Abstract
As the COVID-19 pandemic expanded over the globe, governments implemented a series of technological measures to prevent the disease's spread. The development of the COVID Tracing Application (CTA) was one of these measures. In this study, we employed bibliometric and topic-based content analysis to determine the most significant entities and research topics. Additionally, we identified significant privacy concerns posed by CTAs, which gather, store, and analyze data in partnership with large technology corporations using proximity measurement technologies, artificial intelligence, and blockchain. We examined a series of key privacy threats identified in our study. These privacy risks include anti-democratic and discriminatory behaviors, politicization of care, derogation of human rights, techno governance, citizen distrust and refusal to adopt, citizen surveillance, and mandatory legislation of the apps' installation. Finally, sixteen research gaps were identified. Then, based on the identified theoretical gaps, we recommended fourteen prospective study strands. Theoretically, this study contributes to the growing body of knowledge about the privacy of mobile health applications that are embedded with cutting-edge technologies and are employed during global pandemics.
Keywords: Privacy, Ethics, Covid, Tracing apps, Surveillance, Proximity measurement
1. Introduction
Throughout history, the use of innovative technical methods has prevented public health disasters. Historically, contact tracing was one of the most promising methods; it was initially handled manually through interviews with infected individuals, followed by phone calls to identified individuals' connections to inform them of the condition [1]. Nonetheless, a number of challenges, including labor-intensive procedures, long response times, and the need for human intelligence, have fueled the development of digital solutions [2]. Furthermore, manual procedures were insufficient in situations where people were in close proximity to strangers. The popularity of mobile phones, combined with their ability to track short-range communication and the connections of their owners, facilitated the development of algorithms for immediate contact tracing in conjunction with digital proxies. Historically, digital proximity measurement tools, such as Bluetooth, Radio Frequency Identification Device (RFID), 5G, and Internet of Things, have been widely used in infectious disease surveillance [3].
COVID-19 was the most recent pandemic that afflicted billions of people worldwide. The disease has been widely dubbed the greatest threat to humanity since World War II and the worst global health disaster of the century. COVID-19's increasing prevalence endangers public health, the economy, the environment, and society. The COVID-19 outbreak prompted some governments to build mobile-based proximity measurement applications to alert people in proximity to the infected population and to identify the infected population [[4], [5], [6]].
Prior research has revealed that, if widely adopted by citizens, CTA could be effective in combating the spread of COVID-19 [7]. Previous research concludes that the adoption of CTAs may be hampered by ethical concerns [8,9] and new forms of surveillance and monitoring by governments and corporations collaborating with governments [10,11]. According to prior findings, automatic contact tracing systems exacerbate privacy vulnerabilities by collecting sensitive personal data [12,13] and creating persistent and vulnerable records of individuals' health, movements, and social contacts [14]. Previously, the definition of privacy has been called into question following scandals involving major technology companies, such as the Apple location tracking scandal [15]. There is mounting evidence that digital contact tracing was insufficient in the aftermath of the epidemic, emphasizing its short-term nature as a technical solution [16]. Simultaneously, there are questions about whether these data will be shared with other government agencies or technology firms for commercial or national surveillance purposes. As a result, experts like [13] advocate addressing a number of privacy-related concerns in order to determine whether a contact-tracing application is ethically justified.
CTAs have been a popular scholarly topic, and a number of studies have been carried out to conduct systematic literature reviews or bibliometric analyses of scientific endeavors examining CTAs. In these studies, the CTA has been reviewed in broad strokes. Prior research is also carried out, either through bibliometric analysis or qualitative systematic reviews of the literature. We distinguished ourselves from previous bibliometric or review studies of CTAs such as [6,17,18] by focusing solely on the privacy aspect of CTAs in order to elucidate the historical scientific research on the privacy aspect of CTAs. In addition, to supplement the findings from both methodologies, we combined bibliometric and topic-based content analysis. We evaluated papers quantitatively utilizing co-citation analysis and keyword co-occurrence analysis, two commonly used bibliometric analysis techniques, and qualitatively using the topic-based content analysis methodology. Using bibliometric analysis, we identified a set of scholarly topics and then conducted content analysis on the most relevant documents for each topic. The bibliometric methodology entails the examination of a subject's corpus of literature as well as the evaluation of highly cited publications, nations, institutions, and sources [19]. As a result, our work addresses the following issues:
-
1
Which documents, sources, and authors have received the most citations in research on the privacy implications of CTAs?
-
2
What are the most common research topics concerning CTA privacy?
-
3
What are the most concerning privacy consequences of CTAs?
-
4
What gaps in the literature exist, and what are the future research agendas?
This study may help health practitioners, governments, developers, and researchers focus on the most serious privacy concerns associated with mobile applications designed to manage global pandemics using proximity measurement technologies. In practice, the goal of this paper is to expose privacy vulnerabilities so that monitoring technologies can be developed in accordance with privacy-preserving principles and public authorities can enact appropriate privacy protection regulations to prevent any potential breach. Theoretically, this paper will add to the existing literature on digital health ethics, specifically the privacy of digital mobile health applications and proximity-measuring technologies in the event of a worldwide pandemic.
The paper is structured as follows: We commence by delving into the study's research methods. The next part discusses the findings, beginning with a descriptive analysis of the documents evaluated in this study. The remainder of this paper is organized around the research questions posed by our study. We start by explaining the results of our co-citation study, followed by a keyword co-occurrence analysis that identified nine scientific topics. We delved deeply into each topic by conducting a topic-based content analysis. The combination of co-occurrence analysis and content analysis enabled us to identify the most stressing privacy repercussions of CTAs, which is described in the following section. We conclude the paper with an analysis and conclusion section in which we examine the study's findings, limitations, and prospective future research directions.
2. Research methodology
On July 30, 2021, we collected data from the Scopus database. We set no time constraints. We searched for the terms “COVID-19″ OR “corona” OR “pandemic” AND “contact tracing” AND “privacy” in the title, abstract, and keyword sections. We added the broad keyword “contact tracing” to emphasize the primary functionality of mobile applications that incorporate proximity measurement, artificial intelligence, and other digital technologies. CTAs are known by a variety of names, including “contact surveillance applications” [20], “COVID-19 App” [21] or “digital proximity tracing app” [22]. Since the COVID-19 pandemic started in November 2019, we chose 2020–2021 as the timeframe. We imposed no restrictions other than the language, which was limited to English-language papers. Because CTA privacy is an interdisciplinary scientific subject, we considered all fields in our research. Furthermore, we covered all types of publications. The search yielded 339 results. The titles and abstracts of the publications were screened for relevance and duplication. Any article that did not specifically target CTAs was removed. These findings were independently verified by three researchers. The co-authors repeated this procedure three times. The Kappa value was 0.872, indicating a high level of coding reliability. The Kappa value, which ranges from 1 to 0, indicates the degree of agreement among the authors who coded the papers. A value of one indicates that the document should be included, while a value of zero indicates that it should be excluded. Finally, ten papers were dropped. We randomly selected 11 more papers with the highest relevance to the topic for content analysis.
We conducted descriptive, bibliometric, and content-based analyses in this study. We performed a co-citation analysis of documents to address the study's first inquiry. We utilized keyword co-occurrence analysis and qualitative content analysis of topics to discuss the remaining questions. Co-citation analysis, as one of the most commonly used methods of bibliometric analysis, attempts to answer the following question: which institutions, authors, and documents are most frequently cited in a specific body of literature [23]? Keyword co-occurrence analysis also intends to identify the most common keywords, and thus the most popular research topics pursued by researchers [24,25]. To supplement the findings of the co-occurrence analysis, a method known as topic-based content analysis was used to examine the contents of documents that were most relevant to each topic [26]. We incorporated the VOSviewer software and the Biblioshiny R software library. We visualized social networks by calculating their Total Link of Strength (TLS), which takes into account both the number of connections an object has with other objects and the strength of those connections [27]. To classify components such as keywords based on the strength of their associations, the Association Strength normalization technique was used. The Association Strength metric is the best option for normalizing co-occurrence data [28]. We supplemented our quantitative research with a qualitative content analysis of the publications that contained the most relevant information about each topic [29]. This mixed-methods study improved our quantitative analysis, allowing us to conduct gap analysis and identify future research areas more efficiently.
3. Results
The results section is divided into two sections. The first section is a descriptive study of articles relevant to the privacy of CTAs. We next outline co-citation analysis in order to address the study's first inquiry, followed by co-occurrence and content analysis of topics to address the study's remaining inquiries.
3.1. Descriptive analysis of documents
We have provided a descriptive analysis of the publications analyzed in this section of the paper. Between 2020 and 2021, the annual growth rate of scientific production climbed by 60.63%: 126 papers were published in 2020, and this number expanded to 203 papers in 2021. As shown in Table 1 , the majority of papers are in the fields of medicine, computer science, social sciences, and engineering. Additionally, the publications are predominantly affiliated with the University of Melbourne, King's College London, and the University of Oxford. The majority of papers are also published as articles. The European Union's Horizon 2020 Framework Program, the Korean National Research Foundation, the National Institutes of Health, and the US National Science Foundation also sponsor the majority of studies.
Table 1.
Descriptive analysis of documents.
| Entity | Percentage | Entity | Percentage | ||
|---|---|---|---|---|---|
| Subject Area | Medicine | 40.8 | Affiliation | University of Melbourne | 3.3 |
| Computer Science | 34.7 | King's College London | 2.4 | ||
| Social Sciences | 27.5 | University of Oxford | 2.4 | ||
| Engineering | 15 | Imperial College London | 2 | ||
| Arts and Humanities | 6.3 | University of Toronto | 2 | ||
| Multidisciplinary | 6.3 | University College London | 2 | ||
| Business, Management and Accounting | 6 | Seoul National University | 1.8 | ||
| Decision Sciences | 6 | University of Oxford Medical Sciences Division | 1.5 | ||
| Biochemistry, Genetics and Molecular Biology | 4.5 | Universität Zürich | 1.5 | ||
| Health Professions | 4.5 | University of Bristol | 1.5 | ||
| Materials Science | 4.2 | ETH Zürich | 1.5 | ||
| Nursing | 3.3 | Universiteit Gent | 1.5 | ||
| Mathematics | 2.7 | The Royal Institute of Technology KTH | 1.2 | ||
| Psychology | 2.7 | Université McGill | 1.2 | ||
| Environmental Science | 2.4 | University of Pennsylvania | 1.2 | ||
| Physics and Astronomy | 2.4 | Universitetet i Oslo | 1.2 | ||
| Chemistry | 1.5 | Università degli Studi di Torino | 1.2 | ||
| Funding sponsor | Horizon 2020 Framework Programme | 3.6 | Stanford University | 1.2 | |
| National Research Foundation of Korea | 2 | King Saud University | 1.2 | ||
| National Institutes of Health | 1.8 | Radboud Universiteit | 1.2 | ||
| National Science Foundation | 1.8 | Massachusetts Institute of Technology | 1.2 | ||
| European Research Council | 1.5 | London School of Hygiene & Tropical Medicine | 1.2 | ||
| Horizon 2020 | 1.5 | Interuniversity Micro-Electronics Center at Leuven | 1.2 | ||
| Norges Forskningsråd | 1.5 | European Commission Joint Research Centre | 1.2 | ||
| Entity | Description | Results | Entity | Description | Results |
|---|---|---|---|---|---|
| Main Information about data | Timespan | 2020:2021 | Document Content | Keywords Plus (ID) | 1357 |
| Sources (Journals, Books, etc.) | 202 | Author's Keywords (DE) | 773 | ||
| Documents | 329 | Authors | Authors | 1295 | |
| Average years from publication | 1.38 | Author Appearances | 1472 | ||
| Average citations per documents | 11.42 | Authors of single-authored documents | 43 | ||
| Average citations per year per doc | 4.198 | Authors of multi-authored documents | 1252 | ||
| References | 15,152 | Document Type | Article | 247 | |
| Authors | Single-authored documents | 44 | Editorial | 2 | |
| Documents per Author | 0.256 | Letter | 7 | ||
| Authors per Document | 3.91 | Note | 18 | ||
| Co-Authors per Documents | 4.45 | Review | 54 | ||
| Collaboration Index | 4.36 | Short survey | 1 |
As illustrated in Fig. 1 , there is a significant degree of collaboration among European nations, many of which have strong ties to the United States and Australia. On the other hand, China has a limited amount of international cooperation with Australia, Europe, and the United States. Additionally, Canada maintains a minimal level of communication with a number of European and American countries.
Fig. 1.
Country collaboration map.
3.2. Co-citation analysis
In this section of the paper, we report on the co-citation analysis we conducted on documents, sources, and authors to address the study's first question: Which documents, sources, and authors have garnered the most citations in research on the privacy implications of CTAs? The social networks were then depicted based on their total link strength.
3.2.1. Co-citation analysis of documents
The co-citation analysis of documents reveals that the themes of “acceptability,” “privacy preservation,” “motivations to use,” “data protection,” and " ethics norms” obtained the most citations and had the strongest link strength. This analysis demonstrates the importance of public adoption of CTAs, as well as public concern over personal data and the need for privacy-preserving solutions. As illustrated in Fig. 2 , the top five documents with the highest total link strength and citations are as follows:
-
1
Altmann, Samuel, Luke Milsom, Hannah Zillessen, Raffaele Blasone, Frederic Gerdon, Ruben Bach, Frauke Kreuter, Daniele Nosenzo, Séverine Toussaert, and Johannes Abeler. “Acceptability of app-based contact tracing for COVID-19: Cross-country survey study.” JMIR mHealth and uHealth 8, no. 8 (2020): e19857
-
2
Yasaka, Tyler M., Brandon M. Lehrich, and Ronald Sahyouni. “Peer-to-peer contact tracing: development of a privacy-preserving smartphone app.” JMIR mHealth and uHealth 8, no. 4 (2020): e18936
-
3
Kaspar, Kai. “Motivations for social distancing and app use as complementary measures to combat the COVID-19 pandemic: quantitative survey study.” Journal of medical Internet research 22, no. 8 (2020): e21613
-
4
Abeler, Johannes, Matthias Bäcker, Ulf Buermeyer, and Hannah Zillessen. “COVID-19 contact tracing and data protection can go together.” JMIR mHealth and uHealth 8, no. 4 (2020): e1935
-
5
Morley, Jessica, Josh Cowls, Mariarosaria Taddeo, and Luciano Floridi. “Ethical guidelines for CTAs"(2020): 29-31
Fig. 2.
Visualization of co-citation analysis of documents based on their TLS score.
3.2.2. Co-citation analysis of sources
According to the sources analyzed, JMIR mhealth and Uhealth published 17% of the articles, followed by IEEE access and Journal of Medical Internet Research, which each published 11% of the articles. Moreover, PLOS One published 8% of the publications. JMIR public health and surveillance, IEEE Internet of Things Journal, Scientific Reports, Ethics and Information Technology, and European Journal of Information Systems are additional sources that have published papers at rates of 5% and 4%. Furthermore, Fig. 4 displays the evolution of sources' scientific productivity from 2020 to 2021. As illustrated in the figure, six of the top ten sources have increased their publication of articles on this subject. The h-index analysis also reveals that the top five sources with the highest h-index are JMIR mHealth and uHealth (h-index of 9), Journal of Medical Internet Research (h-index of 7), IEEE Access and PLOS One (h-index of 6), and European Journal of Information Systems and JMIR mHealth and Surveillance (h-index of 6) (H-index of 4). Co-citation analysis of sources (Fig. 3 ) also revealed that Science has the highest TLS score, followed by IEEE Access. Furthermore, PlOS One, JMIR mHealth, uHealth, and Lancent have the greatest TLS scores.
Fig. 4.
The evolution of sources' publications on the privacy of CTAs over time.
Fig. 3.
Visualization of the co-citation analysis of sources based on their TLS score.
3.2.3. Co-citation analysis of authors
There are six clusters of researchers focusing on the privacy of CTAs, as shown in Fig. 5 . Cluster 1 is shown on the right side of the figure, Fretti Luca; Kendall, Michelle; Nurtay, Anel; and Fraser Christophe are all from the University of Oxford's Big Data Institute. They contend in their study published in Science that quantification of SARS-CoV-2 transmission suggests that managing the outbreak would be more effective with digital contact tracing and reducing ethical challenges to enhance the uptake of these technical solutions. There is a dense cluster of three authors, Hyunghoon Cho (Broad Institute of MIT and Harvard), Daphne Ippolito (University of Pennsylvania), and Yun William Yu (University of Toronto), at the top of the figure. In their study, they discuss solutions to minimize privacy concerns while maintaining the efficiency of these applications for improved public health management. The other cluster at the top is composed of two authors, Ramesh Raskar and Praneeth Vepakomma from MIT Media Lab, who have offered various privacy preserving solutions such as differential privacy. At the upper left, a cluster includes Samuel Brack and Björn Scheuermann of Humboldt-Universität Berlin and Leibniz Universität Hannover, respectively. Likewise, these researchers have offered methods for ensuring the privacy of CTAs. At the bottom of the figure is a dense cluster of authors, including Nadeem Ahmed, Regio Michelin, Wanli Xue, Sushmita Ruj, and Salil Kanhere, all from Cyber Security Cooperative Research Center, University of New South Wales. They conducted a thorough technical analysis of the characteristics and privacy risks associated with CTAs.
Fig. 5.
Visualization of co-citation analysis of authors based on their TLS score.
4. Co-occurrence analysis of keywords and content analysis of topics
4.1. Content analysis of topics
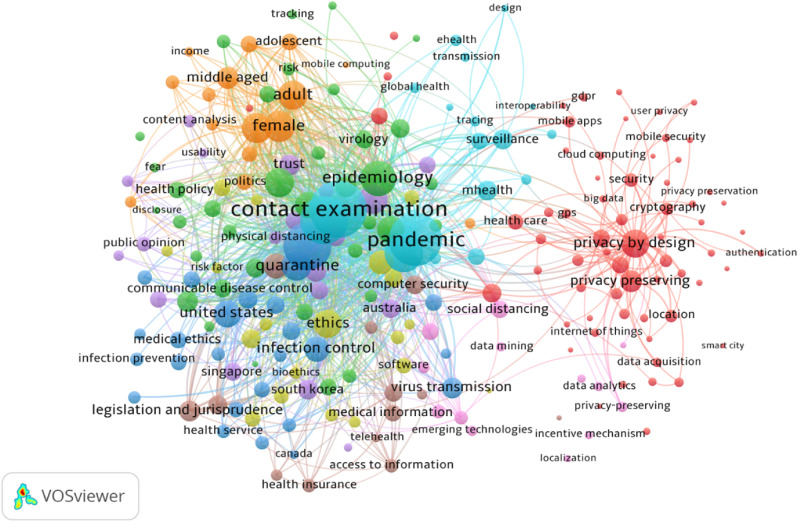
As demonstrated in Fig. 6, Fig. 7 , this phase of the study resulted in the identification of nine important topics. To show the network, we set the normalization method to the default and most popular option of “association strength,” which allows for the categorization of more closely related keywords into a single topic [27]. The authors manually selected publications with the greatest relevance to each topic for content analysis. These analyses enabled us to respond to the study's remaining research concerns. As Fig. 6 shows, there were some overlaps between topics, mainly topics at the left side of the network, which is a common pattern in this methodology [30].
Fig. 6.
Network visualization of co-occurrence analysis of keywords, which yielded 9 hot scholarly topics.
Fig. 7.
Conceptual Structure of research on privacy of CTAs.
Topic 1: Proximity measurement technologies embedded in tracing apps and varied privacy challenges.
We live in an era of tremendous technological growth, and some of these advancements are utilized to determine proximity. When the COVID-19 pandemic ravaged the world, social separation of 1.5 m was recommended to minimize infection. As a result, COVID-19 monitoring apps integrated with digital proximity sensing technologies were developed with the objective of determining exposure distance and duration. Despite the health benefits of these applications, a number of studies have questioned them, suggesting they are vulnerable to user privacy threats [31]. As a result of these problems, as Table 2 summarizes, several solutions have been developed to improve the privacy of CTAs by equipping them with the most privacy-preserving proximity measurement technologies available, including blockchain, Bluetooth, QR, WIFI, GPS, and GIS. Simultaneously, researchers introduced a variety of privacy-preserving alternatives, including decentralized privacy, differential privacy, and privacy by design.
Table 2.
Technical summary of some of COVID-19-tracing applications [12].
| Centralized/Decentralized Application | Country/state | Application Name | Embedded Proximity Measurement Technology |
|---|---|---|---|
| Centralized | Alberta, Canada | ABTraceToghegher | Bluetooth |
| Part of US states, and EU (except UK & France(planed)) | Apple & Google SDK | Bluetooth | |
| Austria | Stopp Corona | Bluetooth | |
| HongKong | Stay Home Safe | Bluetooth, Wi-Fi | |
| Vietnam | Bluezone | Bluetooth | |
| Decentralized | State of Dekota, US | Care19 | GPS |
| State of Utah, US | Healthy Togheter | GPS | |
| Germany | Corona Data Donation | GPS | |
| UK | NHS App | Bluetooth | |
| China | WeChat & Alipay | QR Code, Big data | |
| Singapore | TraceTogheter | Bluetooth | |
| Australia | COVID-19safe | Bluetooth |
One of the technologies embedded in CTAs is blockchain, which has been deployed in the healthcare industry [32] and has been combined with COVID-19 monitoring applications to address privacy, security, and interoperability concerns [33]. In terms of protecting patients' privacy and personal data, blockchain technology appears to be promising. According to studies, blockchain-based tracing apps have a variety of features that solve privacy concerns and data-related trust issues [34], such as facilitating the secure and legitimate exchange of data between individuals and governments [35]. Moreover, blockchain technology has been crucial in combating disinformation and increasing the transparency of accurate data [36]. Provision of blockchain-based privacy-preserving contact tracing applications for the purpose of desensitizing patient ID and location information [37] has yet to become a primary technical intervention, as does the improvement of blockchain features, including time stamping and data immutability [38]. Consolidating sophisticated cryptographic techniques with blockchain technology may potentially lead to a significant diminution in the vulnerabilities connected with tracing applications [39]. For example, crypto-spatiotemporal information contributes to the preservation of personal privacy. Consequently, it is critical to recognize how personal privacy can be jeopardized whenever patients and their close relationships are tracked using spatiotemporal data. Additionally, researchers have designed a blockchain-based solution for preserving transaction anonymity [40]. For illustration, one study developed a self-sovereign identity-enabled contact tracing technology on the blockchain that ensures no user identification is revealed [41]. Various technologies, such as 5G, can be integrated with blockchain to assist users in locating diagnosed COVID-19 patients without jeopardizing privacy [42].
Bluetooth-based apps are one of the most frequently deployed technologies for CTAs given its widespread support by smart devices. However, Bluetooth-tracing applications centralize contact data collection, posing a threat to privacy [43]. One issue of contention in the privacy discussion concerns complex indoor locations, such as nursing homes or hospitals, where short-range wireless devices may generate concerns about privacy [44]. Alternatively, measures such as acquiring large-scale geolocation data are recommended. Nonetheless, some researchers claim that as an application's reach expands, the risk of data leakage and exploitation escalates [43]. Global Positioning System, or GPS, as one of the most widely adopted location data technologies, is also embedded in CTAs and has been critiqued for its potential risks to health surveillance, for recording users' exact locations, for threatening location privacy, and for exposing personal data [45]. While Bluetooth-enabled CTAs compromise privacy through the exchange of identifiers, GPS-enabled solutions violate privacy primarily through mass tracing [46].
One significant technical approach for preserving privacy is the use of privacy-enhancing technologies (PETs), such as differential privacy or the method of privacy by design, to mitigate privacy breaches or attacks by malicious third parties [47]. Privacy by design refers to the process of implementing privacy protection into the overall design of technology [48], whereas differential privacy refers to approaches for acquiring information about sensitive data without disclosing too much about any particular individual [49]. As will be discussed in Section 4.2, privacy by design is among the most heated scholarly topics.
Another technical solution is the development of decentralized tracing applications. Several previous research studies from a variety of fields have proposed unique strategies for limiting the privacy risk connected with contact tracing applications, proposing that both legal and technological remedies may be considered [50]. Some governments, in collaboration with technology companies, have devised a number of privacy-preserving alternatives, such as decentralized systems, in reaction to the constraints of centralized applications developed by some countries, including India or Singapore [14]. While some studies assert that centralized methods can more rapidly and reliably detect infected individuals and high-risk public spaces [51], others argue that centralized systems jeopardize individuals' privacy [52]. Decentralized apps, such as Austria's Stopp Corona or Vietnam's Bluezone [53], do not retain data on a single server but rather interchange it between a network of interconnected servers [54].
Topic 2: Democratic and Social Discriminatory Consequences.
Researchers are concerned with two important difficulties with COVID-19-tracing apps: the disclosure of personal data and the consequent breach of democratic values, and the potential for social discrimination as a result of disease revelation. Democratic principles and a just and equitable society may be compromised because of data and disease disclosure. According to studies, state control was heightened during the COVID-19 epidemic not only in authoritarian regimes, but also in democratic and autocratic countries equally [55]. This dilemma has been aggravated by governments' compulsion to download applications against citizens' consent. Voluntary installation of CTAs has been violated in a number of nation [56]. For instance, in India, the government's requirement that residents install the national CTAs fostered distrust and aversion to adoption [57]; in addition, Israel's authorities have tracked down cases of the virus by utilizing a phone tracing database often used for counterterrorism [58]. Whereas some researchers argue that digital health surveillance does not threaten a democratic society's fundamental characteristics [59], some studies have debated whether mandatory app installation is a type of biopower exercise [60] or a form of state surveillance [55]. Prior studies have disputed the extent to which tracing applications can protect citizens in a democratic society and highlighted the peril of undermining the public's trust if tracing applications do not adhere to data capture privacy principles and result in the unintended disclosing of users' data, such as their disease, contacts, or location data [61]. Whereas several governments have enacted standards demanding limited or no exposure of users' information and utilizing a variety of technical approaches [62], investigations reveal that some tracing apps tend to disclose portions of their users' private information [63]. Certain tracing applications have developed techniques for revealing only a portion of the user's data, such as their movement patterns [64].
Studies contend that infringing on the app's voluntarines may erode civil freedoms such as freedom of movement and gathering [65] and may exacerbate social discrimination [66], particularly among affected populations. Demographic data and socioeconomic status are also disclosed by the apps, including users' race, clan, or region of origin. As a result of this data's influence on the allocation of COVID-19 resources, social and financial injustice may increase [67]. Another vulnerable group is the working class, which resists the installation of CTAs, fearing that doing so will expose them to personal hazards such as stigma, anxiety, and financial loss [68]. According to several studies, COVID-19 is a stigmatized disease because some individuals anticipate that disclosing their illness may result in social isolation, stigma, and psychological distress from their contacts [69]. As a result, one of the worries that may deter individuals from installing and using COVID-19 tracing tools is the possibility of discriminatory confrontations [70].
Topic 3: Human rights aspects of CTAs.
The effects of CTA on human rights is one of the major issues being examined by researchers. Concerns about the effectiveness of digital technologies for health monitoring, the involvement of third parties in the collection, use, and storage of personal data, the potential threat to minority groups, and the misuse of these systems by state and non-state actors have sparked human rights concerns about CTAs [59]. Prior research suggests that, despite global attempts to develop COVID-19-related legislation, they should be more transparent and explicit about personal data protection and human rights [71]. As [72] recommend, urgent COVID-19 solutions should be accessible to open examination and, unless the government can demonstrate that they are necessary and proportionate, should be immediately terminated, considering the fact that in emergencies, temporary suspension of certain human rights are permitted only to the extent that the necessities of the situation warrant it [73]. For instance, Article 17 of the ICCPR recognizes that the right to privacy is violated when a person's contact information is traced. Interferences with privacy that are not arbitrary and proportional are allowed under Article 17(1) [74]. As a consequence, governments should strike a reasonable balance between human rights protection and public health promotion, while seamlessly incorporating human rights principles into COVID-19 initiatives [75]. Some studies have criticized existing and proposed regulatory and technical solutions for failing to defend human rights adequately.
According to previous studies, derogation from human rights must meet a number of criteria, including legality, necessity, and proportionality [76]. One study argues that COVID-19-tracing applications should be evaluated according to four human principles: necessary, proportional, scientifically valid, and time-bound. For instance, in Korea, while the tracing app is scientifically valid and viable and satisfies the necessity criterion, it is too ambiguous in terms of adhering to the time-boundedness principle [77]. According to some other studies, the human rights implications of CTA can be examined via a variety of perspectives, including privacy, autonomy, and nondiscrimination [59], rights to equality, privacy, human dignity, as well as freedom of speech, association and movement, and security of the person [78].
Topic 4: Governance of the CTAs.
There is debate on the prophylactic purpose and practicality of CTA in light of bioethical and governance concerns [79], as well as the difficulties inherent in incorporating key ethical principles into governance processes, particularly when they lack accountability [80]. The World Health Organization has affirmed the critical importance of adequate tracing application governance [62], owing to reservations and mistrust pertaining to the capacity of existing public health infrastructures [81], as well as government partnerships with large technology companies. Some studies refer to CTAs as “corporate tracing apps” to underline the private sector's and large technology corporations' involvement in the deployment of CTAs [82]. These studies offer technical solutions such as decentralized applications [81]. Some research claim that CTAs have been normalized as valid instruments for state governance, leading to the development of a distinct kind of pandemic techno-governance in which the lines between care and control are compromised [83]. Pandemic control may jeopardize data governance, necessitating an assessment of the issue at a time when data may be collected and used without individuals' knowledge or consent or for government-mandated objectives [84].
To allay public suspicion about the vested interests of CTAs and to legitimate government initiatives, several countries, such as Switzerland or France, have incorporated diverse stakeholders throughout the development of CTAs [85]. Some studies recommend the development of locally contextualized governance frameworks in accordance with factors such as immediate health risk, prior experience with pandemics, societal values and national culture, role of government, trust in government and trust in technology in each society [86]. For instance a governance framework for CTAs can contain four unique sorts of decision-making entities that might be involved in societal governance and collective action: individuals, organizations, platforms, and governments [86].
Topic 5: Adoption and Trust.
Regardless of the governments' approach for preventing COVID-19's spread, public participation is critical in effective management of public health. The efficiency of CTAs is highly dependent on individuals' acceptance and favorable attitude toward them, as well as their trust in government [87]. Thus, Topic 5 of this analysis focuses on elucidating factors that drive or prevent individuals from adopting applications and determinants of citizen trust in government. A series of barriers prevents individuals from installing applications, including concerns about their privacy, and perceived stigma [69]. Furthermore, some people have expressed distrust in their governments and concerns about their safety on social media [88]. There is a significant disparity between what individuals profess to perceive and how they behave, since the public claims these applications are ineffective but nonetheless downloads them in reaction to government mandates [89].
While one section of the studies concentrates on factors that contribute to or impede the adoption of tracing applications, another section seeks to offer remedies and techniques to accelerate adoption. For example, research indicates that financial incentives such as gift cards can significantly increase app usage [90,91]. However, adoption is influenced by a variety of factors, not just financial incentives. According to one study, once users experience negative emotions such as rage or annoyance, they remain unwilling to adopt the applications; thus, it is recommended that developers increase users' control over technology to ensure that they avoid experiencing negative emotions [92]. This argument is especially notable given that one study reveals that the app's access authorization constraints have a negative impact on user adoption rates [93]. Trust is a strong component in adoption [94]; for example, research has demonstrated that cognitive and emotional trust favorably affects people's willingness to reveal personal information [95]. Additionally, the literature incorporates the Uncertainty Reduction Theory to indicate that initiatives to reduce uncertainty, such as trust in government, will increase adoption [96]. Additionally, studies advocate for the implementation of blockchain due to its decentralized governance structure and privacy-preserving capabilities, which enable the establishment of a “trustless” system that boosts the effectiveness of CTAs [34].
Topic 6: Monitoring and Surveillance Challenges.
Citizen surveillance, disease surveillance, epistemic surveillance, state surveillance, public health surveillance, and capitalistic surveillance are just a few of the most frequently hurled criticisms directed at CTAs. Apprehensions regarding surveillance stem from CTAs' surveillance capabilities, such as the potential to track users' movements [97]. Concerns about user surveillance and potential threats to democratic society's principles stimulate efforts to design efficient surveillance systems [98].
In health surveillance, patients and their disease state are monitored using data supplied by citizens via mobile phones and social media, rather than self-reported data [99]. This non-participatory technique was presented as a substitute for local “participatory COVID-19 surveillance tools” [100,101] and due to individuals' possible reluctance to install the app on their smartphones [98]. According to scholars, the participatory or non-voluntary nature of CTA will blur the lines between health data and existing government surveillance measures [11,102]. As a result, an emphasis is being devoted to the development of non-participatory, privacy-preserving surveillance systems in which users are not obliged to use CTA and diseases are monitored without relying on citizen self-reports [98]. These scholars argue for the inclusion of smartphone-based GPS and social media data, suggesting that relying on patient self-reports of symptoms to prevent transmission is impractical [99].
Surveillance capitalism [103,104] or biopolitics [105] refers to technology corporations' mishandling of crises and their collaboration with the government to advance their vested interests. With governments increasingly collaborating with technology companies to develop CTAs, concerns about a new model of capitalism based on surveillance technologies and data have arisen. Scholars argue that commercialization of citizens' personal data and behavioral patterns, such as contacts or locations or other ethnic data, will benefit both private companies and the government, enabling the government to raise state surveillance [102]. According to this research, CTAs can legitimize surveillance capitalism by capturing and exploiting citizens' social, spatial, and contact data for commercial advantage [105]. The findings imply that by utilizing CTAs, corporate control over the public domain can be reinforced [82]; as a result, they advocate for remedies such as the socialization of ownership of emerging technology [106]. Epistemic surveillance is another academic discussion that relates to the exploitation of the user's personal data in this scenario [107].
Topic 7: Digital-Politic Nexus.
The link between politics and digital technologies is one of the key issues with CTAs. When science and politics collide, it is said that politics triumphs [108]. To fully grasp how to maintain the functionality of medical applications while also considering the political consequences of these technological breakthroughs, researchers are recommending a closer analysis of the digital-political nexus and the national conflicts it engenders [109]. Throughout COVID-19 pandemic, governments' misinformation and disinformation have posed a significant obstacle to promoting transparency and accountability. Due to surveillance apps' ineffectiveness in reducing COVID-19 patients, studies recommend analyzing the wider context of tracing apps in terms of the influence of complex and interwoven sociopolitical contexts [110]. According to the findings, the COVID-19 “infodemic” is inextricably linked to the pandemic. The term infodemic refers to an abundance of information on a situation that is often erroneous, spreads swiftly, and makes obtaining a solution more complicated and data culture is influenced by pandemics [111,112] and is mostly produced by political misinformation in nations such as the United States of America and India [113]. The majority of COVID-19 misinformation collected on social media varies widely across languages and nations due to cultural and religious diversity, with political position accounting for the majority of misinformation collected [114]. Additionally, reviews of citizen comments on applications reveal that the majority of citizen dialogues or comments on CTAs are political in nature, with less emphasis on the app's usefulness or performance [110]. In terms of the relationship between citizen adoption and political factors, some scholars claim that because state-level data and people's political affiliation have a significant impact on the adoption of CTAs, macro-political contexts should be assessed rather than individual-level factors [115].
Topic 8: Non/Supportive Legislations.
Tracing applications have a predisposition for unanticipated negative implications for their users, such as concerns of confidentiality and transparency [96]. This has prompted countries to enact legislation to protect consumers' privacy and control rights. For instance, data flow and storage have been restricted as a result of the Commonwealth Government's legislation. The COVID-19 Safe Bill 2020, introduced by the Australian government, forbids any entity to force anyone to use the app for any reason [116]. The GDPR, or General Data Protection Regulation, is one of the most well-known and widely recognized data protection laws in the world. In comparison to sector-specific standards, such as the US Health Insurance Portability and Accountability Act (HIPAA) and California's new Consumer Privacy Act (CCPA), both of which contain gaps that make it difficult to manage COVID-19 effectively, some researchers argue that a framework with a broader reach, such as GDPR, is preferable under uncertain COVID-19 app conditions [117].
Apart from examining the legislation controlling the use of CTAs, experts have examined the many ways in which governments regulate their usage. While more democratic nations enact supportive legislation to safeguard citizens against unintended negative consequences, certain governments, like as India [57] and Qatar [118], have compelled residents to use the CTAs.
Additionally, as studies reveal, the government's failure to recognize the legal issues inherent in CTAs and to build permanent regulatory frameworks erodes public faith in the apps, weakening their effectiveness [119]. With the advent of deep learning and complicated artificial intelligence algorithms and their incorporation in digital health care [120], experts have argued for the establishment of regulatory regimes for the advancement, administration, and procurement of AI in order to ensure the ethical and safe use of AI in the national healthcare sector [121].
Topic 9: Artificial Intelligence and Predictive Tracing Practices.
Divergent viewpoints exist regarding the effectiveness of artificial intelligence in boosting the functionality of CTAs. Scholars argue that AI systems lack enough maturity to combat COVID-19 and governments may abuse data-driven AI systems for citizen surveillance [122]. According to one side of the debate, a lack of data for training and pattern extraction may have hampered the deployment of AI in tracing applications [67]. Within the debates, some scholars cast doubts about the validity and accuracy of AI algorithms embedded in contact tracing apps, noting gaps in the detection and prediction of COVID-19 cases, as well as in tracing infected individuals' contacts [123]. Certain studies advocate for the establishment of regulatory frameworks to ensure the development and deployment of ethical and safe AI that is merged with privacy-preserving solutions, given reservations over the use of AI in CTA [121]. On the other hand, one side of the debate contends that artificial intelligence and high-performance computing accelerated the development of personalized treatments to avoid transmission [124]. Additionally, proponents assert that artificial intelligence (AI) has facilitated social distancing by developing novel solutions like symptom prediction, identification and monitoring of quarantined persons, and contact tracing [125].
4.2. The most stressing privacy repercussions of CTAs
Constraints and solutions relating to privacy have an effect on the effectiveness of CTAs. We have summarized the most concerning privacy implications and solutions related with CTAs in this section of the paper (Fig. 8 ). The most important privacy concept is privacy by design, which is a technical approach that will most likely promote the adoption of CTA [126]. According to current research, the primary impediment to citizens adopting CTAs is privacy [127]. Several privacy-protection strategies have been offered, including anonymization, encryption, obfuscation, pseudo-anonymization, and hybrid [128]. In order to alleviate citizens’ concerns, human-centered technologies such as privacy by design were introduced [128,129] that were respectful of societal norms and safeguarded civil freedoms [127]. Privacy by design presupposes that privacy must be a de facto characteristic of networked data systems and technologies, which must adhere to several principles: privacy by design systems are proactive and preventive; privacy is the default and is constructed into the design; the systems have full functionality; and there is end-to-end security and respect for user privacy [130]. Data minimization is also incorporated into these principles which means that only the information that is absolutely essential is stored and processed [131].
Fig. 8.
The most concerning privacy implications of CTAs were deduced through keyword co-occurrence analysis. We chose keywords with the highest TLS score.
As mentioned earlier, decentralized privacy was also recommended to alleviate intrusions. Nations such as the United Kingdom updated their first COVID-19 tracing app with a new one based on Apple and Google's decentralized methodology [132], and several European countries embraced the DP3T (Decentralized Privacy-Preserving Proximity Tracing) protocol [132,133]. Decentralization, in essence, is the transfer of power and authority from a single central authority to a network of distributed participants [134]; thus, a decentralized system is a network that does not rely on a single master node for control; rather, it distributes control among numerous nodes [135].
The second most significant privacy-related issue, surveillance, sparked these solutions. This concern entails reservations about the likelihood of governments and companies misusing individuals' personal data for their own vested interests. The blurred lines between disease surveillance and individual surveillance, as well as each country's unique political economy, led some scholars to refer to the CTAs as pandemic surveillance technologies [20] as governments adopted them as political expedients and rapid policy responses to crises [136].
The other significant privacy component of CTAs is connected to citizen attitudes, notably their trust in government-based applications developed in collaboration with large technological corporations. During uncertain scenarios such as COVID-19 pandemics, trust in government will promote application adoption, as mistrust of governments in the United Kingdom and Australia was the primary barrier to citizens embracing CTAs [137,138]. This lack of trust is exacerbated even further among minorities and vulnerable groups. For example, one analysis revealed that reduced trust in the UK's National Health Service among black, Asian, and minority ethnic populations had an effect on the app's uptake [139]. Moreover, according to one research, immigrants in the United States fear that these applications are actually owned by police [140].
The human rights implications of COVID-19 are also highlighted in the literature, allowing governments to strike a balance between public health management and individual human rights protection [75]. As a result, some researchers have reviewed various legislations to see whether they safeguard individuals' privacy in accordance with concepts like as proportionality and minimization. These human rights principles emphasize the anonymization and consent of individuals during data sharing processes, as well as the generation and processing of data only when a legitimate risk of infection persists [141] or when action is justified and the benefits outweigh the risks [77]. Other human rights considerations for CTA include voluntariness and reversibility [142], transparency and verifiability [143], and accountability [117].
5. Analysis and conclusion
This section of the article will address the study's last query: what gaps exist in the literature and what future research agendas exist?
6. Discussion
We conducted a bibliometric and content analysis of research on the privacy implications of CTAs in this research. We sought to identify the most highly cited countries, institutions, sources, and documents, as well as the most highly addressed academic subjects and most pressing privacy concerns. Additionally, we identified gaps in the literature and proposed future study objectives.
Theoretically, this research contributes to an expanding body of knowledge on digital health ethics, notably the privacy concerns surrounding mobile health applications that include proximity measuring technologies and other cutting-edge digital technologies that capture personal data. This study contributes to the body of knowledge by identifying the most significant entities and research topics that the literature has largely overlooked or not highlighted. The purpose of this study is to identify theoretical research gaps and to recommend prospective research initiatives to address them. Practically, this research serves as a guide for policymakers, governments, application developers, and technology companies interested in garnering citizens' trust and increasing their adoption of tracing applications through the integration of technical and non-technical solutions that mitigate privacy risks and increase user participation in the development of applications and regulations. This study reveals that significant scientific discussions exist regarding the risks connected with digital mobile health applications that incorporate proximity measurement and other cutting-edge digital technologies, such as blockchain or artificial intelligence. We performed co-citation analysis to determine which entities, such as authors, sources, and documents, obtained the most citations so far. After identifying the research topics by keyword co-occurrence analysis, we conducted a topic-based content analysis to gain a deeper understanding of the research topics. Our investigation yielded nine major scholarly topics. The first topic is the measurement technology integrated into tracing apps and the privacy problems that accompany it. The second subject deals with democratic and social discrimination challenges, while the third topic closely addresses the human rights concerns of CTAs. The fourth subject is governance of CTAs, and the fifth is perceptions, attitudes, adoption behavior, and trust among citizens. The sixth theme examines the discussions about surveillance and monitoring. Furthermore, the seventh subject delves into the relationship and tensions between digital health technology and politics. Topic 8 compares helpful and non-supportive regulatory systems and legislation. The ninth research focus discusses how artificial intelligence and its predictive capabilities may be utilized to manage the COVID-19 tracing crisis. Other topics also encompass the application of proximity-measuring technology and artificial intelligence. Based on these analyses, we identified a list of the most pressing privacy challenges and solutions that are widely discussed in the literature.
In this study, we identified seven major privacy challenges of CTAs depicted in Fig. 9 . These challenges are politicization of care; anti-democratic and social discrimination practices; human rights derogation; techno governance; citizen distrust and refusal to adopt; monitoring and surveillance; and mandatory legislations of installing the apps. Tracing applications have an unfavorable reputation among the public despite their promise to safeguard healthcare: Certain studies claim that proximity measurement techniques may be manipulated by certain governments to undertake anti-democratic and socially-biased policies. Patients' anxieties about social shame will be compounded by disclosing their disease, while revealing their location data fuels suspicions of government control and monitoring. Furthermore, researchers contend that governments have established alliances with the world's largest technological corporations to design privacy measures that are decentralized. These studies suggest that these legal measures would safeguard citizens' safety, but given the public's historical mistrust toward governments and their collaboration with major technology corporations, individuals have become more anxious about data privacy and its sharing with tech businesses. Consequently, individuals are concerned not just about government surveillance and control, but also about the partnership between the government and technological firms with economic and vested interests, which will offer such firms incentives to exploit the private information of citizens. The blurring lines between governments and technological corporations, as well as each party's entrenched interests, have rendered health care and politics, as well as financial gain, indistinguishable. Hence, the lack of trust in the government, fear of control, financial vested interests of technology corporations, and societal stigma and prejudice have fostered an environment of anxiety about installing and using the applications. This circumstance may be exacerbated among vulnerable groups, especially racial and ethnic minorities, or among families who have lost loved ones due to COVID-19. As a result of the rising incidence of COVID-19 deaths and the subsequent grief, tracing applications are less likely to be adopted by the affected citizens. Mandatory regulations by the governments that compel their citizens to download and install the apps have aggravated the skepticism and lack of motivation to use the applications, leading to a negative perception of the apps. Aside from that, the absence of explicit legislative frameworks for healthcare tracing applications has exacerbated public mistrust of them. It is important to consult more stakeholders, especially doctors, hospitals, and healthcare providers, throughout the development of tracing apps because privacy concerns have been heightened by the low participation of healthcare stakeholders such as hospitals and clinics in the development of tracing apps. Shifting responsibility from governments and their commercial partners to health care providers, including hospitals and healthcare providers, could undoubtedly enhance confidence and lessen privacy concerns. In this way, there have been very few studies that have tried to improve the understanding of other stakeholders, like patients and citizens, about tracing applications. This lack of information would make people more negative about the applications.
Fig. 9.
Seven major privacy challenges embedded in CTAs derived from content analysis of topics.
While the majority of efforts have been dedicated to developing more advanced technologies and engineering solutions to reduce privacy threats, supplemental steps must be conducted to boost public confidence in these applications through regulatory, educational, and even psychological and emotional support measures. Using a technocratic mindset when introducing new technologies like AI, which are full of unknowns, will not encourage people to use and like tracing applications.
The research also found that data processing must be legitimate from a human rights standpoint. GDPR Articles 1–6 stipulate that data processing is permissible only with the consent of the data subject. A crucial criterion for evaluating the constraints of human rights, particularly the right to privacy, is the need for restrictions. Processing personal data undermines individuals' right to privacy, making it necessary to limit that right. The word “proportional” suggests a connection between the data processed and the intended purpose of the data. This proportion comprises processed data and tools for processing. Only the data necessary for the processing purpose should be gathered and processed. Adequate security measures should also be taken while processing data to make sure that data privacy is protected to the fullest extent possible.
6.1. Limitations of the study and possible future research streams
Fig. 10 depicts a number of other future research initiatives that we propose. While the majority of previous research has focused on the interaction between the state and commercially dominant technology corporations, we presume that more research should be conducted to examine the triple helix of relationships between people, technology companies, and the government. Since both the government and commercial technology corporations have vested interests, it is critical that citizens' interests and perspectives be considered in these relationships. As a result, more research should be conducted to better understand the processes that allow people to participate in these partnerships while also having their interests considered. Constructing mechanisms to improve the interactions of these three players, as well as incorporating citizens' interests, would improve the efficacy of CTAs while also alleviating citizens' privacy concerns. Similarly, more research should be conducted to determine ways to improve oversight and regulation of technology corporations and their use of citizens' location data. It is also critical to understand how governments' political contexts and governance structures influence the triple helix of interactions between the state, citizens, and large corporations. In countries where capitalism is practiced and technological corporations play a significant role in data management, the entrenched interests of each party differ from those in countries where communist principles and fewer commercial companies have an influence. It is critical to understand the impact of governance and political dynamics on government responses to health emergencies in order to meet the demands of all stakeholders. For example, it may be worthwhile to investigate how political and cultural structures influence people's adoption of proximity tracing applications as well as their perceptions of their functionality.
Fig. 10.
Potential strands of future research.
The adoption of tracing applications is not determined by a single factor and direct relationships. As a result, additional research is required to investigate the configurational and indirect relationships between the components that influence the adoption and perceptions of tracing applications. Scholars can then quantify the moderating or mediating effects of mortality rates as well as other socioeconomic and political factors in this regard. Furthermore, it is critical to investigate the intricate relationships between privacy-related technological breakthroughs, privacy legislative frameworks, and the variety of modalities. With the growth of biopower and surveillance capitalism, more research may be conducted to develop mechanisms that increase people's participation in triple helix interactions and provide greater control over their personal data. To grant users more control over their personal data, developers and technology companies should design applications so that citizens can set their own limits on the sharing and disclosure of their personal data with third parties.
Social media and the app store's review section are critical platforms for citizens to express their feelings and thoughts about the CTAs. As a result, more research into social media content and review content may be conducted in order to gain a better understanding of how people perceive CTAs. The exploitation of individuals' personal location data is a significant reason to exercise caution. Aside from differential privacy, non-technical strategic policies and techniques are required to prevent people's location data from being exploited for purposes such as patient monitoring and control in settings such as hospitals.
As previously stated, some previous research emphasizes the development of automated data collection systems with little or no public input in reporting their data. More academic attention is needed for these automated systems since they may jeopardize citizens' control, autonomy, and informed consent. As a result, it is critical to investigate the privacy implications and difficulties associated with disease monitoring systems that use automated data collection systems. The privacy issues surrounding CTA are inextricably linked to double-edged issues such as disease control and citizen control. Furthermore, technology firms are proposing increasingly complex technical solutions that may be perplexing to the public. As a result, additional educational programs to educate the public and broaden their understanding of complex technical jargon are required.
The study discovered that tracing apps use a variety of technologies, such as Wi-Fi, Bluetooth, and GPS. More research can be performed to better understand the relationships between mortality rate, installation rate, and use of various location technologies in order to determine which technologies may improve both the effectiveness of the apps in managing pandemics and the privacy of citizens. Governments also intervene based on the data generated by these location measurement technologies. It is critical to assess the veracity of data generated by any location technology in order to avoid unintended negative consequences of assumptions derived from the data.
The majority of CTAs are developed and implemented as a result of collaboration between governments and technology companies, which have entrenched interests and, as a result, garner less public trust. The government must delegate responsibility for developing and implementing CTAs to local actors such as hospitals and healthcare stakeholders, who are the primary guardians of healthcare. More academic scrutiny is needed to determine whether the devolution of power and accountability to local and specialized actors will result in increased privacy safeguards and increased adoption of mobile health applications embedded with digital technologies.
This research has limitations of its own. We studied only English-language articles and conducted bibliometric analysis, which has its own limitations, such as old papers that receive more citations [144]. Another limitation of this study is that we did not address the evolution of citations for papers over time. We also did not conduct more in-depth bibliometric analyses, such as the number of self-citations or the percentage of cited versus uncited articles, so that future research studies can address these scientific inquiries. Another limitation of our study is that we chose a time span of two years, which is a limited period for analyzing annual topic development. As a result, one possible future research direction could be to consider a longer time span to measure the evolution of topics over time. Co-citation analysis also has a number of benefits and drawbacks. Its primary strength is that it assesses the intellectual development and structure of scientific disciplines and classifies papers that share a common theme or area of research [[144], [145]]. As [146] explains, the primary limitation of co-citation analysis is its inconsistency in coverage over time and the possibility of citation errors. In light of these limitations, we recommend that future studies employ alternative quantitative methods, such as topic modeling, to track the evolution of scientific literature. Furthermore, unlike topic modeling techniques, VOSviewer software does not segment papers by topic; thus, future research can leverage topic-modeling techniques for this purpose. Finally, we recommend that additional studies beyond bibliometric and topic analysis be conducted, such as analyzing papers from a methodological and research methods perspective, or analyzing papers through a theoretical lens.
Declaration of competing interest
We declare no conflicts of interest.
Acknowledgement
We wish to express our gratitude to Hedy Lamar, the first female scientists to invent WiFi, Bluetooth, and GPS.
References
- 1.Ferretti L., Wymant C., Kendall M., Zhao L., Nurtay A., Abeler-Dörner L., Parker M., Bonsall D., Fraser C. Quantifying SARS-CoV-2 transmission suggests epidemic control with digital contact tracing. Science. 2020;80–:368. doi: 10.1126/SCIENCE.ABB6936/SUPPL_FILE/PAPV2.PDF. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Smieszek T., Castell S., Barrat A., Cattuto C., White P.J., Krause G. Contact diaries versus wearable proximity sensors in measuring contact patterns at a conference: method comparison and participants' attitudes. BMC Infect. Dis. 2016;16:1–14. doi: 10.1186/S12879-016-1676-Y/FIGURES/3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 3.Wesolowski A., Buckee C.O., Engø-Monsen K., Metcalf C.J.E. Connecting mobility to infectious diseases: the promise and limits of mobile phone data. J. Infect. Dis. 2016;214:S414–S420. doi: 10.1093/INFDIS/JIW273. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Jalabneh R., Syed H.Z., Pillai S., Apu E.H., Hussein M.R., Kabir R., Arafat S.M.Y., Majumder M.A.A., Saxena S.K. 2021. Use of Mobile Phone Apps for Contact Tracing to Control the COVID-19 Pandemic: A Literature Review; pp. 389–404. [DOI] [Google Scholar]
- 5.Kolasa K., Mazzi F., Leszczuk-Czubkowska E., Zrubka Z., Péntek M. State of the art in adoption of contact tracing apps and recommendations regarding privacy protection and public health: systematic review. JMIR Mhealth Uhealth. 2021;9(6):E23250. doi: 10.2196/23250. Https//Mhealth.Jmir.Org/2021/6/E23250. 9 (2021) e23250. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Akinbi A., Forshaw M., Blinkhorn V. Contact tracing apps for the COVID-19 pandemic: a systematic literature review of challenges and future directions for neo-liberal societies. Health Inf. Sci. Syst. 2021;9 doi: 10.1007/S13755-021-00147-7. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Singh H.J.L., Couch D., Yap K. Mobile health apps that help with COVID-19 management: scoping review. JMIR Nurs. 2020;3(1):E20596. doi: 10.2196/20596. Https//Nursing.Jmir.Org/2020/1/E20596. 3 (2020) e20596. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Morley J., Cowls J., Taddeo M., Floridi L. Ethical guidelines for COVID-19 tracing apps. Nature. 2020;582 doi: 10.1101/2020.02.14.20023036. [DOI] [PubMed] [Google Scholar]
- 9.Tran C.D., Nguyen T.T. Health vs. privacy? The risk-risk tradeoff in using COVID-19 contact-tracing apps. Technol. Soc. 2021;67:101755. doi: 10.1016/J.TECHSOC.2021.101755. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Lee T., Lee H. 2020. Tracing Surveillance and Auto-Regulation in Singapore: ‘smart’ Responses to COVID-19; pp. 47–60. Https://Doi.Org/10.1177/1329878X20949545. 177. [DOI] [Google Scholar]
- 11.Ioannou A., Tussyadiah I. Privacy and surveillance attitudes during health crises: acceptance of surveillance and privacy protection behaviours. Technol. Soc. 2021;67:101774. doi: 10.1016/J.TECHSOC.2021.101774. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Li J., Guo X. Global deployment mappings and challenges of contact-tracing apps for COVID-19, SSRN electron. J. 2020 doi: 10.2139/SSRN.3609516. [DOI] [Google Scholar]
- 13.Morley J., Cowls J., Taddeo M., Floridi L. Ethical guidelines for COVID-19 tracing apps. Nature. 2020;582:29–31. doi: 10.1038/d41586-020-01578-0. 2021 5827810. [DOI] [PubMed] [Google Scholar]
- 14.Ahmed N., Michelin R.A., Xue W., Ruj S., Malaney R., Kanhere S.S., Seneviratne A., Hu W., Janicke H., Jha S.K. A survey of COVID-19 contact tracing apps. IEEE Access. 2020;8:134577–134601. doi: 10.1109/ACCESS.2020.3010226. [DOI] [Google Scholar]
- 15.Kumpu V. Privacy and the emergence of the “ubiquitous computing society”: the struggle over the meaning of “privacy” in the case of the Apple location tracking scandal. Technol. Soc. 2012;34:303–310. doi: 10.1016/J.TECHSOC.2012.10.002. [DOI] [Google Scholar]
- 16.Martens M., De Wolf R., Vadendriessche K., Evens T., De Marez L. Applying contextual integrity to digital contact tracing and automated triage for hospitals during COVID-19. Technol. Soc. 2021;67:101748. doi: 10.1016/J.TECHSOC.2021.101748. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 17.Kahnbach L., Lehr D., Brandenburger J., Mallwitz T., Jent S., Hannibal S., Funk B., Janneck M. Quality and adoption of COVID-19 tracing apps and recommendations for development: systematic interdisciplinary review of European apps. J. Med. Internet Res. 2021;23(6):E27989. doi: 10.2196/27989. Https//Www.Jmir.Org/2021/6/E27989. 23 (2021) e27989. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Yaacob A., Gan J.L. Bibliometric analysis OF global research developments ON the role OF technology during COVID-19: current trends and future prospect. J. Content, Community Commun. 2021;13:166–180. doi: 10.31620/JCCC.06.21/15. [DOI] [Google Scholar]
- 19.Ellegaard O., Wallin J.A. The bibliometric analysis of scholarly production: how great is the impact? Scientometrics. 2015;105:1809–1831. doi: 10.1007/s11192-015-1645-z. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 20.Yang F., Heemsbergen L., Fordyce R. 2020. Comparative Analysis of China's Health Code, Australia's COVIDSafe and New Zealand's COVID Tracer Surveillance Apps: a New Corona of Public Health Governmentality? pp. 182–197. Https://Doi.Org/10.1177/1329878X20968277. 178. [DOI] [Google Scholar]
- 21.Cattuto C., Spina A. The institutionalisation of digital public health: lessons learned from the COVID-19 app. Eur. J. Risk Regul. 2020;11:228–235. doi: 10.1017/ERR.2020.47. [DOI] [Google Scholar]
- 22.Daniore P., Ballouz T., Menges D., Von Wyl V. The SwissCovid digit. Prox. Tracing app after one year were expect. Fulfilled? Swiss Med. Wkly. 2021;151:w30031. doi: 10.4414/SMW.2021.W30031. The SwissCovid Digital Proximity Tracing App after one year: Were expectations fulfilled?, Daniore, Paola; Ballouz, Tala; Menges, Dominik; von Wyl, Viktor (2021) 151w30031. [DOI] [PubMed] [Google Scholar]
- 23.Saheb T., Saheb M. Analyzing and visualizing knowledge structures of health informatics from 1974 to 2018: a bibliometric and social network analysis. Healthc. Inform. Res. 2019;25:61–72. doi: 10.4258/hir.2019.25.2.61. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Tijssen R.J.w., Van Raan A.F.j. 2016. Mapping Changes in Science and Technology: Bibliometric Co-occurrence Analysis of the R&D Literature; pp. 98–115. Http://Dx.Doi.Org/10.1177/0193841X9401800110. 18. [DOI] [Google Scholar]
- 25.Su H.N., Lee P.C. Mapping knowledge structure by keyword co-occurrence: a first look at journal papers in Technology Foresight. Scientometrics. 2010;85:65–79. doi: 10.1007/S11192-010-0259-8. [DOI] [Google Scholar]
- 26.Saheb T., Amini B., Kiaei Alamdari F. Quantitative analysis of the development of digital marketing field: bibliometric analysis and network mapping. Int. J. Inf. Manag. Data Insights. 2021;1:100018. doi: 10.1016/j.jjimei.2021.100018. [DOI] [Google Scholar]
- 27.van Eck N.J., Waltman L. Meas. Sch. Impact. Springer International Publishing; Cham: 2014. Visualizing bibliometric networks; pp. 285–320. [DOI] [Google Scholar]
- 28.Van Eck N.J., Waltman L. How to normalize cooccurrence data? An analysis of some well-known similarity measures. J. Am. Soc. Inf. Sci. Technol. 2009;60:1635–1651. doi: 10.1002/ASI.21075. [DOI] [Google Scholar]
- 29.Hsieh H.F., Shannon S.E. Three approaches to qualitative content analysis. Qual. Health Res. 2005;15:1277–1288. doi: 10.1177/1049732305276687. [DOI] [PubMed] [Google Scholar]
- 30.van Eck N.J., Waltman L. Software survey: VOSviewer, a computer program for bibliometric mapping. Scientometrics. 2010;84:523–538. doi: 10.1007/s11192-009-0146-3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 31.Peng Z., Xu C., Wang H., Huang J., Xu J., Chu X. PB-trace: privacy-preserving blockchain-based contact tracing to combat pandemics. Proc. ACM SIGMOD Int. Conf. Manag. Data. 2021:2389–2393. doi: 10.1145/3448016.3459237. [DOI] [Google Scholar]
- 32.Saheb T., Mamaghani F.H. Exploring the barriers and organizational values of blockchain adoption in the banking industry. J. High Technol. Manag. Res. 2021;32:100417. doi: 10.1016/J.HITECH.2021.100417. [DOI] [Google Scholar]
- 33.Li X., Tao B., Dai H.N., Imran M., Wan D., Li D. Is blockchain for Internet of medical Things a panacea for COVID-19 pandemic? Pervasive Mob. Comput. 2021;75:101434. doi: 10.1016/J.PMCJ.2021.101434. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34.Khurshid A. Applying blockchain technology to address the crisis of trust during the COVID-19 pandemic. JMIR Med. Inf. 2020;8(9):E20477. doi: 10.2196/20477. Https//Medinform.Jmir.Org/2020/9/E20477. 8 (2020) e20477–e20477. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 35.Kaur M., Murtaza M., Habbal M. Post study of Blockchain in smart health environment. CITISIA 2020 - IEEE Conf. Innov. Technol. Intell. Syst. Ind. Appl. Proc. 2020 doi: 10.1109/CITISIA50690.2020.9371819. [DOI] [Google Scholar]
- 36.Odoom J., Soglo R.S., Danso S.A., Xiaofang H. A privacy-preserving covid-19 updatable test result and vaccination provenance based on blockchain and smart contract. Int. Conf. Mechatr., Rem. Sens., Inf. Syst. Ind. Inf. Technol. ICMRSISIIT 2019. 2019 doi: 10.1109/ICMRSISIIT46373.2020.9405872. [DOI] [Google Scholar]
- 37.Xu H., Zhang L., Onireti O., Fang Y., Buchanan W.J., Imran M.A. BeepTrace: blockchain-enabled privacy-preserving contact tracing for COVID-19 pandemic and beyond. IEEE Internet Things J. 2021;8:3915–3929. doi: 10.1109/JIOT.2020.3025953. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 38.Idrees S.M., Nowostawski M., Jameel R. Blockchain-based digital contact tracing apps for COVID-19 pandemic management: issues, challenges, solutions, and future directions. JMIR Med. Inf. 2021;9(2):E25245. doi: 10.2196/25245. Https//Medinform.Jmir.Org/2021/2/E25245. 9 (2021) e25245–e25245. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 39.Wen Z., Yu K., Qi X., Sato T., Katsuyama Y., Sato T., Kameyama W., Kato F., Cao Y., Yoshikawa M., Luo M., Hashimoto J. Blockchain-empowered contact tracing for COVID-19 using crypto-spatiotemporal information, 2020 IEEE Int. Conf. E-Health Networking. Appl. Serv. Health. 2021;2020 doi: 10.1109/HEALTHCOM49281.2021.9398978. [DOI] [Google Scholar]
- 40.Choudhury H., Goswami B., Gurung S.K. CovidChain: an anonymity preserving blockchain based framework for protection against covid-19. Inf. Secur. J. 2021;30:257–280. doi: 10.1080/19393555.2021.1921315. [DOI] [Google Scholar]
- 41.Bandara E., Liang X., Foytik P., Shetty S., Hall C., Bowden D., Ranasinghe N., De Zoysa K., Ng W.K. Connect - blockchain and self-sovereign identity empowered contact tracing platform, lect. Notes Inst. Comput. Sci. Soc. Telecommun. Eng. LNICST. 2021:208–223. doi: 10.1007/978-3-030-70569-5_13. 362 LNICST. [DOI] [Google Scholar]
- 42.Zhang C., Xu C., Sharif K., Zhu L. Privacy-preserving contact tracing in 5G-integrated and blockchain-based medical applications. Comput. Stand. Interfac. 2021;77:103520. doi: 10.1016/J.CSI.2021.103520. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43.Simmhan Y., Rambha T., Khochare A., Ramesh S., Baranawal A., George J.V., Bhope R.A., Namtirtha A., Sundararajan A., Bhargav S.S., Thakkar N., Kiran R. GoCoronaGo: privacy respecting contact tracing for COVID-19 management. J. Indian Inst. Sci. 2020;100:623–646. doi: 10.1007/s41745-020-00201-5. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 44.Di Marco P., Park P., Pratesi M., Santucci F. A bluetooth-based architecture for contact tracing in healthcare facilities. J. Sens. Actuator Netw. 2021;10:2. doi: 10.3390/JSAN10010002. 10 (2020) 2. [DOI] [Google Scholar]
- 45.Wang S., Ding S., Xiong L. A new system for surveillance and digital contact tracing for COVID-19: spatiotemporal reporting over network and GPS. JMIR MHealth UHealth. 2020;8 doi: 10.2196/19457. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 46.Buccafurri F., De Angelis V., Labrini C. A privacy-preserving solution for proximity tracing avoiding identifier exchanging. Proc. 2020 Int. Conf. Cyberworlds, CW 2020. 2020:235–242. doi: 10.1109/CW49994.2020.00045. [DOI] [Google Scholar]
- 47.Shubina V., Holcer S., Gould M., Lohan E.S. Survey of decentralized solutions with mobile devices for user location tracking, proximity detection, and contact tracing in the COVID-19 era. Data. 2020;5(. 5):87. doi: 10.3390/DATA5040087. 2020) 87. [DOI] [Google Scholar]
- 48.Schaar P., Schaar P. Privacy by design. Identity Inf. Soc. 2010;3:267–274. doi: 10.1007/S12394-010-0055-X. 2010 32. [DOI] [Google Scholar]
- 49.EbadiHamid, SandsDavid, SchneiderGerardo Differential privacy. ACM SIGPLAN Not. 2015;50:69–81. doi: 10.1145/2775051.2677005. [DOI] [Google Scholar]
- 50.Bengio Y., Ippolito D., Janda R., Jarvie M., Prud’homme B., Rousseau J.-F., Sharma A., Yu Y.W. Inherent privacy limitations of decentralized contact tracing apps. J. Am. Med. Inf. Assoc. 2021;28:193–195. doi: 10.1093/jamia/ocaa153. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 51.Mao Z., Yao H., Zou Q., Zhang W., Dong Y. Digital contact tracing based on a graph database algorithm for emergency management during the COVID-19 epidemic: case study. JMIR Mhealth Uhealth. 2021;9(1):E26836. doi: 10.2196/26836. Https//Mhealth.Jmir.Org/2021/1/E26836. 9 (2021) e26836. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 52.White L., Van Basshuysen P. How to overcome lockdown: selective isolation versus contact tracing. J. Med. Ethics. 2020;46:724–725. doi: 10.1136/MEDETHICS-2020-106680. [DOI] [PubMed] [Google Scholar]
- 53.Guo C., Lu M., Wei W. An improved LDA topic modeling method based on partition for medium and long texts. Ann. Data Sci. 2019;82:331–344. doi: 10.1007/S40745-019-00218-3. 8 (2019. [DOI] [Google Scholar]
- 54.Rimsan M., Mahmood A.K., Umair M., Hassan F. COVID-19: a novel framework to globally track coronavirus infected patients using blockchain, 2020. Int. Conf. Comput. Intell. ICCI. 2020:70–74. doi: 10.1109/ICCI51257.2020.9247659. 2020. [DOI] [Google Scholar]
- 55.Eck K., Hatz S. 2020. State Surveillance and the COVID-19 Crisis; pp. 603–612. Https://Doi.Org/10.1080/14754835.2020.1816163. 19. [DOI] [Google Scholar]
- 56.Klar R., Lanzerath D. 2020. The Ethics of COVID-19 Tracking Apps – Challenges and Voluntariness; pp. 1–9. Https://Doi.Org/10.1177/1747016120943622. 16. [DOI] [Google Scholar]
- 57.Basu S. Effective contact tracing for COVID-19 using mobile phones: an ethical analysis of the mandatory use of the aarogya setu application in India. Camb. Q. Healthc. Ethics. 2021;30:262–271. doi: 10.1017/S0963180120000821. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 58.O'Neill P.H. MIT Technol. Rev.; 2020. India Is Forcing People to Use its Covid App, unlike Any Other Democracy.https://www.technologyreview.com/2020/05/07/1001360/india-aarogya-setu-COVID-app-mandatory/ accessed. [Google Scholar]
- 59.Sekalala S., Dagron S., Forman L., Meier B.M. Analyzing the human rights impact of increased digital public health surveillance during the COVID-19 crisis. Health Hum. Rights. 2020;22:7. doi: 10.17615/8e8a-m957. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 60.Galloway K., Professor Kate Galloway A. The COVID cyborg: protecting data status. Alternative Law J. 2020;45:162–167. doi: 10.1177/1037969X20930431. [DOI] [Google Scholar]
- 61.Pagliari C. The ethics and value of contact tracing apps: international insights and implications for Scotland's COVID-19 response. J. Glob. Health. 2020;10:1–18. doi: 10.7189/JOGH.10.020103. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 62.Blasimme A., Ferretti A., Vayena E. Digital contact tracing against COVID-19 in Europe: current features and ongoing developments. Front. Digit. Health. 2021;3:660823. doi: 10.3389/FDGTH.2021.660823. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 63.Jung G., Lee H., Kim A., Lee U. Too much information: assessing privacy risks of contact trace data disclosure on people with COVID-19 in South Korea. Front. Public Health. 2020;8:305. doi: 10.3389/FPUBH.2020.00305. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 64.Park S., Choi G.J., Ko H. Privacy in the time of COVID-19: divergent paths for contact tracing and route-disclosure mechanisms in South Korea. IEEE Secur. Priv. 2021;19:51–56. doi: 10.1109/MSEC.2021.3066024. [DOI] [Google Scholar]
- 65.Sweeney Y. Tracking the debate on COVID-19 surveillance tools. Nat. Mach. Intell. 2020;26:301–304. doi: 10.1038/s42256-020-0194-1. 2 (2020. [DOI] [Google Scholar]
- 66.Rowe F. Contact tracing apps and values dilemmas: a privacy paradox in a neo-liberal world. Int. J. Inf. Manag. 2020;55:102178. doi: 10.1016/J.IJINFOMGT.2020.102178. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 67.Mbunge E. Integrating emerging technologies into COVID-19 contact tracing: opportunities, challenges and pitfalls. Diabetes Metab. Syndr. Clin. Res. Rev. 2020;14:1631–1636. doi: 10.1016/j.dsx.2020.08.029. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 68.Jamieson J., Yamashita N., Epstein D.A., Chen Y. Deciding if and how to use a COVID-19 contact tracing app: influences of social factors on individual use in Japan. Proc. ACM Hum. Comput. Interact. 2021;5:30. doi: 10.1145/3479868. [DOI] [Google Scholar]
- 69.Williams S.N., Armitage C.J., Tampe T., Dienes K. Public attitudes towards COVID-19 contact tracing apps: a UK-based focus group study. Health Expect. 2021;24:377–385. doi: 10.1111/HEX.13179. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 70.Megnin-Viggars O., Carter P., Melendez-Torres G.J., Weston D., Rubin G.J. Facilitators and barriers to engagement with contact tracing during infectious disease outbreaks: a rapid review of the evidence. PLoS One. 2020;15 doi: 10.1371/JOURNAL.PONE.0241473. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 71.Viljoen I.M., Castelyn C. de V., Pope A., Botes M., Pepper M.S. Contact tracing during the covid-19 pandemic: protection of personal information in South Africa, South African. J. Bioeth. Law. 2020;13:15–20. doi: 10.7196/SAJBL.2020.V13I1.718. [DOI] [Google Scholar]
- 72.Mykhalovskiy E., Kazatchkine C., Foreman-Mackey A., McClelland A., Peck R., Hastings C., Elliott R. Human rights, public health and COVID-19 in Canada. Can. J. Public Health. 2020;111:975–979. doi: 10.17269/S41997-020-00408-0. 2020 1116. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 73.Spadaro A. COVID-19: testing the limits of human rights. Eur. J. Risk Regul. 2020;11:317–325. doi: 10.1017/ERR.2020.27. [DOI] [Google Scholar]
- 74.Joseph S. International human rights law and the response to the covid-19 pandemic. J. Int. Humanit. Leg. Stud. 2020;11:249–269. doi: 10.1163/18781527-BJA10004. [DOI] [Google Scholar]
- 75.Hostmaelingen N., Bentzen H.B. How to operationalise human rights for COVID-19 measures. BMJ Glob. Health. 2020;5 doi: 10.1136/BMJGH-2020-003048. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 76.Sun W., Zhou Y., Chen W.T., Huang F., Sun M., Shen L., Gao Y., Zhang Q., Ma S., Shiu C., Zhang L., Lu H. Disclosure experience among COVID-19-confirmed patients in China: a qualitative study. J. Clin. Nurs. 2021;30:783–792. doi: 10.1111/JOCN.15616. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 77.Ryan M. In defence of digital contact-tracing: human rights, South Korea and Covid-19. Int. J. Pervasive Comput. Commun. 2020;16:383–407. doi: 10.1108/IJPCC-07-2020-0081/FULL/PDF. [DOI] [Google Scholar]
- 78.Lim W. Assessing the implications of digital contact tracing for COVID-19 for human rights and the rule of law in South Africa. Afr. Hum. Right Law J. 2020;20:540–557. doi: 10.17159/1996-2096/2020/V20N2A8. [DOI] [Google Scholar]
- 79.Cioffi A., Lugi C., Cecannecchia C. Apps for COVID-19 contact-tracing: too many questions and few answers, Ethics, Med. Publ. Health. 2020;15 doi: 10.1016/J.JEMEP.2020.100575. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 80.Samuel G., Lucivero F. Bringing ethics into governance: the case of the UK COVID-19 contact tracing app. Int. J. Health Gov. 2021 doi: 10.1108/IJHG-04-2021-0042/FULL/PDF. [DOI] [Google Scholar]
- 81.Lucivero F., Marelli L., Hangel N., Zimmermann B.M., Prainsack B., Galasso I., Horn R., Kieslich K., Lanzing M., Lievevrouw E., Ongolly F., Samuel G., Sharon T., Siffels L., Stendahl E., Van Hoyweghen I. Normative positions towards COVID-19 contact-tracing apps: findings from a large-scale qualitative study in nine European countries. Crit. Publ. Health. 2021 doi: 10.1080/09581596.2021.1925634/SUPPL_FILE/CCPH_A_1925634_SM3999.PDF. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 82.French M., Guta A., Gagnon M., Mykhalovskiy E., Roberts S.L., Goh S., McClelland A., McKelvey F. 2020. Corporate Contact Tracing as a Pandemic Response. Https://Doi.Org/10.1080/09581596.2020.1829549. [DOI] [Google Scholar]
- 83.Kim Y., Chen Y., Liang F. 2021. Engineering Care in Pandemic Technogovernance: the Politics of Care in China and South Korea's COVID-19 Tracking Apps. Https://Doi.Org/10.1177/14614448211020752. [DOI] [Google Scholar]
- 84.Li V.Q.T., Ma L., Wu X. COVID-19, policy change, and post-pandemic data governance: a case analysis of contact tracing applications in East Asia. Polic. Soc. 2022;41:129–142. doi: 10.1093/POLSOC/PUAB019. [DOI] [Google Scholar]
- 85.Blasimme A., Vayena E. What's next for COVID-19 apps? Governance and oversight. Science. 2020;370:760–762. doi: 10.1126/SCIENCE.ABD9006/ASSET/D3101726-C25D-40B5-AA39-54FE2083D341/ASSETS/GRAPHIC/370_760_F1. 80- (JPEG. [DOI] [PubMed] [Google Scholar]
- 86.Riemer K., Ciriello R., Peter S., Schlagwein D., Ågerfalk P., Conboy K., Myers M. 2020. Digital Contact-Tracing Adoption in the COVID-19 Pandemic: IT Governance for Collective Action at the Societal Level; pp. 731–745. Https://Doi.Org/10.1080/0960085X.2020.1819898. 29. [DOI] [Google Scholar]
- 87.Altmann S., Milsom L., Zillessen H., Blasone R., Gerdon F., Bach R., Kreuter F., Nosenzo D., Toussaert S., Abeler J. Acceptability of app-based contact tracing for COVID-19: cross-country survey study. JMIR Mhealth Uhealth. 2020;8(8):E19857. doi: 10.2196/19857. Https//Mhealth.Jmir.Org/2020/8/E19857. 8 (2020) e19857. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 88.Ittamalla P.S.V.R. General public's attitude toward governments implementing digital contact tracing to curb COVID-19 – a study based on natural language processing. Int. J. Pervasive Comput. Commun. 2020 doi: 10.1108/IJPCC-09-2020-0121/FULL/XML. [DOI] [Google Scholar]
- 89.Garrett P.M., White J.P., Lewandowsky S., Kashima Y., Perfors A., Little D.R., Geard N., Mitchell L., Tomko M., Dennis S. The acceptability and uptake of smartphone tracking for COVID-19 in Australia. PLoS One. 2021;16 doi: 10.1371/JOURNAL.PONE.0244827. e0244827–e0244827. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 90.Fast V., Schnurr D. Incentivising the adoption of COVID-19 contact-tracing apps: a randomised controlled online experiment on the German corona-warn-app, SIGMIS-CPR 2021 - proc. 2021 comput. People Res. Conf. 2021:31–33. doi: 10.1145/3458026.3462158. [DOI] [Google Scholar]
- 91.Munzert S., Selb P., Gohdes A., Stoetzer L.F., Lowe W. Tracking and promoting the usage of a COVID-19 contact tracing app. Nat. Hum. Behav. 2021;5:247–255. doi: 10.1038/s41562-020-01044-x. 2021 52. [DOI] [PubMed] [Google Scholar]
- 92.Suh A., Li M. Digital tracing during the COVID-19 pandemic: user appraisal, emotion, and continuance intention. Sustainability. 2021;13:608. doi: 10.3390/SU13020608. 13 (2021) 608. [DOI] [Google Scholar]
- 93.Ali A.A., Elfadl A.H., Abujazar M.F., Aziz S., Abd-Alrazaq A., Shah Z., Brahim S., Belhaouari, Househ M., Alam T. Contact Tracing Apps for COVID-19: Access Permission and User Adoption, Proc. 2020 7th IEEE Int. Conf. Behav. Soc. Comput. BESC 2020. 2020. [DOI] [Google Scholar]
- 94.Lin J., Carter L., Liu D. Privacy concerns and digital government: exploring citizen willingness to adopt the COVIDSafe app. Eur. J. Inf. Syst. 2021;30:389–402. doi: 10.1080/0960085X.2021.1920857. [DOI] [Google Scholar]
- 95.Chen S. (Joseph), Waseem D., Xia Z. (Raymond), Tran K.T., Li Y., Yao J. To disclose or to falsify: the effects of cognitive trust and affective trust on customer cooperation in contact tracing. Int. J. Hospit. Manag. 2021;94:102867. doi: 10.1016/J.IJHM.2021.102867. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 96.Oldeweme A., Märtins J., Westmattelmann D., Schewe G. The role of transparency, trust, and social influence on uncertainty reduction in times of pandemics: empirical study on the adoption of COVID-19 tracing apps. J. Med. Internet Res. 2021;23(2):E25893. doi: 10.2196/25893. Https//Www.Jmir.Org/2021/2/E25893. 23 (2021) e25893–e25893. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 97.Szocska M., Pollner P., Schiszler I., Joo T., Palicz T., McKee M., Asztalos A., Bencze L., Kapronczay M., Petrecz P., Toth B., Szabo A., Weninger A., Ader K., Bacskai P., Karaszi P., Terplan G., Tuboly G., Sohonyai A., Szoke J., Toth A., Gaal P. Countrywide population movement monitoring using mobile devices generated (big) data during the COVID-19 crisis. Sci. Rep. 2021;11:1–9. doi: 10.1038/s41598-021-81873-6. 2021 111. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 98.Nabil M., Sherif A., Mahmoud M., Alsmary W., Alsabaan M. Privacy-preserving non-participatory surveillance system for COVID-19-like pandemics. IEEE Access. 2021;9:79911–79926. doi: 10.1109/ACCESS.2021.3082910. [DOI] [Google Scholar]
- 99.Wang S., Ding S., Xiong L. A new system for surveillance and digital contact tracing for COVID-19: spatiotemporal reporting over network and GPS. JMIR Mhealth Uhealth. 2020;8(6):E19457. doi: 10.2196/19457. Https//Mhealth.Jmir.Org/2020/6/E19457. 8 (2020) e19457–e19457. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 100.Runkle J.D., Sugg M.M., Graham G., Hodge B., March T., Mullendore J., Tove F., Salyers M., Valeika S., Vaughan E. Participatory COVID-19 surveillance tool in rural appalachia: real-time disease monitoring and regional response. Publ. Health Rep. 2021;136:327–337. doi: 10.1177/0033354921990372. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 101.de Ridder D., Loizeau A.J., Sandoval J.L., Ehrler F., Perrier M., Ritch A., Violot G., Santolini M., Tzovaras B.G., Stringhini S., Kaiser L., Pradeau J.F., Joost S., Guessous I. Detection of spatiotemporal clusters of COVID-19–associated symptoms and prevention using a participatory surveillance app: protocol for the @choum study. JMIR Res. Protoc. 2021;10(10):E30444. doi: 10.2196/30444. Https//Www.Researchprotocols.Org/2021/10/E30444. 10 (2021) e30444. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 102.Bernard R., Bowsher G., Sullivan R. COVID-19 and the rise of participatory sigint: an examination of the rise in government surveillance through mobile applications. Am. J. Publ. Health. 2020;110:1780–1785. doi: 10.2105/AJPH.2020.305912. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 103.Zuboff S. Big other: surveillance capitalism and the prospects of an information civilization. J. Inf. Technol. 2015;30:75–89. doi: 10.1057/JIT.2015.5. 2015 301. [DOI] [Google Scholar]
- 104.Zuboff S. 2019. Surveillance Capitalism and the Challenge of Collective Action; pp. 10–29. Https://Doi.Org/10.1177/1095796018819461. 28. [DOI] [Google Scholar]
- 105.Kitchin R. 2020. Civil Liberties or Public Health, or Civil Liberties and Public Health? Using Surveillance Technologies to Tackle the Spread of COVID-19; pp. 1–20. Https://Doi.Org/10.1080/13562576.2020.1770587. [DOI] [Google Scholar]
- 106.Garrett P.M. ‘Surveillance capitalism, COVID-19 and social work’: a note on uncertain future(s) Br. J. Soc. Work. 2021 doi: 10.1093/BJSW/BCAB099. [DOI] [Google Scholar]
- 107.Ram N., Gray D. Mass surveillance in the age of COVID-19. J. Law Biosci. 2020;7:1–17. doi: 10.1093/JLB/LSAA023. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 108.Newton K. Government communications, political trust and compliant social behaviour: the politics of covid-19 in Britain, polit. Far E. Q. 2020;91:502–513. doi: 10.1111/1467-923X.12901. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 109.Nabben K., Gardner-Stephen P., Poblet M. Identifying and mitigating humanitarian challenges to COVID-19 contact tracing, 2020. IEEE Glob. Humanit. Technol. Conf. GHTC. 2020;2020 doi: 10.1109/GHTC46280.2020.9342852. [DOI] [Google Scholar]
- 110.Bano M., Zowghi D., Arora C. Requirements, politics, or individualism: what drives the success of COVID-19 contact-tracing apps? IEEE Softw. 2021;38:7–12. doi: 10.1109/MS.2020.3029311. [DOI] [Google Scholar]
- 111.Solomon D.H., Bucala R., Kaplan M.J., Nigrovic P.A. The “infodemic” of COVID-19. Arthritis Rheumatol. 2020;72:1806–1808. doi: 10.1002/ART.41468. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 112.Zarocostas J. How to fight an infodemic. Lancet. 2020;395:676. doi: 10.1016/S0140-6736(20)30461-X. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 113.Zeng J., hong Chan C. A cross-national diagnosis of infodemics: comparing the topical and temporal features of misinformation around COVID-19 in China, India, the US, Germany and France. Online Inf. Rev. 2021;45:709–728. doi: 10.1108/OIR-09-2020-0417/FULL/XML. [DOI] [Google Scholar]
- 114.Madraki G., Grasso I., Otala J.M., Liu Y., Matthews J. 2021. Characterizing and Comparing COVID-19 Misinformation across Languages, Countries and Platforms, Web Conf. 2021 - Companion World Wide Web Conf; pp. 213–223. WWW 2021. [DOI] [Google Scholar]
- 115.Chan E.Y., Saqib N.U. Privacy concerns can explain unwillingness to download and use contact tracing apps when COVID-19 concerns are high. Comput. Hum. Behav. 2021;119:106718. doi: 10.1016/J.CHB.2021.106718. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 116.Degeling C., Hall J., Johnson J., Abbas R., · Shopna Bag. Gilbert G.L. Should digital contact tracing technologies be used to control COVID-19? Perspectives from an Australian public deliberation. Health Care Anal. 2021;2021:1–18. doi: 10.1007/S10728-021-00441-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 117.Bradford L., Aboy M., Liddell K. COVID-19 contact tracing apps: a stress test for privacy, the GDPR, and data protection regimes. J. Law Biosci. 2020;7:1–21. doi: 10.1093/JLB/LSAA034. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 118.Saw A.E., Main L.C., Robertson S., Gastin P.B. Sport.; Basel, Switzerland: 2017. Athlete Self-Report Measure Use and Associated Psychological Alterations; p. 5. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 119.Watts D. SSRN Electron. J.; 2020. COVIDSafe, Australia's Digital Contact Tracing App: the Legal Issues. [DOI] [Google Scholar]
- 120.Saheb T., Saheb T., Carpenter D.O. Mapping research strands of ethics of artificial intelligence in healthcare: a bibliometric and content analysis. Comput. Biol. Med. 2021;135:104660. doi: 10.1016/J.COMPBIOMED.2021.104660. [DOI] [PubMed] [Google Scholar]
- 121.Sheikh A., Anderson M., Albala S., Casadei B., Franklin B.D., Richards M., Taylor D., Tibble H., Mossialos E. Health information technology and digital innovation for national learning health and care systems. Lancet Digit. Health. 2021;3 doi: 10.1016/S2589-7500(21)00005-4. e383–e396. [DOI] [PubMed] [Google Scholar]
- 122.Naudé W. Artificial intelligence vs COVID-19: limitations, constraints and pitfalls. AI Soc. 2020;35:761–765. doi: 10.1007/S00146-020-00978-0. 2020 353. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 123.Agbehadji I.E., Awuzie B.O., Ngowi A.B., Millham R.C. Review of big data analytics, artificial intelligence and nature-inspired computing models towards accurate detection of COVID-19 pandemic cases and contact tracing. Int. J. Environ. Res. Publ. Health. 2020;17:5330. doi: 10.3390/IJERPH17155330. 17 (2020) 5330. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 124.Uohara M.Y., Weinstein J.N., Rhew D.C. 2020. The Essential Role of Technology in the Public Health Battle against COVID-19; pp. 361–367. Https://Home.Liebertpub.Com/Pop. 23. [DOI] [PubMed] [Google Scholar]
- 125.Nguyen N.A. Int. Conf. ICT. Smart Soc.; IEEE: 2014. Critical factors facilitating online services delivery: a cross-country study; pp. 176–181. 2014. [DOI] [Google Scholar]
- 126.Sun R., Wang W., Xue M., Tyson G., Camtepe S., Ranasinghe D.C. 2021. An Empirical Assessment of Global COVID-19 Contact Tracing Applications; pp. 1085–1097. [DOI] [Google Scholar]
- 127.Sharma T., Dyer H.A., Bashir M. Enabling user-centered privacy controls for mobile applications. ACM Trans. Internet Technol. 2021;21 doi: 10.1145/3434777. [DOI] [Google Scholar]
- 128.Majeed A., Hwang S.O. A comprehensive analysis of privacy protection techniques developed for COVID-19 pandemic. IEEE Access. 2021;9:164159–164187. doi: 10.1109/ACCESS.2021.3130610. [DOI] [Google Scholar]
- 129.Ayalon O., Toch E. User-centered privacy-by-design: evaluating the appropriateness of design prototypes. Int. J. Hum. Comput. Stud. 2021;154:102641. doi: 10.1016/J.IJHCS.2021.102641. [DOI] [Google Scholar]
- 130.Cavoukian A. Privacy by design: the 7 foundational principles. Inf. Priv. Comm. Ontario. 2009 https://oarc.duke.edu/sites/default/files/documents/Privacy by Design - 7 Foundational Principles.pdf Canada . 5. accessed. [Google Scholar]
- 131.Wirth F.N., Johns M., Meurers T., Prasser F. Citizen-centered mobile health apps collecting individual-level spatial data for infectious disease management: scoping review. JMIR Mhealth Uhealth. 2020;8(11):E22594. doi: 10.2196/22594. Https//Mhealth.Jmir.Org/2020/11/E22594. 8 (2020) e22594. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 132.Jacob S., Lawarée J. 2020. The Adoption of Contact Tracing Applications of COVID-19 by European Governments; pp. 44–58. Https://Doi.Org/10.1080/25741292.2020.1850404. 4. [DOI] [Google Scholar]
- 133.Tahir S., Tahir H., Sajjad A., Rajarajan M., Khan F. Privacy-preserving COVID-19 contact tracing using blockchain. J. Commun. Netw. 2021;23:360–373. doi: 10.23919/JCN.2021.000031. [DOI] [Google Scholar]
- 134.Phanden R.K., Mathiyazhagan K., Kumar R., Davim J.P. Springer Nature; 2021. Advances in Industrial and Production Engineering : Select Proceedings of FLAME 2020.https://books.google.com/books/about/Advances_in_Industrial_and_Production_En.html?id=sdoeEAAAQBAJ accessed. [Google Scholar]
- 135.Bashir I. third ed. Packt Publishing; Limited: 2020. Mastering Blockchain a Deep Dive into Distributed Ledgers, Consensus Protocols, Smart Contracts, DApps, Cryptocurrencies, Ethereum, and More.https://books.google.com/books/about/Mastering_Blockchain.html?id=ZZ_6DwAAQBAJ accessed. [Google Scholar]
- 136.Csernatoni R. 2020. New States of Emergency: Normalizing Techno-Surveillance in the Time of COVID-19; pp. 301–310. Https://Doi.Org/10.1080/23340460.2020.1825108. 6. [DOI] [Google Scholar]
- 137.Jones K., Thompson R. To use or not to use a COVID-19 contact tracing app: mixed methods survey in Wales. JMIR Mhealth Uhealth. 2021;9(11):E29181. doi: 10.2196/29181. Https//Mhealth.Jmir.Org/2021/11/E29181. 9 (2021) e29181. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 138.Thomas R., Michaleff Z.A., Greenwood H., Abukmail E., Glasziou P. Concerns and misconceptions about the Australian government's COVIDSafe app: cross-sectional survey study, JMIR public heal. Surveillance. 2020;6(4):E23081. doi: 10.2196/23081. Https//Publichealth.Jmir.Org/2020/4/E23081. 6 (2020) e23081. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 139.Perez Vallejos E., Dowthwaite L., Creswich H., Portillo V., Koene A., Jirotka M., McCarthy A., McAuley D. The impact of algorithmic decision-making processes on young people's well-being. Health Inf. J. 2021;27 doi: 10.1177/1460458220972750. [DOI] [PubMed] [Google Scholar]
- 140.Lo B., Sim I. 2020. Ethical Framework for Assessing Manual and Digital Contact Tracing for COVID-19; pp. 395–400. Https://Doi.Org/10.7326/M20-5834. 174. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 141.Montanari Vergallo G., Zaami S., Marinelli E. The COVID-19 pandemic and contact tracing technologies, between upholding the right to health and personal data protection. Eur. Rev. Med. Pharmacol. Sci. 2021;25:2449–2456. doi: 10.26355/EURREV_202103_25286. [DOI] [PubMed] [Google Scholar]
- 142.Abuhammad S., Khabour O.F., Alzoubi K.H. COVID-19 contact-tracing technology: acceptability and ethical issues of use, patient prefer. Adherence. 2020;14:1639. doi: 10.2147/PPA.S276183. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 143.Alanoca S., Guetta-Jeanrenaud N., Ferrari I., Weinberg N., Çetin R.B., Miailhe N. Digital contact tracing against COVID-19: a governance framework to build trust. Int. Data Priv. Law. 2021;11:3. doi: 10.1093/IDPL/IPAB001. [DOI] [Google Scholar]
- 144.Kazienko P., Adamski M. AdROSA—adaptive personalization of web advertising. Inf. Sci. 2007;177:2269–2295. doi: 10.1016/J.INS.2007.01.002. [DOI] [Google Scholar]
- 145.Surwase G., Sagar A., Kademani B.S., Bhanumurthy K. Bosla Natl. Conf. Proc. 2011. Co-citation analysis: an overview.https://core.ac.uk/download/pdf/11889658.pdf accessed. [Google Scholar]
- 146.Hicks D. Limitations of Co-citation analysis as a tool for science policy. Soc. Stud. Sci. 1987;17:295–316. doi: 10.1177/030631287017002004. [DOI] [Google Scholar]