Significance
Observing the states of a network is fundamental to our ability to explore and control the dynamics of complex natural, social, and technological systems. The problem of determining whether the system is observable has been addressed by network control researchers over the past decade. Progress on the further problem of actually designing and implementing efficient algorithms to infer the states from limited measurements has been hampered by the high dimensionality of large-scale networks. Noting that often only a small number of state variables in a network are essential for control, intervention, and monitoring purposes, this work develops a graph-based theory and highly scalable methods that achieve accurate estimation of target variables of network systems with minimal sensing and computational resources.
Keywords: network dynamics, observability, network control, complex networks
Abstract
The quantitative understanding and precise control of complex dynamical systems can only be achieved by observing their internal states via measurement and/or estimation. In large-scale dynamical networks, it is often difficult or physically impossible to have enough sensor nodes to make the system fully observable. Even if the system is in principle observable, high dimensionality poses fundamental limits on the computational tractability and performance of a full-state observer. To overcome the curse of dimensionality, we instead require the system to be functionally observable, meaning that a targeted subset of state variables can be reconstructed from the available measurements. Here, we develop a graph-based theory of functional observability, which leads to highly scalable algorithms to 1) determine the minimal set of required sensors and 2) design the corresponding state observer of minimum order. Compared with the full-state observer, the proposed functional observer achieves the same estimation quality with substantially less sensing and fewer computational resources, making it suitable for large-scale networks. We apply the proposed methods to the detection of cyberattacks in power grids from limited phase measurement data and the inference of the prevalence rate of infection during an epidemic under limited testing conditions. The applications demonstrate that the functional observer can significantly scale up our ability to explore otherwise inaccessible dynamical processes on complex networks.
Large-scale complex systems, including power grids, neuronal networks, and food webs, are often represented as sets of interconnected dynamical systems and referred to as dynamical networks. Understanding the properties and control principles of dynamical networks allows for the development of intervention strategies that can shape the behavior of these systems to achieve the desired functionality. As formalized by Wiener (1), the fundamental mechanism enabling precise control of a dynamical system is feedback, which involves sensors, signals, and actuators in a closed loop. A sensor provides immediate measurements of a particular variable of the system. As the dynamical network grows large, it becomes prohibitive to implement a sensor for each state variable, be it due to cost or physical constraints. For instance, our ability to measure each of the tens of billions of neurons present in a human brain is physically limited. Likewise, infrastructure and operation costs may impede the placing of sensors in every node of a large technological system. Therefore, the indirect estimation of the unmeasured states is essential for the control of large-scale dynamical networks.
The property of a dynamical system that enables the reconstruction of the entire system state from its control inputs and sensor measurements is called observability (2). In particular, observability constitutes the necessary and sufficient condition that guarantees the existence and enables the design of full-state estimators—such as Luenberger observers (3) and Kalman filters (4). Despite the success of state observers in uncountable engineering applications, high dimensionality is still an obstacle to the direct use of these methods in large-scale dynamical networks (5–7). This calls for different approaches and novel techniques (8–14) to overcome the lack of scalability of existing methods. Based on a graph-theoretic approach to controllability (15), Liu et al. (9) presented an efficient method that, by duality, can be used to determine a minimum set of sensor nodes required to guarantee the observability of complex networks. However, even if a minimum set of sensors is used, the state observer will have the same dimension as the entire network, making its design and implementation computationally expensive in large-scale systems. Moreover, a minimum set of sensor nodes does not guarantee good quality for the full-state reconstruction in higher-order systems (16–20).
For many real-world problems, estimating the entire state vector of a high-dimensional system is not necessary or even desirable (6). It is often sufficient to focus on a particular subset of nodes of interest. For instance, in decentralized control strategies applied to network systems, each controller only requires feedback signals from a fraction of nodes in the neighborhood determined by the corresponding controlled area (21, 22). This is also true for the detection and monitoring of unforeseen failures and cyberattacks, which find several applications in supply networks (23), power grids (24, 25), and autonomous vehicle coordination (26). Similarly, in biomedical applications, estimation (diagnosis) and control (intervention) often require monitoring of a reduced set of variables in the respective networks (27, 28). Examples include regulatory network states associated with cancer (10) and brain network states associated with Parkinson’s disease (29) and epilepsy (30).
These practical problems motivate the concept of functional observability (31, 32), which characterizes the existence of a functional observer capable of reconstructing a targeted subset of state variables from a limited number of sensors—even when the network is not completely observable. Functional observability can be related to the concept of target controllability (33–37), which establishes the conditions for the existence of a controller capable of steering a targeted subset of state variables and has been applied to problems of drug target identification (38). However, despite the duality between (complete) controllability and observability (2), such duality does not hold between target controllability and functional observability. This is the case because as we show, the state estimation of a subset of variables requires a stronger condition than the dual condition to the control of a subset of variables. Even though the design of functional observers is a problem that dates back to the 1970s (39–41), previous studies on functional observability (31, 32, 42) were based on numerical rank-based conditions, without explicitly taking advantage of the network topology, and thus do not lead to scalable algorithms applicable to large-scale networks.
In this paper, we develop a graph-theoretic characterization of functional observability and the associated algorithms for sensor placement and observer design, making it possible to accurately estimate the target states of a large-scale dynamical network using minimal sensing and computational resources. The contributions of this work are threefold. First, we propose the concept of structural functional observability, which can be seen as a generalization of Lin’s structural observability (15). This allows us to rigorously establish graph-theoretic conditions for functional observability equivalent to the original rank-based conditions (32). Second, based on the proposed theory, two highly scalable algorithms are developed to solve the sensor placement and observer design problems. The first algorithm determines a minimal set of sensors placed on a dynamical network to ensure functional observability with respect to a given set of target nodes. After the sensor placement is decided, the second algorithm designs a minimum-order functional observer whose output converges asymptotically to the target states, achieving accurate estimation. Third, we demonstrate the advantages of the proposed methods with two concrete applications: the cybersecurity of power grids and the monitoring of epidemic spreading. In power grids, we show that the proposed functional observers can be implemented as active detectors of cyberattacks, effectively providing state estimates that allow for cross-validation among different information sources and the detection of fake measurement data in real time. In epidemics such as the COVID-19 pandemic, we demonstrate that the proposed functional observer can infer the fraction of infected population in areas where testing is limited from the data collected in areas with sufficient testing; moreover, our algorithms can also guide the optimal allocation of limited testing resources.
Results
Complete and Functional Observability of Dynamical Systems.
A general linear dynamical system can be written as
| [1] |
where is the vector of state variables, accounts for the control inputs or environmental influences, and represents the direct measurement from available sensors in the system. Matrix A, which is referred to as the system matrix, encompasses the nodal dynamics and network interactions—and can thus correspond to an adjacency matrix, a Laplacian matrix, or more generally, a Jacobian matrix of the system. The system is completely observable if it is possible to reconstruct the entire state trajectory from the input vector and measurement vector . Complete observability is guaranteed when the observability matrix
| [2] |
has full rank (43) [i.e., ]. Under this rank condition, there exist straightforward methods to design a full-state observer. Such observer is an auxiliary dynamical system whose states converge asymptotically to those of the original system (Eq. 1) when taking y and u as inputs, providing an estimation of the state vector . Since the direct measurement already contains q linear combinations of state , only state variables are required to be reconstructed, which can be accomplished by a reduced-order state observer that we refer to as the Luenberger observer (3) (Materials and Methods has details).
In practice, it is often unnecessary to estimate the entire state vector x. Instead, only a lower-dimensional function is of interest, where r can be much smaller than n. Given the desirable F, functional observability characterizes the system property that enables the reconstruction of from and (31). The system is functionally observable if and only if (32, 44)
| [3] |
that is, if and only if the row space is a subspace of the observable space . Clearly, complete observability is a special case of functional observability for F = I. However, the condition in Eq. 3 only guarantees the theoretical existence of a functional observer (32). It does not readily lead to an algorithm to design a functional observer (31, 44), for which two additional conditions must be satisfied (40):
| [4] |
| [5] |
where and Eq. 5 must hold for every eigenvalue λ of A. If a triple (A, C, F) satisfies Eq. 3, then there exists some matrix F0 whose row space contains that of F [i.e., ] that satisfies Eqs. 4 and 5 for the triple (31). A functional observer of order can be designed systematically after such a matrix F0 is determined (Materials and Methods). Finding a matrix F0 with the minimum number of rows r0 satisfying these conditions is then a crucial problem since the functional observer order is directly related to the computational costs of its design and real-time simulation (as demonstrated below).
Structural Functional Observability.
The rank-based conditions (Eqs. 3–5) are not numerically stable and computationally efficient for the design of functional observers for large-scale systems. Here, we adopt a graph-theoretic approach that explicitly leverages the network structure of the dynamical system. The system matrix A can be structurally represented as a corresponding inference graph whose nodes are the internal state variables . The links in capture the interaction pattern among state variables: there is a link from xj to xi on the graph if Aij is nonzero. A node xj on graph is a sensor node if for some i, and a node xk is a target node if for some i. The sets of all sensor and target nodes are denoted and , respectively. We assume that each sensor or target is only related to one internal state variable, meaning that each row of C or F has only one nonzero entry. Throughout, the terms nodes and links are used exclusively in connection with inference graphs and are not to be confused with the vertices and edges, which are the corresponding terms used for the network systems. Fig. 1A illustrates the representation of the inference graph and the set of nodes estimated by a minimum-order functional observer for the indicated sensor and target nodes in a 10-dimensional system.
Fig. 1.
Structural functional observability of dynamical systems. (A) System matrix A and corresponding inference graph . The set of state variables is represented by nodes on the graph, where the set of sensor nodes (defined by C) is marked in blue and the set of target nodes (defined by F) is marked in red. In this example, the system is unobservable [], but it is functionally observable [], enabling the design of a functional observer. We show the minimum-order matrix F0 such that satisfies Eqs. 4 and 5. Nonzero elements in F0 determine the minimum set of auxiliary nodes (highlighted in orange) whose states also have to be estimated by a functional observer in order to estimate the state of the target node. The number of rows of F0 is the order of the functional observer: . (B) Example of a system that is observable and hence functionally observable. Since the system is completely observable, a Luenberger observer can be designed. However, while such Luenberger observer has order because it estimates the state of every unmeasured node, a functional observer can estimate the target node x10 with the much smaller order . (C) Minimum sensor set for functional observability. For the same graph and target set as in B, the sensor node x5 is a minimum sensor set required for the functional observability of x10. However, the absence of sensor node x8 increases the functional observer order to . (D) Functional observability in a strongly connected graph. Due to the stronger connectivity, the functional observer order increases to (compared with B) while remaining smaller than the Luenberger observer order . Differences between graphs are indicated by the pink links.
A system given by the triple (A, C, F) is said to be structurally functionally observable if there exists a functionally observable triple , which shares the same structure as (A, C, F). We define that triples (A, C, F) and have the same structure if, according to the representation described above, they share the same inference graph , sensor set , and target set . Thus, structural functional observability is purely determined by the state interaction structure encoded by graph , the sensor node set , and the target node set —which are all independent of the specific numerical entries of (A, C, F). In fact, if a triple (A, C, F) is structurally functionally observable, a system that shares the same structure as (A, C, F) is functionally observable with probability one.
This structural approach allows us to establish a graph-theoretic characterization of functional observability:
A system (A, C, F) is structurally functionally observable if and only if 1) there exists a direct path from every target node to some sensor node and 2) no target node is an element of a minimal subset of nodes with a dilation.
A rigorous proof of this theorem is given in SI Appendix, section 2. This result can be seen as a significant generalization of Lin’s theory of structural controllability and, by duality, of structural observability (15). Note that when F = I (or equivalently, ), our definition of structural functional observability reduces to Lin’s structural observability. The latter states that a pair (A, C) is structurally observable if and only if 1) there exists a direct path from every state node to some sensor node and 2) the corresponding graph has no dilations. More background on structural observability is presented in SI Appendix, section 1. We further illustrate this characterization in Fig. 1A, where the inference graph has no dilations due to the presence of self-links and thus satisfies conditions 2 and 2 for structural functional and complete observability, respectively. However, because node x9 does not have a direct path to a sensor node, condition 1 for structural observability is not satisfied for the pair (A, C). Nevertheless, condition 1 is satisfied for structural functional observability of the triple (A, C, F) since one can identify a path from the target node x10 to a sensor node (x5 or x8), hence rendering (A, C, F) structurally functionally observable.
The above result lays a foundation for the functional observer design in large-scale dynamical networks. To enable the algorithm development, we further investigate two main design problems:
-
1)
How do we select the minimum set of sensor nodes such that a triple (A, C, F) is structurally functionally observable?
-
2)
Given a structurally functionally observable triple (A, C, F), how do we determine the minimum-order matrix F0 such that Eqs. 4 and 5 are satisfied for ? (In other words, what is the minimum set of “auxiliary” state nodes that must be estimated along with the target nodes so that the systematic functional observer design is possible?)
The examples in Fig. 1 B–D illustrate that both questions are intertwined and inherently related to the structure of .
In the following sections, we assume that no target node is an element of a minimal subset of nodes with a dilation. A sufficient condition for this latter assumption is that every target node has a self-link. The importance of including self-links in dynamical networks models, especially for state control and estimation applications, has been thoroughly discussed in the literature (7, 45, 46). Indeed, dilations are not found in a broad range of dynamical networks, including diffusively coupled systems. Our assumptions can be satisfied for applications in networks of coupled oscillators (47–49), power grids (50, 51), neuronal systems (52, 53), combustion networks (18, 54), regulatory networks (55, 56), consensus problems (21), and multigroup epidemiological models (57).
Minimum Sensor Placement for Functional Observability.
According to the theory and assumptions discussed above, the minimal sensor placement problem is to determine a minimum set such that there is a direct path in from every target node to some sensor node. We show that the minimum sensor placement problem can be formulated as a set cover problem. For each candidate sensor node, let denote the set of target nodes that have a direct path to the state node . By this definition, the minimal sensor placement amounts to identifying the minimal sensor set such that the union of the sets for all covers the target set (i.e., ). This is an NP-hard problem (58), to which we provide an approximate but highly scalable solution via Algorithm 1 (Materials and Methods), where a breadth-first search determines for each node and a greedy algorithm solves the set cover problem. Owing to the submodularity of the problem (59), this approximation is guaranteed to be near optimal.
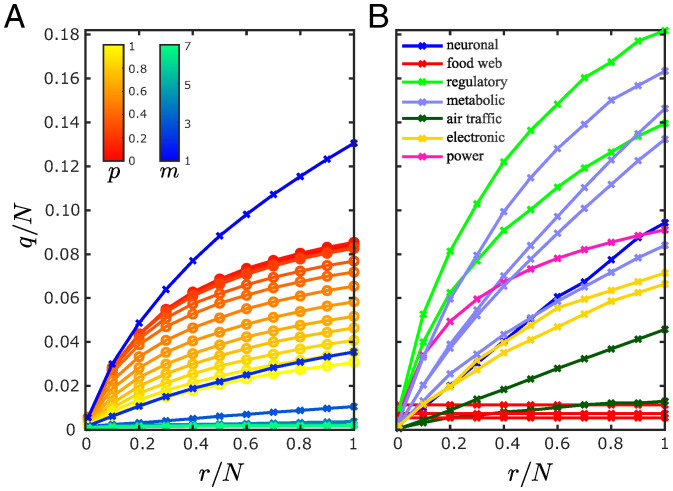
Fig. 2 illustrates the application of Algorithm 1 to randomly generated small-world (SW) and scale-free (SF) networks as well as a selection of real-world networks. As expected, the results show that a smaller number of target nodes tends to require a smaller number of sensor nodes to guarantee the functional observability of a system. Fig. 2A shows, however, that the relation between the minimum set of sensor nodes and the number of target nodes depends on the network structure, where the number of sensor nodes can be substantially smaller if the network connectivity is larger (i.e., higher parameters p and m in SW and SF networks, respectively). Similar conclusions are also noted for the real-world networks shown in Fig. 2B. As r approaches n, the minimum number of sensor nodes tends to the number required for complete observability. For example, in the metabolic networks analyzed, complete observability requires monitoring 8 to 16% of all metabolites, which is consistent with previous findings (11). However, complete observability is often unnecessary for many biomedical applications since the number of biomarkers (e.g., target nodes whose activity is altered by a disease) is usually much smaller than the network size () (27). If only 1% of the metabolites are biomarkers, then functional observability can be guaranteed by placing sensors in only 0.17 to 0.24% of the state nodes. Moreover, SI Appendix, Fig. S3 shows that, for the same metabolic networks, around 78 to 85% of all metabolites are observable from a single optimally placed sensor node. This means, in particular, that in applications where all target nodes belong to this set of observable nodes, functional observability can be achieved with even fewer sensor nodes than shown in Fig. 2B (where the targets were randomly chosen). In addition to their significance for biological and ecological networks, these results are also relevant for cyber–physical systems in engineering applications (e.g., power grids and transportation networks), where the monitoring and detection of potential failures or cyberattacks are often required to be conducted in specific nodes.
Fig. 2.
Minimum sensor placement in large-scale networks. Minimum number of sensors q as a function of the number of target nodes r (normalized by the network size N) in (A) randomly generated directed SW and SF networks and (B) real-world networks. Each data point is an average over 100 realizations of randomly selected target nodes. The minimum set of sensor nodes is determined using Algorithm 1. The SW and SF networks were generated with vertices, where each vertex is a three-dimensional subsystem (i.e., ), while vertices in the real-world networks are assumed to be one-dimensional subsystems (i.e., n = N). The SW networks were generated using the Newman–Watts model, where p is the probability of adding a new edge, and the SF networks were generated using the Barabási–Albert model, where m is the number of existing vertices a new vertex is connected to. Materials and Methods has more details on the network datasets and models.
Minimum-Order Functional Observer Design.
After the sensor nodes have been selected, we need to further choose a matrix F0 to enable the design of a functional observer. The theoretical problem of finding a minimum-order F0 that satisfies Eqs. 4 and 5 was solved in the past decade (31). However, a direct numerical implementation of the method (42) is not scalable for high-dimensional systems because it iteratively uses singular value decomposition (SVD) to construct a matrix F0 that satisfies Eq. 4 and is followed by a combinatorial search to augment the number of rows of F0 in order to satisfy Eq. 5 (SI Appendix, section 4). We circumvent these issues by adopting the structural approach described in the previous sections, in which we convert the rank-based conditions (Eqs. 4 and 5) into equivalent graph-theoretic ones. This is achieved by first noting that, if the corresponding graph of a dynamical system has a self-link in every target node (as assumed throughout), then Eq. 4 implies Eq. 5 with probability one for triples sharing the given structure (SI Appendix, corollary 1). In light of this, only Eq. 4 needs to be considered to determine F0, and hence the combinatorial search is no longer needed. We thus propose Algorithm 2 (Materials and Methods) as a highly scalable solution to determine matrix F0 with the smallest order possible by adding suitable rows to F in such a way that Eq. 4 is satisfied. In Algorithm 2, instead of invoking SVD, the rank condition in Eq. 4 is verified by computing the maximum matching set of an associated bipartite graph. The algorithm is shown to have a computational complexity of order (Materials and Methods), which is a substantial improvement compared with the complexity of order of the numerical procedure in ref. 42.
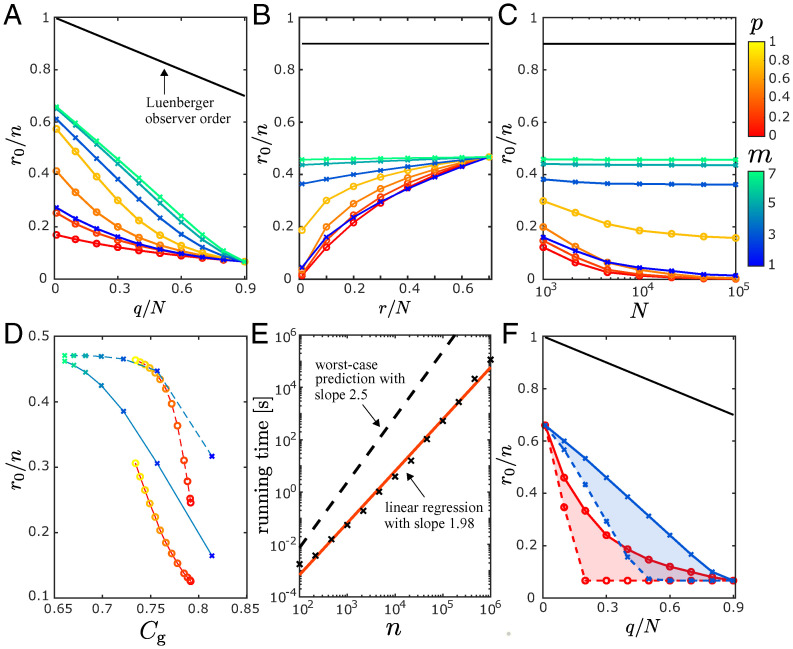
Fig. 3 A and B illustrates the minimum order of the functional observer for randomly generated networks, determined by Algorithm 2, as a function of the numbers of sensor and target nodes. On average, a larger sensor set leads to a lower order r0, whereas a larger target set results in a higher order r0. We note that, overall, functional observers are of much lower order compared with the corresponding Luenberger observers. This leads to a significant improvement in computation efficiency and scalability when designing and implementing observers in large-scale networks. For a fixed number of target nodes, Fig. 3C shows that the functional observer order normalized by the system dimension, , tends to decrease as the network size increases (in SF networks, exhibits weaker dependency on N as m increases). This means that the order reduction gained by the functional observer compared with the Luenberger observer increases with the network size. The extent of this gain depends, however, on other system properties, including the structure of the inference graph , the choice of target nodes in , and how sensor nodes in are placed. In particular, directed links, self-links, and clustering in tend to lead to a larger order reduction in the functional observer design for the random model networks considered. This is illustrated in Fig. 3D, where it is shown for both directed and undirected networks that the functional observer order decreases sharply as a function of the generalized clustering , which is defined to account for both clustering and self-links (Materials and Methods). Interestingly, although directed graphs require a larger minimum set of sensor nodes to guarantee the structural functional observability of a system compared with undirected graphs [which only require one sensor node (45)], directed graphs allow the design of functional observers of smaller orders. This result also highlights that Algorithm 2 brings computational improvement for both directed and undirected network applications compared with existing ones. Furthermore, Fig. 3E illustrates how the running time of Algorithm 2 scales with the network size, showing that it does not surpass our worst-case prediction.
Fig. 3.
Minimum-order functional observer design in large-scale networks. (A–C) Minimum functional observer order r0 (normalized by the system dimension ) as a function of the normalized number of sensor nodes q / N (A), the normalized number of target nodes r / N (B), and the network size N (C). The results are shown for random placement of sensor and target nodes in directed SW and SF networks (color coded by the respective parameters p and m). The other parameters are set to for A, for B, and for C. The black lines indicate the Luenberger observer order for comparison. (D) Normalized order in directed (solid lines) and undirected (dashed lines) SW and SF networks as a function of the generalized clustering of the corresponding undirected graph (Materials and Methods), color coded by p and m for . (E) Running time of Algorithm 2 as a function of n in directed SW networks for . The simulations were implemented in MATLAB, and each network realization was run on a single core of an Intel Xeon Processor E7-8867 v4 at 2.4 GHz. (F) Normalized order as a function of q / N in undirected SW (red; p = 0) and SF (blue; m = 3) networks for randomly (solid lines) and optimally (dashed lines) placed sensors, where . In all panels, each data point corresponds to an average over 100 independent realizations of the network, target placement, and sensor placement (except for the optimal placement in F).
The results shown in Fig. 3 A–E concern sensors and targets randomly placed in the inference graph. The sensor placement, in particular, was implemented by first finding the minimum set of sensor nodes for functional observability and then, increasing q with randomly placed sensor nodes. As shown in Fig. 3F for undirected networks, the functional observer order r0 decreases on average as the number of sensors increases, even if the placement is random. However, r0 can be further reduced by optimizing the placement of the additional sensors. This is a computationally demanding bilevel optimization problem, which—for illustration purposes only—we solve using a (nonscalable) greedy algorithm (Materials and Methods). Fig. 3F shows that such optimization indeed leads to a functional observer with a consistently smaller order compared with the average order for randomly placed sensors. Even though this specific result is illustrated in a lower-dimensional setting, we extrapolate from Fig. 3C that this optimal sensor placement can be relevant for systems of any dimension.
Comparative Analysis of the Observers.
Fig. 4 compares the performances of the functional observer and Luenberger observer when estimating the target variables of a large-scale network. For the target state evolution illustrated in Fig. 4A, which is representative of a trajectory starting away from equilibrium, the transients of the target state estimation error are presented in Fig. 4B for both observers initialized with unknown initial conditions (SI Appendix, section 4). It can be seen that the functional and Luenberger observers have similar dynamical behavior and that their estimates converge to the target states of the system. Statistical analysis further reveals that the two observers perform asymptotically close to each other even under the effects of modeling errors in the system matrix A (Fig. 4C). (Note that if the system were functionally, but not completely, observable, then the target estimation error is only guaranteed to converge for the functional observer.)
Fig. 4.
Comparative performance of the observers for target state estimation in large-scale networks. (A) Dynamical evolution of the target vector , where each color represents a different target variable . (B) Dynamical evolution of the target state estimation error , where is the “true vector value” of the target state and is the estimated target state provided by the functional (blue) or Luenberger (orange) observer initialized with random estimates. (C) Histogram of the steady-state estimation error for s, where both observers are designed using a system matrix for different modeling errors σ. Here, each matrix entry is drawn from a uniform distribution as . (D) Running time of the design algorithms (Left) and simulation time of the observer dynamics (Right) as a function of the network size N (computer specifications are in Fig. 3E). The color code in C and D is the same as in B. In all panels, the results are shown for directed SW networks with randomly selected sensor and target nodes. The undeclared parameters are set as , where each parameter choice in C and D corresponds to 100 realizations of the network, sensor and target selection, and modeling errors (σ = 0 in D). SI Appendix, section 4 has details on the simulations.
Overall, the numerical results show that the considerable order reduction demonstrated here for the functional observer design does not compromise its efficacy. Fig. 4D, on the other hand, shows that such order reduction significantly reduces the computational costs both in the design (Algorithm 2) and in real-time simulations of the functional observer. This computational advantage of functional observers makes them superior or even indispensable to observe large-scale networks, especially when continual redesign of the observer is expected due to the evolution of the system’s equilibrium and/or network structure.
Cyberattack Detection in Power Grids.
The control of man-made technological systems, such as power grids, supply networks, interconnected autonomous vehicles, and swarms of robots, is supported by sensing and communication infrastructure. Decentralized control strategies (60), such as wide-area control in power grids (22), are important to maintain system stability and in particular, mitigate the impact of perturbations that could lead to large-scale failures (61). However, such control strategies rely on resilient communication networks between spatially distributed components, which are arguably more vulnerable to potential failures and cyberattacks than the physical systems themselves. Indeed, there have been growing threats to cybersecurity, including cyberattacks to supervisory control and data acquisition systems, which led to the massive 2015 power outages in Ukraine (62), the 2000 Maroochy Water Services breach in Australia (63), the 2010 Stuxnet computer worm attack on Iran’s nuclear program (64), and communication outages in the western United States power grid in March 2019 (65).
Two common types of cyberattacks are denial of service attacks (e.g., via signal jamming) and deception attacks (e.g., via data corruption) (66). Depending on the specifics of the attack, modeling of the physical system dynamics and transmitted data can still be used to design observers capable of recovering lost data through state estimation. Crucially, state estimation can also be used to detect deception attacks (23, 67, 68), which is significant because such attacks are designed to evade detection. We now show, in the context of power grids, how functional observers can be implemented for cyberattack detection and data recovery and the extent of their computational efficiency improvement compared with the traditional full-state estimators.
The power-grid dynamics can be modeled as a structure-preserving network of coupled first- and second-order Kuramoto oscillators (50, 51). In this model, the generators dynamics are governed by the so-called swing equation,
| [6] |
for , and the dynamics of load buses and generator terminals are described as first-order phase oscillators,
| [7] |
for , where is the number of generators, is the number of load buses, is the number of oscillators (vertices), and is the system dimension. Here, is the phase angle of oscillator i at time t relative to the frame rotating at reference frequency , and Hi and Di are the inertia and damping constants, respectively. In addition, , where Bij is the susceptance of the transmission line connecting buses i and j and Vi and Vj are the voltage magnitudes at these buses. If there is no line connecting buses i and j, Kij = 0. The power injection Pi represents power generation for and power consumption for .
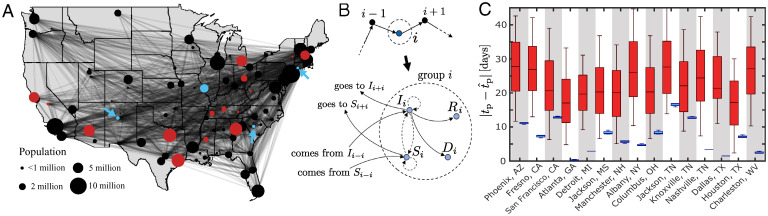
We illustrate our framework on the IEEE-118 benchmark system given by the diagram in Fig. 5A and parameters in Materials and Methods. Fig. 5A, Inset shows a zoomed-in representation of the corresponding inference graph of the power-grid model (Eqs. 6 and 7) around an equilibrium point. We assume that the power grid is equipped with phasor measurement units (PMUs) randomly placed on a subset of load and generator terminal buses, comprising the set of sensor nodes . The PMU measurements are transmitted to a control center in real time to support automated control actions, human decision making, and cyberattack detection. We assume the system initially operates in steady state when, taking advantage of an otherwise inconsequential perturbation at time t = 1 s (Fig. 5B), a deception cyberattack tampers with the measured data from one of the sensors, transmitting instead false data to the control center for t > 1 s. For illustration purposes, in Fig. 5C, we assume that the false data are copied from the measurements of some neighboring vertex j [i.e., ].
Fig. 5.
Deception attack detection in a power grid. (A) Diagram of the IEEE-118 network, which comprises 118 buses with generators (black circles), each connected to a terminal bus (gray circles), and loads (gray squares). PMUs are randomly placed in load and generator terminal buses (blue symbols). The deception attack tampers with the transmitted measurement from the highlighted PMU (red circle). Inset illustrates the inference graph of the dynamical system, where each generator bus (vertex) is represented by two state nodes (phase and frequency in Eq. 6) and each generator terminal and load bus is represented by a single state node (phase in Eq. 7). Links with state nodes outside the highlighted neighborhood are omitted. (B) Dynamics of the oscillators’ phases and the generators’ frequencies over time t. An additive perturbation, drawn from the Gaussian distribution , is applied to each generator’s phase in steady state at t = 1 s. (C) Functional observer-based detection of a deception attack, where the transmitted measurement of the terminal’s phase (blue solid line) is replaced by the false data (red solid line). The data are reconstructed with the state estimates provided by different functional observers (colored dashed lines), where the shaded window illustrates a time of detection s. (D) Histogram of the RMSE between the transmitted measurement and the state estimates provided by the functional observers as a function of . The histograms are shown for the system under attack (red) and not under attack (blue), where an estimate of the statistical properties of the latter can be inferred from training data. Each histogram comprises 10,000 data points corresponding to 100 independent realizations of the system perturbations with 100 functional observers designed for each realization. The contoured histogram at s represents the hardest to detect attack (smallest median value) for the simulated perturbations. (E) Running time of the observer design as a function of the observer order. The results are color coded for functional (blue scale) and Luenberger (red scale) observers as the number of sensors is varied for 100 independent realizations, where the placement of the attack and PMUs is random in each realization and each data point is an average over 100 observers. In all simulations, the observers were designed to estimate the target node using the system model (Eqs. 6 and 7) linearized around the equilibrium point and for t < 1 s (Materials and Methods has details).
We show that this cyberattack can be successfully detected by designing functional observers and cross-validating the transmitted measurements against the state estimates of each observer . This cross-validation takes place during the short transient dynamics that follow the perturbation, where if there is an attack and otherwise. Since one has no access to the true state estimation error , such cross-validation is performed statistically, relying on the state estimation of multiple functional observers designed from distinct , with cardinality , as shown in Fig. 5C. To cross-validate the state estimates against the transmitted data, we use the root-mean-square error (RMSE) index:
| [8] |
where is the time of detection window defined as the time it takes to reliably detect an attack after it is launched. Clearly, the performance of the detection method depends on (shaded window in Fig. 5C), which is also a lower bound of the time interval under which the system is left unprotected waiting for a decision.
Fig. 5D shows that, after a short period of time ( 0.25 s), the separation between the histograms corresponding to the attacked and unattacked systems becomes statistically significant so that reliable detection can be made. Since the separation between the two histograms becomes more pronounced as time increases, the detection becomes more accurate when a larger detection window is allowed. While the histograms show an aggregate representation of attacks under different perturbation scenarios, the same conclusions hold for individual attacks. In our simulations, reliable detection can be achieved even in the hardest to detect attack among all realizations, as illustrated by the contoured histogram for s. The asymptotic convergence of the functional observer is guaranteed if the perturbed state remains in the attraction basin of the given equilibrium. For larger perturbations crossing into the basin of a different equilibrium, the functional observer has to be redesigned around the new equilibrium. Thus, the extent to which the designed observer remains valid upon large perturbations is ultimately determined by the basin stability of the nonlinear system, which can be assessed numerically as proposed in refs. 69 and 70.
In applications with a constantly changing operation point, such as smart power grids, algorithms for the design of controllers and observers have to be sufficiently fast so that they can be implemented in real time following a change of the equilibrium operation point. Moreover, the statistical significance of the cyberattack detection method increases with the number of implemented observers. Thus, the method can be used statistically only if, in addition, the algorithms for the observer design are fast enough to allow for a sufficiently large number of observers to be implemented in real time. To that end, Algorithm 2 provides a fast and scalable solution for the design of minimum-order functional observers. Fig. 5E shows for the IEEE-118 system that the functional observer usually has a much smaller dimension than the Luenberger observer as the number of PMUs increases, leading to a running time reduction by a factor of up to a hundred. This example illustrates for a small power grid the results anticipated in Figs. 3 and 4, and we expect that the computational gain of the functional observers will increase as the network size increases (Fig. 4D).
Estimation of Epidemic Spreading under Limited Testing.
Motivated by the unprecedented impact of the COVID-19 pandemic, recent studies have highlighted the importance of epidemiological models for the design of containment measures. Such models are useful for understanding the growth patterns and scaling laws governing the epidemic spreading (71, 72) as well as for developing control strategies (73–75), which ultimately support policy-making decisions (76). For instance, these models can inform decisions on social distancing and quarantine measures, which cannot be taken lightly as they generally involve social and economic costs. The quality of the model predictions (and thus their ability to inform decisions) is strongly dependent on the state of the epidemic in a population, which is often only partially known due to limitations in testing and reporting. This is especially the case for a new and rapidly evolving pandemic since it takes time to mobilize medical resources and ramp up testing capacity. In particular, as illustrated in the early stages of the COVID-19 pandemic, the testing capacity can vary widely across cities even within the same country. Therefore, it is important to develop the ability to infer as much information as possible from the available incomplete data. Previous work has shown that state estimators can provide meaningful estimates of the true state of the number of infected, susceptible, and recovered individuals in an epidemic when sufficient data are available (74, 77).
Here, we show that, for target estimation, functional observers can be designed to provide reliable information using reduced testing data compared with full-state estimators. As the underlying dynamics in this case are inherently nonlinear, this will give us the opportunity to demonstrate that the methods established here for linear systems are also informative for nonlinear ones. We illustrate this application for the estimation of the infected population in a set of “target cities” (where testing is inadequate) from the known case fatality rate in a set of “sensor cities” (where sufficient testing is conducted). To this end, consider the multigroup model of the spreading of an infectious disease mediated by the air transportation network (57):
| [9] |
for , where N is the number of groups and are the susceptible, infected, recovered, and dead (SIRD) individuals of group i with population size . Parameters γ and η are the recovery and fatality rates, respectively; βi is the contact rate in group i; and K is the adjacency matrix of the transportation network, where Kij describes the number of individuals traveling from group j to i daily. As indicated in Fig. 6A, we assume each group to be a city in the United States and matrix K to describe the air traffic between the cities’ airports, while and K are chosen for illustration purposes to reflect the early stages of the COVID-19 epidemic (Materials and Methods). The epidemiological model (Eq. 9) can be represented as an inference graph, where each state variable is a node and links represent linear and nonlinear interactions between variables, as illustrated by Fig. 6B.
Fig. 6.
Target state estimation in epidemics. (A) US air transportation network, where vertices represent cities and edges represent the direct flights. The target (red) and sensor (blue) cities are highlighted. (B) Network flow between three cities (Upper) and the corresponding inference graph (Lower) of the dynamical system (Eq. 9). The dynamics are taken into account by expanding each vertex i as a set of SIRD state nodes, where links represent the linear (solid lines) and nonlinear (dashed lines) interactions between the state variables in the differential equations. (C) Box plot of the error between the time of the epidemic peak in each target city and the predicted peak time . The red bars show predictions from free-run simulations, while the blue bars show predictions given by the estimates of the designed functional observer, both for 100 independent realizations with arbitrary initial conditions. The bottom, middle, and top of each box represent the 25th, 50th (median), and 75th percentiles of the sample, respectively; the whiskers mark the 5th and 95th percentiles. For illustration purposes, this example assumed an outbreak initiated in Miami, Florida, and its spreading dominated by domestic air transportation. Materials and Methods has simulation and modeling details.
Within the idealized model model described by Eq. 9, if the exact state of the epidemic is known at a given time, subsequent containment measures to “flatten the curve” could be designed based on a free-run simulation of the model. Unfortunately, this would not be the case in practice even if an accurate model was available because as noted above, there are limitations on how precise the data are on the number of infected individuals in a population. This is illustrated in Fig. 6C (red) for the predicted epidemic peaks in a set of 15 target cities. We circumvent this limitation by designing a functional observer that provides more reliable estimates of the number of infected individuals.
A salient property of this problem is that the epidemiological model (Eq. 9) is nonlinear. Our algorithms are not guaranteed to determine a minimum set of sensors and a minimum-order functional observer if the system is nonlinear. Notwithstanding, in many applications, Algorithms 1 and 2 can still be used to identify a small set of sensor nodes (relative to the number of state variables) and a small order matrix F0 (compared with that of a full-state observer) for the design of the corresponding nonlinear functional observer. In particular, it can be shown that the nonlinear functional observer for the system in Eq. 9 satisfies the theoretical conditions for asymptotic convergence of the state estimates (SI Appendix, section 5).
To design the functional observer, let a city i be a sensor (target) city if (if ) is a sensor (target) node. Given the specified set of target cities, Fig. 6A highlights the selected set of four sensor cities for functional observability as provided by Algorithm 1. We then design the nonlinear functional observer based on the inference graph associated with Eq. 9 and the sets and using Algorithm 2 (SI Appendix, section 5). Fig. 6C (blue) shows the estimated time of the epidemic peaks as provided by the designed nonlinear functional observer. Clearly, there is a great improvement in the estimation accuracy (i.e., a smaller deviation between realizations of different initial conditions), which highlights the observer’s resilience to false initial predictions. Note that this functional observer is designed in a situation where the system is unobservable but is functionally observable. This highlights a fundamental advantage of our approach: when the conventional full-state estimators are not applicable, our approach may still provide high-quality estimates of the nonlinear system’s state from sparse measurement data.
Discussion
In large-scale complex networks, it often is physically impossible to ensure complete observability or computationally prohibitive to design full-state observers. This poses fundamental challenges to our ability to observe, understand, and control network processes. Yet, many practical applications only require the observation of a small subset of key variables, which we formalize by introducing the notion of structural functional observability. This work establishes graph-theoretical conditions for functional observability, enabling direct application to large-scale network systems. In particular, the resulting theory allows us to devise highly scalable algorithms to optimally allocate sensors and design functional observers for accurate estimation of a target subset of all state variables.
Observability and controllability are dual properties in control theory (2), which lead to the natural question of what would be the dual of functional observability. By parallelism, one might be tempted to assume that a notion of “target observability” for the given target set could be defined as the target controllability condition (33) for the pair . However, we argue that—in contrast with the target controllability condition for controller design—such a notion of target observability does not lead to the design of an observer capable of estimating the state of the target nodes. Crucially, target estimation in this sense can only be accomplished with functional observability, which is a stronger condition than target observability. Indeed, based on the observability Gramian, we can show that the initial condition of the target nodes is uniquely reconstructable from measurements if and only if Eq. 3 is satisfied (SI Appendix, section 3). This leads us to a fundamental conclusion: despite not being strictly dual, functional observability and target controllability are mirror properties in terms of their functionalities.
Applications of the results presented here may include cybersecurity in the decentralized control of infrastructure and multiagent systems; state estimation for epidemic and ecosystem management from incomplete observation; and identification of biomarkers for prognosis, diagnosis, and treatment. In biomedical and ecological applications, for example, assessment of the state of the system must not interfere significantly with the system dynamics in order to avoid mispredictions and adverse effects. Our results provide a framework under which variables of interest can be estimated from indirect measurements, avoiding variables that interfere with the system’s function and control actions. They also provide an alternative to reduce the computational costs associated with sensing, communication, and data processing in infrastructure, supply, and technological networks that require real-time feedback control (78).
This work also leads to fundamental questions worth pursuing in future research. First, because our theory allows a decision on whether the system is functionally observable or not from the graph structure of the model alone, it is natural to consider how to design functional observers when specific parameters of the system are unknown. This could be addressed by combining our graph-based methods with machine learning techniques to enable data-driven state estimation by functional observers. Second, while here we considered the sensor placement problem and functional observer design in a preexisting cyber–physical network, combining these approaches with the codesign of the communication (and/or physical) layers of the system can lead to further improved resilience against attacks and failures. In particular, the transition to renewable energy is leading to highly heterogeneous networks that integrate conventional synchronous generators, converter-based distributed generation units (solar and wind), flexible alternating current (AC) transmission systems, and high-voltage direct current transmission systems. To ensure the functional observability and stable operation of future power systems, detailed models of these critical components (79) can be incorporated in the codesign of the communication network for wide-area monitoring, protection, and control systems (80). Third, it would be interesting to examine the estimation accuracy, convergence rate, and stability of functional observers in large-scale systems under modeling uncertainties, measurement noise, and round-off errors. A systematic study of the theoretical performance of functional observers in the presence of bounded modeling and measurement errors is still an open problem in the literature, which may be approached in a framework dual to the problem of robust control (81). Finally, our application example to epidemics illustrates how the modeling of the system structure can be used to design functional observers in nonlinear systems. Deriving conditions that allow our methods to be extended to more general nonlinear systems with guarantees of optimality is left for future work.
Materials and Methods
Observer Design.
Both the Luenberger and the functional observer are auxiliary dynamical systems that can be designed under the following structure:
| [10] |
where are design matrices with consistent dimension. In a properly designed Luenberger observer, converges asymptotically to the unmeasured states of the system (Eq. 1), while in a properly designed functional observer, converges asymptotically to . The initial state of the observer can be assigned arbitrarily, and the initial state is unknown.
Despite sharing the same equations (Eq. 10), the Luenberger and functional observers have very different orders (defined by the dimension of vector ) and involve very different design procedures. In what follows, the design procedure for each observer is presented using the linear transformation
| [11] |
where is the transformation matrix, is the Moore–Penrose inverse of C, and is the orthogonal complement of the row space of C.
If (A, C) is observable, then a stable Luenberger observer (with arbitrary stable poles) can be designed by defining , and , where E is a design matrix that can be found using any pole-placement algorithm such that is Hurwitz. Note that .
If (A, C, F) is functionally observable and satisfies Eqs. 4 and 5 for some , then a stable functional observer (with arbitrary stable poles) can be designed as follows (40, 41). 1) Compute and , where and . 2) Find Z using any pole-placement algorithm such that is Hurwitz. 3) Compute , where and T2 = F2. 4) Compute D = Ir, , H = TB, and . Note that .
In this paper, we use the linear-quadratic regulator as a pole-placement algorithm, which requires solving the algebraic Riccati equation for P. For the Luenberger observer design, let , and +
. For the functional observer design, let , and . In both cases, we define , , and R = I, which leads to observers with minimum estimation energy (). The diagonal terms in X guarantee that Z and E are designed to have the rightmost eigenvalues equal to α. This ensures that their dynamics are dominated by the same slowest eigenvalue, allowing a consistent comparison of the observers’ performance despite their different orders.
Minimum Sensor Placement Algorithm.
Algorithm 1 provides an approximate solution to the minimum sensor placement problem in polynomial time. The key steps are as follows. First, a breadth-first search is run for each target node (for loop), allowing us to determine the sets of target nodes that have a direct path to each state node in , where is a set of candidate nodes for sensor placement. Note that a breadth-first search has a complexity of order (82), where is the cardinality of the set of links in , and can be run in parallel for each . Second, a greedy algorithm is used (while loop) to find an approximation of the minimum set of sensor nodes such that structurally functional observability is guaranteed. In the worst-case scenario, the greedy search has a complexity of order .
Algorithm 1:
Minimum sensor placement
input: inference graph , target set , candidate set
output: sensor set
initialize ;
for all
starting at node xi in graph , find the set of reachable nodes using a breadth-first search algorithm;
for all
if , then ;
end
end
initialize .
do
for all , compute gain
[12] add the element with the highest gain
[13] while .
Minimum-Order Functional Observer Design Algorithm.
For cases where (A, C, F) is functionally observable, Algorithm 2 provides a scalable solution to the problem of determining F0 of minimum order such that Eq. 4 is satisfied for the triple (SI Appendix, corollary 2). In this algorithm, we avoid numerical computation of the rank condition in Eq. 4, which is numerically unstable and computationally demanding for high-dimensional matrices [e.g., numerical rank computation based on SVD methods has a complexity of order ]. Instead, we compute the structural (or generic) rank of a matrix by finding the maximum matching of the corresponding bipartite graph of such a matrix. This is a highly scalable alternative since the maximum matching problem can be solved by the Hopcroft–Karp algorithm, which has a complexity of order , where nb and are the numbers of nodes (columns and rows) and links (nonzero entries) in the bipartite graph (matrix). SI Appendix, Fig. S2 presents an illustrative example of Algorithm 2, where it becomes clear how we take advantage of the structural properties of a dynamical system to augment F0 at every iteration until Eq. 4 is satisfied.
Algorithm 2:
Minimum-order functional observer design
input: functionally observable triple (A, C, F)
output: functional observer matrices
initialize ;
do
update ;
build a bipartite graph , where is a set of nodes with each element corresponding to a row of G, is the set of nodes with each element corresponding to a column of G, and is the set of undirected links defined by the nonzero entries Gij of G;
find the maximum matching set associated with (e.g., via the Hopcroft–Karp algorithm);
for all , if and each of its second neighbors are connected to a link in , then update the set of right-matched nodes ;
define the set of candidate nodes , where if is a nonzero entry for some i;
draw an element and update (), where and if j = k and otherwise;
while ;
compute the functional observer matrices for a triple .
Algorithm 2 finds the minimum-order F0 in time, where nb and are the numbers of nodes and links in , respectively. This follows from F0 being determined with recursive iterations, in which a maximum matching algorithm of is run at each iteration. This complexity order can be estimated as a function of n in a worst-case scenario in which one has a single sensor node (q = 1) and a single target node (r = 1), but, in order to satisfy Eq. 4, all other unmeasured nodes must be estimated, resulting in and hence . Since there are at most nodes in , let , where is the average node degree in . Thus, the complexity order is if we assume that . Note that, being a worst-case scenario, this is still a very conservative estimate since usually (Fig. 3). This estimate should be contrasted with the complexity order of in the worst-case scenario for the procedure in ref. 42, which requires computation of the rank condition via SVD in approximately n iterations (SI Appendix, section 4).
Optimal Sensor Placement for Minimum-Order Functional Observers.
Given a functionally observable triple (A, C, F), one may be interested in how to optimally place additional sensor nodes in a network such that the functional observer order r0 is minimized. This is a bilevel optimization problem
| [14] |
where is a set of candidate nodes for sensor placement and is a cost function that returns the minimum order of a functional observer. However, finding F0 depends on (which defines matrix C in Eqs. 3 and 4) and is “embedded” in a lower-level optimization task that requires, for instance, use of Algorithm 2. This is a hard-to-solve problem, but, for illustration purposes, in Fig. 3F we implement a (nonscalable) greedy algorithm that recursively adds elements to by letting until , where , and is the order of F0 returned by Algorithm 2 for this set .
Generation of Complex Dynamical Networks.
For the generation of the N-vertex complex networks used in Figs. 2–4, we explore the following parameters: for Barabási–Albert SF networks (83) and k = 2 and for Newman–Watts SW networks (84). Parameter m is the number of edges of each vertex iteratively added to the network, k is the number of nearest neighbors in a ring graph, and p is the probability of adding a new edge. For each of these undirected networks, a directed model is generated by randomly assigning a single direction to each edge.
Since we are concerned with dynamical networks, we consider that each vertex in an SW or SF network is a dynamical system of possibly more than one dimension. For illustration purposes, we assume that each vertex of a network generated from these models is a three-dimensional subsystem with the following general structure:
| [15] |
To include the effects of heterogeneity in the vertex dynamics of the dynamical networks generated, we let the dynamics of each subsystem be defined by for , where and is a uniform distribution in the interval . Thus, the system matrix A describing the whole dynamical network is given by , where ⊗ is the Kronecker product operator, L is the Laplacian matrix of the generated network, and is defined by if and 0 otherwise. The term means that the second state variable of all subsystems is diffusively coupled according to L. Note that A has dimension , which is also the number of nodes in .
The generalized clustering of the inference graph , studied in Fig. 3D, is defined as , where ki is the node degree of node xi in and . Note that the diagonal entries aii are included to account for self-edges, which distinguishes from the standard clustering coefficient, and that the computation is effectively done for the undirected counterpart of .
For the results presented in Figs. 3 and 4, the target and sensor nodes were chosen randomly among the first state variable of each subsystem (vertex) Ai, under the condition that the sets of sensor nodes and target nodes are nonoverlapping (i.e., ). That is, Fij or Cij is a nonzero entry only if is integer, and thus can have at most N state nodes. This procedure is relaxed in Fig. 2, where all state variables are candidates for sensor placement (i.e., ).
Real-World Networks Datasets.
For the real-world networks used in Fig. 2B, we take several adjacency matrices available in different real-world datasets (described in SI Appendix, section 6). For each real-world network, we define the system matrix A as the Laplacian matrix of in order to model the energy/information flow in such systems as diffusive processes.
Parameters of the IEEE-118 Power-Grid Model.
The IEEE-118 system is derived from a representation of the US Midwest system with 118 buses, 54 generators, and 186 lines (85). The network parameters Kij and generator’s mechanical power Pi are computed from the nominal AC power flow solution, the generator and load dynamical parameters Hi and Di are estimated following the method provided in ref. 51, and the nominal frequency is 60 Hz. The power flow equations were numerically solved using the MATPOWER toolbox (85). The initial conditions were set, for all i, assuming that the power system is in a synchronized steady state , with determined by the power flow solution.
Parameters of the Epidemic Spreading Model.
The parameters in Eq. 9 were set as in order to mimic the coronavirus spreading in each group according to results reported in ref. 72, where here, β is the average value of βi. We define the contact rate of each group as to account for group heterogeneity in the simulation. The air transportation network defined by K describes the traffic of passengers according to the TranStats database for international and domestic flights (https://www.transtats.bts.gov/). Multiple airports belonging to the same city are combined into a single group (vertex) i with a population Pi given by the corresponding city’s population. In Fig. 6, the epidemic peak time is determined by numerically integrating Eq. 9 with the initial conditions and if j is the index for Miami, Florida, and and otherwise. The predicted peak time is determined based on the free-run simulations and functional observer estimations, both initialized with a false guess of the outbreak in a randomly selected city k. That is, and if j = k and and otherwise.
Supplementary Material
Acknowledgments
We acknowledge support from Brazil’s Coordenação de Aperfeiçoamento de Pessoal de Nível Superior Finance Code 001 (to A.N.M.) and Conselho Nacional de Desenvolvimento Científico e Tecnológico Grant 03412/2019-4 (to L.A.A.), and from US Army Research Office Grant W911NF-19-1-0383 (to C.D. and A.E.M.).
Footnotes
The authors declare no competing interest.
This article is a PNAS Direct Submission.
This article contains supporting information online at https://www.pnas.org/lookup/suppl/doi:10.1073/pnas.2113750119/-/DCSupplemental.
Data Availability
Codes and data have been deposited in GitHub (https://github.com/montanariarthur/FunctionalObservability).
References
- 1.Wiener N., Cybernetics or Control and Communication in the Animal and the Machine (The MIT Press, ed. 2, 1961). [Google Scholar]
- 2.Kalman R. E., “On the general theory of control systems” in Proceedings of the First International Conference on Automatic Control (Butterworth, London, UK, 1960), pp. 481–492. [Google Scholar]
- 3.Luenberger G., Observers for multivariable systems. IEEE Trans. Automat. Contr. 11, 190–197 (1966). [Google Scholar]
- 4.Kalman R. E., A new approach to linear filtering and prediction problems. J. Basic Eng. 82, 35–45 (1960). [Google Scholar]
- 5.Chen G. R., Problems and challenges in control theory under complex dynamical network environments. Acta Autom. Sinica 39, 312–321 (2014). [Google Scholar]
- 6.Motter A. E., Networkcontrology. Chaos 25, 097621 (2015). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Montanari A. N., Aguirre L. A., Observability of network systems: A critical review of recent results. J. Control. Autom. Electr. Syst 31, 1348–1374 (2020). [Google Scholar]
- 8.Wang X. F., Chen G., Pinning control of scale-free complex networks. Physica A 310, 521–531 (2002). [Google Scholar]
- 9.Liu Y. Y., Slotine J. J., Barabási A. L., Controllability of complex networks. Nature 473, 167–173 (2011). [DOI] [PubMed] [Google Scholar]
- 10.Cornelius S. P., Kath W. L., Motter A. E., Realistic control of network dynamics. Nat. Commun. 4, 1942 (2013). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Liu Y. Y., Slotine J. J., Barabási A. L., Observability of complex systems. Proc. Natl. Acad. Sci. U.S.A. 110, 2460–2465 (2013). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Fiedler B., Mochizuki A., Kurosawa G., Saito D., Dynamics and control at feedback vertex sets. I. Informative and determining nodes in regulatory networks. J. Dyn. Differ. Equ. 25, 563–604 (2013). [Google Scholar]
- 13.Zañudo J. G. T., Yang G., Albert R., Structure-based control of complex networks with nonlinear dynamics. Proc. Natl. Acad. Sci. U.S.A. 114, 7234–7239 (2017). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Aguirre L. A., Portes L. L., Letellier C., Structural, dynamical and symbolic observability: From dynamical systems to networks. PLoS One 13, e0206180 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Lin C. T., Structural controllability. IEEE Trans. Automat. Contr. 19, 201–208 (1974). [Google Scholar]
- 16.Sun J., Motter A. E., Controllability transition and nonlocality in network control. Phys. Rev. Lett. 110, 208701 (2013). [DOI] [PubMed] [Google Scholar]
- 17.Pasqualetti F., Zampieri S., Bullo F., Controllability, limitations and algorithms for complex networks. IEEE Trans. Control Netw. Syst. 1, 40–52 (2013). [Google Scholar]
- 18.Haber A., Molnar F., Motter A. E., State observation and sensor selection for nonlinear networks. IEEE Trans. Control Netw. Syst. 5, 694–708 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 19.Guan J., Berry T., Sauer T., Limits on reconstruction of dynamics in networks. Phys. Rev. E 98, 022318 (2018). [DOI] [PubMed] [Google Scholar]
- 20.Montanari A. N., Aguirre L. A., Particle filtering of dynamical networks: Highlighting observability issues. Chaos 29, 033118 (2019). [DOI] [PubMed] [Google Scholar]
- 21.Olfati-Saber R., Murray R. M., Consensus problems in networks of agents with switching topology and time-delays. IEEE Trans. Automat. Contr. 49, 1520–1533 (2004). [Google Scholar]
- 22.Xue N., Chakrabortty A., Control inversion: A clustering-based method for distributed wide-area control of power systems. IEEE Trans. Control Netw. Syst. 6, 937–949 (2018). [Google Scholar]
- 23.Pasqualetti F., Dorfler F., Bullo F., Attack detection and identification in cyber-physical systems. IEEE Trans. Automat. Contr. 58, 2715–2729 (2013). [Google Scholar]
- 24.Zhang S., Vittal V., Design of wide-area power system damping controllers resilient to communication failures. IEEE Trans. Power Syst. 28, 4292–4300 (2013). [Google Scholar]
- 25.Singh A. K., Pal B. C., Decentralized dynamic state estimation in power systems using unscented transformation. IEEE Trans. Power Syst. 29, 794–804 (2014). [Google Scholar]
- 26.Vivek S., Yanni D., Yunker P. J., Silverberg J. L., Cyberphysical risks of hacked internet-connected vehicles. Phys. Rev. E 100, 012316 (2019). [DOI] [PubMed] [Google Scholar]
- 27.Barabási A. L., Gulbahce N., Loscalzo J., Network medicine: A network-based approach to human disease. Nat. Rev. Genet. 12, 56–68 (2011). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 28.Vinayagam A., et al., Controllability analysis of the directed human protein interaction network identifies disease genes and drug targets. Proc. Natl. Acad. Sci. U.S.A. 113, 4976–4981 (2016). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 29.Hammond C., Bergman H., Brown P., Pathological synchronization in Parkinson’s disease: Networks, models and treatments. Trends Neurosci. 30, 357–364 (2007). [DOI] [PubMed] [Google Scholar]
- 30.Lehnertz K., et al., Synchronization phenomena in human epileptic brain networks. J. Neurosci. Methods 183, 42–48 (2009). [DOI] [PubMed] [Google Scholar]
- 31.Fernando T. L., Trinh H. M., Jennings L., Functional observability and the design of minimum order linear functional observers. IEEE Trans. Automat. Contr. 55, 1268–1273 (2010). [Google Scholar]
- 32.Jennings L. S., Fernando T. L., Trinh H. M., Existence conditions for functional observability from an eigenspace perspective. IEEE Trans. Automat. Contr. 56, 2957–2961 (2011). [Google Scholar]
- 33.Gao J., Liu Y. Y., D’Souza R. M., Barabási A. L., Target control of complex networks. Nat. Commun. 5, 5415 (2014). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34.Klickstein I., Shirin A., Sorrentino F., Energy scaling of targeted optimal control of complex networks. Nat. Commun. 8, 15145 (2017). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 35.Czeizler E., Wu K. C., Gratie C., Kanhaiya K., Petre I., Structural target controllability of linear networks. IEEE/ACM Trans. Comput. Biol. Bioinformatics 15, 1217–1228 (2018). [DOI] [PubMed] [Google Scholar]
- 36.Li J., Chen X., Pequito S., Pappas G. J., Preciado V. M., “Structural target controllability of undirected networks” in Proceedings of the IEEE Conference on Decision and Control (IEEE, Miami, FL, 2018), pp. 6656–6661. [Google Scholar]
- 37.Commault C., Van der Woude J., Frasca P., Functional target controllability of networks: Structural properties and efficient algorithms. IEEE Trans. Netw. Sci. Eng. 7, 1521–1530 (2019). [Google Scholar]
- 38.Wu L., Shen Y., Li M., Wu F. X., Network output controllability-based method for drug target identification. IEEE Trans. Nanobioscience 14, 184–191 (2015). [DOI] [PubMed] [Google Scholar]
- 39.Luenberger D. G., An introduction to observers. IEEE Trans. Automat. Contr. 16, 596–602 (1971). [Google Scholar]
- 40.Darouach M., Existence and design of functional observers for linear systems. IEEE Trans. Automat. Contr. 45, 940–943 (2000). [Google Scholar]
- 41.Trinh H., Fernando T., Functional Observers for Dynamical Systems (Springer, Berlin, 2012). [Google Scholar]
- 42.Fernando T., Jennings L., Trinh H., “Numerical implementation of a functional observability algorithm: A singular value decomposition approach” in 2010 IEEE Asia Pacific Conference on Circuits and Systems (IEEE, Kuala Lumpur, Malaysia, 2010), pp. 796–799. [Google Scholar]
- 43.Chen C. T., Linear System Theory and Design (Oxford University Press, ed. 3, 1999). [Google Scholar]
- 44.Rotella F., Zambettakis I., A note on functional observability. IEEE Trans. Automat. Contr. 61, 3197–3202 (2016). [Google Scholar]
- 45.Cowan N. J., Chastain E. J., Vilhena D. A., Freudenberg J. S., Bergstrom C. T., Nodal dynamics, not degree distributions, determine the structural controllability of complex networks. PLoS One 7, e38398 (2012). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 46.Leitold D., Vathy-Fogarassy Á., Abonyi J., Controllability and observability in complex networks - The effect of connection types. Sci. Rep. 7, 151 (2017). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 47.Arenas A., Díaz-Guilera A., Kurths J., Moreno Y., Zhou C., Synchronization in complex networks. Phys. Rep. 469, 93–153 (2008). [Google Scholar]
- 48.Rodrigues F. A., Peron T. K., Ji P., Kurths J., The Kuramoto model in complex networks. Phys. Rep. 610, 1–98 (2016). [Google Scholar]
- 49.Eroglu D., Lamb J. S., Pereira T., Synchronisation of chaos and its applications. Contemp. Phys. 58, 207–243 (2017). [Google Scholar]
- 50.Dörfler F., Chertkov M., Bullo F., Synchronization in complex oscillator networks and smart grids. Proc. Natl. Acad. Sci. U.S.A. 110, 2005–2010 (2013). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 51.Nishikawa T., Motter A. E., Comparative analysis of existing models for power-grid synchronization. New J. Phys. 17, 015012 (2015). [Google Scholar]
- 52.Izhikevich E. M., Which model to use for cortical spiking neurons? IEEE Trans. Neural Netw. 15, 1063–1070 (2004). [DOI] [PubMed] [Google Scholar]
- 53.Aguirre L. A., Portes L. L., Letellier C., Observability and synchronization of neuron models. Chaos 27, 103103 (2017). [DOI] [PubMed] [Google Scholar]
- 54.Perini F., Galligani E., Reitz R. D., An analytical Jacobian approach to sparse reaction kinetics for computationally efficient combustion modeling with large reaction mechanisms. Energy Fuels 26, 4804–4822 (2012). [Google Scholar]
- 55.Mirsky H. P., Liu A. C., Welsh D. K., Kay S. A., Doyle F. J. III, A model of the cell-autonomous mammalian circadian clock. Proc. Natl. Acad. Sci. U.S.A. 106, 11107–11112 (2009). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 56.Mochizuki A., Fiedler B., Kurosawa G., Saito D., Dynamics and control at feedback vertex sets. II. A faithful monitor to determine the diversity of molecular activities in regulatory networks. J. Theor. Biol. 335, 130–146 (2013). [DOI] [PubMed] [Google Scholar]
- 57.Colizza V., Barrat A., Barthélemy M., Vespignani A., The role of the airline transportation network in the prediction and predictability of global epidemics. Proc. Natl. Acad. Sci. U.S.A. 103, 2015–2020 (2006). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 58.Corman T. H., Leiserson C. E., Rivest R. L., Stein C., Introduction to Algorithms (The MIT Press, ed. 2, 2001). [Google Scholar]
- 59.Fujito T., On approximation of the submodular set cover problem. Oper. Res. Lett. 24, 169–174 (1999). [Google Scholar]
- 60.Bakule L., Decentralized control: An overview. Annu. Rev. Contr. 32, 87–98 (2008). [Google Scholar]
- 61.Yang Y., Nishikawa T., Motter A. E., Small vulnerable sets determine large network cascades in power grids. Science 358, eaan3184 (2017). [DOI] [PubMed] [Google Scholar]
- 62.Lee R., Assante M., Conway T., “Analysis of the cyber attack on the Ukrainian Power Grid” (Tech. rep. E-ISAC_SANS_Ukraine_DUC_5, SANS Industrial Control Systems, Washington, DC, 2016).
- 63.Slay J., Miller M., Lessons learned from the Maroochy Water Breach. Critical Infrastructure Prot 253, 73–82 (2007). [Google Scholar]
- 64.Farwell J. P., Rohozinski R., Stuxnet and the future of cyber war. Survival (Lond.) 53, 23–40 (2011). [Google Scholar]
- 65. “Lesson learned: Risks posed by firewall firmware vulnerabilities” (Tech. rep. 20190901, North American Electric Reliability Corporation, Atlanta, GA, 2019).
- 66.Amin S., Cárdenas A., Sastry S., Safe and secure networked control systems under denial-of-service attacks. Hybrid Syst. Comput. Control 5469, 31–45 (2009). [Google Scholar]
- 67.Teixeira A., Amin S., Sandberg H., Johansson K. H., Sastry S. S., “Cyber security analysis of state estimators in electric power systems” in Proceedings of the IEEE Conference on Decision and Control (IEEE, Atlanta, GA, 2010), pp. 5991–5998. [Google Scholar]
- 68.Giraldo J., et al., A survey of physics-based attack detection in cyber-physical systems. ACM Comput. Surv. 51, 76 (2018). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 69.Menck P. J., Heitzig J., Marwan N., Kurths J., How basin stability complements the linear-stability paradigm. Nat. Phys. 9, 89–92 (2013). [Google Scholar]
- 70.Menck P. J., Heitzig J., Kurths J., Schellnhuber H. Joachim, How dead ends undermine power grid stability. Nat. Commun. 5, 3969 (2014). [DOI] [PubMed] [Google Scholar]
- 71.Singer H. M., The COVID-19 pandemic: Growth patterns, power law scaling, and saturation. Phys. Biol. 17, 055001 (2020). [DOI] [PubMed] [Google Scholar]
- 72.Blasius B., Power-law distribution in the number of confirmed COVID-19 cases. Chaos 30, 093123 (2020). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 73.Lesniewski A., Epidemic control via stochastic optimal control. arXiv [Preprint] (2020). https://arxiv.org/abs/2004.06680 (Accessed 23 March 2021).
- 74.Tsay C., Lejarza F., Stadtherr M. A., Baldea M., Modeling, state estimation, and optimal control for the US COVID-19 outbreak. Sci. Rep. 10, 10711 (2020). [DOI] [PMC free article] [PubMed] [Google Scholar]
- 75.Morris D. H., Rossine F. W., Plotkin J. B., Levin S. A., Optimal, near-optimal, and robust epidemic control. Commun. Phys. 4, 78 (2021). [Google Scholar]
- 76.Hethcote H. W., The mathematics of infectious diseases. SIAM Rev. 42, 599–653 (2000). [Google Scholar]
- 77.Iggidr A., Souza M. O., State estimators for some epidemiological systems. J. Math. Biol. 78, 225–256 (2019). [DOI] [PubMed] [Google Scholar]
- 78.Wang L., Morse A. S., A distributed observer for a time-invariant linear system. IEEE Trans. Automat. Contr. 63, 2123–2130 (2018). [Google Scholar]
- 79.Vittal V., McCalley J. D., Anderson P. M., Fouad A., Power System Control and Stability (John Wiley & Sons, 2019). [Google Scholar]
- 80.Vaccaro A., Zobaa A. F., Wide Area Monitoring, Protection and Control Systems: The Enabler for Smarter Grids (IET, 2016). [Google Scholar]
- 81.Zhou K., Doyle J. C., Essentials of Robust Control (Prentice Hall, Upper Saddle River, NJ, 1998). [Google Scholar]
- 82.Newman M., Networks: An Introduction (OUP, Oxford, United Kingdom, 2010). [Google Scholar]
- 83.Barabási A. L., Albert R., Emergence of scaling in random networks. Science 286, 509–512 (1999). [DOI] [PubMed] [Google Scholar]
- 84.Newman M. E., Watts D. J., Renormalization group analysis of the small-world network model. Phys. Lett. A 263, 341–346 (1999). [Google Scholar]
- 85.Zimmerman R. D., Murillo-Sanchez C. E., Thomas R. J., MATPOWER: Steady-state operations, planning, and analysis tools for power systems research and education. IEEE Trans. Power Syst. 26, 12–19 (2011). [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
Data Availability Statement
Codes and data have been deposited in GitHub (https://github.com/montanariarthur/FunctionalObservability).