Abstract
Frequency estimation of physical symptoms for peoples is the most direct way to analyze and predict infectious diseases. In Internet of medical Things (IoMT), it is efficient and convenient for users to report their physical symptoms to hospitals or disease prevention departments by various mobile devices. Unfortunately, it usually brings leakage risk of these symptoms since data receivers may be untrusted. As a strong metric for health privacy, local differential privacy (LDP) requires that users should perturb their symptoms to prevent the risk. However, the widely-used data structure called sketch for frequency estimation does not satisfy the specified requirement. In this paper, we firstly define the problem of frequency estimation of physical symptoms under LDP. Then, we propose four different protocols, i.e., CMS-LDP, FCS-LDP, CS-LDP and FAS-LDP to solve the above problem. Next, we demonstrate that the designed protocols satisfy LDP and unbiased estimation. We also present two approaches to implement the key component (i.e., universal hash functions) of protocols. Finally, we conduct experiments to evaluate four protocols on two real-world datasets, representing two different distributions of physical symptoms. The results show that CMS-LDP and CS-LDP have relatively optimal utility for frequency estimation of physical symptoms in IoMT.
Keywords: Health privacy, Frequency estimation, Local differential privacy, Infectious disease analysis
1. Introduction
With the explosive development of Internet of Medical Things (IoMT), there have been various medical applications and services in a large number of mobile devices (e.g., smart phones and wearable devices) [1], [2], [3]. It is efficient and convenient for hospitals or disease prevention departments (i.e., the third party) to estimate the frequency of physical symptoms for mobile users by their devices so as to monitor and predict infectious diseases. For example, if disease prevention departments want to know potential spread range and speed of coronavirus disease 2019 (COVID-19) [4], it is secure for them to remotely estimate the frequency of typical symptoms of peoples by smart phones, including fever, cough and shortness of breath. The novel estimation model reduces the labor costs and improves the detection efficiency. Although human beings benefit from the estimation model in IoMT, users inevitably face leakage risks of disease information, especially when the third party are untrusted [5], [6]. Once disease information is leaked, it may cause a heavier psychological burden for the society and individuals.
In fact, health privacy has been one of the biggest concerns of not only individuals but also the whole society (e.g., European GDPR law) [7], [8], [9], [10], [11], [12]. Therefore, it is necessary to protect individuals’ health privacy when collecting and analyzing their symptoms. Differential privacy (DP) [13], [14] is a strong privacy metric in a central setting. It assumes that there is a trusted third party to collect and perturb symptoms from users and then share them with others. However, DP ignores that it is possible for the third party to threaten users’ health privacy, especially in IoMT. To this end, local differential privacy (LDP) [15] is proposed in the local setting. It requires that each mobile user should locally perturb his/her symptoms before sending to the third party and make them indistinguishable.
In recent years, there have been a series of works to design various protocols for frequency estimation of physical symptoms under LDP in both academia and industry [16], [17], [18], [19]. In the existing privacy protocols, physical symptom is defined as categorical data. For categorical data, it consists of three important components, i.e., encoding, perturbation and aggregation [20], [21], [22], [23], [24]. The first two components are operated by the user while the last one is executed by the third party. Most of perturbation mechanisms to guarantee privacy are based on the Randomized Response (RR) technique, in which reporting a real answer for a Boolean query is derived from a certain probability [25]. Wang et al. [24] surveyed the previous protocols and classified encoding methods into four types, including direct [26], histogram [22], unary [23], [27] and local hashing [20], [21], [24] encoding (i.e., DE, HE, UE and LHE). Protocols based on UE need higher communication cost, while those based on DE and HE have relatively lower accuracy. As a result, protocols based on LHE are a promising solution to balance computation complexity and data utility.
However, the previous protocols do not make full use of the widely applied data structures for frequency estimation of physical symptoms. Sketch is one of the most fundamental and most efficient data structures to estimate frequency for physical symptoms. In general, it uses a small vector to index the position of a symptom by a certain number of hash functions, which saves space but faces possible conflict. There are some basic and classic sketches, such as Count Sketch (CS) [28], Count-Min Sketch (CMS) [29], Fast-AGMS Sketch (FAS) [30] and Fast-Count Sketch (FCS) [31]. The focus of the paper is on how to design the sketch-based protocols for frequency estimation of physical symptoms satisfying local differential privacy. If so, it is convenient for others to directly apply the proposed protocols to estimate the frequency of physical symptoms.
There are two main challenges to solve the above problem. The first one is that the existing private protocols cannot be directly used to perturb query result by sketches. The reasons are that (i) perturbation and aggregation of symptoms are executed by the user and the third party, respectively. It implies that only the RR technique can be leveraged; and (ii) hash functions used in the sketches need to stay the same implying that the existing encoding methods (e.g., DE, HE and UE) are not applicable. The second one is that the designed private sketches should satisfy two important properties, including unbiased estimation and local differential privacy. In other words, it needs to balance privacy guarantee and utility of perturbed data.
To address the above challenges, we make full use of LHE and RR. In brief, we leverage the sketch vector to implement encoding of physical symptoms and then perturb it by RR to achieve privacy guarantee. At first, we propose two CMS- and FCS-based protocols, namely CMS-LDP and FCS-LDP to guarantee privacy. Then, we propose two CS- and FAS-based protocols, namely CS-LDP and FAS-LDP to ensure privacy. In particular, the formers utilize perturbation mechanism of optimal local hashing (OLH) in [24], while the latter directly use RR to perturb each entry of the sketch vector. Finally, we do other operations to make sure that the protocols satisfy unbiased estimation. It is noted that our protocols only increase computation cost rather than space overhead. This is consistent with the initial purpose, i.e., space save. To the best of our knowledge, there are few works to utilize the sketch under LDP to estimate the frequency of symptoms. The contributions of this paper can be summarized as follows:
-
•
We formulate the problem of designing sketches under LDP by mathematical definitions and strong privacy metric to estimate the frequency of physical symptoms in IoMT.
-
•
We propose four different protocols for frequency estimation of symptoms with privacy protection, including CMS-LDP, FCS-LDP, CS-LDP and FAS-LDP. We also demonstrate that all of the protocols satisfy two important properties, including unbiased estimation and LDP. We also analyze the variance of frequency estimation in four protocols.
-
•
We present two approaches to implement universal hash functions. We also evaluate and compare the proposed protocols on two real-world datasets, representing two different distributions of physical symptoms.
The rest of this paper is organized as follows. Section 2 surveys related work about privacy protection in IoMT. Section 3 introduces the preliminaries and gives problem definitions. Section 4 proposes four different protocols for sketches under LDP to estimate the frequency of symptoms. Section 5 analyzes unbiased estimation, privacy guarantee and variance. Section 6 presents two methods to implement universal hash functions. Section 7 evaluates proposed protocols on real datasets. Finally, Section 8 concludes this paper.
2. Related work
2.1. Health privacy protection in IoMT
In IoMT, there are vast amounts of users’ healthy information generated by various mobile devices every day. However, the information is left from mobile users and may be faced with leakage risk from untrusted data collectors or data adversaries [6]. In order to guarantee privacy, there have been a number of protection techniques, including identification, anonymity and differential privacy [5], [7], [14]. In detail, identification technique utilizes authentication mechanism for each mobile user, who must login the system by his/her identity. On the other hand, data collectors use perturbation techniques (e.g., -anonymity [32], -diversity [33] and DP [13]) to perturb raw data from mobile users. These techniques provide a certain degree of privacy protection in some specified scenes.
However, these techniques are not fully suited to applications in IoMT due to their respective shortcomings. Identification and anonymity cannot offer enough privacy protection, while DP usually assumes that the third party is trusted. That is, the third party does not illegally leak users’ health information. Unfortunately, it does not hold in some real environments of IoMT. The reason is that users cannot know the receivers of their healthy information in the local setting so that they do not trust them. In order to overcome the disadvantages, local differential privacy [15] has been proposed to protect private information of each user against the threat from the untrusted third party. Both academical researchers and industrial engineers focus on how to achieve local differential privacy from theory and application.
2.2. Local differential privacy
Different from DP, LDP has higher privacy requirement in a local setting, which requires probability limit between any two values, instead of any two datasets in DP [15]. To this end, the existing mechanisms of DP cannot be fully applied to LDP, including the Laplace mechanism [34] and the exponential mechanism [35]. In order to implement LDP, there have been a number of works to design proper mechanisms [16], [17], [18], [19]. Most of them leveraged the Randomized Response (RR) mechanism [25] or its refinements. RR reports a random answer derived from a certain amount of probability for a Boolean question. For categorical data, Kairouz et al. [36], [37] proposed an extremal privatization mechanism (-RR), which is universally optimal in the low and high privacy regimes. For ordinal data, the value is firstly encoded to a binary one and then perturb it by RR [17], [38], [39]. In general, the proposed algorithms need to satisfy both unbiased estimation and LDP. In addition, these perturbation privacy mechanisms are widely applied to various scenes, including heavy hitter identification, itemset mining, marginal release, data mining, medical analysis and infectious disease prediction [40].
In the industry, there have been a lot of applications to satisfy local differential privacy. RAPPOR is the first product from Google to collect users’ data and ensure privacy [27]. The user firstly encodes his/her data by a special data structure called Bloom filter and then perturbs the encoded output by the randomized response mechanism. The third party collects and decodes perturbed data from the users to get statistical information. In 2017, Apple [41] published a white paper to propose efficient and scalable algorithms satisfying local differential privacy. Microsoft [38] also presented new algorithms with local differential privacy to estimate mean and histogram for telemetry data.
2.3. Frequency estimation under LDP for physical symptoms
Frequency estimation under LDP for physical symptoms is an efficient and convenient way for infectious disease prediction. There have been a few of works to design effective mechanisms for different types of health information, including categorical (e.g., sex and symptoms), ordinal (e.g., age) [36], [37], [40], [42]. The main objective of the existing mechanisms is to maximize the utility and reduce communication cost and computation complexity.
Bassily et al. [21] proposed efficient mechanisms by utilizing Random Matrix Projection. Running time of the third party and the user is and , respectively. Meanwhile, the estimation error is with high probability where is the number of users and is the size of domain. They also proposed improved algorithms, in which server time is and user time is [20]. Bun et al. [22] presented an algorithm called PrivateExpanderSketch, which achieved optimal worst-case error as a function of all possible parameters. Wang et al. [24] introduced a framework to analyze all the previous mechanisms for frequency estimation under LDP. They also proposed an Optimal Local Hashing (OLH) to estimate the frequency with better utility. Different from the previous environment with only an attribute, Qin et al. [23] estimated frequency over set-valued data under LDP. However, to the best of our knowledge, there are few works to combine sketch under LDP to estimate the frequency of physical symptoms in IoMT. Therefore, the focus of this paper is to solve the problem.
3. Preliminaries and problem definition
As aforementioned, the focus of the paper is on frequency estimation of physical symptoms in IoMT. There are two key roles, i.e., an untrusted third party and a large number of mobile users. The third party collects perturbed health information from the users. In the following section, we formulate the frequency estimation problem in the context of local differential privacy.
3.1. Preliminaries
Suppose that there are a set of users denoted by . Each user has a symptom . Then, is defined as a set of symptoms from users. The domain of elements in is with size . An untrusted third party plans to collect statistical information of users’ symptoms. Assume that the untrusted third party has known the domain . Each element in is generalized to an integer . For example in Fig. 1, the domain consists of types of symptoms of COVID-19, such as fever, cough and shortness of breath. Each symptom is labeled as an integer (e.g., fever is labeled by ). Therefore, in the following section, we have .
Fig. 1.
Symptoms of COVID-19.
Here, we focus on the frequency estimation of physical symptoms as follows:
Definition 1 Frequency Estimation of Symptoms [39] —
A query for frequency estimation of some symptom is to compute the frequency of users whose symptom is the same with . Formally, for any ,
(1) Obviously, the range of is .
However, in infectious disease prediction, it is not necessary and impossible to count accurate frequency estimation for physical symptoms. For example, if some disease prevention department wants to estimate the speed or range of COVID-19 by the number of patients with specified symptoms (e.g., fever, cough or shortness of breath), there is no need for the department to get the accurate count for each symptom. What is more, it is not realistic to spend a large amount of labor cost in dealing with it. Thus, an approximate frequency estimation is proposed as follows:
Definition 2 ()-Approximate Frequency Estimation of Symptoms [39] —
A query is to solve the problem of ()-approximate frequency estimation of symptoms if and only if for any symptom , satisfies the following requirement:
(2) where represents the expected error and is the confidence probability.
Unfortunately, the third party may be untrusted because that he/she possibly utilizes health information of users to get illegal profit. Therefore, the users have to perturb their information so as to avoid privacy leakage. Differential privacy [13], [14] is the most common and strong privacy protection metric, which is usually suited for the central setting. Different from DP, local differential privacy is proposed in the local setting, in which it assumes that the third party is untrusted. This means that before the users send their symptoms, perturbation of symptoms should satisfy the following privacy measurement:
Definition 3 Local Differential Privacy [15] —
A sanitized algorithm satisfies -local differential privacy if and only if for any pair of input values and for any output , we have
(3) where denotes the set of all possible outputs of the algorithm and is privacy budget.
represents the strength of privacy protection. The lower value of corresponds to the stronger privacy protection. With the same as DP, LDP has also the composition properties as follows.
Lemma 1 Sequential Composition [43] —
Assume that each privacy algorithm satisfies -local differential privacy. A group of applied to the same dataset satisfy -local differential privacy.
Lemma 2 Parallel Composition [43] —
Assume that each privacy algorithm satisfies -local differential privacy. A group of applied to a set of disjoint datasets satisfy -local differential privacy.
In the algorithms designed by the paper, we will make full use of the composition properties of local differential privacy.
3.2. Private framework
In order to solve the frequency estimation problem under LDP for symptoms, the proposed mechanism should satisfy the privacy measurement as follows:
Definition 4 Frequency Estimation of Symptoms under LDP —
A sanitized protocol for frequency estimation of symptoms satisfies -local differential privacy if and only if , in which each is a local random processor that satisfies -local differential privacy, and is some post-processing function.
Based on the above definition, the key functions are the local random processor and the post-processing function . Each user executes the local random processor, while the third party executes the post-processing function. Furthermore, Wang et al. [24] surveyed the previous work and concluded that a protocol for frequency estimation under LDP generally consists of the following steps:
-
•
Encoding. This operation is executed by the user. In detail, input of the user is generally encoded as a histogram, a vector [27], a single bit [21], or an integer [24] by encoding and decoding algorithms or hash functions.
-
•
Perturbing. The mechanism is also executed by the user. Meanwhile, the perturbed mechanism should satisfy -local differential privacy. The input of is the output of . Therefore, in Definition 4 is .
-
•
Aggregating. The operation is executed by the third party. At first, the third party receives data from users, which is perturbed with the combination of and . Then, he/she aggregates the data and extracts approximate frequency estimation.
Fig. 2 shows the concrete operations and interactions between mobile users and the third party. It is obvious to see that users need to encode and perturb their symptoms locally, while the third party aggregates perturbed data. As a result, these operations increase extra overhead for users, including computation, communication and storage. To this end, it is necessary to make full use of the existing data structure named sketch to decrease the overhead.
Fig. 2.
The framework for frequency estimation of symptoms under LDP.
3.3. Problem formulation
In order to solve the approximate frequency estimation of categorical data (e.g., physical symptoms), Charikar et al. [28] firstly proposed an algorithm by using a special data structure, i.e., Count Sketch, which achieved good space bounds. After that, the refined versions were proposed, such as Fast-AGMS Sketch [30], Count-Min Sketch [29] and Fast-Count Sketch [31]. However, to the best of our knowledge, there are few works to design the new data structure Sketch under LDP to solve the approximate frequency estimation of physical symptoms. In the following sections, we propose improved protocols based on Count Sketch, Fast-AGMS Sketch, Count-Min Sketch and Fast-Count Sketch, which satisfy unbiased estimation, i.e., and local differential privacy. In addition, we also compare the proposed protocols by experiments.
4. Protocols for frequency estimation of symptoms under LDP
In this section, we propose four novel protocols to solve the approximate frequency estimation of physical symptoms under LDP. These protocols are based on CS, FAS, CMS and FCS. We will analyze unbiased estimation and privacy protection of proposed protocols in the next section.
Under no privacy preservation, the third party receives physical symptoms and uses a small vector to count the frequency of each element in , while users do nothing. However, in order to protect privacy, the user should send perturbed symptoms rather than raw values. Therefore, the user needs to generate a small vector locally and then send it to the third party. Finally, the third party aggregates these vectors and derives the full sketch.
4.1. Protocol CMS-LDP
CMS is a simple and effective data structure, which was proposed by Cormode et al. [29]. For a frequency estimation query , its values by CMS is with a probability , in which is the real frequency except . Here, we propose corresponding protocols based on optimal local hashing in [24] to implement CMS under local differential privacy.
Algorithm 1 shows a protocol CMS-LDP for privacy estimation of symptoms under LDP. The protocol consists of four key components. The first one is an initial process, in which and are computed by the input parameters and (line ). represents the domain of universal hash functions, while is the number of hash functions. Then, each user calls to report the perturbed record to the server-side (line ). Next, Line implements the key component, namely Sketch-CMS-LDP. The last one implements the query of server-side (line ). By the above four parts, the algorithm solves the approximate frequency estimation problem of physical symptoms.
Each user executes Algorithm 2 to implement the function of Perturb(Encode ()) in Section 3.2. Algorithm 2 utilizes an existing technique, namely -Randomized Response (-RR), to ensure -local differential privacy, which was designed by Kairouz et al. [37]. In detail, Algorithm 2 firstly implements by universal hash function to map the input into a -length bit array in line . Then, a -RR technique is used to perturb the output of in line . Finally, the user returns the result to the server-side.
After the third party receives perturbed symptoms from users, he/she computes a data structure, namely Sketch-CMS-LDP by Algorithm 3. Compared to CMS, our proposed mechanism has extra operations, i.e., Line . Sketch-CMS-LDP firstly generates an initial sketch, which is a multidimensional array in line . Then, all arrays from users are added to the sketch in line , which is the same with CMS. Finally, Line is to ensure unbiased estimation of CMS-LDP, which will be proved in Section 5.1.
Algorithm 4 gets the approximate estimation for each frequency query , which is executed by the third party. The combination of Algorithms 3 and 4 implement the function of in Section 3.2. For each query , the algorithm chooses the minimum of values, each of which is from an array . The position of each value in the array is decided by hash function and . By Algorithm 14, we solve the problem of frequency estimation under local differential privacy.
For each user in the client-side, the time complexity is and the space complexity in is . For in the server-side, the time complexity is and the space complexity is . Besides, the communication overhead between each user and the server is . Thus, for the third party, our proposed protocol does not increase the space overhead. Section 5.1 will analyze the proposed algorithms in terms of the error bound, unbiased estimation and local differential privacy.
4.2. Protocol FCS-LDP
Thorup et al. [31] proposed a refined version of Count-Min Sketch, namely Fast-Count Sketch (FCS). Compared with CMS, FCS uses a family of -universal hash functions, instead of -universal hash function.
The protocol to implement Fast-Count Sketch under local differential privacy, namely Algorithm , is similar with Algorithm 1. also consists of three important components, i.e., , and . Different from , replaces -universal hash functions with - universal hash functions in line in Algorithm 1. Besides, , and have the same operations with Algorithm , and , respectively. Here, we do not repeat the same algorithms. Meanwhile, these algorithms have the same time and space complexity with Algorithm 14 for each user and the third party.
4.3. Protocol CS-LDP
Among all of various formats of the special data structure called sketch, Count Sketch was firstly proposed in 2002 [28]. The data structure is generally used to point query, range query, inner product query and so on. Compared with Count-Min Sketch, CS needs higher space cost, i.e., . Meanwhile, CS also satisfies unbiased estimation and the value for a frequency estimation query about is with a confidence probability . In the following, we will introduce algorithms to implement CS with LDP.
In Algorithm 5, we describe the overview of protocol CS-LDP to implement CS under LDP. It consists of four key parts, i.e., initialization, perturbation in client-side, construction of sketch and frequency estimation in server-side. In the initial process (line ), it requires hash function pairs . Hash function maps some symptom into -length bits in which c is some constant, while function maps some input value into . Both two classes of hash functions are independent with each other. Compared with -length bits of hash function in Algorithm 1, CS-LDP needs more space cost. Then, each user executes to perturb his/her data (line ), which implements the function of . Next, the third party constructs a special data structure, namely Sketch-CS-LDP, to collect data from users by (line ). Finally, for each frequency estimation , the third party calls to compute the result (line ).
Before each user sends his/her symptom to the third party, Algorithm 6 is executed. firstly initializes a multidimensional integer array , i.e., (line ). The array only consists of two elements, i.e., and . Then, because of the property of sequential composition of local differential privacy, it computes smaller privacy parameter for each hash function (line 2). Next, the specified position of each row in is set as (line ), which implements the function of . For each entry in array , it uses Randomized Response (RR) [25] to ensure -local differential privacy (line ), which implements the function of . At last, the result is returned to the third party.
After the third party receives perturbed symptoms from users, he/she uses Algorithm 7 to get the data structure Sketch-CS-LDP. Firstly, initializes a -integer array, i.e., (line ). Then, line 2 is to compute a parameter , which is used to ensure unbiased estimation due to randomized response. Since data from perturbed mechanism is biased, it needs to be calibrated. Therefore, Algorithm 7 adjusts the data from each user (line ) to get the estimated frequency of each entry in each array . Finally, all adjusted arrays are added to sketch (line ). In Section 5.2, we will prove unbiased estimation and local differential privacy of our proposed protocol CS-LDP.
Algorithm 8 is used to answer the frequency estimation for the third party. The combination of Algorithms 7 and 8 implements the function of . We use function to choose a proper value from the candidates as the final estimation for , rather than function . Charikar et al. [28] has demonstrated that function is sensitive to outliers, while is robust. By Algorithm 58, we solve the problem of frequency estimation with local differential privacy.
Compared with CMS-LDP, CS-LDP needs the higher time and space cost, and has the shaper bound for the frequency estimation. For each user in , the time cost is due to sampling each entry of the matrix by Randomized Response, while the space cost is . For the third party, the cost of time and space is and in , respectively. The cost of time and space is and in , respectively. Therefore, the total time cost for the third party is , while the total space cost is .
4.4. Protocol FAS-LDP
Fast-AGMS Sketch (FAS) is a refined version of Count Sketch [30], which guarantees logarithmic-time sketch update and tracking costs. The only difference between Count Sketch and Fast-AGMS Sketch is that the latter replaces -universal hash functions of the former with -universal hash functions.
Protocol to achieve Fast-AGMS Sketch under local differential privacy is similar with CS-LDP. The only change is that a set of hash functions, namely , are chosen independently from a -universal family of hashing functions mapping to . Besides, other mechanisms, i.e., , and in client-side and server-side are the same with , and , respectively. As a result, these algorithms have the same time and space cost with Algorithms 58 for each user and the third party.
5. Theory analysis of protocols
The protocols that implement the approximate frequency estimation of physical symptoms under LDP must satisfy two fundamental requirements, i.e., unbiased estimation and local differential privacy. In the section, we will demonstrate that our proposed protocols satisfy two requirements. Besides, we discuss the variance of protocols.
5.1. CMS-LDP and FCS-LDP
For the proposed protocols, the most important property is to satisfy local differential privacy. We prove that protocol CMS-LDP satisfies the requirement as follows:
Theorem 3
Protocol CMS-LDP satisfies -local differential privacy.
Proof
Each user utilizes mechanism in CMS-LDP to encode and perturb his/her symptom . According to Eq. (4), for two different value and , it satisfies the follow equation:
Therefore, for each hash function, perturbation satisfies -local differential privacy. Because that there are hash functions for the same symptom , the combination of hash functions satisfy -local differential privacy for each user according to Lemma 1. On the other hand, the third party receives perturbed symptoms from all users. Since records between different users are disjoint, it satisfies -differential privacy for all perturbed symptoms according to Lemma 2. ■
Theorem 4
For each -universal hash function in protocol CMS-LDP, it satisfies unbiased estimation for frequency estimation of symptoms after . Meanwhile, its variance is , in which .
Proof
For each hash function , the third party receives reported symptoms from all users. Let any possible output and the set of symptoms that are hashed to by . Then, the probability that any symptom in is perturbed to is . That is, for any , we have
and
For another input value , it is still possibly mapped to . Let the probability that is mapped to . In line of mechanism , the third party makes the extra operations for the raw records. Thus, the probability is computed by as follows:
In mechanism , we get the final sketch by line . The expectation that the number of elements in which are mapped to is
where is the number of elements in . Therefore, for each -universal hash functions, protocol CMS-LDP satisfies unbiased estimation. The variance is
By the above proof, CMS-LDP satisfies unbiased estimation and LDP. Since protocol FCS-LDP is similar with CMS-LDP except for hash functions, FCS-LDP also satisfies unbiased estimation and local differential privacy. Besides, it has the same variance. The corresponding proof is omitted.
5.2. CS-LDP and FAS-LDP
Here, we firstly prove that protocol CS-LDP satisfies local differential privacy as follows:
Theorem 5
Protocol CS-LDP satisfies -local differential privacy.
Proof
Assume that there are two users and . Both of them have different input values and and the same output . For each pair of hash functions, the third party receives two perturbed arrays and from these two users. Because that all of hash functions and are independent with each other, we have
The reason for is presented as follows. In detail, and . Each entry in is derived from , in which is sampled from Eq. and only an entry is with position decided by hash value . is similar with . In Eq. , only two entries in are different from two entries in , while the others have the same probability. Therefore, Eq. is derived to Eq. .
For Eq. , there are two different cases, i.e., and . For the first case in which , we have
For the second case in which , we have
Assume that and . Then, , , and . If , then , , and . Therefore, according to Eq. , we have
in which . Therefore, for each pair of hash functions in the above cases, it satisfies -local differential privacy. Since there are hash functions to perturb the same symptom, of each user satisfies -local differential privacy according to Lemma 1. Since records between different users are disjoint, it satisfies -differential privacy for all perturbed records according to Lemma 2. ■
Theorem 6
Protocol CS-LDP satisfies unbiased estimation. For any value , the variance of is .
Proof
Protocol CS-LDP satisfies unbiased estimation if and only if . Assume that there is a fixed constant . For any , is denoted as follows:
Meanwhile, assume that there is a perturbation function , namely, Eq. . Then, is equal to
For the expected value of , we have
For , it is equal to . Since hash functions are independent with each other, we have for . Therefore, .
For the variance of , is derived as follows:
Therefore, we complete the proof. ■
Since protocol FAS-LDP is similar with CS-LDP except for hash functions, FAS-LDP also satisfies unbiased estimation and local differential privacy. Besides, it has the same variance. The corresponding proof is omitted.
6. Implementation of universal hash functions
In the section, we introduce the implementation of -universal hash functions. In detail, we propose two different methods to implement universal hash functions. That is, CW-Trick hashing is used to the case in which while Tabulation based hashing is used to .
6.1. Universal hash function
In the protocols proposed by Section 4, the most important component is -universal hash functions, which are defined as follows:
Definition 5 -universal Class of Hash Functions [44] —
A class of hash functions from into is a -universal class of hash functions if for any distinct and any possibly identical ,
(6) where is an positive integer.
According to Definition 5, a large number of values can be hashed to a relatively small set of keys. Meanwhile, there may be collisions, in which two different values are hashed to a key. Parameter is the factor that influences the collision. For example, as parameter increases from to , the probability of collision decreases from to . Here, we focus on how to design the proper hash functions that satisfy Definition 5. In the following section, we present two different implementations for -universal hash functions, i.e., CW-Trick and Tabulation based hash functions.
6.2. CW-trick hashing
The first method for -universal hash functions is implemented by the following equation:
| (7) |
where is a prime that is greater than value and is picked randomly from . This equation was proposed by Wegman et al. [44]. It is obvious to see that this method is very simple and easy to implement. However, it has a disadvantage, especially when is very large. That is, if is an arbitrary prime, this method is fairly slow because the ‘mod ’ is relatively slow. In order to solve the problem, Thorup et al. [31] proposed a simple method, namely CW-trick, in which is a so-called Mersenne prime of the form . In our experiments, we will use . The CW-Trick hashing is used to .
6.3. Tabulation based hashing
If CW-Trick hashing is used to , the time is slow. Thorup et al. [31] proposed another method, namely Tabulation based hashing, to implement -universal hash functions. They compared their method with CW-trick in terms of running time, which shows that the former is faster than the latter by at least a factor of . However, the weakness of Tabulation based hashing is that it requires large pre-computed tables and thus needs the extra space to store.
We firstly introduce Theorem 2.3 in [31] to compute hash value of by -universal hash functions.
Theorem 7 Theorem 2.3 in [31] —
There are any characters . is a generator matrix, which satisfies that any square sub-matrix has full rank over prime field , where is an odd prime. are additional characters . Then, hash function of is
(8) is a -universal hashing function if and are independent -universal hash functions into .
In our experiments, assume that value of each user has 32 bits and each character has bits.1 Therefore, and . In detail, value can be divided into two sub-values with 16-bits, i.e., and as the following equation:
Besides, -universal hash functions and are implemented by tabulation based hashing. That is, we use precomputed tables to replace hash functions and . That is, Eq. (8) is changed as
| (9) |
where is a fully random table of size with values from . Tabulation based hashing thus takes time and space .
7. Experimental evaluation
In the section, our main goal is to study (1) the impact of different parameters on data utility; and (2) the application of protocols for frequency estimation of physical symptoms. The experiments are performed over two real datasets, representing two different distributions of symptoms.
7.1. Experimental setting
The evaluation is performed on a desktop computer, which has G of RAM and Inter(R) Pentium(R) CPU P6200 running Windows operating system. All of protocols are implemented by Python. All of testing datasets are real.
Parameter settings. The number of hash function is and we will choose hash function pairs from them. The implementation of hash functions is based on CW-Trick and Tabulation-based hashing in Section 6. The values of and depend on error and confidence probability . We mainly evaluate four protocols on different values of privacy budget , error and confidence probability .
Datasets. We use two real datasets to evaluate our protocols, including WISDM and BMBD. We select an attribute to estimate its frequency in these two datasets, which represent two different distributions of physical symptoms. The datasets are presented as follows:
-
•
WISDM [45]. The dataset is collected from the accelerometer and gyroscope sensors of a smart-phone and smart-watch as subjects. It is about diverse activities of daily living and has records. We select attribute Activity from seven attributes to estimate its frequency. There are activities, including walking, jogging, Sitting and so on.
-
•
BMBD [46]. The dataset is collected from a public website Bixi,2 which offers bike rental service. It contains bike share information for Bixi Monetreal from to , including start and end station ID of a trip. We select attribute Start_station_code from six attributes to estimate its frequency.
Table 1 shows the statistical information of attribute Activity in WISDM and Start_station_code in BMBD. The distributions of these two attributes are different. Activity is uniformly distributed, while Start_station_code is loose. Therefore, we use them to evaluate our protocols for different distributions of symptoms.
Table 1.
Statistical information of datasets.
| WISDM | BMBD | |
|---|---|---|
| Activity | Start_station_code | |
Evaluation Metrics. We evaluate the top- frequent elements in by RE and MSE, which have the most frequencies [47], [48], [49]. The concrete metrics are presented as follows:
-
•Relative Error (RE). The metric is usually used for SUM/ COUNT/AVG queries and measures how large the error is relatively to the true answer for each query by the following equation:
Furthermore, for the top- elements, we evaluate them by the average and median value of relative errors, i.e., ARE and MRE.(10) -
•Mean Square Error (MSE). It is used to measure the estimation accuracy by the average of the squared errors, namely,
where is the true frequency of users taking value .(11)
7.2. Experimental results
In the following section, we show the impact of three key parameter , and in terms of RE and MSE for different datasets. Then, we show the effectiveness of protocols by estimating top- in different cases. In order to reduce the error, we repeat each experiment times. Since frequency of different records in BMBD is different, we will consider two cases, including top- and top-. That is, we estimate and elements with the most frequency, respectively.
7.2.1. Impact of parameter
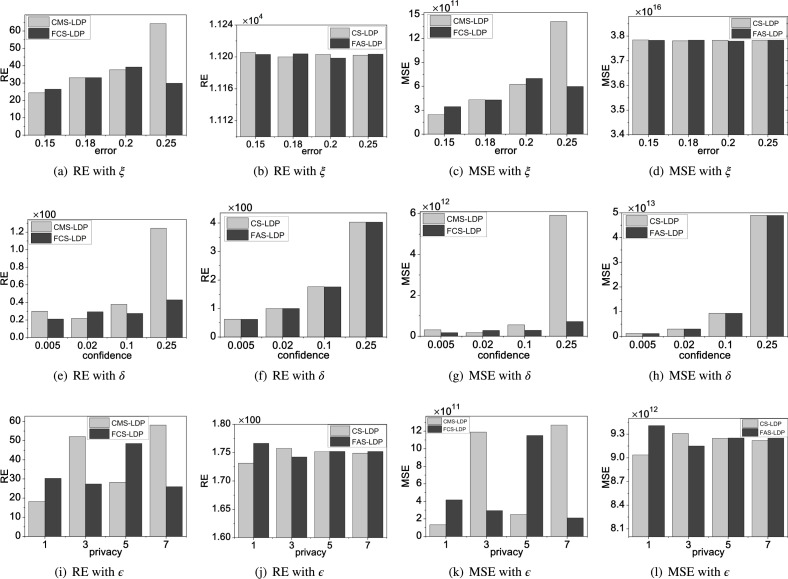
In order to analyze impact of parameter , we firstly set the parameters. That is, confidence probability is 0.1 and privacy budget is . of WISDM is while that is for BMBD.
Figs. 3(a)–3(d) show RE and MSE of WISDM by different protocols, including CMS-LDP, FCS-LDP, CS-LDP and FAS-LDP. It is intuitive to see that RE and MSE in CMS-LDP and FCS-LDP increase as increases from 0.15 to 0.25 in Fig. 3, Fig. 3. This is consistent to CMS and FCS without LDP. This implies that addition of privacy preservation does not change influence of parameter . However, Fig. 3, Fig. 3 show that has little impact on CS-LDP and FAS-LDP, since RE and MSE do not change as increases from 0.15 to 0.25.
Fig. 3.
Results for Top- of WISDM.
Figs. 4(a)–4(d) and 5(a)–5(d) show RE and MSE of BMBD in two different cases by four private protocols. Compared to WISDM, it has the opposite results for protocol CMS-LDP and FCS-LDP. That is, with increasing from 0.004 to 0.00571, RE and MSE decrease. The key factor for this opposition is size of mapped by hash function , in which the size in BMBD is far greater than that in WISDM. Thus, perturbation for privacy preservation is the dominant factor for BMBD, while conflict probability is relatively less. As size of decreases, it leads to less expected error. Fig. 4, Fig. 4 and Fig. 5, Fig. 5 show that RE and MSE of BMBD by CS-LDP and FAS-LDP have no much difference with increasing. That is, has little impact on CS-LDP and FAS-LDP.
Fig. 4.
Results for Top- of BMBD.
Fig. 5.
Results for Top- of BMBD.
Therefore, the impact of on CMS-LDP and FCS-LDP depends on the size of . In contrast, it has little impact on CS-LDP and FAS-LDP.
7.2.2. Impact of parameter
Here, we consider the impact of parameter for four LDP protocols. The expected error is 0.18 for WISDM, while that is 0.005 for BMBD. Privacy budget is . The range of is .
For WISDM, Figs. 3(e)–3(h) show RE and MSE of four protocols. It is intuitive to find that RE and MSE increase with increasing. This implies that adding the number of hash functions can efficiently improve the accuracy for perturbed data. Meanwhile, it needs more time for the users and the third party. From Figs. 3(e)–3(h), RE and MSE are fast increasing once is greater than 0.25. Therefore, is a good choice.
For BMBD, Figs. 4(e)–4(h) and 5(e)–5(h) show RE and MSE of four protocols. Two cases have the similar results. It is easy to see that the impact of on CMS-LDP and FCS-LDP is counter to that on CS-LDP and FAS-LDP. In detail, RE and MSE of CMS-LDP and FCS-LDP decrease as increases while those of CS-LDP and FAS-LDP have the opposite results. This means that it should add the number of hash functions for FCS-LDP and FCS-LDP and decrease the number for CS-LDP and FAS-LDP.
Thus, the impact of on CS-LDP and FAS-LDP is consistent, while that on CMS-LDP and FCS-LDP is changing in different datasets.
7.2.3. Impact of parameter
In order to analyze the impact of , for WISDM is 0.18, while that is 0.005 for BMBD. Confidence probability is 0.1. The range of privacy budget is .
For WISDM, Figs. 3(i)–3(l) show RE and MSE of four protocols. Fig. 3, Fig. 3 show that RE and MSE of CMS-LDP and FCS-LDP do not decrease with increasing. In contrast, they have big fluctuation. Compared to those for BMBD in Figs. 4(i), 4(k), Fig. 5, Fig. 5, the possible reason is the size of . For CS-LDP and FAS-LDP, the accuracy increases as privacy budget increases. However, it does not change once privacy budget exceeds some threshold (e.g., in Fig. 3, Fig. 3).
For BMBD, Figs. 4(i)–4(l) and 5(i)–5(l) show RE and MSE of four protocols. We can find that top- and top- have the same results about RE and MSE. For four protocols, both of RE and MSE decrease as privacy budget increases. In other words, the increase of RE and MSE in CMS-LDP and FCS-LDP is fast, while that in FCS-LDP and FAS-LDP is not obvious. Once privacy budget exceeds some threshold (e.g., in Fig. 4(j)), RE and MSE have little change for CS-LDP and FAS-LDP. The threshold is for CMS-LDP and FCS-LDP.
According to the above results, we can derive that privacy budget has the important impact on four protocols. Meanwhile, once exceeds some threshold, the impact can be ignored.
7.2.4. Protocol applications in IoMT
By our experiments, we analyze two different distributions of symptoms for some infectious disease in IoMT. That is, the symptoms are uniformly distributed in case (i), while those are loose in case (ii). Generally speaking, we have two important findings in Fig. 3, Fig. 4, Fig. 5. The first one is that the utility of CMS-LDP and FCS-LDP is greater than that of CS-LDP and FAS-LDP. Since the time of CMS-LDP and FCS-LDP is smaller than that of CMS-LDP and FAS-LDP, Therefore, CMS-LDP and FCS-LDP are relatively optimal in terms of utility and computation overhead. The second one is that protocol CMS-LDP is not absolutely better than FCS-LDP, and vice versa. Furthermore, different distributions of symptoms have an important influence for the choices of different parameters, including , and . In case (i), FCS-LDP has better stability than CMS-LDP as different parameters change. In case (ii), CMS-LDP and FCS-LDP have the similar changes. Parameter , and should be as small as possible to maximize the utility.
8. Conclusions
The focus of the paper is on how to estimate the frequency of symptoms under local differential privacy for infectious disease analysis in IoMT. Based on basic sketches, this paper has proposed four protocols, including CMS-LDP, FCS-LDP, CS-LDP and FAS-LDP. We have proved that our proposed protocols satisfy two important properties, i.e., unbiased estimation and local differential privacy. Meanwhile, we have presented the variance of four protocols. Through empirical analysis, CMS-LDP and CS-LDP are relatively optimal protocols for frequency estimation of physical symptoms in IoMT. We plan to design better encoding methods to reduce the computation complexity and perturbation techniques to improve the accuracy of our protocols in the future.
CRediT authorship contribution statement
Xiaotong Wu: Conceptualization, Methodology, Formal analysis, Writing - original draft. Mohammad Reza Khosravi: Conceptualization, Methodology, Writing - original draft. Lianyong Qi: Software, Data curation, Validation. Genlin Ji: Writing - review & editing, Computation resources, Project administration. Wanchun Dou: Supervision, Writing - review & editing, Project administration. Xiaolong Xu: Conceptualization, Writing - review & editing, Investigation, Validation, Supervision.
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgments
Our thanks to the reviewers for their constructive comments and suggestions to improve the quality of the manuscript. This work was supported in part by the National Natural Science Foundation of China under Grant No. 41971343.
Here, the length of is not constant. If there are a large number of elements in , the length can be 64 or more bits and thus and .
References
- 1.Xu X., Liu X., Xu Z., Dai F., Zhang X., Qi L. Trust-oriented iot service placement for smart cities in edge computing. IEEE Internet Things J. 2019 [Google Scholar]
- 2.Zhang Y., Yin C., Wu Q., He Q., Zhu H. Location-aware deep collaborative filtering for service recommendation. IEEE Trans. Syst. Man Cybern.: Syst. 2019:1–12. [Google Scholar]
- 3.Zhang Y., Cui G., Deng S., Chen F., Wang Y., He Q. Efficient query of quality correlation for service composition. IEEE Trans. Serv. Comput. 2018:1. [Google Scholar]
- 4.Wu F., Zhao S., Yu B., Chen Y.-M., Wang W., Song Z.-G., Hu Y., Tao Z.-W., Tian J.-H., Pei Y.-Y., Yuan M.-L., Zhang Y.-L., Dai F.-H., Liu Y., Wang Q.-M., Zheng J.-J., Xu L., Holmes E.C., Zhang Y.-Z. A new coronavirus associated with human respiratory disease in China. Nature. 2020;579:265–269. doi: 10.1038/s41586-020-2008-3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Deep S., Zheng X., Jolfaei A., Yu D., Ostovari P., K.Bashir A. A survey of security and privacy issues in the internet of things from the layered context. Trans. Emerg. Telecommun. Technol. 2020 [Google Scholar]
- 6.G. Hatzivasilis, O. Soultatos, S. Ioannidis, C. Verikoukis, G. Demetriou, C. Tsatsoulis, Review of security and privacy for the Internet of Medical Things (IoMT), in: Proceedings of 15th International Conference on Distributed Computing in Sensor Systems, DCOSS, 2019, pp. 457–464.
- 7.Wang T., Zheng Z., Bashir A., Jolfaei A., Xu Y. Finprivacy: A privacy-preserving mechanism for fingerprint identification. ACM Trans. Internet Technol. 2020 [Google Scholar]
- 8.Mirzamohammadi S., Sani A.A. Viola: Trustworthy sensor notifications for enhanced privacy on mobile systems. IEEE Trans. Mobile Comput. 2018;17(11):2689–2702. [Google Scholar]
- 9.Qi L., Wang X., Xu X., Dou W., Li S. Privacy-aware cross-platform service recommendation based on enhanced locality-sensitive hashing. IEEE Trans. Netw. Sci. Eng. 2020 [Google Scholar]
- 10.Xu X., Liu Q., Zhang X., Zhang J., Qi L., Dou W. A blockchain-powered crowdsourcing method with privacy preservation in mobile environment. IEEE Trans. Comput. Soc. Syst. 2019;6(6):1407–1419. [Google Scholar]
- 11.Zuo C., Lin Z., Zhang Y. Proceedings of Symposium on Security and Privacy, SP. IEEE; 2019. Why does your data leak? Uncovering the data leakage in cloud from mobile apps; pp. 1296–1310. [Google Scholar]
- 12.Xu X., He C., Xu Z., Qi L., Wan S., Bhuiyan M.Z.A. Joint optimization of offloading utility and privacy for edge computing enabled iot. IEEE Internet Things J. 2019 [Google Scholar]
- 13.Dwork C. Proceedings of International Conference on Theory and Applications of Models of Computation, TAMC, Vol. 4978. Springer; 2008. Differential privacy: A survey of results; pp. 1–19. [Google Scholar]
- 14.Zheng Z., Wang T., Wen J., Mumtaz S., Bashir A.K., Chauhdary S.H. Differentially private high-dimensional data publication in internet of things. IEEE Internet Things J. 2020;7(4):2640–2650. [Google Scholar]
- 15.Duchi J.C., Jordan M.I., Wainwright M.J. Proceedings of 54th Annual Symposium on Foundations of Computer Science, FOCS. IEEE; 2013. Local privacy and statistical minimax rates; pp. 429–438. [Google Scholar]
- 16.Cormode G., Kulkarni T., Srivastava D. Proceedings of the International Conference on Management of Data, SIGMOD. ACM; 2018. Marginal release under local differential privacy; pp. 131–146. [Google Scholar]
- 17.Duchi J.C., Wainwright M.J., Jordan M.I. Minimax optimal procedures for locally private estimation. J. Amer. Statist. Assoc. 2018;113(521):182–201. [Google Scholar]
- 18.Wang N., Xiao X., Yang Y., Zhao J., Hui S.C., Shin H., Shin J., Yu G. Proceedings of International Conference on Data Engineering, ICDE. IEEE; 2019. Collecting and analyzing multidimensional data with local differential privacy; pp. 638–649. [Google Scholar]
- 19.Ye M., Barg A. Optimal schemes for discrete distribution estimation under locally differential privacy. IEEE Trans. Inform. Theory. 2018;64(8):5662–5676. [Google Scholar]
- 20.R. Bassily, K. Nissim, U. Stemmer, A.G. Thakurta, Practical locally private heavy hitters, in: Proceedings of Annual Conference on Neural Information Processing Systems, 2017, pp. 2288–2296.
- 21.Bassily R., Smith A.D. Proceedings of the Forty-Seventh Annual on Symposium on Theory of Computing, STOC. ACM; 2015. Local, private, efficient protocols for succinct histograms; pp. 127–135. [Google Scholar]
- 22.Bun M., Nelson J., Stemmer U. Heavy hitters and the structure of local privacy. ACM Trans. Algorithms. 2019;15(4):51:1–51:40. [Google Scholar]
- 23.Qin Z., Yang Y., Yu T., Khalil I., Xiao X., Ren K. Proceedings of the Conference on Computer and Communications Security, CCS. ACM; 2016. Heavy hitter estimation over set-valued data with local differential privacy; pp. 192–203. [Google Scholar]
- 24.T. Wang, J. Blocki, N. Li, S. Jha, Locally differentially private protocols for frequency estimation, in: Proceedings of USENIX Security Symposium, 2017, pp. 729–745.
- 25.Warner S.L. Randomized response: A survey technique for eliminating evasive answer bias. J. Amer. Statist. Assoc. 1965;60(309):63–69. [PubMed] [Google Scholar]
- 26.Wang S., Huang L., Wang P., Deng H., Xu H., Yang W. Proceedings of International Conference on Wireless Algorithms, Systems, and Applications, WASA, Vol. 9798. Springer; 2016. Private weighted histogram aggregation in crowdsourcing; pp. 250–261. [Google Scholar]
- 27.Erlingsson Ú., Pihur V., Korolova A. Proceedings of the Conference on Computer and Communications Security, CCS. ACM; 2014. RAPPOR: randomized aggregatable privacy-preserving ordinal response; pp. 1054–1067. [Google Scholar]
- 28.M. Charikar, K.C. Chen, M. Farach-Colton, Finding frequent items in data streams, in: Proceedings of International Colloquium on Automata, Languages and Programming, ICALP, 2002, pp. 693–703.
- 29.Cormode G., Muthukrishnan S. An improved data stream summary: The count-min sketch and its applications. J. Algorithms. 2005;55(1):58–75. [Google Scholar]
- 30.G. Cormode, M.N. Garofalakis, Sketching streams through the net: Distributed approximate query tracking, in: Proceedings of the 31st International Conference on Very Large Data Bases, PVLDB, 2005, pp. 13–24.
- 31.M. Thorup, Y. Zhang, Tabulation based 4-universal hashing with applications to second moment estimation, in: Proceedings of the Fifteenth Annual Symposium on Discrete Algorithms, SODA, 2004, pp. 615–624.
- 32.Sweeney L. K-anonymity: a model for protecting privacy. Int. J. Uncertain. Fuzziness Knowl.-Based Syst. 2002;10(5):557–570. [Google Scholar]
- 33.Machanavajjhala A., Kifer D., Gehrke J., Venkitasubramaniam M. L-diversity: Privacy beyond k -anonymity. ACM Trans. Knowl. Discovery Data. 2007;1(1):3. [Google Scholar]
- 34.Dwork C., McSherry F., Nissim K., Smith A.D. Proceedings of Third Theory of Cryptography Conference, TCC, Vol. 3876. Springer; 2006. Calibrating noise to sensitivity in private data analysis; pp. 265–284. [Google Scholar]
- 35.F. McSherry, K. Talwar, Mechanism design via differential privacy, in: Proceedings of 48th Annual IEEE Symposium on Foundations of Computer Science (FOCS’07), 2007, pp. 94–103.
- 36.P. Kairouz, S. Oh, P. Viswanath, Extremal mechanisms for local differential privacy, in: Proceedings of Advances in Neural Information Processing Systems, 2014, pp. 2879–2887.
- 37.Kairouz P., Oh S., Viswanath P. Extremal mechanisms for local differential privacy. J. Mach. Learn. Res. 2016;17:17:1–17:51. [Google Scholar]
- 38.B. Ding, J. Kulkarni, S. Yekhanin, Collecting telemetry data privately, in: Proceedings of Advances in Neural Information Processing Systems, 2017, pp. 3571–3580.
- 39.Ye Q., Hu H., Meng X., Zheng H. Proceedings of Symposium on Security and Privacy, SP. IEEE; 2019. Privkv: Key-value data collection with local differential privacy; pp. 317–331. [Google Scholar]
- 40.N. Li, Q. Ye, Mobile data collection and analysis with local differential privacy, in: Proceedings of IEEE 20th International Conference on Mobile Data Management (MDM), 2019, pp. 4–7.
- 41.Differential Privacy Team A. Apple; 2017. Learning with Privacy at Scale. [Google Scholar]
- 42.R. Chen, H. Li, A.K. Qin, S.P. Kasiviswanathan, H. Jin, Private spatial data aggregation in the local setting, in: Proceedings of IEEE 32nd International Conference on Data Engineering (ICDE), 2016, pp. 289–300.
- 43.McSherry F. Proceedings of International Conference on Management of Data, SIGMOD. ACM; 2009. Privacy integrated queries: an extensible platform for privacy-preserving data analysis; pp. 19–30. [Google Scholar]
- 44.Wegman M.N., Carter L. New hash functions and their use in authentication and set equality. J. Comput. System Sci. 1981;22(3):265–279. [Google Scholar]
- 45.G. Weiss, WISDM smartphone and smartwatch activity and biometrics dataset data set. http://archive.ics.uci.edu/ml/index.php.
- 46.J. Wang, Bixi montreal bikeshare data - Bikeshare information for bixi montreal. https://www.kaggle.com/jackywang529/bixi-montreal-bikeshare-data.
- 47.Zhang Y., Wang K., He Q., Chen F., Deng S., Zheng Z., Yang Y. Covering-based web service quality prediction via neighborhood-aware matrix factorization. IEEE Trans. Serv. Comput. 2019:1. [Google Scholar]
- 48.Xue X., Han H., Wang S., Qin C. Computational experiment-based evaluation on context-aware O2O service recommendation. IEEE Trans. Serv. Comput. 2019;12(6):910–924. [Google Scholar]
- 49.Xue X., Wang S., Zhang L., Feng Z., Guo Y. Social learning evolution (SLE): computational experiment-based modeling framework of social manufacturing. IEEE Trans. Ind. Inform. 2019;15(6):3343–3355. [Google Scholar]