The secret of a holographic image can be shared across two closely stacked metasurface holograms.
Abstract
Secret sharing is a well-established cryptographic primitive for storing highly sensitive information like encryption keys for encoded data. It describes the problem of splitting a secret into different shares, without revealing any information to its shareholders. Here, we demonstrate an all-optical solution for secret sharing based on metasurface holography. In our concept, metasurface holograms are used as spatially separable shares that carry encrypted messages in the form of holographic images. Two of these shares can be recombined by bringing them close together. Light passing through this stack of metasurfaces accumulates the phase shift of both holograms and optically reconstructs the secret with high fidelity. In addition, the hologram generated by each single metasurface can uniquely identify its shareholder. Furthermore, we demonstrate that the inherent translational alignment sensitivity between two stacked metasurface holograms can be used for spatial multiplexing, which can be further extended to realize optical rulers.
INTRODUCTION
Over the years, several approaches have been developed to protect data from theft and tampering. A common way to enhance data security is information encryption. Nowadays, cryptographic methods are widely used for security-related problems concerning the protection of intellectual property rights and product authentication. Invented by Adi Shamir and George Blakley (1, 2), secret sharing solves the cryptographic task of splitting a secret among multiple shareholders so that it can only be reconstructed when a sufficient number of shares are combined together. In doing so, the corruption of a single shareholder does not leak any information about the shared secret. In another type of security application, optical holography has appeared as a crucial security element against counterfeiting with several important applications in identity cards, passports, and banknotes (3–5). Among the different available holographic techniques, metaholography thrives with its inherent flexibility and compactness, which allows for dense storing and encrypting of optical information into spatially distributed phase and amplitude patterns (6, 7).
The design flexibility of metasurfaces stems from the huge variety of possible nanostructure shapes and can be used to access multiple degrees of freedom (DOFs) per pixel. For metasurface holography, these additional DOFs offer the possibility of realizing novel multiplexing schemes for improved information security, where different holographic images are encoded along multiple optical dimensions (8–16). However, so far, metasurface multiplexing frameworks were usually one-layer solutions, which only allow for the access of different information channels, but not for the physical splitting of these information channels across multiple shareholders. In this context, multilayer layouts offer an alternative as they allow for the physical separation of layers and their inherent information.
Previously, multilayer metasurface layouts were often used to achieve previously unrealized functionalities or to increase the performance of existing optical metasurface elements. This includes the demonstration of high wavelength selectivity (17, 18), multispectral (19, 20) and varifocal (21) metalenses, metasurface retroreflectors (22), holography with asymmetric transmission (23), circular polarization filters (24), multicolor holography (25, 26), image differentiation (27), and quantitative phase microscopy (28), as well as pattern recognition in an all-optical machine learning framework (29). The advantage of multilayer phase mask systems or diffractive deep neural networks is that they are highly customizable as they gradually change the state of light within each layer (29, 30). Some demonstrations based on multiple phase profiles have been proposed for watermarking and optical encryption (31–35). However, independent holographic images of each single-phase profile were not obtained. With advances in design and algorithmic techniques, these multilayer systems can be developed toward innovative holographic security features (36).
RESULTS
Here, we experimentally demonstrate a cascaded metasurface framework that can be used to split and share encrypted holographic information across multiple metasurface layers (Fig. 1). In our optical secret sharing scheme, we use a set of nanostructured optical metasurfaces as “shares.” Each of them contains an encoded phase-only Fourier hologram, which can be reconstructed in the far field upon illumination with circularly polarized light. These single-layer images serve as a unique identifier for each metasurface. Meanwhile, when the two metasurfaces are stacked 100 μm apart, the illumination of the cascaded configuration creates a new holographic image that is distinct from their two single-layer holograms. This cascaded holographic image can be used as an optical secret that is only revealed if both metasurfaces are stacked. The concept can be extended to a larger set of shares where only the combination of all of them will reveal the stored secret. To achieve this behavior, we use an iterative gradient optimization approach that uses the “automatic differentiation” feature of modern machine learning libraries (37).
Fig. 1. Conceptual illustration of the holographic secret sharing via cascaded metasurfaces.
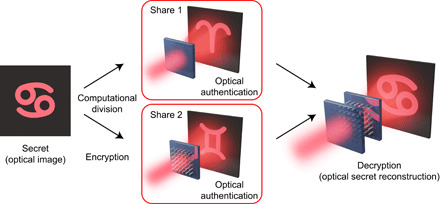
By design, both metasurfaces (shares) contain a Fourier hologram, which reconstructs an image in the visible when they are illuminated with circularly polarized light. At the same time, the illumination in the cascaded configuration creates a completely different image. While the secret of the cascaded image is shared across two metasurfaces, the single-metasurface holographic images can be used as unique identifiers for the shareholders.
In a simple picture, the cascaded hologram’s functionality can be understood as follows: Light passing through the cascaded arrangement accumulates the phase delays of both layers. In an idealized case, where both metasurfaces are virtually placed on top of each other, this would correspond to adding up both phase masks pixelwise. Considering that the same cascaded phase mask can be built up through combinations of different single phase masks, it is possible to share the “secret” of the cascaded image across two metasurface layers without revealing any information about the shared secret within the single-layer images. Meanwhile, by adding up both phase profiles pixelwise, the phase relations of the single phase masks are no longer preserved, which allows for the multiplexing of single and cascaded images.
For our demonstration, we use the concept of the Pancharatnam-Berry phase (PBP) to realize the metasurface phase masks (38, 39). Thus, the metasurfaces are made of silicon nanofin structures, which are designed as local half-wave plates. According to their individual orientation, these nanostructures introduce a spatial variant phase delay into the cross circular polarization state of the transmitted light. The PBP has not only the advantage of being quite robust with regard to fabrication and wavelength, but it also allows for filtering unwanted light through the usage of polarization optics. We fabricate two distinct metasurface holograms on one glass substrate (metasurface set A) and three additional metasurface holograms on a second glass substrate (metasurface set B). This allows for six different combinations in a cascaded configuration. Details about the design and fabrication can be found in Methods.
The experimentally reconstructed images of the encoded astrological symbols for the single metasurface holograms and their combinations are shown in Fig. 2. We observe that all five metasurface holograms reconstruct their individual single-layer image in high quality with low background noise (Fig. 2B). Meanwhile, cascading the metasurface holograms from both sets results in six reconstructed images with a similar quality compared to their single-layer counterparts (Fig. 2C). However, the cascaded image quality strongly depends on the alignment and deteriorates for small translational in-plane shifts between both metasurfaces. This behavior can be understood by considering that the appearance of the cascaded images requires correct pixel matching between both metasurfaces. Thus, we observe a breakdown of the cascaded hologram image when the translational mismatch exceeds the pixel size of 5 μm (see the Supplementary Materials).
Fig. 2. Holographic encryption scheme.
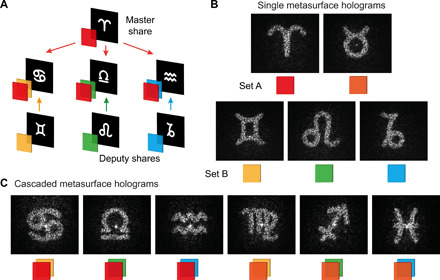
(A) Illustration of the concept using a “master share” metasurface hologram in combination with three distinct “deputy shares.” For the demonstration, we fabricate two distinct master share metasurface holograms on one substrate (set A) and three deputy share metasurface holograms on a second substrate (set B). Within every single metasurface of both sets and each stacked combination, a distinct Fourier hologram of an astrological symbol is encoded. (B) Measured single-metasurface holographic images for a wavelength of 740 nm. For better visualization, every metasurface hologram is represented by a unique color. (C) Measured cascaded metasurface holographic images for the various combinations of the metasurfaces of both sets for the same wavelength. The cascaded images nearly achieve the image quality of their single-layer counterparts.
Furthermore, all images are clearly visible without any apparent cross-talk (single metasurface images are not visible in the cascaded case). The low cross-talk can be explained by the fact that the second metasurface completely wipes out any regularities of the first metasurface’s phase profile and vice versa. In the limit of zero distance between the metasurfaces, this can be understood as follows: Because the Fourier transform of a product is the convolution of its Fourier-transformed elements, the reconstructed cascaded image is effectively the convolution of the two single images’ complex electric fields. In the vast majority of cases, this convolution operation does not preserve any visible information from the single images to the cascaded image. Therefore, we do not observe any image artifacts of the single-layer holograms within the cascaded cases. The low cross-talk is, in particular, important for optical secret sharing applications where the single metasurface hologram should not reveal any information of the secret.
In our example, we chose to use two holograms in set A and three holograms in set B. However, the concept is general, and the number of encoded images can be increased further by adding more metasurfaces to both sets or by increasing the number of sets. Note that the two sets of metaholograms (master set A and deputy set B) can be combined arbitrarily. All individual single-layer metasurface holograms and the various combinations of them carry their holographic information. With the entire series of combinations, the complete secret set can be revealed. On the basis of such scaling of information, we need to recognize that the achievable image quality is fundamentally limited by the ratio of encoded images to available phase masks. A good scaling strategy is to have a master set with a small number of shares and a deputy set with a larger number of shares. In such a scenario, the image quality primarily depends on the number of shares in the master set. Note that a decrease in image quality due to a high number of shares can be compensated by increasing the number of pixels in each hologram.
To obtain high-quality images, the design algorithm for the holograms plays an important role. Here, we treat the metasurface design process as an optimization problem in which we try to minimize the differences between the target images and the calculated images resulting from the simulated light interference. Figure 3 schematically illustrates the calculation of the total error function, which benchmarks the image qualities for a given set of metasurface phase masks. The error calculation is a two-step process, which involves both the physical recreation of the image formation for a given phase mask set and an image comparison to the target images. It is important to note that the entire forward calculation has to be explicitly performed within an automatic differentiation framework to be traced for the gradient calculation. The gradient ∇Φα(Φ), which is the derivative of the total error α with regard to all phase mask values , is then used within a gradient optimization scheme, which converges toward a local optimum (for more details, see the Supplementary Materials). The actual secret splitting is achieved implicitly within the optimization framework. By providing a target for all single-layer configurations, we create an algorithmic incentive to hide the cascaded image for a single shareholder.
Fig. 3. Flow chart of the forward pass for the gradient optimization scheme.
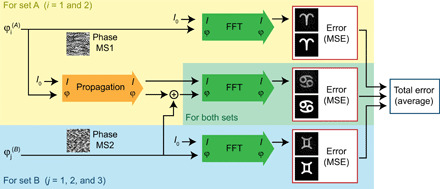
The metasurface phase masks (MS1 and MS2) used in the cascaded configuration were designed using a gradient optimization scheme. The flow chart shows the physical forward pass within the gradient optimization loop, which assigns an error or fitness value to a given set of phase masks. The algorithm performs a fast Fourier transformation (FFT) for all single and cascaded images (sets A and B) and then compares the calculated images with target images by using the mean squared error (MSE). For the light propagation between the two metasurface layers in the cascaded case, we use the angular spectrum method with zero padding. In the optimization loop, we try to find a set of phase masks that minimizes the total error α. This is accomplished by calculating its gradient ∇Φα(Φ) with automatic differentiation and using a gradient optimizer.
Our developed algorithmic approach is an efficient and straightforward design method for the demonstrated holographic secret sharing framework. Note that the gradient optimization with regular numerical gradient calculation becomes infeasible due to the high number of DOFs. Moreover, alternative approaches based on the widely used Gerchberg-Saxton algorithm might not inherently guarantee convergence and can struggle to encode a larger number of holograms (40, 41).
To illustrate the potential of cascaded metasurface holography for optical secret sharing, we additionally introduce the concept of translational multiplexing for cascaded holograms. In the previous example, we showed that the shared secret cannot be revealed if the position of the two metasurfaces is mismatched, resulting in the precise alignment requirement. We take advantage of this feature by using the translational movement as a new multiplexing dimension (additional DOF). For that, we encode multiple images across different relative translational positions. Thus, different holographic images can be reconstructed if the metasurface holograms are slightly repositioned against each other.
As proof of principle, we demonstrate here a case where two different translational positions result in two different images for the cascaded hologram (Fig. 4). The single metasurface holograms (shares 1 and 2) contain the encoded images of the numbers “1” and “2.” At the same time, the images of the numbers “3” and “4” appear in the cascaded arrangement for two distinct overlap positions, which lie five pixels (25 μm) apart along the x axis. As the translational movement naturally changes the overlap area between both metasurfaces, we periodically expand the holographic phase mask of share 1 into a rectangular shape to ensure a square-shaped overlap in both cascaded configurations. Thus, the two cascaded images appear for the alignment of share 2 along with one of the two edges (left and right) of share 1. Because we previously observed that the cascaded holographic image quickly deteriorates for a translational movement of one pixel, we expect a negligible cross-talk here for the implemented translational shift of five pixels. This expectation is confirmed by the measurement results in Fig. 4C (for additional information, see the Supplementary Materials). In terms of practical applications, the translational multiplexing concept has the potential of being used as an optical ruler. There, cascaded images can be encoded into a discrete number of equidistant real space positions that digitally display the current overlap position as a holographic image. Here, the metasurface holograms have the advantage that micrometer pixel sizes and small spacings can be achieved, which, in turn, would allow for an optical ruler with a very high spatial resolution even below the diffraction limit of light.
Fig. 4. Translational multiplexing with cascaded holograms.
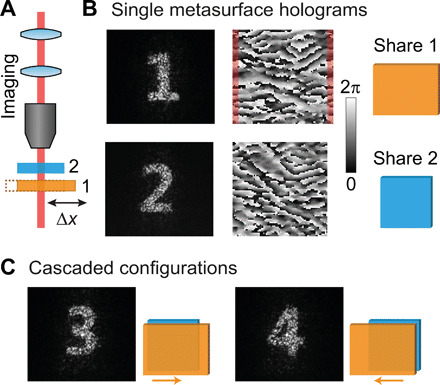
(A) Schematic view of the experiment containing both metasurface shares 1 and 2. The high alignment sensitivity for the cascaded image reconstruction allows for the implementation of translational multiplexing by shifting metasurface 1. (B) The two metasurfaces are designed and fabricated to contain one single Fourier hologram each as well as two cascaded holograms. The phase pattern of the two holograms is shown in the middle. Note that the metasurface for share 1 has been periodically expanded to ensure the same spatial overlap after the translation. (C) A spatial translation of only five pixels (25 μm) in the cascaded case results in a different holographic image reconstruction. The images with the numbers 1 to 4 show the experimentally measured Fourier images.
DISCUSSION
Our demonstrated stacking of multiple holographic metasurfaces and using them in a cascaded way allows for a unique optical secret sharing and encryption platform. The concept is scalable, both in terms of the stack size and the number of keys. It can be also altered into a (t, n)-threshold scheme, where already a subset of shareholders (t of n) can reconstruct the secret. Additional complexity and security can be added by using complex amplitude and phase holograms. Because of their compact shape and their design flexibility, metasurfaces are naturally suited for the realization of cascaded configurations. The high sensitivity for the spatial alignment is also perfectly suited for holographic seals, where two metasurfaces are slightly glued together, and the restoration of the cascaded hologram would become extremely challenging after both metasurfaces have been separated. For realizing a reprogrammable encryption scheme, one can combine a metasurface as the main share, with a spatial light modulator as the deputy share. By generating different phase patterns with the spatial light modulator and using it for the illumination of the metasurface, different holographic images can be revealed.
METHODS
Experiment and sample fabrication
All holographic images were captured by projecting the Fourier space of the metasurface plane on a complementary metal oxide semiconductor (CMOS) camera (EO USB 2.0 CMOS) with the usage of a microscope objective (Nikon S Plan Fluor ELWD 20×/0.45) and two lenses. As a light source, we use a supercontinuum laser (Fianium Whitelase WL-SC-400-2) with a tunable spectral filter (NKT Photonics SuperK VARIA) to obtain a spectral bandwidth of 10 nm. The polarization state of the light was set and after the samples filtered by pairs of a quarter-wave plate and a linear polarizer.
The silicon metasurfaces were fabricated on a glass substrate following the processes of silicon deposition, patterning, lift-off, and etching. First, through plasma-enhanced chemical vapor deposition, we prepared a 600-nm-thick amorphous silicon (a-Si) film. Following this, a poly(methyl methacrylate) resist layer was spin-coated and patterned by standard electron beam lithography. After development, a 20-nm-thick chromium layer was deposited. After a lift-off process, we used inductively coupled plasma reactive ion etching to transfer the predefined structures by the chromium mask to the silicon. Afterward, the residual chromium mask was removed using a standard wet etching process. Each metasurface hologram has a pattern size of 400 μm by 400 μm and consists of 80 × 80 pixels yielding a 5-μm pixel size. Each pixel consists of an array of silicon nanofins, which have a grid periodicity of 500 nm. Each cuboid nanostructure has a length of 190 nm and a width of 130 nm.
Metasurface design
The phase mask calculations were performed in Python v3.8 with the usage of TensorFlow v2.2 as an automatic differentiation library. For the single nanostructure design, we use rigorous coupled-wave analysis. More details can be found in the Supplementary Materials.
Acknowledgments
Funding: We acknowledge the funding provided by the National Key R&D Program of China (no. 2017YFB1002900) and the European Research Council (ERC) under the European Union’s Horizon 2020 research and innovation program (grant agreement no. 724306). We also thank the NSFC-DFG joint program (DFG no. ZE953/11-1 and NSFC no. 61861136010) for additional support. L.H. acknowledges the support from the Beijing Outstanding Young Scientist Program (BJJWZYJH01201910007022), the National Natural Science Foundation of China (no. 61775019) program, and the Fok Ying-Tong Education Foundation of China (no. 161009). Author contributions: L.H. proposed the conceptual idea, which P.G. and Q.W. refined later. P.G. and Q.W. developed the holographic optimization algorithm. Q.W. and L.H. designed and B.S. fabricated the metasurfaces. P.G., C.S., and T.Z. carried out the optical experiments. Y. W., L.H., and T.Z. supervised the overall projects. All authors analyzed the data, discussed the results, and prepared the manuscript. Competing interests: The authors declare that they have no competing interests. Data and materials availability: All data needed to evaluate the conclusions in the paper are present in the paper and/or the Supplementary Materials. The software codes and the raw data that support the plots within this paper are available from the corresponding author upon reasonable request.
SUPPLEMENTARY MATERIALS
Supplementary material for this article is available at http://advances.sciencemag.org/cgi/content/full/7/16/eabf9718/DC1
REFERENCES AND NOTES
- 1.Shamir A., How to share a secret. Commun. ACM 22, 612–613 (1979). [Google Scholar]
- 2.G. R. Blakley, in 1979 International Workshop on Managing Requirements Knowledge (MARK) (IEEE, 1979), pp. 313–318. [Google Scholar]
- 3.L. M. Lancaster, The future for security applications of optical holography, International Conference on Applications of Optical Holography (1995), vol. 2577, pp. 71–76. [Google Scholar]
- 4.L. Kotačka, T. Těthal, V. Kolařík, in Congress on Optics and Optoelectronics (SPIE, 2005), vol. 5954, pp. 59540K. [Google Scholar]
- 5.Javidi B., Carnicer A., Yamaguchi M., Nomura T., Pérez-Cabré E., Millán M. S., Nishchal N. K., Torroba R., Barrera J. F., He W., Peng X., Stern A., Rivenson Y., Alfalou A., Brosseau C., Guo C., Sheridan J. T., Situ G., Naruse M., Matsumoto T., Juvells I., Tajahuerce E., Lancis J., Chen W., Chen X., Pinkse P. W. H., Mosk A. P., Markman A., Roadmap on optical security. J. Opt. 18, 083001 (2016). [Google Scholar]
- 6.Deng Z.-L., Li G. X., Metasurface optical holography. Mater. Today Phys. 3, 16–32 (2017). [Google Scholar]
- 7.Genevet P., Capasso F., Holographic optical metasurfaces: A review of current progress. Rep. Prog. Phys. 78, 024401 (2015). [DOI] [PubMed] [Google Scholar]
- 8.Huang L. L., Mühlenbernd H., Li X., Song X., Bai B., Wang Y., Zentgraf T., Broadband hybrid holographic multiplexing with geometric metasurfaces. Adv. Mater. 27, 6444–6449 (2015). [DOI] [PubMed] [Google Scholar]
- 9.Wen D., Yue F., Li G., Zheng G., Chan K., Chen S., Chen M., Li K. F., Wong P. W. H., Cheah K. W., Pun E. Y. B., Zhang S., Chen X., Helicity multiplexed broadband metasurface holograms. Nat. Commun. 6, 8241 (2015). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Zhao W., Liu B., Jiang H., Song J., Pei Y., Jiang Y., Full-color hologram using spatial multiplexing of dielectric metasurface. Opt. Lett. 41, 147–150 (2016). [DOI] [PubMed] [Google Scholar]
- 11.Lim K. T. P., Liu H., Liu Y., Yang J. K. W., Holographic colour prints for enhanced optical security by combined phase and amplitude control. Nat. Commun. 10, 25 (2019). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Wan W., Gao J., Yang X., Full-color plasmonic metasurface holograms. ACS Nano 10, 10671–10680 (2016). [DOI] [PubMed] [Google Scholar]
- 13.Li J., Kamin S., Zheng G., Neubrech F., Zhang S., Liu N., Addressable metasurfaces for dynamic holography and optical information encryption. Sci. Adv. 4, eaar6768 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Kamali S. M., Arbabi E., Arbabi A., Horie Y., Faraji-Dana M. S., Faraon A., Angle-multiplexed metasurfaces: Encoding Independent wavefronts in a single metasurface under different illumination angles. Phys. Rev. X 7, 041056 (2017). [Google Scholar]
- 15.Ren H., Briere G., Fang X., Ni P., Sawant R., Héron S., Chenot S., Vézian S., Damilano B., Brändli V., Maier S. A., Genevet P., Metasurface orbital angular momentum holography. Nat. Commun. 10, 2986 (2019). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Fang X., Ren H., Gu M., Orbital angular momentum holography for high-security encryption. Nat. Photonics 14, 102–108 (2020). [Google Scholar]
- 17.Li P.-C., Yu E. T., Flexible, low-loss, large-area, wide-angle, wavelength-selective plasmonic multilayer metasurface. J. Appl. Phys. 114, 133104 (2013). [Google Scholar]
- 18.Li P. C., Yu E. T., Wide-angle wavelength-selective multilayer optical metasurfaces robust to interlayer misalignment. J. Optic. Soc. Am. B 30, 27–32 (2013). [Google Scholar]
- 19.Avayu O., Almeida E., Prior Y., Ellenbogen T., Composite functional metasurfaces for multispectral achromatic optics. Nat. Commun. 8, 14992 (2017). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Zhou Y., Kravchenko I. I., Wang H., Nolen J. R., Gu G., Valentine J., Multilayer noninteracting dielectric metasurfaces for multiwavelength metaoptics. Nano Lett. 18, 7529–7537 (2018). [DOI] [PubMed] [Google Scholar]
- 21.Arbabi E., Arbabi A., Kamali S. M., Horie Y., Faraji-Dana M. S., Faraon A., MEMS-tunable dielectric metasurface lens. Nat. Commun. 9, 812 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 22.Arbabi A., Arbabi E., Horie Y., Kamali S. M., Faraon A., Planar metasurface retroreflector. Nat. Photonics 11, 415–420 (2017). [Google Scholar]
- 23.Frese D., Wei Q., Wang Y., Huang L., Zentgraf T., Nonreciprocal asymmetric polarization encryption by layered plasmonic metasurfaces. Nano Lett. 19, 3976–3980 (2019). [DOI] [PubMed] [Google Scholar]
- 24.Zhao Y., Belkin M. A., Alù A., Twisted optical metamaterials for planarized ultrathin broadband circular polarizers. Nat. Commun. 3, 870 (2012). [DOI] [PubMed] [Google Scholar]
- 25.Zhou Y., Kravchenko I. I., Wang H., Zheng H., Gu G., Valentine J., Multifunctional metaoptics based on bilayer metasurfaces. Light Sci. Appl. 8, 80 (2019). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Hu Y., Luo X., Chen Y., Liu Q., Li X., Wang Y., Liu N., Duan H., 3D-Integrated metasurfaces for full-colour holography. Light Sci. Appl. 8, 86 (2019). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 27.Zhou Y., Zheng H. Y., Kravchenko I. I., Valentine J., Flat optics for image differentiation. Nat. Photonics 14, 316–323 (2020). [Google Scholar]
- 28.Kwon H., Arbabi E., Kamali S. M., Faraji-Dana M., Faraon A., Single-shot quantitative phase gradient microscopy using a system of multifunctional metasurfaces. Nat. Photonics 14, 109–114 (2020). [Google Scholar]
- 29.Lin X., Rivenson Y., Yardimci N. T., Veli M., Luo Y., Jarrahi M., Ozcan A., All-optical machine learning using diffractive deep neural networks. Science 361, 1004–1008 (2018). [DOI] [PubMed] [Google Scholar]
- 30.Gao Y., Jiao S., Fang J., Lei T., Xie Z., Yuan X., Multiple-image encryption and hiding with an optical diffractive neural network. Opt. Commun. 463, 125476 (2020). [Google Scholar]
- 31.Refregier P., Javidi B., Optical-image encryption based on input plane and fourier plane random encoding. Opt. Lett. 20, 767–769 (1995). [DOI] [PubMed] [Google Scholar]
- 32.Deng S., Liu L., Lang H., Zhao D., Liu X., Cascaded Fresnel digital hologram and its application to watermarking. Opt. Appl. XXXVI, 413–420 (2006). [Google Scholar]
- 33.Qu G., Yang W., Song Q., Liu Y., Qiu C.-W., Han J., Tsai D.-P., Xiao S., Reprogrammable meta-hologram for optical encryption. Nat. Commun. 11, 5484 (2020). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34.Li Y., Kreske K., Rosen J., Security and encryption optical systems based on a correlator with significant output images. Appl. Optics 39, 5295–5301 (2000). [DOI] [PubMed] [Google Scholar]
- 35.Situ G., Zhang J., A cascaded iterative Fourier transform algorithm for optical security applications. Optik 114, 473–477 (2003). [Google Scholar]
- 36.Chen W., Javidi B., Chen X., Advances in optical security systems. Adv. Opt. Photonics 6, 120–155 (2014). [Google Scholar]
- 37.Baydin A. G., Pearlmutter B. A., Radul A. A., Siskind J. M., Automatic differentiation in machine learning: A survey. J. Mach. Learn. Res. 18, 5595–5637 (2018). [Google Scholar]
- 38.Bomzon Z., Kleiner V., Hasman E., Pancharatnam-Berry phase in space-variant polarization-state manipulations with subwavelength gratings. Opt. Lett. 26, 1424–1426 (2001). [DOI] [PubMed] [Google Scholar]
- 39.Huang L., Chen X., Mühlenbernd H., Li G., Bai B., Tan Q., Jin G., Zentgraf T., Zhang S., Dispersionless phase discontinuities for controlling light propagation. Nano Lett. 12, 5750–5755 (2012). [DOI] [PubMed] [Google Scholar]
- 40.Lu D., Liao M., He W., Xing Q., Verma G., Peng X., Experimental optical secret sharing via an iterative phase retrieval algorithm. Opt. Lasers Eng. 126, 105904 (2020). [Google Scholar]
- 41.Li Z., Premaratne M., Zhu W., Advanced encryption method realized by secret shared phase encoding scheme using a multi-wavelength metasurface. Nanophotonics 9, 3687–3696 (2020). [Google Scholar]
- 42.D. P. Kingma, J. Ba, Adam: A method for stochastic optimization. arXiv:1412.6980 [cs.LG] (2014).
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Supplementary material for this article is available at http://advances.sciencemag.org/cgi/content/full/7/16/eabf9718/DC1


