Abstract
Multimedia encryption innovation is one of the primary ways of securely and privately guaranteeing the security of media transmission. There are many advantages when utilizing the attributes of chaos, for example, arbitrariness, consistency, ergodicity, and initial condition affectability, for any covert multimedia transmission. Additionally, many more benefits can be introduced with the exceptional space compliance, unique information, and processing capability of real mitochondrial deoxyribonucleic acid (mtDNA). In this article, color image encryption employs a confusion process based on a hybrid chaotic map, first to split each channel of color images into n-clusters; then to create global shuffling over the whole image; and finally, to apply intrapixel shuffling in each cluster, which results in very disordered pixels in the encrypted image. Then, it utilizes the rationale of human mitochondrial genome mtDNA to diffuse the previously confused pixel values. Hypothetical examination and trial results demonstrate that the anticipated scheme exhibits outstanding encryption, as well as successfully opposes chosen/known plain text, statistical, and differential attacks.
Keywords: hybrid chaotic, image, encryption, decryption, secured communications, DNA, mitochondrial genome
1. Introduction
Owing to vast development in the modern digital era, the world has grown to be a worldwide community sharing private information. Because of this, people use images instead of long texts for sharing this kind of information securely and privately [1]. Therefore, the protection of such images has become one of the vital concerns in medical, military, and many other areas. Recently, many cryptographic algorithms depending on chaotic systems have been used in image encryption [2]. One of the recognized methods employed before image transmission is to convert an image into an unintelligible form, so that the transmitted message of the distorted image will not be discovered if it has reached an unsought end [3,4]. The encryption process is done with the help of a key, which produces variation on the pixel values of the image and destroys the apparent image attribute. Another encryption process is the scrambling image technique. In this technique, all pixel values are repositioned between different pixels of the image to be different from the original plain image, for example, Arnold transform, exponential transformation, geometry transform, and so on. These transformations have definite regularity, although the results of pixel distribution are different after scrambling, due to changes in only the position of pixels, without changing gray values. Arnold’s map has the property of periodicity. After running the algorithm for a certain number of times, the original image can be restored. Therefore, it has a weakness for the system [5]. However, whilst [6] demonstrated the powerful recovery of an image encryption system based on an Arnold map and Lü map, their encryption system was susceptible to several attacks, such as plaintext and chosen-text attacks when it depended on only the permutation of pixel values [7]. As a result, these attack pixel values have to be rearranged and vary their position. Rearrangement of the values of pixels is called the confusion process, while changing the pixel values is known as the diffusion process. Chaos is a multi-disciplinary hypothesis which states that during the randomness of the chaotic complex technique, the chaotic system generates sequences due to its initial parameters’ sensitivity, periodic and pseudo randomness, and long-term volatility [8], which encouraged us to employ the chaos theory in our new proposed scheme.
In recent years, several scientific papers have concentrated on researching chaotic image encryption. In 2015 [9], S. S. Askar, A. A. Karawia et al. presented an image encryption system based on a chaotic economic map, and the simulation outputs a display so that the proposed algorithm can utilize the same secret keys to encrypt and decrypt the images successfully. The security analysis shows that the encrypted images have a good performance, but cannot resist noise attacks. After one year, Abbas proposed a new image encryption technique based on unconventional element analysis and Arnold’s Cat Map [10], which was easily achieved and afforded an efficient and secure approach for image encryption. However, the algorithm depends on the encryption of square images only, so the domain of application is remarkably restricted. Later, in 2017, Shaikh, Chapaneri et al. [11] proposed a color image encryption algorithm, which is a single round-based hyperchaotic system due to bi-directional pixel diffusion that contributes towards an increased security and improved efficiency. Recently, in 2019, Chenghai Li et al. used the “transforming-scrambling-diffusion” model to introduce a hyperchaotic color image encryption algorithm that depends on converting the pixel values into gray codes before scrambling [12]. In the same year, Priya Ramasamy et al. suggested an improved logistical map while using a chaotic maps function and uncomplicated encryption techniques, such as block scrambling and modified zigzag transformation, for encryption phases [13]. Recently, deoxyribonucleic acid (DNA) was applied to an image chaotic cryptosystem [14,15,16,17,18,19,20,21,22], as a result of its numerous superior characteristics, such as its enormous parallelism, vast storage, small power consumption, etc. In 2016, Kulsoom et al. extracted the most significant bits and the least significant bits for each pixel of an image and performed DNA computing for them. Kulsoom et al.’s algorithm has a low robustness against noise because most digits of each pixel are not changed [23]. After that, in 2018, Ran Wei et al. proposed an image cryptosystem that depends on the combination of DNA encoding and several chaotic maps [24]. The performance analysis illustrated that the system could greatly enhance the sensitivity of plain images and secret keys, but the algorithm was complex and the necessities for hardware were comparatively high. In 2020, J. Wu, J. Shi, T. Li, proposed a novel image encryption algorithm based on a hyperchaotic system and variable kernels for the confusion stage and a DNA technique for the diffusion stage [25].
Mitochondrial DNA (mtDNA) is a small part of the DNA of organelle cells within eukaryotic cells [26]. Eukaryotic cells are organisms that have a nucleus enclosed within membranes that are used to transform chemical energy into a formula that cells can use [27]. In humans, there are 16,569 base duos of mitochondrial DNA to code only 37 genes. The first major part of the human genome that can be sequenced is human mitochondrial DNA [28]. mtDNA is congenital and uniquely from the mother in several organisms, including humans. Since animal mtDNA develops more rapidly than nuclear genetic symbols [29,30], it signifies a mainstay of phylogenetic and evolutionary biology. mtDNA allows inspection of the kinship of inhabitants. Therefore, it has become vital in molecular biology and biotechnology.
In this article, a new image cryptosystem is presented to encrypt a color image using identical encryption and decryption schemes. Both of these processes consist of confusion stages employing a hyperchaotic system, diffusion stage, and mtDNA. The proposed encryption algorithm was applied on three channels of a color plain image to increase uncertainty in the plain image. From the numerical analysis, the proposed algorithm was seen to be robust against various attacks, for example, chosen/known plain text attacks, brute force attacks, differential cipher image attacks, and entropy attacks. It has a large key space and is sensitive to minimal change in the chosen secret key. The encryption scheme was also compared with newly developed encryption techniques. The rest of the article is organized as follows. Section 2 details a brief description of the hyperchaotic system, mtDNA, and DNA encoding. The explanation and argument of the proposed encryption/decryption algorithm are introduced in Section 3. Section 4 gives the numerical simulation results, while the security act of the proposed scheme is analyzed in Section 5. Finally, Section 6 concludes the article.
2. Preliminaries
2.1. Hyperchaotic System
A hyperchaos system, technologically, advanced from chaos. Its dynamical structure is more complicated compared with other chaotic systems. In addition, hyperchaos enhances a higher level of randomization and uncertainty. By adding two or more positive Lyapunov exponents, the hyperchaotic system can be distinguished from chaos. Hyperchaos exists in four-dimension nonlinear systems. Owing to its simpler formula and higher effectiveness, the chaotic system has a smaller key space and lower complexity. Consequently, the chaotic system has lower security protection. On the contrary, the hyperchaotic system has more state variables, a larger key space, and complex nonlinear behavior, resulting in higher security protection. The hyperchaotic system can be determined as follows [31]:
| (1) |
where , and are the control parameters of the 4-D hyperchaotic system. The system presents hyperchaotic behavior when the control parameters are , and
2.2. Fundamentals of Mitochondrial DNA
Mitochondrial DNA is a type of DNA and is a small chromosome in a circular form found inside organelles known as mitochondria. Mitochondria are found in cells and have been determined in all unpredictable or eukaryotic cells, as well as plants, creatures, growths, and single-celled protists, which include their own mtDNA genome. In several creatures, mtDNA is a two-fold stranded particle that is shaped around the genome. Every mitochondrion can have several duplicates of the mtDNA genome. In human embryonic advancement, the variety of mitochondria and the substance of mtDNA in every mitochondrion have an impact on the creation of oocytes, preparation of the oocytes, and early embryonic development and enchantment [32].
For example, a simple sequence for the human mitochondrial genome is as follows:
“GATCACAGGTCTATCACCCTATTAACCACTCACGGGAGCTCTCCATGCAT
TTGGTATTTTCGTCTGGGGGGTGTGCACGCGATAGCATTGCGAGACGCTG
GAGCCGGAGCACCCTATGTCGCAGTATCTGTCTTTGATTCCTGCCTCATT
CTATTATTTATCGCACCTACGTTCAATATTACAGGCGAACATACCTACTAAAGT…”
2.3. DNA Encoding
DNA encoding has a huge data capacity, so it can be used in cryptography [33]. In the transmission process, DNA can also be used to store data in image encryption. DNA computing depends on the DNA logic word, and only two digits are used to create four nucleic acid bases. Therefore, the information is stored in the form of these bases, which are Adenine (A), Cytosine (C), Guanine (G), and Thymine (T) [34]. In DNA cryptography, the four bases are used to capture the information. “A” and “T” are paired duos and the same is true for “C” and “G”. Table 1 displays the rubrics for DNA encoding.
Table 1.
Rubrics for DNA encoding [35].
| Rule No. | DNA Nucleic Acids | |||
|---|---|---|---|---|
| A | T | G | C | |
| Rb1 | 00 | 11 | 01 | 10 |
| Rb2 | 00 | 11 | 10 | 01 |
| Rb3 | 11 | 00 | 01 | 10 |
| Rb4 | 11 | 00 | 10 | 01 |
| Rb5 | 10 | 01 | 11 | 00 |
| Rb6 | 01 | 10 | 11 | 00 |
| Rb7 | 10 | 01 | 00 | 11 |
| Rb8 | 01 | 10 | 00 | 11 |
3. Proposed Cryptosystem
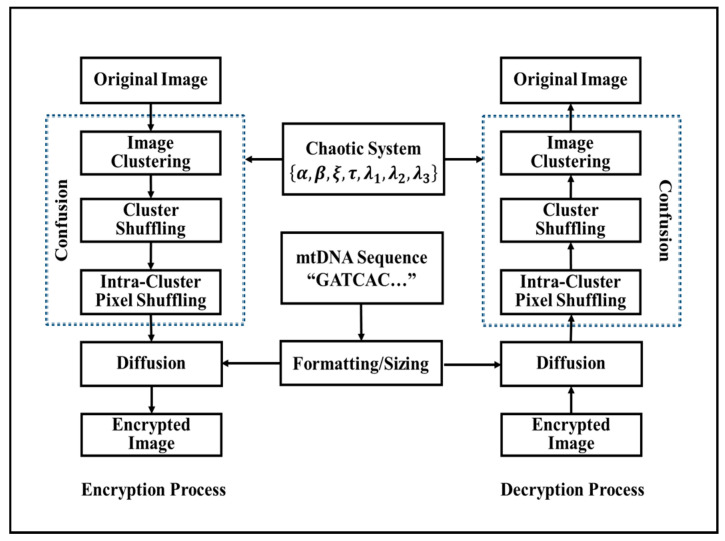
The structure of the proposed cryptosystem is demonstrated in Figure 1, and involves two main phases. In the first phase, the confusion phase, the image pixels are shuffled based on the generated hyperchaotic sequence discussed in the first part of Section 2. For more unpredictability and to increase the efficiency of encryption, the pixels’ positions are scrambled over the entire image, without changing the significance of the pixels, and the image becomes unknown. Hence, the primary and control factors of utilized chaotic maps serve as the employed undisclosed key. To improve the security further, the second stage, the diffusion stage, aims to diffuse the images’ pixel values with the decimal converted values of the mtDNA sequence using the Exclusive OR (XOR) operation.
Figure 1.
The proposed algorithm.
3.1. Hyperchaotic Sequence Generation
We can use the hyperchaotic system discussed in Section 2.1 to generate the pseudorandom sequence. This is necessary for the field of cryptography, as both non-linearity and random performances make chaotic systems able to generate pseudorandom sequences. The following steps describe the sequence generation:
To reduce the cross effects and raise the security, pre-iterate the hyperchaotic system times;
The system is iterated another M × N times after iteration times. In each iteration , four state values are sorted, where denotes the iteration index;
- During each iteration, each state value of the four-state values is used to generate two different key values ( and ), which are calculated by
(2)
where indicates the modulo process;(3) - Concatenate Equation (2) with Equation (3) to get :
(4) - These sequences are concatenated after the whole iteration with Equation (5) to obtain K:
(5)
One component in K can be represented by
3.2. Image Encryption
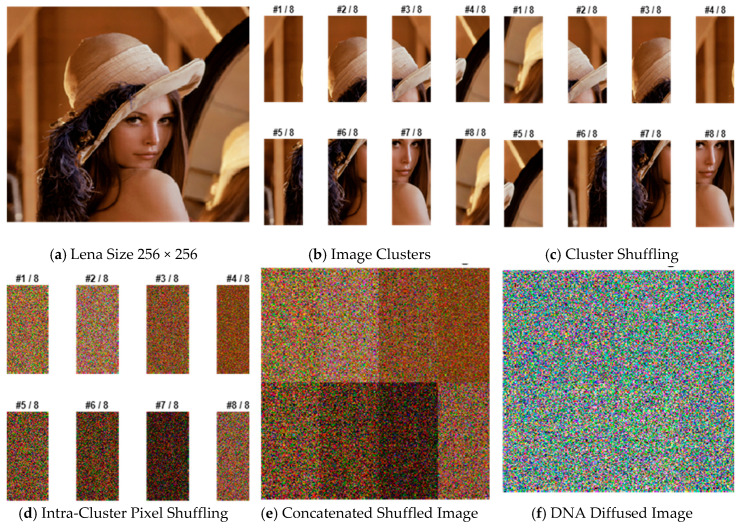
Let represent the whole dimension of the contribution color image P, as displayed in Figure 2a;
Obtain the three channels R, G, and B from the input image;
Divide each channel for both the row and column into clusters, where and randomly depend on the generated chaotic sequence. For example, when and the resulting image is split into eight clusters, as shown in Figure 2b;
Shuffle all the clusters using the generated chaotic sequence K, as illustrated in Figure 2c;
Apply a chaotic sequence for each cluster to shuffle the pixels within every cluster, as clarified in Figure 2d;
Concatenate these permuted clusters to formulate the shuffled image with the same size of the novel colored image illustrated in Figure 2e;
- To get new values of pixels, apply the diffusion process as follows:
- Read the first 64 × 64 × 4 mitochondrial DNA sequence “gatcacaggtctatcaccctattaaccactca……”;
-
Convert it to a binary sequence using the rule discussed in Table 1:“{0001101101110100001011100110110111111110011010010111110……}”;
- Divide the sequence into 8-bit slices: {00011011 01110100 00101110 01101101 11111110…};
- Convert each slice into its decimal representation: [27 116 46 109 254 105 125…];
- Formulate a 64 × 64 rdDNAstring matrix with the above decimal sequences;
- Generate a 3 × 64 × 64 matrix for the three channels R, G, and B, as in
(6) - Generate 128 × 128 × 3 using
where [ ]’ is the transpose of the matrix;(7) - Generate 256 × 256 × 3 using
(8) - Resize the generated matrix to the same size of the concatenated image;
- Apply the XOR operation between the concatenated shuffled pixel values and the decimal converted values of mtDNA classification r1 and r2 to get the diffused encrypted image, as shown in Figure 2f.
Figure 2.
Simulation results of a Lena image.
4. Simulation Results
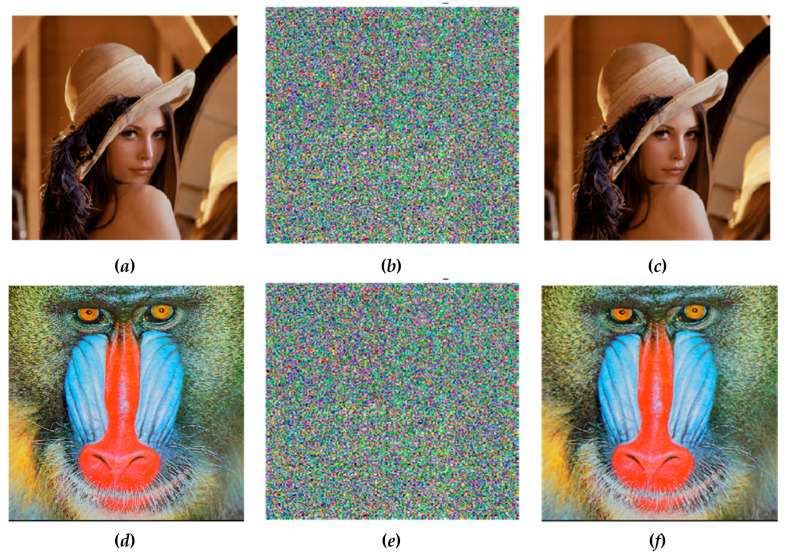
Experimentation was carried out on Lena and baboon images. The Matlab (R2015a) software (MathWorks, Natick, MA, USA) was used to apply the proposed algorithm. In the hyperchaotic map, the control parameters , and were used to produce a chaotic sequence. The hyperchaotic sequences were arranged and the position of arranged sequences was used to split the plain image into n-clusters, shuffle the whole clusters, and scramble the pixels of each cluster. The utilized colored plain images were Lena, with dimensions of 256 × 256 pixels, as shown in Figure 3a, and Baboon, with dimensions of 512 × 512 pixels, as shown in Figure 3d. The corresponding cipher image was generated using the encryption algorithm and is shown in Figure 3b,e. Then, we decrypted the cipher image, as presented in Figure 3b,e, with correct undisclosed key K to get the perfectly reconstructed image shown in Figure 3c,f.
Figure 3.
Simulation results. (a,d) Plain images; (b,e) generated cipher images of (a,d), respectively; and (c,f) recovered images.
5. Performance and Security Analysis
5.1. Key Space
The key space of our new encryption algorithm consisted of the initial conditions of hyper-chaotic systems , and . The value ranges were , , and , each with a step size of , while the value range was , with a step size of . and are two 8-bit random numbers whose value range is [0, 255] with a single step size. These factors were used as undisclosed keys for both the encryption and decryption process. Therefore, the key space of the proposed algorithm is 1.6777 × . The key space must be very large to restrict brute-force attacks; hence, it would take 2.03451 × days to crack the system. Therefore, the proposed cryptosystem is able to protect against brute-force attacks.
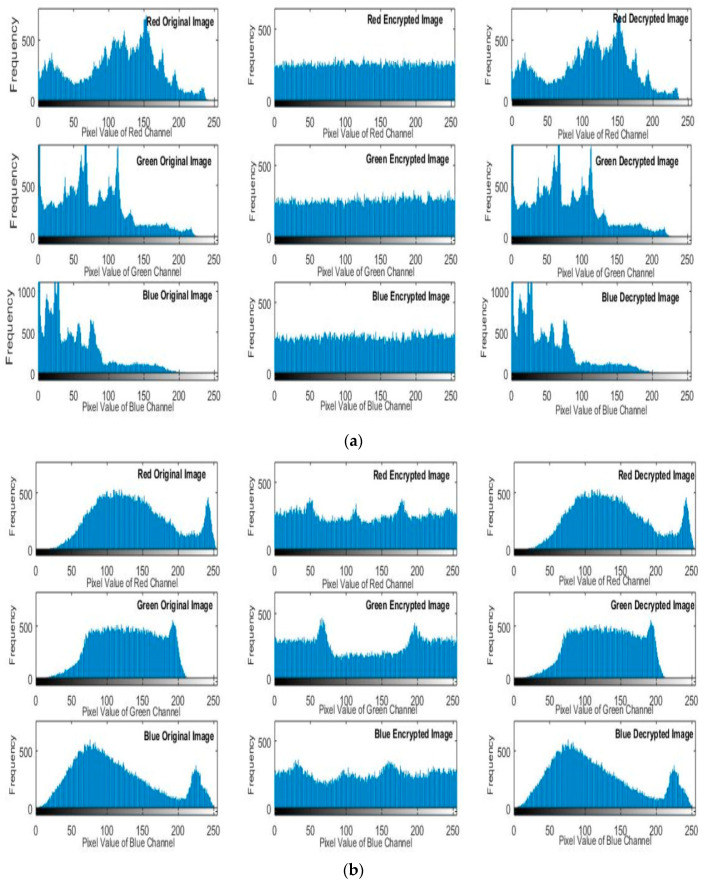
5.2. Histogram Analysis
Histogram analysis is an important statistical feature for estimating the enactment of an image encryption cryptosystem. The histograms for the three channels of original images of Lena and Baboon and their corresponding generated cipher images are presented in Figure 4. The original image’s histogram is non-uniform and the characteristic peak is clear, and most of the image data were achieved smoothly. On the other hand, the recovered image is a perfectly reconstructed form of the original image, and the cipher image is noise-like and not correlated with the original plain image. The recovered image is a perfectly reconstructed version of the original image. In the cipher image, the histogram is very stable and smooth, which proves that no statistical data from the original plain image was included. Therefore, the proposed system can counterattack statistical and cipher image attacks.
Figure 4.
Histograms of colored plain images. (a) Histograms of Lena. (b) Histograms of baboon. The first column includes histograms of the original image, the second column includes histograms of the corresponding cipher image, and the third column includes histograms of the recovered colored image.
5.3. Correlation Factor Analysis
The correlation factor (CF) is an important metric for calculating two adjacent pixels in the three directions of horizontal, vertical, and diagonal. N pairs of neighboring pixels are selected, and are two neighboring pixels. Then, the calculation formula of the correlation factor can be given by
| (9) |
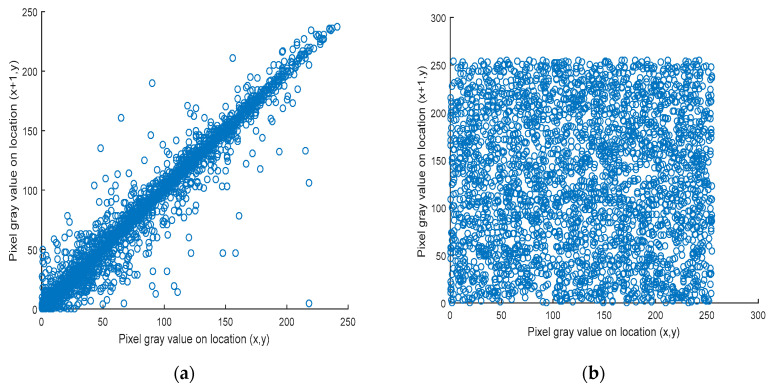
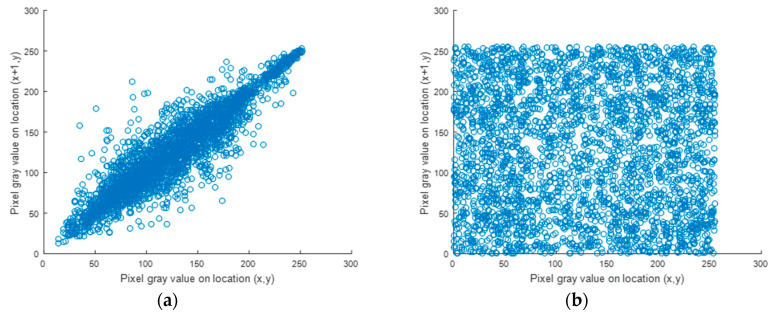
Now, let N = 2000. The results of the correlation of the original and cipher images were computed and are presented in Table 2. The low value of the correlation factor for neighboring pixels in the three directions indicates that the neighboring pixels are uncorrelated. Figure 5 and Figure 6 display the correlation distribution of each pair of horizontally neighboring pixels. The correlation factor of the original image is high and close to 1. In contrast, the correlation factor calculated for the cipher image is low and close to 0. Therefore, these results verify the strength of the proposed cryptosystem.
Table 2.
The various calculated correlation factors.
| Correlation Factors | Direction of Adjacent Pixels | ||
|---|---|---|---|
| Horizontal | Vertical | Diagonal | |
| Plain | 0.9706 | 0.9841 | 0.9639 |
| Cipher | 0.0058 | 0.0033 | 0.0010 |
| Plain | 0.9195 | 0.9005 | 0.8696 |
| Cipher | 0.0013 | 0.0025 | 0.0010 |
Figure 5.
Simulation of the correlation factor. (a) Correlation in the horizontal direction for the Lena plain image; (b) correlation in the horizontal direction for the Lena cipher image.
Figure 6.
Simulation of the correlation factor. (a) Correlation in the horizontal direction for baboon plain images; (b) correlation in the horizontal direction for baboon cipher images.
5.4. Key Sensitivity Analysis
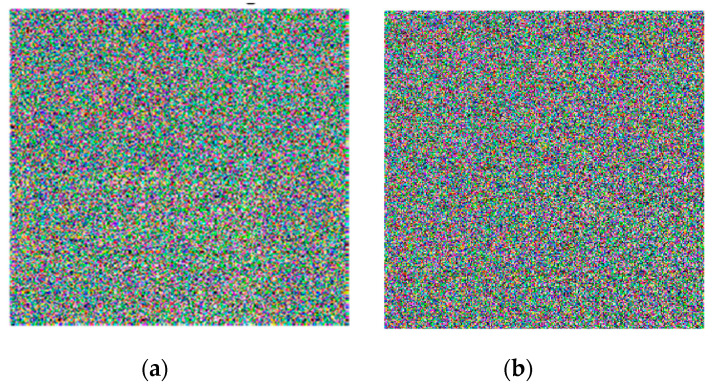
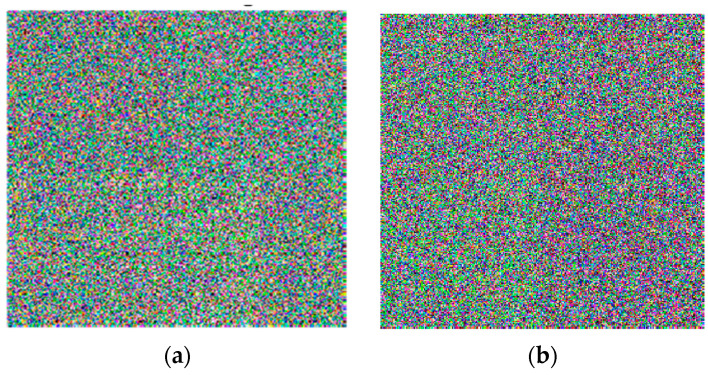
We can observe in the proposed algorithm the sensitivity of the generated secret key , and by modifying and changing one bit in it. The wrong key can be generated by changing any element of secret key by or by , or any value of and by 1. This small change leads to a totally different ciphered image. Therefore, the ciphered image will be wholly dissimilar from the original input image. In the proposed cryptosystem, we encrypted the original plain images twice to exhibit the sensitivity of the generated secret key. In the first encryption process, the plain images were encrypted with the original secret key, while in the second encryption process, the plain images were encrypted with the wrong key. The wrong key was generated from the original key. We ran the algorithm on the images of Lena and the baboon, and the effects are displayed in Figure 7 and Figure 8. As can be seen in the figures, the encrypted images with the wrong key are totally different from those encrypted with the exact key, which proves that the encryption algorithm has a high sensitivity to secret keys.
Figure 7.
Key sensitivity analysis. (a) Encrypted Lena image using the exact secret key; (b) encrypted Lena image using the wrong key.
Figure 8.
Key sensitivity analysis. (a) Encrypted baboon image using the exact secret key; (b) encrypted baboon image using the wrong key.
5.5. Differential Attack
An opponent can get valuable information by altering several pixels of the original plain image. The number of changing pixel rate (NPCR) and the unified averaged changed intensity (UACI) are usually employed to evaluate the resistance of the encrypted plain image against differential raids. We utilized the presented encryption scheme to encrypt and to obtain their corresponding encrypted images, indicated by and , with a unify secret key, where is the change in one pixel of the original plain image . Then, the NPCR and UACI could be given by
| (10) |
| (11) |
We chose randomly, changed the value of one pixel of the original input images 10 times, and calculated the NPCR and UACI of Lena and the baboon, respectively. The outputs are summarized in Table 3 and Table 4, which clarify that our new cryptosystem is very sensitive to variation arising in only one pixel value of the original image. In [36,37,38], NPCR and UACI are close to theoretical values, but they have a reduced noise attack performance. Compared with the proposed cryptosystem, it is clear that the proposed system achieves a high performance by exhibiting average performances very close to their notional amount.
Table 3.
Average performance of NPCR (number of changing pixel rate) (%).
Table 4.
Average performance of UACI (unified averaged changed intensity) (%).
5.6. Information Entropy
The information entropy, which reflects the insecurity of image data, was denoted by of matrix m, and evaluated by
| (12) |
where denotes the probability of . An accurate random image would yield 256-pixel values with an identical probability. Therefore, the theoretical value of the information entropy is closer to 8. Table 5 illustrates that the entropy values of cipher images of Lena and baboon are close to the theoretical value. Therefore, the outcomes prove that the proposed cryptosystem can efficiently counterattack the information entropy.
Table 5.
Information entropy.
5.7. Avalanche Effect
When minor variation in the plain image or the secret key occurs, it will influence variation in the ciphered image. This influence is defined as the avalanche effect. To evaluate the avalanche effect of the proposed cryptosystem, the mean square error was evaluated for the two different cipher images and obtained from a slight change in the secret keys. The MSE can be given by
| (13) |
where is the dimension of cipher images.
From Equation (13), the MSE of the proposed encryption algorithm can be evaluated for cipher images using the original secret key and cipher images obtained by changing each element in the original secret key, as cited in Table 6 and Table 7, for both the Lena and baboon images, respectively. Cipher is obtained by changing only key and maintaining the other keys’ values. Similarly, ciphers , , and are generated by changing , , and , respectively. The large values of MSE in Table 6 and Table 7 indicate that the proposed cryptosystem has a strong avalanche effect.
Table 6.
Mean square error (MSE) between cipher images of Lena.
| Images | MSE | ||||
|---|---|---|---|---|---|
| Cipher | 0.23 | 0.34 | 0.45 | 9.758 | |
| Cipher | 0.12 | 0.34 | 0.45 | 9.614 | |
| Cipher | 0.12 | 0.23 | 0.45 | 9.520 | |
| Cipher | 0.12 | 0.23 | 0.34 | 9.6729 |
Table 7.
MSE between cipher images of the baboon.
| Images | MSE | ||||
|---|---|---|---|---|---|
| Cipher | 0.23 | 0.34 | 0.45 | 10.869 | |
| Cipher | 0.12 | 0.34 | 0.45 | 10.725 | |
| Cipher | 0.12 | 0.23 | 0.45 | 10.8432 | |
| Cipher | 0.12 | 0.23 | 0.34 | 10.631 |
6. Conclusions
This article has presented a novel encryption and decryption algorithm for the purpose of verifying picture transmission over information correspondence frameworks. Both of them are indistinguishable with hybrid chaotic confusion procedures and the mtDNA diffusion process that diminish the equipment usage intricacy and improve framework security. The exhibited algorithm was shown to be powerful against chosen/known plain text attacks. The numerical investigations demonstrated that the proposed cryptosystem has a very large key space for opposing brute-force attacks and scrambled pixels appropriated haphazardly through the figured picture. Likewise, the proposed framework is sensitive to insignificant changes in the covert encryption key and can oppose the known plaintext, chosen plaintext, differential figure picture, and entropy attacks.
Finally, in terms of future research, we suggest additional simulation analysis of the chaotic performance by using a cosine chaotic model and another confusion technique to generate a robust chaotic image encryption technique with the addition of digital signature technology, for the sake of achieving more secure authenticated data transmission.
Acknowledgments
This research was funded by the Deanship of Scientific Research at Princess Nourah Bint Abdulrahman University through the Fast-Track Research Funding Program.
Author Contributions
Conceptualization, H.G.M. and K.H.M.; Methodology, D.H.E.; Software, K.H.M.; Validation, H.G.M., D.H.E. and K.H.M.; Formal Analysis, H.G.M.; Investigation, D.H.E.; Resources, K.H.M.; Data Curation, H.G.M.; Writing-Original Draft Preparation, H.G.M.; Writing-Review & Editing, D.H.E.; Visualization, D.H.E.; Supervision, K.H.M.; Project Administration, H.G.M. All authors have read and agreed to the published version of the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Liu Z., Guo Q., Xu L., Ahmad M.A., Liu S. Double image encryption by using iterative random binary encoding in gyrator domains. Opt. Express. 2010;18 doi: 10.1364/OE.18.012033. [DOI] [PubMed] [Google Scholar]
- 2.Wang X., Zhang H.-L. A novel image encryption algorithm based on genetic recombination and hyper-chaotic systems. Nonlinear Dyn. 2016;83:333–346. doi: 10.1007/s11071-015-2330-8. [DOI] [Google Scholar]
- 3.Ahmad J., Hwang S.O. A secure image encryption scheme based on chaotic maps and affine transformation. Multimed. Tools Appl. 2016;75:13951–13976. doi: 10.1007/s11042-015-2973-y. [DOI] [Google Scholar]
- 4.Ahmad J., Khan M.A., Hwang S.O., Khan J.S. A compression sensing and noise-tolerant image encryption scheme based on chaotic maps and orthogonal matrices. Neural Comput. Appl. 2017;28:953–967. doi: 10.1007/s00521-016-2405-6. [DOI] [Google Scholar]
- 5.Wang X.-Y., Zhang Y.-Q. Analysis and improvement of a chaos-based symmetric image encryption scheme using a bit-level permutation. Nonlinear Dyn. 2014;77:687–698. [Google Scholar]
- 6.Guo J.-S., Jin C.-H. An attack with known image to an image cryptosystem based on general cat map. J. China Inst. Commun. 2005;26:131–135. [Google Scholar]
- 7.Jolfaei A., Wu X.-W., Muthukkumarasamy V. On the security of permutation-only image encryption schemes. IEEE Trans. Inf. Forensics Secur. 2015;11:235–246. doi: 10.1109/TIFS.2015.2489178. [DOI] [Google Scholar]
- 8.Wang X., Zhu X., Zhang Y. An image encryption algorithm based on Josephus traversing and mixed chaotic map. IEEE Access. 2018;6:23733–23746. doi: 10.1109/ACCESS.2018.2805847. [DOI] [Google Scholar]
- 9.Askar S., Karawia A., Alshamrani A. Image encryption algorithm based on chaotic economic model. Math. Prob. Eng. 2015;2015:341729. doi: 10.1155/2015/341729. [DOI] [Google Scholar]
- 10.Abbas N.A. Image encryption based on independent component analysis and arnold’s cat map. Egypt. Inform. J. 2016;17:139–146. doi: 10.1016/j.eij.2015.10.001. [DOI] [Google Scholar]
- 11.Shaikh N., Chapaneri S., Jayaswal D. Hyper chaotic color image cryptosystem; Proceedings of the 2016 IEEE International Conference on Advances in Computer Applications (ICACA); Coimbatore, India. 24–24 October 2016. [Google Scholar]
- 12.Li C., Zhao F., Liu C., Lei L., Zhang J. A Hyperchaotic Color Image Encryption Algorithm and Security Analysis. Secur. Commun. Netw. 2019;2019:8132547. doi: 10.1155/2019/8132547. [DOI] [Google Scholar]
- 13.Ramasamy P., Ranganathan V., Kadry S., Damaševičius R., Blažauskas T. An image encryption scheme based on block scrambling, modified zigzag transformation and key generation using enhanced logistic—Tent map. Entropy. 2019;21:656. doi: 10.3390/e21070656. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Watson J.D., Crick F.H. Molecular structure of nucleic acids. Nature. 1953;171:737–738. doi: 10.1038/171737a0. [DOI] [PubMed] [Google Scholar]
- 15.Ning K. A pseudo DNA cryptography method. arXiv. 20090903.2693 [Google Scholar]
- 16.Zhang Q., Guo L., Wei X. Image encryption using DNA addition combining with chaotic maps. Math. Comput. Modell. 2010;52:2028–2035. doi: 10.1016/j.mcm.2010.06.005. [DOI] [Google Scholar]
- 17.Liu H., Wang X. Image encryption using DNA complementary rule and chaotic maps. Appl. Soft Comput. 2012;12:1457–1466. doi: 10.1016/j.asoc.2012.01.016. [DOI] [Google Scholar]
- 18.Wei X., Guo L., Zhang Q., Zhang J., Lian S. A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J. Syst. Softw. 2012;85:290–299. doi: 10.1016/j.jss.2011.08.017. [DOI] [Google Scholar]
- 19.Zhang Q., Guo L., Wei X. A novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Opt. -Int. J. Light Electron Opt. 2013;124:3596–3600. doi: 10.1016/j.ijleo.2012.11.018. [DOI] [Google Scholar]
- 20.Huang X., Ye G. An image encryption algorithm based on hyper-chaos and DNA sequence. Multimed. Tools Appl. 2014;72:57–70. doi: 10.1007/s11042-012-1331-6. [DOI] [Google Scholar]
- 21.Ur Rehman A., Liao X., Kulsoom A., Abbas S.A. Selective encryption for gray images based on chaos and DNA complementary rules. Multimed. Tools Appl. 2015;74:4655–4677. doi: 10.1007/s11042-013-1828-7. [DOI] [Google Scholar]
- 22.Zhan K., Wei D., Shi J., Yu J. Cross-utilizing hyperchaotic and DNA sequences for image encryption. J. Electron. Imaging. 2017;26:013021. doi: 10.1117/1.JEI.26.1.013021. [DOI] [Google Scholar]
- 23.Kulsoom A., Xiao D., Abbas S.A. An efficient and noise resistive selective image encryption scheme for gray images based on chaotic maps and DNA complementary rules. Multimed. Tools Appl. 2016;75:1–23. doi: 10.1007/s11042-014-2221-x. [DOI] [Google Scholar]
- 24.Ran W., Wei P., Duan A. Image encryption algorithm based on multi-chaotic mapping and DNA coding. Comput. Eng. Des. 2018;7 [Google Scholar]
- 25.Wu J., Shi J., Li T. A novel image encryption approach based on a hyperchaotic system, pixel-level filtering with variable kernels, and DNA-level diffusion. Entropy. 2020;22:5. doi: 10.3390/e22010005. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Sykes B (10 September 2003) “Mitochondrial DNA and Human History”. The Human Genome. Well Come Trust. [(accessed on 7 September 2015)]; Available online: http://genome.wellcome.ac.uk/doc_WTD020876.html.
- 27.Johnston I.G., Williams B.P. Evolutionary inference across eukaryotes identifies specific pressures favoring mitochondrial gene retention. Cell Syst. 2016;2:101–111. doi: 10.1016/j.cels.2016.01.013. [DOI] [PubMed] [Google Scholar]
- 28.Anderson S., Bankier A.T., Barrell B.G., de Bruijn M.H., Coulson A.R., Drouin J., Eperon I.C., Nierlich D.P., Roe B.A., Sanger F. Sequence and organization of the human mitochondrial genome. Nature. 1981;290:457–465. doi: 10.1038/290457a0. [DOI] [PubMed] [Google Scholar]
- 29.Delsuc F., Stanhope M.J., Douzery E.J. Molecular systematics of armadillos (Xenarthra, Dasypodidae): Contribution of maximum likelihood and Bayesian analyses of mitochondrial and nuclear genes. Mol. Phylogenet. Evol. 2003;28:261–275. doi: 10.1016/S1055-7903(03)00111-8. [DOI] [PubMed] [Google Scholar]
- 30.Hassanin A., An J., Ropiquet A., Nguyen T.T., Couloux A. Combining multiple autosomal introns for studying shallow phylogeny and taxonomy of Laurasiatherian mammals: Application to the tribe Bovini (Cetartiodactyla, Bovidae) Mol. Phylogenet. Evol. 2013;66:766–775. doi: 10.1016/j.ympev.2012.11.003. [DOI] [PubMed] [Google Scholar]
- 31.Li C.-L., Yu S.-M. A new hyperchaotic system and its adaptive tracking control. Acta Phys. Sin. 2012;61:22–28. [Google Scholar]
- 32.Haskett D.R. Mitochondrial DNA (mtDNA). Embryo Project Encyclopedia (2014-12-19) [(accessed on 28 January 2020)]; Available online: http://embryo.asu.edu/handle/10776/8269.
- 33.Wang Q., Zhang Q., Zhou C. A multilevel image encryption algorithm based on chaos and DNA coding; Proceedings of the 2009 Fourth International on Conference on Bio-Inspired Computing (BICTA’ 09); Beijing, China. 16–19 October 2009; pp. 70–74. [Google Scholar]
- 34.Sebastian A., Delson T. Secure magnetic resonance image transmission and tumor detection techniques; Proceedings of the 2016 International Conference on Circuit, Power and Computing Technologies (ICCPCT); Nagercoil, India. 18–19 March 2016. [Google Scholar]
- 35.Enayatifar R., Abdullah A.H., Isnin I.F. Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Opt. Lasers Eng. 2014;56:83–93. doi: 10.1016/j.optlaseng.2013.12.003. [DOI] [Google Scholar]
- 36.Chai X., Fu X., Gan Z., Lu Y., Chen Y. A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process. 2019;155:44–62. doi: 10.1016/j.sigpro.2018.09.029. [DOI] [Google Scholar]
- 37.Ur Rehman A., Liao X., Ashraf R., Ullah S., Wang H. A color image encryption technique using exclusive-OR with DNA complementary rules based on chaos theory and SHA-2. Optik. 2018;159:348–367. doi: 10.1016/j.ijleo.2018.01.064. [DOI] [Google Scholar]
- 38.Wu X., Wang K., Wang X., Kan H., Kurths J. Color image DNA encryption using NCA map-based CML and one-time keys. Signal Process. 2018;148:272–287. doi: 10.1016/j.sigpro.2018.02.028. [DOI] [Google Scholar]