Abstract
Australian My Health Record (MyHR) is a significant development in empowering patients, allowing them to access their summarised health information themselves and to share the information with all health care providers involved in their care. Consequently, the MyHR system must enable efficient availability of meaningful, accurate, and complete data to assist an improved clinical administration of a patient. However, while enabling this, protecting data privacy and ensuring security in the MyHR system has become a major concern because of its consequences in promoting high standards of patient care. In this paper, we review and address the impact of data security and privacy on the use of the MyHR system and its associated issues. We determine and analyse where privacy becomes an issue of using the MyHR system. Finally, we also present an appropriate method to protect the security and privacy of the MyHR system in Australia.
Keywords: Data security, Health care, EHR, EMR, PCEHR, MyHR
Introduction
The Australian government announced that the MyHR system would transition to opt-out participation. This means that Australians have been given 195 days period to opt-out of having a MyHR created for them if they do not want one. As a result of this, the end of the opt-out period, the participation rate was 90.1%, with the national opt-out rate of 9.9%. In other words, 9 out of 10 Australians currently have a My Health Record. This is a significant milestone in the Personally Controlled Electronic Health Record (PCEHR)/MyHR implementation in Australia. While the majority of Australians have MyHR, 9.9% which is around 2.5 million people have opted out of MyHR. This raises a number of serious questions around the system. The major concern of the system is privacy and security concerns. Privacy advocates say that, even with the safeguards, the system takes too much information, stores it too simply, and shares it too freely [1]. Better sharing of health data among health care professionals is a good aspect of the system as long as it is done in a controlled manner. Therefore, the question currently remains is, do the MyHR shares the required health information in a controlled manner?
Furthermore, access control of the MyHR has an issue. Every health care provider group should have different access permission or view to protecting the privacy of the system. If a patient has a mental health issue, the patient does not want that shared with a dentist or someone who looks at your feet. If someone has a medical condition that might result in discrimination—specifically HIV or mental health problems, then they do not want their data shared. For example, there are vulnerable communities, the gay community, the HIV community, mental health sufferers, and who feel at risk. Therefore, the proposer access control mechanism must be in place to protect privacy around the system. However, health care organisations are inherently complex and dynamic environments [2, 3], which makes it difficult for administrators to define access control policies [4–6]. MyHR user privileges are therefore often defined at a coarse level to minimize workflow inefficiencies and maximize flexibility in the management of a patient. The consequence of such decisions is that MyHR systems are left vulnerable to misuse and, potentially, abuse, from insiders (authenticated health care provider organisation staff or medical research staff), which ultimately can compromise patient confidentiality. Actual threats that are aimed at a MyHR can be divided into outside threats (i.e. attackers with no access rights) and inside threats (i.e. personnel that misuses access rights). Attackers can be defended against using techniques such as strong authentication methods, access policies, and secure storage [7–9]. Backing up MyHR files into a distributed storage, i.e. cloud storage can improve the accessibility of a document, but this approach is also prone to security threats [10–12].
In some cases, inside threats can be easy to discover, for example using log files that monitor file access. Still, preventing users from accessing files that they have no professional rights to access is difficult. Moreover, many of the popular Electronic Health Record (EHR) systems that were presented are patient-centric, which means that the patient themselves can hand out access rights [13, 14]. This is a tremendous responsibility for the user, who is not always aware of the risks involved when allowing third-party access to the information in EHR.
The use of such EHR systems can be compared to how social networks are used. The same threats that are aimed at social network users can be transferred to the EHR systems. The use of data mining techniques on anonymous data can reveal personal sensitive information. Third-party services that are affiliated with the upholder of the system may be allowed to access data from EHRs. Data can be collected from several sources and combined with a profile. Users can share data with malevolent strangers, either unknowingly or through a scam. These threats can be fought against for example with anonymisation of data and by educating users to recognise risks [15–17].
Motivation
Electronic system usage growth in the last 25 years has been very significant, in particular, the health care industry. Increasing the use of computer systems, existing faster Internet services, efficient storage and retrieval data using the Cloud, reliability of network systems, and effectiveness of distributed systems contribute to easy access to health information when and where it needed [6, 18]. With the support of these modern technology developments, the EHR systems have been developed. Even though the complete benefits of those systems have not been realised yet, there have been several progressions that are existing in the system. Electronic usage in health care impacts the effectiveness and excellence of health care services. All the involved parties in the health care delivery including the patients, health care provider, and health care provider organisation are benefitted by the use of eHealth. Even though all groups of health care providers receive the eHealth benefits, the primary care service settings are in particular. For this reason, the Australian Government firstly targets the GP practices’ MyHR to ensure the success of the system as the majority of the health information is stored in general practice systems in Australia.
With the continued advancement of any EHR systems, on the other hand, there are increasing concerns about security and privacy of the system. These concerns impact the implementation of such systems. In addition, the security and privacy issues question the data integrity in the system. The data integrity, ultimately, compromised patient care, care coordination, and quality reporting, and research as well as fraud and abuse. Inaccurate health information may adversely affect the quality of an individual’s healthcare. Maintaining the integrity and completeness of health data is paramount because the computerisation of health information grows and the scope of organisational exchange of health information widens into Health Information Exchanges (HIEs) [19, 20].
It is obvious that the patients trust the health care providers; however, if they come to know that their health care provider organisation does not take adequate steps to protect their sensitive health information, they will leave from the organisation. This action will affect the organisation business and reputation negatively. A patients survey conducted by the New England Consultancy [21] shows that about half of the population in Australia do have serious concern over the privacy of their health information in Australia. To understand the importance and degree of patients’ concerns of privacy, confidentiality, and security impact the health outcome in Australian communities, further research and discussion are required.
Our contribution
In this paper, we review the literature and previous related work of the data privacy and security of the MyHR system in “Related work” section. In “Privacy and security concerns of the My Health Record” section, we determine and analyse the privacy and security concerns of the MyHR system and examine the impact of those concerns in using the system. We propose an appropriate method to improve accessibility while preserving the data privacy and security of the system in “Proposed model” section and finally “Conclusions and future work” section concludes and suggests future research opportunities.
Related work
Healthcare data is a very attractive target for cybercrimes. The data in health records not only includes most valuable details such as birthdates, addresses, clinical-related information, and next of kin but also they are more permanent and not replaceable. Therefore, the impact of these stolen data can be exploited over a long period of time.
This nature of the data makes privacy and security particularly challenging issues for many healthcare organisations [20, 22]. Hence, the majority of the healthcare organisations (76%) had experienced a “significant security incident” over the previous 12 months in 2018 [23]. In 2013, the majority of data breaches affected 43.8% of healthcare organisations compared to 34% of the business sector [24]. Therefore, the need for protecting such healthcare sensitive data in databases or systems become imperative.
In healthcare settings, EHRs have become a powerful tool in modern health care delivery. While EHR systems replace paper-based medical records electronically, they also facilitate faster access the health information to relevant health care providers. EHRs have greatly improved the safety and quality of health care delivery by increasing access to health information, reducing illegibility, and enabling closer overseeing of clinical care processes [25, 26]. This ability of the EHR includes My Health Record (MyHR) put such systems even more vulnerable, to make the security concerns worse. In this study, we develop a security model that will be used to enhance the security of the Australian’s MyHR in healthcare settings.
While investigating the current settings of privacy, security, and accountability of using any EHR systems including MyHR, it is prominent that insider attacks and lack of access control mechanisms have largely contributed to security threats in EHR systems [18, 27, 28]. In another study of establishing the challenges for protecting the privacy and security of EHR, [29] realised that 90% of attackers were insider attacks with high-level administrative rights while 81% of attacks involved incidences of losses. Threats to the security of EHR can be classified into organisational and systemic threats [30, 31] and the majority of the internal attacks are also identified at the organisational level. These threats arise from inappropriate access to patients’ data by either internal agents while systemic threats arise from agents in the information flow chain exploiting the disclosed data beyond its intended use [32, 33].
MyHR is relatively a new initiative in Australia and for this reason, lack of health data security awareness, legislation, policies, and procedures and technical related issues are also contributing to these insider attacks to the system. In other words, proper administrative controls such as written policies, procedures, standards, and guidelines need to be developed and available for users within and outside the healthcare organisations [34, 35]. These administrative controls inform users on how the business is to be run and how day to day operations are to be conducted when using the MyHR system. In addition to these administrative controls, technical controls include passwords, firewalls, access control lists, and data encryption that must be in place to protect any EHR systems. The technical controls also can be categorised into support, prevent, detect, and recover [36].
In healthcare settings also, physical control takes a major part in protecting health-related information. The physical controls assist to monitor and control the environment of the healthcare organisations and associated computing facilities and they also monitor and control access to and from such facilities.
Privacy and security concerns of the My Health Record
The MyHR system is developed to improve the health care outcome to reduce the cost in the long term perspective in Australia. While the system has backed up with clear benefits, the implementation process of the initiative faces many challenges [37, 38].
Increasing concerns of privacy, security, and confidentiality of sharing sensitive health data over the Internet and storing it in the Cloud is on top of them. With the continued advancement of EHR systems and the introduction of MyHR in Australia, there is increasing concerns of privacy and security of sharing health data over the network and storing sensitive data in the Clouds [39].
When introducing a new system to the public, people should have a better understanding of the system. The first impression is the best, clearer understanding will assist people in their decision making positively. A lack of understanding of a public system cannot be popular in the community who eventually need to use it. Also, the public should know (once the patients’ sensitive health information is stored in the Cloud with the MyHRs), who else can access it other than the patient’s usual health care provider.
In the MyHR current settings, within a health care provider organisation level, a patient’s shared health summary and event summary that was uploaded by the usual health care provider to the MyHR can be accessed by all the health care providers in that organisation. In some other circumstances, these health records are accessible to the reception and administration staff of an organisation. This issue should be managed with access control policies within the clinical system of a health care provider organisation. However, because of the nature of the health care organisations and its complexity and dynamic environments [40, 41], the system administrators are finding difficulties in assigning these consistent access control policies. The MyHR user privileges are, therefore, often defined at a coarse level to minimise workflow inefficiencies and maximise flexibility in the management of a patient [42, 43]. These practices, eventually, result in the MyHR being left more vulnerable to any possible misuse from unauthorised access and intentional leakage of sensitive health information by insiders within the health care organisation.
Additionally, the system administrators and technical staff of the system who maintain the MyHR system and deal with patients’ sensitive information databases can leak that information and put the organisation at risk. This risk of leaking sensitive information impacts negatively for the whole organisation and its business reputation. Usually, the staff members who deal with high-sensitive information do have a privacy and confidentiality agreement with the organisation. However, having these agreements does not completely prevent these leakages from occurring, but they reduce the risk based on the employee’s professional integrity. This scenario indicates the level of risk of disclosure that the health information in the MyHR systems faces. The research, therefore, must investigate and address these possibilities of internal abuse to prevent unauthorised access and preserve the privacy and security of the MyHR system. Understanding and addressing these concerns that are associated with the use of MyHR eventually increase the uptake and usability of the system.
Moreover, the recent MyHR opt-out arrangement has created some more issues. While the global best practice or Australian federal privacy regulations recommend the necessity of consent for the use of patients’ sensitive health information, the Australian MyHR opt-out scheme has disregarded all of these globally accepted best practices. There is an argument that part of the population was not aware of the introduction of the opt-out scheme. The people firstly should know about the MyHR and the opt-out announcement to seek more information about the system to decide whether they go for opt-out or just simply leave it for opt-in. The reality was the majority of the population does not bother or make an effort to follow the instruction to opt-out from the MyHR system, particularly the aged population. The MyHR system and its opt-out initiatives, therefore, will have a national advertisement to bring to the attention of the population in the first place. This approach would have assisted people with an informed choice about the system, making decisions on the opt-out method by explaining the benefits of the system. The additional information that the government provides to the public must include both the benefits and the drawbacks, especially privacy and security concerns. This impartial attitude assists ordinary people in their decisions making and gives a clear understanding of the system. This understanding may work either positively or negatively because while the system shows its benefits, it clarifies the substantial risks in keeping their sensitive health information within MyHR. Subsequently, the public who have concerns including privacy and security of their health information will need to take additional steps to remove themselves from the MyHR system [44, 45] in the opt-out scheme.
One of the other major concerns in addition to the privacy and security of the system is the data integrity of the system. With the introduction and continued implementation of the MyHR, the importance of data integrity has become indispensable. When it is sharing health information that assists health care providers in delivering better health care and to support the right decisions at the point of care, the information shared through the MyHR must be up-to-date and accurate. The MyHR is a summary of a patient’s health information drawn from the clinical systems (that is known as EMR) that the health care provider uses in their organisation. Garbage in, garbage out—the information provided into an EMR must be supplied for any EHR system and the MyHR has no exception to this. Hence, the quality, correctness, and contemporary of the data in the local electronic systems are crucial. The data integrity concerns, including loss of data, erroneousness, and invalid information of the MyHR, could impact patients care and the care-coordination negatively. Eventually, in worse scenarios, these issues may put the patients’ lives at risk. If the MyHR data is worthless, then the outcome of any reports and researches that have drawn based on the system is also useless. The term data integrity covers a wide range of aspects. It encompasses information governance, patient identification, authorship validation, amendments, and record corrections as well as auditing the record [46]. It, therefore, not only outlines the data contained within the MyHR itself but also includes the security measures or controls in place. Poor security controls may also influence data integrity in MyHR systems destructively [47]. In other words, the higher security mechanisms and control put in place for the MyHR system will ensure data integrity within the system. The absence of the safeguards for health records could reflect an inaccurate picture of the patient’s health information and this will be less trustworthy for health care providers.
Proposed model
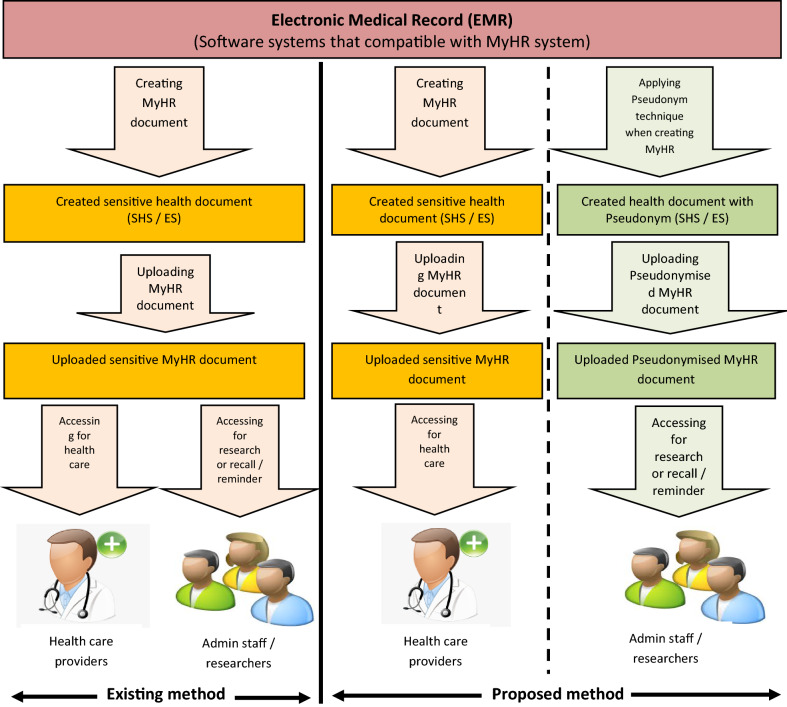
Figure 1 visibly illustrates how the proposed model works in health care provider settings when using the MyHR. The followings are also shown in Fig. 1:
In the existing method, how clinical documents are being uploaded to MyHR and who can access them.
Using the proposed method, how it is going to vary in improving accessibility while preserving privacy and security.
The difference between both under the existing method and the proposed method.
Fig. 1.
The proposed model
With the current settings, even though, a health care provider including doctors and nurses uploads a health document including Shared Health Summary (SHS) or Event Summary (ES) to the MyHR using a compatible Electronic Medical Record (EMR) system such as Medical Director or Best Practice, other employees (e.g. medical admin and reception staff) in a medical practice can access those documents once they uploaded. However, in the proposed model, non-clinical staff cannot access the sensitive clinical details of the record and they have a specific different view of the system with sensitive details pseudonymised for them to satisfy their job requirements.
In the proposed model, privacy and security are being established using the pseudonymisation technique. When using access control and Cryptography (data encryption and decryption techniques) security measures, it was obvious that they will not meet the purpose of securing data in the area of Business Intelligence (BI) because they only permit “all or nothing” access. Generally, in many health care organisations, employees are given access to sensitive information to perform the day to day work such as identifying patients for a health check, processing documents, analysing trends or even testing and maintaining eHealth systems. An employee accessing the sensitive data during routine work is the main reason for putting the privacy and security in high risk where sensitive data can be abused internally. However, the employees could perform their routine works just as effectively with de-sensitised data where the critical sensitive data are some or other blinded.
This led to the thought for developing a security model that permits health care employees to access the required data for routine work but prevents them from viewing the sensitive data linked to these records. This security model will allow the employees to access the data for routine work such as identifying patients for any reason including targeting chronic disease or a health check, processing documents, analysing trends, and testing and maintaining eHealth systems without any need for them to view any sensitive data. Using the pseudonymisation technique patients’ personally identifiable fields including name and health care identifiers within a health data record are replaced by one or more artificial (meaningless) identifiers which are called pseudonym as shown in Table 1.
Table 1.
Original dataset
| Healthcare identifier | Medication | Date | Condition | Full name |
|---|---|---|---|---|
| 8001567898761234 | Insulin | 01–10–2014 | CD | John Smith |
| 8008123456785000 | Dapotum | 05–10–2014 | MH | Jane Doe |
| 8001567898761234 | Thalitone | 10–10–2014 | CKD | John Smith |
The meaningful patients’ sensitive details such as healthcare identifiers and full names are being replaced by pseudonyms to make the patent health record meaningless. Therefore, the accessible data will be the following in Table 2:
Table 2.
Pseudonymised dataset
| Healthcare identifier | Medication | Date | Condition | Full name |
|---|---|---|---|---|
| 01024 | Insulin | 01–10–2014 | CD | 12563 |
| 45237 | Dapotum | 05–10–2014 | MH | 02943 |
| 27128 | Thalitone | 10–10–2014 | CKD | 17906 |
The hidden connective index data is stored in a secure destination or another PC where ordinary (or basic) users cannot access it. Table 3 shows the connective index for the healthcare identifier and Table 4 for patients’ full name.
Table 3.
Connective index data for healthcare identifier
| Healthcare identifier | Healthcare identifier pseudonym |
|---|---|
| Pseudonym | |
| 8001567898761234 | 01025 |
| 8008123456785000 | 14527 |
| 8001567898761234 | 27122 |
Table 4.
Connective index data for full name
| Full name | Full name pseudonym |
|---|---|
| John Smith | 12336 |
| Jane Doe | 02762 |
| John Smith | 17934 |
Adopting a pseudonym technique for health records will preserve privacy. In the pseudonymisation model, while the sensitive health data is protected, the users of the system are allowed to access to insensitive or less sensitive elements in the records. This method manages sensitive data by replacing critical data components with a code or notifications that are known as pseudonyms. The uses that access the information cannot view the data itself because it has no direct accessibility for them, only the certain components of the information related to a request are returned to the user. The consequence of the pseudonymisation method is that while the users can still pursuit data for its relationships, the users cannot identify all the value of the data. Therefore, this technique ensures the users that external to the actual context of the services cannot view and/ or alter the data in an unauthorized manner. Also, simply copying pseudonymised data is similarly useless as the keys linking the useful relations among the available pseudonym and the real data itself are stored in another place away from this location. Thus, with this technique, the sensitive data is concealed and the relationships between the data are visible. Two key requirements that exist with this technique are;
The data patterns are retained for relationships and analysis
Sensitive data that is shared, either internally or externally with a partner, is concealed during the access.
The health software system integrators, developers, systems administrators, and researchers can use de-identified data for estimating eHealth projects that work with health sensitive data, designing and testing new systems that source health sensitive data from existing operations and maintaining eHealth systems that manipulate sensitive data. The health care identifiers and other health-related number systems including Medicare effectively become sensitive through their long term usage. An effective pseudonymisation solution can assign and maintain new pseudonyms for these sensitive identifiers as illustrated in Tables 1 and 2.
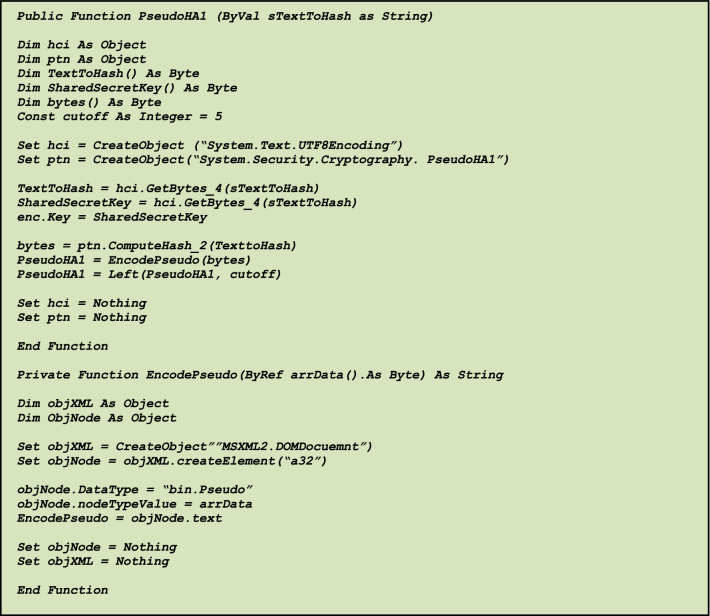
The following hash function, for example, simply explains how real data can be replaced by numbers or codes in Fig. 2. In this example, object 1 is the healthcare identifier (hci) and object 2 is the patient’s name (ptn).
Fig. 2.
Sample code for the technique
Conclusions and future work
Accessibility is the key to any EHR system including MyHR. However, to preserve the privacy and security of the system, the application of appropriate security controls are required. These security controls directly impact the accessibility of the system. Therefore, the right balance of security controls and accessibility is very important to ensure the usage of the MyHR system.
In this proposed model, the pseudonymisation technique is proposed to preserve data security and improve accessibility in the MyHR system in Australia. With the introduction of pseudonymisation for sensitive health information in the MyHR system, indirect identifiable personal data is long-standing privacy to reduce the risks of identifiability. Therefore, this method will preserve privacy and security while sharing sensitive data within and/or outside of a health care provider organisation. This concept offers a role-based view according to the staff members’ job requirements as well.
Contributor Information
Pasupathy Vimalachandran, Email: Pasupathy.Vimalachandran@live.vu.edu.au.
Hong Liu, Email: lhsdcn@126.com.
Yongzheng Lin, Email: ise_linyz@ujn.edu.cn.
Ke Ji, Email: ise_jik@ujn.edu.cn.
Hua Wang, Email: hua.wang@vu.edu.au.
Yanchun Zhang, Email: yanchun.zhang@vu.edu.au.
References
- 1.Zhou N. My Health Record: privacy, cybersecurity and the hacking risk. The Guardian. 2018. https://www.theguardian.com/australia-news/2018/jul/16/my-health-record-privacy-cybersecurity-and-the-hacking-risk. Accessed 12 May 2019.
- 2.Bosch M, et al. Review article: Effectiveness of patient care teams and the role of clinical expertise and coordination: a literature review. Med Care Res Rev. 2009;66(6 Suppl.):5S–35S. doi: 10.1177/1077558709343295. [DOI] [PubMed] [Google Scholar]
- 3.Kannampallil TG, et al. Considering complexity in healthcare systems. J Biomed Inform. 2011;44(6):943–947. doi: 10.1016/j.jbi.2011.06.006. [DOI] [PubMed] [Google Scholar]
- 4.Malin B, Nyemba S, Paulett J. Learning relational policies from electronic health record access logs. J Biomed Inform. 2011;44(2):333–342. doi: 10.1016/j.jbi.2011.01.007. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Wang H, Sun L, Bertino E. Building access control policy model for privacy preserving and testing policy conflicting problems. J Comput Syst Sci. 2014;80(8):1493–1503. doi: 10.1016/j.jcss.2014.04.017. [DOI] [Google Scholar]
- 6.Cheng K, et al. Secure k-nn query on encrypted cloud data with multiple keys. IEEE Trans Big Data. 2017 doi: 10.1109/TBDATA.2017.2707552. [DOI] [Google Scholar]
- 7.Lohr H, Sadeghi A-R, Winandy M. Securing the e-health cloud. In: Proceedings of the 1st ACM international health informatics symposium, IHI’10. New York: ACM. 2010. p. 220–9. 10.1145/1882992.1883024.
- 8.Ma J, et al. Supervised anomaly detection in uncertain pseudoperiodic data streams. ACM Trans Internet Technol (TOIT) 2016;16(1):1–20. doi: 10.1145/2806890. [DOI] [Google Scholar]
- 9.Zhang J, et al. On efficient and robust anonymization for privacy protection on massive streaming categorical information. IEEE Trans Depend Secure Comput. 2015;14(5):507–520. doi: 10.1109/TDSC.2015.2483503. [DOI] [Google Scholar]
- 10.Yu W, Chekhanovskiy M. An electronic health record content protection system using smartcard and PMR. In: 2007 9th international conference on e-Health networking, application and services. 2007. p. 11–18.
- 11.Zhang F, et al. Decision-based evasion attacks on tree ensemble classifiers. World Wide Web. 2020;23(5):2957–2977. doi: 10.1007/s11280-020-00813-y. [DOI] [Google Scholar]
- 12.Rasool RU, et al. Cyberpulse: a machine learning based link flooding attack mitigation system for software defined networks. IEEE Access. 2019;7:34885–34899. doi: 10.1109/ACCESS.2019.2904236. [DOI] [Google Scholar]
- 13.Hu H, et al. Combined gene selection methods for microarray data analysis. In: International conference on knowledge-based and intelligent information and engineering systems. 2006. p. 976–83.
- 14.Kabir M, Wang H. Conditional purpose based access control model for privacy protection. In: Proceedings of the 12th Australasian conference on Australasian Database, vol. 92. 2009. p. 135–142.
- 15.Williams J. Social networking applications in health care: threats to the privacy and security of health information. In: Proceedings of the 2010 ICSE workshop on software engineering in health care. 2010. p. 39–49. 10.1145/1809085.1809091.
- 16.Sun X, et al. Injecting purpose and trust into data anonymization. Comput Security. 2011;30(5):332–345. doi: 10.1016/j.cose.2011.05.005. [DOI] [Google Scholar]
- 17.Khalil F, Wang H, Li J. Integrating markov model with clustering for predicting web page accesses. In: Proceeding of the 13th Australasian world wide web conference. 2007. p. 63–74.
- 18.Wang H, Yi X, Bertino E, Sun L. Protecting outsourced data in cloud computing through access management. Concurr Comput Pract Experience. 2016;28(3):600–615. doi: 10.1002/cpe.3286. [DOI] [Google Scholar]
- 19.Vimalachandran P, et al. The Australian PCEHR System: ensuring privacy and security through an improved access control mechanism. EAI Endorsed Trans Scalable Inf Syst. 2016;3(8):e4. [Google Scholar]
- 20.Li M, Sun X, Wang H, Zhang Y, Zhang J. Privacy-aware access control with trust management in web service. World Wide Web. 2011;14(4):407–430. doi: 10.1007/s11280-011-0114-8. [DOI] [Google Scholar]
- 21.New London Consulting. Australia: how privacy considerations drive patient decisions and impact patient care outcomes. Fair Warning. Australian Patient Survey. 2012.
- 22.Zhang J, Tao X, Wang H. Outlier detection from large distributed databases. World Wide Web. 2014;17(4):539–568. doi: 10.1007/s11280-013-0218-4. [DOI] [Google Scholar]
- 23.Ahmet EFE, Calik E. Holistic security architecture for effective management of healthcare cyber threats. Int J Health Manag Strateg Res. 2018;4(2):150–167. [Google Scholar]
- 24.Hartwig RP. Cyber risks: the growing threat. Glob Risks. 2014;9:5–14. [Google Scholar]
- 25.Wang H, Zhang Z, Taleb T. Special issue on security and privacy of IoT. World Wide Web. 2018;21(1):1–6. doi: 10.1007/s11280-017-0490-9. [DOI] [Google Scholar]
- 26.Peng M, et al. Personalized app recommendation based on app permissions. World Wide Web. 2018;21(1):89–104. doi: 10.1007/s11280-017-0456-y. [DOI] [Google Scholar]
- 27.Omotosho A, Emuoyibofarhe J. A criticism of the current security, privacy and accountability issues in electronic health records. IJAIS. 2014;7(8):11–18. doi: 10.5120/ijais14-451225. [DOI] [Google Scholar]
- 28.Sun X, Wang H, Li J, Pei J. Publishing anonymous survey rating data. Data Min Knowl Discov. 2011;23(3):379–406. doi: 10.1007/s10618-010-0208-4. [DOI] [Google Scholar]
- 29.Sellars C, Easey DA. Electronic health records: data protection issues in Europe. BNA International, BNA‘s World Data Protection Report, April 2008.
- 30.Appari A, Johnson M. Information security and privacy in healthcare: current state of research. Int J Internet Enterprise Manag. 2010;6(4):279. doi: 10.1504/IJIEM.2010.035624. [DOI] [Google Scholar]
- 31.Yi X, Zhang Y. Privacy-preserving distributed association rule mining via semi-trusted mixer. Data Knowl Eng. 2007;63(2):550–567. doi: 10.1016/j.datak.2007.04.001. [DOI] [Google Scholar]
- 32.Åhlfeldt RM, Söderström E. Patient safety and patient privacy in information security from the patient’s view: a case study19. Inf Security Distrib Healthc. 2010;6(4):71–85. [Google Scholar]
- 33.Shen Y, et al. Microthings: a generic IoT architecture for flexible data aggregation and scalable service cooperation. IEEE Commun Mag. 2017;55(9):86–93. doi: 10.1109/MCOM.2017.1700104. [DOI] [Google Scholar]
- 34.Salkind NJ, Kristin R. Encyclopedia of measurement and statistics. 1. Thousand Oaks, CA: SAGE; 2007. p. 5. [Google Scholar]
- 35.Sun X, et al. An efficient hash-based algorithm for minimal k-anonymity. In: Proceedings of the 31st Australasian conference on Computer science, vol. 74 (ACSC ‘08). 2008. p. 101–107.
- 36.National Institute of Standards and Technology. Performance measurement guide for information security. NIST Special Publication. Gaithersburg: NIST; 2012
- 37.Vimalachandran P, Zhang Y, Cao J, Sun L, Yong J (2018) Preserving data privacy and security in australian my health record system: a quality health care implication. In Web information systems engineering—WISE 2018. Lecture notes in computer science, vol. 11234. p. 111–120.
- 38.Wang H, Cao J, Zhang Y. Ticket-based service access scheme for mobile users. Aust Comput Sci Commun. 2002;24(1):285–292. [Google Scholar]
- 39.Wang H, Cao J, Zhang Y. A flexible payment scheme and its role-based access control. IEEE Trans Knowl Data Eng. 2005;17(3):425–436. doi: 10.1109/TKDE.2005.35. [DOI] [Google Scholar]
- 40.Bosch M, et al. Review article: Effectiveness of patient care teams and the role of clinical expertise and coordination: a literature review. Med Care Res Rev. 2009;66(6 Suppl):5S–35S. doi: 10.1177/1077558709343295. [DOI] [PubMed] [Google Scholar]
- 41.Kannampallil TG, et al. Considering complexity in health care systems. J Biomed Informatics. 2011;44(6):943–947. doi: 10.1016/j.jbi.2011.06.006. [DOI] [PubMed] [Google Scholar]
- 42.Malin B, Nyemba S, Paulett J. Learning relational policies from electronic health record access logs. J Biomed Informatics. 2011;44(2):333–342. doi: 10.1016/j.jbi.2011.01.007. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43.Wang K, et al. Medications and prescribing patterns as factors associated with hospitalizations from long-term care facilities: a systematic review. Drugs Aging. 2018;35(5):423–457. doi: 10.1007/s40266-018-0537-3. [DOI] [PubMed] [Google Scholar]
- 44.Kemp K, Arnold BB, Vaile D. My Health Record: the case for opting out. The conversation [Online]. 2018. https://theconversation.com/my-health-record-the-case-for-opting-out-99302.
- 45.Australian Privacy Foundation. MEDIA RELEASE: ‘Open Data’: too much sharing, too little care? Who’s reading your health information now? [Online]. 2018. https://privacy.org.au/2018/01/07/media-release-open-data-too-much-sharing-too-little-care-whos-reading-your-health-information-now/.
- 46.Vimalachandran P, Wang H, Zhang Y. Securing electronic medical record and electronic health record systems through an improved access control. In 4th international health information science conference (HIS), Melbourne, vol. 9085. New York: Springer; 2015. p. 17–30.
- 47.Wang H, Wang Y, Taleb T, Jiang X. Special issue on security and privacy in network computing. World Wide Web. 2020;23(2):951–957. doi: 10.1007/s11280-019-00704-x. [DOI] [Google Scholar]