Abstract
Quantum key distribution (QKD) can share an unconditional secure key between two remote parties, but the deviation between theory and practice will break the security of the generated key. In this paper, we evaluate the security of QKD with weak basis-choice flaws, in which the random bits used by Alice and Bob are weakly controlled by Eve. Based on the definition of Li et al. (Sci Rep 5:16200, 2015) and GLLP’s analysis, we obtain a tight and analytical bound to estimate the phase error and key rate for both the single photon source and the weak coherent source. Our approach largely increases the key rate from that of the original approach. Finally, we investigate and confirm the security of BB84-QKD with a practical commercial devices.
Subject terms: Quantum information, Quantum optics
Introduction
Based on the principle of quantum mechanics, “quantum cryptography” is a possible means of implementing unconditional secure communication. One famous quantum cryptography approach is quantum key distribution (QKD) combined with One-Time pad. Since the proposal of the first QKD protocol BB841, QKD has attracted much interest. The unconditional security of QKD had been proven in both perfect2 and imperfect3,4 devices. QKD has also been experimentally demonstrated in fibers5,6, free space7,8, and satellites9,10. Multi-user quantum networks based on these results have become available in many countries11–14.
However, because practical devices are imperfect, some assumptions of the theoretical analysis may be violated in practical situations. If the gap between theory and practice is exploited by an eavesdropper (Eve), the security of the final key may be broken. In fact, many loopholes have been discovered in practical QKD systems15–21. These loopholes are closed by two main approaches: device-independent QKD protocols and security patches. The former include full-device-independent QKD22,23, measurement-device-independent QKD24–26, and semi-device-independent QKD27. Security patches account for the parameters of practical devices (as many as possible) in the security model. Although device-independent QKD can remove all or a portion of the loopholes, the task remains technologically challenging, especially in practical commercial QKD networks. Thus, most practical QKD systems implement security patches.
In the BB84 protocol, both Alice and Bob must determine how to prepare and measure the quantum states. For this purpose, they require random bits. In practical situations, the random bits may be weakly known or controlled by Eve, and the security of the generated key is compromised. A typical attack that exploits the weak randomness of QKD is wavelength attack16,17. The security of QKD with weak randomness was first studied by Li et al.28, and has since been applied to different cases29,30. In Li’s analysis, if the legitimate parties use the “one-step post processing method” to distill the final key, even a small degree of non-randomness will rapidly reduce the final key rate. The key rate can be improved if the legitimate parties adopt the “two-step post processing method”, or biased basis protocol, in which Alice and Bob distill the key from the rectilinear and diagonal bases, respectively. However, to maximize Eve’s information, they must perform global optimization, which is hampered by at least two disadvantages: large time cost and convergence to a local optimum. The time cost is incurred by the complexity or cost of post processing, and local (rather than global) optimization compromises the security of the generated key.
To mitigate these problems, we develop an analytical formula that estimates the key rate for both the single photon source (SPS) and the weak coherent source (WPS). In numerical simulations, our method significantly increased the key rate over the original method of Li et al.28. For example, the original method of Ref.28 can generate no secure key for a SPS with a basis-choice flaw of 0.1 when the bit error rate exceeds 3.4%, but our method achieves a final key rate of 0.45 under these conditions. Furthermore, to evaluate the performance of QKD under wavelength attack, we also estimate the key rate of a practical QKD system with a passive basis-choice.
Results
Weak randomness and one-step post processing
This section briefly reviews the analysis of Ref.28. Alice determines her quantum state from two random bits: for bit and for basis. Meanwhile, Bob chooses his basis from a random bit, y. As the final key is distilled only when Alice and Bob choose the same basis (), the following analysis is limited to the case . In a practical QKD system, () may be weakly controlled by Eve with a hidden variable (). Setting k and = [0, 1] as the values of and , respectively, the probabilities of obtaining and are respectively given by
| 1 |
Here . Due to the existence of the hidden variable , we cannot guarantee that holds for all i, even if holds. The same conclusion is reached for . To evaluate the weak randomness of and , the deviations is defined as
| 2 |
respectively. Here, define the amount of prior information known to Eve.
When the hidden variables and are given, the quantum state shared by Alice and Bob can be written as28
| 3 |
with
| 4 |
Here, , and is the probability that Eve performs different operators on the quantum state . These probabilities satisfy . I is the unity matrix, X and Z are Pauli matrices, and
In the following, we first discuss the case of SPS, then expand our results to WPS. In SPS, the total key rate is given by
| 5 |
The key rate for a given i, j is
| 6 |
where () is the bit error (phase error) of the given i, j. Because an experiment reveals only the total bit error , Eq. (5) can be rewritten as
| 7 |
Here is the total phase error, and the second inequality uses the Jensen inequality because H(x) is concave. Before obtaining the lower bound of the key rate, we should estimate the upper bound of . The authors of28 proved that for the density matrix given by Eq. (3), the upper bound of the phase error can be written as
| 8 |
where
| 9 |
The final key rate of a SPS (Eq. 7) is then rewritten as
| 10 |
In this expression, the superscript o distinguishes the original method from our proposed method, which is introduced later. Most practical QKD systems use a WPS. Following GLLP’s analysis31, the key rate of Eq. (5) is then written as
| 11 |
Here the subscript s denotes the key generated from the signal state with intensity s. () is the total gain (bit error) for a given i, j, and () is the yield (bit error) of the single photon pulse for the given i, j. The terms () and () are the total gain and error, respectively, for all i, j. is the efficiency of the error correction, which can be considered constant. In the third inequality, we recognize that and for all i, j. The gain and error in the equality can be directly measured in experiments, and the contributions of the single photon pulse ( and ) should be estimated by the decoy state method32–34.
Our method with one-step post processing
In this section, we show that the upper bound of the phase error (Eq. 8) is suboptimal, and that the key rate can be improved by imposing a tight bound. Given the density matrix (Eq. 3), the bit error rate and phase error rate are respectively written as
| 12 |
Here, , ,, are the four Bell states. Thus we have
| 13 |
where is defined in Eq. (9), and for all . Thus, the upper bound of the phase error can be written as
| 14 |
Submitting the above inequality into Eq. (5) and applying the method described in “Weak randomness and one-step post processing”, the final key rate is rewritten as
| 15 |
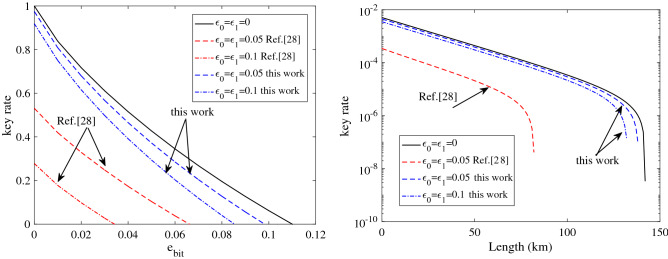
Figure 1 compares the numerical simulation results of the method in Ref.28 (Eqs. 10, 11) and our method (Eq. 15). Our method significantly improved the key rate for both SPS and WPS (the simulation method is given in “ Formulations of simulation”. For example, in the SPS case with , the maximal tolerable error rate was only 3.4% in the method of Ref.28, but was increased to 8.5% by our method. In the WPS case with , no secure key was generated by the method in Ref.28, but a final key of fiber length 132 km was generated by our method.
Figure 1.
Key rates in the original analysis28 (red lines) and the method proposed in this paper (blue lines). Results are plotted for SPS (left) and WPS (right). The black solid line is the result of the ideal case without basis-choice flaws. To simplify the simulation, we assume and infinite decoy states. The WPS case employs the experimental results of GYS31; thus, the signal state intensity is and the other parameters are set as follows: dark count rate , background error rate , fiber loss 0.21 dB/km, Bob’s transmittance , and error rate of optical devices . The method of Ref.28 generates no key in the case of WPS with .
To evaluate the security of practical QKD with weak randomness flaws, we test the performance of commercial BS which may suffer from the wavelength attack. The experimental scheme and results are given in “Formulations of simulation”, and the estimated key rate is listed in Table 1.
Table 1.
Key rates estimated by our method.
| T | |||||
|---|---|---|---|---|---|
| 0.0253 | 0.0235 | 0.0250 | 0.0274 | 0.0275 | |
| (SPS) | 0.0259 | 0.0239 | 0.0255 | 0.0281 | 0.0282 |
| (SPS) | 0.0521 | 0.0482 | 0.0514 | 0.0566 | 0.0567 |
| (SPS) | 0.1017 | 0.0941 | 0.1004 | 0.1105 | 0.1108 |
| (WPS) | 0.0445 | 0.0411 | 0.0438 | 0.0483 | 0.0484 |
| (WPS) | 0.0454 | 0.0420 | 0.0448 | 0.0493 | 0.0495 |
| (WPS) | 0.0548 | 0.0507 | 0.0541 | 0.0596 | 0.0597 |
Here defines the practical key rate () relative to the ideal key rate without basis-choice flaws (). In the simulations, we set , and the other parameters were those assumed in Fig. 1.
Biased base QKD protocol
In some practical QKD systems, two bases (Z and X) can deliver different gain or error rate performances. Therefore, to improve the total key rate, we let Alice and Bob observe bases Z and X, respectively. In this section, we analyze the security of biased base QKD with weak randomness. When Alice and Bob distill the key from their respective bases, the key rate becomes
| 16 |
Here and ( and ) are the bit error and phase error rates, respectively, in the rectilinear (diagonal) basis. Their values are given by
| 17 |
In these expressions, and ( and ) are the bit error rates in the rectilinear and diagonal bases, respectively, given a hidden variable (). and are the probabilities that Bob obtains the outcome in the rectilinear and diagonal bases, respectively. They are calculated as
| 18 |
respectively, where , , , and .
As the bit error rates and can be directly measured in experiments, we need only to estimate the upper bounds of the phase error rates and . Using Eq. (17), the phase error becomes
| 19 |
By the above method, we also obtain
| 20 |
Here we assume that the bit weak randomness in Z-basis is the same as that of X-basis, thus the same is used in the equations above. But, by considering in the bases respectively, our analysis is also valid for the QKD system with different bit weak randomness.Then Eq. (16) can then be written as
| 21 |
Applying the method above and GLLP’s analysis, the key rate given by Eq. (21) can be expanded to the WPS case as follows:
| 22 |
where () and () denote the total gain and bit error rate, respectively, in the rectilinear (diagonal) base, and () and () are the gain and bit error rate, respectively, of a single photon pulse in the rectilinear (diagonal) base.
Discussion
We evaluated the security of QKD with weak basis-choice flaws. The previous analysis of Li et al.28 was extended by applying a tight analytical bound for estimating the phase error. The final key rate was significantly improved by the proposed approach. For example, when and the bit error rate exceeded 3.4%, no final key was generated by the previous method, but a final key rate of 0.45 was achieved by our method. Applying our analysis, we evaluated the security of a practical QKD system in which Bob passively chooses his basis with a BS. In experiments using a practical BS with typical parameters, the key rate was reduced by less than 6%. Thus, the proposed method improves the QKD performance even in weak randomness scenarios.
Note that, although we analyze the weak randomness of basis-choice in this paper, there are other imperfections in source and detection. Thus, how to take all of these imperfections in one general mode is still an open question, and we will discuss it in our further works.
Methods
Formulations of simulation
This Appendix shows the simulation formulations of Fig. 1 and Table 1. In the absence of Eve, the total gain and error rate are respectively written as
| 23 |
Here, and are the intensities of the signal state (s) and decoy state (d), respectively, is the dark count of the single photon detector, and is the background error rate. is the total transmittance of the system, which is given by
| 24 |
In this expression, is the transmittance of Bob’s optical devices and the efficiency of single-photon detectors, and is the channel loss. In QKD with a weak coherent source, photon-number-dependent attacks (such as photon-number splitting attacks) must be removed by the decoy state method. Assuming that Alice and Bob use infinite decoy states, the gain and quantum bit error rate of a single photon pulse are respectively given by
| 25 |
Experiment
In some practical QKD systems, Bob passively chooses his measured basis with a BS. Because this scheme requires no active modulator, it enables high-speed, low-cost, and low-complexity operations. However, (as is well known) the transmittance of the BS may depend on the wavelength of the light, opening a potential loophole for wavelength attack by Eve16,17. In this section, we evaluate the performance of QKD with a passive BS by the above analysis.
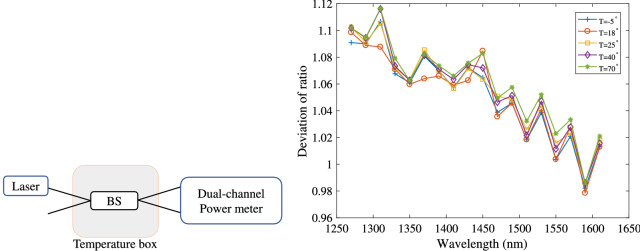
The experimental scheme is shown in the left panel of Fig. 2. The BS was encased in a temperature box that controlled its working temperature. The input of the BS was a tunable laser (model JW3113; province, country), and the light output was measured by a dual-channel power meter (model JW8103D, province, country). In a perfect BS, the measured power of both power meters is identical. The performance of a real BS is defined by its deviation ratio as follows:
| 26 |
Here, and are the powers of the light measured by the two optical power meters, T is the working temperature of the BS, and is the wavelength of the input light.
Figure 2.
Experimental scheme (left) and measured deviation ratio (right) of a practical commercial BS that evaluates the key rate under a weak measured basis flaw. The deviation ratio is determined by Eq. (26) and T is the working temperature of the BS, which is controlled by the temperature box.
The measured deviation ratio of the BS was measured at different wavelengths of the input light and different working temperatures. The results are shown in the right panel of Fig. 2. From the experimental results, the weak randomness in Bob’s basis-choice can be estimated as
| 27 |
The estimated key rates in the SPS and WPS cases are listed in Table 1 (see main text). At communication distances smaller than 100 km, the key rate was reduced by less than 6%. Topical subheadings are allowed. Authors must ensure that their “Methods” section includes adequate experimental and characterization data necessary for others in the field to reproduce their work.
Acknowledgements
The authors thank H.W. Li for helpful discussions on the simulation. This work was supported by the National Natural Science Foundation of China (NSFC) (11674397).
Author contributions
S.-H.S. and M.-S.Z. finish the theoretical analysis. Z.-Y.T. gets the simulation with the help of S.-H.S. Y.M. conducted the experiment. All authors reviewed the manuscript.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of IEEE International Conference on Computers, Systems, and Signal Processing (Bangalore, India), 175–179 (IEEE Press, New York, 1984).
- 2.Lo H-K, Chau HF. Unconditional security of quantum key distribution over arbitrarily long distances. Science. 1999;283:2050–2056. doi: 10.1126/science.283.5410.2050. [DOI] [PubMed] [Google Scholar]
- 3.Gottesman D, Lo H-K, Lütkenhaus N, Preskill J. Security of quantum key distribution with imperfect devices. Quantum Inf. Comput. 2004;4:325–360. [Google Scholar]
- 4.Lo H-K, Preskill J. Security of quantum key distribution using weak coherent states with nonrandom phases. Quantum Inf. Comput. 2007;7:431–458. [Google Scholar]
- 5.Tang Y, et al. Measurement-device-independent quantum key distribution over 200 km. Phys. Rev. Lett. 2014;113:190501. doi: 10.1103/PhysRevLett.113.190501. [DOI] [PubMed] [Google Scholar]
- 6.Yin H-L, et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 2016;117:190501. doi: 10.1103/PhysRevLett.117.190501. [DOI] [PubMed] [Google Scholar]
- 7.Schmitt-Manderbach T, et al. Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Phys. Rev. Lett. 2007;98:010504. doi: 10.1103/PhysRevLett.98.010504. [DOI] [PubMed] [Google Scholar]
- 8.Liao S-K, et al. Long-distance free-space quantum key distribution in daylight towards inter-satellite communication. Nat. Photon. 2017;11:509–513. doi: 10.1038/nphoton.2017.116. [DOI] [Google Scholar]
- 9.Liao S-K, et al. Satellite-to-ground quantum key distribution. Nature. 2017;549:43. doi: 10.1038/nature23655. [DOI] [PubMed] [Google Scholar]
- 10.Liao SK, et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett. 2018;120:030501. doi: 10.1103/PhysRevLett.120.030501. [DOI] [PubMed] [Google Scholar]
- 11.Elliott, C. et al. Current status of the darpa quantum network (2005). arXiv:quant-ph/0503058.
- 12.Peev M, et al. The SECOQC quantum key distribution network in Vienna. New J. Phys. 2009;11:075001. doi: 10.1088/1367-2630/11/7/075001. [DOI] [Google Scholar]
- 13.Sasaki M, et al. Field test of quantum key distribution in the Tokyo QKD Network. Opt. Express. 2011;19:10387–10409. doi: 10.1364/OE.19.010387. [DOI] [PubMed] [Google Scholar]
- 14.Zhang Q, Xu FH, Chen YA, Peng CZ, Pan J. Large scale quantum key distribution: Challenges and solutions [invited] Opt. Express. 2018;26:24260–24273. doi: 10.1364/OE.26.024260. [DOI] [PubMed] [Google Scholar]
- 15.Lydersen L, et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photon. 2010;4:686–689. doi: 10.1038/nphoton.2010.214. [DOI] [Google Scholar]
- 16.Li H-W, et al. Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A. 2011;84:062308. doi: 10.1103/PhysRevA.84.062308. [DOI] [Google Scholar]
- 17.Ma XC, Sun SH, Jiang MS, Liang LM. Wavelength attack on practical continuous-variable quantum key distribution system with a heterodyne protocol. Phys. Rev. A. 2013;87:052309. doi: 10.1103/PhysRevA.87.052309. [DOI] [Google Scholar]
- 18.Tang Y-L, et al. Source attack of decoy-state quantum key distribution using phase information. Phys. Rev. A. 2013;88:022308. doi: 10.1103/PhysRevA.88.022308. [DOI] [Google Scholar]
- 19.Sun S-H, et al. Effect of source tampering in the security of quantum cryptography. Phys. Rev. A. 2015;92:022304. doi: 10.1103/PhysRevA.92.022304. [DOI] [Google Scholar]
- 20.Fung C-HF, Qi B, Tamaki K, Lo H-K. Phase-remapping attack in practical quantum-key-distribution systems. Phys. Rev. A. 2007;75:032314. doi: 10.1103/PhysRevA.75.032314. [DOI] [Google Scholar]
- 21.Xu F, Qi B, Lo H-K. Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 2010;12:113026. doi: 10.1088/1367-2630/12/11/113026. [DOI] [Google Scholar]
- 22.Acín A, et al. Device-independent security of quantum cryptography against collective attacks. Phys. Rev. Lett. 2007;98:230501. doi: 10.1103/PhysRevLett.98.230501. [DOI] [PubMed] [Google Scholar]
- 23.Pironio S, et al. Device-independent quantum key distribution secure against collective attacks. New J. Phys. 2009;11:045021. doi: 10.1088/1367-2630/11/4/045021. [DOI] [Google Scholar]
- 24.Lo H-K, Curty M, Qi B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012;108:130503. doi: 10.1103/PhysRevLett.108.130503. [DOI] [PubMed] [Google Scholar]
- 25.Ma XF, Razavi M. Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A. 2012;86:062319. doi: 10.1103/PhysRevA.86.062319. [DOI] [Google Scholar]
- 26.Zhou Y-H, Yu Z-W, Wang X-B. Making the decoy-state measurement-device-independent quantum key distribution practically useful. Phys. Rev. A. 2016;93:042324. doi: 10.1103/PhysRevA.93.042324. [DOI] [Google Scholar]
- 27.Pawłowski M, Brunner N. Semi-device-independent security of one-way quantum key distribution. Phys. Rev. A. 2011;84:010302. doi: 10.1103/PhysRevA.84.010302. [DOI] [Google Scholar]
- 28.Li HW, et al. Randomness determines practical security of bb84 quantum key distribution. Sci. Rep. 2015;5:16200. doi: 10.1038/srep16200. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29.Li HW, Xu ZM, Cai QY. Small imperfect randomness restricts security of quantum key distribution. Phys. Rev. A. 2018;98:062325. doi: 10.1103/PhysRevA.98.062325. [DOI] [Google Scholar]
- 30.Zhang CM, Wang WB, Li HW, Wang Q. Weak randomness impacts the security of reference-frame-independent quantum key distribution. Opt. Lett. 2019;44:1226. doi: 10.1364/OL.44.001226. [DOI] [PubMed] [Google Scholar]
- 31.Gobby C, Yuan ZL, Shields AJ. Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 2004;84:3762–3764. doi: 10.1063/1.1738173. [DOI] [Google Scholar]
- 32.Hwang W-Y. Quantum key distribution with high loss: Toward global secure communication. Phys. Rev. Lett. 2003;91:057901. doi: 10.1103/PhysRevLett.91.057901. [DOI] [PubMed] [Google Scholar]
- 33.Lo H-K, Ma X, Chen K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005;94:230504. doi: 10.1103/PhysRevLett.94.230504. [DOI] [PubMed] [Google Scholar]
- 34.Wang X-B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 2005;94:230503. doi: 10.1103/PhysRevLett.94.230503. [DOI] [PubMed] [Google Scholar]