Abstract
With the rapid development of mobile networks, there are more and more application scenarios that require group communication. For example, in mobile edge computing, group communication can be used to transmit messages to all group members with minimal resources. The group key directly affects the security of the group communication. Most existing group key agreement protocols are often flawed in performance, scalability, forward or backward secrecy, or single node failure. Therefore, this paper proposes a blockchain-based authentication and dynamic group key agreement protocol. With our protocol, each group member only needs to authenticate its left neighbor once to complete the authentication, which improved authentication efficiency. In addition, our protocol guarantees the forward secrecy of group members after joining the group and the backward secrecy of group members after leaving the group. Based on blockchain technology, we solve the problem of single node failure. Furthermore, we use mathematics to prove the correctness and security of our protocol, and the comparison to related protocols shows that our protocol reduces computation and communication costs.
Keywords: authentication, blockchain, cryptography, group key agreement
1. Introduction
With the rapid development of mobile networks, the secure transmission of data is no longer limited to both parties in communication, but is required in group communication. Group communication can transmit messages to all group members with minimal resources [1]. This is because the sending of the message only needs to be broadcast once within the group, instead of sending the same message to all group members one by one, which results in a significant increase in communication efficiency. In order to reduce network latency in cloud computing, Mobile Edge Computing (MEC) [2] is introduced. In MEC, the Small Cell Manager (SCM) needs to dynamically and elastically manage the computing and/or storage resources of multiple Small Cell Clouds (SCCs) [3]. Therefore, the use of group communication can greatly improve the efficiency of MEC.
In order to provide a reliable and scalable group communication service, the most basic and critical security issue is access control [4]. In most cases, access control can be achieved by encrypting or decrypting messages, because only legitimate group members can get the key and use this to decrypt the ciphertext to access the messages [5,6]. Therefore, in order to ensure efficient and secure communication in the group, all group members need to use the same session key, which is also called the group key. This means that the group key agreement protocol directly affects the security and efficiency of group communication.
In recent years, many researchers have proposed many authentication and group key agreement protocols. However, according to the research of [7,8], we found that most of these protocols have the following defects: (1) performance: before the group key is negotiated, mutual authentication is usually required between group members, which may consume much of the computation and communication costs; (2) scalability: the protocol cannot efficiently handle the joining or leaving of group members, which results in the poor scalability of the protocol; (3) forward or backward secrecy: it is difficult to guarantee the forward or backward secrecy of group members after joining or leaving the group, such as [9]; (4) single node failure: since most existing protocols store the registration information of all group members in a single node, these protocols are vulnerable to the problem of single node failure. Therefore, these protocols are not suitable for MEC. We design a blockchain-based authentication and dynamic group key agreement protocol to solve the above problems in this paper. The protocol has the following characteristics:
In our protocol, before negotiating the group key, each group member only needs to authenticate its left neighbor once and perform batch authentication once, instead of implementing mutual authentication between group members, which reduces much of the computation and communication costs.
The blockchain can be regarded as a shared distributed ledger [10], which can effectively solve the problem of single node failure. Therefore, we use the blockchain to store the public parameters and registration information of all group members. This allows our protocol to solve the problem of single node failure, while also making all the parameters and information stored in the blockchain unmodifiable [11]. In addition, based on blockchain technology, group members can join any group in the entire system after completing registration on any server, which improves convenience.
In our protocol, when group members join or leave a group, they only needs to update the parameters of an adjacent group member, which also improves the scalability of our protocol.
Our protocol guarantees the forward secrecy of group members after joining the group and the backward secrecy of group members after leaving the group.
The rest of this article is arranged as follows. Section 2 describes the related works. Some preliminaries are introduced in Section 3. The proposed protocol is described completely in Section 4. Section 5 analyzes the security of our protocol. The performance analysis is shown in Section 6. Finally, we conclude the article in Section 7.
2. Related Works
Many researchers have proposed many solutions to ensure the security of group keys. These solutions are generally divided into the following three types [12,13].
-
(1)
Centralized group key agreement protocol:
There is usually only one entity for controlling the entire group in this type of protocol, which is called a Key Distribution Center (KDC). The KDC is responsible for key generation, distribution, and management. It also needs to be responsible for tasks such as group communication. The protocol proposed by Wong et al. [14] is a typical group key agreement protocol based on a Logical Key Hierarchy (LKH). A binary tree is stored in the KDC of this type of protocol. The root node of the tree is a shared encryption key; the intermediate nodes of the tree hold different keys along the path from the leaves to themselves; and the leaf nodes of the tree hold keys related to group members. This type of protocol requires less space to store the keys, and when the keys need to be updated, the amount of communication is greatly reduced. The group key agreement protocol of Islam et al. [7] is proposed for the Internet of Vehicles, and the trusted authority in their protocol acts as the KDC. In the centralized group key agreement protocol, since the KDC needs to be responsible for storing and distributing all keys and controlling group communication, the scalability and storage costs of this type of protocol are very large. In addition, once the KDC fails, the entire system cannot continue to operate normally.
-
(2)
Decentralized group key agreement protocol:
This type of protocol usually divides the entire group into several subgroups, and each subgroup has a group controller to manage all group members in the subgroup. In this way, the burden of KDC is greatly reduced, and single node failure is also solved. Mittra [15] proposed a scalable multicast framework, which divides large groups into multiple subgroups, and each subgroup has a controller called a group security intermediate node or a group security agent. In the protocol of Setia et al. [16], the group key is updated at regular intervals, rather than when group members join or leave. Naresh et al. [8] proposed a cluster-based hybrid group key agreement protocol, which divides large groups into a certain number of clusters and specifies the last member of the cluster as the cluster head and group controller. In 2018, Gupta et al. [17] proposed a group key agreement protocol based on self-certified public keys. In their protocol, there is a group controller for each group. Moreover, before generating the group key, each group member needs to mutually authenticate with other group members, which leads to high computation and communication costs. Zheng et al. [18] proposed a multi-domain group key agreement protocol. Their protocol uses authentication between group members and a group controller instead of authentication between each group member to reduce computation and communication costs. However, this makes their protocol vulnerable to single node failure. The main problems faced by decentralized group key agreement protocols are key distribution efficiency, how to establish a trusted relationship with a third party, and mutual authentication of sub-members across groups.
-
(3)
Distributed group key agreement protocol:
All group members in this type of protocol are equal, and there is no group controller. In addition, the KDC usually does not participate in the generation of group keys. Without a base station, Wang et al. [19] proposed a device-to-device group key agreement protocol. The protocol guarantees the anonymity of each device and uses a signature scheme based on the gap Diffie–Hellman group [20]. In 2018, Zhang et al. [21] proposed a distributed group key agreement protocol. Their agreement achieves cross-domain authentication and key self-certification. Based on the hyper elliptic curve digital signature and ElGamal algorithm, Kavitha et al. [22] proposed a distributed group authentication protocol for the healthcare system in the Internet of Things. Since the KDC or group controller in this type of protocol usually does not participate in the process of group key generation, the mutual authentication between group members becomes the largest computational overhead, which means that the cost of generating a group key will increase as the number of group members increases. Therefore, reducing the number of mutual authentications between group members is the core of reducing the cost of generating a group key. There are many protocols dedicated to reducing the number of authentications between group members by reducing the number of authentication rounds. The group key agreement protocol proposed by Geng et al. [23] and Zheng et al. [9] divides the entire protocol into two rounds. The first round is mutual authentication between members, and the second round is group key generation. In the above two protocols, each group member only needs to authenticate the two adjacent group members. The protocol proposed by Zhang et al. [24] and Shi et al. [25] merges the two processes described above into one. The protocol proposed by Alphonse and Reddy [26] forms each group member into a structure similar to a binary tree, and all group members authenticate each other from the leaf node to the root node. Although their protocol reduces the computation and communication costs required to generate group keys, all group members must wait for the final root node to be authenticated before they can negotiate the group key. Therefore, the computing time is still not low.
3. Preliminaries
3.1. Network Model
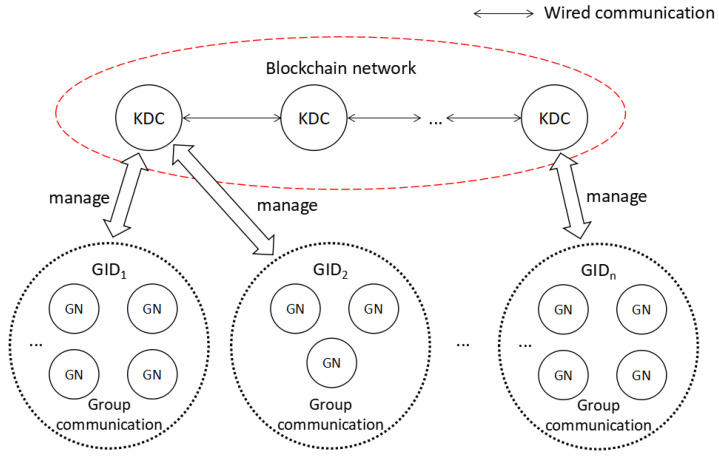
There are two parts in our network model, namely KDC and General Node (). In MEC, the KDC can be regarded as the SCM, and the can be regarded as the SCC. All s are equal, and there is no hierarchy or subordinate relationship. In addition, all s usually have certain computing and storage resources, and they can join or leave a group at any time. All KDCs are wire connected, and each KDC can manage one or more s. The network model used in our protocol is shown in Figure 1.
Figure 1.
The network model used by our protocol.
In our protocol, multiple KDCs form a blockchain network. In order to improve the efficiency of new block generation, we consider using a more efficient Proof-of-Stake (PoS) [27] or Delegated Proof-of-Stake (DPoS) [28] consensus mechanism, such as ouroboros, a provably secure PoS protocol [27], instead of using a Proof-of-Work (PoW) mechanism [29]. According to this consensus mechanism, at regular intervals, all KDCs will regenerate new blocks including groups whose s have changed during this period. In each block, in addition to the hash value of the previous block, the timestamp, and Merkle tree root, it also contains the identifier of these groups, the identity list of all s in these group, and the related parameters of all s in these group. All s only have the permission to read information from the blockchain. In addition, there may be multiple different groups, so after the enters the network, it first needs to select a group to join.
Before the joins the network, it can submit its identity to a KDC closest to it. The KDC will calculate a pair of keys based on the identity and distribute it to the . After that, all KDCs will generate a new block containing the identity and related information of the newly added through the consensus mechanism. The detailed operation of KDCs is described in the next section. Note that not all KDCs participate in group key agreement.
3.2. Threat Model
We define the threat model as follows:
The adversary has the ability to intercept all data transmitted over unsecured channels, and he/she can inject new data and replace or replay the previously sent data.
All KDCs are semi-trusted parties, which means that they may misbehave themselves, but do not conspire with any other KDC [30].
With the help of a Tamper-Proof Device (TPD), we assume that even if the adversary compromises the KDC, he/she cannot extract any secret keys from it.
The adversary has the ability to capture any number of s and can access all the secret information stored in the ’s memory by capturing attack.
3.3. Bilinear Pairing
Let and be cyclic additive and multiplicative groups of prime order q, respectively. The generator of is . Let be a bilinear pairing, which satisfies the following properties:
Bilinearity: and , are satisfied.
Non-degenerate: such that .
Computable: for all , there is always an effective algorithm to compute .
The security of our protocol is based on the following computationally infeasible problems.
Elliptic Curve Discrete Logarithm problem (ECDL): Let , given , and compute a.
Computational Diffie–Hellman problem (CDH): Let , given , , and , and find .
Decisional Diffie–Hellman problem (DDH): Let , given , , , and , and decide if .
4. Proposed Protocol
In the distributed group key agreement protocol, each group member is equal, which means that before the group key is negotiated, each group member usually needs to consume many communication and computing resources to perform mutual authentication with all other group members. In order to reduce these costs, in our protocol, we arrange all s into a list according to their identities. According to the list, before the group key is negotiated, each only needs to send an authentication request to its right neighbor once and be authenticated by its right neighbor. In other words, each will receive an authentication request from its left neighbor and authenticate its left neighbor. Since each only needs to complete authentication once, this can greatly reduce the computation and communication costs caused by authentication between group members. In addition, when any needs to join or leave the group, only the left neighbor of the needs to update the parameters, which can also reduce the computation and communication overhead.
Our protocol has seven parts: the initialization phase, the registration phase, the mutual authentication phase, the group key generation phase, the join phase, the leave phase, and the internal attacker detection process. When the system runs for the first time, the initialization phase is performed by the System Administrator (SA). Each performs the registration phase before entering the network. When the group key needs to be negotiated, all s perform the mutual authentication phase and the group key generation phase. When a wants to join a group, it needs to perform the join phase. When a in the group wants to leave, the leave phase is performed. If the group key fails to be generated multiple times, the KDC will execute the internal attacker detection process to find the malicious and expel it from the group.
Suppose there are that need to generate the group key, and their identities are , where n is the number of . Since there may be multiple groups, we named each group , where u is the number of groups. Each group has a list L that stores the identity of all s in the group and is managed by the KDC. All in L are sorted in descending order, and L is a circular list, which means that the largest and the smallest are linked. Table 1 shows the description of the symbols. The details of the above seven parts are as follows.
Table 1.
Symbols used in our protocol.
| Symbol | Description |
|---|---|
| SA | System Administrator |
| KDC | Key Distribution Center |
| General node | |
| q | A large prime number |
| Cyclic additive groups of prime order q | |
| Cyclic multiplicative groups of prime order q | |
| Q | The generator of |
| e | Bilinear pairing |
| The identity of | |
| The identity of the group | |
| L | A circular list that stores all -related information in the group |
| s | The KDC’s private key |
| The KDC’s public key | |
| , | The ’s public key |
| , | The ’s private key |
| , | Timestamp |
| The timestamp when the latest information was received | |
| Maximum communication transmission delay | |
| Symmetric key | |
| Symmetric encryption algorithm | |
| Symmetric decryption algorithm | |
| Hash operation | |
| Group key | |
| ⊕ | Bitwise XOR operation |
| Concatenation of data a and data b |
4.1. Initialization Phase
First, the SA picks , where is a cyclic additive group of order p, is a cyclic multiplicative group of order p, Q is a generator of , and is a bilinear map. Second, the SA generates a random private key s and computes the corresponding public key . Finally, the SA publishes parameters {p, , , Q, e, , , , } and stores s in the memory of each KDC in a secure environment, where is the hash function used by this protocol, is the symmetric encryption algorithm, and is the symmetric decryption algorithm.
4.2. Registration Phase
Before the joins the network, it needs to choose the nearest KDC to register and receive the corresponding key. The steps in this phase are as follows.
Step R1: The KDC generates a unique identity for the and computes its public key and the corresponding private key . Finally, the KDC sends to through a secure channel.
Step R2: generates a random , computes , and sends to the KDC through a secure channel.
Step R3: The KDC broadcasts , , and .
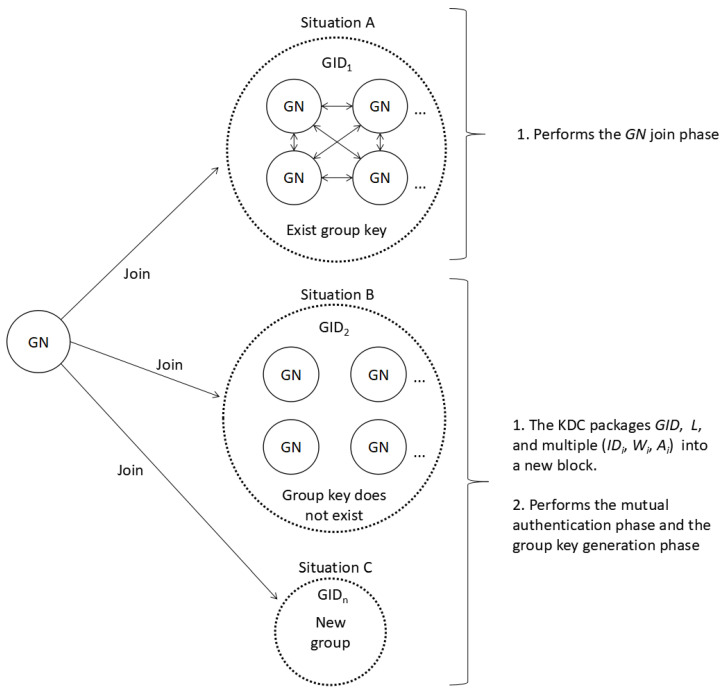
Step R4: According to the group’s identity , the can choose to join a group or pick a new unique to create a new group. Based on the selection of the , there are three different situations: (1) Situation A: the joins a group that already has a group key; (2) Situation B: the joins a group that has not started negotiating group keys; (3) Situation C: the creates a new group. In Situation A, the performs the join phase. In Situation B and Situation C, the KDC will package , the corresponding L, and multiple tuples (, , ) related to all members of the group into a new block, which will be verified by all other KDCs. After successful verification, the new block will be linked to the blockchain. Figure 2 shows the three situations faced by the and the solution strategies.
Figure 2.
The three situations faced by the and the solution strategies.
4.3. Mutual Authentication Phase
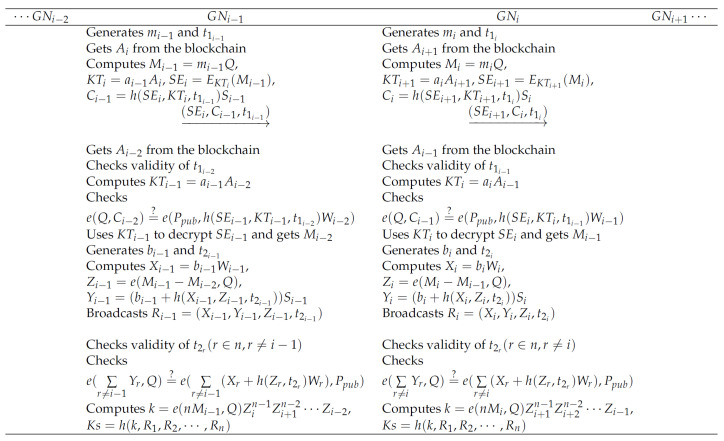
In this phase, first sends a message to its right neighbor , and will authenticate . At the same time, will also receive a message from its left neighbor , and it needs to authenticate . Figure 3 shows the mutual authentication phase and the group key generation phase of our protocol. performs the following operations.
Figure 3.
The mutual authentication phase and the group key generation phase of our protocol.
Step A1: Generates a random and a timestamp and gets from the blockchain.
Step A2: Computes , , , .
Step A3: Sends message (, , ) to .
Step A4: receives a message (, , ) from and gets from the blockchain.
Step A5: Checks that holds or not. If the check fails, it broadcasts an authentication failure message.
Step A6: Computes .
Step A7: Checks whether the condition is satisfied. If the condition is not true, it broadcasts an authentication failure message.
Step A8: Uses to decrypt and get .
Step A9: Generates a random and a timestamp .
Step A10: Computes , , .
Step A11: Broadcasts .
4.4. Group Key Generation Phase
During this phase, each receives the message from all other s. At this point, each will perform a group authentication and then negotiate the group key. The execution steps of each are as follows.
Step K1: Checks that the timestamp in each received message is valid. If the check fails, it broadcasts an authentication failure message.
Step K2: After receiving the message from all other s, it checks that:
holds or not. If the check fails, it broadcasts an authentication failure message.
Step K3: Computes and group key .
4.5. Join Phase
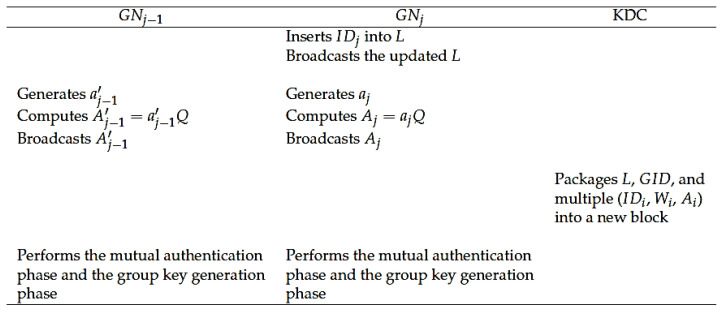
When a new wants to join the group, it needs to be registered in the KDC first. This means that according to the registration phase, has selected a group to join. Figure 4 shows the join phase of our protocol. The detailed steps are as follows.
Figure 4.
The join phase of our protocol.
Step J1: obtains the corresponding list L of the group from the blockchain, inserts its identity into the appropriate position in L, and broadcasts the new L.
Step J2: generates a random number and computes . After that, broadcasts .
Step J3:’s left neighbor regenerates a new random number and computes . After that, broadcasts .
Step J4: The KDC packages the updated L, corresponding , and multiple tuples (, , ) related to all members of the group into a new block, which will be verified by all other KDCs. After successful verification, the new block will be linked to the blockchain.
Step J5: According to the steps in the mutual authentication phase, sends (, , ) to its right neighbor and receives message (, , ) from .
Step J6: After the messages received by and are successfully authenticated, all s broadcast and perform the group key generation phase to complete the key update.
4.6. Leave Phase
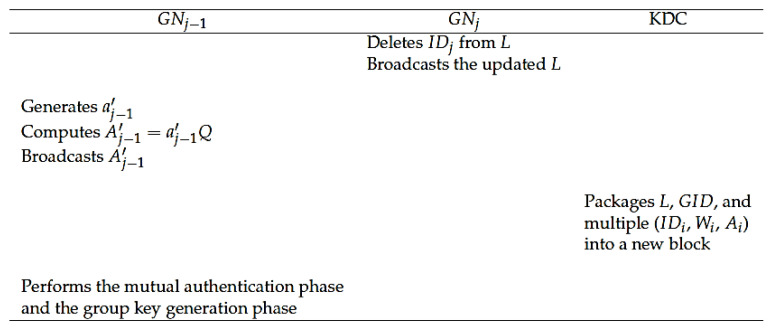
When a in the group wants to leave, the following steps need to be performed. Figure 5 shows the leave phase of our protocol.
Figure 5.
The leave phase of our protocol.
Step L1: deletes its identity from list L and broadcasts the new L.
Step L2: regenerates a new random number , and computes . After that, broadcasts .
Step L3: The KDC packages the updated L, corresponding , and multiple tuples (, , ) related to all members of the group into a new block, which will be verified by all other KDCs. After successful verification, the new block will be linked to the blockchain.
Step L4: According to the steps in the mutual authentication phase, sends (, , ) to .
Step L5: After authenticates , all s broadcast and perform the group key generation phase to complete the key update.
4.7. Internal Attacker Detection Process
It can be found in our protocol that every is required to be honest during the group key generation phase. If a malicious intentionally broadcasts an error message, the entire group cannot generate a group key. However, since all s are equal, it is impossible to discover malicious s through these s. Therefore, our agreement regards KDC as the judging body. When the group fails to negotiate multiple times, the process will be executed and try to find the malicious . The steps of this process are as follows.
Step D1: The KDC first records all messages sent by each in the group .
Step D2: All generate a timestamp , compute , and send the tuple (, , H, , ) to the KDC.
Step D3: After receiving the tuple, the KDC first verifies the validity of the time stamp . Then, the KDC computes , and verifies . If it does not hold, is regarded as a malicious .
Step D4: If the above formula holds, the KDC continues to compute , and verify , . If it does not hold, the corresponding will be expelled from the group immediately.
5. Security and Performance Analysis
5.1. Correctness Analysis
Theorem 1.
and can calculate the same symmetric key , so that can get .
Proof.
Since computes to get and computes to get , then:
Since the same can be obtained by calculating and , and can use the symmetric key to encrypt or decrypt transmitted messages. □
Theorem 2.
It is valid for to authenticate .
Proof.
The authentication of for is achieved by verifying whether the formula holds. The correctness of the formula is proven as follows.
Although the adversary can easily obtain , due to the ECDL and the CDH, he/she cannot calculate s, any , or in polynomial time. Therefore, the adversary also cannot calculate . If the adversary wants to forge a to pass the above verification, he/she needs to create a new valid . However, since the adversary cannot obtain and s, he/she cannot calculate a new . In addition, due to the DDH, for a random , the adversary cannot decide if in polynomial time. □
Theorem 3.
During the group key generation phase, is valid for the batch authentication of other group members.
Proof.
In the group key generation phase, authenticates other group members in batches by verifying whether formula holds. The correctness of the formula is proven as follows.
If the adversary wants to forge a to pass the above batch authentication, he/she needs to create a valid and to satisfy . First, the adversary cannot get , so it is difficult for him/her to calculate . Second, even suppose that is revealed by the adversary, but he/she still cannot calculate a valid or because he/she cannot get s. In addition, due to the DDH, for a random , the adversary cannot decide if in polynomial time. □
Theorem 4.
If all s participating in the group key generation phase are honest, then all s can negotiate the same group key.
Proof.
According to Theorem 1, as long as all s participating in the group key generation phase are honest, each can obtain the parameter sent by its left neighbor. Therefore,
From the above, it can be found that all s can calculate the same parameter k. Therefore, their group keys are also the same. □
5.2. Simulation Based on the ProVerif Tool
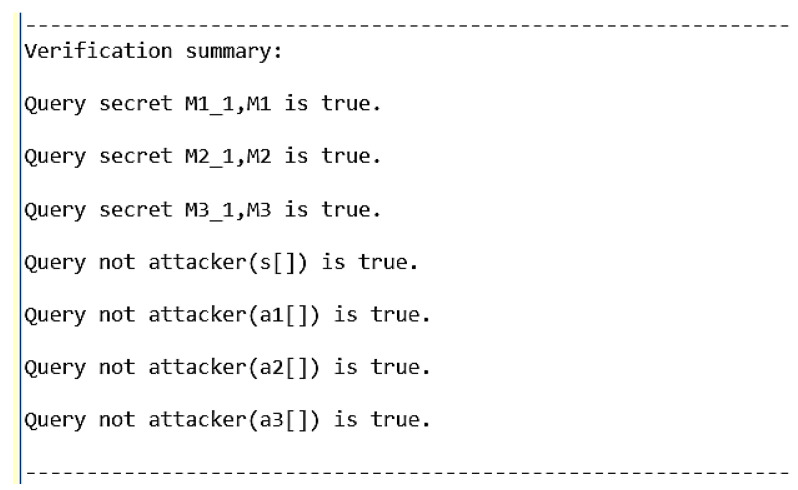
ProVerif is a widely known authentication protocol verification tool that can prove the security of multiple encryption schemes or authentication protocols, such as signature schemes and Diffie–Hellman key exchange algorithms [31,32]. Since each does not need to communicate with other nodes during the group key generation phase, we use ProVerif to verify the security of the mutual authentication phase of our protocol. In addition, since we do not need to verify the performance of our protocol in this section, we assume that there are only three s that need to negotiate a group key, which are , , and . Figure 6 shows the code for the mutual authentication phase of our protocol. Figure 7 shows the simulation results. The results show that in our protocol, the secret parameters , , and for group key generation, as well as the private keys s, , , and will not be obtained by the adversary.
Figure 6.
The code for the mutual authentication phase of our protocol.
Figure 7.
The PV simulation results of our protocol.
5.3. Informal Security Analysis
5.3.1. Impersonation Attack
The adversary needs to create valid messages (, , ) or () to perform an impersonation attack on . However, according to Theorem 2 and Theorem 3, the adversary cannot create a valid message.
5.3.2. Capture Attack
After the adversary has captured several s, we need to ensure that the private key s cannot be obtained by the adversary. After the adversary captures a , he/she can obtain containing information about s. However, according to the ECDL, although the adversary can obtain and , he/she cannot calculate s in polynomial time.
5.3.3. Replay Attack
Our protocol uses timestamps and to defend against replay attacks. In addition, our protocol guarantees that the timestamp cannot be modified. For messages (, , ), the adversary must obtain and before replacing a new valid timestamp . For messages (), the adversary must obtain and before replacing a new valid timestamp . However, the adversary cannot get , or because they are never transmitted directly in the channel. In addition, due to the ECDL, it is difficult for the adversary to calculate these parameters.
5.3.4. Forward Secrecy after a New Joins
When a wants to join a group, it needs to ensure that cannot get the previous group key. In our protocol, we assume that has intercepted all historical communication messages of the group. This results in that when joins the group, as long as it obtains , it can calculate the previous group key. However, when the joins the group, its left neighbor will regenerate a new and send it to , which means can only get instead of . Therefore, our protocol ensures the forward secrecy after a new joins.
5.3.5. Backward Secrecy after a Leaves
When a leaves the group, it needs to ensure that it cannot get the group key generated in the future. We assume that after leaves the group, it still retains the secret parameter sent by its left neighbor and is able to intercept all group communication messages. This means that as long as is kept unchanged, can still calculate the group key after leaving the group. However, in our protocol, after leaves the group, its left neighbor will regenerate a new and send it to . This results in that at Step A11, will broadcast and will broadcast . At this point, has expired, and cannot calculate the group key through this parameter. Therefore, our protocol ensures the backward secrecy after a leaves.
5.3.6. Single Node Failure
Although all KDCs will not participate in the mutual authentication phase and the group key generation phase, each group still needs to be managed by a KDC. This is because each group may need the KDC to act as a judging body to expel malicious nodes. If the KDC fails, since all KDCs share the same blockchain that stores all s’ authentication parameters, it only needs to switch to another KDC. This means that in our protocol, as long as there is a working KDC, the entire system can operate normally.
6. Performance Analysis and Comparison
6.1. Computation Cost
The symbols , , , , and represent the computing time required to implement one symmetric encryption or decryption, one general hash function operation, one point multiplication operation on Elliptic Curve Cryptography (ECC), one point addition operation on ECC, and one bilinear pairing operation, respectively. In the mutual authentication phase and the group key generation phase of our protocol, each needs to perform point multiplication operations on ECC, 4 bilinear pairing operations, hash operations, 2 symmetric encryption or decryption operations, and point addition operations on ECC, where n is the number of . In other words, the total computation cost of each is .
6.2. Communication Cost
We assume C is 256 bits and timestamp T is 64 bits. In the mutual authentication phase of our protocol, each needs to send message (, , ) to and broadcast (, , , ). Therefore, each needs to send messages of length and receive messages of length . The total communication cost in the the mutual authentication phase and the group key generation phase of our protocol is .
6.3. Comparison with Related Protocols
We compare our protocol with the protocol of Zheng et al. [9], the protocol of Zhang et al. [21], and the protocol of Gupta et al. [17] in terms of computation costs, energy consumption, communication costs, and security.
In the protocol of Zheng et al. [9], the total computation cost required to generate the group key is , and each group member needs to send messages of length and receive messages of length . In the protocol of Zhang et al. [21], the total computation cost required to generate the group key is , and each group member needs to send messages of length and receive messages of length . In the protocol of Gupta et al. [17], the total computation cost required to generate the group key is . In their protocol, there is a group controller in each group, which undertakes most of the communication work and causes the communication cost of each group member to be very low. Therefore, we consider that the total length of the messages that need to be sent and received is , rather than the communication cost of each group member. Table 2 shows the comparison of computation cost and communication cost between our protocol and related protocols.
Table 2.
The comparison of computation cost and communication cost between our protocol and related protocols.
| Zheng et al. [9] | Zhang et al. [21] | Gupta et al. [17] | Our Protocol | |
|---|---|---|---|---|
| Point multiplication operations on ECC | ||||
| Bilinear pairing | 6 | 0 | 4 | |
| Hash operation | 0 | 5 | ||
| Symmetric encryption or decryption | 4 | 0 | 0 | 2 |
| Point addition operations on ECC | 0 | |||
| Message length sent by each group member | - | |||
| Message length received by each group member | - | |||
| Total sent message length | ||||
| Total received message length |
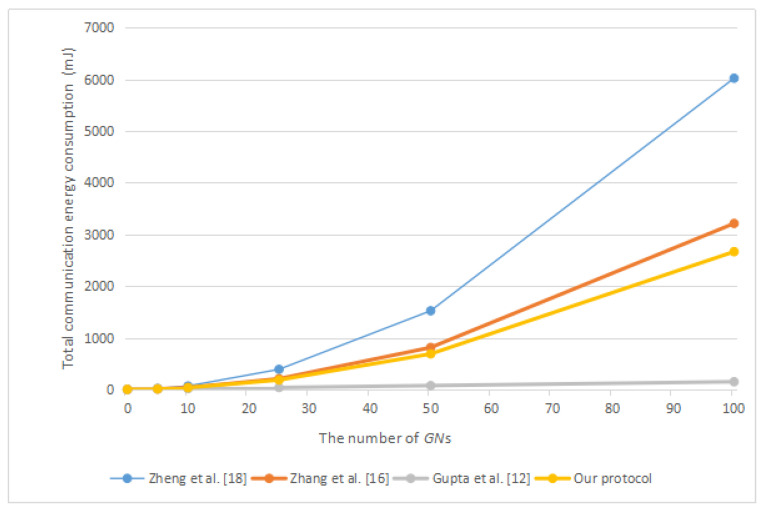
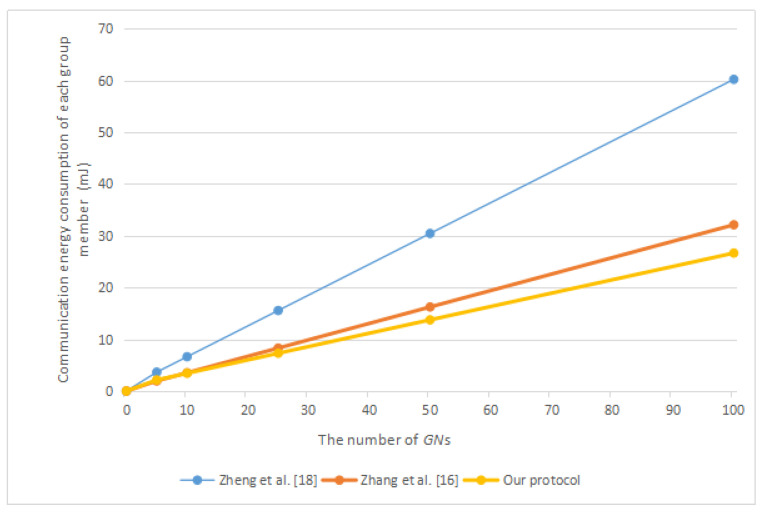
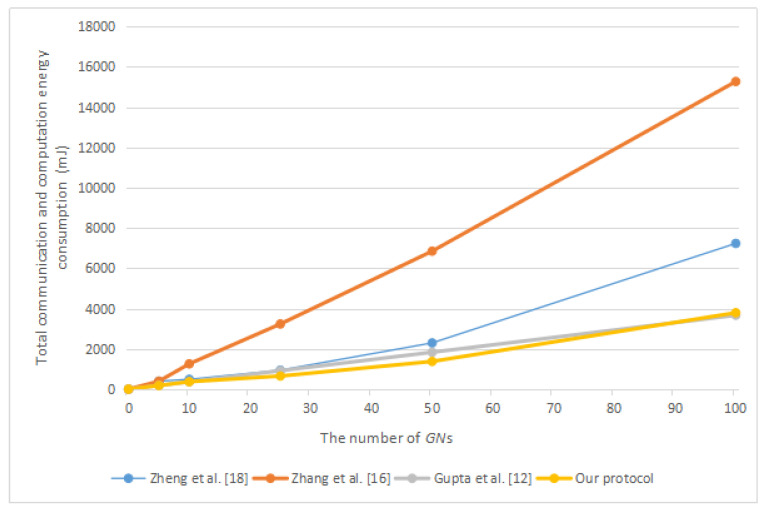
Next, we will compare our protocol with related protocols in terms of energy consumption. According to the work of Carman et al. [33] and Zhang et al. [21], we obtained that a “Strong ARM” microprocessor running at 133MHz performing one symmetric encryption or decryption operation needs to consume 0.00217 mJ, one point multiplication operation on ECC requires 8.8 mJ, one general hash function operation requires 0.000108 mJ, and one bilinear pairing operation requires 47 mJ. According to the work of Makri and Konstantinou [34], we obtained that an IEEE 802.11 Spectrum24 WLAN card requires 0.00066 mJ for the transmission of 1 bit and 0.00031 mJ for the reception of 1 bit. According to [35], the computing time of one point addition operation on ECC is about half of one symmetric encryption or decryption operation. Therefore, we considered that the energy consumption of a point addition operation is about 0.001085 mJ. We summarize the above energy consumption in Table 3. Figure 8 shows the total communication energy consumption in different protocols. Figure 9 shows the communication energy consumption of each group member in different protocols. Figure 10 shows the total communication and computation energy consumption in different protocols.
Table 3.
Energy consumption for computing and communication.
| Operations | Energy Consumption |
|---|---|
| 0.00217 mJ | |
| 8.8 mJ | |
| 0.001085 mJ | |
| 0.000108 mJ | |
| 47 mJ | |
| Transmitting a bit | 0.00066 mJ |
| Receiving a bit | 0.00031 mJ |
Figure 8.
The total communication energy consumption in different protocols.
Figure 9.
The communication energy consumption of each group member in different protocols.
Figure 10.
The total communication and computation energy consumption in different protocols.
It can be found from Table 2 that our protocol has the lowest computation costs, and the computation costs of our protocol and the protocol of Zheng et al. [9] are very similar. However, from Figure 8, it can be found that our protocol consumes less communication resources. In addition, because after group members join or leave a group, neither their left neighbor nor their right neighbor updated the corresponding temporary secret parameter, this leads to the newly joined group members being able to easily obtain the previous group key, and group members who leave the group can also easily obtain the subsequent group key. Therefore, the protocol of Zheng et al. [9] lacks forward or backward secrecy.
According to Figure 10, in the distributed group key agreement protocol, such as the protocol of Zheng et al. [9] and the protocol of Zhang et al. [21], our protocol has the least total communication and computation energy consumption. With the help of the group controller, the decentralized group key agreement protocol such as the protocol of Gupta et al. [17] will consume less energy when there is a large number of group members. However, in the protocol of Gupta et al. [17], each group member needs to perform mutual authentication with the group controller one by one, which requires much total computing time. Moreover, the existence of the group controller makes their protocol vulnerable to single node failure. Once the group controller fails, the group cannot continue to negotiate the group key. According to Figure 8 and Figure 9, excluding the protocol of Gupta et al. [17], the total communication energy consumption of our protocol is the lowest, and the communication energy consumption of each group member in our protocol is also the lowest.
7. Conclusions
This paper proposes a blockchain-based authentication and dynamic group key agreement protocol. Each group member in our protocol only needs to authenticate its left neighbor once to complete the authentication, which improves authentication efficiency. When a node joins or leaves a group, only the left neighbor of the node needs to update the data, which also improves the scalability of our protocol. Our protocol also guarantees forward or backward secrecy when group members join or leave the group. In addition, we use blockchain technology to store group identities, a list of group members, and some group member-related parameters, which can solve the problem of single node failure. Finally, we use mathematics and ProVerif to prove the correctness and security of our protocol. The comparison with related protocols shows that our protocol reduces computation and communication costs.
Abbreviations
The following abbreviations are used in this manuscript:
| MEC | Mobile Edge Computing |
| SCM | Small Cell Manager |
| SCC | Small Cell Cloud |
| GN | General Node |
| KDC | Key Distribution Center |
| LKH | Logical Key Hierarchy |
| TPD | Tamper-Proof Device |
| ECC | Elliptic Curve Cryptography |
| SA | System Administrator |
| ECDL | Elliptic Curve Discrete Logarithm problem |
| CDH | Computational Diffie–Hellman problem |
| DDH | Decisional Diffie–Hellman problem |
Author Contributions
Conceptualization, Z.X.; funding acquisition, F.L., H.D. and J.X.; project administration, M.T.; writing, original draft, Z.X.; writing, review and editing, F.L., Z.X. and J.Z. All authors read and agreed to the published version of the manuscript.
Funding
This work was supported in part by National Natural Science Foundation of China under Grant 61872138 and Grant 61772185.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Rafaeli S., Hutchison D. A survey of key management for secure group communication. ACM Comput. Surv. CSUR. 2003;35:309–329. doi: 10.1145/937503.937506. [DOI] [Google Scholar]
- 2.Wang T., Qiu L., Sangaiah A.K., Liu A., Bhuiyan M.Z.A., Ma Y. Edge-Computing-Based Trustworthy Data Collection Model in the Internet of Things. IEEE Internet Things J. 2020;7:4218–4227. doi: 10.1109/JIOT.2020.2966870. [DOI] [Google Scholar]
- 3.Mach P., Becvar Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Commun. Surv. Tutorials. 2017;19:1628–1656. doi: 10.1109/COMST.2017.2682318. [DOI] [Google Scholar]
- 4.Gong L., Shacham N. Multicast security and its extension to a mobile environment. Wirel. Netw. 1995;1:281–295. doi: 10.1007/BF01200847. [DOI] [Google Scholar]
- 5.Liang W., Huang W., Long J., Zhang K., Li K.C., Zhang D. Deep reinforcement learning for resource protection and real-time detection in IoT environment. IEEE Internet Things J. 2020;7:6392–6401. doi: 10.1109/JIOT.2020.2974281. [DOI] [Google Scholar]
- 6.Wang T., Cao Z., Wang S., Wang J., Qi L., Liu A., Xie M., Li X. Privacy-enhanced data collection based on deep learning for Internet of vehicles. IEEE Trans. Ind. Inform. 2019;16:6663–6672. doi: 10.1109/TII.2019.2962844. [DOI] [Google Scholar]
- 7.Islam S.H., Obaidat M.S., Vijayakumar P., Abdulhay E., Li F., Reddy M.K.C. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Future Gener. Comput. Syst. 2018;84:216–227. doi: 10.1016/j.future.2017.07.002. [DOI] [Google Scholar]
- 8.Naresh V.S., Reddi S., Murthy N.V. A provably secure cluster-based hybrid hierarchical group key agreement for large wireless ad hoc networks. Hum. Centric Comput. Inf. Sci. 2019;9:26. doi: 10.1186/s13673-019-0186-5. [DOI] [Google Scholar]
- 9.Zheng J., Yang C., Xue J., Zhang C. A Dynamic ID-based Authenticated Group Key Agreement Protocol; Proceedings of the 2015 4th National Conference on Electrical, Electronics and Computer Engineering; Xi’an, China. 12–13 December 2015; Xi’an, China: Atlantis Press; 2015. [Google Scholar]
- 10.Hussien H.M., Yasin S.M., Udzir S., Zaidan A.A., Zaidan B.B. A systematic review for enabling of develop a blockchain technology in healthcare application: Taxonomy, substantially analysis, motivations, challenges, recommendations and future direction. J. Med. Syst. 2019;43:320. doi: 10.1007/s10916-019-1445-8. [DOI] [PubMed] [Google Scholar]
- 11.Zubaydi H.D., Chong Y.W., Ko K., Hanshi S.M., Karuppayah S. A review on the role of blockchain technology in the healthcare domain. Electronics. 2019;8:679. doi: 10.3390/electronics8060679. [DOI] [Google Scholar]
- 12.Seetha R., Saravanan R. A survey on group key management schemes. Cybern. Inf. Technol. 2015;15:3–25. doi: 10.1515/cait-2015-0038. [DOI] [Google Scholar]
- 13.Barskar R., Chawla M. A survey on efficient group key management schemes in wireless networks. Indian J. Sci. Technol. 2016;9:14. doi: 10.17485/ijst/2016/v9i14/87972. [DOI] [Google Scholar]
- 14.Wong C.K., Gouda M., Lam S.S. Secure group communications using key graphs. IEEE/ACM Trans. Netw. 2000;8:16–30. doi: 10.1109/90.836475. [DOI] [Google Scholar]
- 15.Mittra S. ACM SIGCOMM Computer Communication Review. Volume 27. ACM; New York, NY, USA: 1997. Iolus: A framework for scalable secure multicasting; pp. 277–288. [Google Scholar]
- 16.Setia S., Koussih S., Jajodia S., Harder E. Kronos: A scalable group re-keying approach for secure multicast; Proceedings of the 2000 IEEE Symposium on Security and Privacy, S&P 2000; Berkeley, CA, USA. 14–17 May 2000; Piscataway, NY, USA: IEEE; 2000. pp. 215–228. [Google Scholar]
- 17.Gupta S., Kumar A., Kumar N. Design of ECC based authenticated group key agreement protocol using self-certified public keys; Proceedings of the 2018 4th International Conference on Recent Advances in Information Technology (RAIT); Dhanbad, India. 15–17 March 2018; Piscataway, NY, USA: IEEE; 2018. pp. 1–5. [Google Scholar]
- 18.Zheng J., Zhang X., Zhang Q., Zhang Q., Zhang C. Multi-domain lightweight asymmetric group key agreement. Chin. J. Electron. 2018;27:1085–1091. doi: 10.1049/cje.2018.07.002. [DOI] [Google Scholar]
- 19.Wang L., Tian Y., Zhang D., Lu Y. Constant-round authenticated and dynamic group key agreement protocol for D2D group communications. Inf. Sci. 2019;503:61–71. doi: 10.1016/j.ins.2019.06.067. [DOI] [Google Scholar]
- 20.Boneh D., Lynn B., Shacham H. Short signatures from the Weil pairing; Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security; Gold Coast, Australia. 9–13 December 2001; Berlin/Heidelberg, Germany: Springer; 2001. pp. 514–532. [Google Scholar]
- 21.Zhang Q., Gan Y., Zhang Q., Wang R., Tan Y.A. A dynamic and cross-domain authentication asymmetric group key agreement in telemedicine application. IEEE Access. 2018;6:24064–24074. [Google Scholar]
- 22.Kavitha S., Alphonse P., Reddy Y.V. An Improved Authentication and Security on Efficient Generalized Group Key Agreement Using Hyper Elliptic Curve Based Public Key Cryptography for IoT Health Care System. J. Med. Syst. 2019;43:260. doi: 10.1007/s10916-019-1378-2. [DOI] [PubMed] [Google Scholar]
- 23.Geng M., Zhang F., Gao M. A secure certificateless authenticated group key agreement protocol; Proceedings of the 2009 International Conference on Multimedia Information Networking and Security; Wuhan, China. 18–20 November 2009; Piscataway, NY, USA: IEEE; 2009. pp. 342–346. [Google Scholar]
- 24.Zhang Q., Wang R., Tan Y. Identity-based authenticated asymmetric group key agreement. J. Comput. Res. Dev. 2014;51:1727–1738. [Google Scholar]
- 25.Shi Y., Chen G., Li J. ID-based one round authenticated group key agreement protocol with bilinear pairings; Proceedings of the International Conference on Information Technology: Coding and Computing (ITCC’05)-Volume II; Las Vegas, NV, USA. 4–6 April 2005; Piscataway, NY, USA: IEEE; 2005. pp. 757–761. [Google Scholar]
- 26.Alphonse P., Reddy Y.V. A method for obtaining authenticated scalable and efficient group key agreement for wireless ad-hoc networks. Clust. Comput. 2019;22:3145–3151. doi: 10.1007/s10586-018-2008-3. [DOI] [Google Scholar]
- 27.Kiayias A., Russell A., David B., Oliynykov R. Ouroboros: A provably secure proof-of-stake blockchain protocol; Proceedings of the Annual International Cryptology Conference; Santa Barbara, CA, USA. 18–22 August 2017; Berlin/Heidelberg, Germany: Springer; 2017. pp. 357–388. [Google Scholar]
- 28.Liang W., Fan Y., Li K.C., Zhang D., Gaudiot J.L. Secure data storage and recovery in industrial blockchain network environments. IEEE Trans. Ind. Inform. 2020;16:6543–6552. doi: 10.1109/TII.2020.2966069. [DOI] [Google Scholar]
- 29.Liang W., Zhang D., Lei X., Tang M., Li K.C., Zomaya A. Circuit Copyright Blockchain: Blockchain-based Homomorphic Encryption for IP Circuit Protection. IEEE Trans. Emerg. Top. Comput. 2020 doi: 10.1109/TETC.2020.2993032. [DOI] [Google Scholar]
- 30.Franklin M.K., Reiter M.K. Fair exchange with a semi-trusted third party; Proceedings of the 4th ACM Conference on Computer and Communications Security; Zurich, Switzerland. 1–4 April 1997; pp. 1–5. [Google Scholar]
- 31.Xu Z., Xu C., Chen H., Yang F. A lightweight anonymous mutual authentication and key agreement scheme for WBAN. Concurr. Comput. Pract. Exp. 2019;31:e5295. doi: 10.1002/cpe.5295. [DOI] [Google Scholar]
- 32.Blanchet B., Smyth B. Automated reasoning for equivalences in the applied pi calculus with barriers. J. Comput. Secur. 2018;26:367–422. doi: 10.3233/JCS-171013. [DOI] [Google Scholar]
- 33.Carman D.W., Kruus P.S., Matt B.J. Constraints and Approaches for Distributed Sensor Network Security (Final) The Security Research Division of Network Associates Inc; Glenwood, MD, USA: Sep 1, 2000. Technical Report. [Google Scholar]
- 34.Makri E., Konstantinou E. Constant round group key agreement protocols: A comparative study. Comput. Secur. 2011;30:643–678. doi: 10.1016/j.cose.2011.08.008. [DOI] [Google Scholar]
- 35.He D., Zeadally S., Kumar N., Wu W. Efficient and anonymous mobile user authentication protocol using self-certified public key cryptography for multi-server architectures. IEEE Trans. Inf. Forensics Secur. 2016;119:2052–2064. doi: 10.1109/TIFS.2016.2573746. [DOI] [Google Scholar]