Abstract
In the present paper, we investigate the performance of the simultaneous wireless information and power transfer (SWIPT) based cooperative cognitive radio networks (CCRNs). In particular, the outage probability is derived in the closed-form expressions under the opportunistic partial relay selection. Different from the conventional CRNs in which the transmit power of the secondary transmitters count merely on the aggregate interference measured on the primary networks, the transmit power of the SWIPT-enabled transmitters is also constrained by the harvested energy. As a result, the mathematical framework involves more correlated random variables and, thus, is of higher complexity. Monte Carlo simulations are given to corroborate the accuracy of the mathematical analysis and to shed light on the behavior of the OP with respect to several important parameters, e.g., the transmit power and the number of relays. Our findings illustrate that increasing the transmit power and/or the number of relays is beneficial for the outage probability.
Keywords: decode–and–forward, outage probability, relay selection, cognitive radio network, SWIPT
1. Introduction
Cognitive radio networks (CRNs) are considered one of the most effective solutions to overcome the scarcity of the frequency spectrum [1,2]. The principal idea of CRNs is to permit unlicensed users to concurrently operate with licensed users while strictly guaranteeing the quality-of-service (QoS) of primary users. To realize such networks two popular protocols are proposed in the literature, namely, the overlay and underlay protocols [3,4]. The former allows secondary devices to opportunistically occupy the temporarily unused spectrum in terms of space, time, and frequency. Regarding the underlay protocol, on the other hand, secondary users are always granted permission to access the licensed spectrum provided that the aggregate interference created by secondary networks measured on the primary devices is below the predefined threshold. Compared to the overlay protocol, the underlay protocol is preferable due to its high availability and, thus, is suitable for urgent services, video conferences, video gaming, and so forth. Nevertheless, the cons of this protocol are that it does not support a long transmission and/or high-quality services owing to the low transmit power to avoid exceeding the interference threshold of the primary networks. As a consequence, in order to employ the underlay CRNs in practice, the combination with other techniques is necessary. Fortunately, relaying or cooperative communications is a good complement to the underlay CRNs [5,6,7]. More precisely, cooperative communications networks are wireless networks where one or several relays are deployed among end-users to help them exchange information. With the help of the relay, the transmission distance is dramatically decreased, improving the system performance. Additionally, relaying technology has also been proven to be an effective way to extend the coverage area. The spectral efficiency and QoS issues can be addressed in a straightforward manner by employing the cooperative cognitive radio networks (CCRNs) [8,9]. Nonetheless, there still exists an urgent issue, which is to improve the energy efficiency of wireless networks. The problem escalates seriously in either the Internet of Things (IoTs), low power wide area networks (LPWAN) [10], or 5G and beyond networks owing to the exponential growth of wireless-connected devices accompanied by their power-hungry applications. In fact, improving energy efficiency is one of the highest priorities in wireless communications. Fortunately, simultaneous wireless information and power transfer (SWIPT) has recently been proposed to deal with this issue [11,12,13]. In particular, SWIPT transmits both information and energy on the same carrier frequency, thus boosting both the spectral and energy efficiency. Consequently, in the present paper, we investigate the performance of the SWIPT-based cooperative cognitive radio networks (CCRNs) with the help of multiple relays. Before highlighting our novel contributions, the state-of-the-art is given as follows.
The performance of CCRNs networks was studied widely in [14,15,16,17,18,19,20]. Specifically, the outage probability (OP) of the cognitive radio non-orthogonal multiple access (NOMA) networks was derived in [14]. The authors in [15], on the other hand, investigated the secrecy performance of the underlay cooperative multihop CRNs. In particular, the secrecy outage probability (SOP) was derived in the approximated closed-form expression. Lee et al. in [16] addressed the minimization of the number of feedback bits required in order to satisfy the QoS in both primary and secondary networks. The optimal power allocation of non-orthogonal amplify–and–forward (AF) relaying of underlay CRNs was provided in [17] to maximize the system throughput. In [18], the capacity of voice over IP (VoIP) in CRNs was analyzed and maximized by modelling the VoIP traffic and channel coefficients as a Markov-modulated Poisson process. Liu et al. in [19] investigated the spectrum sensing problem in the full-duplex cooperative spectrum sensing CRNs. It was noted that spectrum sensing is important in overlay CRNs to guarantee the opportunistic access of secondary devices while not interrupting the primary device’s transmission.
Meanwhile, the performance of SWIPT-enabled networks was investigated in [21,22,23,24,25,26,27,28,29]. The energy-efficient optimization of SWIPT-assisted relaying networks was addressed in [21]. Tan et al. in [22] derived the OP and ergodic capacity of the power splitting (PS) based relaying networks under the asymmetric channel, i.e., the Nakagami-m and Rayleigh channels. The error probability and outage probability of SWIPT-based NOMA networks were derived in [23]. In particular, the pairwise error probability was computed in closed-form expression in [23]. The asymptotic framework under a high SNRs regime was provided as well. The work in [24], differently, derived the symbol error rate (SER) of SWIPT-enabled relaying networks, where the noncoherent modulation was employed in place of the conventional phase-shift keying (PSK) and/or quadrature amplitude modulation (QAM). The authors in [25] also addressed the noncoherent modulation. Specifically, this work first derived the moments and moment generating function (MGF) of the end-to-end (e2e) signal-to-noise ratios (SNRs). Based on the MGF, they then computed the outage probability, the amount of fading, and the system throughput. The authors in [26,27] dealt with the physical layer security (PLS) issue of the simultaneous wireless information and power transfer assisted relaying networks. Furthermore, the performance of SWIPT-based cellular networks with and without utilizing millimeter wave (mmWave) was provided in [28,29].
Despite the extensive study of either the CCRNs or the SWIPT-aided networks, the performance of SWIPT-enabled underlay CCRNs is still in the infancy stage. In particular, there only a few works addressing this combination [30,31,32,33]. Specifically, Prathima et al. in [30] studied the performance of the primary networks with the help of the secondary users that also act as the relay of primary users. This work, however, concentrated on the performance of primary networks. Moreover, it solely considered two relay nodes instead of the general scenario. The work in [31], diversely, addressed the secrecy performance of the SWIPT-assisted cognitive relaying networks. The power allocation and transceiver design were investigated in [32].
In this paper, different from the abovementioned works, we focus on the performance of the secondary networks as well as the reliability of SWIPT-based underlay cooperative cognitive radio networks with regard to transceiver design, power allocation, and physical layer security. In particular, the principal novel contributions are summarized as follows:
We consider a single-input single-output (SISO) underlay cooperative cognitive radio network with the assistance of multiple relays. Additionally, the transmit power of the relay nodes relies only on the harvested energy from the transmitter S. The partial relay selection is adopted to both enhance the system performance and reduce the complexity compared to the fully relay selection.
Different from the conventional underlay CRNs where the transmit power of the secondary transmitter considers merely the interference power, the transmit power of the considered networks is constrained by both the interference power and the harvested energy. The mathematical framework, thus, is of higher complexity owing to dealing with more correlated random variables. Nonetheless, we are still able to derive the outage probability in the closed-form expressions.
Simulation results are presented to corroborate the exactness of our analysis and to identify the behavior of OP with respect to several important parameters, namely, the transmit power, the number of relays, the power splitting ratio, and so on. Our findings show that both increasing the transmit power and number of relays are beneficial to the OP. Additionally, an optimal value of the power splitting ratio exists that minimizes the OP.
The remainder of this paper is organized as follows. The system model is given in Section 2. The derivation of the OP is provided in Section 3. Numerical results are shown in Section 4. Section 5 concludes the paper.
2. System Model
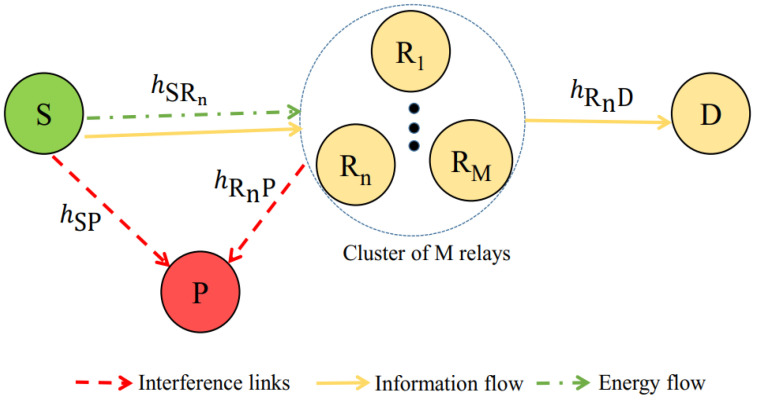
Let us consider SWIPT-based underlay cognitive radio networks as shown in Figure 1. In particular, the secondary networks comprise one source node denoted by S, one destination denoted by D, and M relay nodes denoted by , while the primary networks are represented by a primary receiver denoted by P. Here, P measures the aggregate interference created by the secondary networks on the primary networks.
Figure 1.
SWIPT-based cognitive radio relaying networks.
2.1. Channel Modeling
Considering a generic transmission from node X to node Y, the channel coefficients denoted by , , are followed by a Rayleigh distribution. As a result, the channel gain denoted by is followed by an exponential distribution with parameter whose cumulative distribution function (CDF) and probability density function (PDF) are given as follows [6]:
| (1) |
| (2) |
Here is also the large-scale path loss from X to Y and is formulated as follows:
| (3) |
where is the Euclidean distance between node X and Y and is the path loss exponent. Additionally, the block fading is taken into consideration in this work, hence the channel coefficients remain constants for the whole transmission T and change independently between each transmission.
2.2. PS-Based Relaying Networks
In this work, we adopt the power-splitting (PS) protocol at the relay node. To be more precise, the received power at R is divided into two separate parts according to the power-splitting ratio , i.e., one is put into the energy harvester and another goes to the information decoder. takes into account all loss introduced by the energy harvesting receiver, e.g., noise introduced by the received antenna, loss due to the converting RF-to-DC circuit, and so on [34,35]. Additionally, to realize the power-splitting protocol, each SWIPT-enabled receiver needs to be equipped with a power splitter to split the received power into two parts. The first part is sent to the conventional information decoding circuit, and the remaining part is sent to the energy harvesting circuit [35,36].
2.3. Opportunistic Partial Relaying (OPR) Protocol
In this paper, the opportunistic partial relaying (OPR) protocol is adopted. In particular, only the relay n denoted by R, which has the highest channel gain from S to all relay nodes, is selected to help exchange information between S and D. Other relay nodes, as a result, keep silent in order to save energy consumption and avoid creating co-channel interference.
| (4) |
Compared with the scenario where all relays participate in the transmission, our adopted protocol is simpler since it does not require perfect channel state information (CSI) of all nodes of the networks at the destination and perfect synchronization among relays [37,38,39]. To be more precise, the adopted OPR protocol can be employed as follows. Each relay is equipped with a timer, and the value of the timer is set inversely with the channel gain from S to relay. Thus, the best relay is the one having the smallest timer. When the timer ends, the best relay forwards the source’s signal to the destination. Other relays sense the availability of the medium and keep silent once the medium is occupied.
2.4. Information Transmission
The whole transmission takes place in two phases. In the first phase, source S broadcasts its signals to all relay nodes. Here, we assume that the direct channel between S and D does not exist due to the long transmission distance and deep fades; thus, destination D does not receive the broadcast signal from S. Although all relays are received signals sent by S, only relay R is selected to assist the transmission from S to D. The criteria for selecting R is given in Section 2.3. At relay R, parts of the incoming signals are sent to the information decoder to decode the information sent by S and are given as
| (5) |
where is the additive white Gaussian noise (AWGN) at relay R, which follows a complex Gaussian distribution with zero mean and variance, ; is the transmitted signal of S and ; is the expectation operator; and is the transmit power of S and is defined in the sequel. The remaining part of the incoming signals from S is put into the energy harvested receiver. The amount of harvested energy denoted by are then formulated as
| (6) |
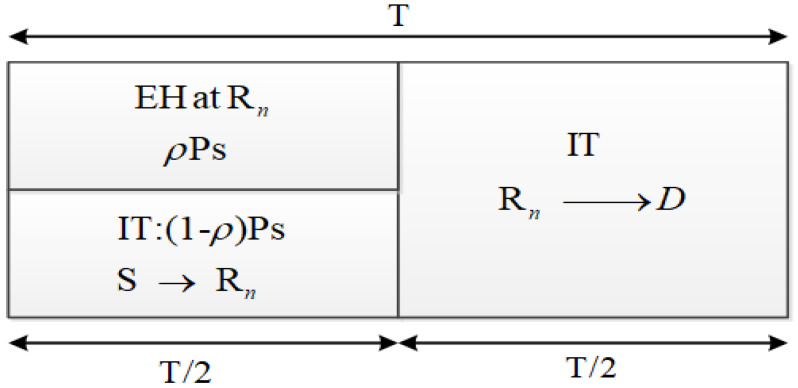
where is the energy conversion coefficient [34,40]; the factor implies that the energy harvesting only takes place in half of the whole transmission procedure. At the end of the first phase, relay R decodes the information sent by S and forwards the re-encoded version to the destination D in the second phase. The whole transmission procedure is shown in Figure 2. The received signals at D is then formulated as
| (7) |
where is the AWGN noise at D with zero mean and variance; is the transmitted signals of the relay R with , and is the transmit power of R and is defined in Section 2.5. It is noted that the received signal at and D in Equations (5) and (7) is a function of the large-scale path loss via the channel coefficient and , respectively. The signal-to-noise ratios at R and D are then formulated as follows:
| (8) |
Figure 2.
Energy harvesting (EH) and information transmission (IT) processes. EH takes place only in the first half of the transmission duration, while IT takes place during the whole transmission duration.
2.5. Transmit Power at Source and Relay Nodes
In the underlay cognitive radio networks, all secondary transmitters, i.e., the source node S and all relay R, have to adjust their transmit power to strictly satisfy the interference power threshold denoted by (in Watt) on the primary networks, i.e., the primary node P. As a result, the transmit power of S is then given as ([15], Equation (5))
| (9) |
Regarding the transmit power of R, we have
| (10) |
Additionally, the transmit power of the relay is also constrained by the amount of the harvested energy in the first phase and is formulated as ([22], Equation (2))
| (11) |
As a consequence, can be rewritten as follows
| (12) |
where is obtained by substituting in (9).
2.6. End-to-End Signal-to-Noise Ratios at D
Since the decode and forward (DF) protocol is employed, the e2e SNRs is then computed as
| (13) |
where ; is held by substituting and in (9) and (12) into (8).
Through direct inspection (13), we observe that the e2e SNR of the considered system is more challenging than other work described in the literature. More precisely, the SNR is the composite of two minimum functions instead of only one. Additionally, the random variables inside these minimum functions are fully correlated as well. As a result, the proposed mathematical framework is novel and more complicated than others.
3. Outage Probability (OP) Analysis
In this section, we investigate one of the most important metrics of a wireless communications system, namely, the outage probability which measures the quality-of-service of the whole network. The OP referrs to the probability that the e2e SNRs at D is below a predefined threshold. Mathematically speaking, it is formulated as follows ([12], Equation (23)):
| (14) |
where , and is the targeted rate [in bps/Hz]. In order to compute OP in (14), we first derive Lemma 1 as follows:
Lemma 1.
Given independent and identically distributed (i.i.d.) exponential random variables (RVs) with parameters Ω denoted by . The CDF and PDF of the maximal RV denoted by are given as follows:
(15) where is the binomial coefficient.
Proof.
Let us begin with the definition of the CDF as follows:
(16) where is held owing to the independence property between RVs; is attained by yielding the CDF of ; and is achieved with the help of the binomial theorem. Taking the first-order derivative of the CDF with respect to x, we attain the PDF as follows:
(17) We close the proof here. □
Next, the OP in (14) is rewritten as follows:
| (18) |
where is attained by substituting (13) into (14), in (18) can be calculated as follows:
| (19) |
in (19) can be split into two probabilities, i.e., and , as follows:
| (20) |
where is evaluated as
| (21) |
Looking at (21), to compute , we first compute as follows:
| (22) |
where is achieved by utilizing Lemma 1. Next, is calculated as
| (23) |
From (22) and (23), in (21) is then computed as
| (24) |
where . Having obtained the , we now move to . Let us first rewrite as
| (25) |
Here, is held by employing the results of (22). Having and in hand, in (20) is then computed as
| (26) |
After obtaining , we now compute in (19) as follows:
| (27) |
where is held with the help of Lemma 1. By employing integration by parts, is evaluated as
| (28) |
By changing variable , we obtain ; is the outcome of ([41], 3.462.17), , and is the incomplete gamma function.
Next, substituting (28) into (27), can be recomputed as
| (29) |
Investigating (29), we observe that , unfortunately, is not able to be computed in closed-form expression due to the fact that the upper limit of the integration does not approach infinity as well as the generality of the incomplete Gamma function. It, however, is effortlessly computed by employing a numerical method with the help of several commercial software such as Matlab, Python, and Mathematica. Moreover, contrary to , can be evaluated in the closed-form expression by deploying the integration by parts and the assistance of ([41], 3.462.17) as follows:
| (30) |
Finally, substituting (26) and (29) into (19), OP defined in (14) is computed as
| (31) |
4. Simulation Results
In this section, computer-based simulation results are given to verify the correctness of the derived mathematical framework and to discover the behaviors of OP with respect to several essential system parameters, namely, the transmit power, the number of relays, the power splitting ratio, and so forth. In particular, the Monte Carlo method is utilized, and the number of realizations is to avoid fluctuation due to insufficient samples. Unless otherwise stated, the following parameters are applied: , , = 0.5, = 5 dB, and = 0.5 bps/Hz. All nodes are located on the two-dimensional plane where the source is fixed at the origin, i.e., (0, 0), the positions of other nodes, i.e., relay , destination D, and primary P, are (1, 0), (1.5, 0), and (1, 1), respectively.
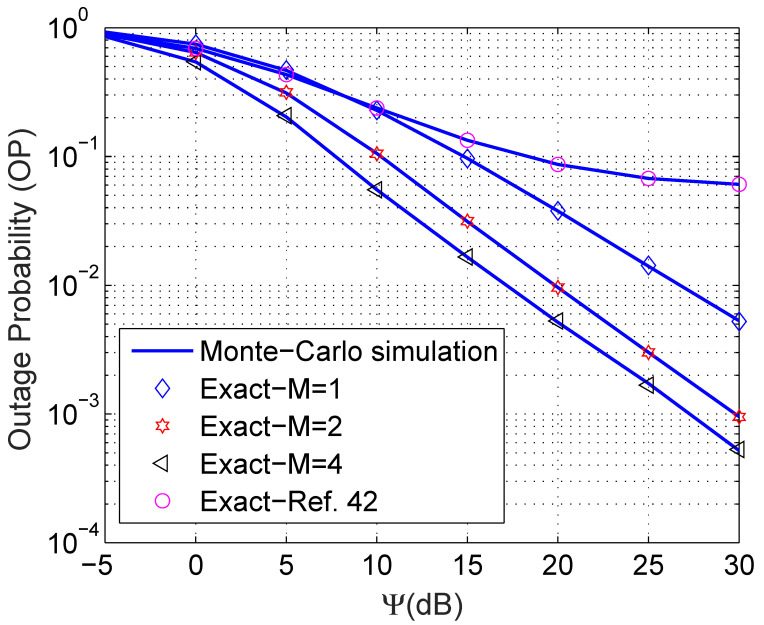
Figure 3 shows the impact of the interference power over noise variance on the performance of the OP. The proposed mathematical framework absolutely matches the Monte Carlo simulations. Moreover, we observe that increasing the number of relays M obviously improves the OP. To be more precise, with dB, the OP of is approximately , while the OP of is better and is around . Additionally, the proposed framework outperforms work presented in the literature [42]. In particular, the OP of Ref. [42] only achieves around 0.06 when , while the OP of the proposed scheme with is already approximately 0.005. In addition, the pace of improvement when is small and large is different. In particular, the OP dramatically improves when is small and a fair improvement is experienced when is large. The main reason behind this phenomenon is that when is sufficiently large, the outage event almost disappears, as a consequence, a slight enhancement is observed.
Figure 3.
Outage probability versus (dB) with , = 0.5, and = 0.5 bps/Hz.
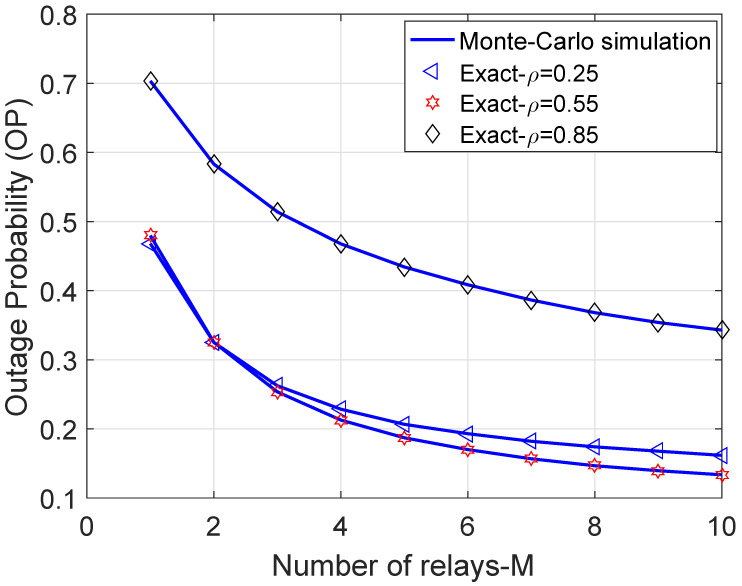
Figure 4 shows the outage probability versus the number of relays M. As mentioned in Figure 3, scaling up M certainly ameliorates the OP. Nevertheless, the benefits of increasing M are not the same when M is limited versus M as large. More precisely, when , OP declines exponentially, while when , OP fairly decreases. Figure 4 confirms again the accuracy of the derived mathematical framework.
Figure 4.
Outage probability versus number of relays-M with = 0.8, = 0.5 bps/Hz, and = 5 dB.
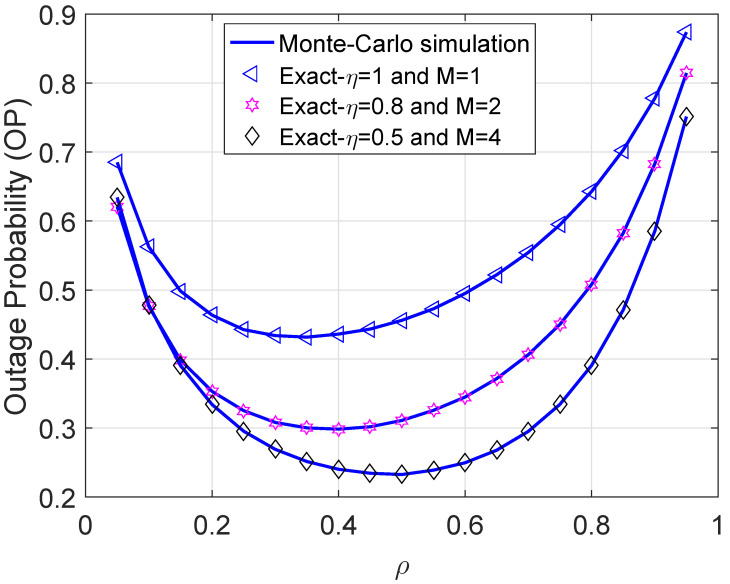
We investigate the behavior of OP regarding the power splitting ratio in Figure 5. We see that OP first plunges with after reaching its minimum, OP then turns and constantly rises when moves from 0 to 1. When is small, the amount of harvested energy at R is limited, which leads to lower SNR thereby degrading system performance. When is close to 1, on the other hand, the received signals being added into the information decoder of R are limited too, hence, scaling up the OP. In addition, the curve with is not always superior to the others for all values of . In particular, when is small, the curve with is better than the case of . However, in general, increasing the number of relays can overcome the constraint of the hardware limitation. Furthermore, the optimal value of denoted by where OP achieves its minimum can be straightforwardly derived from this figure. For example, the of curve with and is approximately 0.5, while the of the curve with and is just below 0.4.
Figure 5.
Outage probability versus with = 0.5 bps/Hz and = 5 dB.
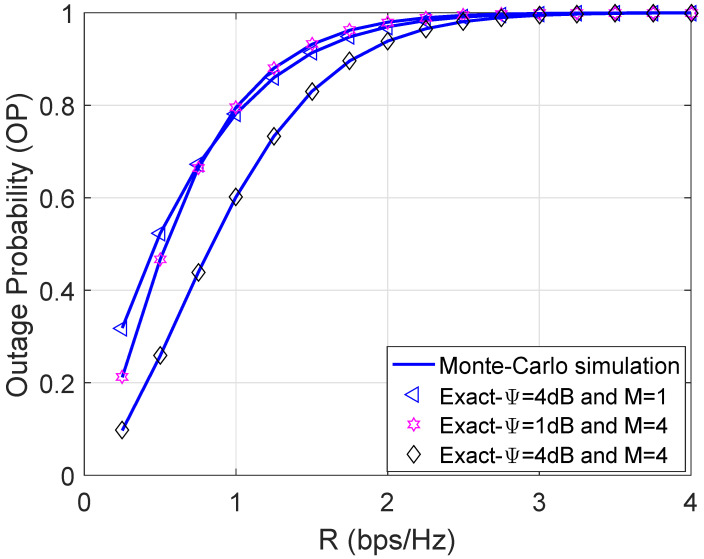
Figure 6 stretches the OP versus the targeted rate . There is no doubt that the larger the the higher the OP. We can directly explain this trend by yielding the definition of the OP. Interestingly, the curve with and dB does not consistently outperform case and dB. This means that we can ameliorate the system performance either by increasing the number of relay nodes or scaling up the transmit power.
Figure 6.
Outage probability versus with and = 0.5.
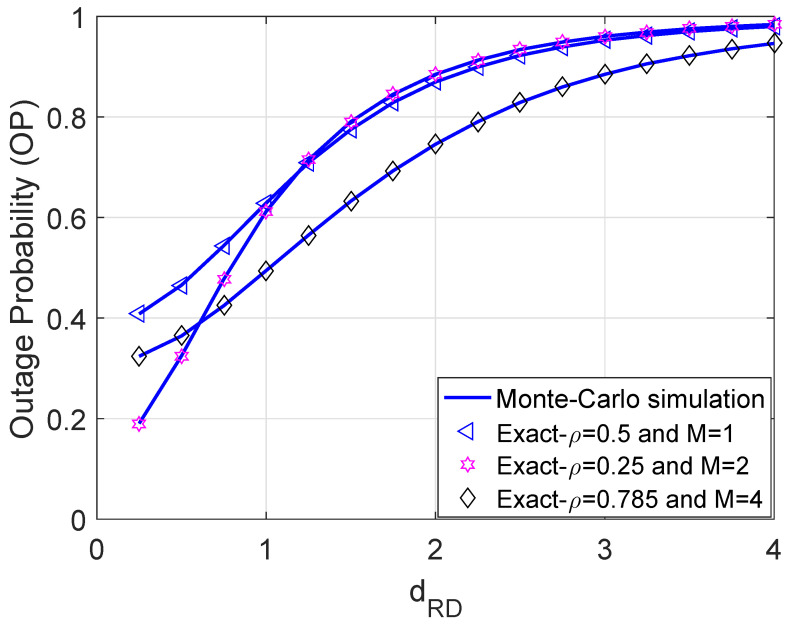
Figure 7 addresses the impact of the mobility of the destination on the performance of the considered networks. To be more precise, destination D is moving from R to far away. The further the is, the worse the OP. The rationale behind this trend is that increasing is directly proportional to the large-scale path loss; thus, this deteriorates the channel gain and increases the OP. Moreover, the OP performance can be improved significantly by properly optimizing the power splitting ratio. In particular, we observe that the performance of curves with and is more or less equivalent unless the approaches zero.
Figure 7.
Outage probability versus with = 0.8, = 0.5 bps/Hz, and = 5 dB.
5. Conclusions
The outage performance of the SWIPT-based cognitive radio networks was addressed in this paper. In particular, all relay nodes were equipped not only with a conventional information decoder but also an energy harvester, so that they were able to concurrently receive information and harvest the energy from the incoming signals. Additionally, the opportunistic relaying was taken into account to both ameliorate the outage probability and save the consumed resources. The numerical results illustrated that either increasing the number of relay nodes or raising the transmit power was beneficial for the considered networks. The paper can be extended in several directions: (i) We can replace the fixed relay by high mobility unmanned aerial vehicles (UAVs) devices [43,44] or employ advanced meta material technology to enhance energy efficiency, i.e., the reconfigurable intelligent surfaces (RIS) [45,46]; (ii) Diversity combining at the destination, i.e., maximal ratio combining or selection combining, would also be considered a simple solution to raise the system’s diversity gain [47,48]; (iii) Consideration of the networks could extend to investigating the security aspect as well [49,50]; and (iv) Two-way relaying or full-duplex relaying would be a feasible and interesting extension as well [51,52].
Author Contributions
The main contributions of P.T.T., V.-D.P., and T.N.N. were to execute performance evaluations by theoretical analysis and simulations, while B.V.M., M.V., and P.F. advised V.-D.P. and T.N.N. in discussing, creating, and evaluating performance. The mathematical framework and numerical results were revised by L.-T.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Industrial University of Ho Chi Minh City (IUH), Vietnam, under grant No. 131/HD-DHCN and the Ministry of Education, Youth and Sports of the Czech Republic under the grant SP2021/25 and e-INFRA CZ (ID:90140).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Footnotes
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Yu H., Zikria Y.B. Cognitive Radio Networks for Internet of Things and Wireless Sensor Networks. Sensors. 2020;20:5288. doi: 10.3390/s20185288. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Bilibashi D., Vitucci E.M., Degli-Esposti V., Giorgetti A. An Energy-Efficient Unselfish Spectrum Leasing Scheme for Cognitive Radio Networks. Sensors. 2020;20:6161. doi: 10.3390/s20216161. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 3.Goldsmith A., Jafar S.A., Maric I., Srinivasa S. Breaking Spectrum Gridlock With Cognitive Radios: An Information Theoretic Perspective. Proc. IEEE. 2009;97:894–914. doi: 10.1109/JPROC.2009.2015717. [DOI] [Google Scholar]
- 4.Duy T.T., Thanh T.L., Quoc Bao V.N. A hybrid spectrum sharing approach in cognitive radio networks; Proceedings of the 2014 International Conference on Computing, Management and Telecommunications (ComManTel); Da Nang, Vietnam. 27–29 April 2014; pp. 19–23. [DOI] [Google Scholar]
- 5.Gebremichail A.A., Beard C. Multi-hop relay selection based on fade durations; Proceedings of the 2015 Wireless Telecommunications Symposium (WTS); New York, NY, USA. 15–17 April 2015; pp. 1–6. [DOI] [Google Scholar]
- 6.Tin P.T., Nguyen T.N., Tran D.H., Voznak M., Phan V.D., Chatzinotas S. Performance Enhancement for Full-Duplex Relaying with Time-Switching-Based SWIPT in Wireless Sensors Networks. Sensors. 2021;21:3874. doi: 10.3390/s21113847. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Tin P.T., Phan V.D., Ha D.H., Nguyen T.N., Tran M., Voznak M. Non-linear energy harvesting based power splitting relaying in full-duplex AF and DF relaying networks: System performance analysis. Proc. Est. Acad. Sci. 2020;69:368–381. [Google Scholar]
- 8.Xu D., Zhu H. Sum-Rate Maximization of Wireless Powered Primary Users for Cooperative CRNs: NOMA or TDMA at Cognitive Users? IEEE Trans. Commun. 2021;69:4862–4876. doi: 10.1109/TCOMM.2021.3073952. [DOI] [Google Scholar]
- 9.Arzykulov S., Nauryzbayev G., Celik A., Eltawil A.M. Hardware and Interference Limited Cooperative CR-NOMA Networks Under Imperfect SIC and CSI. IEEE Open J. Commun. Soc. 2021;2:1473–1485. doi: 10.1109/OJCOMS.2021.3091606. [DOI] [Google Scholar]
- 10.Tu L.T., Bradai A., Pousset Y., Aravanis A.I. Energy Efficiency Analysis of LoRa Networks. IEEE Wirel. Commun. Lett. 2021;10:1881–1885. doi: 10.1109/LWC.2021.3084996. [DOI] [Google Scholar]
- 11.Rajaram A., Khan R., Tharranetharan S., Jayakody D.N.K., Dinis R., Panic S. Novel SWIPT Schemes for 5G Wireless Networks. Sensors. 2019;19:1169. doi: 10.3390/s19051169. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Ha D.H., Nguyen T.N., Tran M.H.Q., Li X., Tran P.T., Voznak M. Security and Reliability Analysis of a Two-Way Half-Duplex Wireless Relaying Network Using Partial Relay Selection and Hybrid TPSR Energy Harvesting at Relay Nodes. IEEE Access. 2020;8:187165–187181. doi: 10.1109/ACCESS.2020.3030794. [DOI] [Google Scholar]
- 13.Nguyen T.N., Tran P.T., Voznák M. Wireless energy harvesting meets receiver diversity: A successful approach for two-way half-duplex relay networks over block Rayleigh fading channel. Comput. Netw. 2020;172:107176. doi: 10.1016/j.comnet.2020.107176. [DOI] [Google Scholar]
- 14.Arzykulov S., Nauryzbayev G., Tsiftsis T.A., Maham B. Performance Analysis of Underlay Cognitive Radio Nonorthogonal Multiple Access Networks. IEEE Trans. Veh. Technol. 2019;68:9318–9322. doi: 10.1109/TVT.2019.2930553. [DOI] [Google Scholar]
- 15.Tran Tin P., The Hung D., Nguyen T.N., Duy T.T., Voznak M. Secrecy Performance Enhancement for Underlay Cognitive Radio Networks Employing Cooperative Multi-Hop Transmission with and without Presence of Hardware Impairments. Entropy. 2019;21:217. doi: 10.3390/e21020217. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Lee D., So J. Feedback Bits Allocation for Guaranteed Bit Rate Services in Cooperative Cognitive Radio Networks. Sensors. 2020;20:469. doi: 10.3390/s20020469. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Elsaadany M., Hamouda W. Performance Analysis of Non-Orthogonal AF Relaying in Cognitive Radio Networks. IEEE Wirel. Commun. Lett. 2015;4:373–376. doi: 10.1109/LWC.2015.2421910. [DOI] [Google Scholar]
- 18.Lee H., Cho D.H. Capacity Improvement and Analysis of VoIP Service in a Cognitive Radio System. IEEE Trans. Veh. Technol. 2010;59:1646–1651. doi: 10.1109/TVT.2009.2039503. [DOI] [Google Scholar]
- 19.Liu P., Qi W., Yuan E., Wei L., Zhao Y. Full-Duplex Cooperative Sensing for Spectrum-Heterogeneous Cognitive Radio Networks. Sensors. 2017;17:1773. doi: 10.3390/s17081773. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Thanh T.L., Quoc Bao V.N., Duy T.T. Capacity analysis of multi-hop decode-and-forward over Rician fading channels; Proceedings of the 2014 International Conference on Computing, Management and Telecommunications (ComManTel); Da Nang, Vietnam. 27–29 April 2014; pp. 134–139. [DOI] [Google Scholar]
- 21.Amjad M., Chughtai O., Naeem M., Ejaz W. SWIPT-Assisted Energy Efficiency Optimization in 5G/B5G Cooperative IoT Network. Energies. 2021;14:2515. doi: 10.3390/en14092515. [DOI] [Google Scholar]
- 22.Nguyen T.N., Tran M., Nguyen T.L., Ha D.H., Voznak M. Performance Analysis of a User Selection Protocol in Cooperative Networks with Power Splitting Protocol-Based Energy Harvesting Over Nakagami-m/Rayleigh Channels. Electronics. 2019;8:448. doi: 10.3390/electronics8040448. [DOI] [Google Scholar]
- 23.Bariah L., Muhaidat S., Al-Dweik A. Error Probability Analysis of NOMA-Based Relay Networks With SWIPT. IEEE Commun. Lett. 2019;23:1223–1226. doi: 10.1109/LCOMM.2019.2897770. [DOI] [Google Scholar]
- 24.Lu Y., Mow W.H. SER Analysis for SWIPT-Enabled Differential Decode-and-Forward Relay Networks. IEEE Trans. Green Commun. Netw. 2021;5:348–361. doi: 10.1109/TGCN.2020.3037818. [DOI] [Google Scholar]
- 25.Mohjazi L., Muhaidat S., Dianati M., Al-Qutayri M. Performance Analysis of SWIPT Relay Networks With Noncoherent Modulation. IEEE Trans. Green Commun. Netw. 2018;2:1072–1086. doi: 10.1109/TGCN.2018.2856363. [DOI] [Google Scholar]
- 26.Tin P.T., Dinh B.H., Nguyen T.N., Ha D.H., Trang T.T. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry. 2020;12:106. doi: 10.3390/sym12010106. [DOI] [Google Scholar]
- 27.Saber M.J., Keshavarz A., Mazloum J., Sazdar A.M., Piran M.J. Physical-Layer Security Analysis of Mixed SIMO SWIPT RF and FSO Fixed-Gain Relaying Systems. IEEE Syst. J. 2019;13:2851–2858. doi: 10.1109/JSYST.2019.2902309. [DOI] [Google Scholar]
- 28.Thanh T.L., Di Renzo M., Coon J.P. MIMO cellular networks with Simultaneous Wireless Information and Power Transfer; Proceedings of the 2016 IEEE 17th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC); Edinburgh, UK. 3–6 July 2016; pp. 1–5. [DOI] [Google Scholar]
- 29.Tu L.T., Di Renzo M. Analysis of millimeter wave cellular networks with simultaneous wireless information and power transfer; Proceedings of the 2017 International Conference on Recent Advances in Signal Processing, Telecommunications Computing (SigTelCom); Da Nang, Vietnam. 9–11 January 2017; pp. 39–43. [DOI] [Google Scholar]
- 30.Prathima A., Gurjar D.S., Nguyen H.H., Bhardwaj A. Performance Analysis and Optimization of Bidirectional Overlay Cognitive Radio Networks With Hybrid-SWIPT. IEEE Trans. Veh. Technol. 2020;69:13467–13481. doi: 10.1109/TVT.2020.3029067. [DOI] [Google Scholar]
- 31.Hoang An N., Tran M., Nguyen T.N., Ha D.H. Physical Layer Security in a Hybrid TPSR Two-Way Half-Duplex Relaying Network over a Rayleigh Fading Channel: Outage and Intercept Probability Analysis. Electronics. 2020;9:428. doi: 10.3390/electronics9030428. [DOI] [Google Scholar]
- 32.Wu F., Xiao L., Yang D., Cuthbert L., Liu X. Transceiver Design and Power Allocation for SWIPT in MIMO Cognitive Radio Systems. Symmetry. 2018;10:647. doi: 10.3390/sym10110647. [DOI] [Google Scholar]
- 33.Tang K., Liao S. Outage Analysis of Relay-Assisted NOMA in Cooperative Cognitive Radio Networks with SWIPT. Information. 2020;11:500. doi: 10.3390/info11110500. [DOI] [Google Scholar]
- 34.Song C., Huang Y., Zhou J., Zhang J., Yuan S., Carter P. A High-Efficiency Broadband Rectenna for Ambient Wireless Energy Harvesting. IEEE Trans. Antennas Propag. 2015;63:3486–3495. doi: 10.1109/TAP.2015.2431719. [DOI] [Google Scholar]
- 35.Jiang Z., Leach M., Wang Z., Lim E.G., Huang Y. Modelling and Performance Analysis of an Efficient Compact Integrated Rectifier-Receiver for SWIPT; Proceedings of the 2020 IEEE MTT-S International Microwave Workshop Series on Advanced Materials and Processes for RF and THz Applications (IMWS-AMP); Suzhou, China. 29–31 July 2020; pp. 1–3. [DOI] [Google Scholar]
- 36.Tu L.T. Ph.D. Thesis. Thèse de Doctorat Dirigée par Di Renzo, Marco Réseaux, Information et Communications Université Paris-Saclay (ComUE); Paris, France: 2018. New Analytical Methods for the Analysis and Optimization of Energy-Efficient Cellular Networks by Using Stochastic Geometry. [Google Scholar]
- 37.Liu K.J.R., Sadek A.K., Su W., Kwasinski A. Cooperative Communications and Networking. Cambridge University Press; New York, NY, USA: 2009. [Google Scholar]
- 38.Hong Y.W., Huang W.J., Kuo C.C. Cooperative Communications and Networking: Technologies and System Design. Springer; Berlin/Heidelberg, Germany: 2010. [Google Scholar]
- 39.Thanh T.L., Bao V.N.Q., An B. On the performance of outage probability in underlay cognitive radio with imperfect CSI; Proceedings of the 2013 International Conference on Advanced Technologies for Communications (ATC 2013); Ho Chi Minh City, Vietnam. 16–18 October 2013; pp. 125–130. [DOI] [Google Scholar]
- 40.Le T., Mayaram K., Fiez T. Efficient Far-Field Radio Frequency Energy Harvesting for Passively Powered Sensor Networks. IEEE J. Solid-State Circuits. 2008;43:1287–1302. doi: 10.1109/JSSC.2008.920318. [DOI] [Google Scholar]
- 41.Gradshteyn I.S., Ryzhik I.M. Table of Integrals, Series, and Products. Academic Press; Cambridge, MA, USA: 2014. [Google Scholar]
- 42.Son P., Trung Duy T. Performance analysis of Underlay Cooperative Cognitive Full-duplex Networks with Energy-Harvesting Relay. Comput. Commun. 2018;122:9–19. doi: 10.1016/j.comcom.2018.03.003. [DOI] [Google Scholar]
- 43.Saraereh O.A., Alsaraira A., Khan I., Uthansakul P. Performance Evaluation of UAV-Enabled LoRa Networks for Disaster Management Applications. Sensors. 2020;20:2396. doi: 10.3390/s20082396. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 44.Tatar Mamaghani M., Hong Y. On the Performance of Low-Altitude UAV-Enabled Secure AF Relaying With Cooperative Jamming and SWIPT. IEEE Access. 2019;7:153060–153073. doi: 10.1109/ACCESS.2019.2948384. [DOI] [Google Scholar]
- 45.Van Chien T., Tu L.T., Chatzinotas S., Ottersten B. Coverage Probability and Ergodic Capacity of Intelligent Reflecting Surface-Enhanced Communication Systems. IEEE Commun. Lett. 2021;25:69–73. doi: 10.1109/LCOMM.2020.3023759. [DOI] [Google Scholar]
- 46.Chien T.V., Papazafeiropoulos A.K., Tu L., Chopra R., Chatzinotas S., Ottersten B. Outage Probability Analysis of IRS-Assisted Systems Under Spatially Correlated Channels. IEEE Wirel. Commun. Lett. 2021;10:1815–1819. doi: 10.1109/LWC.2021.3082409. [DOI] [Google Scholar]
- 47.Cheng W., Wang X., Ma T., Wang G. On the Performance Analysis of Switched Diversity Combining Receivers over Fisher–Snedecor Composite Fading Channels. Sensors. 2021;21:3014. doi: 10.3390/s21093014. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 48.Thanh T.L., Renzo M., Coon J. System-level analysis of receiver diversity in SWIPT-enabled cellular networks. J. Commun. Netw. 2016;18:926–937. [Google Scholar]
- 49.Lei W., Zhan M. Beamforming and Antenna Grouping Design for the Multi-Antenna Relay with Energy Harvesting to Improve Secrecy Rate. Information. 2016;7:38. doi: 10.3390/info7030038. [DOI] [Google Scholar]
- 50.Deng Z., Li Q., Zhang Q., Yang L., Qin J. Beamforming Design for Physical Layer Security in a Two-Way Cognitive Radio IoT Network With SWIPT. IEEE Internet Things J. 2019;6:10786–10798. doi: 10.1109/JIOT.2019.2941873. [DOI] [Google Scholar]
- 51.Peng C., Li F., Liu H. Wireless Energy Harvesting Two-Way Relay Networks with Hardware Impairments. Sensors. 2017;17:2604. doi: 10.3390/s17112604. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 52.Srivantana T., Maichalernnukul K. Two-Way Multi-Antenna Relaying with Simultaneous Wireless Information and Power Transfer. Symmetry. 2017;9:42. doi: 10.3390/sym9030042. [DOI] [Google Scholar]