Abstract
Quantum catalysis is a feasible approach to increase the performance of continuous-variable quantum key distribution (CVQKD), involving the special zero-photon catalysis (ZPC) operation. However, in the practical point of view, the improvement effect of this operation will be limited by the imperfection of the photon detector. In this paper, we show that the ZPC operation at the sender can be simulated by a post-selection method without implementing it in practical devices. While performing this virtual version of ZPC in CVQKD, we can not only reach the ideal case of its practical implementation with minimal hardware requirement, but also keep the benefit of Gaussian security proofs. Based on Gaussian modulated coherent state protocols with achievable parameters, we enhance the security of the proposed scheme from the asymptotical case to the finite-size scenario and composable framework. Simulation results show that similar to the asymptotical case, both the maximal transmission distance and the tolerable excess noise of virtual ZPC-involved CVQKD outperform the original scheme and the scheme using virtual photon subtraction while considering finite-size effect and composable security. In addition, the virtual ZPC-involved CVQKD can tolerate a higher imperfection of the detector, enabling its practical implementation of the CVQKD system with state-of-the-art technology.
Subject terms: Quantum information, Quantum optics
Introduction
Quantum key distribution (QKD)1,2, the best known application of quantum communication, enables two remote legal parties, called Alice and Bob, to establish secret keys over an insecure quantum channel controlled by an eavesdropper (Eve). One implementation approach of QKD is to encode the information in the state of single photon3, such as polarization. However, this discrete-variable (DV) QKD requires single-photon detector in practice, which may bring about challenges for the commercial popularization of DVQKD because of its cost and limited detection efficiency. Alternatively, continuous variable (CV) QKD, which encodes the information in the quadratures ( and )4–7, can be implemented with coherent state and thus be compatible with standard telecommunication optical networks. In theory, its unconditioned security has been proven to be secure against general collective attacks8,9. In practice, high secret key rate and long transmission distance of CVQKD have also been achieved10–16. Nevertheless, restricted by the limited data post-processing speed and the sensitivity to excess noise, the transmission distance of CVQKD can not catch up with its DV counterpart17.
One of feasible methods that can improve the transmission distance of CVQKD is the use of linear amplifiers, including deterministic and probabilistic amplifiers. Deterministic linear amplifier18–20, such as phase-insensitive amplifier, can amplify each incoming signal deterministically so that the performance of CVQKD can be improved21–23. However, actual deterministic linear amplifier not only amplifies the incoming signal and its own noise linearly, but also unavoidably adds extra noise on the signal, which reduces the signal-to-noise ratio. Alternatively, probabilistic amplifier, such as noiseless linear amplifier, amplifies the incoming signal linearly with a certain probability, which is heralded, but introduces less even no noise24–28. Such a noiseless linear amplifier is demonstrated to extend the transmission distance of CVQKD29,30. However, a successfully heralded event of noiseless amplifying needs a single-photon event on photon detector, which renders its practical employment challenging. Interestingly, such probabilistic amplifying can be emulated by post-selection method, namely virtual noiseless amplification31. Although this virtual method makes possible its application for CVQKD, the post-selection probability function of it is diverging, which will complicate the security analysis32. Recently, the combination of deterministic and noiseless linear amplifier has been investigated theoretically and experimentally33,34. Such heralded linear amplifier can also be applied to improve the performance of CVQKD35.
Another viable approach that can improve the transmission distance of CVQKD is the employing of quantum operation, including photon subtraction, quantum scissors and quantum catalysis (QC) operation. The photon-subtraction and quantum scissors operations are non-Gaussain operation. They degrade the secret key rate in short distance but increase the maximal transmission distance of CVQKD36–43. Yet, there exists a possible drawback when taking photon number resolving detector (PNRD) into account. Fortunately, the propose of virtual photon-subtraction for CVQKD enables the photon-subtraction operation to a worthy of practical implementation44–47. However, rigorous security proof of such non-Gaussian protocol is still an open problem. Attractively, the quantum photon catalysis operation, especially for zero-photon catalysis (ZPC), compared with the photon-subtraction operation applied to CVQKD, has larger success probability as well as better performance improvement in terms of secret key rate, transmission distance and tolerable excess noise48–50. Nevertheless, this approach also needs a PNRD or an on/off detector to herald a successful quantum photon catalysis operation, which degrades its practical significance.
To remove the above-mentioned imperfections of the photon detector, in this paper, we propose a scheme of virtual zero-photon catalysis (VZPC)-based CVQKD, which can be implemented via Gaussian post-selection at the sender. One advantage of this method of VZPC is that it can not only emulate an ideal ZPC operation but also implement it without practical devices. Another advantage is that the post-selection probability function or the acceptance function is Gaussian and bounded, and thus our proposed scheme remains equivalent to an effective deterministic Gaussian protocol, which can follow all the Gaussian security proofs as well as the corresponding conventionally Gaussian data post-processing. Furthermore, considering the imperfection of the detector, we expand the security of the proposed scheme from the asymptotical case to the finite-size scenario and composable framework based on Gaussian modulated coherent state protocol and experimentally reachable parameters, in homodyne and heterodyne detection configurations. The VZPC-based CVQKD not only outperforms the original scheme and the scheme with virtual photon subtraction, but also has a higher toleration of the imperfection of the detector.
Results
The VZPC-based CVQKD
Quantum catalysis can be applied to facilitate the conversion of the target ensemble51 and enhance the coherence of the coherent state52, which could prevent the loss of information effectively. It has been demonstrated theoretically that the performance of CVQKD can be improved when acting quantum catalysis operation on it, in both the Einstein-Podolsky-Rosen (EPR)-based scheme48 and the locally generated local oscillator (LLO)-based scheme49. To make our description self-contained, in this section, we introduce the characteristics of quantum catalysis operation, and then propose the VZPC-based CVQKD.
The characteristics of quantum catalysis operation can be illustrated in Fig. 1a. An auxiliary mode Y with number state interacts with the input mode C at the beam splitter (BS) with a transmittance T. The output of mode Y then launches into an ideal PNRD to herald whether a successful quantum catalysis operation happened or not. If there remains m photons registered in the PNRD, we call the process above a successful m-photon quantum catalysis operation, which is represented by an equivalent operator 48,
| 1 |
where T is the transmittance of the BS in Fig. 1a, and c are the creation and annihilation operators of the input state in mode C. Note that, for the auxiliary modes Y and of quantum catalysis operation, the input and output photon number seems like invariable, which means the detection result of the PNRD must be equal to the photon number of mode Y and is different from the m-photon subtraction operation (m > 0) shown in Fig. 1b. The post-selection state of for ZPC is conditioned on the 0 photon event on the PNRD while for m-photon subtraction is conditioned on the m (m > 0) photon event on the PNRD.
Figure 1.

Illustrations of the quantum operation. (a) Quantum catalysis operation. (b) Photon subtraction operation. BS, beam splitter. PNRD, photon number resolving detector.
The quantum catalysis operation has larger success probability than the photon subtraction operation, and hence the ZPC-based CVQKD has better performance improvement in terms of secret key rate, transmission distance and tolerable excess noise48,49, especially for the ZPC. Therefore, in this work, we mainly focus on the ZPC operation. The specific application scheme of the ZPC in the equivalent entanglement-based (EB) CVQKD and its corresponding prepare-and-measure (PM) scheme can be simply described in Fig. 2a, b, respectively. However, from a practical point of view, the requirement of a PNRD or an on-off detector brings about practical difficulties. The imperfection of the detector and the augment to CVQKD system’s complexity reduce the attractiveness of quantum catalysis operation. To overcome the difficulties mentioned above, in what follows, we suggest an equivalent post-selection method to emulate the ZPC operation in CVQKD with Gaussian modulated coherent state protocol. By using this method, one can not only enjoy the perfect ZPC operation but also remove the problem of increasing the system’s complexity.
Figure 2.
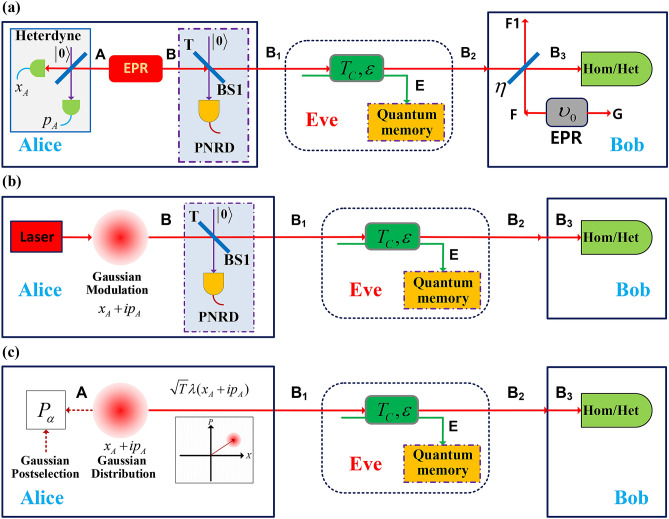
(a) Equivalent entanglement-based (EB) scheme of CVQKD with the ZPC. (b) Prepare-and-measure (PM) scheme of CVQKD with the ZPC. (c) PM scheme of CVQKD with the VZPC. , the quantum efficiency if the detector. T, the transmittance of the BS1. , acceptance probability. , the equivalent variance of EPR state modelling the electronic noise of the detector. for homodyne detector and for heterodyne detector.
Now, let us begin the description of the equivalent post-selection method with the EB scheme of the ZPC-based CVQKD. As shown in Fig. 2a, Alice prepares a pair of EPR state, including two modes A and B with a modulation variance V, i.e.
| 2 |
where . She retains mode A of the two modes and sends the other mode B to Bob. For the preserved mode A, Alice performs heterodyne detection on it and gets the results {, }, which obeys Gaussian distribution with probability distribution 53. It is known that heterodyne detection on mode A will project mode B onto a coherent state with 54. Consequently, the mixed state can be given by
| 3 |
where 53. Before Alice sends mode B to Bob, she performs the ZPC operation on mode B and yields the mode if this operation is successful. Therefore, after the BS1, the mixed state of mode undergone a successful ZPC operation can be given by
| 4 |
with
| 5 |
where is the success probability of the ZPC operation. It can be obtained by the relationship of , given by Comparing with the state in Eq. (4) and the state in Eq. (3), one can find two differences between them. One is the additional weighting function , which leads to an acceptance probability for each pair of measured results . The total acceptance probability for all the data measured by Alice is , resulting in the success probability of the ZPC operation. The other one is the rescaling of the mean value of the coherent state from to (). Although the ZPC operation is probabilistic, is Gaussian so that is still a Gaussian distribution, and thus this filter is Gaussian in the sense that it converts one Gaussian state into another Gaussian state, which means the ZPC operation preserves Gaussianity while the m-photon quantum catalysis operation () is non-Gaussian55. As the heterodyne detection and the ZPC operation are conducted on two different modes A and B, these two processes can be commuted with each other. Thus, we get an equivalent VZPC through Gaussian post-selection of Alice’s each measurement result with an acceptance probability after exchanging the heterodyne detection and the ZPC operation. To be more specific, the PM version of the VZPC-based CVQKD, as shown in Fig. 2c, can be summarized as follows:
- Step 1
Alice prepares a coherent state with and sends it to Bob, where and obey Gaussian distribution with zero mean and variance of .
- Step 2
Bob receives the coherent state sent by Alice and performs homodyne or heterodyne detections. The measurement results are and , respectively.
- Step 3
After performing many rounds of step 1 and 2, Alice and Bob preserve enough data. Alice uses the acceptance probability to determine which data will be accepted and reveals them to Bob.
- Step 4
Using the accepted data determined by step 3, Alice and Bob accomplish the conventional post-processing steps, involving parameter estimation, information reconciliation and privacy amplification.
Since the Gaussian post-selection can not change the Gaussianity of the data that Alice finally determined for generating secret keys, the suggested scheme remains equivalent to an effective deterministic Gaussian protocol, which can follow all the Gaussian security proofs as well as the corresponding conventionally Gaussian data post-processing. Note that since , the acceptance probability function is bounded. As a result, for arbitrary probability distribution of , the integration is convergent. Therefore, differing from the virtual noiseless amplification31, there is no divergence problem for the VZPC-based CVQKD.
Performance analysis
In this section, based on Gaussian modulation of the quadratures of coherent states, we show the performance of our scheme for the security frameworks of asymptotic, finite-size and composable scenarios under a collective Gaussian attack assumption.
In order to derive the analytical expression of the secret key rate, we need get the covariance matrix of the state in the equivalent EB-based version of our scheme. The covariance matrix of the EPR state that Alice prepared can be given by56
| 6 |
where and . After performing the ZPC operation on mode B, the covariance matrix of the yield state can be expressed as
| 7 |
where
| 8 |
| 9 |
The explicit derivation of the above expressions and the covariance matrix , containing the cases of asymptotic, finite-size and composable scenario, are shown in Supplementary S1. With the covariance matrices obtained in Supplementary S1, we can calculate the secret key rates using techniques shown in Refs.8,9,48,56 for asymptotic, finite-size and composable security, as shown in Supplementary S2. For comparison, in what follows, we also show the simulation results of CVQKD with virtual photon subtraction (VPS). Its computing of covariance matrixes and secret key rates under asymptotic, finite-size and composable security are shown in Supplementary S3. Since the CVQKD with virtual 1-photon subtraction (V1-PS) has the optimal performance improvement44, we only show results of V1-PS-based CVQKD here. Note, as the 1-PS operation is non-Gaussian, all the calculated results for it are lower bounds based on the Gaussian hypothesis according to the extemality of Gaussian quantum states57.
Asymptotic security
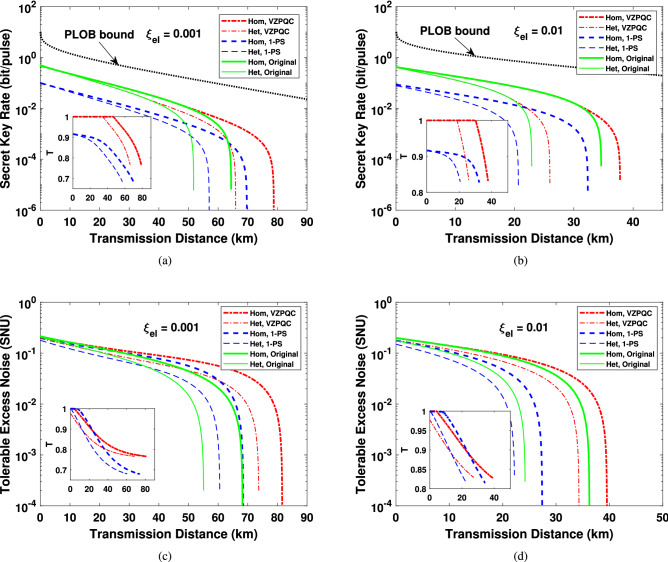
We now give the asymptotical security of the VZPC-based CVQKD. The global parameters that are used for simulation are the variance V of the equivalent EPR state, the transmission efficiency and the excess noise of the quantum channel, the quantum efficiency and electronic noise of the detector, the reconciliation efficiency of the reverse reconciliation phase. The parameters , and are fixed to values (in shot noise units), , 14. The variance V takes the value 20 (in shot noise units), while we set the electronic noise of the detector to 0.01 or 0.001 (in shot noise units)11. In addition, the channel transmission efficiency is written as , where dB/km is the loss coefficient of optical fibers, and L is the fiber length.
The simulation results for homodyne and heterodyne detection are shown in Fig. 3a, b, where dash-dotted, dashed and solid lines are related to the results of the VZPC-based CVQKD, the V1-PS-based CVQKD and the original CVQKD, respectively. The dotted lines are the fundamental benchmark of CVQKD, i.e. PLOB bound58. Note that represents catalysis operation is not performed. From the above results we can find that similar to the results in Ref.48, our proposed scheme can improve the maximal transmission distance and outperforms the V1-PS-based CVQKD CVQKD, while considering the imperfection of the detector. When the electronic noise arises to 0.01, the V1-PS-based CVQKD can no longer improve the transmission distance, whereas our proposed scheme is still effective. Actually, the ZPQC operation will decrease not only the final mutual information shared by Alice and Bob but also the stolen information available to Eve on Bob’s key, as shown in Fig. 4. Interestingly, compared to the former, the latter has a relatively larger degradation, which enables the secret key rate to remain positive in the long-distance regime, as shown in Fig. 4, where the vertical axis represents the ratio between the decrement of and the decrement of (in the unit of dB), which is defined as . Furthermore, from the green solid line in Fig. 4, we can find that increases with the transmission distance, which enables our proposed system to reach a longer maximal transmission distance.
Figure 3.
The simulation results under asymptotical security. (a), (b) The results of secret key rate for the VZPC-based scheme, the 1-photon-subtraction-based scheme and the original scheme, when the electronic noise of the detector are 0.001 and 0.01, respectively. The optimal value of T at each distance are shown in the insets. (c), (d) The tolerable excess noise and the corresponding values of T (the insets) for the proposed scheme and the original scheme, when is equal to 0.001 and 0.01, respectively. The black dotted line represents the PLOB bound. 1-PS: 1-photon subtraction.
Figure 4.
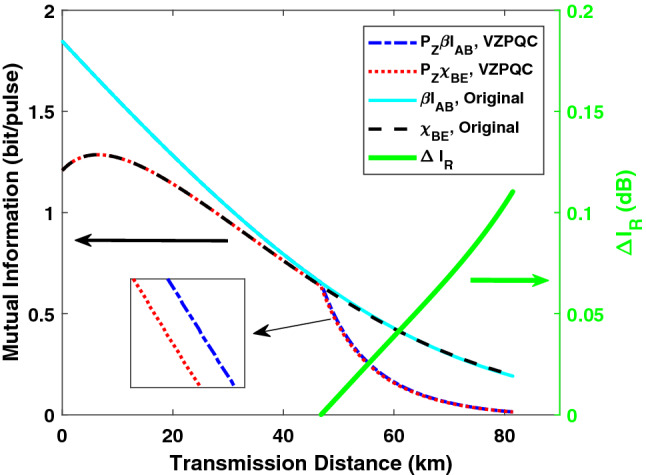
The final mutual information between Alice and Bob and between Bob and Eve, and the result of as a function of transmission distance (green solid line). Here, we only show the results of homodyne detection when .
In addition, the electronic noise of the detector at the receiver has a significant effect on our suggested scheme. Larger electronic noise not only degrades the entire performance significantly, but also decreases the performance improvement of CVQKD with the VZPC, which shows the possibly large limit of detector to practical system. Besides, except within very short transmission distance (smaller than 10 km), the performance of homodyne detection is better than heterodyne detection for . While the electronic noise of detector arising to 0.01, the performance of homodyne detection is always better than heterodyne detection. The reason is a extra unit of shot noise introduced by the heterodyne detection.
We also give the tolerable excess noise for the given parameters above, as shown in Fig. 3c, d, where the insets mean the corresponding optimal value of T. The tolerable excess noise is larger than the original scheme and the V1-PS-based scheme. Similar the secret key rate results in Fig. 3b, for the electronic noise up to 0.01, the tolerable noise can no longer be improved for the V1-PS-based protocol. These mean a more robust CVQKD system can be obtained with the VZPC, by optimizing the parameter T.
Finite-size analysis
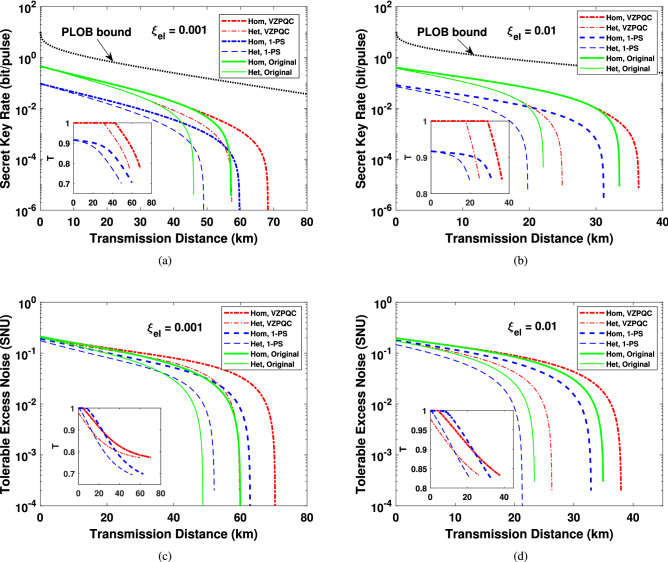
In the practical implementation of CVQKD, the amount of signal uses is not infinite, which means that we must consider the finite-size effect of the proposed scheme. Moreover, some of the signal uses are discarded in the post-selection process, which will decrease the final signals used for parameter estimation and secret key generation. This post-selection process may generate significant impact on finite-size regime. Therefore, for protocols using post-selection, finite-size analysis is of great significance for practical application. In the following, we expand our suggested VZPC-based CVQKD to the finite-size case, which is more in line with the practical situation. We note that the final simulation results are similar to that of the asymptotic case, as shown in Fig. 5, where the block size N is set to be , the parameters , and are all set to be 8. The rate , which is the rate of signals uses used for parameter estimation, is optimized for each distance in Fig. 5a, b, while it is fixed with 11 for Fig. 5c, d. It is visible that not only the maximal transmission distance but also the tolerable excess noise can be improved for the VZPC-based CVQKD when considering the finite-size effect, although the degree of improvement is slightly decreased. Moreover, our proposed scheme outperforms the V1-PS-based scheme as well. While the block size N is up to , the results considering finite-size effect will closely approach that of the asymptotical case.
Figure 5.
The simulation results considering finite-size effect. (a), (b) The results of secret key rate for the VZPC-based scheme, the 1-photon-subtraction-based scheme and the original scheme, when the electronic noise of the detector are 0.001 and 0.01, respectively. The rate r is optimized and the optimal value of T at each distance are shown in the insets. (c) , (d) The tolerable excess noise and the corresponding values of T (the insets) for the proposed scheme and the original scheme with a fixed , when is equal to 0.001 and 0.01, respectively. The black dotted line represents the PLOB bound.
From a practical point of view, the evaluation of the optimal value of T will be under certain region. If the fluctuation of the estimated value of T has large impact on the proposed CVQKD system with the VZPC, complicated implementations will be required to acquire an accurate evaluation of T, leading to the employment of the VZPC non of worthy. Therefore, we inspect the variation of secret key rate under finite-size scenario when the parameter T diverging from its optimal value a certain range. Fortunately, the secret key rate changes slowly with the fluctuation of T at each distance around its optimum value , as illustrated in Fig. 6, where and . We can get that higher than 90% of the optimum secret key rate () can be obtained while T changing in a relative large region, which is within the scope between the dashed line () and the dash-dotted line (). Similar results can be acquired for the case of asymptotical and composable security and we do not show it for simplicity.
Figure 6.

The secret key rate as a function of transmission distance and T. The blue solid line denotes the optimal value of T to acquire the optimum secret key rate (). The red dash-dotted line represents the upper bound of T at each distance while the secret key rate remains up to 90% of its optimum. The magenta dashed line denotes the lower bound of T at each distance while the secret key rate remains up to 90% of its optimum. The variance V and the electronic noise are set to 20 and 0.001. The block size and .
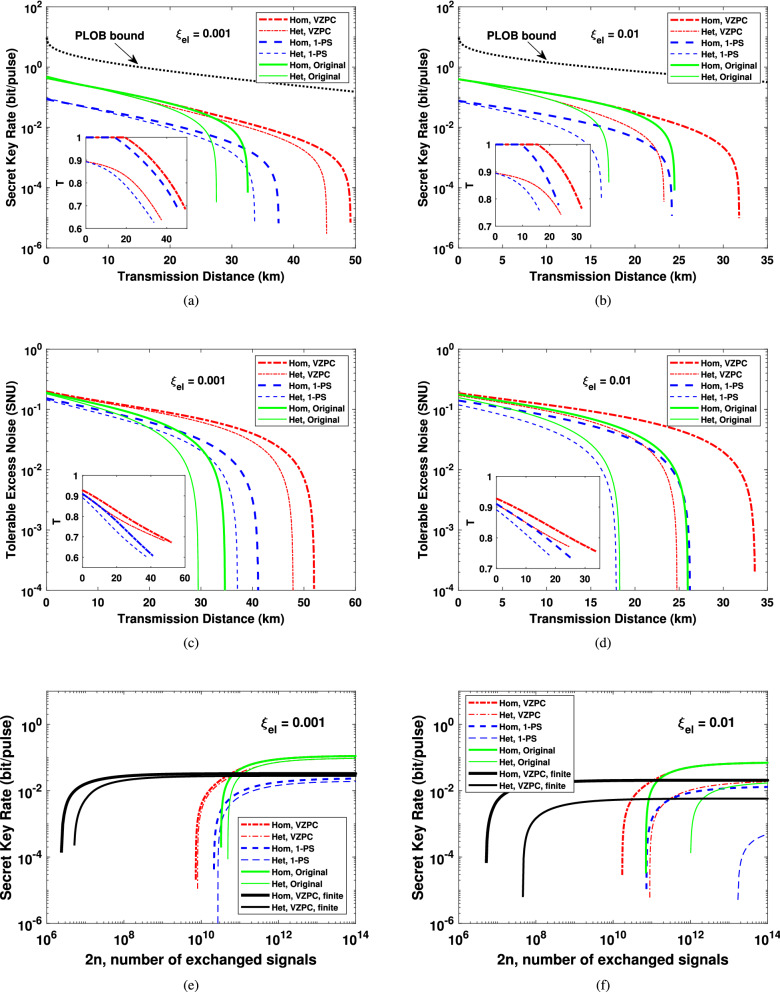
Finally, we focus on the comparison of the extent of the effect on our proposed CVQKD scheme between the detector’s quantum efficiency and electronic noise. We depict the secret key rate simulation results in Fig 7a with electronic noise , while the quantum efficiency the detector is equal to 1. We find that even the quantum efficiency is up to the perfect case, the performance remains a big gap compared to the case of and (see Fig. 5a), which reflects that the detector’s electronic noise is a more sensitive parameter than its quantum efficiency, either homodyne or heterodyne detection. To make the results more clear, we draw the secret key rate as a function of detector’s quantum efficiency and electronic noise in Fig. 7b, where the transmission distance is 40 km. Since there is little even no performance improvement for 1-photon subtraction operation, we don’t show its results here. We find that the imperfection toleration of homodyne detection is better than that of the heterodyne detection. In particular, compared with the original CVQKD protocol, our suggested scheme can tolerate a higher imperfection of the detector, especially for homodyne detection. These results related to the detector are also applied to the case under previous asymptotical security and the latter composable security.
Figure 7.
(a) The secret key rate as a function of transmission distance considering finite-size effect. The detector’s quantum efficiency is equal to 1. (b) To obtain a secret key rate of bit/pulse, the detector’s quantum efficiency as a function of electronic noise under the finite-size security. Here we set the transmission distance km. The block size and for all these two figures.
Composable security
The composable security is of great significance for CVQKD to apply in more complex and unpredictable environments, whereas the finite-size analysis is a foundation for the practical implementation of CVQKD. Actually, for realistical application of CVQKD in complex environments, there exists a probability that the finally generated secret keys do not meet the requirement of the CVQKD protocol, i.e. the protocol has “flaw”. The composable security can relax the problem of how to evaluate the degree of this “flow” of a CVQKD protocol, and can also solve the problem of evaluating “flow degree” while the flowed keys are applied in other subsequent protocols. Therefore, it is of importance that whether the proposed scheme can also be applied to real complex environments and composed with other composable secure protocols. Composable security against collective attack for CVQKD has been proven in Ref.9, which further implies composable security against general security combining the de Finetti theorem or postselection technique. Here, we give a further analysis of the proposed scheme in composable security framework against collective attacks, exploring the feasibility of the scheme under general security framework and therefore demonstrating the practical significance of it. All the values of the security parameters are chosen as follows9:
| 10 |
We plot the numerical results of secret key rate and tolerable noise as well as the corresponding optimal value of T in Fig. 8a–d, where the total exchanged signals between Alice and Bob is set to be . From the simulation results, we can see that similar to the finite-size case, the maximum transmission distance can be improved in composable security framework as well. However, although the block size is up to , the maximally reachable transmission distance is even less than that of the finite-size case with . The performance of finite-size case will approach to the asymptotical case while the block size reaches , whereas the block size should come up to for composable security. Moreover, the results will be even worse for composable security with a lower block size. If the block size and (not shown), only less than 24 km and 22 km can be reached for our proposed scheme with homodyne and heterodyne detection, respectively. For and , the results are even worse, merely less than 17 km and 12 km can be reached for our proposed scheme while performing homodyne and heterodyne detection. Non positive key rate can be obtained for all cases when . Therefore, it is more sensitive to the block size for the practical system under composable security framework. We plot the secret key as a function of 2n, the number of exchanged signals, in Fig. 8e, f, where the transmission distance is 20 km. From these results we can conclude that compared to the V1-PS-based and the original CVQKD protocol, our proposed scheme can tolerate smaller limit of block size. Meanwhile, in Fig. 8e, f, we also show the corresponding results of our proposed scheme under finite-size security (two black solid lines), with a fixed rate . Obviously, compared with the finite-size case, composable security has a higher security level and thus it requires much larger number of channel uses.
Figure 8.
The simulation results considering composable security. (a), (b) The results of secret key rate for the VZPC-based scheme, the 1-photon-subtraction-based scheme and the original scheme, when the electronic noise of the detector are 0.001 and 0.01, respectively. The optimal value of T at each distance are shown in the insets. (c), (d) The tolerable excess noise and the corresponding values of T (the insets) for the proposed scheme and the original scheme, when is equal to 0.001 and 0.01, respectively. (e), (f)Expected secret key rate as a function of 2n for 20 km transmission distance, when is equal to 0.001 and 0.01, respectively. The black dotted line represents the PLOB bound.
Discussion
We have proposed an approach, virtual zero-photon catalysis, to emulate the ideal zero-photon catalysis operation without practical devices in coherent-state CVQKD, which can be realized by Gaussian post-selection according to Alice’s data. The post-selection probability function or the acceptance function is Gaussian and bounded, which guarantees our proposed protocol remains equivalent to an effective deterministic Gaussian protocol, and thus enables it to follow all the Gaussian security proofs as well as the corresponding conventionally Gaussian data post-processing. The simulation results show that by optimizing the main parameter, i.e., the transmittance T of Alice’s BS1, both the maximal transmission distance and the tolerable excess noise can be increased and outperform the V1-PS-based CVQKD scheme, which is true for the asymptotical security and the security considering finite-size effect. By comparing the results of homodyne and heterodyne detection, additionally, we find that the performance of homodyne detection is superior to that of the heterodyne detection. Attractively, the CVQKD using virtual zero-photon quantum catalysis can tolerate a higher imperfection of the detector, especially for homodyne detection. These results indicate that our proposed scheme offers an opportunity of practically implementing the zero-photon catalysis on CVQKD systems.
Supplementary information
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61871407, 61872390, 61801522), Postgraduate Scientific Research Innovation Project of Hunan Province (Grant No. 0171BCB23034) and Postgraduate Independent Exploration and Innovation Project of Central South University (Grant Nos. 2019zzts070, 2020zzts136).
Author contributions
H.Z. performed the security analysis and wrote the manuscript, Y.G. and Y.M. supervised the project, Y.G. and W.Y. design the work, W.Y., Y.M. and D.H. reviewed the manuscript.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Ying Guo, Email: yingguo@csu.edu.cn.
Wei Ye, Email: yeweicsu@csu.edu.cn.
Supplementary information
is available for this paper at 10.1038/s41598-020-73379-4.
References
- 1.Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. in Proceedings of IEEE International Conference on Computers Systems, and Signal Processing, Bangalore, India, 175–179 (1984).
- 2.Grosshans F, Grangier P. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 2002;88:057902. doi: 10.1103/PhysRevLett.88.057902. [DOI] [PubMed] [Google Scholar]
- 3.Lo HK, Curty M, Tamaki K. Secure quantum key distribution. Nat. Photon. 2015;8:595–604. doi: 10.1038/nphoton.2014.149. [DOI] [Google Scholar]
- 4.Braunstein SL, van Loock P. Quantum information with continuous variables. Rev. Mod. Phys. 2005;77:513–577. doi: 10.1103/RevModPhys.77.513. [DOI] [Google Scholar]
- 5.Weedbrook C, et al. Gaussian quantum information. Rev. Mod. Phys. 2012;84:621–669. doi: 10.1103/RevModPhys.84.621. [DOI] [Google Scholar]
- 6.Laudenbach F, et al. Continuous-variable quantum key distribution with Gaussian modulation-the theory of practical implementations. Adv. Quantum Technol. 2018;1:1800011. doi: 10.1002/qute.201800011. [DOI] [Google Scholar]
- 7.Pirandola, S. et al. in Advances in Quantum Cryptography. arXiv e-prints arXiv:1906.01645 (2019).
- 8.Leverrier A, Grosshans F, Grangier P. Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A. 2010;81:062343. doi: 10.1103/PhysRevA.81.062343. [DOI] [Google Scholar]
- 9.Leverrier A. Composable security proof for continuous-variable quantum key distribution with coherent states. Phys. Rev. Lett. 2015;114:070501. doi: 10.1103/PhysRevLett.114.070501. [DOI] [PubMed] [Google Scholar]
- 10.Huang D, et al. Continuous-variable quantum key distribution with 1 mbps secure key rate. Opt. Express. 2015;23:17511–17519. doi: 10.1364/OE.23.017511. [DOI] [PubMed] [Google Scholar]
- 11.Huang D, Huang P, Lin D, Zeng G. Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 2016;6:19201. doi: 10.1038/srep19201. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Zhang Y, et al. Continuous-variable qkd over 50 km commercial fiber. Quantum Sci. Technol. 2019;4:035006. doi: 10.1088/2058-9565/ab19d1. [DOI] [Google Scholar]
- 13.Zhang G, et al. An integrated silicon photonic chip platform for continuous-variable quantum key distribution. Nat. Photon. 2019;13:839–842. doi: 10.1038/s41566-019-0504-5. [DOI] [Google Scholar]
- 14.Zhang Y, et al. Long-distance continuous-variable quantum key distribution over 202.81 km of fiber. Phys. Rev. Lett. 2020;125:010502. doi: 10.1103/PhysRevLett.125.010502. [DOI] [PubMed] [Google Scholar]
- 15.Lin D, Huang D, Huang P, Peng J, Zeng G. High performance reconciliation for continuous-variable quantum key distribution with ldpc code. Int. J. Quantum Inf. 2015;13:1550010. doi: 10.1142/S0219749915500100. [DOI] [Google Scholar]
- 16.Milicevic M, Feng C, Zhang LM, Gulak PG. Quasi-cyclic multi-edge ldpc codes for long-distance quantum cryptography. npj Quantum Inf. 2018;4:21. doi: 10.1038/s41534-018-0070-6. [DOI] [Google Scholar]
- 17.Yin H, et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 2016;117:190501. doi: 10.1103/PhysRevLett.117.190501. [DOI] [PubMed] [Google Scholar]
- 18.Caves CM. Quantum limits on noise in linear amplifiers. Phys. Rev. D. 1982;26:1817. doi: 10.1103/PhysRevD.26.1817. [DOI] [Google Scholar]
- 19.Andersen UL, Josse V, Leuchs G. Unconditional quantum cloning of coherent states with linear optics. Phys. Rev. Lett. 2005;94:240503. doi: 10.1103/PhysRevLett.94.240503. [DOI] [Google Scholar]
- 20.Andersen, U. L. & Filip, R. Quantum Feed-Forward Control of Light, Vol. 53, 365–414 (Elsevier, 2009).
- 21.Fossier S, Diamanti E, Debuisschert T, Tualle-Brouri R, Grangier P. Improvement of continuous-variable quantum key distribution systems by using optical preamplifiers. J. Phys. B At. Mol. Opt. Phys. 2009;42:114014. doi: 10.1088/0953-4075/42/11/114014. [DOI] [Google Scholar]
- 22.Zhang H, Fang J, He G. Improving the performance of the four-state continuous-variable quantum key distribution by using optical amplifiers. Phys. Rev. A. 2012;86:022338. doi: 10.1103/PhysRevA.86.022338. [DOI] [Google Scholar]
- 23.Guo Y, Lv GL, Zeng GH. Balancing continuous-variable quantum key distribution with source-tunable linear optics cloning machine. Quantum Inf. Process. 2015;14:4323–4338. doi: 10.1007/s11128-015-1100-3. [DOI] [Google Scholar]
- 24.Ralph, T. & Lund, A. Nondeterministic noiseless linear amplification of quantum systems. AIP Conf. Proc.1110, 155–160. 10.1063/1.3131295 (AIP, 2009).
- 25.Ferreyrol F, et al. Implementation of a nondeterministic optical noiseless amplifier. Phys. Rev. Lett. 2010;104:123603. doi: 10.1103/PhysRevLett.104.123603. [DOI] [PubMed] [Google Scholar]
- 26.Xiang G, Ralph T, Lund A, Walk N, Pryde GJ. Heralded noiseless linear amplification and distillation of entanglement. Nat. Photon. 2010;4:316. doi: 10.1038/nphoton.2010.35. [DOI] [Google Scholar]
- 27.Ferreyrol F, Blandino R, Barbieri M, Tualle-Brouri R, Grangier P. Experimental realization of a nondeterministic optical noiseless amplifier. Phys. Rev. A. 2011;83:063801. doi: 10.1103/PhysRevA.83.063801. [DOI] [PubMed] [Google Scholar]
- 28.Combes J, Walk N, Lund AP, Ralph TC, Caves CM. Models of reduced-noise, probabilistic linear amplifiers. Phys. Rev. A. 2016;93:052310. doi: 10.1103/PhysRevA.93.052310. [DOI] [Google Scholar]
- 29.Blandino R, et al. Improving the maximum transmission distance of continuous-variable quantum key distribution using a noiseless amplifier. Phys. Rev. A. 2012;86:012327. doi: 10.1103/PhysRevA.86.012327. [DOI] [Google Scholar]
- 30.Xu B, Tang C, Chen H, Zhang W, Zhu F. Improving the maximum transmission distance of four-state continuous-variable quantum key distribution by using a noiseless linear amplifier. Phys. Rev. A. 2013;87:062311. doi: 10.1103/PhysRevA.87.062311. [DOI] [Google Scholar]
- 31.Fiurášek J, Cerf NJ. Gaussian postselection and virtual noiseless amplification in continuous-variable quantum key distribution. Phys. Rev. A. 2012;86:060302. doi: 10.1103/PhysRevA.86.060302. [DOI] [Google Scholar]
- 32.Walk N, Ralph TC, Symul T, Lam PK. Security of continuous-variable quantum cryptography with Gaussian postselection. Phys. Rev. A. 2013;87:020303. doi: 10.1103/PhysRevA.87.020303. [DOI] [Google Scholar]
- 33.Haw JY, et al. Surpassing the no-cloning limit with a heralded hybrid linear amplifier for coherent states. Nat. Commun. 2016;7:13222. doi: 10.1038/ncomms13222. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34.Zhao J, et al. Quantum enhancement of signal-to-noise ratio with a heralded linear amplifier. Optica. 2017;4:1421–1428. doi: 10.1364/OPTICA.4.001421. [DOI] [Google Scholar]
- 35.Zhou J, Shi R, Feng Y, Shi J, Guo Y. Enhancing continuous variable quantum key distribution with a heralded hybrid linear amplifier. J. Phys. A Math. Theor. 2019;52:245303. doi: 10.1088/1751-8121/ab1ecd. [DOI] [Google Scholar]
- 36.Huang P, He G, Fang J, Zeng G. Performance improvement of continuous-variable quantum key distribution via photon subtraction. Phys. Rev. A. 2013;87:012317. doi: 10.1103/PhysRevA.87.012317. [DOI] [Google Scholar]
- 37.Guo Y, et al. Performance improvement of continuous-variable quantum key distribution with an entangled source in the middle via photon subtraction. Phys. Rev. A. 2017;95:032304. doi: 10.1103/PhysRevA.95.032304. [DOI] [Google Scholar]
- 38.Liao Q, Guo Y, Huang D, Huang P, Zeng G. Long-distance continuous-variable quantum key distribution using non-Gaussian state-discrimination detection. New J. Phys. 2018;20:023015. doi: 10.1088/1367-2630/aaa8c4. [DOI] [Google Scholar]
- 39.Ma H, et al. Continuous-variable measurement-device-independent quantum key distribution with photon subtraction. Phys. Rev. A. 2018;97:042329. doi: 10.1103/PhysRevA.97.042329. [DOI] [Google Scholar]
- 40.Wu X, Wang Y, Zhong H, Liao Q, Guo Y. Plug-and-play dual-phase-modulated continuous-variable quantum key distribution with photon subtraction. Front. Phys. 2019;14:41501. doi: 10.1007/s11467-019-0881-8. [DOI] [Google Scholar]
- 41.Lim K, Suh C, Rhee J-KK. Longer distance continuous variable quantum key distribution protocol with photon subtraction at the receiver. Quantum Inf. Process. 2019;18:73. doi: 10.1007/s11128-018-2167-4. [DOI] [Google Scholar]
- 42.Ghalaii M, Ottaviani C, Kumar R, Pirandola S, Razavi M. Long-distance continuous-variable quantum key distribution with quantum scissors. IEEE J. Sel. Top. Quantum Electron. 2020;26:1–12. doi: 10.1109/JSTQE.2020.2964395. [DOI] [Google Scholar]
- 43.Ghalaii M, Ottaviani C, Kumar R, Pirandola S, Razavi M. Discrete-modulation continuous-variable quantum key distribution enhanced by quantum scissors. IEEE J. Sel. Areas Commun. 2020;38:506–516. doi: 10.1109/JSAC.2020.2969058. [DOI] [Google Scholar]
- 44.Li Z, et al. Non-Gaussian postselection and virtual photon subtraction in continuous-variable quantum key distribution. Phys. Rev. A. 2016;93:012310. doi: 10.1103/PhysRevA.93.012310. [DOI] [Google Scholar]
- 45.Zhao Y, Zhang Y, Li Z, Yu S, Guo H. Improvement of two-way continuous-variable quantum key distribution with virtual photon subtraction. Quantum Inf. Process. 2017;16:184. doi: 10.1007/s11128-017-1617-8. [DOI] [Google Scholar]
- 46.Zhao Y, Zhang Y, Xu B, Yu S, Guo H. Continuous-variable measurement-device-independent quantum key distribution with virtual photon subtraction. Phys. Rev. A. 2018;97:042328. doi: 10.1103/PhysRevA.97.042328. [DOI] [Google Scholar]
- 47.Zhong H, et al. Enhancing of self-referenced continuous-variable quantum key distribution with virtual photon subtraction. Entropy. 2018;20:578. doi: 10.3390/e20080578. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 48.Guo Y, Ye W, Zhong H, Liao Q. Continuous-variable quantum key distribution with non-Gaussian quantum catalysis. Phys. Rev. A. 2019;99:032327. doi: 10.1103/PhysRevA.99.032327. [DOI] [Google Scholar]
- 49.Ye W, et al. Improvement of self-referenced continuous-variable quantum key distribution with quantum photon catalysis. Opt. Express. 2019;27:17186–17198. doi: 10.1364/OE.27.017186. [DOI] [PubMed] [Google Scholar]
- 50.Ye, W., Zhong, H., Wu, X., Hu, L. & Guo, Y. Continuous-Variable Measurement-Device-Independent Quantum Key Distribution via Quantum Catalysis. arXiv e-prints arXiv:1907.03383 (2019).
- 51.Lvovsky AI, Mlynek J. Quantum-optical catalysis: Generating nonclassical states of light by means of linear optics. Phys. Rev. Lett. 2002;88:250401. doi: 10.1103/PhysRevLett.88.250401. [DOI] [PubMed] [Google Scholar]
- 52.Zhang S, Zhang X. Photon catalysis acting as noiseless linear amplification and its application in coherence enhancement. Phys. Rev. A. 2018;97:043830. doi: 10.1103/PhysRevA.97.043830. [DOI] [Google Scholar]
- 53.Pirandola S, Spedalieri G, Braunstein SL, Cerf NJ, Lloyd S. Optimality of Gaussian discord. Phys. Rev. Lett. 2014;113:140405. doi: 10.1103/PhysRevLett.113.140405. [DOI] [PubMed] [Google Scholar]
- 54.Grosshans, F., Cerf, N. J., Wenger, J., Tualle-Brouri, R. & Grangier, P. Virtual Entanglement and Reconciliation Protocols for Quantum Cryptography with Continuous Variables. arXiv e-prints quant–ph/0306141 (2003).
- 55.Hu L, Liao Z, Zubairy MS. Continuous-variable entanglement via multiphoton catalysis. Phys. Rev. A. 2017;95:012310. doi: 10.1103/PhysRevA.95.012310. [DOI] [Google Scholar]
- 56.Sánchez, G.-P. & Raúl. Quantum Information with Optical Continuous Variables: From Bell Tests to Key Distribution (2007).
- 57.Navascues M, Grosshans F, Acin A. Optimality of Gaussian attacks in continuous-variable quantum cryptography. Phys. Rev. Lett. 2006;97:190502. doi: 10.1103/PhysRevLett.97.190502. [DOI] [PubMed] [Google Scholar]
- 58.Pirandola S, Laurenza R, Ottaviani C, Banchi L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017;8:15043. doi: 10.1038/ncomms15043. [DOI] [PMC free article] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.