Abstract
In this paper, the multi-state synchronization of chaotic systems with non-identical, unknown, and time-varying delay in the presence of external perturbations and parametric uncertainties was studied. The presence of unknown delays, unknown bounds of disturbance and uncertainty, as well as changes in system parameters complicate the determination of control function and synchronization. During a synchronization scheme using a robust-adaptive control procedure with the help of the Lyapunov stability theorem, the errors converged to zero, and the updating rules were set to estimate the system parameters and delays. To investigate the performance of the proposed design, simulations have been carried out on two Chen hyper-chaotic systems as the slave and one Chua hyper-chaotic system as the master. Our results showed that the proposed controller outperformed the state-of-the-art techniques in terms of convergence speed of synchronization, parameter estimation, and delay estimation processes. The parameters and time delays were achieved with appropriate approximation. Finally, secure communication was realized with a chaotic masking method, and our results revealed the effectiveness of the proposed method in secure telecommunications.
Keywords: time-delayed chaotic systems, adaptive-robust control, multi-state synchronization, unknown time delays, secure communications, time varying parameter, circular multi state synchronization
1. Introduction
Applications of digital telecommunications can be seen in all aspects of daily life and all industries including medicine and education, as well as social interactions [1]. Hence, there is a need to have secure communication. To do this, many cryptography methods have been introduced, mainly encoding the data from the sender and decoding them at the receiver [1]. Cryptographical methods are based on various schemes, and a number of related papers have been published in this field [2,3,4,5]. There has been a considerable amount of work done in this field, and chaotic systems play a significant role among all cryptographical schemes [6,7,8].
One of the fundamental characteristics of chaotic systems is the extreme response to small changes in initial circumstances. The main goal of proposing synchronization methods is the suitable tuning of controller parameters in chaotic systems [9,10,11,12]. In chaotic synchronization, the vector state of the master system follows the slave system [13]. Various control-based schemes have been used previously for synchronization, such as adaptive [14,15,16], sliding mode [17,18], back stepping [19], fuzzy [20], predictive [21], and robust [22].
The work on applications of chaotic synchronization in secure communication has grown dramatically in recent years [23,24,25,26,27,28,29,30,31,32,33,34,35,36]. Developing control systems for synchronization of various chaotic systems has been one of the main focuses of prior works, aiming to improve security in communication. Furthermore, few researchers have concentrated on the hardware implementation of these systems in order to create reliable and rapid hardware for sending and receiving data securely [23]. The summary of various works done on this topic is given below.
Çiçek et al. [24] conducted the design and implementation of an analog circuit of a secure telecommunications system based on slipping mode control (SMC). The chaos system is the jerk, which is less complex than other chaotic systems. The most significant novelty of this work is applying SMC synchronization along with the jerk chaos system, which was introduced for the first time. The results of Op-Amp-based analog circuit simulation in SMC and jerk-based synchronization demonstrated the effectiveness of the proposed method.
A method based on a four-dimensional chaotic system has been proposed by Ayub Khan et al. [25]. The chaotic system proposed is of the fractional-order type, contributing greatly to the confidentiality of information. The results obtained justified the theoretical scheme and simulation results.
Yu et al. [26] recommended a system based on hyper-chaotic theory for secure telecommunications. The proposed chaotic system is multistable four-wing memristive (FWMHS), which is five-dimensional and was used to conduct the experiments. The disturbance included in the inputs of the proposed method enhanced the security factor in telecommunications. The sliding mode control is also used in this method, the parameters of which are unknown.
A novel model for synchronization in secure telecommunications based on the fractional-order complex chaotic system has been proposed in [27]. The fractional difference function synchronization (FDFS) method used in this work yielded good results.
In [28], a new synchronization approach for utilization in internet of things (IoT) applications has been used. The design of the synchronization system in their work is based on the Lyapunov stability theorem. Synchronization is based on a nonlinear adaptive controller. In their work, the input signals are first decomposed into small segments and then combined and transmitted with chaotic signals. Subsequently, important information is separated from the chaotic signals at the receiver. The simulation results proved the effectiveness of the proposed scheme in sending and receiving confidential information.
Another work by [29] proposed the design of an Op-Amp-based analog circuit to obtain secure communication. The proposed analog circuit of the seven-dimensional chaotic system is designed and implemented. The results of the circuit simulation confirm the greater capability of the circuit designed for secure communication.
Chen et al. [30] proposed a novel methodology for the synchronization of secure telecommunications. This new technique is based on the polynomials fuzzy model applied to the Chen chaotic system. The approach proposed in this paper is implemented on several various examples, and the results showed that the receiver worked successfully in retrieving the signals transmitted by the transmitter.
Wangli He et al. [31] introduced a new approach based on quantized synchronization of neural networks. In their work, the implementation of the master and slave section of the chaos system is done on the Chua circuit. In order to perform experiments, different images for synchronization with the proposed procedure are employed, and successful results were achieved.
The idea of utilizing adaptive control for synchronization is proposed in [32]. The master and slave chaos systems discussed in this work are of the memristor type. Additionally, to enhance the security of information, an unknown parameter in the slave system is applied. The most significant contribution of this scheme is that it is simple to implement, and it helps to achieve valuable results in secure communication applications.
Ouannas et al. [33] adopted linear and nonlinear controllers to synchronize in secure telecommunications applications. The improved Robinovich chaotic system employed in this study is of the fractional order type. The stability investigation of the proposed technique is proven by means of the Lyapunov theorem. Numerical results illustrated the effectiveness of their proposed scheme in maintaining the confidentiality of information.
In a study, Wang et al. [34] proposed a novel idea of synchronization in secure telecommunications based on neural networks. Associative memory neural networks are widely employed in various applications for synchronization. This network has been chosen based on memristor. In the Lyapunov stability theorem, two controllers with different activation functions are applied. The proposed approach ensured synchronization of drive and response systems in a finite time.
Jing Wang et al. [35] conducted the implementation of analog hardware for a synchronization method; the chaotic system tested in this method is six-dimensional. In order to implement the hardware, all conditions are considered so that the theory of the proposed scheme is consistent with the simulation results.
Zirkohi et al. [36] used terminal slipping model control (TSM) for synchronization. The Duffing–Holmes oscillator is considered the first chaotic system, and the chaotic gyro oscillator as the second chaotic system. Uncertainty, unknown parameters, and ultimately external disturbances are taken into account in both chaotic systems. In the controller section, Chebyshev polynomials are applied to approximate the master and slave systems.
In this paper, a robust adaptive controller was proposed for multi-mode synchronization of chaotic systems. In the proposed method, both slave and master systems have uncertainty, disturbance, unknown parameters, and time-varying delay characteristics. By defining a suitable Lyapunov function, rules for updating parameters, time delays, and estimation errors of uncertainty and disturbance bounds were determined. The proposed controller guarantees that convergence of disturbance and uncertainty bounds estimation error and synchronization error to zero. To prevent the chattering phenomenon, the control law is a continuous function. By using the masking method and using chaotic signals as a carrier signal, the security of communication channels was improved. In the provided example, a 3D Chua system was chosen as the master system, and two Rössler systems were chosen as the slave system. Given the proper and quick reconstruction of message signals and also the convergence of all errors to zero, it was shown that the proposed method has the ability to obtain better performance for synchronization of chaotic systems.
In time-delayed chaotic systems, little work has been done on delay uncertainty with parametric uncertainties, external perturbations, and uncertainty in modeling the multi-state synchronization problems of chaotic systems. The novelties of this paper are as follows:
-
(1)
synchronization of chaotic systems with unknown time delays;
-
(2)
synchronization of chaotic systems in the presence of disturbance and uncertainty with unknown boundaries and variable parameters;
-
(3)
guarantee of convergence of tracking errors and parameters estimation to zero;
-
(4)
Determining the rules for updating parameters, time delays, and disturbance and uncertainty boundaries.
The paper is organized as follows. First, the concept of multi-state synchronization in the presence of perturbation and uncertainty is described. Then, the essential theorems to prove the convergence of errors to zero are explained. Adaptive rules for updating parameters and delays are achieved. Finally, the concept of masking the synchronization of three chaotic systems and its application in secure communication is presented.
2. Multi-State Synchronization of Chaotic Systems in the Presence of Disturbance and Uncertainty
In multi-state synchronization of chaotic systems, a master chaotic system is synchronized with multiple chaotic systems. Figure 1 shows the synchronization of the master system with multiple system slave systems.
Figure 1.
Synchronization of the master system with multiple slave systems.
We represent the driver system with the following equation [30]:
| (1) |
The N-1 slave systems control function can be represented as [30]
| (2) |
where is the state vector of i-th system, is a continuous function, is a continuous function with Lipschitz [30] condition and constant is the unknown variable system delay, and is a matrix function. Moreover, are the main parameters with unknown step changes, uncertainties, and bounded disturbance .
Based on Equations (1) and (2), the synchronization of chaotic system with control function is as follows:
| (3) |
in which it is assumed that is the i-th slave system control function, uncertainties and disturbance have unknown bounds,
| (4) |
In Equation (4) and are unknown constants, is a known function, and in few cases .
In multi-state synchronization, the synchronization error is defined as [37]
| (5) |
Hence, the error dynamics can be represented as [37]
| (6) |
Assuming that the control function is defined as
| (7) |
The control function is selected in such a way that first it removes well-determined sentences () from the error dynamics, and then it approximates the sentences with variable parameters ( and ). To stabilize the system, it exploits the state feedback, and finally the sentence determines the proper estimation of the disturbance and uncertainty boundaries.
Where and are the estimates of and , and is a part of the control function (introduced later in the paper), the feedback gain matrix is defined as
| (8) |
is a diagonal matrix with negative elements that result in the synchronization error to converge to zero in the design.
Plugging the control function into Equation (6), the errors dynamics read as
| (9) |
where is the approximation error.
Theorem 1.
If the derivative of functionis bounded ini.e.,, thenis Lipschitz.
Proof of Theorem 1.
Considering the mean value theorem,
(10)
Theorem 2.
In a chaotic system, all the state variables are Lipschitz.
Proof of Theorem 2.
Considering a chaotic system characteristic, all of its state variables are bounded. On the other hand, the derivative of state variables is nothing but a set of addition, subtraction, and multiplication operations. Hence, the state variable derivatives are bounded so according to Theorem 1, the state variables are Lipschitz with constant, which in turn implies
(11) where is the state vector of i-th system.
Theorem 3.
The errors dynamics System (6), controlled by (46), using updating Rules (29)–(34) is stable. Moreover, the synchronization errors assuming uncertainty and disturbance will converge to zero.
Proof of Theorem 3.
Defining the Lyapunov function as
(12) where
(13)
(14)
In Equation (14), are the estimation errors. Computing the Lyapunov function derivative,
| (15) |
The adapting rules of system parameters are determined as
| (16) |
| (17) |
If are constant, then their derivatives are zero (, and the update rules for the parameters estimation are computed as
| (18) |
| (19) |
Plugging the updating rules (16–17) in Equation (15) yields
| (20) |
If and are the j-th component of vectors , and , respectively, then
| (21) |
Therefore,
| (22) |
In Equation (22), bounds of disturbance and uncertainty can be applied on components and as follows:
| (23) |
| (24) |
Since and are Lipschitz, their components are Lipschitz as well:
| (25) |
Substituting the above equation in Equation (22) yields
| (26) |
Defining as
| (27) |
yields
| (28) |
To determine the update rules, we determine the derivatives of the signals in (28) in such a way that is negative. To that end, the updating rules can be set as follows:
| (29) |
| (30) |
| (31) |
| (32) |
| (33) |
| (34) |
where , , and are positive values. Substituting the update rules (Equations (29)–(34)) in Equation (28) yields
| (35) |
Given that the matrixes are diagonal and have negative elements (Hurwitz). Therefore:.
Defined μ as
| (36) |
Using (35) for the derivative of the Lyapunov function, the following inequality is established:
| (37) |
As the values of the parameters augment, the convergence speed of synchronization errors and estimation error signals to zero increases.
Therefore, the system stability is proved. Additionally, the convergence of synchronization errors to zero in the presence of time delay, uncertainty, and disturbance is guaranteed. The update rules for delays estimation, disturbance bounds, and uncertainty are as follows
| (38) |
| (39) |
| (40) |
| (41) |
| (42) |
| (43) |
Theorem 4.
Ifare constant values, then. In other words, the delays are identified accurately.
Proof of Theorem 4.
Based on Equations (29) and (30), , as approaches infinity (), approaches zero (). Therefore, estimation approaches the true value.
Theorem 5.
If the delays change in a step-wise manner and the steps are large enough, the update Rules (17) and (19) hold.
Proof of Theorem 4.
Similar to Theorem 4 with the exception that condition is replaced with condition “the step changes are large enough”.
Note 1: If the delays vary with time and holds with , then the update rules in (38-39) are valid with reasonable approximation.
Considering that , , the update rules (38-39) are valid with reasonable approximation. Moreover, under such conditions, update Rule (29-30) is exactly valid.
Note 2: If the systems vary with time, i.e., , Equations (16) and (17) hold, which allow us to apply Theorem (3) based on which Lyapunov Function (12) can be used, and its derivative satisfies Condition (35) as well. Hence, the Lyapunov function approaches zero:
| (44) |
Therefore, if is a vector function with step changes and appropriate temporal distance between the changes, the update Rules (16) and (17) hold and parameter are estimated accurately. Let , then update Rules (18) and (19) are valid with reasonable accuracy.
Note 3: To guarantee the continuity of the control function, the following equation can be used:
| (45) |
Note 4: If the uncertainties are in their typical form, i.e., .., it suffices to set in the update equations and the control rule.
Note 5: The final control function is as below:
| (46) |
3. Application in Secure Communication Based on Chaotic Masking
In chaotic masking, an information signal is added to the linear combination of base state signals. Given that Q(t) is the primary signal carried by the master system and W(t) is the transfer message given by [38,39]:
| (47) |
where is the i-th component of the master system, and W(t) is masked using the chaotic signal. This signal is transmitted via the communication channel from sender to the receiver. Using the proposed controller, the multi-state chaotic synchronization is performed in one of its states. The received signal can be recovered using the following equation [40]:
| (48) |
where is the i-th component of the slave system. Considering the synchronization concept, the following equation is obtained [40]:
| (49) |
Figure 2 shows the block diagram of chaotic masking using multi-state synchronization. Since we have one master and two slave systems, two independent messages are sent to the master which are encrypted, then the master is synchronized with two slaves. After the synchronization with the receiver side, the signals are decrypted and the original messages are recovered.
Figure 2.
Block diagram of chaotic masking using multi-state synchronization.
Using chaotic masking, we demonstrated the encryption and decryption of two sinusoidal signals using our proposed multi-state synchronization approach. The simulation is carried out with Matlab software. The encryption and decryption are applied when the chaotic signals are synchronized. To evaluate this, two sinusoidal signals are added to the master system signals. Next, the master system is synchronized with two slave systems. Finally, based on the synchronization error, the signal is decrypted and recovered at the receiver side.
4. Simulation and Results
We used one Chua chaotic system and two Rössler time-delayed chaotic systems as master and slaves, respectively. These systems are defined as follows:
| (50) |
| (51) |
| (52) |
where are system parameters. The values of the parameters are set as ,
| (53) |
| (54) |
| (55) |
The initial values of the parameters are set as below:
| (56) |
Under such circumstances, the parameters have step changes. In addition, the disturbance and uncertainties influencing the master and slave systems are expressed as
| (57) |
| (58) |
| (59) |
| (60) |
| (61) |
The controller’s parameters are chosen as
| (62) |
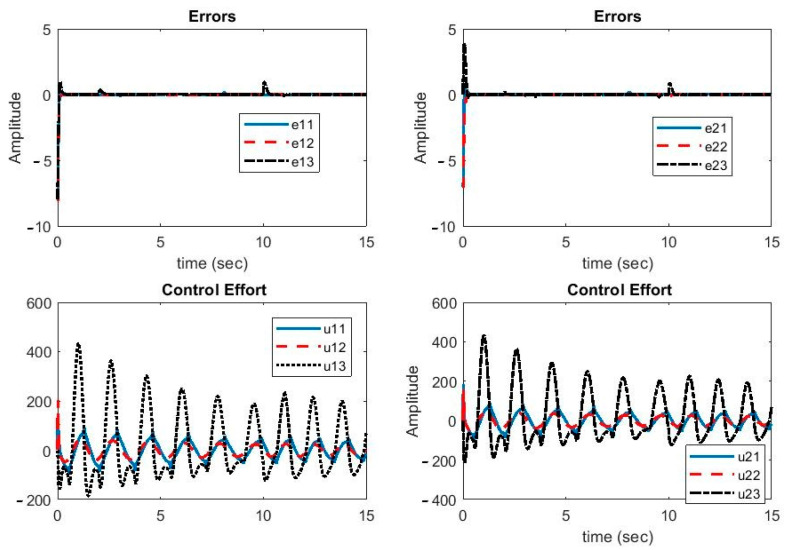
In Figure 3, the synchronization errors and control efforts are illustrated. As can be seen, despite the parameter uncertainties and time-variable delays, the error signals were reduced to zero quickly. During large parameter changes, the error increased slightly but turned back to zero quickly. Hence, the proposed controller was robust against parameter uncertainties, external disturbance, and variable delays. Moreover, the control function was continuous and smooth, which was helpful in the implementation of the proposed method.
Figure 3.
Plots of synchronization errors and control efforts.
It can be noted from Figure 4 that the estimated parameters of Chua and Rössler systems have converged to their real values. It is evident from this figure that, despite being variable with time, the delays have also converged to their real values quickly. During the instances when delays exhibited step changes, the system parameters deviated from their real values, but they were corrected in short duration. Since Lipschitz conditions are functions, the parameter changes do not affect the delays significantly. On the other hand, Chua is a non-smooth system, which causes more complication in the control as well as synchronization problems.
Figure 4.
Plots of parameters and delays estimations versus time.
In Figure 5, the plots of estimation error of unknown uncertainties bounds and unknown disturbances bounds are shown.
Figure 5.
Estimation error of disturbance bounds (left). Estimation error of uncertainties bounds versus time (right).
It can be seen in Figure 5 that the estimation error of unknown parameter bounds and uncertainties bounds have approached zero quickly. In the tenth second, little error is observed, which is compensated in a short amount of time. Figure 6, Figure 7 and Figure 8 shows the phase curves of the slave system and indicates the chaotic behavior of the system. In spite of various changes, the behavior of the system is still chaotic.
Figure 6.
Sample phase curves of the Master system.
Figure 7.
Sample phase curves of the first slave system.
Figure 8.
Sample phase curves of the second slave system.
Phase curves of the master system: Chua time-delayed chaotic system ) indicating the chaotic behavior for the provided parameters.
The phase curve of the first slave system: Rössler time-delayed chaotic systems () which shows the chaotic behavior for the given parameters.
The phase curve of the second slave system: Rössler time-delayed chaotic systems ) representing the chaotic behavior for the given parameters.
5. Discussion
The presented results reveal good performance of the proposed method in estimating parameters, delays, as well as disturbance bounds and uncertainties. This in turn leads to an acceptable performance of the overall system in synchronization and convergence of errors to zero.
In the rest of the paper, the proposed method was evaluated in secure communication using chaotic masking. To evaluate this, five sinusoid signals were added as messages to the master system’s signal, independently. The decryption and recovering of each message was done by synchronization of the master system with two slave systems. The message signals added to the master system are given below:
| (63) |
After the synchronization, the recovered signals were obtained. In Figure 9, Figure 10, Figure 11, Figure 12 and Figure 13, the original and recovered message signals obtained using multi-state synchronization and chaotic masking are shown.
Figure 9.
Plot of original signal and recovered signal obtained using multi-state synchronization and chaotic masking.
Figure 10.
Plot of original signal and recovered signal obtained using multi-state synchronization and chaotic masking.
Figure 11.
Plot of original signal and recovered signal obtained using multi-state synchronization and chaotic masking.
Figure 12.
Plot of original signal and recovered signal obtained using multi-state synchronization and chaotic masking.
Figure 13.
Plot of original signal and recovered signal obtained using multi-state synchronization and chaotic masking.
Figure 9 shows the recovered signal (R1) followed the original signal (S1) very well. Due to sudden changes in delays and parameters, there was a pick at 10 s, which was dealt with, and after that the recovered signal faithfully followed the original signal again.
Figure 10, Figure 11, Figure 12 and Figure 13 show that the original signal given to the master and received by the slave has been recovered faithfully using our proposed multi-state synchronization method. The advantages of the proposed method are as follows:
Guaranteed closed loop stability in the presence of disturbance, uncertainty, parameter changes, and delays.
Accurate estimation of variable time delays and parameters.
Specifying the control laws as continuous time functions.
Capable of dealing with disturbance and uncertainties with unknown boundaries.
Faithful recovery of message signal in secure communication.
The disadvantages of our method are given below:
Involves relatively large magnitude of control signal in a few cases (control functions ).
Changes occur solely in a step-like manner; hence, there is a large distance between parameter changes.
In the future, we intend to extend this work by multi-state synchronization with minimization of sum of control efforts and synchronization of chaotic systems with variable parameters. Secure communication can be employed in medical applications as well [41]. Medical data stored in hospitals contain significant information about the patients. In future work, the proposed method for secure communication can be used for medical applications [42,43,44,45,46,47]. Synchronization of chaotic systems is also used in some other applications such as electromagnetism [48] and mechanics [49,50]. As a future work, the chaotic synchronization method of this paper can be developed and implemented for electromagnetic and mechanical applications.
In this paper, we have proposed that, using our multi-state synchronization and chaotic masking method, secure communication can be achieved. In secure communication, encoding (masking) and accurately recovering the message signal is very important. The most important feature in secure communication is the security of the method and complexity of the algorithm, which makes decoding practically impossible or very difficult. In this regard, important points of the proposed method are given below:
-
(1)
Presence of delay and variable parameters in master and slave systems.
-
(2)
Ability to switch to different slave systems.
-
(3)
Presence of undesirable and unwanted factors such as disturbances and uncertainty.
Therefore, our proposed method helps to ensure secure communication. Accurate retrieval of message signal was another prominent feature of this method. It can be noted from our examples that our proposed method is able to recover the message signal faithfully at the receiver. Hence, our proposed approach has two important properties: the ability to mask the data and to recover the message accurately, which can be used in secure communications.
6. Conclusions
In this paper, multi-state synchronization of two time-delayed chaotic systems with unknown parameters and delays in the presence of unknown parameters and external disturbance was investigated. The disturbance and uncertainties have unknown bounds, and the master system was non-smooth. To estimate the parameters and time delays, the Lyapunov method was used. This way, convergence of various types of defined errors were guaranteed, and the adaptive rules for estimation of parameters and time delays were determined. Moreover, the update of rules for the bounds of unknown parameters and external disturbance were established. To evaluate the proposed method, the simulations were carried out in a multi-state synchronization setting with time variable delays and parameters. Our results revealed that the proposed controller was good at reducing the synchronization errors to zero with little oscillations. In addition, despite changes such as step and sinusoid, the time delays have been identified and estimated well. Moreover, the errors related to the bounds of unknown parameters and external disturbance converged to zero quickly. The experimental results revealed the capability and flexibility of the proposed method in synchronization of chaotic systems, parameters, and time delay identification in the presence of uncertainty and disturbance. Finally, the capability of the proposed method to recover the message signals in secure communication applications was presented. Due to time variability of the system, the chaotic behavior was more complex, which leads to better protection in secure communication.
Author Contributions
Conceptualization, A.A.K.J. and A.S.; methodology, A.Z. and S.N.; software, A.A.K.J. and A.S.; validation, A.Z., U.R.A., A.A.K.J. and A.M.; formal analysis, A.S., R.A., N.H.I. and M.J.; resources, A.Z. and A.A.K.J.; writing-original draft preparation, A.A.K.J., A.S., R.A. and P.M.; writing-review and editing, A.S., A.Z., A.M., U.R.A., N.H.I. and M.J.; visualization, A.Z., A.A.K.J. and A.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Footnotes
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Bendoukha S., Abdelmalek S., Ouannas A. Mathematics Applied to Engineering, Modelling, and Social Issues. Springer; Cham, Switzerland: 2019. Secure communication systems based on the synchronization of chaotic systems; pp. 281–311. [Google Scholar]
- 2.Mewada D., Dave N., Prajapati R.K. A survey: Prospects of Internet of Things (IoT) using cryptography based on its subsequent challenges. Aust. J. Wirel. Technol. Mobil. Secur. 2019;1:28–30. doi: 10.21276/Ausjournal.2019.1.3. [DOI] [Google Scholar]
- 3.Taha M.S., Rahim M.S.M., Lafta S.A., Hashim M.M., Alzuabidi H.M. IOP Conference Series: Materials Science and Engineering. Vol. 518. IOP Publishing; Bristol, UK: 2019. Combination of steganography and cryptography: A short survey; p. 052003. [Google Scholar]
- 4.AlMajed H., AlMogren A. A Secure and Efficient ECC-Based Scheme for Edge Computing and Internet of Things. Sensors. 2020;20:6158. doi: 10.3390/s20216158. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Gulsezim D., Zhansaya S., Razaque A., Ramina Y., Amsaad F., Almiani M., Oun A. 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019. IEEE; New York, NY, USA: 2019. Two Factor Authentication using Twofish Encryption and Visual Cryptography Algorithms for Secure Data Communication; pp. 405–411. [Google Scholar]
- 6.Yang T., Wu C.W., Chua L.O. Cryptography based on chaotic systems. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 1997;44:469–472. doi: 10.1109/81.572346. [DOI] [Google Scholar]
- 7.Crandall R.E. Cryptographic system using chaotic dynamics. 6587563. U.S. Patent. 2003
- 8.Liu S., Wei Y., Liu J., Chen S., Zhang G. Multi-Scroll Chaotic System Model and Its Cryptographic Application. Int. J. Bifurc. Chaos. 2020;30:2050186. doi: 10.1142/S0218127420501862. [DOI] [Google Scholar]
- 9.Pham V.T., Kingni S.T., Volos C., Jafari S., Kapitaniak T. A simple three-dimensional fractional-order chaotic system without equilibrium: Dynamics, circuitry implementation, chaos control and synchronization. AEU Int. J. Electron. Commun. 2017;78:220–227. doi: 10.1016/j.aeue.2017.04.012. [DOI] [Google Scholar]
- 10.Chen D., Li S., Wu Q. Rejecting chaotic disturbances using a super-exponential-zeroing neurodynamic approach for synchronization of chaotic sensor systems. Sensors. 2019;19:74. doi: 10.3390/s19010074. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Pham V.T., Ouannas A., Volos C., Kapitaniak T. A simple fractional-order chaotic system without equilibrium and its synchronization. AEU Int. J. Electron. Commun. 2018;86:69–76. doi: 10.1016/j.aeue.2018.01.023. [DOI] [Google Scholar]
- 12.Zare A., Mirrezapour S.Z., Hallaji M., Shoeibi A., Jafari M., Ghassemi N., Mosavi A. Robust Adaptive Synchronization of a Class of Uncertain Chaotic Systems with Unknown Time-Delay. Appl. Sci. 2020;10:8875. doi: 10.3390/app10248875. [DOI] [Google Scholar]
- 13.Tirandaz H., Hajipour A. Adaptive synchronization and anti-synchronization of TSUCS and Lü unified chaotic systems with unknown parameters. Optik. 2017;130:543–549. doi: 10.1016/j.ijleo.2016.10.093. [DOI] [Google Scholar]
- 14.Vaidyanathan S., Pham V.T., Volos C. Advances in Memristors, Memristive Devices and Systems. Springer; Cham, Switzerland: 2017. Adaptive control, synchronization and circuit simulation of a memristor-based hyperchaotic system with hidden attractors; pp. 101–130. [Google Scholar]
- 15.Khan A. Hybrid function projective synchronization of chaotic systems via adaptive control. Int. J. Dyn. Control. 2017;5:1114–1121. doi: 10.1007/s40435-016-0258-6. [DOI] [Google Scholar]
- 16.Mani P., Rajan R., Shanmugam L., Joo Y.H. Adaptive control for fractional order induced chaotic fuzzy cellular neural networks and its application to image encryption. Inf. Sci. 2019;491:74–89. doi: 10.1016/j.ins.2019.04.007. [DOI] [Google Scholar]
- 17.Chen X., Park J.H., Cao J., Qiu J. Adaptive synchronization of multiple uncertain coupled chaotic systems via sliding mode control. Neurocomputing. 2018;273:9–21. doi: 10.1016/j.neucom.2017.07.063. [DOI] [Google Scholar]
- 18.Song C., Fei S., Cao J., Huang C. Robust synchronization of fractional-order uncertain chaotic systems based on output feedback sliding mode control. Mathematics. 2019;7:599. doi: 10.3390/math7070599. [DOI] [Google Scholar]
- 19.Shukla M.K., Sharma B.B. Control and synchronization of a class of uncertain fractional order chaotic systems via adaptive backstepping control. Asian J. Control. 2018;20:707–720. doi: 10.1002/asjc.1593. [DOI] [Google Scholar]
- 20.Zhu Z.Y., Zhao Z.S., Zhang J., Wang R.K., Li Z. Adaptive fuzzy control design for synchronization of chaotic time-delay system. Inf. Sci. 2020;535:225–241. doi: 10.1016/j.ins.2020.05.056. [DOI] [Google Scholar]
- 21.Mohammadzadeh A., Ghaemi S., Kaynak O. Robust predictive synchronization of uncertain fractional-order time-delayed chaotic systems. Soft Comput. 2019;23:6883–6898. doi: 10.1007/s00500-018-3328-1. [DOI] [Google Scholar]
- 22.Xu S., Lv H., Liu H., Liu A. Robust Control of Disturbed Fractional-Order Economical Chaotic Systems with Uncertain Parameters. Complexity. 2019;2019 doi: 10.1155/2019/7567695. [DOI] [Google Scholar]
- 23.Chen H.C., Liau B.Y., Hou Y.Y. Hardware implementation of Lorenz circuit systems for secure chaotic communication applications. Sensors. 2013;13:2494–2505. doi: 10.3390/s130202494. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Cicek S., Kocamaz U.E., Uyaroğlu Y. Secure chaotic communication with jerk chaotic system using sliding mode control method and its real circuit implementation. Iran. J. Sci. Technol. Trans. Electr. Eng. 2019;43:687–698. doi: 10.1007/s40998-019-00184-9. [DOI] [Google Scholar]
- 25.Khan A., Jahanzaib L.S., Trikha P. Secure communication: Using parallel synchronization technique on novel fractional order chaotic system. IFAC PapersOnLine. 2020;53:307–312. doi: 10.1016/j.ifacol.2020.06.052. [DOI] [Google Scholar]
- 26.Yu F., Zhang Z., Liu L., Shen H., Huang Y., Shi C., Xu Q. Secure communication scheme based on a new 5D multistable four-wing memristive hyperchaotic system with disturbance inputs. Complexity. 2020;2020 doi: 10.1155/2020/5859273. [DOI] [Google Scholar]
- 27.Liu J., Wang Z., Shu M., Zhang F., Leng S., Sun X. Secure communication of fractional complex chaotic systems based on fractional difference function synchronization. Complexity. 2019;2019 doi: 10.1155/2019/7242791. [DOI] [Google Scholar]
- 28.Wang T., Wang D., Wu K. Chaotic adaptive synchronization control and application in chaotic secure communication for industrial Internet of Things. IEEE Access. 2018;6:8584–8590. doi: 10.1109/ACCESS.2018.2797979. [DOI] [Google Scholar]
- 29.Yu W., Wang J., Wang J., Zhu H., Li M., Li Y., Jiang D. Design of a new seven-dimensional hyperchaotic circuit and its application in secure communication. IEEE Access. 2019;7:125586–125608. doi: 10.1109/ACCESS.2019.2935751. [DOI] [Google Scholar]
- 30.Chen Y.J., Chou H.G., Wang W.J., Tsai S.H., Tanaka K., Wang H.O., Wang K.C. A polynomial-fuzzy-model-based synchronization methodology for the multi-scroll Chen chaotic secure communication system. Eng. Appl. Artif. Intell. 2020;87:103251. doi: 10.1016/j.engappai.2019.103251. [DOI] [Google Scholar]
- 31.He W., Luo T., Tang Y., Du W., Tian Y.C., Qian F. Secure communication based on quantized synchronization of chaotic neural networks under an event-triggered strategy. IEEE Trans. Neural Netw. Learn. Syst. 2019;31 doi: 10.1109/TNNLS.2019.2943548. [DOI] [PubMed] [Google Scholar]
- 32.A Rahman Z.A.S., Al-Kashoash H.A., Ramadhan S.M., Al-Yasir Y.I. Adaptive Control Synchronization of a Novel Memristive Chaotic System for Secure Communication Applications. Inventions. 2019;4:30. doi: 10.3390/inventions4020030. [DOI] [Google Scholar]
- 33.Ouannas A., Bendoukha S., Volos C., Boumaza N., Karouma A. Synchronization of fractional hyperchaotic Rabinovich systems via linear and nonlinear control with an application to secure communications. Int. J. Control. Autom. Syst. 2019;17:2211–2219. doi: 10.1007/s12555-018-0216-5. [DOI] [Google Scholar]
- 34.Wang W., Jia X., Luo X., Kurths J., Yuan M. Fixed-time synchronization control of memristive MAM neural networks with mixed delays and application in chaotic secure communication. Chaos Solitons Fractals. 2019;126:85–96. doi: 10.1016/j.chaos.2019.05.041. [DOI] [Google Scholar]
- 35.Wang J., Yu W., Wang J., Zhao Y., Zhang J., Jiang D. A new six-dimensional hyperchaotic system and its secure communication circuit implementation. Int. J. Circuit Theory Appl. 2019;47:702–717. doi: 10.1002/cta.2617. [DOI] [Google Scholar]
- 36.Zirkohi M.M. An efficient approach for digital secure communication using adaptive backstepping fast terminal sliding mode control. Comput. Electr. Eng. 2019;76:311–322. doi: 10.1016/j.compeleceng.2019.04.007. [DOI] [Google Scholar]
- 37.Chen X., Park J.H., Cao J., Qiu J. Sliding mode synchronization of multiple chaotic systems with uncertainties and disturbances. Appl. Math. Comput. 2017;308:161–173. doi: 10.1016/j.amc.2017.03.032. [DOI] [Google Scholar]
- 38.Ren H.P., Bai C., Huang Z.Z., Grebogi C. Secure communication based on hyperchaotic Chen system with time-delay. Int. J. Bifurc. Chaos. 2017;27:1750076. doi: 10.1142/S0218127417500766. [DOI] [Google Scholar]
- 39.Lin T.C., Huang F.Y., Du Z., Lin Y.C. Synchronization of fuzzy modeling chaotic time delay memristor-based Chua’s circuits with application to secure communication. Int. J. Fuzzy Syst. 2015;17:206–214. doi: 10.1007/s40815-015-0024-5. [DOI] [Google Scholar]
- 40.Kwon O.M., Park J.H., Lee S.M. Secure communication based on chaotic synchronization via interval time-varying delay feedback control. Nonlinear Dyn. 2011;63:239–252. doi: 10.1007/s11071-010-9800-9. [DOI] [Google Scholar]
- 41.Ali T.S., Ali R. A Novel Medical Image Signcryption Scheme Using TLTS and Henon Chaotic Map. IEEE Access. 2020;8:71974–71992. doi: 10.1109/ACCESS.2020.2987615. [DOI] [Google Scholar]
- 42.Shoeibi A., Ghassemi N., Khodatars M., Jafari M., Hussain S., Alizadehsani R., Zare A. Epileptic seizure detection using deep learning techniques: A Review. arXiv. 2020;2007:01276. doi: 10.3390/ijerph18115780. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43.Shoeibi A., Ghassemi N., Alizadehsani R., Rouhani M., Hosseini-Nejad H., Khosravi A., Nahavandi S. A comprehensive comparison of handcrafted features and convolutional autoencoders for epileptic seizures detection in EEG signals. Exp. Syst. Appl. 2020;163:113788. doi: 10.1016/j.eswa.2020.113788. [DOI] [Google Scholar]
- 44.Martin-Isla C., Campello V.M., Izquierdo C., Raisi-Estabragh Z., Baeßler B., Petersen S.E., Lekadir K. Image-based cardiac diagnosis with machine learning: A review. Front. Cardiovasc. Med. 2020;7:1. doi: 10.3389/fcvm.2020.00001. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 45.Alizadehsani R., Khosravi A., Roshanzamir M., Abdar M., Sarrafzadegan N., Shafie D., Bishara A. Coronary Artery Disease Detection Using Artificial Intelligence Techniques: A Survey of Trends, Geographical Differences and Diagnostic Features 1991–2020. Comput. Biol. Med. 2020;128:104095. doi: 10.1016/j.compbiomed.2020.104095. [DOI] [PubMed] [Google Scholar]
- 46.Shoeibi A., Khodatars M., Alizadehsani R., Ghassemi N., Jafari M., Moridian P. Alizadehsani, Z. Automated detection and forecasting of covid-19 using deep learning techniques: A review. arXiv. 2020;2007:10785. [Google Scholar]
- 47.Kumar A., Gupta P.K., Srivastava A. A review of modern technologies for tackling COVID-19 pandemic. Diabet. Metab. Syndr. Clin. Res. Rev. :2020. doi: 10.1016/j.dsx.2020.05.008. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 48.Abd-Elaziz E.M., Marin M., Othman M.I. On the effect of Thomson and initial stress in a thermo-porous elastic solid under GN electromagnetic theory. Symmetry. 2019;11:413. doi: 10.3390/sym11030413. [DOI] [Google Scholar]
- 49.Vlase S., Marin M., Öchsner A., Scutaru M.L. Motion equation for a flexible one-dimensional element used in the dynamical analysis of a multibody system. Contin. Mech. Thermodyn. 2019;31:715–724. doi: 10.1007/s00161-018-0722-y. [DOI] [Google Scholar]
- 50.Jian B.L., Wang C.C., Chang J.Y., Su X.Y., Yau H.T. Machine tool chatter identification based on dynamic errors of different self-synchronized chaotic systems of various fractional orders. IEEE Access. 2019;7:67278–67286. doi: 10.1109/ACCESS.2019.2917094. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data sharing not applicable.