Abstract
Nowadays the sharing of trade in counterfeit and pirated goods is constantly growing and fake products are found in a large number of industries – particularly pharmaceuticals, food, and medical equipment – that can pose serious health and safety risks. With the intention of avoiding any loss of client confidence and any disclosure of sensitive information, Internet of Things (IoT) solutions are increasingly used to fulfill this need for a reliable and secure infrastructure in medical & pharmaceutical industry. When looking at the technologies used to identify products and packaging, balancing security and hardware limitations is often a difficult task and using cost-effective techniques such as bit-oriented lightweight functions is a challenge. In this study, we first assess the security level of a recently proposed protocol and prove its vulnerabilities, due to a lack of complexity in bit-oriented functions. Then, to address these exposed flaws, a lightweight improved protocol based on Authenticated Encryption (AE) cryptosystems is presented. Security analysis results demonstrate that weaknesses of previous efforts have all been adequately addressed; additionally, the improved protocol has a robust security posture in terms of confidentiality and integrity. Moreover, FPGA and ASIC simulations are carried out using five different AE schemes from CAESAR competition to develop three use-cases, in whose best scenario the proposed tag has 731 LUT and needs 3335 gates for the security module.
Keywords: Internet of Things, Medical IoT, Supply chain, Security, RFID, Authenticated Encryption, SecLAP
1. Introduction
Illicit trade in fake goods is a major challenge in the global economy, resulting in a plethora of adverse effects on the economy, as well as on public health, safety, and security [1]. Organized criminal groups operate wherever there is an opportunity to make profits from counterfeiting or piracy operations, frequently bypassing security measures. Despite continuous efforts to monitor this risk, the share of trade in counterfeit and pirated goods is constantly growing, and fake or fraudulent products are found in a large and growing number of industries, particularly pharmaceuticals, food and drink, and medical equipment, that can pose serious health and safety risks. Every day new threats of counterfeits are reported [2] in this billion-dollar market, in which approximately half of the counterfeit pharmaceuticals sold are fraudulent versions of treatments. This is “an unaffordable vulnerability” [3]. With “counterfeiting and piracy on the rise”, it is no surprise that the current context of the COVID-19 pandemic opens great opportunities for counterfeiters [4], as governments the world over are looking for COVID-19 facemasks and test kits. Since the onset of the crisis, many cases have been reported in the news where authorities have intercepted counterfeit COVID-19 test kits, pressing worldwide anti-fraud centers as well as the United States’ Food and Drug Administration (FDA) [5] to alert consumers about unauthorized fraudulent test kits.
To combat this risk surrounding the rising significance of counterfeit products and medications, government agencies (e.g. the FDA) and organization (e.g. pharmaceutical suppliers) are exploring enforcement solutions, among which IoT solutions can help maintain a secure supply chain [6]. Moreover, the adoption of IoT technologies in the healthcare and pharmaceutical sectors is continuously expanding, including – among other aspects – a high demand for hospital-based IoT services oriented towards patient safety, work efficiency, and medical environment management [7]. Within the IoT ecosystem, radio frequency identification (RFID) technologies are among the technologies most used to enable automatic identification and tracking of products, people, and assets. In fact, various RFID initiatives have been undertaken since the early 2000s to secure supply chain integrity by supporting real-time tracking, tracing & authentication of pharmaceuticals products. Since then, the RFID market has grown and is currently estimated to be valued at over one billion US$ [8]. Assuredly, counterfeit drugs concerns have encouraged the industry to use RFID technologies within pharmaceutical supply chains, with industry players ranging from drug manufacturers to packaging solutions providers, warehouse and distribution centers, to clinical facilities. Today “mass serialization” is proposed as the standard for identifying drug packages, by equipping each of them with a unique identifier, such as a 2D barcode or RFID entered into an online database for track-and-trace purposes. Unfortunately, weaknesses in track-and-trace the system leave the system vulnerable to counterfeiters, calling for an increased attention towards RFID technology adoption [9], aligned with the Drug Quality and Security Act [10] and the Drug Supply Chain Security Act [11].
Ironically, if these technologies are to prevent trade in counterfeit and pirated goods, they may themselves constitute an issue. Given the importance of RFID (and other IoT devices) used to track and manage supply chains, security issues are raised by the professional and academic community, calling for security requirements at all layers of any IoT-based infrastructure [12]. In fact, in a recent bibliometric analysis on IoT, Dachyar et al. [13] found a significant increase in the number of articles on IoT – with growth and development in an interdisciplinary manner – and, following a pattern of analysis of research trends, they show a clearly-increasing number of researches on security attacks and protocols. This is particularly important with passive Ultra High Frequency (UHF) RFID tags equipped with a highly constrained microchip holding limited processing power and memory capabilities. These tags, constituting the first layer of an RFID infrastructure (Fig. 1), are used to identify drugs, high value and consignment products in hospitals, to track biospecimen sampling or COVID-19 test kits in the supply chain. Fig. 2 (adapted from GS1[14]) shows the supply chain activities where key steps are undertaken. Without the proposed RFID tag security – at any of these steps – malicious attacks may be undertaken. For better understanding, COVID-19 test kits will be employed here as a realistic use case to illustrate the effect of health and safety risks in bypassing security measures. In the following scenario we consider a supply chain process involved in production of a COVID-19 test kit from a plant to a hospital, assuming that RFID tags are encoded and applied to final assembled kits targeted for tracking as well as to the component products contained in the kits requiring identification. A potential attack scenario could be implemented as follows:
Fig. 1.
The infrastructure of an IoT-enabled traceability system.
Fig. 2.
Opportunities to conduct a malicious attack in the supply chain.
-
1.
RFID tags are applied to COVID-19 test kits (for collection of nasal swab specimens) to ensure automatic identification (for efficient logistics management), authentication (for patient safety), and anti-counterfeit measures (for brand protection).
-
2.
Kits are shipped from the assembly plant.
-
3.Kits are received and completed at the packaging sites (where RFID tag is applied) opportunity to conduct an attack:
-
(a)Tags information is captured (using an unauthorizedreader);
-
(b)Kits equipped with original RFID tags are identified in the shipping zone;
-
(c)New tags are cloned;
-
(d)New tags are applied to the fake kits;
-
(e)Fake kits are shipped as “authentic kits” to the distribution center;
-
(f)Authentic kits are sold to selected customers.
-
(a)
-
4.Fake kits are received at the distribution center where they are stored and cross the dock to clinical sites:
-
(a)Opportunity for conducting a similar attack to the one described at the packaging site above.
-
(a)
-
5.Kits are received at the hospital, where they are temporarily stored and used. Another opportunity to conduct an attack arises here:
-
(a)Tags information is captured (using an unauthorizedreader);
-
(b)Kits (tags) are identified and retrieved in the storage area in the hospital;
-
(c)Authentic kits are stolen;
-
(d)Fake kits are produced to replace authentic kits;
-
(e)Fake kits are used with potential harmful effects to the health of the patients;
-
(f)Authentic kits are sold directly to selected customers (according to the best offer).
-
(a)
As discussed in the above scenario, a malicious attack can be undertaken at various phases of the supply chain, compromising it’s integrity and raising the critical importance for securing any layer of the supporting IT infrastructure. In an IoT-based medical system, one of the weakest layer may be the technology used for item automatic identification and data capture. By incurring an unauthorized access to the information on tags (e.g. passive disclosure attack) an adversary could then compromise the whole system. Therefore, researchers are working on the development of secure authentication and communication protocols to prevent malicious attacks. For example, Li et al. [15] presented an authentication protocol for Telecare Medicine Information Systems (TMIS) and claimed that the proposed protocol is able to satisfy the security requirements of a Medical IoT system. However, Bensallah et al. and Zhou et al. [16], [17], in two different research papers, proved that Li et al.’s protocol is vulnerable to desynchronization and impersonation attacks. In addition, Zheng et al. [18] proposed another lightweight authentication protocol for TMIS system based on a Hash function by which Safkhani and Vasilakos [19] showed that their protocol is not resistant against replay, impersonation, and desynchronization attacks. On the other hand, other researchers attempted to present an authentication protocol based on ECC (Elliptic Curve Cryptography) cryptosystems for medical applications. For example, Liao and Hsiao [20] designed an ECC-based protocol which Zhao et al. [21] proved their vulnerability to a tag disclosure attack. In addition, in order to increase the security level, Chou et al. [22] used a combination of a hash function and an ECC module in their protocol. However, Zhang and Qi [23] – by showing the weaknesses of Zhou et al.’s protocol – presented a new protocol with the same concept. Finally, Farash [24] proved in turn that Zhang and Qi’s protocol is also vulnerable to an impersonation attack. Fotouhi et al. suggested a lightweight protocol based on the two-factor authentication scheme [25]. The proposed protocol was designed for wireless body area networks (WBAN) in health-care IoT applications and by using XOR and hash functions provided a secure environment. Another WBAN-based protocol for e-health systems was introduced by Arfaoui et al. [26]. In order to respect patients’ privacy and protect the confidential data of medical records, the authors presented a context-aware and lightweight anonymous authentication and key agreement scheme which was suitable for applications in emergency and normal situations.
Since using an ECC cryptosystem alone cannot guarantee the security of a protocol, as well as it causes more burden on a tag’s hardware, some research have been undertaken on ultra-lightweight and lightweight protocols. For instance, Fan et al. [27] recently proposed a lightweight RFID mutual authentication scheme and suggested relevance to application in medical privacy protection in IoT systems. The authors analyzed the security of the proposed protocol and claimed that it provides tag anonymity, replay attack resistance, synchronization attack resistance, forward secrecy, mutual authentication, and DoS attack resistance. However, a subsequent review revealed that the proposed protocol suffers from trivial weaknesses, as was shown by Aghili and Malla [28] and more comprehensively later by Aghili et al. [29]. In those works, the security of the proposed scheme is scrutinized and serious security pitfalls are shown. More precisely, they present an efficient secret disclosure and traceability attacks that violate the designers’ claims. In addition, by focusing on bit-oriented operations in the ultra-lightweight function, Aghili et al. [29] also proposed an improved protocol called SecLAP following the same design strategy and stated optimum security against an active adversary who can control the channel between the tag and the reader as well as between the reader and the server. Although the authors claimed SecLAP was fully secure, we show that this protocol has serious security breaches, which we intend to address here. We present traceability and passive secret disclosure attacks against this protocol, with the complexity of eavesdropping one session of the protocol and with success probability of ‘1’. The disclosed parameters can be used to trace the tag/reader in any later session, which compromises tag/reader privacy. In addition, we present below a passive full secret disclosure attack against SecLAP which is capable of disclosing a -bit secret key, -bit and -bit with the computational complexity of . We explain limitations of ultra-lightweight protocols that cause the above protocols to compromise. Given that new authentication protocols have recently been introduced with lightweight cryptographic methods which have complicated protocol’s structures [30], we present an uncomplicated improved protocol and employ a cryptosystem that provides a higher security level than ultra-lightweight functions and is able to satisfy the hardware requirements of lightweight tags.
The Paper’s Contribution: This paper has three main contributions:
-
1.
We provide the first third-party security analysis of SecLAP, which may be the latest attempt to design a secure ultra-lightweight protocol for constrained environments. More precisely, we execute a passive attack, which can partially disclose secret parameters of the protocol with the complexity of eavesdropping on one session of the protocol with negligible computational complexity. In addition, we present a full secret disclosure attack that can extract all secret parameters of the protocol with the complexity of .
-
2.
To overcome the security flaws in SecLAP, we present an improved protocol based on an Authenticated Encryption (AE) scheme and provide informal and formal security evaluations to show the robustness of the protocol. This scheme not only is able to solve the confidentiality issues of the current protocols, but also provides the message integrity simultaneously.
-
3.
Given that an AE module can use different implementation designs, we simulate the structure of a tag (FPGA and ASIC) under five encryption schemes and measure its hardware requirement as a candidate for constrained environments. We show that the improved protocol can meet the security requirements with a reasonable hardware cost.
Paper Organization : The required preliminaries and a brief description of SecLAP protocol are introduced in Section 2. We present results of security investigation of SecLAP protocol in Section 3. Then, we discuss our suggested encryption scheme in Section 4 and propose the improved protocol in Section 5. The security analysis and hardware implementation results are respectively explained in Sections 6, 7 and we conclude the paper in Section 8.
2. Preliminaries
2.1. Notations
Table 1 depicts the notations used in the rest of this paper. In order to propose a robust ultra-lightweight protocol, Aghili et al. presented a new component called modular rotation function which is used in the structure of SecLAP. Given two -bit strings and and a -bit string , the modular rotation function is defined as follows:
Table 1.
Notations used in this paper.
| Symbol | Description |
|---|---|
| An RFID reader | |
| The identification value of the reader | |
| A cloud server | |
| An RFID tag | |
| The identification value (ID) of the tag | |
| The current session number | |
| The new session number | |
| The pseudo random number generator | |
| The bit-oriented operation defined by Fan et al. | |
| The rotation of sting based on the hamming weight of | |
| The bit-oriented operation defined which is used in SecLAP | |
| Odd bits of string . | |
| Even bits of string . | |
| The bitwise XOR operation | |
| The concatenation operation | |
| Two temporary bits that are used to indicate the status of the last session | |
| The bitwise complement of the string | |
| Tag’s ID in the improved protocol | |
| Secret Tag’s ID in the improved protocol | |
| Encryption key | |
| A random number |
-
•
As illustrated in Fig. 3, the odd bits of are concatenated with the even bits of , the result is XORed by the bits of and the result is rotated to the left depending on the value of . The result is used as the odd bits of the final result. We can represent it as , where and respectively denote the odd bits of and the even bits of .
-
•
The even bits of are concatenated with the odd bits of , the result is XORed by the bits of and the result is rotated to the left depending on the value of . The result is used as the even bits of the final result. We can represent it as .
Fig. 3.
The structure of function in SecLAP, where .
It is clear is more complicated compared to that has been explained in the Appendix.
2.2. Random Oracle Model (ROM)
Random Oracle [31] is a random black box function that provides a unique response for a truly random input as a security proof for evaluating protocols. Every time a same input is given to the random oracle function, the same output is returned. A Random Oracle Model, denoted by , is defined by . Here is a function chosen uniformly at random from the set of all functions with the same domain and range.
In general (as in our paper), the output’s length of is predefined to some fixed value, e.g. bits. Hence, we re-define as . Given an input , will give as the output.
2.2.1. Adversary
We consider a computationally unbounded adversary with access to or a real cryptographic component , which could be a cryptographic protocol and is the total length of the observable messages in each query. The adversary’s “running time” is determined by the number of oracle queries that it makes to . We use the symbol (big-Oh), for “the expected running time of at most” and (big-Omega), for “the expected running time not less than”.
2.2.2. Indistinguishability
In the cryptology terminology, is considered as an ideal system and the distinguisher tries to distinguish the candidate crypto system with -bit output length from . In the framework of indistinguishability, the distinguisher faces with either or and aims to understand whether interacts with or . Now we present the formal definition of indistinguishability following [32]:
Considering a probabilistic polynomial time (PPT) algorithm (called distinguisher) as an algorithm that its running time on input is at most and may use (true) randomness to produce (possibly) non-deterministic results. The crypto system and the random oracle are (computationally) indistinguishable if for any PPT distinguisher , interacting with one of these components and generating a binary output ( or ), it holds that:
where is a negligible function of the security parameter .
In this framework, the maximum number of queries is bounded and denoted by .
A crypto system is said to be indistinguishable from a random oracle if for any PPT distinguisher with and performs at most queries to it holds that:
where is a negligible function of the security parameter .
2.3. Description of SecLAP
SecLAP was proposed to improve the security drawbacks of its predecessor (Fan et al.) based on a similar designing paradigm. As depicted in Fig. 4, it is implemented as follows:
Fig. 4.
Mutual authentication phase of SecLAP [29].
-
1.
The reader starts the authentication process by generating a new random number and sends it along with to the tag.
-
2.Once the tag receives the message, it:
-
•generates a random number ;
-
•computes and ;
-
•and sends to the reader;
-
•
-
3.
Upon receipt of the message, the reader obtains from and verifies the received . Then, it computes , , and , and forwards to the server. If the tag is not authenticated, the protocol will be terminated.
-
4.When the server receives the message:
-
•extracts and finds the related and in the database and verifies the received ;
-
•generates another random number ;
-
•computes , and sends to the reader.
-
•
-
5.Once the reader receives , it:
-
•retrieves from and verifies the received ;
-
•computes and ;
-
•and sends to the tag;
-
•
-
6.Once receipt the message , the tag:
-
•retrieves from and verifies to authenticate the server/reader;
-
•calculates ;
-
•computes and ;
-
•and sends to the reader.
-
•
-
7.When the reader receives the message, it:
-
•calculates and verifies the received ;
-
•computes , , , , , , , ;
-
•and sends to the server.
-
•
-
8.Once the server receives the message, it:
-
•extracts , and respectively from , , , and and verifies accordingly to update and ,
-
•adds to its database ,
-
•computes and sends it to the reader.
-
•
-
9.
Upon receipt of the message , the reader verifies it before updating as . If is verified correctly, the reader computes and sends it to the tag.
-
10.
The tag verifies the correctness of received to update as and the protocol is completed.
3. Security analysis of SecLAP
Aghili et al. have claimed the optimum security of SecLAP against an active adversary, and showed that SecLAP is completely secure by using informal and formal evaluations like Burrows–Abadi–Needham (BAN) logic. In this section, we present a security evaluation and prove that SecLAP is not resistant against secret disclosure and traceability attacks.
3.1. Partial secret disclosure attack
This section explains some properties of SecLAP that can be used to reveal information related to secret parameters. Based on this information, the adversary can trace the tag or the reader which compromise their anonymity. More precisely:
| (1) |
On the other hand, from the definition of we know that the and . Hence:
| (2) |
The above equation can be simplified as follow:
| (3) |
Next, assume that the adversary has eavesdropped the first run of the exchanged messages between the reader and the tag, i.e., and , where and . According to the above argument, we can write:
| (4) |
and:
| (5) |
Similarly, we can argue that:
| (6) |
| (7) |
In any of Eqs. (5), (6), the left side is a linear combination of the public parameters and the right side is a linear combination of secret parameters. Hence, each equations reveals a bit of the secret information. In addition, as long as the tag has not updated its secrets those bits of information remain fixed and the adversary can use it as a source of traceability, which compromises the designers claim on the security of the protocol against traceability.
Given that the channel between the reader and the server is also insecure, to trace the reader, the adversary eavesdrops , a sent message from the reader to the server, where . Recall from Eq. (3):
| (8) |
Combining Eqs. (8), (5), reveals a single bit of as follows:
| (9) |
It worth noting that the related information in Eq. (9) is independent of the tag’s data. Hence it is enough to compromise the reader anonymity.
Other eavesdropped messages by the adversary could be used to disclose other information as follows:
-
1.
, and sent from the reader to the server,
-
2.
, sent from the server to the reader,
-
3.
and sent from the reader to the tag,
-
4.
and sent from the tag to the reader,
-
5.
, , , , , , sent from the reader to the server,
-
6.
sent from the server to the reader,
-
7.
sent from the reader to the tag,
For example:
| (10) |
Now the combination of Eqs. (5), (10), reveals a bit of , as follows:
| (11) |
Given that will not be updated at the end of the session, it can be used to compromise the tag’s anonymity and trace the tag holder in any session.
Similarly,
| (12) |
and from and Eqs. (7), (9), (11) we can disclose , which combined with Eq. (12) reveals two bits of and also .
The success probability of disclosing all values mentioned in this section is ‘1’ and the complexity is only eavesdropping one session of the protocol.
In Fig. 5, a toy example of calculation of when , , and is provided. Following this example, . On the other hand: see equations in Box I.
Fig. 5.
A toy example of calculation of .
Box I.
Which shows that as it is expected from Eq. (5), . In this way, the adversary could extract one bit hidden information.
3.2. Full secret disclosure attack
The secret parameters of SecLAP are , and , where and are constant values while is a dynamic value which is updated after each successful run of the protocol. Most of the transferred messages are masked by and produced by , which is more complicated than the used by Fan et al. Hence, designers of SecLAP expect decent protocol security against secret disclosure attacks. However, we present an attack to extract those secret parameters efficiently. Despite the designers’ claim that SecLAP is secure even against an active adversary – with full control over the channel between the tag and the reader and the reader and the server – we consider the weakest adversary who can only eavesdrop the channel between the tag and the reader, let alone the server and the reader. To initiate the attack, we assume that the adversary eavesdrops any transferred message from the tag to the reader or from the to in session ; this is known as the learning phase of the attack. Hence, at the end of this learning phase, the adversary very likely has the following information:
-
•
sent from to ;
-
•
and and sent from to ;
-
•
and sent from to ;
-
•
and sent from to ;
-
•
sent from to ;
On the other hand, from the definition of we know that the while is used to produce the even bits of . Hence, we can argue that any bit of the output, , is a linear function of a bit from with either a bit from or a bit from , i.e. , where , , and . However we may not know the exact value of and , from the definition of , we know that if is an odd value then will also be an odd value while will be even and if is an even value then will also be even while will be odd. In addition, if then , for any , obviously addition takes place module . In addition, given and in , we can uniquely determine related values of and . It comes from the fact that while . Therefore, given to extract -linear equation out of , the only unknown parameter will be and , which has the total complexity of . In the rest of the paper, we use odd-offset and even-offset to denote and respectively. Now, given the eavesdropped and from a session of the protocol and the above properties of , the adversary uses the below procedure to extract the secret parameters of SecLAP:
-
1.
for :
-
2.for :
-
(a);
-
(b);
-
(c)for :
- (d)
-
(a)
-
3.
Given that , , and the returned and should also pass.
The above attack has the complexity of time solving a linear equation with equations of independent variable. Hence, it is expected to do not return any candidate exclude the correct pair of and in Step 2(d)iv. However, any possible wrong guess also filtered in Step 3. Given that any wrong guess passes Step 3 with the probability of , the algorithm will return the correct value of and . Next, given and and also the eavesdropped the adversary extracts and calculates as . The adversary can also use other eavesdropped messages, i.e. , , and to filter any possible wrong guess.
Because the computational complexity of solving a system of linear equation of variables has the complexity of , the expected complexity of extracting , and is . For , the adversary will be able to extract those secret parameters with the complexity of , while the expected complexity is at least , which shows a huge gape.
It should be noted that since the channel between the reader and the server is also insecure, the adversary can eavesdrop . Assuming that the adversary has already disclosed and , it can easily also extract . Similarly, the adversary can use to extract which – along with other known parameters – can be used to construct . In this way, the adversary reveals the entire secret parameter of the protocol with the computation complexity of with only one eavesdropping session of the protocol between the parties, i.e. tag, reader, and server.
3.3. Traceability attack
In Section 3.2, we presented an attack where any passive adversary who eavesdrops the transferred messages of a session of the protocol between the legitimate tag, the reader, and the server will be able to extract , , and with the complexity of . Given that and are constant values for any tag/reader and will not be updated after the protocol completion, they can be used to trace the tag/reader, which contradicts the designers’ claim.
3.4. Distinguishability in ROM
In this section, we show that SecLAP is not also a secure protocol in ROM. To distinguish SecLAP from ROM we use the observation used to partial recover secret parameters in Section 3.1. From the structure of the messages one can deduce that:
| (13) |
This property can be used as a metric to determine that the used protocol is SecLAP and not .
To distinguish SecLAP from , the adversary does as follows:
-
1.
eavesdrops messages of a session of the given protocol, transferred over the channel.
-
2.
evaluates Eq. (13) and returns if it is true; otherwise returns .
To determine the adversary’s advantage, it is clear if the adversary communicates with SecLAP then with the probability of ‘1’ returns in Step 2 while if it communicates with then returns with the probability of ‘2−1’. To improve the adversary’s advantage, we can increase the number of eavesdropped sessions. For an adversary who eavesdropped sessions, the advantage will be as follows:
which is the maximum advantage that an adversary can get after queries. It should be noted that the other combinations of transferred messages can also be used for distinguishing SecLAP from ROM. For example:
| (14) |
An interesting point with Eq. (14) is the fact that to distinguish the protocol the adversary only requires to eavesdrop the channel between the tag and the reader. It is clear that the adversary can use both Eqs. (13), (14) (and several other combinations) to achieve same advantage with eavesdropping less number of sessions. Therefore, SecLAP has security flaws in ROM.
4. Authenticated encryption
Given that the improved protocol in Section 5 uses an AE-based encryption module, in this section we provide a brief introduction to this concept. The common approach to provision of confidentiality and integrity in a communication process is to use a secure encryption scheme and a secure message authentication code (MAC) respectively. Authenticated encryption (AE) provides these two security objectives simultaneously. An important objective in using an AE scheme as opposed to a simple encryption function is to prevent message forgery. By adding an authentication service to the message, the received ciphertext is not accepted as it is and will be verified to determine whether it has been manipulated or forged. Encrypt-then-MAC, Encrypt-and-MAC and MAC-then-Encrypt are traditional approaches of AE scheme designs. Unfortunately, these methods are inefficient, as they use two separate keys, one for encryption and another for authentication [33].
An AEAD scheme is an AE model which supports associated data (AD) also. Associate data is part of the transferred information, for which confidentiality may not appear important but integrity in this element is nonetheless necessary, e.g. with headers or routing information. As shown in Fig. 6, the AEAD takes a plaintext of an arbitrary length upper-bounded to a fixed value, a key, and a nonce, and produces a ciphertext and a MAC-value. Its encryption and decryption functions are respectively as follows, where are key, nonce, associated data, plaintext, ciphertext, and MAC-value, respectively.
MAC generator is a built-in component of an AEAD module that generally receives the output of the last step of an encryption process and transforms data by some simple operations. In most AEAD schemes, if the MAC-value () is verified then the decryption function returns the plaintext ; otherwise it returns an error symbol, e.g. .
Fig. 6.
General structure of an AEAD module.
To design a secure AEAD scheme for different applications, in 2014 a competition entitled CAESAR (Competition for Authenticated Encryption: Security, Applicability, and Robustness) was created [34], which was a competition to promote research related to authenticated encryption and to boost the understanding of AE in the cryptographic research community. Such competitions have a long and promising story in the field of symmetric cryptography, e.g. AES [35], eStream [36], SHA3 [37], and PHC [38]. It should be noted that NIST [39] has also begun a competition for standardization of lightweight AE and hash function schemes for which the candidates of its second round were announced September 9, 2019. A secondary aim of the CAESAR competition was to design a dedicated AEAD scheme which could be more resource-efficient than conventional approaches. A dedicated scheme would indicate an AE module that needs only one key for encryption and MAC processes. The first round of CAESAR received 57 submissions, and all of them have been confirmed as approved candidates. After almost five years of analysis and comparisons by independent researchers, following the last round in 2019, six designs were been selected as the final portfolio to be implemented here in our protocol. As shown in Table 2, the selected designs were classified into three use-cases, (i) lightweight applications; (ii) high-performance applications; and (iii) defense in depth.
Table 2.
CAESAR Competition final portfolio [34].
5. AE-based improved protocol
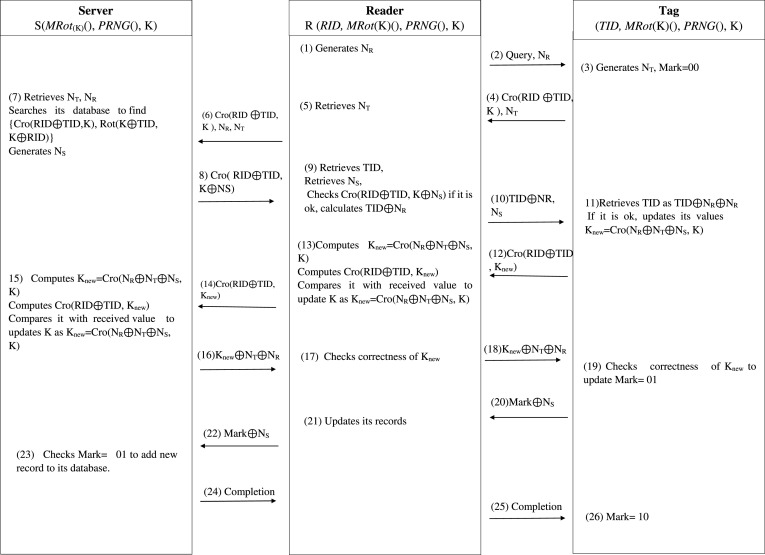
In order to overcome the security flaws of previous protocols, in this section we propose an AE-based authentication protocol. The goal of using an AE module is to achieve a higher security level (i.e. confidentiality and integrity simultaneously) rather than previous protocols with reasonable hardware and communication cost. The notations employed from the improved protocol have been listed in Table 1. Since the structure of this protocol is based on an AEAD design with single-key, the stored information in the header is not encrypted and the sender could transfer some general values via this route. In addition, by using only one key for encryption and integrity processes, the structure of the protocol and the tag could be simpler. To gain a deeper understanding of the counterfeiting scenario in the introduction, an authentication process for a COVID-19 test kit in a hospital is considered. Hence, we assume each kit has been equipped with an RFID tag and the nurse uses an RFID reader to detect the tag and check its authenticity. Our proposed protocol has two phases and functions as follows:
5.1. Initialization phase
In this phase, the default values of the parameters are stored into the parties (Tag, Reader, and Database) and the encryption key is shared. In the database there is a record for each tag that consists the set , where and respectively denotes the old and the new tag’s parameters. These values are updated after each successful session of the protocol and are initially blank. is also stored in the tag. The database could be local and integrated with the reader or a dedicated server with remote access.
In Fig. 7, we assume the reader hosts the local database; in the security analysis section, we discuss two different situations.
Fig. 7.
Authentication and key agreement phase of the improved protocol.
5.2. Authentication phase
When a nurse wants to use a kit, she has to activate the reader and the following steps must be taken.
-
1.
The reader generates a random number , and sends and Hello message to the embedded tag in the kit.
-
2.
Upon receiving the messages, the tag generates as a nonce and computes as and its using an AEAD scheme, actually the output of the AEAD scheme will be and is the ciphertext. The random number is used in the AD part of the message and the tag sends to the reader.
-
3.
When the reader receives the messages, given , looks up the database, finds related , decrypts and verifies the received to authenticate the tag.
-
4.
It then generates and updates the tag’s records as , , , – and have same length– and updates its database accordingly. It worth noting is used in the AD segment and is XORed with the ciphertext part,
-
5.
Since the tag has the required parameters to compute and in order to decrease the communication cost, the reader only sends the generated and to the tag.
-
6.
After receiving the messages, the tag computes and verifies the received . If the comparison holds, the tag authenticates the reader and updates its to and to . Therefore, the mission is completed and the kit is valid; otherwise it terminates the session.
6. Security analysis of the improved protocol
The following section describes the security evaluation of the improved protocol. Both informal and formal methods are utilized to prove that the proposed protocol is resistant against various kinds of IoT threats. In terms of the informal evaluation, the protocol robustness is analyzed against various attacks such as traceability, replay, and disclosure. In addition, the formal evaluation is performed by a manual as well as an automated method, which will be introduced later.
6.1. Informal security analysis
In order to assess the resistance of the improved protocol based on the informal method, we present an adversary model with some assumptions. We consider that the adversary has access to communication channels and can eavesdrop all transferred messages. She can intercept the line and transfer her packets to the tag or the reader. In addition, she is able to run all functions – such as PRNG and encryption – without having access to secret keys.
6.1.1. Traceability attack
To perform the traceability attack on a protocol, the adversary needs an instant and fixed value to detect a tag in various situations. In the proposed protocol, the tag transfers and that is randomized by and and is also updated after each successful session of the protocol. Although, as far as the tag has not participated in a successful session of the protocol, is constant and could be used to trace the tag, however, it is not possible to use it to do traceability attack after a successful session of the protocol. It should be noted is used to provide scalability in the proposed protocol. In this way, the reader finds the related tag in its database in constant time, independent of the number of tags that are covered by the reader. If After receiving a new Hello message with an iterative , the tag typically generates a fresh and calculates a new ; consequently the adversary could not find the similarity among different messages from a tag and the protocol is resistant against the traceability attack, assuming that it has participated in a successful session. It worth noting that it is possible to drop in the sent message by the tag. Thereby, the adversary will not be able to trace the tag even if the tag has not participated in a successful session, because it sends and , and and the are randomized by and . However, in this case the reader must do an exhaustive search in its database to find the target tag, which is not scalable.
Table 3.
GNY logic notations and logic rules in this paper.
| Notations | Description |
|---|---|
| is fresh | |
| Combination of two formula and | |
| Shows is a secret parameter | |
| is encrypted using as the key | |
| receives | |
| is securely shared between and | |
| possesses | |
| is recognizable | |
| was not originated by the party who receives it. | |
| Means that if believes freshness of , then it deduced that believes freshness of any formula of . | |
| Means that if believes freshness of and possesses , then it deduced that believes freshness of any one-way formula of i.e. . | |
| Means that if possesses and , it also possesses any formula of them. | |
| , where , and | Means that if receives an one-way formula of and a secret parameter which was not originated by itself, and he possesses or and he believes is a shared secret between itself and , and also believes freshness of or , then it is deduced that believes sent a formula of with , and also believes sent the one-way formula of and i.e. . |
6.1.2. Secret disclosure attack
The secret disclosure attack occurs when the tag or the reader is unable to protect confidential information (e.g. encryption keys or identification numbers) against unauthorized users. In the improved protocol, the confidential and important tag’s parameters are and . Hence, if the attacker has access to them or is able to reveal them, she can potentially have full access to the system. Given that all transferred messages on a public channel will be encrypted by an AE-based algorithm and the important parameters are not sent as a cleartext, if the attacker eavesdrops transferred packets, useful information about confidential values cannot be found and the probability of revealing information is negligible. Therefore, the proposed protocol is not vulnerable to the secret disclosure attack.
6.1.3. Replay attack
To implement the replay attack on a protocol, the adversary needs to store what is being exchanged on a channel and later sends to the same tag or reader as a valid response without knowing the content of the message itself. To prevent this attack in the improved protocol, both parties must transfer fresh data. Hence, two random numbers and guarantee the freshness of and messages. If the adversary eavesdrops the transferred messages in a valid session and sends this to the reader as a legitimate tag, when the reader checks the validity of based on a fresh , the comparison does not hold. In addition, due to using a fresh in the tag’s side, the replay attack is also impossible on the tag. Therefore, we can claim that the improved protocol is resistant against the replay attack.
6.1.4. Back-end channel security
As mentioned earlier, the communication channel between the tag and the reader is public and the adversary is able to capture transferred messages. The implementation concerning the back-end channel between the reader and the server could adopt one of two possible models. The channel could be private and the adversary would thus have no access to it, or it could be considered as a public channel. Because a modern reader like the ZEBRA MC3390R handheld RFID reader has powerful hardware components (e.g. 1.8 GHz hexa-core 64-bit Processor, up to 4 GB RAM, and Android operating system), it can support all encryption algorithms and can establish a VPN (Virtual Private Network) connection. Therefore, by assuming a public channel between the reader and the server in the improved protocol, the transferred messages are protected and the protocol remains secure. Furthermore, whether the database server is local or cloud-based has no significant impact on the improved protocol security.
6.2. Formal analysis
While in Section 6.1 we heuristically proved the security of the improved protocol against various attacks, in this section we use formal approaches to validate the robustness. To evaluate the security of a cryptography protocol, several formal methods are available from literature, which are either manual, such as GNY logic [46] and BAN logic [47] or automatic such as Scyther [48], AVISPA [49], Proverif [50] and CryptoVerif [51]. Among them, in this section, we use GNY logic – as a manual method – and Scyther tool – as an automated method – to analyze the security of the improved protocol formally, and both are widely accepted in literature to validate the security of a cryptographic protocol formally (e.g. see [52], [53], [54]).
6.2.1. Formal security evaluation through GNY logic
According to Table 3’s notations, the robustness of the improved protocol is deduced as below:
-
1.
The messages of the improved protocol are rewritten using GNY logic notations, as represent in Table 4.
-
2.
The plain messages are deleted that Table 5 shows the output.
-
3.
The improved protocol’s assumptions and goals are extracted, as represented in Table 6.
-
4.
Given messages and protocol assumptions and using GNY logic rules, we deduce security goals as depicted in Table 7.
Table 4.
Improved protocol messages’ GNY logic expression.
| # M. | Description |
|---|---|
Table 5.
Improved protocol messages’ idealization (M. denotes Message).
| # M. | Description |
|---|---|
Table 6.
Assumptions and security goals of improved protocol (A./G. denotes Assumption/Goal).
| # A./G. | Description |
|---|---|
Table 7.
Security goals deduction of the improved protocol.
| DN | GMA | UR | DD | GN |
|---|---|---|---|---|
| , , , | – | |||
| – | ||||
| , , , | ||||
| , , , | – | |||
| – | ||||
| , , , |
As presented in Table 7, according to rule of GNY logic and considering , we deduce that . Then, using and based on rule , it is deduced that . Given and based on rule , since is one-way function we deduce that . Considering and based on rule , it is deduced that which is the security goal. guaranties the integrity of the messages which are sent by through the insecure channel. According to rule of GNY logic and considering , we deduce that . Then, using and based on rule , it is deduced that . Given and based on rule , since is one-way function, we deduce that . Considering and based on rule , it is deduced that which is the security goal.Similar to , guaranties the integrity of the random number , which is sent by .
6.2.2. Formal security evaluation through Scyther tool
The Scyther tool as an automated security evaluation method is also considered as part of this analysis. The evaluation begins with the description of the improved protocol in the Security Protocol Description Language (SPDL) as the input for the Scyther tool. As Fig. 8 depicts, there is no security breach in the verification results and the robustness of the protocol has been confirmed.
Fig. 8.
Security results of improved protocol through the Scyther tool.
In reliance on the analysis results and security breaches reported for previous protocols, Table 8 compares the robustness of the improved protocol to other protocols against traceability, desynchronization, replay and secret disclosure attacks. As shown, the AE-based protocol can resist against attacks and has an acceptable security level.
Table 8.
Comparison of resistance to different attacks.
7. Hardware implementation
In order to better understand the impact of using different cryptography schemes on the proposed protocol, the FPGA and ASIC implementation of a tag were simulated. By the FPGA implementation, the very low-level information and fundamental building blocks of a proposed tag (e.g. Lookup Table (LUT) and Flipflop) were measured. In addition, ASIC implementation was also simulated, with the intention of having the manufacturing technology information and Gate Equivalent (GE) comparison.
For FPGA implementation, Vivado 2017.7 synthesis tool of Xilinx has been employed to synthesize the proposed cryptography algorithms on spartan-7 FPGA family of Xilinx of which Table 9 shows the results. However, as the aim of the proposed protocol is to introduce a new lightweight authentication protocol, the hardware implementation was simulated for five CAESAR finalist candidates with different use-cases. Namely, ACORN and ASCON from the lightweight use-case, OCB and AEGIS-128 from the high-performance category, and COLM from the defense-in-depth use-case have been selected. As an example, the schematic model of ACORN has been illustrated in Fig. 9 consisting of the encryption module, PRNG, XOR, and Concatenation functions, and the hardware implementation result is based not only on the encryption module but also covers a group of all mentioned components.
Table 9.
FPGA and ASIC implementation results, where SM and AE-P denote Security-module and AE-protocol respectively.
| Encryption scheme | FPGA |
ASIC |
|||||
|---|---|---|---|---|---|---|---|
| LUT | FlipFlop | Area (m) | Delay (ns) | Power (mW) | GE (SM) | GE (AE-P) | |
| ACORN | 731 | 476 | 23 321.49 | 1.42 | 1.003 | 3338 | 6743 |
| ASCON | 1540 | 980 | 41 962.73 | 0.59 | 1.167 | 12 157 | 15 565 |
| AEGIS-128 | 5582 | 1970 | 110 996.52 | 1.71 | 7.396 | 38 934 | 42 342 |
| OCB | 4124 | 1699 | 245 625.71 | 0.62 | 5.869 | 71 966 | 75 374 |
| COLM | 7535 | 2771 | 276 981.16 | 0.61 | 4.690 | 107 810 | 111 218 |
Fig. 9.
Schematic model of ACORN circuit.
In addition, the key-length and data-length of the encryption module have been considered, at 128-bit and 64-bit respectively. As shown in Table 9, in terms of the area of FPGA simulation, two lightweight candidates show the least LUT and are suitable for designing alightweight tag.
For ASIC implementation, the CMOS 90 nm technology was used in 1-round. The implementation target was set to reach a minimum area and maximum performance. Hence, the number of gates (GE), area overhead, power consumption, and delay are reported in Table 9.
By using ACORN, a given tag totally needs to accommodate 6743 gates for all components (named AE-Protocol) that 3408 gates are used to implement PRNG and logical functions, and 3335 gates for the ACORN cryptography module (named Security-module). It is worth noting that 3335 gates are the total amount of a complete encryption module, including cipher core, pre-processor and post-processor. The results of other encryption schemes are listed in Table 9 and it is clear that the proposed protocol could be applicable in different domains and applications.
In order to have a clearer picture of the tag’s weight and required area on a chip, Fig. 10 compares five candidates based on LUT and GE.
Fig. 10.
Area Comparison based on FPGA and ASIC results.
As expected – and as shown in the chart – both CAESAR lightweight schemes (i.e. ACORN and ASCON) utilize the least amount of hardware circuits to implement an RFID tag. However, the number of LUT of the new protocol is greater than LUT in Fanet al. and SecLAP, a lightweight tag needs roughly 3K to 4K GE for the security module [55]. Hence, the proposed protocol can satisfy the lightweight requirements and the results prove that it is applicable in other domains of IoT with minimum resource consumption.
8. Discussion and conclusion
At the starting point of this paper, we have looked at illicit trade in fake goods as a major challenge in the global economy, and discussed IoT technologies as a mean to combat this risk and help maintain a secure supply chain. While the presented scenario relies on compromising the supply chain integrity for COVID-19 test kits, the reader is aware that the same malicious attacks could be conducted in any supply chain; raising the importance of securing the supporting IT infrastructure.
Within the scope of this paper, we have focused on the data capture/sensing layer of an IoT infrastructure and explored the recent development of secure authentication and communication protocols to prevent malicious attacks. Accordingly, we have presented a traceability and passive secret disclosure attacks against the studied protocols (e.g. SecLAP) where we extracted all secret parameters with the complexity of . In fact, attempting to increase the robustness of current protocols by improving the way messages are calculated, while keeping their basic structure would just provide incremental improvements, and would not prevent ways to break them. By their nature, we believe that the weak-point of ultra-lightweight protocols is the structure of bit-oriented functions. Therefore, we proposed an AE lightweight uncomplicated improved protocol that employs a cryptosystem able to satisfy the hardware requirements of lightweight tags. Informal and formal security evaluations to show the robustness of the protocol were also provided. The security analysis and hardware implementation results were also presented to validate our work. More specifically, we simulated the structure of a tag (FPGA and ASIC) under five encryption schemes and measured its hardware requirement as a candidate for constrained environments. While the scope of the discussion was limited to passive UHF RFID technologies, similar research may be conducted for ensuring the data integrity gathered from other technologies used (a) in different activities of a supply chain (b) at all the layers of the supporting IoT infrastructure. For instance, for the data capture/sensing layer, numerous competitive technologies and techniques are available to develop counterfeit-proof packaging. For instance, passive HF RFID tags for NFC (Near Field Communications) are increasingly used in retail applications for security purposes as well as a means to interact with customers. Otherwise, with billions of bar codes scanned every day one can rightly argue that automatic recognition technologies such as bar codes should be considered as a stand-alone or as a complementary technology to prevent counterfeiting. This is particularly true for innovative covert bar codes using inks that fluoresce when exposed to ultraviolet (UV) or infrared (IR) light. Since they cannot be detected or duplicated by commonly available methods, covertly printed two-dimensional (2D) QR or Data Matrix codes can be used to replicate the ID encoded in the RFID tag applied or integrated into the packaging. At the point of use, there is therefore a need to have a reader equipped with an RFID module as well as a UV–IR lighting module to illuminate and decipher the code using the proper decoding algorithms. More recently we have also witnessed the availability of invisible bar code hidden into colored surfaces (e.g. Digimarc Barcode) that carries the same data as 2D Data Matrix codes and repeated across the entire surface of thermal-printed labels. With the compatibility of numerous cameras and scanners, existing reading devices would then need to be upgraded by installing the required automatic content recognition software to unlock the code and verify it. This last step can also be done using a track & match application with related information hosted on an IoT platform. Otherwise, security issues of “less constrained devices” could be explored, including electronic data loggers used to verify the end-to-end condition compliance in a distribution channel or active RFID tags used for wireless monitoring of environmental fluctuations with real-time alert capabilities. These devices rely on other technologies and use other authentication and communication protocols, but all of them may be vulnerable to security breaches. Whatever the selected identification–authentication technology, stakeholders may also want to track the progress of the products (i.e. COVID-19 kits) throughout the supply chain, using ubiquitous cloud based-IoT traceability platforms. As these platforms constitute another layer in the IoT Infrastructure (Fig. 1), they are used to store critical information and prevent counterfeit and pirated goods, but, they may themselves constitute another target in the design of a secure solution. This has raised higher requirements for data encryption, and the design of secure public key encryption schemes for securing sharing of sensitive data in the cloud [56], [57] as well for the development of lightweight AE scheme to prevent unauthorized data manipulation (i.e. data integrity) and access to information hosted on the cloud (i.e. data confidentiality) [58], [59] Security and privacy become even more important, as healthcare organizations are increasingly targeted by cyberattacks leading experts to call for national standards in “battle” against healthcare data security breaches [60]. In this context, this is no surprise that the Canadian Centre for Cybersecurity released a warning that the COVID-19 pandemic presents an elevated level of risk to the cybersecurity of Canadian health organizations involved in the national response to the pandemic [61]. But while organizations are warned to apply cyber defense best practices, they mainly analyze their monitoring of network logs, monitor the behavior of their servers, and address security vulnerabilities as they discover them — but they never look at the thousands of sensors evolving in their own ecosystem.
CRediT authorship contribution statement
Masoumeh Safkhani: Conception and design of study, Acquisition of data, Analysis and/or interpretation of data, Writing - original draft, Writing - review & editing. Samad Rostampour: Conception and design of study, Acquisition of data, Analysis and/or interpretation of data, Writing - original draft, Writing - review & editing. Ygal Bendavid: Conception and design of study, Acquisition of data, Analysis and/or interpretation of data, Writing - original draft, Writing - review & editing. Nasour Bagheri: Conception and design of study, Acquisition of data, Analysis and/or interpretation of data, Writing - original draft, Writing - review & editing.
Declaration of Competing Interest
No author associated with this paper has disclosed any potential or pertinent conflicts which may be perceived to have impending conflict with this work. For full disclosure statements refer to https://doi.org/10.1016/j.comnet.2020.107558.
Acknowledgments
The authors would like to thank the reviewers for their time spent on reviewing our manuscript and their thoughtful comments towards improving our manuscript. All authors approved the version of the manuscript to be published.
Biographies

Masoumeh Safkhani is an assistant professor at Computer Engineering Department, Shahid Rajaee Teacher Training University, Tehran, Iran. She received her Ph.D. in electrical engineering from Iran University of Science and Technology, 2012, with the security analysis of RFID protocols as her major field. Her current research interests include the security analysis of lightweight and ultra-lightweight protocols, targeting constrained environments such as RFID, IoT, VANET and WSN. She is the author/coauthor of more than 50 technical articles in information security and cryptology in major international journals and conferences.

Samad Rostampour is a professor at Vanier College, Montréal-Canada and a Researcher at IoT Laboratory in the department of Analytics, Operations & Information Technology (AOTI) / School of Management (ESG) at the Université du Québec à Montréal (UQAM). He works in the design and the implementation of IoT systems. Prior to join the IoT Lab., Samad completed his Ph.D. in computer systems architecture where he worked on the security of RFID systems. As a specialist in RFID/IoT he is a member of the judges for RFID Journal awards.

Ygal Bendavid is a full professor in the department of Analytics, Operations & Information Technology (AOTI)/School of Management (ESG) at the Université du Québec à Montréal (UQAM) - Canada. Dr. Bendavid holds M.Sc. and Ph.D. degrees in industrial engineering from the École Polytechnique de Montréal. He is the director of the IoT Lab, a collaborative applied research environment with the goal to develop and share an expertise in IoT. As a specialist in RFID/IoT he is a frequent presenter at RFID Journal LIVE! Conferences, and a member of the judges for RFID Journal awards.

Nasour Bagheri is an associate professor at the Electrical Engineering Department, Shahid Rajaee Teacher Training University, Tehran, Iran. He is also a part-time researcher with the Institute for Research in Fundamental Sciences (IPM). Nasour Bagheri received the M.S. and Ph.D. degrees in electrical engineering from the Iran University of Science and Technology (IUST), Tehran, Iran, in 2002 and 2010, respectively. He is the author of more than 100 articles in information security and cryptology. His research interests include cryptology, more precisely, designing and analysis of symmetric schemes, such as lightweight ciphers, e.g., block ciphers, hash functions, and authenticated encryption schemes, cryptographic protocols for constrained environments, such as RFID tags and the IoT edge devices and hardware security, e.g., the security of symmetric schemes against side-channel attacks, such as fault injection and power analysis.
Appendix. Fan et al. ’s protocol
In this section, we explain Fan et al.’s protocol and investigate its security level against secret disclosure and traceability attacks. Moreover, we evaluate the protocol in the ROM and showed that the adversary’s advantage to distinguish it from an ideal protocol, is , where is the complexity of eavesdropped messages. Although Fan et al.’s protocol is already known to be insecure, this is another look at the protocol which provides better understanding of the design.
A.1. Cro. function
Fan et al. introduced a special bit-oriented operation in their protocol, called . Assuming that and as the binary representation of and respectively, where denotes the th bit of string . Since the operation is defined as below, for :
We provide an example to show the functionality of as follows:
Based on this expression, the length of will be equal to the length of and which is twice that of or . On the other hand, later we see that this function is used to update a secret value as which makes a confusion, because the length of then will be twice that of the length of . However, per our personal communication with the protocol designers[62], they stated that to reduce the length of the produced , XOR operation is performed on the top and the bottom of the operation result, see Fig. A.11. Hence, the length of and would be the same before the next round of authentication is begun.
Fig. A.11.
To reduce the output length of [62].
A.2. Protocol description
The Fanet al. authentication protocol, as depicted in Fig. A.12, is executed as follows:
Fig. A.12.
Mutual authentication phase of Fan et al.’s protocol [27].
-
1.
The reader starts the authentication process by generating a new random number and sending it along with to the tag.
-
2.Once the tag receives the message, it:
-
•generates a random number ;
-
•computes ;
-
•sets
-
•and sends and to the reader;
-
•
-
3.
Upon receipt of the message, the reader stores and sends , and to the server.
-
4.When the server receives the message, it:
-
•stores and ;
-
•searches its database for any entry related to received ;
-
•generates another random number ;
-
•computes , and sends them to the reader.
-
•
-
5.Once the reader receives the message, it:
-
•retrieves and from and respectively;
-
•computes and checks whether it equals with the received ; if it does not then it stops the protocol, otherwise calculates ;
-
•and sends and to the tag;
-
•
-
6.Once receipt the message, the tag:
-
•retrieves as ;
-
•checks whether the retrieved equals with its or not; if it does not then it stops the protocol, otherwise updates the key as ;
-
•computes ;
-
•and sends to the reader.
-
•
-
7.When the reader receives the message, it:
-
•calculates and checks whether it is equal to the corresponding received value or not; if it does not then it terminates the protocol, otherwise updates as
-
•and sends to the server.
-
•
-
8.Once the server receives the message, it:
-
•calculates and checks whether it equals to the corresponding received value or not; if it does not then it terminates the protocol otherwise updates as ;
-
•and sends to the reader.
-
•
-
9.
Upon receipt of the message, the reader extracts , verifies it and if the verification is passed, the reader sends to the tag.
-
10.
The tag verifies the correctness of by computing and if passes the verification, the tag sets and sends to the server through the reader.
-
11.The server:
-
•checks whether equals to , if it is, a new record will be generated and added in the database;
-
•sends a record completion notification to the tag via the reader.
-
•
-
12.
When the tag received the message, sets .
A.3. Secret disclosure and traceability attacks
Fan et al.’s protocol has trivial vulnerabilities, also reported by Aghili and Mala [28]. More precisely, consider a passive adversary which only eavesdrops the transferred messages between a legitimate reader and the target tag . In this case, the adversary achieves the following set of information that is transferred over an insecure channel between and :
-
•
is sent from to ;
-
•
and are sent from to ;
-
•
and are sent from to ;
-
•
is sent from to ;
-
•
is sent from to ;
-
•
is sent from to ;
Given the above information, it would be trivial to extract, and , as follows:
Given that is a constant parameter which determines the tag identity, it can be employed to trace the tag holder. This fact compromises the security of the protocol against traceability and tag anonymity.
Remark
This attack does not depend on the definition of and works for any . Hence it is not possible to improve the security of the protocol against this attack by only using a more complicated function instead of the current .
On the other hand, on Step 6, the tag sends to the reader over public channel. Now assume that the adversary also eavesdrops that message between and , where the values of and have been extracted by the adversary already.
Given , we denote for simplicity, i.e. its th bit. Given that any , for an even value of , we can extract the following equations, for different cases of :
| (A.1) |
where is the length of parameters in the protocol, e.g. . In Eq. (A.1), exclude for , all variables are known. Hence, will be retrieved easily from that linear equations. Given , the reader anonymity is compromised.
Remark
It should be noted the success probability of the presented attack to recover depends on the exact definition of . Hence, it may be possible to improve the security of the protocol against this attack by only using a more complicated function instead of the current .
A.4. Fan et al. ’s protocol distinguishability in ROM
Any cryptographic scheme is expected to behave unpredictable form the adversary’s point of view. To model this property, indistinguishability from a random oracle is used, which we defined in Section 2.2. In this section, we show that Fan et al.’s protocol is not a secure protocol in ROM. Given that for any value of we can state that , Eq. (A.1) can be rewritten as follows:
| (A.2) |
It is clear that, for and for even values of , and . This property can be used as a metric to determine that the used protocol is the Fan et al.’s protocol and not . Moreover, Fan et al.’s protocol has zero-sum property. More precisely, it is easy to show that:
| (A.3) |
It comes for the fact that any variable appears in the above summation exactly two times, e.g. or , and for any and any value of we have . This property can be used as a metric to determine that the used protocol is the Fan et al.’s protocol or .
To distinguish Fan et al.’s protocol from , the adversary does as follows:
-
1.
eavesdrops a message produced by function, transferred over channel, e.g. .
-
2.
if returns ; otherwise returns .
To determine the adversary’s advantage, it is clear that if the adversary communicates with Fan et al.’s protocol then with the probability of ‘1’ returns in Step 2 while if it communicates with then returns with the probability of ‘2−1’. To improve the adversary’s advantage, we can increase the number of eavesdropped messages. For an adversary who eavesdropped messages, all produced by function, the advantage will be as follows: which is the maximum advantage that an adversary can get after queries. Hence, Fan et al.’s protocol has security flaws in ROM.
References
- 1.OECD and E.U.I.P. Office . OECD Publishing; 2019. Trends in Trade in Counterfeit and Pirated Goods; p. 84. [Google Scholar]
- 2.FDA . 2020. Counterfeit medicine. https://www.fda.gov/drugs/buying-using-medicine-safely/counterfeit-medicine. Accessed: 2020-06-07. [Google Scholar]
- 3.Behner P., Hecht M.-L., Wahl F. PWC; 2020. Fighting Counterfeit Pharmaceuticals. https://www.strategyand.pwc.com/gx/en/insights/2017/fighting-counterfeit-pharmaceuticals/fighting-counterfeit-pharmaceuticals.pdf. Accessed: 2020-06-07. [Google Scholar]
- 4.Interpol . Interpol; 2020. Global Operation Sees a Rise in Fake Medical Products Related to COVID-19. https://www.interpol.int/en/News-and-Events/News/2020/Global-operation-sees-a-rise-in-fake-medical-products-related-to-COVID-19. Accessed: 2020-06-07. [Google Scholar]
- 5.FDA . FDA Press release; 2020. Coronavirus (COVID-19) Update: FDA Alerts Consumers About Unauthorized Fraudulent COVID-19 Test Kits. Accessed: 2020-06-07. [Google Scholar]
- 6.Bendavid Y. RFID-enabled applications to improve the delivery of healthcare services: a typology and supporting technologies. J. Med. Biol. Eng. 2013;33(5):433–442. [Google Scholar]
- 7.Kang S., Baek H., Jung E., Hwang H., Yoo S. Survey on the demand for adoption of Internet of Things (IoT)-based services in hospitals: Investigation of nurses’ perception in a tertiary university hospital. Appl. Nurs. Res. 2019;47:18–23. doi: 10.1016/j.apnr.2019.03.005. [DOI] [PubMed] [Google Scholar]
- 8.FutureMarketInsight . Future Market Insight; 2020. Radio-Frequency Identification (RFID) in Pharmaceuticals Market. https://www.futuremarketinsights.com/reports/rfid-in-pharmaceuticals-market. Accessed: 2020-06-07. [Google Scholar]
- 9.Coustasse A., Kimble C.A., Stanton R.B., Naylor M. Could the pharmaceutical industry benefit from full-scale adoption of radio-frequency identification (RFID) technology with new regulations? Perspect. Health Inf. Manage. 2016;13(Fall) [PMC free article] [PubMed] [Google Scholar]
- 10.L. of Congress . Congress.gov; 2020. Drug Quality and Security Act. https://www.congress.gov/bill/113th-congress/house-bill/3204. Accessed: 2020-06-07. [Google Scholar]
- 11.FDA . Food and Drug Administration; 2020. Drug Supply Chain Security Act (DSCSA) https://www.fda.gov/drugs/drug-supply-chain-integrity/drug-supply-chain-security-act-dscsa. Accessed: 2020-06-07. [Google Scholar]
- 12.Tewari A., Gupta B. Security, privacy and trust of different layers in internet-of-things (IoTs) framework. Future Gener. Comput. Syst. 2018 [Google Scholar]
- 13.Dachyar M., Zagloel T.Y.M., Saragih L.R. Knowledge growth and development: internet of things (IoT) research, 2006–2018. Heliyon. 2019;5(8) doi: 10.1016/j.heliyon.2019.e02264. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.GS1 . GS1; 2020. Identification of Investigational Products in Clinical Trials Application Standard. https://www.gs1.org/docs/barcodes/GS1_ClinicalTrial_Application_Standard.pdf. Accessed: 2020-06-07. [Google Scholar]
- 15.Li C.-T., Weng C.-Y., Lee C.-C. A secure RFID tag authentication protocol with privacy preserving in telecare medicine information system. J. Med. Syst. 2015;39(8):77. doi: 10.1007/s10916-015-0260-0. [DOI] [PubMed] [Google Scholar]
- 16.Benssalah M., Djeddou M., Drouiche K. Security analysis and enhancement of the most recent RFID authentication protocol for telecare medicine information system. Wirel. Pers. Commun. 2017;96(4):6221–6238. [Google Scholar]
- 17.Zhou Z., Wang P., Li Z. A quadratic residue-based RFID authentication protocol with enhanced security for TMIS. J. Ambient Intell. Humaniz. Comput. 2019;10(9):3603–3615. [Google Scholar]
- 18.Zheng L., Song C., Cao N., Li Z., Zhou W., Chen J., Meng L. A new mutual authentication protocol in mobile RFID for smart campus. IEEE Access. 2018;6:60996–61005. [Google Scholar]
- 19.Safkhani M., Vasilakos A. A new secure authentication protocol for telecare medicine information system and smart campus. IEEE Access. 2019;7:23514–23526. [Google Scholar]
- 20.Liao Y.-P., Hsiao C.-M. A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Netw. 2014;18:133–146. [Google Scholar]
- 21.Zhao Z. A secure RFID authentication protocol for healthcare environments using elliptic curve cryptosystem. J. Med. Syst. 2014;38(5):46. doi: 10.1007/s10916-014-0046-9. [DOI] [PubMed] [Google Scholar]
- 22.Chou J.-S. An efficient mutual authentication RFID scheme based on elliptic curve cryptography. J. Supercomput. 2014;70(1):75–94. [Google Scholar]
- 23.Zhang Z., Qi Q. An efficient RFID authentication protocol to enhance patient medication safety using elliptic curve cryptography. J. Med. Syst. 2014;38(5):47. doi: 10.1007/s10916-014-0047-8. [DOI] [PubMed] [Google Scholar]
- 24.Farash M.S. An improved password-based authentication scheme for session initiation protocol using smart cards without verification table. Int. J. Commun. Syst. 2017;30(1) [Google Scholar]
- 25.Fotouhi M., Bayat M., Das A.K., Far H.A.N., Pournaghi S.M., Doostari M. A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Comput. Netw. 2020 [Google Scholar]
- 26.Arfaoui A., Kribeche A., Senouci S.-M. Context-aware anonymous authentication protocols in the internet of things dedicated to e-health applications. Comput. Netw. 2019;159:23–36. [Google Scholar]
- 27.Fan K., Jiang W., Li H., Yang Y. Lightweight RFID protocol for medical privacy protection in IoT. IEEE Trans. Ind. Inform. 2018;14(4):1656–1665. [Google Scholar]
- 28.Aghili S.F., Mala H. 2018. Security Analysis of Fan et al. Lightweight RFID Authentication Protocol for Privacy Protection in IoT: Cryptology ePrint Archive, Report 2018/388. https://eprint.iacr.org/2018/388. [Google Scholar]
- 29.Aghili S.F., Mala H., Kaliyar P., Conti M. SecLAP: Secure and lightweight RFID authentication protocol for medical IoT. Future Gener. Comput. Syst. 2019;101:621–634. [Google Scholar]
- 30.Tanveer M., Abbas G., Abbas Z.H., Waqas M., Muhammad F., Kim S. S6AE: Securing 6LoWPAN using authenticated encryption scheme. Sensors. 2020;20(9):2707. doi: 10.3390/s20092707. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.Bellare M., Rogaway P. In: 1st Conference on Computing and Communications Security. Ashby V., editor. ACM Press; 1993. Random oracles are practical : A paradigm for designing efficient protocols; pp. 62–73. [Google Scholar]
- 32.Maurer U.M., Renner R., Holenstein C. In: First Theory of Cryptography Conference, TCC. Naor M., editor. vol. 2951. Springer; 2004. Indifferentiability, impossibility results on reductions, and applications to the random oracle methodology; pp. 21–39. (Lecture Notes in Computer Science). [Google Scholar]
- 33.Jahanbani M., Bagheri N., Norouzi Z. Lightweight implementation of SILC, CLOC, AES-JAMBU and COLM authenticated ciphers. Microprocess. Microsyst. 2020;72 [Google Scholar]
- 34.CAESAR . 2014. CAESAR: Competition for authenticated encryption: Security, applicability,and robustness. Updated on: 2019-02-20. http://competitions.cr.yp.to/caesar.html. [Google Scholar]
- 35.AES . 1997. AES: the advanced encryption standard. http://competitions.cr.yp.to/aes.html. [Google Scholar]
- 36.CAESAR . 2004. ESTREAM: the ECRYPT stream cipher project. http://competitions.cr.yp.to/caesar.html. [Google Scholar]
- 37.SHA3 . 2007. SHA-3: a secure hash algorithm. http://competitions.cr.yp.to/sha3.html. [Google Scholar]
- 38.PHC . 2013. PHC: Password hashing competition. https://password-hashing.net/ [Google Scholar]
- 39.C.S.R. Center . Lightweight Cryptography. Springer; 2019. NIST lightweight cryptography standardization process; pp. 2–3. accessed 01 Novamber 2019. [Google Scholar]
- 40.Wu H. Candidate for the CAESAR Competition. 2016. ACORN: a lightweight authenticated cipher (v3) See also https://competitions.cr.yp.to/round3/acornv3.pdf. [Google Scholar]
- 41.Dobraunig C., Eichlseder M., Mendel F., Schläffer M. CAESAR First Round Submission, March. 2014. Ascon v1. 2. submission to the CAESAR competition. [Google Scholar]
- 42.Wu H., Preneel B. International Conference on Selected Areas in Cryptography. Springer; 2013. AEGIS: A fast authenticated encryption algorithm; pp. 185–201. [Google Scholar]
- 43.Krovetz T., Rogaway P. Submission to the CAESAR Competition. 2016. OCB (v1. 1) [Google Scholar]
- 44.Andreeva E., Luykx A., Mennink B. 2016. COLM v1. [Google Scholar]
- 45.Jean J., Nikolic I., Peyrin T., Seurin Y. Deoxys v1. 41. CAESAR. 2016 https://competitions.cr.yp.to/round1/deoxysv1.pdf. [Google Scholar]
- 46.Gong L., Needham R., Yahalom R. Research in Security and Privacy, IEEE Computer Society Symposium on. IEEE; 1990. Reasoning about belief in cryptographic protocols; pp. 234–248. [Google Scholar]
- 47.Burrows M., Abadi M., Needham R. Digital Equipment Systems Research center; Palo Alto, California: 1989. BAN a Logic of Authentication: Technical report 39. [Google Scholar]
- 48.Cremers C.J.F. Computer Aided Verification. Springer Berlin Heidelberg; 2008. The scyther tool: Verification, falsification, and analysis of security protocols; pp. 414–418. [Google Scholar]
- 49.Armando A., Basin D., Boichut Y., Chevalier Y., Compagna L., Cuéllar J., Drielsma P.H., Héam P.-C., Kouchnarenko O., Mantovani J., et al. International Conference on Computer Aided Verification. Springer; 2005. The AVISPA tool for the automated validation of Internet security protocols and applications; pp. 281–285. [Google Scholar]
- 50.Blanchet B., Chaudhuri A. Security and Privacy, IEEE Symposium on. IEEE; 2008. Automated formal analysis of a protocol for secure file sharing on untrusted storage; pp. 417–431. [Google Scholar]
- 51.Blanchet B. Dagstuhl Seminar “Formal Protocol Verification Applied”. 2007. CryptoVerif: Computationally sound mechanized prover for cryptographic protocols; p. 117. [Google Scholar]
- 52.Ma Y., Yan L., Huang X., Ma M., Li D. DTLShps: SDN-based DTLS handshake protocol simplification for IoT. IEEE Internet Things J. 2020;7(4):3349–3362. [Google Scholar]
- 53.Vijaykumar V.R., Sekar S.R., Elango S., Ramakrishnan S. Implementation of modulo adder based RFID mutual authentication protocol. IEEE Trans. Ind. Electron. 2018;65(1):626–635. doi: 10.1109/TIE.2017.2711864. [DOI] [Google Scholar]
- 54.Islam S.H., Vijayakumar P., Bhuiyan M.Z.A., Amin R., Rajeev M.V., Balusamy B. A provably secure three-factor session initiation protocol for multimedia big data communications. IEEE Internet Things J. 2018;5(5):3408–3418. doi: 10.1109/JIOT.2017.2739921. [DOI] [Google Scholar]
- 55.Sundaresan S., Doss R., Piramuthu S., Zhou W. A robust grouping proof protocol for RFID EPC C1G2 tags. IEEE Trans. Inf. Forensics Secur. 2014;9(6):961–975. [Google Scholar]
- 56.Yu Z., Gao C.-z., Jing Z., Gupta B.B., Cai Q. A practical public key encryption scheme based on learning parity with noise. IEEE Access. 2018;6:31918–31923. [Google Scholar]
- 57.Li Z., Zhao M., Jiang H., Xu Q. Keyword guessing on multi-user searchable encryption. Int. J. High Perform. Comput. Netw. 2019;14(1):60–68. [Google Scholar]
- 58.Kumar A., Gupta S. 2018 IEEE 8th International Advance Computing Conference (IACC) IEEE; 2018. A secure technique of image fusion using cloud based copyright protection for data distribution; pp. 228–232. [Google Scholar]
- 59.Zheng Q., Wang X., Khan M.K., Zhang W., Gupta B.B., Guo W. A lightweight authenticated encryption scheme based on chaotic scml for railway cloud service. IEEE Access. 2017;6:711–722. [Google Scholar]
- 60.Burke D. Radio-Canada; 2020. Cyber Threats to Canadian Health Organizations. Alert Number: AL20-008. https://www.cbc.ca/news/canada/nova-scotia/hospitals-health-care-cybersecurity-federal-government-funding-1.5493422. Accessed: 2020-06-02. [Google Scholar]
- 61.C.C. for Cyber Security . Canadian Center for Cyber Security; 2020. Hospitals ‘Overwhelmed’ by Cyberattacks Fuelled by Booming Black Market. https://cyber.gc.ca/en/alerts/cyber-threats-canadian-health-organizations. Accessed: 2020-06-07. [Google Scholar]
- 62.Fan K. 2018. Email: clarification of personal communication. [Google Scholar]