Abstract
In this research, pure deterministic system has been established by a new Distributed Energy Efficient Clustering Protocol with Enhanced Threshold (DEECET) by clustering sensor nodes to originate the wireless sensor network. The DEECET is very dynamic, highly distributive, self-confessed and much energy efficient as compared to most of the other existing protocols. The MATLAB simulation provides aim proved result by means of energy dissipation being emulated in the networks lifespan for homogeneous as well as heterogeneous sensor network, which when contrasted for other traditional protocols. An enhanced result has been obtained for equitable energy dissipation for systematized networks using DEECET.
Keywords: WSN, DEEC, DEECET, Cluster head, Energy efficient algorithms, Clustering energy
Introduction
WSN is mostly recognized as an area, having small shape and simple sensing hardware devices called as wireless sensing nodes. These sensor nodes can senses the area and collects information data from these fields and transferred via wireless links. Data gathered is delivered through different hops towards sink (the base station and also called as controller) being used had locally as well as in the different networks [1–3]. Hence, creating the model for these type networks required full focus on the power consumption and network lifespan. Low cost and low power consumption are the basic requirement of sensor nodes . Therefore these hardware have so many constraints specially data gathering. Hence it is a necessary to search effective protocol for data aggregation [4, 5]. From all these issues, capacity of batteries is very important parameter in the construction of wireless sensor network models. The substitution of set of batteries is difficult, when the nodes are connected. Every sensor has limited power of battery and accordingly, the battery reinstatement cells are not possible. The constraint of energy is tough to be solved in less time because of the less progress in the battery capacity development. Thus, the only method to follow is the searching of an algorithm that may provides more power for a longer life span of network [6]. Normal wireless sensor network contains sensor nodes in the range of five hundred to one thousand. Efficient energy sensor may improve the life span of sensor network up to large extent. Clustering can be executed on the basis of two major aspects, sensor nodes co-ordinates and energy levels [7]. Number of clustering methods [8, 9] are accessible that can lessen the dissipation of energy with the well known LEACH (low energy adaptive clustering hierarchy). Varied studies of clustering are there with respect to WSN. The formation of leaders among the sensor nodes is known as clustering. Cluster heads (CHs) are selected, than they collect the data from the clustering members. The collected information can be refined by utilizing techniques of data compression and the integrated data is transferred towards the “Base Station” (BS). The main energy consuming task is cluster-head formation [10]. The fixed cluster heads consume more energy as compared to rotating cluster-heads.To conclude the most thing to keep in mind during distributive wireless sensor networks protocol design is energy dissipation. In previous work the cluster-heads are rotated randomly therefore the optimum election is not guaranteed. But in this case we used an DEEC-ET technique that based on a residual energy for the nodes for the optimum selection of CHs.
Clustering Protocols
Clustering has the advantage of scalability when the sensor network expands. It also provides reliability by localized solutions. Clustering solution can reduce power consumption by sleep/wakeup scheduling. In majority of WSN applications all sensors are not required in their wakeup state as during wakeup state they consume energy. Considering this fact few sensor nodes are allowed to go in sleep mode that preserves energy. There are various clustering protocols proposed by different researchers.
LEACH Protocol
Low Energy Adaptive Cluster Hierarchy (LEACH) is a hierarchical cluster-based routing protocol used in WSN’s [11]. In this protocol, the network is split into the different clusters that are based on Time Division Multiple Access (TDMA) schedule for member nodes. In it there are r number of rounds and each round has two phases: one is called the set up phase and the other is called steady-state phase. In first phase i.e., the set up phase cluster head (CH) selection is done based on two factors. First factor is the percentage p of the nodes in network, and second is the number of nodes that has served as CH. A value T(n), called threshold is set and it is decided by each node n based on a random number chosen between 0 and 1. T(n) can be given as
| 1 |
If the random number generated at a node is less then the threshold value then that node becomes the CH for that round. Similarly, every sensor node has a probability 1/p of becoming CH in each round. In the second phase i.e. steady state phase, sensor nodes use their allocated TDMA slot to send the collected data to the CH. The data collected by the CH is aggregated and then send to the base station (BS). The major disadvantage of using LEACH protocol is the selection of CH random and every node in the cluster has equal probability to become CH. And after many rounds, the node having higher remaining energy and the node having lower remaining energy both have equal probability of becoming CH. If a sensor node having lower remaining energy is chosen as the CH, then that node will run out of energy and die quickly that will severely affect the network lifetime.
PEGASIS Protocol
Power Efficient Gathering Sensor Informative System (PEGASIS) is a modified form of LEACH protocol [12]. In this protocol only one of the nodes connects with BS at the same time and remaining nodes connects only with their neighbours [13]. In this protocol every node measures the distance with respect to its neighbour nodes and identifies the nearest node. A chain is formed as shown in Fig. 1 and a leader is elected from chain on the basis of Residual Energy (RE) in every round. The leader collects data from neighbours and transmits the collected data to BS and thus the average energy consume by each node per round is decreased.
Fig. 1.
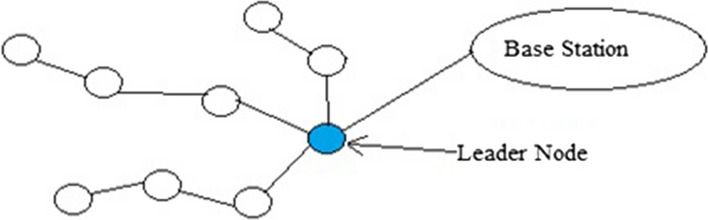
PEGASIS protocol
HEED Protocol
Hybrid Energy Efficient Distributed Clustering (HEED) protocol uses RE as primary parameter whereas other topology characteristics like node degree, spans to neighbours that are used as second parameter to obtain power balancing in sensor network. The clustering process is splitting into the number of repetitions, in every repetition nodes which are not enclosed by any CH and therefore doubles their possibility of being a CH. Therefore, these energy-efficient cluster protocols that in addition enable each node to possibly and independently determine its role in this clustered network. Moreover they cannot guarantee optimal elected set of CH’s [1].
DEEC Protocol
The Distributed Energy-Efficient Clustering Protocol (DEEC) was proposed to cope with energy-heterogeneity. The DEEC protocol election of CH’s based on the ratio between the RE of each node and the average network energy. The epos CH’s of being CH’s for the nodes are different according to the initial and also their residual energies. The nodes with more initial and remaining energy have greater chances of the becoming CH’s compared to nodes with lower energy. Probability P of any sensor node becoming the CH is given as:
| 2 |
where is the RE of node i at round r, is the initial probability of a node to become CH in a homogeneous setup as used in LEACH and E(r) is the estimated average energy of the network at round r given as:
| 3 |
where RT is the total round of the network lifetime, n is the number of nodes in the network, and are the total energy at the beginning of the network and the energy consumed in the network in each round respectively. By using this method of estimation, DEEC is able to further extending the network’s lifetime compared with the LEACH and Stable Election Protocol (SEP) protocols [14].
SEP Protocol
Stable Election Protocol (SEP) is the first approach employed to extending the network’s lifetime by investigating the possibility and the impact of energy-heterogeneity, which is a result of sensor nodes consuming different amount of energy in the network over time. This could be due to:
Their distance or position to the BS.
The amount of data aggregation performed as a CH, which depends on the size of each cluster.
Some nodes could fail during transmission as a result of the deployment terrain.
The network could be recharged by introducing new set of additional nodes.
The nodes could be powered by energy harvesting sources like solar, wind etc.
All the above reasons could potentially be sources of energy-heterogeneity. Based on this investigation, SEP protocol is based on weighted election probabilities of each node to become CH according to the remaining energy in each node. SEP protocol improvs significantly the network lifetime of WSNs as compared with the LEACH protocol [15].
ESEP Protocol
Enhanced Stable Election Protocol (ESEP) is a modified clustering algorithm with a three-tier energy set-up to characterize energy-heterogeneity, where energy consumption among sensor nodes is adaptive to their energy levels. This protocol is a direct enhancement to the original SEP protocol and the nodes are called ‘intermediate nodes’ to further characterize energy-heterogeneity. ESEP protocol is designed to exploit different levels of heterogeneity in the network, which proved to further improve the network lifetime to a significant extend in comparison to LEACH and SEP protocols [16].
DEC Protocol
Deterministic Energy-efficient Clustering (DEC) protocol reduces the computational overhead costs of the self-organized networks. This protocol uses RE of each node that in cluster that for the election process of CH’s. The setup phase that was used in LEACH protocol is modified, but the steady-state phase is kept the same. Because energy of node can be defined a priori, that CH’s election process is reconstructed by using the RE of every node [15]. In DEC protocol, the BS elects no. of CH’s at round m for the network. The BS take only be part in the election of the CH’s in the case that m = 1. Also, elected CH’s will advertise their role by using Carrier Sense Multiple Access (CSMA MAC) like in LEACH protocol.
Problem Formulation
Number of work is presented by researchers on probabilistic approach for decreasing energy dissipation for the network. The primary goal of the protocols was the enhancement of the network lifespan with wide information without focusing on local data gathering from the nodes residual energy. Major demerits of the protocol is that no confirmation of required amount of cluster heads will elected with sufficient amount of energy to perform its task. According to latest search new deterministic cluster’s head selection approach give better results than old probabilistic model in the scenario of energy dissipation. The model having similar issues that of un-guaranteed CH selection for one round with another model. LEACH protocol gives satisfactory results even by using their stochastic model, but results are not optimum because of the doubts in CH election technique. Equation of probabilistic system utilized in LEACH protocols is shown below:
| 4 |
Px is the CH probability to be elected, here x will be defined as normal nodes, advance nodes or super nodes rand is a constant value or function of ratio of an additional residual energy value added to every node. The deterministic quotient is calculated for every round in each node for the enhancement of LEACH performance. According to T(Px) function of threshold indicator each and every node take part in electing the CH intended for every round. Then wireless node selects the number among zero and one. In case this value is less as compared to nodes ‘n’ threshold value, then the wireless node is considered as CH. Group of non-elected cluster member is represented by symbol ‘G’. DEEC (Distributed Energy-Efficient Clustering Protocol) is an improved version of LEACH with the consideration of heterogeneous environment. Also, “Balanced and Centralized Distributed Energy-Efficient Clustering Protocol” (BCDEEC) enhance the DEEC with LEACH for heterogeneous environment by three-nodes. BCDEEC and DEEC protocols are used for the indicator function of threshold for their judgment.
In wireless sensing network different probabilities known as () for nodes are defined by Eq. (4). The process of clustering starts with a initial phase while each nodes in the network uses the “indicator function” to be elected like a CH. Advertisement message is broadcasted over carrier sense multiple access protocol by elected (CHs). Broadcasting message has CH ID’s with a header known as “Announcement”. A cluster member (non-elected nodes) discovers the cluster and chooses the cluster head having least transmission cost .Cost has been formulate on the strength of received signal containing advertising message. Using carrier sense multiple access protocol request of joining transmit towards selected CH by the cluster member. The message has cluster member-ID (CMID), cluster head-ID (CHID) with the header that shows the message being a request. Intra-cluster communication between cluster heads is held by time division multiple access at the end of setup phase. In the “Steady-state” phase of the protocol, the data will be transmits from the cluster members to the CHs and from cluster heads towards BS. Direct Sequencing Spread Spectrum (DSSS) technique is used for inter-cluster communication Therefore, proposed deterministic model capable to give a maximum residual energy for the nodes and improves life span of network. This technique gives a better idea for energy dissipation in WSN. Therefore, adapts a deterministic approach to get permanent number CHs elections for each round. The flowchart for DEC algorithm is presented in Fig. 2.
Fig. 2.
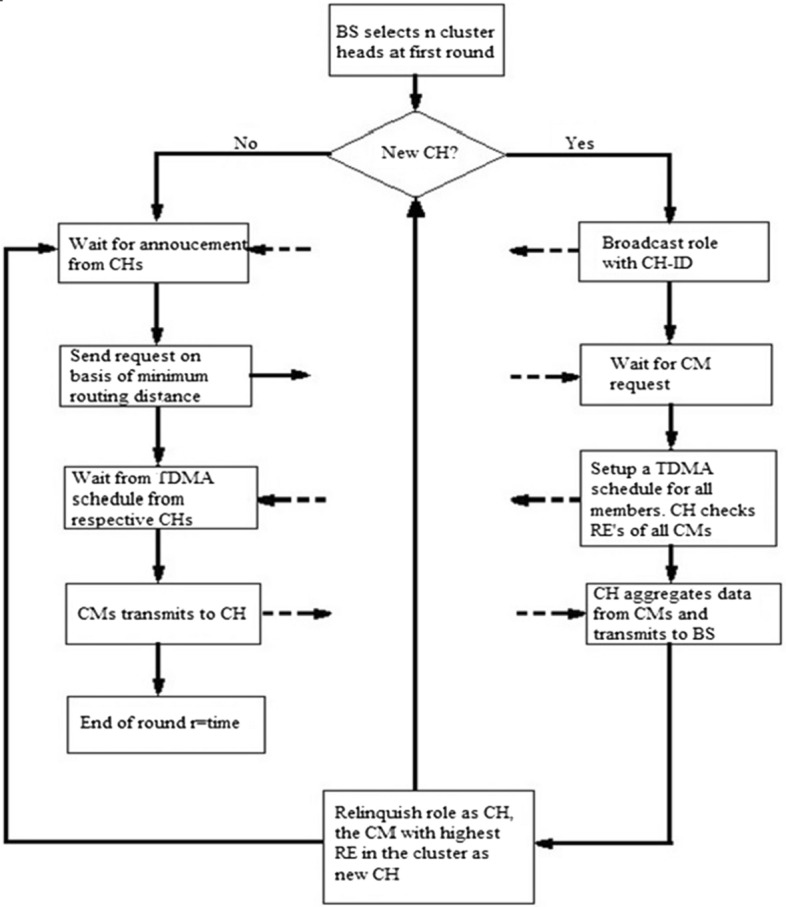
Flowchart of DEC algorithm
Network Model
Signal to noise ratio (SNR) defines the difference in level between the signal and the noise for a given signal level. The lower the noise generated by the receiver, the better the signal to noise ratio. For transferring the data frames by a distance (d) having satisfactory “Signal to Noise Ratio” (SNR), amplification energy () to conquer the (free space loss) () or (multi-path) (mp) loss, on the basis of transmission distances, the dissipation of energy is given below (Fig. 3).
| 5 |
| 6 |
To receive a k-bit message, the radio will expend:
| 7 |
Fig. 3.
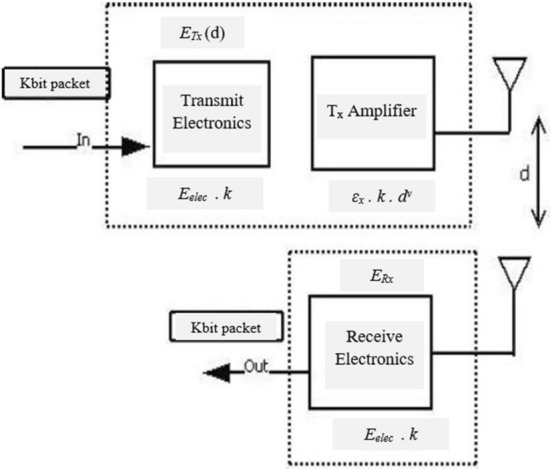
Network model diagram
Consider a symmetry radio channel. Symmetric means it required equal value of energy to send or receive (k) number of bits from nodes 1 to node 2 and nodes 2 to node 1. In existing protocols for example in LEACH we consider an ideal “data aggregation” that collects the packets from varied cluster members integrated by their particular CHs and only one single packet is transferred towards BS.
Now, total dissipated of energy in during a round in the network is given by:
| 8 |
Where, (dtoCH) denotes average distance among cluster members with the CH, (dtoBS) denotes average distance among CH with the BS, K denotes the amount of clustersm, EDA denotes the data aggregation cost in CH
| 9 |
| 10 |
| 11 |
we can optimize number of clusters by finding the derivative of Eround with respect to k to zero
| 12 |
Simulation and Result
In DEEC-ET the multilevel clustering is deployed at three different levels of nodes is defined which is better suited for defining heterogeneous environment as compared to two nodes levels being defined in DEEC protocol. The novel type of nodes being used in the DEEC-ET termed as “Super -nodes” for energy greater as compared to each two nodes (advanced nodes with the general nodes). It should be noted that network of total energy is remained similar like a DEEC protocol. Varied nodes has Eo as Energy, the nodes with fraction with the time having more energy as compared to each normal nodes equivalent to () while the super nodes having fraction mo with b value time extra energy as compared to normal nodes as compared to as the total number for super nodes with the as total number for the advanced nodes. Initial energy of three heterogeneous WSN is provided by (Table 1):
| 13 |
| 14 |
Table 1.
DEEC-ET protocol parameters
| Parameter | Description | Value |
|---|---|---|
| Xm × Ym | Field dimensions | 100 m x 100 m |
| N | Nodes number | 100 |
| Rmax | Utmost rounds | 10000 |
| P | The nodes probability to be a CH | 0.1 |
| Eo | Nodes initial energy | 0.5 J |
| ETX | Nodes transmission energy | 50 nJ/bit |
| ERX | Nodes receiving energy | 50 nJ/bit |
| EDA | Energy of data aggregation | 5 nJ/bit/message |
| Efs | Free space energy dissipation | 10 pJ/bit/m2 |
| Emp | Multi-path delay for Energy dissipation | 0.0013 pJ/bit/m4 |
| Packet | Size of packets | 4000 |
DEEC-ET uses almost similar CH mechanism selection and the energy estimation approximately than previous DEEC. At each round, nodes chooses while to be a CH or not by selecting an arbitrary number among zero or one. When the number of less as compared to T(px) being the threshold value as depicted in Eq. (1) as compared to nodes will select towards CH for the some provided round. In the DEEC-ET, the threshold value being accustomed which is dependent on that the value having the node which chooses the CH value by establishing the Eresi as a residual energy with the as the average energy of that round respectively towards the optimal CHs. Modified Threshold value is presented by DEEC-ET protocol is shown below:
| 15 |
= optimum no. of CHs, =residue energy of nodes, = network average energy
In the start-of-art, several researchers have used the common simulation parameters for performance analysis of their proposed research [17–20]. Hence, similar parameters were used to analyze the performance of the proposed protocol. The proposed protocols are simulated using area 1000 m x 1000 m. The standard values for = 10 pJ/bit/, = 0.0013 pJ/bit/, = 50 nJ/bit for transmission and receiving are considered.
New clustering technique enhance the lifetime and stability of nodes in heterogeneous environment named DEECET protocol. Performance comparisons given below
The levels taken for nodes are: normal nodes, intermediate nodes, advanced nodes, super nodes. The normal nodes are deployed randomly in the field as shown in Fig. 4. The normal nodes are represented as circles with cyan colour and sink in the middle with blue colour. The percentage of nodes exist in this area is 60% of the total nodes. The energy associated with normal node is 0.5 J per normal node. The intermediate nodes are deployed randomly in the field as shown in Fig. 4. These nodes have energy level greater than normal nodes but lesser than advanced and super nodes. The intermediate nodes are represented as squares with pink colour. The percentage of intermediate nodes exist in this area is 20% of the total nodes. The energy associated with intermediate node is 1.25 J per node. The advance nodes are deployed randomly in the field as shown in Fig. 4. The advance nodes are represented as rhombus with green colour. The percentage of advance nodes exist in this area is 10% of the total nodes. The energy associated with advanced nodes is 2.0 J per node which is greater than normal as well as intermediate nodes.
Fig. 4.
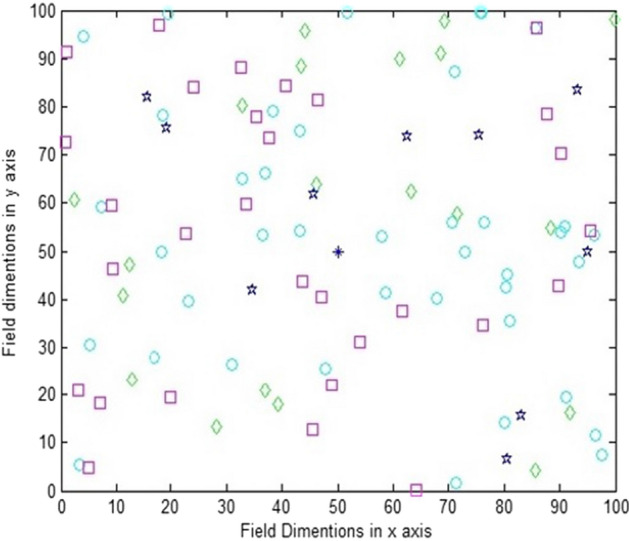
Deployment of nodes in field
In step 4 bunch of nodes elect its leader that act as cluster-head where, Non cluster-head nodes become member nodes of that cluster, this process is known as clustering. The clustering technique is shown in Fig. 5. The nodes which act as CH’s are represented by pointer symbol on those nodes. At the end of each round the CH is changed.
Fig. 5.
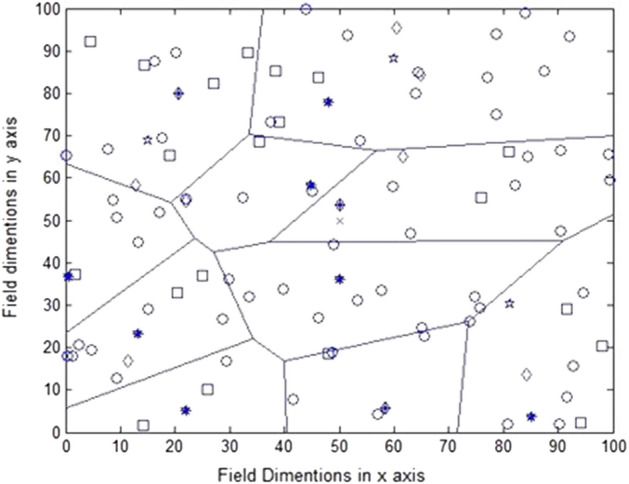
Clustering of network
After exact amount rounds, each network nodes become dead. The Fig. 6 shows all dead nodes. The results obtained from DEECET protocol shows improvement in number of rounds and stability of WSN. It is found that The first node dead (FND) also known as stability period is at 1839th round for DEEC means that the network is stable up to 1839 rounds. The last node dead (LND) is at 2350th round by using original DEEC protocol. Whereas DEECET performed better and the FND is at around 2350th round means that the network is stable up to 2350 rounds. The LND is at around 2400th round by using DEECET protocol.
Fig. 6.
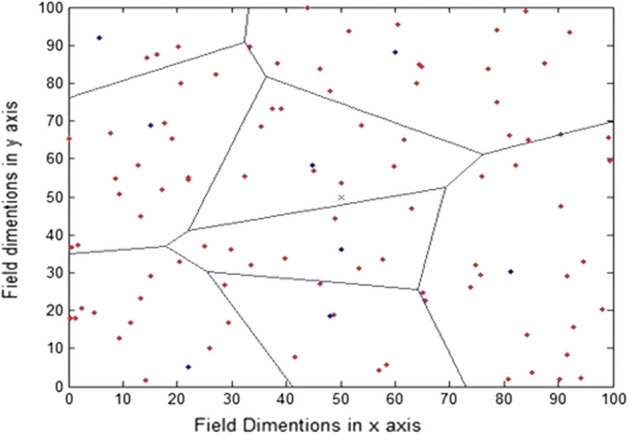
Dead member nodes and cluster head
Figure 7 shows Performance difference plot between DEECET and previous DEEC protocol on the basis of alive nodes and rounds. This can be concluded from above discussion that the EDEC is around 500 rounds more stable than original DEC and the network lifetime of EDEC is also increased by 50 rounds.
Fig. 7.
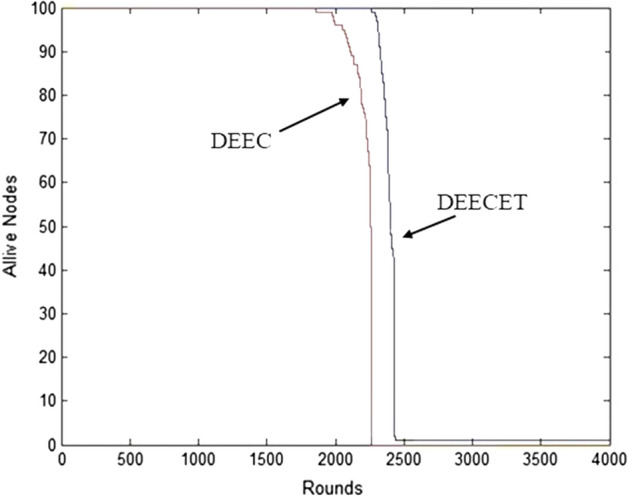
Comparison between DEEC and DEECET for live nodes w.r.t. to rounds
Figure 8 shows comparison between original DEC and EDEC in terms of total energy versus number of rounds. The energy management of EDEC is better than Original DEC as shown in Figure 4.17 proving that EDEC is more energy efficient than original DEC protocol.
Fig. 8.
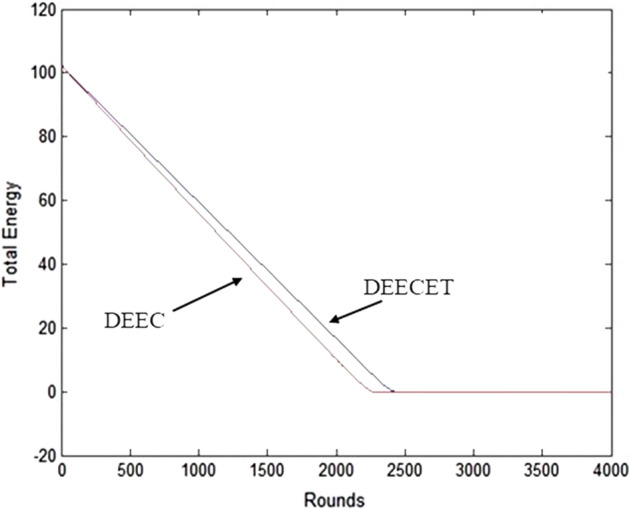
Total energy versus number of rounds plot comparison
Scalability is an important parameter pertaining to wireless sensor networks. The present work has number of sensors as 100. It can be changed and interpretation of results for behaviour of network with respect to scalability can be analysed. The present works analyses the count of alive nodes and rounds. Other QoS parameters can also be considered for study.
Conclusions
The performance evaluated from the results clearly shows that DEECET proposed deterministic protocol gives better network lifetime as compared to previous probabilistic protocols. DEECET purely deterministic protocol optimize the utilization of energy resources in wireless sensor network. The new proposed DEECET protocol uses heterogeneous environment to improve the performance of wireless network. Heterogeneous environment contains new nodes known as “super nodes” in the sensor network. This protocol can be used in those application where power consumption is the main constraint.
Biographies
Jyoti Bhola
has completed her B.Tech, M.Tech and Ph.D. in Electronics and Communication Engineering from NIT, Hamirpur, India. She has published many research papers in various journals indexed in Scopus/Web of Science. He area of research is WSN, Optical Fiber and Semiconductor devices.
Mohammad Shabaz
has completed his B.Tech in Information Technology and Telecommunication Engineering from Baba Ghulam Shah Badshah University, J&K, M.E and Ph.D. in Computer Science Engineering from Chandigarh University, Mohali. He is working as Assistant Professor, CSE at Chitkara University, India and Visiting Faculty at Arba Minch University, Ethiopia. He is Currently holding the positions of Managing Editor and Publisher at Journal of Engineering, Science and Mathematics (JESM). Managing Guest Editor at Informatics in Medicine Unlocked (Elsevier), Neuroscience Informatics (Elsevier). His area of interest is application of computer science in interdisciplinary domains. He has Published over 60 research papers in various journals indexed in Scopus/Web of Science, 4 Indian Patents and 3 Australian Patents. His major work is on healthcare domain. His major contributions include the creation of novel algorithms like SA Sorting, Shabaz-Urvashi Link Prediction. On the Covid-19 Pandemic, his first publication appears in May 2020 titled “Prediction of COVID-19 Cases Over Globe with Expeditious Recovery” published at Journal of Research in Medical and Dental Science indexed in Web of Science (ESCI). His second publication on Covid-19 titled “COVID-19: Challenges and its Technological Solutions using IoT” published at Current Medical Imaging indexed in Web of Science (SCIE). His third publication on Covid-19 titled “Chest CT Findings and Differential Diagnosis of Mycoplasma pneumoniae Pneumonia and Mycoplasma pneumoniae Combined with Streptococcal Pneumonia in Children” published at Journal of Healthcare Engineering indexed in Web of Science (SCIE) and many more.
Gaurav Dhiman
received his Ph.D. in Computer Engineering from Thapar Institute of Engineering & Technology, Patiala. He has completed his Master Degree of Computer Applications from Thapar Institute of Engineering & Technology, Patiala. He is currently working as an Assistant Professor with the Department of Computer Science, Government Bikram College of Commerce, Patiala. He was selected as an outstanding reviewer from Knowledge-Based Systems (Elsevier). He has published more than 50 peer-review research papers (indexed in SCI-SCIE) and 5 international books. He is also serving as the guest editor of more than five special issues in various peer-reviewed journals. He is also in editorial board members of Current Chinese Computer Science (Bentham Science), Current Dissertations (Bentham Science), Journal of Fuzzy Logic and Modelling in Engineering (Bentham Science), Journal of the Institute of Electronics and Computer (IEC Science), Journal of Peer Scientist, Artificial Intelligence Evolution, Acta Scientific Computer Sciences. His research interest includes Single-, Multi-, Many-objective optimization (Bio-inspired, Evolutionary and Quantum), Soft computing (Type-1 and Type-2 fuzzy sets), Power systems, and Change detection using remotely sensed high-resolution satellite data. His research articles can be found in Knowledge-Based Systems (Elsevier), Advances in Engineering Software (Elsevier), Applied Intelligence (Springer), Journal of Computational Science (Elsevier), Engineering with Computers (Springer), Applied Soft Computing (Elsevier), Engineering Applications of Artificial Intelligence (Elsevier), Journal of Ambient Intelligence and Humanized Computing (Springer), among others. His research can also be seen in http://www.dhimangaurav.com
S. Vimal
is working in Department of Computer Science and Engineering, Ramco Institute of Technology, Tamilnadu, India. He has around Fourteen years of teaching experience, EMC certified Data science Associate and CCNA certified professional too. He holds a Ph.D in Information and Communication Engineering from Anna University Chennai and he received Masters Degree from Anna University Coimbatore. He is a member of various professional bodies and organized various funded workshops and seminars. He has wide publications in the highly impact journals in the area of Data Analytics, Networking and Security issues and published 04 book chapters. He has hosted two special session for IEEE sponsored conference in Osaka, Japan and Thailand. He has acted as Session chairs, organizing committee member, advisory committee and outreach committee member in various international conferences in IEEE and Other prestiguos Conferences. His areas of interest include Game Modelling, Artificial Intelligence, Cognitive radio networks, Network security, Machine Learning and Big data Analytics. He is a Senior member in IEEE and holds membership in various professional bodies. He has served as reviewer for Springer, Elsevier and Wiley journals. He has hosted 9 special issues in Elsevier, Springer and CMC tech science journals. He has served as Guest editor for SCI journals and editored 3 books in scopus indexed. He is a Senior Member in IEEE.
Subbulakshmi Pasupathi
is working as Assistant professor (Senior Grade), School of Computer Science and Engineering, Vellore Institute of Technology, Chennai, Tamil Nadu, India. She has around 11 years of teaching experience. Her modest areas of interest include Cognitive Radio Networks, Computer networks, Cryptography, Wireless Networks & security, Big data analytics, Game theory and Machine Learning. She has mentored various MHRD certifications and institutional expert member in Outcome Based Education-NBA.
Sunil Kumar Soni
has completed his B.Tech, M.Tech in Electronics and Communication Engineering. He has published many research papers in various journals indexed in Scopus/Web of Science. He area of research is WSN, Optical Fiber and Semiconductor devices.
Footnotes
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Jyoti Bhola, Email: jyotib@nith.ac.in.
Mohammad Shabaz, Email: bhatsab4@gmail.com.
Gaurav Dhiman, Email: gdhiman0001@gmail.com.
S. Vimal, Email: svimalphd@gmail.com
P. Subbulakshmi, Email: subbu.psk@gmail.com
Sunil Kumar Soni, Email: sunilsoni.vlsi@gmail.com.
References
- 1.Younis O, Fahmy S. HEED: A hybrid, energy-efficient, distributed clustering approach for ad-hoc sensor networks. IEEE Transactions on Mobile Computing. 2004;3(4):366. doi: 10.1109/TMC.2004.41. [DOI] [Google Scholar]
- 2.Zhou Y, Sharma A, Masud M, Gaba GS, Dhiman G, Ghafoor KZ, AlZain MA. Urban rain flood ecosystem design planning and feasibility study for the enrichment of smart cities. Sustainability. 2021;13(9):5205. doi: 10.3390/su13095205. [DOI] [Google Scholar]
- 3.Kothai, G., Poovammal, E., Dhiman, G., Ramana, K., Sharma, A., AlZain, M. A., Gaba, G. S., & Masud, M. (2021). A new hybrid deep learning algorithm for prediction of wide traffic congestion in smart cities. Wireless Communications and Mobile Computing,2021,
- 4.Ozdemir S, Xiao Y. Secure data aggregation in wireless sensor networks: A comprehensive overview. Computer Networks. 2009;53(12):2022. doi: 10.1016/j.comnet.2009.02.023. [DOI] [Google Scholar]
- 5.Madasamy, K., Shanmuganathan, V., Dhiman, G., Vijayalakshmi, K., & Suresh Kumar, P. (2021). Materials Today: Proceedings
- 6.Abbasi AA, Younis M. A survey on clustering algorithms for wireless sensor networks. Computer Communications. 2007;30:2826–2841. doi: 10.1016/j.comcom.2007.05.024. [DOI] [Google Scholar]
- 7.Rathi Viswanathan. two phase clustering method for leach protocol for effective cluster head selection. Journal of Computer Science. 2014;10(3):366. doi: 10.3844/jcssp.2014.366.375. [DOI] [Google Scholar]
- 8.M. Poongodi, M. Hamdi, M. Malviya, A. Sharma, G. Dhiman, S. Vimal, Personal and ubiquitous computing, pp. 1–11 (2021) [DOI] [PMC free article] [PubMed]
- 9.Dhiman G, Oliva D, Kaur A, Singh KK, Vimal S, Sharma A, Cengiz K. Knowledge-Based Systems. 2021;211:106560. doi: 10.1016/j.knosys.2020.106560. [DOI] [Google Scholar]
- 10.Bhargava N, Bharagava R, Mathuria M, Gupta S, Kumar K. International Journal of Computer Networks and Wireless. Communications. 2013;3(1):32. [Google Scholar]
- 11.Heinzelman WR, Chandrakasan A, Balakrishnan H. Proceedings of the Hawaii International Conference on System Sciences. Maui: Hawai; 2000. pp. 1–10. [Google Scholar]
- 12.Lindsey S, Raghavendra C. PEGASIS: Power-efficient gathering in sensor information systems. IEEE Aerospace Conference Proceedings. 2002;3(9):1125. [Google Scholar]
- 13.Almazaydeh L, Abdelfattah E, Al-Bzoor M, Al-Rahayfeh A. International Journal of Computer Science and Information Technology. 2010;2(2):64. doi: 10.5121/ijcsit.2010.2206. [DOI] [Google Scholar]
- 14.Qing L, Zhu Q, Wang M. Computer Communications. 2006;29(12):2230. doi: 10.1016/j.comcom.2006.02.017. [DOI] [Google Scholar]
- 15.G. Smaragdakis, I. Matta, A. Bestavros, Second International Workshop on Sensor and Actor Network Protocols and Applications (2004)
- 16.Aderohunmu FA, Deng JD. Enhancing Clustering in Wireless Sensor. Networks with Energy Heterogeneity. International Journal of Bus Data Communication Network. 2011;7(4):1. doi: 10.4018/jbdcn.2011100102. [DOI] [Google Scholar]
- 17.Heinzelman, W., Chandrakasan, A., & Balakrishnan H. (2000). In: Proceedings of the 33rd Hawaii International Conference on System Sciences (HICSS-33), vol. 8, pp. 8020–8030
- 18.Akkaria W, Bouhdida B, Belghithb A. Procedia Computer Science. 2015;52:365. doi: 10.1016/j.procs.2015.05.110. [DOI] [Google Scholar]
- 19.Bhola, J., Soni, S., Cheema, G. K. (2020). Genetic algorithm based optimized leach protocol for energy efficient wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing, 1281–1288.
- 20.Zhang F, Wang Q. Electronics Computer Technology. 2011;4:348. [Google Scholar]


