Abstract
We study the equivalence between the entanglement-based scheme and prepare-and-measure scheme of unidimensional (UD) continuous-variable quantum key distribution protocol. Based on this equivalence, the physicality and security of the UD coherent-state protocols in the ideal detection and realistic detection conditions are investigated using the Heisenberg uncertainty relation, respectively. We also present a method to increase both the secret key rates and maximal transmission distances of the UD coherent-state protocol by adding an optimal noise to the reconciliation side. It is expected that our analysis will aid in the practical applications of the UD protocol.
Keywords: continuous-variable quantum key distribution, unidimensional modulation, Heisenberg uncertainty relations
1. Introduction
Quantum key distribution (QKD), which is a prominent application of the quantum information, enables two remote parties, conventionally called Alice and Bob, to share a common secret key through an insecure quantum channel and an authenticated classical channel [1,2]. This unconditional security is guaranteed by the basic principles of quantum mechanics. Continuous-variable quantum key distribution (CV-QKD) has attracted considerable attention over the past years because of its good performances in the secret key rates and compatibility with the current optical networks [3,4,5,6,7,8,9,10,11,12,13,14,15,16]. A particular class of CV-QKD protocols that is based on the Gaussian modulation of coherent states has experienced a rapid development [17,18,19,20,21,22,23,24,25,26,27]. In a coherent-state protocol, Alice encodes her information in the amplitude and phase quadratures of the coherent light field by using amplitude and phase modulators, and Bob performs homodyne or heterodyne detection.
Recently, a further simplified unidimensional (UD) CV-QKD protocol has been proposed [28]. In such protocol, Alice, still using coherent states, encodes her information by using one modulator (e.g., amplitude modulator) instead of two, whereas Bob performs a homodyne detection, hence simplifying both the modulation scheme and the key extraction task. The security against collective attacks has been proved in asymptotic regime. However, this early work only considered the UD model under an idea homodyne detector. It does not refer to the realistic condition, such as the efficiency and electronic noise of the homodyne detector. Then, a model of the UD protocol under realistic condition was designed and realized in an experiment [29]. Furthermore, the finite size effect was analyzed in paper [30], and an optimum ratio in parameters estimation was proposed.
In the UD protocol, due to the fact that the phase quadrature is not modulated in Alice’s side, we cannot estimate the correlation in the phase quadrature between Alice and Bob. However, this unknown parameter is bounded by the requirement of the physicality of the state. A Gaussian state can typically be characterized by a covariance matrix. However, not all covariance matrices correspond to physical states, as the covariance matrix must respect the Heisenberg uncertainty relation [31,32]. By using this uncertainty relation, we can calculate the physical region boundary of a covariance matrix, which is crucial for the security of the protocol. We can see that the UD CV-QKD protocol is very different from the previous symmetrical (SY) coherent-state protocol [18,21]. Due to the equivalence between the prepare-and-measure (PM) and entanglement-based (EB) scheme of UD protocol, the differences of the Heisenberg uncertainty relations under the idea and realistic condition, and the effect of noise from Bob’s setup on secret key rate under realistic condition are not described or investigated in depth [28,29,30], a further study about above questions is required.
In this paper, we first consider the equivalence between the PM scheme and the EB scheme of the UD CV-QKD protocol. Then, we analyze the boundary of the physical region of the symmetrical coherent-state protocol based on the Heisenberg uncertainty relation. We also study the variances of the physical region of the UD coherent-state protocol under the conditions of different detection efficiency and electronic noise. Secure and unsecure regions of both the protocols are further analyzed under ideal and realistic detection conditions. It is found that adding an optimal noise to Bob’s side can truly help the improvement of the secret key rate and increase the transmission distance of the UD coherent-state protocol under the assumption of reverse reconciliation.
The paper is organized as follows. In Section 2, we introduce the equivalence between the EB scheme and the PM scheme of the UD CV-QKD protocol. In Section 3, a comparison between the physical and secure regions of the UD protocol under ideal and realistic detection conditions is shown, and a method to improve the performance of the UD coherent-state protocol by adding an optimal noise to Bob’s side is proposed. In Section 4, we give our conclusions and discussions.
2. Unidimensional Quantum Key Distribution
2.1. Equivalence between the EB Scheme and the PM Scheme
Generally, most of the experimental systems in CV-QKD are focused on PM schemes currently, given their ease of implementation in practice. However, it’s hard to analyze the security in theory. On the contrary, the theoretical analysis based on EB scheme is maturity. The involved entangled states make the calculations feasible and simpler [33]. Especially in UD CV-QKD protocol, the security analysis based on EB scheme has more advantages. The covariance matrices achieved from the EB schemes contain the constraints of phase amplitude quadrature. However these constraints is difficult to achieve from the PM scheme. More details about the security analysis will be shown later. Now, it is necessary to study the equivalence of EB and PM schemes, firstly. This equivalence is based on the indistinguishability between these two protocols for Bob and Eve. The consequent advantage of this equivalence is that it is sufficient to implement the PM scheme and study the EB scheme.
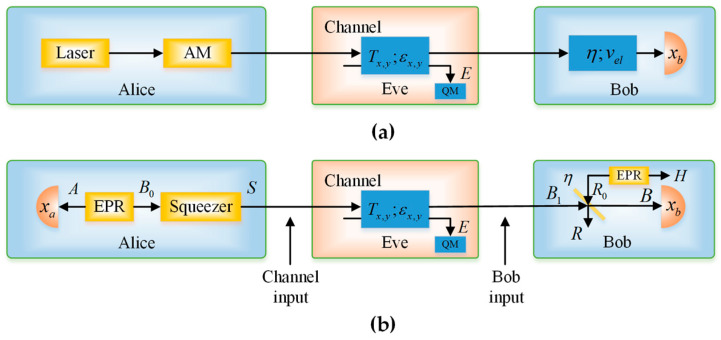
In the PM scheme, as depicted in Figure 1a, the sender, Alice, prepares coherent states using a laser source. Then, she encodes the information in the amplitude or phase quadratures of coherent states by using either amplitude or phase modulators. Here, without losing generality, we assume that Alice uses an amplitude modulator with a modulation variance VM, which is assumed to be expressed in shot-noise units, and that the coherent states follow the uncertainty principle of variance 1. Thus, the mixture of Gaussian-modulated coherent states gives rise to a unidimensional chain structure with a thickness of 1 and a length of in the phase space. These quantum states are then sent to Bob through an untrusted quantum channel with transmittance , and excess noise , .
Figure 1.
Unidimensional (UD) protocol schemes under realistic conditions. (a) Prepare-and-measure (PM) scheme of the UD protocol; (b) Entanglement-based (EB) scheme of the UD protocol.
In the EB scheme, as shown in Figure 1b, Alice starts with a two-mode squeezed vacuum state with variance . Then, she performs homodyne detection on the first half of the state and squeezes the second half by . The result is the covariance matrix
| (1) |
The covariance matrix of mode , conditioned on Alice’s measurement result (), can be written as
| (2) |
and the displacement vector can be expressed as
| (3) |
where is the result of the homodyne measurement, and are the covariance matrices of the modes and , respectively, is the correlation matrix of the two modes, , and denotes the Moore–Penrose inverse of the matrix [34].
Then, we obtain
| (4) |
which is a coherent state centered on . Furthermore, the variance of is
| (5) |
where is exactly the variance of the Alice’s . Then, we can establish a one-to-one correspondence between the EB scheme and the PM scheme by multiplying the outcome of Alice’s measurements by the factor .
2.2. Calculation of Secret Key Rate with Reverse Reconciliation
Thus far, we have established the equivalence between the EB scheme and the PM scheme of the UD CV-QKD protocol. In this subsection, we present a brief overview of the calculation of the secret key rates. In the EB protocol, the realistic Bob’s detector can be modeled by an ideal balanced homodyne detector and a beam splitter, with transmission efficiency and input noise , as the one shown in Figure 1b. The secret key rate against collective attacks for reverse reconciliation in the asymptotic regime can be calculated as [29,30]
| (6) |
where is the reverse reconciliation efficiency and is the mutual information between Alice and Bob. can expressed as
| (7) |
where
| (8) |
Still from Equation (6), is the Holevo bound, which represents an upper bound on the information acquired for reverse reconciliation by the potential eavesdropper Eve. The procedures to calculate can be written as:
| (9) |
where is the von Neumann entropy of the quantum state , and are the symplectic eigenvalues of the covariance matrix , with
| (10) |
| (11) |
where is the variance of the mode in phase quadrature with and is the correlation between and in phase quadrature with .
3. Security Analysis Using Uncertainty Relations
In this section, we provide a security analysis of continuous variable quantum key distribution with coherent states based on the Heisenberg uncertainty relation. Before describing the UD coherent-state protocol case, it is useful to first consider the SY coherent-state protocol case.
3.1. Uncertainty Relations for Symmetrical Coherent-State Protocol
Let us consider a -mode quantum mechanical system that is described by the canonical conjugate operators and , with . In terms of the annihilation and creation operators ( and , respectively), one has
| (12) |
which are the dimensionless position and momentum operators. Such operators also satisfy the bosonic canonical commutation relations (CCR)
| (13) |
Furthermore, if we group together the canonical conjugate operators in a vector as
| (14) |
we can express the CCR in a compact form:
| (15) |
where is defined as
| (16) |
By combining this CCR relation and the positive semi-definiteness of the density operator , we obtain the following uncertainty relation [35]
| (17) |
which is a more precise and complete version of the Heisenberg uncertainty relation. This well-known inequality is the only constraint that has to respect to be a covariance matrix satisfying a physical state.
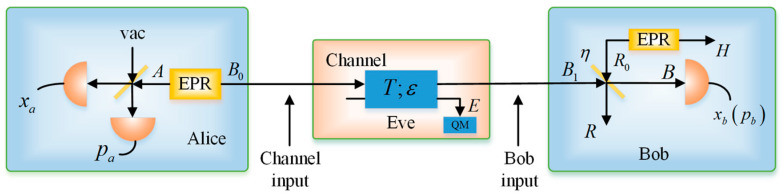
Let us consider the physicality of the SY coherent-state protocol by using the uncertainty relation in Equation (17). In the EB protocol, as shown in Figure 2, we have:
| (18) |
| (19) |
where , , , and , is the modulation variance of the Alice’s side. According to the Heisenberg uncertainty relation, we have:
| (20) |
Figure 2.
EB scheme of the SY protocol under realistic conditions.
Then, we obtain
| (21) |
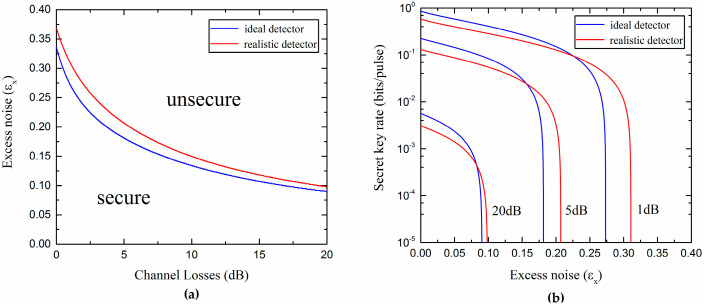
The two inequalities in Equation (21) are simultaneously satisfied if and . Here, we further consider the secure and unsecure regions of the protocol for both ideal and realistic Bob’s detectors, which are shown in Figure 3a. In the secure region, the secret key rate is greater than zero; in the unsecure region, the secret key rate is less than zero. We observe that the realistic protocol can provide a bigger secure region. The secret key rate as a function of the excess noise, in correspondence of three values of channel losses, under ideal and realistic detection conditions, is shown in Figure 3b. We can see that the realistic Bob detection improves the resistance of the protocol to the excess noise, although the total noise is increased, which will lead to the appearance of a phenomenon called “fighting noise with noise” [36], and will be discussed in detail in the following. Here, we set the values of the actual parameters: the reconciliation efficiency is [37] and the modulation variance is .
Figure 3.
(a) Secure and unsecure regions of the SY protocol using ideal homodyne detector () and realistic homodyne detector (); (b) Secret key rate versus the excess noise for different channel losses.
3.2. Uncertainty Relations for Unidimensional Coherent-State Protocol
In the above, we have discussed the physicality of the SY coherent-state protocol by using the Heisenberg uncertainty relation. The securities under ideal and realistic homodyne detectors have also been analyzed. Next, let us consider the UD coherent-state protocol. As shown in Figure 1b, in the EB scheme, we have
| (22) |
| (23) |
In the UD protocol, in order to estimate the information of the Eve eavesdropping, , we have to know the parameters and . Here, can be estimated by randomly measuring the phase quadrature in Bob’s side, while is unknown due to the fact that the phase quadrature is not modulated in Alice’s side. However, such an unknown parameter is constrained by the requirement of the physicality of the state. Differently from Ref. [30], under realistic condition, when the mode is transformed into mode after the beam splitter, there will have to be a new constraint on the covariance matrix in order to make it correspondent to a physical state. According to the Heisenberg uncertainty relation, we have
| (24) |
Then, we obtain the following two parabolic equations:
| (25) |
where , , and .
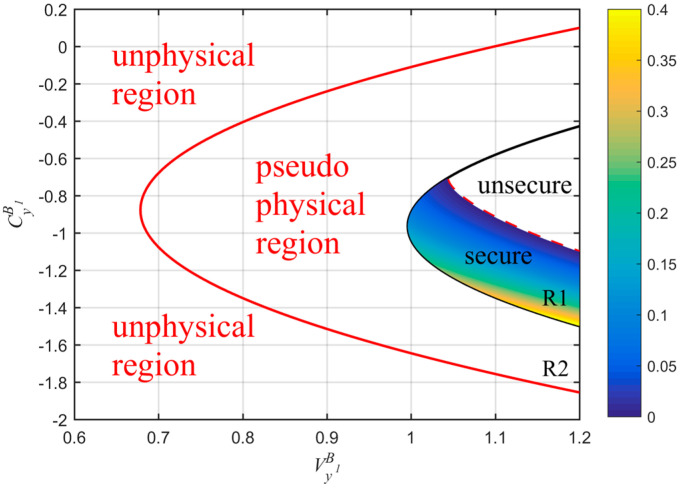
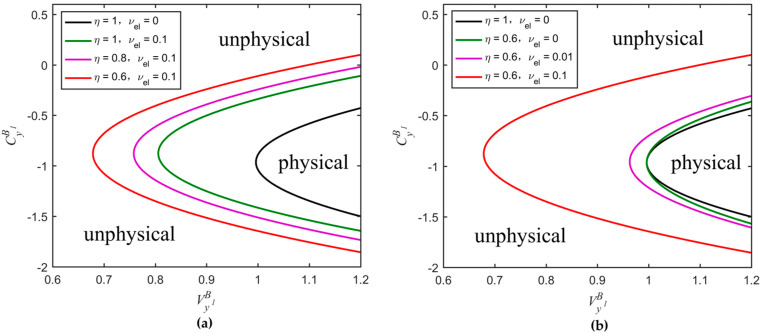
The parabolic curves between and , under ideal and realistic detection conditions, are shown in Figure 4. The whole plane is divided into two regions: the unphysical and physical regions. In the unphysical region, the values of the parameters and cannot be satisfied simultaneously, otherwise, the Heisenberg uncertainty principle will be violated. In the physical region, the whole region is divided into two parts, R1 and R2. The R1 represents the real physical region, which is delimited by the ideal parabolic curve and ensures the attacks of Eve to the quantum channel complying with the physical principles. The red dashed line further divides the region R1 into unsecure and secure regions. The R2 represents the pseudo physical region, which is the overlapped part between the physical region contained by the realistic parabolic curve and the unphysical region, as defined by the ideal parabolic curve. The appearance of the pseudo physical region is due to the fact that, even if some attacks of Eve are unphysical, after the transform of the realistic homodyne detection of Bob, the final covariance matrix can satisfy a physical state. Hence, the physical region should be delimited at the input side of Bob, or equivalently, Bob performs an ideal detection. Furthermore, in Figure 5, we see how the physical region delimited by the realistic parabolic curve changes according to different conditions of detection efficiency and electronic noise. We also compare such regions with the one delimited by the ideal parabolic curve (black solid line in Figure 5). We find that the physical region defined by the realistic parabolic curve gradually decreases as the detection efficiency increases and the electronic noise decreases. Therefore, also in this case, in order to ensure the physicality of the UD protocol, we select the smaller region R1.
Figure 4.
Comparison among physical regions of the UD protocol under both ideal and realistic detection conditions. The red solid line represents the realistic parabolic curve (equivalent to Bob using a realistic homodyne detector with ) and black solid line is the ideal parabolic curve (equivalent to Bob using an ideal homodyne detector with ). The red dashed line represents the part where the key rate is zero under realistic detection condition. Here, we set: , (corresponding to a distance of 20 km fiber), and .
Figure 5.
Comparison among physical regions delimited by the parabolic curves of the UD protocol. The black solid curve corresponds to the ideal parabolic curve, whereas the others to the realistic parabolic curves obtained for different parameter conditions. (a) Changes of the physical region extension according to different values of ( remains constant); (b) Changes of the physical region extension according to different values of ( remains constant). The values of the parameters , , and are the same as in Figure 4.
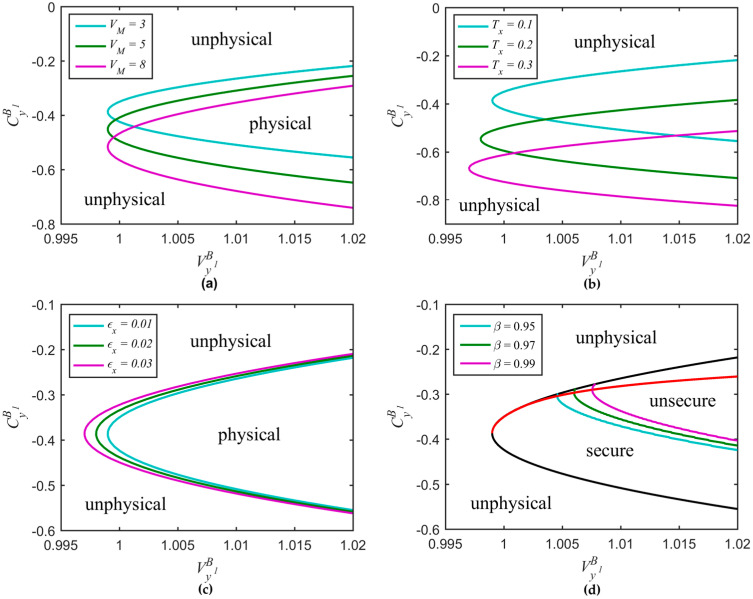
In Figure 6, we consider the dependence of the ideal parabolic curve (R1) on related parameters, including , , , and . From Figure 6a, we can find that the parabolic curve moves down and gradually becomes broader as the modulation variance increases. In Figure 6b, the parabolic curve moves towards bottom-left corner and gradually becomes narrower as the transmission efficiency increases. In Figure 6c, as the excess noise increases, the parabolic curve moves towards left and gradually becomes larger. The reconciliation efficiency does not change the shape of the parabola, but rather expands the secure region. In Figure 6d, the red solid line represents the minimum secret key rate, which was obtained by scanning the parameter . The black solid line represents the ideal parabolic curve. It is interesting that a larger does not always give a higher secret key rate, more details about the red solid line can be seen in paper [30]. Later, we can see that the minimum secret key rate can also be achieved by scanning and simultaneously.
Figure 6.
Ideal parabolic curve versus related parameters. (a) Different modulation variance values with and ; (b) Different transmission efficiency values with and ; (c) Different excess noise values with and ; (d) Different reconciliation efficiency values with , , and .
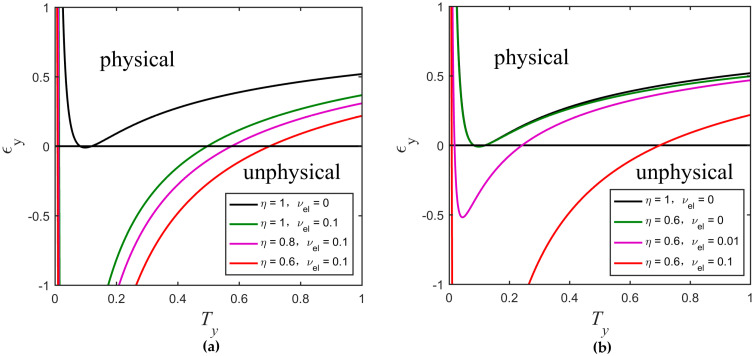
Furthermore, if we assume and , the parabolic equations (Equation (25)), as determined by the Heisenberg uncertainty relation under ideal and realistic detection conditions transform into
| (26) |
where and . By this way, more details about eavesdropping method taken by Eve can be found. Moreover, one can easily see that the transformed equations do not depend on . We redraw the physical regions delimited by the new curves for different values of detection efficiency and electronic noise as shown in Figure 7. We obtain the same rule as in Figure 5 that the physical region gradually decreases as the detection efficiency increases and the electronic noise decreases. Secure and unsecure regions under the realistic detection condition are shown in Figure 8. The cyan curve with the secret key rate of zero represents the boundary of two regions. Although the parameters and are unknown, they are confined to the curve , which can be estimated by randomly measuring the phase quadrature in Bob’s side, meaning that and cannot be set simultaneously in other physical places outside this curve. We can see that Eve essentially changes the value of the parameter by controlling the value of . For a constant value of , we can calculate the minimum secret key rate by scanning or in the physical region. As shown in Figure 8, the curve corresponding to the minimum secret key rate is divided into three parts. The red curve part overlaps with the left boundary of the black solid curve which corresponds to the black solid curve in Figure 6d. As the value of increases, the worst-case and (green curve part) gradually separate from the black solid curve, meaning that the secret key rate of the protocol is not always monotonically decreasing as increases or decreases, but still lie in the secure region. The blue curve represents the part where the minimum secret key rate is less than zero. We also find that this minimum secret key rate is equal to the minimum secret key rate that was obtained by scanning (corresponding to the red solid line of Figure 6d) when other parameter values are set to be consistent.
Figure 7.
Comparison among physical regions delimited by the new curves of the UD protocol. (a) Changes of the physical region according to different values of ( remains constant); (b) Changes of the physical region according to different values of ( remains constant). The other parameters are , , , and .
Figure 8.
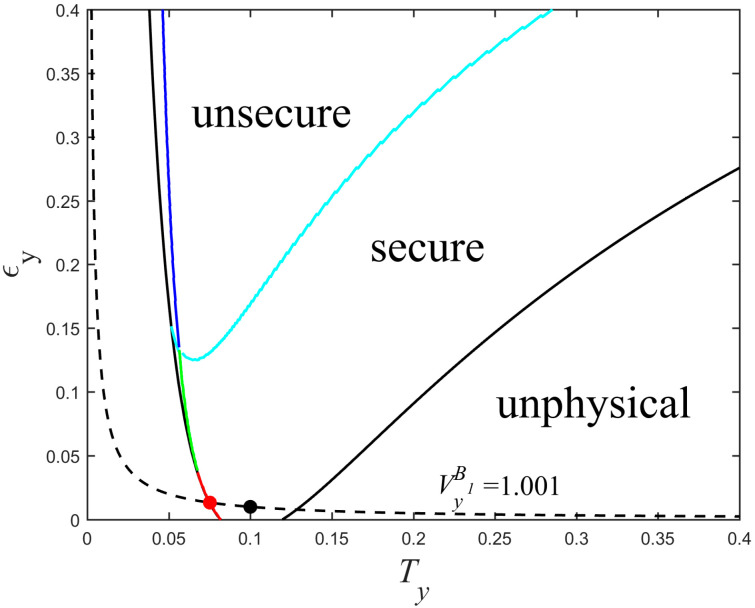
Secure and unsecure regions of the UD protocol under realistic detection condition. The parameters are set to , , , , , and .
In typical communication channels, the value of can be estimated by setting , which is plotted with the black dashed line of Figure 8. At the black point, the conditions and are satisfied. The red point represents the worst-case and , which is the intersection of the red line and black dashed line. Because Eve can distinguishes , from , by measuring coherent states sent by Alice, she can arbitrarily change the values of both and , while keeps unchanged, eventually, obtains more information. If Alice and Bob use and to estimate and (black point), then this will underestimate the ability of the eavesdropper Eve and provide security loopholes. Therefore, here we should consider the minimum secret key rate (red point).
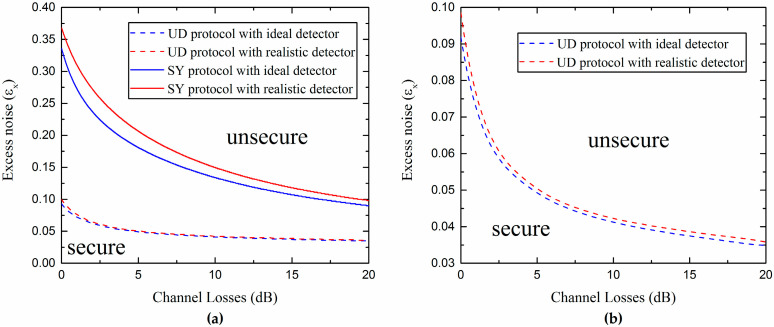
In Figure 9, the curves representing the maximal tolerable excess noise versus the channel losses under ideal and realistic detection conditions are shown. We observe that the UD protocol has a lower tolerance to the excess noise than the SY protocol. However, the UD protocol reduces the complexity of the experiment and still provides a reasonable secure region (all of the parameters are set under the actual conditions).
Figure 9.
(a) Comparison between secure and unsecure regions for the SY coherent-state protocol and UD coherent-state protocol under different detection conditions; (b) Secure and unsecure regions of the UD protocol using an ideal homodyne detector () and a realistic one (). Here we consider , , and the estimated value .
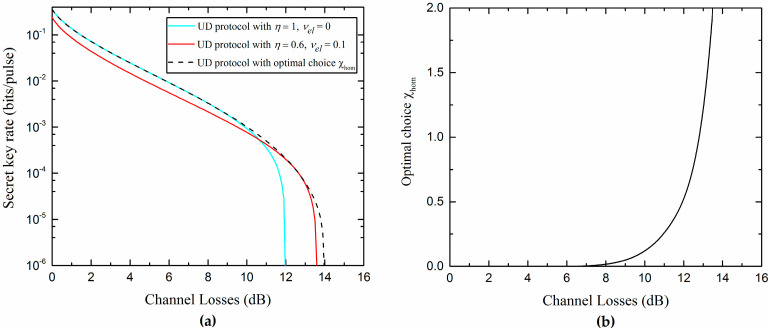
In addition, from Figure 9b, it is not difficult to find out that the realistic Bob’s detection can slightly increase the secure region of the UD protocol. This effect can be explained by considering the fact that the noise added on Bob’s side not only affects Alice’s and Bob’s mutual information, but also decreases Eve’s information in reverse reconciliation. Due to the detection at Bob’s side, which can be controlled and observed by Bob, the noise added on Bob’s side could be considered as a believable noise not controlled by the eavesdropper Eve. Moreover, it is found that there is an optimal noise (characterized by the detection efficiency and electronic noise ) that Bob needs to add to maximize the secret key rate for each channel loss. Then, we can effectively improve the secret key rate and increase the transmission distance by adding proper noise to Bob’s side, as we show in Figure 10.
Figure 10.
(a) Minimum secret key rate as a function of the channel losses; (b) Optimal choice of that maximizes the secret key rate in (a). The other parameters are , , , and .
4. Conclusions
In this paper, we have proven the equivalence between the EB scheme and the PM scheme of the UD CV-QKD protocol, and investigated the physical and secure regions of the SY coherent-state protocol based on the Heisenberg uncertainty relation. It was shown that the realistic detection condition in UD protocol results in an excess pseudo physical region, which corresponds to the unphysical attack of Eve. In order to ensure the physicality, we should select the physical region delimited by the ideal curve. We also found that a realistic Bob’s detection improves the resistance of the protocol to the channel excess noise, therefore, the performance in terms of the secret key rates and transmission distances of the UD coherent-state protocol can be improved by adding an optimal noise to the reconciliation side. Overall, the results confirm the potential of a long-distance secure communication through the usage of the UD CV-QKD protocol.
Acknowledgments
This work was supported by the Key Project of the Ministry of Science and Technology of China (2016YFA0301403), the National Natural Science Foundation of China (NSFC) (Grants No. 11504219, No. 61378010), the Shanxi 1331KSC, and the Program for the Outstanding Innovative Teams of Higher Learning Institutions of Shanxi.
Author Contributions
Pu Wang conceived the study, performed theoretical calculations and numerical simulations and drafted the article. Xuyang Wang designed the conception of the study, discussed the results, checked the draft and critically reviewed the manuscript. Yongmin Li proposed and supervised the project, checked the draft and provided a critical revision of the manuscript. All authors have read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Gisin N., Ribordy G., Tittel W., Zbinden H. Quantum cryptography. Rev. Mod. Phys. 2002;74:145–195. doi: 10.1103/RevModPhys.74.145. [DOI] [Google Scholar]
- 2.Scarani V., Bechmann-Pasquinucci H., Cerf N.J., Dušek M., Lütkenhaus N., Peev M. The security of practical quantum key distribution. Rev. Mod. Phys. 2009;81:1301–1350. doi: 10.1103/RevModPhys.81.1301. [DOI] [Google Scholar]
- 3.Cerf N.J., Levy M., Van Assche G. Quantum distribution of gaussian keys using squeezed states. Phys. Rev. A. 2001;63:052311. doi: 10.1103/PhysRevA.63.052311. [DOI] [Google Scholar]
- 4.Silberhorn C., Ralph T.C., Lütkenhaus N., Leuchs G. Continuous variable quantum cryptography: Beating the 3 db loss limit. Phys. Rev. Lett. 2002;89:167901. doi: 10.1103/PhysRevLett.89.167901. [DOI] [PubMed] [Google Scholar]
- 5.Weedbrook C., Lance A.M., Bowen W.P., Symul T., Ralph T.C., Lam P.K. Quantum cryptography without switching. Phys. Rev. Lett. 2004;93:170504. doi: 10.1103/PhysRevLett.93.170504. [DOI] [PubMed] [Google Scholar]
- 6.Fossier S., Diamanti E., Debuisschert T., Villing A., Tualle-Brouri R., Grangier P. Field test of a continuous-variable quantum key distribution prototype. New J. Phys. 2009;11:045023. doi: 10.1088/1367-2630/11/4/045023. [DOI] [Google Scholar]
- 7.Leverrier A., Grangier P. Continuous-variable quantum-key-distribution protocols with a non-gaussian modulation. Phys. Rev. A. 2011;83:042312. doi: 10.1103/PhysRevA.83.042312. [DOI] [Google Scholar]
- 8.Madsen L.S., Usenko V.C., Lassen M., Filip R., Andersen U.L. Continuous variable quantum key distribution with modulated entangled states. Nat. Commun. 2012;3:1083. doi: 10.1038/ncomms2097. [DOI] [PubMed] [Google Scholar]
- 9.Wang X.Y., Bai Z.L., Du P.Y., Li Y.M., Peng K.C. Ultrastable fiber-based time-domain balanced homodyne detector for quantum communication. Chin. Phys. Lett. 2012;29:124202. doi: 10.1088/0256-307X/29/12/124202. [DOI] [Google Scholar]
- 10.Weedbrook C., Pirandola S., García-Patrón R., Cerf N.J., Ralph T.C., Shapiro J.H., Lloyd S. Gaussian quantum information. Rev. Mod. Phys. 2012;84:621–669. doi: 10.1103/RevModPhys.84.621. [DOI] [Google Scholar]
- 11.Wang X.Y., Bai Z.L., Wang S.F., Li Y.M., Peng K.C. Four-state modulation continuous variable quantum key distribution over a 30-km fiber and analysis of excess noise. Chin. Phys. Lett. 2013;30:010305. doi: 10.1088/0256-307X/30/1/010305. [DOI] [Google Scholar]
- 12.Gehring T., Handchen V., Duhme J., Furrer F., Franz T., Pacher C., Werner R.F., Schnabel R. Implementation of continuous-variable quantum key distribution with composable and one-sided-device-independent security against coherent attacks. Nat. Commun. 2015;6:8795. doi: 10.1038/ncomms9795. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 13.Zhang Y., Li Z., Weedbrook C., Marshall K., Pirandola S., Yu S., Guo H. Noiseless linear amplifiers in entanglement-based continuous-variable quantum key distribution. Entropy. 2015;17:4547. doi: 10.3390/e17074547. [DOI] [Google Scholar]
- 14.Li H.S., Wang C., Huang P., Huang D., Wang T., Zeng G.H. Practical continuous-variable quantum key distribution without finite sampling bandwidth effects. Opt. Express. 2016;24:20481–20493. doi: 10.1364/OE.24.020481. [DOI] [PubMed] [Google Scholar]
- 15.Bai D.Y., Huang P., Ma H.X., Wang T., Zeng G.H. Performance improvement of plug-and-play dual-phase-modulated quantum key distribution by using a noiseless amplifier. Entropy. 2017;19:546. doi: 10.3390/e19100546. [DOI] [Google Scholar]
- 16.Bai Z.L., Yang S.S., Li Y.M. High-efficiency reconciliation for continuous variable quantum key distribution. Jpn. J. Appl. Phys. 2017;56:044401. doi: 10.7567/JJAP.56.044401. [DOI] [Google Scholar]
- 17.Grosshans F., Grangier P. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 2002;88:057902. doi: 10.1103/PhysRevLett.88.057902. [DOI] [PubMed] [Google Scholar]
- 18.Grosshans F., Van Assche G., Wenger J., Brouri R., Cerf N.J., Grangier P. Quantum key distribution using gaussian-modulated coherent states. Nature. 2003;421:238–241. doi: 10.1038/nature01289. [DOI] [PubMed] [Google Scholar]
- 19.Iblisdir S., Van Assche G., Cerf N.J. Security of quantum key distribution with coherent states and homodyne detection. Phys. Rev. Lett. 2004;93:170502. doi: 10.1103/PhysRevLett.93.170502. [DOI] [PubMed] [Google Scholar]
- 20.Grosshans F. Collective attacks and unconditional security in continuous variable quantum key distribution. Phys. Rev. Lett. 2005;94:020504. doi: 10.1103/PhysRevLett.94.020504. [DOI] [PubMed] [Google Scholar]
- 21.Lance A.M., Symul T., Sharma V., Weedbrook C., Ralph T.C., Lam P.K. No-switching quantum key distribution using broadband modulated coherent light. Phys. Rev. Lett. 2005;95:180503. doi: 10.1103/PhysRevLett.95.180503. [DOI] [PubMed] [Google Scholar]
- 22.Lodewyck J., Bloch M., Garcia-Patron R., Fossier S., Karpov E., Diamanti E., Debuisschert T., Cerf N.J., Tualle-Brouri R., McLaughlin S.W., et al. Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phys. Rev. A. 2007;76:042503. doi: 10.1103/PhysRevA.76.042305. [DOI] [Google Scholar]
- 23.Qi B., Huang L.L., Qian L., Lo H.K. Experimental study on the gaussian-modulated coherent-state quantum key distribution over standard telecommunication fibers. Phys. Rev. A. 2007;76:052323. doi: 10.1103/PhysRevA.76.052323. [DOI] [Google Scholar]
- 24.Yang S.S., Bai Z.L., Wang X.Y., Li Y.M. FPGA-based implementation of size-adaptive privacy amplification in quantum key distribution. Photonics J. 2017;9:7600308. doi: 10.1109/JPHOT.2017.2761807. [DOI] [Google Scholar]
- 25.Jouguet P., Kunz-Jacques S., Leverrier A., Grangier P., Diamanti E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photonics. 2013;7:378–381. doi: 10.1038/nphoton.2013.63. [DOI] [Google Scholar]
- 26.Li Y.M., Wang X.Y., Bai Z.L., Liu W.Y., Yang S.S., Peng K.C. Continuous variable quantum key distribution. Chin. Phys. B. 2017;26:040303. doi: 10.1088/1674-1056/26/4/040303. [DOI] [Google Scholar]
- 27.Liu W.Y., Wang X.Y., Wang N., Du S.N., Li Y.M. Imperfect state preparation in continuous-variable quantum key distribution. Phys. Rev. A. 2017;96:042312. doi: 10.1103/PhysRevA.96.042312. [DOI] [Google Scholar]
- 28.Usenko V.C., Grosshans F. Unidimensional continuous-variable quantum key distribution. Phys. Rev. A. 2015;92:062337. doi: 10.1103/PhysRevA.92.062337. [DOI] [Google Scholar]
- 29.Wang X.Y., Liu W.Y., Wang P., Li Y.M. Experimental study on all-fiber-based unidimensional continuous-variable quantum key distribution. Phys. Rev. A. 2017;95:062330. doi: 10.1103/PhysRevA.95.062330. [DOI] [Google Scholar]
- 30.Wang P., Wang X.Y., Li J.Q., Li Y.M. Finite-size analysis of unidimensional continuous-variable quantum key distribution under realistic conditions. Opt. Express. 2017;25:27995–28009. doi: 10.1364/OE.25.027995. [DOI] [Google Scholar]
- 31.Braunstein S.L., van Loock P. Quantum information with continuous variables. Rev. Mod. Phys. 2005;77:513–577. doi: 10.1103/RevModPhys.77.513. [DOI] [Google Scholar]
- 32.Serafini A. Detecting entanglement by symplectic uncertainty relations. J. Opt. Soc. Am. B. 2007;24:347–354. doi: 10.1364/JOSAB.24.000347. [DOI] [Google Scholar]
- 33.Grosshans F., Cerf N.J., Wenger J., Tualle-Brouri R., Grangier P. Virtual entanglement and reconciliation protocols for quantum cryptography with continuous variables. Quantum Inform. Comput. 2003;3:535–552. [Google Scholar]
- 34.Ben-Israel A., Greville T.N.E. Generalized Inverses: Theory and Applications. 2nd ed. Springer; New York, NY, USA: 2003. [Google Scholar]
- 35.Serafini A., Paris M.G.A., Illuminati F., Siena S.D. Quantifying decoherence in continuous variable systems. J. Opt. B. 2005;7:R19. doi: 10.1088/1464-4266/7/4/R01. [DOI] [Google Scholar]
- 36.Garcia-Patron R., Cerf N.J. Continuous-variable quantum key distribution protocols over noisy channels. Phys. Rev. Lett. 2009;102:130501. doi: 10.1103/PhysRevLett.102.130501. [DOI] [PubMed] [Google Scholar]
- 37.Milicevic M., Feng C., Zhang L.M., Gulak P.G. Key reconciliation with low-density parity-check codes for long-distance quantum cryptography. arXiv. 2017. 1702.07740