Li H., Yang Y.T. Medblock: Efficient and Secure Medical Data Sharing via Blockchain. J. Med Syst. 2018;42:136–147. doi: 10.1007/s10916-018-0993-7. [DOI] [PubMed] [Google Scholar]
- 14.Xue T.F., Fu Q.C., Wang C., Wang X.Y. A Medical Data Sharing Model via Blockchain. Acta Autom. Sin. 2017;43:1555–1562. (In Chinese) [Google Scholar]
- 15.Xia Q., Sifah E.B., Asamoah K.O., Gao J.B., Du X.J., Guizani M. MeDShare: Trust-less Medical Data Sharing among Cloud Service Providers via Blockchain. IEEE Access. 2017;5:14757–14767. doi: 10.1109/ACCESS.2017.2730843. [DOI] [Google Scholar]
- 16.Aitzhan N.Z., Svetinovic D. Security and Privacy in Decentralized Energy Trading through Multi-signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2016;15:840–852. doi: 10.1109/TDSC.2016.2616861. [DOI] [Google Scholar]
- 17.Zhao Y. Aggregation of Gamma-Signatures and Applications to Bitcoin. [(accessed on 7 January 2020)];IACR Cryptol. ePrint Arch. 2018 2018:414. Available online: https://eprint.iacr.org/eprint-bin/getfile.pl?entry=2018/414&version=20180510:203542&file=414.pdf. [Google Scholar]
- 18.Gao Y., WU J.X. Efficient Multi-party Fair Contract Signing Protocol based on Blockchains. J. Cryptologic Res. 2018;5:556–567. [Google Scholar]
- 19.Liu Y., Li R., Liu X., Wang J., Tang C., Kang H. Enhancing Anonymity of Bitcoin Based on Ring Signature Algorithm; Proceedings of the 13th International Conference on Computational Intelligence and Security (CIS 2017); HongKong, China. 15–18 December 2017; pp. 317–321. [Google Scholar]
- 20.Lin Q., Yan H., Huang Z., Chen W., Shen J., Tang Y. An ID-based Linearly Homomorphic Signature Scheme and Its Application in Blockchain. IEEE Access. 2018;6:20632–20640. doi: 10.1109/ACCESS.2018.2809426. [DOI] [Google Scholar]
- 21.Gao Y.L., Chen X.B., Chen Y.L., Sun Y., Niu X.X., Yang Y.X. A Secure Cryptocurrency Scheme Based on Post-quantum Blockchain. IEEE Access. 2018;6:27205–27213. doi: 10.1109/ACCESS.2018.2827203. [DOI] [Google Scholar]
- 22.Shamir A. Identity-based Cryptosystems and Signature Schemes; Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques; Paris, France. 9–11 April 1984; pp. 47–53. [Google Scholar]
- 23.Kumar P., Sharma V., Sharma G. Certificateless Aggregate Signature Schemes: A Review; Proceedings of the 2016 International Conference on Computing, Communication and Automation (ICCCA); Greater Noida, India. 29–30 April 2016; pp. 531–536. [Google Scholar]
- 24.Al-Riyami S.S., Paterson K.G. Certificateless Public Key Cryptography; Proceedings of the Advances in Cryptology—ASIACRYPT 2003, 9th International Conference on the Theory and Application of Cryptology and Information Security; Taipei, Taiwan. 30 November–4 December 2003. [Google Scholar]
- 25.Zhang Z.F., Wong D.S., Xu J., Feng D. Certificateless Public-key Signature: Security Model and Efficient Construction; Proceedings of the International Conference on Applied Cryptography and Network Security; Singapore. 6–9 June 2006; pp. 293–308. [Google Scholar]
- 26.Boneh D., Gentry C., Lynn B., Shacham H. Aggregate and Verifiably Encrypted Signatures from Bilinear Maps; Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2003); Warsaw, Poland. 4–8 May 2003; pp. 416–432. [Google Scholar]
- 27.He D.B., Tian M., Chen J. Insecurity of an Efficient Certificateless Aggregate Signature with Constant Pairing Computations. Inf. Sci. 2014;268:458–462. doi: 10.1016/j.ins.2013.09.032. [DOI] [Google Scholar]
- 28.Zhou Y.W., Yang B., Zhang W.Z. Efficient and Provide Security Certificateless Aggregate Signature Scheme. J. Softw. 2015;26:3204–3214. (In Chinese) [Google Scholar]
- 29.Cui J., Zhang J., Zhong H., Shi R.H., Xu Y. An Efficient Certificateless Aggregate Signature without Pairings for Vehicular Ad Hoc Networks. Inf. Sci. 2018;451:1–15. doi: 10.1016/j.ins.2018.03.060. [DOI] [Google Scholar]
- 30.Wang Z.Y., Liu J.W., Zhang Z.Y., Yu H. Fully Anonymous Blockchain based on Aggregate Signature and Confidential Transaction. J. Comput. Res. Dev. 2018;55:2185–2198. (In Chinese) [Google Scholar]
- 31.Yao A.C.-C., Zhao Y.L. Online/offline Signatures for Low-power Devices. IEEE Trans. Inf. Forensic Secur. 2012;8:283–294. doi: 10.1109/TIFS.2012.2232653. [DOI] [Google Scholar]
- 32.Danzi P., Kalør A.E., Stefanović Č., Popovski P. Repeat-Authenticate Scheme for Multicasting of Blockchain Information in IoT Systems. arXiv. 20191904.07069 [Google Scholar]
- 33.Kaga Y., Fujio M., Naganuma K., Takahashi K., Murakami T., Ohki T., Nishigaki M. A Secure and Practical Signature Scheme for Blockchain Based on Biometrics; Proceedings of the Information Security Practice and Experience (ISPEC 2017); Melbourne, VIC, Australia. 13–15 December 2017; pp. 877–891. [Google Scholar]
- 34.Johnson D., Menezes A., Vanstone S. The Elliptic Curve Digital Signature Algorithm (ECDSA) Int. J. Inf. Secur. 2001;1:36–63. doi: 10.1007/s102070100002. [DOI] [Google Scholar]
- 35.Krawczyk H.M., Rabin T.D. Chameleon Signatures; Proceedings of the Network and Distributed System Security Symposium (NDSS 2000); San Diego, CA, USA. 2–4 February 2000; pp. 143–154. [Google Scholar]
- 36.Shamir A., Tauman Y. Improved Online/Offline Signature Schemes; Proceedings of the 21th Annual International Cryptology Conference (CRYPTO 2001); Santa Barbara, CA, USA. 19–23 August 2001; pp. 355–367. [Google Scholar]
- 37.Shu H., Chen F.L., Xie D., Sun L.P., Qi P., Huang Y.Q. An Aggregate Signature Scheme Based on a Trapdoor Hash Function for the Internet of Things. Sensors. 2019;19:4239. doi: 10.3390/s19194239. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 38.Chandrasekhar S., Singhal M. Efficient and Scalable Aggregate Signcryption Scheme based on Multi-trapdoor Hash Functions; Proceedings of the 1st Workshop on Security and Privacy in the Cloud; Florence, Italy. 28–30 September 2015; pp. 610–618. [Google Scholar]
- 39.Chandrasekhar S., Ibrahim A., Singhal M. A Novel Access Control Protocol Using Proxy Signatures for Cloud-based Health Information Exchange. Comput. Secur. 2017;67:73–88. doi: 10.1016/j.cose.2017.02.008. [DOI] [Google Scholar]
- 40.Cheng L., Wen Q.Y., Jin Z.P., Zhang H., Zhou L.M. Cryptanalysis and Improvement of a Certificateless Aggregate Signature Scheme. Inf. Sci. 2015;295:337–346. doi: 10.1016/j.ins.2014.09.065. [DOI] [Google Scholar]
- 41.Maji H.K., Prabhakaran M., Rosulek M. Attribute-based Signatures; Proceedings of Cryptographers’ Track at the RSA conference; San Francisco, CA, USA. 14–18 February 2011; pp. 376–392. [Google Scholar]
- 42.Health informatics-Pseudonymization, ISO 25237. [(accessed on 7 January 2020)];2017 Available online: https://www.iso.org/standard/63553.html.