Abstract
In recent times, security in cloud computing has become a significant part in healthcare services specifically in medical data storage and disease prediction. A large volume of data are produced in the healthcare environment day by day due to the development in the medical devices. Thus, cloud computing technology is utilised for storing, processing, and handling these large volumes of data in a highly secured manner from various attacks. This paper focuses on disease classification by utilising image processing with secured cloud computing environment using an extended zigzag image encryption scheme possessing a greater tolerance to different data attacks. Secondly, a fuzzy convolutional neural network (FCNN) algorithm is proposed for effective classification of images. The decrypted images are used for classification of cancer levels with different layers of training. After classification, the results are transferred to the concern doctors and patients for further treatment process. Here, the experimental process is carried out by utilising the standard dataset. The results from the experiment concluded that the proposed algorithm shows better performance than the other existing algorithms and can be effectively utilised for the medical image diagnosis.
1. Introduction
The development in the medical field and the advancement of medical devices such as magnetic resonance imaging (MRI) and computed topography (CT) produces huge data on daily basis, and the data collected from these devices are high dimensional and rich in variables [1]. Thus, the medical image databases and their dimensionality are increasing tremendously. Due to this increase in medical databases, it is difficult to handle the file system with increasing data volume. Thus, handling of medical data turns into a biggest concern for healthcare service providers [2]. Hence, cloud computing was utilised in the medical field for storing and computing the medical data since the medical image cloud is easy to handle. Cloud computing offers flexible and scalable computing resources from the distant locations, and they are accessible depending on the necessity of the user [3]. It is also efficient for delivering computing resources in the high end-computing environment [4]. For cloud computing, the users do not need their own storage and servers at their computers because the cloud platform is utilised for data storage. Hence, the users will be free from having large storage and huge number of servers in their computers [5]. Therefore, computing and storage of long-term medical image records in the cloud are efficient for solving many problems in the medical field [6]. So cloud computing is widely used in the medical field for storing, computing, and sharing the patients' medical records. In cloud computing, the hospital only needs to collect the information about the patients from the files and transfer the data to the cloud for storage.
Moreover, Internet of Things (IoT) is also extended in cloud computing for developing new facilities and applications in the healthcare process [7]. IoT is defined as the network of things or objects such as sensors, software, and electronic devices interconnected with each other for exchanging data with the operator, manufacturer, or other connected devices to attain greater values and services. Also, IoT offers advanced connectivity among the systems, services, and devices which includes various domains, protocols, and applications. IoT and cloud computing are profited equally while combining the technologies. The IoT technology always supports the cloud for enhancing the performance such as computational ability, energy, storage, and high resource utilization. Also, it favours the cloud to provide many new services through a distributed and active approach.
While storing medical data in the cloud platform, it is necessary to safeguard the information so that the cloud cannot learn anything about the data. Thus, securing the medical images in cloud platform is necessary. Generally, medical images are highly sensitive to modifications, and thus, any alterations in their contents can cause errors in medical diagnosis [8]. Hence, it is also important to maintain the sensitive contents of medical images during a reconstruction phase. Thus, an encryption algorithm is required for increasing the security and privacy of data which secures the medical data without leaking any sensitive information. Many encryption algorithms are proposed based on chaotic systems like 1D and 2D chaotic systems, but these chaotic systems with low dimensions only contain simple orbits and lesser parameters. Thus, the initial values and parameters can be easily estimated from the image [9]. To minimise these limitations, chaotic system based on backpropagation (BP) neural network is utilised for the image encryption process which effectively secures the medical data in the cloud environment.
For medical image analysis and disease diagnosis, machine learning technique is extensively used in the medical field [10]. It has many functions such as pattern recognition, disease prediction, fraud detection, and image segmentation [11]. However, the conventional machine learning techniques are not adequate for the large medical databases. Thus, high performance computing was employed in machine learning data for accurate and efficient diagnosis of big medical data. A division of machine learning process is the deep learning which depends on learning data illustrations for feature classification, and it utilises supervised and unsupervised machine learning methods. It is an advanced technique which has the ability to discriminate features of data without human intervention. It has an ability to consequentially produce robust and representative features layer by layer in neural networks [12]. Data used for deep learning are obtained from different sources with precise data types, and it is significant to develop suitable models for handling data analysis. The typical modelling of data analysis includes clustering model, classification model, neural network model, and other efficient models. Neural network is considered as a vital element in deep learning, which replicates biological systems for communication node distribution and information processing. Deep learning process consists of various types such as recurrent neural network (RNN), restricted Boltzmann machine (RBM), autoencoder (AE), multilayer perceptron (MLP), and convolutional neural network (CNN) [13–16].
The storage, handling, and processing are challenging for large sized medical images, and thus, high performance processors are required for medical image processing [17]. Hence, CNN is utilised in the medical field for processing large volume of medical data. CNN is a feed-forward neural network which helps in the modelling of sequential data. It also helps to easily predict and classify the disease and aids in decision-making during disease diagnosis by utilising various approaches. Thus, it assists the clinicians to detect and characterize the important features in large image series. Convolutional neural networks are utilised for different computer applications such as superresolution, medical image classification, and sematic segmentation [18]. They are also used for detecting the objects from satellite image and for implementing many real-time applications [19]. Convolutional neural network effectively learns the local and global features from the image dataset, so it is widely employed in the image classification process. CNN utilises the supervised learning techniques, and thus, it gives better classification results than the unsupervised techniques like RBM neural networks [20].
Convolutional neural networks enable accurate and robust big data feature learning. They utilise many samples for extracting meaningful information from data. Yet, the data may be ambiguous because of inadequate information or complexity of the data source which is known as data ambiguity. Instead, the fuzzy logic is the effective tool for modelling human thinking and perception. It offers the mathematical model for processing ambiguous data by executing numerical computations using linguistic labels and fuzzy set degrees of membership, but the fuzzy systems lack learning ability and the fuzzy rules are determined by the human experts. Thus, the fuzzy system is combined with neural networks so that the fuzzy rules can be derived from a large source of training data by automatically learning the membership functions. Hence, fuzzy convolutional neural network is proposed by integrating fuzzy logic and convolutional neural networks. It utilises the advantages of both fuzzy logic and CNN for accurate and robust classification of data.
This paper is formulated as follows: the literature survey related to the article is explained in Section 2. The architecture of the proposed system is described in Section 3. In Section 4, the proposed methodology regarding the secured cloud storage and medical image processing is explained. Section 5 gives the experimental results for the proposed system. Finally, Section 6 illustrates the conclusion and future works.
2. Literature Survey
Due to the momentary advancement in the healthcare services, there is a rapid growth in medical data. The healthcare services in medical field involve diagnosing the diseases, treatment, injury, disease prevention, and treating other mental or physical injuries in patients. The quality of these healthcare sectors lies in the problem detection efficiency and allocation of medical resources which require application and collection and management of medical data [21]. Previously, many organisations used manual records about the patients organized in the form of reports [22], but for large number of datasets, a modern technology is required in data analysis and management. Hence, cloud computing technology and IoT have been introduced in the medical field for effectively handling, storing, processing, and transferring the medical information of patients. Cloud computing is a smooth and dynamic process which offers a reasonable strategy for handling medical data [23], whereas Internet of Things provides interconnectivity among the devices, applications, data, objects, and sensors which highly influence the data transmission process in medical field. Thus, IoT provides continuous communication and interaction between the sensors and devices in the cloud computing environment. Now, many organisations have initiated to utilise the IoT and cloud computing technology due to its convenience in their operations [24]. Also, cloud computing and IoT are utilised by pharmaceutical and medical research organisations whose applications can have great impact for the welfare of society.
The developments in the medical technology made the storage of medical data in cloud become more convenient. The medical images contain much significant information about patients, and thus, the secure transmission of data and secure storage is important. Hence, for the security of the data, the encryption and the decryption algorithm has been utilised. The chaotic system is extensively applied in the encryption process as it provides better results for randomness and sensitivity of parameter and initial values [25]. Many investigations have been conducted by utilising chaotic system in encryption algorithms. Zhou et al. [26] suggested 1D chaotic system for the encryption process, and Cao et al. [27] offered 2D chaotic system for the encryption process. These are low-dimensional chaotic system with simple orbits and few parameters, and thus, the initial values and parameters can be estimated easily. Gupta and Silakari [28] suggested an image encryption algorithm by utilising 3D cat map. Then, Huang and Nien [29] analysed about the colour image encryption process by utilising 3D chaotic system. Also, Wu et al. [30] proposed the 6D hyperchaotic algorithm for colour image encryption. However, these algorithms have less safety factors including low differential attraction, larger correlation coefficients, and smaller key space. Thus, for improving the safety features of the image encryption algorithm, the backpropagation (BP) neural network- and chaotic system-based encryption algorithm was proposed for the image encryption process.
The progressions in the data storage capabilities, computational resources, hardware design, and safety procedures have increased the necessity of medical data. The medical data undergo processing for effective analysis of diseases using data processing techniques. The medical data processing includes classification, segmentation, and abnormality prediction by utilising the images produced from the medical devices. For large volume of medical data, an efficient data processing technique is required for collecting the valuable insights from datasets. Deep learning [31, 32] is a part of machine learning which has the ability to classify the data based on feature learning without manual interference. It is the widely applied machine learning technique [33] which can produce robust and representative features automatically [34, 35]. It is especially suitable for analysing large dataset and also utilised in speech analysis, computer vision, natural language processing (NLP), scene classification [36], and face recognition [37]. Many investigations have been conducted on image classification by utilising deep learning algorithms like convolutional neural networks and stacked autoencoder (SAE) [30].
Among the deep learning methods, the convolutional neural network provides better classification accuracy with most powerful architecture [38]. CNN is a deep learning process used for solving complex classification problems [12]. It improves the computational performance and precision rate for large datasets. Also, it automatically extracts the feature maps in association with training data. During the classification process, the model is pretrained with related and sufficient data through which the feature description of the model is assigned. Thus, the model begins with the pattern which is related to the task rather than starting from certain random values. Still, the learning process needs training dataset related to testing dataset because the CNN cannot perform efficiently without relevant data [39]. Thus, the convolutional neural networks are combined with fuzzy logic system to form fuzzy convolutional neural network for modelling nonlinear functions. This fuzzy convolutional neural network improves the effect of function approximation. Generally, the convolutional neural networks utilise the fully connected neural networks for analysing the information from feature maps. Here, the convolutional neural network is integrated with the fuzzy logic system instead of fully connected neural network to increase the ability to estimate ideal hypothesis.
3. System Architecture
The conceptual structure of the proposed system comprises the following phases. At the initial phase, the necessary datasets such as query images and medical images are collected for image processing. The collected medical image datasets are then transferred to cloud subsystem using IoT and are stored into cloud database. Before transmission, these medical images undergo the encryption process to eliminate the security threats. This encryption process is carried out using BP neural network and chaotic system. After encryption, the medical will be transferred to the cloud platform where disease diagnosis takes place. The diagnosing process in the medical images is carried out using the proposed algorithm called fuzzy convolutional neural network algorithm which classifies the processed images into normal and disease affected. The classification results from the cloud are transferred to the doctors or experts in context of person's health by IoT. The architecture of the proposed system is displayed in Figure 1.
Figure 1.
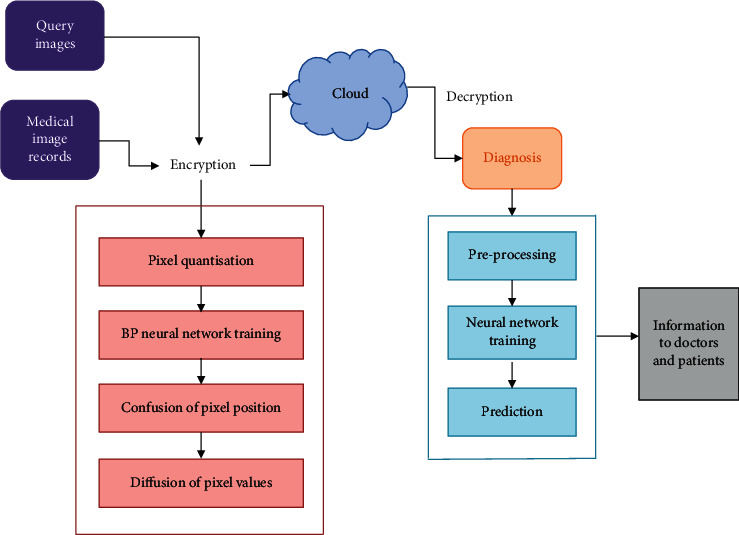
System architecture.
4. Proposed Methodology
4.1. Secured Cloud Data Storage and Transmission Using IoT
The medical images are generally distributed to various organisations for accurate analysis of diseases. Thus, medical data sharing is necessary for improving the quality of healthcare services. The connectivity made through the Internet by IoT devices and the development in the cloud computing technologies made the users to utilise accessible and distributed cloud computing platforms. Here, the medical images are stored in the cloud where the image classification for disease diagnosis takes place. It classifies the images into normal and abnormal images, and the results are then transferred to the doctors and patients using IoT devices. IoT-based medical image transmission is given in Figure 2.
Figure 2.
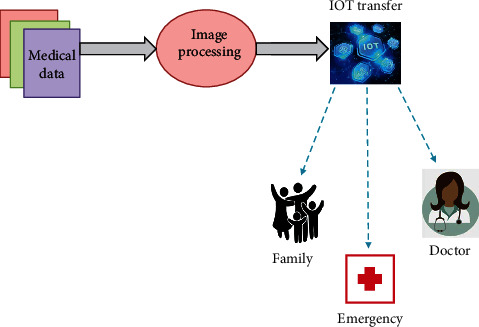
IoT-based medical image transmission.
In cloud computing, the medical datasets are stored in the third party service provider which concerns the privacy of the user. Due to this privacy-related problems, the application of cloud sharing platforms is limited in the medical field. For secured data storage on cloud database, BP neural network- and chaotic system-based encryption algorithm is proposed in this system.
4.1.1. Medical Image Encryption
The reason for implementing an encryption-decryption system is privacy. As information travels over the Internet, it is necessary to examine the access from unauthorized organisations or individuals. Hence, the data are encrypted to reduce data loss and theft. Encryption is the process in which the information is converted into secret code for concealing the actual information. The encryption and decryption processes are collectively called as cryptography. The algorithm utilised for encoding and decoding data is known as ciphers or encryption algorithms, while the unencrypted data are called plaintext and the encrypted data are known as ciphertext. The encryption process converts the plaintext into alternate form called ciphertext. The variable known as a key is required for decrypting the encrypted images. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Encryption is commonly used to protect data in transit and data at rest. Encryption has been a longstanding way for sensitive information to be protected. In modern times, encryption is used to protect data stored on computers and storage devices, as well as data in transit over networks. The time and difficulty in guessing the information is what makes encryption such a valuable security tool.
(1) Preprocessing. For preprocessing, the input image of size P × Q is used. The image size P × Q is disintegrated into H subimage blocks, and each block is given as m × m. For accelerating the convergence of network training, it is necessary to normalise the generated subimage blocks. Here, mean distribution pretreatment is used for normalising the grayscale image range which is given as [Xmax, Xmin], and the transformation domain is given as [Ymax − Ymin]. The pixel value for processing is assumed as Xvalue and Yvalue which is obtained as given in the following equation:
| (1) |
By equation (1), the pixel values of the plain image are distributed from [0, 1] through which the preprocessing of training samples takes place.
(2) Image Compression. After preprocessing, image compression takes place in the medical images by employing the BP neural network. During compression, the image data samples are given as the input. The number of hidden nodes in the network is denoted as ut, and the number of nodes in input layer is denoted as ui. The compression rate of BP neural network is denoted as t, and the association among them is given as follows:
| (2) |
During neural network training, the network coupling weight remains unaltered during the compression process. Thus, the newff function is employed for generating a trainable feed-forward network. The compression image is obtained by utilising newff function for training. The transfer functions are calculated as follows:
| (3) |
| (4) |
(3) Image Scrambling Using Extended Zigzag Confusion. The extended zigzag confusion algorithm is utilised for image encryption which scrambles the BP neural network trained image data. It is an extended form of zigzag confusion which is designed for eliminating the drawbacks in zigzag confusion. The scrambling process in zigzag confusion begins with the upper left corner of the matrix. During zigzag confusion, some values in particular positions are not altered even after scrambling for numerous times, and thus, it can be cracked easily. Also, the zigzag transformation is only suitable for square matrix and not suitable for nonsquare matrix. Hence, extended zigzag confusion is used which overcomes the limitations in regular zigzag confusion. In extended zigzag confusion, the scrambling process can begin from any of the four corners which are chosen by the random number created in the chaotic system. The extended zigzag confusion is also suitable for nonsquare matrix. Figure 3 shows the zigzag confusion for square matrix and the extended zigzag confusion for nonsquare matrix.
Figure 3.
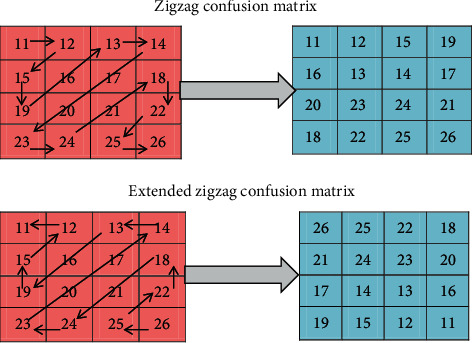
Zigzag confusion matrix and extended zigzag confusion for nonsquare matrix.
For extended zigzag confusion, set the initial values and parameters of fractional-order chaotic system and then iterate the chaotic system (m + P × Q) times. For improving the sensitivity of initial values and parameters in chaotic system, the initial m values are discarded and three chaotic series are obtained. By combining these three series, two pseudorandom series R1 and R2 are formed. These series R1 and R2 are utilised for diffusing pixel values. Equations (5) and (6) give the xor diffusion algorithm.
Positive algorithm:
| (5) |
Reverse algorithm:
| (6) |
where E is denoted as ciphertext, which is a one-dimensional vector; R is denoted as the password vector; and Q is denoted as an expanded form of confusion image. Based on equations (5) and (6), the ciphertext vector E is formed which is the recovered pixel matrix. From the above equations, the encrypted image is attained.
4.1.2. Medical Image Decryption
Generally, the data are encrypted to make it difficult for someone to steal the information. The conversion of encrypted data into its original form is called decryption. It is generally a reverse process of encryption which recovers the original image from the encrypted image. It transforms the data that has been rendered unreadable through encryption back to its unencrypted form. Thus, it decodes the encrypted information so that an authorized user can only decrypt the data because decryption requires a secret key or password. If a decryption passcode or key is not available, special software may be needed to decrypt the data using algorithms to crack the decryption and make the data readable. In decryption, the system extracts and converts the corrupted data and transforms it to texts and images that are easily understandable not only by the reader but also by the system. Decryption may be accomplished manually or automatically. It may also be performed with a set of keys or passwords. Decryption is taking encoded or encrypted text or other data and converting it back into text user or the computer can read and understand.
The decryption algorithm comprises inversing the pixel value diffusion, inversing the pixel position confusion, and reconstructing the BP neural network algorithm. For the decryption process, the encrypted image is given as input. Then, the inverse vectors S1 and S2 are obtained, and the inverse diffusion algorithms are expressed in equations (7) and (8).
Positive inverse algorithm:
| (7) |
Reverse inverse algorithm:
| (8) |
Then, using the extended inverse zigzag algorithm, the scrambled pixels are recovered. The pixel values quantization and the pixel blocks are retrieved, and the vectors also retrieved into subimage blocks. Finally, the decrypted image is formed by combining every subimage. Algorithm 1 illustrates the encryption and decryption processes in medical images.
Algorithm 1.
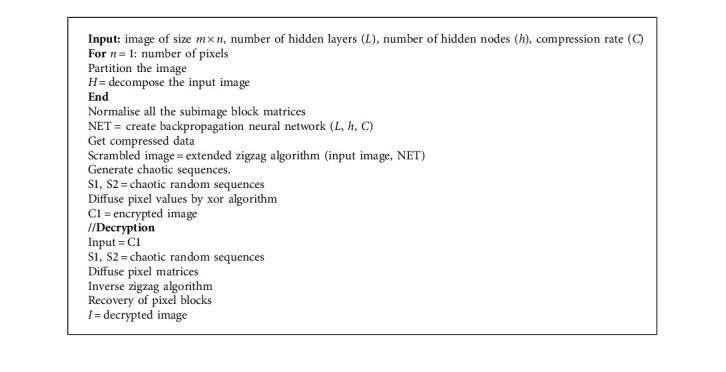
Medical image encryption and decryption.
4.2. Medical Image Processing
Medical image processing plays a major role in the diagnosis of diseases and makes the treatment process more efficient. The medical image processing in this system is carried out using the fuzzy convolutional neural network. The medical images are generally collected as high dimensional type. Due to this high dimensional data, the functioning of the learning process in the fuzzy CNN can be weakened. Hence, before the implementation of fuzzy CNN, there is a requirement for dimensionality reduction and segmentation for improving classification performance.
4.2.1. Improved Principal Component Analysis (IPCA)
Dimensionality reduction is very efficient for processing high dimensional images. The principal component analysis (PCA) is widely utilised for decreasing the dimensions of the original data. It utilises the linear transformation to create a simplified dataset while preserving the important features of original dataset. During principal component analysis, the output variables of eigenvectors are exposed through a variance and it has a huge impact in the analysis. This drawback in the analysis is improved using improved principal component analysis (IPCA). The IPCA requires lesser training time, and it experiences a smooth dimension reduction process.
(1) Covariance Matrix Formation. In covariance matrix formation, Xn is assumed as training vector and it is given as Xn=[x1, x2,…,xn]T. The method for improved principal component analysis is illustrated as follows:
| (9) |
where the sample size is denoted as n, dimension number is denoted as m, and the normalization value of xsv is expressed as xsv′. In this process, there is no loss in information and the correlation matrix does not have any difference. The covariance Co matrix is formed as follows:
| (10) |
(2) Calculation of Eigenvalue. For decomposing the covariance matrix Co, the eigenvalue is calculated. It is expressed as
| (11) |
where the eigenvalue is denoted as μy and the rank of matrix is considered as y. The subeigen values of the vector in the orthogonal basis of [E1, E2,…, Ey] is given as Ey. The diagonal of matrix (μ1, μ2,…, μy) is given as Δ, and we have μ1 > μ2 > ,…, μy.
(3) Principal Components Calculation. After setting up the covariance matrix Co and normalization, the original vector Mn is shifted to the uncorrelated vector zn, which is illustrated as
| (12) |
Cumulative contribution rate αn consists of information proportion of the initial n principal components. Also, the threshold value of αn is taken as 85% for collecting necessary information. The contribution rate αs and cumulated contribution rate αn are determined from the following equations:
| (13) |
| (14) |
After estimating the accurate value of n, the principal component of Ps sample is determined as follows:
| (15) |
where (u=1,2,…, q).
4.2.2. Image Segmentation Based on K-Means Clustering
Image segmentation is utilised efficiently in many medical imaging practices such as recognising the tumour in brain and determining the size of the tumour and its response to the treatment. Having good segmentation process will help the clinicians and patients as they present necessary information for 3D visualization, surgical planning, and disease detection. K-means clustering is the widely utilised method for image segmentation. It is an unsupervised learning algorithm which has relatively low computational complexity. Also, it is the simplest clustering method which divides a set of data into precise number of clusters. Generally, K-means algorithm identifies the number of clusters (K) in the particular regions of images, and thus, it is suitable for medical image segmentation [40].
K-means clustering is the data partitioning algorithm, where n observations are iteratively assigned to exactly one of the k clusters defined by centroids, where k is selected before the initiation of the algorithm. Here, C={c1, c2,…, ck} is given as the set of m cluster centres and Y={y1, y2, y3,…, ym} is given as the set of n data points. These n data points will be clustered into m cluster centres. The objective function of K-means clustering algorithm is given as
| (16) |
where yi is the ith data point and cj is the jth cluster centre. By minimising the objective function, the optimal centres can be attained. The initial cluster centre greatly influences the K-means clustering results. Thus, the cluster centres must be selected delicately. Algorithm 2 illustrates the process of K-means clustering algorithm.
Algorithm 2.
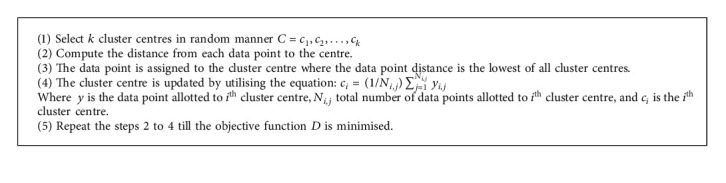
K-means clustering.
4.2.3. Computational Complexity Analysis
The most relevant way to measure the complexity of an algorithm is in terms of how much time it takes to run (space, i.e., memory, can also be used as the basis for a complexity measure, but time is usually the more useful measure). For a complexity measure to reflect the intrinsic nature of the algorithm, it should summarize performance on all problem instances, and it should not reflect inconsequential implementation details.
Computational complexity is the method of measuring the complexity of the algorithm especially the running time of the algorithm. The space (memory) occupied by the algorithm can also be used for calculating the computational complexity, but time is generally more efficient than space. For reflecting the intrinsic nature of the algorithm, the complexity measure must summarize the performance on all problematic cases, and it must never reflect the insignificant implementation factors. The computational complexity of K-means clustering algorithm according to Algorithm 3 is illustrated.
(i) Input: n denotes the number of clusters, Maxt denotes the maximum number of iterations, yi,j denotes the data point allotted to ith cluster centre, Ni,j denotes the total no. of data points allotted to ith cluster centre, and Ci is the ith cluster centre.
(ii) Ensure: best cluster centre: O(Maxt × n).
(iii) Initialization: O(1).
(iv) Randomly select cluster centres k, C=c1, c2,…, ck: O(1).
(v) Calculate the distance to each centre.
(vi) Assign the data point to the cluster centre, whose distance from the data point is least of all cluster centres.
(vii) Objective function evaluation, Ci=(1/Ni,j)∑j=1Ni,jyi,j: O(n).
(viii) Update the location of cluster centre: O(Maxt × n).
(ix) Repeat steps 3 to 6 until the objective function D is minimised.
(x) Iteration counterincrement: O(Maxt).
Algorithm 3.
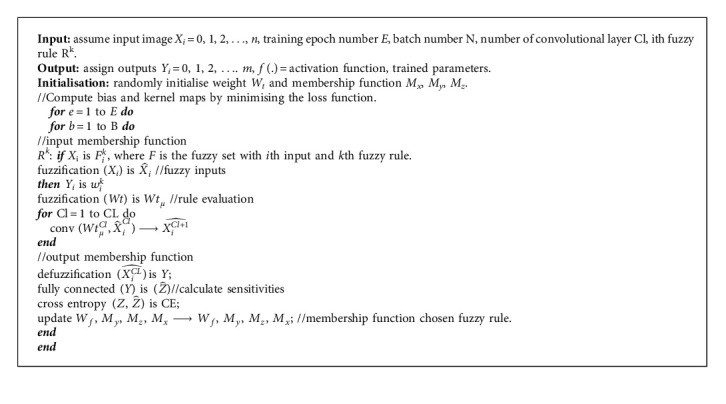
Fuzzy convolutional neural network algorithm.
4.2.4. Fuzzy Convolutional Neural Network (FCNN)
The image processing is complex in medical images because it has high resolution images. Thus, an effective classification algorithm like fuzzy convolutional neural network algorithm is utilised for medical image classification. The FCNN algorithm utilises both neural and fuzzy systems for the classification process. The information collected through CNN and fuzzy is merged together for creating the entire system for classification. In FCNN, fuzzy minimises the uncertainties and the neural network reduces the noises in the original data. The structure of FCNN is presented in Figure 4.
Figure 4.
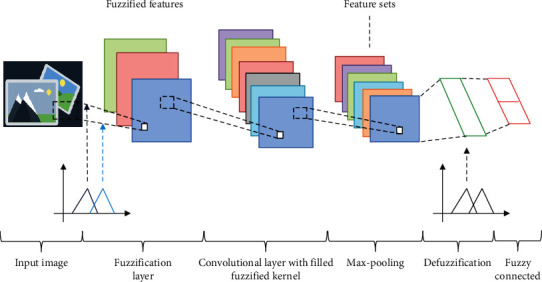
Structure of fuzzy convolutional neural network.
The structure of the proposed FCNN consists of convolutional layer and fully connected layer. The convolutional layer undergoes three stages such as convolution stage, nonlinearity stage, and pooling stage. At the initial stage, the input data undergo processing in the fuzzification layer for creating the fuzzy logic representation. Accordingly, the fuzzy representation is convoluted in the fuzzy convolutional stage which contains fuzzified convolution kernels. Fuzzy convolution is the min-max composition of fuzzified kernels which obtain higher level fuzzy features from its input spatial features. During the defuzzification layer, the crisp values are produced from the features obtained by pooling. In the final stage, a fully connected layer functions as an output classifier of FCNN.
To perform fuzzy inference, fuzzy rule is needed to be generated. For a multi-input method, every input is graded with each fuzzy set for its degree of membership. Next, inputs xi, i=1,2,…, n and outputs yj=1,2,…, m are assigned and the kth fuzzy rule Rk is generated as follows:
| (17) |
where Fik is denoted as the fuzzy set with ith input and kth fuzzy rule. Based on membership functions, multiple linguistic labels are assigned for each element in input matrix. The input node membership to a certain fuzzy set is described as grade which is calculated by the fuzzy membership function. The fuzzy set () is illustrated as
| (18) |
where the centre of input fuzzy membership function is denoted as Mx and the input matrix is denoted as Xi.
The processing phases in the fuzzy convolutional layer include fuzzy convolutional phase, nonlinearity phase, and pooling phase. In the fuzzy convolutional phase, the fuzzy convolutional filter Wtμ is applied to the original data, which is given as
| (19) |
The fuzzy convolutional filter Wtμ is calculated as follows with Wt as the original convolution filter:
| (20) |
Equation (21) gives the nonlinear transformation of gained output from the fuzzy convolutional phase. The final phase in the fuzzy convolutional neural network is the max pooling phase. By this phase, the size of the input may be reduced in the next fuzzy convolution layer:
| (21) |
In the convolution phase, the activation function is denoted as f(.). The fully connected phase of fuzzy convolutional neural network works as a classifier with input features. By the process of defuzzification with centre of gravity, the crisp value yi is calculated, which is illustrated as
| (22) |
where My denotes the centre of the defuzzification membership function. The output of the FCNN is represented as which is given as
| (23) |
In the fully connected layer, the weight matrix is denoted as Wf. For evaluating the output error, cross entropy is utilised. Equation (24) illustrates the estimation of cross entropy function:
| (24) |
where the output of the classifier is given as , target is given as z, and the number of samples is denoted as N. The model parameters are trained using cross entropy loss function. Equation (25) gives the weight update:
| (25) |
Equation (26) gives the updated defuzzification membership function, where the centres are denoted as My(k), the learning rate is denoted as δMy:
| (26) |
Equation (27) gives the updated fuzzification membership function with centre value as Mz and learning rate as δMz:
| (27) |
Equation (28) gives the updated fuzzification membership function with centre value as Mx and learning rate as δMx:
| (28) |
Algorithm 3 summarizes the process of the fuzzy convolutional neural network algorithm.
5. Experimental Evaluation
5.1. Dataset Descriptions
The image classification is an important task in the proposed system which classifies the image dataset into normal dataset and disease affected dataset. Here, the experiments are performed on medical datasets for evaluating the proposed algorithm using parameters like specificity, sensitivity, and accuracy. Besides, the other existing algorithms like decision tree (DT), Naïve Bayes (NB), K-nearest neighbour (KNN), and artificial neural network (ANN) are also compared with the proposed algorithm for analysing the efficiency of the proposed algorithm. For evaluating the effect of preprocessing techniques on classification of medical images, two different types of datasets acquired through noninvasive modalities like MRI are utilised. The datasets comprise BRATS images [41] and Brain MRI [42]. They are utilised for training, testing, and validation of the proposed algorithm. Table 1 gives the description of the datasets utilised for classification.
Table 1.
Dataset description.
| Dataset | BRATS images | Brain cancer |
|---|---|---|
| Imaging modality | MRI | MRI |
| Total images | 469 | 81,325 |
| Number of patients | 300 | 49 |
5.2. Classification Results
5.2.1. Parameter Settings
The parameter settings of proposed algorithm and the comparative algorithms for classification are presented in Table 2. Here, 75% datasets are utilised for training the classifier and 25% datasets are utilised for testing the classifier. The proposed approach is implemented in Matlab platform.
Table 2.
Parameter settings.
| Algorithm | Parameters | Values |
|---|---|---|
| KNN | Number of neighbours | 5 |
| Distance function | Euclidean distance | |
| (N × D) training data | N, no. of samples; D, dimensionality of each data point | |
| (M × D) testing data | M, no. of data points | |
| NB | Model | Gaussian base distribution |
| N | Size of data | |
| DT | Splitting criterion | Gini |
| Minimum instances per leaf | 2 | |
| ANN | Size of input layer | Size of data |
| Type of ANN | Feed-forward | |
| Number of neurons | 20 | |
| Training and testing set | 75% of training and 25% of testing set | |
| FCNN | Input | 56 × 28 |
| Fuzzification | 2 × (input)-Gaussian MF | |
| In and out channel range | 1 to 100 | |
| Stride and padding | 1 & 0 | |
| Conv3x d | 2 × (in & out channels, kernel size = (3 × 128), stride & padding), ReLU, Max_Pooling (55 × 1) | |
| Conv4x d | 2 × (in & out channels, kernel size = (4 × 128), stride & padding), ReLU, Max_Pooling (54 × 1) | |
| Conv5x d | 2 × (in & out channels, kernel size = (5 × 128), stride & padding), ReLU, Max_Pooling (53 × 1) | |
| Defuzzification | 2 × 128 |
5.2.2. Evaluation Parameters
The parameters like specificity, accuracy, sensitivity, and F-measure are considered in the evaluation process. The evaluation parameters are determined using the number of true positive (TP), number of false positive (FP), number of true negative (TN), and number of false negative (FP). The specificity, accuracy, and sensitivity are illustrated as follows:
| (29) |
| (30) |
| (31) |
In true positive (TP), the right values will be predicted as the correct value. In true negative (TN), the right values will be predicted as the wrong value. In false positive (FP), the false values will be predicted as the right value, and in false negative (FN), the false value will be predicted as the wrong value.
Figure 5 illustrates the analysis of specificity among the proposed algorithm and other existing algorithms such as KNN, NB, DT, and ANN. The analysis is conducted for five different sets of images such as 5000, 10000, 15000, 20000, and 25000. It shows that the specificity is high for the proposed algorithm than the other existing algorithms like KNN, NB, DT, and ANN.
Figure 5.
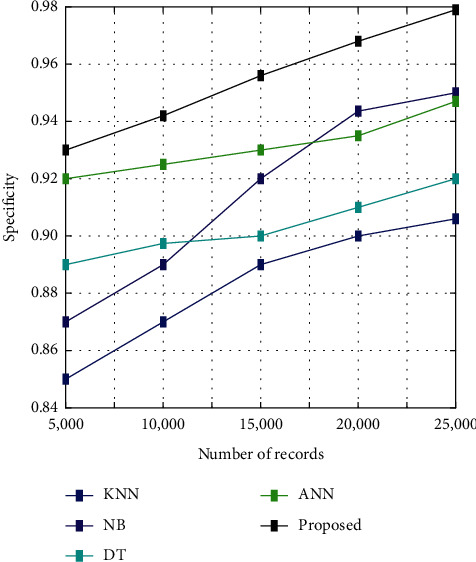
Specificity analysis.
Figure 6 illustrates the analysis of sensitivity among the proposed algorithm and other existing algorithms such as KNN, NB, DT, and ANN. The analysis is conducted for five different sets of images such as 5000, 10000, 15000, 20000, and 25000. It shows that the sensitivity is high for the proposed algorithm than the other existing algorithms like KNN, NB, DT, and ANN.
Figure 6.
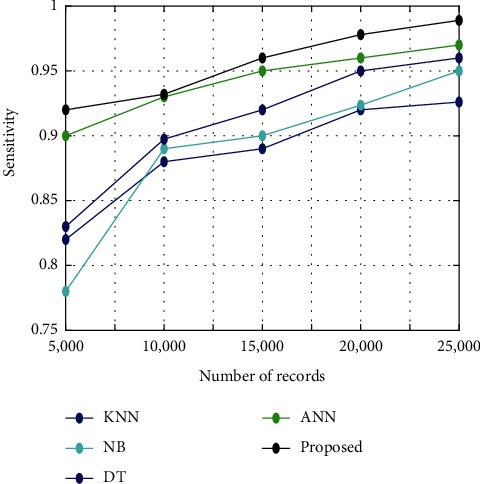
Sensitivity analysis.
Figure 7 illustrates the classification accuracy among the proposed algorithm and other existing algorithms such as KNN, NB, DT, and ANN. The analysis is conducted for five different sets of images such as 5000, 10000, 15000, 20000, and 25000. It shows that the accuracy is high for the proposed algorithm than the other existing algorithms like KNN, NB, DT, and ANN.
Figure 7.
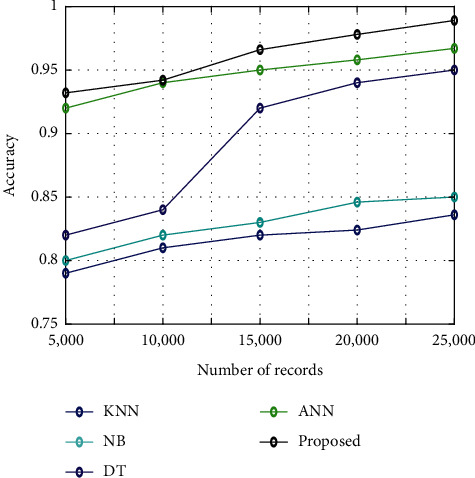
Classification accuracy.
F-measure is utilised for measuring the effectiveness of the classification process. If the F-measure value is high, the predicting potential of classification process will be high. The F-measure is evaluated from the mean values of recall and precision. The recall is measured by the ratio of true positive values to the sum of true positive and false negative values. Instead, the precision is measured by the ratio of true positive values to the sum of true positive and false positive values. The F-measure based on precision and recall is expressed as
| (32) |
Figure 8 illustrates the analysis of F-measure among the proposed algorithm and other existing algorithms like KNN, NB, DT, and ANN. The analysis is conducted for five different sets of images such as 5000, 10000, 15000, 20000, and 25000. It shows that the F-measure is high for the proposed algorithm than the other existing algorithms like KNN, NB, DT, and ANN.
Figure 8.
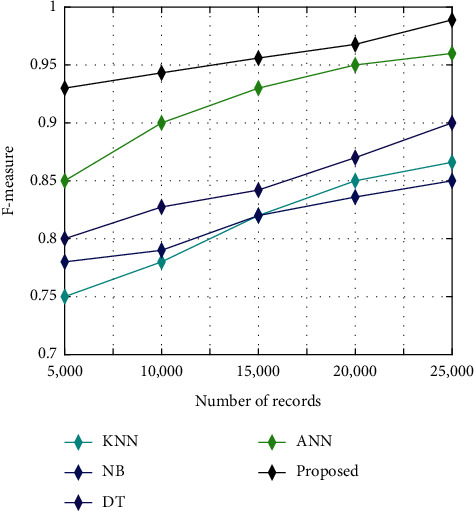
F-measure analysis.
The comparison results are given for the classification methods mentioned above. From the results, it is known that the proposed approach has superior performance over other classification methods. Particularly, the proposed approach has been able to attain better accuracy compared to other techniques like KNN, NB, DT, and ANN, respectively. In case of specificity, the proposed approach has competently acquired the higher value as compared to KNN, NB, DT, and ANN. Similarly, the proposed approach yielded better value for sensitivity and F-measure, which is comparatively higher than other classification methods. Hence, it is concluded that, for medical image classification, the proposed model is highly efficient.
5.2.3. Computation Time for Classification
Table 3 displays the computation time between the proposed fuzzy convolutional neural network algorithm and other existing algorithms like KNN, NB, ANN, and DT. It displays that the computation time is greater for the proposed algorithm than the other existing algorithms like KNN, NB, DT, and ANN.
Table 3.
Computation time.
| Techniques | Time (sec) |
|---|---|
| KNN | 150.012 |
| NB | 178.329 |
| DT | 140.000 |
| ANN | 60.001 |
| Proposed | 54.091 |
5.2.4. Statistical Analysis
The statistical analysis was performed for analysing the improvement in the performance of the proposed algorithms than the other existing algorithms. It analyses classification problems such as the error rates and classification accuracy. Many tests were conducted for this statistical analysis which includes post hoc test, Dunnett test, Tukey test, Friedman test, and ANOVA test. For concluding whether there is any statistical difference among the proposed algorithm and other compared algorithms, a one-way analysis of variance (ANOVA) test has been conducted which analyses the statistical correctness of the proposed algorithms over other existing algorithms. It comprises mean and variance for determining the test statistic. The test statistic is then utilised for determining either the group of data is same or different. The box plots for ANOVA test are illustrated in Figure 9.
Figure 9.
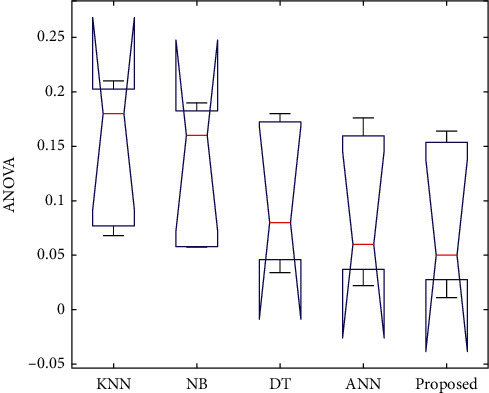
ANOVA test.
Table 4 gives the applications of CNN-based methods for medical image retrieval, computer-aided diagnosis, and classification task. Convolutional neural networks have proven to provide high performance in medical image processing than the other techniques. Thus, CNNs can be successfully applied for various tasks in medical image analysis. The results may differ based on choice of CNN model, number of classes, and number of images used.
Table 4.
Recent medical applications of CNN-based methods.
| Method | Dataset | Number of images/classes | Application | Accuracy (%) |
|---|---|---|---|---|
| Convolutional neural network [43] | Kaggle dataset | 80000 images, 5 classes | Diabetic retinopathy | 75 |
| Pretrained convolutional neural network [44] | Ultrasound images | 15000 ultrasound images, 2 classes | Thyroid nodule diagnosis | 83 |
| Convolutional restricted Boltzmann machine [45] | ILD (interstitial lung diseases) CT scans | 73 CT scans, 5 classes | Lung texture classification and airway detection | 89 |
| Fuzzy-based pooling in convolutional neural network [46] | MNIST dataset | 60000 grayscale images, 10 classes | Image classification | 94.4 |
| CIFAR-10 dataset | 60000 RGB images, 10 classes | 27.92 | ||
| Tree-based convolutional neural network [19] | NWPU-VHR-10 dataset | More than 60000 images | Object classification in segmented satellite images | 96.5 |
5.3. Encryption Results
5.3.1. Analysis of Information Entropy
Entropy is known as the significant aspect of randomness, and it can be utilised for defining the degree of uncertainty of the image. Information entropy computes the uniform distribution of gray pixel throughout the image. If the information entropy value is greater, the image confusion level of the encrypted image will be high. Assume E as the source of information and the information entropy of E is computed as follows:
| (33) |
where all the possibilities of Ei is denoted as n and the probability of occurrence of Ei is denoted as p(Ei). Based on the equation, information entropy for the proposed algorithm is analysed in the encrypted image.
The comparative analysis is carried out in the proposed system for analysing the influence of proposed encryption algorithm in the security performance of medical images. Different types of encryption algorithms are utilised for comparative analysis of proposed algorithm. The most commonly used approaches for the encryption process are feed-forward, feed-forward backpropagation, and fitting neural network algorithms. All these algorithms have been proved as highly effective in many security-related approaches. The information entropy results for the proposed algorithm, and other existing algorithms are displayed in Table 5. From the table, it is observed that the information entropy value is high for the proposed encryption algorithm than the other existing algorithms.
Table 5.
Information entropy results.
| Technique | Information entropy |
|---|---|
| Feed-forward | 7.986 |
| Feed-forward backpropagation | 7.987 |
| Fitting neural network | 7.941 |
| Proposed | 7.999 |
5.3.2. Correlation Coefficients
Correlation analysis is the statistical testing process which has the ability to crack the encryption algorithm. Also, the correlation coefficients provide evaluation standard for testing the encryption algorithm. For plain images, the correlation between adjacent pixels will be generally high. In order to avoid the statistical attacks due to correlation among adjacent pixels, correlated coefficients must be reduced for encrypted image. Here, the correlation coefficient of different pixels is utilised for determining the ability of encryption algorithm and to minimise the correlation between adjacent pixels. Correlation analysis of encrypted image considers all the possible adjacent situations such as diagonal, vertical, and horizontal directions. The following equations are utilised for assessing the correlation between the adjacent pixels in encrypted and plain images:
| (34) |
where M is represented as the overall pixels of the image and x and y are denoted as the neighbouring pixel values. The mean values are represented as B(x) and B(y), and the covariance and variance are represented as cov(x, y) and A(x). Based on the correlation equations, 2000 sets of adjacent pixels are selected from the diagonal, vertical, and horizontal directions. During the proposed encryption process, the pixels in the image are entirely randomized so that there will be no leaking of statistical information from encrypted image. Hence, the proposed algorithm has the potential to withstand statistical attack.
Figure 10 displays the correlation coefficients of plain image for the proposed encryption algorithm and other existing algorithms such as feed-forward, feed-forward backpropagation, and fitting neural network in diagonal, vertical, and horizontal directions. From the figure, it can be observed that the correlation coefficients of plain image are very high for the proposed encryption algorithm than the other existing algorithms in all directions.
Figure 10.
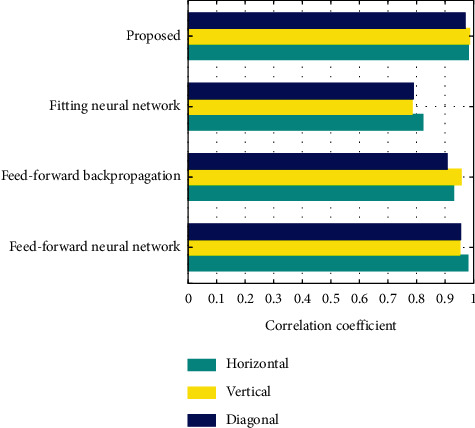
Correlation coefficient of plain image.
Figure 11 displays the correlation coefficient of encrypted image for the proposed algorithm and other existing algorithms such as feed-forward, feed-forward backpropagation, and fitting neural network in horizontal, vertical, and diagonal directions. From the figure it is known that the correlational coefficient of encrypted image is comparatively less for the proposed algorithm than the other existing algorithms in all directions.
Figure 11.
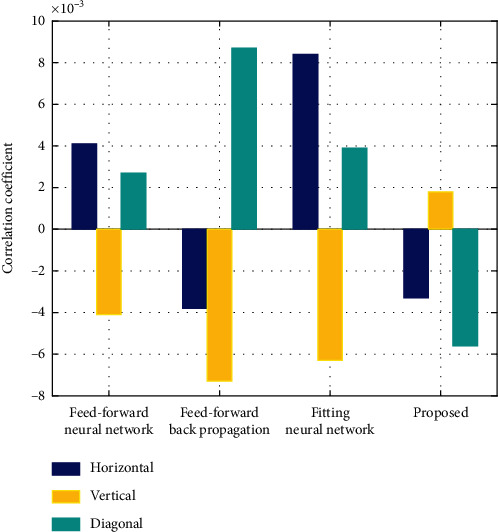
Correlation coefficient of encrypted image.
5.3.3. Differential Attack Analysis
Generally, a small variation in the original image can lead to noticeable variation in the encrypted image. To measure these changes in the original image, unified average changing intensity (UACI) and number of pixels change rate (NPCR) are utilised. The objective of NPCR is to calculate the exact number of altered pixel values in the differential attack. If the NPCR value is high, the result will be better. Instead, UACI focuses on the average variance between two paired encrypted images. If the value of UACI is low, the result will be better. NPCR and UACI quantitatively and qualitatively analyse the processed image and measure the sensitivity of original image. They can also determine whether the images will be able to resist differential attack. The UACI and NPCR are computed by the following equations:
| (35) |
| (36) |
where E1 and E2 are represented as an encrypted image before and after changing one pixel of the plain image. If E1(i, j) ≠ E2(i, j), then H(i, j)=1, if not H(i, j)=0. The estimated average UACI value is 33.46% and NPCR value is 99.56%. If the proposed algorithm attains this value, then the algorithm will have better performance.
The experimental results for NPCR and UACI are compared with other existing encryption algorithms such as feed-forward, feed-forward backpropagation, and fitting neural network. Table 6 displays the results of UACI and NPCR for the proposed and other existing encryption algorithms. The values from the table illustrate that, for NPCR, the proposed algorithm has the highest value than the other existing algorithms. But for UACI, feed-forward neural network has the lowest value than the other algorithms.
Table 6.
NPCR and UACI results.
| Technique | NPCR | UACI |
|---|---|---|
| Feed-forward | 99.412 | 33.615 |
| Feed-forward backpropagation | 99.702 | 33.572 |
| Fitting neural network | 99.684 | 33.551 |
| Proposed | 99.821 | 33.617 |
5.3.4. Computational Time Analysis
The time consumed by the algorithm for encryption and decryption processes is utilised for analysing the efficiency of proposed algorithm. However, the time consumed by the same algorithm will be varied for different hardware platforms. Table 7 displays the computation time of the proposed and the other existing algorithms such as feed-forward, feed-forward backpropagation, and fitting neural network. From the table, it is observed that the computation time required for the decryption process in the proposed encryption algorithm is less when it is compared with the other existing algorithms.
Table 7.
Time taken for image encryption and decryption.
| Technique | Encryption (sec) | Decryption (sec) |
|---|---|---|
| Feed-forward neural network | 0.132 | 0.121 |
| Feed-forward backpropagation | 0.264 | 0.119 |
| Fitting neural network | 0.195 | 0.245 |
| Proposed | 0.174 | 0.109 |
6. Discussion
In this study, IoT and cloud computing-based medical image analysis using fuzzy convolutional neural network has been proposed. IoT and cloud computing are the emerging technology and has been applied successfully in many fields. Many research works are conducted for utilising IoT and cloud computing in medical field. They can be effectively utilised for storing, processing, and sharing. Even though IoT and cloud computing has many advantages, it is not widely employed in the medical field due to the security aspects. Cancer has grown as the deadly disease for human beings from children to older generations. The earlier prediction of this disease can considerably reduce the mortality rate. By utilising IoT and cloud computing, the time required for predicting the disease can be minimised. This is because the data generated from the medical devices can be directly transferred to the cloud platform through Internet. Thus, the time required for the manual transmission of medical data will be reduced. Similarly, the image processing is carried out in the cloud, and thus, the processing time is also minimised. In medical images, the accuracy of the result should be precise for the effective treatment. Thus, an effective image processing technique is necessary for the effective prediction of diseases. Classification is one of the major tasks during image processing, and for obtaining more accurate classification results, the fuzzy logic system is integrated with convolutional neural network to form fuzzy convolutional neural network. It classifies the images into disease infected and not infected, and the results will be immediately transferred to the doctors and healthcare works. Thus, it helps the doctors to analyse the results and treat the patients at the initial stage. Furthermore, in order to increase the security and privacy of the data, encryption process based on BP neural network is employed in the proposed study. The perspective of this study is to create an efficient IoT-based cloud computing environment for earlier and accurate prediction of diseases. The proposed system can be effectively utilised in cancer centres for earlier prediction of disease and also analysing the progress in the treatment process. The proposed system can be also applied in large hospitals and healthcare centres with numerous patients' data. Implementing the IoT-based cloud computing system in the hospitals can greatly reduce the storage, and also it will ease managing patient's data.
7. Limitation of Proposed Approach and Future Prospects
The CNN has provided better performance for many applications in clinical domain, but it still has some limitations. More computational power and huge amount of training data are required for the architecture of CNN. If there is any deficiency in computational power, more time is required for training the data which depends on the size of the training data. These limitations can be minimised by better architecture of CNNs, increasing the number of digitally stored medical images, improved computational power, and enhanced data storage facilities. IoT-based cloud computing can be utilised for enhancing the data storage facilities. Even though the Internet of Things and cloud computing can be of huge benefit to healthcare, there are still major challenges to tackle before the complete implementation of connected devices in healthcare. Security and privacy are the major concerns which prevent the users from utilising IoT technology for medical purposes, as healthcare monitoring systems have the possibility to get hacked or breached. The disclosure of sensitive information about the patient's health and location and interfering with sensor data may cause great consequences, which would counteract the advantages of IoT. For privacy protection, encryption and decryption processes are utilised in the proposed approach. However, the encrypted image can be potentially decrypted without acquiring the key if there is an availability of considerable computational resources and skills. Thus, the skilled hackers may be able to decrypt the encrypted data. Also, failure or bugs in the hardware or even power failure can impact the performance of sensors and connected equipment placing healthcare operations at risk. In addition, skipping a scheduled software update may be even more hazardous than skipping a doctor checkup. Moreover, regarding IoT protocols and standards, there is no consent, so devices made by different manufacturers may not work well together. The lack of uniformity prevents full-scale integration of IoT, therefore limiting its potential effectiveness. Although IoT promises to reduce the cost of healthcare in the long-term, the cost of its implementation in hospitals and staff training is quite high.
8. Conclusion
IoT and cloud computing are considered as the significant techniques in big data processing since they are closely related to each other. The experimental process mainly focuses on utilising both IoT and cloud computing in healthcare procedure especially in brain tumour prediction. The dataset required for disease diagnosis is collected and securely transformed to the cloud. Then, the fuzzy convolutional neural network algorithm is proposed for medical image diagnosis. The proposed algorithm classifies the images into normal and abnormal images, and the results from the analysis are transferred to the doctors and healthcare providers with the help of IoT for further treatment process. From the results, it is concluded that the proposed algorithm outperforms other existing algorithms and can be effectively utilised for image diagnosis. In future, other deep learning neural network algorithms can be applied for improving the accuracy of disease prediction and for efficiently analysing large volume of medical data by utilising the medical resources.
Data Availability
The image data used to support the findings of this study are included within the article. We can visit https://www.smir.ch and create an account to get the BRATS dataset.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
References
- 1.Andriole K. P., Wolfe J. M., Khorasani R., et al. Optimizing analysis, visualization, and navigation of large image data sets: one 5000-section CT scan can ruin your whole day. Radiology. 2011;259(2):346–362. doi: 10.1148/radiol.11091276. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Silva L. A. B., Costa C., Oliveira J. L. A PACS archive architecture supported on cloud services. International Journal of Computer Assisted Radiology and Surgery. 2012;7(3):349–358. doi: 10.1007/s11548-011-0625-x. [DOI] [PubMed] [Google Scholar]
- 3.Kagadis G. C., Kloukinas C., Moore K., et al. Cloud computing in medical imaging. Medical Physics. 2013;40(7) doi: 10.1118/1.4811272. [DOI] [PubMed] [Google Scholar]
- 4.Kanagaraj G., Sumathi A. C. Proposal of an open-source cloud computing system for exchanging medical images of a hospital information system. Proceedings of the 3rd International Conference on Trendz in Information Sciences & Computing (TISC2011); December 2011; Chennai, India. IEEE; pp. 144–149. [Google Scholar]
- 5.Langer S. G. Challenges for data storage in medical imaging research. Journal of Digital Imaging. 2011;24(2):203–207. doi: 10.1007/s10278-010-9311-8. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Teng C. C., Mitchell J., Walker C., et al. A medical image archive solution in the cloud. Proceedings of the 2010 IEEE International Conference on Software Engineering and Service Sciences; July 2010; Beijing, China. IEEE; pp. 431–434. [Google Scholar]
- 7.Kumar P. M., Lokesh S., Varatharajan R., Chandra Babu G., Parthasarathy P. Cloud and IoT based disease prediction and diagnosis system for healthcare using fuzzy neural classifier. Future Generation Computer Systems. 2018;86:527–534. doi: 10.1016/j.future.2018.04.036. [DOI] [Google Scholar]
- 8.Janani T., Darak Y., Brindha M. Secure similar image search and copyright protection over encrypted medical image databases. IRBM. 2020 doi: 10.1016/j.irbm.2020.02.005. [DOI] [Google Scholar]
- 9.Yang F., Mou J., Cao Y., Chu R. An image encryption algorithm based on BP neural network and hyperchaotic system. China Communications. 2020;17(5):21–28. doi: 10.23919/jcc.2020.05.003. [DOI] [Google Scholar]
- 10.Suzuki K. Overview of deep learning in medical imaging. Radiological Physics and Technology. 2017;10(3):257–273. doi: 10.1007/s12194-017-0406-5. [DOI] [PubMed] [Google Scholar]
- 11.Sahoo A. K., Pradhan C., Das H. Nature Inspired Computing for Data Science. Cham, Switzerland: Springer; 2020. Performance evaluation of different machine learning methods and deep-learning based convolutional neural network for health decision making; pp. 201–212. [Google Scholar]
- 12.Zhao W., Du S., Emery W. J. Object-based convolutional neural network for high-resolution imagery classification. IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing. 2017;10(7):3386–3396. doi: 10.1109/jstars.2017.2680324. [DOI] [Google Scholar]
- 13.Jan B., Farman H., Khan M., et al. Deep learning in big data analytics: a comparative study. Computers & Electrical Engineering. 2019;75:275–287. doi: 10.1016/j.compeleceng.2017.12.009. [DOI] [Google Scholar]
- 14.Zhao R., Yan R., Chen Z., Mao K., Wang P., Gao R. X. Deep learning and its applications to machine health monitoring. Mechanical Systems and Signal Processing. 2019;115:213–237. doi: 10.1016/j.ymssp.2018.05.050. [DOI] [Google Scholar]
- 15.Miotto R., Wang F., Wang S., Jiang X., Dudley J. T. Deep learning for healthcare: review, opportunities and challenges. Briefings in Bioinformatics. 2018;19(6):1236–1246. doi: 10.1093/bib/bbx044. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Sahoo A. K., Pradhan C., Barik R. K., Dubey H. DeepReco: deep learning based health recommender system using collaborative filtering. Computation. 2019;7(2) doi: 10.3390/computation7020025. [DOI] [Google Scholar]
- 17.Ali M., Fard N. G., Shamsi M. A cloud solution for medical image processing. International Journal of Engineering Research and Applications. 2014;4(7):74–82. [Google Scholar]
- 18.Kayalibay B., Jensen G., van der Smagt P. CNN-based segmentation of medical imaging data. Computer Vision and Pattern Recognition. 2017;1:1–24. [Google Scholar]
- 19.Harold Robinson Y., Vimal S., Khari M., Hernandez F. C. L., Crespo R. G. Tree-based convolutional neural networks for object classification in segmented satellite images. The International Journal of High Performance Computing Applications. 2020;1:1–14. doi: 10.1177/1094342020945026. [DOI] [Google Scholar]
- 20.Li Q., Cai W., Wang X., Zhou Y., Feng D. D., Chen M. Medical image classification with convolutional neural network. Proceedings of the 2014 13th International Conference on Control Automation Robotics & Vision (ICARCV); March 2015; Singapore. [Google Scholar]
- 21.Yang J.-J., Li J.-Q., Niu Y. A hybrid solution for privacy preserving medical data sharing in the cloud environment. Future Generation Computer Systems. 2015;43-44:74–86. doi: 10.1016/j.future.2014.06.004. [DOI] [Google Scholar]
- 22.Kaur P., Sharma M., Mittal M. Big data and machine learning based secure healthcare framework. Procedia Computer Science. 2018;132:1049–1059. doi: 10.1016/j.procs.2018.05.020. [DOI] [Google Scholar]
- 23.Shin D.-H. User centric cloud service model in public sectors: policy implications of cloud services. Government Information Quarterly. 2013;30(2):194–203. doi: 10.1016/j.giq.2012.06.012. [DOI] [Google Scholar]
- 24.Sultan N. Cloud computing for education: a new dawn? International Journal of Information Management. 2010;30(2):109–116. doi: 10.1016/j.ijinfomgt.2009.09.004. [DOI] [Google Scholar]
- 25.Liu H., Kadir A., Sun X. Chaos‐based fast colour image encryption scheme with true random number keys from environmental noise. IET Image Processing. 2017;11(5):324–332. doi: 10.1049/iet-ipr.2016.0040. [DOI] [Google Scholar]
- 26.Zhou Y., Bao L., Chen C. L. P. A new 1D chaotic system for image encryption. Signal Processing. 2014;97(7):172–182. doi: 10.1016/j.sigpro.2013.10.034. [DOI] [Google Scholar]
- 27.Cao C., Sun K., Liu W. A novel bit-level image encryption algorithm based on 2D-LICM hyperchaotic map. Signal Processing. 2018;143:122–133. doi: 10.1016/j.sigpro.2017.08.020. [DOI] [Google Scholar]
- 28.Gupta K., Silakari S. Novel approach for fast compressed hybrid color image cryptosystem. Advances in Engineering Software. 2012;49(1):29–42. doi: 10.1016/j.advengsoft.2012.03.001. [DOI] [Google Scholar]
- 29.Huang C. K., Nien H. H. Multi chaotic systems based pixel shuffle for image encryption. Optics Communications. 2009;282(11):2123–2127. doi: 10.1016/j.optcom.2009.02.044. [DOI] [Google Scholar]
- 30.Wu X., Wang D., Kurths J., Kan H. A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Information Sciences. 2016;349-350:137–153. doi: 10.1016/j.ins.2016.02.041. [DOI] [Google Scholar]
- 31.Hinton G. E., Osindero S., Teh Y.-W. A fast learning algorithm for deep belief nets. Neural Computation. 2006;18(7):1527–1554. doi: 10.1162/neco.2006.18.7.1527. [DOI] [PubMed] [Google Scholar]
- 32.LeCun Y., Bengio Y., Hinton G. Deep learning. Nature. 2015;521(7553):436–444. doi: 10.1038/nature14539. [DOI] [PubMed] [Google Scholar]
- 33.Shelhamer E., Long J., Darrell T. Fully convolutional networks for semantic segmentation. IEEE Transactions on Pattern Analysis and Machine Intelligence. 2017;39(4):640–651. doi: 10.1109/tpami.2016.2572683. [DOI] [PubMed] [Google Scholar]
- 34.Le Q. V. Building high-level features using large scale unsupervised learning. Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing; 2013; Vancouver, Canada. pp. 8595–8598. [Google Scholar]
- 35.Krizhevsky A., Sutskever I., Hinton G. E. ImageNet classification with deep convolutional neural networks. Communications of ACM. 2017;60(6) doi: 10.1145/3065386. [DOI] [Google Scholar]
- 36.Li L.-J., Su H., Fei-Fei L., Xing E. P. Object bank: a high-level image representation for scene classification & semantic feature sparsification. Advances in Neural Processing Systems. 2010;1:1378–1386. [Google Scholar]
- 37.Sun Y., Chen Y., Wang X., Tang X. Deep learning face representation by joint identification-verification. Advances in Neural Processing Systems. 2014;1:1988–1996. [Google Scholar]
- 38.Cheng G., Yang C., Yao X., Guo L., Han J. When deep learning meets metric learning: remote sensing image scene classification via learning discriminative CNNs. IEEE Transactions on Geoscience and Remote Sensing. 2018;56(5):2811–2821. doi: 10.1109/tgrs.2017.2783902. [DOI] [Google Scholar]
- 39.Hsu M.-J., Chien Y.-H., Wang W.-Y., Hsu C.-C. A convolutional fuzzy neural network architecture for object classification with small training database. International Journal of Fuzzy Systems. 2020;22(1):1–10. doi: 10.1007/s40815-019-00764-1. [DOI] [Google Scholar]
- 40.Chen C. W., Luo J., Parker K. J. Image segmentation via adaptive K-mean clustering and knowledge-based morphological operations with biomedical applications. IEEE Transactions on Image Processing. 1998;7(12):1673–1683. doi: 10.1109/83.730379. [DOI] [PubMed] [Google Scholar]
- 41.Menze B. H., Jakab A., Bauer S., et al. The multimodal brain tumor image segmentation benchmark (BRATS) IEEE Transactions on Medical Imaging. 2015;34(10):1993–2024. doi: 10.1109/TMI.2014.2377694. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 42.Cheng J., Huang W., Cao S., et al. Enhanced performance of brain tumor classification via tumor region augmentation and partition”. PLoS One. 2015;10(10) doi: 10.1371/journal.pone.0140381.e0140381 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43.Pratt H., Coenen F., Broadbent D. M., Harding S. P., Zheng Y. Convolutional neural networks for diabetic retinopathy. Procedia Computer Science. 2016;90:200–205. doi: 10.1016/j.procs.2016.07.014. [DOI] [Google Scholar]
- 44.Ma J., Wu F., Zhu J., Xu D., Kong D. A pre-trained convolutional neural network based method for thyroid nodule diagnosis. Ultrasonics. 2017;73:221–230. doi: 10.1016/j.ultras.2016.09.011. [DOI] [PubMed] [Google Scholar]
- 45.van Tulder G., de Bruijne M. Combining generative and discriminative representation learning for lung CT analysis with convolutional restricted Boltzmann machines. IEEE Transactions on Medical Imaging. 2016;35(5):1262–1272. doi: 10.1109/tmi.2016.2526687. [DOI] [PubMed] [Google Scholar]
- 46.Sharma T., Singh V., Sudhakaran S., Verma N. K. Fuzzy based pooling in convolutional neural network for image classification. Proceedings of the 2019 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE); June 2019; New Orleans, LA, USA. pp. 1–6. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The image data used to support the findings of this study are included within the article. We can visit https://www.smir.ch and create an account to get the BRATS dataset.


