Abstract
The current pandemic situation due to COVID-19 is seriously affecting our daily work and life. To block the propagation of infectious diseases, an effective contact tracing mechanism needs to be implemented. Unfortunately, existing schemes have severe privacy issues that jeopardize the identity-privacy and location-privacy for both users and patients. Although some privacy-preserving systems have been proposed, there remain several issues caused by centralization. To mitigate this issues, we propose a Privacy-preserving contact Tracing scheme in 5G-integrated and Blockchain-based Medical applications, named PTBM. In PTBM, the 5G-integrated network is leveraged as the underlying infrastructure where everyone can perform location checking with his mobile phones or even wearable devices connected to 5G network to find whether they have been in possible contact with a diagnosed patient without violating their privacy. A trusted medical center can effectively trace the patients and their corresponding close contacts. Thorough security and performance analysis show that the proposed PTBM scheme achieves privacy protection, traceability, reliability, and authentication, with high computation & communication efficiency and low latency.
Keywords: 5G, Blockchain, Contact tracing, Medical applications, Privacy protection
1. Introduction
We are currently in a critical period of fighting the corona virus (COVID-19) epidemic, where everyone hopes that the whole society will restore to the original order as soon as possible. To achieve this, both commercial healthcare/pharmaceutical organizations and academic researchers in related fields are actively contributing. Until now, hundreds of COVID-19-related papers have been published that have enabled researchers and the general public to know more about overcoming the spread of disease. For example, researchers in [21] used natural language processing techniques to find the propagation characteristics of situation information related to COVID-19 in social media such as Sina Weibo1 .
Besides, more novel technicians have been used to help people fight for this aggressive epidemic. The 5G technology has been considered as one of the promising technicians during the COVID-19 pandemic, which enables higher communication resources with low latency. A report of the World Economic Forum (WEF) [14] shows that COVID-19 rises 5G to the 2nd rank of most discussed tech topics (before COVID-19 is 7th rank). Another report [13] figures that COVID-19 is accelerating 5G demand in some industries such as healthcare. Under this circumstance, more research papers related to 5G and healthcare [1], [9], [23], [31], [42] have been published, which indicates that it is valuable to research 5G-based medical applications especially COVID-19-related applications.
During those medical applications, contact tracing can be considered as an important step in the prevention and control of infectious diseases such as COVID-19. In a typical contact tracing scenario, the close contacts of a patient will be traced and advised to seek proactive treatment from medical organizations as they have a higher probability to be infected compared to non-contacts. A recent study published in Lancet [5] shows that aggressive close contact tracking and isolation is the key measure to Shenzhen city’s control of COVID-19 transmission. Hence, it will be helpful to stop the infectious virus from spreading further, if an effective solution of contact tracing is established.
In the current pandemic situation, the privacy of information has become an extremely sensitive issue, as, on one hand, immediate information sharing related to contacts is necessary, while on the flip side medical records (and identity) have to be kept confidential. Because users’ medical data seems to be more sensitive, medical-related privacy issues appear to be more serious and will cause greater losses compared with privacy issues in scenarios like IoT [35], [38], vehicular network [40], smart grid [36], and cloud computing [33], [34], [37], [39]. A report of IBM in 2019 [18] shows that the average cost of data loss per leakage has risen to $3.92 million, where healthcare suffers from the highest loss of $6.45 million per security breach. To mitigate these severe issues caused by privacy leakage, research in both academic and industrial areas has tried to propose new medical applications with the privacy-preserving properties. For example, MIT [27] uses Bluetooth signals from smartphones to perform automated contact tracing privately. Besides, Apple and Google jointly announced a contact tracing system that also makes use of Bluetooth-based proximity-detection technology to find close contacts without compromising location privacy [3].
Unfortunately, there are still some issues with existing contact tracing solutions that need to be solved. More specifically:
-
•
Centralized Architecture: All the existing schemes are based on a centralized architecture. In that case, the system may suffer from single-point failure (data breach) that will affect the availability of the whole system.
-
•
Unreliable Data Storage: Data stored on a centralized server can be easily deleted or tampered with, by malicious system administrators. Besides, malicious users may upload fake information to the system to evade supervision.
-
•
Limited Privacy Protection: Privacy protection cannot be fully guaranteed. Existing privacy-preserving solutions can prevent privacy from violating by external adversaries. However, different companies, entities, and agencies who possess the user’s private data have unlimited access privileges to them, which may also lead to privacy abuse.
In light of these issues that limit the practical use of existing contact tracing systems, we propose a novel privacy-preserving contact tracing scheme in blockchain-based medical applications, named PTBM. More specifically, the 5G-integrated network architecture is leveraged to achieve high communication bandwidth with low propagation & response latency. Blockchain is used to achieve reliable data storage & verification, and secure cryptographic primitives are also leveraged to protect identity privacy and location privacy for both users and patients. To the best of our knowledge, this is the first privacy-preserving contact tracing scheme with a decentralized architecture that achieves reliability in large scale emergency systems.
Following are the major contributions of this work.
-
•
We design a novel decentralized architecture of contact tracing applications, where the 5G-integrated blockchain network is leveraged as underlying infrastructures. Both permissionless and permissioned blockchains are used to achieve public location checking and supervised data storage & tracing, respectively.
-
•
We propose PTBM, a decentralized contact tracing scheme based on the hierarchy of blockchain and secure cryptographic primitives to protect the identity privacy and location privacy for both public users and patients without losing the tracing ability of trusted medical center.
-
•
We make thorough security analysis and performance evaluation to prove that the proposed PTBM scheme achieves privacy protection, reliability, authentication, and traceability with high computation & communication efficiency and low latency.
The rest of the paper is organized into seven sections. Section 2 gives the background and motivation of the scheme including the related works. Section 3 introduces the fundamentals of blockchain, PCSD cryptosystem, and the bloom filter. Section 4 presents the formalized system model, security model, and design goals of PTBM. In Section 5, we elaborate on the complete working of the proposed scheme, followed by the security analysis and performance evaluation in sections 6 and 7, respectively. Finally, Section 8 concludes the paper.
2. Related works and motivations
In this section, some related works about blockchain with 5G, existing contact tracing mechanism and blockchain-based medical applications are introduced, which prove the novelty of the proposed scheme because to the best of our knowledge, none of the existing schemes supports reliable and privacy-preserving contact tracing with low latency.
2.1. Blockchain with 5G technology
Both the blockchain and 5G can be considered as the next-generations technology, hence their integration also attracts the attention of researchers, which covers a variety of scenarios including Internet-of-Things (IoT) [4], [17], [41], and edge computing [15], [19], [28].
In the IoT scenario, Zhang et al. [41] proposed an edge intelligence and blockchain empowered IIoT framework under the 5G environment. The proposed scheme includes a cross-domain resource scheduling mechanism and a credit-differentiated edge transaction approval mechanism. It also achieves secure service management and low latency with the help of blockchain and 5G. Hewa et al. [17] presented an automatic certificate revocation scheme, where Elliptic Curve Qu Vanstone (ECQV) certificates are used to achieve lightweight authentication for the resource-restricted IoT devices, and smart contracts are used to achieve reliable and automatic certificate revocation. The proposed scheme realizes a lightweight certificate store, update, and revocation, hence it is suitable for the 5G-based wireless network that interconnects millions of IoT devices. Bera et al. [4] introduced the issues and challenges of applying blockchain in the 5G-based IoT environment. They also presented a secure framework for blockchain-based data management that can resist several potential attacks and achieve reliability. Detailed analysis shows that the proposed scheme provides less communication and computation overheads as compared to other relevant works.
In the edge computing scenario, Nkenyereye et al. [28] adopted a 5G cellular architecture of Emergency Driven Message (EDM) Protocol which provides higher scalability with lower latency. They also constructed a blockchain-based system where each node is seen as an edge node to reliably store EDM records of which the privacy is protected by a lightweight signcryption scheme. Jangirala et al. [19] designed a lightweight RFID-based authentication protocol for supply chains, named LBRAPS. Their proposed LBRAPS protocol uses several lightweight cryptographic primitives such as bitwise XOR and one-way hash functions, hence it is suitable for the 5G mobile edge computing environment. Gao et al. [15] incorporated another novel technique, software-defined networks (SDNs) to ensure effective management for blockchain-enabled fog computing in 5G networks. The article also shows that the combination of blockchain and the SDN relieves the pressure of the centralized controller.
Besides, some privacy-preserving schemes that try to leverage 5G technology in blockchain-oriented solutions have been presented [7], [10], [11], [16], [22], [26]. We can conclude that more and more researchers are paying attention to solve the privacy issues in 5G-integrated blockchain networks.
2.2. Contact tracing
The current outbreak of coronavirus in the world has attracted extensive attention from both academic institutions and researchers in various fields. The work in [30] analyzed the advantages and shortcomings of several existing privacy-aware contact tracing solutions. It concludes from observations in existing solutions that: 1) the importance of location information is usually ignored, 2) the privacy concerns and trust relationship are generally missing, 3) the reliability cannot be guaranteed because large companies or malicious users can manipulate the uploaded data, and 4) deployment of the systems in the real-world scenario is not specified.
In the contact tracing scenario, Ahmed et al. [2] summarizes existing mobile contact tracing APPs which can be divided into three architectures: centralizing, decentralizing, and hybrid. It also concludes that security and privacy issues are one of the most concerns that these APPs are still facing. Fitzsimons et al. [12] designed a privacy-preserving contact tracing mechanism by introducing secure two-party computation (2PC). More specifically, 2PC is used to securely calculate the distance between the location trajectory for a patient and a user. If the calculated distance is below the given threshold, the user will be considered as a close contact of the patient. However, the computation and communication costs of verification are relatively high because the 2PC protocol should be followed for each user who wants to perform the contact tracing operation.
Xu et al. presented BeepTrace [32], a blockchain-based privacy-preserving contact tracing scheme where pseudonyms are used to achieve the unlinkability between the on-chain data and the real-world identity, and the uploaded on-chain data are also encrypted by the corresponding user. Compared with other existing technicians, BeepTrace achieves privacy protection with a decentralized architecture. Unfortunately, the user uses Geo public key to encrypt the location information, and the location privacy cannot be well guaranteed if the Geo Solver who holds the decryption private key is malicious. Besides, it cannot actively trace the contact of a given patient.
2.3. Blockchain-based medical applications
Because of the decentralization and immutability of the blockchain, several works have introduced blockchain in medical applications to achieve reliable medical data storage, analysis, and sharing. Biswas et al. [6] present a comprehensive analysis of challenges and solutions for using blockchain effectively in e-healthcare systems. Liu at al[24]. proposed a blockchain-based data sharing scheme to address the privacy issue of Electronic Medical Record (EMR) sharing. The proposed scheme also used CP-ABE-based access control and the content extraction signature scheme. Li et al. [20] proposed a blockchain-based medical data preservation system to realize privacy-preserving and verifiable medical data storage. Shen et al. [29] presented a privacy-preserving image retrieval mechanism for medical IoT systems that used customized blockchain transaction structures to store the feature vector for each image. Smart contracts are also used to execute privacy-preserving image retrieval based on the feature vectors. Chang et al. [8] discussed how blockchain can help people in the fight against COVID-19. From their perspective, blockchain will be widely used in future medical applications.
2.4. Motivations
Based on the above analysis, we make three conclusions that form the major motivation of this work:
-
1.
The integration of blockchain achieves reliable data storage and program execution in a decentralized manner, which also mitigates the computation & computation loads and the probability of single-point failure of centralized servers. Unfortunately, the communication delay of blockchain is relatively high because of the decentralization property.
-
2.
The incorporation of the 5G network brings out more powerful communication ability with higher bandwidth and lower latency compared with the existing 4G-based wireless networks. However, most of the 5G devices are small IoT or fog devices such as communication base station, smartphone, or even wearable devices, has relative low computation ability and storage capacity, which results in unreliable data storage and transmission.
-
3.
The techniques of contact tracing are just in their infancy, which means more effective mechanisms and solutions need to be developed. Besides, the decentralization property of blockchain can be widely used in medical applications to solve the issues caused by centralized architecture.
In PTBM, we use the blockchain-based 5G network and lightweight cryptographic primitives as the underlying infrastructure and higher construction respectively to achieve reliable and privacy-preserving contact tracing with high efficiency and low latency. More specifically, the reliability of blockchain and enhanced communication bandwidth with low latency of 5G network will be utilized, whereas the deficiencies bring from using either of them alone will be eliminated. The privacy of the user’s identity and the patient route can be well protected, whereas the traceability can be also guaranteed.
3. Preliminaries
In this section, some basic primitives used in the proposed scheme are introduced. These include the blockchain system, public-key cryptosystem with strong key decryption (PCSD), and the bloom filter (BF).
3.1. Blockchain
The concept of blockchain originates from the Bitcoin cryptocurrency that achieves reliable transactions under decentralized and trust-less circumstances. Blockchain can be seen as a distributed and append-only ledger with immutability, hence the data stored on the blockchain cannot be deleted or tampered with.
Blockchain can be primarily categorized into two types: permissioned and permissionless blockchain. Before participating in the permissioned blockchain, all users must register with the Trusted Authority (TA), hence only the authorized (registered) users can get access to the data block stored on the ledger. The permissionless blockchain does not need access control, and anyone can participate in and query the data stored on the blockchain, however, this leads to scalability and public accountability as well as some privacy issues. For example, external attackers can perform inference attacks that use statistical analysis to shrink the data privacy and identity privacy of the blockchain users with the help of background knowledge.
For the purpose of mitigating these privacy issues, we use the hierarchical architecture of blockchain with secure cryptographic primitives to achieve privacy protection without losing the decentralization & accountability properties.
3.2. Public-key cryptosystem with strong private key decryption
The concept of PCSD derives from the Public-Key Cryptosystem with Distributed Decryption (PCDD) presented in [25]. PCSD consists of the following algorithms:
-
•
is a probabilistic algorithm that receives a security parameter and a number of key-pairs as input, and outputs a strong private key and key-pairs . Let be two large prime numbers that satisfy . Set and . Choose with order and define a function . For each compute where is randomly selected. The public key and private key for is and respectively. The strong private key is .
-
•
is a probabilistic algorithm that receives ’s public key and a message and outputs a ciphertext associated with . Given ’s public key and a message choose randomly and compute the ciphertext where and .
-
•
is a deterministic algorithm that receives ’s private key and a ciphertext and outputs the message . With ’s private key the message can be recovered by computing .
-
•
is a deterministic algorithm that receives a strong private key and a ciphertext as input, and outputs the message . For any ciphertext the corresponding message can be recovered by computing .
Assume is encrypted by ’s public key note that for all the corresponding message can be recovered by using . Hence we call a strong private key. Entities (other users and attackers) that do not know or the cyphertext cannot be decrypted. We leverage this property of PCSD to achieve privacy-preserving tracing in the proposed PTBM scheme.
3.3. Bloom filter
The BF can be considered as an indexed structure used for membership queries. The idea of BF is to choose independent secure hash functions with the same domain and range . The BF consists of three algorithms described as follows:
-
•
Init: Choose an -bit vector that will be used to store the membership information. All the bits in are set to 0.
-
•
Insert: All the members in will be inserted into the vector . More specifically, to insert a membership hashed values will be computed, and each position of will be set to 1.
-
•
Query: To query whether hashed values will be computed. If there exists an such that the corresponding position of is 0, it means otherwise .
Note that can also be implemented using a hash table. The Insert algorithm inserts all the entries indexed by with value 1 (i.e., for each ). In the Query algorithm if there exists an such that it means . In the proposed scheme, we use this implementation to store the location state information to protect the user’s location privacy as well as realizing efficient location checking operations.
4. Problem formalization
In this section, we formalize the system model, threat model, and design goals of the proposed PTBM scheme.
4.1. System model
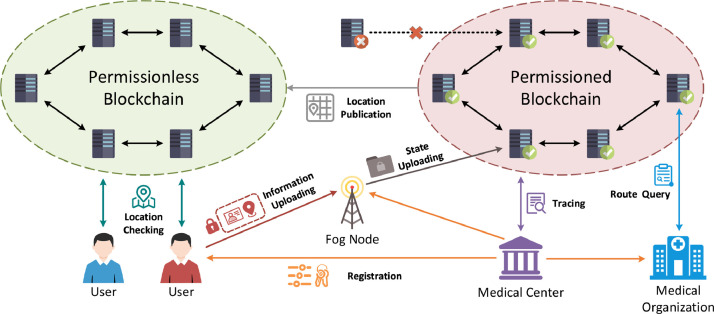
The system consists of five entities: Medical Center (MC), Fog Nodes, Users, Medical Organization (MO), and Blockchain systems, as shown in Fig. 1 .
Fig. 1.
System model.
4.1.1. Medical center
The MC can be considered as a trusted authority controlled by the government. It performs the registration operation to generate & distribute the system parameter and key-pairs for each user, MO, and fog node. MC will stay offline after registration unless it needs to trace the patient information or MO’s misbehavior. In that case, it will trace the data stored on the permissioned blockchain. Hence, the introduction of MC cannot violate the decentralization property of the blockchain. Furthermore, this allows that any MC (public or private sector entity) can be easily made part of the existing healthcare infrastructure.
4.1.2. Fog nodes
The fog nodes are deployed beside the checkpoints that are also controlled by the government. These checkpoints are specially set up to check body temperature and/or other parameters for public health monitoring. Because we utilize the 5G-integrated network as the underlying infrastructure, which means all the fog nodes are connected by 5G wireless network via 5G base station. Besides, then can also connect other 5G terminals such as the user’s mobile phone or other 5G-supported wireless devices. It uploads the user’s encrypted location checking information and periodically uploads its current state to the permissioned blockchain.
4.1.3. Users
When a user wants to cross a checkpoint, they will use their mobile phone to upload their identity and location information encrypted by their respective public key via 5G wireless channel. Besides, they can execute location checking on the permissionless blockchain to check whether their historical route includes dangerous areas where infected patients have been found.
4.1.4. Medical organizations
The MOs can be seen as primary healthcare institutions (e.g., community clinics) that treat infectious patients. MO will maintain several nodes in both permissioned and permissionless blockchain for patient route query and location publication respectively. The patients’ activity areas will be published to the permissionless blockchain so that every user can check whether they have been to these areas. If they have, then they can go to a nearby MO for examination and treatment in time.
4.1.5. Blockchain
In our proposed system, there exist two kinds of blockchain: permissionless and permissioned blockchain. Everyone can get access to the data stored on the permissionless blockchain, whereas, only the MC, MO, and Fog Nodes have the read & write permissions for the permissioned blockchain. The hierarchical architecture of blockchain enables enhanced security guarantees and advanced privacy protection for both users and patients. Note that all the blockchain nodes can be also connected via 5G wireless networks which enable higher communication channel capacity with lower latency.
4.2. Threat model
In our threat model, we assume that MC cannot be compromised, and the data stored in MC cannot be leaked. Moreover, MC distributes the system parameter and key-pairs via secure channels.
Both the fog nodes and MOs are honest-but-curious, which means that they exactly perform the presented algorithms and protocols, however, they try to infer both users’ and patients’ private information from the data stored on the blockchain. Note that the collusion between fog nodes and MOs is not allowed because fog nodes are controlled by the government as mentioned earlier.
Most of the users are honest, however, there exist several malicious users that try to impersonate other legitimate users to upload fake information to evade supervision.
4.3. Design goals
Here we introduce the design goals of PTBM. Note that in Section 6, we prove that PTBM realizes all of these design goals.
Privacy Protection: The proposed scheme should protect every user/patient’s identity privacy and route location privacy simultaneously. More specifically, both honest-but-curious MO and external adversaries cannot infer the real-world identity or recover the exact route of both users and patients.
Reliability & Authentication: The data uploaded by both users and MOs cannot be modified by both external or internal adversaries, and all the users, fog nodes, MOs, and MC can obtain the correct query/tracing result. Besides, an effective authentication mechanism should be introduced to avoid impersonation attacks by malicious users.
Traceability: Given a designated patient, his route should be traced, and all the users that might have been in close contact with the patient should also be traced. Note that this tracing operation should only be executed by MC. Besides, MC can also trace the misbehavior of MO.
Efficiency: Due to the limited computation and storage capacity of the devices in the 5G-integrated network, the computation complexity should be as low as possible, especially for users and fog nodes that make use of mobile and IoT devices, respectively. Besides, the communication costs should also below to save the channel resource and bring out low latency.
5. The proposed PTBM scheme
In this section, a detailed description of the proposed PTBM scheme is given. The notations used in this work are illustrated in Table 1 .
Table 1.
List of notations.
| Notation | Description |
|---|---|
| Security parameter | |
| The number of users | |
| The number of fog nodes | |
| The pseudonym of user and fog node | |
| Signature key-pair for user | |
| Encryption key-pair for fog node | |
| Secret key and strong private key for MC | |
| A secure pseudo-random function. | |
| secure hash functions |
5.1. Registration
In this process, MC first generates a secret key held by MC itself, and the strong private key & signature key-pair where the key-pairs will be distributed to the corresponding fog nodes.
Besides, MC randomly chooses a secure digital signature scheme DS that consists of three algorithms: KeyGen (key generation), Sig (signature), and Ver (verification). Then it chooses a secure random function and secure hash functions . These functions can be seen as system parameters that will be sent to all the users and fog nodes.
For each user associated with the real identity MC generates ’s pseudonym and signature key-pair . Then it sends to user through secure channels, and publishes to the permissioned blockchain. Besides, it will initialize a list on permissioned blockchain for each user that will be used to store the encrypted route information.
For each fog node associated with the real identity MC also generates the pseudonym . Then is sends to fog node through secure channels. Besides, it will initialize a dictionary on the permissioned blockchain that will be used to store the encrypted state information. Note that each is associated with a geographic location about the checkpoint, of which the correspondence is held by MC secretly.
For each MO it needs the real identity and the public key for registration. MC will generate the corresponding blockchain address used on both permissioned and permissionless blockchain to invoke smart contracts of Route Query and Location Publishing, respectively. Finally, MC publishes to the permissioned blockchain.
5.2. Information uploading
When a user wants to cross a checkpoint associated with fog node it first sends a request to where is the current timestamp and is the signature generated by ’s private key.
After receiving first check whether the timestamp is obsolete. If the difference between current time and exceeds the threshold will be rejected. If the time checking is successful, it queries ’s public key by searching the permissioned blockchain with the index and verifies the signature by executing . If the verification returns true, it inserts to the bloom filter where is a random string that represents ’s current state. If the verification returns false, will also be rejected. Finally, adds to stored on the permissioned blockchain where represents the current timestamp.
Note that is periodically updated, and will upload the current state information to stored on the permissioned blockchain before the update operation, where is the encrypted pseudonym of and represents the users that passed-by in this time period. For each .
5.3. Route query
When a medical organization MO receives a patient it uses the address to execute route query contract of the corresponding given by with the preset start timestamp . More specifically, MO queries the permissioned blockchain and obtains ’s recent route where each satisfies . Note that elements in are arranged in chronological order, hence the elements in also follow a chronological order.
5.4. Location publication
During the route tracing operation, MO obtains ’s recent route then it uses the address to perform location publication contract. More specifically, for each MO obtains from the permissioned blockchain. The encrypted pseudonym and user’s information are used for MC’s tracing, and the corresponding bloom filter will be published as the activity area information to the permissionless blockchain.
In our scenario, all the patients are seen as infectious disease patients, hence their recent activity areas should be published under the premise of protecting their privacy. In that case, everyone can check whether their historical route includes these dangerous areas. If so, they can go to the medical organizations nearby for further examination.
5.5. Location checking
Each user can use his mobile phones or other 5G-support devices to check the location information published on the permissionless blockchain to check whether they have been to these dangerous areas. More specifically, computes and finds whether all the hashed values appear in the bloom filter . If so, it means should go to the MO nearby for further examination because the published area includes the patient’s recent activity area.
Note that is based on the time state which means and the patient are in the same location at the same time period if all the are in . It is obvious to conclude that the user was in close contact with the patient with a high probability. Therefore, should go to an MO nearby to determine whether they are infected or not.
5.6. Tracing
Note that not all patients are active in executing the location checking operation. In that case, the MC can trace the users who might have been in close contact with the patient and inform them to get a thorough examination. More specifically, like Route Query and Location Publication, the MC finds and for each . Then for each it recovers the user’s pseudonym by executing . Because in the registration operation, each user uses their real identity to register, MC can contact them easily.
Besides, for an MO it uses its address to invoke the contract of route query and location publication, and all the operations will be recorded to the immutable blockchain. During the Registration process, uses the real-world identity to register from MC and obtains . Hence, each address is associated with the corresponding MO’s real-world identity, which means that the misbehavior of MO (e.g., publishing fake location information, abusing the route query operation) can be traced by MC.
6. Theoretical analysis
To show that the proposed PTBM scheme achieves the aforementioned design goals of privacy protection, reliability, authentication, and traceability, here we present a thorough analysis.
6.1. Privacy protection
In the proposed scheme, both the privacy of patients and other users should be protected, which includes identity privacy and route privacy.
6.1.1. Identity privacy
In PTBM, each user will be assigned a pseudonym generated by MC by computing . If the pseudo-random function is secure, the user ’s pseudonym and the corresponding real-world identity is unlinkable without knowing the secret key held by MC.
The patient can be considered as a special kind of user. During the Route Query process, their pseudonym will be used. As mentioned above, the proposed PTBM scheme achieves unlinkability between and . Hence, only the query requester MO knows the real identity of which is inevitable because the MO is responsible for ’s examination and treatment.
For external adversaries, the inference attack cannot be performed because they can only access the permissionless blockchain that only stores the published location information.
Therefore, both honest-and-curious MO and external adversaries cannot infer the real-world identity of both patients and other users, which means the proposed PTBM scheme achieves identity privacy protection.
6.1.2. Route privacy
In the permissioned blockchain, given a pseudonym the encrypted route information can be obtained, where reflects the user ’s location at time . For each state the state dictionary stores the tuple . Assuming represents one of the fog node ’s states, only the corresponding private key and MC’s strong private key can recover the encrypted result. Note that and is encrypted by . The bloom filter only stores an obfuscated location information which consists of several hashed values of users’ pseudonym. If all the hash function are secure, then all the pre-hash value (i.e., the user’s pseudonym) cannot be recovered. In summary, for each state cannot leak the location information for any user.
In the permissionless blockchain, only the bloom filter associated with a patient ’s activity area is published. As mentioned above, external adversaries cannot find which user has been to this area associated with .
Therefore, both honest-and-curious MO and external adversaries cannot recover the exact route of any user which means the proposed PTBM scheme achieves location privacy protection.
6.2. Reliability & authentication
Due to the reliability of blockchain which has been well established in the literature, all the data stored on the permissionless and permissioned blockchain cannot be modified or deleted. Hence, the correctness of query/tracing results on the blockchain can also be guaranteed.
In PTBM, each user is assigned a key-pair for generating digital signatures. For a malicious user, it cannot impersonate another legitimated user to upload the information without knowing the private key. Besides, we use timestamp to resist replay attacks, which means the malicious users cannot use the obsolete request of others. Therefore, PTBM achieves effective user authentication.
6.3. Traceability
As mentioned above, MC can perform route tracing operations of a given pseudonym of a patient or tracing of all the users that might have been in close contact with . Besides, all misbehaviors can be traced by MC with the help of access mechanisms in the permissioned blockchain and registration rules in PTBM scheme. In that case, MC can punish the misbehaving MOs by both economical and administrative mechanisms to regulate their behavior.
7. Performance evaluation
In this section, we evaluate both computation & communication complexity based on a blockchain platform to prove that the proposed PTBM scheme has high computation efficiency with low communication costs.
7.1. Experimental setup
We have implemented the proposed PTBM scheme in the Go language, which includes the implementation of PCSD scheme based on [25]. The security parameter and the number of shared keys in the bloom filter is set to . All the pseudo-random functions and hash functions are instantiated by HMAC-256 and SHA256, respectively. All programs are compiled in Go 1.14 x64 environment.
We choose the Hyperledger Fabric2 as the underlying blockchain platform. Hyperledger Fabric provides permissioned management with flexible programmability & efficiency. Fabric is suitable for our scenario where both permissioned & permissionless blockchains are required, and its high transaction throughput as compared with Bitcoin and Ethereum makes it a practical real-world solution.
We deploy four peer nodes of Fabric as the test blockchain network, where each node is running on a virtualized server on an Intel i7-9700K CPU and 8GB RAM with a 64-bit Ubuntu 16.04 operating system. The client-side programs (by users, fog nodes, and MOs) are executed on a tablet with Intel i5-7300U CPU and 4GB RAM with a 64-bit Windows 10 operating system.
7.2. Computational costs
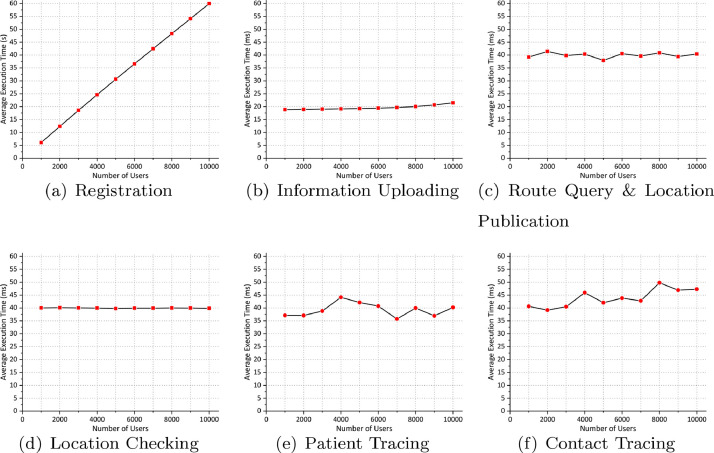
To evaluate the computational performance of PTBM, we set the number of users ranging from 1000 to 10,000 with increments of 1000, the number of fog nodes the number of patients and the number of users that perform location checking operation to . We randomly generate the route of each user, and the patients are also uniformly & randomly selected. All the evaluations are executed 5 times, and we calculate the average execution time for each process to remove relative errors. The results are shown in Fig. 2 .
Fig. 2.
Experimental evaluation of computational costs.
7.2.1. Registration
During the Registration process, each user is assigned as a pseudonym and a signature key-pair each fog node is assigned as a pseudonym and an encryption/decryption key-pair . Assume represents the average execution time of operation the average execution time of Registration is where and represents the number of user and fog node, respectively. Therefore, the corresponding computation complexity is for MC.
Because the number of fog nodes is relatively fixed, we mainly evaluate the time cost by different numbers of users. It can be seen in Fig. 2a, as the number of users increases, the time cost also increases. Note that even if the number of users raises to 10000, it only takes about 1 min for registration. Besides, the registration operation only performs once, and in the real world situation, it will be done immediately when a new user joins.
7.2.2. Information uploading
During the Information Uploading process, the user generates a request which includes pseudonym a timestamp and a signature . Hence for user, it takes to generate in the Information Uploading process, and the corresponding time complexity is . Note that we omit the calculation of negligible time consuming such as generating hash value.
For each the fog node checks the timestamp and verifies the signature. If the checking & verification are successful, ’s state will be updated with the current state of via Update operation of smart contract. Periodically, the state information will be uploaded to the permissioned blockchain which includes several encrypted user’s pseudonym passed by in this period of time, and ’s encrypted pseudonym. Assume the number of users pass by is the time cost in the Information Uploading process for a fog node is and the corresponding time complexity is . However, in the real-world scenario, a fog node can handle the users’ request in parallel, which means the time complexity can be decreased to .
As is illustrated in Fig. 2(b), the execution time is not related to the number of users pass by. We also notice that the execution time slightly increases with the number of users increases. That is because a larger number of users bring out a larger size of state information for node that will be uploaded to the permissioned blockchain, which results in higher communication delay.
7.2.3. Route query & location publication
During the Route Query process, the MO queries the patient ’s route with the help of which only needs one Query operation of smart contract. Hence, the time cost of Route Query for MO is with the corresponding time complexity .
During the Location Publication process, the MO queries the permissioned blockchain to obtain ’s recent activity areas, and uploads the associated bloom filter to the permissionless blockchain. Assume the number of ’s recent activity area is the time cost of Location Publication process for MO is the corresponding time complexity is .
As can be seen in Fig. 2(c), the execution time is not related to the number of users, and it only takes about 40ms to perform the complete route query & location publication process.
7.2.4. Location checking
During the Location Checking process, each user will check the location information published by MO previously. Assume that only one bloom filter is published, and in that case, only executes the Query algorithm once, which is negligible. Hence, the time cost of Location Checking process for user is the corresponding time complexity is also .
As is illustrated in Fig. 2(d), although the number of users increases from 1000 to 10000, the execution time looks almost the same, which proves that the proposed PTBM scheme achieves complexity during this process.
7.2.5. Patient tracing
During the Patient Tracing process, the MC obtains the state information related to ’s recent activity as what the MO does in the Location Publication process. Hence, the time cost of Patient Tracing for MC is with the corresponding time complexity .
As is seen in Fig. 2(e), the execution time is irrelevant to the number of users and ranges from 35ms to 45ms, which is efficient.
7.2.6. Contact tracing
During the Contact tracing process, MC recovers each contact’s pseudonym by executing PCDD.SDec operations for each state obtained by Patient Tracing process. Hence, it takes to recover all the pseudonym for all states, and the corresponding time complexity is .
As is seen in Fig. 2(f), the execution time is irregular, that is because, in our experimental setting, each user’s route is randomly generated which results in random and .
7.3. Communication costs
The communication behavior mainly happens during the Information Uploading, Location Query, Location Publication and Location Checking process. For users, it is obvious that the communication complexity of Information Uploading and Location Checking processes are both because he only sends one request and performs one query operation, respectively. For fog node, the communication complexity is because encrypted pseudonyms will be uploaded to the permissioned blockchain. For MO, it takes communication complexity for both Location Query and Location Publication processes because the information of states will be obtained by querying the permissioned blockchain and uploading on the permissionless blockchain, respectively.
We evaluate the communication cost for users, fog nodes, and MOs in our experiment, as shown in Table 2 , where we set the number of users . It can be observed that the communication costs for users, fog nodes, and MOs are all less than 10KB, which is quite efficient. Therefore, PTBM achieves high communication efficiency and can well save the bandwidth usage and reduce the delay of the 5G-integrated infrastructure.
Table 2.
Communication costs.
| Operation | User | Fog Node | MO |
|---|---|---|---|
| Information Uploading | 1KB | 8.74KB | - |
| Route Query | - | - | 1KB |
| Location Publication | - | - | 5.61KB |
| Location Ckecking | 5.24KB | - | - |
7.4. Summary
Table 3 shows both the time and communication complexity of the proposed PTBM. Through the experimental evaluation, it is observed that the execution time of the most aforementioned processes (except the Registration process that is executed only once) is not related to the number of users. More specifically, it only takes less than 40ms for each of the given operations to complete. Hence, PTBM can operate with high computation efficiency, which means that the fog nodes can handle a large number of user requests. For users and MOs, they can efficiently check the published location and query the location of a given patient, respectively. Besides, MC can quickly trace the information of patient activity or contacts uploaded by fog nodes. Besides, the empowerment of the 5G-integrated and blockchain-based network eliminates the burden of the centralized server compared to existing schemes with centralized architecture with higher communication bandwidth & lower delay.
Table 3.
Time and communication complexity of PRVB.
| Process | Entity | Time Complexity | Communication Complexity |
|---|---|---|---|
| Registration | MC | - | |
| Information Uploading | User | ||
| Fog Node | |||
| Route Query | MO | ||
| Location Publication | MO | ||
| Location Checking | User | ||
| Patient Tracing | MC | - | |
| Contact Tracing | MC | - |
8. Conclusion and future work
Int his work, we propose PTBM, a privacy-preserving patient contact tracing scheme that enables tracing the current route of a patient with infectious diseases (e.g., COVID-19), and location checking of public without violating their identity & location privacy. More specifically, permissionless and permissioned blockchain is used to achieve public location checking and reliable route storage respectively. Bloom filters, PCSD cryptosystem, pseudo-random functions, and hash function also enhance the privacy-preserving property of the proposed scheme. Theoretical analysis and experimental evaluations also show that the proposed PTBM scheme achieves privacy protection, reliability, and traceability with low computation & communication complexity.
For future work, we will consider leveraging this blockchain-based solution for more comprehensive patient management, vaccination protocols, and protected information sharing with the international organizations in a global pandemic scenario. Besides, how to integrate the emerging 5G technology to other relevant medical application that demands high communication reliability and low latency is also a promising research direction.
CRediT authorship contribution statement
Can Zhang: Conceptualization, Methodology, Software, Writing - original draft. Chang Xu: Resources, Investigation, Formal analysis. Kashif Sharif: Writing - review & editing. Liehuang Zhu: Supervision, Funding acquisition.
Declaration of Competing Interest
We declare that we have no conflicts of interest to this work. We do not have any commercial or associative interest that represents a conflict of interest in connection with the work submitted.
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61972037, 61402037, 61872041, U1836212).
Footnotes
References
- 1.Ahad A., Tahir M., Sheikh M.A., Ahmed K.I., Mughees A., Numani A. Technologies trend towards 5g network for smart health-care using iot: a review. Sensors. 2020;20(14):4047. doi: 10.3390/s20144047. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Ahmed N., Michelin R.A., Xue W., Ruj S., Malaney R.A., Kanhere S.S., Seneviratne A., Hu W., Janicke H., Jha S.K. A survey of COVID-19 contact tracing apps. IEEE Access. 2020;8:134577–134601. doi: 10.1109/ACCESS.2020.3010226. [DOI] [Google Scholar]
- 3.G. Apple, How Apple and Google are enabling COVID-19 contact-tracing, 2020, URL https://www.wired.com/story/apple-google-bluetooth-contact-tracing-covid-19/.
- 4.Bera B., Saha S., Das A.K., Kumar N., Lorenz P., Alazab M. Blockchain-envisioned secure data delivery and collection scheme for 5g-based iot-enabled internet of drones environment. IEEE Trans. Veh. Technol. 2020;69(8):9097–9111. doi: 10.1109/TVT.2020.3000576. [DOI] [Google Scholar]
- 5.Bi Q., Wu Y., Mei S., Ye C., Zou X., Zhang Z., Liu X., Wei L., Truelove S.A., Zhang T., Gao W., Cheng C., Tang X., Wu X., Wu Y., Sun B., Huang S., Sun Y., Zhang J., Ma T., Lessler J., Feng T. Epidemiology and transmission of COVID-19 in 391 cases and 1286 of their close contacts in shenzhen, china: a retrospective cohort study. The Lancet Infectious Diseases. 2020 doi: 10.1016/S1473-3099(20)30287-5. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Biswas S., Sharif K., Li F., Mohanty S.P. Blockchain for e-health-care systems: easier said than done. Computer (Long Beach Calif) 2020;53(7):57–67. doi: 10.1109/MC.2020.2989781. [DOI] [Google Scholar]
- 7.Chamola V., Hassija V., Gupta V., Guizani M. A comprehensive review of the COVID-19 pandemic and the role of iot, drones, ai, blockchain, and 5g in managing its impact. IEEE Access. 2020;8:90225–90265. doi: 10.1109/ACCESS.2020.2992341. [DOI] [Google Scholar]
- 8.Chang M.C., Park D. How can blockchain help people in the event of pandemics such as theCOVID-19? J. Medical Systems. 2020;44(5):102. doi: 10.1007/s10916-020-01577-8. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Chowdhury M.Z., Hossan M.T., Shahjalal M., Hasan M.K., Jang Y.M. A new 5g ehealth architecture based on optical camera communication: an overview, prospects, and applications. IEEE Consum. Electron. Mag. 2020:1. [Google Scholar]
- 10.Dagher G.G., Mohler J., Milojkovic M., Marella P.B. Ancile: privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustainable Cities and Society. 2018;39:283–297. doi: 10.1016/j.scs.2018.02.014. [DOI] [Google Scholar]
- 11.Fan K., Ren Y., Wang Y., Li H., Yang Y. Blockchain-based efficient privacy preserving and data sharing scheme of content-centric network in 5g. IET Commun. 2018;12(5):527–532. doi: 10.1049/iet-com.2017.0619. [DOI] [Google Scholar]
- 12.Fitzsimons J.K., Mantri A., Pisarczyk R., Rainforth T., Zhao Z. A note on blind contact tracing at scale with applications to the COVID-19 pandemic. In: Volkamer M., Wressnegger C., editors. ARES 2020: The 15th International Conference on Availability, Reliability and Security, Virtual Event, Ireland, August 25–28, 2020. ACM; 2020. pp. 92:1–92:6. [DOI] [Google Scholar]
- 13.W.E. Forum, 5g outlook series: The impact of mobile technology on the response to COVID-19, 2020, URL http://www3.weforum.org/docs/WEF_Global_Accelerator_Program_5G_Outlook_Report_2020.pdf.
- 14.W.E. Forum, These are the 10 most discussed tech topics during covid-19, 2020, URL https://www.weforum.org/agenda/2020/07/0-top-tech-topics-during-covid-19-india-china-us-eu/.
- 15.Gao J., Agyekum K.O.O., Sifah E.B., Acheampong K.N., Xia Q., Du X., Guizani M., Xia H. A blockchain-sdn-enabled internet of vehicles environment for fog computing and 5g networks. IEEE Internet Things J. 2020;7(5):4278–4291. doi: 10.1109/JIOT.2019.2956241. [DOI] [Google Scholar]
- 16.Gorla P., Vinay C., Vikas H., Neeraj K. Blockchain for 5g: a prelude to future telecommunication. IEEE Netw. 2020;PP(99) [Google Scholar]
- 17.Hewa T., Bracken A., Ylianttila M., Liyanage M. 2020 IEEE International Conference on Communications, ICC 2020, Dublin, Ireland, June 7–11, 2020. IEEE; 2020. Blockchain-based automated certificate revocation for 5g iot; pp. 1–7. [DOI] [Google Scholar]
- 18.IBM, How much would a data breach cost your business?, 2019, URL https://www.ibm.com/security/data-breac.
- 19.Jangirala S., Das A.K., Vasilakos A.V. Designing secure lightweight blockchain-enabled RFID-based authentication protocol for supply chains in 5g mobile edge computing environment. IEEE Trans. Ind. Informatics. 2020;16(11):7081–7093. doi: 10.1109/TII.2019.2942389. [DOI] [Google Scholar]
- 20.Li H., Zhu L., Shen M., Gao F., Tao X., Liu S. Blockchain-based data preservation system for medical data. J. Medical Systems. 2018;42(8):141:1–141:13. doi: 10.1007/s10916-018-0997-3. [DOI] [PubMed] [Google Scholar]
- 21.Li L., Zhang Q., Wang X., Zhang J.J., Wang T., Gao T., Duan W., Tsoi K.K., Wang F. Characterizing the propagation of situational information in social media during COVID-19 epidemic: a case study on weibo. IEEE Trans. Comput. Social Systems. 2020;7(2):556–562. doi: 10.1109/TCSS.2020.2980007. [DOI] [Google Scholar]
- 22.Linoy S., Mahdikhani H., Ray S., Lu R., Stakhanova N., Ghorbani A.A. IEEE International Conference on Blockchain, Blockchain 2019, Atlanta, GA, USA, July 14–17, 2019. IEEE; 2019. Scalable privacy-preserving query processing over ethereum blockchain; pp. 398–404. [DOI] [Google Scholar]
- 23.Liu E., Effiok E.E., Hitchcock J. Survey on health care applications in 5g networks. IET Commun. 2020;14(7):1073–1080. doi: 10.1049/iet-com.2019.0813. [DOI] [Google Scholar]
- 24.Liu J., Li X., Ye L., Zhang H., Du X., Guizani M. IEEE Global Communications Conference, GLOBECOM 2018, Abu Dhabi, United Arab Emirates, December 9–13, 2018. IEEE; 2018. BPDS: A blockchain based privacy-preserving data sharing for electronic medical records; pp. 1–6. [DOI] [Google Scholar]
- 25.Liu X., Qin B., Deng R.H., Lu R., Ma J. A privacy-preserving outsourced functional computation framework across large-scale multiple encrypted domains. IEEE Trans. Computers. 2016;65(12):3567–3579. doi: 10.1109/TC.2016.2543220. [DOI] [Google Scholar]
- 26.Mistry I., Tanwar S., Tyagi S., Kumar N. Blockchain for 5g-enabled iot for industrial automation: a systematic review, solutions, and challenges. Mech Syst Signal Process. 2020;135:106382. doi: 10.1016/j.ymssp.2019.106382. [DOI] [Google Scholar]
- 27.MIT, Bluetooth signals from your smartphone could automate COVID-19 contact tracing while preserving privacy, 2020, URL http://news.mit.edu/2020/bluetooth-covid-19-contact-tracing-0409.
- 28.Nkenyereye L., Tama B.A., Shahzad M.K., Choi Y. Secure and blockchain-based emergency driven message protocol for 5g enabled vehicular edge computing. Sensors. 2020;20(1):154. doi: 10.3390/s20010154. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29.Shen M., Deng Y., Zhu L., Du X., Guizani N. Privacy-preserving image retrieval for medical iot systems: a blockchain-based approach. IEEE Netw. 2019;33(5):27–33. doi: 10.1109/MNET.001.1800503. [DOI] [Google Scholar]
- 30.Tang Q. Privacy-preserving contact tracing: current solutions and open questions. CoRR. 2020;abs/2004.06818 [Google Scholar]
- 31.Wong A.M., Hsu C., Le T., Hsieh M., Lin T. Three-factor fast authentication scheme with time bound and user anonymity for multi-server e-health systems in 5g-based wireless sensor networks. Sensors. 2020;20(9):2511. doi: 10.3390/s20092511. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 32.Xu H., Zhang L., Onireti O., Fang Y., Buchanan W.B., Imran M.A. Beeptrace: blockchain-enabled privacy-preserving contact tracing for COVID-19 pandemic and beyond. CoRR. 2020;abs/2005.10103 doi: 10.1109/JIOT.2020.3025953. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 33.Xu S., Ning J., Li Y., Zhang Y., Xu G., Huang X., Deng R.H. Match in my way: fine-grained bilateral access control for secure cloud-fog computing. IEEE Transactions on Dependable and Secure Computing. 2020 doi: 10.1109/TDSC.2020.3001557. [DOI] [Google Scholar]
- 34.Xu S., Yang G., Mu Y. Revocable attribute-based encryption with decryption key exposure resistance and ciphertext delegation. Inf. Sci. 2019;479:116–134. doi: 10.1016/j.ins.2018.11.031. [DOI] [Google Scholar]
- 35.Xu S., Yang G., Mu Y., Liu X. A secure iot cloud storage system with fine-grained access control and decryption key exposure resistance. Future Gener. Comput. Syst. 2019;97:284–294. doi: 10.1016/j.future.2019.02.051. [DOI] [Google Scholar]
- 36.Xue K., Zhu B., Yang Q., Wei D.S.L., Guizani M. An efficient and robust data aggregation scheme without a trusted authority for smart grid. IEEE Internet Things J. 2020;7(3):1949–1959. doi: 10.1109/JIOT.2019.2961966. [DOI] [Google Scholar]
- 37.Xue Y., Xue K., Gai N., Hong J., Wei D.S.L., Hong P. An attribute-based controlled collaborative access control scheme for public cloud storage. IEEE Trans. Inf. Forensics Secur. 2019;14(11):2927–2942. doi: 10.1109/TIFS.2019.2911166. [DOI] [Google Scholar]
- 38.Zhang C., Zhu L., Xu C., Sharif K., Liu X. PPTDS: A privacy-preserving truth discovery scheme in crowd sensing systems. Inf. Sci. 2019;484:183–196. doi: 10.1016/j.ins.2019.01.068. [DOI] [Google Scholar]
- 39.Zhang C., Zhu L., Xu C., Sharif K., Zhang C., Liu X. PGAS: Privacy-preserving graph encryption for accurate constrained shortest distance queries. Inf. Sci. 2020;506:325–345. doi: 10.1016/j.ins.2019.07.082. [DOI] [Google Scholar]
- 40.Zhang C., Zhu L., Xu C., Zhang C., Sharif K., Wu H., Westermann H. BSFP: blockchain-enabled smart parking with fairness, reliability and privacy protection. IEEE Trans. Veh. Technol. 2020;69(6):6578–6591. doi: 10.1109/TVT.2020.2984621. [DOI] [Google Scholar]
- 41.Zhang K., Zhu Y., Maharjan S., Zhang Y. Edge intelligence and blockchain empowered 5g beyond for the industrial internet of things. IEEE Netw. 2019;33(5):12–19. doi: 10.1109/MNET.001.1800526. [DOI] [Google Scholar]
- 42.Zhaolong N., Peiran D., Xiaojie W., Xiping H., Liang G., Bin H., Yi G., Tie Q., Ricky K. Mobile edge computing enabled 5g health monitoring for internet of medical things: a decentralized game theoretic approach, ieee journal on selected areas in communications, 2020. IEEE J. Sel. Areas Commun. 2020 [Google Scholar]