Abstract
Reliable data exchange and efficient image transfer are currently significant research challenges in health care systems. To incentivize data exchange within the Internet of Things (IoT) framework, we need to ensure data sovereignty by facilitating secure data exchange between trusted parties. The security and reliability of data-sharing infrastructure require a community of trust. Therefore, this paper introduces an encryption frame based on data fragmentation. It also presents a novel, deterministic grey-scale optical encryption scheme based on fundamental mathematics. The objective is to use encryption as the underlying measure to make the data unintelligible while exploiting fragmentation to break down sensitive relationships between attributes. Thus, sensitive data distributed in separate data repositories for decryption and reconstruction using interpolation by knowing polynomial coefficients and personal values from the DBMS Database Management System. Aims also to ensure the secure acquisition of diagnostic images, micrography, and all types of medical imagery based on probabilistic approaches. Visual sharing of confidential medical imageries based on implementing a novel method, where transparencies ≤k − 1 out of n cannot reveal the original image.
Keywords: Visual secret sharing, Confidentiality, Data exchange, Fragmentation, IoT internet of things, Encryption, Cloud computing
Introduction
The exchange of health information enables the electronic transfer of clinical data between different health systems and preserving their importance. Facilitate access and retrieval of clinical data to provide safe, timely, effective, and equitable patient-centred care, the World Health Organization (WHO) digitally-enabled health systems that place people at the centre of digital health, adopt and use digital health technologies [33]. Therefore, this scope requires countries to empower an integrated patient-centred approach. Innovative technologies integrated via IoT for virtual care and remote monitoring, such as smartphones connected to healthcare platforms, will allow data exchange, storage, and acquisition. The objective is to share information throughout the health ecosystem by creating ongoing care to enhance health outcomes. Of paramount importance to achieve innovation in current digitalization is to unfold the full potential data exchange activity between countries, industries, companies, healthcare systems, etc. To incentivize data exchange, we must ensure data sovereignty by facilitating the secure exchange of data between trusted parties.
The Fast Healthcare Interoperability Resources (FHIR) standard, created by Health Level Seven International (HL7), is currently the most widely used set of protocols for merging different healthcare systems. It is also an Application Programming Interface (API) for interoperability and exchanging health information [20]. Substitutable Medical Apps, Reusable Technologies (SMART) integrated with FHIR to enable healthcare applications connection to Electronic Health Record EHR systems with the appropriate safety guarantees and support authorization, authentication, and User Interface UI integration [26]. FHIR profiles assure SMART applications that resource coding of medication, procedures, conditions, laboratory results, or allergies meet data quality compliance requirements [31]. SMART’s integration with FHIR also seeks to restraint significant fragmentation by implementing widely applicable data constraints based on the terms introduced by the US Meaningful Use program [11].
Security and reliability of data-sharing infrastructure require a trusted community; therefore, mutually customized components such as the encryption system are mandatory. Fragmentation is a fundamental cryptographic technique for a data exchange strategy and is also required when COVID-19 deteriorates [6]. This paper proposes distributing fragments to Cloud Repositories (CR) from where the server module will further spread the datasets into separated data repositories. The shares can only be retrieved and reconstruct from the reliable DBMS deployed in the cloud. Thus, this approach improves data privacy and confidentiality during the data exchange process and facilitates the process without further complex encryption techniques. The primary requirement for healthcare innovation is to ensure the confidentiality of the patient’s data, stored in the system, or sharing with reliable external parties. The demand for secure image sharing in the healthcare sector has prompted us to include a virtual plan for sharing secret binary images.
The objectives that guide the development of the architectural model in Fig. 1 are the following:
Personal data must be processed legitimately, confirming judicature to the owner. Therefore, restrictions should apply by the individuals whose personal data processed, such as the terms of usage;
Data acquisition should be secure along with the flow from the initial phase of the development. For instance, from sensors to the backend repository and IoT devices;
Interlinked data, becoming beneficial through semantic interrogations. Thus, linking data should be simple and effective between trusted sites;
Delivering quality digital healthcare services requires the system to be compatible and able to serve multiple operating environments. We aim to implement a system that requires low computational complexity to maintain the advantage of limited calculation time and memory usage;
Government legislation obliges healthcare ecosystems to use secure data management and privacy techniques. The cross-border healthcare data exchange aligned with the country’s bioethics legislation that provides the data;
Since the COVID-19 pandemic, it is a prerequisite for healthcare systems to exchange and share through internet medical records. Thus, the paper aims to provide a novel method for the safe exchange of confidential datasets and medical images.
Fig. 1.
Architecture of the proposed model
Initially, we implement a literature review from various scientific articles and books to study the relevant work in this domain and set our innovative contribution. After that, the paper analyses the proposed model’s architecture, including the VPN’s data flow process. In the same section, we analyze the fragmentation process by applying an example of separating health care data into fragments. Using Newton-Gregory’s divided difference interpolation, we implement reconstruction and retrieve a specific health record from the primary dataset. The prerequisite requirement for medical data exchange is medical image transfer. We dedicate a subsection on image secret sharing framework based on the same theory of k out of n secret sharing, including an example. The last section comprises the conclusion and further discussion for future work and contribution in this domain framework.
Literature review
Limitation to integrate smart services by connecting heterogeneous platform devices through the IoT because they are prone to hardware/software and network attacks and, if not properly secured, can lead to privacy issues. To resolve the problem, S. Sridhar and S. Smys et al. proposed an Intelligent Security Framework for IoT Devices [30]. Snezana S. et al. introduced a novel concept of personal health records based on an e-health strategy where patients own their data using different ways of obtaining data [29]. The article [3] developed a hybrid measurement technique for digital image watermarking using medical images (X-ray, MRA, and CT), an extremely robust method for protecting clinical information. An innovative watermarking scheme based on the biorthogonal family (biorthogonal 2.2, biorthogonal 3.5, and biorthogonal 5.5) wavelet transform [4]. Simultaneously, it used a convolution for eyelets wavelet transform and conflicts wavelet transform to exchange images in the IoT frame. In the paper [2], the authors proposed a watermarking scheme in the structure of Daubechies wavelets, Daubechies-5, and Daubechies-7 wavelet transform. This wavelet approach is highly robust against various attacks, prohibiting the digital data’s piracy and authentication.
Aggarwal et al. have initially proposed the fragmentation cryptographic technique model by dividing the dataset among two data repositories. Although the idea was innovative, the collaboration between the two servers and the restriction of repositories lead to a lack of security and require further encryption to ensure the data’s privacy [21]. After that, Ciriani et al. proposed a model without limitations on the number of datasets partitioning based on improved security frame encryption derived from fragments [15, 18]. In 2009 Ciriani et al. proposed a cryptographic fragmentation model where the data owner manages his reliable DBMS [16, 17]. Following Shamir’s [28] proposal for a secret sharing scheme, Agrawal et al. and Emekci et al. extended the model by dividing and storing data into CRs, which could only be reconstructed by the knowledge of any k of the n shares and the secret value [1]. The model also reveals information by queries without deciphering the essential attributes of the subsets [19]. Sareen et al. contribute to their work by proposing a new model to protect the confidentiality of outsourced data [27].
Naor and Shamir et al. introduced the idea of image secret sharing by distributing an image into several different images, and the reconstruction is done only by aligning the shares [25]. Based on Naor’s and Shamir’s secret sharing scheme, which referred to as black and white images, Verheul and Tilborg et al. extended this framework to coloured photos [32]. The same approach of secret image share without the use of cryptography followed by Chin-Chen Chang et al. as well as Ching-Nung Yang et al. [13, 14, 36]. Bisio, I., Fedeli, A., Lavagetto, F. et al. conducted a numerical study dedicated to evaluating the implementation of a microwave imaging method to detect stroke [9]. I. Bisio, C. Garibotto, A. Grattarola, F. Lavagetto and A. Sciarrone et al. introduced the IoT as the key to I4.0 production optimization [10]. I. Bisio, F. Lavagetto, M. Márchese and A. Sciarrone et al. obtainable a performance assessment among AR approaches based on the accelerometer signal recorded through patients’ smartphones [8].
In the healthcare industry, some limited caregivers vigorously promote innovative technologies. Based on the above research projects, this paper aims to integrate confidentiality into the exchange of healthcare data provided as a text, either as an image. The novel idea generates a state-of-the-art model based on a fundamental mathematical approach that could be the key to ensuring the digitization of an ecosystem framework for virtual medical therapy and remote treatment. The goal is health data exchange architectures, application interfaces that allow data to be accessed and shared securely and adequately across the spectrum of care, in all applicable settings, and with relevant stakeholders.
Proposed model
For prosperous and interoperable data sharing, we proposed the development of data spaces where everyone accepted. Still, the entry should be secure, the management system will identify who uses the system, and all trusted sites will align with the regulations. Figure 1 is a visual presentation of the proposed approach. The raw data generated by sensors applied to users or the data provided by doctors, hospitals, laboratories, etc., will be distributed in fragments based on the owners’ requirements and the regulation of restriction concerning the level of confidentiality. In terms of data holder requirements, the distribution unit increases or decreases privacy level to distribute sections to multiple servers and maintain security. Thus, a commitment from the SLA Service Level Agreement will establish appropriate service and confidentiality levels by cloud storage service providers. After that, dataset fragments are distributed in separate cloud data repositories. The original dataset can be reconstructed only from the DBMS and provide data strictly only to certified users.
Interpretation
Figure 1 shows the end user’s gateway server is connected to VPG Virtual Private Gateway in VPC Virtual Private Cloud to establish a VPN Virtual Private Network connection [24]. This scheme provides a connection via a private IP address. It allows the exchange of VPCs in different areas in a public cloud that can connect multiple VPCs within a public cloud for communication without the Internet connection [23]. We propose constraining constraints that will be the rule for distribution among the attributes as agreed through SLA regarding the data owner requirements. If A is a set of users’ attributes and c is a set of confidentiality constraints, then c will be a subset of A, c ⊆ A and each constraint cannot be a subset of another constraint [22]. A constraint is defined as the restriction for combining sensitive attributes within the same fragment [5]. The Singleton pattern’s deployment will ensure that a dataset has only one acute attribute instance and provides a global access point [7]. The distribution module will manage sharing datasets into separated CR concerning user requirements regarding which attributes agreed in SLA to be together. After that, each CR server module will further distribute the encrypted datasets into cloud repositories. The reconstruction phase will follow the VPN path through the reliable DBMS, which will compute each share, recover, and present the data to the end-users.
Mathematical approach
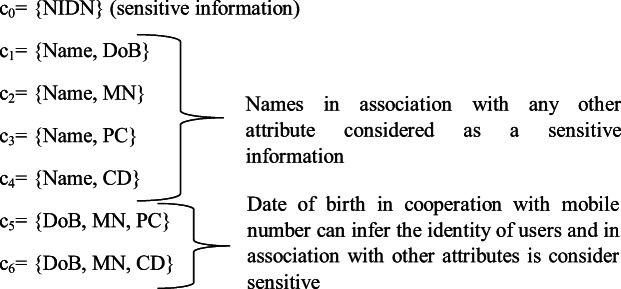
Let A be the set of attributes a1, a2, …, an which the provider requires to distribute among CR and C the set of confidential constraints c1, c2, …, cn where ci ⊂ A. Constraints separated into singleton where unique sensitive attributes are alone in a set and subset of constraints where the attributes within cannot merge with others. The attributes fragmentation will be applied in the distribution unit by an algorithm based on the decision tree approach. It will calculate the minimum fragmentation that satisfies all confidence-building correlation constraints [18]. Singleton constraints will be distributed from the same unit by a (k. n) threshold scheme approach in such a way that the knowledge of any k ≤ n sensitive attribute values and the knowledge of the secret xi, i ∈ 1, 2…, n stored in DBMS can retrieve the information, but no group of k − 1 or fewer can do so even with the knowledge of xi. By k − 1 coefficients we mean the set of {a0, a1, …, ak − 1} constants which derives from a0 the National Identity Number (NIDN) and the respective divided differences as . Therefore, if we want to distribute the information into k fragments, then we choose (k − 1) randomly coefficients and we let the constant value a0 be the sensitive value of NIDN, thus creating a (k − 1) degree polynomial as follow:
According to the above, the DBMS stores the secret information x = (x1, x2, …, xn), whereby the knowledge of polynomial coefficients and the substitution of xi, (the large of i, corresponds to the number of shares) can compute the encrypted values of NIDN National Identity Number from P(xi), i = 1, 2, …, k, and thus by just substituting k of the n values from the vector x. Through Newton-Gregory’s divided difference interpolation and by the knowledge of k order pairs (xi, P(xi)), i = 1, 2, …, k we can determine the (k − 1) coefficients of the polynomial as well as the original value of NIDN corresponding to the constant a0 as follow:
Where will be the 1st, 2nd and (n − k − 1)th divided differences, respectively.
Paradigm
Let A be the set of patients’ attributes that includes the following information to be distributed among CR:
A = {National Identity Number (NIDN), Name, Date of Birth (DoB), Mobile Number (MN), Postal Code (PC), Chronic Disease (CD)}
By fragmentation, we mean the distribution of attributes so that their associated values are separated and linked only to the encryption key. An example of fragmenting the attributes involved in the constraints so that they are not visible together could be f1 = {Name}, f2 = {DoB, MN} and f3 = {PC, CD}. Fragments are stored in three separate CR CR1, CR2, and CR3, respectively. We will develop a second-degree polynomial to share the data among CRs as follow:
Where a0 represents the NIDN and the coefficients a1 = (1,2,5,6,4) and a2 = (7,3,2,1,9) randomly selected. Also, the secret values of xi, i = 1, 2, 3 are randomly selected and correspond to each SP respectively, let x1 = 1, x2 = 2, x3 = 4. Tables 1, 2, 3, 4 and 5 presents the computational results of substitution for each polynomial of the coefficients and the secret values.
Table 1.
Registered data
| NIDN | Name | DoB | MN | PC | CD |
|---|---|---|---|---|---|
| 880,618 | Andrew | 26/03/1984 | 96,536,499 | 4529 | Cancer |
| 526,548 | Nicolas | 12/05/1968 | 99,652,342 | 2324 | Diabetes |
| 616,636 | Jane | 13/07/1975 | 96,521,548 | 2528 | Heart disease |
| 844,131 | David | 25/04/1983 | 99,215,482 | 4528 | Asthma |
| 321,131 | Mathew | 01/09/1950 | 99,992,272 | 5232 | Epilepsy |
Table 2.
Substitution results
| NIDN | Polynomial | x = 1 | x = 2 | x = 4 |
|---|---|---|---|---|
| P(x) | CR1 | CR2 | CR3 | |
| 880,618 | 1 × 2 + 7x + 880,618 | 880,626 | 880,636 | 880,662 |
| 526,548 | 2 × 2 + 3x + 526,548 | 526,553 | 526,562 | 526,592 |
| 616,636 | 5 × 2 + 2x + 616,636 | 616,643 | 616,660 | 616,724 |
| 844,131 | 6 × 2 + 1x + 844,131 | 844,138 | 844,157 | 844,231 |
| 321,131 | 4 × 2 + 9x + 321,131 | 321,144 | 321,165 | 321,231 |
Table 3.
Data of CR1
| NIDN | Name |
|---|---|
| 880,626 | Andrew |
| 526,553 | Nicolas |
| 616,643 | Jane |
| 844,138 | David |
| 321,144 | Mathew |
Table 4.
Data of CR2
| NIDN | DoB | MN |
|---|---|---|
| 880,636 | 26/03/1984 | 96,536,499 |
| 526,562 | 12/05/1968 | 99,652,342 |
| 616,660 | 13/07/1975 | 96,521,548 |
| 844,157 | 25/04/1983 | 99,215,482 |
| 321,165 | 01/09/1950 | 99,992,272 |
Table 5.
Data of CR3
| NIDN | PC | CD |
|---|---|---|
| 880,662 | 4529 | Cancer |
| 526,592 | 2324 | Diabetes |
| 616,724 | 2528 | Heart disease |
| 844,231 | 4528 | Asthma |
| 321,231 | 5232 | Epilepsy |
The fragments will distribute as shown within the following tables, presenting an incorrect value of NIDN for each data from Table 2:
Reconstruction implementation can only be done by the knowledge of the three ordered pairs {(xi, P(xi)), i = 1, 2, 3} corresponding to the three CRs which kept stored in DBMS. The decryption implemented using Newton-Gregory’s divided difference interpolation, as shown in Table 6, which will reconstruct the polynomial and reveal the original value of NIDN as the constant part of it a0 [27].
Table 6.
Newton-Gregory’s divided difference interpolation
| i | xi | P(xi) | ||
|---|---|---|---|---|
| 1 | 1 | 880,626 | ||
| 2 | 2 | 880,636 | ||
| 3 | 4 | 880,662 |
The calculations resulting from Table 6 shown below:
After computing the constant value a0 that reveals the initial NIDN number. As shown in Table 7, we can retrieve any information from the patient’s record.
Table 7.
Reconstructed table
| NIDN | Name | DoB | MN | PC | CD |
|---|---|---|---|---|---|
| 880,618 | Andrew | 26/03/1984 | 96,536,499 | 4529 | Cancer |
Image exchange
A visual secret sharing scheme is a method of sharing intimate images among a group of stakeholders. Each participant gets a piece of the secret image, called a share. The allowed coalition of the participators can reveal the original image by accumulating their shares. However, any subsets of the alliance cannot retrieve the secret image by amassing their shares. For instance, if we called each share, transparency, the secret is visible in a (k, n) visual cryptography scheme if ≥ k transparencies stack together.
Nevertheless, none can see the original image if <k transparencies are stacked together. Transmitting and sharing information in a healthcare system requires medical image sharing (e.g., MRI images). Thus, we propose a secure fragmentation scheme for image exchange in the same concept of k out of n secret sharing. We have incorporated a visual secret sharing scheme to encode an image required to be secure in “shadow” embodiments called shares. The secret can be visually reconstructed only when k or more shares are available. Each pixel of the secret image is “expanded” into m sub-pixels in each share, and in the reconstruction process, the stacking of the sub-pixels is a Boolean ‘OR’ operation.
Implementation
The method requires distributing the image’s pixels in n modified versions and sharing them among n cloud repositories through VPN. Each fragment is a collection of m subpixels. It is essential for logic disciplines, including cryptography, to use a fundamental rule named Richard Hamming and Hamming Weight. The determination comes from the count of ‘1’ within a binary number. For instance, the Hamming Weight for 101,001 is 3, and 1,110,011 is 5. Hence the architecture is represented by n × m Boolean matrix A = [Aij], where aij = 1 if the jth subpixel in the ith share is black; otherwise, it is 0, represented by white. Grey-scale on images revealed using the Hamming weight defined as the amount of ‘1’ from the ‘OR’ operation on matrix A [34]. More specifically, B = OR(i1, i2, …, ir) where i1, i2, …, ir are the rows of matrix A and H(B) is the Hamming weight. C0 and C1 are defined as the n × m Boolean matrices that can compute the k out of n secret sharing. White and black pixel corresponds to the two matrices respectively, which specify the m-subpixels’ colour among the n shares in n repositories. The requirements for a calculation to be considered valid are the following:
For any A ⊆ C0 the B0 among k out of the n rows satisfies H(B0) ≤ l, l ∈ ℤ+
For any A ⊆ C1 the B1 among k out of the n rows satisfies H(B1) ≤ h, l ∈ ℤ+, l < h ≤ m
For any {i1, i2, …, iq} ⊆ {i1, i2, …, in}, q < k the q × m matrices Dt, t ∈ {0, 1} derive by restricting each Ct to rows i1, i2, …, iq cannot be distinguished
The definition of contrast, which is the combination of the Hamming Weight difference between white and black pixels in a share, could be calculated as follows:
Let P0 and P1 be the probability of white and black pixel appearing in a white and black area respectively, and let Pth ∈ [0, 1] be a threshold probability. If P0 ≥ Pth and P1 ≤ Pth − a where a ≥ 0 is the contrast as defined above, then the frequency of white pixels in a white area of the recovered image will be higher than in a black area. E0 and E1 are white and black sets respectively with nλ and nγ (n × 1, matrices). The reconstruction probability is valid if the following conditions are met [35]:
The ‘OR’ operation of any n × 1 matrix is H(B)
If P0 and P1 are the probabilities of white (white = 0) appearing in the sets λ and γ respectively, then we have the satisfaction of P0 ≥ Pth and P1 ≤ Pth − a
For any {i1, i2, …, iq} ⊆ {i1, i2, …, in}, q < k, P0 = P1
The probabilities P0 and P1 are calculated as follow:
Let Gi = A0 ∘ … ∘ A0A1 ∘ … ∘ A1, i = 0, …, g − 1, where g ≥ 2 collections of Gi matrices develop a secret sharing scheme for g grey-levels with pixel expansion defined by mg. Reconstruction applied with a(1, 0), …, a(g − 1, g − 2) representing contrast and {di}, i = 0, …, g − 2 the threshold sets for n × mg, Gi matrices if the following two conditions met:
H(Bi) ≤ di − a(i + 1, i), where for Gi + 1 the Hamming weight for the ‘OR’ operation of any k of n rows results that H(Bi + 1) ≥ di
For any {r1, r2, …, rj} ⊆ {1, …, k}, 1 ≤ j < k, the matrices obtained by restricting to rows r1, r2, …, rj are equal up to a column permutation.
The following equation calculates contrast:
If ai is the amount of ‘1’ in Gi and bi the amount of ‘0’ then ai = H(Bi) = l × (g − i − 1) + h × i and bi = mg − ai = (m − l) × (g − i − 1) + (m − h) × i ⟹ ai + bi = m × (g − 1) = mg [12].
After that, we select s = 1, …, mg random columns from Gi matrices and obtain the n × s matrices . The average Hamming weight of the ith grey-level reconstructed pixel is and defined as the probabilistic of the Hamming weight of the ‘OR’ operation of any k rows, which is j = 0, …, s. The average grey-level and average contrast, respectively, are calculated as follow:
Thus, the grey level i = 0, 1, …, g − 1 is constructed by the Gi|s, p matrices respectively, where and the set can be used to construct a grey-scale probabilistic visual secret sharing scheme.
Paradigm
Let and be the two fundamental Boolean matrices for a black and white pixel respectively the ‘OR’ operation (the operator ‘OR’ gives 1 as a result if at least one of the two elements is 1) of the elements in any two rows of A0 gives as a result of two zeros, thus h = 2 and respectively for the same reason from A1 derives l = 1. Therefore, we assume that the contrast of results, which is also known as the relative difference between the black and white pixel reconstruction, is .
From the definition of E0 and E1 we have and and as mentioned λ and γ calculated by the ‘OR’ operation of the column vectors, so and . Thus, the appearance probabilities of white colour are , and the threshold probability , since the contrast was the second condition was met. The last requirement referring to the equality of the two probabilities fulfilled as for all the shadows λ = {H([0]), H([0]), H([1])} = {0, 0, 1} and γ = {H([1]), H([0]), H([0])} = {1, 0, 0}, γ = {H([0]), H([1]), H([0])} = {0, 1, 0} and γ = {H([0]), H([0]), H([1])} = {0, 0, 1} for shadows 1,2 and 3 respectively, so .
The pixel expansion is mg = (g − 1) × m = 6 and the contrasts computed as ,
The ‘OR’ operation of the q1th row and the q2th row of the set are j ∈ {0, 1, 2, 3, 4, 5}. The data included in the first row of Table 8 calculated as follow:
Table 8.
Values of average grey-levels of probabilistic scheme
| j = 0 | j = 1 | j = 2 | j = 3 | j = 4 | j = 5 | ||
|---|---|---|---|---|---|---|---|
| I = 1 | 0 | 1/3 | 2/3 | 0 | 0 | 0 | 1/3 |
| I = 2 | 0 | 0 | 1/2 | 1/2 | 0 | 0 | 1/2 |
| I = 3 | 0 | 0 | 0 | 2/3 | 1/3 | 0 | 2/3 |
Table 9 contains data of and in which s = 1, 2, 3, 4, 5, 6 and i = 1, 2, 3 from where derives that .
Table 9.
Data for ps,j and es
| j = 0 | j = 1 | j = 2 | j = 3 | j = 4 | j = 5 | j = 6 | ||
|---|---|---|---|---|---|---|---|---|
|
For i = 1, 2, 3 |
||||||||
| 2/3 | 1/3 | – | – | – | – | – | 1/3 | |
| 6/15 | 8/15 | 1/15 | – | – | – | – | 1/3 | |
| 1/5 | 3/5 | 1/5 | 0 | – | – | – | 1/3 | |
| 1/15 | 8/15 | 6/15 | 0 | 0 | – | – | 1/3 | |
| 0 | 1/3 | 2/3 | 0 | 0 | 0 | – | 1/3 | |
| 0 | 0 | 1 | 0 | 0 | 0 | 0 | 1/3 | |
| 1/2 | 1/2 | – | – | – | – | – | 1/2 | |
| 3/15 | 9/15 | 3/15 | – | – | – | – | 1/2 | |
| 1/20 | 9/20 | 9/20 | 1/20 | – | – | – | 1/2 | |
| 0 | 1/5 | 3/5 | 1/5 | 0 | – | – | 1/2 | |
| 0 | 0 | 1/2 | 1/2 | 0 | 0 | – | 1/2 | |
| 0 | 0 | 0 | 1 | 0 | 0 | 0 | 1/2 | |
| 1/3 | 2/3 | – | – | – | – | – | 2/3 | |
| 1/15 | 8/15 | 6/15 | – | – | – | – | 2/3 | |
| 0 | 1/5 | 3/5 | 1/5 | – | – | – | 2/3 | |
| 0 | 0 | 6/15 | 8/15 | 1/15 | – | – | 2/3 | |
| 0 | 0 | 0 | 2/3 | 1/3 | 0 | – | 2/3 | |
| 0 | 0 | 0 | 0 | 1 | 0 | 0 | 2/3 |
Conclusions & future work
Sharing data over the cloud requires confidentiality, privacy, control, and compliance with laws and regulations. Thus, our approach suggested a framework that presents secure encryption of data stored in cloud repositories. Encryption based on an innovative data set fragmentation technique uses CRs through VPN to distribute data to separate sensitive data securely. In the future, we introduce a mathematical approach to Newton-Gregory interpolation to retrieve and reconstruct original data. A detailed example using random data explains the fragmentation data distribution and then the reconstruction application to retrieve a specific record. Fragmentation further improves current data encryption approaches by reducing the burden of high computing on the server. As shown, it can effectively apply to images to avoid cryptographic calculations and be used to transfer confidential images through the cloud. Therefore, we have proposed a binary secret sharing solution for grayscale images to be used in healthcare for a completely secure data exchange framework.
Integrating edge computing with cloud computing requires an efficient and secure data exchange during data flow and secure cloud repositories. Also, big data growth increases the obligations to secure information from data breaches and leakages of information. Therefore, we aim to continue contributing to data privacy mechanisms on big data to protect healthcare data exchange and storage confidentiality in future work. The data-rich environments resulting from cloud computing’s radical innovation in collaboration with ML Machine Learning and AI Artificial Intelligence require advanced encryption and security techniques with a low computational load. A cypher approach that satisfies the fundamental security properties of image could be used in conjunction with fragment images for further data exchange safety.
Acknowledgements
The research work presented in this article was partially supported by the project entitled ‘Smart and Health Ageing through People Engaging in supporting Systems’ with acronym SHAPES, which has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 857159. Undertaken by the SPHINX project through the European Union’s Horizon 2020 Research and Innovation Programme (Digital Society, Trust & Cyber Security E-Health, Well-Being and Ageing) under grant agreement 826183. It is also part of the Ambient Assisted Living (AAL) project vINCI: “Clinically-validated INtegrated Support for Assistive Care and Lifestyle Improvement: The Human Link” funded by Research & Innovation Foundation in Cyprus under the AAL framework with Grant Nr. vINCI /P2P/AAL/0217/0016.
We sincerely thank anonymous reviewers for critically reading the manuscript and suggesting substantial improvements, which helped us significantly improve our paper’s presentation and research work quality.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Andreou Andreas, Email: andreou.andreas@unic.ac.cy.
Constandinos X. Mavromoustakis, Email: mavromoustakis.c@unic.ac.cy
George Mastorakis, Email: gmastorakis@hmu.gr.
Dinh-Thuan Do, Email: dodinhthuan@iuh.edu.vn.
Jordi Mongay Batalla, Email: jordi.mongay.batalla@pw.edu.pl.
Evangelos Pallis, Email: pallis@hmu.gr.
Evangelos K. Markakis, Email: markakis@pasiphae.eu
References
- 1.Agrawal D, Abbadi AE, Emekci F, Metwally A (2009) Database management as a service: challenges and opportunities, in 2009 IEEE 25th International Conference on Data Engineering, Shanghai
- 2.Alshayea T, Mavromoustakis C, Mastorakis G, Batalla JM, Markakis E, Pallis E (2018) On the Efficiency evaluation of a novel scheme based on daubechies wavelet for watermarking in 5G,” in 2018 IEEE 23rd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Barcelona
- 3.Alshayeh T, Mavromoustakis C, Batalla JM, Mastorakis G (Dec. 2019) A hybridized measurement methodology for different wavelet transformations targeting medical images in internet of things (IoT) infrastructures. Measurement 148(106813)
- 4.Alshayeh T, Mavromoustakis C, Batalla JM, Mastorakis G, Mukherjee M, Chatzimisios P (2019) Efficiency-aware watermarking using different wavelet families for the internet of things, in 2019 IEEE International Conference on Communications (ICC), Shanghai
- 5.Anderson S, Revesz P (2007) CDB-PV: a constraint database-based program Verifier, in International Symposium on Abstraction, Reformulation, and Approximation
- 6.Andreas A, Mavromoustakis C, Mastorakis G, Mumtaz S, Batalla JM, Pallis E. IEEE international workshop on computer aided modeling and Design of Communication Links and Networks (CAMAD) 2020. Modified machine learning Techique for curve fitting on regression models for COVID-19 projections. [Google Scholar]
- 7.Barták R (2007) Generating implied boolean constraints via singleton consistency, in International Symposium on Abstraction, Reformulation, and Approximation
- 8.Bisio I, Lavagetto F, Márchese M, Sciarrone A (2014) Comparison of situation awareness algorithms for remote health monitoring with smartphones, in 2014 IEEE Global Communications Conference, Austin
- 9.Bisio I, Fedeli A, Lavagetto F, Pastorino M, Randazzo A, Sciarrone A, Tavanti E. A numerical study concerning brain stroke detection by microwave imaging systems. Multimed Tools Appl. 2017;77:9341–9363. doi: 10.1007/s11042-017-4867-7. [DOI] [Google Scholar]
- 10.Bisio I, Garibotto C, Grattarola A, Lavagetto F, Sciarrone A. Exploiting context-aware capabilities over the internet of things for industry 4.0 applications. IEEE Netw. 2018;32(3):101–107. doi: 10.1109/MNET.2018.1700355. [DOI] [Google Scholar]
- 11.Blumenthal D, Tavenner M. The “meaningful use” regulation for electronic health records. N Engl J Med. 2010;363:501–504. doi: 10.1056/NEJMp1006114. [DOI] [PubMed] [Google Scholar]
- 12.Blundo C, Santis AD, Naor M. Visual cryptography for grey level images. Inf Process Lett. 2000;75(6):255–259. doi: 10.1016/S0020-0190(00)00108-3. [DOI] [Google Scholar]
- 13.Chang C-C, Yu T-X (2002) Sharing a secret gray image in multiple images, in First International Symposium on Cyber Worlds, Tokyo, Japan
- 14.Chang C-C, Tsai C-S, Chen T-S (2000) A new scheme for sharing secret color images in computer network, in Seventh International Conference on Parallel and Distributed Systems, Iwate, Japan
- 15.Ciriani V, Vimercati SDCd, Foresti S, Jajodia S, Paraboschi S, Samarati P (2007) Fragmentation and encryption to enforce privacy in data storage, in 12th European Symposium On Research In Computer Security
- 16.Ciriani V, Vimercati SDCd, Foresti S, Jajodia S, Paraboschi S, Samarati P (2009) Keep a few: outsourcing data while maintaining confidentiality, in European Symposium on Research in Computer Security
- 17.Ciriani V, Vimercati SDCd, Foresti S, Jajodia S, Paraboschi S, Samarati P(2009) Enforcing confidentiality constraints on sensitive databases with lightweight trusted clients, in IFIP Annual Conference on Data and Applications Security and Privacy
- 18.Ciriani V, Vimercati SDCD, Foresti S, Jajodia S, Paraboschi S, Samarati P. Combining fragmentation and encryption to protect privacy in data storage. ACM Trans Inf Syst Secur. 2010;13(3):1–33. doi: 10.1145/1805974.1805978. [DOI] [Google Scholar]
- 19.Emekci F, Methwally A, Agrawal D, Abbadi AE. Dividing secrets to secure data outsourcing. Inf Sci. 2014;263:198–210. doi: 10.1016/j.ins.2013.10.006. [DOI] [Google Scholar]
- 20.“enovacom,” Enovacom Canada Inc., [Online]. Available: https://www.enovacom.com/interoperability/fhir-what-are-the-challenges-to-adoption/.
- 21.Gagan A, Mayank B, Prasanna G, Hector GM, Krishnaram K, Rajeev M, Utkarsh S, Dilys T, Ying X (2005) Two can keep a secret: a distributed architecture for secure database services, in The Second Biennial Conference on Innovative Data Systems Research (CIDR 2005), Asilomar, California
- 22.Le DN, Seth B, Dalal S. A hybrid approach of secret sharing with fragmentation and encryption in cloud environment for securing outsourced medical database: a revolutionary approach. J Cyber Secur Mobility. 2018;7(4):379–408. doi: 10.13052/jcsm2245-1439.742. [DOI] [Google Scholar]
- 23.Leng C, Yu H, Wang J, Huang J. Securing personal health Records in the Cloud by enforcing sticky policies. TELKOMNIKA. 2013;11(4):2200–2208. doi: 10.11591/telkomnika.v11i4.2406. [DOI] [Google Scholar]
- 24.Mavromoustakis C, Batalla JM, Mastorakis G, Markakis E, Pallis E. Socially oriented edge computing for energy awareness in IoT architectures. IEEE Commun Mag. 2018;56(7):139–145. doi: 10.1109/MCOM.2018.1700600. [DOI] [Google Scholar]
- 25.Naor M, Shamir A. Visual cryptography. Advances in Cryptology, EUROCRYPT. 1994;950:1–12. [Google Scholar]
- 26.Odisho A, Lui H, Yerramsetty R, Bautista F, Gleason N, Martin E, Young J, Blum M, Neinstein A (2020) Design and development of referrals automation, a SMART on FHIR solution to improve patient access to specialty care. JAMIA Open 3(3):405–412 [DOI] [PMC free article] [PubMed]
- 27.Sareen S, Sood S, Gupta SK. Towards the design of a secure data outsourcing using fragmentation and secret sharing scheme. Inform Secur J A Global Perspective. 2016;25(1–3):39–53. doi: 10.1080/19393555.2015.1134732. [DOI] [Google Scholar]
- 28.Shamir A (Nov 1979) How to share a secret. Commun ACM 22(11)
- 29.Snezana S, Kilintzis V, Jakimovski B, Jolevski I, Beredimas N, Mourouzis A, Corbev I, Chouvarda I, Maglaveras N, Trajkovik V (2020) Cloud based personal health records data exchange in the age of IoT: The Cross4all Project,” in Machine Learning and Applications. ICT Innovations 2020. Communications in Computer and Information Science, vol. 1316, Springer, Cham, pp. 28–41.
- 30.Sridhar S, Smys S (2017) Intelligent security framework for iot devices cryptography based end-to-end security architecture, in International Conference on Inventive Systems and Control , Coimbatore
- 31.Stoldt J-P, Weber J (2020) Safety Improvement for SMART on FHIR Apps with Data Quality by Contract,” in IEEE International Conference on Software Architecture Companion , Salvador, Brazil
- 32.Verheul E, Tilborg H. Constructions and properties of k out of n visual secret sharing schemes. Des Codes Crypt. 1997;11:179–196. doi: 10.1023/A:1008280705142. [DOI] [Google Scholar]
- 33.WH Organization, 2020-2024. [Online]. Available: https://www.who.int/docs/default-source/documents/gs4dhdaa2a9f352b0445bafbc79ca799dce4d.pdf?sfvrsn=f112ede5_42.
- 34.Wang D, Yi F, Li X. Probabilistic visual secret sharing schemes for grey-scale images and color images. Inf Sci. 2011;181(11):2189–2208. doi: 10.1016/j.ins.2011.01.019. [DOI] [Google Scholar]
- 35.Yang C-N. New visual secret sharing schemes using probabilistic method. Pattern Recogn Lett. 2004;25(4):481–494. doi: 10.1016/j.patrec.2003.12.011. [DOI] [Google Scholar]
- 36.Yang C-N, Laih C-S. New colored visual secret sharing schemes. Des Codes Crypt. 2000;20:325–336. doi: 10.1023/A:1008382327051. [DOI] [Google Scholar]