Abstract
Digital medical images contain important information regarding patient’s health and very useful for diagnosis. Even a small change in medical images (especially in the region of interest (ROI)) can mislead the doctors/practitioners for deciding further treatment. Therefore, the protection of the images against intentional/unintentional tampering, forgery, filtering, compression and other common signal processing attacks are mandatory. This manuscript presents a multipurpose medical image watermarking scheme to offer copyright/ownership protection, tamper detection/localization (for ROI (region of interest) and different segments of RONI (region of non-interest)), and self-recovery of the ROI with 100% reversibility. Initially, the recovery information of the host image’s ROI is compressed using LZW (Lempel-Ziv-Welch) algorithm. Afterwards, the robust watermark is embedded into the host image using a transform domain based embedding mechanism. Further, the 256-bit hash keys are generated using SHA-256 algorithm for the ROI and eight RONI regions (i.e. RONI-1 to RONI-8) of the robust watermarked image. The compressed recovery data and hash keys are combined and then embedded into the segmented RONI region of the robust watermarked image using an LSB replacement based fragile watermarking approach. Experimental results show high imperceptibility, high robustness, perfect tamper detection, significant tamper localization, and perfect recovery of the ROI (100% reversibility). The scheme doesn’t need original host or watermark information for the extraction process due to the blind nature. The relative analysis demonstrates the superiority of the proposed scheme over existing schemes.
Keywords: Medical image watermarking, Ownership verification, Tamper localization, ROI recovery, Reversibility, Blind watermarking
Introduction
Healthcare facilities are improving these days to facilitate people in a familiar way. The uses of advanced communication technologies and internet have been increased to provide healthcare services to patients. Tele-health, telemedicine and teleradiology are some of the growing fields to provide medical facilities to people without the need to go to the hospitals or clinics. Online consultations with doctors are being common and necessary (during critical times such as COVID-19 pandemic) procedures, further it also help patients to avoid travelling in general cases [4]. The availability of high speed internet and user friendly online platforms makes the sharing of digital data such as voice messages, diagnosis reports, and radiological images (i.e. CT scan, X-ray, MRI etc.) easier along with the online video consultations [30]. It is obvious that the medical images or reports are an important data in terms of deciding future actions for better results. Any modification in digital data (e.g. Medical images) due to signal processing attacks or intentional alterations by attackers can affect diagnosis process that can be hazardous for patients. Specifically, the change in the ROI part of the medical images can be more harmful [10]. Medical images are shared in the same way as the general digital images and therefore the signal or image processing attacks can affect the medical images in a similar fashion. A large number of images are shared/communicated by the people in day-to-day life. Due to easy availability and widespread use of the online medium, digital data security has been an essential and demanding research issue [2, 38]. Data security can be effectively achieved by using Data hiding techniques [20] such as steganography [21, 22], data encryption [23, 42] and digital watermarking [11]. Digital image watermarking [41] offers effective solutions to provide security to digital images against intended or accidental attacks [25, 26].
In the digital image watermarking process [19, 35], the digital information (i.e. watermark) is inserted into the digital image (i.e. host or carrier) in a well-defined algorithmic manner to provide copyright protection [24], tamper detection, proof of ownership, image authentication and restoration etc. Digital image watermarking can be categorized into different types [27]. It is classified as robust, semi-fragile and fragile watermarking based on the robustness [15]; whereas it is categorized as blind, semi-blind and non-blind watermarking based on extraction process [16]. It can also be divided into visible or invisible watermarking based on the imperceptibility of the watermark. Another classification divides the digital watermarking into spatial domain and frequency domain watermarking based on the type of domain used for the process. Generally, robust watermarking is used for copyright protection and ownership identification [32]. Fragile watermarking is preferred for tamper detection, localization and restoration of the tampered region [40]. According to the watermarking literature, frequency domain techniques are preferred for robust watermark insertion because of their effective performance against various signal processing attacks. On the other side, spatial domain approaches are mostly used for fragile watermark insertion. In all these cases, a blind mechanism does not need the original host or watermark at the time of extraction process; but the host or other side information is required for the extraction procedure in case of a non-blind approach [6]. Digital watermarking is an open, ongoing, and challenging research domain in the modern time of digital advancements and progressive teleradiological applications.
As per the literature, Coatrieux et al. [7] presented the importance of watermarking in medical field for providing security solutions such as integrity control and authentication of medical information. The manuscript discussed different scenarios to provide solutions to the security issues and requirements of the medical field with the help of digital watermarking. Chao et al. [5] proposed a non-blind data hiding method for communicating digital medical information among different hospitals securely. The method combined different types of medical data into a mark image that can be extracted by the authorized personnel at the time of extraction. Nonetheless, the scheme can’t be used for tamper localization and self-recovery purposes. Guo and Zhuang [12] introduced a watermarking scheme for the authentication and integrity verification of medical images. The scheme has lossless nature in terms of the recovery of the complete image. However, there is a limitation due to the non-blind nature of the scheme that the original watermark data such as EPR (electronic patient record) is needed for authentication purposes. Das and Kundu [8] offered a blind watermarking scheme using SHA (Secure Hash Algorithm)-256 and AES (advanced encryption standard) encryption for authentication and integrity control of medical images. The scheme has significant parametric results in terms of payload (in bits per pixel) and PSNR, nevertheless the scheme didn’t have the ability to protect copyright and recover the tampered portion of the medical image. Eswaraiah and Reddy [9] presented a fragile medical image watermarking scheme for tamper detection and ROI recovery. The scheme embedded the authentication code and the recovery information into the RONI region using an LSB replacement approach. The experimental results proved that the scheme had significant performance in terms of imperceptibility, tamper detection, and ROI recovery; but the scheme didn’t provide copyright/ownership protection.
Badshah et al. [3] proposed an LZW compression mechanism-based watermarking scheme for ultrasound medical images. The ROI information and the secret key were combined to get the watermark. This watermark was compressed using the LZW algorithm to reduce the payload. The LSB replacement was performed to embed the compressed watermark information into the RONI region. The scheme has high imperceptibility, significant ROI authentication, and ROI restoration; however, the scheme lacks in the authentication of the embedding region (i.e. RONI). Additionally, the scheme does not provide ownership verification that is an important aspect to confirm the patient’s credentials. Parah et al. [28] introduced two medical image watermarking schemes for copyright protection. The schemes were based on block-wise division and DCT transform. The scheme provided satisfactory results in terms of imperceptibility and robustness, however the ability of tamper detection and self-recovery were not achieved. Zear et al. [39] offered a robust watermarking technique for the images related to healthcare. The method used multi-level DWT (Discrete wavelet transform), DCT (Discrete cosine transform), and SVD (Singular value decomposition) for the watermarking process. During embedding, three different watermark were embedded into the host image for verifying information regarding doctor, patient’s reports and data integrity. The method reported only ownership/copyright protection. The scheme is not able to provide tamper detection and restoration, which are very essential features for medical images. Swaraja et al. [34] offered a multipurpose watermarking method for medical images for protection of copyrights/ownership, tamper detection, and the recovery of ROI. An optimization algorithm was used to select the embedding region in the RONI for inserting dual watermarks. Although the scheme has multiple features and acceptable results in terms of parametric values, it did not discuss the case of tampered RONI. In case of tampered RONI, the reliability or authenticity of the extracted data should had been investigated because the authentication and the recovery of ROI depends on the reliability of the extracted information. Alshanbari [1] recently proposed a non-blind multipurpose watermarking scheme for medical images using DWT, SVD, and LZW (Lempel-Ziv-Welch) algorithm. Although the imperceptibility is high but robustness results are marginal. Moreover, the scheme provides tamper detection and restoration only for ROI (region of interest) regions at low tampering rates. Further, the RONI has been selected as the embedding region, but the effect of the tampered embedding region (i.e. RONI) on the ROI recovery has not been discussed.
Since the intentional/unintentional manipulations usually affect the complete image (ROI and RONI) in the same manner, the possibility of modifications in the embedding region can’t be ignored. It is also an important fact that the reliability of the extracted watermark depends on the originality of the embedding region (i.e. RONI). Therefore, the authentication of both regions (ROI and RONI) is indispensable against modification due to different signal processing attacks and tampering/forgery. In the proposed work, a recently proposed robust scheme [32] and the fragile scheme [3] are merged in an improved manner to offer an effective multipurpose watermarking scheme for medical images. Due to its multipurpose nature, the scheme includes the features of robust as well as fragile watermarking. It offers copyright protection, tamper detection and localization (for ROI and RONI), and recovery of the ROI. The RONI region is divided into different segments for better tamper localization. Additionally, the scheme does not require the original host data or other side information for watermark extraction because of the blind nature of the scheme. The scheme is able to recover the ROI part (100% reversibility) in case of tampering (excluding embedding region); which can surely be beneficial in medical image watermarking. The prime contribution of the proposed work are as follows:
To the best knowledge of authors, the first-ever scheme that offers tamper detection/localization for the ROI as well as the segmented RONI regions.
Unlike many existing medical watermarking schemes, the proposed work ensures the authenticity of the embedding region (i.e. RONI), thus it increases the possibility of the ROI recovery even in case of severe tampering.
The scheme can recover the ROI with 100% reversibility even after having blind nature.
The scheme confirms that the image is not usable for further processing when the embedding region has tampered with. Thus, it alerts timely for further actions related to the patient’s health.
The scheme offers significant imperceptibility and high robustness against different attacks even after having multipurpose nature.
The successive sections present the proposed scheme, experimental results and discussion, and conclusion respectively.
Preliminaries
LZW (Lempel-Ziv-Welch) algorithm
It is a widely utilized compression algorithm presented in 1984 by Terry Welch [37]. It is lossless in nature, which means there is no data loss while compressing and decompressing the data. It has been utilized in the UNIX utility program (named as ‘compress’) for faster performance with less storage space. The image file format “GIF” (Graphics interchange format) is also based on the LZW compression algorithm. The LZW technique is structured using a table (which is known as a string table), which maps or converts the input character strings into the codes of fixed- length. This string table commonly has 4096 entries, out of which the first 256 entries are allocated for representing 8-bit characters (single bytes) from the input data. The remaining entries are used during the encoding process for the repeated sequences of input data. During the decoding process, the data of the compressed (or encoded) version is translated back into characters using the string table [3].
SHA-256 algorithm
The SHA-256 is an extensively used hash algorithm for cryptographic operations. It is a part of a set of hash functions named as SHA-2, published by NIST (National Institute of Standards and Technology) in 2001 [17, 18]. It is a one-way hash algorithm, which means that the hash key can be generated from the input data but the input data cannot be obtained from the hash key. The SHA-256 has larger digests (hash values) messages having 256-bit length. This feature helps to protect against attacks more effectively. Additionally, it can handle bigger block size of data. In SHA-256, the data is first preprocessed by padding the input data and then the padded input is partitioned into blocks. After setting the initialization values, the hash operation is performed. Finally, the 256-bit hash key (message digest) is obtained [29].
Slantlet transform
The Slantlet transform is a modified orthogonal form of DWT having superior time localization with two zero moments [31]. Instead of using the concept of filter bank iteration (as in DWT), the slantlet transform framework used diverse filters at each scale. The frequency selectivity of the filter bank is lower. This low frequency selectivity results in better time localization. Due to better time localization feature, the Slantlet transform can provide better edge representation. The Slantlet transform can be utilized for the study of piecewise linear function having discontinuities. It has better ability to model the discontinuous nature and can be used in the image processing applications for the analysis of abrupt changes, texture feature, and the detection of the edges. It is also used in denoising applications very well because it has ability to smoothen the data without compromising the edges [33, 36].
Proposed scheme
The proposed scheme comprises of watermark embedding, watermark extraction, tamper detection (ROI and RONI) and the recovery of ROI region (if found tampered) with 100% reversibility. Initially, the host image is divided into ROI and RONI regions. The ROI information is then compressed using LZW compression algorithm, to ensure less memory requirement for embedding. Next, the robust watermark is embedded into the host image using a block wise transform domain approach. Later, the hash keys are generated using SHA-256 algorithm for ROI and segmented RONI regions of robust watermarked image. Subsequently, the fragile watermark is prepared by combining compressed ROI data and hash keys. This fragile watermark is then embedded into the RONI region of the robust watermarked image using LSB replacement approach. During extraction, the robust watermark extraction is performed to verify copyright/ownership. Likewise, the fragile watermark gets extracted and separated into ROI data (i.e. compressed) and hash keys. As similar to embedding process, the hash keys are generated for ROI and RONI parts of the received watermarked image. The extracted and generated hash keys are then compared to detect tampering/forgery. If the ROI part is found tampered, then it can be recovered using the extracted ROI data (when the RONI part (used for fragile embedding) is not tampered/forged). Similarly, the segmented RONI parts are marked as tampered or not tampered based on the hash keys.
Generally, the watermarking schemes designed for medical imaging focus on the tampering detection and recovery of the ROI region only. It is because the ROI part is used for diagnosis purposes and helps the practitioners/doctors to decide future directions. However, it is important to note that accurate tampering detection and the recovery of ROI are based on the extracted data from the RONI region. If the RONI part (in which the fragile watermark had been inserted during embedding) has been tampered with, then the extracted recovery information cannot be used for the recovery of the ROI region. As it can further result in a faulty diagnosis and may risk the patient’s health. Therefore, it is also essential to authenticate the RONI region. Additionally, it would also help in dealing with attacks like fake ownership claims, etc. in the proposed scheme due to the multipurpose nature and dual watermarking approach. The following sub-sections present the proposed scheme in detail.
Embedding process
The schematic description of the proposed embedding scheme is shown in Fig. 1. At first, select the host image (512 × 512) and divide it into two parts namely ROI and RONI. Convert the pixel values of ROI (100 × 100) into the binary form and organize it in the form of a binary sequence (ROIbin). Compress ROIbinusing the LZW algorithm to obtain the compressed binary sequence (ROIcompress _ bin). Now, select the robust binary watermark WatR(32 × 32 bits) and partitioned the original host image into 8 × 8 size blocks for robust embedding. Select 1024 blocks out of 4096 blocks in a random manner using key (K1). Now, embed the 1024 robust watermark bits into the selected 1024 blocks sequentially using the following steps. Let us consider that a robust bit is br and the 8 × 8 size block is represented as B.
-
Step 1.
Apply Slantlet transform (SLT) on B to generate sub-bands LL, LH, HL and HH.
-
Step 2.
Calculate average intensity I1and I2 for sub-bands LH and HL respectively.
- Step 3.
-
Step 4.Modify LH band using the eq. (3) given as:
3 -
Step 5.Modify HL band using the eq. (4) given as:
4 (Here Pi, j denotes the coefficient value at row = i and column = j of block B)
-
Step 6.
Perform inverse Slantlet transform using the modified LH and HL band to get the watermarked block.
Fig. 1.
The proposed watermark embedding process
At last, recombine the blocks to obtain the robust watermarked image Wimg _ r. The image Wimg _ r will be used as the carrier signal (i.e. image) for fragile watermarking. To prepare the fragile watermark, generate the hash keys (i.e. 256-bit binary sequences) for ROI and RONI parts of Wimg _ r.The illustrative example to generate a 256-bit hash key for a region (e.g. ROI) is shown in Fig. 2. Likewise, the hash keys are obtained for different RONI regions. It is important to note that, the RONI region has been segmented into eight subparts (as shown in Fig. 3) for partial tamper localization. Hence, there is a different hash key for each sub-part of RONI. It would help to understand the tampering area, and confirms the authenticity of the extracted recovery data. Let Hroi denotes the hash key for the ROI of the robust watermarked imageWimg _ r. SimilarlyHroni − 1, Hroni − 2, Hroni − 3, Hroni − 4, Hroni − 5, Hroni − 6, Hroni − 7 and Hroni − 8characterize the hash keys for eight non-overlap regions of RONI. Although, one hash key is sufficient to detect tampering in the RONI part but the partitioned RONI helps to detect tampering with partial localization capability. Next, cascade the ROIcompress _ bin, Hroi, Hroni − 1, Hroni − 2, Hroni − 3 and Hroni − 4 to produce the complete fragile sequence WatF. The following steps are used to embed WatF into the robust watermarked image Wimg _ r.
-
Step 1.
Select n pixels of RONI to embed WatF. Here n is the length of fragile sequence WatF.
-
Step 2.
Convert all the pixel values into binary form.
-
Step 3.
Serially replace the first LSB of all pixels using the bit values of the fragile watermark WatF.
-
Step 4.
Convert all pixel values from binary to decimal form. Lastly, the final watermarked image Wimg _ (r + f) is obtained.
Fig. 2.
The process for generating 256-bit hash key for a region (e.g. ROI or other RONI regions)
Fig. 3.
Benefit of RONI segmentation and partial tamper localization in ROI recovery
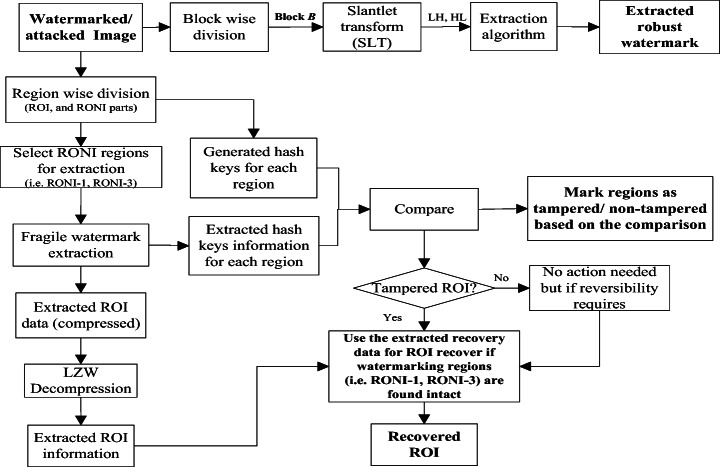
Extraction process
At the receiver-end, it is always desired that the watermarked image Wimg _ (r + f)has not been distorted by intentional/unintentional attacks. However, some common attacks may affect/modify the image and therefore the effect of these attacks on the performance of the scheme should be analysed carefully.The schematic description of the proposed extraction process is shown in Fig. 4.
Fig. 4.
The proposed watermark extraction process
Robust watermark extraction
The process of extracting the robust watermark information from the received image Wimg _ (r + f) comprises of the succeeding steps.
-
Step 1.
Divide the image Wimg _ (r + f) into 8 × 8 size non-overlapping blocks.
-
Step 2.
Select the 1024 blocks (that had been used during embedding) using key (K1).
-
Step 3.
Choose the first block out of these 1024 blocks and perform SLT transform to get LL, LH, HL, and HH sub-bands.
-
Step 4.
Calculate average intensity values I1and I2 for LH and HL sub-bands respectively.
-
Step 5.Use the eq. (5) for extracting the bit value br.
5 -
Step 6.
Repeat steps 3, 4, and 5 on each selected block to extract the total 1024 bits.
-
Step 7.
Reshape these 1024 bits to 32 × 32 size to obtain the extracted watermark (WatR _ ext).
-
2)
Fragile watermark extraction
The fragile watermark is extracted from the image Wimg _ (r + f) as follows: Firstly, separate the image into ROI and RONI regions. Afterward, select the n pixels (i.e. used for embedding) and convert them into binary form. Sequentially extract the first LSB bit concerning each pixel and get the extracted fragile sequence WatF _ ext. Now, partition the WatF _ ext sequence to get ROIcompress _ bin _ ext, Hroi _ ext,Hroni − 1 _ ext, Hroni − 2 _ ext, Hroni − 3 _ ext, Hroni − 4 _ ext,Hroni − 5 _ ext, Hroni − 6 _ ext, Hroni − 7 _ extand Hroni − 8 _ ext. Here, ROIcompress _ bin _ ext denotes the extracted ROI recovery information and Hroi _ ext denotes the 256-bit hash key for the ROI region. Hroni − 1 _ ext, Hroni − 2 _ ext, Hroni − 3 _ ext, Hroni − 4 _ ext,Hroni − 5 _ ext, Hroni − 6 _ ext, Hroni − 7 _ extand Hroni − 8 _ extrepresent the extracted hash keys for eight RONI regions.
Tamper detection and ROI recovery
Check for tampering
To detect tampering/alteration in the image Wimg _ (r + f), get the hash keys for ROI and RONI regions as similar to the embedding process. Let the generated hash keys are Hroi _ new,Hroni − 1 _ new, Hroni − 2 _ new, Hroni − 3 _ new, Hroni − 4 _ new, Hroni − 5 _ new, Hroni − 6 _ new, Hroni − 7 _ newand Hroni − 8 _ new. Finally, compare the corresponding hash keys to detect tampering. For example, if all analogous bits of Hroi _ ext and Hroi _ new are equal then it confirms that the ROI region has not been tampered with. On the other hand, even if a single bit is not similar to the analogous bit then the complete ROI region can be considered as tampered. Likewise, check the all the eight RONI regions for tampering.
-
2)
ROI recovery
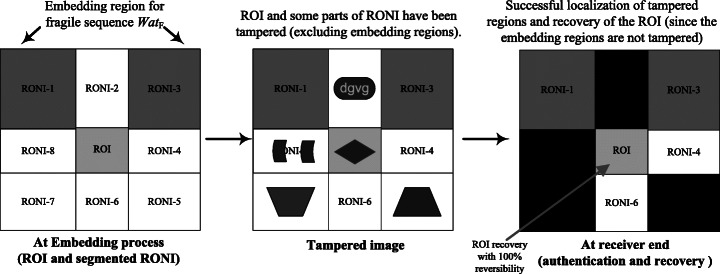
When the ROI region is found tampered, then decompress the binary sequence ROIcompress _ bin _ ext to get the sequence ROIbin _ ext. Reorganize the ROIbin _ ext by converting every eight bits into a decimal value in a sequential manner and finally reshape the data as per the size of the ROI region. This way, 100% reversibility in terms of the recovery of the ROI region can be achieved. It should be noted that before recovering ROI, the embedding RONI region (in which the recovery data were stored) should be checked carefully for tampering. The segmentation of the RONI region into eight sub-parts facilitates the tamper localization, which further helps to confirm the precision of the extracted recovery data and hash keys. Since the number of pixels (say Npixels) required for fragile embedding is equal to the length (n) of the fragile sequence WatF. Normally, the value of Npixels is relatively small as compared to the complete RONI region of the image. Hence, all segmented RONI regions would not be needed for watermarking. As shown in Fig. 3, RONI-1 and RONI-3 (only when RONI-1 is completely used for embedding) regions have been used for embedding the fragile sequence WatF. In that case, tampering in other RONI regions would not affect the extracted fragile sequence WatF _ ext. Thus, the extracted recovery information still can be used to recover the ROI region with 100% reversibility.
Results and discussion
This section presents the experimental analysis of the proposed scheme and its merits over the other existing schemes in the field of medical imaging. From the experimental point of view, 120 medical images from different databases [14] have been used to test the performance of the scheme. However, five medical images are employed to present the experimental and graphical results in this manuscript. In the experiment, the size of the host medical image is 512 × 512, and the robust binary watermark is of size 32 × 32. The size of region of interest (ROI) is 100 × 100, and the remaining part of the image is considered as region of non-interest (RONI). The RONI region is further segmented into eight parts for partial localization of tampering/forgery. The experimental observations have been performed using different watermarking parameters such as PSNR (peak signal to noise ratio), SSIM (structural similarity index), BER (bit error rate), and NC (normalized correlation) [13, 24]. Figure 5 presents the test images and their watermarked versions along with the imperceptibility results in terms of PSNR and SSIM. The robust binary watermark (32 × 32) is also shown in Fig. 4 in succeeding column with robust watermarked images.
Fig. 5.
Host and corresponding watermarked images with imperceptibility results (PSNR, SSIM) and the robust binary watermark
As presented in Fig. 5, the watermarked images are highly imperceptible in terms of PSNR, and SSIM. It confirms that the watermark embedding (robust as well as fragile) does not affect the visual quality of the image. For all the test images (120) used in the experiment, the average values of PSNR and SSIM are 40.21 and 0.9984 respectively. On the other side, 25 different attacks (as presented in the next subsection) have been used to check the robustness. The average BER and NC values are found to be 0.0155 and 0.9603 respectively. This certifies that the scheme has high imperceptibility and robustness for different type of medical images and can surely be helpful in medical image watermarking.
As discussed earlier, the schemes [3, 32] are merged in an improved manner in the proposed work to get better performance with multipurpose nature. Consequently, a comparative analysis given in Table 1 clearly justifies the superiority of the proposed work over [3, 32]. The scheme [32] has a robust nature that can be used only for the robust applications such as source/ownership verification, whereas the scheme [3] has a fragile nature, and can be used for the fragile applications only. On the other hand, the proposed scheme has can be used for both type (robust and fragile) applications effectively with added advantages of region-wise tamper localization.
Table 1.
| S. No. | Characteristics | Sinhal & Ansari [32] | Badshah et al. [3] | Proposed scheme | |
|---|---|---|---|---|---|
| 1 | Signal type | Image | Image | Image | |
| 2 | Scheme type | Robust | Fragile | Robust + Fragile | |
| 3 | Multipurpose nature | No | No | Yes | |
| 4 | PSNR (watermarked) | ~ 37 dB | ~ 51 dB | ~ 40 dB | |
| 5 | Capacity | Low (only robust watermark) | High (Only fragile watermark) | High (Robust + fragile watermark) | |
| 6 | Robustness | Yes | No | Yes | |
| 7 | Copyright/ownership verification | Yes | No | Yes | |
| 8 | Tamper detection | ROI | No | Yes | Yes |
| RONI | No | No | Yes | ||
| 9 | Region-wise Tamper localization | No | No | Yes | |
| 10 | Reversibility (for ROI) | No | Yes | Yes | |
A relative comparison with the existing medical watermarking schemes in terms of the features and parametric performance has been performed as presented in Table 2. As described in Table 2, existing medical watermarking schemes such as [3, 8, 9] have been proposed to provide tamper detection and restoration features, but they are unable to provide copyright/ownership protection. Instead, the schemes [28, 39] are unable in providing tampering detection/localization, and restoration. In [1], the multipurpose nature has been provided but it has poor results in terms of robustness. Moreover, the scheme [1] has a non-blind nature that bounds the extraction procedure as it requires additional information (e.g. original host image) for the extraction. In addition, most of the watermarking schemes (as discussed in the manuscript) used RONI as the embedding region but none of them concerned about the authentication of embedding region (i.e. RONI). Since the intentional/unintentional tampering or modification can affect any part of the image. Therefore, the authenticity of the embedding region should be examined carefully.
Table 2.
Relative comparison with existing medical watermarking schemes
| S. No. | Characteristics | Das and Kundu [8] | Eswaraiah and Reddy [9] | Badshah et al. [3] | Parah et al. [28] | Zear et al. [39] | Alshanbari [1] | Proposed scheme | |
|---|---|---|---|---|---|---|---|---|---|
| 1 | Host image type | Medical | Medical | Medical | Medical | Medical | Medical | Medical | |
| 2 | Scheme type | Fragile | Fragile | Fragile | Robust | Robust | Robust + Fragile | Robust + Fragile | |
| 3 | Embedding domain | Spatial | Spatial | Spatial | Transform | Transform | Transform + spatial | Transform + spatial | |
| 4 | Type of extraction | Blind | Blind | Blind | Blind | Non-blind | Non-blind | Blind | |
| 5 | PSNR (watermarked) | ~ 44 dB | ~ 50 dB | ~ 51 dB | ~ 41 dB | ~ 33 dB | ~ 48 dB | ~ 40 dB | |
| 6 | Capacity | High | High | High | Low | Very high | High | High | |
| 7 | Robustness | – | – | – | High | High | Poor | High | |
| 8 | Copyright/ownership verification | No | No | No | Yes | Yes | Yes | Yes | |
| 9 | Tamper detection | ROI | Yes | Yes | Yes | No | No | Yes | Yes |
| RONI | No | No | No | No | No | No | Yes | ||
| 10 | Region-wise Tamper localization | No | No | No | No | No | No | Yes | |
| 11 | Reversibility (for ROI) | No | Yes (only in case of no attack) | Yes | No | No | Yes | Yes | |
-- denotes that the mentioned characteristic is not provided
The proposed work provides an efficient multipurpose scheme with significant parametric performance and additional features. It resolves some of the existing issues in the field of medical image watermarking. The authentication of ROI as well as RONI has been provided in the proposed work. Additionally, the RONI region has been segmented into small subparts to ensure effective region-wise tamper localization. It also increases the possibility of ROI recovery even in case of severe tampering in any part of the image (except the embedding region). Further, the proposed scheme is able to alert about authenticity of the extracted data in case of the tampered embedding region. It can surely help the practitioners to take subsequent treatment related decisions. The relative analysis shows that the proposed scheme has more features with significant parametric values as compared to existing schemes, while having a blind extraction mechanism.
Robust watermarking results
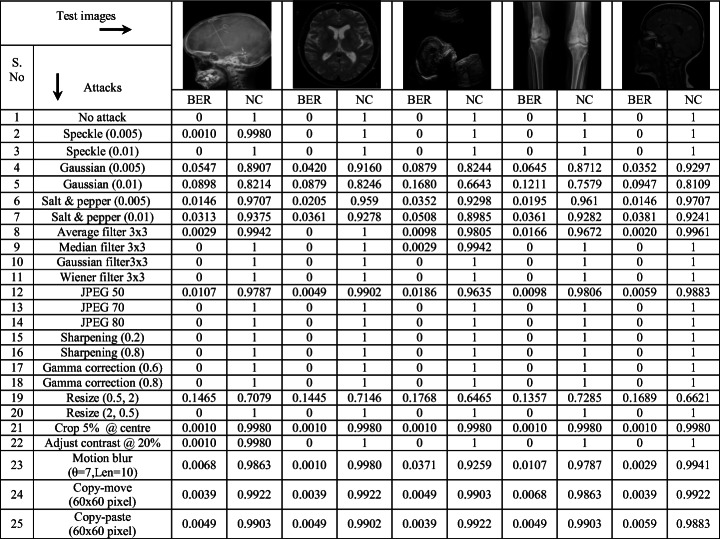
A variety of signal and image processing attacks are applied on the watermarked images before the extraction process to testify the robustness of the scheme. The embedding strength parameter α is set to 15 after thorough experimentation. It gives significant parametric features for imperceptibility and robustness simultaneously. Even though the PSNR >30 dB is considered to be good for images in the literature [3], it has been maintained at ~40 dB in the manuscript for medical images with a little compromise in robustness. The extracted watermarks are of high quality for most of the applied attacks. The obtained parametric results in terms of BER and NC are highly significant. The robustness analysis presented in Table 3 shows that the scheme can sustain different signal processing attacks effectively. Therefore, the proposed blind watermarking scheme can be used for copyright/ ownership verification.
Table 3.
Robustness analysis in terms of BER and NC for test images against different attacks
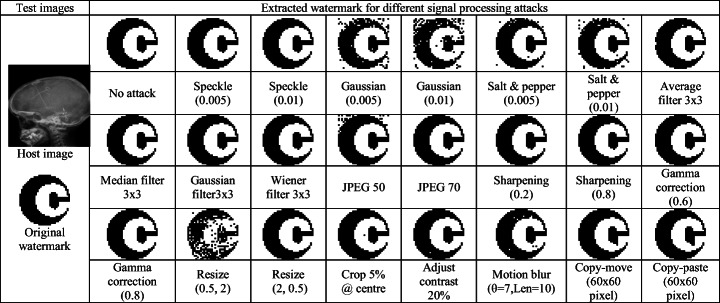
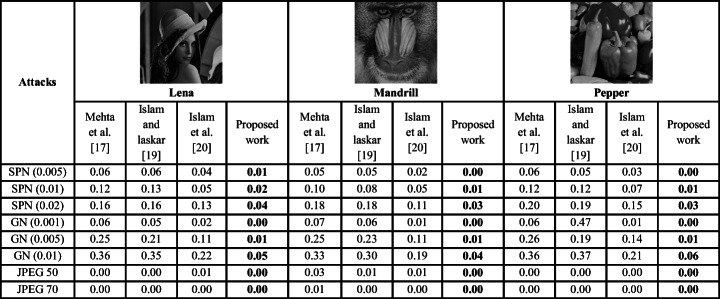
The visual results of the extracted watermark for a test image are also presented in Table 4, which confirms that the visual quality of the extracted watermarks against attacks is good enough. The robustness of the proposed scheme has also been compared with the existing robust watermarking schemes (with same payload = 1024 bits) as shown in Table 5. Some general test images like Lena, Mandrill and Pepper with size 512 × 512 are selected for comparison purpose. Here, it is observed that even after having multipurpose nature, the proposed scheme has superior robustness results for different signal processing attacks. Moreover, the visual quality is also found to be significant with average PSNR value is 39.5 dB and average SSIM value is 0.97. Thus, the proposed scheme gives similar results for different types of images and can be used even for general digital images.
Table 4.
Extracted watermark information against different attacks
Table 5.
Robustness comparison in terms of BER with existing robust watermarking schemes
Fragile watermarking results
Different tampering attacks are applied on the ROI and different parts of the RONI region to investigate the fragile nature of the proposed scheme. Further, the tamper detection and partial localization (region-wise) results are evaluated along with the recovery of the ROI region. In general, the medical image watermarking schemes embed the ROI recovery information into the RONI region, but investigate the tamper detection, and recovery of the ROI only. With no doubt, it is true that the ROI part is important for further diagnosis by the medical practitioners; but the authentication of RONI is also having importance for verifying the intactness of the extracted data. As the accurate recovery of ROI is based on accuracy of the extracted data, the authentication of RONI region becomes essential. Moreover, the ROI part is a small region as compared to the whole image. Therefore, the complete RONI region is not required for embedding the fragile watermark (recovery data + hash keys). It means that if some part of RONI got tampered even then there is a possibility of efficient extraction of embedded data. It can be possible by dividing RONI region into parts and authenticate each part individually. This way, it would be possible to localize tampered region more specifically. The proposed scheme offers authentication of ROI as well as RONI part of the image. The scheme divides RONI part into eight sub-regions for better localization of tampered area. The individual 256-bit hash key is assigned to each sub-region for authentication. Let us consider that the complete watermarked image is of size MxM, in which the ROI (100 × 100) part is (m1 : m2, n1 : n2). The remaining part of the image is considered as RONI region. In the proposed scheme, the eight sub-division of RONI are RONI-1, RONI-2, RONI-3, RONI-4, RONI-5, RONI-6, RONI-7 and RONI-8. To understand the division of RONI part mathematically, the pixel positions of the segmented RONI regions are presented as in the eq. (6).
| 6 |
Although the subdivision of RONI region is arbitrary in nature and can be customized as per the situation, yet it can be decided for optimum use of RONI part for watermarking. Thus, even if a large part of RONI (not used for fragile embedding) would be tampered, the ROI can be recovered with 100% reversibility. For the experimental evaluation, the ROI region has pixel co-ordinates (m1 : m2, n1 : n2) = (201:300, 201:300). The RONI-1 and RONI-3 have been used for fragile embedding. Therefore, if other RONI regions would be tampered, even then the lossless recovery of the tampered ROI is possible.
As shown in Table 6, different tampering attacks are applied on the test images to verify the performance of the proposed scheme. It is found that the scheme can authenticate ROI and RONI (all four regions) efficiently. The scheme can also recover ROI with 100% reversibility. The only requirement for perfect region-wise tamper detection/ localization and ROI recovery is that the embedding region (i.e. RONI-1 and RONI-3 in the manuscript) should not be tampered. Since the tampering in the embedding region can harm the data and then it cannot be used for recovery purpose. The tamper detection of the RONI with region-wise tamper localization help to authenticate the image more specifically. Additionally, it is able to provide ROI recovery even when RONI (except the embedding region) is tampered. Therefore, the tampering/forgery in the ROI and RONI regions (excluding the region used for embedding) does not interrupt the tamper detection/localization and the ROI recovery with 100% reversibility. Instead, the tampering in the RONI region (used for embedding) alerts that the extracted data has been modified and should not be used for tamper detection, localization, and the self-recovery of the ROI. Thus, the scheme can ensure the doctors/practitioners about the authenticity of the medical image in a better way. The fragile nature of the proposed watermarking framework is investigated as compared to some of the existing fragile schemes as presented in Table 7. It is observed that the fragile mechanism of the proposed framework has significant performance over already existing fragile schemes.
Table 6.
Tamper detection, region-wise localization and ROI recovery for different tampering attacks
Table 7.
The comparison of fragile nature of the proposed scheme with existing fragile watermarking schemes
| Fragile Schemes | Characteristics | |||||
|---|---|---|---|---|---|---|
| Purpose | Payload | Imperceptibility (PSNR, SSIM) | Blind nature | Tamper localization | ROI recovery | |
| Guo and Zhuang [12] | Data hiding, Image authentication, Restoration | High | ~ 57 dB | No | No | Yes |
| Das and Kundu [8] | Data hiding, Image authentication | High | ~ 44 dB | Yes | Yes | No |
| Eswaraiah and Reddy [9] | Data hiding, Image authentication, Restoration | High | ~ 50 dB | Yes |
Yes (only for ROI) |
Yes (only in case of no attack) |
| Proposed scheme (only fragile nature) | Data hiding, Image authentication, Restoration | High | ~ 57 dB | Yes | Yes | Yes |
Conclusion
This study proposed a multipurpose and blind image watermarking scheme for medical images. The multiple (robust and fragile) watermarking mechanism provide ability of copyright/ownership protection, tamper detection, region-wise tamper localization and the self-recovery of the ROI part. The robust mechanism is based on block-wise division and slantlet transform, whereas the fragile watermarking used an LSB replacement approach to embed the recovery information of ROI and the authentication keys (i.e. hash keys). The LZW lossless compression technique is used to compress the recovery data before embedding. To authenticate the ROI and different RONI regions, 256-bit hash keys are generated using SHA-256 algorithm. Both the regions (ROI and RONI) get checked for tampering to ensure the integrity of the image. It is important in terms of verifying the extracted information against any intentional/accidental modification. The RONI region is further divided into eight sub-regions to offer region-wise localization capability. The scheme is tested against different signal processing and tampering attacks. Investigational results confirm that the scheme has high robustness, significant imperceptibility, effective tamper detection/localization, and perfect ROI recovery (100% reversibility) capability. The comparison with the other medical watermarking schemes shows the omnipotence of the proposed scheme in terms of parametric results and multipurpose nature. Future work comprises of the improvement in the embedding strategy for better parametric results. The division of the RONI region into sub-regions will also be optimized for better region-wise tamper localization.
Funding
This research work was supported by Jagadish Chandra Bose Research Organisation (JCBRO).
Declarations
Conflicts of interest/competing interests
There is no conflict of interest.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Rishi Sinhal, Email: rishi.sinhal.jec@gmail.com.
Sachin Sharma, Email: sheorajsachin@gmail.com, Email: sachinsharma@jcbrolabs.org.
Irshad Ahmad Ansari, Email: irshad@iiitdmj.ac.in.
Varun Bajaj, Email: varunb@iiitdmj.ac.in.
References
- 1.Alshanbari HS (2020) Medical image watermarking for ownership & tamper detection. Multimed Tools Appl 80(11):16549–16564
- 2.Avudaiappan T, Balasubramanian R, Pandiyan SS, Saravanan M, Lakshmanaprabu SK, Shankar K. Medical image security using dual encryption with oppositional based optimization algorithm. J Med Syst. 2018;42(11):208. doi: 10.1007/s10916-018-1053-z. [DOI] [PubMed] [Google Scholar]
- 3.Badshah G, Liew SC, Zain JM, Ali M. Watermark compression in medical image watermarking using Lempel-Ziv-Welch (LZW) lossless compression technique. J Digit Imaging. 2016;29(2):216–225. doi: 10.1007/s10278-015-9822-4. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Casado-Vara R, Corchado J. Distributed e-health wide-world accounting ledger via blockchain. J Intell Fuzzy Syst. 2019;36(3):2381–2386. doi: 10.3233/JIFS-169949. [DOI] [Google Scholar]
- 5.Chao HM, Hsu CM, Miaou SG. A data-hiding technique with authentication, integration, and confidentiality for electronic patient records. IEEE Trans Inf Technol Biomed. 2002;6(1):46–53. doi: 10.1109/4233.992161. [DOI] [PubMed] [Google Scholar]
- 6.Cheung WN (2000) Digital image watermarking in spatial and transform domains. In: 2000 TENCON proceedings. Intelligent systems and Technologies for the new Millennium (cat. No. 00CH37119) (Vol. 3, pp. 374-378). IEEE.
- 7.Coatrieux G, Maître H, Sankur B, Rolland Y, Collorec R (2000) Relevance of watermarking in medical imaging. In: Proceedings 2000 IEEE EMBS international conference on information technology applications in biomedicine. ITAB-ITIS 2000. Joint meeting third IEEE EMBS international conference on information Technol. IEEE. pp. 250-255
- 8.Das S, Kundu MK. Effective management of medical information through ROI-lossless fragile image watermarking technique. Comput Methods Prog Biomed. 2013;111(3):662–675. doi: 10.1016/j.cmpb.2013.05.027. [DOI] [PubMed] [Google Scholar]
- 9.Eswaraiah R, Sreenivasa Reddy E. Medical image watermarking technique for accurate tamper detection in ROI and exact recovery of ROI. Int J Telemed Appl. 2014;2014:1–10. doi: 10.1155/2014/984646. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Giakoumaki A, Pavlopoulos S, Koutsouris D. Secure and efficient health data management through multiple watermarking on medical images. Med Biol Eng Comput. 2006;44(8):619–631. doi: 10.1007/s11517-006-0081-x. [DOI] [PubMed] [Google Scholar]
- 11.Gong LH, Tian C, Zou WP, Zhou NR. Robust and imperceptible watermarking scheme based on canny edge detection and SVD in the contourlet domain. Multimed Tools Appl. 2021;80(1):439–461. doi: 10.1007/s11042-020-09677-w. [DOI] [Google Scholar]
- 12.Guo X, Zhuang TG. A region-based lossless watermarking scheme for enhancing security of medical data. J Digit Imaging. 2009;22(1):53–64. doi: 10.1007/s10278-007-9043-6. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 13.Hore A, Ziou D (2010) Image quality metrics: PSNR vs. SSIM. In 2010 20th international conference on pattern recognition. IEEE. pp. 2366-2369
- 14.“Image databases,” Accessed Sep. 2020. [Online]. Available: http://www.imageprocessingplace.com/root_files_V3/
- 15.Islam M, Laskar RH. Geometric distortion correction based robust watermarking scheme in LWT-SVD domain with digital watermark extraction using SVM. Multimed Tools Appl. 2018;77(11):14407–14434. doi: 10.1007/s11042-017-5035-9. [DOI] [Google Scholar]
- 16.Islam M, Roy A, Laskar RH. SVM-based robust image watermarking technique in LWT domain using different sub-bands. Neural Comput & Applic. 2020;32(5):1379–1403. doi: 10.1007/s00521-018-3647-2. [DOI] [Google Scholar]
- 17.Jeong C, Kim Y (2014) Implementation of efficient SHA-256 hash algorithm for secure vehicle communication using FPGA. In: 2014 international SoC design conference (ISOCC). IEEE. pp. 224-225
- 18.Kammoun M, Elleuchi M, Abid M, BenSaleh MS (2020) FPGA-based implementation of the SHA-256 hash algorithm. In 2020 IEEE international conference on Design & Test of Integrated Micro & Nano-Systems (DTS). IEEE. pp. 1-6
- 19.Lai CC, Tsai CC. Digital image watermarking using discrete wavelet transform and singular value decomposition. IEEE Trans Instrum Meas. 2010;59(11):3060–3063. doi: 10.1109/TIM.2010.2066770. [DOI] [Google Scholar]
- 20.Liao X, Li K, Yin J. Separable data hiding in encrypted image based on compressive sensing and discrete fourier transform. Multimed Tools Appl. 2017;76(20):20739–20753. doi: 10.1007/s11042-016-3971-4. [DOI] [Google Scholar]
- 21.Liao X, Guo S, Yin J, Wang H, Li X, Sangaiah AK. New cubic reference table based image steganography. Multimed Tools Appl. 2018;77(8):10033–10050. doi: 10.1007/s11042-017-4946-9. [DOI] [Google Scholar]
- 22.Liao X, Yin J, Chen M, Qin Z (2020) Adaptive payload distribution in multiple images steganography based on image texture features. IEEE Trans Dependable Secure Comput:1. 10.1109/TDSC.2020.3004708
- 23.Luo AW, Gong LH, Zhou NR, Zou WP. Adaptive and blind watermarking scheme based on optimal SVD blocks selection. Multimed Tools Appl. 2020;79(1):243–261. doi: 10.1007/s11042-019-08074-2. [DOI] [Google Scholar]
- 24.Mehta R, Rajpal N, Vishwakarma VP. LWT-QR decomposition based robust and efficient image watermarking scheme using Lagrangian SVR. Multimed Tools Appl. 2016;75(7):4129–4150. doi: 10.1007/s11042-015-3084-5. [DOI] [Google Scholar]
- 25.Mousavi SM, Naghsh A, Abu-Bakar SAR. Watermarking techniques used in medical images: a survey. J Digit Imaging. 2014;27(6):714–729. doi: 10.1007/s10278-014-9700-5. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Navas KA, Sasikumar M (2007) Survey of medical image watermarking algorithms. In: Proc. Internation Conf. Sciences of electronics, Technologies of Information and Telecommunications (pp. 25-29).
- 27.Panchal UH, Srivastava R (2015) A comprehensive survey on digital image watermarking techniques. In: 2015 fifth international conference on communication systems and network technologies. IEEE. pp. 591-595
- 28.Parah SA, Sheikh JA, Ahad F, Loan NA, Bhat GM. Information hiding in medical images: a robust medical image watermarking system for E-healthcare. Multimed Tools Appl. 2017;76(8):10599–10633. doi: 10.1007/s11042-015-3127-y. [DOI] [Google Scholar]
- 29.Rachmawati D, Tarigan JT, Ginting ABC (2018, March) A comparative study of message digest 5 (MD5) and SHA256 algorithm. J Phys Conf Ser 978(1):012116 IOP publishing
- 30.Ray PP, Dash D, De D. Edge computing for internet of things: a survey, e-healthcare case study and future direction. J Netw Comput Appl. 2019;140:1–22. doi: 10.1016/j.jnca.2019.05.005. [DOI] [Google Scholar]
- 31.Selesnick IW. The slantlet transform. IEEE Trans Signal Process. 1999;47(5):1304–1313. doi: 10.1109/78.757218. [DOI] [Google Scholar]
- 32.Sinhal R, Ansari IA (2020) A source and ownership identification framework for Mobile-based messenger applications. In: Pant M, Sharma T, Verma O, Singla R, Sikander A (eds) Soft computing: theories and applications. Advances in Intelligent Systems and Computing, vol 1053. Springer, Singapore. 10.1007/978-981-15-0751-9_89
- 33.Sinhal R, Ansari IA, Jain DK. Real-time watermark reconstruction for the identification of source information based on deep neural network. J Real-Time Image Proc. 2020;17(6):2077–2095. doi: 10.1007/s11554-019-00937-z. [DOI] [Google Scholar]
- 34.Swaraja K, Meenakshi K, Kora P. An optimized blind dual medical image watermarking framework for tamper localization and content authentication in secured telemedicine. Biomed Signal Process Control. 2020;55:101665. doi: 10.1016/j.bspc.2019.101665. [DOI] [Google Scholar]
- 35.Tang CW, Hang HM. A feature-based robust digital image watermarking scheme. IEEE Trans Signal Process. 2003;51(4):950–959. doi: 10.1109/TSP.2003.809367. [DOI] [Google Scholar]
- 36.Thabit R, Khoo BE. Robust reversible watermarking scheme using Slantlet transform matrix. J Syst Softw. 2014;88:74–86. doi: 10.1016/j.jss.2013.09.033. [DOI] [Google Scholar]
- 37.Welch TA. A technique for high-performance data compression. Computer. 1984;17(06):8–19. doi: 10.1109/MC.1984.1659158. [DOI] [Google Scholar]
- 38.Zain J, Clarke M (2005) Security in telemedicine: issues in watermarking medical images. Sciences of Electronic, Technologies of Information and Telecommunications, Tunisia.
- 39.Zear A, Singh AK, Kumar P. A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimed Tools Appl. 2018;77(4):4863–4882. doi: 10.1007/s11042-016-3862-8. [DOI] [Google Scholar]
- 40.Zhang X, Wang S. Fragile watermarking with error-free restoration capability. IEEE Trans Multimedia. 2008;10(8):1490–1499. doi: 10.1109/TMM.2008.2007334. [DOI] [Google Scholar]
- 41.Zhou NR, Hou WMX, Wen RH, Zou WP. Imperceptible digital watermarking scheme in multiple transform domains. Multimed Tools Appl. 2018;77(23):30251–30267. doi: 10.1007/s11042-018-6128-9. [DOI] [Google Scholar]
- 42.Zhou NR, Luo AW, Zou WP. Secure and robust watermark scheme based on multiple transforms and particle swarm optimization algorithm. Multimed Tools Appl. 2019;78(2):2507–2523. doi: 10.1007/s11042-018-6322-9. [DOI] [Google Scholar]