Abstract
Objectives
This systematic review seeks to collate and synthesize putative risk and protective factors for the different outcomes of radicalization.
Methodology
Drawing on an established theoretical framework, we will categorize putative risk and protective factors as they relate to the domains of radical attitudes, intentions, and behaviors. We will utilize meta‐analytic techniques to develop a rank‐order of factors according to effect size. Meta‐regression and sub‐group analyses will be used to assess sources of heterogeneity.
Implications
The results of the review are intended to inform evidence‐based policy in the areas of both assessment and intervention.
1. BACKGROUND
1.1. The problem
Terrorism continues to be one of the most serious challenges in the world today, especially for democratic countries that have experienced an uptick in terrorism in recent times. This uptick has coincided with a growth in specific threats, such as homegrown terrorism, lone‐wolf terrorism, and the issue of departing and returning foreign fighters (Global Terrorism Index, 2016). Already beginning in about 15 years ago, a shift began to occur in which scholars and practitioners recognized that there was no profile of a terrorist, and that predicting terrorism was exceptionally difficult. It became clear that military might, intelligence, and policing alone are not capable of countering the multitude of threats posed by terrorism. Rather, an effective approach to combatting terrorism is one that balances active security with efforts to stymie those factors that lead to the radicalization that underpins terrorism (European Commission, 2014; OSCE, 2014; White House, 2011). Since there are far more radicalized individuals than there are terrorists, but almost all terrorists are radicalized, the new logic focused on reducing the prevalence of radicalization in the population as a means of reducing the risk of terrorism (European Commission, 2005a, 2014; OSCE, 2014; White House, 2011).
It is this logic that has given rise to an increased focus on efforts to improve risk assessment, and a host of counter‐radicalization and deradicalization strategies that seek to target the factors that increase risk, and promote factors that decrease it. Under the umbrella of counter violent extremism (CVE) policies, such strategies and initiatives seek to both predict future radical behavior, as well as change it. CVE strategies include a range of socio‐economic interventions, community and education initiatives, and online interventions. All of these approaches share the common underlying assumption and approach that by tackling the radicalization that underpins the likelihood of recruitment to terrorism, and by reducing the prevalence of radicalized individuals in the population, there will ultimately be a reduction in the likelihood of terrorism (EU, 2014; OSCE, 2014).
Currently, many of these initiatives are not evidence based. Despite the growth of radicalization and terrorism research in recent years, the empirical study still only accounts for a small percentage of the knowledge (Christmann, 2012; Lum, Kennedy, & Sherley, 2006; Schuurman, 2018; Silke, 2008). There is therefore little concrete information upon which policies and interventions can be developed, and they are therefore unlikely to have the desired impact (Davis, 2014). While such policies and strategies aim to tackle risk factors, there is often mixed and contradictory evidence about what the risk factors are, and their relative importance (Hafez & Mullins, 2015). The lack of systematic investigation has left it to policy makers to develop policies and strategies that are not evidence based (Neumann & Kleinmann, 2013; Victoroff, 2005). Only “Greater analytical depth may eventually reconcile contradictory claims" (Wikström & Bouhana, 2017, p. 183).
It is for these reasons that a systematic review and meta‐analysis are needed. While systematic reviews are intended to focus on specific and narrow research questions, previous systematic reviews on radicalization have been overly broad, in part because of a lack of a cohesive for conceptualizing radicalization. In this review, we take a more focused approach, enabling a meaningful synthesis and organization of quantifiable data, whilst maintaining a broad enough scope as to capture the complexity of the factors related to radicalization outcomes. To achieve this, we follow an established theoretical model for predetermining our outcomes of interest, namely different measures of cognitive and behavioral radicalization; the two‐pyramid model (TPM; McCauley & Moskalenko, 2017). Moreover, unlike previous reviews, the current study is limited to examining rigorous quantitative studies only, which provide sufficient data to calculate effect sizes for input into a meta‐analysis.
1.2. Defining radicalization and recruitment
The suffix of the word radicalization indicates that it is a process, something which all scholars agree can take place over a period of time from as short as a few weeks to as long as many years (Borum, 2011a, 2011b; Klausen, Libretti, Hung, & Jayasumana, 2018; Silke, 2008). But definitions of radicalization that focus too much on the process element can cause confusion, since they highlight violent extremism, or terrorism as being the ultimate outcome of this process. In fact, very few radicalized individuals will even go on to carry out any acts of violence. That is, only a small percentage of individuals who hold radical attitudes, arguably less than 1%, will ever engage in any form of radical behaviors (Borum, 2011a, 2011b; Horgan, 2008; McCauley & Moskalenko, 2017).
According to the EU, radicalization is defined as "the phenomenon of people embracing opinions, views and ideas which could [sic] lead to acts of terrorism” (European Commission, 2005a). As this definition indicates, there is a clear difference between the ideas, attitudes, and opinions that connote radicalization on one hand, and acts of terrorism on the other hand. Indeed, the EU has a separate definition for recruitment to terrorism, with recruitment being when someone has been solicited “to commit or participate in the commission of a terrorist offense, or to join an association or group, for the purpose of contributing to the commission of one or more terrorist offenses by the association or the group” (European Commission, 2005b), or in short, “Recruitment to carry out terrorist offenses” (European Commission, 2014). As such, anyone who has participated in a terrorist offense is said to have been recruited.
The EU's definitions for radicalization and recruitment underscore the ever‐important distinction that needs to be made between the cognitive and behavioral dimensions and outcomes of radicalization (Bartlett, Birdwell, & King, 2010; Borum, 2011a, 2011b; Hafez & Mullins, 2015; Khalil, 2014; P. R. Neumann, 2013; Vidino & Brandon, 2012). However, they do not indicate what types of ideas, attitudes, or opinions constitute radicalization. A variety of proxies have been used in the literature for radicalization, or extremism, including support for extreme right‐wing parties (Perry, Wikström, & Roman, 2018; Rydgren & Ruth, 2013); measuring personality traits, such as the authoritarian personality scales (RWA), or fundamentalism (Beller & Kröger, 2017; McCann, 2009; McCleary, Quillivan, Foster, & Williams, 2011); and measures of orthodoxy and religious fundamentalism (Slootman & Tillie, 2006). On their own, these are all considered poor proxies as they have a low degree of specificity with respect to the associated behavioral outcome of interest, namely terrorism (Koopmans, 2015; Mudde, 2004).
Indeed, in any research that seeks to explore the attitudinal or cognitive antecedents of a given behavior, it is important that they have a high level of specificity with reference to the behavioral outcome of interest (Ajzen & Fishbein, 1980; Fishbein & Ajzen, 1975). This approach underpins McCauley and Moskalenko's "radical opinions" outcomes, in which radical opinions, or what we refer to as attitudes, constitute the support for, justification of, or a belief that there is a personal obligation toward the carrying out of radical violence and/or terrorism. Using constructs that are in line with such measures to assess cognitive radicalization has become the standard in research (e.g., K. Bhui, Warfa, & Jones, 2014; Doosje et al., 2016; Kruglanski, Jasko, Chernikova, & Milyavsky, 2018; McCauley & Moskalenko, 2008; Schmid, 2013; Webber et al., 2018) and policy (e.g. Agerschou, 2014).
1.2.1. The two‐pyramid model
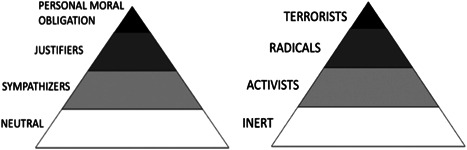
This systematic review follows this highly specific approach by utilizing the outcome‐based typology (attitudes‐intentions‐behavior) embodied in the increasingly popular TPM model of radicalization developed by McCauley and Moskalenko (2017), Moskalenko and McCauley (2009) and McCauley and Moskalenko (2011) for which there is already strong empirical backing (Gøtzsche‐Astrup, 2018). The TPM was largely developed to be consistent with psychological models that deal with attitudinal and behavioral outcomes as they relate to the same object or action. As noted above, when seeking to examine the attitudinal antecedents of behavior, it is important that the attitude being examined achieves a high level of specificity with respect to the associated behavior (Fishbein and Ajzen, 1975). As such, the TPM's radical opinions period, or cognitive radicalization pyramid, is constructed in reference to the outcomes of the “radical actions” pyramid.
Starting with the radical behaviors pyramid, activism and radicalism are differentiated from each other primarily in that the former generally consists of legal, nonviolent ideologically motivated behaviors, and the latter generally consists of illegal and violent ideologically motivated behaviors. With respect to the latter, however, these behaviors are essentially still subterroristic in nature, with terrorism being the targeted use of ideologically motivated lethal violence (McCauley & Moskalenko, 2017).
Behaviors are in theory much easier to categorize than attitudes, however, which are more hypothetical constructs. Following Ajzen's (1988, p. 4) definition of an attitude as being “a disposition to respond favorably or unfavorably to an object, person, institution, or event,” and like criminal attitudes towards violence (Fincham, Cui, Braithwaite, & Pasley, 2008; Nunes, Hermann, Maimone, & Woods, 2015), radical attitudes should be assessed by a high level of specificity with respect to an object (e.g., terrorism), person (e.g., Osama bin Laden), institution (e.g., Al‐Qaeda), or event (e.g., 9/11) Borum, 2015; Schmid, 2017). Indeed, even before the development of the TPM, scholars were already assessing cognitive radicalization from responses to questions assessing support, acceptance, or justification of these items. And whilst imperfect, these are still the best measures we have for cognitive radicalization (Schmid, 2017). Radical attitudes can, therefore, be assessed by examining support, justification, or acceptance of radical behaviors in a general sense, or with respect to others engaging in such behaviors.
This distinguishes the attitudinal outcome from the intentional outcome, which the TPM calls “personal moral obligation,” in which an individual feels, or expresses their feelings that they should engage in radical behaviors. Along the spectrum of intentions, and with respect to radicalization specifically, there is a close relationship between desire, readiness, willingness, and behavioral intentions (Brynielsson et al., 2013). Indeed, based on the TPM framework, Moskalenko and McCauley (2009) created the Activism‐Radicalism‐Intentions‐Scale (ARIS), an instrument used to assess intentions toward engagement in activist or radical actions and behaviors. This tool has been used in a number of studies to assess radical intentions and is growing in popularity. However, given the sensitivity of asking study participants about their intentions toward illegal behaviors, some researchers have adapted the ARIS to assess attitudes. For example, instead of asking respondents if they would engage in a specific radical behavior, they ask them to what degree they support, or agree with someone else who engages in that behavior (e.g., Ellis et al., 2016).
Unlike other frameworks, the TPM is nondirectional and does not specify any particular direction to the move from and between its different levels nor does it require passing through one level to progress to the next. The TPM thereby provides for the possibility that terrorists need not be exceptionally radicalized, and pathways that lead to nonviolent outcomes, accepting that most people who hold radical views will never turn to violence (Borum, 2011a, 2011b). According to the model, every individual "radical" exists at some level on both pyramids simultaneously. The narrowing shape of the pyramid at each subsequent level indicates that a smaller population displays the outcome. For example, while there may be 5% or more of a given sample that are “justifiers” of terrorism, a much smaller percentage are likely to believe they have a personal moral obligation to carry it out (Leuprecht, Hataley, Moskalenko, & McCauley, 2010). Even among those who hold that they have a personal moral obligation, or express intentions or a willingness to engage in violent radical behaviors, the majority will remain forever inert. However, whilst there are exceptions, it can be assumed that the majority of terrorists did at some point prior to their actions, hold that they had such a personal moral obligation. Nevertheless, these represent the smallest proportion of the population of radicals. (Figures 1 and 2).
Figure 1.
McCauley and Moskalenko's (2017) two‐pyramid model
Figure 2.
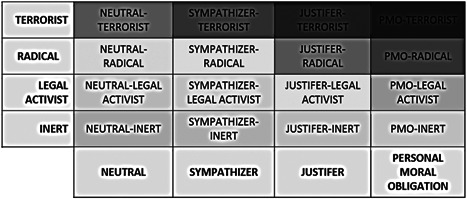
Possible beliefs‐actions combinations (Orlina & Desjardins, 2012, p. 16)
There are many advantages to a typological and outcome‐based framework such as the TPM as part of a systematic review and meta‐analysis. First, it provides the type of definitional clarity and consistency that is needed for operationalization, whilst simultaneously reflecting the approaches taken by organizations such as the EU and the general logic underpinning counter‐radicalization initiatives more generally. For this reason, the TPM, and pyramid models in general, have also become popular in counter‐radicalization and counter‐terrorism interventions research (Orlina & Desjardins, 2012). Second, it sets clear categorization standards that exclude distantly related beliefs that may provide important comparisons but detract from the object of interest.
The TPM does not, however, provide a set of mechanisms or explanation as to why some may move from opinions to actions, or attitudes to behaviors, and also why some who may feel a personal moral obligation will remain forever inert. But the researchers who developed the TPM have offered some possible explanations, in the form of different risk and protective factors. For example, personal or group grievances, or thrill‐seeking may be risk factors for the move from beliefs to actions, and parental bonds may inhibit it (Leuprecht et al., 2010; McCauley & Moskalenko, 2008; Moskalenko & McCauley, 2011). Indeed, the entire relationship between attitudes, intentions, and behaviors as it pertains to criminal and criminal‐analogous outcomes, is mediated by risk and protective factors (Tuck & Riley, 1986). That is, the presence or absence of risk and protective factors can explain why a small percentage of individuals with radical attitudes and/or intentions will eventually engage in radical behaviors, whilst most would not (Malthaner, 2017; Stern, 2016).
1.3. Overlaps between criminal and radical attitudes, intentions, and behaviors: a risk and protective factor framework
The risk‐protective factor framework is a probabilistic, rather than a deterministic one. That is, while risk factors can be found to predict a range of criminal and criminal‐analogous outcomes, such as gang involvement (Higginson et al., 2015; Hill, Howell, Hawkins, & Battin‐Pearson, 1999) or general violent offending (Herrenkohl et al., 2000), most individuals possessing even all the most important risk factors will never actually offend. Risk factors only increase the propensity to offending and do not predict offending as a given. However, they can help to identify and differentiate the types of individuals at greater risk (Kazdin, Kraemer, Kessler, Kupfer, & Offord, 1997; Murray & Thomson, 2010; Shader, 2001) and which risk factors and the degree of their presence differentiate between different types of offending outcomes (Esbensen, Peterson, Taylor, & Freng, 2009; Horgan, Shortland, Abbasciano, & Walsh, 2016). Similarly, protective factors can cancel out or override the effects of risk factors (Farrington, Ttofi, & Piquero, 2016). As such, it is the likelihood that an individual will hold on to certain criminal attitudes, or engage in criminal behaviors, that will be increased or decreased by the cumulative and interactive weight of risk factors over protective factors, or vice versa ( Folk et al., 2018; Lösel & Farrington, 2012).
In criminology, it has long been found that criminal attitudes and criminal intentions are among the best predictors of criminal behaviors (Gendreau, Little, & Goggin, 1996; Simourd, Hoge, Andrews, & Leschied, 1994). However, not all measures of criminal attitudes are equal. For example, Fincham et al. (2008) found that a revised version of an interpersonal violence attitudes scale had greater predictive value for actual interpersonal violence behaviors than a more general version. Nunes et al. (2015) found that support for the use of violence is a distinct type of criminal attitude and that it is a better predictor of violent behavioral outcomes than general criminal attitudes. Traditional criminogenic factors such as deviant peers (e.g., Megens & Weerman, 2010), low self‐control (Walters, 2016) are known moderators of the attitude‐behavior consistency for an ordinary crime. There is evidence that similar risk factors may mediate the relationship between radical attitudes and behaviors (Bélanger, Caouette, Sharvit, & Dugas, 2014; Kruglanski et al., 2018). Given these similarities, and a growing body of evidence pointing to overlaps between terrorism and crime, terrorists and criminals (e.g., Clarke & Newman, 2006; LaFree & Dugan, 2004; Mullins, 2009), and the risk and protective factors for criminality and radicalization (e.g., LaFree, Jensen, James, & Safer‐Lichtenstein, 2018; Lösel, King, Bender, & Jugl, 2018), it makes sense to approach the study of risk and protective factors in a similar fashion (Borum, 2015).
1.4. A systematic review of putative risk and protective factors: taking a “field‐wide approach”
As described above, risk and protective factors are mediators of the attitude‐intention‐behavior continuity. However, they also directly affect attitudinal, intentional, and behavioral outcomes in and of themselves. It is a research imperative to “tease out the often subtle and complex interactions between attitudes and non‐belief‐related factors” (P. R. Neumann, 2013, p. 880). This is only possible by organizing and comparing the magnitude of the effects between belief and non‐belief‐related factors, including across‐related outcomes.
This systematic review follows an epidemiological approach and will attempt to present a “field‐wide meta‐analysis of observational associations” regarding putative risk and protective factors for the different outcomes of radicalization. Unlike traditional reviews that focus on a specific factor, type of factor, or set of factors (e.g., education, mental health), the field‐wide approach seeks to collect and organize the evidence for an unspecified array of factors, allowing the literature to determine what will be included, rather than the researchers. Many reviews from criminology and psychology take such an approach, even if they do not explicitly refer to it as such. This approach seeks to "consider all data on all assessed risk factors for the outcome of interest and to compare the relative availability of data for each of the putative risk factors across the respective studies" (Serghiou, Patel, Tan, Koay, & Ioannidis, 2016, p. 59).
The field‐wide approach used by this review offers a number of potential benefits. First, it enables the identification of factors that are not as frequently considered as others. Second, it enables the assessment of the relative magnitude of factors. Third, it enables a comparison of the different factors and their magnitudes across a range of outcomes for the phenomenon under inquiry. Through the use of meta‐analytic techniques, this approach can also identify differential effects for factors in different contexts (e.g., US and the EU), as well as between different radicalizing doctrines (e.g., right‐wing, left‐wing, religious, etc) (Jensen, Atwell Seate, & James, 2018; Monahan, 2012, 2017). Given that there is great heterogeneity among violent offenders in general, and “one‐size‐fits‐all” solutions are inappropriate for this subfield of criminology as well (Widom, 2014), these benefits will enable the production of the type of evidence needed to assist in avoiding such pitfalls.
1.5. Why it is Important to do the review
As noted above, despite the growth in terrorism research, it continues to be lamented that empirical study accounts for only a small percentage of terrorism research, especially relating to risk factors (Christmann, 2012; Lum et al., 2006; Silke, 2008). This gap in the research has left it to policy makers to develop policies and strategies that are not grounded in evidence and which are based on untested theoretical assumptions and political considerations (Neumann & Kleinmann, 2013; Sageman, 2014; Victoroff, 2005). It seems that we do not actually know much about what risk factors should be being examined to assess the risk of future radical behaviors, or which should be targeted in order to reduce the risk of future radical behaviors, namely because we do not know what the risk and protective factors are (Scarcella, Page, & Furtado, 2016). Among the evidence that does exist are mixed and often contradictory findings (Allan, Glazzard, Jesperson, Reddy‐Tumu, & Winterbotham, 2015; Bondokji, Wilkinson, & Aghabi, 2017; Victoroff, 2005). We also know very little about the relative magnitude and clustering of risk and protective factors. That is, we do not know whether, for example, unemployment is more or less important than education (Crenshaw, 2007; Gill, 2016; Hafez & Mullins, 2015; Haggerty & Bucerius, 2018; Staring, 2014).
Recently Scarcella et al. (2016) conducted a systematic review on methodologies used to perform risk assessments of individual radicalization. They found that for many of the tools used, even those that apparently take a more evidence‐based approach (e.g., Extremism Risk Guidelines [ERG22+]), the risk factors they included were not evidence‐based. On account of this, and related to the issue of absent and mixed evidence, most tools reviewed used a nominal scaling method, in which the presence or absence of each factor is given an equal weighting (Klausen, Campion, Needle, Nguyen, & Libretti, 2016). There are two dangers inherent in risk assessments used to predict future radical behavior based on misidentified or misspecified factors. First is the failure to properly identify those most at risk, which could result in a terror attack. Second is the false identification of those who pose little or no risk, which could lead to impinging on the rights of innocents, which also entails wide‐reaching social implications (Scarcella et al., 2016). Third, when used in the context of targeting dynamic factors in order to reduce the risk of future radical behavior, as in the context of the Risk‐Needs‐Responsivity approach, a poor identification of specific needs is likely to lead to unsuccessful intervention outcomes (Dean, 2016; Mullins, 2010).
To date, the only Campbell Collaboration systematic review that has been identified as being somewhat related to the current topic is Lum et al.'s (2006) review on counter‐terrorism policies. There have however been a few non‐Campbell reviews conducted on radicalization more generally; however, they either only refer to risk and protective factors in passing, or have otherwise been unable to provide any sort of quantitative synthesis of the evidence and (e.g., Christmann, 2012; Madriaza & Ponsot, 2015; McGilloway, Ghosh, & Bhui, 2015; Munton et al., 2011; Vergani, Iqbal, Ilbahar, & Barton, 2018). Some recent reviews have focused on specific factors, such as mental health (Misiak et al., 2019), and the Internet (Hassan et al., 2018); however, they too have been unable to provide any quantitative synthesis. To date, no review or meta‐analysis specifically on the topic of risk factors in radicalization and recruitment to terrorism.
The current review represents an important first step toward developing knowledge and understanding concerning what the putative risk and protective factors are, what their relative magnitude is. This will, of course, represent only a starting point in enabling the development of more scientifically based and effective interventions (Blum & Ireland, 2004; Borum, 2015; Piquero, Farrington, Welsh, Tremblay, & Jennings, 2009).
Beyond the direct contributions to the literature that this review will ultimately provide, the results of this review will also be utilized in the development of inputs for agent‐based modeling simulations that are being conducted by the reviewers as part of project PROTON, a Horizon 2020 funded project on the processes of radicalization and recruitment to terrorism. This project includes direct involvement and cooperation of leading policy makers from the European Union. Therefore, the results of this systematic review will play an important role in informing policy makers in the context of the development of evidence‐based policies.
2. OBJECTIVES
The primary objectives of this systematic review are to provide information that can help in answering important questions regarding the risk and protective factors associated with radicalization outcomes. As a field‐wide review, the first objective is to identify what the different individual‐level, putative risk, and protective factors are for which empirical evidence exists. The second objective is to categorize, organize, and arrange the factors in a series of rank orders according to their identified effect sizes in order to assess the relative importance of the different factors. The third objective is to identify areas of overlap and divergence in the effect sizes for the different factors across outcomes, and also between variables such as region (e.g., US and the EU) and ideological association (e.g., right‐wing, left‐wing, religious, etc). In summary, through the use of meta‐analytic techniques, this review seeks to address the following questions.
-
1.
What are the risk and protective factors associated with cognitive radicalization?
-
2.
What are the risk and protective factors associated with behavioral radicalization?
-
3.
What are the shared and differentiating risk factors for the different outcomes of radicalization?
-
4.
What are the relative magnitudes of the effect sizes for the different factors across the different outcomes?
-
5.
What are the sources of heterogeneity between factors as they pertain to different ideologies and radical doctrines (e.g., right‐wing and Islamist inspired), and to different regions (e.g., EU and the US)?
In addition, the review's secondary objectives are as follows.
-
6.
To provide guidance for a secondary systematic review that will focus on antiradicalization interventions and how risk factors can be mitigated.
-
7.
To provide data and inputs in the form of effect sizes to be used in the development of agent‐based modeling.
3. METHODOLOGY
3.1. Criteria for including and excluding studies
3.1.1. Types of studies
The literature is heavily characterized by studies representing theoretical discussions or literature reviews, with only a small percentage of studies being empirically based (Christmann, 2012; King & Taylor, 2011; Sageman, 2011; Silke, 2008), and an even smaller percent being quantitative (Neumann & Kleinmann, 2013; Schuurmann, 2018). This review seeks to extract only quantitative studies and excludes qualitative studies, including studies that are purely theoretical, provide theoretical models, literature reviews, opinion pieces, and those studies based on basic descriptive statistics. Given the nature of the review, we will collect data from studies employing case‐control, single‐sample longitudinal, and single‐sample cross‐sectional designs (see eligibility criteria below).
As Jolliffe, Murray, Farrington and Vannick (2012) explain, when conducting systematic reviews on risk factors—as opposed to interventions—there is a need, or at least a justification, for lowering the number of variables relating to the inclusion quality threshold. As such, with regards to these observational studies, the review will only include those studies which have an N of >50. With regard to the sampling methodology, a wide range of methods will be considered acceptable as long as they provide a reasonable basis for making inferences to the intended population of the review.
3.1.2. Dependent variables
In order for a study to be included in the review, the dependent variable(s) must be in line with at least one of the top two tiers of each of the pyramids in the TPM. For cognitive radicalization, this includes studies whose dependent variable(s) assess support for, justification of, or a willingness or intention toward the commission of radical violence or terrorism. The literature includes the use of some validated instruments for assessing these outcomes. Some examples of the most well‐known tools are listed and described in Table 1. Studies utilizing any of these or similar instruments, or adapted versions of these or similar instruments, will be eligible for inclusion in the review.
Table 1.
Examples of instruments used to measure cognitive radicalization
| Instrument name | Description | Example of usage |
|---|---|---|
| Sympathy for violent radicalization and terrorism (K. Bhui et al., 2014) | A 16‐item tool measuring sympathies and condemnations of radical behaviors from violent protest to suicide bombings | Rousseau et al. (2019) |
| Activism‐Radicalism‐Intentions Scales (Moskalenko & McCauley, 2009) | 10‐item tool assessing intentions to engage in legal and illegal forms of activism | Decker and Pyrooz (2019) |
| Pro‐Violence and Illegal Acts in Relation to Extremism Scale (Ozer & Bertelsen, 2018) | A six‐item tool using a seven‐point Likert scale | Ozer (2020) |
| Militant‐Extremist Mindset Pro‐Violence Subscale (Stankov, Higgins, Saucier, & Knežević, 2010) | A 10‐item subscale using a five‐point Likert scale | Vergani, O'Brien, Lentini, and Barton (2019) |
In addition, studies using other single‐ and multiple‐item measures will be eligible for inclusion when they are found to be in line with the above‐noted outcomes of the TPM. These measures may measure sympathy, support, or justification of general forms of radical violence, or may refer to specific types of radical violence (e.g., suicide bombings), or specific events of radical violence (e.g., 9/11, 7/7 bombings). Some examples are listed in Table 2.
Table 2.
Examples of nonvalidated measures of cognitive radicalization
| Measure | Assessment | Usage |
|---|---|---|
| Some people think that suicide bombing and other forms of violence against civilian targets are justified in order to defend Islam from its enemies. Other people believe that, no matter what the reason, this kind of violence is never justified. Do you personally feel that this kind of violence is often justified to defend Islam, sometimes justified, rarely justified, or never justified? | Four‐point scale: 1 = often, 4 = never | PEW report (see McCauley, 2012; Victoroff, Adelman, & Matthews, 2012) |
| What is your attitude towards the murder of Theo van Gogh, in November 2004? | Five‐point scale: 1 = very negative, 5 = very positive | Doosje, Loseman, and Van Den Bos (2013) |
| Some people said that the July (7/7) bombings were justified because of British support for the US war on terror. Do you agree? | Four‐point scale: 1 = strongly disagree, 4 = strongly agree | Tausch, Spears, and Christ (2009) |
For behavioral radicalization, this includes studies whose dependent variable(s) assess involvement in or commission of radical violence or terrorism offenses. For the most part, we expect that studies will measure having engaged in radical violence or terrorism offenses as a dichotomous variable (e.g., LaFree et al., 2018). However, when studies assess self‐reported involvement in radical violence they may employ an ordinal or interval measure that combines a variety of self‐reported behaviors (e.g., Pauwels & Schils, 2016).
3.1.3. Controls/sample
In order for a study to be included in the review, the sample must include a control or comparison group that does not display the outcome of interest. That is, a study's sample must display variation on the dependent variable. For example, in a cross‐sectional or longitudinal study examining support for terrorism, the sample must include respondents or participants who do not support terrorism. Similarly, in a case‐control study containing a sample of terrorists, it must also include a sample of nonterrorists or nonviolent terrorists.
3.1.4. Population
The review will include studies whose samples are made up of individuals. The review sets no limitations on the population of a sample based on the age, sex, race, or religion of the sample or those included in it. The review sets no limitations based on the ideological doctrine associated with the inquiry of the study being assessed for inclusion and will include studies that assess radicalization outcomes across the entire spectrum of guiding doctrines (e.g., religious, right‐wing, left‐wing, ethno‐nationalist and single issue, etc). As detailed ahead (see Section 3.1.7******), populations will only be limited by the geographic locations from which they are drawn.
The populations that will be included will, therefore, include terrorists, behavioral radicals, cognitive radicals, and individuals not displaying these outcomes who form part of the larger control or comparison portion of the sample.
3.1.5. Types of risk and protective factors
According to Kraemer et al. (1997), for a factor to be classified as a risk factor, it must demonstrate a predictive quality and also be shown as having been present prior to the outcome (e.g., radicalization, recruitment, or terrorism). Theoretically, only single‐sample longitudinal studies can establish the temporal ordering of factors, namely that an independent predictor preceded the outcome temporally (Murray, Farrington, & Eisner, 2009). This means that even for case‐control or cross‐sectional studies, even when employing regression techniques that may produce results showing a predictive quality of a given factor, temporal ordering is still absent. Nevertheless, when a factor is found to correlate with the outcome of interest in the theorized direction, we can classify it as a “putative factor” (Kraemer et al., 1997, Kraemer, Stice, Kazdin, Offord, & Kupfer, 2001). Such a classification is common in psychology (e.g., May & Klonsky 2016), criminology (Assink et al., 2019), and radicalization research (K. S. Bhui, Hicks, Lashley, & Jones, 2012; Lloyd & Dean, 2015; Monahan, 2012).
For the purposes of the current study, we refer to all factors that display a positive or negative correlation with one of the included outcomes of interest as being a “putative risk/protective factor,” respectively, even though some factors could be characterized as risk factors (Jacobi, Hayward, de Zwaan, Kraemer, & Agras, 2004). As such, we derive effect sizes for such factors, as described below (see Section 3.8****), from case‐control, longitudinal, and cross‐sectional studies using a combination of the correlation matrices, descriptive factors, and/or partial effect sizes/coefficients from regression models.
As a field‐wide review, no specific factors are specifically sought and no predeterminations will be made as to which factors will be identified, and as such does not include any outcome labels in its search terms (Murray et al., 2009; Serghiou et al., 2016). We will include all individual‐level factors, including both static and dynamic factors, that can be said to fall under domains such as, but not limited to: socio‐demographic, experiential and background, social, psychological, economic, socio‐economic, socio‐psychological, environmental, or push, pull, and personal factors. Based on our initial examination of the literature, the below list provides some of the most commonly discussed and studied factors, and those that are likely to be included the review (this list is not exhaustive nor should it be taken to be representative of what will feature in the final review).
Individual and experiential characteristics
Age, gender, education, immigrant status, marital status, criminal history, drug and alcohol use, victimization, encounters with police and procedural justice, trauma, and so forth.
Social factors
Discrimination, marginalization, ostracism/isolation, societal connectedness, previous criminal history, poor employment history, family issues, immigrant status, Religion, community, discrimination, political grievances, policing and counter‐terrorism, access to social services such as education and healthcare, education level, media influence, peer groups, Collective efficacy, legitimacy, and so forth.
Economic factors
Unemployment, real poverty, perceived poverty, economic disparity, real and relative deprivation, wage gap, income level, individual socio‐economic class, meso‐level (community level) economic situation, property ownership/housing status, welfare situation, and so forth.
Psychological factors
Mental illness, depression, anxiety disorder, narcissism, neurological problems, slow motor development, lack of empathy, ideological mentality, utopian/messianic worldview, dualistic mentality, personal grievance, personality traits (e.g., low self‐control, anger, hate, authoritarianism/fundamentalism), and so forth.
3.1.6. Measurement of outcomes and risk/protective factors
As described above, the review will include studies whose measurement of both outcomes and factors are dichotomous, ordinal, discrete, or continuous, and which will be based off of a range of instruments and forms of coding. Measures of outcomes and factors will be derived from self‐reported, family reported, government reported, law‐enforcement reported, practitioner reported, and open‐source database‐generated data.
The review will employ the appropriate statistical conversions in order to enable the grouping of effect sizes based on these different measures into single analyses.
3.1.7. Types of settings
Systematic reviews on risk factors for behavioral outcomes, such as violence, delinquency, and gang involvement, are often examined separately between high‐income and low‐middle income countries. The rationale is that the macrolevel settings and contexts are too dissimilar and as such, issues of heterogeneity would mask the true effects. As such, there is great methodological value to narrow risk factor systematic reviews to specific types of contexts (Higginson et al., 2015; Murray et al., 2018). In addition, there may be added methodological value in the separating of searches based on country and country type, including with regard to the databases that should be searched and also with respect to the synthesis of the data identified (Shenderovich et al., 2016).
It is often pointed out in the literature that the “driving factors” of terrorism are quite different between democratic and nondemocratic countries. In addition, trends in terrorism, as well as radicalization processes appear to be quite different between these different regime types (GTI, 2016). Taking such issues into consideration, some researchers have recognized the importance of examining democracies and nondemocracies separately with regard to terrorism‐related studies, since aggregated analyses often produce confounding results. Similarly, some researchers examine terrorism and violence‐related issues separately between high‐income and low‐income countries (e.g., Enders & Hoover, 2012). While both these approaches have methodological value and a similar theoretical underpinning, this review has chosen to the former approach, since democratic countries represent open societies, coupled with economic prosperity, and therefore provide similar societal (macro) and community level (meso) contexts. In addition, terrorism in democratic countries appears to be more prevalent and more stable. Furthermore, the recent rise in the threat of terrorism in such countries demands further development of our understanding risk factors leading to radicalization that are specific to such places.
Since there is no established preference as to whether reviews should separate by income or regime type, in this review, we seek to bridge these approaches by limiting our inclusion to democratic countries that are also Organization for Economic Co‐Operation and Development (OECD) countries. As such, the Democracy Index was cross‐matched with the OECD countries, resulting in the inclusion of all 37 OECD countries with the only exclusion being Turkey. In order for a study to be included in the review, the majority of its sample must come from at least one of the included countries, and the country must have met the criteria for inclusion in this list at the time at which the study was carried out, or at the time period in which the sample was collected from (Table 3).
Table 3.
List of included countries
| Australia | Czech republic | Greece | Japan | Netherlands | Slovenia |
| Austria | Denmark | Hungary | Korea | New Zealand | Spain |
| Belgium | Estonia | Iceland | Latvia | Norway | Sweden |
| Canada | Finland | Ireland | Lithuania | Poland | Switzerland |
| Chile | France | Israel | Luxemburg | Portugal | UK |
| Columbia | Germany | Italy | Mexico | Slovakia | USA |
3.1.8. Languages
Primary searches will be conducted in English as the overwhelming majority of relevant studies will at least be indexed in English and/or have abstracts in English. Supplementary searches will also be conducted in Dutch and German as relevant research that may not have been translated is known to exist. Relevant studies that are found to be published in any other language will be sent for translation.
3.1.9. Exclusion criteria
The following types of studies will be excluded.
-
1.
Studies examining radicalization and recruitment in nondemocratic countries.
-
2.
Studies examining general political radicalism/political extremism as generally assessed by; support for specific types or sets of legitimate policies, such as those pertaining to immigration, or crime and punishment, or legal political parties running in elections (including using voting for legal parties as a proxy).
-
3.
Studies examining radicalization by way of analyzing antidemocratic attitudes, anti‐western attitudes, or racist, xenophobic, or anti‐semitic attitudes as a proxy for radicalism.
-
4.
Studies examining general violence and racially motivated violence.
-
5.
Studies examining predictors of the occurrence of terrorism events.
-
6.
Studies examining differences between activities or events between groups or countries.
3.1.10. Relevance decisions
The first stage of the review process will consist of two trained reviewers conducting searches and making initial judgments regarding study suitability and inclusion based on title and abstract reviews. In addition, the following will be considered.
-
1.
An extraction sheet (excel format) will be used and completed for a study that passes the first threshold based on title and abstract. During data extraction, a quality/inclusion checklist will be used (see Supplorting information materials).
-
2.
An assessment tool to check for reviewer consensus will be used. Where a study has been selected by only one of the reviewers, it will subsequently be checked by a senior reviewer where the full text of the article will be reviewed and the senior reviewer will then present their decision to the two reviewers.
-
3.
In order to minimize reviewer inclusion bias, senior reviewers will analyze a sample of 5% of included studies and check for rater reliability.
3.2. Search strategy
The review will search for both published and unpublished literature based on the above inclusion criteria. The search terms have been developed in order to increase the likelihood that the most relevant studies will not be missed and so that the literature on risk factors will be broadly covered. Specifically, there is a delicate balance between sensitivity and specificity, and this varies greatly between different databases. It was decided that none of the outcomes would be part of our search terms in order to avoid limiting the number of relevant studies that may come from other fields, such as psychology. Our familiarity with the current body of literature has also been the basis for the decision to utilize the range of different terms that are used to describe radicalization and recruitment to terrorism and which can often be found in the different literatures that study these issues. As has been noted in the literature on systematic reviews, reviews dealing with risk factors may have limited search tiers due to the need to balance sensitivity and search precision (Hammerstrøm, Wade, Hanz, & Jørgensen, 2009; Shenderovich et al., 2016). Following is a list of our four search tiers.
-
1.
Radical* OR recruit* OR extrem* OR violent extrem* OR violent radical* OR foreign fighter* OR Terror* OR Lone wol* OR lone‐wol* OR homegrown OR home‐grown OR sympath* OR support OR OR Justif* OR facilitate OR engage* OR activis*
-
2.
Jihad* OR Islam* OR Salaf* OR right‐wing OR neo‐Nazi OR far‐right OR nationalist OR white‐supremacist OR left wing OR extreme left OR anarchist OR single‐issue
-
3.
*Risk* OR *factor* OR predict* OR propensity OR likelihood OR predispose* OR predisposition OR vulnerab* OR causal OR putative OR determinant OR Root OR correlate*
-
4.
*Democra* OR West* OR Europ* OR "country name"
Search strings will be applied on the databases mentioned in Table 4.
Table 4.
Databases in which searches will be performed
|
|
In addition, as this review is being carried out as part of a larger research project, we will include relevant studies being conducted by members of the research consortium. We expect that at least 1–2 of these studies will fit our inclusion criteria. In addition, whilst searches are ongoing, leading researchers and research institutions will be contacted in an effort to try and identify unpublished research and gray literature. We will also share the protocol and the list of included studies at the time contact is made with these researchers to better assist them in assessing whether they are aware of any missing studies that would meet the inclusion criteria.
3.3. Pilot search
Based on the above‐mentioned inclusion and exclusion criteria, pilot searches were conducted on PsychInfo (Ovid). This search engine was chosen since it is known to contain essential studies pertaining to radicalization. We carried out a number of pilot searches to test the balance of sensitivity and specificity of our search strings. To ensure that our search strategy was capturing the studies of relevance, we carried out multiple search combinations. One example pilot search utilized a two tier search strings “((radicalization or radicalization or radical or terrorism) and (risk factor or risk or vulnerability or association or associated)).ti. and (radicalization or radicalization or radical or terrorism).ab. and (risk factor or risk or vulnerability or association or associated).ab,” where only titles and abstracts were searched using the search filters for titles and abstracts. An initial 82 results were returned from this search. Based on a skimming review of the citations and abstracts, the four studies passed to the extraction phase. Subsequently, two of these studies were excluded based on criteria pertaining to their settings (Table 5).
Table 5.
Pilot search excerpt
| Reference | Study design | Incl/Excl |
|---|---|---|
| Elbakidze, L. & Jin, Y. H., Are economic development and education improvement associated with participation in transnational terrorism? Risk Analysis. Vol. 35(8), 2015, pp. 1520‐1535 | Cross‐sectional | Excluded based on dependent variable |
| Najeeb Shafiq, M., & Sinno, A. H. (2010). Education, income, and support for suicide bombings: Evidence from six Muslim countries. Journal of Conflict Resolution, 54(1), 146‐178 | Cross‐sectional | Excluded based on country |
| Bhui K, Warfa N, Jones E., Is violent radicalisation associated with poverty, migration, poor self‐reported health and common mental disorders? PLoS ONE 9(3), 2014 | Cross‐sectional | Included |
| Krueger, A. B. (2008). What makes a homegrown terrorist? Human capital and participation in domestic Islamic terrorist groups in the USA. Economics Letters, 101(3), 293‐296 | Case‐control | Included |
3.4. Description of methods used in primary research
Based on the reviewers' familiarity with the current body of literature, including from a wide range of disciplines, we expect that the majority of studies will be single‐sample cross‐sectional studies examining different outcomes associated with cognitive radicalization. These studies, together with the odd longitudinal study, generally provide descriptive statistics, bivariate correlations, as well as multivariate models employing different regression techniques and path analyses. The majority of these studies are expected to be based off of self‐reported measures.
Case‐control studies, which may compare cognitive or behavioral radicals (e.g., terrorists) with a sample of those not displaying the outcome, may provide descriptive statistics, bivariate correlations, null‐hypothesis tests such as t tests, χ2 tests, F tests, as well as multivariate models employing different regression techniques. Most of these studies are expected to be based off of open‐source based databases which have been constructed from a variety of sources. While control group samples may also be derived from similar sources, they may also be based off of self‐reported measures or clinician‐reported measures.
3.5. Criteria for determination of independent findings
Our pilot searches have revealed that some studies base their analyses on the same secondary datasets (e.g., Pew Report, 2007). Other studies may report multiple statistical models. As such, in order to maintain independence of findings, a single report will only be allowed to provide one effect size for each risk factor. Where multiple effect sizes are reported for the same risk factor, an internal meta‐analysis will be conducted in order to obtain a single, pooled effect size (Higginson et al., 2014). A similar approach will be followed for studies based on the same original datasets published by the same authors since sometimes the same set of authors will conduct different studies based on the same datasets. As such, the reviewers will attempt to identify any overlaps of this nature and where possible will conduct an internal meta‐analysis and bias assessment. This assessment will be based on the completeness of the data and the risk of bias assessment of the studies, and all decisions will be reported in the final review.
3.6. Details of study coding categories
The data extraction and coding will be based on a code book that is made up of 70 items and which includes categories relating to publication information, methodology, study‐level characteristics, risk of study bias, the outcomes (risk and protective factors) included in the study, and the authors' conclusions (see Supporting Information Material). Following each set of 200 decisions, a random sample of 10 decisions (or 5%) will be chosen and intercoder reliability will be checked using κ statistical testing.
3.7. Assessment of methodological quality and risk of bias
We will use a risk of bias tool and apply it through a set of questions in the coding fields of the extraction tool shown in the Supporting Information Material (Higginson, Mazerolle, Ham Benier, & Bedford, 2014). Study quality assessment will be carried out by two trained reviewers. If there is disagreement, it will be mediated by a third member of the team, who will not be blind to the original quality assessment and who will make any final decisions. In the event that discrepancies arise in the coding stage, a senior reviewer will perform a review and make the final decisions.
3.8. Statistical procedures and conventions
This review will carry out a series of meta‐analyses, with a separate analysis being conducted for each factor for which two or more inputs, derived from two or more unique samples are identified. All effect sizes will be calculated as r and subsequently transformed to Fisher's Z in order to approximate a normal sampling distribution and achieve a more stable variance across different values (Borenstein, Hedges, Higgins, & Rothstein, 2009; Rosenthal, 1984). Fisher's Z will thus be used as the input for the meta‐analyses, as well as the statistic used for reporting of the outputs.
Studies such as the current review, which examine multiple factors and outcomes, generally use bivariate correlations for imputing effect size. Compared to effect sizes derived from multivariate models, bivariate effect sizes are more consistent and uncontaminated between studies (Hanushek & Jackson, 1977; Hunter & Schmidt, 2004; Pratt, Turanovic, Fox, & Wright, 2014). However, some studies may not provide correlation matrices, or sufficient descriptive data to enable the calculation of bivariate correlations. Instead, they may only report the results from a range of different types of multivariate regression models. In such cases, we will first contact the authors of the publication to attempt to acquire data needed to calculate bivariate effect sizes (Aloe & Thompson, 2013). Where such information is not forthcoming, we will standardize the partial effect sizes to be included as supplementary effect sizes (e.g., Higginson et al., 2014; Najaka, Gottfredson, & Wilson, 2001; Wong, Slotboom, & Bijleveld, 2010). While not ideal, this approach is preferable to conducting multiple separate meta‐analyses for each risk factor split by effect size measurement type, which would entail losing important data (Borenstein et al., 2009). In such instances, where there are more than two effect sizes from each category of derivation, metaregression will be used in order to assess whether the source of effect size derivation has an impact on the pooled estimate and the results will be reported (Aloe, Tanner‐Smith, Becker, & Wilson, 2016).
With regard to the calculation of effect sizes when no correlation matrix is available but the study includes adequate descriptive statistics, we will utilize the available information to calculate effect sizes using the appropriate formulas for the type of data present in accordance with Lipsey and Wilson's (2001) conventions by way of the "Practical Meta‐Analysis Effect Size Calculator" available through the Campbell Collaboration website.
With regard to the standardization of partial effects sizes, there are no standard conventions (Aloe & Thompson, 2013). As such, we adopt a number of widely accepted methods for each of the different types of measures that we anticipate will be encountered.
-
1.For linear regression models where the independent variable (IV) and dependent variable (DV) are both continuous, we calculate r as
-
2.In situations in which standard deviations (SD) are not reported, or when the IV is dichotomous and the DV is continuous, or where the IV is ordinal or continuous and the DV is dichotomous, r will be calculated based on the t ratio (B/SE)
-
3.
In instances in which both IV and DV are dichotomous, and only B is reported, we will first calculate Cohen's d and then convert this to r as follows:
where only the odds ratio (Exp. B) is reported, r will be calculated as
Biostat's Comprehensive Meta‐Analysis (CMA) software (Borenstein et al., 2009) will be used for performing the meta‐analyses, including tests for publication bias, metaregressions, and moderator analyses. Random effects models will be used in order to deal with the expected homogeneity of the studies that will be included and which will also undoubtedly arise from the use of primarily correlational data from the types of observational studies that the review anticipates to include. In addition, risk factor effect sizes are often more heterogeneous than for interventions, in part because they are being examined among vastly different populations. For imputation, studies will be weighted based on their sample size. We will utilize the random effects estimator for τ2, the between‐study variance, that is preprogrammed in CMA V3, which is the Method of Moments approach of DerSimonian and Laird (1986).
3.9. Moderator analyses
The review will code a number of key study‐level characteristics: see Table 6.
Table 6.
Study‐level characteristics
| Variable | Description |
|---|---|
| Effect size derivation | Categorical: effect size derived from bivariate or partial effect size |
| Age | Continuous: mean age of the sample |
| Gender composition | Continuous: proportion of the sample that is male |
| Year | Continuous: last year of data collection |
| Ideology | Categorical: right‐wing, left‐wing, religious, and so forth |
| Region | Categorical: US, EU, other |
Other possible study‐level characteristics for coding include: whether the outcome variable used a validated instrument, whether the risk/protective variable used a validated instrument, the measurement of the outcome or independent variable, whether a study was published or unpublished, and whether the study was in a language other than English.
A series of metaregression analyses will be carried out in order to assess the degree to which such factors may impact the results. Limitations for these analyses will be based on the number of studies included in each analysis, and whether, especially in the case of categorical variables, there are enough studies from each category in order to enable such analysis.
CONFLICT OF INTERESTS
The authors declare that there are no conflict of interests.
AUTHOR CONTRIBUTIONS
M. W. and B. H. contributed to the content. Y. L. and D. W. contributed to systematic review methods. M. W. and D. W. contributed to statistical analysis. M. W. and Y. L. contributed to information retrieval.
Supporting information
Supporting information
ACKNOWLEDGMENTS
This study was supported by the Horizon 2020 Grant 699824 and the Campbell Collaboration DHS systematic review grant.
Wolfowicz M, Litmanovitz Y, Weisburd D, Hasisi B. PROTOCOL: Cognitive and behavioral radicalization: A systematic review of the putative risk and protective factors. Campbell Systematic Reviews. 2020;16:e1102. 10.1002/cl2.1102
REFERENCES
- Agerschou, T. (2014). Preventing radicalization and discrimination in Aarhus. Journal for Deradicalization, 1, 5–22. [Google Scholar]
- Ajzen, I., & Fishbein, M. (1980). Understanding attitudes and predicting social behavior. Englewood Cliffs, NJ: Prentice‐Hall. [Google Scholar]
- Ajzen, I. (1988). Attitudes, personality, and behavior. Milton Keynes: Open University Press. [Google Scholar]
- Allan, H., Glazzard, A., Jesperson, S., Reddy‐Tumu, S., & Winterbotham, E. (2015). Drivers of violent extremism: Hypotheses and literature. London, UK: Royal United Services Institute. [Google Scholar]
- Aloe, A. M., & Thompson, C. G. (2013). The synthesis of partial effect sizes. Journal of the Society for Social Work and Research, 4(4), 390–405. [Google Scholar]
- Aloe, A. M., Tanner‐Smith, E. E., Becker, B. J., & Wilson, D. B. (2016). Synthesizing bivariate and partial effect sizes. The Campbell Collaboration, Oslo, 12, 1–9. [Google Scholar]
- Assink, M., van der Put, C. E., Meeuwsen, M. W., de Jong, N. M., Oort, F. J., Stams, G. J. J., & Hoeve, M. (2019). Risk factors for child sexual abuse victimization: A meta‐analytic review. Psychological Bulletin, 145, 459–489. [DOI] [PubMed] [Google Scholar]
- Bartlett, J., Birdwell, J., & King, M. (2010). The edge of violence: A radical approach to extremism. London, UK: Demos, 5–75.
- Bélanger, J. J., Caouette, J., Sharvit, K., & Dugas, M. (2014). The psychology of martyrdom: Making the ultimate sacrifice in the name of a cause. Journal of Personality and Social Psychology, 107(3), 494–515. [DOI] [PubMed] [Google Scholar]
- Beller, J., & Kröger, C. (2017). Is religious fundamentalism a dimensional or a categorical phenomenon? A taxometric analysis in two samples of youth from Egypt and Saudi Arabia. Psychology of Religion and Spirituality, 9(2), 158–164. [Google Scholar]
- Bhui, K. S., Hicks, M. H., Lashley, M., & Jones, E. (2012). A public health approach to understanding and preventing violent radicalization. BMC Medicine, 10(1), 16. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Bhui, K., Warfa, N., & Jones, E. (2014). Is violent radicalisation associated with poverty, migration, poor self‐reported health and common mental disorders? PLoS One, 9(3), e90718. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Blum, R. W., & Ireland, M. (2004). Reducing risk, increasing protective factors: Findings from the Caribbean Youth Health Survey. Journal of Adolescent Health, 35(6), 493–500. [DOI] [PubMed] [Google Scholar]
- Bondokji, N., Wilkinson, K., & Aghabi, L. (2017). Trapped between destructive choices: Radicalisation drivers affecting youth in Jordan. Amman, Jordan: WANA Institute. [Google Scholar]
- Borenstein, M., Hedges, L. V., Higgins, J. P., & Rothstein, H. R. (2009). Introduction to meta‐analysis. Hoboken, NJ: John Wiley & Sons. [Google Scholar]
- Borum, R. (2011a). Radicalization into violent extremism I: A review of social science theories. Journal of Strategic Security, 4(4), 2–36. [Google Scholar]
- Borum, R. (2011b). Radicalization into violent extremism II: A review of conceptual models and empirical research. Journal of Strategic Security, 4(4), 3–62. [Google Scholar]
- Borum, R. (2015). Assessing risk for terrorism involvement. Journal of Threat Assessment and Management, 2(2), 63–87. [Google Scholar]
- Brynielsson, J., Horndahl, A., Johansson, F., Kaati, L., Mårtenson, C., & Svenson, P. (2013). Harvesting and analysis of weak signals for detecting lone wolf terrorists. Security Informatics, 2(1), 11. [Google Scholar]
- Christmann, Kris (2012). Preventing religious radicalisation and violent extremism: A systematic review of the research evidence. London, UK: Youth Justice Board for England and Wales.
- Clarke, R., & Newman, G. (2006). Outsmarting the terrorists. London, UK: Praeger. [Google Scholar]
- Crenshaw, M. (2007). Explaining suicide terrorism: A review essay. Security Studies, 16(1), 133–162. [Google Scholar]
- Davis, W. L. (2014). Terrorism, homeland security, and risk assessment via research proposal (3rd ed.). Bloomington, IN: Xlibris. [Google Scholar]
- Dean, C. (2016). Addressing Violent Extremism in Prisons and Probation. Policy Brief. Global Center on Cooperative Security. [Google Scholar]
- Decker, S. H., & Pyrooz, D. C. (2019). Activism and radicalism in prison: Measurement and correlates in a large sample of inmates in Texas. Justice Quarterly, 36(5), 787–815. [Google Scholar]
- DerSimonian, R., & Laird, N. (1986). Meta‐analysis in clinical trials. Controlled Clinical Trials, 7(3), 177–188. [DOI] [PubMed] [Google Scholar]
- Doosje, B., Loseman, A., & Van Den Bos, K. (2013). Determinants of radicalization of Islamic youth in the Netherlands: Personal uncertainty, perceived injustice, and perceived group threat. Journal of Social Issues, 69(3), 586–604. [Google Scholar]
- Doosje, B., Moghaddam, F. M., Kruglanski, A. W., De Wolf, A., Mann, L., & Feddes, A. R. (2016). Terrorism, radicalization and de‐radicalization. Current Opinion in Psychology, 11, 79–84. [Google Scholar]
- Ellis, B. H., Abdi, S. M., Lazarevic, V., White, M. T., Lincoln, A. K., Stern, J. E., & Horgan, J. G. (2016). Relation of psychosocial factors to diverse behaviors and attitudes among Somali refugees. American Journal of Orthopsychiatry, 86(4), 393–408. [DOI] [PubMed] [Google Scholar]
- Enders, W., & Hoover, G. A. (2012). The nonlinear relationship between terrorism and poverty. American Economic Review, 102(3), 267–72. [Google Scholar]
- Esbensen, F. A., Peterson, D., Taylor, T. J., & Freng, A. (2009). Similarities and differences in risk factors for violent offending and gang membership. Australian & New Zealand Journal of Criminology, 42(3), 310–335. [Google Scholar]
- European Commission . (2005a). Council of Europe Convention on the prevention of terrorism. Warsaw, Poland: Council of Europe Treaty Series, No. 196.
- European Commission (2005b). The European Union counter‐terrorism strategy. Brussels, Belgium: European Commission.
- European Commission (2014). Communication from the Commission to the European Parliament, the Council, the European Economic and Social Committee and the Committee of the Regions: Preventing radicalisation to terrorism and violent extremism: Strengthening the EU's response. Brussels, Belgium: European Commission.
- Farrington, D. P., Ttofi, M. M., & Piquero, A. R. (2016). Risk, promotive, and protective factors in youth offending: Results from the Cambridge study in delinquent development. Journal of Criminal Justice, 45, 63–70. [Google Scholar]
- Fincham, F.D., Cui, M., Braithwaite, S., & Pasley, K. (2008). Attitudes toward intimate partner violence in dating relationships. Psychological Assessment, 20(3), 260–269. [DOI] [PubMed] [Google Scholar]
- Fishbein, M., & Ajzen, I. (1975). Belief, attitude, intention and behavior: An introduction to theory and research. Boston, MA: Addison‐Wesley. [Google Scholar]
- Folk, J. B., Stuewig, J. B., Blasko, B. L., Caudy, M., Martinez, A. G., Maass, S., … Tangney, J. P. (2018). Do demographic factors moderate how well criminal thinking predicts recidivism? International Journal of Offender Therapy and Comparative Criminology, 62(7), 2045–2062. [DOI] [PubMed] [Google Scholar]
- Gendreau, P., Little, T., & Goggin, C. (1996). A meta‐analysis of the predictors of adult offender recidivism: What works! Criminology, 34(4), 575–608. [Google Scholar]
- Gill, P. (2016). Toward a scientific approach to identifying and understanding indicators of radicalization and terrorist intent: Eight key problems. Journal of Threat Assessment and Management, 2(3), 187–191. [Google Scholar]
- Gøtzsche‐Astrup, O. (2018). The time for causal designs: Review and evaluation of empirical support for mechanisms of political radicalisation. Aggression and Violent Behavior, 39, 90–99. [Google Scholar]
- GTI . (2016). Global Terrorism Index 2016: Measuring and understanding the impact of terrorism. New York, NY: The Institute for Economics and Peace. [Google Scholar]
- Hafez, M., & Mullins, C. (2015). The radicalization puzzle: A theoretical synthesis of empirical approaches to homegrown extremism. Studies in Conflict & Terrorism, 38(11), 958–975. [Google Scholar]
- Haggerty, K. D., & Bucerius, S. M. (2018). Radicalization as martialization: Towards a better appreciation for the progression to violence. Terrorism and Political Violence, 32, 1–21. [Google Scholar]
- Hammerstrøm, K., Wade, A., Hanz, K., & Jørgensen, A. (2009). Searching for studies: Information retrieval methods group policy brief. Oslo, Norway: Campbell Information Retrieval Methods Group. [Google Scholar]
- Hanushek, E. J., & Jackson, E. (1977). Statistical methods for social scientists. New York, NY: Academic Press. [Google Scholar]
- Hassan, G., Brouillette‐Alarie, S., Alava, S., Frau‐Meigs, D., Lavoie, L., Fetiu, A., … Sieckelinck, S. (2018). Exposure to extremist online content could lead to violent radicalization: A systematic review of empirical evidence. International Journal of Developmental Science, 12(1‐2), 71–88. [Google Scholar]
- Herrenkohl, T. I., Maguin, E., Hill, K. G., Hawkins, J. D., Abbott, R. D., & Catalano, R. F. (2000). Developmental risk factors for youth violence. Journal of adolescent health, 26(3), 176–186. [DOI] [PubMed] [Google Scholar]
- Higginson, A., Mazerolle, L., Ham Benier, K., & Bedford, L. (2014). Predictors of youth gang membership in low‐and middle‐income countries: A systematic review. Campbell Systematic Reviews, 10, 1–67. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Higginson, A., Murray, J., Benier, K., Shenderovich, Y., Bedford, L., & Mazerolle, L. (2014). PROTOCOL: Predictors of youth gang membership in low‐and middle‐income countries: A systematic review. Campbell Collaboration, 10(1), 1–67. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Higginson, A., Benier, K., Shenderovich, Y., Bedford, L., Mazerolle, L., & Murray, J. (2015). Preventive interventions to reduce youth involvement in gangs and gang crime in low‐and middle‐income countries: A systematic review. Campbell Collaboration, 11(1), 1–176. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hill, K. G., Howell, J. C., Hawkins, J. D., & Battin‐Pearson, S. R. (1999). Childhood risk factors for adolescent gang membership: Results from the Seattle Social Development Project. Journal of Research in Crime and Delinquency, 36(3), 300–322. [Google Scholar]
- Horgan, J. (2008). From profiles to pathways and roots to routes: Perspectives from psychology on radicalization into terrorism. The Annals of the American Academy of Political and Social Science, 618(1), 80–94. [Google Scholar]
- Horgan, J., Shortland, N., Abbasciano, S., & Walsh, S. (2016). Actions speak louder than words: A behavioral analysis of 183 individuals convicted for terrorist offenses in the United States from 1995 to 2012. Journal of Forensic Sciences, 61(5), 1228–1237. [DOI] [PubMed] [Google Scholar]
- Hunter, J. E., & Schmidt, F. L. (2004). Methods of meta‐analysis: Correcting error and bias in research findings. Thousand Oaks, CA: Sage Publications. [Google Scholar]
- Jacobi, C., Hayward, C., de Zwaan, M., Kraemer, H. C., & Agras, W. S. (2004). Coming to terms with risk factors for eating disorders: Application of risk terminology and suggestions for a general taxonomy. Psychological Bulletin, 130(1), 19–65. [DOI] [PubMed] [Google Scholar]
- Jensen, M. A., Atwell Seate, A., & James, P. A. (2018). Radicalization to violence: A pathway approach to studying extremism. Terrorism and Political Violence, 1–24. [Google Scholar]
- Jolliffe, D., Murray, J., Farrington, D., & Vannick, C. (2012). Testing the Cambridge Quality Checklists on a review of disrupted families and crime. Criminal Behaviour and Mental Health, 22(5), 303–314. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Kazdin, A. E., Kraemer, H. C., Kessler, R. C., Kupfer, D. J., & Offord, D. R. (1997). Contributions of risk‐factor research to developmental psychopathology. Clinical Psychology Review, 17(4), 375–406. [DOI] [PubMed] [Google Scholar]
- King, M., & Taylor, D. M. (2011). The radicalization of homegrown jihadists: A review of theoretical models and social psychological evidence. Terrorism and Political Violence, 23(4), 602–622. [Google Scholar]
- Khalil, J. (2014). Radical beliefs and violent actions are not synonymous: How to place the key disjuncture between attitudes and behaviors at the heart of our research into political violence. Studies in Conflict & Terrorism, 37(2), 198–211. [Google Scholar]
- Klausen, J., Libretti, R., Hung, B. W., & Jayasumana, A. P. (2018). Radicalization trajectories: An evidence‐based computational approach to dynamic risk assessment of “Homegrown” jihadists. Studies in Conflict & Terrorism, 43, 1–28. [Google Scholar]
- Klausen, J., Campion, S., Needle, N., Nguyen, G., & Libretti, R. (2016). Toward a behavioral model of “homegrown” radicalization trajectories. Studies in Conflict & Terrorism, 39(1), 67–83. [Google Scholar]
- Koopmans, R. (2015). Religious fundamentalism and hostility against out‐groups: A comparison of Muslims and Christians in Western Europe. Journal of Ethnic and Migration Studies, 41(1), 33–57. [Google Scholar]
- Kraemer, H. C., Kazdin, A. E., Offord, D. R., Kessler, R. C., Jensen, P. S., & Kupfer, D. J. (1997). Coming to terms with the terms of risk. Archives of General Psychiatry, 54(4), 337–343. [DOI] [PubMed] [Google Scholar]
- Kraemer, H. C., Stice, E., Kazdin, A., Offord, D., & Kupfer, D. (2001). How do risk factors work together? Mediators, moderators, and independent, overlapping, and proxy risk factors. American journal of psychiatry, 158(6), 848–856. [DOI] [PubMed] [Google Scholar]
- Kruglanski, A. W., Jasko, K., Chernikova, M., & Milyavsky, M. (2018). The rocky road from attitudes to behaviors: Charting the goal systemic course of actions, The Motivated Mind (pp. 261–306). London, UK: Routledge. [DOI] [PubMed] [Google Scholar]
- LaFree, G., & Dugan, L. (2004). How does studying terrorism compare to studying crime? Terrorism and counter‐terrorism (pp. 53–74). Bingley, UK: Emerald Group Publishing Limited. [Google Scholar]
- LaFree, G., Jensen, M. A., James, P. A., & Safer‐Lichtenstein, A. (2018). Correlates of violent political extremism in the United States. Criminology, 56(2), 233–268. [Google Scholar]
- Leuprecht, C., Hataley, T., Moskalenko, S., & McCauley, C. (2010). Containing the narrative: Strategy and tactics in countering the storyline of global jihad. Journal of Policing, Intelligence and Counter Terrorism, 5(1), 42–57. [Google Scholar]
- Lipsey, M. W., & Wilson, D. B. (2001). Practical meta‐analysis. Thousand Oaks, CA: SAGE Publications, Inc. [Google Scholar]
- Lloyd, M., & Dean, C. (2015). The development of structured guidelines for assessing risk in extremist offenders. Journal of Threat Assessment and Management, 2(1), 40–52. [Google Scholar]
- Lösel, F., & Farrington, D. P. (2012). Direct protective and buffering protective factors in the development of youth violence. American Journal of Preventative Medicine, 43(2S1), S8–S23. [DOI] [PubMed] [Google Scholar]
- Lösel, F., King, S., Bender, D., & Jugl, I. (2018). Protective factors against extremism and violent radicalization: A systematic review of research. International Journal of Developmental Science, 12(1‐2), 89–102. [Google Scholar]
- Lum, C., Kennedy, L. W., & Sherley, A. (2006). The effectiveness of counter‐terrorism strategies: A Campbell systematic review. Washington, DC: Crime and Justice Coordinating Group, The Campbell Collaboration.
- Madriaza, P., & Ponsot, A. S. (2015). Preventing radicalization: A systematic review. Montreal, QC, Canada: International Centre for the Prevention of Crime.
- Malthaner, S. (2017). Radicalization: The evolution of an analytical paradigm. European Journal of Sociology/Archives Européennes de Sociologie, 58(3), 369–401. [Google Scholar]
- May, A. M., & Klonsky, E. D. (2016). What distinguishes suicide attempters from suicide ideators? A meta‐analysis of potential factors. Clinical Psychology: Science and Practice, 23(1), 5–20. [Google Scholar]
- McCann, S. J. (2009). Authoritarianism, conservatism, racial diversity threat, and the state distribution of hate groups. The Journal of Psychology, 144(1), 37–60. [DOI] [PubMed] [Google Scholar]
- McCauley, C. (2012). Testing theories of radicalization in polls of US Muslims. Analyses of Social Issues and Public Policy, 12(1), 296–311. [Google Scholar]
- McCauley, C., & Moskalenko, S. (2008). Mechanisms of political radicalization: Pathways toward terrorism. Terrorism and Political Violence, 20(3), 415–433. [Google Scholar]
- McCauley, C., & Moskalenko, S. (2017). Understanding political radicalization: The two‐pyramids model. American Psychologist, 72(3), 205–216. [DOI] [PubMed] [Google Scholar]
- McCleary, D. F., Quillivan, C. C., Foster, L. N., & Williams, R. L. (2011). Meta‐analysis of correlational relationships between perspectives of truth in religion and major psychological constructs. Psychology of Religion and Spirituality, 3(3), 163–180. [Google Scholar]
- McCauley, C., & Moskalenko, S. (2011). Friction: How radicalization happens to them and u. Oxford University Press. [Google Scholar]
- McGilloway, A., Ghosh, P., & Bhui, K. (2015). A systematic review of pathways to and processes associated with radicalization and extremism amongst Muslims in Western societies. International Review of Psychiatry, 27(1), 39–50. [DOI] [PubMed] [Google Scholar]
- Megens, K. C., & Weerman, F. M. (2010). Attitudes, delinquency and peers: The role of social norms in attitude‐behaviour inconsistency. European Journal of Criminology, 7(4), 299–316. [Google Scholar]
- Misiak, B., Samochowiec, J., Bhui, K., Schouler‐Ocak, M., Demunter, H., Kuey, L., … Dom, G. (2019). A systematic review on the relationship between mental health, radicalization and mass violence☆. European Psychiatry, 56(1), 51–59. [DOI] [PubMed] [Google Scholar]
- Monahan, J. (2012). The individual risk assessment of terrorism. Psychology, Public Policy, and Law, 18(2), 167–205. [Google Scholar]
- Monahan, J. (2017). The individual risk assessment of terrorism: Recent developments, The handbook of the criminology of terrorism (pp. 520–534). Hoboken, NJ: John Wiley & Sons, Inc. [Google Scholar]
- Moskalenko, S., & McCauley, C. (2009). Measuring political mobilization: The distinction between activism and radicalism. Terrorism and Political Violence, 21(2), 239–260. [Google Scholar]
- Moskalenko, S., & McCauley, C. (2011). The psychology of lone‐wolf terrorism. Counselling Psychology Quarterly, 24(2), 115–126. [Google Scholar]
- Mudde, C. (2004). The populist zeitgeist. Government and Opposition, 39(4), 541–563. [Google Scholar]
- Mullins, S. (2009). Parallels between crime and terrorism: A social psychological perspective. Studies in Conflict & Terrorism, 32(9), 811–830. [Google Scholar]
- Mullins, S. (2010). Rehabilitation of Islamist terrorists: Lessons from criminology. Dynamics of Asymmetric Conflict, 3(3), 162–193. [Google Scholar]
- Munton, T., Martin, A., Lorenc, T., Marrero‐Guillamon, I., Jamal, F., Lehmann, A., … Sexton, M. (2011). Understanding vulnerability and resilience in individuals to the influence of Al Qaida violent extremism: A Rapid Evidence Assessment. Technical Report Occasional Paper 98. London, UK: Home Office.
- Murray, J., Shenderovich, Y., Gardner, F., Mikton, C., Derzon, J. H., Liu, J., & Eisner, M. (2018). Risk factors for antisocial behavior in low‐and middle‐income countries: A systematic review of longitudinal studies. Crime and Justice, 47(1), 255–364. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Murray, J., & Thomson, M. E. (2010). Clinical judgement in violence risk assessment. Europe's Journal of Psychology, 6(1), 128–149. [Google Scholar]
- Murray, J., Farrington, D. P., & Eisner, M. P. (2009). Drawing conclusions about causes from systematic reviews of risk factors: The Cambridge Quality Checklists. Journal of Experimental Criminology, 5(1), 1–23. [Google Scholar]
- Najaka, S. S., Gottfredson, D. C., & Wilson, D. B. (2001). A meta‐analytic inquiry into the relationship between selected risk factors and problem behavior. Prevention Science, 2(4), 257–271. [DOI] [PubMed] [Google Scholar]
- Neumann, P. R. (2013). The trouble with radicalization. International Affairs, 89(4), 873–893. [Google Scholar]
- Neumann, P., & Kleinmann, S. (2013). How rigorous is radicalization research? Democracy and Security, 9(4), 360–382. [Google Scholar]
- Nunes, K. L., Hermann, C. A., Maimone, S., & Woods, M. (2015). Thinking clearly about violent cognitions: Attitudes may be distinct from other cognitions. Journal of Interpersonal Violence, 30(8), 1322–1347. [DOI] [PubMed] [Google Scholar]
- Orlina, E. C., & Desjardins, A. (2012). Insights from neurobiology on influence and extremism strategic multi‐layer assessment. Strategic Multi‐Layer Assessment Report. Washington, DC: National Strategies.
- OSCE (2014). Preventing terrorism and countering violent extremism and radicalization that lead to terrorism: A community‐policing approach. Vienna, Austria: Organization for Security and Co‐Operation in Europe. [Google Scholar]
- Ozer, S., & Bertelsen, P. (2018). Capturing violent radicalization: Developing and validating scales measuring central aspects of radicalization. Scandinavian Journal of Psychology, 59(6), 653–660. [DOI] [PubMed] [Google Scholar]
- Ozer, S. (2020). Globalization and radicalization: A cross‐national study of local embeddedness and reactions to cultural globalization in regard to violent extremism. International Journal of Intercultural Relations, 76, 26–36. [Google Scholar]
- Pauwels, L., & Schils, N. (2016). Differential online exposure to extremist content and political violence: Testing the relative strength of social learning and competing perspectives. Terrorism and Political Violence, 28(1), 1–29. [Google Scholar]
- Perry, G., Wikström, P. O. H., & Roman, G. D. (2018). Differentiating right‐wing extremism from potential for violent extremism: The role of criminogenic exposure. International Journal of Developmental Science, 12, 103–113. [Google Scholar]
- PEW , (2007). Pew Global Attitudes & Trends. Washington, D.C.: Pew Research Center. [Google Scholar]
- Piquero, A., Farrington, D., Welsh, B., Tremblay, R., & Jennings, W. (2009). Effects of early family/parent training programs on antisocial behavior and delinquency. Journal of Experimental Criminology, 5, 83–120. [Google Scholar]
- Pratt, T. C., Turanovic, J. J., Fox, K. A., & Wright, K. A. (2014). Self‐control and victimization: A meta‐analysis. Criminology, 52(1), 87–116. [Google Scholar]
- Rosenthal, R. (1984). Meta‐analytic procedures for social research. Applied social research methods series (6). Newbury Park, CA: Sage Publications. [Google Scholar]
- Rousseau, C., Oulhote, Y., Lecompte, V., Mekki‐Berrada, A., Hassan, G., & El Hage, H. (2019). Collective identity, social adversity and college student sympathy for violent radicalization. Transcultural Psychiatry, 1363461519853653.1–25. [DOI] [PubMed] [Google Scholar]
- Rydgren, J., & Ruth, P. (2013). Contextual explanations of radical right‐wing support in Sweden: socioeconomic marginalization, group threat, and the halo effect. Ethnic and Racial Studies, 36(4), 711–728. [Google Scholar]
- Sageman, M. (2014). The stagnation in terrorism research. Terrorism and Political Violence, 26(4), 565–580. [Google Scholar]
- Sageman, M. (2011). Leaderless jihad: Terror networks in the twenty‐first century. Philadelphia: University of Pennsylvania Press. [Google Scholar]
- Scarcella, A., Page, R., & Furtado, V. (2016). Terrorism, radicalisation, extremism, authoritarianism and fundamentalism: a systematic review of the quality and psychometric properties of assessments. PLoS One, 11(12), e0166947. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Schmid, A. P. (2013). Radicalisation, de‐radicalisation, counter‐radicalisation: A conceptual discussion and literature review. ICCT Research Paper, 97(1), 22. [Google Scholar]
- Schmid, A. P. (2017). Public opinion survey. Data to measure sympathy and support for Islamist terrorism. International Centre for Counter‐Terrorism‐The Hague, 8.
- Schuurman, B. (2018). Research on terrorism, 2007–2016: A review of data, methods, and authorship. Terrorism and Political Violence. 1–16. [Google Scholar]
- Serghiou, S., Patel, C. J., Tan, Y. Y., Koay, P., & Ioannidis, J. P. (2016). Field‐wide meta‐analyses of observational associations can map selective availability of risk factors and the impact of model specifications. Journal of Clinical Epidemiology, 71, 58–67. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Shader, M. (2001). Risk factors for delinquency: An overview. Washington, DC: US Department of Justice, Office of Justice Programs, Office of Juvenile Justice and Delinquency Prevention. [Google Scholar]
- Shenderovich, Y., Eisner, M., Mikton, C., Gardner, F., Liu, J., & Murray, J. (2016). Methods for conducting systematic reviews of risk factors in low‐and middle‐income countries. BMC Medical Research Methodology, 16(1), 32. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Silke, A. (2008). Research on terrorism, Terrorism Informatics (pp. 27–50). Boston, MA: Springer. [Google Scholar]
- Simourd, D. J., Hoge, R. D., Andrews, D. A., & Leschied, A. W. (1994). An empirically‐based typology of male young offenders. Canadian J. Criminology, 36, 447–461. [Google Scholar]
- Slootman, M., & Tillie, J. (2006). Processes of radicalisation: Why some Amsterdam Muslims become radicals (pp. 1–129). Amsterdam, The Netherlands: Institute for Migration and Ethnic Studies, Universiteit van Amsterdam. [Google Scholar]
- Stankov, L., Higgins, D., Saucier, G., & Knežević, G. (2010). Contemporary militant extremism: A linguistic approach to scale development. Psychological Assessment, 22(2), 246–258. [DOI] [PubMed] [Google Scholar]
- Staring, R. (2014). Risks of radicalization among Turkish‐Dutch young adults? CIROC Nieuwsbrief, 1(August 2014), 5–6. [Google Scholar]
- Stern, J. (2016). Radicalization to extremism and mobilization to violence: What have we learned and what can we do about it? The Annals of the American Academy of Political and Social Science, 668(1), 102–117. [Google Scholar]
- Tausch, N., Spears, R., & Christ, O. (2009). Religious and national identity as predictors of attitudes towards the 7/7 bombings among British Muslims: An analysis of UK opinion poll data. Revue Internationale de Psychologie Sociale, 22(3), 103–126. [Google Scholar]
- Tuck, M., & Riley, D. (1986). The theory of reasoned action: A decision theory of crime. In Cornish D. (Ed.), The reasoning criminal: Rational Choice perspectives on offending (pp. 156–167). New York, NY: Springer‐Verlag. [Google Scholar]
- Vergani, M., O'Brien, K. S., Lentini, P., & Barton, G. (2019). Does the awareness of mortality shape people's openness to violence and conflict? An examination of terror management theory. Political Psychology, 40(1), 111–124. [Google Scholar]
- Vergani, M., Iqbal, M., Ilbahar, E., & Barton, G. (2018). The three Ps of radicalization: Push, pull and personal. A systematic scoping review of the scientific evidence about radicalization into violent extremism. Studies in Conflict & Terrorism, 1–32. [Google Scholar]
- Victoroff, J. (2005). The mind of the terrorist: A review and critique of psychological approaches. Journal of Conflict Resolution, 49(1), 3–42. [Google Scholar]
- Victoroff, J., Adelman, J. R., & Matthews, M. (2012). Psychological factors associated with support for suicide bombing in the Muslim diaspora. Political Psychology, 33(6), 791–809. [Google Scholar]
- Vidino, L., & Brandon, J. (2012). Countering radicalization in Europe, ICSR, Kings College Policy Report. London, UK: Kings College.
- Walters, G. D. (2016). Low self‐control, peer rejection, reactive criminal thinking, and delinquent peer associations: connecting the pieces of the crime puzzle. Journal of Developmental and Life‐Course Criminology, 2(2), 209–231. [Google Scholar]
- Webber, D., Babush, M., Schori‐Eyal, N., Vazeou‐Nieuwenhuis, A., Hettiarachchi, M., Bélanger, J. J., … Gelfand, M. J. (2018). The road to extremism: Field and experimental evidence that significance loss‐induced need for closure fosters radicalization. Journal of Personality and Social Psychology, 114(2), 270–285. [DOI] [PubMed] [Google Scholar]
- White House . (2011). Empowering local partners to prevent violent extremism in the United States. Washington, DC: White House. [Google Scholar]
- Widom, C. S. (2014). Varieties of violent behavior. Criminology, 52(3), 313–344. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Wikström, P. O. H., & Bouhana, N. (2017). Analyzing radicalization and terrorism: A situational action theory. LaFree G. & Freilich J. The handbook of the criminology of terrorism, (175–186). Chichester: John Wiley & Sons, Inc. [Google Scholar]
- Wong, T. M., Slotboom, A. M., & Bijleveld, C. C. (2010). Risk factors for delinquency in adolescent and young adult females: A European review. European Journal of Criminology, 7(4), 266–284. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Supporting information


