Abstract
In this paper, a novel medical image encryption method based on multi-mode synchronization of hyper-chaotic systems is presented. The synchronization of hyper-chaotic systems is of great significance in secure communication tasks such as encryption of images. Multi-mode synchronization is a novel and highly complex issue, especially if there is uncertainty and disturbance. In this work, an adaptive-robust controller is designed for multimode synchronized chaotic systems with variable and unknown parameters, despite the bounded disturbance and uncertainty with a known function in two modes. In the first case, it is a main system with some response systems, and in the second case, it is a circular synchronization. Using theorems it is proved that the two synchronization methods are equivalent. Our results show that, we are able to obtain the convergence of synchronization error and parameter estimation error to zero using Lyapunov’s method. The new laws to update time-varying parameters, estimating disturbance and uncertainty bounds are proposed such that stability of system is guaranteed. To assess the performance of the proposed synchronization method, various statistical analyzes were carried out on the encrypted medical images and standard benchmark images. The results show effective performance of the proposed synchronization technique in the medical images encryption for telemedicine application.
Keywords: medical images, encryption, multi-mode synchronization, robust control, adaptive control, time varying, lyapunov stability
1. Introduction
Recently, telemedicine systems have been introduced to assist the diagnosis and treatment of various diseases [1,2,3]. These systems, through telecommunication systems and clinical data registration devices, have been able to yield good medical services between specialists and patients easily; the significance of this issue arises when some patients for any reason cannot attend medical specialty centers [4,5]. Specialist physicians can apply telemedicine to diagnose the disease using clinical data such as medical images and signals.
When sending and receiving clinical data in telecommunication channels, information security is one of the main dilemmas of telemedicine systems [6]; because telecommunication channels are not secure enough to send medical information. Various medical information of patients is confidential, and at the time of sending and receiving from the patient to the specialist must have a sufficient security communication channel and cannot be accessed by other individuals and organizations [7,8]. In order to enhance the security of patients’ information at the time of sending, various approaches are exploited that the most important of which are cryptographic techniques.
One of the most important fields of cryptography is chaotic systems [9,10]. The most significant feature of chaotic systems is the high reaction to small changes in the initial conditions [11,12]. Much research has been conducted in this field for the last two decades since Correll et al. [13,14,15] introduced the synchronization of chaotic systems. In recent years, the employment of chaotic systems in clinical data encryption has grown remarkably [16]. Because chaos systems mainly guarantee medical information confidentiality when sending and receiving from telecommunication channels [16].
Data encryption is usually done by chaotic or hyper-chaotic methods [17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37]. In some researches, chaotic or hyper-chaotic systems are used to encrypt peripheral data [38,39,40,41,42,43]. In recent years, researchers have focused on the encryption of medical data using chaotic methods [17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35]. Medical data contains important information about patients [41,44,45,46]. Therefore, the confidentiality of medical information is essential when sending it through telecommunication channels. Chaotic theory, as a nonlinear and complex phenomenon, plays an important role in increasing the security of medical data. In the following, a number of conducted investigations using cryptographic procedures in clinical data have been examined.
Lin et al. [17] used chaos theory to the encryption of electroencephalogram (EEG) signals. In this paper, the chaos-based EEG encryption system involves three levels of encryption and is implemented in the C# programming language.
A chaotic theory-based cryptographic method for clinical signals is presented in [18]. The proposed encryption algorithm is based on a logistic map with double chaotic layer encryption (DCLE). In this study, EEG, electrocardiograms (ECG), and blood pressure (BP) data from the PhysioBank database were acquired.
The idea of the optical chaos method for secure EEG signals transmission in telemedicine applications has been discussed in Shahzadi et al.’s research [19]. In the proposed scheme, a semiconductor laser source is utilized to generate optical chaos and conceals the EEG signal in the chaotic signal before transmission over the optical fiber. The generated data is then sent over optical fiber.
Applying chaotic modulation in intrinsic mode functions to encrypt medical ECG and EEG data is done in [20]. The results prove that the proposed method for encrypting and decrypting EEG and ECG signals containing chaotic behavior has satisfactory results.
In the research of Ibrahim et al. [21], medical image encryption was conducted using dynamic S-boxes and chaotic maps. Experimental results explicate that the proposed scheme has successfully passed all security tests in medical image encryption.
Gafsi et al. [22] proposed an improved chaotic system for medical image encryption. In this paper, a complex chaotic-based pseudorandom number generator (PRNG) has been designed to generate a high-quality encryption key. The generated key indicates the high complexity behavior of the approach.
In [23], a medical image encryption method has been proposed based on a chaotic map and fractional discrete cosine transform (FrDCT) coefficients. The proposed method comprises two steps of applying FrDCT on an image and, after that, a chaotic map on the coefficients.
The fourth-order chaotic system for clinical data encryption introduced in reference [24]. They calculated a variety of significant statistical parameters, such as correlation for the encrypted images in the proposed scheme.
An encryption algorithm based on the properties of block encryption, 4-dimensional logistics map and, DNA systems has been introduced by Stalin et al. [25]. In this method, multiple key sequences are generated first. In the second step, the pixel is substituted by a 4D nonlinear logistic map. Finally, encryption is performed using DNA rules to ensure that the various blocks are securely encrypted.
A chaotic system based on the Arnold cat method for medical images encryption in reference [26] is presented. The results demonstrate the high security and robustness of the proposed approach for secure medical image transmission.
In another research, Choi et al. [27] presented a secure and robust medical images encryption method. The proposed method include two permutations based on plain image and Latin square (PPILS) and bi-directional adaptive diffusion.
Choi et al. [28] proposed the NCA-based color medical image encryption algorithm and the generalized 3D chaotic cat map in another study. In this work, the NCA is an effective PRNG generating nonlinear pseudorandom sequences. Generalized 3D chaotic cat mapping is also adopted to create effective shuffle in encryption of color medical images.
A medical image encryption system based on multiple chaotic and message-digest algorithm 5 (MD5) has been discussed in [29]. The system employs two rounds of chaotic diffusion using XOR bit operation to encrypt an image. The results show that the proposed method is highly efficient in medical image encryption.
Designing a cryptographic algorithm based on pseudorandom sequence generation using a generalized double humped logistic map was done in [30], which ensures the transmission of magnetic resonance imaging (MRI) and X-ray images with high security. In this work, various statistical analyzes have been exploited.
Chaotic map-based authentication for telecare medicine information systems (TMISs) was examined by Li et al. in [31]. The results show that the proposed method presented in this paper can be applied in e-health services.
A method based on the integration of fused coupled chaotic map (FCCM) to encrypt ECG signals has been proposed in Pandey et al.’s study [32]. The FCCM generates four different chaotic maps based on control parameters. The effective-ness of the proposed approach has been confirmed using various analyzes, including key sensitivity, key space, correlation evaluation, and histogram analysis.
In the research of Sangavi et al. [33], the method (MMIE) using Rossler dynamical system and sine map (Sine) for medical image encryption has been proposed. For the method, statistical metrics such as histogram analysis, entropy, differential, and correlation have been computed.
Presented by researchers in [34] is an improved technique for medical image encryption based on discrete wavelet transform (DWT), discrete cosine transform (DCT) and, singular value decomposition (SVD) transformations. Additionally, the security of the method has been improved by exploiting 2D logistic maps based on chaotic cryptography.
In Zheng et al.’s [35] study, the data encryption standard (DES) and elliptic curves cryptography (ECC) algorithms are used for EEG signals. The results reveal that the ECC method has superior performance in encryption and decryption of EEG signals.
In this paper, a novel medical images encryption based on synchronization of hyper chaotic systems is presented. The main purpose of providing synchronization methods is to ad-just the controller parameters in chaotic systems properly. In order to synchronize, various control methods such as adaptive control [47,48], sliding mode [49,50], fuzzy [51,52], optimal [53,54], predictive [55,56], etc. have been proposed so far. Chaotic synchronization is such that the state paths of the following system follow the state paths of a base system [57,58].
Due to the numerous applications of synchronization, various other methods have been proposed that have different applications based on the existence of chaos and uncertainty in them. The following are some of the newest synchronization methods. In [59], the idea of synchronization based on the sliding mode control method and developing the advanced encryption standard algorithm is presented. Synchronization of chaotic systems based on additional Fourier modes is one of the newest methods proposed by [60]. Ding et al. [38] performed the encryption based on fractional-order Henon chaotic map and the discrete-time wavelet transform for a hyper-chaotic system. A new encryption idea based on the discrete-time sliding mode method and the improved El-Gamal encryption system is presented in [61]. Synchronization with the optimized proportional integral derivative (PID) controller with particle swarm optimization (PSO) algorithm is another new method in this field that has been introduced by [62].
In this paper, the main idea of medical image encryption is based on robust adaptive control. Also, the synchronization method is multi-mode. The multi-state synchronization with the presence of uncertainty, disturbance, unknowns, and variable parameters has been carried out. The proposed synchronization method is used alongside the Chen hyper chaotic system to encrypt medical images. In the provided example, one Chen hyper-chaotic system is considered as the master system, and two Chen hyper chaotic systems are considered as the slave systems. According to the simulations, the robustness of the proposed method and the convergence of all error types to zero verify its capabilities. In the following, taking the advantage of masking technique, it is possible to use the proposed synchronization method for medical images encryption. For encryption, first, a variety of standard benchmark images have been employed. Then, the chest CT and X-ray images of COVID-19 patients with various noises have been examined. Also, to accurately verify the performance of the proposed method, a variety of important cryptographic parameters including histogram analysis, correlation, differential attack, PSNR and information entropy of CT images with different noises have been calculated to represent the performance of the proposed method correctly. The results reveal that the synchronization technique of the proposed hyper-chaotic system for encrypting standard images and medical images has shown successful results and can therefore be adopted as an encryption section in a COVID-19 detection telemedicine system. The proposed approach is capable of encrypting other medical images.
In the following, other sections of the paper are presented. The second part is devoted to the theories of the proposed synchronization method. In the Section 3, the idea of encrypting medical images and standard benchmarks based on the chaotic masking method is expressed. The implementation of the proposed synchronization method on the Chen hyper-chaotic system is introduced in Section 4. The types of statistical parameters to show the efficiency of the proposed synchronization method in the encryption of different images are provided in the Section 5. The Section 6 is devoted to the results of the proposed method in encrypting medical images and standard benchmarks. The advantages and disadvantages of the proposed method are described in Section 7. Finally, the discussion and conclusion are presented in Section 8.
2. Formulation of the Theorem
This section first describes the problem of synchronization of multi-mode transitive chaotic systems. The multiple loop synchronization is then checked. In both cases, the adaptive laws and controllers are designed using the adaptive control method.
2.1. Comparative Synchronization between More Response Systems and a Master System
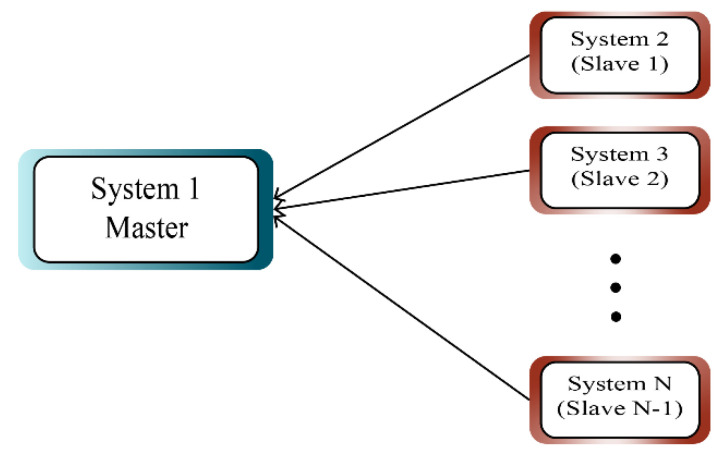
Figure 1 shows the synchronization model between a master system and several slave systems.
Figure 1.
Structure of transmission synchronization.
The master chaotic system is defined as follows [48]:
| (1) |
where is the state vector of the system. is the continuous function, is matrix function and is the main parameters of the master system, which are piecewise constant.
There are (N − 1) chaotic slave systems with control function as given by (2) [63]:
| (2) |
where is the state vector of the ith system, is the continuous function, is matrix function, are the main parameters which are piecewise constant of the ith slave system, and , is the control function of ith system. Therefore, according to Equations (1) and (2), synchronization of the chaotic system with the control function is as follows:
| (3) |
In the form of multiple synchronization mode, the synchronization error is defined as follows:
Definition 1.
Chaotic system (3) using the controllers and unknown parameters have multi-state transformative synchronization if the following condition is held:
where the error dynamic defined as follows:
(4) is met, then the adaptive transmission synchronization between N chaotic systems with unknown parameters is realized.
The design of controllers and adaptive laws to achieve the above goal is based on Lyapunov’s function, and the synchronization under the mode of transmission synchronization is performed. The control law for can be designed as follows:
(5) in which:
Therefore, error dynamics are given as follows:
(6) where is an approximation of and is an approximation error.
Theorem 1.
Transmission synchronization of chaotic systems (3) with controls (5), error dynamics (6) and update laws (9a), (9b), (10a), and (10b) is guaranteed.
Proof.
Consider the following Lyapunov function:
(7) The derivative of Lyapunov’s function (7) is obtained according to Equation (8)
(8) Therefore, the parameters laws are chosen as follows:
(9a)
(9b) If are constant then and the parameters estimation laws are determined as follows:
(10a)
(10b) By setting the estimation laws in (8), we will have:
(11) where and are Hurwitz. So system (6) is stable and 0. Therefore, obtain an adaptive synchronization between (N − 1) slave systems and a master system. □
Note 1.
If the systems are time varying: Equations (9a) and (9b) are still stablished, then in these cases the Theorem 1 is also established. Since the synchronization error converges to zero, the Equations (10a) and (10b) are converted as follows for relatively long periods of time:
Therefore, if is a vector with piecewise constant element and the appropriate time interval between changes in any element, the updating rule (10) is established and the parameters are estimated accurately. If then the update Equation (10) are also well established.
2.2. Circular Synchronization of Multiple Chaotic Systems with Unknown Parameters
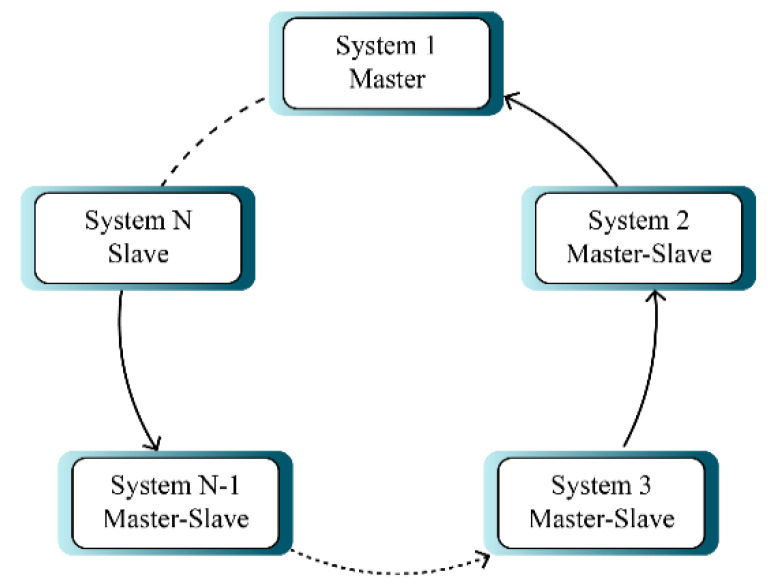
Figure 2 displays circular multi-mode synchronization. In this type of synchronization, systems 1 and N have the role of master and slave respectively and other systems both have the role of slave and master at the same time (i-th system is master role of i + 1-th system), which makes it more complex.
Figure 2.
Structure of circular synchronization.
According to Figure 2, the systems are synchronized with a circular structure. In this case, the first chaotic system is described by the following expression:
| (12) |
The (N − 1) chaotic systems are as follows:
| (13) |
The control input is
For N chaotic system described by Equation (13), if there are adaptive controllers, so that the error dynamics systems are defined as follows:
| (14) |
and condition:
is met then a circular synchronization between the N chaotic system and the unknown parameters is realized.
Theorem 2.
The following statements are used to synchronize in both circular and transmission modes.
- (A)
If there is a transmission and circular synchronization with the u(t) and m(t) controllers. Then:
- (B)
If transmission synchronization is established, circular synchronization is also realized and vice versa.
Proof.
Assume that a transmission synchronization is established, so: so:
If a circular synchronization is established (assuming ):
(15) □
Proof.
The following relationships between errors are established in two synchronization modes:
If a transmission synchronization is established, therefore:
So circular synchronization is established. Conversely, suppose a circular synchronization is established, therefore:
Therefore, transmission synchronization is also established. So the two types of synchronization are equivalent. □
Theorem 3.
The control law is same for transmission synchronization and circular synchronization. In other words: .
Proof.
Using the relationship between two types of errors:
Which is obtained by placing in Equations (2) and (14):
(16) For i = 1, we have:
By placing in Equation (16), we have: so the proof is completed. □
2.3. Synchronization with the Presence of Disturbance and Uncertainty in the System
In this case, the master and slave systems are accompanied by disturbance and uncertainty as follows:
| (17) |
where it is assumed that uncertainties and disturbances are bounded but with unknown bound.
where and di are constant but indefinite and is a definite function and in the special case. The dynamics of the errors are as follows:
| (18) |
By defining the control function as follows:
| (19) |
where is an estimate of and is part of the control function which is introduced below. By placing the control function in (18), the dynamics of errors are as follows:
| (20) |
Theorem 4.
The dynamic system of error Equation (20) under control Equation (19), Equation (25) and update laws Equations (29) and (31) is stable and synchronization errors are convergent to zero despite uncertainty and disturbance.
Proof.
by defining the Lyapunov function as follows:
(21) where:
By calculating the derivative of Lyapunov’s function:
(22) Note that for the same laws (9) and (10) are established, so Equation (22) becomes the following:
(23) If and are the component j of the vectors and then:
(24) Therefore:
(25) The bounded condition of disturbance and uncertainty can be developed on the components and as follows:
Which we have placed in the following equation.
(26) If is defined as follows:
(27) Then:
(28) By defining the estimation error: . The update laws are as follows:
(29a)
(29b)
(29c)
(29d) where and are positive values. By placing the above update laws in Equation (28) we have:
(30) where: .
Therefore, since are Hurwitz, the stability of the system is proved. Also, the convergence of synchronization errors to zero is guaranteed despite the uncertainty and disturbance. The laws for updating estimates will also be as follows:
(31a)
(31b)
(31c)
(31d) □
Note 2.
Theorems 2 and 3 are established in spite of uncertainty and disturbance, because the nature of proving them does not depend on the existence or non-existence of uncertainty and disturbance. Therefore, the problem of circular synchronization is also solved in the presence of uncertainty and disturbance.
Note 3.
If systems are time-varying: Equations (9a) and (9b) are still established, so in these circumstances the Theorem 4 is also established. Therefore, as stated in note 1: circular synchronization of time-varying chaotic systems is also proven in the presence of uncertainty and disturbance.
Note 4.
The following relation can be used to make the control function continuous:
(32)
Note 5.
If uncertainty forms are:then in update and control laws, it should be.
Note 6.
The final control function is as follows:
3. Application in Secure Communication Based on Chaotic Masking
In this scheme, the information signal is added to the linear composition of the master chaotic system state signals. Assuming that S(t) is the information signal carried by the master system, then the transmission message is defined as follows [64,65]:
| (33) |
In the given relation, denotes i-th component of the master system and the signal is masked using the chaotic signal. This signal is transmitted from the sender to the receiver through the communication channel. Adopting the proposed controller, multi-state chaotic synchronization is conducted on one of its states. Using Equation (34), the received signal can be recovered [66]:
| (34) |
| (35) |
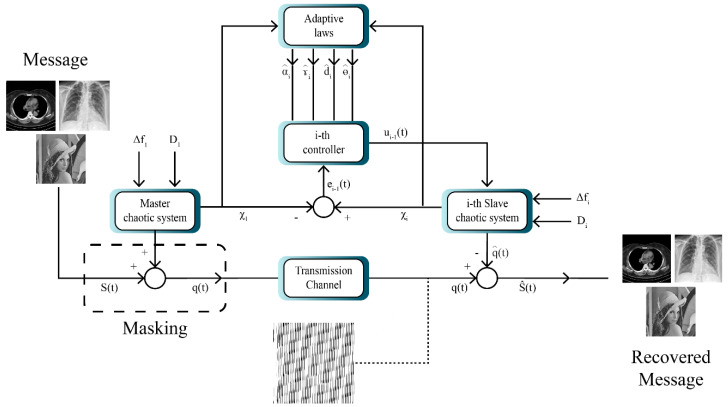
The multistate system for image masking is shown in Figure 3. According to Figure 3, the model entails a master system and several slave systems. Consequently, here the message is first transmitted to the master system. In the next step, the image is encrypted and synchronized using the slave system. Finally, after synchronization in the receiver, the image is decrypted and the original messages are recovered.
Figure 3.
Block diagram of chaotic masking with the aid of multi-state synchronization.
Utilizing the masking method, encryption and decryption of two signals are fulfilled using the proposed multi-state synchronization method. The simulation is executed with MATLAB software. Decryption and encryption are implemented after the synchronization of the master and slave chaotic systems in the presence of disturbance and uncertainty. To that end, the given image is first converted into a signal. In the next step, this signal is added to one of the components of the master system state vector and is transmitted to the receiver through a communication channel. In the receiver part, first using the synchronization, the message signal is extracted from the chaotic signal and then converted into an image.
4. Implementation of the Proposed Synchronization Method on Chen Hyper-Chaotic System
A Chen hyper- chaotic system is considered as a master system and two Chen hyper chaotic systems are considered as slaves. They are defined as follows:
Slave systems:
In all examples, the parameters are set as follows:
Case A. Multi-mode synchronization with time-varying parameters (without disturbance and uncertainty).
For parameter values, all systems are chaotic as follows:
In the simulation of the basic conditions, the master system and two slave systems are selected as follows:
|
(x11(0), x12(0), x13(0), x14(0)) = (10, 10, 10, 10) (x21(0), x22(0), x23(0), x24(0)) = (2, 2, 2, 2) (x31(0), x32(0), x33(0), x34(0)) = (3, 3, 3, 3) |
The initial values of the parameters are assumed to be as follows:
The main parameters over time are in the form of variable steps and as follows:
For a time from zero to 2 s:
| θ11 = 35, 12θ = 7, 21θ = 35, 22θ = 7, 31θ = 35, 32θ = 7 |
For a time from 2 to 6 s:
| 13θ = 12, 14θ = 3, 15θ = 0.3, 23θ = 12, 24θ = 3, θ25 = 0.3, 33θ = 12, 34θ = 3, 35θ = 0.3, |
For a time from 2 to 5 s:
| 11θ = 33, 12θ = 6, 21θ = 32, 22θ = 5, 31θ = 34, 32θ = 5, |
For a time from 6 to 10 s:
| 13θ = 13 14θ = 1, 15θ = 0.1, 23θ = 12, 24θ = 5, θ25 = 0.2, 33θ = 10, 34θ = 2, 35θ = 0.2, |
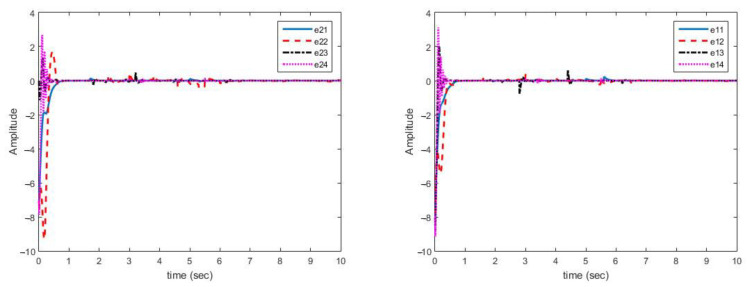
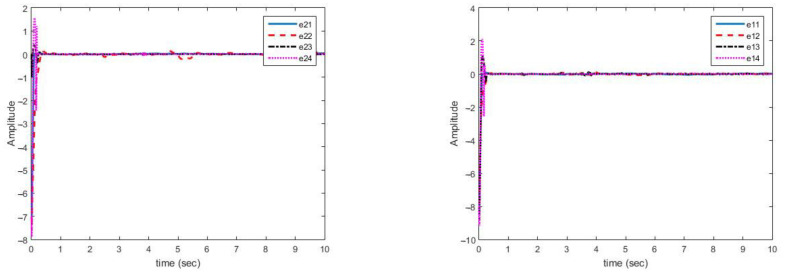
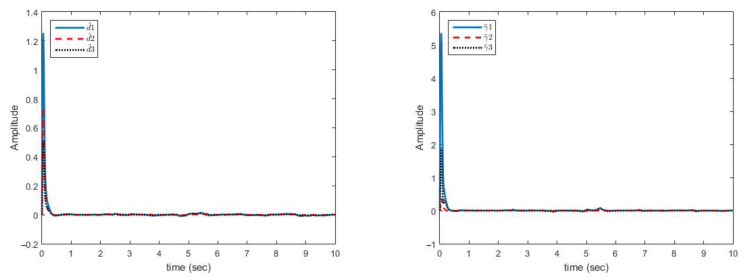
Figure 4 shows that synchronization errors in presence of uncertainty and disturbances are quickly converged to zero. On the other hand, parameter changes have little effect on synchronization errors and are quickly attenuated.
Figure 4.
Multi-state synchronization error curves (case A).
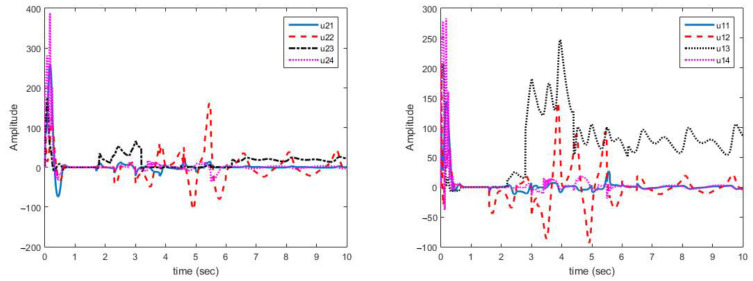
Figure 5 shows that control laws are continuous functions prevent the phenomenon of chattering.
Figure 5.
Multi-mode synchronization control effort curves (case A).
As displayed in Figure 4, synchronization of chaotic systems as the main objective is well carried out and synchronization errors converge to zero despite changes in parameters.
As shown in Figure 5, the obtained control signals are continuous. In addition, changes in the parameters are met with a rapid reaction in the control signals to converge the synchronization errors to zero.
Case B. Multi-mode synchronization with time-varying parameters despite disturbance and uncertainty. In this case, disturbance and uncertainties are applied to master and slave systems as follows:
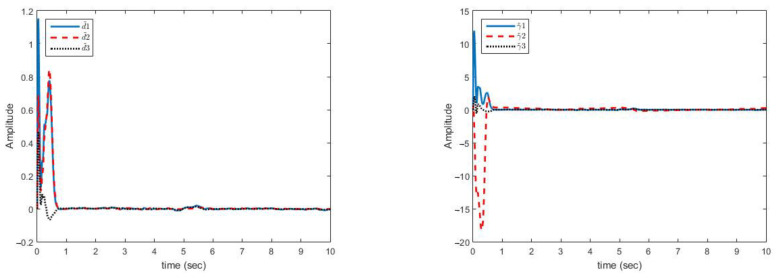
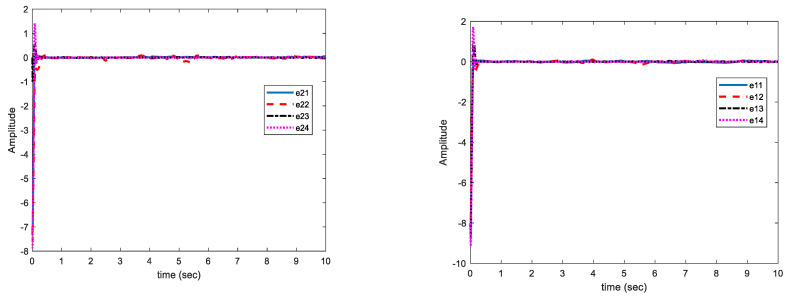
In this case, the change in parameters is similar to case (A). Figure 6 shows the estimation of variable parameter of the system. It can be noted that, estimating time-varying parameters in the presence of uncertainty and disturbance is correctly done.
Figure 6.
Synchronization error curves for disturbance and structural uncertainty (case B).
Figure 6 shows the multi-mode synchronization errors despite the structural uncertainty and disturbance. We have obtained good performance as the synchronization errors are close to zero. Multi-mode synchronization errors for both master and slave systems, despite disturbance and uncertainties, have quickly reached to zero. Subsequently, change in the parameter causes small errors, which quickly converges to zero (Figure 7).
Figure 7.
Estimation error curves of bounds related to uncertainties (right) and disturbances (left)—(case B).
As can be seen in Figure 6, the synchronization of chaotic systems as the main aim is well done, and the synchronization errors converge to zero despite changes in parameters, presence of disturbance, and uncertainty.
Case C. Multi-mode synchronization, taking into account the disturbance and uncertainties bounded with the function:
For the case C
In this case, the change in parameters is similar to case (A), the disturbances are similar to case (B) and uncertainties are not bounded with norm of states but bounded with a function of state norms. This increases the control problem complexity. In Figure 8, the multi-mode synchronization error in case (C) shows that despite the time-varying parameters, the functional bounded uncertainty and disturbance converge to zero.
Figure 8.
Curves of synchronization errors in case of disturbance and structural uncertainty of case (C).
As displayed in Figure 8, the synchronization of chaotic systems as the main objective is well fulfilled, and in spite of changes in parameters, the presence of disturbance, and uncertainty, synchronization errors are converged to zero.
Figure 9 shows that the estimation errors of uncertainties are more fluctuating than in case (B) but are close to zero. Estimation errors of disturbance and uncertainty bounds have reached zero with low fluctuations. The uncertainties are complex functions. The peaks appear in the figures only when the parameters have changed. However, over a short period of time, the magnitude of curves are decreased and eventually approached to zero. The proposed approach is able to reject uncertainties bounded with polynomial of state norms and unknown non-negative coefficients.
Figure 9.
Estimation error curves for uncertainty (right) and disturbance (left) case (C).
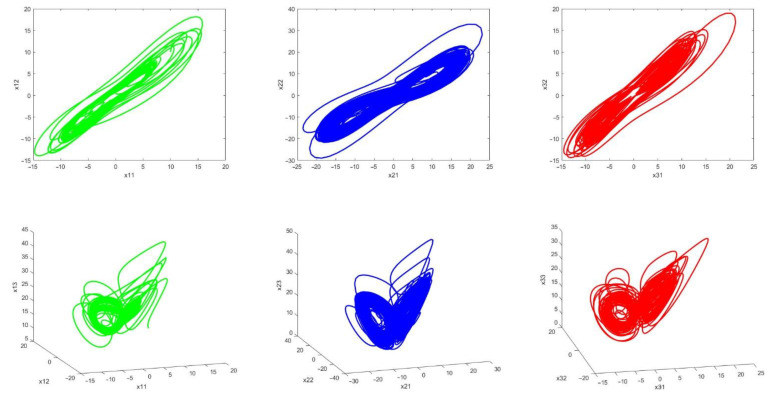
The chaotic behavior of systems is shown in Figure 10. The above figures exhibit the chaotic behavior of the master (green) and slave systems (blue and red). The presence of disturbance and uncertainty as well as changes in system parameters make the system behavior more complex.
Figure 10.
Phase curves for master chaotic system (green), Slave 1 (blue) and slave 2 (red) chaotic systems.
Chaotic behavior leads to the complicatedness of secure communications method and the possibility of detecting it is so low because in chaotic systems, in addition to uncertainty and disturbance, its parameters are assumed to be variable, which promotes the security of the approach.
5. Statistical Metrics
5.1. Histogram Analysis
In image processing, the histogram represents the distribution of the pixel values of an image. Histogram variance is employed in image encryption. In this manner, low variance values indicate higher uniformity in encrypted images. The variance of histograms is expressed by Equation (36) [24]:
| (36) |
According to Equation (36), I denotes the vector of histogram values, Ii and Ij indicate the number of pixels whose gray values are equal to i and j, respectively [24].
5.2. Correlation Analysis
Correlation distributions and correlation coefficients play a crucially significant role in the analysis of encrypted images, which are discussed in this section. The following statements are taken into account to calculate these values [24]:
| (37) |
5.3. Differential Attack Analysis
Pixel change rate (NPCR) and unified average changing Intensity (UACI) are two other important measurable parameters in image encryption, whose relationships of each are shown below [24]:
| (38) |
| (39) |
Evaluation of encrypted images by NPCR and UACI parameters is depicted in Table 1, Table 2, Table 3, Table 4 and Table 5. The results reveal that a swift change in the original image leads to a change in the ciphered image. This signifies that the proposed scheme has a high ability to resist differential attack [24].
Table 1.
Statistical metrics for CT modality without noise.
| Images | Histogram | Correlation | Differential Attack | PSNR | Information Entropy | ||
|---|---|---|---|---|---|---|---|
| Standard | Encrypted | NPCR (%) | UACI (%) | ||||
| Image 1 | 1,555,164 | 3,375,508 | 0.9970 | 99.611 | 33.461 | 34.623 | 5.5081 |
| Image 2 | 1,942,777 | 5,880,577 | 0.9964 | 99.610 | 33.460 | 33.186 | 5.2665 |
| Image 3 | 2,926,366 | 6,511,850 | 0.9976 | 99.609 | 33.463 | 34.982 | 4.8647 |
| Image 4 | 1,969,829 | 5,299,018 | 0.9954 | 99.611 | 33.459 | 33.182 | 5.077 |
| Image 5 | 2,776,087 | 5,805,249 | 0.9967 | 99.610 | 33.460 | 34.945 | 4.6828 |
| Image 6 | 1,983,221 | 5,394,168 | 0.9956 | 99.610 | 33.462 | 33.198 | 5.0558 |
| Image 7 | 3,108,704 | 6,811,427 | 0.9974 | 99.611 | 33.460 | 35.053 | 4.5683 |
| Image 8 | 2,783,671 | 8,248,927 | 0.9958 | 99.610 | 33.460 | 33.483 | 4.5248 |
| Image 9 | 2,887,118 | 6,433,437 | 0.9976 | 99.612 | 33.461 | 34.979 | 4.7115 |
| Image 10 | 1,168,385 | 3,379,135 | 0.9956 | 99.610 | 33.463 | 32.850 | 5.6934 |
Table 2.
Statistical metrics for CT Modality (Gaussian noise with 0.001 variance).
| Images | Histogram | Correlation | Differential Attack | PSNR | Information Entropy | ||
|---|---|---|---|---|---|---|---|
| Standard | Encrypted | NPCR (%) | UACI (%) | ||||
| Image 1 | 371,790.95 | 414,854.68 | 0.9965 | 99.611 | 33.459 | 34.146 | 6.4966 |
| Image 2 | 637,672.20 | 775,806.22 | 0.9958 | 99.609 | 33.461 | 32.599 | 5.9531 |
| Image 3 | 704,174.55 | 770,799.32 | 0.9969 | 99.610 | 33.462 | 34.284 | 5.8406 |
| Image 4 | 655,672.19 | 823,316.52 | 0.9941 | 99.612 | 33.459 | 32.583 | 5.7021 |
| Image 5 | 711,500.39 | 800,070.88 | 0.9959 | 99.608 | 33.460 | 34.286 | 5.5608 |
| Image 6 | 658,916.62 | 837,271.82 | 0.9944 | 99.611 | 33.461 | 32.603 | 5.6814 |
| Image 7 | 764,189.21 | 849,713.85 | 0.9966 | 99.612 | 33.463 | 34.304 | 5.5387 |
| Image 8 | 910,672.69 | 1,120,143.86 | 0.9942 | 99.611 | 33.462 | 32.728 | 5.3159 |
| Image 9 | 712,326.25 | 774,208.57 | 0.9969 | 99.613 | 33.458 | 34.276 | 5.6761 |
| Image 10 | 377,977.28 | 471,233.22 | 0.9948 | 99.611 | 33.461 | 32.426 | 6.4675 |
Table 3.
Statistical metrics for CT Modality (Gaussian noise with 0.003 variance).
| Images | Histogram | Correlation | Differential Attack | PSNR | Information Entropy | ||
|---|---|---|---|---|---|---|---|
| Standard | Encrypted | NPCR (%) | UACI (%) | ||||
| Image 1 | 239,642.29 | 273,559.38 | 0.9963 | 99.611 | 33.461 | 34.052 | 6.6729 |
| Image 2 | 399,917.39 | 493,824.29 | 0.9954 | 99.609 | 33.462 | 32.376 | 6.2428 |
| Image 3 | 439,060.82 | 492,967.11 | 0.9967 | 99.613 | 33.458 | 34.141 | 6.1468 |
| Image 4 | 453,864.31 | 566,619.14 | 0.9937 | 99.610 | 33.460 | 32.416 | 5.9343 |
| Image 5 | 490,271.52 | 542,562.67 | 0.9956 | 99.611 | 33.461 | 34.115 | 5.8208 |
| Image 6 | 450,636.56 | 557,774.79 | 0.9939 | 99.612 | 33.459 | 32.399 | 5.9312 |
| Image 7 | 505,486.28 | 558,333.49 | 0.9963 | 99.613 | 33.463 | 34.156 | 5.8280 |
| Image 8 | 585,431.25 | 723,173.69 | 0.9936 | 99.609 | 33.462 | 32.481 | 5.6384 |
| Image 9 | 456,812.35 | 501,600.98 | 0.9966 | 99.611 | 33.462 | 34.120 | 5.9823 |
| Image 10 | 244,061.98 | 307,606.74 | 0.9944 | 99.612 | 33.460 | 32.263 | 6.6424 |
Table 4.
Statistical metrics for CT Modality (Gaussian noise with 0.006 variance).
| Images | Histogram | Correlation | Differential Attack | PSNR | Information Entropy | ||
|---|---|---|---|---|---|---|---|
| Standard | Encrypted | NPCR (%) | UACI (%) | ||||
| Image 1 | 183,606.33 | 207,963.36 | 0.9961 | 99.611 | 33.461 | 33.975 | 6.7881 |
| Image 2 | 287,175.67 | 347,957.53 | 0.9951 | 99.610 | 33.459 | 32.271 | 6.4632 |
| Image 3 | 318,969.51 | 351,484.97 | 0.9965 | 99.608 | 33.458 | 34.027 | 6.3680 |
| Image 4 | 353,759.37 | 420,480.95 | 0.9934 | 99.611 | 33.462 | 32.302 | 6.1234 |
| Image 5 | 379,975.17 | 413,399.53 | 0.9954 | 99.609 | 33.457 | 34.054 | 6.0266 |
| Image 6 | 347,921.57 | 414,116.53 | 0.9936 | 99.611 | 33.456 | 32.304 | 6.1326 |
| Image 7 | 381,476.11 | 422,535.34 | 0.9962 | 99.612 | 33.461 | 34.097 | 6.0471 |
| Image 8 | 435,904.80 | 517,108.82 | 0.9932 | 99.610 | 33.460 | 32.354 | 5.8833 |
| Image 9 | 333,557.81 | 368,586.44 | 0.9965 | 99.611 | 33.459 | 34.073 | 6.2279 |
| Image 10 | 185,554.28 | 227,767.28 | 0.9942 | 99.607 | 33.454 | 32.185 | 6.7663 |
Table 5.
Statistical metrics for CT Modality (Gaussian noise with 0.009 variance).
| Images | Histogram | Correlation | Differential Attack | PSNR | Information Entropy | ||
|---|---|---|---|---|---|---|---|
| Standard | Encrypted | NPCR (%) | UACI (%) | ||||
| Image 1 | 160,406.07 | 181,599.02 | 0.9961 | 99.609 | 33.459 | 33.965 | 6.8530 |
| Image 2 | 234,952.50 | 276,693.14 | 0.9950 | 99.611 | 33.461 | 32.237 | 6.6058 |
| Image 3 | 262,347.29 | 294,388.46 | 0.9964 | 99.608 | 33.458 | 34.007 | 6.5026 |
| Image 4 | 300,806.96 | 345,570.37 | 0.9931 | 99.610 | 33.457 | 32.204 | 6.2599 |
| Image 5 | 319,370.10 | 347,968.94 | 0.9953 | 99.612 | 33.462 | 34.046 | 6.1673 |
| Image 6 | 295,654.72 | 341,419.34 | 0.9934 | 99.607 | 33.457 | 32.213 | 6.2688 |
| Image 7 | 320,298.48 | 349,954.05 | 0.9960 | 99.611 | 33.459 | 33.995 | 6.1951 |
| Image 8 | 364,283.38 | 423,633.80 | 0.9930 | 99.609 | 33.462 | 32.290 | 6.0396 |
| Image 9 | 276400.42 | 307161.05 | 0.9964 | 99.610 | 33.460 | 34.000 | 6.3806 |
| Image 10 | 162565.94 | 191476.22 | 0.9940 | 99.612 | 33.461 | 32.139 | 6.8390 |
5.4. PSNR Analysis
PSNR (peak signal to noise ratio) is the ratio of peak signal power to noise power. An encryption method achieves successful performance when the encrypted image has a low PSNR. PSNR relationships are described below [24]:
| (40) |
where MSE is the mean squared error and MAXI is the maximum possible pixel value of the image [24].
5.5. Information Entropy Analysis
Information entropy is another image analysis procedure in cryptographic applications and is defined as follows [24]:
| (41) |
6. Experiment Results
The results of images encryption based on the synchronization method of the proposed chaotic systems are yielded in this section. In the following, first, the images used to perform the experiments are introduced. Then, the results of the proposed approach are expressed by application.
6.1. Image Benchmarks
In this paper, in order to evaluate the proposed cryptographic method, multiple medical images and benchmarks have been adopted. The images tested in this section contain a variety of standard benchmark images and medical images including CT and X-ray. In Figure 11, 10 images of standard benchmarks for conducting experiments are displayed. Also, shown in Figure 12 are X-ray images of COVID-19 patients. Finally, 10 CT images of patients with COVID-19 are used for the final tests, as shown in Figure 13.
Figure 11.
Standard benchmark images used in the proposed method.
Figure 12.
X-ray images used in the proposed method.
Figure 13.
CT images used in the proposed method.
6.2. Simulation
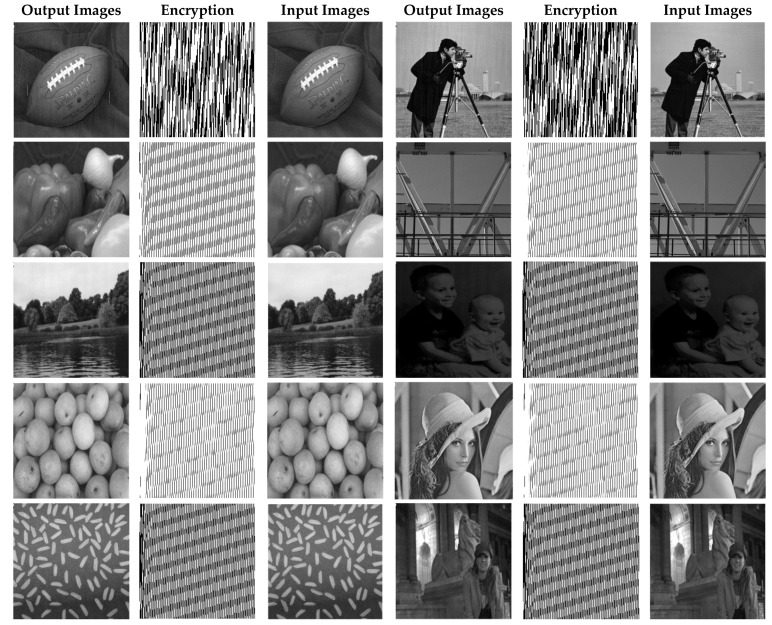
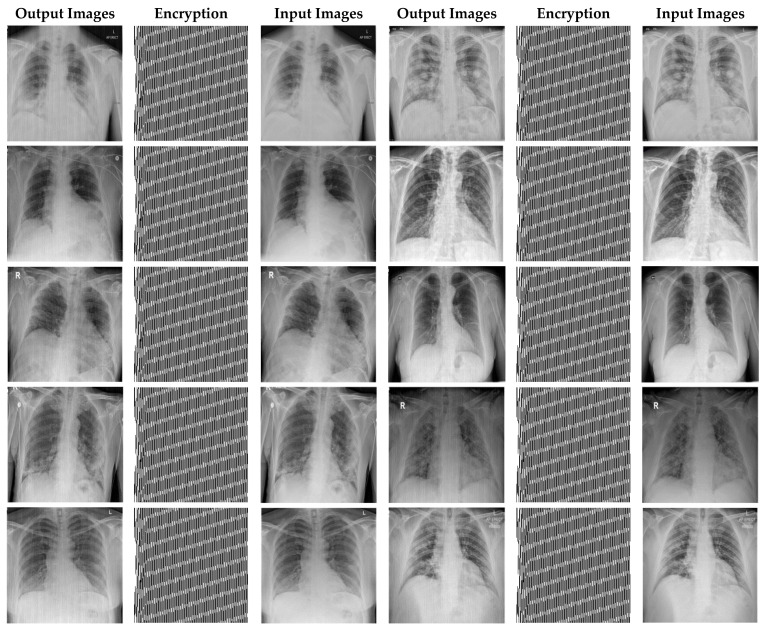
In this section, the results of the proposed synchronization method of chaotic systems for various images encryption are discussed. All images utilized in this research have a size of 300 × 300 in png format. Figure 14, Figure 15 and Figure 16 show encrypted images of standard benchmark, X-ray, and CT patients with COVID-19, respectively.
Figure 14.
Standard benchmarks images encryption using the proposed method.
Figure 15.
X-ray images encryption using the proposed method.
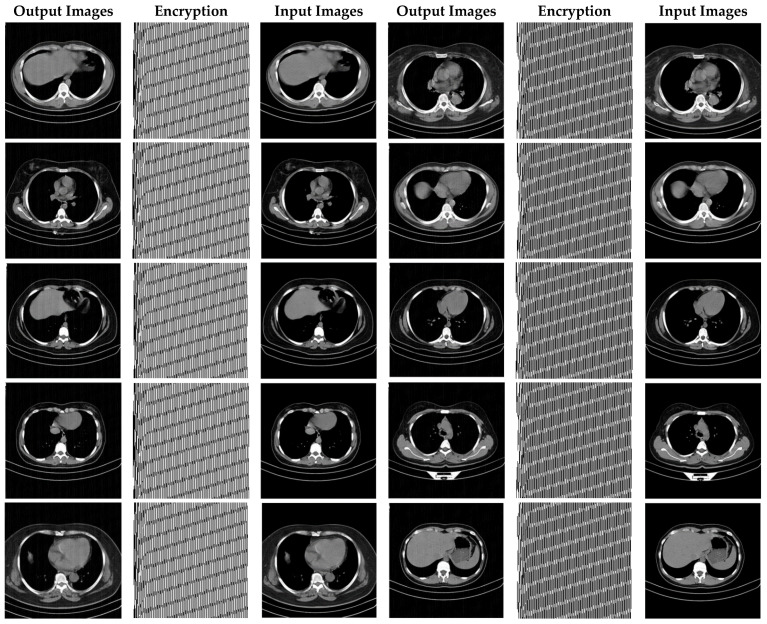
Figure 16.
CT images encrypted using the proposed method.
The results of the proposed chaotic synchronization method for famous benchmark images encryption are shown in Figure 14. As it is manifest, the ten selected images have different contrasts, and the results displayed in Figure 14 verify the high effectiveness of the proposed techniques in the encryption of these images.
In Figure 15, X-ray images of patients with COVID-19 for cryptography are exploited. According to Figure 13, it can be seen that the synchronization method of the proposed chaotic system also achieves highly successful outcomes in X-ray images encryption.
Figure 16 demonstrates the various CT encrypted images. According to the figure, the CT images are first fed to the input of the proposed chaotic synchronization method. CT images encrypted are then generated. Finally, reconstructed CT images are represented. According to Figure 16, it can be seen that the cryptographic procedure based on synchronization of the proposed chaotic system achieves successful results.
As can be observed in Figure 16, the recommended method has also been very successful in CT images encryption of people with COVID-19. Additionally, with a conclusion, it is perceived that the cryptographic method based on synchronization of chaotic systems presented in this paper for various medical images and standard benchmarks achieves satisfactory results.
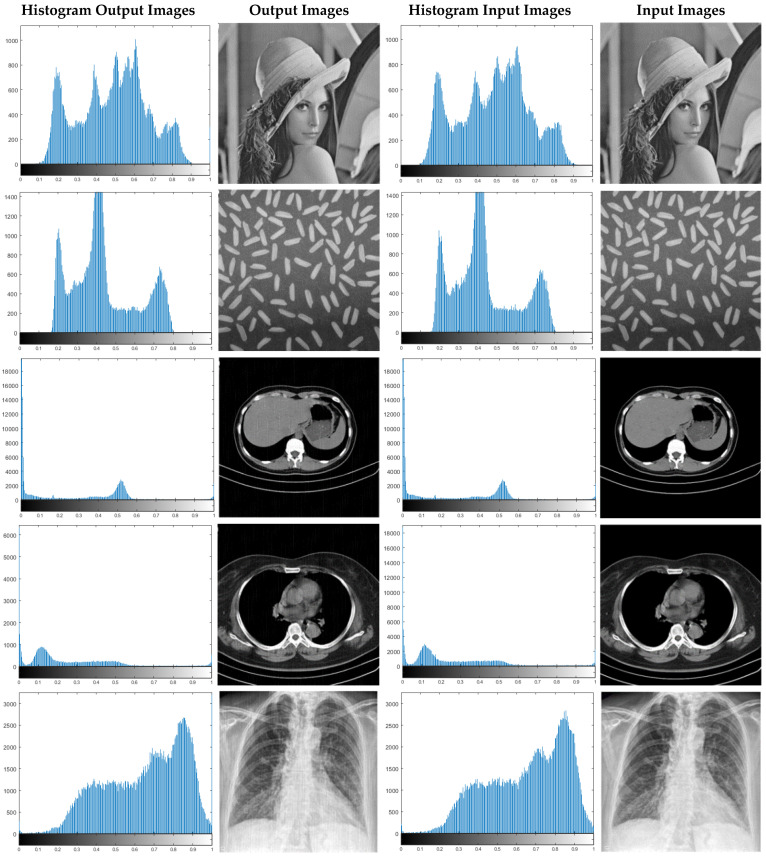
In Figure 17, a number of standard X-ray and CT images are randomly selected and their histogram diagrams are drawn. According to Figure 17, histograms related to input and decoded images are displayed.
Figure 17.
Displayed histograms for various images encrypted using the proposed method.
In Figure 17, histogram diagrams of the number of the original input images and encrypted images are illustrated. The results show that the histograms of the input and decoded images are very close to each other. This means that the proposed synchronization method of the chaotic system has performed highly successfully in encrypting and recovering various images. For further experiments, Gaussian noises with different variances have been applied to CT images. Then, the types of statistical parameters of Section 5 are calculated for them. CT images have been corrupted by Gaussian noise with 0.001, 0.003, 0.006, and 0.009 variances, and the results of their statistical analysis are shown in Table 1, Table 2, Table 3, Table 4 and Table 5.
In Table 1, the results of the proposed methodology have been yielded on CT images without noise. As can be seen, this method has statistically satisfactory results in CT cryptography of patients with COVID-19.
In Table 2, the results of the synchronization method of chaotic systems for CT images with Gaussian noise with 0.001 variance are shown. The results in this table prove that the proposed method for encrypting CT images with Gaussian noise with 0.001 variance has been successful.
Table 3 indicates the statistical results of the proposed synchronization approach for CT images cryptography of COVID-19 patients with Gaussian noise (variance 0.003). It can be perceived that the proposed technique has been functioned successfully in encrypting these noise-corrupted CT images.
The findings of CT images encryption corrupted by Gaussian noise with 0.006 variance are given in Table 4. It is obvious that the proposed scheme for CT images for Gaussian noise with 0.006 variance compared to the previous modes has been able to report good results.
Finally, in Table 5 the results of the proposed method cryptography with CT images for Gaussian noise with 0.009 variance have been illustrated. From the results in this table, it can be seen that the proposed synchronization method is also robust to this type of Gaussian noise in CT images encryption.
7. Advantages and Disadvantages
The proposed method has the ability to deal with uncertainty, disturbance, and changes in system parameters. On the other hand, the resulting control functions are continuous, which prevents the chattering problems. The only problem with our proposed algorithm is the large magnitude of few control functions. In the future, we intend to develop the proposed method for synchronization of chaotic and hyper-chaotic fractional-order systems. Using an objective function as the total of control norms can reduce the magnitude of control functions.
The proposed method has strengths from various perspectives, the most important of which are discussed in the following. Ensuring the synchronization error converges to zero, which is the most mattering objective in the synchronization issue. These errors converge to zero in a short period of time, despite uncertainty and disturbance, as well as changes in the master and slave systems. Providing a continuous control function that prevents the occurrence of the chattering phenomenon. Proving the equivalence of control functions in two synchronization methods is another significant result. Finally, according to the conducted analysis, the resulting procedure has good robustness against noise, which is one of the most important outcomes of this paper.
Also, the disadvantages of the proposed method are expressed in this paragraph. In the proposed approach, there are some constraints, which incorporate: large control signal that increases the cost of synchronization. On the other hand, there is no physical factor and a significant delay in the master and slave systems. Ideal communication channel, as well as parameter changes that are considered stepwise, are other limitations of this method.
8. Discussion and Conclusions
Today, telemedicine is employed in a variety of medical applications. In all telemedicine systems, the issue of information security is vitally significant. To this end, various approaches for the information security of these systems have been presented so far [12]. Cryptography based on chaotic theory is one of the best approaches to protect the information in secure communications.
Encryption techniques based on chaos theory in medicine have also attracted the attention of many. In the control field, it has been proven that synchronization techniques of hyper chaotic systems to enhance information security have reported remarkably successful outcomes [54,55,56,66]. In this paper, for the first time, a novel multi-mode synchronization of a chaotic system has been utilized to encrypt medical images of CT and X-ray for COVID-19 patients. This method can be employed as an encryption section in the various telemedicine systems.
In this paper, the multi-mode synchronization of two hyper chaotic systems in two forms of multi slave, and one master system synchronization and circular synchronization are examined. Firstly, it is proved that two forms of synchronizations are equivalent and control laws are exactly equal. The adaptive control method and the definition of appropriate Lyapunov function are used for synchronization. The convergence of synchronization errors to zero is ensured despite variable parameters with time and disturbance, and uncertainty is bounded with a known function. Adaptive laws to estimate the system-time-varying parameters, disturbance, and uncertainty bounds, are also determined to ensure that the system stability is guaranteed. For preventing the phenomenon of chattering, the law of controls is established as a continuous function. To test the effectiveness of the proposed method, simulations are performed in the presence of structural uncertainty and disturbance. The results show that the proposed controller is able to perform efficiently by yielding zero errors for synchronization, estimations of disturbance, and uncertainty bounds.
After implementing the proposed multi-mode synchronization method, subsequently, medical image encryption of COVID-19 patients has been fulfilled. To verify the efficiency of the recommended method, CT images were corrupted by Gaussian noise with different variances and the statistical analysis results revealed the effectiveness of the proposed approach.
The advantages of the method involve synchronization in the presence of disturbance and uncertainty, which indicates its robustness. Using the Lyapunov function, which guarantees the convergence of all types of errors, including synchronization error and the estimation error to zero. On the other hand, the variables of the system are another great issue that makes the synchronization problem more complicated, and finally, the images are encrypted with high security, which is very difficult to detect. In Table 6, the advantages of the proposed method are compared with other researches in this field.
Table 6.
Comparison of the proposed method with other related works.
| Properties Encryption Method | Encryption Method | Data Types | Works | ||
|---|---|---|---|---|---|
| Disturbance | Unknown Parameter | Uncertainty | |||
| ✕ | ✕ | ✕ | Chaos Logic Map | EEG Signals | [17] |
| ✕ | ✕ | ✕ | Double Chaotic Layer Encryption (DCLE) | EEG, ECG Signals | [18] |
| ✕ | ✕ | ✕ | Optical Chaos (Additive Chaos Masking) | EEG Signals | [19] |
| ✕ | ✕ | ✕ | Chaotic Modulation on the Intrinsic Mode Functions | EEG, ECG Signals | [20] |
| ✕ | ✕ | ✕ | Dynamic S-Boxes and Chaotic Maps | Medical Images | [21] |
| ✕ | ✕ | ✕ | Improvement Chaotic System | Medical Images | [22] |
| ✕ | ✕ | ✕ | chaotic Map + Fractional Discrete Cosine Transform (FrDCT) Coefficients | Medical Images | [23] |
| ✕ | ✕ | ✕ | Fourth Order Chaotic System | Medical Images | [24] |
| ✕ | ✕ | ✕ | Non Linear 4D Logistic Map and DNA Sequences (NL4DLM_DNA) | Medical Images | [25] |
| ✕ | ✕ | ✕ | Chaotic Method Based on Arnold’s Cat Map | MRI Images | [26] |
| ✕ | ✕ | ✕ | Latin Square + Memristive Chaotic System | Medical Images | [27] |
| ✕ | ✕ | ✕ | 3D Chaotic Cat Map + NCA | Medical Images | [28] |
| ✕ | ✕ | ✕ | Multiple Chaotic Systems + MD5 | Medical Images | [29] |
| ✕ | ✕ | ✕ | Double-Humped Logistic Map | MRI, X-ray Images | [30] |
| ✕ | ✕ | ✕ | Chaotic Map-based Remote Authentication Scheme | Medical Informatics | [31] |
| ✕ | ✕ | ✕ | Fused Coupled Chaotic Map (FCCM) | ECG Signals | [32] |
| ✕ | ✕ | ✕ | Rossler Dynamical Chaotic system + Sine Map | Medical Images | [33] |
| ✕ | ✕ | ✕ | DWT, DCT, SVD + Chaotic System | MRI Images | [34] |
| ✕ | ✕ | ✕ | Data Encryption Standard (DES), and Elliptic Curves Cryptography (ECC) | EEG Signals | [35] |
| Chen Hyper-Chaotic System + Adaptive-Robust Multi-Mode Synchronization | Medical Images (CT, X-ray), Standard Benchmarks | Proposed Method | |||
According to Table 6, the proposed method has more advantages than other proposals in the field of medical data encryption using chaotic methods.
For future work, the proposed method can be utilized to encrypt EEG signals of epileptic seizures [67,68], attention deficit hyperactivity disorder (ADHD) [69,70], schizophrenia [71,72], and multiple sclerosis [73]. Additionally, the technique presented in this study can be adopted to encrypt MRI [74,75], X-ray [76], mammography [77,78], and other medical data [79,80,81,82,83,84].
In the continuation of this paper in order to develop and eliminate deficiencies such as applying optimal control to synchronize with less control effort and considering the important factor of delay in master and slave systems as well as method extension for fractional-order systems in which case the complexity of the control method increases and the security of the method is enhanced. For another future works, due to the fact that medical data has uncertainty, neuro fuzzy, fuzzy type1 or fuzzy type 2 systems can be used [85,86,87,88,89,90].
Author Contributions
Conceptualization, A.A.K.J. and A.S.; methodology, A.Z., A.A.K.J., A.S. and J.M.G.; software, A.A.K.J. and A.S.; validation, A.Z. and A.A.K.J.; formal analysis, A.S., R.A., M.K. and N.G.; resources, A.Z. and A.A.K.J.; writing—original draft preparation, A.A.K.J., A.S., R.A. and M.J.; writing—review and editing, A.S., A.Z., M.K., J.M.G., N.G. and M.J.; visualization, A.Z., A.A.K.J., and A.S. All authors have read and agreed to the published version of the manuscript.
Funding
This work was partly supported by the MINECO/ FEDER under the RTI2018-098913-B100 CV20-45250 and A-TIC- 080-UGR18 projects.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Footnotes
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Fadhil A. Beyond patient monitoring: Conversational agents role in telemedicine & healthcare support for home-living elderly individuals. arXiv. 20181803.06000 [Google Scholar]
- 2.Wijesinghe I., Gamage C., Perera I., Chitraranjan C. A smart telemedicine system with deep learning to manage diabetic retinopathy and foot ulcers; Proceedings of the 2019 Moratuwa Engineering Research Conference (MERCon); Moratuwa, Sri Lanka. 3–5 July 2019; pp. 686–691. [Google Scholar]
- 3.Leite H., Hodgkinson I.R., Gruber T. New development: ‘Healing at a distance’—Telemedicine and COVID-19. Public Money Manag. 2020;40:483–485. doi: 10.1080/09540962.2020.1748855. [DOI] [Google Scholar]
- 4.Portnoy J., Waller M., Elliott T. Telemedicine in the era of COVID-19. J. Allergy Clin. Immunol. Pract. 2020;8:1489–1491. doi: 10.1016/j.jaip.2020.03.008. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Angelucci A., Kuller D., Aliverti A. A home telemedicine system for continuous respiratory monitoring. IEEE J. Biomed. Health Inform. 2020;25:1247–1256. doi: 10.1109/JBHI.2020.3012621. [DOI] [PubMed] [Google Scholar]
- 6.Garg V., Brewer J. Telemedicine security: A systematic review. J. Diabetes Sci. Technol. 2011;5:768–777. doi: 10.1177/193229681100500331. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Abou El Kalam A., Ferreira A., Kratz F. Bilateral teleoperation system using QoS and secure communication networks for telemedicine applications. IEEE Syst. J. 2015;10:709–720. doi: 10.1109/JSYST.2015.2422992. [DOI] [Google Scholar]
- 8.Rezaeibagha F., Mu Y. Practical and secure telemedicine systems for user mobility. J. Biomed. Inform. 2018;78:24–32. doi: 10.1016/j.jbi.2017.12.011. [DOI] [PubMed] [Google Scholar]
- 9.Murillo-Escobar M.A., Meranza-Castillón M.O., López-Gutiérrez R.M., Cruz-Hernández C. Suggested integral analysis for chaos-based image cryptosystems. Entropy. 2019;21:815. doi: 10.3390/e21080815. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Alvarez G., Li S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos. 2006;16:2129–2151. doi: 10.1142/S0218127406015970. [DOI] [Google Scholar]
- 11.Mirrezapour S.Z., Zare A. A new fractional sliding mode controller based on nonlinear fractional-order proportional integral derivative controller structure to synchronize fractional-order chaotic systems with uncertainty and disturbances. J. Vib. Control. 2021 doi: 10.1177/1077546320982453. [DOI] [Google Scholar]
- 12.Kekha Javan A.A., Shoeibi A., Zare A., Hosseini Izadi N., Jafari M., Alizadehsani R., Moridian P., Mosavi A., Acharya U.R., Nahavandi S. Design of Adaptive-Robust Controller for Multi-State Synchronization of Chaotic Systems with Unknown and Time-Varying Delays and Its Application in Secure Communication. Sensors. 2021;21:254. doi: 10.3390/s21010254. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 13.Zare A., Mirrezapour S.Z., Hallaji M., Shoeibi A., Jafari M., Ghassemi N., Alizadehsani R., Mosavi A. Robust Adaptive Synchronization of a Class of Uncertain Chaotic Systems with Unknown Time-Delay. Appl. Sci. 2020;10:8875. doi: 10.3390/app10248875. [DOI] [Google Scholar]
- 14.Pecora L.M., Carroll T.L. Synchronization in chaotic systems. Phys. Rev. Lett. 1990;64:821. doi: 10.1103/PhysRevLett.64.821. [DOI] [PubMed] [Google Scholar]
- 15.Sweetha S., Sakthivel R., Harshavarthini S. Finite-time synchronization of nonlinear fractional chaotic systems with stochastic actuator faults. Chaos Solitons Fractals. 2021;142:110312. doi: 10.1016/j.chaos.2020.110312. [DOI] [Google Scholar]
- 16.Yang F., Mou J., Ma C., Cao Y. Dynamic analysis of an improper fractional-order laser chaotic system and its image encryption application. Opt. Lasers Eng. 2020;129:106031. doi: 10.1016/j.optlaseng.2020.106031. [DOI] [Google Scholar]
- 17.Lin C.F., Shih S.H., Zhu J.D. Chaos based encryption system for encrypting electroencephalogram signals. J. Med. Syst. 2014;38:1–10. doi: 10.1007/s10916-014-0049-6. [DOI] [PubMed] [Google Scholar]
- 18.Murillo-Escobar M.A., Cardoza-Avendaño L., López-Gutiérrez R.M., Cruz-Hernández C. A double chaotic layer encryption algorithm for clinical signals in telemedicine. J. Med. Syst. 2017;41:59. doi: 10.1007/s10916-017-0698-3. [DOI] [PubMed] [Google Scholar]
- 19.Shahzadi R., Anwar S.M., Qamar F., Ali M., Rodrigues J.J., Alnowami M. Secure EEG signal transmission for remote health monitoring using optical chaos. IEEE Access. 2019;7:57769–57778. doi: 10.1109/ACCESS.2019.2912548. [DOI] [Google Scholar]
- 20.Chen J., Ling B.W.K., Feng P., Lei R. Computer cryptography through performing chaotic modulation on intrinsic mode functions with non-dyadic number of encrypted signals. IET Signal. Process. 2018;13:7–13. doi: 10.1049/iet-spr.2018.5256. [DOI] [Google Scholar]
- 21.Ibrahim S., Alhumyani H., Masud M., Alshamrani S.S., Cheikhrouhou O., Muhammad G., Hossain M.S., Abbas A.M. Framework for Efficient Medical Image Encryption Using Dynamic S-Boxes and Chaotic Maps. IEEE Access. 2020;8:160433–160449. doi: 10.1109/ACCESS.2020.3020746. [DOI] [Google Scholar]
- 22.Gafsi M., Abbassi N., Hajjaji M.A., Malek J., Mtibaa A. Improved Chaos-Based Cryptosystem for Medical Image Encryption and Decryption. Sci. Program. 2020;2020:6612390. [Google Scholar]
- 23.Kumar S., Panna B., Jha R.K. Medical image encryption using fractional discrete cosine transform with chaotic function. Med. Biol. Eng. Comput. 2019;57:2517–2533. doi: 10.1007/s11517-019-02037-3. [DOI] [PubMed] [Google Scholar]
- 24.Liu J., Tang S., Lian J., Ma Y., Zhang X. A novel fourth order chaotic system and its algorithm for medical image encryption. Multidimens. Syst. Signal. Process. 2019;30:1637–1657. doi: 10.1007/s11045-018-0622-0. [DOI] [Google Scholar]
- 25.Stalin S., Maheshwary P., Shukla P.K., Maheshwari M., Gour B., Khare A. Fast and secure medical image encryption based on non linear 4D logistic map and DNA sequences (NL4DLM_DNA) J. Med. Syst. 2019;43:1–17. doi: 10.1007/s10916-019-1389-z. [DOI] [PubMed] [Google Scholar]
- 26.Banday S.A., Mir A.H., Malik S. Advances in Computational Techniques for Biomedical Image Analysis. Academic Press; Cambridge, MA, USA: 2020. Multilevel medical image encryption for secure communication; pp. 233–252. [Google Scholar]
- 27.Chai X., Zhang J., Gan Z., Zhang Y. Medical image encryption algorithm based on Latin square and memristive chaotic system. Multimed. Tools Appl. 2019;78:35419–35453. doi: 10.1007/s11042-019-08168-x. [DOI] [Google Scholar]
- 28.Choi U.S., Cho S.J., Kang S.W. Color medical image encryption using 3D Chaotic Cat Map and NCA; Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS); Canary Islands, Spain. 24–26 June 2019; pp. 1–5. [Google Scholar]
- 29.Dagadu J.C., Li J., Shah F. An efficient di-chaotic diffusion based medical image cryptosystem; Proceedings of the 2017 14th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP); Chengdu, China. 15–17 December 2017; pp. 206–210. [Google Scholar]
- 30.Ismail S.M., Said L.A., Radwan A.G., Madian A.H., Abu-Elyazeed M.F. Generalized double-humped logistic map-based medical image encryption. J. Adv. Res. 2018;10:85–98. doi: 10.1016/j.jare.2018.01.009. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.Li X., Wu F., Khan M.K., Xu L., Shen J., Jo M. A secure chaotic map-based remote authentication scheme for telecare medicine information systems. Future Gener. Comput. Syst. 2018;84:149–159. doi: 10.1016/j.future.2017.08.029. [DOI] [Google Scholar]
- 32.Pandey A., Singh B., Saini B.S., Sood N. A novel fused coupled chaotic map based confidential data embedding-then-encryption of electrocardiogram signal. Biocybern. Biomed. Eng. 2019;39:282–300. doi: 10.1016/j.bbe.2018.11.012. [DOI] [Google Scholar]
- 33.Sangavi V., Thangavel P. An exotic multi-dimensional conceptualization for medical image encryption exerting Rossler system and Sine map. J. Inf. Secur. Appl. 2020;55:102626. [Google Scholar]
- 34.Thakur S., Singh A.K., Ghrera S.P., Elhoseny M. Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed. Tools Appl. 2019;78:3457–3470. doi: 10.1007/s11042-018-6263-3. [DOI] [Google Scholar]
- 35.Zheng L., Wang Z., Tian S. Comparative study on electrocardiogram encryption using elliptic curves cryptography and data encryption standard for applications in Internet of medical things. Concurr. Comput. Pract. Exp. 2020:e5776. doi: 10.1002/cpe.5776. [DOI] [Google Scholar]
- 36.Murillo-Escobar M.A., Cruz-Hernández C., Abundiz-Pérez F., López-Gutiérrez R.M., Del Campo O.A. A RGB image encryption algorithm based on total plain image characteristics and chaos. Signal. Process. 2015;109:119–131. doi: 10.1016/j.sigpro.2014.10.033. [DOI] [Google Scholar]
- 37.Ye G., Jiao K., Wu H., Pan C., Huang X. An asymmetric image encryption algorithm based on a fractional-order chaotic system and the RSA public-key cryptosystem. Int. J. Bifurc. Chaos. 2020;30:2050233. doi: 10.1142/S0218127420502338. [DOI] [Google Scholar]
- 38.Ding L., Ding Q. A Novel Image Encryption Scheme Based on 2D Fractional Chaotic Map, DWT and 4D Hyper-chaos. Electronics. 2020;9:1280. doi: 10.3390/electronics9081280. [DOI] [Google Scholar]
- 39.Zhang S., Gao T., Gao L. A novel encryption frame for medical image with watermark based on hyperchaotic system. Math. Probl. Eng. 2014;2014:240749. doi: 10.1155/2014/240749. [DOI] [Google Scholar]
- 40.Ye G., Wong K.W. An image encryption scheme based on time-delay and hyperchaotic system. Nonlinear Dyn. 2013;71:259–267. doi: 10.1007/s11071-012-0658-x. [DOI] [Google Scholar]
- 41.Alizadehsani R., Roshanzamir M., Hussain S., Khosravi A., Koohestani A., Zangooei M.H., Abdar M., Beykikhoshk A., Shoeibi A., Zare A., et al. Handling of uncertainty in medical data using machine learning and probability theory techniques: A review of 30 years (1991–2020) Ann. Oper. Res. 2021:1–42. doi: 10.1007/s10479-021-04006-2. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 42.Ye G., Pan C., Dong Y., Shi Y., Huang X. Image encryption and hiding algorithm based on compressive sensing and random numbers insertion. Signal. Process. 2020;172:107563. doi: 10.1016/j.sigpro.2020.107563. [DOI] [Google Scholar]
- 43.Zhou J., Zhou N.R., Gong L.H. Fast color image encryption scheme based on 3D orthogonal Latin squares and matching matrix. Opt. Laser Technol. 2020;131:106437. doi: 10.1016/j.optlastec.2020.106437. [DOI] [Google Scholar]
- 44.Sharifrazi D., Alizadehsani R., Joloudari J.H., Shamshirband S., Hussain S., Sani Z.A., Hasanzadeh F., Shoaibi A., Dehzangi A., Alinejad-Rokny H. CNN-KCL: Automatic Myocarditis Diagnosis using Convolutional Neural Network Combined with K-means Clustering. Preprints. 2020 doi: 10.20944/preprints202007.0650.v1. [DOI] [PubMed] [Google Scholar]
- 45.Bashashati A., Fatourechi M., Ward R.K., Birch G.E. A survey of signal processing algorithms in brain–computer interfaces based on electrical brain signals. J. Neural Eng. 2007;4:R32. doi: 10.1088/1741-2560/4/2/R03. [DOI] [PubMed] [Google Scholar]
- 46.Chow L.S., Paramesran R. Review of medical image quality assessment. Biomed. Signal. Process. Control. 2016;27:145–154. doi: 10.1016/j.bspc.2016.02.006. [DOI] [Google Scholar]
- 47.Jin X., Wang Z., Yang H., Song Q., Xiao M. Synchronization of Multiplex Networks with Stochastic Perturbations via Pinning Adaptive Control. J. Frankl. Inst. 2021;358:3994–4012. doi: 10.1016/j.jfranklin.2021.03.004. [DOI] [Google Scholar]
- 48.Ji Y., Gong Y., Su S., Bai X. Fixed-Time Synchronization for Different Dimensional Complex Network Systems with Unknown Parameters via Adaptive Control. Complexity. 2021;2021:6680287. doi: 10.1155/2021/6680287. [DOI] [Google Scholar]
- 49.Mofid O., Momeni M., Mobayen S., Fekih A. A Disturbance-Observer-Based Sliding Mode Control for the Robust Synchronization of Uncertain Delayed Chaotic Systems: Application to Data Security. IEEE Access. 2021;9:16546–16555. doi: 10.1109/ACCESS.2021.3053014. [DOI] [Google Scholar]
- 50.Yao Q. Synchronization of second-order chaotic systems with uncertainties and disturbances using fixed-time adaptive sliding mode control. Chaos Solitons Fractals. 2021;142:110372. doi: 10.1016/j.chaos.2020.110372. [DOI] [Google Scholar]
- 51.Balootaki M.A., Rahmani H., Moeinkhah H., Mohammadzadeh A. Non-singleton fuzzy control for multi-synchronization of chaotic systems. Appl. Soft Comput. 2021;99:106924. doi: 10.1016/j.asoc.2020.106924. [DOI] [Google Scholar]
- 52.Soleimanizadeh A., Nekoui M.A. Optimal type-2 fuzzy synchronization of two different fractional-order chaotic systems with variable orders with an application to secure communication. Soft Comput. 2021;25:6415–6426. doi: 10.1007/s00500-021-05636-1. [DOI] [Google Scholar]
- 53.Rigatos G., Abbaszadeh M. Nonlinear optimal control and synchronization for chaotic electronic circuits. J. Comput. Electron. 2021;20:1050–1063. doi: 10.1007/s10825-021-01655-1. [DOI] [Google Scholar]
- 54.Motallebzadeh F., Motlagh MR J., Cherati Z.R. Synchronization of different-order chaotic systems: Adaptive active vs. optimal control. Commun. Nonlinear Sci. Numer. Simul. 2012;17:3643–3657. doi: 10.1016/j.cnsns.2012.01.012. [DOI] [Google Scholar]
- 55.Khan A., Kumar S. TS fuzzy modeling and predictive control and synchronization of chaotic satellite systems. Int. J. Model. Simul. 2019;39:203–213. doi: 10.1080/02286203.2018.1563393. [DOI] [Google Scholar]
- 56.Kaheni H.R., Yaghoobi M. A new approach in anti-synchronization of a fractional-order hyper-chaotic Duffing system based on new nonlinear predictive control. Int. J. Dyn. Control. 2020;8:917–931. doi: 10.1007/s40435-020-00609-y. [DOI] [Google Scholar]
- 57.Gupta S., Varshney P., Srivastava S. Whale optimization based synchronization and control of two identical fractional order financial chaotic systems. J. Intell. Fuzzy Syst. 2021:1–14. doi: 10.3233/JIFS-189761. [DOI] [Google Scholar]
- 58.Xiong P.Y., Jahanshahi H., Alcaraz R., Chu Y.M., Gómez-Aguilar J.F., Alsaadi F.E. Spectral Entropy Analysis and Synchronization of a Multi-Stable Fractional-Order Chaotic System using a Novel Neural Network-Based Chattering-Free Sliding Mode Technique. Chaos Solitons Fractals. 2021;144:110576. doi: 10.1016/j.chaos.2020.110576. [DOI] [Google Scholar]
- 59.Lin C.H., Hu G.H., Chan C.Y., Yan J.J. Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm. Appl. Sci. 2021;11:1329. doi: 10.3390/app11031329. [DOI] [Google Scholar]
- 60.Moon S., Baik J.J., Seo J.M. Chaos synchronization in generalized Lorenz systems and an application to image encryption. Commun. Nonlinear Sci. Numer. Simul. 2021;96:105708. doi: 10.1016/j.cnsns.2021.105708. [DOI] [Google Scholar]
- 61.Wan P.Y., Liao T.L., Yan J.J., Tsai H.H. Discrete sliding mode control for chaos synchronization and its application to an improved El-Gamal cryptosystem. Symmetry. 2019;11:843. doi: 10.3390/sym11070843. [DOI] [Google Scholar]
- 62.Yau H.T., Hung T.H., Hsieh C.C. Bluetooth based chaos synchronization using particle swarm optimization and its applications to image encryption. Sensors. 2012;12:7468–7484. doi: 10.3390/s120607468. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 63.Chen X., Park J.H., Cao J., Qiu J. Sliding mode synchronization of multiple chaotic systems with uncertainties and disturbances. Appl. Math. Comput. 2017;308:161–173. doi: 10.1016/j.amc.2017.03.032. [DOI] [Google Scholar]
- 64.Ren H.P., Bai C., Huang Z.Z., Grebogi C. Secure communication based on hyperchaotic Chen system with time-delay. Int. J. Bifurc. Chaos. 2017;27:1750076. doi: 10.1142/S0218127417500766. [DOI] [Google Scholar]
- 65.Lin T.C., Huang F.Y., Du Z., Lin Y.C. Synchronization of fuzzy modeling chaotic time delay memristor-based Chua’s circuits with application to secure communication. Int. J. Fuzzy Syst. 2015;17:206–214. doi: 10.1007/s40815-015-0024-5. [DOI] [Google Scholar]
- 66.Kwon O.M., Park J.H., Lee S.M. Secure communication based on chaotic synchronization via interval time-varying delay feedback control. Nonlinear Dyn. 2011;63:239–252. doi: 10.1007/s11071-010-9800-9. [DOI] [Google Scholar]
- 67.Shoeibi A., Ghassemi N., Alizadehsani R., Rouhani M., Hosseini-Nejad H., Khosravi A., Panahiazar M., Nahavandi S. A comprehensive comparison of handcrafted features and convolutional autoencoders for epileptic seizures detection in EEG signals. Expert Syst. Appl. 2021;163:113788. doi: 10.1016/j.eswa.2020.113788. [DOI] [Google Scholar]
- 68.Ghassemi N., Shoeibi A., Rouhani M., Hosseini-Nejad H. Epileptic seizures detection in EEG signals using TQWT and ensemble learning; Proceedings of the 2019 9th International Conference on Computer and Knowledge Engineering (ICCKE); Mashhad, Iran. 24–25 October 2019; pp. 403–408. [Google Scholar]
- 69.Ahmadi A., Kashefi M., Shahrokhi H., Nazari M.A. Computer aided diagnosis system using deep convolutional neural networks for ADHD subtypes. Biomed. Signal. Process. Control. 2021;63:102227. doi: 10.1016/j.bspc.2020.102227. [DOI] [Google Scholar]
- 70.Chen H., Song Y., Li X. A deep learning framework for identifying children with ADHD using an EEG-based brain network. Neurocomputing. 2019;356:83–96. doi: 10.1016/j.neucom.2019.04.058. [DOI] [Google Scholar]
- 71.Sadeghi D., Shoeibi A., Ghassemi N., Moridian P., Khadem A., Alizadehsani R., Teshnehlab M., Gorriz J.M., Nahavandi S. An Overview on Artificial Intelligence Techniques for Diagnosis of Schizophrenia Based on Magnetic Resonance Imaging Modalities: Methods, Challenges, and Future Works. arXiv. 2021 doi: 10.1016/j.compbiomed.2022.105554.2103.03081 [DOI] [PubMed] [Google Scholar]
- 72.Górriz J.M., Ramírez J., Ortíz A., Martínez-Murcia F.J., Segovia F., Suckling J., Leming M., Zhang Y.-D., Álvarez-Sánchez J.R., Bologna G., et al. Artificial intelligence within the interplay between natural and artificial computation: Advances in data science, trends and applications. Neurocomputing. 2020;410:237–270. doi: 10.1016/j.neucom.2020.05.078. [DOI] [Google Scholar]
- 73.Shoeibi A., Khodatars M., Jafari M., Moridian P., Rezaei M., Alizadehsani R., Khozeimeh F., Gorriz J.M., Heras J., Panahiazar M., et al. Applications of Deep Learning Techniques for Automated Multiple Sclerosis Detection Using Magnetic Resonance Imaging: A Review. arXiv. 2021 doi: 10.1016/j.compbiomed.2021.104697.2105.04881 [DOI] [PubMed] [Google Scholar]
- 74.Ghassemi N., Shoeibi A., Rouhani M. Deep neural network with generative adversarial networks pre-training for brain tumor classification based on MR images. Biomed. Signal. Process. Control. 2020;57:101678. doi: 10.1016/j.bspc.2019.101678. [DOI] [Google Scholar]
- 75.Manni F., van der Sommen F., Fabelo H., Zinger S., Shan C., Edström E., Elmi-Terander A., Ortega S., Callicó G.M., de With P.H.N. Hyperspectral imaging for glioblastoma surgery: Improving tumor identification using a deep spectral-spatial approach. Sensors. 2020;20:6955. doi: 10.3390/s20236955. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 76.Ahsan M., Based M., Haider J., Kowalski M. COVID-19 Detection from Chest X-ray Images Using Feature Fusion and Deep Learning. Sensors. 2021;21:1480. doi: 10.3390/s21041480. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 77.Mohammadpoor M., Shoeibi A., Shojaee H. A hierarchical classification method for breast tumor detection. Iran. J. Med. Phys. 2016;13:261–268. [Google Scholar]
- 78.Mambou S.J., Maresova P., Krejcar O., Selamat A., Kuca K. Breast cancer detection using infrared thermal imaging and a deep learning model. Sensors. 2018;18:2799. doi: 10.3390/s18092799. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 79.Shoeibi A., Khodatars M., Alizadehsani R., Ghassemi N., Jafari M., Moridian P., Khadem A., Sadeghi D., Hussain S., Zare A., et al. Automated detection and forecasting of covid-19 using deep learning techniques: A review. arXiv. 20202007.10785 [Google Scholar]
- 80.Alizadehsani R., Sharifrazi D., Izadi N.H., Joloudari J.H., Shoeibi A., Gorriz J.M., Hussain S., Arco J.E., Sani Z.A., Khozeimeh F., et al. Uncertainty-aware semi-supervised method using large unlabelled and limited labeled COVID-19 data. arXiv. 20212102.06388 [Google Scholar]
- 81.Ayoobi N., Sharifrazi D., Alizadehsani R., Shoeibi A., Gorriz J.M., Moosaei H., Khosravi A., Nahavandi S., Chofreh A.G., Goni F.A., et al. Time Series Forecasting of New Cases and New Deaths Rate for COVID-19 using Deep Learning Methods. arXiv. 2021 doi: 10.1016/j.rinp.2021.104495.2104.15007 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 82.Ghassemi N., Shoeibi A., Khodatars M., Heras J., Rahimi A., Zare A., Pachori R.B., Gorriz J.M. Automatic Diagnosis of COVID-19 from CT Images using CycleGAN and Transfer Learning. arXiv. 2021 doi: 10.1016/j.asoc.2023.110511.2104.11949 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 83.Khozeimeh F., Sharifrazi D., Izadi N.H., Joloudari J.H., Shoeibi A., Alizadehsani R., Gorriz J.M., Hussain S., Sani Z.A., Moosaei H., et al. CNN AE: Convolution Neural Network combined with Autoencoder approach to detect survival chance of COVID 19 patients. arXiv. 2021 doi: 10.1038/s41598-021-93543-8.2104.08954 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 84.Alizadehsani R., Khosravi A., Roshanzamir M., Abdar M., Sarrafzadegan N., Shafie D., Khozeimeh F., Shoeibi A., Nahavandi S., Panahiazar M., et al. Coronary Artery Disease Detection Using Artificial Intelligence Techniques: A Survey of Trends, Geographical Differences and Diagnostic Features 1991–2020. Comput. Biol. Med. 2020;128:104095. doi: 10.1016/j.compbiomed.2020.104095. [DOI] [PubMed] [Google Scholar]
- 85.Fereydouneyan F., Zare A., Mehrshad N. Using a fuzzy controller optimized by a genetic algorithm to regulate blood glucose level in type 1 diabetes. J. Med. Eng. Technol. 2011;35:224–230. doi: 10.3109/03091902.2011.569050. [DOI] [PubMed] [Google Scholar]
- 86.Namadchian Z., Zare A. Stability analysis of dynamic nonlinear interval type-2 TSK fuzzy control systems based on describing function. Soft Comput. 2020;24:14623–14636. doi: 10.1007/s00500-020-04811-0. [DOI] [Google Scholar]
- 87.Baydokhty M.E., Zare A., Balochian S. Performance of optimal hierarchical type 2 fuzzy controller for load–frequency system with production rate limitation and governor dead band. Alex. Eng. J. 2016;55:379–397. doi: 10.1016/j.aej.2015.12.003. [DOI] [Google Scholar]
- 88.Bajestani N.S., Kamyad A.V., Zare A. A piecewise type-2 fuzzy regression model. Int. J. Comput. Intell. Syst. 2017;10:734–744. doi: 10.2991/ijcis.2017.10.1.49. [DOI] [Google Scholar]
- 89.Zare A., Okauti M. Automatic road extraction based on neuro-fuzzy algorithm; Proceedings of the 10th WSEAS International Conference on Robotics, Control and Manufacturing Technology; Hangzhou, China. 11–13 April 2010. [Google Scholar]
- 90.Bajestani N.S., Kamyad A.V., Esfahani E.N., Zare A. Nephropathy forecasting in diabetic patients using a GA-based type-2 fuzzy regression model. Biocybern. Biomed. Eng. 2017;37:281–289. doi: 10.1016/j.bbe.2017.01.003. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data sharing not applicable.