Abstract
Recent growth in the Internet of Things (IoT) has raised security concerns over the confidentiality of data exchanged between IoT devices and the edge. Many IoT systems adopt asymmetric cryptography to secure their data and communications. A drawback of asymmetric cryptography is the sizeable computation and space requirements. However, elliptic curve cryptography (ECC) is widely used in constrained environments for asymmetric cryptography due its superiority in generating a powerful encryption mechanism with small key sizes. ECC increases device performance and lowers power consumption, meaning it is suitable for diverse applications ranging from the IoT to wireless sensor network (WSN) devices. To ensure the confidentiality and security of data and communications, it is necessary to implement ECC robustly. A special area of focus in this regard is the mapping phase. This study’s objective was to propose a tested and trusted scheme that offers authenticated encryption (AE) via enhancing the mapping phase of a plain text to an elliptic curve to resist several encryption attacks such as Chosen Plaintext Attack (CPA) and Chosen Ciphertext Attack (CCA). The proposed scheme also undertakes evaluation and analysis related to security requirements for specific encryption attributes. Finally, results from a comparison of the proposed scheme and other schemes are presented, evaluating each one’s security characteristics and performance measurements. Our scheme is efficient in a way that makes so suitable to the IoT, and in particular to the Industrial IoT and the new Urbanization where the demands for services are huge.
Keywords: authenticated encryption, asymmetric cryptography, chosen cipher text attack, chosen plain text attack, edge computing, elliptic curve cryptography, encryption, internet of things, industrial internet of things
1. Introduction
The continuous growth of industrialization and urbanization in recent years has led to the estimate that by 2025 there will be 21.5 billion actively connected Internet of Things (IoT) devices worldwide [1] as depicted in Figure 1. This remarkable growth of IoT shows that edge computing is increasingly used in today’s society [2]. In particular, the constrained properties of IoT devices, which include low performance in terms of computational resources and storage space, led to the adoption of edge computing [3]. For these reasons, the need to maintain data confidentiality and integrity has increased, which has caused an explosion of interest in cryptography schemes [4]. There are two types of encryption scheme, which are based on the nature of the key that will be used to encrypt and decrypt the data: which known as, symmetric cryptography and asymmetric cryptography [5]. The first type uses a one key for encryption and decryption, and it is useful if the two parties know the key before exchanging data. However, if the sender and the recipient cannot agree on a secure secret key exchange, then asymmetric cryptography is needed. In asymmetric cryptography, elliptic curve cryptography (ECC) is known for its superiority in producing a powerful encryption mechanism with small key sizes [6]. Therefore, ECC plays a valuable role in securing communications in constrained and resource-limited environments, including the IoT and wireless sensor networks (WSNs) [7].
Figure 1.
New technologies raised by the growth of industrialization and urbanization.
1.1. Encryption Attacks on Asymmetric Cryptography
Information security consists of three aspects: confidentiality, integrity, and availability (CIA) [8,9,10]. Confidentiality and integrity are assured via cryptography schemes. One such scheme is asymmetric cryptography, which uses two key types: a public key and a private key [11]. The public key is used by the sender to encrypt the plain text, which gives it its name. This key is publicly available for use by anyone. By contrast, the recipient uses the private key to decrypt the received cipher text, which means that it must be known only by the recipient.
Asymmetric cryptography settles the dilemma of securing a shared key between two parties. At the same time, however, asymmetric cryptography suffers from a drawback in the key sizes used to encrypt and decrypt messages. Larger key sizes correspond to larger computation overheads for encrypting and decrypting plain text. However, ECC provides the same level of security as the Rivest–Shamir–Adleman (RSA) algorithm with short keys [12]. Therefore, ECC has emerged as the preferred approach for solving key size issues and for maintaining performance in constrained environments [13].
Many known attacks weaken existing cryptography schemes. They exploit vulnerabilities in the encryption process. For instance, the Known Plain Text Attack (KPA), Chosen Plain Text Attack (CPA), Cipher Text Only Attack (COA), and several types of Chosen Cipher Text Attack (CCA) have been identified. The KPA occurs when an attacker obtains a plain text and its corresponding cipher text. Specifically, the attacker attempts to obtain the encryption key [14]. The CPA occurs when an attacker selects random plain texts and requests the corresponding cipher texts for each text. Thus, the attacker aims to reduce the security of the scheme by analyzing both the plain text and cipher text [15]. In COA, the assumption is made that an attacker only has access to a set of cipher texts, where they can extract the secret key and/or the plain text [16]. The final attack, the CCA, involves the attacker gaining information by obtaining a sample of decrypted cipher texts of his/her choice [17].
In this research, the following attacks are used for the security analysis phase, denoted as [18]:
IND-CPA: Indistinguishable under chosen plain text attack
IND-CCA: Indistinguishable under chosen cipher text attack
1.2. Elliptic Curve Cryptography
The first curve used in elliptic curve cryptography (ECC) was introduced by Koblitz in 1987 [19]. ECC is widely used for devices in constrained environments, including the IoT and WSN devices. This stems from ECC’s value in affording the same level of hardness in terms of encryption as other asymmetric cryptography schemes, with significantly smaller key sizes and a lower computation overhead. As an illustration, the complexity of encryption in the RSA algorithm with a 1024-bit key is the same as the ECC algorithm with a 160-bit key. This noticeable difference in key sizes reduces the requirement for computation, and it lowers the storage needed to perform encryption. As a result, ECC supports low computation device capabilities, enabling them to perform more effectively [20]. ECC applications vary in the ways keys are exchanged between senders and recipients, as well as the approach used to secure communications between the two parties. In addition, ECC maintains message integrity by signing plain texts to prevent forgery.
The elliptic curve group operations are denoted as “+” for the addition of two points. For instance, let and , Therefore, the addition of can be expressed as . In some cases, where , the group operation is denoted as multiplication on elliptic curve over that satisfy Equation (1), such that and where is an integer value. For instance, , similarly, is equal to , and so on. It is important to note the the EC must be nonsingular curves (i.e., have no multiples roots).
| (1) |
The main operation in elliptic curves is the group multiplication operation [21,22,23,24]. For , this refers to d times of the addition of point P, which results in a new point . The private key is a large integer d, and the value of the multiplication operation is known as the public key. The hardness of ECC is caused by the hardness of the mathematical problem, which states that, by knowing the public key point and the starting point P, it is not possible to compute d in polynomial time [25]. This hardness is known in the literature as the elliptic curve discrete logarithm problem (ECDLP).
Several phases are involved in ECC to secure communications and encrypt transmitted data [26,27,28]. These phases are used together and/or separately, and they are listed as follows:
Initializing system parameters
Converting text values to numerical values
Mapping numerical values to the elliptic curve
Encrypting mapped points
Hashing the message (for signing)
Similarly, the decryption phases are listed below:
Verifying integrity of received message (signature verification)
Decrypting cipher text
Decoding mapped points to numerical values
Converting numerical values to text values to represent plain text
The main computation process involved in the first phase is the calculation of the public keys derived by the multiplication of d (i.e., the private key) and G (i.e., the base point) [29,30,31,32]. The following phase involves the conversion of the plain text into numerical values, which is required because ECC depends on the use of numbers [33]. Therefore, the text must be securely converted in order to resist encryption attacks. Similarly, the third phase involves mapping the encoded value to the generated elliptic curve to find corresponding value of such that . If the mapping process fails in the first round, then is incremented by 1 until mapping is successful [34,35,36,37]. In the encryption phase, the cipher text is combined with the mapped point and secret key point . The fifth phase maintains the integrity of the cipher text and ensures the sender’s nonrepudiation [38,39,40]. This is achieved by signing the cipher text using the sender’s signature, and it depends on the following steps [41,42,43]:
Compute r, s.t. r is the of , where k is a random number and G is a base point
Compute and obtain
Compute s, where , and where d is the sender’s private key
The sent message is
Having provided an introductory overview, the rest of this paper is organized as follows: a literature review of other schemes is provided in Section 2; in Section 3, the details of the proposed scheme are described; in Section 4, security analysis and performance evaluations are presented in detail; and finally, concluding remarks and future research are discussed in Section 5.
2. Related Works
Elliptic curve cryptography (ECC) is frequently used to reduce the computational overhead caused by the limited capabilities of devices in constrained environments. Many schemes use ECC to secure communications between two parties by safeguarding the shared key exchange process. In particular, the elliptic curve integrated encryption scheme (ECIES) first employed the asymmetric approach by generating the shared key between two parties using ECC, after which the plain text was encrypted using the symmetric approach under the AES scheme [44,45,46,47]. On the other hand, many of these schemes failed to provide detail on how ECC was used to secure the plain text and/or how they were encoded into numerical values for use in ECC’s mapping phase.
Various proposed systems have enhanced key elements of the encryption process in ECC, but gaps have been identified in the literature. For instance, schemes proposed in [48,49,50] employ ECC without providing sufficient detail about how the plain text was encoded and mapped onto an elliptic curve. Therefore, enhancing these schemes tended to focus on performance rather than security. Similarly, [51,52,53] provided efficient algorithms for scalar multiplication in ECC that speed up the multiplication process. However, many schemes focus on securing ECC, and they offer more insights into the approach used to encode plain text and map it onto an elliptic curve. The rest of this literature review focuses on these schemes and, in particular, on the question of how the plain texts are encoded into numerical values, in addition, how these values are mapped onto the elliptic curve.
Several schemes proposed ways to secure plain text by encoding the characters to numerical values, thus giving them the ability to be mapped onto the elliptic curve. Many approaches use these schemes to encode the plain text. For instance, using the ASCII table, each character is converted into its decimal number [26,54,55,56]. In this case, the plain text “Hello” would be encoded to become “72” “101” “108” “108” “111”. These values are then mapped directly onto the elliptic curve as cipher text. However, this approach falls under the chosen plain text attack (CPA). This is because the attacker has the power to decrypt the chosen cipher text (in this case, a commonly used scheme). For this reason, other schemes manipulate the ASCII table by multiplying it by a secure number that is agreed on by both parties [57].
Critically, the issue of sharing the secure number is similar to the challenge of agreeing on the sharing of a secure key between the two parties. Such a scheme could also fall under the CPA and CCA. Similarly, other schemes are based on different encoding approaches that rely on matrix-based methods to conceal the matching table [58]. Specifically, these schemes use secret mapping tables that are unknown to anyone except the recipient, and which are used to encode and decode the plain text in a secure manner. While this may be true, there are two weakness associated with this approach: first, the dilemma of how to secure the delivery of the matrix table to the recipient in a secure way, thereby preventing CPA; and second, it is known that if the matrix-table is assumed to be securely delivered, then the cipher text falls under the CCA. This is because the same encrypted characters are repeated for the same plain characters in each encryption process.
The third approach to overcome flaws in ECC involves Block Chaining operations. The first step is to divide the plain text into a set of fixed-size blocks. In turn, the first block of the plain text is XORed with an initial vector [59]. Following this, the result of the first XORed value is used for the second XOR operation with a second block, and the process is repeated for all plain text blocks. This is a good approach, but it is vulnerable to CPA and CCA when the plain text is divided into a set of blocks and all blocks are same (e.g., the plain text is a repeated character). As a result, the second XORing process results in the value of the as following . This is because . Therefore, the result of the XORing operation becomes , where . Additionally, this scheme lacks AE property, which increases vulnerability to cipher text tampering attacks and nonrepudiation issues.
Barman et al. [60] proposed an encryption method to secure IoT communications informed by DNA-based ECC. For each set of characters in the plain text, a DNA genome sequence is mapped to it. There are many genome sequences publicly available, and so randomizing the selection of genome sequences is part of the encryption process for the plain text. Furthermore, the decryption process should use the same DNA genome sequences. Therefore, both parties, the sender and the recipient, must use the same sequences before encrypting and decrypting the plain text. For this reason, the DNA genome sequences should be securely used only by the sender and recipient. If an attacker discovers the sequence, the scheme will be vulnerable to encryption attacks such as CPA. Additionally, even if the sequence is delivered securely, the cipher text will be the same for each repeated plain text encryption process. Resultantly, the scheme is also vulnerable to other encryption attacks, including CCA.
Duarah et al. [61] introduced Securing IoT Using Machine Learning and ECC. In their scheme, the authors first classified the data set to enhance the transmitted data, where the accurate data were transmitted only to reduce computation efforts. If the data were clean, then they were moved into a second stage, namely encryption via ECC. However, if the data is malicious then it is discarded to save the encryption computation efforts. In the encryption phase, the authors wrote the key generation algorithms that use the ECC scalar multiplication operation s.t. P is a point in the elliptic curve, and d is the private random integer. In their encryption algorithm, the authors defined how the shared key is constructed in order to encrypt the plain text by the addition operation between the plain text and the shared key. Although the scheme produced a new strategy for performance enhancement in the IoT environment by limiting data transmission only to clean data, the security analysis indicates that it is vulnerable to CPA when the same data are encrypted and sent using the same scheme.
Joglekar et al. [62] proposed Lightweight ECC for Data Integrity and User Authentication in Smart Transportation IoT System. In their scheme, the authors use One Time Password (OTP) to exchange the shared key securely to prevent the man in the middle attack (MITM). The 4-digit OTP is encrypted using ECC and transmitted to the recipient to complete the registration process. The shared key between the two parties is constructed as follows: , where are private keys for Sender A and Recipient B, respectively. Similarly, and are the public keys for Sender A and Recipient B. Using OTP to prevent the MITM is a good approach, but the authors neglected to state whether there is an assumption about the 4-digit OTP. It is relevant that the brute force attack needs possible choices to break the OTP, which can be completed in several minutes. Furthermore, the authors did not state how to encrypt the OTP or how to map it onto an elliptic curve.
Finally, Das & Giri [55] proposed two encoding algorithms, which generate sets of numerical values via the sum of weight n with base b . The first encoding algorithm is used when the value of the base b is a dynamic integer. In this case, the highest accepted value is (i.e., the highest value of ASCII table). In addition, n is the size of the prime field, where the authors suggest the use of a 192-bit key. Resultantly, the set of groups that can be combined based on their method is . The base b can be reduced below , which increases the set of groups more than 11 based on b. However, the reduction of b should also contribute to a reduction in ASCII table mapping, and the authors did not provide a safe reduction mechanism. When b is not dynamic in the second algorithm, the suggested set of the combing group is equal to . Based on the scheme described by the authors, it is , and the number of groups based on both algorithms is small. Thus, the computation overhead will increase compared to other schemes. Notably, the encoding and mapping phases did not manipulate the plain text characters after using the ASCII table values, which heightened the scheme’s vulnerability to CPA.
All schemes in the literature are vulnerable to CPA and/or CCA, such that the encryption of the same plain texts always produce same cipher texts. Besides, these schemes use the appending method in the mapping phase which results in increasing the computation overhead. Although, some schemes that use the probability method to map points to EC failed to justify the chosen value of k. Moreover, many of the existing schemes fail to offer secure AE scheme, which means they are vulnerable to tampering attacks. An attacker can modify the transmitted cipher text without detection by the receiver. The cipher text offers confidentiality only; it does not offer integrity by itself. Therefore, to prevent tampering, to maintain the integrity of the cipher text, to ensure that the transmitted message is secured against encryption attacks, and to enhance the mapping phase performance, the proposed scheme ensures the AE property, resists CPA and CCA, and enhances the mapping phase performance.
3. The Proposed Scheme
The proposed scheme contains nine phases: initializing system parameters; converting the plain text message into numerical values (encoding); finding the mapping points on the elliptic curve; encrypting the mapped points; signing the aggregated mapped points as cipher text; and finally, undertaking the reverse of the previous phases by verifying and decrypting the received cipher text, decoding the mapped points, and converting the mapped points into plain text.
This study’s main contribution is to offer a secure and efficient encryption scheme in the form of ECC. It facilitates secure communication by creating a shared key for a group of parties, which they can use to secure their shared messages. Notably, shared key creation is undertaken in the first phase, and many recent studies neglect to highlight the importance of having a shared key between parties for shared message encryption. In addition, this study provides a secure and enhanced method to encode and map plaintext to EC. Therefore, this study focuses on the three phases that start the ECC because it constitutes a major feature of any system for securing group communication (e.g., IoT environments). Figure 2 shows the nine phases of the proposed scheme.
Figure 2.
High-level overview of proposed scheme.
3.1. Generating System Parameters
The aim of this phase is to generate the parameters needed to secure communication between all parties by setting up public and private keys. This phase contributes to the creation of the shared group key , which is used to encrypt the message shared between group members. The notations that the system generates, which are used for each session in the proposed scheme, are illustrated in Table 1.
Table 1.
Notation relevant to the proposed scheme.
| Notation | Description |
|---|---|
| Edge identification number | |
| Node identification number | |
| Edge private key | |
| Node private key | |
| G | EC base point |
| Edge public key = | |
| Node public key = | |
| p | Large prime number (192-bit) |
| EC coefficients, s.t. | |
| EC map points equation | |
| Hash function used only by edge | |
| Node list containing references and | |
| Signing message hash function | |
| Shared group key | |
| Shared group point () | |
| Random initial vector (192-bit) | |
| Private random key (192-bit) | |
| k | Random integer chosen from |
| Cipher text (all encrypted points) | |
| ⊕ | XOR used in mapping phase to secure mapped points |
| + | Addition operation used in ECC to encrypt mapped points with |
It is important for the edge to create and maintain the shared group key . This enables the parties to decrypt cipher text effectively. Therefore, creates the initial using its and . The key generation process is illustrated in Algorithm 1.
| Algorithm 1:Edge algorithm for generating initial shared group key . |
| Input: |
| Output: |
| 1 ; |
| 2 |
In a similar way, for every new node that joins the group, is updated by the following Equation (2).
| (2) |
To maintain the forward and backward secrecy, it is important to ensure that all new nodes that join cannot decrypt the cipher text sent before it joined the group using . Similarly, any nodes that leave the group cannot decrypt the cipher text sent after their departure. To achieve this, the proposed scheme allows each node to perform certain operations to maintain .
For a new node to join the group, the edge sends the joined node hashed ID to all current nodes. In turn, each node adds the hashed ID to its node list , and it simultaneously updates using Equation (2). Similarly, the edge updates its using the same equation. In turn, the edge sends to the newly joined node, along with a list of all hashed IDs of existing node (with the exception of the hashed ID of the new node). Figure 3 illustrates this process, and Algorithm 2 describes the steps required to perform the joining process.
| Algorithm 2:Updating , , and for a newly joined node. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 ; |
| 7 |
Figure 3.
Sequence diagram for new node joining the group.
Similarly, when the current node leaves the group, the edge sends its reference ID to all currently joined nodes, and each node updates using Equation (2). At the same time, the corresponding hashed IDs are removed from the node list. Additionally, the edge updates using Equation (2), and it removes the corresponding hashed ID from its node list. Figure 4 presents a sequence diagram illustrating the process, and Algorithm 3 describes the steps required to perform the leaving process.
| Algorithm 3:Updating , , and for node leaving the group. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 |
Figure 4.
Sequence diagram for node leaving the group.
3.2. Encoding and Mapping the Plain Text
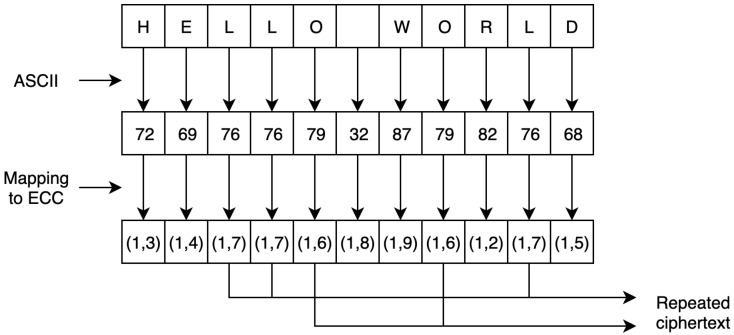
This study extended the encoding and mapping mechanism steps proposed in [63]. As described in related work, a security flaw exists in the study’s encoding process. The main encryption flaw associated with the encoding and mapping phases in ECC stems from the fact that using the same encryption scheme produces the same ciphertext. As such, by analyzing the ciphertext, the adversary can gain important information about the plaintext. To illustrate this flaw, Figure 5 shows how the same letter is encoded with the same value every time. Thus, the corresponding ciphertext of the encoded value is transformed into the same ciphertext value each time, which allows the adversary to distinguish between the set of ciphertexts to extract the plaintext, as shown in Figure 6.
Figure 5.
Repeated encoded characters using the ASCII table.
Figure 6.
Repeated mapped points to the designated elliptic curve using the ASCII table.
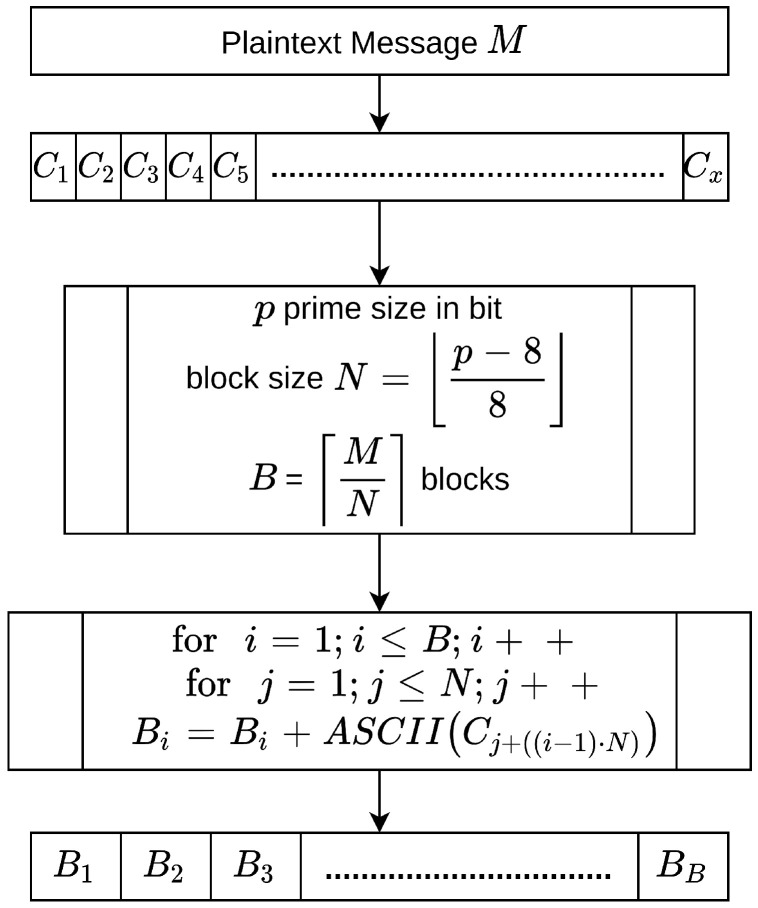
Every scheme discussed in this study’s literature review in Section 2 is vulnerable to an encryption flaw. Therefore, the study provides an improved encoding process to overcome this flaw by dividing the plain text into a set of blocks denoted by B. Then, the characters of each block B are counted, denoted by N, which can be calculated as follows:
| (3) |
It is worth noting that 8 is subtracted from p to allow a maximum of 8 bits in terms of the padding bits used in the mapping phase. Therefore, in the proposed scheme, we can determine the value of N as follows:
| (4) |
In a similar way, the number of blocks B needed in each plain text, denoted by the number of characters M, is determined by the following equation:
| (5) |
The to divide the plaintext to this length is because every block B must be mapped to the 192-bit ECC (field size 192). As discussed previously, 8 bits in every block are reserved for the mapping phase, in which they serve as padding bits to secure the number of rounds required to find the mapping points for each block. Figure 7 illustrates the process needed to convert the plain text M into set of blocks.
Figure 7.
Converting plain text into a set of blocks.
Algorithm 4 provides an overview of the steps involved in converting plain text into a set of blocks.
| Algorithm 4:Converting a plain text into a set of blocks. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 ; |
| 7 ; |
| 8 ; |
| 9 ; |
| 10 |
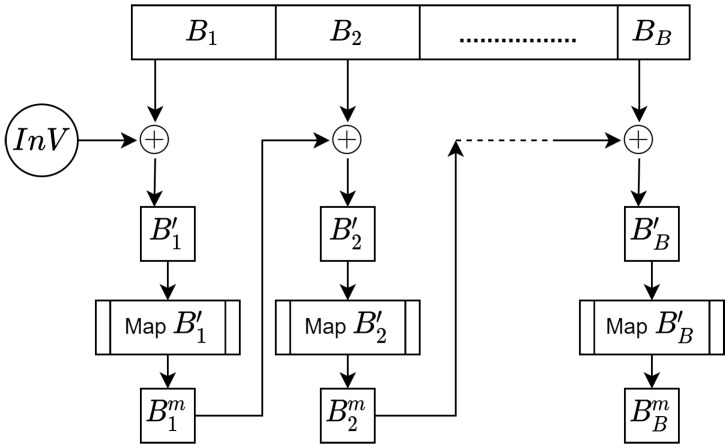
Following the conversion of M into a set of blocks, the next critical issue is to ensure that the blocks are secure against encryption attacks (e.g., CPA and CCA). Therefore, the Cipher Block Chaining (CBC) was used to make the blocks resistant to such attacks. Figure 8 shows the process of ⊕ the blocks to increase their security.
Figure 8.
Securing blocks for resistance against encryption attacks using Cipher Block Chaining (CBC).
Algorithm 5 describes the process that secures the blocks.
| Algorithm 5:Securing blocks for resistance against encryption attacks. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 |
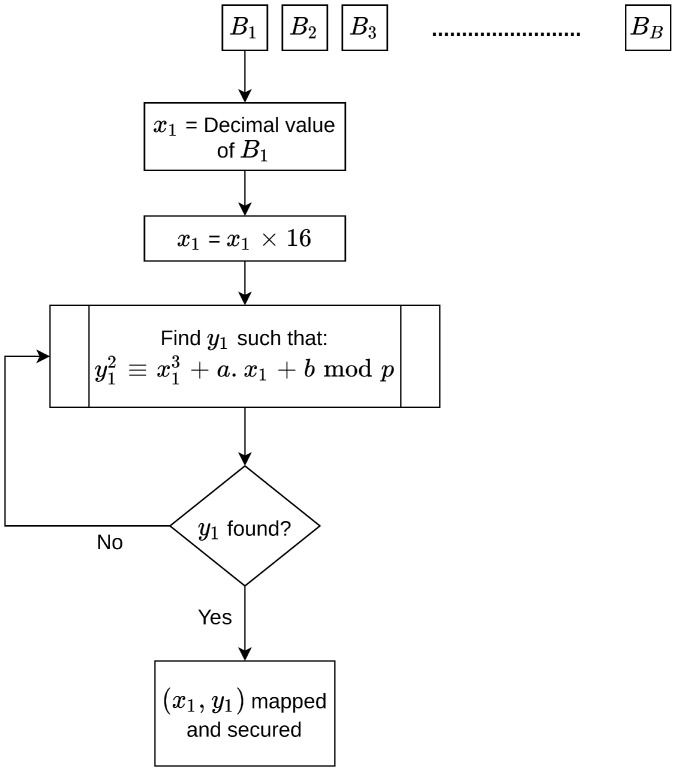
Mapping a point to an elliptic curve means that satisfies Equation (1). Therefore, it is important to find the value of corresponding to for each point. Every secured block is converted into a decimal value, and these values are then mapped to the elliptic curve generated in the first phase to find the corresponding value of . Figure 9 illustrates the steps involved in mapping the secured blocks to an elliptic curve.
Figure 9.
Mapping secured blocks to an elliptic curve.
Algorithm 6 outlines the steps involved in mapping the secured blocks to an elliptic curve.
| Algorithm 6:Mapping secured blocks to an elliptic curve. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 ; |
| 7 ; |
| 8 |
3.3. Encrypting and Decrypting the Mapped Points
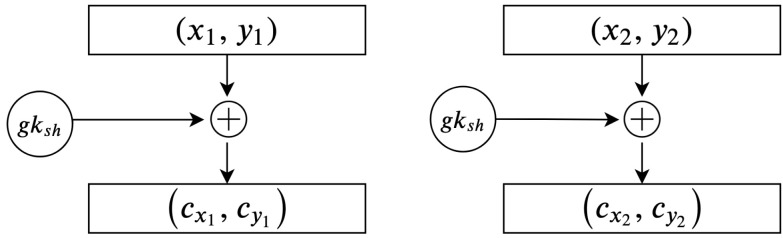
In many schemes, the assumption is made that the mapping phase is sufficient to secure the plain text and plays the encryption phase. However, this assumption is incorrect because the mapping phase to the elliptic curve means that these points belong to the generated elliptic curve and can benefit from the elliptic curve discrete logarithm problem (ECDLP). In our proposed scheme, we encrypt these points by adding them to . Figure 10 illustrates the process for encrypting the mapped points.
Figure 10.
Encrypting mapped points using the shared group point.
The algorithm used to secure the transmitted message using the shared group point is given below.
| Algorithm 7:Encrypting mapped points using the shared group point. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 |
The remaining phases constitute a reversal of the previous phases. Therefore, the secured points are decrypted, and the recipient subtracts them with . As illustrated before, all parties have the same shared group point , which is used to encrypt and decrypt the messages. In Figure 11, an illustration of how to decrypt secured points is given.
Figure 11.
Decrypting secured points using the shared group key.
Algorithm 8 provides an overview of the steps involved in completing the decryption process:
| Algorithm 8:Decrypting cipher texts using the shared group key. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 |
3.4. Decoding and Converting the Decrypted Points into Plain Text
The next phases are concerned with completing the previous phase, which focus on decoding and converting the decrypted points into a plain text M. There are two pairs on each set of these points, denoted and . It is worth noting that is used in two phases only: the encryption and decryption phases. In these phases, the values are used to add and subtract two points on the elliptic curve. Therefore, in this phase, we are only concerned with , that represent the binary values of the characters in the plain text. The process that describes the decoding phase is illustrated in Figure 12.
Figure 12.
Converting and decoding values into binary values.
Algorithm 9 demonstrates the steps required to convert the decrypted points into binary values:
| Algorithm 9:Decoding decrypted points into binary values. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 ; |
| 7 ; |
| 8 |
Finally, the binary values obtained in the previous phase are converted into their corresponding characters. These binary values represent the plain text message M, and so they need to be converted into their ASCII values. The conversion process is illustrated in Figure 13.
Figure 13.
Converting binary values into plain text M.
Algorithm 10 shows how to convert binary values into a plaintext M.
| Algorithm 10:Converting binary values into plain text. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 |
3.5. Signing and Verifying the Encrypted Message
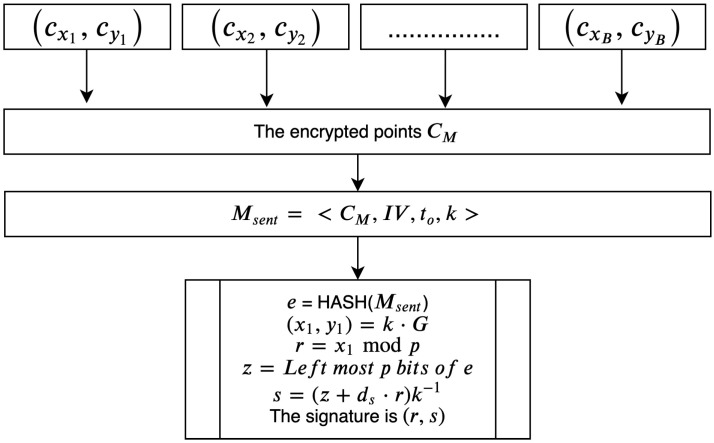
The intention of AE schemes using the encrypt then sign approach is to transmit messages between parties without compromising confidentiality, security, and integrity. In the proposed scheme, confidentiality (encryption) is maintained by the previous phases. Thus, to assure integrity (sign), the sender signs the message using his or her private key , which relies on ECDSA. The message consists of a set of tuples, which contain the encrypted points and , the timestamp , and a random signature integer k. The signing process is illustrated in Figure 14.
Figure 14.
Sender ensures message integrity by signing it with .
The following algorithm outlines the process used to sign the :
| Algorithm 11:Process of signing the message. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 ; |
| 7 ; |
| 8 |
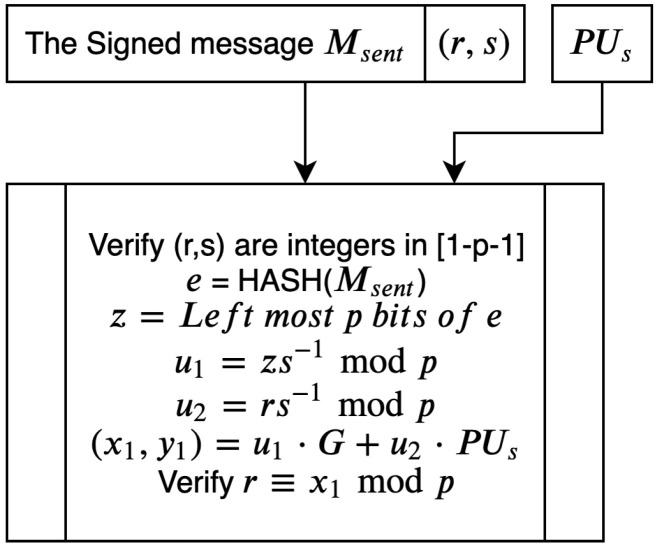
The receiver of a signed message verifies it using the sender’s public key. The verification process is illustrated in Figure 15.
Figure 15.
Receiver verifies signed message.
Algorithm 12 outlines the steps involved in verifying the integrity of the received message using the sender’s public key.
| Algorithm 12:Recipient verification of a signed message. |
| Input: |
| Output: |
| 1 ; |
| 2 ; |
| 3 ; |
| 4 ; |
| 5 ; |
| 6 ; |
| 7 |
4. Security Analysis and Performance Evaluation
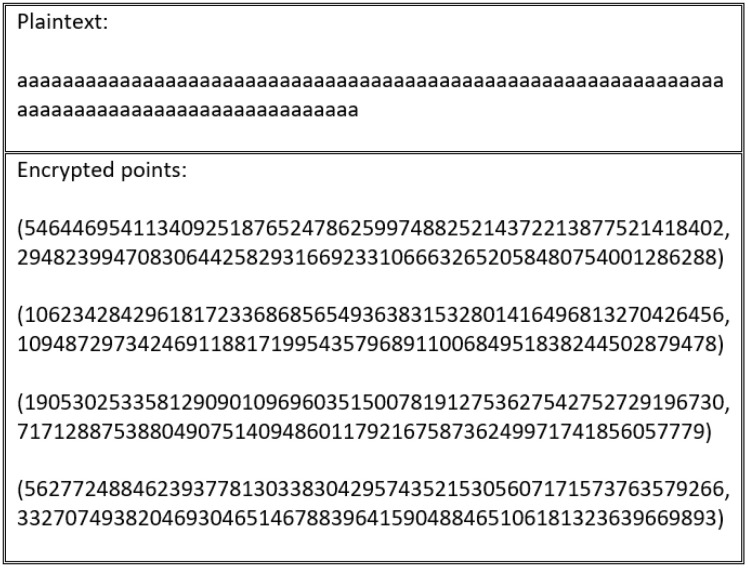
Every scheme discussed in this study’s literature review is vulnerable to an encryption flaw. For instance, the encryption schemes presented in [55,60,61,62] produce the same cipher text when repeated several times, as outlined in Figure 16 and Figure 17.
Figure 16.
Cipher text generated by first encryption process.
Figure 17.
Cipher text generated by second encryption process using the same plain text as in Figure 16.
These schemes suffer from an encryption weakness because they offer the same cipher text if the sender encrypts the plain text using the same encryption key. The main factor that underlies this flaw is that the encryption process in these schemes neglects to consider the importance of manipulating plain text before encrypting and decrypting it. This ensures that a distinct cipher text is produced for every encryption process. Therefore, in the absence of a manipulation step, the adversary can learn from the cipher text, determining whether certain cipher texts are the same or different.
In the scheme proposed by [59], this flaw is resolved by using XOR with . Figure 18 shows that the cipher text outputted from the encryption process is different to the cipher text generated by the process depicted in Figure 19, which uses the same plain text. However, these schemes are vulnerable to the same flaw, particularly in the special cases outlined in Figure 20. This flaw occurs when the blocks divided for XOR with are equal to . In this case, , , , and so on. Therefore, in the event that all blocks are the same, an attacker can exploit the encryption flaw because XOR with operations become:
| (6) |
Figure 18.
Cipher text generated by first encryption process using XOR with .
Figure 19.
Cipher text generated by second encryption process with XOR different using the same plain text as in Figure 18.
Figure 20.
Cipher text generated via encryption of plain text, followed by XORing with using a special text that produces the same blocks.
This encryption flaw is illustrated in Figure 20.
Based on the flaws identified in existing schemes, it is a valuable contribution to the literature to improve the encryption process with CBC. In the proposed scheme, all previous flaws are resolved by using CBC with derived from mapping points to secure the cipher text in all forms, as described in Algorithm 5. The encryption operation generated by the optimized encryption process is illustrated in Figure 21.
Figure 21.
Improved encryption process generating different encrypted points even with the same blocks.
To evaluate the proposed schemes, security analysis was used with IND-CPA and IND-CCA. In the next subsections, results are given to show that the schemes examined in the literature review are not IND-CPA and IND-CCA. Therefore, it is necessary to prove that the novel scheme proposed in the presented study is both IND-CPA and IND-CCA.
4.1. Indistinguishability under Chosen Plain Text Attack IND-CPA
A scheme known as IND-CPA if the adversary has the power to submit as many , as desired and also when he or she receives the cipher texts for each message. Then, the adversary must submit two distinct messages, , to the encryption oracle, receiving . This is illustrated in Figure 22. The challenge is that the adversary is required to guess the value of b with a probability of the following:
| (7) |
Figure 22.
Adversary’s power to submit unlimited messages to encryption oracle in CPA.
Thus, schemes proposed in [55,60,61,62] are insecure under CPA. An adversary can win a challenging game by submitting two identical messages, , to the encryption oracle. In turn, the encryption oracle sends the cipher text , which is the cipher text for . In an experiment, the adversary sends two messages, where , and the encryption oracle responds by encrypting one message and sending one cipher text . The adversary is then challenged to guess the value of , and to determine which cipher text belongs to or . However, the adversary can win the challenge with . This is because the encryption oracle in such schemes always encrypts the same messages with the same cipher texts and the same key. Therefore, since the adversary already has , he or she can determine whether the value of b is 0 or 1. This is achieved by matching with . If , then ; otherwise, . This process is illustrated in Figure 23.
Figure 23.
Steps needed for an adversary to win the Chosen Plain Text Attack (CPA) challenge.
Theorem 1.
The proposed scheme is (IND-CPA) such that the probability of the adversary to decrypt the message in the two experiments is negligible, as written in Equation (7).
Proof.
This theorem is proven by the fact that the proposed scheme uses a different value of for each experiment. Hence, the adversary can submit as many messages as he or she wants to the encryption oracle. The cipher texts generated by the experiment will not be the same, even for the same message. For example, in the second experiment, in was different compared to in . Therefore, when the adversary submits the same message in , he or she will receive the corresponding cipher text in that experiment, which is . However, when the adversary moves to where the encryption oracle challenges the adversary, the two messages submitted by the adversary are not distinguishable. This is because the cipher text from in is different from the cipher text from the same message in . For this reason, the probability that the adversary wins the challenge is
Let be an ECC encryption scheme, and let us define the experiment between the challenger and the attacker A as follows:
Consider the following games:
Game (0)
The attacker A makes a request for encrypting a message , and receives .
Game (1)
The attacker A sends two messages , where is the same as in game 0. The challenger outputs to challenge A to guess the value of b.
Game (3)
The attacker A returns the value of b based on the comparison he or she can perform to distinguish between , which relies on game 0 and 1. However, the probability that A achieves this is 0 because the in game 0 is not the same as in game 1. It is also relevant to note that the XOR operation in both games is undertaken with different . □
4.2. Indistinguishability under Chosen Ciphertext Attack IND-CCA
An encryption scheme is IND-CCA if the adversary has the ability to submit as cipher texts as he wants , and to receive the plain text for that cipher text. In addition, the adversary submits any two distinct messages and , where to the encryption oracle and receives . This process is depicted in Figure 24. The challenge is that the adversary is required to guess the value of b to differentiate between the two experiment’s games, with probability as follows:
| (8) |
Figure 24.
An adversary’s power to submit countless messages to the encryption oracle in CCA.
With the above in mind, the scheme proposed in [59] is not secure under CCA. The adversary can win the challenging game by submitting two messages, , to the encryption oracle. In turn, the encryption oracle sends the cipher text , which is the cipher text for either or . Subsequently, the adversary modifies c by XORing with R, where . This produces where , which is sent to the decryption oracle for decryption.
The decryption oracle responds by decrypting the cipher text . This process relies on the modified . The result is that the decryption process is . Consequently, an adversary can guess the value of or by XORing , after which it can be compared directly with the received message . Therefore, the adversary can win the challenge with . This process is illustrated in Figure 25.
Figure 25.
Steps needed for an adversary to win the CCA challenge.
Theorem 2.
The proposed scheme is indistinguishable under IND-CCA such that the probability of the adversary decrypting the message in the two experiments is negligible, as written in Equation (8).
Proof.
The proof for starts by noting the adversary’s ability to access both the encryption and decryption oracle. At the same time, the adversary cannot submit received from the encryption oracle and then submit it for decryption to distinguish the experiment game. However, the adversary can modify the received and submit it for decryption as the modified . Thus, the adversary can win the challenging game by XORing with a random R, thereby guessing (see Figure 25). The proposed scheme offers integrity to cipher texts. It also protects transmitted cipher texts from tampering. Therefore, the decryption oracle drops any modified , meaning that the oracle responds to the adversary with for every modified message, as illustrated in Figure 26. Resultantly, the proposed scheme is negligible under Equation (8), meaning that it is indistinguishable under IND-CCA.
Let be an ECC encryption scheme, and let us define an experiment between the challenger and attacker A as follows:
Consider the following games:
Game (0)
The attacker A makes a request for encrypting a message , and receives .
Game (1)
The attacker A modifies the cipher text from game 0 to XOR the with a random value . A request is made for the challenger to decrypt the cipher text .
Game (3)
The attacker A can compute the plain text from , which results in . In this case, A can compare with and . However, A will fail to win because the challenger will discard the modified . This stems from the fact that is invalid, meaning that probability of the success of A is 0. □
Figure 26.
Proposed scheme IND-CCA proof.
4.3. Malleability Attack
Changing encrypted data can lead to the modification of the plain text after decryption, which is known as a malleability attack. For instance, the attacker modifies the with the value of 1, which means that the first block of the plain text message will be XORed with 1. As a result, the reset of blocks in the CBC will also be modified. The steps involved in the malleability attack are depicted in Figure 27.
Figure 27.
Overview of the malleability attack.
Theorem 3.
The proposed scheme is resistant to the malleability attack.
Proof.
It is known that an adversary can eavesdrop on the messages sent between the two parties. Adversaries can also change messages and return them to either party. However, the recipient checks the received message’s integrity before decrypting the cipher text. Therefore, the recipient ignores the received message because it has an invalid signature. An illustration of this proof is given in Figure 28
□
Figure 28.
Resistance of the proposed scheme to the malleability attack.
A security analysis comparison was undertaken between the scheme proposed in this study and others mentioned in the literature (see Table 2).
Table 2.
Security analysis comparison of proposed scheme and other schemes.
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | |
|---|---|---|---|---|---|---|---|---|
| Barman, [60] | N | N | N | N | N | n | N | |
| Joglekar, [62] | N | N | N | N | N | N/A | N/A | N |
| Muthukuru, [59] | Y | N | N | N | N | n | N | |
| Duarah, [61] | N | N | N | N | N | n | N | |
| Das, [55] | N | N | N | N | N | N/A | N/A | N |
| Proposed scheme | Y | Y | Y | Y | Y | Y |
1. IND-CPA; 2. IND-CCA; 3. Resistance to malleability attack; 4. Integrity; 5. Authenticated encryption; 6. Complexity of mapping phase; 7. No of rounds based on n appending bits; 8. Offers nonrepudiation
4.4. Performance Evaluation
The main goal of the proposed scheme was to provide a secure scheme that resolved encryption flaws that yield to CPA and CCA attacks. The study also sought to offer a scheme with a suitable level of performance in constrained environments. The security aspect of the proposed scheme was proven in the previous section, and this section evaluated the performance of the scheme based on two criteria: enhancing the process of mapping points to an elliptic curve; and time, space overhead, and power consumption in a simulation environment.
4.4.1. Mapping Points to an Elliptic Curve
Mapping points to an elliptic curve should be undertaken correctly and efficiently. As illustrated in Figure 29, 50% of points cannot be mapped to the EC as there is no axis that meets the EC’s equation. Therefore, it is necessary to increase the value of by 1, and then to recompute until a value is found that matches. As a result, the point is eventually mapped. In many schemes, the characters in plain text are converted into numerical values based on the ASCII table, which facilitates their mapping onto the elliptic curve. Therefore, when these values are not mapped from the beginning, the value to be mapped increases. However, this step changes the original value, and the plain text is lost. For this reason, to overcome this problem, two methods are widely used to map points: the probability method and the appending method.
Figure 29.
Probability of successfully mapping points to an elliptic curve based on number of rounds.
In the probability method, which was introduced by King (2009) [64], the value of k is defined, which represents the number of rounds needed to map the points. This value is multiplied by , and the product is used in the mapping phase with ability to increment it in k rounds. In turn, the value of can be restored by calculating the value of the mapped point: . In the second method, the appending method, is appended by number of bits representing the number of rounds required. For instance, if the scheme defines the appended bits as 000, then the number of rounds that can be safely used in the mapping phase is rounds.
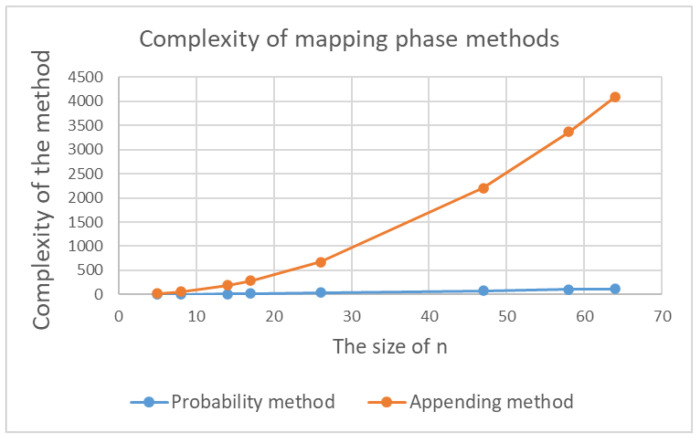
Each method has advantages and disadvantages relating to computational efficiency and the maximum number of rounds. The probability method is more efficient and less complex than the appending method. Using the Harvey-Hoeven algorithm [65], the multiplication operation complexity is , where n is the numerical value size in bits. However, the complexity of appending two texts (i.e., concatenations) is denoted as [66], which highlights the fact that the appending method is more complex than the probability method. This is illustrated in Figure 30.
Figure 30.
Complexity comparison of probability and appending mapping methods.
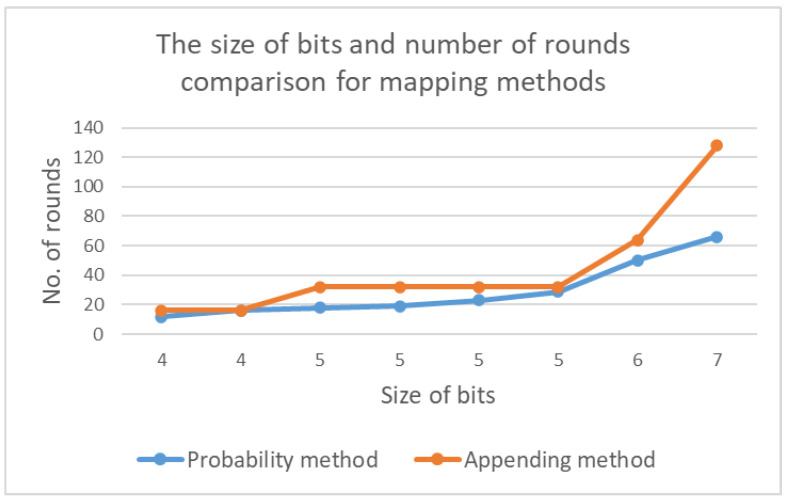
The appending method guarantees to provide a maximum number of rounds base on the appended bits. As the appending methods concatenate fixed bits b to the corresponding binary value, can be incremented times. In contrast, the probability method increases the same size of bits, but in many cases, it would allow fewer round increments compared to the appending method. This is outlined in Figure 31.
Figure 31.
Comparison of number of rounds used in mapping phase method and the size of bits added to .
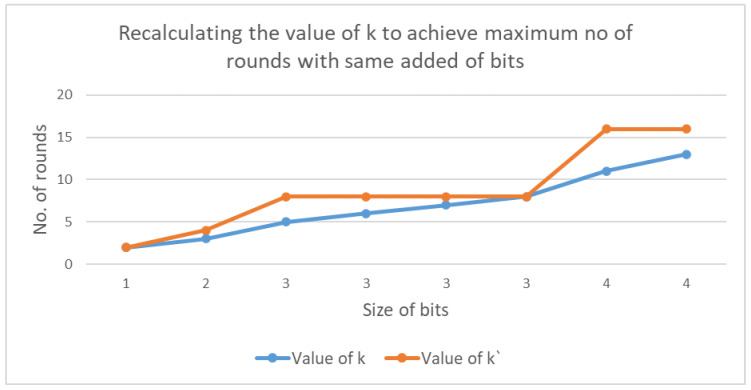
In the proposed scheme, the probability method was used to improve performance. Hoevewr, to increase the efficiency of the choice of k, the proposed scheme took advantage of the appending method to select this value. This was achieved by recalculating , which was used to set the number of rounds to the maximum value of the extra bits added to the value of , as shown in Figure 32.
Figure 32.
Recalculating to increase the maximum number of rounds to the size of added bits.
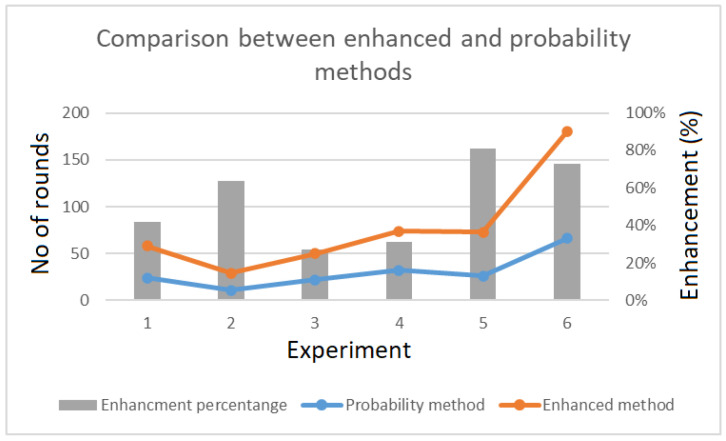
The enhancement made to the probability method increases the number of mapping rounds with same size of the padding bit. As a result, the efficiency was more than 80% in some cases. Figure 33 shows the percentage of improvement that the proposed enhanced selection of k method offers compared to the probability method.
Figure 33.
Percentage improvement between the enhanced selection of k provides in comparison with probability method.
4.4.2. Simulation Performance Evaluation
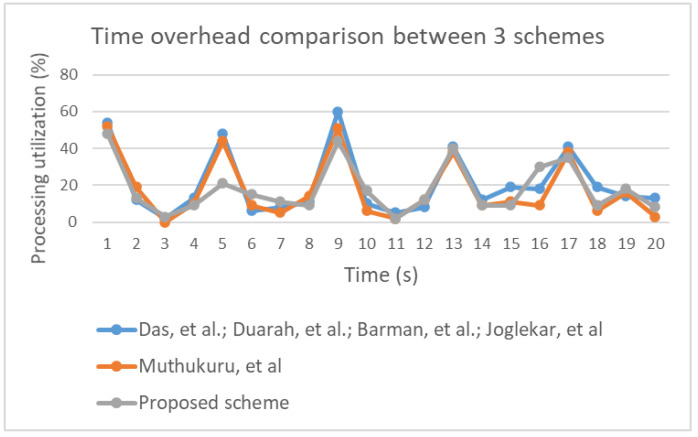
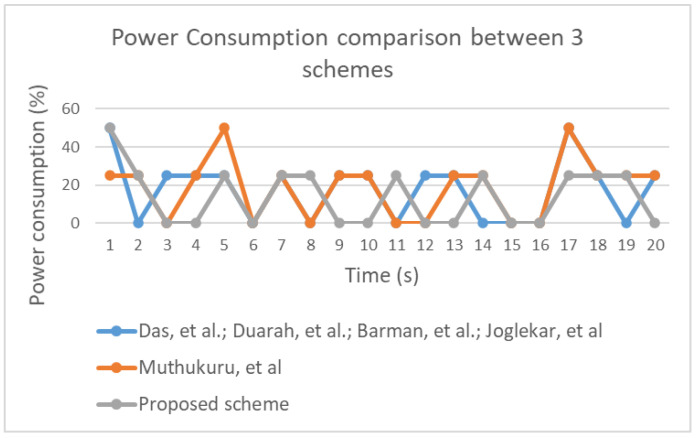
The performance evaluation of the proposed scheme focused on whether the enhancement of the encoding and mapping phases, which was intended to improve resistance to encryption attacks, negatively affected performance. Therefore, the performance of the proposed scheme against other schemes took place to evaluate time overhead, space usage, and power consumption. The schemes are divided to three groups: schemes that did not use or any other methods to manipulate the mapped points as [55,60,61,62]; schemes that used fixed to overcome CPA, including [59]; and finally, schemes that used CBC to overcome the CCA (in this case, only the proposed scheme).
The performance evaluation involved running an experimental simulation 5 times for 20 s each using a low computation device. Figure 34 illustrates time overhead in the three groups included in the performance evaluation. Notably, all three groups were associated with similar levels of utilization. Therefore, it is reasonable to conclude that improving the security of the proposed scheme did not affect the time overhead. Space usage variation was identified during the experiment, as illustrated in Figure 35. Additionally, power consumption for each group was determined based on values (high, medium, low, or none), which are shown in Figure 36. The results indicate that power consumption was similar across the three groups.
Figure 34.
Comparison of time overhead between the proposed scheme and other schemes.
Figure 35.
Comparison of space usage between the proposed scheme and other schemes.
Figure 36.
Comparison of power consumption between the proposed scheme and other schemes.
It is worth mentioning that, the proposed scheme was simulated, tested and compared to the state of the art schemes in a simulated environment using an Android Virtual Device (AVD). AVD has variety of low computation devices images built by Android OS, and it provides processing space and power consumption monitoring and logging. In addition, we used the Bluej Java Development Environment to code the proposed scheme. The platform used to host the AVD is based on Windows 10, and, in terms of hardware, an Intel Core i7-4510U was used with a 128 GB SSD and 8 GB RAM.
5. Conclusions and Future Research
This study proposes a novel approach to elliptic curve cryptography (ECC) that offers AE properties to secure cipher text and to enhance the encoding of text effectively and map the encoded text to an elliptic curve. Previous schemes neglect to consider the importance of the encoding phase, which makes them vulnerable to attack. Therefore, this study focused on the encoding phase, seeking to secure it against several encryption attacks, including CPA, CCA, and malleability attacks. This study also undertook a security analysis to present a proof for the resistance of the proposed scheme against specific encryption attacks. Additionally, the study conducted a performance evaluation to compare the impact of the security enhancement of the proposed scheme on time overhead, space usage, and power consumption to other schemes. The simulation experiment shows that the proposed scheme performed just as well as the other schemes, with no noticeable increase in computation overhead. As a result, the proposed scheme outperforms the security of other schemes and maintains the same computational overhead.
In future research, the authors intend to implement the proposed scheme in different environments such as enhance the protection using TPM-based for mobile agents. Moreover, adapt the scheme in Monitoring the cloud computing architecture to enhance Dynamic Security Properties. In addition, apply the proposed scheme with Policy Based Management to increase the Security of Cloud Computing. These application of proposed scheme lead to study the security analysis and performance evaluation in comparison with other similar schemes. Additionally, more security properties may be added to the study to increase the security requirements, which might be required in new environments.
Acknowledgments
The authors extend their appreciation to the Deputyship for Research & Innovation, “Ministry of Education“ in Saudi Arabia for funding this research work through the project number IFKSURG-1437-035.
Abbreviations
The following abbreviations are used in this manuscript:
| ECC | Elliptic Curve Cryptography |
| IoT | Internet of Things |
| InV | Initial Vector |
| CBC | Cipher Block Chaining |
| AE | Authenticated Encryption |
| CPA | Chosen Plaintext Attack |
| CCA | Chosen Ciphertext Attack |
| ECIES | Elliptic Curve Integrated Encryption Scheme |
| ECDLP | Elliptic Curve Discrete Logarithm Problem |
Author Contributions
Conceptualization, H.A. and A.A.; methodology, A.A.; software, H.A.; validation, A.A.; formal analysis, H.A.; investigation, H.A.; resources, A.A.; data curation, A.A.; writing—original draft preparation, H.A.; writing—review and editing, A.A.; visualization, H.A.; supervision, A.A.; project administration, A.A.; funding acquisition, A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Footnotes
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Labrado C., Thapliyal H., Prowell S., Kuruganti T. Use of thermistor temperature sensors for cyber-physical system security. Sensors. 2019;19:3905. doi: 10.3390/s19183905. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Abdullah A., Kaur H., Biswas R. New Paradigm in Decision Science and Management. Springer; Singapore: 2020. Universal Layers of IoT Architecture and Its Security Analysis; pp. 293–302. [Google Scholar]
- 3.Ram R.S., Kumar M.V., Ramamoorthy S., Balaji B.S., Kumar T.R. Wireless Personal Communications. Springer; Cham, Switzerland: 2020. An Efficient Hybrid Computing Environment to Develop a Confidential and Authenticated IoT Service Model; pp. 1–25. [Google Scholar]
- 4.Pasupuleti S.K., Varma D. Real-Time Data Analytics for Large Scale Sensor Data. Elsevier; Amsterdam, The Netherlands: 2020. Lightweight ciphertext-policy attribute-based encryption scheme for data privacy and security in cloud-assisted IoT; pp. 97–114. [Google Scholar]
- 5.Vishnoi P., Shimi S., Kumar A. Intelligent Communication, Control and Devices. Springer; Singapore: 2020. Symmetric Cryptography and Hardware Chip Implementation on FPGA; pp. 945–955. [Google Scholar]
- 6.Chatterjee S., Samaddar S.G. Smart Computing Paradigms: New Progresses and Challenges. Springer; Singapore: 2020. A robust lightweight ECC-based three-way authentication scheme for IoT in cloud; pp. 101–111. [Google Scholar]
- 7.Moghadam M.F., Mohajerzdeh A., Karimipour H., Chitsaz H., Karimi R., Molavi B. Handbook of Big Data Privacy. Springer; Cham, Switzerland: 2020. A privacy protection key agreement protocol based on ECC for smart grid; pp. 63–76. [Google Scholar]
- 8.Yuen K.K.F. Towards a Cybersecurity Investment Assessment method using Primitive Cognitive Network Process; Proceedings of the 2019 International Conference on Artificial Intelligence in Information and Communication (ICAIIC); Okinawa, Japan. 11–13 February 2019; pp. 068–071. [Google Scholar]
- 9.Biswas C., Gupta U.D., Haque M.M. An Efficient Algorithm for Confidentiality, Integrity and Authentication Using Hybrid Cryptography and Steganography; Proceedings of the 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE); Cox’sBazar, Bangladesh. 7–9 February 2019; pp. 1–5. [Google Scholar]
- 10.Tiburski R.T., Moratelli C.R., Johann S.F., Neves M.V., de Matos E., Amaral L.A., Hessel F. Lightweight Security Architecture Based on Embedded Virtualization and Trust Mechanisms for IoT Edge Devices. IEEE Commun. Mag. 2019;57:67–73. doi: 10.1109/MCOM.2018.1701047. [DOI] [Google Scholar]
- 11.Verma G., Liao M., Lu D., He W., Peng X., Sinha A. An optical asymmetric encryption scheme with biometric keys. Opt. Lasers Eng. 2019;116:32–40. doi: 10.1016/j.optlaseng.2018.12.010. [DOI] [Google Scholar]
- 12.Paar C., Pelzl J. Understanding Cryptography: A Textbook for Students and Practitioners. Springer Science & Business Media; Berlin/Heidelberg, Germany: 2009. [Google Scholar]
- 13.Almajed H.N., Almogren A.S., Altameem A. A Resilient Smart Body Sensor Network Through Pyramid Interconnection. IEEE Access. 2019;7:51039–51046. doi: 10.1109/ACCESS.2019.2909557. [DOI] [Google Scholar]
- 14.Mangia M., Pareschi F., Rovatti R., Setti G. Low-cost security of iot sensor nodes with rakeness-based compressed sensing: Statistical and known-plaintext attacks. IEEE Trans. Inf. Forensics Secur. 2018;13:327–340. doi: 10.1109/TIFS.2017.2749982. [DOI] [Google Scholar]
- 15.Liao M., He W., Lu D., Wu J., Peng X. Security enhancement of the phase-shifting interferometry-based cryptosystem by independent random phase modulation in each exposure. Opt. Lasers Eng. 2017;89:34–39. doi: 10.1016/j.optlaseng.2016.03.015. [DOI] [Google Scholar]
- 16.Ahmed S., Zaman A., Zhang Z., Alam K.M.R., Morimoto Y. Semi-Order Preserving Encryption Technique for Numeric Database. Int. J. Netw. Comput. 2019;9:111–129. doi: 10.15803/ijnc.9.1_111. [DOI] [Google Scholar]
- 17.Davoli L., Veltri L., Ferrari G., Amadei U. Smart Grids and Their Communication Systems. Springer; Singapore: 2019. Internet of Things on Power Line Communications: An Experimental Performance Analysis; pp. 465–498. [Google Scholar]
- 18.Debnath S., Nunsanga M.V., Bhuyan B. Advances in Computer, Communication and Control. Springer; Singapore: 2019. Study and Scope of Signcryption for Cloud Data Access Control; pp. 113–126. [Google Scholar]
- 19.Koblitz N. Elliptic curve cryptosystems. Math. Comput. 1987;48:203–209. doi: 10.1090/S0025-5718-1987-0866109-5. [DOI] [Google Scholar]
- 20.AlMajed H.N., AlMogren A.S. Simple and Effective Secure Group Communications in Dynamic Wireless Sensor Networks. Sensors. 2019;19:1909. doi: 10.3390/s19081909. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21.Yin Y., Wu L., Peng Q., Zhang X. A Novel SPA on ECC with Modular Subtraction; Proceedings of the 2018 12th IEEE International Conference on Anti-counterfeiting, Security, and Identification (ASID); Xiamen, China. 9–11 November 2018; pp. 179–182. [Google Scholar]
- 22.Galbraith S.D., Vercauteren F. Computational problems in supersingular elliptic curve isogenies. Quantum Inf. Process. 2018;17:265. doi: 10.1007/s11128-018-2023-6. [DOI] [Google Scholar]
- 23.Wu T., Wang R. Fast unified elliptic curve point multiplication for NIST prime curves on FPGAs. J. Cryptogr. Eng. 2019;9:401–410. doi: 10.1007/s13389-019-00211-9. [DOI] [Google Scholar]
- 24.Shahroodi T., Bayat-Sarmadi S., Mosanaei-Boorani H. Low-Latency Double Point Multiplication Architecture Using Differential Addition Chain Over GF (2m) IEEE Trans. Circuits Syst. 2019;66:1465–1473. doi: 10.1109/TCSI.2018.2883557. [DOI] [Google Scholar]
- 25.Mrabet A., El-Mrabet N., Lashermes R., Rigaud J.B., Bouallegue B., Mesnager S., Machhout M. International Conference on Risks and Security of Internet and Systems. Springer; Cham, Switzerland: 2016. High-performance Elliptic Curve Cryptography by Using the CIOS Method for Modular Multiplication; pp. 185–198. [Google Scholar]
- 26.Ganesh M.G.G. Secure Method for Text Encryption using Elliptic Curve Cryptography. Int. J. 2018;3:11–15. [Google Scholar]
- 27.Mahto D. Ph.D. Thesis. Nit Jamshedpur; Jharkhand, India: 2018. Data Communication Security Modeling Using Elliptic Curve Cryptography and Biometrics. [Google Scholar]
- 28.Kumar R. Knowledge Computing and Its Applications. Springer; Singapore: 2018. Cryptanalysis of Protocol for Enhanced Threshold Proxy Signature Scheme Based on Elliptic Curve Cryptography for Known Signers; pp. 191–211. [Google Scholar]
- 29.Liu Z., Seo H. IoT-NUMS: Evaluating NUMS elliptic curve cryptography for IoT platforms. IEEE Trans. Inf. Forensics Secur. 2019;14:720–729. doi: 10.1109/TIFS.2018.2856123. [DOI] [Google Scholar]
- 30.Shah D.P., Shah P.G. Revisting of elliptical curve cryptography for securing Internet of Things (IOT); Proceedings of the 2018 Advances in Science and Engineering Technology International Conferences (ASET); Abu Dhabi, UAE. 6 Febuary–5 April 2018; pp. 1–3. [Google Scholar]
- 31.Fournaris A.P., Dimopoulos C., Moschos A., Koufopavlou O. Design and leakage assessment of side channel attack resistant binary edwards Elliptic Curve digital signature algorithm architectures. Microprocess. Microsyst. 2019;64:73–87. doi: 10.1016/j.micpro.2018.07.003. [DOI] [Google Scholar]
- 32.Reddy A.G., Das A.K., Odelu V., Ahmad A., Shin J.S. A Privacy Preserving three-factor authenticated key agreement protocol for client–server environment. J. Ambient. Intell. Humaniz. Comput. 2019;10:661–680. doi: 10.1007/s12652-018-0716-4. [DOI] [Google Scholar]
- 33.AlSaad S.N., Naji A.K. Elliptic Curve Video Encryption in Mobile Phone Based on Multi-Keys and Chaotic Map. Al-Mustansiriyah J. Sci. 2018;29:106–116. [Google Scholar]
- 34.Shah D.P., Shah N.P. Implementation of Digital Signature Algorithm by using Elliptical Curve p-192. Aust. J. Wirel. Technol. Mobil. Secur. 2019;1:1–4. doi: 10.21276/Ausjournal/2019.1.1.1. [DOI] [Google Scholar]
- 35.Abdullah K.E., Ali N.H.M. Security Improvement in Elliptic Curve Cryptography. Int. J. Adv. Comput. Sci. Appl. 2018;9:122–131. doi: 10.14569/IJACSA.2018.090516. [DOI] [Google Scholar]
- 36.Hu X., Zheng X., Zhang S., Li W., Cai S., Xiong X. A High-Performance Elliptic Curve Cryptographic Processor of SM2 over GF (p) Electronics. 2019;8:431. doi: 10.3390/electronics8040431. [DOI] [Google Scholar]
- 37.Reyad O. Text message encoding based on elliptic curve cryptography and a mapping methodology. Inf. Sci. Lett. 2018;7:7–11. doi: 10.18576/isl/070102. [DOI] [Google Scholar]
- 38.Kanchan S., Chaudhari N.S. Recent Findings in Intelligent Computing Techniques. Springer; Singapore: 2019. Signcrypting the Group Signature with Non-transitive Proxy Re-encryption in VANET; pp. 15–23. [Google Scholar]
- 39.Chen F.L., Wang Z.H., Hu Y.M. A New Quantum Blind Signature Scheme with BB84-State. Entropy. 2019;21:336. doi: 10.3390/e21040336. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 40.Zhou Y., Li Z., Hu F., Li F. Information Technology and Applied Mathematics. Springer; Singapore: 2019. Identity-Based Combined Public Key Schemes for Signature, Encryption, and Signcryption; pp. 3–22. [Google Scholar]
- 41.Kittur A.S., Pais A.R. A trust model based batch verification of digital signatures in IoT. J. Ambient. Intell. Humaniz. Comput. 2019;11:313–327. doi: 10.1007/s12652-019-01289-z. [DOI] [Google Scholar]
- 42.Gomez A.I., Gomez-Perez D., Renault G. A probabilistic analysis on a lattice attack against DSA. Des. Codes Cryptogr. 2019;87:2469–2488. doi: 10.1007/s10623-019-00633-w. [DOI] [Google Scholar]
- 43.Aldaya A.C., Brumley B.B., Sarmiento A.J.C., Sánchez-Solano S. Memory Tampering Attack on Binary GCD Based Inversion Algorithms. Int. J. Parallel Program. 2018;47:621–640. doi: 10.1007/s10766-018-0610-x. [DOI] [Google Scholar]
- 44.Zuccherato R. Elliptic Curve Cryptography Support in Entrust. Entrust Ltd.; Kanata, ON, Canada: 2000. [Google Scholar]
- 45.Tyagi M., Manoria M., Mishra B. International Conference on Advanced Computing Networking and Informatics. Springer; Singapore: 2019. A Framework for Data Storage Security with Efficient Computing in Cloud; pp. 109–116. [Google Scholar]
- 46.Louw J., Niezen G., Ramotsoela T., Abu-Mahfouz A.M. A key distribution scheme using elliptic curve cryptography in wireless sensor networks; Proceedings of the 2016 IEEE 14th International Conference on Industrial Informatics (INDIN); Poitiers, France. 19–21 July 2016; pp. 1166–1170. [Google Scholar]
- 47.Kanda G., Antwi A.O., Ryoo K. Advanced Multimedia and Ubiquitous Engineering. Springer; Singapore: 2018. Hardware Architecture Design of AES Cryptosystem with 163-Bit Elliptic Curve; pp. 423–429. [Google Scholar]
- 48.Ferretti L., Marchetti M., Colajanni M. Fog-based Secure Communications for Low-power IoT Devices. ACM Trans. Internet Technol. (TOIT) 2019;19:27. doi: 10.1145/3284554. [DOI] [Google Scholar]
- 49.Albalas F., Al-Soud M., Almomani O., Almomani A. Security-aware CoAP Application Layer Protocol for the Internet of Things using Elliptic-Curve Cryptography. Power. 2018;1333:151. [Google Scholar]
- 50.Khan S., Khan R. Elgamal Elliptic Curve Based Secure Communication Architecture for Microgrids. Energies. 2018;11:759. doi: 10.3390/en11040759. [DOI] [Google Scholar]
- 51.Ay A.U., Mancillas-López C., Öztürk E., Rodríguez-Henríquez F., Savaş E. Constant-time hardware computation of elliptic curve scalar multiplication around the 128 bit security level. Microprocess. Microsyst. 2018;62:79–90. doi: 10.1016/j.micpro.2018.05.005. [DOI] [Google Scholar]
- 52.Liu S., Yao H., Wang X.A. Fast elliptic curve scalar multiplication for resisting against SPA. Int. J. Comput. Sci. Eng. 2018;17:343–352. doi: 10.1504/IJCSE.2018.095845. [DOI] [Google Scholar]
- 53.Ezzouak S., Azizi A. International Conference Europe Middle East & North Africa Information Systems and Technologies to Support Learning. Springer; Cham, Switzerland: 2018. On the Efficiency of Scalar Multiplication on the Elliptic Curves; pp. 393–399. [Google Scholar]
- 54.Dawahdeh Z.E., Yaakob S.N., Othman R.R.B. A New Modification for Menezes-Vanstone Elliptic Curve Cryptosystem. J. Theor. Appl. Inf. Technol. 2016;85:290. [Google Scholar]
- 55.Das P., Giri C. An Efficient Method for text Encryption using Elliptic Curve Cryptography; Proceedings of the 2018 IEEE 8th International Advance Computing Conference (IACC); Greater Noida, India. 14–15 December 2018; pp. 96–101. [Google Scholar]
- 56.Keerthi K., Surendiran B. Elliptic curve cryptography for secured text encryption; Proceedings of the 2017 International Conference on Circuit, Power and Computing Technologies (ICCPCT); Kollam, India. 20–21 April 2017; pp. 1–5. [Google Scholar]
- 57.Bh P., Chandravathi D., Roja P.P. Encoding and decoding of a message in the implementation of Elliptic Curve cryptography using Koblitz’s method. Int. J. Comput. Sci. Eng. 2010;2:1904–1907. [Google Scholar]
- 58.Amounas F., El Kinani E. Fast mapping method based on matrix approach for elliptic curve cryptography. Int. J. Inf. Netw. Secur. (IJINS) 2012;1:54–59. [Google Scholar]
- 59.Muthukuru J., Sathyanarayana B. Fixed and Variable Size Text Based Message Mapping Technique Using ECC. [(accessed on 15 October 2020)];Glob. J. Comput. Sci. Technol. 2012 Available online: https://computerresearch.org/index.php/computer/article/view/448. [Google Scholar]
- 60.Barman P., Saha B. DNA Encoded Elliptic Curve Cryptography System for IoT Security. Int. J. Comput. Intell. 2019;2:7. [Google Scholar]
- 61.Duarah D., Uma V. International Conference on Emerging Current Trends in Computing and Expert Technology. Springer; Cham, Switzerland: 2019. Securing IoT Using Machine Learning and Elliptic Curve Cryptography; pp. 482–491. [Google Scholar]
- 62.Joglekar J., Bhutani S., Patel N., Soman P. International Conference on Sustainable Communication Networks and Application. Springer; Cham, Switzerland: 2019. Lightweight Elliptical Curve Cryptography (ECC) for Data Integrity and User Authentication in Smart Transportation IoT System; pp. 270–278. [Google Scholar]
- 63.Almajed H.N., Almogren A.S. SE-Enc: A Secure and Efficient Encoding Scheme Using Elliptic Curve Cryptography. IEEE Access. 2019;7:175865–175878. doi: 10.1109/ACCESS.2019.2957943. [DOI] [Google Scholar]
- 64.King B. Mapping an Arbritrary Message to an Elliptic Curve When Defined over GF (2n) IJ Netw. Secur. 2009;8:169–176. [Google Scholar]
- 65.Harvey D., van der Hoeven J. Faster integer multiplication using short lattice vectors. Open Book Ser. 2019;2:293–310. doi: 10.2140/obs.2019.2.293. [DOI] [Google Scholar]
- 66.Bazlur Rahman A.N.M. We Don’t Need StringBuilder for Simple Concatenation—DZone Java. [(accessed on 15 October 2020)];2019 Available online: https://dzone.com/articles/string-concatenation-performacne-improvement-in-ja.