Highlights
-
•
The research investigates the role of trust and privacy concerns by augmenting Technology Acceptance Model (TAM).
-
•
Structural equation model is employed to model the effects and influences and survey data from healthcare recipients in New, Delhi, India is utilized.
-
•
The research provides an empirical contribution to the literature on effect of trust and privacy concerns on acceptance of technology in healthcare.
Keywords: Public health, Trust, Technology, Privacy concern, Technology acceptance, TAM
Abstract
This paper augments the technology acceptance model (TAM) by empirically investigating the influence of behavioral traits (privacy concerns and trust) and cognitive beliefs (perceived usefulness and perceived ease of use) on patients’ behavioral intention to accept technology in healthcare service delivery. Despite increased emphasis on healthcare service delivery, there has been limited studies as to how various behavioral constructs are related to adoption of new technology in healthcare sector. To this end, and to develop meaningful insights, a conceptual model integrating behavioral constructs with constructs related to technology acceptance model is devised. The aim here is essentially to understand relationships that predict patients’ acceptance of technology in healthcare services. The devised model is tested on responses obtained from survey of 416 patients availing healthcare service at various primary health centers in New Delhi, India. Structural equation modeling (SEM) is employed to conceptualize the model and validate nine hypotheses entailing key constructs. The results indicate that perceived usefulness, perceived ease of use, trust and privacy concern are direct predictors of patients’ behavior to accept technology in availing healthcare services. In summary, this research provides an empirical contribution to the literature on effect of trust and privacy concerns on acceptance of technology in healthcare.
1. Introduction
In the declaration of Alma Ata in 1978, governments across the globe pledged for health for all by the year 2000, emphasizing improved access to primary health facilities and services by setting country specific healthcare targets. However, the targets were missed and considerable gaps in delivering and accessing healthcare services remain, particularly in developing countries (World Health Statics 2010). Great disparities in terms of measured health inequalities prominently and visibly persist across the developing countries [118]. Poor in developing countries continue to have minimal access to health services, resulting in deterioration of health and thus, further aggravating poverty [110]; [93]. In order to access healthcare services, adoption of technology by patients has often been considered a key enabler for mitigating widespread disparities and poor accessibility [60]. In this backdrop, acceptance and utilization of technology in healthcare service delivery are crucial for both service providers and service consumers (patients).
To address the question of adoption of new technology by the consumers, various models and theories have been developed in the past. Some of the widely explored theories are Theory of Reasoned Action (TRA) [39], Theory of Planned Behaviour (TPB) [4], Technology Acceptance Model (TAM) [28]; [29], Innovation Diffusion Theory (IDT) [101], Unified Theory of Acceptance and Use of Technology (UTAUT) [117], Technology Readiness Index (TRI) [88]; [87]. Among these theories, TAM is perhaps one of the widely explored models by information science (IS) researchers [52]; [116]. It establishes parsimonious relationships amongst ease of use, usefulness, and intention to use. TAM posits that usefulness and ease of use are the major determinants of the end-user’s intention to use information technology (IT) [28]; [29].
Numerous studies have explored impact of technology (Mainly IT) on several aspects, such as quality, efficiency, and cost of healthcare services [20]. However, researchers have kept their focus primarily on design and implementation from the service provider’s perspective. Extant research literature is relatively limited in providing the understanding of the ways in which patients perceive technology usage and how technology is related to behavioral aspects [48]. Healthcare being expensive, complex and universally used service, is also one of the most personalized services. [13]. Building and maintaining trust and ensuring privacy are essential for continued participation of patients in a healthcare delivery system [72]. Patients are often concerned about possible unwanted economic and social consequences resulting from misuse (or even abuse) of their health-related information [69]. Few studies have augmented original TAM model to include the behavioural constructs particularly in context of healthcare delivery [100]. Studies have also focussed on qualitative exploration of challenges associated with technology adoption without taking pertinent quantitative analysis into account [85]. However, a detailed empirical study aimed at examination of nuances pertaining to technology adoption by patients in relation to privacy and trust in healthcare, particularly from a patient centric viewpoint (as opposed to service provider centric perspective) is a key contribution of our research. To this end, this empirical study focuses on patients receiving treatment in primary health centers (PHCs) in New Delhi, India is aimed at answering the following research questions:
RQ1. From a patient centric perspective, what is the impact of trust on acceptance of new technology in healthcare service delivery?
RQ2. From a patient centric perspective, what is the impact of privacy concerns on acceptance of new technology in healthcare service delivery?
In order to answer these questions, based on a comprehensive review of extant literature, we propose extending TAM by integrating two latent behavioural variables, i.e., trust and privacy concern. This study puts forward a model apt for healthcare services in order to identify relationships between relevant factors affecting intention to use technology by patients. Structural equation model (SEM) is employed to analyse the structural relationships using survey based responses obtained from 416 respondents belonging to the age group of 18 to 60 years, availing healthcare service at primary health centers in New Delhi, India.
We contribute to the extant research literature in three ways. First, we focus on acceptance of technology in healthcare from a patient centric perspective. Second, we extend the TAM framework with behavioural dimensions, aiming to explicate how these factors influence patients’ perceived ease of use, perceived usefulness, and behavioural intention to use healthcare services. Third, this study reaffirms theoretical foundation of TAM in healthcare setup.
Rest of the paper is structured as follows. Section 2 gives details of the relevant literature related to TAM and broad domain of healthcare. Section 3 illustrates research model and associated hypotheses. Methodology is explained in section 4. Data analysis and results are presented in Section 5. Section 6 discusses the analysis and research implications associated with the study. Limitation and future research directions associated with the study are presented in Section 7. Finally, concluding remarks are presented in Section 8.
2. Literature review
The research gaps that we seek to address in this research are related to three key research streams namely, (a) IT in healthcare and its adoption, (b) TAM, and (c) privacy concerns and trust. Now we present the relevant and recent literature for each of these three streams.
2.1. IT in healthcare and its adoption
Information technology has transformed ways in which health information are obtained and utilized. Based on respective health technology assessments, countries prioritize healthcare delivery in order to create sustainable health systems [68]. Exclusively designed technologies for healthcare services have contributed to the digital health phenomenon [70]. Researchers have studied impact of information technology on quality, efficiency and cost of healthcare services [20]. Most of the studies show positive effect of IT on healthcare services with some studies reporting mixed findings [17]. For example, positive outcomes such as reduced healthcare costs for both service providers and consumers were reported by [65] and increased service satisfaction by Queenan et al., (2011). [31] surveyed hospitals in US and substantiated using Theory of Swift Even flow (TSEF), the finding that adoption of IT results in improved revenue. [96] reported reduced costs associated with management of healthcare due to centralization of healthcare service using IT. [59] reported reduced flexibility as an undesired outcome of technology adoption in healthcare service delivery. [108] suggested complementarities between clinical health information technologies (primarily used for patient data collection, diagnosis and treatment) and augmented clinical health information technology (used for integrating information for augmented decision making) with respect to process quality. [44] identified crucial features of medical sensor networks and introduced relevant node behaviors, including transmission rate and leaving time, etc., within the trust evaluation framework of healthcare delivery.
Emerging technologies such as big data, cloud computing, block chain and health sensing are revolutionizing healthcare operations and delivery [128], [119] and [40]. [120] enumerated a number of capabilities of big data analytics in healthcare sector, particularly for decision support capability, analytical capability for pattern of care, predictive capability, unstructured data analysis capability and traceability. [131] proposed application of big data analytics for raising adoption of digitized health records. Cloud computing as an enabler for cost effective solution for patient information, sensor-based health data collection and delivery has been proposed in many studies [14]; [90]; [102].
Available literature on adoption of technology in healthcare can be broadly categorized in two streams. First, studies concerned with extent of IT related adoption in healthcare by analyzing pervasiveness, scope and scale. Second, studies examining enablers and barriers in adoption of IT [1]. Studies belonging to first stream have explored various characteristics of healthcare service providers, such as size, location, competition, ownership status, etc., that have adopted IT [24]; [54]; [57]; [74]. Major barriers in adoption of IT as enumerated by second stream of studies include financial, functional, environmental and individuals including service providers and service users (Bhattacharjee et al., 2006; [30]; [54]; [115]. One key challenge with adoption of IT in healthcare is that the systems are typically not designed for multi-institutional lifetime records. Ethically managing health data, guarantee of security, auditability of records, and interoperability and immutability are few concerns that need to be addressed [38]. [99] in their study of emerging technologies for healthcare delivery advocated for IoT (Internet of things) and AI (artificial intelligence) oriented healthcare delivery system. Further, this study conceptualized the tenets of H-IoT (healthcare internet of things). The arguments for adoption of H-IoT was also supported by [98]. [79] in their surveyed stakeholders belonging to 12 different healthcare organizations developed a trust-based approach to figure out malicious devices in a healthcare environment. Yan et al., (2015) proposed trust based framework for virtualized networks and software-defined networking. The study in particular argued for adoption of cloud computing to securely deploy various trustworthy security services over the virtualized networks. [3] explored the recent advances in big data analytics for IoT systems as well as the key requirements for managing big data and for enabling analytics in an IoT environment. [67] presented a blockchain-based system for secure mutual authentication to enforce fine-grained access control polices. Yan et al., (2016a, 2016b) proposed two trust evaluation algorithms to support different application cases. Specifically, these algorithms can overcome attacks raised by internal malicious evidence providers. [92] argued for adoption of FOG (edge) computing based approach for solving analytical and computational problems for diverse problems including those related to medical industry and smart cities. [121] devised a novel authentication framework for medicine anticounterfeiting system considering the IOT environment aimed at ascertaining the authenticity of pharmaceutical products. The key benefit of the proposed scheme was in terms of its lower communication and computation cost over other similar authentication schemes. [122] proposed a new secure remote user authentication scheme for implantable medical devices communication environment to overcome security and privacy issues associated with existing schemes.
2.2. Technology Acceptance Model (TAM)
There has been effective evolution and acceptance of technology globally since second half of 20th century. This has resulted in improvements in social lives, interpersonal relationships and even self-expression (Gucin and Berk, 2015). TAM, as a research stream, is a widely deployed model for accessing acceptance of technology in information systems because of its simplicity and understandability [58]. Its proponents articulated that the key to enhancing use was to first increase acceptance of IT, which could be assessed by measuring individuals’ future intentions to use [28]; [29]; [27]. The model is based on the theory of reasoned action (TRA) [39], a psychological approach that illustrates how individual’s belief system mediates human behavior. TRA theorizes that behavioral intention (BI) of an individual to use a product or a system is decided by the individual's attitude and subjective norms related to the behavior. TRA assumes behavioral intention to be closely linked to actual behavior. In comparison to TRA that explains many divergent human tendencies, TAM focuses on a particular kind of behavior, i.e., the rational acceptance of technology by the technology user [29]. TAM involves two primary concepts namely perceived ease of use (PEOU) and perceived usefulness (PU) to influence dependent variable behavioral intentions (BI) [58]. PU and PEOU are defined in the following way:
Perceived Usefulness (PU)- “the degree to which a person believes that using a particular system would enhance his or her job performance” [29], p. 320).
Perceived Ease of Use (PEOU) - “the degree to which a person believes that using a particular system would be free of effort” [29], p. 320).
TAM has been studied in different contexts with different technologies (e-mail, world wide web, hospital information systems, etc.). It has been applied with different control factors such as organizational size, type, gender, etc., on different subjects such as undergraduate students, MBAs, and knowledge workers resulting in establishment of robustness among its proponents. TAM has received enormous empirical support in elucidation and prediction of technology acceptance and use in various settings [26]; [25], and [127]). Divergent external factors such as training, compatibility, anxiety, computing support, experience, relevance, personal innovativeness, etc., have been studied in context of TAM [63]. TAM has also been applied to study various aspects in healthcare services. Online disability evaluation systems, personal digital assistant for healthcare, telemedicine technology, electronic health records (EHR) and mobile applications are few of them. Adoption of e-health monitoring using smart wearable healthcare devices has been one of the recent contributions to extant research literature [64]; [86]; [123]; [132]. [100] employing a systematic literature review approach identified three ICT application areas namely, telemedicine, electronic health records, and mobile application for TAM in healthcare service delivery. The literature review also reported of a few studies wherein mediating role of behavioural aspects in conjunction with other factors such as mobile health, etc., were investigated.
2.3. Privacy concern and Trust
With ever increasing competition and growing personalization of markets, service providers are increasingly focusing on understanding the consumers (patients) better, thus leading to proliferation of consumer information. Although, most consumers welcome the increased convenience and personalization as natural outcomes, many remain concerned about privacy associated with their personal information [61]. Privacy concern has been typically defined as concern for loss of privacy and need for protection against uncalled-for communication and misuse of personal information [109]. It concerns with being in control of personal information exchanges and security, and whether the beholder of the information will use it appropriately [61]. [124] suggested that privacy concern is the result of individual’s outlook to privacy and circumstantial cues that enable him/her to assess the outcome of information disclosure. [34] argued that perception of privacy develops socially through transactions with social entities. Cognitive processes of identifying information boundary comprising of privacy risk, privacy intrusion and privacy control is vital for structuring the privacy concerns of an individual. The demographic factors such as age, gender, income status affect privacy concerns of consumers [23]. Individuals are found more concerned about their privacy when information is used without their knowledge or permission or when intended use of the information is not revealed [95]. These attributions have also been concluded and validated empirically in various models [95], [21]; [35]. For some, protection of patients’ information is part of core professional ethics and for others, it is simply occupational work in the interest of organization [8].
Research on addressing privacy concerns of consumers has grown considerably in the recent past and shifted from general contexts to specific ones [129]. Researchers have explored privacy concerns in diverse fields like social networking [46]; [53]; [62], online services [34], [55], healthcare [11]; [126], location-based services [125]; [134]. Studies have explored a large number of antecedents of privacy concerns. [66] categorized these antecedents into five groups on the basis of their level of study. These are individual factors, socio-relational factors, macro-environmental factors, organizational and task environment factors, and information contingencies. Studies have conceptualized various instruments and models for privacy concerns in different contexts. For example, the Concern for Information Privacy (CFIP) [109] conceptualizes organizational privacy practices. Internet Users Information Privacy Concerns (IUIPC) [71] operationalizes multidimensional notion of internet users’ privacy. However, for our study in healthcare services, we use model suggested by [124]. This model explains molding of individual’s privacy concern towards specific practices through a cognitive process comprising of privacy control, privacy intrusion and perceived privacy risk. Drawing on information boundary theory, this integrative model implies that the individual’s disposition to situational or privacy indications thus enabling them to assess consequences of their information disclosures shape the privacy concern of the individual.
Trust, on the other hand, has received a great deal of attention in sociology, social psychology, economics and as well as in marketing field. It is an elusive multiplex concept [19] and a multi-dimensional construct with two inter-related components, i.e., trusting beliefs and trusting intentions [78]. [103] defined trust as “a psychological state comprising of the intention to accept vulnerability based upon positive expectations of the intentions or behavior of another under conditions of risk and interdependence”. Trust is essentially needed in uncertain situations, since it eventually implies accompanying risks and becoming susceptible to trusted parties [50]. It has been identified as a catalyst of transactions providing service receivers with expectations of fruitful exchange relationship with service providers. Drawing on various literatures, [36] defined trust as perceived credibility and benevolence of a target trust. Here credibility refers to the extent to which the receiver believes that the service provider has the required expertise to perform the job effectively and reliably. Whereas, benevolence refers to extent to which the receiver believes that the service provider has the intentions and motives beneficial for the receiver in unforeseen conditions for which commitment is not made (Ganeshan, 1994). [105] contended that all three factors related to integrity, ability, and benevolence could affect trust in a group or organization.
Consumers’ loyalty, long term relationships, commitment and product acceptance are underpinned by their trust in service providers [16]. Trust plays a crucial role in virtually all shared economy interactions (Hwlitschek et al., 2018). In online domain, it often functions as the sole foundation for the consumers to take purchase decisions in case of scarce information [15]. [41] called for re-examination of dimensionality of trust in context of online environments. They argued that besides existing methods like case studies, field interviews, surveys, econometric analysis, experiments, analytical modeling etc., for examining trust, other techniques like cognitive neuroscience too can be deployed for better understanding of nature, antecedents and consequences. [111] reasoned that survey-based approaches postulate valuable insights about the interrelations of diverse trust concepts in IS literature. These are frequently applied to distinguish between targets of trust that determine IS use.
In order to study technology acceptance in healthcare with respect to trust, we need to appreciate distinctions of healthcare services from other services. People commonly demand healthcare services under distress in that either they are sick or at risk thus relinquishing privacy. There is risk of loss of privacy associated with providing personal information [23]. If the service provider cannot be trusted, there is no reason why consumers should expect to gain from using the particular service [91]. Number of public opinion polls establish that individuals are quite concerned about threats to their personal information [124]. However, partial mediation of trust and privacy concern reduce the perception of risk [6]. Once consumers trust the service provider, the service provider seeks more health-related information [81]. [11] established that personal disposition indirectly impacts trust through information sensitivity and privacy concern. [97] found that expectations of benefits and positive views of health information sharing are associated with system trust. Steininger et al., (2015) in their study pertaining to acceptance of electronic health record (EHR) demonstrated that privacy concerns impact perceived usefulness of EHRs negatively. [44] identified the security challenges facing a sensor network for wireless medical monitoring and suggested that the network should follow a two-tier architecture. Based on such an architecture, the study also devised an attack-resistant and lightweight trust management scheme termed as ReTrust. [133] described the goals and tactics, and presented a distributed architecture of m-healthcare social network
A critical review of extant literature reveals crucial research gaps that we seek to address in this research. Majority of studies exploring influence of information technology in healthcare are limited to analysing impact on quality, cost effectiveness and efficiency of the service. Likewise, researchers have extensively explored behavioural constructs namely, trust and privacy concern, their enablers and their influence on technology acceptance independently in online transactions and e-commerce applications. However, studies on effect of behavioural aspects of patients on acceptance of IT in healthcare are lacking. Because of various distinct characteristics of healthcare service, it would be fruitless to apply canonical approaches for assessing users’ response by espousing inferences from studies carried out in other service setups.
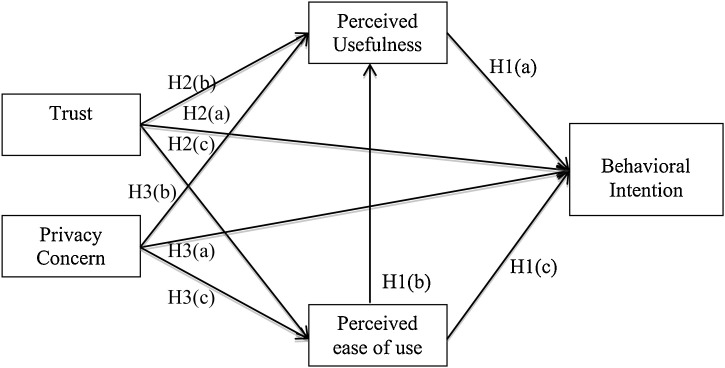
3. Research model and hypotheses development
In this section, we present research model that encompasses elements affecting behavioral intentions of healthcare service users to adopt technology. Researchers have widely explored IT in healthcare from the perspective of associated merits and limitations within the sector. Extant studies, primarily, have focused on enablers and barriers in implementation of IT in healthcare sector from service provider’s perspective [1]; [32]; [75]. We find limited studies on adoption of technology concerning patients’ perspectives. In this study, we extend TAM from patient centric perspective by incorporating variables such as patients’ cognitive belief, trust and privacy concerns in addition to TAM variables. To this end, following hypotheses are conceptualized.
3.1. Perceived usefulness and Perceived ease of use
Perceived usefulness is the degree to which the consumer perceives a service useful, while perceived ease of use is the consumers’ perception about effortless use of the service system [29]. Consumers evaluate usefulness of a service based on what they get and what they pay for it. Similar to other services, within healthcare services as well, the patient strives for timely and right treatment without much burden on his/her resources. If the patient perceives that any technology can help in getting effective treatment, the patient is more likely to avail the service facilitated by that technology. Similarly, given major parameters remaining same, if patients are provided with option to get themselves treated at any place without physically carrying their case history and using technology as facilitator, they would most likely gravitate towards accepting the technology. Further, ease of use is vital for acceptance, as familiarity with technology and skills to use technology are likely to vary significantly within the diverse population. There is extensive literature that has established that perceived usefulness and perceived ease of use directly and positively influence behavioral intention to use. Perceived ease of use also influences indirectly through perceived usefulness [26]; [25]; [29]; [114]; [116]. Therefore, in line with these arguments and extant literature, we hypothesize the following.
H1(a)
Perceived usefulness (PU) is positively correlated with Behavioral Intention (BI) to use technology in healthcare.
H1(b)
Perceived ease of use (PEOU) is positively correlated with Perceived usefulness (PU) in adoption of technology in healthcare.
H1(c)
Perceived ease of use (PEOU) is positively correlated with Behavioral Intention (BI) to use technology in healthcare.
3.2. Trust and technology acceptance in healthcare
In e-commerce and IS literature, trust has been widely acknowledged in influencing user behavior in adoption of technologies [5]; [43]; [91]. Healthcare delivery, however, is more personalized and vital service for consumers [13]. The patient has to give access to personal information and previous health records to the service providers. Extant studies have established an array of divergent aspects in delivery and patients’ ability to evaluate healthcare services [77]. Healthcare is one such typical service, wherein efficacy of primary service availed (treatment) cannot be evaluated or verified even after consumption of service. Hence, the consumer has to solely rely on the diagnosis made by the service provider. Handing over personal details to the service provider is predicated upon trust, a vital factor in acceptance of technology in healthcare services. Trust is one of the defining factors in such exchanges, where uncertainty is present. Practically, trust is a prerequisite for interactions conducted in uncertain environment [9]. In such situations, beliefs about the service provider (apart from usefulness and ease of use) also becomes crucial. If the service providers fail to convey trustworthiness, the consumer is not likely to engage in transaction [47]. Similarly, in case of healthcare, if the patient trusts the healthcare provider to fulfill his or her needs, then the patient is more likely to view technology as beneficial for him or her [60]. Ensuring trust, by creating positive attitude towards service provider, is likely to ameliorate consumers’ fear of the service provider’s opportunism. In line with the existing literature, we have incorporated trust with TAM, hypothesizing the following:
H2(a)
Trust (T) is positively associated with Behavioral intention (BI) to use technology in healthcare.
Studies have supported trust as a vital construct for predicting acceptance of technology [18]; [42]; [89]; [91]. Studies have theoretically and empirically supported integration of trust with TAM constructs. If service provider cannot be trusted by the consumer, the consumer is not likely to see any usefulness in the service provided. At the same time, trust on service provider will reduce efforts needed to verify, monitor and control the service interaction. On the other hand, if trust is low, consumer would be forced to devote more time and effort to gauge the service thus to avoid any opportunism on part of the service provider. Therefore, in line with the existing literature, we hypothesize the following hypotheses.
H2(b):Trust (T) is positively associated with Perceived usefulness (PU) to use technology in healthcare.
H2(c)
Trust (T) is positively associated with Perceived ease of use (PEOU) of use of technology in healthcare.
3.3. Privacy concerns and technology acceptance in healthcare
Researchers have studied privacy extensively. Privacy concern (PCON) has been one of the most widely used variable amongst privacy related constructs in IS research. It has been one of the strongest predictors of the privacy related behavior [35]; [71]; [112]. Capturing nuances related to privacy have gained significance, as IT is increasingly expanding capabilities to store, process, explore and exploit personal information [34]. Despite growing research interest in privacy concerns, there are lack of empirical evidences as to how privacy concerns affect acceptance of technology in healthcare.
Privacy concern (a part of our proposed model) is considered a direct determinant of BI. The rationale is extracted out of the existing studies carried out in different domains. Existing literature suggests that privacy concerns make users circumspect about using technology and sharing personal information. In sensitive areas, privacy concern of health information may even cause individuals to avoid obtaining certain healthcare services. If privacy concerns of the customer are not mitigated by the service provider, it will have significant negative effect on the consumer’s attitude and behavior towards the service [82]; [94]. In an empirical study on internet uses, [34] also found out negative impact of privacy concern on intention to use. Privacy of the personal information is the focal concern of the individual [112]. [83] identified that security to privacy along with shared values positively influences behavioral intentions of the customers. This study follows the perception that privacy concerns measure the patient’s assessment of lack of reliance on the service provider, especially when one has to share personal details. Therefore, in line with the above presented arguments, we hypothesize the following.
H3(a)
Privacy Concern (PCON) is negatively associated with Behavioral intention (BI) to use technology in healthcare.
Though various researchers have explored privacy in different contexts and environments, we found a few literatures on the effect of privacy concern on PU and PEOU. [6] asserted that higher privacy concerns negatively mediate the relationship between perceived risk and attitude of the user. Intuitively, we can argue that patients will not find usefulness in a technology that is likely to invade their privacy. Individuals are likely to put more effort into monitoring if they feel that their privacy is at stake while using any service. Therefore, concern for the privacy of the user will reduce the ease of use and will affect his/her perceived usefulness for any service negatively. Along these arguments, we hypothesize the following.
H3(b)
Privacy Concern (PCON) is negatively associated with Perceived usefulness (PU) to use technology in healthcare.
H3(c)
Privacy Concern (PCON) is negatively associated with Perceived ease of use (PEOU) of use of technology in healthcare.
Based on our developed hypotheses, the proposed conceptual model comprising of the related constructs is presented in Fig. 1 .
Fig. 1.
Proposed conceptual model.
4. Methodology
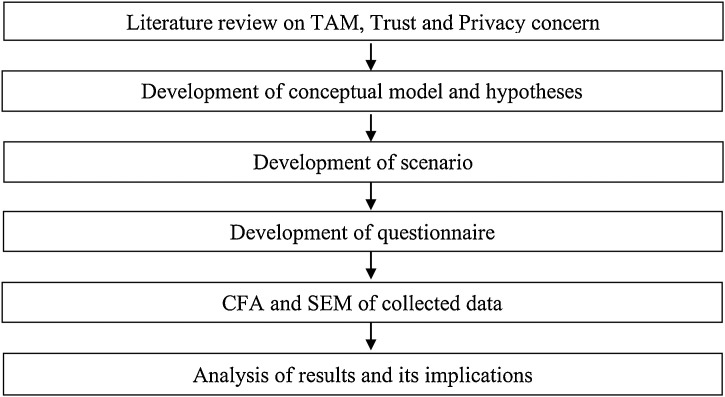
To test our model, we have adopted survey-based strategy consisting of structured self-administered questionnaire. We considered five latent constructs and twenty-three manifest variables to measure them. Methodology of research is summarized in Fig. 2 . Data for testing hypotheses has been collected using scenario and questionnaire-based approach. The respondents were given a scenario (presented in Appendix 1) before responding to the questionnaire. This approach is adopted as healthcare services linked to unique identity that does not yet exist in targeted area. However, validity of the response of individual based on a scenario has been well documented by [12]. To make the scenario as realistic as possible, it was discussed with the patients in primary health centers. Based on the inputs received, scenario was modified to make it more understandable to the patients.
Fig. 2.
Methodology of Research.
4.1. Prelude to scenario and questionnaire
Presently available electronic healthcare record systems are not designed to manage multi- institutional, multi-format lifetime health records of patients. Patients leave their health data scattered across various health service providers wherein they have availed treatment. These healthcare providers work in silos and hardly any inter-organizational data transfer takes place. Whenever a patient visits any healthcare provider, either the patient carries the related previous records (in the form of case history) obtained from previous healthcare providers, or the case is registered as a fresh case. In such redundant process, lots of scarce resources that could have been provided to a new patient, are used on the same patients repetitively. To facilitate availability of medical records, we propose that healthcare records to be linked to unique identity (Aadhaar –unique identification number for the citizen of India) of the patient. These records can be accessed at any health center by patients providing authentication of their unique identity. Aadhaar, a 12-digit unique number allotted to the citizen of India, stores demographic, biometric and financial information of the individual. Aadhaar number can be used as an identity and has been made mandatory for availing benefits of many governmental social schemes. As Aadhaar number is linked to personal and financial information, sharing Aadhaar identification can raise apprehensions about safety and security of data in the mind of individual. Scenario for collection of data has been developed highlighting concern of sharing Aadhaar identification with healthcare provider (see Appendix 1).
4.2. Measurement
As argued by [85], we designed our questionnaire on a five point Likert scale with 1 being “strongly disagree” to 5 being “strongly agree” to collect data on demographic profile of respondents and twenty-three manifest variables. All items were adopted from published sources to ensure psychometric properties (internal consistency, test-retest reliability, factor structure etc.). These measures were adjusted in consonance with healthcare environment. Experts in the field of operation management examined the questionnaire for its clarity, terminology, logical consistency and contextual relevance. Constructs, observed variables, questions and their sources are presented in Table 1 . Questionnaire was prepared in English and Hindi (local language). A pilot study was carried out on 25 respondents, who had visited Delhi Government’s dispensaries in the recent past. Respondents were asked to give comments on wording and relevance of the questionnaire items, length of survey, difficulty, if any, in answering and time taken to complete it. Based on qualitative assessment of their comments, language of the questions was simplified to make them more understandable and eliminate any ambiguity.
Table 1.
Operationalization of Constructs.
| Constructs | Observed Variables | Questions (Response 1-strongly disagree to 5-strongly agree) | Sources |
|---|---|---|---|
| Primary Concern (PCON) | PCON1 | It bothers me when health providers ask me this much personal information. | [124] |
| PCON2 | I am concerned that health centres will be collecting too much of personal information. | ||
| PCON3 | I am concerned that unauthorized people may access my personal information. | ||
| PCON4 | I am concerned that health providers may keep my personal information in non-accurate manner. | ||
| PCON5 | I am concerned about giving information to health providers. | ||
| Trust (T) | T1 | Healthcare service providers are trustworthy. | [91] |
| T2 | Healthcare service provider is one that keeps promises and commitments. | ||
| T3 | I trust healthcare service provider because they keep my best interests in mind. | ||
| Perceived Utility (PU) | PU1 | Aadhaar linked healthcare services will enable me quick service. | [28], [29], Davis, Bagozzi and Warshaw (1989) |
| PU2 | Using Aadhaar linked healthcare services will increase productivity of service provider. | ||
| PU3 | Aadhaar linked healthcare services will improve performance of service providers. | ||
| PU4 | Using Aadhaar linked healthcare services will enhance effectiveness of service providers. | ||
| PU5 | Using Aadhaar linked healthcare services will make it easier to get healthcare services. | ||
| PU6 | Overall, I find Aadhaar linked healthcare services system useful for me. | ||
| Perceived Ease of Use (PEOU) | PEOU1 | Learning to get healthcare services using Aadhaar will be easy for me. | [28], [29], Davis, Bagozzi and Warshaw (1989) |
| PEOU2 | It will be easy to get healthcare service using Aadhaar based service. | ||
| PEOU3 | It will be easy for me to remember how to get required service using Aadhaar based healthcare service. | ||
| PEOU4 | My interaction with healthcare service providers is clear and understandable. | ||
| PEOU5 | I find [that it will not] take a lot of effort in using healthcare services. | ||
| PEOU6 | Overall, I find the Aadhaar based healthcare service will be easy to use. | ||
| Behavioral Intention (BI) | BI1 | I intend to use Aadhaar based healthcare service in future. | [86] |
| BI2 | I plan to use Aadhaar based healthcare service. | ||
| BI3 | I expect to use Aadhaar based healthcare service in future. |
4.3. Data Collection
In Delhi, both Government and Non-Government organizations provide healthcare facilities. Directorate General of Health Services (DGHS), Government of NCT (National capital territory) of Delhi provide healthcare facilities at primary and secondary levels through various health outlets. Network of dispensaries, polyclinics, Mohalla clinics and mobile health clinics throughout the city fulfill primary health care needs of citizens (http://www.delhi.gov.in/ accessed on 28 Aug 2019). Dispensaries are the frontline health outlets equipped to provide treatment for common ailments, taking preventive and promoting activities, and providing essential medicines. Facilities at dispensaries include general OPD (out-patient department), free distribution of medicines, basic emergency care, laboratory services, immunization and family welfare activities, health education, etc. As per DGHS’s [7], there are 185 dispensaries spread in 11 districts of Delhi. 1, 574, 112 patients attended OPD and 1, 970, 632 tests were conducted in dispensaries during the year.
4.4. Basic Information
We randomly selected 11 dispensaries from 8 out of 11 districts of Delhi for data collection. Patients and their accompanying member(s), both females and males, in the age group of 18-60 years were approached. Patients seemingly in critical medical state were not disturbed. Consent from the respondents was taken before asking for their response. Respondents were asked to read the scenario before giving responses. Few, who were not willing to read the scenario, were personally explained. 458 responses were received. On scrutiny, 42 responses were rejected due to incomplete or multiple responses. In all 416 responses were statistically analyzed for verification of our conceptual model. Demographic characteristics of the sample are presented in Table 2a and descriptive statistics are presented in Table 2b . Careful observation of the descriptive statistics presented in Table 2b, indicates that on an average, perhaps, mean related to privacy related items are lowest as compared to items pertaining to trust, PU, PEOU, and BI. Further, within privacy related items itself, perhaps PCON1 has the lowest mean, implying that respondents in general are already concerned about the providing much personal information.
Table 2a.
Respondents Demography.
| Demography and descriptive statistics | ||||
|---|---|---|---|---|
| Gender | Dispensary | |||
| Female | 165 | 39.66% | DGD Begumpur | 22 |
| Male | 251 | 60.34% | DGD Bholanath Nagar | 41 |
| Total | 416 | 100% | DGD Dilshad Garden | 56 |
| Age | DGD Dwarka -12 | 41 | ||
| 18 - 30 | 162 | 38.94% | DGD Jharoda Majra | 29 |
| 31 - 40 | 150 | 36.05% | DGD Narela | 41 |
| 41 - 50 | 80 | 19.24% | DGD Nawada | 39 |
| 51 - 60 | 24 | 5.77% | DGD Sarai Rohilla | 35 |
| Total | 416 | 100% | DGD Seema Puri | 34 |
| Education | PUHC Aya Nagar | 28 | ||
| Primary | 60 | 14.42% | PUHC Mohan Garden | 50 |
| High school | 41 | 9.86% | ||
| Higher Secondary | 115 | 27.64% | ||
| Above | 200 | 48.08% | ||
| Total | 416 | 100% | Total | 416 |
Table 2b.
Descriptive Statistics
| Demography and descriptive statistics | ||
|---|---|---|
| Survey Question | Mean | Standard Deviation |
| PRIVACY CONCERN | 2.16 | 1.12 |
| PCON1 | 2.16 | 1.12 |
| PCON2 | 2.46 | 0.96 |
| PCON3 | 2.42 | 1.13 |
| PCON4 | 2.29 | 1.06 |
| PCON5 | 2.29 | 1.09 |
| TRUST | ||
| T1 | 3.91 | 0.76 |
| T2 | 3.77 | 0.89 |
| T3 | 4.00 | 0.77 |
| PERCEIVED UTILITY | ||
| PU1 | 3.68 | 0.94 |
| PU2 | 3.68 | 0.93 |
| PU3 | 3.56 | 0.93 |
| PU4 | 3.70 | 0.92 |
| PU5 | 3.65 | 0.90 |
| PU6 | 3.70 | 0.96 |
| PERCEIVED EASE OF USE | ||
| PEOU1 | 3.97 | 0.91 |
| PEOU2 | 3.83 | 0.83 |
| PEOU3 | 3.89 | 0.82 |
| PEOU4 | 3.87 | 0.92 |
| PEOU5 | 3.98 | 0.89 |
| PEOU6 | 4.00 | 0.93 |
| BEHAVIORAL INTENTIONS | ||
| BI1 | 3.76 | 0.76 |
| BI2 | 3.80 | 0.80 |
| BI3 | 3.87 | 0.70 |
The non-response bias in this study was also tested by performing a series of t-tests between the last twenty five percent of respondents and the rest of the sample on a large number of variables in the survey following the framework developed by [2]. As the data was collected from single respondents, there is also an accompanying risk of spurious covariance between the measures in the survey, i.e., common method variance (CMV) possibly resulting in biased estimators [107]. Step was taken to minimize CMV and limit its potential effect on the analysis. The wordings of the survey items were refined to improve their clarity by using expert judgment (in this case by both academic and industry expert) and q-sort techniques, resulting in tentative item reliability and item validity [80].
5. Data Analysis and Results
5.1. Measurement Model Evaluation
Evaluation of quality of measurement model is the primary stage of any structural equation modeling involving examination of convergence, content and discriminant validity, and reliability of constructs. Since all the items are adopted from published research literature and experts in the field conducted item-by-item evaluation before and after the pilot study, content validity of the measurement is established [113]. Construct validity is established by ascertaining convergent validity and discriminant validity. Factor analysis with Varimax rotation using SPSS16 is carried out to ascertain convergent validity. Kaiser-Meyer-Olkin measure of sampling adequacy value is 0.92, higher than justifiable value for carrying out factor analysis (0.5) [56]. Bartlett’s test of sphericity is significant (Table 4). All the items displayed clear loading unto their five respective components as given in Table 5. Average variance extracted (AVE) for all constructs and quality parameters, i.e., Cronbach's alpha, composite reliability (CR) are reported in Table 3 . All measures representing constructs have Cronbach’s alpha above the acceptable limit of 0.70, CR above 0.7 and AVE more than 0.5 [22] confirming convergent validity, discriminant validity and reliability of the constructs.
Table 4.
KMO and Bartlett's Test
| Kaiser-Meyer-Olkin Measure of Sampling Adequacy. | .920 | |
| Bartlett's Test of Sphericity | Approx. Chi-Square | 3.882E3 |
| df | 253 | |
| Sig. | .000 | |
Table 5.
Factor loadings
| Components |
|||||
|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | |
| PCON1 | 0.688 | ||||
| PCON2 | 0.762 | ||||
| PCON3 | 0.769 | ||||
| PCON4 | 0.794 | ||||
| PCON5 | 0.794 | ||||
| T1 | 0.783 | ||||
| T2 | 0.784 | ||||
| T3 | 0.769 | ||||
| PU1 | 0.721 | ||||
| PU2 | 0.650 | ||||
| PU3 | 0.727 | ||||
| PU4 | 0.713 | ||||
| PU5 | 0.689 | ||||
| PU6 | 0.742 | ||||
| PEU1 | 0.744 | ||||
| PEU2 | 0.705 | ||||
| PEU3 | 0.761 | ||||
| PEU4 | 0.723 | ||||
| PEU5 | 0.699 | ||||
| PEU6 | 0.697 | ||||
| BI1 | 0.738 | ||||
| BI2 | 0.685 | ||||
| BI3 | 0.814 | ||||
Extraction Method: Principal Component Analysis.
Rotation Method: Varimax with Kaiser Normalization.
Table 3.
Reliability measures
| Constructs | Cronbach's alpha | CR | AVE |
|---|---|---|---|
| Privacy Concern | 0.896 | 0.873 | 0.581 |
| Trust | 0.738 | 0.807 | 0.583 |
| Perceived utility | 0.838 | 0.875 | 0.500 |
| Perceived ease of use | 0.853 | 0.867 | 0.521 |
| Behavioural intention | 0.744 | 0.790 | 0.558 |
5.2. Hypothesis Testing
We use SEM for analysis of the proposed measurement model. Use of SEM will substantiate robustness of findings as it is based on maximum likelihood algorithm that considers error terms in establishing loadings, correlations and other related measures. The measurement model is evaluated on primary fit criteria, overall model fit and fit of internal structure of model as proposed by [10]. Widely accepted and reported fit indices including absolute fit, incremental fit and parsimony fit indices of the conceptual model are examined (Hooper at al., 2008). Absolute fit measures, i.e., chi-square static, GFI (goodness-of-fit index), AGFI (adjusted goodness-of-fit index) and RMSEA (root mean square error approximation) determine degree to which the overall model predicts the observed covariance or correlation matrix. Incremental fit indices, i.e., NFI (normed fit index), CFI (comparative fit index) and NNFI (non-normed fir index) compare the proposed model to baseline model, often referred to as null model. PNFI (parsimonious normed fit index) and PGFI (parsimonious goodness-of-fit index) are termed as parsimony fit indices. These indices determine impact of additional parameters on the conceptualized model. All the indices of the proposed model obtained using LISREL are within acceptable limit are presented in Table 6 . All the fit indices were within acceptable limit indicating good model fit [76,84,85,106].
Table 6.
Goodness of Fit Statistics
| Measures index | General rule of acceptance | Overall Model (Sample size 416) |
|---|---|---|
| Absolute Fit Measures | ||
| χ2 | 249.83 | |
| df | 220 | |
| χ2/df | <3 | 1.14 |
| RMSEA | <.06 | 0.018 |
| GFI | >.80 | 0.95 |
| AGFI | >.80 | 0.94 |
| Incremental Fit Measures | ||
| NFI | >.90 | 0.98 |
| IFI | >.90 | 1 |
| CFI | >.90 | 1 |
| Parsimonious Fit Measures | ||
| PNFI | >.50 | 0.85 |
| PGFI | >.50 | 0.76 |
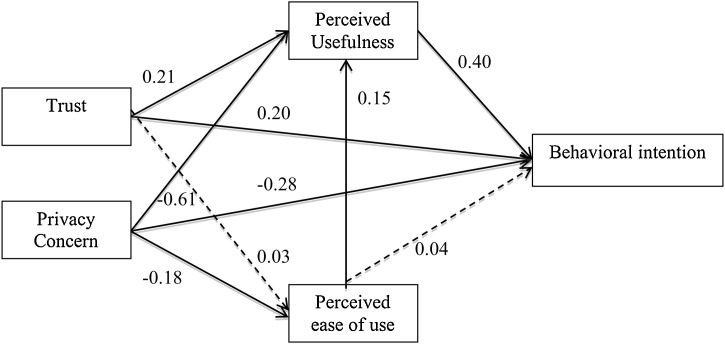
Path coefficients along with t-statistics of corresponding hypothesized paths are presented in Table 7 and Fig. 3 . Seven path coefficients are found considerably high and statistically significant. As per the established TAM, PU is found to influence BI and PEOU to PU. PEOU influence on BI found to be insignificant. Trust influence on PEOU is not found significant, however, trust has direct influence on PU and BI. Privacy concern is found to influence PU, PEOU and BI negatively.
Table 7.
SEM Results
| Hypothesis | Influencing variable | Influenced variable | Path Coefficient | t-statistics | Significance |
|---|---|---|---|---|---|
| H1a | PU | BI | 0.40 | 5.64 | Significant |
| H1b | PEOU | PU | 0.15 | 2.16 | Significant |
| H1c | PEOU | BI | 0.04 | 0.60 | Not Significant |
| H2a | T | BI | 0.20 | 2.85 | Significant |
| H2b | T | PU | 0.21 | 2.16 | Significant |
| H2c | T | PEOU | 0.03 | 0.53 | Not Significant |
| H3a | PCON | BI | −0.28 | 3.48 | Significant |
| H3b | PCON | PU | −0.61 | 8.37 | Significant |
| H3c | PCON | PEOU | −0.18 | 2.27 | Significant |
Fig. 3.
Final Model with path coefficients.
6. Analysis and implications
6.1. Analysis of results
The obtained results from our empirical analysis support proposed hypotheses on acceptance of technology in healthcare. However, the significance of individual hypotheses warrants further discussion. This research examines technology acceptance in healthcare services, hypothesizing and validating role of trust and privacy concerns. In addition to reaffirming relations of original TAM constructs, our results elucidate that trust and privacy concern directly affect patients’ intention to use technology in healthcare services. Growing interest in patients’ reaction to introduction of technology in healthcare has given impetus to theories that predict and explain technology acceptance and usage. The results suggest that while enhanced trust positively affects behavioral intention and perceived utility of the service, privacy concern, on other hand, has negative effect on behavioral intention, perceived utility and perceived ease of use of medical services. In particular, the studies carried out by [6] and [49] are important to be discussed here, since both of these studies, investigated the acceptance of technology by people availing healthcare services. [6], while investigating Australian general public perception of adopting a personally controlled electronic health record (PCEHR), argued that individuals appreciate the value associated with PCEHR. However, adoption of PCEHR was explained by perceived value and perceived risk. Further, individuals also liked to have two key concerns, viz., reduction in privacy and lack of trust to be mitigated before committing to PCEHR. However, how and to what degree trust and privacy concerns impact the behavioral intentions of individuals is something ascertained by our study. Unlike the study by [6], our study also considers the relationships amongst behavioral constructs and perceived utility associated with adoption of technology in healthcare delivery.
Trust does not seem to have significant effect on ease of use of any technology in healthcare. All hypotheses are confirmed through empirical assessment. The results also confirm findings of similar studies carried out in online services. However, evaluation of effect of trust and privacy concern on technology acceptance in healthcare services provides the aspect of originality in respect of existing literature. Our results in regard to behavioral intention also somewhat support the findings from [49] arguing that positive relationship exists between perceived utility and behavioral intention in adopting electronic patient portal (EPP). Our study supports earlier literature on trust and transactions and confirms their relevance in healthcare services also. Data from primary health centres shows that trust has direct bearing on behavioural intentions of patients to use the service or avoid to it. The study also establishes positive relationship between trust and perceived utility. Based on these results, we can assert that trust is an enabler of acceptance of technology in healthcare services. The results also demonstrate that privacy concerns of patients are negatively associated with perceived utility, perceived ease of use and as a result behavioural intention of adaptation of new technology in healthcare. Our results support previous studies, carried out in different services, which suggest that if consumers’ privacy concerns are not mitigated, they will have negative impact on consumers’ decision on availing that service [37]. Given the potential repercussion on consumer’s attitude, it is essential that researchers accurately understand the concern related to consumer’s information privacy. Above analysis synthesizes the assertion that privacy concern is an inhibiter of acceptance of technology in healthcare services.
6.2. Research implications
Following implications can be clearly derived from the research analysis discussed above.
6.2.1. Managerial implications
From managerial point of view, major implications of this study can be summarized as follows. Firstly, in today’s technologically intensive and competitive health care domain, the citizens’ need (particularly in developing countries) is oriented around high quality care at an affordable cost. Health care managers, therefore, must find cogent ways to obtain superior healthcare results considering rather limited resources. Secondly, as numerous studies have shown that adoption of new technologies in healthcare can provide quality healthcare to all socioeconomic strata of the society particularly in rural and remote areas, it is pivotal for healthcare service providers to understand the driving forces of patients’ acceptance of technology. This study demonstrates factors that affect behavioural intentions of patients in acceptance of newer technologies. Thirdly, this study reflects needs for strategic planning, assessing and understanding the role of trust to allay ethical concerns related to the user sensitive data. Finally, success of any e-health program hinges on acceptance of technology to put in place robust IT enabled models designed for providing access to affordable healthcare. It mandates service managers to strive for greater technology acceptance amongst patients.
6.2.2. Theoretical implications
On theoretical front, this research provides significant contributions in establishing link between behavioral aspects and acceptance of technology in health services. The study explores a vital issue of patients’ trust and their privacy concerns in context of new technology acceptance, thus providing a theoretical foundation to understand behavioral responses of patients on introduction of a new technology in healthcare service delivery. Additionally, our study also contributes to the extant literature by proposing and testing extended TAM by integrating behavioral constructs in healthcare context. Adapting to the conceptualization of trust and privacy concern in various other services, this research reaffirms effect of these constructs on acceptance of technology in healthcare services. This approach will help us in building a holistic picture of technology acceptance in healthcare.
This study suggests that perceived usefulness, perceived ease of use, trust and privacy concerns are valid predictors of technology acceptance in healthcare service delivery. Our study lends support to theoretical foundation of TAM in healthcare setting associated with credence, co-creation and co-production, and vulnerability of service receiver as few key attributes. Partly, implementation of new technology in healthcare is marred by lack of engagement of the service consumers. Theoretically, existing literature is rather inadequate in satisfactorily exploring contingent factors emerging from application of smart technologies in public healthcare [86]. This study provides relationship between an individual’s behavioral constructs and final acceptance of technology in healthcare service setting.
6.2.3. Policy implications
Countries have been spending significantly on new technologies for improving healthcare service delivery. However, when adopted technology is not acceptable to the patients, then the purpose of these technological advancements gets defeated. Despite notable gains in improving life expectancy, improving maternal and child mortality outcomes and addressing other health priorities, the rate of improvement has been far from satisfactory (particularly in developing world). For policy makers and researchers, this study does a redressal of four issues to obtain acceptance and desired outcome of technology being introduced in healthcare services. Firstly, introduced technology must focus on expected usefulness to the patients. Secondly, service providers must focus on ease of use and convenience associated with the technology. Thirdly, trust has been found to impact patients’ perception of utility and thus, behavioral intention to use that technology. While expected use and ease of use can be explained to the user, trust is something, which has to be earned. Onus here lies with implementing agencies (health centers in this case) and the Governments to develop trust amongst patients for delivery of healthcare services. Finally, privacy concern has influence on utility, ease of use and final acceptance of any technology. Like trust, apprehensions related to privacy concern of the patients have to be mitigated by the implementing agencies and the Government. Technology induction in healthcare will not only create value for patients, but also for the entire social and economic ecosystem.
In India, availability of enabling technologies like mobile internet, cloud computing and social media augmented by favorable demographics and healthcare infrastructure can create a fertile ground for induction of technologies in health care delivery. Various governmental direct benefit schemes are already linked with Aadhaar numbers of citizens. However, healthcare services are yet to be linked to any unique identity in the country. One such study proposed blockchain and big data assisted, unique id linked model for universal healthcare coverage [33]. As an augmentation to [33], this research delineates behavioral factors to be considered while implementing any technology assisted healthcare model for achieving universal healthcare coverage.
As already ascertained by extant studies [6], mitigating privacy related concerns in patients’ minds thus ensuring enhanced trust between patients and service providers, is crucial to success of medical services delivery including e-services. In this regard there are certain concrete steps can be taken by the concerned stakeholders including both government and healthcare providers. In Indian context and on a governmental level, of particular interest would be HIPAA (Health Insurance Portability and Accountability Act of 1996) and EUs safe harbor law (Barua et al., 2011). These laws usually mandate strict security measures for sharing and exchanging health data, and failure to comply with them is accompanied by severe penalties. From the standpoint of health care service providers, only authorized users such as medical staff should have access to the collected health data as it almost always contains confidential and sensitive data. This security critical system, however, requires careful balancing between confidentiality and availability. The dichotomous nature of these two goals is clear: while all the patient’s data should be available to be shared and monitored to deliver professional healthcare services; for security reasons, part of the data may be considered confidential and therefore must not be accessible. Clearly, rationalization of the paired goals should be achieved to provide the best possible care for patients. Further, when dealing with privacy concerns in e-healthcare models, security models revolving around data collection, data transmission, and data storage would have to be designed carefully [130]). Of particular interest in this context would be use of blockchain concept for patients’ registration and handling of medical record as proposed by Dhaggara et al., (2019) as a way of creating immutable and secure framework.
7. Limitations and future methodological improvements
7.1. Limitations
To the best of authors’ knowledge, this is first study aimed to explore technology acceptance linking unique identity with healthcare records in India. Since such conceptualization is yet to be implemented, there exists many limitations in our study. We recommend a pilot project implementing integration of healthcare records based on unique identity. This study has been carried out in urban area of one city of the country wherein the respondents were relatively young and educated. Educated respondents therefore pose less of a challenge as far as interpretation of survey responses are concerned. Though data has been collected by randomly selecting healthcare centers and patients, it may not reflect huge diversity of the population. To further validate present findings, proposed model may be investigated in different countries in different geographical spreads. Model may further be cross validated in developing and developed countries. This will further boost the reliability of results and may result in some degree of generalization of managerial and theoretical inferences. To further boost robustness and validity of the proposed model, study may be replicated with larger sample size and at different levels of healthcare services like in specialty hospitals. Finally, the study investigates effect of only two additional behavioral constructs on technology acceptance in healthcare delivery. Future study may include more behavioral constructs to study their effects on technology acceptance in healthcare. Of particular interest would be to include behavioral constructs that can explain patients’ behavioral and psychological traits in the time of pandemics (for instance the ongoing COVID-19 situation). Psychological interventions for all or specific (e.g., more vulnerable) groups aimed at identification of adverse psychological impacts and psychopathological symptoms in the general population during the pandemics would be of use to governments and healthcare service providers.
7.2. Future methodological improvements
The methodological analysis as carried out in our study can be further refined by taking into account the fixed and random effects. In particular, the motivation for using fixed effect (FE) and random effect (RE) regression model would emanate from identification of such effects explaining variations on measurement items related to output variables, i.e., variables explaining behavioral intention in our case [73]. However, such methods, for instance, those related to FE (e.g., ordinary regression, uni/multivariate regression models) and RE including meta-analysis related (e.g., Hunter-Schmidt/Hedges-Vevea) are often considered data hungry methods, wherein some important questions such as how much and what kind of data need to be collected to deploy such models meaningfully and reliably need to be addressed. Questions, for instance, whether the data would be pooled in nature or individual respondent based would also aid practitioners in determining the right sampling strategy [73].
[104] in their study discussed comparison of FE and RE model for empirical data. They argued that results often vary substantially given the type of model used since FE is often associated with apriori while RE takes into account statistical calibration. Further, deploying FE models and generalizing findings are often dichotomous in nature in that FE models can lead to inflated Type I error rates and erroneously narrow confidence interval [45]; [51].
8. Concluding remarks
With the advent and phenomenal growth of new technologies based on big data, cloud computing, and blockchain, technology usage is rapidly increasing due to numerous advantages. In healthcare service delivery, technologies concerning professionals, like online appointments, data recording for diagnosis and tracking, etc., are increasingly being adopted. Moreover, not only professionals, but patients and their relatives also get influenced by technology. Intent of this empirical work was to explore constructs that affect patients’ acceptance of technology in healthcare. Technology in healthcare has many advantages and at times seems to be only answer to the enormous task of providing universal health coverage. However, for implementation and acceptance of technology in this sector, practitioners and researchers have to take behavioral traits of patients into consideration as well. This empirical study presents an extension to the well-established TAM model. Primary contribution of this study is integration of behavioral variables (trust and privacy concern) with TAM constructs into a parsimonious model that predicts patients’ acceptance of technology in healthcare service. This study suggests that trust, privacy concern and perceived utility shape patients attitude towards technology acceptance; while trust and privacy concern directly influence perceived utility. As healthcare service is often characterized by credence of highest degree and different from other services on many accounts, there remains significant scope of unauthorized exploitation of patients’ health data. This study suggests that patients’ fears about losing privacy has to be dispelled for their acceptance of any newer technology. Practitioners and agencies responsible for healthcare need to earn trust of patients before implementing any new technology. The study empirically establishes relationship between trust and privacy concern of patients with their intention of technology acceptance. Based on a scenario, the data was collected from primary health centers in India to understand various constructs and to test related hypotheses. Based on results and analysis, theoretical and managerial implications are drawn and discussed in detail.
Conflict of interest
None.
Appendix 1 Scenario
One morning you wake up suffering from fever and headache. You had similar problem a few weeks ago and you got all your tests done. You took medicines as prescribed by the doctor. Now you feel worried and would like to get in touch with a medical doctor to receive a diagnosis and treatment. You have two options: You may collect all your previous treatment case history, reports, prescriptions, etc., and preferably go to the same doctor from whom you received your treatment on the last time.
Second option is that, you carry your Aadhaar card and go to any health center, which is capable of providing healthcare services by using your Aadhaar data.
If you choose second option, you have to give your thumb impression to identify yourself. After identification, your all the medical records will be available with the doctor. You don’t have to carry any of your previous health records. The doctor, after examining your records and previous diagnosis, will be able to prescribe future course of action. With more certainty, the doctor will be able to decide which tests need to be done.
Whatever treatment you receive here, everything will be added to your health history so that next time whenever you need health service, you don’t have to carry any physical record with you. Just by identifying yourself by giving your thumb impression at any health center, all your previous treatment details will be available with stationed doctor there. I am sure that you are aware that your Aadhaar is linked with your bank accounts, and other financial subsidies you receive from Government. However, such data is safe and secure. At a health center, only your health related data will be accessed.
References
- 1.Agarwal R., Gao G., DesRoches C., Jha A.K. Research commentary—The digital transformation of healthcare: Current status and the road ahead. Information Systems Research. 2010;vol. 21(4):796–809. [Google Scholar]
- 2.Armstrong J.S., Overton T.S. Estimating nonresponse bias in mail surveys. Journal of Marketing Research. 1977;14(3):396–402. [Google Scholar]
- 3.Ahmed E., Yaqoob I., Hashem I.A.T., Khan I. The role of big data analytics in Internet of Things. Computer Networks. 2017;129:459–471. [Google Scholar]
- 4.Ajzen I. The Theory of Planned Behavior. Organizational Behavior and Human Decision Processes. 1985;50(March):179–211. [Google Scholar]
- 5.Amoako-Gyampah K., Salam A.F. An extension of the technology acceptance model in an ERP implementation environment. Information & Management. 2004;41(6):731–745. [Google Scholar]
- 6.Andrews L., Gajanayake R., Sahama T. The Australian general public’s perceptions of having a personally controlled electronic health record (PCEHR) International Journal of Medical Informatics. 2014;83(12):889–900. doi: 10.1016/j.ijmedinf.2014.08.002. [DOI] [PubMed] [Google Scholar]
- 7.Annual Report 2016-17 . Directorate General of Health Services; 2016. Government of National Capital Territory of Delhi. [Google Scholar]
- 8.Anthony D.L., Stablein T. Privacy in practice: professional discourse about information control in healthcare. Journal of Health Organization and Management. 2015;30(2):207–226. doi: 10.1108/JHOM-12-2014-0220. [DOI] [PubMed] [Google Scholar]
- 9.Ba S., Paulov P.A. Evidence of the effect of trust building technology in electronic market: price premium and buyer behaviour. MIS Quarterly. 2002;26(No. 3) pp.243-268/September 2002. [Google Scholar]
- 10.Bagozzi R., Yi Y. On the evaluation of structure equation models. Journal of Academy of Marketing Science. 1988 doi: 10.1007/BF02723327. [DOI] [Google Scholar]
- 11.Bansal G., Zahedi F.M., Gefen D. The impact of personal dispositions on information sensitivity, privacy concern and trust in disclosing health information online. Decision Support Systems. 2010;49:138–150. [Google Scholar]
- 12.Bem D.J. An alternative interpretation of cognitive dissonance phenomena. Psychological Review. 1967;74(3):183–200. doi: 10.1037/h0024835. [DOI] [PubMed] [Google Scholar]
- 13.Berry L.L., Bendapudi N. Healthcare: A fertile field for service research. Journal of Service Research. 2007;10(2):111–122. [Google Scholar]
- 14.Binczewski A., Kurowski K., Mazurek C., Stroinski M. A concept of a patient-centered healthcare system based on the virtualized networking and information infrastructure. Proceedings of the eTELEMED 2011: The Third International Conference on eHealth, Telemedicine, and Social Medicine. 2011:51–58. [Google Scholar]
- 15.Bleier A., Eisenbeiss M. The Importance of Trust for Personalized Online Advertising. Journal of Retailing. 2015;91(3):390–409. [Google Scholar]
- 16.Bozic B. Consumer trust repair: A critical literature review. European Management Journal. 2017;35(4):1–10. [Google Scholar]
- 17.Buntin B.B., Burke M.F., Hoaglin M.C., Blumenthal D. The benefits of health information technology: A review of the recent literature shows predominantly positive results. Health Affairs. 2011;30(3):464–471. doi: 10.1377/hlthaff.2011.0178. [DOI] [PubMed] [Google Scholar]
- 18.Carter L., Bélanger F. The utilization of e-government services: Citizen trust, innovation and acceptance factors. Information Systems Journal. 2005;15(2105):5–25. [Google Scholar]
- 19.Castaldo S., Premazzi K., Zerbini F. The Meaning(s) of Trust. A Content Analysis on the Diverse Conceptualizations of Trust in Scholarly Research on Business Relationships. Journal of Business Ethics. 2010;96:657–668. [Google Scholar]
- 20.Chaudhry B., Wang J., Shinyi Wu S., Maglione M., Mojica W., Roth E., Morton S.C., Shekelle P.G. Systematic review: Impact of health information technology on quality, efficiency, and costs of medical care. Annals of Internal Medicine. 2006;144:742–752. doi: 10.7326/0003-4819-144-10-200605160-00125. [DOI] [PubMed] [Google Scholar]
- 21.Chellappa R.K., Sin R. Personalization versus Privacy: An empirical examination of the online consumer’s dilemma. Information Technology and Management. 2005;6(2):181–202. [Google Scholar]
- 22.Cortina J.M. What is coefficient alpha? An examination of theory and applications. Journal of Applied Psychology. 1993;78:98–104. [Google Scholar]
- 23.Culnan M.J., Armstrong P.K. Information privacy concerns, procedural fairness, and impersonal trust: An empirical investigation. Organization Science. 1999;10(1):104–105. [Google Scholar]
- 24.Cutler D.M., Feldman N.E., Horwitz J.R. U.S. adoption of computerized physician order entry systems. Health Affairs. 2005;24(6):1654–1663. doi: 10.1377/hlthaff.24.6.1654. [DOI] [PubMed] [Google Scholar]
- 25.Dabholkar P.A., Bagozzi R.P. An attitudinal model of technology-based self-service: moderating effects of consumer traits and situational factors. Journal of the Academy of Marketing Science. 2002;30(3):184–201. [Google Scholar]
- 26.Dabholkar P.A. Consumer evaluations of new technology-based self-service options: an investigation of alternative models of service quality. International Journal of Research in Marketing. 1996;13(1):29–51. [Google Scholar]
- 27.Davis F.D., Bagozzi R.P., Warshaw P.R. User acceptance of computer technology: A comparison of two. Management Science. 1989;35(8):982–1003. [Google Scholar]
- 28.Davis F.D. 1986. A Technology Acceptance Model for empirical testing new end-user information systems: Theory and results.https://dspace.mit.edu/handle/1721.1/15192 Doctoral Dissertation, MIT. Available at. [Google Scholar]
- 29.Davis F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly. 1989;13:319–340. [Google Scholar]
- 30.DesRoches C.M., Campbell E.G., Rao S.R., Donelan K., Ferris T.G., Jha A.K., Kaushal R. Electronic health records in ambulatory care—A national survey of physicians. New England Journal of Medicine. 2008;359(1):50–60. doi: 10.1056/NEJMsa0802005. [DOI] [PubMed] [Google Scholar]
- 31.Devaraja S., Terence T., &Kohli R. Examining the impact of information technology and patient flow on healthcare performance: A Theory of Swift and Even Flow (TSEF) perspective. Journal of Operations Management. 2013;31:181–192. [Google Scholar]
- 32.Dey A., Sinha K.K., Thirumalai S. IT Capability for Health Care Delivery: Is More Better? Journal of Service Research. 2013;16(3):326–340. [Google Scholar]
- 33.Dhagarra D., Goswami M., Sarma P.R.S., Choudhury A. Big Data and blockchain supported conceptual model for enhanced healthcare coverage: The Indian context. Business Process Management Journal. 2019;25(7):1612–1632. [Google Scholar]
- 34.Dinev T., Hart P. Internet privacy concerns and social awareness as determinants of intention to transact. International Journal of Electronic Commerce. 2005 doi: 10.2753/JEC1086-4415100201. [DOI] [Google Scholar]
- 35.Dinev T., Hart P. An extended privacy calculus model for e-commerce transactions. Information Systems Research. 2006;17(1):61–80. [Google Scholar]
- 36.Doney P.M., Cannon J.P. An examination of the nature of trust in buyer-seller relationships. Journal of Marketing. 1997;61(2):35–51. [Google Scholar]
- 37.Eastlick M.A., Lotz S.L., Warrington P. Understanding online B-to-C relationships: An integrated model of privacy concerns, trust, and commitment. Journal of Business Research. 2006:877–886. pp. 59. [Google Scholar]
- 38.Ekblaw A., Azaria A., Halamka J.D., Lippman A. White Paper. MIT Media Lab, Beth Israel Deaconess Medical Center; 2016. A case study for blockchain in healthcare: “MedRec” prototype for electronic health records and medical research data. August 2016. [Google Scholar]
- 39.Fishbein M., Ajzen I. Addison-Wesley; Reading, Mass: 1975. Belief, attitude, intention and behavior: An introduction to theory and research. [Google Scholar]
- 40.Gan W., Lin J.C.-W., Chao H.-C., Vasilakos A.V., Yu P.S. Utility-Driven Data Analytics on Uncertain Data. IEEE Systems Journal. 2020 doi: 10.1109/JSYST.2020.2979279. [DOI] [Google Scholar]
- 41.Gefen D., Benbasat I., Paulov P. A Research Agenda for Trust in Online Environments. Journal of Management Information Systems. 2008;24(4):275–286. [Google Scholar]
- 42.Gefen D., Karahanna E., Straub D.W. Trust and TAM in online shopping: An integrated model. MIS Quarterly. 2003;27(1):51–90. [Google Scholar]
- 43.Ha S., Stoel L. Consumer e-shopping acceptance: Antecedents in a technology acceptance model. Journal of Business Research. 2009;62(5):565–571. [Google Scholar]
- 44.He D., Chen C.L.P., Chan S., Bu J. ReTrust: Attack-Resistant and Lightweight Trust Management for Medical Sensor Networks. IEEE transactions on information technology in biomedicine: a publication of the IEEE Engineering in Medicine and Biology Society. 2012;16(4):623–632. doi: 10.1109/TITB.2012.2194788. [DOI] [PubMed] [Google Scholar]
- 45.Hedges L.V., Vevea J.L. Fixed- and random-effects models in meta-analysis. Psychological Methods. 1998;3:486–504. [Google Scholar]
- 46.Heravi A., Mubarak S., Choo K.R. Information privacy in online social networks: Uses and gratification perspective. Computers in Human Behavior. 2017:441–459. pp. 84 (2018) [Google Scholar]
- 47.Hoffman D.L., Novak T.P., Peralta M. Building consumer trust online. Communication of the ACM. 1999;42(4):80–85. [Google Scholar]
- 48.Holden R.J., Karsh B.T. The Technology Acceptance Model: Its past and its future in health care. Journal of Biomedical Informatics. 2010:159–172. doi: 10.1016/j.jbi.2009.07.002. pp. 43. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 49.Honein-AbouHaidar G.N., Antoun J., Badr K., Hlais S., Nazaretian H. Users’ acceptance of electronic patient portals in Lebanon. BMC Medical Informatics and Decision Making. 2020 doi: 10.1186/s12911-020-1047-x. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 50.Hosmer L.T. Trust: The connection link between organizational theory and philosophical ethics. Academy of Management Review. 1995;20(2):379–403. [Google Scholar]
- 51.Hunter J.E., Schmidt F.L. Fixed effects vs. random effects meta-analysis models: Implications for cumulative research knowledge. International Journal of Selection and Assessment. 2000;8:275–292. [Google Scholar]
- 52.Hwang Y. Investigating enterprise systems adoption: uncertainty avoidance, intrinsic motivation, and the technology acceptance model. European Journal of Information Systems. 2005;14(2):150–161. [Google Scholar]
- 53.Jeong Y., Kim Y. Privacy concerns on social networking sites: Interplay among posting types, content, and audiences. Computers in Human Behavior. 2017;69:302–310. [Google Scholar]
- 54.Jha A.K., DesRoches C.M., Campbell E.G., Donelan K., Rao S.R., Ferris T.G., Shields A., Rosenbaum S., Blumenthal D. Use of electronic health records in U.S. hospitals. New England Journal of Medicine. 2009;360(16):1628–1638. doi: 10.1056/NEJMsa0900592. [DOI] [PubMed] [Google Scholar]
- 55.Jiang Z., Heng C.S., Choi B.C.F. Privacy concerns and privacy-protective behavior in synchronous online social interactions. Information Systems Research. 2013;24(3):579–595. [Google Scholar]
- 56.Kaiser H.F. An index for factor simplicity. Psychometrica. 1974;39(1):49–60. [Google Scholar]
- 57.Kazley A., Ozcan Y. Organizational and environmental determinants of hospital EMR adoption: A national study. Journal of Medical Systems. 2007;31(5):375–384. doi: 10.1007/s10916-007-9079-7. [DOI] [PubMed] [Google Scholar]
- 58.King W.R., He J. A meta-analysis of the technology acceptance model. Information& Management. 2006;43:740–755. [Google Scholar]
- 59.Lahiri A., Seidmann A. Information hangovers in healthcare service systems. Manufacturing & Service Operations Management. 2012;14(4):634–653. [Google Scholar]
- 60.Lalseng E.J., Andreassen T.W. Electronic Healthcare: A study of people’s readiness and attitude toward performing self-diagnosis. International Journal of Service Industry Management. 2007 doi: 10.1108/09564230710778155. [DOI] [Google Scholar]
- 61.Lanier C.D., Jr., Saini A. Understanding consumer privacy: A review and future directions. Academy of Marketing Science Review. 2008;12(02):1–48. [Google Scholar]
- 62.Lankton N.K., McKnight D.H., Tripp J.F. Facebook privacy management strategies: A cluster analysis of user privacy behaviors. Computers in Human Behavior. 2017;76:149–163. [Google Scholar]
- 63.Lee Y., Kozar K.A., Larsen K.R.T. The Technology Acceptance Model: Past, present, and future. Communications of the Association for Information Systems. 2003;50(12):752–780. [Google Scholar]
- 64.Li H., Wu J., Gao Y., Shi Y. Examining individuals’ adoption of healthcare wearables devices: An empirical study from privacy calculus perspective. International Journal of Medical Informatics. 2016;88:8–17. doi: 10.1016/j.ijmedinf.2015.12.010. [DOI] [PubMed] [Google Scholar]
- 65.Li L., Benton W.C. Hospital technology and nurse staffing management decisions. Journal of Operations Management. 2006;24:676–691. [Google Scholar]
- 66.Li Y. Empirical studies on online information privacy concerns: literature review and an integrative framework. Communication of the Association for Information System. 2011;28:453–496. [Google Scholar]
- 67.Lin C., He D., Huang X., Choo K.-K.R., Vasilakos A. BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0. Journal of Network and Computer Applications. 2018;116:42–52. [Google Scholar]
- 68.Littlejohns P., Kieslich K., Weale A., Stokes T., Gauld R., Scuffham P. Creating sustainable healthcare system. Journal of Health Organization and Management. 2018;33(1):18–34. doi: 10.1108/JHOM-02-2018-0065. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 69.Luck J., Chang C., Brown E.R., Lumpkin J. Using local health information to promote public health. Health Affairs. 2006;25(4):979–991. doi: 10.1377/hlthaff.25.4.979. [DOI] [PubMed] [Google Scholar]
- 70.Lupton D. Health promotion in the digital era: A critical commentary. Health Promotion International. 2014;30(1):174–183. doi: 10.1093/heapro/dau091. [DOI] [PubMed] [Google Scholar]
- 71.Malhotra K.N., Kim S.S., Agarwal J. Internet Users’ Information Privacy Concerns (IUIPC): The construct, the scale, and a causal model. Information Systems Research. 2004;15(4):336–355. [Google Scholar]
- 72.Mandl K.D., Szolovits P., Kohane I.S. Public standards and patients’ control: how to keep electronic medical records accessible but private. British Medical Journal. 2001;322:283–287. doi: 10.1136/bmj.322.7281.283. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 73.Martin J.G.A., Hussey D.H., Wilson A., Reale D. Measuring individual differences in reaction norms in field and experimental studies: a power analysis of random regression models. Methods in Ecology and Evolution. 2010;4(2) doi: 10.1111/j.2041-210X.2010.00084.x. [DOI] [Google Scholar]
- 74.McCullough J.S. The adoption of hospital information systems. Health Economics. 2008;17(5):649–664. doi: 10.1002/hec.1283. [DOI] [PubMed] [Google Scholar]
- 75.McCullough J.S., Casey M., Moscovice I., Prasad S. The Effect of Health Information Technology on Quality in U. S. Hospitals. Health Affairs. 2010;29(4):647–654. doi: 10.1377/hlthaff.2010.0155. [DOI] [PubMed] [Google Scholar]
- 76.McDonald R.P., Ho M.R. Principles and practice in reporting statistical equation analyses. Psychological Methods. 2002;7(1):64–82. doi: 10.1037/1082-989x.7.1.64. [DOI] [PubMed] [Google Scholar]
- 77.McGlynn E.A., Asch S.M., Adams J., Keesey J., Hicks J., DeCristofaro A., Kerr E.A.M. The quality of healthcare delivered to adults in the United States. The New England Journal of Medicine. 2003;348:2635–2645. doi: 10.1056/NEJMsa022615. [DOI] [PubMed] [Google Scholar]
- 78.McKnight D.H., Choudhury V., Kacmar C. The impact of initial consumer trust on intentions to transact with a web site: a trust building model. Journal of Strategic Information Systems. 2002;11:297–323. [Google Scholar]
- 79.Meng W., Choo K.-K.R., Furnell S., Vasilakos A.V., Probst C.W. Towards Bayesian-Based Trust Management for Insider Attacks in Healthcare Software-Defined Networks. IEEE Transactions on Network and Service Management. 2018;15(2):761–773. [Google Scholar]
- 80.Menor L.J., Roth A.V. New service development competence in retail banking: construct development and measurement validation. Journal of Operations Management. 2007;25(4):825–846. [Google Scholar]
- 81.Miller L.M.S., Bell R.A. Online health information seeking: the influence of age, information trustworthiness, and search challenges. Journal of Aging and Health. 2012;24(3):525–541. doi: 10.1177/0898264311428167. [DOI] [PubMed] [Google Scholar]
- 82.Milne G.R., Boza M. Trust and concern in consumers’ perceptions of marketing information management practices. Journal of Interactive Marketing. 1999;13(1):5–24. [Google Scholar]
- 83.Mukherjee A., Nath P. Role of electronic trust in online retailing: A re-examination of the commitment-trust theory. European Journal of Marketing. 2007;41(9):1173–1202. [Google Scholar]
- 84.Mulaik S.A., James L.R., Alstine J.V., Bennett N., Lind S., Stilwell C.D. Evaluation of goodness-of-fit Indices for structural equation models. Psychological Bulletin. 1989;105(3):430–445. [Google Scholar]
- 85.Pai F.Y., Huang K. Applying the Technology Acceptance Model to the introduction of healthcare information systems. Technological Forecasting & Social Change. 2011;78:650–660. [Google Scholar]
- 86.Papa A., Mital M., Pisano P., Giudice M.D. E-health and wellbeing monitoring using smart healthcare devices: An empirical investigation. Technological Forecasting & Social Change. 2018;153:pp. 119226. [Google Scholar]
- 87.Parasuraman A., Colby C.L. An updated and streamlined Technology Readiness Index: TRI 2.0. Journal of Service Research. 2015;18(1):59–74. [Google Scholar]
- 88.Parasuraman A. Technology Readiness Index (TRI): A Multiple item scale to measure readiness to embrace new technologies. Journal of Service Research. 2000;2(4):307–320. [Google Scholar]
- 89.Parasuraman R., Sheridan T.B., Wickens C.D. Situation awareness, mental workload, and trust in automation: Viable, empirically supported cognitive engineering constructs. Journal of Cognitive Engineering and Decision Making. 2008;2(2):140–160. [Google Scholar]
- 90.Patra M.R., Das R.K., Padhy R.P. Cloud based rural healthcare information system. Proceedings of the 6th International Conference on Theory and Practice of Electronic Governance; ICEGOV’ 12, ACM, New York, NY; 2012. pp. 402–405. [Google Scholar]
- 91.Paulov P.A. Consumer acceptance of electronic commerce: Integrating trust and risk with the Technology Acceptance Model. International Journal of Electronic Commerce. 2003;7(3):101–134. [Google Scholar]
- 92.Perera C., Qin Y., Estrella J.C., Reiff-Marganiec S., Vasilakos A. Fog Computing for Sustainable Smart Cities: A Survey. ACM Computing Surveys. 2017;50(3):32–43. [Google Scholar]
- 93.Peters D.H., Garg A., Bloom G., Walker D.G., Brieger W.R., Rahman M.H. Poverty and access to health care in developing countries. Annals of New York Academy of Science. 2008;1136:161–171. doi: 10.1196/annals.1425.011. [DOI] [PubMed] [Google Scholar]
- 94.Phelps J., D’Souza G., Nowak G.J. Antecedents and consequences of consumer privacy concerns: An empirical investigation. Journal of Interactive Marketing. 2001;15(4):2–17. [Google Scholar]
- 95.Phelps J., Nowak G., Ferrell E. Privacy concerns and consumer willingness to provide personal information. Journal of Public Policy & Marketing. 2000;19(1):27–41. [Google Scholar]
- 96.Piccinini P., Gamberini R., Prati A., Rimini B., Cucchiara R. An automated picking workstation for healthcare applications. Computers & Industrial Engineering. 2013;64:653–668. [Google Scholar]
- 97.Platt J., Raj M., Kardia S.L.R. The public’s trust and information brokers in healthcare, public health and research. Journal of Health Organization and Management. 2019;33(7/8):929–948. [Google Scholar]
- 98.Porambage P., Ylianttila M., Schmitt C., Kumar P., Gurtov A., Vasilakos A.V. The Quest for Privacy in the Internet of Things. IEEE Cloud Computing. 2016;3:36–45. [Google Scholar]
- 99.Qadri Y.A., Nauman A., Zikria Y.B., Vasilakos A.V., Kim S.W. The Future of Healthcare Internet of Things: A Survey of Emerging Technologies. IEEE Communication Surveys & Tutorials. 2020 doi: 10.1109/COMST.2020.2973314. [DOI] [Google Scholar]
- 100.Rahimi B., Nadri H., Afshar H.L., Timpka T. A systematic review of the technology acceptance model in health informatics. Applied Clinical Informatics. 2018;9(3):604–634. doi: 10.1055/s-0038-1668091. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 101.Rajagopal P. An innovation—Diffusion view of implementation of enterprise resource planning (ERP) systems and development of a research model. Information & Management. 2002;40(2):87–114. [Google Scholar]
- 102.Rolim C.O., Koch F.L., Westphall C.B., Werner J., Fracalossi A., Salvador G.S. A cloud computing solution for patient’s data collection in health care institutions. 2nd International Conference on eHealth, Telemedicine, and Social Medicine. 2010:95–99. 2010. ETELEMED’10, 2010. [Google Scholar]
- 103.Rousseau D.M., Sitkin S.B., Burt R.S., Camerer C. Not so different after all: a cross-discipline view of trust. Academy of Management Review. 1998;23:393–404. [Google Scholar]
- 104.Schmidt F.L., Oh I.-S., Hayes T.L. Fixed‐ versus random‐effects models in meta‐analysis: Model properties and an empirical comparison of differences in results. British Journal of Mathematical and Statistical Psychology. 2011;62(1):97–128. doi: 10.1348/000711007X255327. [DOI] [PubMed] [Google Scholar]
- 105.Schoorman F.D., Mayer R.C., Davis J.H. An integrative model of organizational trust: past, present, and future. Academy of Management Review. 2007;32(2):344–354. [Google Scholar]
- 106.Schreiber J.B., Stage F.K., King J. Reporting structural equation modeling and confirmatory factor analysis results: A review. The Journal of Educational Research. 2006;99(July/August (6)):323–337. [Google Scholar]
- 107.Siemsen E., Roth A.V., Oliveira P. Common method bias in regression models with linear, quadratic, and interaction effects. Organizational Research Methods. 2010;13(3):456–476. [Google Scholar]
- 108.Sharma L., Chandrasekaran A., Kenneth K., Boyer K.K., McDermott C.M. The impact of Health Information Technology bundles on hospital performance: An econometric study. Journal of Operations Management. 2016:25–41. pp. 41(2016) [Google Scholar]
- 109.Smith H.J., Milberg S.J., Burke S.J. Information privacy: Measuring individuals’ concerns about organizational practices. MIS Quarterly. 1996;20(2):167–196. [Google Scholar]
- 110.Smith J.P. Healthy bodies and thick wallets: The dual relation between health and economic status. Journal of Economic Perspective. 1999;13(2):144–166. [PMC free article] [PubMed] [Google Scholar]
- 111.Söllner M., Hoffmann A., Leimeister J.M. Why different trust relationships matter for information systems users. European Journal of Information Systems. 2016;25(3):274–287. [Google Scholar]
- 112.Stewart K.A., Segars A.H. An empirical examination of the concern for information privacy instrument. Information Systems Research. 2002;13(1):36–49. [Google Scholar]
- 113.Straub D., Boudreau M.C., Gefen D. Validation guidelines for IS positivist research. Communications of the Association for Information Systems. 2004;13(1):380–427. [Google Scholar]
- 114.Szajna B. Empirical evaluation of the revised technology acceptance model. Management Science. 1996;42(1):85–92. [Google Scholar]
- 115.Tang P.C., Ash J.S., Bates D.W., Overhege J.M., Sands D.Z. Personal Health Records: Definitions, Benefits, and Strategies for Overcoming Barriers to Adoption. Journal of the American Medical Informatics Association. 2006;13(2):121–126. doi: 10.1197/jamia.M2025. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 116.Venkatesh V. Determinants of perceived ease of use: Integrating control, intrinsic motivation, and emotion into the Technology Acceptance Model. Information Systems Research. 2000;11(4):342–365. [Google Scholar]
- 117.Venkatesh V., Morris M.G., Davis G.B., Davis F.D. User Acceptance of Information Technology: Toward a Unified View. MIS Quarterly. 2003;27(3):425–478. [Google Scholar]
- 118.Wagstaff A. Poverty and health sector inequalities. Bulletin of the World Health Organization. 2002;80(2):97–105. [PMC free article] [PubMed] [Google Scholar]
- 119.Wan J., Zheng P., Si H., Xiong N., Zhang W., Vasilakos A.V. An Artificial Intelligence Driven Multi-Feature Extraction Scheme for Big Data Detection. IEEE Access. 2019;7:80122–80132. [Google Scholar]
- 120.Wang Y., Kung L., Byrd T.A. Big data analytics: Understanding its capabilities and potential benefits for healthcare organizations. Technological Forecasting & Social Change. 2016 doi: 10.1016/j.techfore.2015.12.019. [DOI] [Google Scholar]
- 121.Wazid M., Das A.K., Khan M.K., Al-Ghaiheb A.a.-D, Kumar N., Vasilakos A.V. Secure Authentication Scheme for Medicine Anti-Counterfeiting System in IoT Environment. IEEE Internet of Things Journal. 2017;4(5):1634–1646. [Google Scholar]
- 122.Wazid M., Das A.K., Kumar N., Conti M., Vasilakos A.V. A Novel Authentication and Key Agreement Scheme for Implantable Medical Devices Deployment. IEEE Journal of Biomedical and Health Informatics. 2018;22(4):1299–1309. doi: 10.1109/JBHI.2017.2721545. [DOI] [PubMed] [Google Scholar]
- 123.Wu I.L., Li J.Y., Fu C.Y. The adoption of mobile healthcare by hospital’s professionals: an integrative perspective”. Decision Support Systems. 2011;51(3):587–596. [Google Scholar]
- 124.Xu H., Dinev T., Smith H.J., Hart P. Examining the formation of individual’s privacy concerns: Toward an integrative view. ICIS 2008 Proceedings. 2008:1–16. [Google Scholar]
- 125.Xu H., Luo X., Carroll J.M., Rosson M.B. The personalization privacy paradox: an exploratory study of decision making process for location-aware marketing. Decision Support Systems. 2011;51:42–52. [Google Scholar]
- 126.Xu Z. An empirical study of patients’ privacy concerns for health informatics as a service. Technological Forecasting & Social Change. 2019;143:297–306. [Google Scholar]
- 127.Yan Z., Zhang P., Vasilakos A.V. A security and trust framework for virtualized networks and software-defined networking. Security and Communication Networks. 2016;9(16):3059–3069. [Google Scholar]
- 128.Yang J.J., Li J., Mulder J., Wang Y., Chen S., Wu H., Wang Q., Pan H. Emerging information technologies for enhanced healthcare. Computers in Industry. 2015;69:3–11. [Google Scholar]
- 129.Yun H., Lee G., Kim D.J. A chronological review of empirical research on personal information privacy concerns: An analysis of contexts and research constructs. Information & Management. 2019;56:570–601. [Google Scholar]
- 130.Zriqat I.A., Altamimi A.M. Security and Privacy Issues in Healthcare Systems: Towards Trusted Services. International Journal of Advanced Computer Sciences and Applications. 2016;7(9):229–236. [Google Scholar]
- 131.Zhong R.Y., Newman S.T., Huang G.Q., Lan S. Big Data for supply chain management in the service and manufacturing sectors: challenges, opportunities, and future perspectives. Computers & Industrial Engineering. 2016;101:572–591. [Google Scholar]
- 132.Zhou M., Zhao L., Kong N., Campy K.S., Qu S., Wang S. Factors influencing behaviour intentions to telehealth by Chinese elderly: An extended TAM model. International Journal of Medical Informatics. 2019;126:118–127. doi: 10.1016/j.ijmedinf.2019.04.001. [DOI] [PubMed] [Google Scholar]
- 133.Zhou J., Cao Z., Dong X., Lin X., Vasilakos A. Securing m-healthcare social networks: challenges, countermeasures and future directions. IEEE Wireless Communications. 2013;20(4):12–21. [Google Scholar]
- 134.Zhou T. The impact of privacy concern on user adoption of location-based services. Industrial Management & Data System. 2011;111(2):212–226. [Google Scholar]