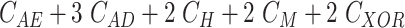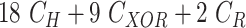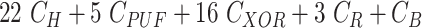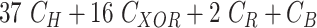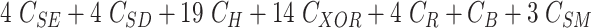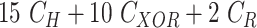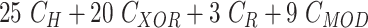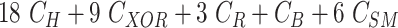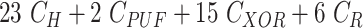Abstract
Due to the outbreak of COVID-19, the Internet of Medical Things (IoMT) has enabled the doctors to remotely diagnose the patients, control the medical equipment, and monitor the quarantined patients through their digital devices. Security is a major concern in IoMT because the Internet of Things (IoT) nodes exchange sensitive information between virtual medical facilities over the vulnerable wireless medium. Hence, the virtual facilities must be protected from adversarial threats through secure sessions. This article proposes a lightweight and physically secure mutual authentication and secret key establishment protocol that uses physical unclonable functions (PUFs) to enable the network devices to verify the doctor’s legitimacy (user) and sensor node before establishing a session key. PUF also protects the sensor nodes deployed in an unattended and hostile environment from tampering, cloning, and side-channel attacks. The proposed protocol exhibits all the necessary security properties required to protect the IoMT networks, like authentication, confidentiality, integrity, and anonymity. The formal AVISPA and informal security analysis demonstrate its robustness against attacks like impersonation, replay, a man in the middle, etc. The proposed protocol also consumes fewer resources to operate and is safe from physical attacks, making it more suitable for IoT-enabled medical network applications.
Keywords: COVID-19, cyber–physical system, Internet of Medical Things (IoMT), key management, security
I. Introduction
Internet of Medical Things (IoMT) has evolved from the Internet of Things (IoT), where the doctors can use the wireless media to communicate with IoT enabled sensor nodes, such as smart thermometers, smart ventilators, and so on [1]. The IoT enables sensor nodes to gather, analyze, and disseminate the health-related information of the patients in real-time to the doctors [2] and enable them to diagnose, treat, and monitor patients remotely. Since the outbreak of COVID-19, hospitals are now leveraging the remote monitoring framework using IoMT to transform healthcare professionals’ physical medical practices to telemedical practices to perform their duty safely. However, there are many challenges in utilizing IoMT networks and the issues concerning patients’ security and privacy and healthcare institutions’ sensitive information. The possible adversarial threats are eavesdropping, data breach, and Denial of Service (DoS) [3], [4]. The situation becomes more adverse in IoMT since medical users and vendors have limited awareness of security threats [5] and possible remedies. The adversary likes to breach the data that mainly includes patients’ medical records, home health data, bank details, insurance information, etc., [6]–[8].
The adversaries exploit the systems and networks’ vulnerabilities to conduct cyberattacks and achieve their evil desires. The absence of robust mutual authentication and key establishment scheme is the key factor attracting the adversaries toward IoMT networks [9]. The existing mutual authentication schemes are not directly applicable to IoMT networks as they are computation and communication expensive and can drain the precious energy reserves of IoT sensor nodes [10]. Moreover, most of the schemes do not consider the hostile environment of deployment of sensor nodes and become vulnerable to physical, cloning, and side-channel attacks [11]. Therefore, IoMT networks need practical mutual authentication and a secret key establishment approach to provide robust security in all environments while being lightweight in computation and communication.
Due to the communicable nature of COVID-19, doctors prefer to diagnose and monitor the COVID-19 patients remotely with IoT-enabled sensor nodes. Security and privacy are major concerns in IoMT since the sensitive information is exchanged over the unguarded wireless channel that is used in IoMT. The attacker can exploit this vulnerability and control medical equipment that may cause damage to the medical equipment, resulting in fatalities and infrastructure damage. To prevent adversarial threats, the doctors and the IoT sensor nodes need to register with the network and prove their legitimacy to the gateway before establishing the secret session key at the time of access. Designing such an approach, particularly in the IoMT network, is challenging due to resource limitations and the likelihood of physical capturing of IoT sensor nodes deployed in a hostile environment.
This article proposes a lightweight, robust, and physically secure mutual authentication and secret key (MASK) establishment protocol for securing the sensitive health information of the patients. The proposed protocol uses lightweight cryptography primitives, such as one-way hash function, nonce, physical unclonable function (PUF), and bitwise XOR operations. The reliability is verified using formal and informal security analysis. The protocol also prevents the physical loss of a device and side-channel attacks. The protocol also consumes fewer resources to operate and is safe from physical attacks, making it more suitable for IoT-enabled medical network applications.
This article is structured as follows. Section II discusses related work. Section III presents the system model, adversary model, security and other goals, and PUF. Section IV demonstrates how the MASK protocol works. Section V provides formal and informal security analysis. Section VI discusses performance and comparative analysis. Section VII concludes and highlights future scope.
II. Related Work
El-Latif et al. [12] proposed a quantum steganography protocol using hash function verify security. However, Tseng et al. [13] asserted that the [12] approach is only applicable to secure message in cloud-based IoT platform. To overcome the deficits, Das independently constructed a 2-factor user authentication protocol for wireless sensor networks (WSNs) [14]. But as per the cryptanalysis [15], the approach of Das [14] is found susceptible to impersonation attacks. Likewise, Chang et al. [16] examined the approach of Turkanović et al. [17] for user authentication and key agreement and found it vulnerable to impersonation attacks. Similarly, Gope et al. [18] introduced a novel real-time authentication and key agreement protocol. However, the protocol did not ascertain the anonymity of sensor nodes. Yeh et al. [19] introduced an asymmetric cryptography-based authentication protocol. Still, the scheme did not accomplish mutual authentication and is computationally expensive due to public-key cryptography. Hossain et al. [20] propose two-factor authentication schemes for end-to-end secured IoT environment using biometric traits, which are subjected to masquerade and replay attacks. Das et al. [21] developed an IoT specific authentication approach using biometric and smart card to address the shortcomings. Likewise, Li et al. [22] designed a robust but resource expensive 3-factor user authentication scheme based on user identity, password, and biometrics. To reduce the computation expenditure, Esfahani et al. [23] introduced a lightweight scheme that uses a one-way hash function and bitwise XOR operations. Independently, Paliwal [24] tried to address the security issues of [25] by developing hash based mutual authentication and key agreement scheme. In summary, most of the protocols are insecure against significant adversarial threats, fail to exhibit essential security properties to keep the communication secure, and are computationally and communication expensive.
III. Preliminaries
System Model:
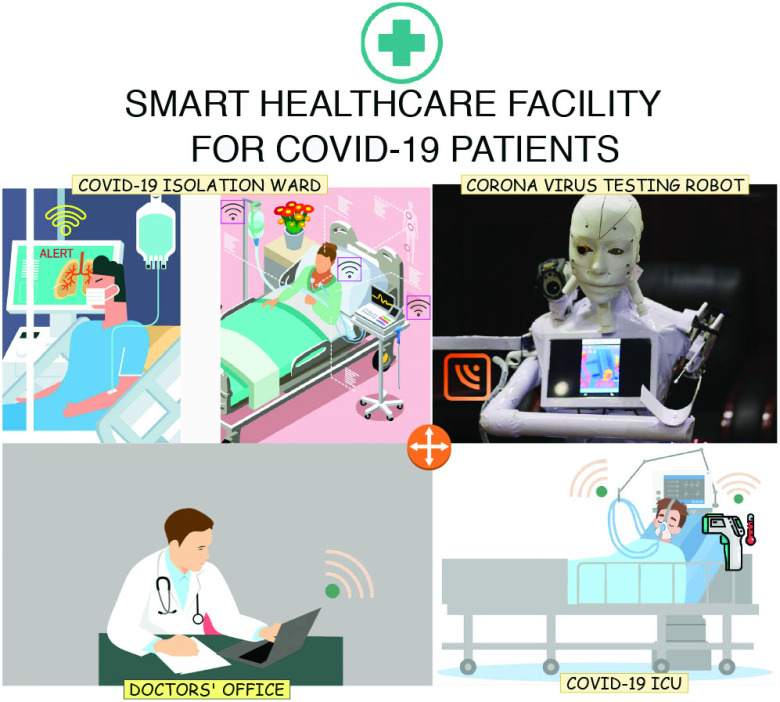
Fig. 1 depicts the scenario of a smart healthcare facility where COVID-19 affected patients are diagnosed. Hossain et al.
[26] and Abdulsalam and Hossain [27] framework consists of sensor nodes, a gateway, and the user (e.g., doctor). The sensor nodes are integrated with the medical equipment to monitor the patients’ health, etc. Gateway is used to relay the information between the doctor, and IoT enabled sensor nodes in Healthcare-IoT [28]. The user (e.g., doctor) is interested in receiving real-time information from sensor nodes [e.g., ZigBee (IEEE 802.15.4), Z-Wave (e.g.,
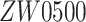 )]) to take decisive actions regarding the patients’ treatment.
)]) to take decisive actions regarding the patients’ treatment.
Fig. 1.
System model for mutual authentication and key exchange between IoT devices in smart healthcare facility.
Adversary Model: In a smart healthcare facility, IoT sensor nodes relay real-time patient diagnosis reports. According to the Dolev–Yao (DY) adversary model [18], an adversary may disrupt the IoMT network’s operation through malicious actions eavesdropping on the information related to the drug formula of the COVID-19 vaccine. The adversary can replay the eavesdropped message to get privileged access and intercept the messages to retrieve security credentials that can be used later for generating keys to compromise subsequent communications. Besides, the adversary can delete or alter the patient medicine prescription. IoT sensors are deployed openly in smart healthcare facilities; therefore, they are subjected to cloning, side channel, and physical attacks.
Security and Other Goals: The “robust” and “efficient” [10], [18] goals of a security protocol are 1) performs MASK establishment; 2) protects against prominent attacks, such as MITM, replay, modification, impersonation, DoS, etc.; 3) keep data privacy property, i.e., a security protocol must implement a robust procedure considering eavesdropping by an adversary; 4) identity anonymity and untraceability, i.e., security protocol must exhibit identity anonymity and untraceability to prevent MITM and DoS attacks; 5) a security protocol must introduce a mechanism to protect the IoT devices when deployed in a hostile environment from physical tampering, cloning, and side-channel attacks; and 6) must use lightweight cryptography operations to utilize the resources efficiently.
Physically Unclonable Function: PUF is recommended as a solution to secure the hardware from adversarial threats. PUF neither stores any keys on edge devices nor uses public-key cryptography for performing authentication between devices. Besides, it cannot be cloned since the PUF is formed by making nanoscale variations during the integrated chip’s manufacturing process (IC). All these attributes make the above a good choice for authentication of lightweight devices in IoHT [29]. An ideal PUF should exhibit the property of uniqueness, reliability, and unpredictability. Mathematically, PUF can be expressed as
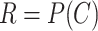 , wherein
, wherein
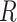 denotes output response,
denotes output response,
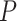 denotes PUF, and
denotes PUF, and
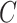 denotes the input challenge. Since the output of the PUF depends upon the intrinsic physical variations in the IC, any tampering to the PUF would destroy the unique characteristics of the device [11].
denotes the input challenge. Since the output of the PUF depends upon the intrinsic physical variations in the IC, any tampering to the PUF would destroy the unique characteristics of the device [11].
IV. Proposed Security Framework
The proposed protocol is executed in three phases, namely, user registration, device registration, and MASK establishment. Table I provides the notations that are used throughout this article. The following assumptions are considered in designing the protocol.
-
1)
The IoT sensor node is integrated into medical equipment consist of a micro-controller (
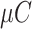 ) attached to a PUF.
) attached to a PUF. -
2)
User device, gateway, and sensor nodes compute identical cryptography operations.
-
3)
User devices and sensor nodes have some resource constraints (i.e., limited compute power and memory, etc.). But the gateway has no restrictions on computing and storage.
-
4)
Sensor nodes are vulnerable to physical.
Now we present different phases of the protocol.
TABLE I. Symbols, Abbreviations, and Operators Description.
| Notation | Definition |
|---|---|
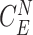 , ,
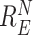
|
C: Challenge, R: Response, N: Number, E: Entity |
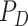 , ,
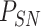
|
Physically Unclonable Function |
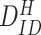 |
Unique identity of doctor issued by Hospital |
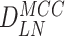 |
Unique license no. issued by Medical Council |
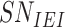 |
International equipment identity of Sensor Node |
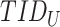 , ,
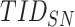
|
Temporary identity of User and Sensor Node |
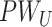 , F , F |
User password, Strong cryptography function |
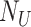 , ,
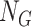 , ,
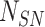
|
Nonce |
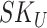 , ,
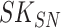
|
Session Key |
| h(.) | one way cryptography hash function |
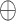 , ,
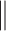
|
Bit-wise XOR and concatenation operator |
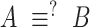 |
Is A identical to B? |
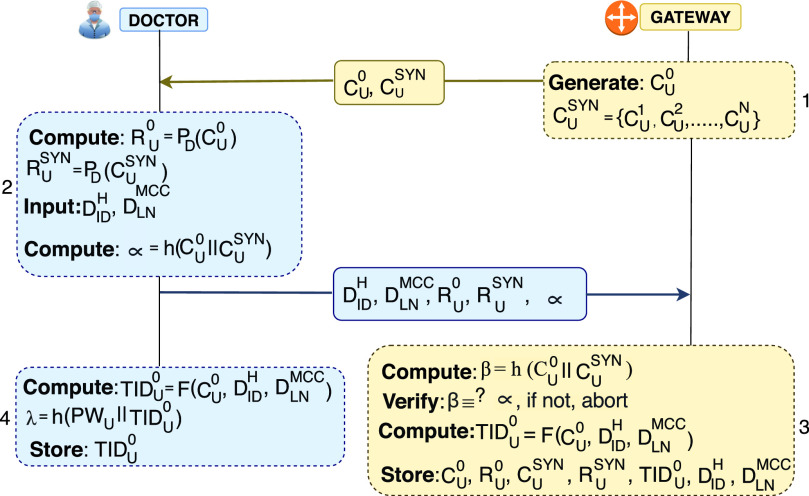
User Registration Phase: Fig. 2 illustrates the process of how a user(“doctor”) needs to register its trusted device in the gateway to obtain real-time health information of the patients.
-
Step 1:
The gateway first generates a random challenge
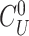 for the current registration process along with another set of challenges
for the current registration process along with another set of challenges
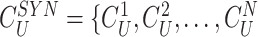 }.
}.
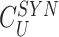 consists of many random challenges used by the gateway in the future to verify the user device. The gateway forms the message {
consists of many random challenges used by the gateway in the future to verify the user device. The gateway forms the message {
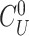 ,
,
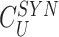 } and sends it to the doctor’s device.
} and sends it to the doctor’s device. -
Step 2:
Upon receiving, {
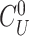 ,
,
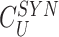 }, doctor’s device triggers the PUF to generate the response,
}, doctor’s device triggers the PUF to generate the response,
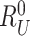 and
and
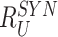 .
.
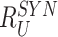 comprises of responses to many random challenges (
comprises of responses to many random challenges (
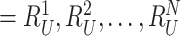 ) that will be used by the gateway to authenticate the doctor’s device in future correspondences. Afterwards, doctor inputs his/her unique identity details,
) that will be used by the gateway to authenticate the doctor’s device in future correspondences. Afterwards, doctor inputs his/her unique identity details,
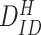 , and
, and
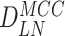 . Thereafter, doctor’s device compute
. Thereafter, doctor’s device compute
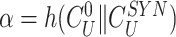 to enable the gateway to verify the association between received responses (
to enable the gateway to verify the association between received responses (
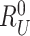 ,
,
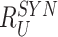 ) and sent challenges
) and sent challenges
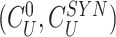 . Lastly, the doctor’s device compose a message, including
. Lastly, the doctor’s device compose a message, including
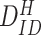 ,
,
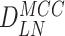 ,
,
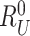 ,
,
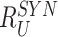 ,
,
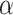 and sends it to gateway for requesting authorization to communicate with sensor nodes.
and sends it to gateway for requesting authorization to communicate with sensor nodes. -
Step 3:
After reception, gateway computes
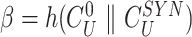 and verifies the identicalness between
and verifies the identicalness between
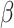 and
and
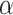 ; the gateway terminates the session if result is distinct, otherwise computes
; the gateway terminates the session if result is distinct, otherwise computes
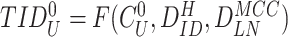 . At the end of the registration, gateway stores the
. At the end of the registration, gateway stores the
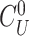 ,
,
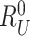 ,
,
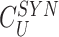 ,
,
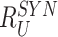 ,
,
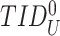 ,
,
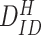 ,
,
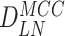 for future communication with user.
for future communication with user. -
Step 4:
Likewise, doctor’s device also computes and stores
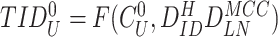 and
and
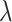 .
.
Fig. 2.
User registration phase.
Remark 1:
It is worth noting that
is a function of
,
, and
. The use of new challenge
for every session assures distinct temporal identity
for every session, thus achieving untraceability. Moreover, instead of real identity of user {
,
}, temporary identity
is used to preserve user anonymity during message exchanges.
is a function of
and updates every session to protect the device from adversarial threats.
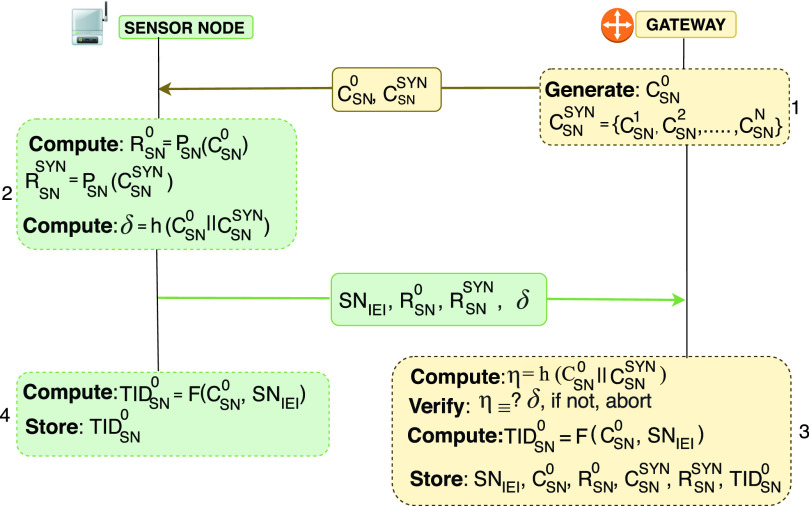
Device Registration Phase: The IoT node at the healthcare institution is first registered with the gateway. Fig. 3 illustrates registration process.
-
Step 1:
The gateway generates a challenge for sensor node registration
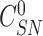 followed by another set of challenges
followed by another set of challenges
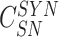 {
{
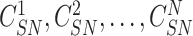 }. The composed message {
}. The composed message {
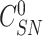 ,
,
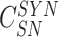 } is sent to the sensor node through a secure channel.
} is sent to the sensor node through a secure channel. -
Step 2:
Upon reception {
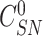 ,
,
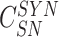 }, sensor node begins to prepare the responses
}, sensor node begins to prepare the responses
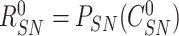 ,
,
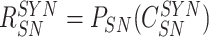 to the received challenges (
to the received challenges (
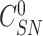 ,
,
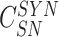 ). The sensor node computes
). The sensor node computes
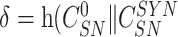 ) to enable the gateway in verifying the association between response and challenges. Finally, {
) to enable the gateway in verifying the association between response and challenges. Finally, {
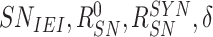 } is delivered.
} is delivered. -
Step 3:
Gateway at first computes
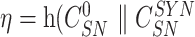 ) followed by a comparison of
) followed by a comparison of
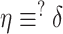 to verify the relationship between responses and challenges. Subsequently, the gateway derives the temporary identity of the sensor node
to verify the relationship between responses and challenges. Subsequently, the gateway derives the temporary identity of the sensor node
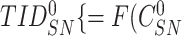 ,
,
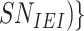 . After the computations and retrieval, the gateway stores the
. After the computations and retrieval, the gateway stores the
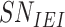 ,
,
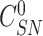 ,
,
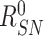 ,
,
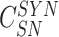 ,
,
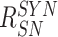 , and
, and
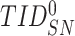 .
. -
Step 4:
The sensor node computes and stores the temporary identity
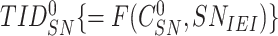 .
.
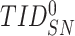 enables the sensor node to accomplish anonymity and untraceability.
enables the sensor node to accomplish anonymity and untraceability.
Fig. 3.
Sensor node registration phase.
Remark 2:
Gateway records the real identity of the sensor node
during registration. It is noteworthy that
is a function of
, and
. The use of new challenge
for every session assures distinct short-term identity of sensor node
for every session, therefore accomplishing untraceability. Moreover,
does not disclose the real identity of the sensor node during message exchanges, thus preserving sensor node identity anonymity.
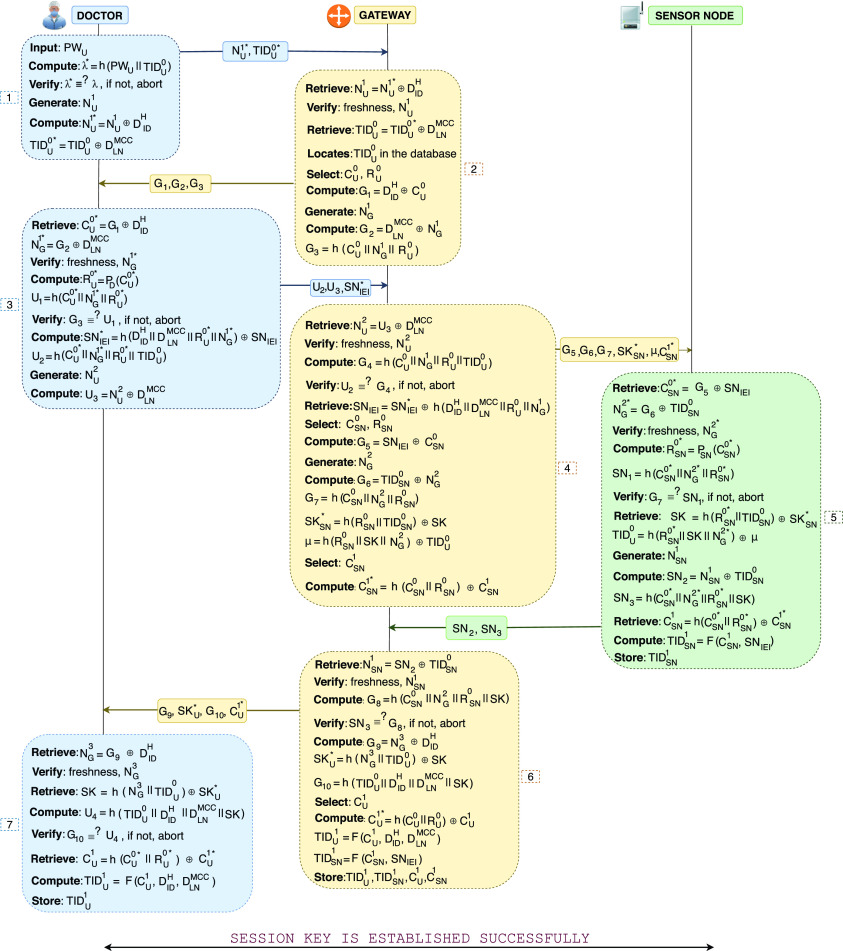
Mutual Authentication and Secret Key Establishment Phase: Fig. 4 illustrates the process of MASK establishment and explained as follows.
-
Step 1:
Initially, the doctor has to prove his/her identity by entering his password
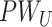 . The doctor’s device then calculates
. The doctor’s device then calculates
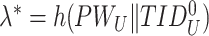 and verifies the user’s authenticity,
and verifies the user’s authenticity,
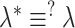 . After successful verification the device generates a nonce
. After successful verification the device generates a nonce
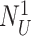 , and computes
, and computes
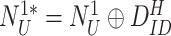 to protect the nonce privacy. The doctor’s device creates a pseudo-identity
to protect the nonce privacy. The doctor’s device creates a pseudo-identity
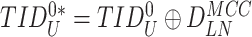 from the temporary identity
from the temporary identity
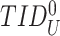 to add a second layer of identity anonymity and untraceability protection. Finally, the doctor’s device sends the message {
to add a second layer of identity anonymity and untraceability protection. Finally, the doctor’s device sends the message {
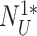 ,
,
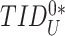 } to the gateway.
} to the gateway. -
Step 2:
After receiving {
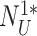 ,
,
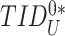 }, the gateway extracts the real nonce,
}, the gateway extracts the real nonce,
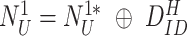 . The gateway then verifies the freshness of the
. The gateway then verifies the freshness of the
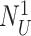 . Subsequently, the gateway derives the temporary identity from pseudo-identity,
. Subsequently, the gateway derives the temporary identity from pseudo-identity,
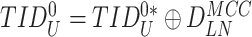 and matches with the database. Once
and matches with the database. Once
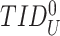 is located, the gateway selects the corresponding challenge (
is located, the gateway selects the corresponding challenge (
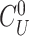 ) and response (
) and response (
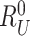 ). To meet the privacy requirements, the gateway encloses the real
). To meet the privacy requirements, the gateway encloses the real
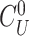 ,
,
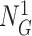 within the
within the
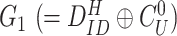 and
and
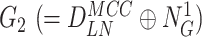 . Finally, the gateway computes
. Finally, the gateway computes
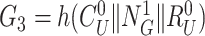 ;
;
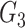 helps the doctor’s device to verify the authenticity of the gateway. The gateway sends the challenge
helps the doctor’s device to verify the authenticity of the gateway. The gateway sends the challenge
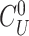 , nonce
, nonce
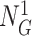 , and authentication message enclosed in
, and authentication message enclosed in
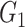 ,
,
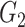 , and
, and
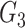 , respectively to the doctor’s device.
, respectively to the doctor’s device. -
Step 3:
Upon receiving the
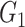 ,
,
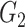 , and
, and
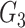 from the gateway, the doctor’s device begins extracting the challenge
from the gateway, the doctor’s device begins extracting the challenge
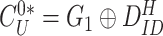 , and nonce
, and nonce
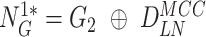 . After examining the freshness of
. After examining the freshness of
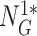 , doctor’s device extracts response from PUF,
, doctor’s device extracts response from PUF,
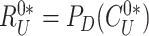 . Subsequently, the doctor’s device calculates
. Subsequently, the doctor’s device calculates
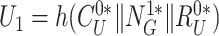 and compares with
and compares with
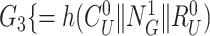 }. After proving the authenticity, the user device prepares the pseudo-identity of the sensor node
}. After proving the authenticity, the user device prepares the pseudo-identity of the sensor node
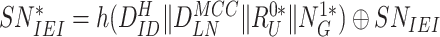 . Thereafter, the doctor device prepares device authentication value,
. Thereafter, the doctor device prepares device authentication value,
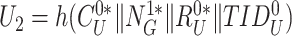 .
.
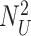 is also shared secretly with gateway. Finally, {
is also shared secretly with gateway. Finally, {
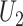 ,
,
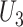 ,
,
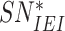 } is sent to the gateway.
} is sent to the gateway. -
Step 4:
Initially, the gateway derives the
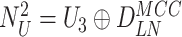 and evaluates the freshness. If fresh, gateway begins the computation of
and evaluates the freshness. If fresh, gateway begins the computation of
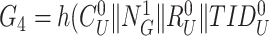 and examines the identicalness between
and examines the identicalness between
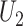 and
and
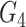 . The mutual authentication between doctor and gateway gets accomplished if
. The mutual authentication between doctor and gateway gets accomplished if
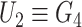 , else fails. The gateway afterward extracts the real identity of the sensor node for accomplishing mutual authentication,
, else fails. The gateway afterward extracts the real identity of the sensor node for accomplishing mutual authentication,
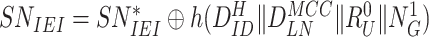 . After retrieving
. After retrieving
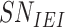 , the gateway then selects the corresponding
, the gateway then selects the corresponding
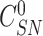 ,
,
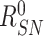 pair and generates the
pair and generates the
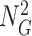 . To ensure privacy, the challenge
. To ensure privacy, the challenge
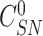 and the nonce
and the nonce
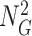 is secretly enclosed within
is secretly enclosed within
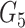 and
and
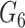 , respectively. Gateway also prepares
, respectively. Gateway also prepares
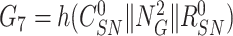 to prove its identity to the sensor node. The gateway calculates
to prove its identity to the sensor node. The gateway calculates
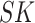 for the sensor node and enclose it secretly within
for the sensor node and enclose it secretly within
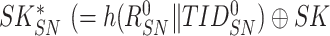 ). Correspondingly, gateway also encloses the
). Correspondingly, gateway also encloses the
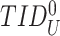 within
within
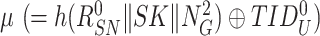 . Finally, gateway selects a random new challenge
. Finally, gateway selects a random new challenge
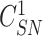 from the set of challenges
from the set of challenges
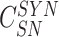 generated at the time of registration and computes
generated at the time of registration and computes
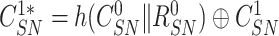 . The gateway compose a message consisting of
. The gateway compose a message consisting of
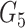 ,
,
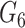 ,
,
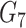 ,
,
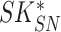 ,
,
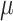 ,
,
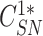 and send it to the sensor node.
and send it to the sensor node. -
Step 5:
After receiving {
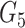 ,
,
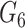 ,
,
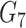 ,
,
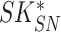 ,
,
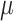 ,
,
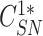 } from gateway, the sensor node retrieves
} from gateway, the sensor node retrieves
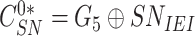 . Then the sensor node calculates
. Then the sensor node calculates
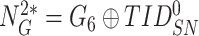 and examines the freshness of
and examines the freshness of
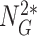 . The sensor node extracts the response from the PUF,
. The sensor node extracts the response from the PUF,
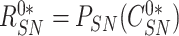 . The sensor node derives
. The sensor node derives
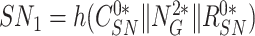 and compares
and compares
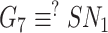 ; If authentication is successful, the sensor node determines its session key by calculating
; If authentication is successful, the sensor node determines its session key by calculating
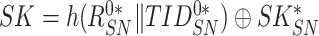 . Likewise, sensor node extracts the
. Likewise, sensor node extracts the
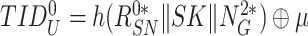 . Afterward, the sensor node generates the nonce
. Afterward, the sensor node generates the nonce
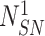 and encloses it within
and encloses it within
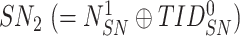 . Besides, the sensor node computes
. Besides, the sensor node computes
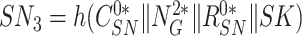 to accomplish mutual authentication with gateway and also to assure the gateway of correct
to accomplish mutual authentication with gateway and also to assure the gateway of correct
 generation. The sensor node retrieves the new challenge
generation. The sensor node retrieves the new challenge
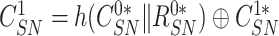 provided by the gateway to generate new temporary identity
provided by the gateway to generate new temporary identity
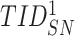 required for next future session. Once new challenge
required for next future session. Once new challenge
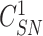 is extracted, the sensor node calculates the
is extracted, the sensor node calculates the
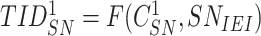 and stores the new temporary identity for future communication with gateway. At last, the sensor node composes a message {
and stores the new temporary identity for future communication with gateway. At last, the sensor node composes a message {
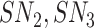 } and send it to gateway.
} and send it to gateway. -
Step 6:
Upon receiving
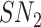 and
and
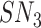 , the gateway starts the retrieval of
, the gateway starts the retrieval of
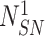 (
(
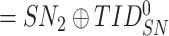 ) and verifies the freshness of
) and verifies the freshness of
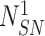 . After the nonce verification, the gateway computes,
. After the nonce verification, the gateway computes,
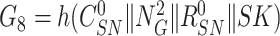 and compares,
and compares,
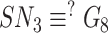 . Succeeding verification, the gateway calculates
. Succeeding verification, the gateway calculates
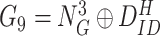 . Thereafter, gateway encloses the session key of the user within
. Thereafter, gateway encloses the session key of the user within
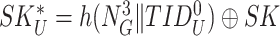 . Then the gateway calculates
. Then the gateway calculates
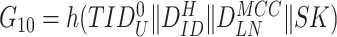 to let the user node verify the correct key generation. Post
to let the user node verify the correct key generation. Post
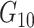 computation, the gateway selects a random new challenge
computation, the gateway selects a random new challenge
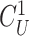 from the list of challenges
from the list of challenges
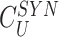 constructed during registration. Hence, the gateway encloses the new challenge within
constructed during registration. Hence, the gateway encloses the new challenge within
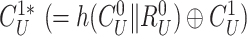 to ensure confidentiality. Finally, the gateway calculates the fresh
to ensure confidentiality. Finally, the gateway calculates the fresh
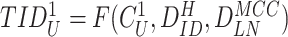 and
and
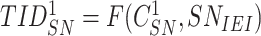 . The gateway stores the
. The gateway stores the
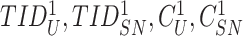 into the database. The gateway compose a message {
into the database. The gateway compose a message {
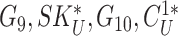 } and sends it to doctor’s device.
} and sends it to doctor’s device. -
Step 7:
The doctor’s device receives {
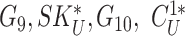 } from the gateway and retrieves the nonce
} from the gateway and retrieves the nonce
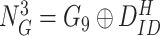 and examines its freshness. Then the device extract session key,
and examines its freshness. Then the device extract session key,
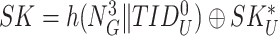 . Upon successful extraction, the device computes
. Upon successful extraction, the device computes
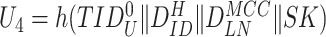 and verifies the identicalness between
and verifies the identicalness between
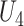 and
and
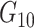 . Successful verification assures the doctor’s device of correct key generation. Finally, the device extracts the new challenge
. Successful verification assures the doctor’s device of correct key generation. Finally, the device extracts the new challenge
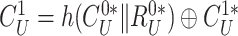 and computes the fresh
and computes the fresh
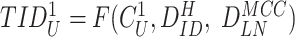 . The doctor’s device stores the
. The doctor’s device stores the
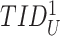 for future communication with the gateway.
for future communication with the gateway.
Fig. 4.
Lightweight and physically protected MASK establishment protocol for real time data access in IoMT networks.
Remark 3:
The gateway verifies the
and
and permits only legitimate devices to communicate. To accomplish identity anonymity and untraceability temporary identities
and
are used. Neither the challenge {
,
} nor the nonce {
,
,
,
,
} are disclosed on the public channel, therefore only authorized entities are entitled to retrieve this information. The message (
) is sent as a message digest, hence not allows the attacker to interpret and modify despite eavesdropping the
,
, and
. Moreover, the attacker cannot prepare
because he does not know
,
,
, and
. The parameter
creates an association between session key (
) and (
). Identities {
} and key (
) in the proposed protocol are reproduced after the expiry of every session.
V. Security Analysis
A. Formal Analysis
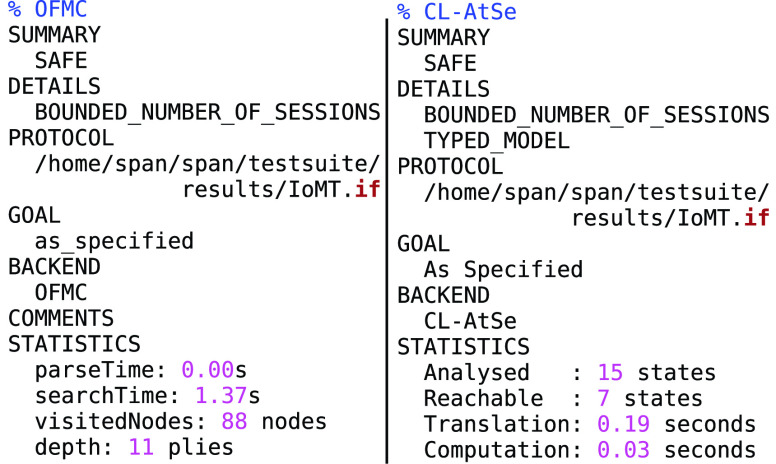
We considered the AVISPA tool [21] to examine the strength of the proposed MASK protocol. The protocol is written with the AVISPA-HLPSL script. AVISPA supports four backends, namely, “on-the-fly model-checker (OFMC),” “Constraint-Logic-based Attack Searcher (CL-AtSe),” “SAT-based model-checker (SATMC),” and “Tree Automata tool based on Automatic Approximations for the Analysis of Security Protocols (TA4SPs).” The MASK-HLPSL script contains the description of 3 primary roles, “user,” “gateway,” and “IoT node.” Besides, the environment role defines the various sessions and intruder knowledge. The goals declared in the environment role of MASK protocol are data privacy, freshness, and authentication, etc. As illustrated in Fig. 5, the OFMC backend produced the result as “safe” after visiting 88 nodes with a depth of 11 plies. Likewise, simulation of CL-AtSe took 0.19s to declare the protocol as safe. The MASK-HLPSL-IF script has been fed to other 2 backends (SATMC and TA4SP) as well, but resulted inconclusive because these backends do not support bitwise XOR operations. Therefore, the results of OFMC and CL-AtSe backends show that MASK protocol is safe from all prominent attacks, including, replay and MITM.
Fig. 5.
Results obtained from AVISPA using OFMC and CL-AtSe backend.
B. Informal Analysis
Theorem 1:
Secured from impersonation attacks.
Proof:
Consider a scenario where an attacker intercepted the message
, and
. The message contains the identity of user,
and secret key,
but enclosed secretly within
} and
{
}. It is computationally infeasible for the attacker to retrieve
and
from
and
due to collision-resistant property of hash functions [11]. Moreover, every device employing MASK protocol is integrated with unique PUF. The attacker neither know responses generated by the PUF (
,
) nor can predict [18]; therefore, the attacker cannot duplicate the identity of the user and sensor node. Hence, the protocol is protected from impersonation attacks.
Theorem 2:
Resistant to MITM attacks.
Proof:
Assuming that adversary has captured the message {
,
,
}. Now, the adversary can try to modify the message to execute MITM but will be unsuccessful to make any modifications since the information in the messages
,
, and
are processed through one-way hash function and bitwise XOR operation. The collision resistant property of hash functions [11] restrict the attacker to either predict or revive the challenge (
), response (
), identity (
), and nonce (
) values. Hence, the messages of the MASK protocol are safe from MITM attacks.
Theorem 3:
Protection against physical attacks.
Proof:
Assume that an attacker has physically captured the sensor node. The attacker aims to prepare a clone or steal information from the chip of the sensor node. The MASK protocol integrates the user device and sensor node with the PUF. Since the output of the PUF {
,
} depends upon the intrinsic physical variations in the IC, hence any attempt to tamper with the PUF would destroy the unique characteristics of the device and render the PUF useless [11]. Consequently, the protocol is safe against cloning and side-channel attacks.
Theorem 4:
Exhibits data privacy.
Proof:
Assume an adversary has captured the message
to extract the useful information.
is composed of (
) and (
); the attacker will not be able to retrieve the real nonce (
) as (
) is never disclosed openly. Similarly
,
, and
are computed using secret values and one way hash function. Therefore, the information in the message remains confidential.
Theorem 5:
Attainment of user and sensor node identity anonymity and untraceability.
Proof:
Imagine an adversary has captured the message {
} to extract the identity details (
) of the user. Despite successful capturing, the adversary can not reveal (
) since it is never used during mutual authentication and key agreement phase. During the registration phase, the gateway generates the temporary identity of the sensor node
and user device
for future correspondence. Moreover, the temporary identity is further transformed into pseudo-identity during the mutual authentication for enhanced security. The user device sends the pseudo-identity of sensor node
and itself
while communicating with the gateway. Hence, the real identities of the sensor node and user device are never disclosed, thus keeping the communication anonymous. Moreover, the temporary identities
,
,
) changes every session due to change in input challenge (
), thus ensuring untraceability of user device and sensor node.
VI. Performance and Comparative Analysis
The MASK protocol has been tested considering CM5000 TelosB mote with specifications as TI MSP430F1611 micro-controller, CC2420 RF chip, memory 1 MB, and a power source of
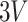 (
(
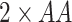 battery) [30]. The results shows that MASK protocol uses only 0.0008% of total memory space available in CM5000 TelosB mote (1 MB), whereas the schemes [10], [23], [24] require 0.036%, 0.027%, and 0.015% of the storage space, respectively. Hence, the MASK protocol needs very little storage space than the conventional protocols [10], [23], [24].
battery) [30]. The results shows that MASK protocol uses only 0.0008% of total memory space available in CM5000 TelosB mote (1 MB), whereas the schemes [10], [23], [24] require 0.036%, 0.027%, and 0.015% of the storage space, respectively. Hence, the MASK protocol needs very little storage space than the conventional protocols [10], [23], [24].
Table II shows that MASK protocol ensures data privacy, identity anonymity, untraceability, integrity, freshness, and session key security. The MASK protocol also is guarded against impersonation, modification, MITM, replay, cloning, and side-channel attacks. Meanwhile, the conventional approaches [10], [16], [21]–[25] do not guarantee data privacy and untraceability. Moreover, these schemes are also vulnerable to side-channel and cloning attacks. Also, the scheme in [18] does not protect against DoS attacks. Hence, their deployment in a hostile environment can pose threats to the entire network.
TABLE II. Comparison of MASK Protocol Versus Conventional Protocols.
 |
[10] | [16] | [18] | [21] | [22] | [23] | [24] | [25] |
 |
|---|---|---|---|---|---|---|---|---|---|
 |
✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
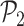 |
✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
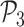 |
✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
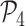 |
✔ |
 |
 |
✔ |
 |
 |
✔ |
 |
✔ |
 |
✔ |
 |
✔ | ✔ |
 |
✔ | ✔ |
 |
✔ |
 |
✔ | ✔ | ✔ |
 |
 |
✔ | ✔ | ✔ | ✔ |
 |
 |
 |
✔ |
 |
 |
 |
 |
 |
✔ |
 |
 |
 |
✔ |
 |
 |
 |
 |
 |
✔ |
 |
✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
 |
✔ |
 |
 |
✔ |
 |
 |
 |
 |
✔ |
 |
✔ | ✔ | ✔ | ✔ |
 |
 |
✔ | ✔ | ✔ |
 |
✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
 |
✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
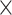 |
✔ |
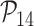 |
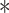 |
✔ | ✔ | ✔ | ✔ |
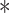 |
✔ | ✔ | ✔ |
 |
✔ |
 |
✔ |
 |
 |
✔ |
 |
 |
✔ |
 |
 |
 |
✔ | ✔ | ✔ |
 |
✔ | ✔ | ✔ |
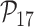 |
 |
 |
✔ |
 |
 |
 |
 |
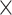 |
✔ |
Acronyms:
 : Security goals,
: Security goals,
 : MASK protocol, ✔: Secure against attack/preserves a security attribute,
: MASK protocol, ✔: Secure against attack/preserves a security attribute,
 : Vulnerable/non accomplishment of security attribute,
: Vulnerable/non accomplishment of security attribute,
 : Not applicable,
: Not applicable,
 : Replay,
: Replay,
 : Impersonation,
: Impersonation,
 : Modification of messages,
: Modification of messages,
 : DoS,
: DoS,
 : MITM,
: MITM,
 : Known key,
: Known key,
 : Cloning,
: Cloning,
 : Side-channel,
: Side-channel,
 : Mutual authentication,
: Mutual authentication,
 : Data privacy,
: Data privacy,
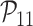 : Session key security,
: Session key security,
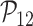 : Message integrity,
: Message integrity,
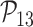 : Message freshness,
: Message freshness,
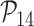 : User identity anonymity,
: User identity anonymity,
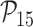 : Sensor node identity anonymity,
: Sensor node identity anonymity,
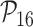 : User untraceability,
: User untraceability,
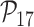 : Sensor node untraceability
: Sensor node untraceability
The TelosB mote [30] consumes 0.72
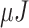 and 0.81
and 0.81
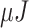 of energy [10], [3], [9] while transmitting and receiving, respectively. Table III provides the number of bits (
of energy [10], [3], [9] while transmitting and receiving, respectively. Table III provides the number of bits (
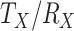 ) and the quantity of energy consumption (
) and the quantity of energy consumption (
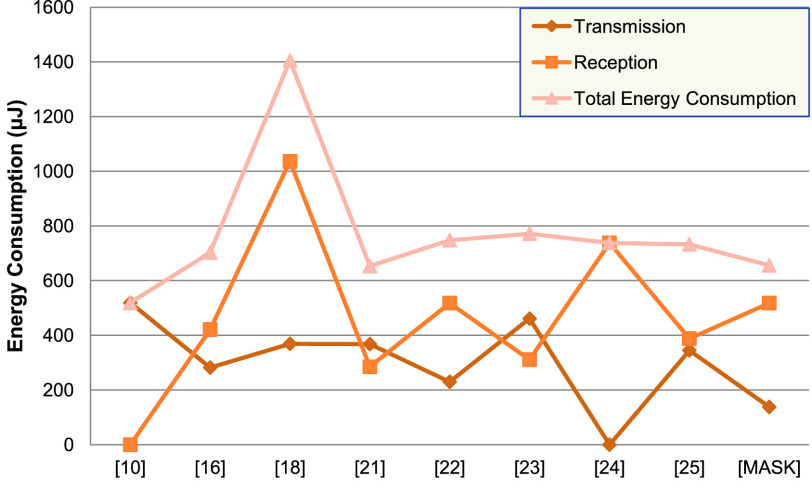
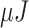 ) by a sensor node during the mutual authentication and key establishment phase. Note that the registration phase is excluded since it executes only once during network set-up. Table III shows that MASK protocol uses the resources of sensor node efficiently than the traditional approaches [16], [18], [22]–[25]. The schemes [10], [21] though they consume less energy than the proposed protocol, are insecure because these schemes neither prevent physical attacks nor ensure untraceability. Hence, the approaches [10], [16], [18], [21]–[25] in IoMT networks can result in unexpected adverse consequences. Fig. 6 depicts the amount of energy spent by a sensor node for transmission and reception during the mutual authentication and key establishment phase. It is noticeable that the MASK protocol’s sensor node consumes the least energy during transmission and affordable energy while reception. Thus, the energy-efficient characteristics of the MASK protocol makes it superior in comparison to other existing protocols.
) by a sensor node during the mutual authentication and key establishment phase. Note that the registration phase is excluded since it executes only once during network set-up. Table III shows that MASK protocol uses the resources of sensor node efficiently than the traditional approaches [16], [18], [22]–[25]. The schemes [10], [21] though they consume less energy than the proposed protocol, are insecure because these schemes neither prevent physical attacks nor ensure untraceability. Hence, the approaches [10], [16], [18], [21]–[25] in IoMT networks can result in unexpected adverse consequences. Fig. 6 depicts the amount of energy spent by a sensor node for transmission and reception during the mutual authentication and key establishment phase. It is noticeable that the MASK protocol’s sensor node consumes the least energy during transmission and affordable energy while reception. Thus, the energy-efficient characteristics of the MASK protocol makes it superior in comparison to other existing protocols.
TABLE III. Communication Cost of Sensor Node.
Fig. 6.
Energy cost comparison.
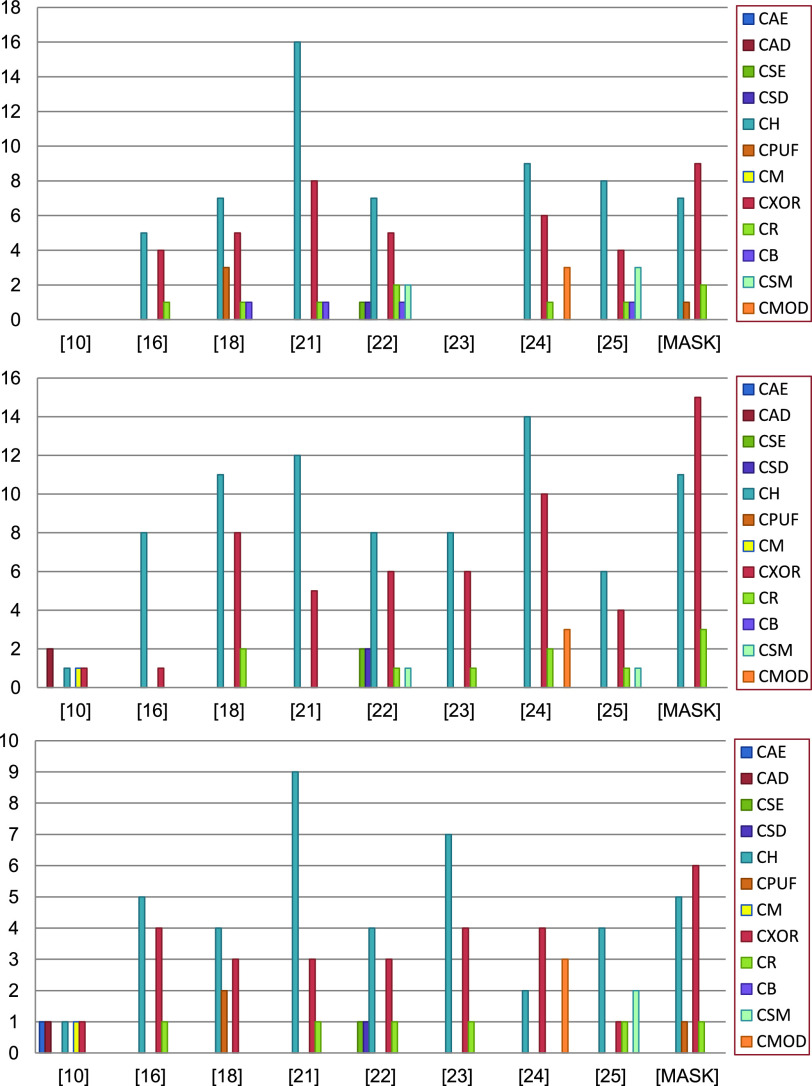
Table IV shows that the MASK protocol is computationally efficient. It employs only lightweight operations, such as hash, PUF, and XOR rather than bulky cryptography operations like asymmetric and symmetric ciphers, scalar multiplications, and fuzzy extractors. Table V compares the computation cost of the MASK and other conventional protocols during the mutual authentication and key agreement phase. The scheme proposed by Gope et al. [18] executed the PUF 5 times, whereas the MASK protocol only does it twice. Moreover, the scheme in [18] uses the fuzzy extractor to retrieve biometrics, whereas the MASK protocol does not use any biometrics. The approaches developed by Gaba et al. [10] and Li et al. [22] utilized asymmetric and symmetric ciphers that overburden the tiny processor of the sensor node. The other protocols designed by Das et al. [21], Li et al. [25], and Paliwal [24] are also computing expensive since they calculate biometrics, scalar multiplications, and modulus, respectively. Besides, the approaches in [21] and [24] also make excessive use of hash and XOR operations. The protocols [16], [23] have reasonable computation complexity. However, it is achieved at the cost of compromised security. The schemes in [16] and [23] are vulnerable to DoS, cloning, and side-channel attacks and fail to provide data privacy and sensor node untraceability. Additionally, the approaches [16], [23] are communication expensive as well. Fig. 7 demonstrates the computation cost spent by a user, gateway, and sensor node in MASK protocol and also compares it with other protocols. From Fig. 7, it is clear that the MASK protocol has attained all essential security properties with very reasonable communication and computation cost.
TABLE IV. Computation Cost of MASK Protocol.
| Phase | User Device | Gateway | Sensor Node | Total Cost |
|---|---|---|---|---|
| Registration |
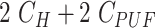 |
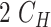 |
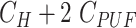 |
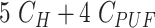 |
| Key Establishment |
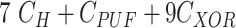 |
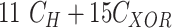 |
5
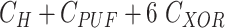
|
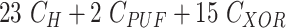 |
| Total Cost |
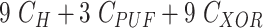 |
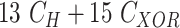 |
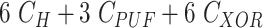 |
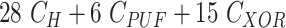 |
Acronyms:
 - Computation,
- Computation,
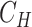 - Computation of Hash,
- Computation of Hash,
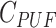 - Computation of Physically Unclonable Function,
- Computation of Physically Unclonable Function,
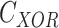 - Computation of Bit-wise XOR, Integers - defines the frequency of operation.
- Computation of Bit-wise XOR, Integers - defines the frequency of operation.
TABLE V. Computation Cost Comparison of MASK Protocol Versus Conventional Protocols.
Acronyms:
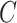 - Computation,
- Computation,
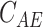 - Computation of asymmetric encryption,
- Computation of asymmetric encryption,
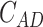 - Computation of asymmetric decryption,
- Computation of asymmetric decryption,
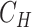 - Computation of Hash,
- Computation of Hash,
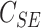 - Computation of symmetric encryption,
- Computation of symmetric encryption,
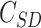 - Computation of symmetric decryption,
- Computation of symmetric decryption,
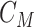 - Computation of hash based MAC,
- Computation of hash based MAC,
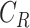 - Computation of random number,
- Computation of random number,
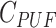 - Computation of Physically Unclonable Function,
- Computation of Physically Unclonable Function,
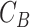 - Computation of bio-metric,
- Computation of bio-metric,
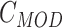 - Computation of modulus,
- Computation of modulus,
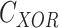 - Computation of Bit-wise XOR,
- Computation of Bit-wise XOR,
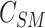 - Computation of Scalar Multiplication, Integers - defines the frequency of operation.
- Computation of Scalar Multiplication, Integers - defines the frequency of operation.
Fig. 7.
Computation cost of user (topmost), gateway (middle), and sensor node (bottom-most) of MASK protocol versus conventional protocols.
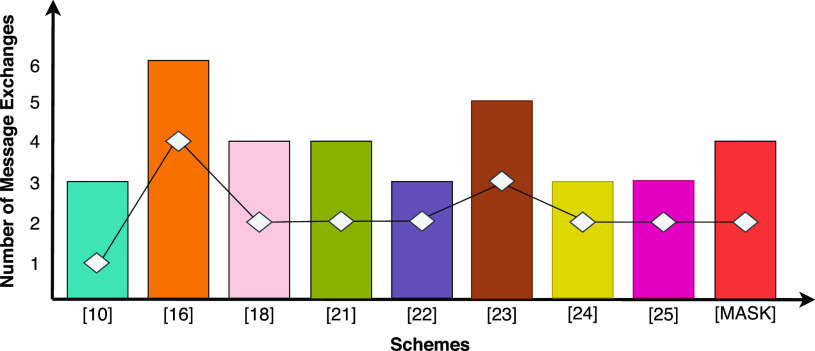
The vertical bars in Fig. 8 illustrates the total number of messages exchanged by the sensor node throughout the protocol. The diamond tag in the bar indicates the number of messages exchanged by the sensor node during the MASK establishment phase. The resource-constrained sensor node employing MASK protocol exchanges an equal number of messages as in other protocols. Hence, computation is inexpensive. The sensor nodes in the schemes [16] and [21] exchange 3 and 4 messages, respectively, which is more than the MASK protocol. The number of message exchanges is also a performance metric to select a particular application protocol because more messages lead to more delay, overhead, and energy exhaustion. Therefore, the MASK protocol is more robust and lightweight compared to the state-of-the-art protocols.
Fig. 8.
Communication cost comparison.
VII. Conclusion
This article has introduced a robust and lightweight security protocol to provide MASK establishment between doctor and sensor node. We evaluated the strength of the MASK protocol through formal and informal security analysis. The performance analysis has proven the capability of MASK protocol to protect the sensor node from physical and other prominent attacks. MASK protocol consumes only
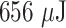 of energy and 0.0008% of tiny node memory. The comparison shows that the MASK protocol outperforms the other conventional protocols to prevent attacks, computation and communication efficiency, and so forth. In the future, the MASK protocol may be extended for those hostile environments where network devices like gateways are also subjected to physical attacks.
of energy and 0.0008% of tiny node memory. The comparison shows that the MASK protocol outperforms the other conventional protocols to prevent attacks, computation and communication efficiency, and so forth. In the future, the MASK protocol may be extended for those hostile environments where network devices like gateways are also subjected to physical attacks.
Funding Statement
This work was supported by the Deanship of Scientific Research at King Saud University, Riyadh, Saudi Arabia, through the Vice Deanship of Scientific Research Chairs: Chair of Pervasive and Mobile Computing.
Contributor Information
Mehedi Masud, Email: mmasud@tu.edu.sa.
Gurjot Singh Gaba, Email: gurjot.17023@lpu.co.in.
Salman Alqahtani, Email: salmanq@ksu.edu.sa.
Ghulam Muhammad, Email: ghulam@ksu.edu.sa.
B. B. Gupta, Email: bbgupta@nitkkr.ac.in.
Pardeep Kumar, Email: pardeep.kumar@swansea.ac.uk.
Ahmed Ghoneim, Email: ghoneim@ksu.edu.sa.
References
- [1].Lin H., Garg S., Hu J., Wang X., Md.Piran J., and Hossain M. S., “Privacy-enhanced data fusion for covid-19 applications in intelligent Internet of Medical Things,” IEEE Internet Things J., early access, Oct. 22, 2020, doi: 10.1109/JIOT.2020.3033129. [DOI] [PMC free article] [PubMed]
- [2].Hossain M. S., “Cloud-supported cyber–physical localization framework for patients monitoring,” IEEE Syst. J., vol. 11, no. 1, pp. 118–127, Mar. 2017. [Google Scholar]
- [3].Gaba G. S., Kumar G., Monga H., Kim T.-H., and Kumar P., “Robust and lightweight mutual authentication scheme in distributed smart environments,” IEEE Access, vol. 8, pp. 69722–69733, 2020. [Google Scholar]
- [4].Sun Y., Lo F. P.-W., and Lo B., “Security and privacy for the Internet of Medical Things enabled healthcare systems: A survey,” IEEE Access, vol. 7, pp. 183339–183355, 2019. [Google Scholar]
- [5].Rahman A., Hossain M. S., Alrajeh N. A., and Alsolami F., “Adversarial examples—Security threats to COVID-19 deep learning systems in medical IoT devices,” IEEE Internet Things J., early access, Aug. 3, 2020, doi: 10.1109/JIOT.2020.3013710. [DOI] [PMC free article] [PubMed]
- [6].Masud M., Hossain M. S., and Alamri A., “Data interoperability and multimedia content management in e-health systems,” IEEE Trans. Inf. Technol. Biomed., vol. 16, no. 6, pp. 1015–1023, Nov. 2012. [DOI] [PubMed] [Google Scholar]
- [7].Muhammad G., Hossain M. S., and Kumar N., “EEG-based pathology detection for home health monitoring,” IEEE J. Sel. Areas Commun., early access, Aug. 31, 2020, doi: 10.1109/JSAC.2020.3020654. [DOI]
- [8].Hossain M. S. and Muhammad G., “Emotion-aware connected healthcare big data towards 5G,” IEEE Internet Things J., vol. 5, no. 4, pp. 2399–2406, Aug. 2018. [Google Scholar]
- [9].Choudhary K., Gaba G. S., Butun I., and Kumar P., “Make–A lightweight mutual authentication and key exchange protocol for industrial Internet of Things,” Sensors, vol. 20, no. 18, p. 5166, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [10].Gaba G. S., Kumar G., Monga H., Kim T.-H., Liyanage M., and Kumar P., “Robust and lightweight key exchange (LKE) protocol for industry 4.0,” IEEE Access, vol. 8, pp. 132808–132824, 2020. [Google Scholar]
- [11].Gope P., Lee J., and Quek T. Q. S., “Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions,” IEEE Trans. Inf. Forensics Security, vol. 13, no. 11, pp. 2831–2843, Nov. 2018. [Google Scholar]
- [12].El-Latif A. A. A., Abd-El-Atty B., Hossain M. S., and Elmougy S., “Secure quantum steganography protocol for fog cloud Internet of Things,” IEEE Access, vol. 6, pp. 10332–10340, 2018. [Google Scholar]
- [13].Tseng H.-R., Jan R.-H., and Yang W., “An improved dynamic user authentication scheme for wireless sensor networks,” in Proc. IEEE GLOBECOM IEEE Global Telecommun. Conf., 2007, pp. 986–990. [Google Scholar]
- [14].Das M. L., “Two-factor user authentication in wireless sensor networks,” IEEE Trans. Wireless Commun., vol. 8, no. 3, pp. 1086–1090, Mar. 2009. [Google Scholar]
- [15].Khan M. K. and Alghathbar K., “Cryptanalysis and security improvements of ‘two-factor user authentication in wireless sensor networks,”’ Sensors, vol. 10, no. 3, pp. 2450–2459, 2010. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [16].Chang C.-C. and Le H.-D., “A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks,” IEEE Trans. Wireless Commun., vol. 15, no. 1, pp. 357–366, Jan. 2016. [Google Scholar]
- [17].Turkanović M., Brumen B., and Hölbl M., “A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion,” Ad Hoc Netw., vol. 20, pp. 96–112, Sep. 2014. [Google Scholar]
- [18].Gope P., Das A. K., Kumar N., and Cheng Y., “Lightweight and physically secure anonymous mutual authentication protocol for real-time data access in industrial wireless sensor networks,” IEEE Trans. Ind. Informat., vol. 15, no. 9, pp. 4957–4968, Sep. 2019. [Google Scholar]
- [19].Yeh H.-L., Chen T.-H., Liu P.-C., Kim T.-H., and Wei H.-W., “A secured authentication protocol for wireless sensor networks using elliptic curves cryptography,” Sensors, vol. 11, no. 5, pp. 4767–4779, 2011. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [20].Hossain M. S., Muhammad G., Md M. Rahman S., Abdul W., Alelaiwi A., and Alamri A., “Toward end-to-end biomet rics-based security for IoT infrastructure,” IEEE Wireless Commun., vol. 23, no. 5, pp. 44–51, Oct. 2016. [Google Scholar]
- [21].Das A. K., Wazid M., Kumar N., Vasilakos A. V., and Rodrigues J. J. P. C., “Biometrics-based privacy-preserving user authentication scheme for cloud-based industrial Internet of Things deployment,” IEEE Internet Things J., vol. 5, no. 6, pp. 4900–4913, Dec. 2018. [Google Scholar]
- [22].Li X., Peng J., Niu J., Wu F., Liao J., and Choo K.-K. R., “A robust and energy efficient authentication protocol for industrial Internet of Things,” IEEE Internet Things J., vol. 5, no. 3, pp. 1606–1615, Jun. 2018. [Google Scholar]
- [23].Esfahani A.et al. , “A lightweight authentication mechanism for M2M communications in industrial IoT environment,” IEEE Internet Things J., vol. 6, no. 1, pp. 288–296, Feb. 2019. [Google Scholar]
- [24].Paliwal S., “Hash-based conditional privacy preserving authentication and key exchange protocol suitable for industrial Internet of Things,” IEEE Access, vol. 7, pp. 136073–136093, 2019. [Google Scholar]
- [25].Li X., Niu J., Bhuiyan M. Z. A., Wu F., Karuppiah M., and Kumari S., “A robust ECC-based provable secure authentication protocol with privacy preserving for industrial Internet of Things,” IEEE Trans. Ind. Informat., vol. 14, no. 8, pp. 3599–3609, Aug. 2018. [Google Scholar]
- [26].Hossain M. S., Muhammad G., and Guizani N., “Explainable AI and mass surveillance system-based healthcare framework to combat COVID-I9 like pandemics,” IEEE Netw., vol. 34, no. 4, pp. 126–132, Jul./Aug. 2020. [Google Scholar]
- [27].Abdulsalam Y. and Hossain M. S., “COVID-19 networking demand: An auction-based mechanism for automated selection of edge computing services,” IEEE Trans. Netw. Sci. Eng., early access, Sep. 24, 2020, doi: 10.1109/TNSE.2020.3026637. [DOI] [PMC free article] [PubMed]
- [28].Hu L., Qiu M., Song J., Hossain M. S., and Ghoneim A., “Software defined healthcare networks,” IEEE Wireless Commun., vol. 22, no. 6, pp. 67–75, Dec. 2015. [Google Scholar]
- [29].Rahman M. A., Hossain M. S., Islam M. S., Alrajeh N. A., and Muhammad G., “Secure and provenance enhanced Internet of Health Things framework: A blockchain managed federated learning approach,” IEEE Access, vol. 8, pp. 205071–205087, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [30].Fajarado S.. (2010). CM5000 Datasheet. Accessed: Feb. 15, 2020. [Online]. Available: http://www.epssilon.cl/files/EPS5000.pdf [Google Scholar]