Abstract
Rips complexes are important structures for analyzing topological features of metric spaces. Unfortunately, generating these complexes is expensive because of a combinatorial explosion in the complex size. For n points in , we present a scheme to construct a 2-approximation of the filtration of the Rips complex in the -norm, which extends to a -approximation in the Euclidean case. The k-skeleton of the resulting approximation has a total size of . The scheme is based on the integer lattice and simplicial complexes based on the barycentric subdivision of the d-cube. We extend our result to use cubical complexes in place of simplicial complexes by introducing cubical maps between complexes. We get the same approximation guarantee as the simplicial case, while reducing the total size of the approximation to only (cubical) cells. There are two novel techniques that we use in this paper. The first is the use of acyclic carriers for proving our approximation result. In our application, these are maps which relate the Rips complex and the approximation in a relatively simple manner and greatly reduce the complexity of showing the approximation guarantee. The second technique is what we refer to as scale balancing, which is a simple trick to improve the approximation ratio under certain conditions.
Keywords: Persistent homology, Rips filtrations, Approximation algorithms, Topological data analysis
Introduction
Context. Persistent homology (Carlsson 2009; Edelsbrunner and Harer 2010; Edelsbrunner et al. 2002) is a technique to analyze data sets using topological invariants. The idea is to build a multi-scale representation of data sets and to track its homological changes across the scales.
A standard construction for the important case of point clouds in Euclidean space is the Vietoris-Rips complex (usually abbreviated as simply the Rips complex): for a scale parameter , it is the collection of all subsets of points with diameter at most . When increases from 0 to , the Rips complexes form a filtration, an increasing sequence of nested simplicial complexes whose homological changes can be computed and represented in terms of a barcode.
The computational drawback of Rips complexes is their sheer size: the k-skeleton of a Rips complex (that is, where only subsets of size at most are considered) for n points consists of simplices because every -subset joins the complex for a sufficiently large scale parameter. This size bound makes barcode computations for large point clouds infeasible even for low-dimensional homological features1. This difficulty motivates the question of what we can say about the barcode of the Rips filtration without explicitly constructing all of its simplices.
We address this question using approximation techniques. The space of barcodes forms a metric space: two barcodes are close if similiar homological features occur on roughly the same range of scales. More precisely, the bottleneck distance is used as a distance metric between barcodes. The first approximation scheme by Sheehy (2013) constructs a -approximation of the k-skeleton of the Rips filtration using only simplices for arbitrary finite metric spaces, where is the doubling dimension of the metric. Further approximation techniques for Rips complexes (Dey et al. 2014) and the closely related Čech complexes (Botnan and Spreemann 2015; Cavanna et al. 2015; Kerber and Sharathkumar 2013) have been derived subsequently, all with comparable size bounds. More recently, we constructed an approximation scheme (Choudhary et al. 2019) for the Čech filtrations of n points in that had size for the k-skeleton, improving the size bound from previous work.
In Choudhary et al. (2017b), we constructed an approximation scheme for Rips filtration in Euclidean space that yields a worse approximation factor of only O(d), but uses only simplices. In Choudhary et al. (2017b), we also show a lower bound result on the size of approximations: for any with some constant , any -approximate filtration has size .
There has also been work on using cubical complexes to compute persistent homology, such as in Wagner et al. (2012). Cubical complexes are typically smaller than their simplicial counterparts, simply because they avoid triangulations. However, to our knowledge, there has been no attempt to utilize them in computing approximations of filtrations. Also, while there are efficient methods to compute persistence for simplicial complexes connected with simplicial maps (Dey et al. 2014; Kerber and Schreiber 2017), we are not aware of such counterparts for cubical complexes.
Our contributions. For the Rips filtration of n points in with distances taken in the -norm, we present a 2-approximation whose k-skeleton has size at most where denotes Stirling numbers of the second kind. This translates to a -approximation of the Rips filtration in the Euclidean metric and hence improves the asymptotic approximation quality of our previous approach (Choudhary et al. 2017b) with the same size bound. Our scheme gives the best size guarantee over all previous approaches.
On a high level, our approach follows a straightforward approximation scheme: given a scaled and appropriately shifted integer grid on , we identify those grid points that are close to the input points and build an approximation complex using these grid points. The challenge lies in how to connect these grid points to a simplicial complex such that close-by grid points are connected, while avoiding too many connections to keep the size small. Our approach first selects a set of active faces in the cubical complex defined over the grid, and defines the approximation complex using the barycentric subdivision of this cubical complex.
We also describe an output-sensitive algorithm to compute our approximation. By randomizing the aforementioned shifts of the grids, we obtain a worst-case running time of in expectation, where is the spread of the point set (that is, the ratio of the diameter to the closest distance of two points) and M is the size of the approximation.
Additionally, this paper makes the following technical contributions:
-
We follow the standard approach of defining a sequence of approximation complexes and establishing an interleaving between the Rips filtration and the approximation. We realize our interleaving using chain maps connecting a Rips complex at scale to an approximation complex at scale , and vice versa, with being the approximation factor. Previous approaches (Choudhary et al. 2017b; Dey et al. 2014; Sheehy 2013) used simplicial maps for the interleaving, which induce an elementary form of chain maps and are therefore more restrictive.
The explicit construction of such maps can be a non-trivial task. The novelty of our approach is that we avoid this construction by the usage of acyclic carriers (Munkres 1984). In short, carriers are maps that assign subcomplexes to subcomplexes under some mild extra conditions. While they are more flexible, they still certify the existence of suitable chain maps, as we exemplify in Sect. 2. We believe that this technique is of general interest for the construction of approximations of cell complexes.
- We exploit a simple trick that we call scale balancing to improve the quality of approximation schemes. In short, if the aforementioned interleaving maps from and to the Rips filtration do not increase the scale parameter by the same amount, one can simply multiply the scale parameter of the approximation by a constant. Concretely, given maps
interleaving the Rips complex and the approximation complex , we can define and obtain maps
which improves the interleaving from c to . While it has been observed that the same trick can be used for improving the worst-case distance between Rips and Čech filtrations,2 our work seems to be the first to make use of it in the context of approximations. We extend our approximation scheme to use cubical complexes instead of simplicial complexes, thereby achieving a marked reduction in size complexity. To connect the cubical complexes at different scales, we introduce the notion of cubical maps, which is a simple extension of simplicial maps to the cubical case. While we do not know of an algorithm that can compute persistence for the case of cubical complexes with cubical maps, we believe that this is a first step towards advocating the use of cubical complexes as approximating structures.
Our technique can be combined with dimension reduction techniques in the same way as in Choudhary et al. (2017b) (see Theorems 19, 21, and 22 therein), with improved logarithmic factors. We state the main results in the paper, while omitting the technical details.
Updates from the conference version. An earlier version of this paper appeared at the 25th European Symposium on Algorithms (Choudhary et al. 2017a). In that version, we achieved a -approximation of the Rips filtration and correspondingly, a -approximation of the case. In this version, we improve the weak interleaving of Choudhary et al. (2017a) to a strong interleaving to get improved approximation factors. We expand upon the details of scale balancing, among other proofs that were missing from the conference version. We add the case of cubical complexes in this version.
There is a subtle yet important distinction between the approximation complexes used in the conference version and the current result. In the conference version, our simplicial complex was built using only active faces, while the current version uses both active and secondary faces (please see Sect. 4 for definitions). This makes it easier to relate the simplicial and the cubical complexes in the current version. On the other hand the complexes are different, hence the associated proofs have been adapted accordingly.
Outline. We start by explaining the relevant topological concepts in Sect. 2. We give details of the integer grids that we use in Sect. 3. In Sect. 4 we present our approximation scheme that uses the barycentric subdivision, and present the computational aspects in Sect. 5. The extension to cubical complexes is presented in Sect. 6. We discuss practical aspects of our scheme and conclude in Sect. 7. Some details of the strong interleaving from Sect. 4 are deferred to Appendix A.
Preliminaries
We briefly review the essential topological concepts needed. More details are available in standard references (see Bubenik et al. 2015; Chazal et al. 2009; Edelsbrunner and Harer 2010; Hatcher 2002; Munkres 1984).
Simplicial complexes. A simplicial complex K on a finite set of elements S is a collection of subsets called simplices such that each subset is also in K. The dimension of a simplex is , in which case is called a k-simplex. A simplex is a sub-simplex of if . We remark that, commonly a sub-simplex is called a “face” of a simplex, but we reserve the word “face” for a different structure. For the same reason, we do not introduce the common notation of of “vertices” and “edges” of simplicial complexes, but rather refer to 0- and 1-simplices throughout. The k-skeleton of K consists of all simplices of K whose dimension is at most k. For instance, the 1-skeleton of K is a graph defined by its 0-simplices and 1-simplices.
Given a point set and a real number , the (Vietoris-)Rips complex on P at scale consists of all simplices such that , where diam denotes the diameter. In this work, we write for the Rips complex at scale with the Euclidean metric, and when using the metric of the -norm. In either way, a Rips complex is an example of a flag complex, which means that whenever a set has the property that every 1-simplex is in the complex, then the k-simplex is also in the complex.
A related complex is the Čech complex of P at scale , which consists of simplices of P for which the radius of the minimum enclosing ball is at most . We do not study Čech complexes in this paper, but we mention them briefly while showing a connection with the Rips complex later in this section.
A simplicial complex is a subcomplex of K if . For instance, is a subcomplex of for . Let L be a simplicial complex. Let be a map which assigns a vertex of L to each vertex of K. A simplicial map is a map induced by a vertex map , such that for every simplex in K, the set is a simplex of L. For a subcomplex of K, the inclusion map is an example of a simplicial map. A simplicial map is completely determined by its action on the 0-simplices of K.
Chain complexes. A chain complex with is a collection of abelian groups and homomorphisms such that . A simplicial complex K gives rise to a chain complex for a fixed base field : define for as the set of formal linear combinations of p-simplices in K over , and . The boundary of a k-simplex with is the (signed) sum of its sub-simplices of co-dimension one3; the boundary of a 0-simplex is simply set to 1. The homomorphisms are then defined as the linear extensions of this boundary operator. Note that is sometimes called augmented chain complex of K, where the augmentation refers to the addition of the non-trivial group .
A chain map between chain complexes and is a collection of group homomorphisms such that . For simplicial complexes K and L, we call a chain map augmentation-preserving if is the identity. A simplicial map between simplicial complexes induces an augmentation-preserving chain map between the corresponding chain complexes. This construction is functorial, meaning that for the identity function on a simplicial complex K, is the identity function on , and for composable simplicial maps , we have that .
Homology. The p-th homology group of a chain complex is defined as . The p-th homology group of a simplicial complex K, , is the p-th homology group of its induced chain complex . Note that this definition is commonly referred to as reduced homology, but we ignore this distinction and consider reduced homology throughout. is an -vector space because we have chosen our base ring as a field. Intuitively, when the chain complex is generated from a simplicial complex, the dimension of the p-th homology group counts the number of p-dimensional holes in the complex. We write for the direct sum of all for .
A chain map induces a linear map between the homology groups. Again, this construction is functorial, meaning that it maps identity maps to identity maps, and it is compatible with compositions.
Acyclic carriers. We call a simplicial complex K acyclic, if K is connected and all homology groups are trivial. For simplicial complexes K and L, an acyclic carrier is a map that assigns to each simplex in K, a non-empty acyclic subcomplex , and whenever is a sub-simplex of , then . We say that a chain is carried by a subcomplex , if c takes value 0 except for p-simplices in . A chain map is carried by , if for each simplex , is carried by . We state the acyclic carrier theorem (Munkres 1984, Thm 13.3), adapted to our notation:
Theorem 1
Let be an acyclic carrier. Then,
There exists an augmentation-preserving chain map carried by .
If two augmentation-preserving chain maps are both carried by , then .4
We remark that “augmentation-preserving” is crucial in the statement: without it, the trivial chain map (that maps everything to 0) turns the first statement trivial and easily leads to a counter-example for the second claim.
Filtrations and towers. Let be a set of real values which we refer to as scales. A filtration is a collection of simplicial complexes such that for all . For instance, is a filtration which we call the Rips filtration. A (simplicial) tower is a sequence of simplicial complexes with J being a discrete set (for instance ), together with simplicial maps between complexes at consecutive scales. For instance, the Rips filtration can be turned into a tower by restricting to a discrete range of scales, and using the inclusion maps as . The approximation constructed in this paper will be another example of a tower.
We say that a simplex is included in the tower at scale , if is not in the image of the map , where is the scale preceding in the tower. The size of a tower is the number of simplices included over all scales. If a tower arises from a filtration, its size is simply the size of the largest complex in the filtration (or infinite, if no such complex exists). However, this is not true in general for simplicial towers, because simplices can collapse in the tower and the size of the complex at a given scale may not take into account the collapsed simplices which were included at earlier scales in the tower.
Barcodes and Interleavings. A collection of vector spaces connected with linear maps is called a persistence module, if is the identity on and for all for the index set I.
We generate persistence modules using the previous concepts. Given a simplicial tower , we generate a sequence of chain complexes . By functoriality, the simplicial maps of the tower give rise to chain maps between these chain complexes. Using functoriality of homology, we obtain a sequence of vector spaces with linear maps , forming a persistence module. The same construction applies to filtrations as a special case.
Persistence modules admit a decomposition into a collection of intervals of the form (with ), called the barcode, subject to certain tameness conditions. The barcode of a persistence module characterizes the module uniquely up to isomorphism. If the persistence module is generated by a simplicial complex, an interval in the barcode corresponds to a homological feature (a “hole”) that comes into existence at complex and persists until it disappears at .
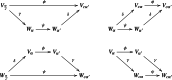
Two persistence modules and with linear maps and are said to be weakly (multiplicatively) c-interleaved with , if there exist linear maps and , called interleaving maps, such that the diagram
| 1 |
commutes, that is, and for all (we have skipped the subscripts of the maps for readability). In such a case, the barcodes of the two modules are 3c-approximations of each other in the sense of Chazal et al. (2009). We say that two towers are c-approximations of each other if their persistence modules are c-approximations.
Under the more stringent conditions of strong interleaving, the approximation ratio can be improved. Two persistence modules and with respective linear maps and are said to be (multiplicatively) strongly c-interleaved if there exist a pair of families of linear maps and for , such that Diagram (2) commutes for all (the subscripts of the maps are excluded for readability). In such a case, the persistence barcodes of the two modules are said to be c-approximations of each other in the sense of Chazal et al. (2009).
 |
2 |
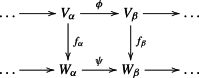
Finally, we mention a special case that relates equivalent persistence modules (Carlsson and Zomorodian 2005; Goodman et al. 2017). Two persistence modules and that are connected through linear maps respectively are isomorphic if there exists an isomorphism for each for which the following diagram commutes for all :
 |
3 |
Isomorphic persistence modules have identical persistence barcodes.
Scale balancing. Let and be two persistence modules with linear maps , respectively. Let there be linear maps and for such that all . Suppose that the following diagram commutes, for all .
| 4 |
Let . Then, by replacing by in Diagram (4), the diagram still commutes, so is a -approximation of .
We define a new vector space , where and . This gives rise to a new persistence module, . The maps and can then be interpreted as , or and . Then, Diagram (4) can be re-interpreted as
| 5 |
which still commutes. Therefore, is a -approximation of , which is an improvement over , since . and have the same barcode up to a scaling factor.
This scaling trick also works when and are strongly interleaved. If we have the following commutative diagrams: (where we have skipped the maps for readability):
 |
6 |
then and are -approximations of each other. By defining as before, the following diagrams
 |
7 |
commute for , so we can improve a -approximation to an -approximation.
We end the section by discussing a basic but important relation between Čech and Rips filtrations. It is well-known that for any , (Edelsbrunner and Harer 2010). This gives a strong interleaving between the towers and with and . Applying the scale balancing technique, we get that
Lemma 1
The scaled Čech persistence module and the Rips persistence module are -approximations of each other.
Shifted integer lattices
In this section, we take a look at simple modifications of the integer lattice.
We denote by with , a discrete set of scales. For each scale in I, we define grids which are scaled and translated (shifted) versions of the integer lattice.
Definition 1
(Scaled and shifted grids) For each scale , we define the scaled and shifted grid inductively as:
For , is simply the scaled integer grid , where each basis vector has been scaled by .
- For , we choose an arbitrary point and define
where the signs of the components of the last vector are chosen independently and uniformly at random (and the choice is independent for each s).8 - For , we define
where the last vector is chosen as in the case of .9
Equations (8) and (9) are consistent at . A simple example of the above construction is the sequence of grids with for even s, and for odd s.
Next, we motivate the shifting of the grids. Let denote the Voronoi cell of any point with respect to the point set . It is clear that the Voronoi cell is a cube of side length centered at x. The shifting of the grids ensures that each lies in the Voronoi region of a unique . Using an elementary calculation, we show a stronger statement:
Lemma 2
Let be such that . Then,
Proof
Without loss of generality, we can assume that and x is the origin, using an appropriate translation and scaling. Also, we assume for the sake of simplicity that ; the proof is analogous for any other translation vector. In that case, it is clear that . Since , the Voronoi region of x is the set . Since is a translated version of , the Voronoi region of y is the cube , which covers . The claim follows. For an example look to Fig. 1.
Fig. 1.
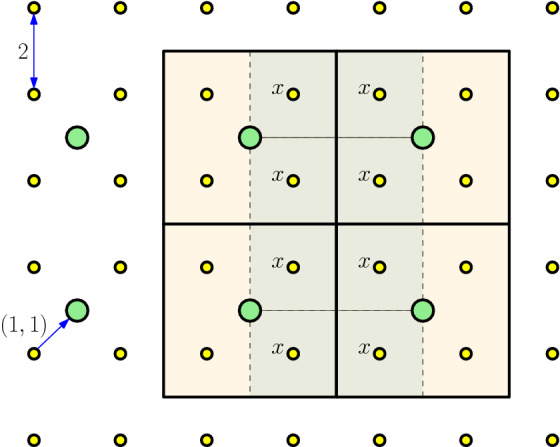
is represented by small disks (yellow), while is represented by larger disks (green). Possible locations of x are indicated with their Voronoi regions. The Voronoi regions of the larger grid contain those of x
Cubical complex of
The integer grid naturally defines a cubical complex, where each element is an axis-aligned, k-dimensional cube with . To define it formally, let denote the set of all integer translates of faces of the unit cube , considered as a convex polytope in . We call the elements of faces of .
Each face has a dimension k; the 0-faces, or vertices are exactly the points in . The facets of a k-face E are the -faces contained in E. We call a pair of facets of E opposite facets, if they are disjoint. Naturally, these concepts carry over to scaled and shifted versions of , so we define as the cubical complex defined by .
We define a map as follows: for vertices of , we assign to the (unique) vertex such that (see Lemma 2). For a k-face f of with vertices in , we set to be the convex hull of ; the next lemma shows that this is a well-defined map. In this paper, we sometimes call a cubical map, since it is a counterpart of simplicial maps for cubical complexes.
Lemma 3
Let f be k-face of with vertices . Then
the set of vertices form a face e of .
for every face , there is a face such that .
if are any two opposite facets of e, then there exists a pair of opposite facets of f such that and .
Proof
First claim: We prove the first claim by induction on the dimension of faces of . Base case: for vertices, the claim is trivial using Lemma 2. Induction case: let the claim hold true for all -faces of . We show that the claim holds true for all k-faces of .
Let f be a k-face of . Let and be opposite facets of f, along the m-th coordinate. Let us denote the vertices of by and those of by taken in the same order, that is, and differ in only the m-th coordinate for all . By definition, all vertices of share the m-th coordinate, and we denote coordinate of these vertices by z. Then, the m-th coordinate of all vertices of equals . Then and have the same coordinates, except possibly the m-th coordinate. By induction hypothesis, and are two faces of . This implies that is a translate of along the m-th coordinate.
There are two cases: if and share the m-th coordinate, then and therefore , so the claim follows. On the other hand, if and do not share the m-th coordinate, then they are two faces of which differ in only one coordinate by . So they are opposite facets of a co-dimension one face e of . Using induction, the claim follows.
Second claim: We prove the claim by induction over the dimension of . Base case: is a vertex. The vertices of f in Voronoi region of form . Since f is an axis parallel face and the Voronoi region is also axis-parallel, it is immediate that is a face of f. Assume that the claim is true up to dimension i. For a face of dimension , consider opposite facets and of e. By the induction claim, there exist faces that satisfy . and are disjoint since otherwise would be common to both and , a contradiction. If is a translate of along the m-th coordinate, then is also a translate of along the same coordinate. Therefore and are opposite faces of a face and .
Third claim: Without loss of generality, assume that is the direction in which is a translate of . Using the second claim, let h denote the maximal face of f such that . Clearly, , since that would imply , which is a contradiction.
Suppose h has dimension less than . Let be the facet of f that contains h and has the same coordinates for all vertices. Then , which contradicts the maximality of h.
Therefore, the only possibility is that h is a facet of f such that . Let be the opposite facet of . From the proof of the first claim, it is easy to see that . The claim follows.
Barycentric subdivision
We discuss a special triangulation of . A flag in is a set of faces of such that
The barycentric subdivision of , denoted by , is the (infinite) simplicial complex whose simplices are the flags of (Munkres 1984).
In particular, the 0-simplices of are the faces of . An equivalent geometric description of can be obtained by defining the 0-simplices as the barycenters of the faces in , and introducing a k-simplex between barycenters if the corresponding faces form a flag. For a simple example, see Figs. 2 and 3. It is easy to see that is a flag complex. Given a face f in , we write sd(f) for the subcomplex of consisting of all flags that are formed only by faces contained in f.
Fig. 2.
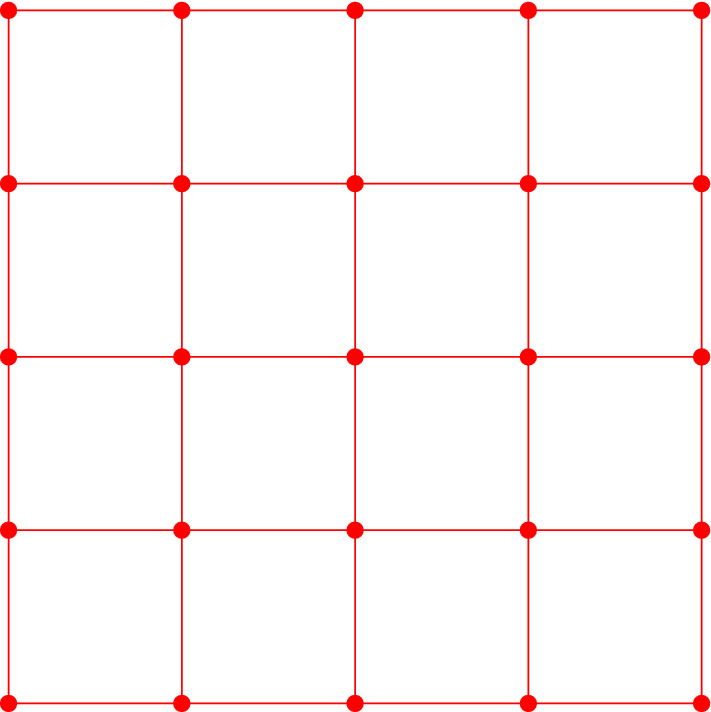
A portion of the grid in two dimensions. The dots are the grid points which form the 0-faces of the cubical complex
Fig. 3.
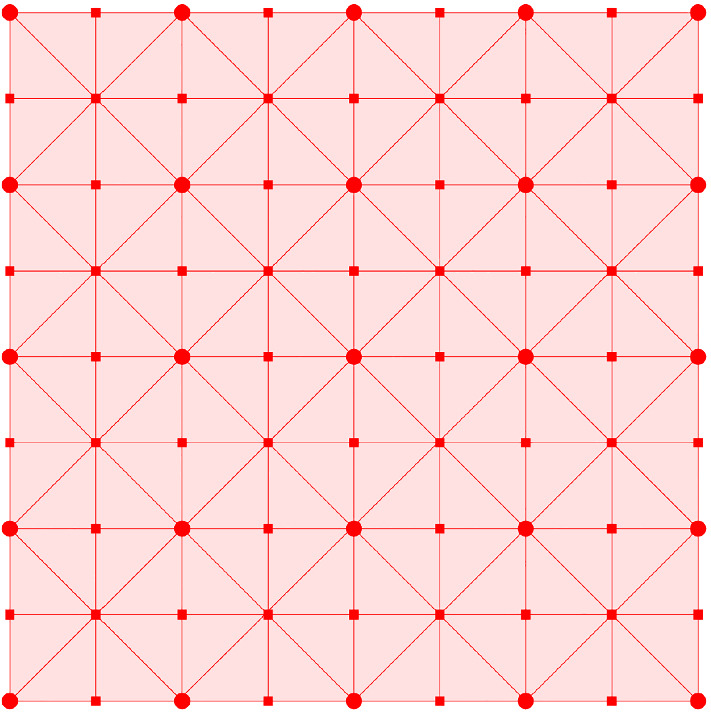
The barycentric subdivision of the grid. The tiny squares are barycenters of the 1-faces and 2-faces of the cubical complex
Approximation scheme with simplicial complexes
We define our approximation complex for a finite set of points in . Recall from Definition 1 that we can define a collection of scaled and shifted integer grids over a collection of scales in . To make the exposition simple, we define our complex in a slightly generalized form.
Barycentric spans
Fix some and let V denote any non-empty subset of .
Vertex span. We say that a face is spanned by V, if the set of vertices
is non-empty, and
not contained in any facet of f.
Trivially, the vertices of which are spanned by V are precisely the points in V. Any face of which is not a vertex must contain at least two vertices of V in order to be spanned. We point out that the set of spanned faces of is not closed under taking sub-faces. For instance, if V consists of two antipodal points of a d-cube, the only faces spanned by V are the d-cube and the two vertices; all other faces of the d-cube contain at most one vertex and hence are not spanned.
It is simple to test whether any given k-face is spanned by the set of points V(f). Let be the set of common coordinates of the points in V(f). V(f) spans f if and only if the standard basis vectors of corresponding to T span f. T can be computed in time by a linear scan of the coordinates. The coordinate directions spanned by f can also be found and compared with T within the same time bound.
Barycentric span. The barycentric span of V is the subcomplex of obtained by taking the union of the complete barycentric subdivisions of the maximal faces of that are spanned by V. The barycentric span of V is indeed a simplicial complex by definition. Moreover, the barycentric span is a flag complex. Then for any face , the barycentric span of V(f) is either empty or acyclic.
Furthermore, for any non-empty subset , the faces of that are spanned by W are also spanned by V. Consequently, the barycentric span of W is a subcomplex of the barycentric span of V.
Approximation complex
We denote by a finite set of points. We define two maps:
- : for each point , we let denote the grid point in that is closest to p, that is, . We assume for simplicity that this closest point is unique, which can be ensured using well-known methods (Edelsbrunner and Mücke 1990). We define the active vertices of as
that is, the set of grid points that have at least one point of P in their Voronoi cells. : the map takes an active vertex of to its closest point in P. By taking an arbitrary total order on P to resolve multiple assignments, we ensure that this assignment is unique.
Naturally, is a point inside for any . It follows that the map is a section of , that is, is the identity on . However, this is not true for in general.
Recall that the map takes grid points of to grid points of . Using Lemma 2, it follows at once that:
Lemma 4
For all and each , .
Recall that denotes the Rips complex at scale for the -norm. The next statement is a direct application of the the triangle inequality; let denote the diameter in the -norm.
Lemma 5
Let be a non-empty subset such that . Then, the set of grid points is contained in a face of .
Equivalently, for any simplex on P, the set of active vertices is contained in a face of .
Proof
We prove the claim by contradiction. Suppose that the set of active vertices is not contained in a face of . Then, there exists at least one pair of points such that , are not in a common face of . By the definition of the grid , the grid points , therefore have -distance at least . Moreover, x has -distance less than from , and the same is true for y and . By the triangle inequality, the -distance of x and y is more than , which is a contradiction to the fact that .
We now define our approximation tower. For any scale , we define as the barycentric span of the active vertices . See Figs. 4, 5 and 6 for a simple illustration.
Fig. 4.

A two-dimensional grid, shown along with its cubical complex. The green points (small dots) denote the points in P and the red vertices (encircled) are the active vertices (color figure online)
Fig. 5.
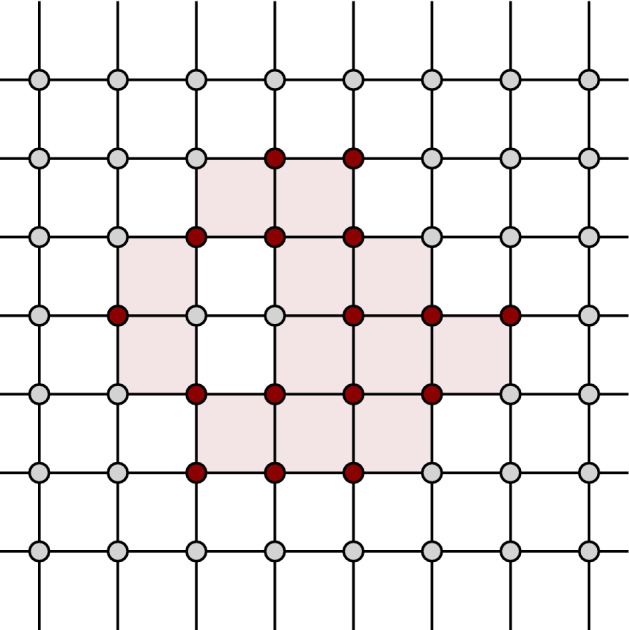
The active faces are shaded. The closure of the active faces forms the cubical complex
Fig. 6.

The generated approximation complex, whose vertices consist of those of the cubical complex and the blue vertices (small dots), which are the barycenters of active and secondary faces
To simplify notation, we denote
the faces of spanned by as active faces, and
the faces of active faces that are not spanned by as secondary faces.
To complete the description of the approximation tower, we need to define simplicial maps of the form , which connect the simplicial complexes at consecutive scales. We show that such maps are induced by .
Lemma 6
Let f be any active face of . Then, is an active face of .
Proof
Using Lemma 3, is a face of . If e is a vertex, then it is active, because f contains at least one active vertex v, and in this case. If e is not a vertex, we assume for a contradiction that it is not active. Then, it contains a facet that contains all active vertices in e. Let denote the opposite facet of in e. By Lemma 3, f contains opposite facets , such that and . Since f is active, both and contain active vertices; in particular, contains an active vertex v. But then the active vertex must lie in , contradicting the fact that contains all active vertices of e.
As a result, g is well defined for each face , since there exists some active face with , and . By definition, a simplex is a flag of faces in . We set
where is a flag of faces in by Lemma 6, and hence is a simplex in . It follows that is a simplicial map. This completes the description of the simplicial tower
Interleaving with the Rips module
First, we show that our tower is a constant-factor approximation of the the -Rips filtration of P. We then show the relation between our approximation tower and the Euclidean Rips filtration of P.
We start by defining two acyclic carriers. First, we set and abbreviate to simplify notation.
: for any simplex in , we set as the barycentric span of , which is a subcomplex of . Using Lemma 5, U lies in a maximal active face f of , so that is acyclic. The barycentric span of any subset of U is a subcomplex of the barycentric span of U, so is a carrier. Therefore, is an acyclic carrier.
: let be any flag of and let E be the smallest active face of that contains (we break ties by making use of an arbitrary global order on P)5. We collect all the points of P that map to vertices of E under the map and set as the simplex on this set of points. By an application of the triangle inequality, we see that the -diam of is at most , so and is acyclic. It is also clear that for each , so is an acyclic carrier.
Using the acyclic carrier theorem (Theorem 1), there exist augmentation-preserving chain maps
between the chain complexes, which are carried by and respectively, for each . We obtain the following diagram of augmentation-preserving chain maps:
 |
10 |
where inc corresponds to the chain map for inclusion maps, and denotes the chain map for the corresponding simplicial map g (we removed indices of the maps for readability).
The chain complexes give rise to a diagram of the corresponding homology groups, connected by the induced linear maps :
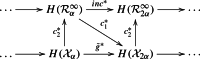 |
11 |
Lemma 7
For all , the linear maps in the lower triangle of Diagram (11) commute, that is,
Proof
We look at the corresponding triangle in Diagram (10). We show that the (augmentation-preserving) chain maps and are both carried by an acyclic carrier . The claim then follows from the acyclic carrier theorem.
Let be any flag and let denote the minimal active face containing . Let be the active vertices of E. Let be the set of points of P that map to under the map . Since the -diameter of is at most , using Lemma 5 we see that is a face of . We set as the barycentric span of . It follows that D is an acyclic carrier.
Further, from Lemma 2, so is the barycentric subdivision of . As a result so that it carries . We show that D also carries the map .
By definition, for each face , and . This means that is contained in g(E). This shows that implying that is carried by , as required.
Lemma 8
For all , the linear maps in the upper triangle of Diagram (11) commute, that is,
Proof
The proof technique is analogous to the proof of Lemma 7. We define an acyclic carrier which carries inc and , both of which are augmentation-preserving.
Let be any simplex. The set of active vertices
lie in a face f of , using Lemma 5. We can assume that f is active, as otherwise, we argue about a facet of f that contains U. We set as the simplex on the subset of points in P, whose closest grid point in is any vertex of f. Using the triangle inequality we see that , so D is an acyclic carrier. The vertices of are a subset of , so D carries the map inc. Showing that D carries requires further explanation.
Let be any simplex in for which the chain takes a non-zero value. Since is carried by , we have that , which is the barycentric span of U. Furthermore, for any , is a simplex on the set of vertices . It follows that . In particular, since is carried by , as well.
Using Lemmas 7 and 8, we see that the two persistence modules and are weakly 2-interleaved.
With elementary modifications in the definition of and , we can get a tower of the form . Furthermore, with minor changes in the interleaving arguments, we show that the corresponding persistence module is strongly 4-interleaved with the -Rips module. Using scale balancing, this result improves to a strong 2-interleaving (see Lemma 16). Since the techniques used in the proof are very similar to the concepts used in this section, for the sake of brevity we defer all further details to Appendix A.
Using the strong stability theorem for persistence modules and taking scale balancing into account, we immediately get that:
Theorem 2
The scaled persistence module and the -Rips persistence module are 2-approximations of each other.
For any pair of points , it holds that
This in turn shows that the - and the -Rips filtrations are strongly -interleaved. Using the scale balancing technique for strongly interleaved persistence modules, we get:
Lemma 9
The scaled persistence module and are strongly -interleaved.
Using Theorem 2, Lemma 9 and the fact that interleavings satisfy the triangle inequality (Bubenik and Scott 2014, Theorem 3.3), we see that the module is strongly -interleaved with the scaled Rips persistence module . We can remove the scaling in the Rips filtration simply by multiplying the scales on both sides with and obtain our final approximation result:
Theorem 3
The module and the Euclidean Rips persistence module are -approximations of each other.
Computational complexity
In this section, we discuss the computational aspects of constructing the approximation tower. In Sect. 5.1 we discuss the size complexity of the tower. An algorithm to compute the tower efficiently is presented in Sect. 5.2.
Range of relevant scales. Set and let CP(P) denote the closest pair distance of P. At scale and lower, no two active vertices lie in the same face of the grid, so the approximation complex consists of n isolated 0-simplices. At scale and higher, points of P map to active vertices of a common face (by Lemma 5), so the generated complex is acyclic. We inspect the range of scales to construct the tower, since the barcode is explicitly known for scales outside this range. For this, we set in the definition of the scales. The total number of scales is
where is the spread of the point set.
Size of the tower
The size of a tower is the number of simplices that do not have a preimage, that is, the number of simplex inclusions in the tower. We start by counting the number of active faces used in the tower.
Lemma 10
The number of active faces without pre-image in the tower is at most .
Proof
At scale , there are n inclusions of 0-simplices in the tower, due to n active vertices. Using Lemma 2, g is surjective on the active vertices of (for any scale). Hence, no further active vertices are added to the tower.
It remains to count the maximal active faces of dimension without preimage. We will use a charging argument, charging the existence of such an active face to one of the points in P. We show that each point of P is charged at most times, which proves the claim. For that, we first fix an arbitrary total order on P. Each active vertex on any scale has a non-empty subset of P in its Voronoi region; we call the maximal such point with respect to the order the representative of the active vertex.
For each active face f of dimension at least one, we define the signature of f as the set of representatives of the active vertices of f. If for any set of active vertices we have that , then the representative of v is one of the representatives of , using Lemma 2. Therefore, the signatures of the active faces that are images of f under g are subsets of the signature of f. This implies that each maximal active face that is included has a unique maximal signature. We bound the number of maximal signatures to get a bound on the number of maximal active face inclusions. We charge the addition of each maximal signature to the lowest ordered point according to .
Each signature contains representatives of active vertices from a face of . Since each active vertex v has neighboring vertices in the grid that lie in a common face, the representative p of v can be charged times. There is a canonical isomorphism between the neighboring vertices of v at each scale. Then, for p to be charged more times, the image of v and some neighboring vertex u must be identical under g at some scale. But then, the representative of is not p anymore, since p was the lowest ranked point in its neighborhood, hence the representative changes when the Voronoi regions are combined. So, p could not have been charged in such a case. Therefore, each point is indeed charged at most times.
There are n active faces of dimension 0 and at most active faces of higher dimension. The upper bound is , as claimed.
Theorem 4
The k-skeleton of the tower has size at most
where denotes the Stirling number of the second kind.
Proof
Each k-simplex that is included in the tower at any given scale is a part of the barycentric subdivision of an active face that is also included at . Therefore, we can account for the inclusion of this simplex by including the barycentric subdivision of its parent active face.
From Lemma 10 at most active faces are included in the tower over all dimensions. We bound the number of k-simplices in the barycentric subdivision of a d-cube. Multiplying with gives the required bound.
Let c be any d-cube of . To count the number of flags of length contained in c that start with some vertex and end with c, we use similar ideas as in Edelsbrunner and Kerber (2012): first, we fix any vertex v of c and count the flags of the form . Every -face in c incident to v corresponds to a subset of coordinate indices, in the sense that the coordinates not chosen are fixed to the coordinates of v for the face. With this correspondence, a flag from v to c of length corresponds to an ordered m-partition of . The number of such partitions is known as m! times the quantity , which is the Stirling number of second kind (Rennie and Dobson 1969), and is upper bounded by . Since c has vertices, the total number of flags of length with any vertex v is hence .
We now count the number of flags of length . Each such flag is -subset of some flag of length that start with a vertex and end with c. There are such flags and each of them has subsets of size . The number of -flags is upper bounded by . The k-skeleton has size at most
Computing the tower
From Sect. 3, we know that is built from by making use of an arbitrary translation vector . In our algorithm, we pick the components of this translation vector uniformly at random from , and independently for each scale. The choice behind choosing this vector randomly becomes more clear in the next lemma.
From the definition, the cubical maps can be composed for multiple scales. For a fixed , we denote by the j-fold composition of g, that is,
for .
Lemma 11
For any k-face with , let Y denote the minimal integer j such that is a vertex, for a given choice of the randomly chosen translation vectors. Then, the expected value of Y satisfies
which implies that no face of survives more than scales in expectation.
Proof
Without loss of generality, assume that the grid under consideration is and f is the k-face spanned by the vertices , so that the origin is a vertex of f. The proof for the general case is analogous.
Let denote the randomly chosen first coordinate of the translation vector, so that the corresponding shift is one of .
If , then the grid on the next scale has some grid point with -coordinate 1/2. Clearly, the closest grid point in to the origin is of the form , and thus, this point is also closest to . The same is true for any point and its corresponding point on the opposite facet of f. Hence, for , g(f) is a face where all points have the same -coordinate.
On the other hand, if , the origin is mapped to some point which has the form and is mapped to , as one can directly verify. Hence, in this case, in g(f), points do not all have the same coordinate.
We say that the -coordinate collapses in the first case and survives in the second. Both events occur with the same probability 1/2. Because the shift is chosen uniformly at random for each scale, the probability that did not collapse after j iterations is .
f spans k coordinate directions, so it must collapse along each such direction to contract to a vertex. Once a coordinate collapses, it stays collapsed at all higher scales. As the random shift is independent for each coordinate direction, the probability of a collapse is the same along all coordinate directions that f spans. Using the union bound, the probability that has not collapsed to a vertex is at most . With Y as in the statement of the lemma, it follows that
Hence,
As a consequence of the lemma, the expected “lifetime” of k-simplices in our tower with is rather short: given a flag , the face will be mapped to a vertex after steps, and so will be all its sub-faces, turning the flag into a vertex. It follows that summing up the total number of k-simplices with over for all yields an upper bound of as well.
Algorithm description
Recall that a simplicial map can be written as a composition of simplex inclusions and contractions of vertices (Dey et al. 2014; Kerber and Schreiber 2017). That means, given the complex , to describe the complex at the next scale , it suffices to specify
which pairs of vertices in map to the same image under , and
which simplices in are included at scale .
The input is a set of n points . The output is a list of events, where each event is of one of the three following types:
A scale event defines a real value and signals that all upcoming events happen at scale (until the next scale event).
An inclusion event introduces a new simplex, specified by the list of vertices on its boundary (we assume that every vertex is identified by a unique integer).
A contraction event is a pair of vertices (i, j) from the previous scale, and signifies that i and j are identified as the same from that scale.
In a first step, we estimate the range of scales that we are interested in. We compute a 2-approximation of diam(P) by taking any point and calculating . Then we compute CP(P) using a randomized algorithm in expected time (Khuller and Matias 1995).
Next, we proceed scale-by-scale and construct the list of events accordingly. On the lowest scale, we simply compute the active vertices by point location for P in a cubical grid, and enlist n inclusion events (this is the only step where the input points are considered in the algorithm).
For the data structure, we use an auxiliary container S and maintain the invariant that whenever a new scale is considered, S consists of all simplices of the previous scale, sorted by dimension. In S, for each vertex, we store an id and a coordinate representation of the active face to which it corresponds. Every -simplex with is stored just as a list of integers, denoting its boundary vertices. We initialize S with the n active vertices at the lowest scale.
Let be any two consecutive scales with the respective cubical complexes and the approximation complexes, with being the simplicial map connecting them. Suppose we have already constructed all events at scale .
First, we enlist the scale event for .
Then, we enlist the contraction events. For that, we iterate through the vertices of and compute their value under g, using point location in a cubical grid. We store the results in a list (which contains the simplices of ). If for a vertex j, g(j) is found to be equal to g(i) for a previously considered vertex i, we choose the minimal such i and enlist a contraction event for (i, j).
- We turn to the inclusion events:
- We start with the case of vertices. Every vertex of is either an active face or a secondary face of . Each active face must contain an active vertex, which is also a vertex of . We iterate through the elements in . For each active vertex v encountered, we go over all faces of the cubical complex that contain v as a vertex, and check whether they are active. For every active face E encountered that is not in yet, we add it to and enlist an inclusion event of a new 0-simplex. Additionally, we go over each face of E, add it to and enlist a vertex inclusion event, thereby enumerating the secondary faces that are in E. At termination, all vertices of have been detected.
- Next, we iterate over the simplices of S of dimension , and compute their image under using the pre-computed vertex map; we store the result in .
- To find the simplices of dimension included at , we exploit our previous insight that they contain at least one vertex that is included at the same scale (see the proof of Theorem 4). Hence, we iterate over the vertices included in and find the included simplices inductively in dimension. Let v be the current vertex under consideration; assume that we have found all -simplices in that contain v. Each such -simplex is a flag of length p in . We iterate over all faces e that extend to a flag of length . If e is active, we have found a p-simplex in incident to v. If this simplex is not in yet, we add it and enlist an inclusion event for it. We also enqueue the simplex in our inductive procedure, to look for -simplices in the next round. At the end of the procedure, we have detected all simplices in without preimage, and contains all simplices of . We set and proceed to the next scale.
This ends the description of the algorithm.
Theorem 5
To compute the k-skeleton, the algorithm takes
time in expectation and M space, where M denotes the size of the tower. In particular, the expected time is bounded by
and the space is bounded by .
Proof
In the analysis, we ignore the costs of point locations in grids, checking whether a face is active, and searches in data structures S, since all these steps have negligible costs when appropriate data structures are chosen.
Computing the image of a vertex of costs time. Moreover, there are at most vertices altogether in the tower in expectation (using Lemma 10), so this bound in particular holds on each scale. Hence, the contraction events on a fixed scale can be computed in time. Finding new active vertices requires iterating over the cofaces of a vertex in a cubical complex. There are such cofaces for each vertex. This has to be done for a subset of the vertices in , so the running time is also . Further, for each new active face, we go over its faces to enlist the secondary faces, so this step also consumes time. Since there are scales considered, these steps require over all scales.
Computing the image of for a fixed scale costs at most . M is the size of the tower, that is, the simplices without preimage, and I is the set of scales considered. The expected bound for , because every simplex has an expected lifetime of at most by Lemma 11. Hence, the cost of these steps is bounded by .
In the last step of the algorithm, we find the simplices of included at . We consider a subset of simplices of , and for each, we iterate over a collection of faces in the cubical complex of size at most . Hence, this step is also bounded by per scale, and hence bounded as well.
For the space complexity, the auxiliary data structure S gets as large as , which is clearly bounded by M. For the output complexity, the number of contraction events is at most the number of inclusion events, because every contraction removes a vertex that has been included before. The number of inclusion events is the size of the tower. The number of scale events as described is . However, it is simple to get rid of this factor by only including scale events in the case that at least one inclusion or contraction takes place at that scale. The space complexity bound follows.
Dimension reduction
When the ambient dimension d is large, our approximation scheme can be combined with dimension reduction techniques to reduce the final complexity, very similar to the application in Choudhary et al. (2017b). For a set of n points , we apply the dimension reduction schemes of Johnson-Lindenstrauss (JL) (Johnson et al. 1986), Matoušek (MT) (Matoušek 1990), and Bourgain’s embedding (BG) (Bourgain 1985). We then compute the approximation on the lower-dimensional point set. We only state the main results in Table 1, leaving out the proofs since they are very similar to those from Choudhary et al. (2017b).
Table 1.
Comparison of dimension reduction techniques: here the approximation ratio is for the Rips persistence module, and the size refers to the size of the k-skeleton of the approximation
| technique | approximation ratio | size | runtime |
|---|---|---|---|
| JL | |||
| MT | |||
| BG + MT |
Approximation scheme with cubical complexes
We extend our approximation scheme to use cubical complexes in place of simplicial complexes. We start by detailing a few aspects of cubical complexes.
Cubical complexes
We now briefly describe the concept of cubical complexes, essentially expanding upon the contents of Sect. 3.1. For a detailed overview of cubical homology, we refer to Kaczynski et al. (2004).
Definition
We define cubical complexes over the grids . For any fixed , the grids defines a natural collection of cubes. An elementary cube is a product of intervals , where each interval is of the form , such that the vertex and each is either 0 or . That means, an (elementary) cube is simply a face of a d-cube of the grid. An interval is said to be degenerate if . The dimension of is the number of non-degenerate intervals that defines it. We define the boundary of any interval as the two degenerate intervals that form its endpoints and denote this by . Taking the boundary of any fixed subset of the intervals defining consecutively gives a sum of faces of . A cubical complex of is a finite collection of cubes of .
We define chain complexes for the cubical case in the same way as in simplicial complexes. The chain complexes are connected by boundary homomorphisms, where the boundary of a cube is defined as:
where denotes the sum
It can be quickly verified that for each cube , since each term appears twice in the expression and the addition is over .
Cubical maps and induced homology
Let and denote the cubical complexes defined by the grids and , respectively, for . We use the vertex map to define a map between the cubical complexes. Note that if (a, b) are vertices of a cube of that differ in one coordinate, then (g(a), g(b)) are vertices of a cube of that differ in at most one coordinate. A cubical map is a map defined using g, such that for each cube of , spans a cube of . The cubical map can also be restricted to sub-complexes of and , provided that the image is well-defined.
Each cubical map also defines a corresponding continuous map between the underlying spaces of the respective complexes. Let be a point in . Then, the coordinates of x can be uniquely written as where each . The image of x under the continuous extension of f is the point in the cube .
The cubical map f gives rise to a chain map between the p-th chain groups of the complexes, for each . For each cube , if and 0 otherwise. For any chain , the chain map is defined linearly . It is simple to verify that , so this gives a homomorphism between the chain groups.
Moving to the homology level, we get the respective homology groups and and the chain map from above induces a linear map between them. The concept of reduced homology and augmentation maps is also applicable to the cubical chain complexes. For a sequence of cubical complexes connected with cubical maps, this generates a persistence module.
Cubical filtrations and towers are defined in a similar manner to the simplicial case. A cubical filtration is a collection of cubical complexes such that for all . A (cubical) tower is a sequence of cubical complexes with J being an index set together with cubical maps between complexes at consecutive scales. A cubical tower can be written as a sequence of inclusions and contractions, where an inclusion refers to the addition of a cube and a contraction refers to collapsing a cube along a coordinate direction to either of the endpoints of the interval.
Description
We choose the simplest possible cubical complex to define our approximation cubical tower: for each scale , we define the cubical complex as the set of active faces and secondary faces spanned by . Hence the cubical complex is closed under taking faces and is well-defined. See Fig. 5 for a simple example.
Recall from Sect. 4 that for each , and are related by a cubical map , which gives rise to the cubical tower
We extend this to a tower by using techniques from Appendix A. In Sect. 4 we saw that the tower gives an approximation to the Rips filtration. The relation between the simplicial and cubical towers is trivial: is simply a triangulation of . Hence and have the same homology (Munkres 1984). Moreover, the simplicial map is derived from an application of the cubical map. In particular, the continuous versions of both maps are the same. For any , let
denote the homomorphism induced by the cubical map,
denote the homomorphism induced by the simplicial map, and
denote the homomorphism induced by the common continuous map.
It is well-established that (Kaczynski et al. 2004, Chapter. 6) and (Munkres 1984, Chapter. 2). Therefore, we conclude that the persistence modules and are persistence-equivalent. Combining this observation with the result of Theorem 3, we get
Theorem 6
The scaled persistence modules
and the -Rips module are 2-approximations of each other, and
and the Rips module -approximate each other.
To compute the cubical tower, we simply re-use the algorithm for the simplicial case, with small changes:
In the simplicial case, we used a container S to hold the simplices from the previous scale. We alter S to store the cubes from the previous scale. For each interval, we store an id and its coordinates. Each cube is stored as the set of ids of the intervals that define it.
At each scale, we enumerate the image of the cubical map by computing the image of each interval, and then use this pre-computed map to compute the image of -dimensional cubes.
For the inclusions, we find all the active and secondary faces but do not compute the simplices. The inclusions in the cubical tower correspond exactly to the inclusions of active and secondary faces in the simplicial tower, so this enumerates all inclusions correctly.
From Lemma 10 at most active faces are added to the tower. Hence at most active and secondary faces are added to the tower. Computing the tower takes time as in Theorem 5 by replacing M with the size bound. We conclude that:
Theorem 7
The cubical tower has size at most and takes at most time in expectation to compute, where is the spread of the point set.
Discussion
Practicality
We now touch upon the practical aspects of our constructions. An implementation of our approximation scheme would be a tool that computes the (approximate) persistence barcode for any input data set. For any scheme to be useful in practice, it should be able to compute sufficiently close approximations using a reasonable amount of resources.
Our cubical tower consists of cubical complexes connected via cubical maps. To our knowledge, there are no algorithms to compute barcodes in this setting where the cubical maps are more than just trivial inclusions. As such, although our cubical scheme has exponentially lower theoretical guarantees compared to the simplicial tower, we can not hope to test it in practice unless the appropriate primitives are available. It could be an interesting research direction to develop this primitive and in particular investigate whether the techniques used in computing persistence barcodes for a simplicial tower allow a generalization to the cubical case.
It makes more sense to inspect the simplicial tower. We saw in Theorem 4 that the size of the tower is . Unfortunately, this bound is already too large so that the storage requirement of the Algorithm (Theorem 7) explodes exponentially. Let us assume a conservative bound of 1 Byte of memory requirement per simplex. For a point set in dimensions and , the complexity bound is already at least 4000 Terabytes, before factoring in n. For a point set in dimensions and , this explodes to Terabytes. While these are upper bounds, in practice the complexity will still need to be many orders of magnitude smaller to be feasile, which is unlikely. Even with conservative estimates our storage requirement is impractical.
Therefore we are not very hopeful that implementing the scheme in its current state will provide any useful insight for high dimensional approximations. Making it implementation-worthy demands more optimizations and tools at the algorithmic level. This is worth another Algorithmic engineering project in its own right. We plan to pursue this line of research in the future. Since our focus in this paper was geared towards theoretical aspects of approximations, we exclude experimental results in the current work. We hope that a more careful implementation-focussed approach may prove more practical.
On the other hand, the upper bound for the cubical case is simply . Even for , the storage requirement would be less than 100 Megabytes before factoring in n. This is far more attractive than the simplicial case. As such, it may make more sense to invest time and effort in developing tools to compute barcodes in the cubical setup.
Summary
We presented an approximation scheme for the Rips filtration, with improved approximation ratio, size and computational complexity than previous approaches for the case of high-dimensional point clouds. In particular, we are able to achieve a marked reduction in the size of the approximation by using cubical complexes in place of simplicial complexes. This is in contrast to all other previous approaches that used simplicial complexes as approximating structures.
An important technique that we used in our scheme is the application of acyclic carriers to prove interleaving results. An alternative would to be explicitly construct chain maps between the Rips and the approximation towers; unfortunately, this make the interleaving analysis significantly more complex. While the proof of the interleaving in Sect. 4.3 is still technically challenging, it greatly simplifies by the usage of acyclic carriers. There is also no benefit in knowing the interleaving maps because they are only required for the analysis of the interleaving, and not for the actual computation of the approximation tower. We believe that this technique is of general interest for the construction of approximations of cell complexes.
Our simplicial tower is connected by simplicial maps; there are (implemented) algorithms to compute the barcode of such towers (Dey et al. 2014; Kerber and Schreiber 2017). It is also quite easy to adapt our tower construction to a streaming setting (Kerber and Schreiber 2017), where the output list of events is passed to an output stream instead of being stored in memory.
Acknowledgements
We would like to thank the reviewers end editors for their feedback, which was very helpful in improving the presentation.
Strong interleaving for barycentric scheme
Recall that we build the approximation tower over the set of scales . The tower connected with the simplicial map can be extended to the set of scales with simple modifications:
for , we define in the usual manner. The map stays the same as before for complexes at such scales.
for all , we set , for any . That means, the complex stays the same in the interval between any two scales of I, so we define as the identity within this interval.
These give rise to the tower , that is connected with the simplicial map . This modification helps in improving the interleaving with the Rips persistence module.
First, we extend the acyclic carriers and from before to the new case:
: we define as before, simply changing the scales in the definition. It is straightforward to see that is still a well-defined acyclic carrier.
: this stays the same as before. It is simple to check that is still a well-defined acyclic carrier.
These give rise to augmentation-preserving chain maps between the chain complexes:
using the acyclic carrier theorem as before (Theorem 1).
Lemma 12
The diagram
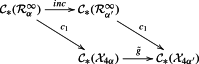 |
12 |
commutes on the homology level, for all .
Proof
Consider the acyclic carrier . It is simple to verify that this carrier carries both and , so the induced diagram on the homology groups commutes, from Theorem 1.
Lemma 13
The diagram
 |
13 |
commutes on the homology level, for all .
Proof
We construct an acyclic carrier which carries and , thereby proving the claim (Theorem 1).
Consider any simplex and let be the minimal active face of containing . We set as the simplex on the set of input points of P, which lie in the Voronoi regions of the vertices of g(E). By the triangle inequality, is a simplex of , so that D is a well-defined acyclic carrier. It is straightforward to verify that D carries both and .
Lemma 14
The diagram
| 14 |
commutes on the homology level, for all .
Proof
The diagram is essentially the same as the lower triangle of Diagram 10, with a change in the scales. As a result, the proof of Lemma 7 also applies for our claim directly.
Lemma 15
The diagram
| 15 |
commutes on the homology level, for all .
Proof
The diagram can be re-interpreted as:
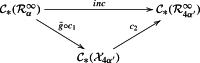 |
16 |
The modified diagram is essentially the same as the upper triangle of Diagram 10, with a change in the scales and a replacement of with , that is equivalent to the chain map at the scale . Hence, the proof of Lemma 8 also applies for our claim directly.
Using Lemmas 12, 13, 14, 15, and the scale balancing technique for strongly interleaved persistence modules, it follows that
Lemma 16
The persistence modules and are strongly 2-interleaved.
Funding
Open Access funding enabled and organized by Projekt DEAL.
Declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Footnotes
An exception are point clouds in and , for which alpha complexes (Edelsbrunner and Harer 2010) are an efficient alternative.
Ulrich Bauer, private communication.
To avoid thinking about orientations, it is often assumed that is the field with two elements.
In the language of Munkres (1984), this result is stated as the existence of a chain homotopy between and . As evident from Munkres (1984), Theorem 12.4, this implies that the induced linear maps are the same.
We define an order between the active faces of , using : for each active face , there are at least two points of P whose images under are vertices of F; say are the points that map to F. We assign to F the string of length n:  . Each active face has a unique string associated to it. A total order on the faces is obtained by taking the lexicographic orders of the strings of each active face.
. Each active face has a unique string associated to it. A total order on the faces is obtained by taking the lexicographic orders of the strings of each active face.
Aruni Choudhary is supported in part by European Research Council StG 757609. Michael Kerber is supported by Austrian Science Fund (FWF) grant number P 29984-N35. Sharath Raghvendra acknowledges support of NSF CRII grant CCF-1464276.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Aruni Choudhary, Email: arunich@inf.fu-berlin.de.
Michael Kerber, Email: kerber@tugraz.at.
Sharath Raghvendra, Email: sharathr@vt.edu.
References
- Botnan M, Spreemann G. Approximating persistent homology in Euclidean space through collapses. Appl. Algebra Eng. Commun. Comput. 2015;26(1–2):73–101. doi: 10.1007/s00200-014-0247-y. [DOI] [Google Scholar]
- Bourgain J. On Lipschitz embedding of finite metric spaces in Hilbert space. Israel J. Math. 1985;52(1–2):46–52. doi: 10.1007/BF02776078. [DOI] [Google Scholar]
- Bubenik P, Scott JA. Categorification of persistent homology. Discrete Comput. Geom. 2014;51(3):600–627. doi: 10.1007/s00454-014-9573-x. [DOI] [Google Scholar]
- Bubenik P, de Silva V, Scott J. Metrics for generalized persistence modules. Found. Comput. Math. 2015;15(6):1501–1531. doi: 10.1007/s10208-014-9229-5. [DOI] [Google Scholar]
- Carlsson G. Topology and data. Bull. Am. Math. Soc. 2009;46:255–308. doi: 10.1090/S0273-0979-09-01249-X. [DOI] [Google Scholar]
- Carlsson G, Zomorodian A. Computing persistent homology. Discrete Comput. Geom. 2005;33(2):249–274. doi: 10.1007/s00454-004-1146-y. [DOI] [Google Scholar]
- Cavanna, N., Jahanseir, M., Sheehy, D.: A Geometric perspective on sparse filtrations. In: Proceedings of the 27th Canadian Conference on Computational Geometry (CCCG), pp. 116–121 (2015)
- Chazal, F., Cohen-Steiner, D., Glisse, M., Guibas, L., Oudot, S.: Proximity of persistence modules and their diagrams. In: ACM Symposium on Computational Geometry (SoCG), pp. 237–246 (2009)
- Choudhary, A., Kerber, M., Raghavendra, S.: Improved approximate rips filtrations with shifted integer lattices. In: Proceedings of the 25th Annual European Symposium on Algorithms (ESA), pp. 28:1–28:13 (2017)
- Choudhary, A., Kerber, M., Raghavendra, S.: Polynomial-sized topological approximations using the permutahedron (extended version). Discrete Comput. Geom. (2017)
- Choudhary, A., Kerber, M., Raghavendra, S.: Improved topological approximations by digitization. In: Proceedings of the Symposium on Discrete Algorithms (SODA), pp. 448:1–448:14 (2019)
- Dey, T.K., Fan, F., Wang, Y.: Computing topological persistence for simplicial maps. In: Proceedings of the 30th Annual Symposium on Computational Geometry (SoCG), pp. 345–354 (2014)
- Edelsbrunner H, Harer J. Computational Topology—An Introduction. New York: American Mathematical Society; 2010. [Google Scholar]
- Edelsbrunner H, Kerber M. Dual complexes of cubical subdivisions of . Discrete Comput. Geom. 2012;47(2):393–414. doi: 10.1007/s00454-011-9382-4. [DOI] [Google Scholar]
- Edelsbrunner, H., Mücke, E.P.: Simulation of simplicity: a technique to cope with degenerate cases in geometric algorithms. ACM Trans. Gr. 66–104 (1990)
- Edelsbrunner H, Letscher D, Zomorodian A. Topological persistence and simplification. Discrete Comput. Geom. 2002;28(4):511–533. doi: 10.1007/s00454-002-2885-2. [DOI] [Google Scholar]
- Goodman JE, O’Rourke J, Tóth CD, editors. Handbook of Computational Geometry. Boca Raton: CRC Press; 2017. [Google Scholar]
- Hatcher A. Algebraic Topology. Cambridge: Cambridge University Press; 2002. [Google Scholar]
- Johnson WB, Lindenstrauss J, Schechtman G. Extensions of Lipschitz maps into Banach spaces. Israel J. Math. 1986;54(2):129–138. doi: 10.1007/BF02764938. [DOI] [Google Scholar]
- Kaczynski T, Mischaikow K, Mrozek M. Computational Homology. New York: Springer; 2004. [Google Scholar]
- Kerber, M., Schreiber, H.: Barcodes of towers and a streaming algorithm for persistent homology. In: Proceedings of 33rd International Symposium on Computational Geometry (SoCG), pp. 57:1–57:15 (2017) [DOI] [PMC free article] [PubMed]
- Kerber, M., Sharathkumar, R.: Approximate Čech complex in low and high dimensions. In: Algorithms and Computation—24th International Symposium (ISAAC), pp. 666–676 (2013)
- Khuller S, Matias Y. A simple randomized sieve algorithm for the closest-pair problem. Inf. Comput. 1995;118(1):34–37. doi: 10.1006/inco.1995.1049. [DOI] [Google Scholar]
- Matoušek, J.: Bi-Lipschitz embeddings into low-dimensional Euclidean spaces. Commentationes Mathematicae Universitatis Carolinae (1990)
- Munkres JR. Elements of Algebraic Topology. Milton Park: Westview Press; 1984. [Google Scholar]
- Rennie BC, Dobson AJ. On stirling numbers of the second kind. J. Comb. Theory. 1969;7(2):116–121. doi: 10.1016/S0021-9800(69)80045-1. [DOI] [Google Scholar]
- Sheehy D. Linear-size approximations to the Vietoris-rips filtration. Discrete Comput. Geom. 2013;49(4):778–796. doi: 10.1007/s00454-013-9513-1. [DOI] [Google Scholar]
- Wagner, H., Chen, C., Vuçini, E.: Efficient Computation of Persistent Homology for Cubical Data, pp. 91–106. Springer, Berlin (2012)


