Abstract
5G-Vehicle-to-Everything (5G-V2X) supports high-reliability and low latency autonomous services and applications. Proposing an efficient security solution that supports multi-zone broadcast authentication and satisfies the 5G requirement is a critical challenge. In The 3rd Generation Partnership Project (3GPP) Release 16 standard, for Cellular- Vehicle-to-Everything (C-V2X) single-cell communication is suggested to reuse the IEEE1609.2 security standard that utilizes the Public Key Infrastructure (PKI) cryptography. PKI-based solutions provide a high-security level, however, it suffers from high communication and computation overhead, due to the large size of the attached certificate and signature. In this study, we propose a light-weight Multi-Zone Authentication and Privacy-Preserving Protocol (MAPP) based on the bilinear pairing cryptography and short-size signature. MAPP protocol provides three different authentication methods that enable a secure broadcast authentication over multiple zones of large-scale base stations, using a single message and a single short signature. We also propose a centralized dynamic key generation method for multiple zones. We implemented and analyzed the proposed key generation and authentication methods using an authentication simulator and a bilinear pairing library. The proposed methods significantly reduce the signature generation time by 16 times–80 times, as compared to the previous methods. Additionally, the proposed methods significantly reduced the signature verification time by 10 times–16 times, as compared to the two previous methods. The three proposed authentication methods achieved substantial speed-up in the signature generation time and verification time, using a short bilinear pairing signature.
Keywords: vehicular communication, security of bilinear pairing, privacy issues, authentication requirements, signatures aggregation, signature concatenation, cellular-V2X, multi-hop authentication
1. Introduction
Vehicle-to-Everything (V2X) communication [1] is the technology for connected vehicles to support road safety and prevent traffic accidents. V2X allows vehicles to broadcast periodic messages about the surrounding area. Recently, many technologies target road safety with high data rates to provide alerts about upcoming crashes. Multiple accessing technologies provide connectivity in vehicular networks, such as Wi-Fi, IEEE 802.11p, and cellular radio communications. Recently, Cellular-V2X (C-V2X) was standardized by the third-generation partnership project (3GPP) for automotive services. LTE-V2X is the current 3GPP Release 14 [2] standard that has many enhancements to provide the new 3GPP Release 16 for the new 5G radio generation [3]. The majority of the shortcomings of DSRC, 802.11p, and LTE-V2X are meant to be handled through the efficient function handlers in 5G-V2X. Proposing efficient light-weight security solutions against known and unknown threats depends on the deployment strategies of 5G-V2X. The deployment of 5G Base Stations (BSs) defines the exploitation of possible network vulnerabilities. Moreover, key exposure and the insecure communication channel were considered as points of attack in 5G-V2X. Due to the high mobility conditions, attack possibilities are increasing. Optimizing the 5G-NR in V2X communication has high requirements and efficient light-weight security methods to support many V2X services and applications [4]. The 5G NewRadio (NR) was developed to enhance the network scalability, flexibility, and efficiency of the spectrum and power usage [5]. V2X communication offers different benefits, but it creates many privacy and security concerns [6]. Many proposed security protocols are trying to satisfy the security standards requirements and challenges [7]. V2X authentication and privacy are the most critical issues that are our basic concerns in this study. A few studies looked at the security requirements of C-V2X networks [8,9]. C-V2X security standards in the 3GPP Release 15 and beyond are based on the Public Key Infrastructure (PKI), to preserve privacy and support message authentication. PKI-based solutions suffer high communication and computation overhead due to the large size of the attached certificate and signature [10]. 5G-V2X infrastructure plays a vital role in designing efficient security protocol. The intensive deployment of 5G BSs at short distances can serve as Road Side Units (RSUs) to offer security services for road vehicles [11]. Each vehicle authenticates itself to the joined cell BS before communication. The handover authentication between BSs consumes long delays to transfer the authentication parameters of vehicles between different cells. Moreover, in 3GPP Release 15, LTE-V2X supports 100 ms End-to-End latency that can allow vehicles to communicate with BSs, request the authentication parameters, and authenticate messages within this time. However, in Release 16, for the 5G-V2X it was assumed that latency was 5 ms or less, which required fast authentication procedures to satisfy the 5G requirements. One enhancement introduced by the 5GCAR project was related to the concept of zones as a solution to provide common local services using BSs as roadside units (RSUs). As considered in 5GCAR, the BSs were grouped to form smart radio access service areas, referred to as Smart Zones (SM-Zones) [12]. In this study, we assumed that the 5G-V2X network is divided into zones, and every zone is covered by BSs. For a single zone, all vehicles were configured with common security parameters to securely communicate without high-cost re-authentication, when they moved from one BS to another.
We propose a Multi-Zone Authentication and Privacy-Preserving Protocol (MAPP), based on the bilinear pairing cryptography and a short digital signature. The proposed protocol supports the message and identity authentication within single-zone and multiple zones that enhance the 5G-V2X network security and availability.
In summary, the contributions of this study are as follows:
Proposing a dynamic key generation method that provides short-lived authentication keys per vehicle in each zone.
Proposing a Transmitter Centric Authentication (TCA) method where signature generation at transmitters and signature verification at receivers are based on the transmitter zone parameters.
Proposing a Signature Concatenation-based Authentication (SCA) method, in which the transmitter generates a concatenated signature that can be individually verified by all receivers, using their corresponding zone parameters.
Proposing a Receiver Centric Authentication (RCA) method, where transmitters and receivers aggregate the security parameters of the overlapped zones to generate and verify signatures.
Comparing the three proposed authentication methods in terms of signature generation time, signature verification time, and communication cost.
Comparing the communication cost in terms of message size for the three proposed authentication methods and six previous related methods for single-zone and multi-zone scenarios.
Comparing the computation cost in terms of signature generation time and signature verification.
The rest of this paper is organized as follows. Section 2 describes the previous V2X security methods based on the bilinear pairing and free of certificates solutions. Section 3 presents the proposed protocol architecture and the three proposed authentication methods. Section 4 describes security analysis, and the proposed communication overhead analysis is presented in Section 5. In Section 6, the computation overhead is analyzed. Conclusions are provided in Section 7.
2. Related Work
Many security methods are proposed to support authentication for all exchanged periodic information in V2X. Public Key Infrastructure (PKI) authentication methods were proposed to support message authentication using digital signatures and identity authentication using a certificate [13]. The digital signatures in PKI provide authentication and integrity, using long size certificates incurs high communication and computation overhead. Due to the high-cost of PKI-based methods, some identity-based (ID-based) authentication methods are proposed in [14,15,16,17].
In [14], He et al. proposed an identity-based privacy-preserving authentication method for V2X. In [15], Lo et al. designed a new ID-based authentication method using Elliptic Curve (ECC) for authentication and privacy-preserving. These ID-based methods require less communication overhead to support authentication and preserve privacy. In [16], Liu et al. presented an efficient anonymous authentication method using message recovery and signatures to enhance system efficiency. In [17], Tzeng et al. proposed the batch verification method based on identity authentication for V2X and defined different security risks. In [18], Hu et al. improved the proposed Tzeng et al. [17] methods, by proposing a secure batch verification method based on ID, without bilinear pairings. Though these ID-based solutions could eliminate the PKI problems, it suffers from a key escrow problem. To overcome the PKI overhead and the key escrow problems of ID-based solutions, many certificateless (CLS) signature methods were proposed [19,20,21,22,23,24]. Horng et al. [19] proposed a privacy-preserving aggregated signatures method for V2V communication. In this method, only the partial private key of the users was generated by a trusted Key Generator Center (KGC). A secret random value was picked by each user and combined with the partial private key to generate a new private key. Therefore, the user’s private keys were not stored at the KGC. In certificateless CPPA methods, vehicles do not need to store certificates to guarantee the authenticity of the used public keys. Li et al. [20] proved that the proposed method in [19] was not secure against the passive malicious KGC, using the existing security model. Malhi et al. [21] proposed a new efficient certificateless aggregate signature protocol for V2X, and proved the security level using the random oracle model. Additionally, the proposed protocol was computationally more efficient due to its constant pairing operations. After discussing the vulnerabilities of malicious-but-passive KGC attacks, Lin et al. [22] presented an improved protocol. They presented a new security method, based on authentication using group signatures for V2X. In this method, a single manager issues the secret keys for each vehicle. Bayat et al. [23] proposed a new Conditional Privacy-Preserving Authentication (CPPA) method, based on bilinear pairing cryptography, to improve identity-based authentication in V2X. However, this method could not prevent the message modification attacks in which an attacker could repeat the transmission of old messages after modifying its content. In [24], Boneh et al. proposed the first protocol for group signature, based on bilinear pairing. This group signature protocol suffers from high computation and communication cost. All mentioned methods in [19,20,21,22,23,24], employ the bilinear pairing cryptography for a single cell or group authentication. It also limits the network scalability and availability, and suffers from high computation time and complexity. We summarize the advantages and disadvantages of the security protocols [19,20,21,22,23,24] in Table 1.
Table 1.
Comparison of the previous certificateless bilinear pairing authentication methods.
| Message Authentication Done by Signing Message Using Individual Secret Keys and Verification is Done Using the Bilinear Pairing Function. IDENTITY Authentication Is Satisfied Using Pseudo-Identities | |||
|---|---|---|---|
| Certificateless Bilinear Pairing Cryptography Is Used in All Compared Methods [19,20,21,22,23,24] for Single Group Communication | |||
| Security Method | Advantages | Disadvantages | Communication Type |
| Horng et al. [19] |
|
|
|
| Li et al. [20] |
|
|
|
| Malhi et al. [21] |
|
|
|
| Lin et al. [22] |
|
|
|
| Bayat et al. [23] |
|
|
|
| Boneh et al. [24] |
|
|
|
In this study, we proposed a Multi-Zone Authentication and Privacy-Preserving Protocol (MAPP), based on bilinear pairing cryptography. The proposed protocol supports privacy-preserving by generating pseudo-identities to hide the vehicle’s real identities. MAPP provides broadcast authentication methods over multiple-zones, using short bilinear pairing signatures. We utilize special elliptical curves to reduce the authentication time and storage requirements. MAPP supports dynamic key generation per vehicle in each zone that enhances the security level and resists the key attacks in previous V2X methods.
3. The Proposed Protocol
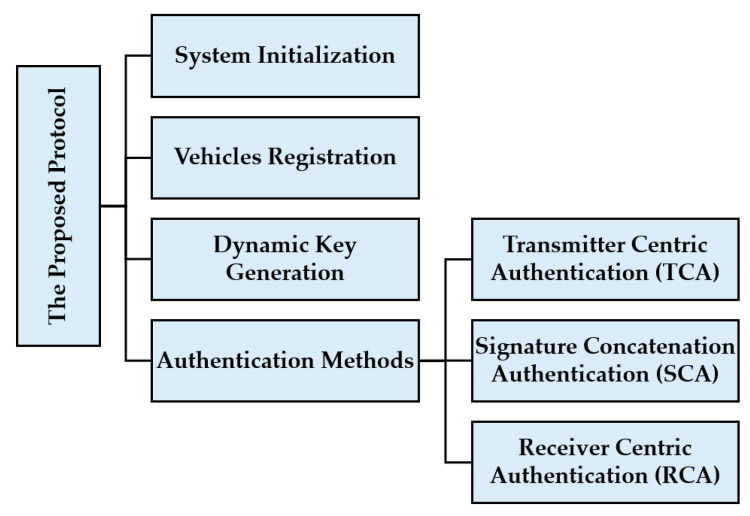
In this section, we describe the proposed protocol with the following steps—a system model, system initialization, and the proposed authentication methods. Figure 1 summarizes the proposed protocol architecture that introduces three new authentication methods. Table 2 summarizes the system notations and the commonly mentioned variables.
Figure 1.
The proposed protocol architecture.
Table 2.
The system notations and abbreviations.
| Notations | Descriptions |
|---|---|
| BSs | Base Stations |
| CA | Certificate Authority |
| ECC | Elliptic Curve Cryptography |
| a list of pseudo identities | |
| list of secret keys | |
| a list of the corresponding public keys | |
| Zone of ID list | |
| A random integer number represents a secret key of vehicle in each zone | |
| Finite field of elements in the range . | |
| two cyclic additive groups of prime order based on the elliptic curve over the finite field where → | |
| Acyclic multiplicative group containing the bilinear pairing result of the two groups . | |
| The bilinear pairing function that maps elements from group and group to group | |
| Represents the generator point of the group for each zone | |
| An ECC point represents the public key of vehicle in each zone: | |
| A cryptographic hash function that maps a message to a point in the group | |
| Represents the pseudo-identity of to hide it’s real identity and allow vehicle to communicate anonymously | |
| Represents message payload transmitted from vehicle | |
| Is a timestamp to ensure message freshness | |
| The number of base stations | |
| The number of zones | |
| H(m) | Hashed message to a point over the elliptic curve group |
| Generate a signatureover message m using the secret key of each vehicle | |
| Represents the concatenation operation of two elements | |
| Represents the aggregation of zones generators ( to generate a new value |
|
| Represents the aggregation of vehicle secret keys for different zone destinations |
|
| Represents the aggregated public key of vehicle where | |
| The aggregated signature over message m using the aggregated secret key , where | |
| The concatenated signatures that consists of signatures generated by vehicle for different zones destinations: | |
| The concatenated public keys that consists of public keys of vehicle for different zones destinations: |
3.1. System Model
5G is the next mobile radio generation that supports ultra-high data speeds and low latency [25]. It was predicted that the number of 5G devices would be high, with high generated traffic [26]. Thus, there is a critical need for the improvement of cell deployment. The 5G new antenna techniques use the mmWave carrier frequencies. mmWave offers a short range of communication with a large amount of data [27]. There are several advantages of using mmWave frequencies in 5G networks, such as privacy and security, due to the short transmission range of mmWave, and also reusing the same frequency in a very short distance. Thus, many Base Stations should be placed at short distances to offer local management services with better frequency reuse [28].
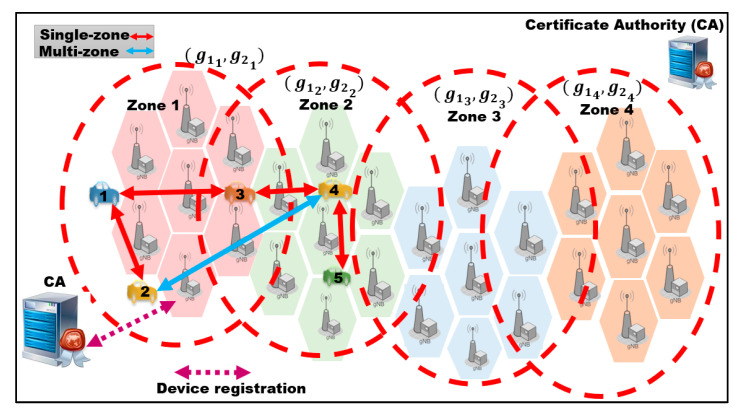
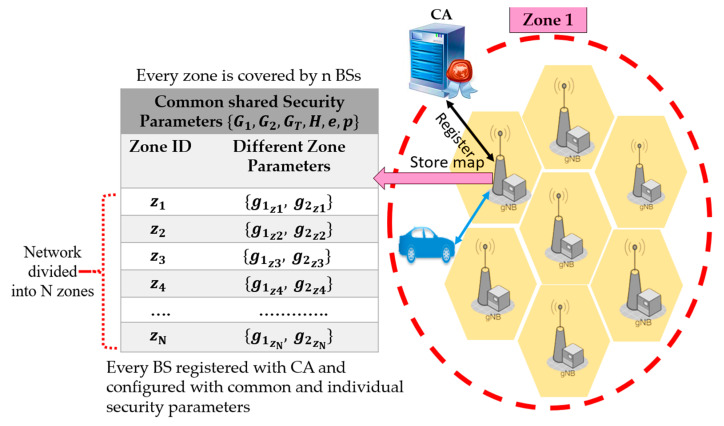
The deployment of 5G infrastructure requires many Base Stations (BSs), due to its shorter communication range than 4G. For network management purposes, the 5G standard uses a notion of a zone, which is a group of a few BSs. Therefore, we assume that the 5G-V2X network is divided into zones, where each zone consists of a few BSs, as shown in Figure 2. Our proposed system model includes the certificate authority (CA) that offers security services for the BSs and vehicles. CA has a map for the surrounding road and the positions of BSs on the road. CA initializes security parameters for the BSs in each zone, as shown in Figure 3. Each BS stores the security parameters that are configured by the CA. When entering a zone, each vehicle connects to the nearest BS and requests the key material and authentication parameters for the current zone. Vehicles can communicate in two modes. The first mode is single-zone communication that allows vehicles to securely communicate with other vehicles in the same zone (e.g., in Figure 2, in zone 1 communicates with ). The second mode is the multi-zone communication that allows vehicles in one zone to securely communicate with other vehicles positioned in other neighboring zones (e.g., in Figure 2, in zone 1 communicates with in zone 2). In each zone, all vehicles are configured with common security parameters. However, the vehicles also receive messages from the neighboring zones and thus require the security parameters of the neighboring zones for authentication.
Figure 2.
Single-zone and multi-zone communication in the 5G-V2X network model time for the three proposed authentication methods, and six previous related methods for single-zone and multi-zone scenarios.
Figure 3.
BSs registration with CA.
3.2. System Initialization
In this section, we discuss the vehicle registration process and the dynamic key generation, based on the elliptical curve cryptography (ECC) bilinear pairing technique.
3.2.1. Vehicle Registration
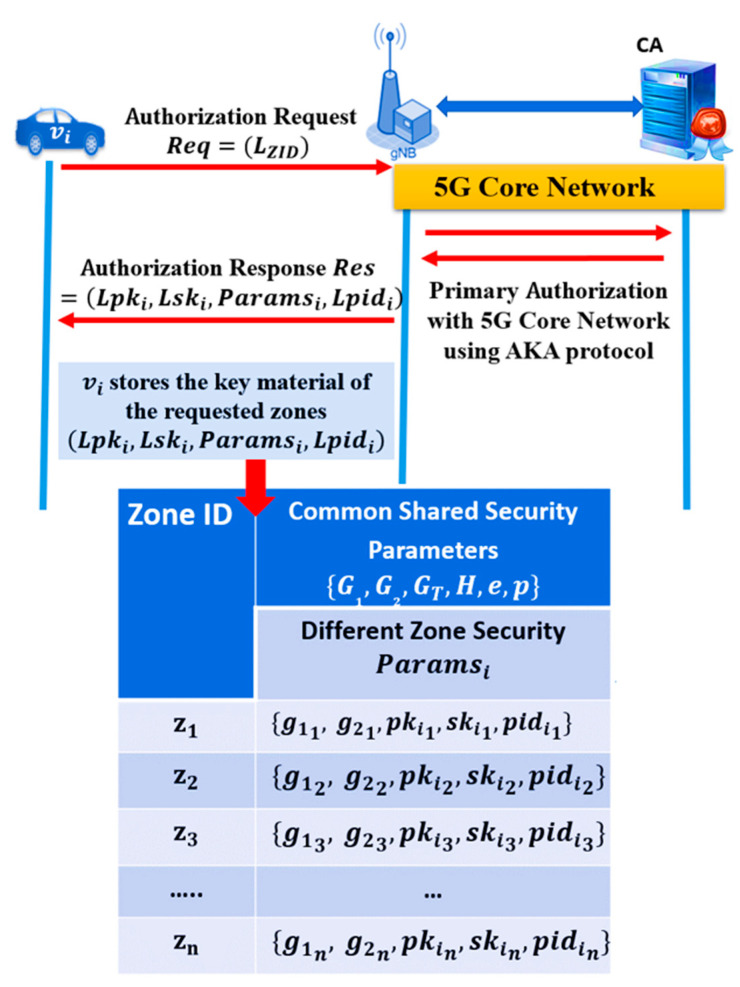
Vehicles in each zone have a unique pair of secret and public keys to communicate securely with vehicles in the same zone or another zone. A vehicle can send a message to vehicles using a single key pair or a set of key pairs, depending on the selected authentication method. Each vehicle requests the security parameters in advance, including the key pairs for multiple zones that are near the vehicle or are in its travel direction. BSs in each zone provides a security parameters list (secret keys, public keys, zone generators, and pseudo-identities) to the vehicles entering the zone. When a vehicle enters a new zone, it connects directly with the nearest base station and requests the authentication parameters for the current and neighboring zones. The process of authorizing the vehicles to access a 5G cell or zone is conducted using the AKA protocol of 5G standards. The details of the AKA protocol is out of scope for this study, but can be found in [29]. For example, vehicle sends an authorization request to the nearest BS, which might include a list of neighboring zone IDs . The BS forwards the authorization request message to the 5G core network, and sends back a response to the vehicle, once the authorization is successful. For each vehicle , BS generates a list of pseudo identities list of secret keys, and a list of the corresponding public keys , for every zone in the zone ID list , using the zone security parameters. Pseudo identities are used to preserve privacy and allow vehicles to communicate anonymously without exposing their real identities. These pseudo-identities can hide the real identity of the vehicle from other vehicles and prevent tracking attacks. BSs generate a list of pseudo-identities per vehicle, to reduce the vehicles’ frequent communication with the BSs. Pseudo-identities are short IDs that represent the anonymous identity of each vehicle and can replace the full certificate in PKI traditional solutions. We target a certificateless security solution that provides identity authentication using short size IDs. In authentication-based certificate solutions, each vehicle transmits a long certificate with each message that introduce long delays and a high communication cost. In contrast, our protocol supports anonymity and identity authentication, using a short size pseudo-identity. Pseudo-identities are generated by the BSs to allow CA to track vehicles under misbehaving conditions. Each vehicle stores a list of pseudo identities that are valid for a short time to support unlinkability and prevent traceability. Linking of pseudo-identities can disclose some information about the vehicle. We recommend changing pseudo-identity every 10 min, to enhance the security level while protecting the real vehicle information.
We also introduce a dynamic key generation by delegating the key generation to the BSs in each zone. In previous certificate-based methods, vehicles use a pair of the secret key and public key for a long time, which exposes the system key attacks. In contrast, our protocol supports updated key generation in each zone, which allows vehicles to use a different pair of secret and public keys for a short time. We provide the key generation based on the bilinear pairing cryptography over the Elliptic Curve. The BSs configured by the CA with commonly shared security parameters (elliptic curve E, two groups of points over the , one-way hash function , and a bilinear pairing function ).
The pseudo-identities, the secret, and public keys are used to support identity authentication and message authentication, respectively. stores until the next security parameters update, as shown in Figure 4.
Figure 4.
Vehicle primary authorization.
3.2.2. Dynamic Key Generation
We assume that all zones in the city share the common bilinear pairing parameters described below:
—two cyclic additive groups of prime order p, based on the elliptic curve E over the finite field where → .
—a cyclic multiplicative group containing the bilinear pairing result of the two groups .
—a cryptographic hash function that maps a message to a point in the group.
—the bilinear pairing function that maps elements from group and group to group , as in Equation (1).
—a large prime number representing the group order.
Additionally, all zones are configured with individual zone generator parameter .represents the generator point of the group for each zone. The generator point of a group is different for each zone, in order to provide different public keys per vehicle. Each elliptic curve group has a basic point that is used as a generator for all security parameters generated using this group. In our implementation, we used the elements of group over the elliptic curve, , to represent the public keys. We configured zones with individual zone to support different public keys. BS picks different random integers to represent the secret keys and use the correspondingto generate different public keys. Instead of using a single secret and public key for a long time without updating, our protocol allows vehicles to receive different secret and public key in every zone that makes the system resist different key attacks. In the following lines, we describe the key generation method in every zone and the security properties of bilinear pairing cryptography.
BS picks a random integerthe finite field that represents a finite element in the range {1 and p − 1.
BS picks a random integerthe finite field that represents a finite element in the range {1 and p − 1.
BS generates a public key for each vehicle in each zone, using the corresponding zone generator and the vehicle assigned secret key: , where .
After authorization of a vehicle entering a zone, BS sends to a message that contains parameters for , as well as the common parameters for the zone.
We generate public keys using the group , then any transmitter can sign a message using its corresponding secret key, to generate a signature that belongs to the group We called this operation bilinear pairing between two groups over the elliptic curve. Using the bilinear pairing between the two groups over the elliptic curve makes the security more complex than the traditional elliptic curve. At the receiver side, the sender’s public key, signature, and the pre-stored zone generator is used to verify the message and accept or reject it. The receiver hash the received message and try to map it to a point in group , based on the used bilinear pairing function and the zone common parameters. The bilinear pairing-based cryptography relies on the difficulty of the Elliptic Curve Discrete Logarithm Problem (ECDLP).
Before going further to illustrate the bilinear pairing properties, we briefly introduce the ECDLP, and for more information, readers can refer to [30]. Let be an elliptic curve that is defined over a finite field , of order . All points on the elliptic curve form an additive group usually denoted by In [31], Miller proposed a cryptosystem using a group of elliptic curve points defined over a finite field . The security level of this cryptosystem relies on the fact that the discrete logarithm problem over this defined group was shown to be hard to solve. This meant that cryptosystems that are designed based on the defined additive groups could achieve a higher or equal level of security with a smaller size for the used secret keys, as compared to other cryptosystems based on different arbitrary groups.
Let be a finite cyclic group with a generator point . Given a point , then for some secret . Find . In cryptosystems based on the discrete logarithm, the problem that is required to break and solve the system is defined as the Computational Diffie-Hellman Problem (CDHP).
In other words, Elliptic Curve Discrete Logarithm Problem (ECDLP)) can be defined as follows. Given , find an integer ∈ such that there is no efficient algorithm that can obtain 𝑎 in a short time. Up to now, there is no polynomial algorithm that can solve the ECDLP problem. We briefly introduce the bilinear pairing function properties using Equations (1)–(4).
Each operation for computing is a pairing operation where , and (finite field) [32].
In Equations (1)–(4), is a pairing function that efficiently satisfies bilinearity, non-degeneracy, and computable properties.
| (1) |
| (2) |
| (3) |
| (4) |
3.3. Three Proposed Authentication Methods
In this study, we propose a lightweight multi-zone authentication protocol that utilizes the bilinear pairing cryptography in message signing and verification. The zoning concept allows vehicles to have security parameters for every zone, without the need for high-cost re-authentication, every time the vehicle moves from one cell to another. The proposed protocol reduces the frequency of key request messages to BSs, by allowing vehicles to request all destination zone parameters in advance.
We propose three authentication methods that utilize ECC pairing-friendly curves to support broadcast multi-zone authentication. The proposed authentication methods are Transmitter Centric Authentication (TCA), Signature Concatenation-Authentication (SCA), and Receiver Centric Authentication (RCA).
3.3.1. Transmitter Centric Authentication (TCA)
In the TCA authentication method, transmitter vehicles generate signatures using their current zone parameters. The receivers in the transmitter’s zone or other zones use the security parameters of the transmitter’s zone to verify the signatures. While the receivers in the same transmitter zone use their pre-stored zone parameters to verify messages, the receivers in other zones search their security parameter table for the transmitter’s zone parameters. If the transmitter’s zone parameters do not exist in the table, the receivers request them from the nearest BS, through a secure channel. The TCA method can also be applied to a single-zone communication, where transmitters and receivers belong to the same zone. In the following, we first describe a single-zone case, followed by a multi-zone case.
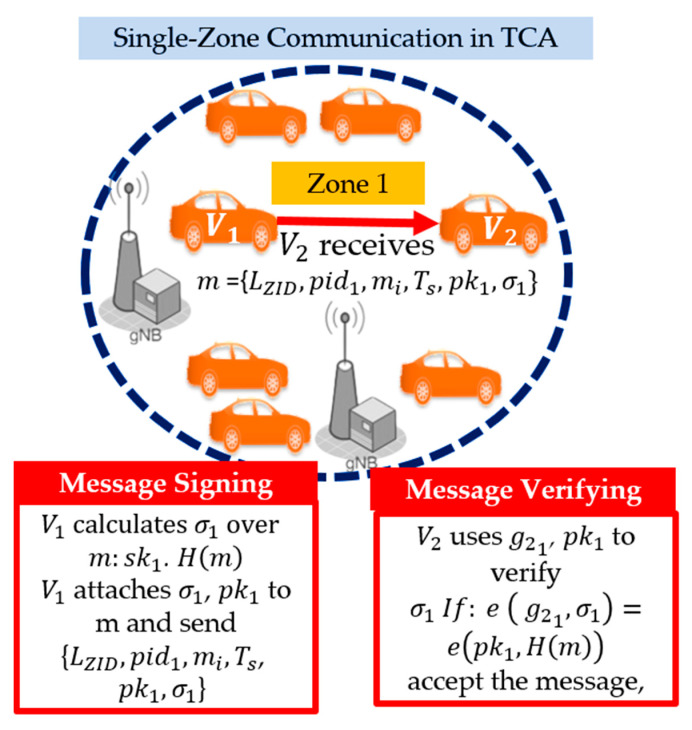
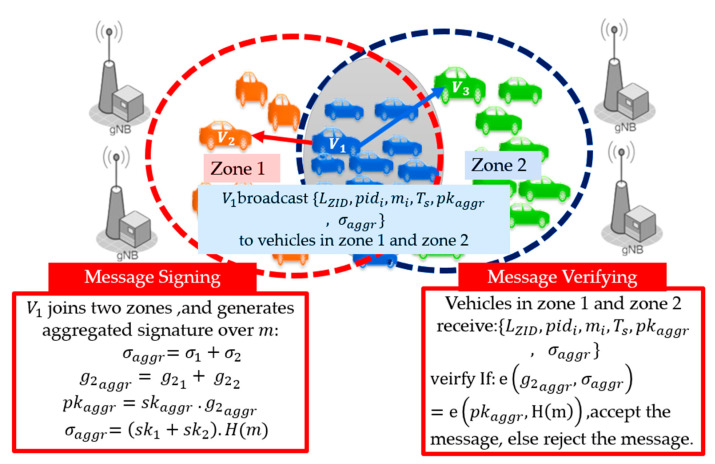
Single-Zone Case: A sender vehicle authenticates message m by calculating a bilinear pairing signature that can be verified by the receiver vehicle computes a hashed message H(m), where m = { In which represents a list of zone IDs, represents the pseudo-identity of , represents the message payload, and is a timestamp. Then, the hashed message H(m) is mapped to a point in the bilinear group using its secret key in zone 1. Then, attaches to each transmitted message the following resulting information—the signature, the public key, the sender’s pseudo-identity, zone ID (), and the current time stamp , which are illustrated in Figure 5. When receiver receives a signed message that contains checks the freshness of timestamp Ts. If is invalid, rejects the message; otherwise, checks the list of zone IDs . If the receiver’s zone ID matches the sender’s zone ID (), receiver starts verification of the signature using , and . Receivers accept the message if Equation (5) holds. Otherwise, they reject it.
Figure 5.
Single-zone communication in the TCA method.
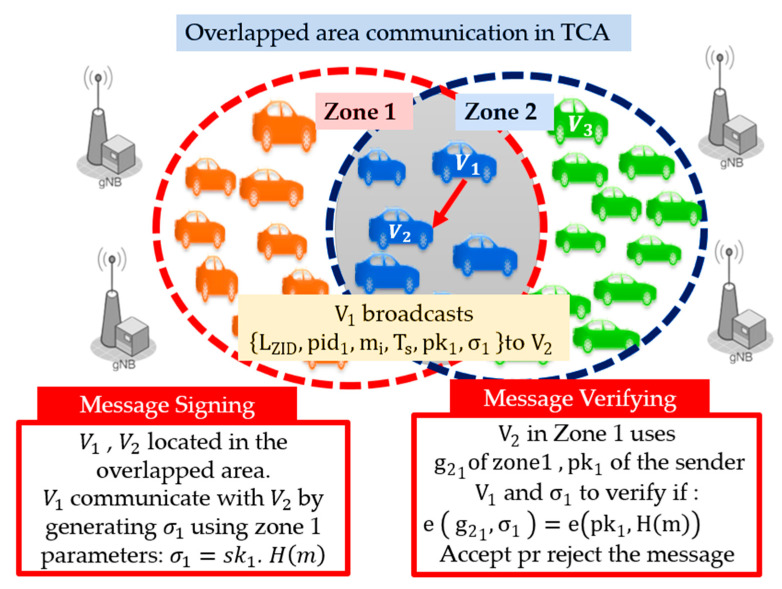
For the transmitter and receiver vehicles located in the overlapped area, they are considered as single-zone communication. TCA algorithm allows vehicles to choose the most updated zone parameters to communicate securely. If the security parameters are updated, all vehicles in the overlapped area receive the updates at the same time. Thus, the vehicles are free to choose the zone parameters, they can use zone 1 information or zone 2 information. As shown in Figure 6, and are located in the overlapped area where uses zone 1 security parameters to generate the signature over message m. received m, checks the freshness of , if its valid, checks the list of zone IDs The zone ID of the transmitter matches the zone ID of the receiver , starts verification of the signature using , and. Receivers accept the message if Equation (5) holds. Otherwise, they reject it, as shown in Figure 6.
Figure 6.
Overlapped area communication in TCA method.
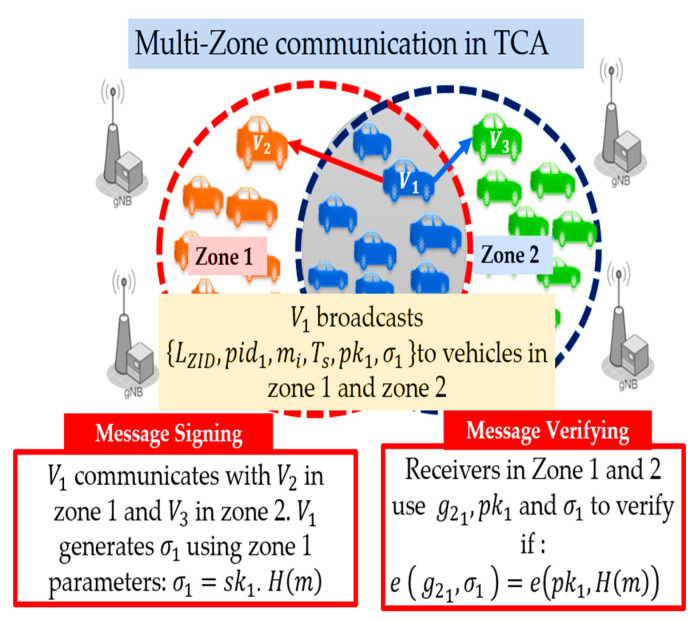
Multi-Zone Case: The multi-zone communication of the TCA method is shown in Figure 7. Here, transmitter joins zone 1 and zone 2, and thus simultaneously transmits to in zone 1 and in zone 2. In the TCA method, signs the message using zone 1 parameters, while the receivers in zone 1 and in zone 2 verify using the same parameters as the transmitter.
Figure 7.
Multi-zone communication in TCA.
Receivers in the same zone as transmitter use their zone information to verify the signature, while receivers in different zones search the zone parameter storage to find the transmitter’s zone information. If the information is not found, the receiver requests the transmitter’s zone parameters from the nearest BS. Algorithm 1 illustrates the signature generation and verification procedure of the proposed TCA authentication method. The signature verification depends on the bilinear pairing algebraic properties described in Equations (2)–(4). To verify a message under given , it checks if Equation (5) is held.
| Algorithm 1: Transmitter-Centric Authentication (TCA) Method |
|
Scenarios: -One transmitter to many receivers in the same zone (single-zone) -One transmitter to many receivers in different zones (multi-zone) Signature Generation:
|
| (5) |
If Equation (5) is satisfied, the receiver accepts the message, otherwise, it rejects it. The proof of bilinear pairing verification can be given by Equation (6):
| (6) |
Here,
| (7) |
In the TCA method, the transmitter vehicle uses the current zone parameters and allows receivers to find the correct zone parameters required to verify the message. The TCA method can allow vehicles in a boundary area to continue using the old zone security parameters. However, the zone parameters might be updated individually, making the verification process for receivers invalid, if some receivers are not updated in a timely manner with the transmitter’s parameter. The next proposed method can provide an alternative solution to this problem.
3.3.2. Signature-Concatenation Authentication (SCA)
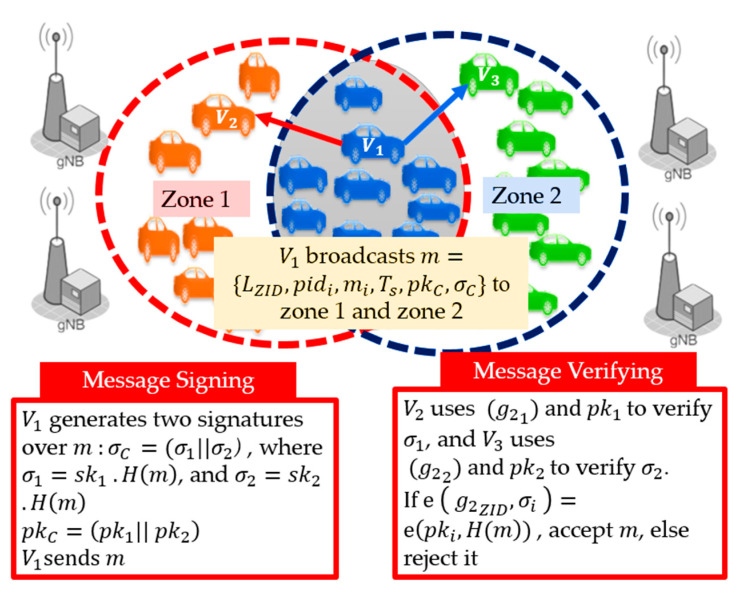
We introduce the second proposed method, Signature-Concatenation Authentication (SCA), using the example of Figure 8. We propose the Signature-Concatenation Authentication (SCA) method calculates the individual signatures for the receivers that belong to different zones and concatenates the signatures into one. For the case where the receivers are located in different zones, the transmitter vehicle attaches to its message a concatenated signature of different signatures, calculated for each zone. Then, the receivers in each zone verify only their signature corresponding to its zone, among the signatures. The transmitter generates signatures using the pre-stored secret keys of the transmitter within these communicated neighbor zones and attaches its corresponding public keys for verification. The transmitter provides the zone ID list , which indicates the ordering of the receiver zones to inform each receiver the signature that it should verify among the concatenated signatures. Each receiver verifies only the signature corresponding to their zone ID, using each receiver zone information, as shown in Figure 8.
Figure 8.
Multi-zone authentication using the signature concatenation (SCA) method.
Algorithm 2 illustrates the authentication procedure of SCA for the example of Figure 6. Vehicles in zone 1 substitutein Equation (5), to verify over message m, while vehicles in zone 2 verify using and .This method suffers from a high communication overhead in high-density scenarios where the target receivers are located in multiple zones.
| Algorithm 2: Signature-Concatenation based Authentication (SCA) |
Signature Generation:
|
3.3.3. Receiver Centric Authentication (RCA)
Next, we present the third method, Receiver Centric Authentication (RCA). It is a light-weight authentication method that allows vehicles in different zones to communicate using a short aggregated single signature that can be verified by any receiver vehicle that belongs to multiple neighbor zones. In this method, the transmitter vehicle aggregates the generator values of neighbor zones to generate aggregated public keys that allow the receivers to verify the message. In this method, receivers aggregate the neighboring zone’s generators to verify the message. For example, in zone 1 received messages from in zone 1 and in zone 2. Instead of broadcasting one message carrying two signatures for the receivers in the two zones like in the conventional method, RCA generates one message with a single signature to be verified by all vehicles in both zones. Vehicles generate a new aggregated secret key from their original zone’s secret keys to hide the original secrets and increase the security level. The transmitter vehicle searches the security parameters in its pre-stored table for the required. If the parameter cannot be found, it requests the possible combinations of from the nearest BS. It generates an aggregated public key corresponding to the secret keys { for the neighboring zones that have receivers. The generation of an aggregated public key and aggregated generators for the neighboring zones can be done offline, to reduce the computation time in the vehicles for every transmission. In the RCA method, the transmitter vehicles generate an aggregated secret key using the pre-stored vehicle secret keys for the neighboring zones and their corresponding aggregated public key, where represents the aggregated generators. The transmitter generates message m = {, and signs it using the aggregated secret key for the neighboring zones. It then generates a single signature. The transmitter broadcasts to all receivers in the neighboring zones. The receivers aggregate the required generators of the neighboring zones as the start of the verification process. Given , and , the receivers verify the message by checking if Equation (8) holds.
| (8) |
If Equation (8) is satisfied, the receiver accepts the message, else it rejects the message. Equations (9)–(11) define, and .
| (9) |
| (10) |
where
| (11) |
| (12) |
Algorithm 3 summarizes the signature generation and verification procedure of the proposed RCA method. Figure 9 illustrates an example of the RCA authentication method for the two zones. In Figure 7, the vehicles in orange belong to zone 1, the vehicles in green belong to zone 2, and the vehicles in blue belong to zone 1 and 2. Transmitter broadcasts a message m to the orange and green receivers, simultaneously. signs a message m in the following steps. calculates followed by . attaches an aggregated signature to the message. Then, the receivers in zone 1 and zone 2 can verify . The proof of the verification can be proved as follows, in Equation (13):
| (13) |
| Algorithm 3: Receiver-Centric Authentication (RCA) |
Signature Generation:
|
Figure 9.
Multi-zone authentication using Receiver-Centric Authentication (RCA) method.
4. Security Analysis of the MAPP Protocol
4.1. Security Requirement Analysis
Every security protocol must satisfy some primary security functions defined by the V2X security standards. The security requirements that must be satisfied by the proposed protocol is identity authentication, message authentication, non-repudiation, privacy-preserving, unlinkability, and system update [33].
In this section, we show how the proposed MAPP protocol accomplishes the required security functions.
4.1.1. Identity Authentication
In our protocol, each vehicle is registered with the BS using its real information. BSs are configured with common security parameters and individual security parameters to generate pseudo-identities for the vehicle. Pseudo-identities allow vehicles to communicate without revealing their real identities. Identity authentication is satisfied in the three proposed authentication methods, by allowing the dynamic random numbers to hide the real identity. Each transmitted message in our proposed methods is attached with , that is generated by an authorized third party (BSs). Each vehicle receives a list of updated pseudo-identities from the nearest BS, which can be used to authenticate the identity of each vehicle. Under misbehaving conditions, vehicles report the to the BS to remove the malicious vehicle from the network. We called our protocol certificatless bilinear pairing, as we replaced the long certificate in PKI solutions with a short size pseudo-identity that provides identity authentication and anonymity.
4.1.2. Message Authentication
Message authentication represents proof that the message has not been changed during transmission. Our protocol provides message authentication by calculating a short bilinear pairing signature over each transmitted message. The signature calculation is done by hashing the message and mapping it to a point over the elliptic curve, then signing it with the sender’s secret key. Verification of signature at receivers can provide the message authentication. In Equations (5), (7), and (8), each receiver in the different proposed methods can use the corresponding bilinear pairing equation to verify the signature, based on the received public key, the zone generator and the calculated signature. Verifying the validity of proves the message authenticity. If the verification failed at the receiver side, the message must be discarded.
4.1.3. Non-Repudiation
Any proposed security protocol must allow the non-repudiation service by providing the identity of the message sender, the accurate sending time, and the accurate location. The non-repudiation can prevent any sender from denying sending of any malicious message. If this service is not guaranteed, any driver can disseminate malicious messages without any punishment. Our proposed MAPP protocol attaches a pseudo-identity and a timestamp to each message m , to prove the non-repudiation requirement.
4.1.4. Privacy-Preserving
Privacy is an important security requirement that should be satisfied by the proposed security protocol. Privacy preservation is satisfied by hiding the real identity of vehicles and providing anonymity using pseudo-identity. In our protocol, we provide anonymity while allowing certificate authority organizations to trace the misbehaving vehicle and revoke them under misbehaving conditions. The trade-off between hiding the real identity and allowing CA to trace vehicles is a critical requirement that is satisfied in our protocol by generating a that has a relation with the initial registered information of each vehicle. Under misbehaving conditions, CA maps the vehicle’s pseudo-identity. In our proposed protocol, we assume that the pseudo-identity consists of two parts, the first part is , where Ri is a dynamic random number Ri, the second part is fixed , represented by the XORing between the initial pseudo-identity and the hashed value of reflects the real identity of each vehicle. The can preserve privacy while allowing the traceability of vehicles by the CA, under misbehaving conditions.
4.1.5. Unlinkability
The proposed methods use pseudo-identity change to make it hard for an attacker to link the new pseudo-identity with the old one, which preserves both the identity and the location privacy. The previous V2X standards suffer from position tracking problems. Our methods, however, never disclose the vehicle’s real identity, as the real identity is stored securely in the CA. Each pseudo-identity is composed of two parts—the first dynamic part is with a random number that changes with every transmitted message The second part is where a fixed value allows the CA to track the malicious vehicle, while the full pseudo-identity makes it hard to link two pseudo-identities.
4.1.6. System Updates
Our protocol provides a dynamic key generation in each zone that allows vehicles to use different secret and public keys for a short time. System updates prevent the key compromising attacks and protect the security material from sniffing attacks. Using a single key for a long time can be hacked within a defined time, after many trials to break it. Our system supports a list of secret keys, public keys, and pseudo-identities that help the vehicles to use short time keys and pseudo-identities.
From the previous analysis of different security requirements, we can prove that the proposed authentication methods support the standard security requirements, with a low-cost overhead.
4.2. Resistance to Attacks
The proposed protocol is secure against some common attacks described below.
4.2.1. Replay Attack
The proposed authentication method ensures the freshness of the transmitted message by attaching the current timestamp. For example, in the TCA method, the message format is , where is the attached time stamp. All vehicles should be synchronized to provide accurate time and resistance against the replay attacks. The synchronization of vehicles can be provided using GPS devices.
4.2.2. Modification Attack
In our protocol, message integrity is achieved using a short signature generated using an elliptic curve. The sender generates a message m, then calculates a signature over m by hashing m and then mapping it to a point on the elliptic curve using the secret key . The sender attaches the signature and the public key to allow the receiver to calculate a signature over the received message and then compare the transmitted signature and calculated signature to accept or reject the message. If the verification of is true, the receiver accepts the message, else it drops it. In this way, by verifying the signature over each message, our protocol ensures the message integrity and prevents-message alteration that proves our protocol’s ability to resist modification attacks.
4.2.3. System Key Compromising Attacks
In our protocol, we use a certificataless public key authentication algorithm that supports the high-security level, using a pair of secret keys and public keys. In contrast to protocols based on a single secret key that sends the shared secret for each message, to allow message verification at the receiver side. In our methods, we send the public key to allow the receiver to authenticate the signature that generated the message, using the corresponding secret key. For the RCA method, we generated a new secret key from the original secrets and for the communicated zones and a new public key using the zone generators of the communicated overlapped zones. Hiding the original secret keys, enhances the security level of the RCA method over the TCA and SCA method. Only authorized vehicles that registered with the BSs have access to the security zone parameters (. All vehicles at the initialization step register with the BS to receive the zone security parameters, after this, all parameters are stored securely at vehicles. Our protocol did not transmit the individual security parameters that make the system security high and difficult to break.
4.2.4. DOS Attacks
Our three proposed authentication methods support the immediate verification of packets. In contrast to key disclosure protocols that allow the receiver to wait till the sender discloses the signing key. The key disclosure protocols allow receivers to buffer a high number of packets until the key is received. Overwhelming the receiver buffer prevents the receiver from verifying the packets and result in message loss. For this, a large buffer size is required for key disclosure protocols, while in our authentication method, a small buffer is required to store a list of pseudo-identities, secret keys, and public keys .
From the previous analysis, we can summarize that our protocol can satisfy a wide range of security analysis and can resist a different type of attacks.
5. Communication Overhead Analysis
In this section, we compare the proposed MAPP protocol and the certificateless bilinear pairing methods [19,20,21,22,23,24]. To calculate the communication cost, we analyze the message structure of the MAPP protocol and the previous methods, based on the bilinear pairing [19,20,21,22,23,24]. For the security overhead calculations, we exclude the size of the traffic message payload, since it is common for all methods. In our implementation, we define the elliptic curve equation over a finite field , which is given by Equation (14).
| (14) |
We employ the Barreto–Naehrig (BN256) curves that offer asymmetric bilinear pairing (e.g., ≠ ) [34]. For BN256, we choose = 256 bits to give finite field points and a random number ≠ 0 to be a non-singular curve, which means that the curve has no cusps or self-intersections. The BN curve chooses = 2 to satisfy the non-singular condition and give optimum security. indicates the cyclic additive subgroup defined over ,, denoting a cyclic additive subgroup defined over , and represents the cyclic multiplicative subgroup defined over. , , and are defined with order . and elements are represented in a compressed form by the values of the x-coordinate instead of representing them by (x, y, z), which reduces their sizes to 32 and 64 bytes, respectively [35]. Table 3 summarizes the BN256 curve’s parameters and element size in the bilinear groups.
Table 3.
The BN256 bilinear pairing curve parameters.
| Pairing Curve equation | E: |
| Size of elements in the finite field | || = 32 bytes |
| Integer number over where = 2 | |
| Size of elements in the elliptic curve group | || = 32 bytes |
| Size of elements in the elliptic curve group | || = 2 || = 64 bytes |
| Size of elements in the result mapping group | || = 12 || = 384 bytes |
In the following, we analyze the overhead message of six previous methods (1) Horng et al. [19], (2) Li et al. [20], (3) Malhi et al. [21], (4) Lin et al. [22], (5) Bayat et al. [23], and (6) Boneh et al. [24], as well as the proposed MAPP.
(1) Horng et al. [19]:
The structure of the transmitted message is expressed by Equation (15):
| (15) |
where is the message payload, represents the vehicle pseudo-identity, represents the vehicle public key, represents the time stamp, and represents the signature. consists of two parts , where , . The total communication overhead for the message of Equation (15) is 64 + 32 + 64 + 4 +64 = 228 bytes.
(2) Li et al. [20]:
The structure of the transmitted message in [20] is also represented by Equation (15) and introduces a total communication overhead of 228 bytes.
(3) Malhi et al. [21]:
The structure of the transmitted message is expressed by Equation (16):
| (16) |
where is the message payload, while the vehicle’s pseudo-identity is represented by two parts {}. represents the public key , and represents the time stamp. represents the signature over the message and consists of two parts {}. The total communication overhead for the message of Equation (16) is = 64 + 64 + 64 + 4 + 64 + 64 = 324 bytes.
(4) Lin et al. [22]:
The structure of the transmitted message is defined in Equation (17), where group ID is used to identify the group where the vehicle belongs. The message payload includes information about the vehicle’s position, time of transmission, the direction of travel, and traffic events. A timestamp of 4 bytes is used to prevent the message replay attack. The signature over the message consists of 3 elements of . The Time-To-Live (TTL) controls how long the message is allowed to remain in the network.
| (17) |
The total communication overhead for the message of Equation (18) is
| (18) |
(5) Bayat et al. [23]:
The parameters for transmitted messages are represented by Equation (19):
| (19) |
where a message payload , a pseudo-identity ∈ consists of two parts (), a signature ∈ , and a timestamp . The communication overhead of one message is 64 + 64 + 4 = 196 bytes.
(6) Boneh et al. [24]:
The parameters for the transmitted message are calculated using Equation (20):
| (20) |
where a message payload , represents the group public key that consists of 5 elements and . Additionally, a group signature σ consists of three elements of and six elements of , and a timestamp .
The total communication overhead for the message of Equation (20) is = 32 + 64 + (3 × 32) + 64 + (3 × 32) + 6 × 32 + 4 = 548 bytes.
5.1. Proposed TCA Method
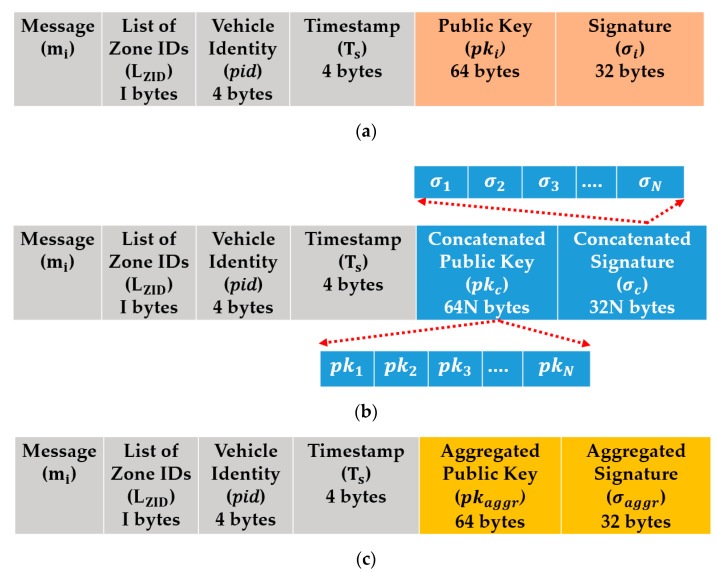
The message structure of the proposed authentication TCA method is shown in Figure 10a, which is analyzed as follows. In the TCA method for single-zone communication, the transmitted message structure is represented by Equation (21).
| (21) |
Figure 10.
The proposed protocol message structure. (a) TCA method, (b) SCA method, and (c) RCA method. Where represents the message payload, represents the pseudo-identity of , and represents a list of zone IDs. represents the time stamp, represents the public key of , and represents the signature over the message. In our implementation, a signature and the public key is . The total communication overhead of one message is 4 + 4 + 1 + 64 + 32 = 105 bytes.
5.2. Proposed SCA Method
The message structure of the proposed authentication SCA method is shown in Figure 10b, we analyzed the SCA message structure using Equation (22):
| (22) |
where Therefore, the total communication overhead was 4 + 1 + 4 + 64N + 32N = 9 + 96N bytes. The communication overhead for the SCA method depend on the number of communicated zones N.
5.3. Proposed RCA Method
The message structure of the proposed authentication RCA method is shown in Figure 10c, we analyzed the RCA message structure using Equation (23). RCA method support multi-zone authentication based on the aggregated security parameters of the communicated zones.
| (23) |
In RCA, the total communication overhead is = 1 + 4 + 4 + 64 + 32 = 105 bytes.
In SCA and RCA, we choose 1 byte for , as we assume that the maximum number of zones cannot exceed 256. While in the TCA method, we only send a single transmitter zone ID.
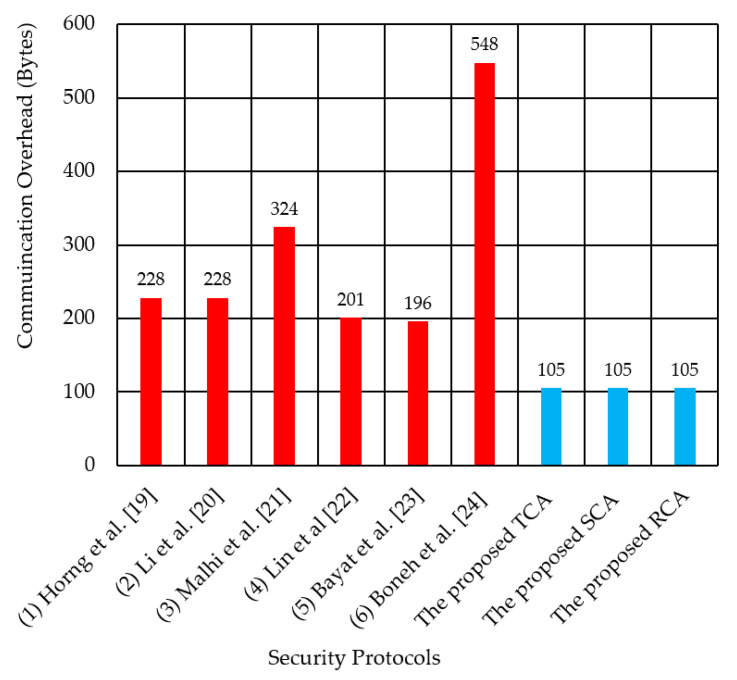
Figure 11 compares the communication cost of the three proposed methods and the six previous methods in single-zone communication. It shows that the three proposed methods outperform all six previous methods, by reducing the communication cost by 50–80% in a single-zone scenario.
Figure 11.
Comparison of communication cost per message for the three proposed authentication methods and the compared security protocols for single-zone scenario.
In a multi-zone scenario, all previous methods repeatedly transmit the same message for multiple individual destination zones that require different signing keys. In contrast, the proposed authentication methods (TCA, SCA, RCA) send a single signed message to zones and allow the receivers in multiple zones to verify the same message.
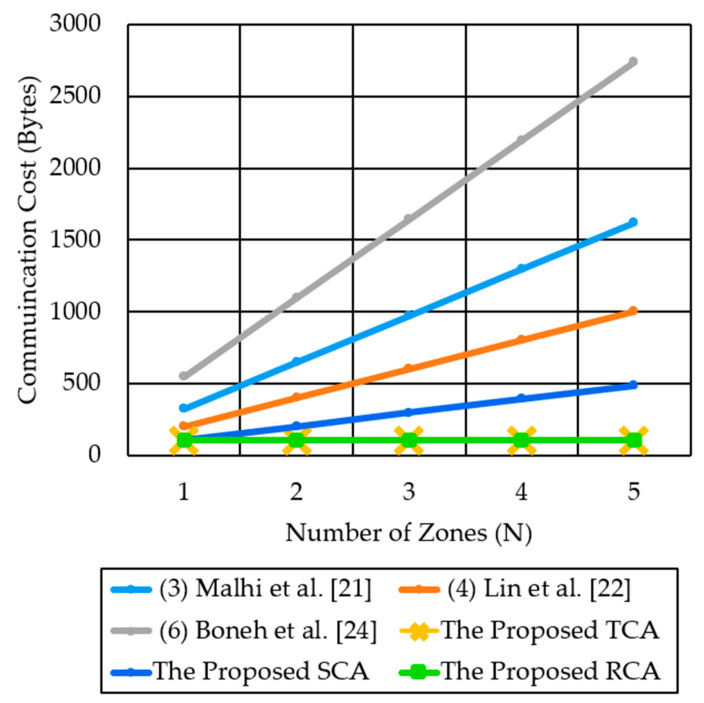
Figure 12 compares the communication cost of the three proposed methods with three previous methods (3) Malhi et al. [21], (4) Lin et al. [22], and (6) Boneh et al. [24]. We choose to compare our methods with the previous [21,22,24], only because we found that the other protocols introduce nearly the same communication overhead. We tried to show the differences between our methods and the previous methods.
Figure 12.
Comparison of communication cost for the proposed authentication methods and the compared security protocols for the multi-zone scenario.
TCA and RCA incur a constant communication cost of 105 bytes per message, irrespective of the number of destination zones. In contrast, the proposed SCA method and the previous methods [21,22,24] show the communication cost increasing along with the number of destination zones . However, the proposed SCA method shows much lower growth in the increase of the cost than the previous methods. For example, in the case of = 5, SCA has a cost of only 489 bytes, while the previous methods, Boneh et al. [24], Lin et al. [22] and Malhi et al. [21] incur significantly higher communication cost, as high as 2740, 1005, and 1620 bytes, respectively. For multi-zone communication of 5 destination zones, the proposed TCA and RCA methods reduce the communication cost by 26 times, while the SCA method reduces the communication cost by 2–5 times, as compared to the three previous methods of [21,22,24].
6. Computation Overhead Analysis
To evaluate the computation overhead of the proposed protocol, we implemented it using a simplified C-V2X protocol simulator and a bilinear pairing cryptography library called MCL [36]. MCL implements functions for the elliptic curve cryptography that supports optimal pairing over (BN) curves. We chose a BN curve with an embedding degree = 12, which supports a 128-bit security level over a prime field of size 256 bits [37].
To compare the computation overhead, we also implemented the six previous methods [19,20,21,22,23,24] that were analyzed in Section 4. We tested all methods under the same experimental environment for a fair comparison. Table 4 shows the average execution time of the primary cryptographic operations of the BN256 curve in our simulator. The simulations are conducted in a hardware platform employing an Intel Core I7-4770 processor with a 3.6 GHz clock, Linux gcc.5.4.0, and a main memory of 4 GB.
Table 4.
Average execution time of the BN254 pairing functions used in our simulation.
| Operation | Definition | Time in (ms) |
|---|---|---|
| Bilinear pairing | The time needed to perform one bilinear pairing of elements from group and group to group | TP = 2.446 |
| Addition in | The time of addition of two points inside group | TAG1 = 0.007 |
| Multiplication in | Scalar multiplication of a point inside group and a random integer | TMG1 = 0.479 |
| Addition in | The time of addition of two points inside group | TAG2 = 0.013 |
| Multiplication in | Scalar multiplication of a point inside group and a random integer | TMG2 = 0.989 |
| HashAndMap to or | The time of hashing message using sha-256 then map the hashed result to a point in the group or group | TM2P = 0.135 |
| Hashing Operation | the time defined for one hash function operation using SHA-256 algorithm | TH = 0.006 |
| Addition in | The time of addition of two points over the finite filed | TAFp = 0.001 |
In the following, we analyze the signature generation time and signature verification time of the six previous methods—(1) Horng et al. [19], (2) Li et al. [20], (3) Malhi et al. [21], (4) Lin et al. [22], (5) Bayat et al. [23], and (6) Boneh et al. [24], as well as the proposed MAPP for the single-zone and multi-zone scenarios. We analyze the computation overhead for signature generation and signature verification. In Horng et al.’s protocol [19], the signature generation per message requires two scalar multiplication and two addition in the group, which results in a computation overhead of 2TMG1 + 2TAG1 = 0.9594 ms. Its signature verification per message requires three pairings, one scalar multiplication in, and one hash map, which results in a computation overhead of 3TP + TMG1 + TM2P = 3 × 2.446 + 0.479 + 0.135 = 7.8305 ms.
Similarly, we analyzed the signature generation time and verification time of the other previous methods [20,21,22,23,24]. The analysis results are summarized by the formulas in Table 5.
Table 5.
A comparison of signature generation time and verification time for the proposed authentication methods and the previous methods in single-zone and multi-zone scenarios.
| Security Methods | Signature Generation Time Per Message for Single Zone Case (ms) | Signature Verification Time Per Message for Single Zone Case (ms) | Signature Generation Time Per Message for n Receivers in n Multi-Zones (ms) | Signature Verification Time Per Message for Each Receiver in n Multi-Zones (ms) |
|---|---|---|---|---|
| (1) Horng et al. [19] | 2TMG1 + 2TAG1 = 0.9594 | 3TP + TMG1 + TM2P = 7.8305 | 0.9594n | 3 nTP + nTMG1 + nTM2P = 952.7n |
| (2) Li et al. [20] | TAG1 + 2TMG1 + TM2P = 1.1 | 3TP + TMG1 + 2TM2P + TAG1 = 8.094 | 1.1n | 3nTP + nTMG1 + 2nTM2P + nTAG1 = 8.094n |
| (3) Malhi et al. [21] | 4TMG1 + 2TAG1 = 1.93 | 3TP + 3TMG1 + TAG1 = 8.782 | 1.93n | 3nTP + 3nTMG1 + nTAG1 = 8.778n |
| (4) Lin et al. [22] | 3TP + TM2P = 7.473 | 5TP + 8TMG1 = 16.132 | 7.473n | 5nTP + 8nTMG1 = 16.132n |
| (5) Bayat et al. [23] | 5TMG1 + TAG1 + TH + TM2P = 2.549 |
3TP + TMG1 + TH + TM2P = 7.8365 | 2.549n | 3n TP + nTMG1 + nTM2P = 7.952n |
| (6) Boneh et al. [24] | 3TP + 5TMG1 = 9.7275 | 4TP + 2TM2P = 10.054 | 9.7275n | 4nTP + 2nTM2P = 10.054n |
| The proposed TCA | TM2P + TMG1 = 0.614 | 2TP + TM2P = 4.9 + 0.135 = 5.035 | 0.614 | 2TP = 5.035 |
| The proposed SCA | TM2P + TMG1 = 0.614 | 2TP + TM2P = 4.9 + 0.135 = 5.035 | 0.614n | 2TP = 5.035 |
| The proposed RCA |
= 0.600 + 0.014n |
0.600 + 0.014n | 5.014 + 0.013n |
Finally, we analyzed the signature generation time and verification time for the three proposed MAPP protocol.
6.1. Proposed TCA Method
For the TCA method in single-zone communication, signature generation requires one hash computation, mapping to a point in the group and one scalar multiplication over group, where Hence, the signature generation time can be represented by TM2P + TMG1 = 0.479 + 0.135 = 0.614 ms. Signature verification requires two pairing operations to check the validity of the bilinear pairing operation, where Thus, the signature verification time is two pairing operations and one HashAndMapTo operation = 2TP + TM2P = 4.9 + 0.135 = 5.035 ms. For the case of TCA, both the signature generation and verification overhead is constant, irrespective of the number of destination zones. The total computation time due to security overhead is the combination of signature generation time and signature verification time. For the TCA method, the computation overhead is TM2P + TMG1 +2TP+TM2P = 0.479 + 0.135 + 4.9 + 0.135 = 5.649 ms; (the cryptographic operations used in the computation time calculations are defined in Table 4).
6.2. Proposed SCA Method
In the case of the SCA method, the signature generation time of, where is n concatenated signatures per message that consumes n(TM2P + TMG1) = n (0.479 + 0.135) = 0.614n ms, where a single signature generation time is 0.614ms. On the other hand, the signature verification consumes two pairing operations and one HashAndMapTo operation = 2TP+TM2P = 4.9 + 0.135 = 5.035 ms. Verification time incurs only a constant overhead of 5.035 ms, since the individual receiver verifies only its corresponding signature and ignores the other signatures. We also assume that concatenation operations of n signatures at the transmitter side is neglected, as compared to the signature generation time. We assume that the searching time for the correct zone parameters is negligible, as compared to the verification time. Thus, the total computation time for the SCA method is the concatenated signature generation time, and the individual verification time at each receiver is (0.614n) ms + 5.035 ms. The computation time of SCA depends on the number of destination zones .
6.3. Proposed RCA Method
The computation time at senders including the aggregation time of and
consumes addition operations over (TAFp = While needs addition operations in a group = (TAG2 = 0.013ms.
Therefore, the generation time of single signature requires mapping to a point in the group, and one scalar multiplication over and the aggregation time of and Therefore, the signature generation time is TM2P + TMG1 + = 0.600 ms + n*0.014 ms.
While the signature verification per message requires the aggregation of that requires addition in mapping to a point in the group, and one scalar multiplication over . Therefore, the signature verification time is (TAG2 + TM2P + 2TP = 0.135 + 4.9 = 5.014 + n*0.013 ms.
Thus, the total computation time for the RCA method including the signature generation time, the verification time, and the aggregation time of at the transmitter 0.600 ms + n*0.014 ms + 5.014 + n*0.013 ms. Therefore, the total computation time is 5.614 ms + (0.027n) ms. The computation time of SCA depends on the number of destination zones .
From the described analysis, we found that the TCA method computation time is the lowest among the other proposed methods (SCA and RCA). While the RCA method introduces a little overhead, as compared to the high overhead of the SCA method that requires the generation of n signatures at transmitters.
Table 5 compares the computation overhead of the three proposed authentication methods and the six previous methods [19,20,21,22,23,24], for single-zone and multi-zone scenarios. In a multi-zone scenario, the six previous methods incur a high computation overhead to sign messages for destination zones. In contrast, the three proposed methods in a multi-zone scenario send a single message with a single short signature.
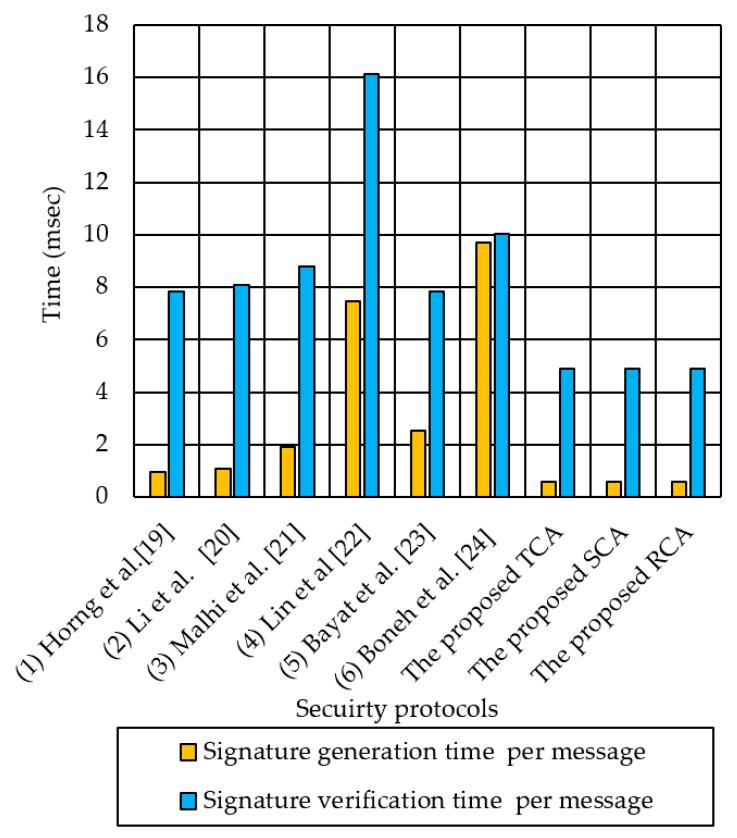
Figure 13 shows the computation cost per message, including the signature generation time and verification time for the three proposed authentication methods and the six previous methods [19,20,21,22,23,24], for the single-zone scenario. For the single-zone, the signature generation time per message of Boneh et al. [24] is as long as 9.7275 ms, as one signature generation requires 3 bilinear pairings and five scalar multiplication over group . It is 16 times longer than the proposed three authentication methods, which consume only 0.614 ms for signature generation. For signature verification, the previous methods [19,20,21,22,23,24] incur as long as 16 ms (for the case of [22]), due to their excessive use of bilinear pairing in verification. It is 4 times longer than the three proposed authentication methods that incur only 5.035 ms for verification.
Figure 13.
A comparison of signature generation time and verification time for the proposed TCA method and the six previous methods in a single-zone scenario.
In a multi-zone scenario, the previous methods repeatedly transmit the same message with different signatures to multiple destination zones. However, the three proposed authentication methods send a single signed message to multiple receivers in different zones. Each receiver in multiple zones individually verifies the same signature by just one verification step, which provides a constant verification time regardless of . As shown in Figure 14, we compare the signature generation time in multi-zone scenarios for the three proposed authentication methods (TCA, SCA, RCA) and three previous methods, Lin et al. [22], Bayat et al. [23], and Boneh et al. [24]. TCA for multi-zone scenarios introduces a fixed computation time of 0.614 ms for a signature generation, regardless of the number of destination zones. SCA introduces 0.614n ms, which linearly increases with the number of destination zones. While RCA introduces a little increase in singing time, due to aggregation of and .
Figure 14.
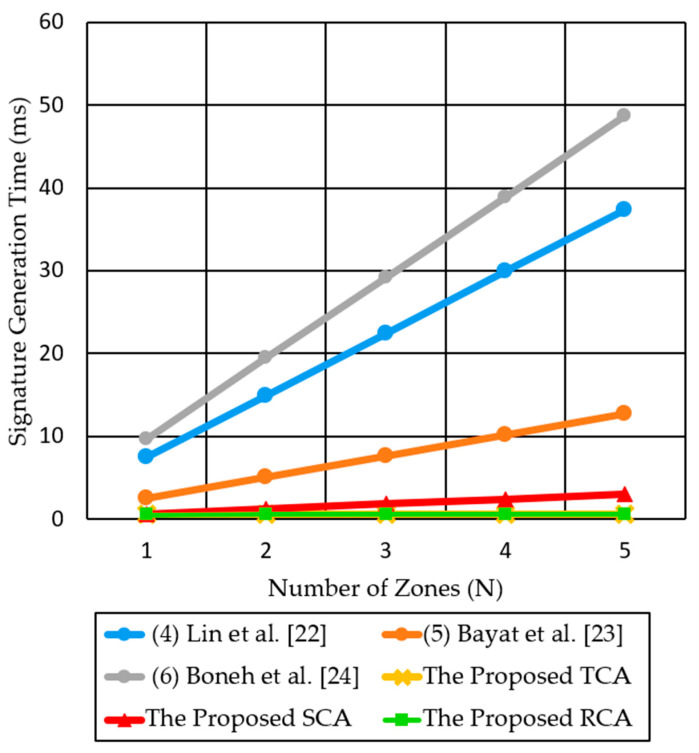
Comparison of signature generation time for the three proposed authentication methods and the two previous methods for multi-zone scenarios.
For = 5, Lin et al. [22], Bayat et al. [23], Boneh et al. [24], SCA, TCA, and RCA consume signature generation time of 37.3 ms, 12.745 ms, 48.6 ms, 3.07 ms, 0.614 ms, and 0.67 ms, respectively. Therefore, the proposed methods significantly reduce the signature generation time by 16 times–80 times, as compared to the two previous methods [22,24].
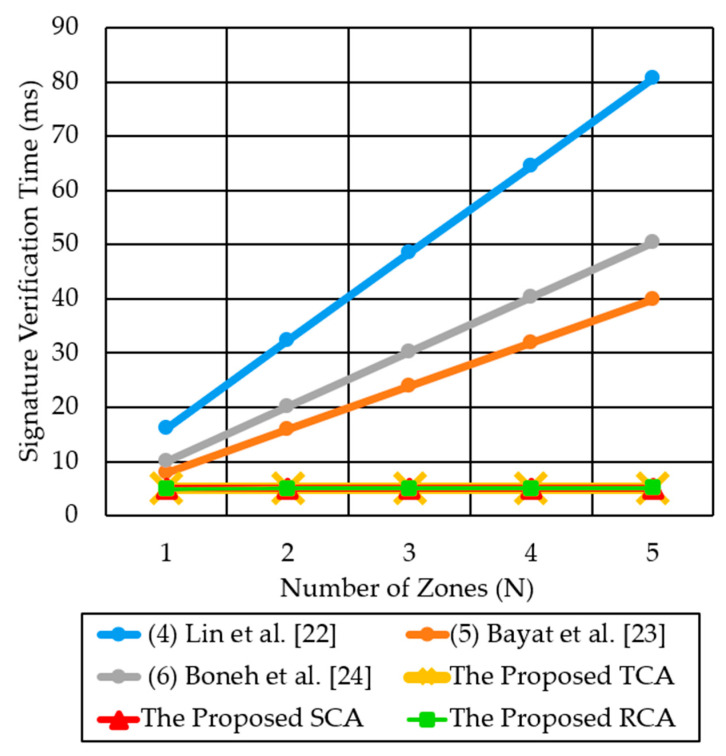
As shown in Figure 15, we compare the signature verification time in multi-zone scenarios for the three proposed authentication methods (TCA, SCA, RCA) and two previous methods, Lin et al. [22] and Boneh et al. [24]. TCA and SCA for multi-zone scenarios introduce a fixed computation time of 5.035 ms, for a signature verification, regardless of the number of destination zones. For = 5, Lin et al. [22], Boneh et al. [24], SCA, TCA, and RCA consume signature generation times of 80.66 ms, 50.27 ms, 5.035 ms, 5.035 ms, and 5.079 ms, respectively. Therefore, the proposed methods significantly reduce the signature verification time by 10–16 times, as compared to the two previous methods.
Figure 15.
Comparison of signature verification time for the three proposed authentication methods and the two previous methods for multi-zone scenarios.
In summary, the reduction ratio in communication and computation overhead that the proposed methods provide, tends to rapidly increase for a large-scale network with a large number of neighboring zones. In our future work, we intend to improve the proposed authentication methods by integrating them into different 5G applications, as recommended by the authors of [38]. We also intend to implement the proposed authentication methods using hardware devices and compare the performance with the results of our previous decentralized hash-chain-based protocol [39].
7. Conclusions
In this paper, we presented three authentication methods for multi-zone communications, based on the bilinear pairing cryptography and short signatures. The 5G-V2X standards support the installation of many base stations at short distances, which can be utilized to provide a dynamic key generation and multi-hop authentication for vehicles. In this paper, we divide the network into N zones, each zone covered by n BSs. Each vehicle communicates securely using different keys per zone, which enhances the security level and supports updated keys through different zones. In the proposed TCA method, the signature generation and verification depend on the transmitter zone parameters. In the proposed SCA method, the transmitter generates a concatenated signature that can be verified individually by all receivers, using their corresponding zone parameters. Transmitters and receivers in the RCA method aggregate the security parameters of the communicated neighboring zones to generate and verify signatures. The proposed three authentication methods support message signing and verification at a low cost, using short signatures over bilinear pairing curves. We compared the communication and computation cost of the proposed authentication methods and six previous methods for single-zone and multi-zone scenarios. The proposed methods significantly reduce the signature generation time by 16 times–80 times, as compared to the compared previous methods. Additionally, the proposed methods significantly reduce the signature verification time by 10 times–16 times, as compared to the two previous methods. The three proposed authentication methods achieved substantial speed-up in the signature generation time and verification time, using a short bilinear pairing signature.
Author Contributions
S.A.A.H. did the data collection, conceptualization, experiments, software implementation, writing the draft, editing, and reviewing. H.K. did the conceptualization, editing, reviewing, and funding. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by IITP grant (No. 2020-0-01304), Development of Self-learnable Mobile Recursive Neural Network Processor Technology Project, and also supported by the Grand Information Technology Research Center support program (IITP-2020-0-01462) supervised by the IITP and funded by the MSIT (Ministry of Science and ICT), Korean government. It was also supported by Industry coupled IoT Semiconductor System Convergence Nurturing Center under System Semiconductor Convergence Specialist Nurturing Project funded by the National Research Foundation (NRF) of Korea (2020M3H2A107678611).
Conflicts of Interest
The authors declare no conflict of interest.
Footnotes
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.jurisdictional Atallah R.F., Khabbaz M.J., Assi C.M. Vehicular networking: A survey on spectrum access technologies and persisting challenges. Veh. Commun. 2015;2:125–149. doi: 10.1016/j.vehcom.2015.03.005. [DOI] [Google Scholar]
- 2.Abboud K., Omar H.A., Zhuang W. Interworking of DSRC and Cellular Network Technologies for V2X Communications: A Survey. IEEE Trans. Veh. Technol. 2016;65:9457–9470. doi: 10.1109/TVT.2016.2591558. [DOI] [Google Scholar]
- 3.Hoymann C., Astely D., Stattin M., Wikstrom G., Cheng J.-F., Hoglund A., Frenne M., Blasco R., Huschke J., Gunnarsson F. LTE release 14 outlook. IEEE Commun. Mag. 2016;54:44–49. doi: 10.1109/MCOM.2016.7497765. [DOI] [Google Scholar]
- 4.Mir Z.H., Filali F. LTE and IEEE 802.11p for vehicular networking: A performance evaluation. EURASIP J. Wirel. Commun. Netw. 2014;89 doi: 10.1186/1687-1499-2014-89. [DOI] [Google Scholar]
- 5.Hakeem S.A.A., Hady A.A., Kim H.-W. 5G-V2X: Standardization, architecture, use cases, network-slicing, and edge-computing. Wirel. Netw. 2020:1–27. doi: 10.1007/s11276-020-02419-8. [DOI] [Google Scholar]
- 6.Muhammad M., Safdar G.A. Survey on existing authentication issues for cellular-assisted V2X communication. Veh. Commun. 2018;12:50–65. doi: 10.1016/j.vehcom.2018.01.008. [DOI] [Google Scholar]
- 7.Alnasser A., Sun H., Jiang J. Cyber security challenges and solutions for V2X communications: A survey. Comput. Netw. 2019;151:52–67. doi: 10.1016/j.comnet.2018.12.018. [DOI] [Google Scholar]
- 8.Rajavelsamy R., Das D. A Review on 3GPP 5G Security Aspects. Adv. Comput. Commun. 2019 doi: 10.34048/2019.2.cf. [DOI] [Google Scholar]
- 9.Ben Henda N. Overview on the Security in 5G Phase 2. J. ICT Stand. 2020:1–14. doi: 10.13052/jicts2245-800X.811. [DOI] [Google Scholar]
- 10.Lu R., Zhang L., Ni J., Fang Y. 5G Vehicle-to-Everything Services: Gearing Up for Security and Privacy. Proc. IEEE. 2020;108:373–389. doi: 10.1109/JPROC.2019.2948302. [DOI] [Google Scholar]
- 11.Xiaohu G., Song T., Guoqiang M., Wang C., Han T. 5G ultra-dense cellular networks. IEEE Wirel. Commun. 2016;23:72–79. [Google Scholar]
- 12.Condoluci M., Gallo L., Mussot L., Kousaridas A., Spapis P., Mahlouji M., Mahmoodi T. 5G V2X System-Level Architecture of 5GCAR Project. Future Internet. 2019;11:217. doi: 10.3390/fi11100217. [DOI] [Google Scholar]
- 13.Haidar F., Kaiser A., Lonc B. On the Performance Evaluation of Vehicular PKI Protocol for V2X Communications Security; Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall); Toronto, ON, Canada. 24–27 September 2017; Piscataway, NJ, USA: IEEE; pp. 1–5. [DOI] [Google Scholar]
- 14.He D., Zeadally S., Xu B., Huang X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015;10:2681–2691. doi: 10.1109/TIFS.2015.2473820. [DOI] [Google Scholar]
- 15.Lo N.-W., Tsai J.-L. An Efficient Conditional Privacy-Preserving Authentication Scheme for Vehicular Sensor Networks Without Pairings. IEEE Trans. Intell. Transp. Syst. 2016;17:1319–1328. doi: 10.1109/TITS.2015.2502322. [DOI] [Google Scholar]
- 16.Liu Y., He Z., Zhao S., Wang L. An efficient anonymous authentication protocol using batch operations for VANETs. Multimed. Tools Appl. 2016;75:17689–17709. doi: 10.1007/s11042-016-3614-9. [DOI] [Google Scholar]
- 17.Tzeng S.-F., Horng S.-J., Li T., Wang X., Huang P.-H., Khan M.K. Enhancing Security and Privacy for Identity-Based Batch Verification Scheme in VANETs. IEEE Trans. Veh. Technol. 2017;66:3235–3248. doi: 10.1109/TVT.2015.2406877. [DOI] [Google Scholar]
- 18.Hu X., Wang J., Xu H., Liu Y., Zhang X. Intelligent Computing Methodologies. Volume 9773. Springer; Berlin/Heidelberg, Germany: 2016. Secure and Pairing-Free Identity-Based Batch Verification Scheme in Vehicle Ad-Hoc Networks; pp. 11–20. [Google Scholar]
- 19.Horng S.-J., Tzeng S.-F., Huang P.-H., Wang X., Li T., Khan M.K. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Inf. Sci. 2015;317:48–66. doi: 10.1016/j.ins.2015.04.033. [DOI] [Google Scholar]
- 20.Li J., Yuan H., Zhang Y. Cryptanalysis and Improvement of Certificateless Aggregate Signature with Conditional Privacy Preserving for Vehicular Sensor Networks. IACR; Lyon, France: 2016. [(accessed on 10 December 2020)]. Available online: https://eprint.iacr.org/2016/692. [Google Scholar]
- 21.Malhi A.K., Batra S. An efficient certificateless aggregate signature scheme for vehicular ad-hoc networks. Discret. Math. Theor. Comput. Sci. 2015;17:317–338. [Google Scholar]
- 22.Lin X., Sun X., Ho P.-H., Shen X. GSIS: A Secure and Privacy-Preserving Protocol for Vehicular Communications. IEEE Trans. Veh. Technol. 2007;56:3442–3456. doi: 10.1109/tvt.2007.906878. [DOI] [Google Scholar]
- 23.Bayat M., Barmshoory M., Rahimi M., Aref M.R. A secure authentication scheme for VANETs with batch verification. Wirel. Netw. 2015;21:1733–1743. doi: 10.1007/s11276-014-0881-0. [DOI] [Google Scholar]
- 24.Boneh D., Lynn B., Shacham H. Short signatures from the Weil pairing. J. Cryptol. 2004;17:297–319. doi: 10.1007/s00145-004-0314-9. [DOI] [Google Scholar]
- 25.Wymeersch H., Seco-Granados G., Destino G., Dardari D., Tufvesson F. 5G mmWave Positioning for Vehicular Networks. IEEE Wirel. Commun. 2017;24:80–86. doi: 10.1109/MWC.2017.1600374. [DOI] [Google Scholar]
- 26.Bergren S. Design Considerations for a 5G Network Architecture. arXiv. 20171705.02902 [Google Scholar]
- 27.El-Beaino W., El-Hajj A.M., Dawy Z. On Radio network planning for next generation 5G networks: A case study; Proceedings of the 2015 International Conference on Communications, Signal Processing, and their Applications (ICCSPA’15); Sharjah, UAE. 17–19 February 2015; Piscataway, NJ, USA: Institute of Electrical and Electronics Engineers (IEEE); 2015. pp. 1–6. [Google Scholar]
- 28.Tsai C.-W., Cho H.-H., Shih T.K., Pan J.-S., Rodrigues J.J.P.C. Metaheuristics for the deployment of 5G. IEEE Wirel. Commun. 2015;22:40–46. doi: 10.1109/MWC.2015.7368823. [DOI] [Google Scholar]
- 29.Braeken A. Symmetric key based 5G AKA authentication protocol satisfying anonymity and unlinkability. Comput. Netw. 2020;181:107424. doi: 10.1016/j.comnet.2020.107424. [DOI] [Google Scholar]
- 30.Miller V.S. Use of Elliptic Curves in Cryptography; Proceedings of the Conference on the Theory and Application of Cryptographic Techniques; Santa Barbara, CA, USA. 18–22 August 1985; Berlin/Heidelberg, Germany: Springer; 1986. pp. 417–426. [Google Scholar]
- 31.Koblitz N. Elliptic curve cryptosystems. Math. Comput. 1987;48:203–209. doi: 10.1090/S0025-5718-1987-0866109-5. [DOI] [Google Scholar]
- 32.Galbraith S.D., Paterson K.G., Smart N.P. Pairings for cryptographers. Discret. Appl. Math. 2008;156:3113–3121. doi: 10.1016/j.dam.2007.12.010. [DOI] [Google Scholar]
- 33.Hakeem S.A.A., El-Gawad M.A.A., Kim H. A Decentralized Lightweight Authentication and Privacy Protocol for Vehicular Networks. IEEE Access. 2019;7:119689–119705. doi: 10.1109/ACCESS.2019.2937182. [DOI] [Google Scholar]
- 34.Barreto P.S.L.M., Naehrig M. Pairing-Friendly Elliptic Curves of Prime Order. In: Preneel B., Tavares S., editors. SAC 2005: Selected Areas in Cryptography. Lecture Notes in Computer Science. Volume 3897. Springer; Berlin/Heidelberg, Germany: 2006. [DOI] [Google Scholar]
- 35.Scott M., Barreto P.S.L.M. Compressed pairings. In: Franklin M., editor. Annual International Cryptology Conference—CRYPTO 2004. Lecture Notes in Computer Science. Volume 3152. Sringer; Berlin/Heidelberg, Germany: 2004. pp. 140–156. [Google Scholar]
- 36.GitHub herumi/mcl. [(accessed on 19 August 2020)]; Available online: https://github.com/herumi/mcl.
- 37.Devegili A.J., Scott M., Dahab R. Implementing Cryptographic Pairings over Barreto-Naehrig Curves. In: Takagi T., Okamoto T., Okamoto E., Okamoto T., editors. Pairing-Based Cryptography—Pairing 2007. Lecture Notes in Computer Science. Volume 4575. Springer; Berlin/Heidelberg, Germany: 2007. [DOI] [Google Scholar]
- 38.Hakeem S.A.A., Hady A.A., Kim H.-W. Current and future developments to improve 5G-NewRadio performance in vehicle-to-everything communications. Telecommun. Syst. 2020;75:1–23. doi: 10.1007/s11235-020-00704-7. [DOI] [Google Scholar]
- 39.Hakeem S.A.A., El-Gawad M.A.A., Kim H.-W. Comparative Experiments of V2X Security Protocol Based on Hash Chain Cryptography. Sensors. 2020;20:5719. doi: 10.3390/s20195719. [DOI] [PMC free article] [PubMed] [Google Scholar]