Abstract
Meta-holographic encryption is a potentially important technique for information security. Despite rapid progresses in multi-tasked meta-holograms, the number of information channels available in metasurfaces is limited, making meta-holographic encryption vulnerable to some attacking algorithms. Herein, we demonstrate a re-programmable metasurface that can produce arbitrary holographic images for optical encryption. The encrypted information is divided into two matrices. These two matrices are imposed to the incident light and the metasurface, respectively. While the all-dielectric metasurface is static, the phase matrix of incident light provides additional degrees of freedom to precisely control the eventual functions at will. With a single Si metasurface, arbitrary holographic images and videos have been transported and decrypted. We hope that this work paves a more promising way to optical information encryption and authentication.
Subject terms: Applied optics, Metamaterials
Here, the authors demonstrate a re-programmable metasurface that can produce arbitrary holographic images for optical encryption. The encrypted information is divided into two matrices and defined to the incident laser to produce arbitrary holographic images.
Introduction
In modern society, almost everything is closely related to the internet currently or in the near future. The recent reports of attacks by hackers on the databases show that the information security and authentication are more challenging, especially for the large commercial and financial companies1. In past decade, many types of optical encryption techniques based on classic and quantum optics have been developed to achieve reliable security of information2,3. Owing to its compact and non-replicable nature, metasurface-based hologram has gradually been a promising approach4–10. Metasurface is a kind of two-dimensional materials that has the capability of precisely and fully controlling the incident light11. By carefully designing the response of each antenna to different polarization, incident angle, wavelength, or orbital angular momentum (OAM), multiple holographic images have been successfully implemented into a single metasurface in the past few years, significantly expanding the capacity and security of information encryption7,12–19. Despite of these progresses, the demonstrated meta-holograms are either static or binary4–20. While different multiplexing techniques based on spatial, polarization, wavelength, and OAM have been combined recently, the number of information channels is still finite and the current record value is only ~26 (refs. 7,15–26). Similar to the double-random-phase encryption technique, the finite channel number makes the meta-holographic encryption vulnerable to certain attacks because the key for decryption has to be used repeatedly without frequent update27. Therefore, from the point view of information security, it is highly desirable and urgent to realize a meta-hologram with infinite channels and higher security. Here, we revisit the light–metasurface interaction and experimentally demonstrate a reprogrammable meta-hologram for optical security and authentication.
Results
Working principle
In principle, the interaction between light and metasurface can be expressed as28:
| 1 |
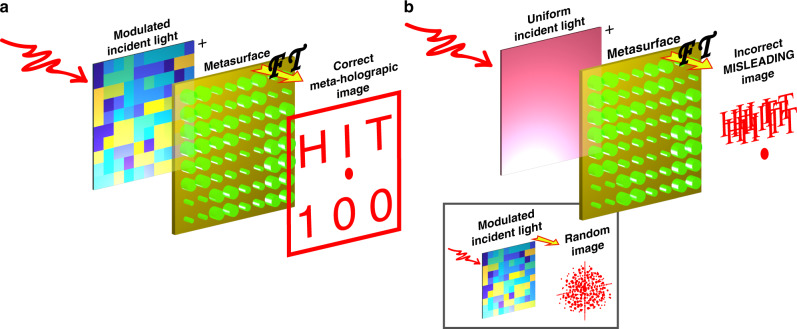
where Uinc(x0, y0) and Umeta(x0, y0) correspond to the functions of incident light and metasurface, h(x, y, z) is an impulse response. The conventional approaches are mostly focusing on the response of nanoantennas in metasurface4–19. Only few parameters of the incident light have been considered, e.g., polarization and OAM etc.7,15–26. Since the metasurface is typically static, the information channel is thus determined by the degrees of incident light and is strongly limited7,15–26. In this research, we divide the required phase profile of a holographic image into two matrices. One matrix is imposed to the metasurface (Umeta(x0, y0)) as before, the other one is defined on the incident beam (Uinc(x0, y0)). This assumption is not only valid for algorithm but also consistent with the modern optical security system, which consists of light source, lens, detectors, phase only masks, and spatial light modulators (SLMs) etc.29,30. On one hand, the two-dimensional matrix of incident beam can significantly expand the number of information channels. Even though the metasurface is static, the large matrix of incident beam still has enough large parameters to alter the output beam (U(x, y, z)) and the corresponding holographic images. On the other hand, the split information in transported light and metasurface can improve the security. The codes for the modulation of incident light is transported through the internet, whereas the metasurface can be implemented into the terminal decrypted devices. In case that the transported codes are cracked, they can only produce a random beam without any useful information (see inset in Fig. 1b). If the metasurface is stolen and illuminated with an incorrect beam, no information can be hacked or a misleading image could be shown up (Fig. 1b). Only when the modulated incident light matches the metasurface, as shown in Fig. 1a, the encrypted image can be displayed. According to Eq. (1), for encrypted information with fixed overall matrix, the matrices for the incident light and the metasurface can be separated arbitrarily. Consequently, the roles of two matrices can be interchanged and the flexibility of the system has been dramatically increased (see Supplementary Fig. 2).
Fig. 1. The working principle of reprogrammable meta-hologram.
a The schematic of the meta-holographic image with the modulated incident beam. b The holographic image of metasurface when it is illuminated with an incorrect uniform laser beam. The inset shows that the incident beam itself cannot provide correct information.
Experiments
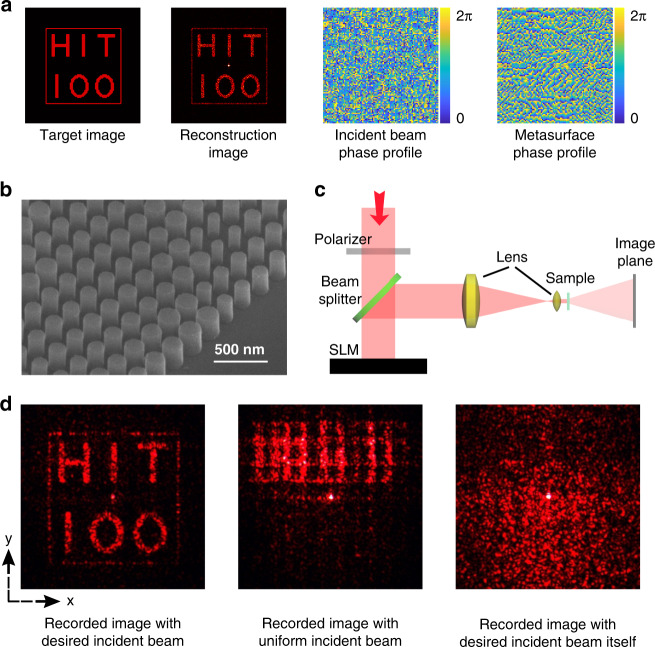
To test the above analysis, we have numerically designed the reprogrammable meta-hologram31,32. Taking an image of “HIT 100 (100th anniversary of Harbin Institute of Technology)”as an example, the required phase profile for a holographic image has been calculated based on Gerchberg–Saxton algorithm. After considering both of the efficiency and the fabrication difficulty, the continuous phase profile is discretized into eight-level phase steps (Supplementary Fig. 3). Then the discretized matrix is separated into two matrices, which are imposed on the incident beam and the nanoantennas of Si metasurface, respectively (Fig. 2a). The phase profile of incident light is controlled by a SLM (UPOLabs-HDSLM80R). The phase only metasurface is fabricated with standard silicon on sapphire wafer via a combined process of electron-beam lithography and reactive ion etching (Supplementary Notes 1–3)32. Figure 2b shows the top-view scanning electron microscope (SEM) image of the metasurface. It is composed as Si nanopillars with different radius R. The height of Si nanopillar is fixed at 230 nm. In Fig. 2b, eight types of nanopillars with R = 44, 58, 64, 68, 73, 78, 85, and 95 nm are employed to provide relative high transmittance, and abrupt phases from 0 to 7π/4, simultaneously (Supplementary Notes 1–3). In this experiment, each phase pixel of Si metasurface in Fig. 2b consists of multiple nanopillars with the same size. This setting is designed to fit the pixel size of Si metasurface and the matrix size of incident light.
Fig. 2. The experimental demonstration of meta-hologram.
a The designed image, the simulated holographic image, and two separated phase profiles. b The top-view SEM of the Si metasurface. c Schematic for capturing the meta-hologram. d The recorded meta-holographic images with the designed incident beam (left), with a uniform laser beam (middle), and the image of incident laser itself (right). Here the lattice size is L = 240 nm.
The Si metasurface is optically characterized with the setup in Fig. 2c. Basically, the linearly polarized laser is generated with a He–Ne laser (633 nm) and a linear polarizer. The light is modulated by the SLM before it is focused onto the sample via a 4f system. The transmitted hologram is projected onto a screen in the far field and captured with a CCD camera (see the “Methods” section). Figure 2d shows the image of intensity distribution generated by the metasurface. Similar to the numerical calculation, a “HIT 100” image has been experimentally produced when the Si metasurface is illuminated by the laser beam with the designed phase profile. The calibrated conversion efficiency of the meta-hologram is ~67% (Supplementary Fig. 8). For a direct comparison, the same Si metasurface has also been illuminated with a uniform laser beam. As depicted in the middle panel of Fig. 2d, a misleading pattern with incorrect information is achieved. Similar encryption also holds true for the light source only. The modulated laser beam itself is also an uniform laser spot with speckles instead of the designed information (right panel in Fig. 2d).
The above experiments show that the encrypted information can be protected even though the key or the metasurface was stolen. For a better demonstration, the vulnerability of the optical encryption scheme has also been tested with a different key mismatch ratio. Figure 3 summarizes the experimental results as a function of the modification on incident beam. It is clear to see that the meta-holographic image becomes blurry when the mismatch ratio is >10%. In case of the mismatch ratio exceeds 40%, the “HIT 100” image is close to the noise level and hard to be identified. This means that the eavesdropper has to steal ~60% of the incident matrix and the terminal devices, simultaneously to barely recover the encrypted information. This is even higher than the recently demonstrated metasurface-based ghost imaging algorithm8. Note that the above case is valid for the situation that both of the initial positions ((0,0) point of two matrices and the longitudinal deviation from the focal point) and pixel sizes are known, and matched one another. Without the above information, it shall consume orders of magnitude longer time to randomly test the right key for decryption (Supplementary Figs. 6 and 7).
Fig. 3. The vulnerable test of the meta-hologram.
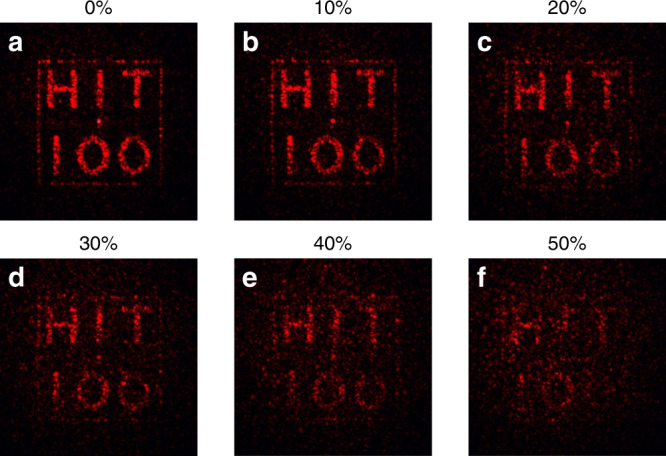
From a–f, the mismatch ratio of the incident light increases from 0 to 50% with a step of 10%.
In principle, the right key for decryption can still be hacked if the random test time is infinitely long27. To avoid the potential attack, the key must be updated frequently. As a result, the reprogrammable metasurface is highly desirable for the applications of optical encryption. According to Eq. (1), even though Umeta(x0, y0) is fixed and known, the displayed holographic image U(x, y, z) can still be changed by controlling the incident light Uinc(x0, y0). Then the meta-hologram becomes all-optically controllable. In this sense, although the terminal hardware, such as Si metasurfaces are hard to be tuned in pixel level, the precise control of the incident beam can still frequently update the keys for decryption. Figure 4 summarizes the experimental demonstration of the all-optically reprogrammable meta-hologram. In this experiment, the Si metasurface is kept as the same one as Fig. 2b. By only modifying the phase distributions of the incident light, the displayed holographic image becomes an image of hydrogen element “H”, which is totally different from the image of “HIT 100” in Fig. 2. With the further modification on incident light, the displayed hologram can be switched to an image of hydrogen element or any other elements. With the continuous change of incident light, we have experimentally realized the holographic images of the entire periodic table of the elements, with 118 types of elements. Here, each element is an individual holographic image produced by the same metasurface. The periodic table of elements is a clear demonstration of the programmable and all-optically controllable meta-hologram.
Fig. 4. The reprogrammable meta-hologram.
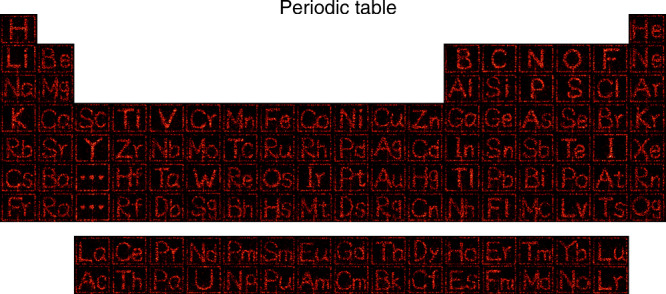
The holographic images of periodic element table. Each element in this table is one holographic image that is generated with the same metasurface in Fig. 2.
We note that the number of periodic element table is not the limit of the information channel of our design. With the same Si metasurface, we basically can realize arbitrarily shaped holographic images, including the holographic image with complicated contents (Supplementary Fig. 10). To verify this possibility, we have also produced a set of holographic images by modulating the incident beam and plotted them in Supplementary Fig. 11. Each panel corresponds to one frame of a pinball classic game. By playing these frames sequentially, a video of the pinball game from start to the end has also been achieved (Supplementary Movie 1). These results further demonstrate the potential of the proposed technique in the transportation of videos as well, significantly expanding the potential applications of metasurface holograms.
Discussion
In summary, we have revisited the light–metasurface interaction and experimentally realized the reprogrammable meta-hologram. By separating the designed phase profile to two matrices, and defining them to incident laser and metasurface, we find that the lack of pixel-level control of metasurface in optical frequency range can be made up via the all-optical control. With the phase control of incident beam, we have experimentally demonstrated that a single metasurface can display arbitrary holographic images, as well as encrypted videos. This technique shall find its applications in information security and authentication. It also paves a promising step toward dynamic displays as well.
Methods
The numerical simulation
The silicon metasurface was numerically simulated with a commercial software COMSOL Multiphysics. The Si nanorods are placed on a sapphire substrate with refractive indices of 3.88 and 1.76 at 633 nm. The height of nanorod was kept at 230 nm. The radius of nanorod and the lattice size are R and L, respectively. Periodic boundary conditions were applied in horizontal direction to mimic the periodic structure, and perfectly matched layers were used to absorb the transmission and reflection waves. The details are shown in Supplementary Notes 1 and 2.
The fabrication of Si metasurface
The Si metasurfaces were fabricated by a combined process of electron-beam lithography and reactive ion etching. The 230 nm single-crystal silicon film on a sapphire wafer was cleaned with acetone and coated with 100 nm electron-beam resist polymethyl methacrylate. The sample was baked at 180 °C for 1 h and then patterned by electron-beam writer (Raith E-line) with a dose 90 µC/cm2 under an acceleration voltage 30 kV. After developing with MIBK&IPA (1:3) solution, 15 nm Cr was deposited on the sample using E-beam evaporation (SKE_A_75), and Cr hard mask was realized via a liftoff process in remover PG solution (Micro Chem) for 24 h. The pattern was transferred to the Si through reactive ion etching with SF6 and CHF3 in Oxford Plasmalab System 100. The vacuum degree was 10−5 and the gas flow was 5 and 50 sccm for SF6 and CHF3, respectively. Finally, the Si metasurfaces were obtained by removing the Cr mask in Cr etchant solution (Aldrich Chemistry) for 30 min.
The optical characterization
During the optical characterization, the alignment of the phases in incident beam the phases in metasurface is crucial. The light is modulated by the SLM before it is focused onto the sample via a 4f system. The transmitted hologram is projected onto a screen in the far field and captured with a CCD camera. The SLM is switched to intensity module to clearly seen the focused beam, and precisely match it with the metasurface. Then it is switched back to phase module and measure the meta-hologram.
Supplementary information
Description of Additional Supplementary Files
Acknowledgements
This research was supported by the National Key Research and Development Project (Grant No. 2018YFB2200403), National Natural Science Foundation of China (Grant Nos. 11974092, 91850204, 11934012, and 61975041), Shenzhen Fundamental research projects (Grant No. JCYJ20180507184613841, JCYJ20180507183532343, and JCYJ20180306172041577), Shenzhen engineering laboratory on organic–inorganic perovskite devices, and the Fundamental Research Funds for the Central Universities. The authors also acknowledge financial support from Shenzhen Science and Technology Innovation Commission (No. SGDX2019081623281169). The authors are grateful to the Department of Electronic and Information Engineering, The Hong Kong Polytechnic University for their support as well.
Author contributions
S.X. and D.P.T. conceived the idea and supervise the research. G.Q. performed the device designs and experimental measurements. W.Y. and Y.L. helped the fabrication of nanostructures. Q.S., C.-W.Q. and J.H. analyzed the results. All the authors discussed the contents and prepared the manuscript.
Data availability
The data that support the findings of this study are available on request from the corresponding authors.
Competing interests
The authors declare no competing interests.
Footnotes
Peer review information Nature Communications thanks Juan Liu and the other, anonymous, reviewer(s) for their contribution to the peer review of this work.
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
These authors jointly supervised this work: Din-Ping Tsai, Shumin Xiao.
Contributor Information
Din-Ping Tsai, Email: dinping.tsai@polyu.edu.hk.
Shumin Xiao, Email: shumin.xiao@hit.edu.cn.
Supplementary information
Supplementary information is available for this paper at 10.1038/s41467-020-19312-9.
References
- 1.Check point research. Cyber Attach Trends: 2020 Mid-year Reporthttps://research.checkpoint.com/2020/cyber-attack-trends-2020-mid-year-report/ (2020).
- 2.Refregier P, Javidi B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995;20:767–769. doi: 10.1364/OL.20.000767. [DOI] [PubMed] [Google Scholar]
- 3.Unnikrishnan G, Joseph J, Singh K. Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 2000;25:887–889. doi: 10.1364/OL.25.000887. [DOI] [PubMed] [Google Scholar]
- 4.Ni X, Kildishev AV, Shalaev VM. Metasurface holograms for visible light. Nat. Commun. 2013;4:2807. doi: 10.1038/ncomms3807. [DOI] [Google Scholar]
- 5.Zheng G, et al. Metasurface holograms reaching 80% efficiency. Nat. Nanotechnol. 2015;10:308–312. doi: 10.1038/nnano.2015.2. [DOI] [PubMed] [Google Scholar]
- 6.Chen WT, et al. High-efficiency broadband meta-hologram with polarization-controlled dual images. Nano Lett. 2014;14:225–230. doi: 10.1021/nl403811d. [DOI] [PubMed] [Google Scholar]
- 7.Wen D, et al. Helicity multiplexed broadband metasurface holograms. Nat. Commun. 2015;6:8241. doi: 10.1038/ncomms9241. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Liu HC, et al. Single-pixel computational ghost imaging with helicity-dependent metasurface hologram. Sci. Adv. 2017;3:e1701477. doi: 10.1126/sciadv.1701477. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Gao LH, et al. Broadband diffusion of terahertz waves by multi-bit coding metasurfaces. Light Sci. Appl. 2015;4:e324. doi: 10.1038/lsa.2015.97. [DOI] [Google Scholar]
- 10.Yoon G, Lee D, Nam KT, Rho J. Pragmatic metasurface hologram at visible wavelength: the balance between diffraction efficiency and fabrication compatibility. ACS Photon. 2018;5:1643–1647. doi: 10.1021/acsphotonics.7b01044. [DOI] [Google Scholar]
- 11.Yu N, et al. Light Propagation with phase discontinuities: generalized laws of reflection and refraction. Science. 2011;334:333–337. doi: 10.1126/science.1210713. [DOI] [PubMed] [Google Scholar]
- 12.Cui TJ, Qi MQ, Wan X, Zhao J, Cheng Q. Coding metamaterials, digital metamaterials and programmable metamaterials. Light Sci. Appl. 2014;3:e218. doi: 10.1038/lsa.2014.99. [DOI] [Google Scholar]
- 13.Li J, et al. Addressable metasurfaces for dynamic holography and optical information encryption. Sci. Adv. 2018;4:eaar6768. doi: 10.1126/sciadv.aar6768. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Li L, et al. Electromagnetic reprogrammable coding-metasurface holograms. Nat. Commun. 2017;8:197. doi: 10.1038/s41467-017-00164-9. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Ye W, et al. Spin and wavelength multiplexed nonlinear metasurface holography. Nat. Commun. 2016;7:11930. doi: 10.1038/ncomms11930. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Huang L, et al. Broadband hybrid holographic multiplexing with geometric metasurfaces. Adv. Mater. 2015;27:6444–6449. doi: 10.1002/adma.201502541. [DOI] [PubMed] [Google Scholar]
- 17.Yue Z, Ren H, Wei S, Lin J, Gu M. Angular-momentum nanometrology in an ultrathin plasmonic topological insulator film. Nat. Commun. 2018;9:4413. doi: 10.1038/s41467-018-06952-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Xu HX, et al. Interference-assisted kaleidoscopic meta-plexer for arbitrary spin-wavefront manipulation. Light Sci. Appl. 2019;8:3. doi: 10.1038/s41377-018-0113-y. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 19.Li L, et al. Machine-learning reprogrammable metasurface imager. Nat. Commun. 2019;10:1082. doi: 10.1038/s41467-019-09103-2. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Zhang L, et al. Ultrabroadband design for linear polarization conversion and asymmetric transmission crossing X- and K-band. Sci. Rep. 2016;6:33826. doi: 10.1038/srep33826. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21.Liu M, et al. Temperature-controlled asymmetric transmission of electromagnetic waves. Sci. Rep. 2019;9:4097. doi: 10.1038/s41598-019-40791-4. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 22.Khalid AUR, et al. Multipurpose thermoresponsive hydrogel: a platform for dynamic holographic display. Opt. Lett. 2020;45:479–482. doi: 10.1364/OL.383567. [DOI] [Google Scholar]
- 23.Chen L, Ruan Y, Cui HY. Liquid metal metasurface for flexible beam-steering. Opt. Express. 2019;27:23282–23292. doi: 10.1364/OE.27.023282. [DOI] [PubMed] [Google Scholar]
- 24.Khalid AUR, Liu J, Ullah N, Jia S. Tunable beam deflection based on plasmonic resonators mounted freestanding thermoresponsive hydrogel. Chin. Opt. Lett. 2020;18:062402. doi: 10.3788/COL202018.062402. [DOI] [Google Scholar]
- 25.Jin L, et al. Noninterleaved metasurface for (26-1) Spin- and wavelength-encoded holograms. Nano Lett. 2018;18:8016–8024. doi: 10.1021/acs.nanolett.8b04246. [DOI] [PubMed] [Google Scholar]
- 26.Fang X, Ren H, Gu M. Orbital angular momentum holography for high-security encryption. Nat. Photon. 2019;14:102–108. doi: 10.1038/s41566-019-0560-x. [DOI] [Google Scholar]
- 27.Peng X, Zhang P, Wei H, Yu B. Known-plaintext attack on optical encryption based on double random phase keys. Opt. Lett. 2006;31:1044–1046. doi: 10.1364/OL.31.001044. [DOI] [PubMed] [Google Scholar]
- 28.Jin L, et al. Dielectric multi-momentum meta-transformer in the visible. Nat. Commun. 2019;10:4789. doi: 10.1038/s41467-019-12637-0. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29.Matoba O, Javidi B. Optical retrieval of encrypted digital holograms for secure real-time display. Opt. Lett. 2002;27:321–323. doi: 10.1364/OL.27.000321. [DOI] [PubMed] [Google Scholar]
- 30.Javidi B, Nomura T. Securing information by use of digital holography. Opt. Lett. 2000;25:28–30. doi: 10.1364/OL.25.000028. [DOI] [PubMed] [Google Scholar]
- 31.Zhang C, et al. Dynamic perovskite metasurfaces: lead halide perovskite-based dynamic metasurfaces. Laser Photon. Rev. 2019;13:1900079. doi: 10.1002/lpor.201900079. [DOI] [Google Scholar]
- 32.Gao Y, et al. Nonlinear holographic all-dielectric metasurfaces. Nano Lett. 2018;18:8054–8061. doi: 10.1021/acs.nanolett.8b04311. [DOI] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Description of Additional Supplementary Files
Data Availability Statement
The data that support the findings of this study are available on request from the corresponding authors.