Abstract
We theoretically investigate the problem of finding optimal characteristics of photon pairs, produced in the spontaneous parametric down-conversion (SPDC) process, for fiber-based quantum communication protocols. By using the accessible setup parameters, the pump pulse duration and the extended phase-matching function width, we minimize the temporal width of SPDC photons within the general scenario. This allows one to perform more effectively the temporal filtering procedure, which aims at reducing the noise acquired by the measurement devices. Moreover, we compare the obtained results with the achievable parameter values for SPDC sources based on -Barium Borate crystal. We also investigate the influence of non-zero detection timing jitter. Finally, we apply our optimization strategy to a simple quantum key distribution scheme to show that the full optimization of an SPDC source can potentially extend the maximal security distance by several tens of kilometres, which is around 30% more as compared to previous approaches.
Subject terms: Nonlinear optics; Quantum optics; Fibre optics and optical communications; Lasers, LEDs and light sources
Introduction
Quantum communication is a vast field of physical science focused on improving the process of information distribution among spatially separated entities with the use of quantum mechanics. The exploration of various types of quantum correlation and application of fundamental quantum laws has lead to a plethora of proposals for novel communication protocols, including quantum key distribution1,2, secret sharing3, quantum teleportation4 and dense coding5. However, the initially proposed theoretical versions of these protocols have typically assumed ideal performance of the setup elements required for their physical realization, which is unreachable in practice. As a consequence, the performance of real-life implementations of QC protocols has been severely limited.
Realization of many such schemes requires using sources of single photons or entangled photon pairs. One of the most popular types of them are the devices utilizing the phenomenon of spontaneous parametric down-conversion6,7. They have many advantages, including high quality of the emitted photons8,9, high generation and collection efficiency10–12 and relatively low cost of their construction. Therefore, they have been extensively used in practical implementations of many QC protocols13–17. However, photons born in the SPDC process are not monochromatic. Thus, they propagate through dispersive media (e.g. the standard telecommunication fibers) with wavelength-dependent velocity. As a consequence, their temporal width, defined as the standard deviation of the probability distribution function for the time of their arrival at the destination point, grows with the length of the utilized dispersive quantum channel. It forces the experimenter to define longer detection windows for the photon measurement system in order not to lose considerable amount of real signals. However, the longer detection windows are, the more noise is registered during the realization of a given QC protocol, negatively affecting its performance.
Taking into account the above consideration, the minimization of the temporal width of the emitted photons after their propagation through telecommunication fibers is very important. Nevertheless, to the best of our knowledge such a general optimization has not yet been done. Only recently it was shown that changing the properties of pairs of photons can indeed significantly influence the performance of quantum protocols18–20. A preliminary optimization of SPDC source for a specific setup configuration was also performed20. In this manuscript we generalize this optimization to an arbitrary QC scheme. We also investigate the influence of non-zero timing jitter of realistic detectors on the obtained results and discuss whether the theoretically optimal values can be implemented in practice. Finally, we estimate the advantage stemming from the optimization of SPDC source on the maximal security distance of a basic quantum key distribution (QKD) scheme.
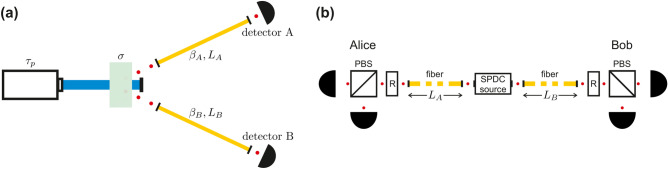
In our work we consider SPDC source of photon pairs based on a nonlinear crystal parametrized by the effective phase-matching function width , pumped by laser pulses of temporal width . Throughout this manuscript we assume that the information on the time moments at which the laser sends pump pulses to the crystal is available to everyone interested. Photons generated by the SPDC source are subsequently transfered to single-photon detectors through quantum channels of length and , characterized by the group velocity dispersion (GVD) equal to and , respectively. This scheme is illustrated in Fig. 1a. We use the following notation to simplify the analytical calculations: (for ). To show the potential to improve the performance of QC schemes by optimizing the SPDC source we also consider a basic setup configuration for the realization of BB84 protocol in the entanglement-based variant, presented in Fig. 1b. All the subsequent figures shown in this manuscript are made for . For the standard wavelength of 1550 nm it corresponds21 to the dispersion value of 18 ps/nm km, that is typical for single-mode fibers (SMFs)22, which are the most common telecommunication channels utilized in practical QC schemes. During the QKD security analysis we also assume the typical value of their attenuation coefficient: dB/km.
Figure 1.
Setup configurations. (a) The generic setup configuration for the detection of SPDC photons. (b) A simple discrete-variable QKD scheme with the source of entangled photon pairs placed outside of Alice’s and Bob’s laboratories. R denotes polarization rotators.
Results
Optimization of temporal widths
As has already been stated in the Introduction, in the context of QC applications it is desirable for the temporal widths of SPDC photons to be as narrow as possible. Therefore, a natural question is: what are the optimal values of the source parameters, and , for which the temporal widths of SPDC photons, written explicitly in the “Methods” section [formulas (3) and (4)], are the lowest? In practice it is much easier to calibrate the temporal width of pump laser pulses than to modify the effective phase-matching function for the nonlinear crystal, since the latter usually requires replacing the crystal itself. Therefore, we first consider the situation in which the experimenter can only change the pump laser utilized by the SPDC source, while the crystal is fixed.
In this case the temporal width of the unheralded photon A, , reaches its lowest value, equal to , for . Since dos not depend on , the above result is identical for the symmetric and asymmetric setup configurations. In the symmetric case also the temporal width of the heralded photon A, , reaches its minimum for the same value of . It reads: . On the othe hand, the optimization of over for the asymmetric setup configuration is much more complicated. In this case the function does not always have a global minimum and the conditions for its existence heavily depend on the relationship between , and . The details of this dependence can be found in the “Methods” section, along with the derivation of the above formulas for and .
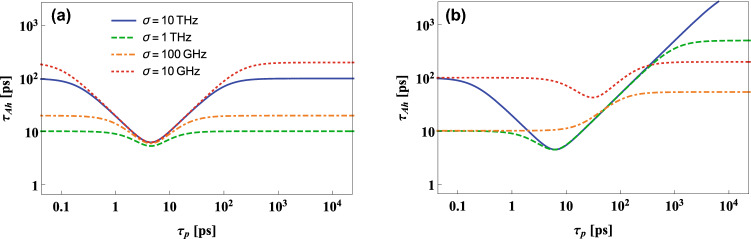
The examples of the relationship for the symmetric and highly asymmetric setup configurations can be seen in Fig. 2. In the symmetric case, presented in panel (a), the function has a well-defined minimum for any . Its value depends on the effective phase-matching function width relatively weekly, while the value of for which this minimum is reached is independent of . The situation is much different in the highly asymmetric case, illustrated in panel (b). Here both the optimal value of and the minimal value of significantly depend on the effective phase-matching function width. Moreover, for GHz (corresponding to nm at nm in terms of wavelength) none of the conditions for the existence of the global minimum of is fulfilled. In this situation is monotonically increasing function (see the orange dot-dashed line). It can also be seen that in the asymmetric scenario the comparison between the functions of plotted for different heavily depends on . For example, while for very short pump pulses the value of calculated for THz is much smaller than for GHz, it is the opposite for large . The situation like this cannot be seen in the symmetric case.
Figure 2.
The dependence of on the pump laser. The temporal width of the heralded photon A, , plotted as a function of the duration time of a pump laser pulse for the case when two standard single-mode fibers (SMFs) of length km and (a) km, (b) km are placed between the crystal and single-photon detectors. The legend corresponds to both panels.
Contrary to the scenario when the nonlinear crystal is fixed, full optimization of a SPDC source over the parameters and cannot be done analytically in the general case. Nevertheless, it can be performed for the symmetric setup configuration, when . This task has already been done in our previous paper18, where it was shown that in the symmetric case the optimal values of the SPDC source parameters are and . For these numbers the function reaches its absolute minimum, equal to . In the symmetric case exhibits high symmetry both as a function of and . It can be seen in Fig. 3a, where the temporal width of the photon A is plotted for km. For comparison, in Fig. 3b we plot for the highly asymmetric case of km and km. As for the type of spectral correlation between the photons produced by a partially or fully optimized SPDC source, in general situation it is impossible to find such a simple expression as the formula (9) in our previous paper18, which works only for the symmetric schemes. However the conclusions that can be drawn from the numerical analysis of this issue are generally the same as before: fully optimized source produces spectrally uncorrelated photons, while the type and strength of correlation generated in the case when only the pumping laser is optimized depend on the relationship between the effective phase-matching function width and the channel parameters and . For short (long) propagation distances the optimal correlation is positive (negative).
Figure 3.
The dependence of on the pump laser and the nonlinear crystal. Logarithm of the temporal width of the heralded photon A, , at the entrance to the detector, plotted as a function of the duration time of the pump laser pulse, , and the effective phase-matching function width of the nonlinear crystal, , for the case when the source is connected with the detectors by SMFs of length km and (a) km or (b) km. The contours shown in both plots represent values from to with constant 0.2 spacing.
Dependence on the length of the heralding arm
For the asymmetric QC scheme it is possible to reduce the temporal width of SPDC photons propagated through one of its arms by introducing a proper amount of dispersion to the other arm (e.g. by adjusting its length). This can have positive effect on the performance of QC protocols in some setup configurations, as has already been shown in the context of the asymmetric QKD scenario19. However, the framework used in the aforementioned work was based on the analysis of spectral correlation and generated photon widths. It gave general insight into the physical mechanisms yielding the optimal performance of the QKD scheme, but must be reformulated to be directly related to the typical experimental scenario. Here we accomplish this goal using the parameters and .
In Fig. 4 it can be seen how the temporal width , optimized over the duration time of the pump laser pulses, changes with different values of and . This picture shows that the conditions for the function to have a global minimum, derived in the “Methods” section, are always fulfilled when the channel parameters, and , are of the same order of magnitude. Only for highly asymmetric schemes this function can be minimized asymptotically for or . Furthermore, if the effective phase-matching function width is significantly larger than its optimal value, , extending the length of the heralding arm always leads to the reduction of . This effect is more prominent for smaller distances, while for the temporal width of the heralded photon asymptotically decreases to a fixed value. On the other hand, when , extending the heralding arm has the opposite effect on to the one described above. Therefore, one can conclude that for the asymmetric QKD scheme the maximal security distance in one arm can be extended by introducing more dispersion to the other arm, as long as . This conclusion is similar to the one stated in our previous work19. However, it is important to underline that contrary to the aforementioned paper, here the global time reference, i.e. the timing information on the pump pulses, is assumed to be known by Alice and Bob, as has already been stated in the Introduction. Consequently, it can potentially have much broader practical application than it was previously thought19.
Figure 4.

The dependence of on nonlinear crystal and the length of the heralding arm. Logarithm of the temporal width of the heralded photon A at the entrance to the detector, , shown as a function of the length of the heralding SMF quantum channel, , and the effective phase-matching function width of the nonlinear crystal, , plotted for the case when the source is connected with the detector A by another SMF quantum channel of length km. For every pair of values the calculated temporal width has been optimized over the pump laser pulse duration . The overshadowed area near the left [right] edge of the figure corresponds to the range of , for which the optimal value of is reached for []. For other combinations of and the optimal value of is given by the formula (7). The spacing between the neighboring contours becomes smaller than 0.2 for in order to better illustrate how this function behaves near its minimum.
Since the simplest way of introducing more dispersion to the heralding arm is to use longer telecommunication fiber, one should be aware of the fact that such action would always reduce the probability of registering the heralding photon. Therefore, one should avoid it as long as the length of the heralded arm is short enough to provide the QKD security even without introducing additional dispersion, as it would unnecessarily decrease the key generation rate. Only when the length of the heralded arm is indeed too long for the security of the traditional setup configuration, lengthening the heralding fiber may provide positive results for the participants of the QKD protocol.
Dependence on the detector timing jitter
It can be seen in Figs. 2, 3 and 4 that if the SMF connecting the source with the detector A is of the order of km, the temporal width can be reduced even below the level of ps. This value is comparable with the timing jitter of the best currently existing single-photon detectors23–26. In order to estimate the range of fiber lengths for which non-zero jitter can have significant influence on the temporal widths of SPDC photons, in Fig. 5 we compare the temporal widths of the heralded photon A, , optimized over the source parameters, and , calculated as a function of the propagation distance for a few different values of the timing jitter and . The mathematical formula for is derived in the “Methods” section. The plots in Fig. 5 are made for the symmetric QC scheme. As one can see there, if and are shorter than a few kilometers, the jitter significantly influences even if it is much smaller than in the case of the state-of-the-art single-photon detectors. Therefore, to exploit the full potential of the optimization method presented in this paper further development of photon detection technology will be needed. At present, however, it is certainly possible to make the influence of detection jitter negligible if the propagation distance is of the order of tens of kilometers or more. To conclude, the results of our investigation, presented in Fig. 5, indicate that if the experimenter wants to fully optimize the short-distance QC scheme, the detection jitter of realistic single-photon detectors can become one of the most important factors. On the other hand, for long-distance communication schemes the jitter can be safely neglected.
Figure 5.
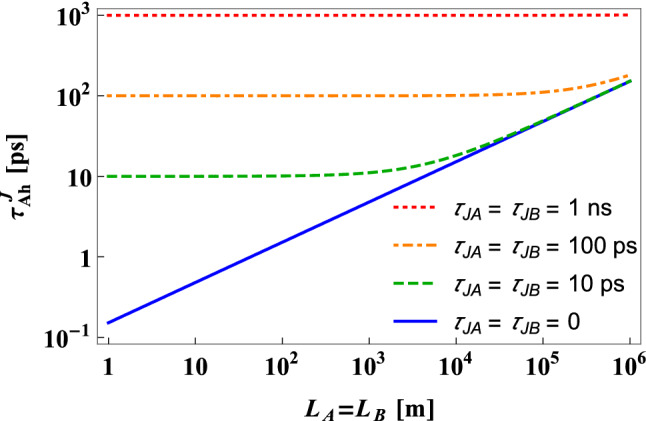
The influence of non-zero timing jitter on . Temporal width of the heralded photon, , given by the formula (8),optimized over the SPDC source parameters and , plotted as a function of the length of SMFs separating the source and the photon detection systems in the case of symmetric setup configuration. The detectors’ timing jitter is defined as the standard deviation of the detection time probability function.
Realistic values of the effective phase-matching function width
In principle, in the case of any specific QC setup configuration, using the optimization rules presented in this paper allows the experimenter to easily find the most favourable values of a pump laser pulse duration and an effective phase-matching function width. However, one may wonder if these theoretically optimal values would be achievable for realistic SPDC sources. It is much easier to answer this question in the context of the pump laser pulse duration, owing to the variety of commercially available lasers, ranging from the CW to femtosecond ones. Since the optimal value of generally grows with the propagation distance and already for m it is approximately equal to fs, one can safely say that the theoretically optimal pump laser pulse duration should be achievable for basically every realistic QC scheme.
Performing similar analysis in the context of the effective phase-matching function width associated with different kinds of nonlinear crystals is much more complexed. The value of depends not only on the type of nonlinear material, but also on several other parameters such as the crystal length or its optical axis orientation27. However, in order to get some intuition in this matter, we analyzed here a specific case of BBO crystal cut for degenerate type I SPDC process, in which nm pump photons are converted to pairs of nm photons. The results of our investigation are presented in Fig. 6, where the effective phase-matching function width was plotted as a function of the angle between the central propagation directions of the pump photons and the generated photons. The calculations were made for several different values of the crystal length, , and the width of transverse spatial mode collected by the SMFs, . Additionally, the optimal values of for symmetric QC setup configuration using SMFs of length km and km were indicated in this figure for comparison.
Figure 6.
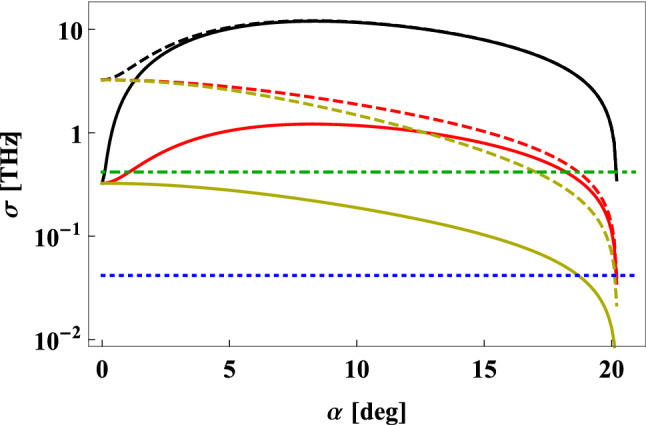
Realistic values of for BBO crystal. The effective phase-matching function width, , calculated for type I SPDC process, plotted as a function of the angle between the central propagation directions for the pump photons and the generated photons. The plots are made for the crystal length equal to Lcryst = 1 cm (solid lines) and Lcryst = 1 mm (dashed lines), and for the following widths of the transverse spatial modes collected by the SMFs, : 10 μm (black lines), 100 μm (red lines), 1 mm (yellow lines). Blue dotted (green dot-dashed) line correspond to the optimal value of , calculated for the symmetric QC setup with SMF quantum channels of 100 km (1 km) length.
The most important conclusion that can be drawn from Fig. 6 is that for the source based on BBO crystal, analyzed here, the theoretically optimal values of the effective phase-matching function width can be very difficult to obtain in most practical situations. This goal seems to be especially hard to achieve for , which is often the most convenient one in practice. In this situation, even when using exceptionally long BBO crystals, one may hope to obtain width only for short-distance QC schemes. In principle, smaller widths of the effective phase-matching function can be get when the values of are sufficiently large and the BBO crystal is cut to emit pairs of photons at broad angle from the direction of propagation of the pump laser pulses. However, this kind of SPDC source would be significantly more difficult to construct. Moreover, its pair production efficiency and heralding efficiency would most likely be much smaller than for the case of collinear configuration. This would negatively affect the performance of many QC protocols28.
An example of application: quantum key distribution
The potential of the presented method for the optimization of a SPDC source for its use in QC applications can be seen in Fig. 7a, where we plot the lower bound for the key generation rate that can be obtained from the realization of BB84 protocol in the symmetric version of the setup configuration schematically illustrated in Fig. 1b. We analyzed the cases of (1) non-optimized source with and , (2) the source with the same , but optimized over the value of and (3) the fully optimized SPDC source. The value of the pump laser pulse duration used in the case (1) is roughly the same as in one of the rare experimental realizations of long-distance QKD with SPDC sources29. Since the authors of the aforementioned paper did not calculate the effective phase-matching function width for their crystal, we decided to use a typical value here. Technical details of the security analysis can be found in the “Methods” section.
Figure 7.
Key generation rate. The lower bound for the key generation rate, K, plotted as a function of the length of the SMF used to connect the SPDC source with the laboratory of Alice for the BB84 protocol performed in (a) symmetric, (b) asymmetric version of the QKD scheme presented in Fig. 1b. In panel (a) the plots are calculated for the following values of the source parameters: and (dashed yellow line), and (dotted red line), and (solid black line). The three aforementioned curves are drawn assuming ideal single-photon detectors with no timing jitter. Additionally, dot–dashed black line illustrates the lower bound for the key generation rate calculated in the case when the jitter of all the detectors utilized by Alice and Bob is , while the source parameters are and . In panel (b) all of the plots are made for , while the values of are numerically optimized and the jitter is assumed to be zero.
It can be seen in Fig. 7a that in principle by fully optimizing the source the maximal security distance for the analyzed scheme can be extended by almost sixty kilometers for each of the two existing quantum channels, which is around 30% compared to the non-optimized case. Moreover, even partial optimization of the source, just over the pump laser pulse duration, can provide the legitimate participants of the BB84 protocol with about of additional security distance. It is also important to notice, that the results plotted in Fig. 7a do not change considerably if we assume that Alice and Bob use single-photon detectors characterized by detection timing jitter of , which is well above the best achievable value for the modern devices23–25. In this situation the maximal security distance is shortened only by a few kilometers compared to the case with ideal single-photon detectors. This result is consistent with the jitter influence analysis presented earlier in this work.
The results shown in Fig. 7a were obtained for the security analysis of the symmetric version of the QKD setup. In Fig. 7b we present the results concerning more general situation, in which the two SMFs connecting the SPDC source with Alice and Bob are not of the same length. In this part of our work we specifically focus on checking how changing the length of Bob’s fiber can influence the maximal security distance between the source and Alice. This investigation is motivated by the possibility of decreasing the temporal width of the heralded SPDC photon by extending the distance between the source and the heralding detector, discussed before. While such possibility is available only when (see Fig. 4a), the plots shown in Fig. 6 strongly suggest that this requirement can be fulfilled in most practical situations. As can be seen in Fig. 7b, the maximal security distance between the source and Alice can be increased by several tens of kilometers just by optimizing the value of for any given , instead of fixing it on some short level.
Discussion
In this work we performed theoretical optimization of SPDC photon pairs for QC schemes with two dispersive quantum channels of arbitrary lengths. It was done over the pump laser pulse duration and the effective phase-matching function width of nonlinear crystal. We derived an analytical formula for the best setting of the pump laser for a given crystal in the most general case. Moreover, we performed full numerical optimization of a SPDC source, demonstrating the possibility to further refine the performance of quantum protocols. We also showed that the temporal width of a SPDC photon can be minimized in one of two possible ways, depending on the exact value of the effective phase-matching function width: either by increasing the dispersion in the quantum channel or by decreasing it. The first (second) of these possibilities is available when the effective phase-matching function width is larger (smaller) than its optimal value.
To compare theoretical predictions of our work with capabilities of realistic SPDC sources we investigated the source based on BBO crystal, designed for type I SPDC process generating pairs of photons. For such source we performed analytical estimation of the effective phase-matching function width. It should be noted here that precise calculation of this parameter can be done only numerically and is beyond the scope of this analysis. The obtained results suggests that for most QC schemes the achievable value of the effective phase-matching function width would be significantly larger than the theoretically optimal one. While in some situations the optimal value could be achieved, it would often require relatively large angles between the pump laser pulse direction and the propagation directions of the generated photons. However, such setup configuration would negatively affect the efficiency of SPDC source. The above consideration raises the question in what situations it would be more beneficial to abandon the full optimization of the SPDC source based on BBO crystal and use the collinear configuration to produce pairs of photons, and when it would be better to push for the full optimization at the expense of efficiency of the source. Further analysis of this problem would be required to reliably answer such question. Moreover, similar investigation performed for other types of nonlinear crystals would be necessary.
To demonstrate the potential for improving the performance of QC protocols by optimizing SPDC source, we analyzed simple entanglement-based QKD scheme. We showed that the maximal secure communication distance can be significantly increased just by properly adjusting the pump laser. Furthermore, if the full optimization of the source is possible, the improvement may even reach in comparison with the practical non-optimized scheme. We also showed that in realistic cases the detection timing jitter reduces the maximal security distance by no more than a few kilometers. We would like to strongly underline here that the presented method for improving the QKD security is not limited to the particular scheme analyzed in our work. Since its essence is the reduction of the amount of uncorrelated noise registered by photon detectors during the key generation process by minimizing the widths of detection windows, it has the potential to significantly improve the security of all single-photon-based protocols, including the currently most popular measurement-device-independent30 and twin-field31 schemes, as long as they are implemented using SPDC sources.
Nevertheless, it should be remembered that the effectiveness of this method could be significantly smaller if the decrease of the key generation rate to zero at the maximal security distance was mainly caused by some other factors than the reduction of signal-to-noise ratio below the critical level. Specifically, if the SPDC source is used in a prepare-and-measure type of QKD setup configuration, the security of such scheme could be higly dependent on the probability for producing more than one pair of photons, which is always non-zero in realistic situations. However, the damaging influence of the multipair generation events on QKD security can be efficiently reduced by using decoy-pulse method32, which greatly limits the possibility to attack multiphoton pulses by a potential eavesdropper. While most of the recent record-breaking long-distance realizations of QKD protocols reported in the literature have been implemented using weak coherent pulses and decoy-pulse method33–35, many papers suggest that heralded single-photon sources could potentially be better for this task36–38. This notion can be supported by taking into account the recent advances in the field of heralding efficiency of the SPDC sources10–12. While the strong temporal broadening of the generated signals has always been a serious obstacle for using these sources in fiber-based long-distance communication, their optimization method presented here allows to overcome this important problem.
Taking into account the above considerations, the noise registered by the measurement systems during the key generation procedure appears to be much bigger issue for long-distance QC than the aforementioned imperfection of photon pair sources. Since in our work we considered dark counts as the only source of noise, one can expect that the SPDC source optimization method can provide even better results in more realistic cases. It seems to be especially promising for the QKD performed in commercial fibers populated by strong classical signals, where the level of channel noise caused by those signals is typically very high39. Our results can be particularly useful in the case of asymmetric QKD scheme in which the distance between one of the parties and the source is relatively small and the goal is to maximally extend the security length of the quantum channel connecting the source with the other party. A good example of such scenario can be found when considering a communication between a single individual user and a distant node in a multilevel quntum network with several access networks connected to the central backbone40,41. Then, the maximal security distance between two separate access networks could be substantially increased by introducing more dispersion to the quantum channels connecting the individual users with their respective central nodes, as we also demonstrated in this work.
Methods
Temporal widths of SPDC photons
The spectral wavefunction of the pairs of photons produced by an SPDC source can be written in the following approximate form27,42:
| 1 |
where , are frequency detunings from the respective central frequencies. To calculate the temporal wavefunction of the pair of SPDC photons after their propagation through the dispersive media we utilize the following formula18:
| 2 |
where denotes the initial temporal wavefunction. It can be obtained from through Fourier transform.
Without any loss of generality we focus on calculating the temporal width of the photon entering the detector A (photon A) in Fig. 1a. If an experimenter knows nothing about the detection time of the other photon (photon B), the probability distribution function for the detection time of photon A can be calculated as the marginal distribution . In this case the temporal width of photon A reads:
| 3 |
On the other hand, if the detection time of photon B is known to be , the probability distribution function for the detection time of photon A takes the form of . Its temporal width is then given by:
| 4 |
The temporal width of photon B in the non-heralded and heralded case can be obtained immediately from the expressions (3) and (4), respectively, by switching to and vice versa.
Optimization of the pump laser in the asymmetric case
The conditions for the function to have a well-defined global minimum are very complicated in the general case. However, they can be considerably simplified if we assume that and have the same sign, which is certainly a justified assumption in realistic situations. To write them explicitly we first introduce the following notation:
| 5 |
| 6 |
Here we focus on the typical QC scheme with SMFs, in which case it is always . Then the right-hand side of the expression (4) reaches its minimum for
| 7 |
in the three following cases: (1) when , (2) when and one of the inequalities or is true, (3) when and one of the inequelities or is true. If none of the above sets of conditions is fulfilled, then the function does not have a global minimum. If but it is monotonically increasing, meaning that the lowest temporal width of photon A is reached for . On the other hand if but the function always decreases when grows. Therefore, in this situation the lowest temporal width of photon A is reached for .
Temporal widths of SPDC photons when the detection timing jitter is non-zero
When the timing jitter, , is non-zero the difference between the detection time of photon A, , and the time of its arrival at the measurement system, , can be described by the probability distribution function , where is the normalization constant. Then, the probability distribution for the detection time of this photon in the case when the detection time of photon B is unknown can be calculated as . The marginal distribution function has already been defined in the text between the Eqs. (2) and (3). It is straightforward to check that the standard deviation of is equal to . The above formula gives the temporal width of the non-heralded photon A for the case of non-zero jitter.
While the value of depends only on the timing jitter of the detector A, the analogous temporal width of photon A found in the heralded case, , would be influenced also by the timing jitter of the other detector, . In order to calculate it, one has to take the joint probability formula for the detection of photon A at the time and the detection of photon B at the time , which can be derived from (2) as , and modify it to the following form: . In the above formula is the arrival time of photon B to the heralding detector. The probability distribution of the detection time of photon A, conditioned on the detection of photon B at the time , is then given by . The standard deviation of the resulting function is
| 8 |
where is the temporal width of the photon A calculated for zero jitter case and .
Effective phase-matching function width for the BBO crystal
The approximate value of the effective phase-matching function width for a particular nonlinear crystal can be calculated by using the following formula: , where is the width of transverse spatial mode collected by the SMF and L is the length of the crystal27. Furthermore, by and we defined the partial derivatives of the phase mismatch over the transverse component of wave vector of the produced signal photons and their angular frequencies, respectively. In this work we are interested in type I SPDC process taking place in BBO crystal. It is a negative uniaxial crystal, which means that the pump photons have to be extraordinarily polarized, while the polarizations of signal and idler photons are always ordinary43. Assuming that the pump pulses propagate along the z direction, the phase mismatch for the investigated process is given by , where () is the angular frequency of the signal (idler) photon and () is its transverse wave vector component. The refractive index for pump photons depends on the angle between the Z axis and the optic axis, , as follows43:
| 9 |
The approximate formula for the dependence of the refractive index of the ordinarily [extraordinarily] polarized photons propagating in the BBO crystal, [], on their angular frequency can be found in the literature43. The expression for can be obtained by solving the equation .
QKD security analysis
For the BB84 protocol realized in the setup configuration illustrated in Fig. 1b the lower bound on the key generation rate is given by , where is the Shannon entropy and Q denotes the quantum bit error rate (QBER) in the raw key generated by the legitimate participants of the protocol44. In the above formula is the probability of accepting a given event by Alice and Bob for the process of key generation. Obviously, both Q and depend on the duration time of the detection windows chosen by the participants of the protocol. For a single such window of width the probability for registering a photon of temporal width is given by
| 10 |
On the other hand, the probability for registering a dark count in one of the two single-photon detectors can be calculated as
| 11 |
where d is the dark count rate for a given single-photon detector. For the calculations performed in this work we assume that both in the case of Alice’s and Bob’s detectors. Taking different values of d would obviously influence the obtained maximal security distances, but would not change the properties of different curves presented in Fig. 7, nor the relationships between them. Also, for every pair of the investigated values of and we separately optimize the parameters and in order to get the best possible outcomes for the legitimate parties. We consider the situation in which the dark counts are the only source of errors in the raw key. Since narrowing the detection windows reduces all the possible errors that are uncorrelated with the real signals in exactly the same way, adding such errors to the model can be easily made just by appropriate increase of d. On the other hand, the errors that are connected to the real signals, e.g. polarization rotation, would only slightly change the obtained results and not in qualitative way.
We consider the case of perfect SPDC source, always emitting a single pair of photons when the pump pulse propagates through the crystal. With this assumption the probability for the scheme illustrated in Fig. 1b can be approximated by
| 12 |
where () is the transmittance of quantum channel connecting the SPDC source with Alice (Bob), given by (). The probabilities for a dark count to be registered by Alice or Bob in a particular detection window, denoted by and respectively, can be calculated by inserting the expression (4), and the analogous expression for the temporal width of the heralded photon B, into the formula (11). On the other hand, in order to obtain one should use the Eq. (3) instead of (4). This probability, appearing only in the last term on the right-hand side of Eq. (13), is needed to properly account for the case when neither of the signal photons is detected by the measurement systems of Alice and Bob. In this situation one of the dark counts registered by them has to be treated as a “heralding” click, while the other one is “heralded” by it (obviously, the exact choice does not matter here, as can be confirmed by checking that ). On the other hand, the second and third terms on the right-hand side of Eq.(13) correspond to the case when only one of the two photons produced by the source causes a click in one of the measurement systems, but the event is still accepted for the key generation process due to a dark count registered in the other detection system in the appropriately narrowed time window. Finally, the first term on the right-hand side of Eq.(13) accounts for the desired situation in which both SPDC photons from a given pair are detected by Alice’s and Bob’s measurement systems.
In the case of the simplified QKD scheme considered in our work an error in the raw key can be generated only if at least one of the signal photons from a given SPDC pair is lost, but the event is still accepted for key generation. Since dark counts occur in the detectors of Alice and Bob totally randomly, in all of such situations the error probability is . Therefore, QBER can be calculated using the expression
| 13 |
Acknowledgements
The authors acknowledge financial support by the Foundation for Polish Science (FNP) (project First Team co-financed by the European Union under the European Regional Development Fund). We wish to thank National Laboratory of Atomic, Molecular and Optical Physics, Torun, Poland for the support.
Author contributions
M.L. performed the analytical and numerical calculations. P.K. initiated and supervised the research. Both authors contributed to writing the paper.
Competing interests
The authors declare no competing interests.
Footnotes
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, India, vol. 11, 175–179 (IEEE, New York, 1984).
- 2.Ekert AK. Quantum cryptography based on bell theorem. Phys. Rev. Lett. 1991;67:661–663. doi: 10.1103/PhysRevLett.67.661. [DOI] [PubMed] [Google Scholar]
- 3.Hillery M, Bužek V, Berthiaume A. Quantum secret sharing. Phys. Rev. A. 1999;59:1829–1834. doi: 10.1103/PhysRevA.59.1829. [DOI] [Google Scholar]
- 4.Bennett CH, et al. Teleporting an unknown quantum state via dual classical and Einstein–Podolsky–Rosen channels. Phys. Rev. Lett. 1993;70:1895. doi: 10.1103/PhysRevLett.70.1895. [DOI] [PubMed] [Google Scholar]
- 5.Bennett CH, Wiesner SJ. Communication via one- and two-particle operators on Einstein–Podolsky–Rosen states. Phys. Rev. Lett. 1992;69:2881. doi: 10.1103/PhysRevLett.69.2881. [DOI] [PubMed] [Google Scholar]
- 6.Louisell WH, Yariv A, Siegman AE. Quantum fluctuations and noise in parametric processes. I. Phys. Rev. 1961;124:1646–1654. doi: 10.1103/PhysRev.124.1646. [DOI] [Google Scholar]
- 7.Burnham DC, Weinberg DL. Observation of simultaneity in parametric production of optical photon pairs. Phys. Rev. Lett. 1970;25:84–87. doi: 10.1103/PhysRevLett.25.84. [DOI] [Google Scholar]
- 8.Fasel S, et al. High-quality asynchronous heralded single-photon source at telecom wavelength. New J. Phys. 2004;6:163. doi: 10.1088/1367-2630/6/1/163. [DOI] [Google Scholar]
- 9.Bock M, Lenhard A, Chunnilall C, Becher C. Highly efficient heralded single-photon source for telecom wavelengths based on a ppln waveguide. Opt. Express. 2016;24:23992–24001. doi: 10.1364/OE.24.023992. [DOI] [PubMed] [Google Scholar]
- 10.Pomarico E, Sanguinetti B, Guerreiro T, Thew R, Zbinden H. MHz rate and efficient synchronous heralding of single photons at telecom wavelengths. Opt. Express. 2012;20:23846. doi: 10.1364/OE.20.023846. [DOI] [PubMed] [Google Scholar]
- 11.Ramelow S, et al. Highly efficient heralding of entangled single photons. Opt. Express. 2013;21:6707. doi: 10.1364/OE.21.006707. [DOI] [PubMed] [Google Scholar]
- 12.Kaneda F, Garay-Palmett K, U’Ren AB, Kwiat PG. Heralded single-photon source utilizing highly nondegenerate, spectrally factorable spontaneous parametric downconversion. Opt. Express. 2016;24:10733–10747. doi: 10.1364/OE.24.010733. [DOI] [PubMed] [Google Scholar]
- 13.Mattle K, Weinfurter H, Kwiat PG, Zeilinger A. Dense coding in experimental quantum communication. Phys. Rev. Lett. 1996;76:4656–4659. doi: 10.1103/PhysRevLett.76.4656. [DOI] [PubMed] [Google Scholar]
- 14.Bouwmeester D, et al. Experimental quantum teleportation. Nature (London) 1997;390:575–579. doi: 10.1038/37539. [DOI] [Google Scholar]
- 15.Pan J-W, Bouwmeester D, Weinfurter H, Zeilinger A. Experimental entanglement swapping: Entangling photons that never interacted. Phys. Rev. Lett. 1998;80:3891–2894. doi: 10.1103/PhysRevLett.80.3891. [DOI] [Google Scholar]
- 16.Jennewein T, Simon C, Weihs G, Weinfurter H, Zeilinger A. Quantum cryptography with entangled photons. Phys. Rev. Lett. 2000;84:4729–4732. doi: 10.1103/PhysRevLett.84.4729. [DOI] [PubMed] [Google Scholar]
- 17.Tittel W, Zbinden H, Gisin N. Experimental demonstration of quantum secret sharing. Phys. Rev. A. 2001;63:042301. doi: 10.1103/PhysRevA.63.042301. [DOI] [Google Scholar]
- 18.Sedziak K, Lasota M, Kolenderski P. Reducing detection noise of a photon pair in a dispersive medium by controlling its spectral entanglement. Optica. 2017;4:84. doi: 10.1364/OPTICA.4.000084. [DOI] [Google Scholar]
- 19.Lasota M, Kolenderski P. Quantum communication improved by spectral entanglement and supplementary chromatic dispersion. Phys. Rev. A. 2018;98:062310. doi: 10.1103/PhysRevA.98.062310. [DOI] [Google Scholar]
- 20.Sedziak-Kacprowicz, K., Lasota, M. & Kolenderski, P. Remote temporal wavepacket narrowing. Sci. Rep.9, 3111 (2019). [DOI] [PMC free article] [PubMed]
- 21.The recalculation can be easily done e.g. using the script placed on the website www.rp-photonics.com/group_velocity_dispersion.html.
- 22.See e.g. Corning SMF-28e+ Optical Fiber specifications. www.corning.com/media/worldwide/coc/documents/Fiber/PI1463_07-14_English.pdf.
- 23.Shcheslavskiy V, et al. Ultrafast time measurements by time-correlated single photon counting coupled with superconducting single photon detector. Rev. Sci. Instrum. 2016;87:053117. doi: 10.1063/1.4948920. [DOI] [PubMed] [Google Scholar]
- 24.Yan Z, et al. An ultra low noise telecom wavelength free running single photon detector using negative feedback avalanche diode. Rev. Sci. Instrum. 2012;83:073105. doi: 10.1063/1.4732813. [DOI] [PubMed] [Google Scholar]
- 25.Tosi, A. et al. Ingaas/inp single-photon avalanche diodes show low dark counts and require moderate cooling. In Society of Photo-Optical Instrumentation Engineers (SPIE) Conference Series, vol. 7222, 72221G (Proc. of SPIE, 2009).
- 26.Divochiy A, et al. Single photon detection system for visible and infrared spectrum range. Opt. Lett. 2018;43:6085–6088. doi: 10.1364/OL.43.006085. [DOI] [PubMed] [Google Scholar]
- 27.Gajewski A, Kolenderski P. Spectral correlation control in down-converted photon pairs. Phys. Rev. A. 2016;94:013838. doi: 10.1103/PhysRevA.94.013838. [DOI] [Google Scholar]
- 28.Kolenderski P, Wasilewski W, Banaszek K. Modelling and optimization of photon pair sources based on spontaneous parametric down-conversion. Phys. Rev. A. 2009;80:013811. doi: 10.1103/PhysRevA.80.013811. [DOI] [Google Scholar]
- 29.Sun P, Guo J, Wang T, Liu L, Feng J. Method for measuring the intensity distribution of a small beam spot with phase retrieval. Opt. Laser Eng. 2014;57:109–113. doi: 10.1016/j.optlaseng.2014.01.020. [DOI] [Google Scholar]
- 30.Lo H-K, Curty M, Qi B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012;108:130503. doi: 10.1103/PhysRevLett.108.130503. [DOI] [PubMed] [Google Scholar]
- 31.Lucamarini M, Yuan ZL, Dynes JF, Shields AJ. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature (London) 2018;557:400–403. doi: 10.1038/s41586-018-0066-6. [DOI] [PubMed] [Google Scholar]
- 32.Hwang W-Y. Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 2003;91:057901. doi: 10.1103/PhysRevLett.91.057901. [DOI] [PubMed] [Google Scholar]
- 33.Korzh B, et al. Provably secure and practical quantum key distribution over 307 km of optical fibre. Nat. Photon. 2015;9:163–168. doi: 10.1038/nphoton.2014.327. [DOI] [Google Scholar]
- 34.Yin H-L, et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Opt. Express. 2016;117:190501. doi: 10.1103/PhysRevLett.117.190501. [DOI] [PubMed] [Google Scholar]
- 35.Boaron A, et al. Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett. 2018;121:190502. doi: 10.1103/PhysRevLett.121.190502. [DOI] [PubMed] [Google Scholar]
- 36.Wang Q, Wang X-B, Guo G-C. Practical decoy-state method in quantum key distribution with a heralded single-photon source. Phys. Rev. A. 2007;75:012312. doi: 10.1103/PhysRevA.75.012312. [DOI] [Google Scholar]
- 37.Wang Q, Wang X-B. Efficient implementation of the decoy-state measurement-device-independent quantum key distribution with heralded single-photon sources. Phys. Rev. A. 2013;88:052332. doi: 10.1103/PhysRevA.88.052332. [DOI] [Google Scholar]
- 38.Zhu J-R, Li J, Zhang C-M, Wang Q. Parameter optimization in biased decoy-state quantum key distribution with both source errors and statistical fluctuations. Quantum Inf. Process. 2017;16:238. doi: 10.1007/s11128-017-1687-7. [DOI] [Google Scholar]
- 39.Eraerds P, Walenta N, Legre M, Gisin N, Zbinden H. Quantum key distribution and 1 gbit/s data encryption over a single fibre. New J. Phys. 2010;12:063027. doi: 10.1088/1367-2630/12/6/063027. [DOI] [Google Scholar]
- 40.Elkouss D, Martínez-Mateo J, Ciurana A, Martín V. Secure optical networks based on quantum key distribution and weakly trusted repeaters. IEEE J. Opt. Commun. Netw. 2013;5:316–328. doi: 10.1364/JOCN.5.000316. [DOI] [Google Scholar]
- 41.Ciurana A, et al. Quantum metropolitan optical network based on wavelength division multiplexing. Opt. Express. 2014;22:1576–1593. doi: 10.1364/OE.22.001576. [DOI] [PubMed] [Google Scholar]
- 42.Lutz T, Kolenderski P, Jennewein T. Demonstration of spectral correlation control in a source of polarization entangled photon pairs at telecom wavelength. Opt. Lett. 2014;39:1481. doi: 10.1364/OL.39.001481. [DOI] [PubMed] [Google Scholar]
- 43.Dmitriev VG, Gurzadyan GG, Nikogosyan DN. Handbook of Nonlinear Optical Crystals. 3. Berlin: Springer; 1999. [Google Scholar]
- 44.Kraus B, Gisin N, Renner R. Lower and upper bounds on the secret-key rate for quantum key distribution protocols using one-way classical communication. Phys. Rev. Lett. 2005;95:080501. doi: 10.1103/PhysRevLett.95.080501. [DOI] [PubMed] [Google Scholar]