Abstract
The COVID-19 pandemic has caused serious consequences in the last few months and trying to control it has been the most important objective. With effective prevention and control methods, the epidemic has been gradually under control in some countries and it is essential to ensure safe work resumption in the future. Although some approaches are proposed to measure people's healthy conditions, such as filling health information forms or evaluating people's travel records, they cannot provide a fine-grained assessment of the epidemic risk. In this paper, we propose a novel epidemic risk assessment method based on the granular data collected by the communication stations. We first compute the epidemic risk of these stations in different intervals by combining the number of infected persons and the way they pass through the station. Then, we calculate the personnel risk in different intervals according to the station trajectory of the queried person. This method could assess people's epidemic risk accurately and efficiently. We also conduct extensive simulations and the results verify the effectiveness of the proposed method.
Keywords: COVID-19, communication station risk, epidemic risk assessment, personnel risk
I. Introduction
THE outbreak of the coronavirus (COVID-19) pandemic has caused very serious consequences in the last few months. According to the statistics, as of July 21 of 2020, the COVID-19 pandemic has spread to 215 counties around the world and a total of 15 million people have been infected. The epidemic has caused nearly 610 000 deaths and caused huge economical losses in almost every country. According to the research report [27], the COVID-19 pandemic has caused 3.8 trillion economic losses and 147 million people lost their jobs. Due to the strong infectious nature of the virus, many cultural activities and sport events have been suspended or cancelled, which has greatly affected people's daily life. The COVID-19 pandemic has become a very serious problem in every country, and the most important and crucial thing is to fight the epidemic.
Many governments have issued policies to fight the epidemic, such as quarantine, isolation guidelines, social distancing, and suspending many large gathering activities. Meanwhile, many scientific researchers have denoted themselves to the prevention and control of the epidemic. Medical experts are studying the characteristics and the spreading ways of the virus, and are committed to develop vaccines against this virus. For example, the clinical characteristics of COVID-19 patients are studied in [39] and it provided reliable medical evidence for the treatment and prevention of COVID-19. In [37], it verifies that the strict prevention and control methods in China are effective in protecting people from the virus. With the fast development of information technologies [14], [16], [43], [44], many scientific researchers from the computer science field have proposed efficient methods to assist the prevention of the epidemic. For example, a knowledge graph of the COVID-19 is introduced in [7], which discusses the basis knowledge of the epidemic. A mathematical model of predicting the spread of the COVID-19 pandemic is proposed in [20], which helps understand the spreading range and impact of the epidemic. To acquire the public's perception of the COVID-19 epidemic, an intelligent model is introduced in [26] by analyzing twitter data.
Due to the effective prevention and control methods, the epidemic has gradually been under control in some countries, such as in China. Currently, it is an important issue to resume the work and production safely under this situation. How to assess the personnel's epidemic risk is an essential and important problem in assisting resuming work safely? There are mainly two approaches taken by the government and enterprises. The first one is to ask people to report his/her daily health information, such as filling health information forms. However, some people might report the information incorrectly intentionally or accidentally, which would cause serious consequences if some infected people are allowed to work with other colleagues. The second approach is adopting applications that show the epidemic risk according to people's travel records (such as flights, trains, etc) and the cities he/she has been in the last half a month. However, many applications compute the epidemic risk by judging whether the person has been to a city where infected cases exist or not; it is inaccurate such as a healthy person drives through the city. In addition, a city or a district contains a large number of people, computing the epidemic risk in a more refined way is needed in assisting resuming work safely.
In this paper, we propose a novel communication station based method to assess the people's epidemic risk. Since almost everyone is using mobile phones for communication, it is sufficient to judge a person's trajectory according to the mobile phone's trajectory. A mobile phone would exchange information with the nearest communication station timely, and a communication station covers a relative small range, such as a few hundred meters in residential areas and a few kilometers in open areas such as a highway. The station records the time interval that a mobile phone passes through its communication range, and it provides more accurate information for assessing the epidemic risk. Compared with the traditional two above discussed approaches, the communication station based epidemic risk assessment method could utilize more fine-grained data to provide more accurate assessment.
There are three challenges in handling the epidemic risk assessment by the communication station information. First of all, people's trajectory data (collected by the communication stations) has significant temporal and spatial characteristics, such as the time interval of passing through the communication station is the temporal characteristic while the physical locations of the station is the spatial characteristic. It is difficult and inefficient to utilize such data directly. Second, there are many different ways that a person passes through or stays within a station, such as driving a car, walking, staying at home, or staying in the office, it is necessary to consider different situations in assessing a person's epidemic risk. Third, some people may move together with some infected persons, it is needed to find out the person with high epidemic risk according to the station's information.
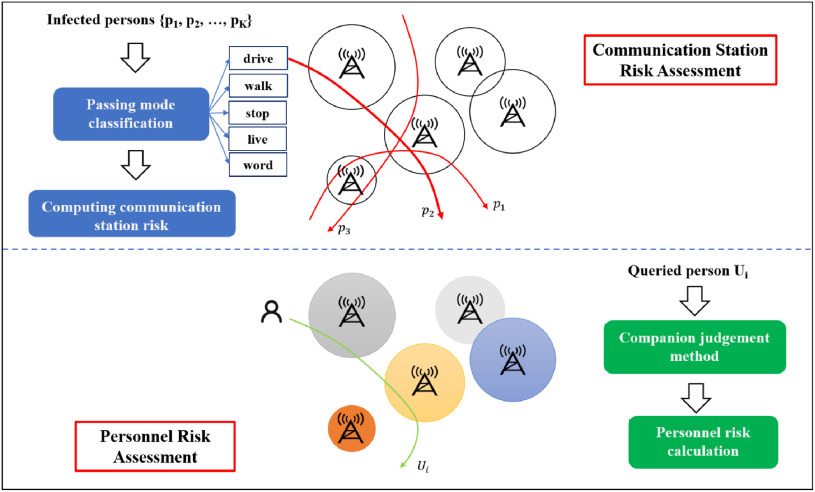
In this paper, our proposed epidemic risk assessment method addressed all these challenges. As depicted in Fig. 1, there are two stages in assessing a person's epidemic risk. We first evaluate the epidemic risk of each communication station in different time intervals according to the trajectories of the infected people. Then, we evaluate a person's epidemic risk according to the stations that he/she passes through. By calculating the epidemic risk of each station in each time interval, we could efficiently utilize people's trajectory data, which addresses the first challenge. In the first stage of our method, we propose a passing mode classification method where five passing modes (drive, walk, stop, live, and work) reflect how the person passes through a communication station. By assigning different risk weights to these models, such as driving through the station has less risk weight than walking, we can compute the epidemic risk of each station in each time interval and it addresses the second challenge. In the second stage of our method, we introduce a companion judgement method which automatically decides whether two people move together. After that, we compute the epidemic risk of a person according to the epidemic risks of the passed communication stations, which addresses the third challenge.
Fig. 1.
The epidemic risk assessment method has two stages: the first stage computes the risk of each communication station while the second stage computes the risk of the queried person.
In order to verify the efficiency of the proposed method, we also conduct extensive simulations. We generate a large number of communication stations and the trajectories of some infected persons according to the released information by the Centers for Disease Control (CDC). We generate different types of people's trajectory and our method could compute each person's epidemic risk accurately, which verifies the effectiveness of the proposed method. We summarize the contributions of this work as follows:
-
1)
We propose a novel epidemic risk assessment method on the basis of the communication station's information, which provides a fine-grained assessment in assisting resuming work safely;
-
2)
We first compute the epidemic risks of each station in different time intervals, and then a person's epidemic risk is calculated by combining the passed communication stations. This two-stage method could help compute a person's epidemic risk accurately and efficiently;
-
3)
We conduct extensive simulations to evaluate our method and the results confirm its effectiveness.
The rest of the paper is organized as follows. The next section highlights the related work about the COVID-19 epidemic. Then, we introduce the preliminaries in Section III. We introduce the first stage of computing the epidemic risk of each station in Section IV and present the second stage of calculating a person's epidemic risk in Section V. We describe the simulation results in Section VI and we conclude the paper in Section VII.
II. Related Work
During the outbreak of COVID-19 epidemic, there have been a large number of research attempts analyzing the epidemic's characteristics, providing prevention and control applications, and proposing epidemic risk assessment algorithms. In this section, we introduce these related attempts in three categories. First, we introduce research on the characteristics of the epidemic in Section II-A, then we provide an overview of various methods and applications to prevent and control the epidemic in Section II-B. Finally, we discuss some methods in assessing the epidemic risk in Section II-C.
A. Characteristics of the COVID-19 Epidemic
In December of 2019, the first released case of the unknown pneumonia appeared in Wuhan [18]. Though high-throughput sequencing, it revealed a novel coronavirus that is named COVID-19 officially [25]. The new virus resembled severe acute respiratory syndrome coronavirus (SARS-CoV) [50].
The COVID-19 coronavirus spreads rapidly from person to person, with a median incubation period of three days and a relatively low fatality rate. By studying some infected patients, some preliminary studies immediately concluded that older males and those with comorbid conditions are more likely to become severe cases. Considering the spreading routes, the virus spreads mainly through direct contact and droplets, and it is likely to be transmitted even in a brief contact with an infected person, such as chatting and/or eating. Until now, there is no directly effective vaccine against the virus and the treatments are mainly symptomatic support therapy, as many antibiotics and antiviral drugs were confirmed ineffective. Even though the COVID-19 virus is highly contagious, according to the latest research, some control methods have proven to be very effective, particularly wearing masks, which could prevent most infections [3], [11], [13], [21], [28], [29], [35], [36], [47].
Some works characterized the temporal and spatial dynamics of the COVID-19 epidemic. The spatial and temporal scan statistics are adopted to quantify the trends of the COVID-19 according to the weekly released infected cases in [46], and it is suggested that the temporal and spatial trends during the spread of the COVID-19 epidemic should be taken into consideration when people are prepared to return to their normal routines.
B. Applications of Epidemic Prevention and Control
With the fast development of information technologies [2], [8]–[10], [15], [42], many methods have been proposed for the epidemic prevention and control.
The Internet of Things (IoT) have been adopted in medicine and it is referred to as the medical IoT (MIoT) [4], [40]. MIoT aims to establish a decision-oriented big data analysis model that is supported by many latest information technologies such as communication technologies, electronics, biology, and medicine. A point of view is proposed in [33] that human were ill-prepared to deal with the challenges the COVID-19 epidemic has posed. Future research should attempt to address the uses and implications of IoT technologies for mapping the spread of infection.
In China, nCapp (COVID-19 Intelligent Diagnosis and Treatment Assistant Program) [1] is proposed for early COVID-19 diagnose and enhance treatment. According to the available data, questionnaire and examination results, the program can automatically classify a case to different diagnostic results such as confirmed case, suspected case, or normal cases. The application also updates a real-time database of the COVID-19 epidemic, and updates the diagnostic model timely on the basis of the latest confirmed case to improve the diagnostic accuracy. In addition, nCapp can guide physicians, specialists, and managers in counseling and prevention of the epidemic. The ultimate goal of the application is to raise the level of COVID-19 diagnosis and to improve the treatment of different doctors in different hospitals to a high level (such as national and international levels) through the assistance of the system. 5 G wireless transmission technology is also introduced in the field of medical care for faster video transmission in [6], and it is suggested that more cutting-edge technologies such as IoT, big data, and artificial intelligence could largely improve the medical services [38].
Some works also analyze the spreading of the epidemic. The susceptible exposed infectious recovered (SEIR) model is introduced in [19] to analyze the effectiveness of the quarantine approaches of Wuhan, and the result shows that by reducing the contacts with infected cases or potentially infected cases, many interventions could reduce the number of infected cases and help prevent the spread of the virus efficiently by these quarantine and isolation methods. A disease spreading model based on SEIR is proposed in [5] to simulate the spreading of the disease and it uses several parameters to quantify different ways to control the disease spreading. A probabilistic model that describes the worldwide spread of the infectious diseases is proposed in [17] and it demonstrates that a forecast of the geographical spread of the epidemic is indeed possible.
C. Assessment of the Epidemic Risk
The outbreak and spread of the COVID-19 epidemic is a complex system constituted by etiology, host, and environment. It is not only related to the spread method between people, but also related to the crowd of social relations and daily behaviors [30]. Particularly, in a large-scale mobile population, close contact with each other would directly accelerate the spread of the virus [32], [45]. To assess the epidemic risk of a specific district of a specific person accurately is important for timely epidemic control, but is also very challenging.
It is examined in [31] that several key factors are important in forecasting the epidemic risk. It is assumed that several factors such as the geographical scale and the temporal duration are identified as important components in predicting the epidemic risk accurately. A similar assessment system has been developed in [41] to forecast the probabilities of anomalously high and low malaria incidence, with a dynamical, seasonal-timescale, multi-model ensemble prediction model of the climate. This forecast system has been successfully applied to the prediction of malaria risk in Botswana, where links between malaria and climate variability are well established, and it has a comparably high level of prediction accuracy. A risk assessment method of the infectious disease is presented in [12], which calculates the risk based on the spatiotemporal trajectory data. This method uses the spatial density and the average speed of the users to determine the risk of infectious disease, and it is assumed that it can be utilized to evaluate the high-risk areas according to different data sources. A new approach of the epidemic risk assessment is proposed in [34], which constructs a novel data-driven framework for assessing the epidemic risk of a geographical area and identifying high-risk areas within a country. The risk value is evaluated as a function of three different components: the hazard of the disease, the exposure of the area and the vulnerability of its inhabitants.
In this paper, we utilize people's trajectory to assess the epidemic risk. Some works utilize WiFI sensing technology or crowdsensed data to track human mobility [22]–[24], [48], [49]. Different from these works, we utilize the trajectory data that are collected by the communication stations. On the basis of that data, we can calculate the epidemic risk of the stations and the epidemic risk of each person using a more integrated approach.
III. Preliminaries
In this section, we first introduce the system model, including the commonly adopted notations in the paper. Then, we present formal definitions of the epidemic risk assessment problem, including communication station risk assessment and personnel risk assessment.
A. System Model
For the convenience of description, we denote the communication stations as set 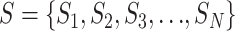 where
where 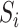 represents a specific and unique station. Each communication station has its position coordinates and we denote the coordinates of station
represents a specific and unique station. Each communication station has its position coordinates and we denote the coordinates of station 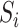 as
as 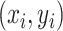 , which represent the longitude and latitude of the communication station respectively. Denote a set of
, which represent the longitude and latitude of the communication station respectively. Denote a set of 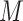 different persons as
different persons as 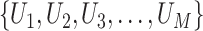 (we omit the situation that a person carries multiple mobile phones). For each person
(we omit the situation that a person carries multiple mobile phones). For each person 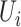 who moves among the communication stations, each station
who moves among the communication stations, each station 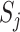 would record the time when the person enters and leaves the communication range and we denote the time interval as
would record the time when the person enters and leaves the communication range and we denote the time interval as 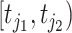 where
where 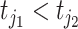 .
.
In practical scenarios, different communication stations have different sensing ranges and a person's mobile phone might be connected to multiple stations. In addition, when a person enters indoor or goes underground, the stations might not detect the person correctly. To simplify the problem, we assume a person's mobile phone is only connected to the nearest station at any time; if a person is not detected by any station, we assume he/she is connected to the previous station. Hence, we can denote the communication station trajectory of person 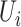 as a sequence
as a sequence 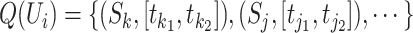 , where
, where 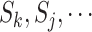 are the communication stations that the person passed.
are the communication stations that the person passed.
In order to count the number of persons passing through a specific communication station in different time intervals, we first divide the time period of everyone passing through the station according to a certain time granularity 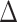 , which implies the time is slotted with length
, which implies the time is slotted with length 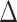 . Therefore, denoting the outbreak time of the epidemic as the initial time slot 0, we denote the other time segments as
. Therefore, denoting the outbreak time of the epidemic as the initial time slot 0, we denote the other time segments as 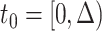 ,
, 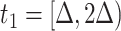 ,
, 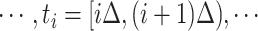 . In order to compute the epidemic risk in a more fine-grained way, we set
. In order to compute the epidemic risk in a more fine-grained way, we set 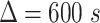 in our simulation and each time segment contains 10 minutes. Actually,
in our simulation and each time segment contains 10 minutes. Actually, 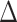 can be set as other values according to the system requirements. All these notation are listed in Table I.
can be set as other values according to the system requirements. All these notation are listed in Table I.
TABLE I. Notations for the Epidemic Risk Assessment Problems.
| Notation | Description |
|---|---|
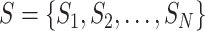
|
The communication stations |
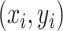
|
The coordinates of station 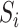
|
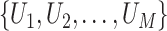
|
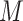 different persons different persons |
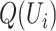
|
The communication station trajectory of user 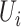
|
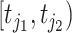
|
The time interval of passing 
|
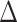
|
The time length of each slot |
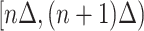
|
The time interval of 
|
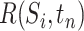
|
The communication station risk of 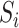 during during 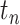
|
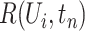
|
The personnel risk of 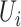 during during 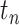
|
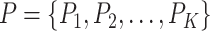
|
A set of infected and suspected persons |
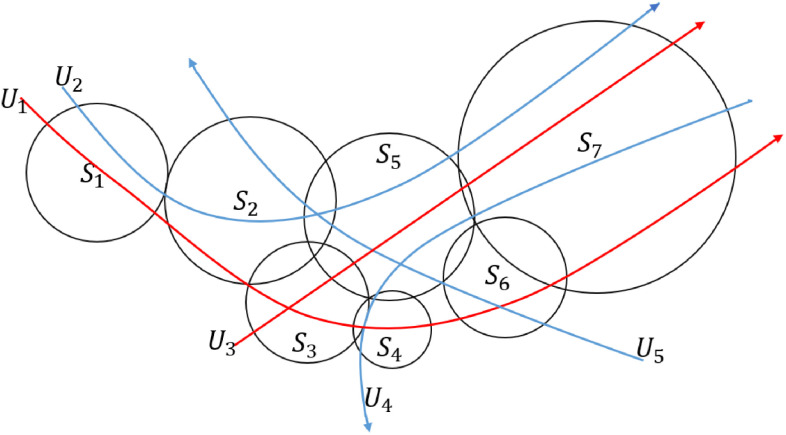
For example, seven communication stations and five persons are depicted in Fig. 2, where different stations have different communication ranges as the circles. Considering the trajectory of person 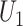 who passes through stations
who passes through stations 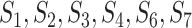 , denote the trajectory as
, denote the trajectory as 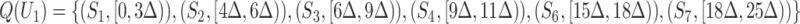 , which represents the enter and leave time of each communication station. Similarly, suppose person
, which represents the enter and leave time of each communication station. Similarly, suppose person 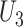 passes through stations
passes through stations 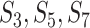 sequentially and we denote the trajectory as
sequentially and we denote the trajectory as 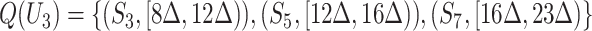 . With this method, we can efficiently represent each person's trajectory by the communication stations’ information.
. With this method, we can efficiently represent each person's trajectory by the communication stations’ information.
Fig. 2.
An illustration example with seven communication stations and five persons.
B. Problem Definition
In this paper, we assess the epidemic risk of both the communication stations and a specific person. As we divided time into different slots, we denote the communication station risk as 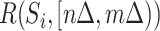 , which implies the epidemic risk value of the communication station
, which implies the epidemic risk value of the communication station 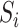 during the time period
during the time period 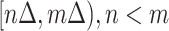 . When
. When 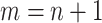 ,
, 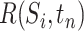 represents the epidemic risk value of
represents the epidemic risk value of 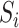 during time segment
during time segment  . Similarly, we denote the personnel risk as
. Similarly, we denote the personnel risk as 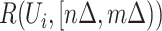 , which implies the epidemic risk value of person
, which implies the epidemic risk value of person 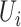 during the time period
during the time period 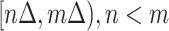 . Notice that,
. Notice that, 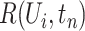 represents the epidemic risk value during time segment
represents the epidemic risk value during time segment 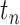 .
.
Assuming the current time segment is 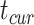 , we formulate the problem of computing the communication station risk as:
, we formulate the problem of computing the communication station risk as:
Problem 1: —
Given a set of infected and suspected persons
, denote the trajectories of them as
, compute the communication station risk
for each station
in each time segment
.
Taking Fig. 2 as the example, supposing 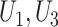 are patients (red line), it is easy to check that
are patients (red line), it is easy to check that 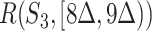 is high since both
is high since both 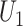 and
and 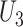 pass through the station during the time segment. We need to compute the epidemic risk of all these stations and then to calculate the other persons’ epidemic risk values.
pass through the station during the time segment. We need to compute the epidemic risk of all these stations and then to calculate the other persons’ epidemic risk values.
Computing the communication station risk plays a fundamental role in calculating the personnel risk. We formulate the problem of calculating the personnel risk as:
Problem 2: —
Given a person
and the trajectory
, calculate the personnel risk
for the person in each segment
.
Normally, it is more important to assess the personnel risk of a specific person during a long period, for example many places need to compute the risk within the last 14 days. Hence, we define the personnel risk during time period 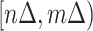 as
as
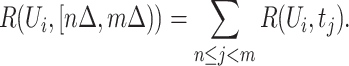 |
Considering the work resumption and production, many governments and enterprises require a person's risk to be relatively low (even 0) within the past 14 days. Hence, we can calculate the personnel risk and grant the admission if the risk is 0.
IV. Communication Station Risk Assessment
In this section, we introduce the epidemic risk computation method of the communication stations. According to the station trajectories of the patients  , the goal is to calculate the risk value of each station
, the goal is to calculate the risk value of each station 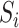 in any time interval
in any time interval 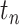 as
as 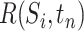 . There are many different ways that a person passes through a communication station, such as driving a car or walking. We first propose a passing mode classification method in Section IV-A, which introduces five different passing modes. Then, we present a statistic method counting the persons of different passing modes in Section IV-B and we compute the communication station risk in Section IV-C combining these modes.
. There are many different ways that a person passes through a communication station, such as driving a car or walking. We first propose a passing mode classification method in Section IV-A, which introduces five different passing modes. Then, we present a statistic method counting the persons of different passing modes in Section IV-B and we compute the communication station risk in Section IV-C combining these modes.
A. Passing Mode Classification
People could pass through a communication station in different ways, which would affect the station risk computation. For example, patients driving in a car have less effect than patients who are walking during the station range, hence it is necessary to classify a person's station trajectory into different passing modes. In this paper, we consider five different passing modes which are described as follows:
-
1)
Driving mode: a person passes through the communication station in a car or bus (denote the mode as drive for short);
-
2)
Walking mode: a person walks within the communication station's range (denote the mode as walk for short);
-
3)
Stop mode: a person stays in a communication station for a long time, for example, he is in a restaurant or a market (denote the mode as stop for short);
-
4)
Living mode: a person lives at home which is within the communication range (denote the mode as live for short);
-
5)
Working mode: a person works in a building which is within the communication range (denote the mode as work for short).
Different modes should be assigned with different risk weights in computing the communication station's risk. For example, patients of walk mode have larger risk weight than patients of drive mode, work mode has lager risk than live mode since it is more likely to contact more people in the working mode. We introduce the details in classifying the passing modes. Considering the station trajectory of a patient 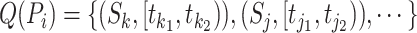 , the passing mode classification method aims at classifying the trajectory segment in each communication station
, the passing mode classification method aims at classifying the trajectory segment in each communication station 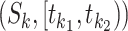 to the five passing modes. Since the presented five modes have significant patterns, we design some features and rules for classifying the passing modes.
to the five passing modes. Since the presented five modes have significant patterns, we design some features and rules for classifying the passing modes.
1). Driving Mode
Commonly speaking, a person would pass a communication station in a short time by driving a car or taking a bus, hence an important feature of the driving mode is that the time period passing through the station is quite short. We formulate the first classifying rule as
 |
where 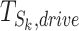 is a parameter that reflects the time threshold of driving through station
is a parameter that reflects the time threshold of driving through station 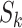 . Suppose the station range is
. Suppose the station range is 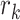 , for example
, for example 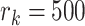 meters in the resident areas or
meters in the resident areas or 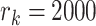 meters in the open areas, we can set
meters in the open areas, we can set  as
as 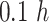 and
and 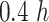 respectively, assuming the driving speed is no less than
respectively, assuming the driving speed is no less than 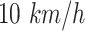 . If the trajectory segment
. If the trajectory segment 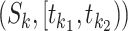 satisfies Eqn. (1), we call it a potential driving segment.
satisfies Eqn. (1), we call it a potential driving segment.
Notice that, a person may be very close to the edge of the station range, when the person walks outside the range, the station trajectory may be classified to the driving mode. Hence, we introduce a new feature which requires at least 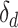 continuous potential driving segments. For example, the segment
continuous potential driving segments. For example, the segment 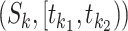 satisfies Eqn. (1), we need to check whether the following
satisfies Eqn. (1), we need to check whether the following 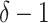 segments also satisfy the equation. The feature could help better classify the person's station trajectory.
segments also satisfy the equation. The feature could help better classify the person's station trajectory.
In this paper, we only adopt these two features and they could achieve good result in classifying the driving mode. Obviously, more features could achieve better results and it is an important work to add more features during the classification.
2). Walking Mode
Similarly, we assume the time period passing through the communication station is relatively larger than the driving mode. Hence, we formulate the basic classifying rule as:
 |
where 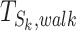 is a parameter that reflects the time threshold of walking through station
is a parameter that reflects the time threshold of walking through station 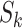 . We can assume the slowest walk speed as
. We can assume the slowest walk speed as 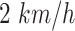 and the threshold can be correspondingly calculated. For example,
and the threshold can be correspondingly calculated. For example, 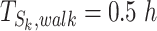 when
when 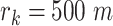 and
and 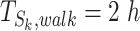 when
when 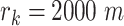 . These parameters can be designed by different situations. If the trajectory segment
. These parameters can be designed by different situations. If the trajectory segment 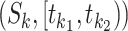 satisfies Eqn. (1), we call it a potential walking segment.
satisfies Eqn. (1), we call it a potential walking segment.
Since there might also exist some counterexamples, we also add another feature which requires the following 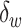 segments should also be classified as potential ones.
segments should also be classified as potential ones.
3). Stop Mode
Suppose a person is in a restaurant or a market, he/she would stay within the communication range for a long time. Hence, we formulate the basic classifying rule as:
 |
More features can be extracted and we only use the simple one in classifying the stop mode in this paper. In order to better assist work resumption, we introduce two more modes: living mode and working mode. These two modes share the same classifying rule as the stop mode, and we introduce how to distinguish them as follows.
4). Living Mode
Living mode has some special features other than the stop mode. First, the station range is normally small since the many people are communicating through the station. Second, the time interval belongs to a person's rest time, such as in the evening. Third, the living mode segments of a person's trajectory follow a quite similar schedule, since a normal person go back home regularly.
Hence, we can first adopt the feature: the station range 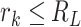 where
where 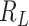 is a range parameter such as
is a range parameter such as 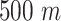 . Then, we describe the second feature as
. Then, we describe the second feature as 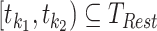 which implies the time interval belongs to the person's rest time, such as
which implies the time interval belongs to the person's rest time, such as 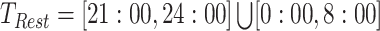 . The third feature is extracted by checking the patterns in several days. With these additional features, we can classify a trajectory segment from the stop mode to the living mode in a more refined way.
. The third feature is extracted by checking the patterns in several days. With these additional features, we can classify a trajectory segment from the stop mode to the living mode in a more refined way.
5). Working Mode
Similar as the living mode, we can extract more features other than the stop mode. First, the station range is normally small and it can formulated as 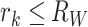 where
where 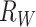 is a range parameter such as
is a range parameter such as 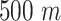 . Second, the time interval belongs to a person's working time and we formulate it as
. Second, the time interval belongs to a person's working time and we formulate it as 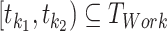 , where
, where 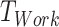 represents a person's working time such as
represents a person's working time such as 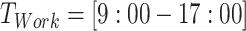 . Third, the working mode segments of a person's trajectory also follow a quite similar schedule, and we can extract the feature by checking the segments in several days or weeks.
. Third, the working mode segments of a person's trajectory also follow a quite similar schedule, and we can extract the feature by checking the segments in several days or weeks.
There might exist many methods to classify the passing mode according to the station trajectory. In this section, we only present a simple method which works on some predefined detection rules. However, this classification method might make incorrect results. For example, on some crowded roads, walking might be faster than driving; the method would not classify the passing mode correctly. Deep neural networks based methods could improve the accuracy and this would be an important and interesting work in the future.
After classifying a person's station trajectory into different passing modes as drive, walk, stop, live, or work, we can represent the trajectory as 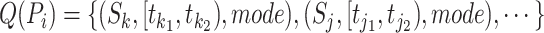 . Since the proposed features are not definitely correct, we need to correct some abnormal results of these segments. For example, the segments of the living mode are usually continuous, and we need to modify some incorrect modes; the segments of the driving mode would be continuous for a sufficient time, and it is incorrect when some scattered living or working segments are located within a long driving segments. Hence, with these modification principles, we can correct some abnormal modes and the method could achieve better classification results.
. Since the proposed features are not definitely correct, we need to correct some abnormal results of these segments. For example, the segments of the living mode are usually continuous, and we need to modify some incorrect modes; the segments of the driving mode would be continuous for a sufficient time, and it is incorrect when some scattered living or working segments are located within a long driving segments. Hence, with these modification principles, we can correct some abnormal modes and the method could achieve better classification results.
B. Statistics on Different Passing Modes
In order to compute the epidemic risk of each communication station, we need to find out how many patients have passed through the station and how do they pass through it. Hence, we introduce the method to computing the number of different passing patients.
Since the station's trajectory has temporal and spatial characteristics, we need to reduce the problem from different dimensions. After dividing the time into slots of equal length 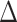 , we can find out the statistical features in each time segment. Denote
, we can find out the statistical features in each time segment. Denote 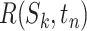 as the station's risk in time segment
as the station's risk in time segment 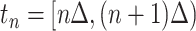 , we need to compute the number of patients who are in different passing modes for each
, we need to compute the number of patients who are in different passing modes for each 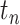 . Denote
. Denote 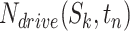 as the number of patients who are in the driving mode when passing
as the number of patients who are in the driving mode when passing 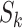 during
during 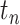 . Similarly, denote
. Similarly, denote 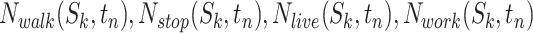 as the number of patients who are in the walking, stop, living, working modes correspondingly.
as the number of patients who are in the walking, stop, living, working modes correspondingly.
To account the number, we first convert a person's station trajectory to a detailed time-segment representation. For each trajectory segment 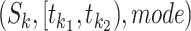 where the passing mode is one of the five introduced modes, find out
where the passing mode is one of the five introduced modes, find out 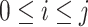 such that
such that 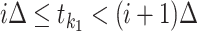 and
and 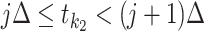 , we convert the segment to time-segment representation as:
, we convert the segment to time-segment representation as:
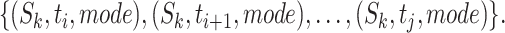 |
Then, the number of patients in the related time segments (from 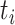 to
to 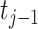 ) can be updated. For example, if the mode is drive,
) can be updated. For example, if the mode is drive, 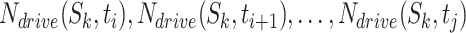 could be updated by adding this instance.
could be updated by adding this instance.
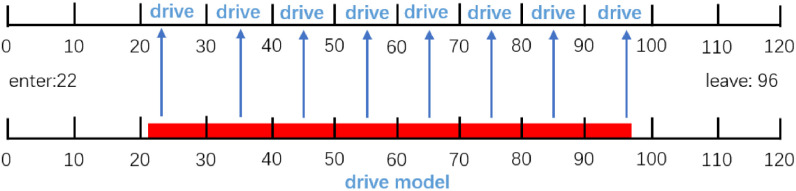
Supposing time length 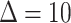 and the trajectory segment is
and the trajectory segment is 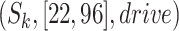 as depicted in Fig. 3, we convert the segment to
as depicted in Fig. 3, we convert the segment to 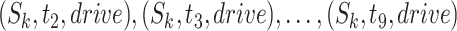 as the upper part of the figure. Then,
as the upper part of the figure. Then, 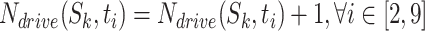 . This step could convert non-aligned time segments to aligned ones for computation.
. This step could convert non-aligned time segments to aligned ones for computation.
Fig. 3.
An illustration example of converting a trajectory segment to a detailed time-segment representation.
After converting all patients’ trajectories, we can compute the number of patients passing through these communication stations in each time segment.
C. The Computation of the Communication Station Risk
As stated above, we assign different risk weights to different passing modes. Denote 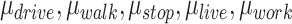 as the risk weights of the driving mode, walking mode, stop mode, living mode and working mode respectively. According to the epidemic features of these modes, the living mode has the highest risk since people living together or in the same building would be infected easily as people rarely take precautions at home. After that, the working mode also has large risk since many people are working together and only a few of them may take precautions. The risk of the stop mode is larger than the walking and driving mode, since people staying in a restaurant, market, or a hospital has larger probability being infected. The walking mode has small risk since most people would take precautions such as wearing masks, while the driving mode has the smallest risk value since patients in a car affect little to the station. Hence, these risk weights satisfy the following inequality:
as the risk weights of the driving mode, walking mode, stop mode, living mode and working mode respectively. According to the epidemic features of these modes, the living mode has the highest risk since people living together or in the same building would be infected easily as people rarely take precautions at home. After that, the working mode also has large risk since many people are working together and only a few of them may take precautions. The risk of the stop mode is larger than the walking and driving mode, since people staying in a restaurant, market, or a hospital has larger probability being infected. The walking mode has small risk since most people would take precautions such as wearing masks, while the driving mode has the smallest risk value since patients in a car affect little to the station. Hence, these risk weights satisfy the following inequality:
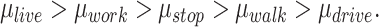 |
Then, we can compute the epidemic risk of the communication station by combining the risks of each passing modes. We formulate the computation process of 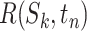 as the following equation:
as the following equation:
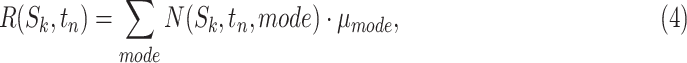 |
where  .
.
Algorithm 1: Communication Station Risk Assessment.
-
1:
List the station trajectories
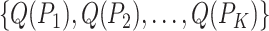 of the patients;
of the patients; -
2:
Initialize
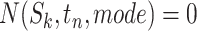 for each station
for each station 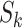 , each time
, each time 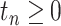 , and each passing mode;
, and each passing mode; -
3:
for each trajectory
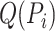 do
do -
4:
for each segment
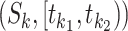 in
in 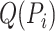 do
do -
5:
Classify the segment to a specific passing mode
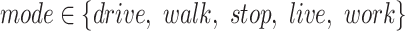 ;
; -
6:
Update the segment as
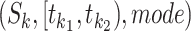 ;
; -
7:
end for
-
8:
Modify the passing mode of each segment by correcting abnormal modes;
-
9:
end for
-
10:
for each trajectory
 do
do -
11:
for each segment
 of
of 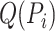 do
do -
12:
Find out
 such that
such that 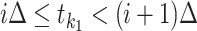 and
and 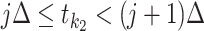 ;
; -
13:
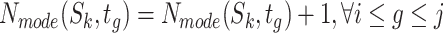 ;
; -
14:
end for
-
15:
end for
-
16:
for each station
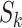 and each time segment
and each time segment 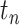 do
do -
17:
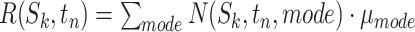 .
. -
18:
end for
Putting it together, we describe the method of computing the communication station risk as Alg. 1. The first two lines initialize the related parameters. The passing mode classification is applied as Lines 4-7 and abnormal modes are corrected on Line 8. Then the statistics on different passing modes are computed as Lines 10-15, and we finally generate the epidemic risk of each communication station as Lines 16-18. After the assessment, the risks are normalized to [0,1] to represent the communication station's risk value.
V. Personnel Risk Assessment
In this section, we introduce the method of calculating personnel risk on the basis of the communication station epidemic. For any person 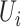 who is to be enquired, for example a person is going to enter a building for work, denote the trajectory as
who is to be enquired, for example a person is going to enter a building for work, denote the trajectory as 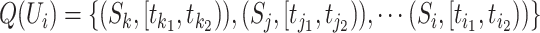 where
where 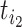 is the current time
is the current time 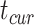 and
and 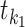 is the start time of the querying (such as 14 days before the current time), the goal is to calculate his personnel risk
is the start time of the querying (such as 14 days before the current time), the goal is to calculate his personnel risk 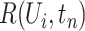 in each time segment
in each time segment 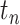 . Commonly speaking, the officer would check the current personnel risk to decide whether the person can return to work.
. Commonly speaking, the officer would check the current personnel risk to decide whether the person can return to work.
Before invoking the communication stations’ risk, we first introduce a companion judgement model which decides whether the queried person has been with any patient together in Section V-A. Then, we propose the personnel risk calculation method according to communication stations the person passed through in Section V-B.
A. Companion Judgement Method
Traditional companion judgement can be fulfilled by checking whether the person has travelled with a infected person simultaneously. For example, the flight information contains each person's detailed data (such as the date of the flight, the seat number of the person, etc). Such travel information could be utilized to judge whether they are in the same plane or in the same train. However, when two persons drive or walk together, such travel information is useless in the judgement. So we introduce a companion judgement method based on the communication stations’ information.
Considering the station trajectory of the queried person 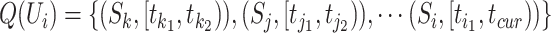 , we first adopt the passing mode classification method in Section IV-A and each trajectory segment
, we first adopt the passing mode classification method in Section IV-A and each trajectory segment 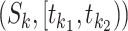 can be classified to a specific passing mode.
can be classified to a specific passing mode.
Since the communication station risk computation method in Section IV has already classified each infected person's trajectory with different passing modes, and these information are stored in memory. Then, we need to judge whether person 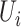 has been together with any infected person
has been together with any infected person 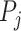 . We describe the method as Alg. 2.
. We describe the method as Alg. 2.
Algorithm 2: Companion Judgement Method.
-
1:
Denote person
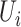 's station trajectory as
's station trajectory as 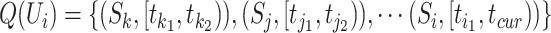 ;
; -
2:
Invoke the passing mode classification method to each segment as
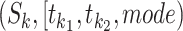 ;
; -
3:
for each infected person's trajectory
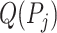 do
do -
4:
Find segments
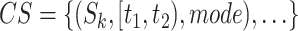 such that they are passing through
such that they are passing through 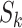 during time period
during time period 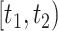 with the same passing mode;
with the same passing mode; -
5:
for each segment
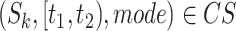 do
do -
6:
if they share the same passing mode in the same station within next
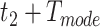 time then
time then -
7:
Return the companion infected person
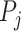 ;
; -
8:
end if
-
9:
end for
-
10:
end for
-
11:
Return the judgement that no companion exists.
The first two lines describe the passing mode classification results of the queried person. For the station trajectory of each infected person 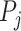 , we find the set of common segments
, we find the set of common segments  such that both people are passing through the station
such that both people are passing through the station 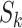 during the time period
during the time period 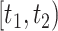 simultaneously with the same passing mode (as Line 4). For each common segment
simultaneously with the same passing mode (as Line 4). For each common segment 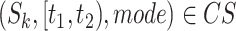 , two people satisfy the companion judgement requirement if they share the passing mode in the next
, two people satisfy the companion judgement requirement if they share the passing mode in the next 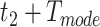 time, where
time, where 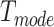 is defined according to different passing modes. For example, the living mode has larger
is defined according to different passing modes. For example, the living mode has larger 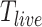 as persons are likely to stay at home for a long time (such as more than 10 hours), while the driving mode or the walking mode have smaller
as persons are likely to stay at home for a long time (such as more than 10 hours), while the driving mode or the walking mode have smaller  . This judgement is described as Lines 6-8. Finally, if the queried person's trajectory does not match the companion requirement with any infected person, the algorithm outputs no companion is detected.
. This judgement is described as Lines 6-8. Finally, if the queried person's trajectory does not match the companion requirement with any infected person, the algorithm outputs no companion is detected.
Notice that, if the queried person once moved together with any infected person, we set the risk as 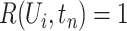 ; otherwise we need to calculate the personnel risk based on the communication stations’ risk.
; otherwise we need to calculate the personnel risk based on the communication stations’ risk.
B. Personal Risk Assessment Based on the Communication Station Risk
If the queried person does not satisfy the companion judgement with any infected person, we need to calculate the person's risk value. For the station trajectory 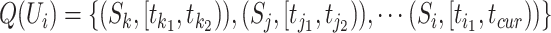 and the passing mode of each segment
and the passing mode of each segment 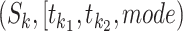 , we also convert the trajectory segment to a time-segment representation
, we also convert the trajectory segment to a time-segment representation  where
where 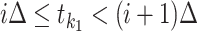 and
and 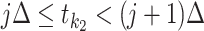 .
.
We design infection weights for each passing modes as 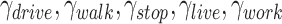 , where
, where 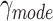 (
(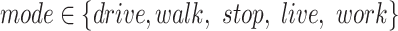 ) implies the probability that a person might be infected by the passing
) implies the probability that a person might be infected by the passing 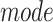 . Hence, we can calculate the personnel risk when the person passes through station
. Hence, we can calculate the personnel risk when the person passes through station 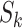 in time
in time 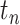 as
as
 |
Normally, it is useless to merely compute the personnel risk in a time segment 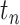 . For example, many places require that the queried person should be at low risk for the past 14 days, thus we need to compute the personnel risk in the past
. For example, many places require that the queried person should be at low risk for the past 14 days, thus we need to compute the personnel risk in the past 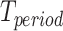 time. We formulate the personnel risk calculation method as
time. We formulate the personnel risk calculation method as
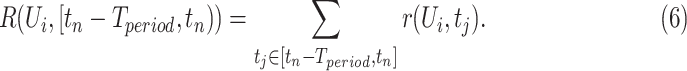 |
Combining these steps, the whole process the personnel risk assessment is described as Alg. 3.
Algorithm 3: Personal Risk Assessment.
-
1:
For a queried person
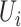 and the trajectory
and the trajectory 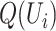 ;
; -
2:
Invoke the Companion Judgement Method (Alg. 2) to the queried person, if it detects companion, return the personnel risk as high as 1;
-
3:
for each trajectory segment
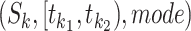 do
do -
4:
Find out
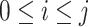 such that
such that 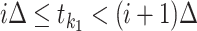 and
and 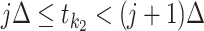 ;
; -
5:
Compute
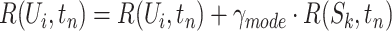 where
where 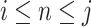 ;
; -
6:
end for
-
7:
Set
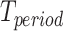 as the risk querying time;
as the risk querying time; -
8:
Compute
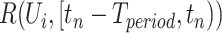 as Eqn. (6).
as Eqn. (6).
The first two lines of Alg. 3 invokes the companion judgement method and the personnel risk is set as high as 1 if companion with any infected person is detected. Otherwise, the personnel risk in each time segment 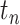 is computed as Lines 3-6. Finally, we set the querying period and compute the personnel risk on Line 8. When the risk
is computed as Lines 3-6. Finally, we set the querying period and compute the personnel risk on Line 8. When the risk 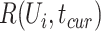 is very small, we can regard the queried person as healthy.
is very small, we can regard the queried person as healthy.
VI. Simulations
In this section, we generate some station trajectory data for both infected persons and queried persons since the real data might cause privacy leakage. We first introduce the settings in our simulations, including the generation of the communication stations and the method of generating the station trajectory of each person. Then, we show the simulation results of the proposed epidemic risk assessment method. Finally, we introduce the implemented system for querying a person's epidemic risk, which could help assist safe work resumption.
A. Simulation Settings
We introduce the settings for evaluating the assessment method. First, we introduce the generation of the communication stations that are deployed in a certain area. Then, we generate the station trajectories of users (including infected persons and the person to be queried).
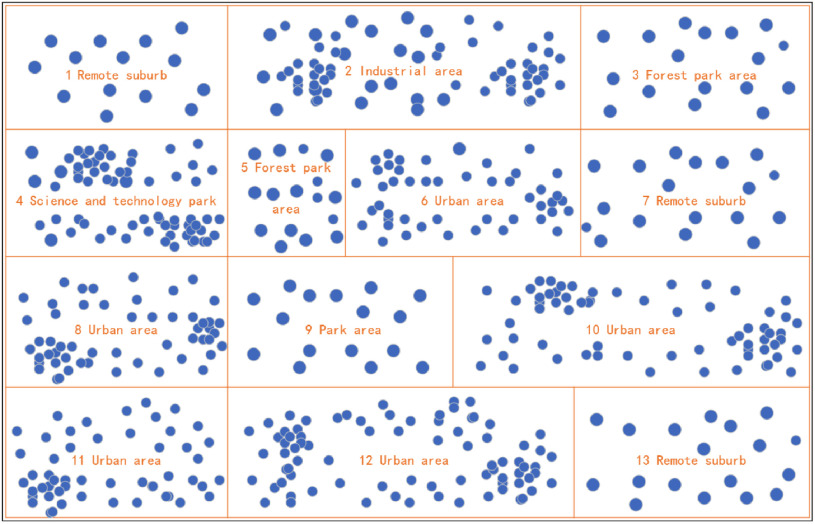
1). Generation of the Communication Stations
Assume all communication stations are deployed in a certain geographic range and we divide the area into 13 sub-areas (districts) of different types for more realistic simulation. As shown in Table II, the second column describes the main type of the area such as remote suburb, industrial area, urban area, etc. The third column describes the radius range of the deployed stations in each sub-area, and the fourth column is the number of the stations. Generally speaking, the station's range in the remote suburb is larger than that in the urban area or industrial area. The generated sub-areas are illustrated in Fig. 4.
TABLE II. Station Characteristics of Different Sub-Areas.
| ID (sub-areas) | Area type | Radius (km) |
 of stations of stations |
|---|---|---|---|
| 1 | Remote suburb |
|
300 |
| 2 | Industrial area |
|
500 |
| 3 | Forest park area | [0.8,2] | 100 |
| 4 | Science and technology park | [0.3,0.5] | 500 |
| 5 | Forest park area | [0.8,2] | 100 |
| 6 | Urban area | [0.3,0.5] | 300 |
| 7 | Remote suburb |
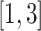
|
200 |
| 8 | Urban area | [0.3,0.5] | 500 |
| 9 | Park area | [0.5,1] | 50 |
| 10 | Urban area | [0.3,0.5] | 500 |
| 11 | Urban area | [0.3,0.5] | 500 |
| 12 | Urban area | [0.3,0.5] | 500 |
| 13 | Remote suburb |
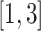
|
300 |
Fig. 4.
The area is divided into 13 sub-area of different types.
We divide the type of communication stations into 8 different categories according to the covered places: residence (Re), supermarket (Sp), restaurant (Rt), workplace (Wp), hotel (Ho), shopping mall (M), park (P), and hospital (Hp). We introduce the characteristics of these types in Table III, where the second column shows the enter time range, the third column lists the normally passing modes, and the fourth column shows the time period a person may stay within the station. Different sub-areas may contain different types of stations, and we introduce the distribution of these stations in each sub-area as Table IV.
TABLE III. Characteristics of Different Types of Communication Stations.
| Station Type | Enter time range | Passing mode | Time period (h) |
|---|---|---|---|
| residence | 00:00:00-23:59:59 |

|
|
| supermarket | 9:00:00-22:00:00 |
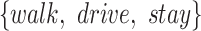
|
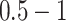
|
| restaurant | 11:00:00-21:00:00 |
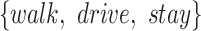
|
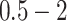
|
| workplace | 8:30:00-14:00:00 |
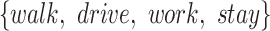
|
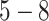
|
| hotel | 00:00:00-23:59:59 |
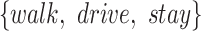
|
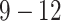
|
| mall | 9:00:00-23:00:00 |
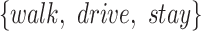
|
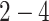
|
| park | 6:00:00-22:00:00 |
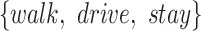
|
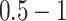
|
| hospital | 00:00:00-23:59:59 |
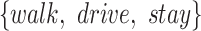
|
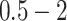
|
TABLE IV. The Distribution of Different Stations in the Sub-Areas.
| ID | Station Types | Distribution |
|---|---|---|
| 1 | {Re, Sp, Rt} | {0.6,0.2,0.2} |
| 2 | {Re, Sp, Rt, Wp, Ho} | {0.1,0.1,0.2,0.5,0.1} |
| 3 | {Sp, P} | {0.2,0.8} |
| 4 | {Sp, Re, Wp, Ho} | {0.1,0.2,0.6,0.1} |
| 5 | {Sp, P} | {0.2,0.8} |
| 6 | {Hp, M, Res, Sp, Re, Ho} | {0.1,0.3,0.2,0.2,0.1,0.1} |
| 7 | {Re, Sp, Rt} | {0.6,0.2,0.2} |
| 8 | {Hp, M, Res, Sp, Re, Ho} | {0.1,0.3,0.2,0.2,0.1,0.1} |
| 9 | {Sp, P } | {0.2,0.8} |
| 10 | {Hp, M, Res, Sp, Re, Ho} | {0.1,0.3,0.2,0.2,0.1,0.1} |
| 11 | {Hp, M, Res, Sp, Re, Ho} | {0.1,0.3,0.2,0.2,0.1,0.1} |
| 12 | {Hp, M, Res, Sp, Re, Ho} | {0.1,0.3,0.2,0.2,0.1,0.1} |
| 13 | {Re, Sp, Rt} | {0.6,0.2,0.2} |
2). Generation the Station Trajectory of the Users
We show the method to generate the station trajectory of the users. We first simulate 10 000 users with distinct name and identifiers, and we suppose 2000 persons are infected. Hence, the other 8000 users can be utilized for the querying test.
In order to simulate the trajectories of the patients, we collect some released news from the Centers for Disease Control (CDC) and simulate the trajectories of some infected persons according to the released locations the person passed by, such as in some hospital or stay in some market. The generated trajectories can reflect some characteristics of the infected persons.
To evaluate the risk assessment method, we generate four different types of station trajectories for the queried persons.
-
•
Non-overlapping trajectory implies the queried person has no overlapping trajectory segments with any infected persons;
-
•
Overlapping trajectory implies the queried person has some overlapping trajectory segments with some infected person, and different passing modes are simulated;
-
•
Companion trajectory implies the queried person has once moved together with an infected person;
-
•
Home/work trajectory simulates a periodical pattern that the queried person goes to work or stays at home. Notice that, the enter time range of the home/work trajectory satisfies the characteristics in Table III.
We generate these types of trajectories with distribution 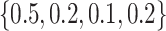 which means half of the queried persons have non-overlapping with the infected person, while 20% people has overlapping trajectory segments but some of them might be at low risk by the driving or walking passing mode.
which means half of the queried persons have non-overlapping with the infected person, while 20% people has overlapping trajectory segments but some of them might be at low risk by the driving or walking passing mode.
Notice that, we can obtain some real information of the communication stations through some public data, such as https://opencellid.org/. However, the trajectory of each person is sensitive and such information is unobtained in real experiment. In order to protect person's privacy, we generate the communication stations and people's trajectory to show the performance of the proposed method.
B. Communication Station Risk Assessment
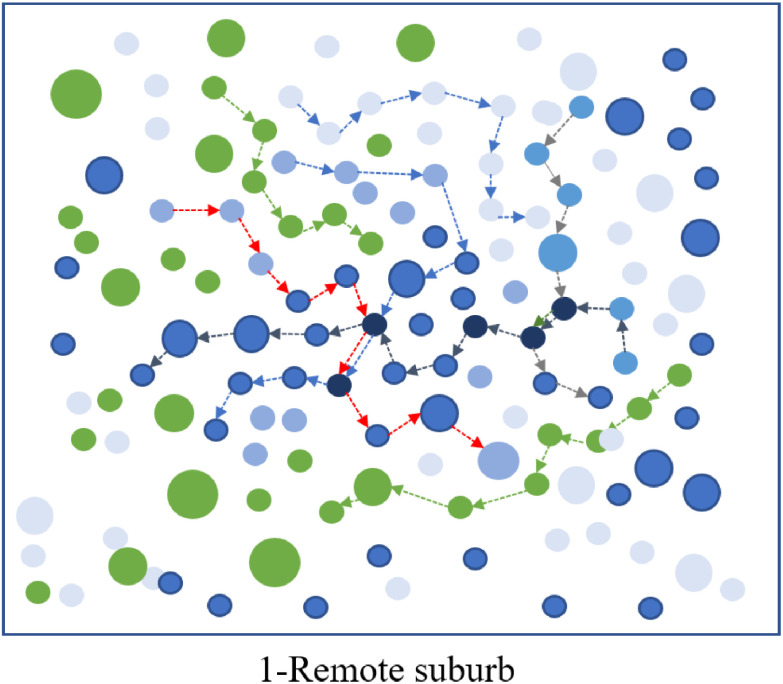
We implement the assessment method in Section IV and we can compute the epidemic risk values of each station in each time segment. To show some intuitive results, we fix any time segment and the risk values of these communication station is depicted with different colors. We depict an example in Fig. 5 when we choose a specific time segment, and the figure shows the epidemic risk of the communication stations in the 1-th sub-area. Green means the station has no risk while the degree of the blue color means the risk level. The communication station with larger risk value is depicted with darker blue in the figure. Notice that, the blue arrows imply the station trajectories of the infected persons, while the green arrows imply the station trajectory of the queried person. From the figure, with more infected persons passing through, the communication station has larger risk value.
Fig. 5.
An example of the communication station risk in the sub-area 1.
C. Personnel Risk Assessment
We first show the distribution of the personnel risks of different types of trajectories. As shown in Table V, if a queried person has no overlapping trajectory segments with any infected person, the person is assessed with no risk (4000 such persons have low risk within [0,0.1). For the 800 companion trajectories, the proposed algorithm could detect the companion person and the risk is set as high as 1; hence all these trajectories have high risk value within 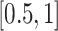 . Considering the overlapping trajectories, many persons are in the driving or the walking mode, and they are not affected too much. In addition, only a small portion of the queried persons have high risk value for this type of trajectory. Similarly, most of the home/work trajectories have low risk value, and only a few of them have high risk value.
. Considering the overlapping trajectories, many persons are in the driving or the walking mode, and they are not affected too much. In addition, only a small portion of the queried persons have high risk value for this type of trajectory. Similarly, most of the home/work trajectories have low risk value, and only a few of them have high risk value.
TABLE V. The Personnel Risk of the Queried Persons.
| Trajectory Type | Number of Persons |
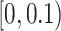
|
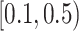
|
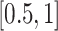
|
|---|---|---|---|---|
| Non-overlapping | 4000 | 4000 | 0 | 0 |
| Overlapping | 1600 | 832 | 545 | 223 |
| Companion | 800 | 0 | 0 | 800 |
| Home | 800 | 715 | 3 | 82 |
| Work | 800 | 550 | 190 | 60 |
To better illustrate different situations of the queried person, we introduce and evaluate the following special cases.
1). The User Has Been to a Certain Sub-Area, but he/she Has Not Contacted Any Infected Person in the Same Time
When our algorithm calculates the user's personnel risk, it would find out the stations he/she has passed through. Since no infected persons pass through the station simultaneously, the communication station risk is low when the user passes through the station. Hence, the personnel risk is low and the simulation results also corroborate our analyses.
2). The User Drives Through Some Communication Stations With High Risk, but he/she Has Not Contacted Any Infected Person
This is a classic overlapping trajectory where the user passes through some communication stations with high risk values, but the personnel risk is low since the driving mode is not affected by the station. By setting a very small 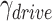 value (Section V-B), the simulation results verify that the user has low epidemic risk.
value (Section V-B), the simulation results verify that the user has low epidemic risk.
3). The User Drives in a Sub-Area With an Infected Person
For example, the user has a good relationship with an infected person and they have driven together in some area. Though the driving mode has low infection weight, the companion judgement method could detect the companion trajectory and assess the user's epidemic risk value as high as 1. The simulation results of the companion trajectories corroborate the analyses.
D. The Epidemic Risk Assessment System
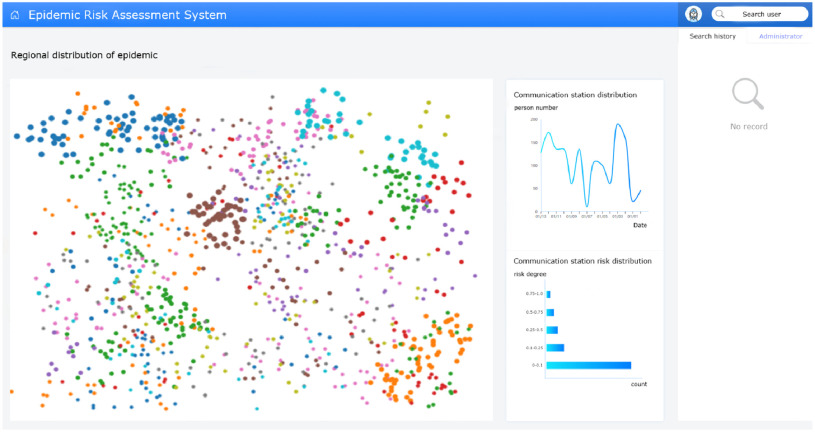
On the basis of the proposed method, we implemented the epidemic risk assessment system as Fig. 6. The left side of the system shows the distribution of the communication stations in a specific area. The middle part shows the characteristics of the communication stations, including the number of persons who pass through the station and the distribution of the station risk. The right side is utilized to query and search the personnel risk. By inputting the personnel information, the system would output the calculated risk value. This system can help assist safe work resumption by verifying the personnel risk.
Fig. 6.
The epidemic risk assessment system.
VII. Conclusion
In this paper, we propose a novel epidemic risk assessment method on the basis of the granular data collected by the communication stations. This method is composed of two stages: computing the communication station risk and calculating the personnel risk. The first stage aims at evaluating the stations’ risk values in different time intervals, while the second stage calculates a fine-grained personnel risk value according to the station trajectory of the specific person. In order to compute the communication station risk more accurately, we define five different passing modes which reflect different ways of passing through the station and these modes are assigned with different risk weights. The risk values of the stations are computed according to the number of infected persons and the passing mode of each person. To calculate the personnel risk, we propose a companion judgement method which could automatically decide whether two people have moved together. If no companion trajectory is detected, we then calculate a person's epidemic risk according to the risks of stations he/she has passed through. This two-stage assessment method could better calculate people's epidemic risk, which plays an important role in assisting safe work resumption.
In the future, we would like to extend and apply the proposed method in practice by collecting real data from the telecommunications operators. Furthermore, there exist many important and interesting problems to handle, such as improving the passing mode classification accuracy by more advanced methods.
Biographies

Zhaoquan Gu received the bachelor's and Ph.D. degrees in computer science from Tsinghua University, Beijing, China, in 2011 and 2015, respectively. He is currently a Professor with the Cyberspace Institute of Advanced Technology, Guangzhou University, Guangzhou, China. His research interests include wireless networks, distributed computing, big data analysis, and artificial intelligence security.

Le Wang received the Ph.D. degree in computer science from the National University of Defense Technology, Changsha, China. He is currently an Associate Professor with the Cyberspace Institute of Advanced Technology, Guangzhou University, Guangzhou, China. His current research interests include network and big data security. He was a Member of the China Computer Federation.

Xiaolong Chen received the bachelor's degree in computer science from Sichuan Agricultural University, Ya'an, China, in 2018. He is currently working toward the master's degree in computer science and technology from Guangzhou University, Guangzhou, China. His research interests include knowledge graph and data mining.

Yunyi Tang received the bachelor's degree in information security from Guizhou University, Guiyang, China, in 2018. He is currently working toward the master's degree in computer science and technology from Guangzhou University, Guangzhou, China. His research interests include knowledge graph and natural language processing.

Xingang Wang received the bachelor's degree in computer science and technology from the Taiyuan University of Technology, Taiyuan, China, in 2016. He is currently working toward the master's degree in computer science and technology from Guangzhou University, Guangzhou, China. His research interests include deep learning, knowledge graph, and malware detection.

Xiaojiang Du (Fellow, IEEE) received the B.S. and M.S. degrees in electrical engineering (Automation Department) from Tsinghua University, Beijing, China in 1996 and 1998, respectively. He received the M.S. and Ph.D. degrees ine electrical engineering from the University of Maryland, College Park, MD, USA, in 2002 and 2003, respectively. He is a tenured Full Professor and the Director of the Security And Networking (SAN) Lab in the Department of Computer and Information Sciences at Temple University, Philadelphia, PA, USA. His research interests are security, wireless networks, and systems. He has authored more than 500 journal and conference papers in these areas, as well as a book published by Springer. He won the best paper award at IEEE ICC 2020, IEEE GLOBECOM 2014 and the best poster runner-up award at the ACM MobiHoc 2014. He serves on the editorial boards of three IEEE journals. He is a Life Member of ACM.

Mohsen Guizani (Fellow, IEEE) received the B.S. (with distinction) and M.S. degrees in electrical engineering, the M.S. and Ph.D. degrees in computer engineering from Syracuse University, Syracuse, NY, USA, in 1984, 1986, 1987, and 1990, respectively. He is currently a Professor with the Computer Science and Engineering Department, Qatar University, Qatar. His research interests include wireless communications and mobile computing, computer networks, mobile cloud computing, security, and smart grid. Throughout his career, he received three teaching awards and four research awards. He also received the 2017 IEEE Communications Society WTC Recognition Award as well as the 2018 AdHoc Technical Committee Recognition Award for his contribution to outstanding research in wireless communications and Ad-Hoc Sensor networks. He was the Chair of the IEEE Communications Society Wireless Technical Committee and the Chair of the TAOS Technical Committee. He served as the IEEE Computer Society Distinguished Speaker and is currently the IEEE ComSoc Distinguished Lecturer. He is a Senior Member of ACM.

Zhihong Tian (Member, IEEE) is currently a Professor, and Dean, with the Cyberspace Institute of Advanced Technology, Guangzhou University, Guangdong Province, China. Guangdong Province Universities and Colleges Pearl River Scholar (Distinguished Professor). He is also a part-time Professor at Carlton University, Ottawa, ON, Canada. Previously, he served in different academic and administrative positions at the Harbin Institute of Technology. He has authored more than 200 journal and conference papers in these areas. His research interests include computer networks and cyberspace security. His research has been supported in part by the National Natural Science Foundation of China, National Key research and Development Plan of China, National High-tech R&D Program of China (863 Program), and National Basic Research Program of China (973 Program). He also served as a member, Chair, and General Chair of a number of international conferences. He is a Senior Member of the China Computer Federation.
Funding Statement
This work was supported in part by the National Natural Science Foundation of China under Grant U1636215, Grant 61902082, the National Key Research and Development Program of China 2018YFB1004003, the Guangdong Key Research and Development Program of China 2019B010136003, and in part by the Guangdong Province Universities and Colleges Pearl River Scholar Funded Scheme (2019).
Contributor Information
Zhaoquan Gu, Email: zqgu@gzhu.edu.cn.
Le Wang, Email: wangle@gzhu.edu.cn.
Xiaolong Chen, Email: 2111806010@e.gzhu.edu.cn.
Yunyi Tang, Email: 2111806047@gzhu.edu.cn.
Xingang Wang, Email: 2111906082@e.gzhu.edu.cn.
Xiaojiang Du, Email: dxj@ieee.org.
Mohsen Guizani, Email: mguizani@ieee.org.
Zhihong Tian, Email: tianzhihong@gzhu.edu.cn.
References
- [1].Bai L., Yang D., Wang X., Tong L., Zhu X., and Zhong N., “Chinese experts’ consensus on the Internet of Things-aided diagnosis and treatment of coronavirus disease 2019 (COVID-19),” Clin. ehealth, vol. 3, pp. 7–15, 2020. [Google Scholar]
- [2].Brown J. and Du, X.“Detection of selective forwarding attacks in heterogeneous sensor networks,” in Proc. IEEE Int. Conf. Commun., 2008, pp. 1583–1587.
- [3].J. F. W.. Chan, et al. , “A familial cluster of pneumonia associated with the 2019 novel coronavirus indicating person-to-person transmission: A study of a family cluster,” The Lancet, vol. 395, no. 10223, pp. 514–523, Feb. 15-21 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [4].Bai C. and Zhao J., Medical Internet of Things. Beijing: Science Press, 2016. [Google Scholar]
- [5].Cooke K. L. and Driessche P. V. D., “Analysis of an SEIRS epidemic model with two delays,” J. Math. Biol., vol. 35, pp. 240–260, 1996. [DOI] [PubMed] [Google Scholar]
- [6].Dong L., “5G and intelligence medicine how the next generation of wireless technology will reconstruct healthcare?,” Precis. Clin. Med., vol. 2, no. 4, pp. 205–208, Dec. 2019. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [7].Domingo-Fernndez D., et al. , “COVID-19 knowledge graph: A computable, multi-modal, cause-and-effect knowledge model of COVID-19 pathophysiology,” Biorxiv, 2020, doi: 10.1101/2020.04.14.040667. [DOI] [PMC free article] [PubMed]
- [8].Du, X., “QoS routing based on multi-class nodes for mobile ad hoc networks,” Ad Hoc Netw., vol. 2, no. 3, pp. 241–254, 2004. [Google Scholar]
- [9].Du X. and Lin F., “Improving sensor network performance by deploying mobile sensors,” in Proc. 24th IEEE Int. Perform., Comput. Commun. Conf., 2005, pp. 67–71.
- [10].Du X. and Wu, D.“Adaptive cell-relay routing protocol for mobile ad hoc networks,” IEEE Trans. Veh. Technol., vol. 55, no. 1, pp. 278–285, Jan. 2006. [Google Scholar]
- [11].Gao Q., Hu Y., Dai Z., Wu J., Xiao F., and Wang J., “The epidemiological characteristics of 2019 novel coronavirus diseases (COVID-19) in Jingmen, Hubei, China, Medicine, vol. 99, no. 23, 2020, Art. no. e20605. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [12].Gong L., Liu X N., and Zou X., “Spread of infectious disease risk assessment based on the spatial-temporal trajectory data analysis,” Acta Geodaetica Et Cartographica Sinica, 2015, doi: 10.11947/j.AGCS.2015.F062. [DOI]
- [13].Guan W., et al. , “Clinical characteristics of 2019 novel coronavirus infection in China,” Medrxiv, 2020, doi: 10.1101/2020.02.06.20020974. [DOI]
- [14].Gu Z., Hu W., Zhang C., Lu H., Yin L., and Wang L., “Gradient shielding: Towards understanding vulnerability of deep neural networks,” IEEE Trans. Netw. Sci. Eng., vol. 8, no. 2, pp. 921–932, Apr.-Jun. 2021. [Google Scholar]
- [15].Gu Z., Wang Y., Shen T., and Lau F. C. M., “On heterogeneous sensing capability for distributed rendezvous in cognitive radio networks,” IEEE Trans. Mobile Comput., vol. 20, no. 11, pp. 3211–3226, Nov. 2021. [Google Scholar]
- [16].Gu Z., Shen T., Wang Y., and Lau F. C. M., “Efficient rendezvous for heterogeneous interference in cognitive radio networks,” IEEE Trans. Wireless Commun., vol. 19, no. 1, pp. 91–105, Jan. 2020. [Google Scholar]
- [17].Hufnagel L., Brockmann D., and Geisel T., “Forecast and control of epidemics in a globalized world,” Proc. Nat. Acad. Sci. USA, 2004. [Online]. Available: https://doi.org/10.1073/pnas.0308344101 [DOI] [PMC free article] [PubMed]
- [18].Huang C., et al. , “Clinical features of patients with 2019 novel coronavirus in Wuhan, China,” The Lancet, vol. 395, no. 10223, pp. 497–506, Feb. 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [19].Hou C., et al. , “The effectiveness of quarantine of Wuhan city against the corona virus disease 2019 (COVID-19): A well-mixed SEIR model analysis,” J. Med. Virol., vol. 92, no. 7, pp. 841–848, Jul. 2020. [DOI] [PubMed] [Google Scholar]
- [20].Jun-feng L., “Assessment and prediction of COVID-19 based on SEIR model with undiscovered people,” J. Univ. Electron. Sci. Technol. China vol. 49,no. 3, pp. 375–382, vol. 148, 2020, Art. no. E130. [Google Scholar]
- [21].Khalili M., Karamouzian M., Nasiri N., Javadi S., Mirzazadeh A., and Sharifi H., “Epidemiological characteristics of COVID-19: A systematic review and meta-analysis,” Epidemiol. Infect., 2020, doi: 10.1017/S0950268820001430. [DOI] [PMC free article] [PubMed]
- [22].Lau B. P. L., et al. , “A survey of data fusion in smart city applications,” Inf. Fusion, vol. 52, pp. 357–374, 2019. [Google Scholar]
- [23].Li K., et al. , “An experimental study for tracking crowd in smart cities,” IEEE System J., vol. 13, no. 3, pp. 2966–2977, Sep. 2019. [Google Scholar]
- [24].Li W., Piechocki R. J., Woodbridge K., Tang C., and Chetty K., “Passive WiFi radar for human sensing using a stand-alone access point,” IEEE Trans. Geosci. Remote Sens., vol. 59, no. 3, pp. 1986–1998, Mar. 2021. [Google Scholar]
- [25].Lu R., et al. , “Genomic characterization and epidemiology of 2019 novel coronavirus: Implications of virus origins and receptor binding,” The Lancet, 2020, vol. 395, no. 10224, pp. 565–574, Feb. 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [26].Lopez C. E., Vasu M., and Gallemore C., “Understanding the perception of COVID--19 policies by mining a multilanguage twitter dataset,” 2020, arXiv:2003.10359. [Google Scholar]
- [27].Lenzen M., et al. , “Global socio-economic losses and environmental gains from the coronavirus pandemic,” PLoS One, vol. 15,no. 7, 2020, Art. no. e0235654 https://doi.org/10.1371/journal.pone.0235654 [DOI] [PMC free article] [PubMed] [Google Scholar]
- [28].Liu B. M., Yang Q. Q., Zhao L. Y., Xie W., and Si Y., “Epidemiological characteristics of COVID-19 patients in convalescence period,” Epidemiol. Infect., vo. [DOI] [PMC free article] [PubMed]
- [29].Li Q., et al. , “Early transmission dynamics in wuhan, china, of novel coronavirus-infected pneumonia,” New Engl. J. Med, vol. 382, pp. 1199–1207, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [30].Moore C. and Newman M. E. J., “Epidemics and percolation in small-world networks,” Phys. Rev. E, 2000, vol. 61, 2000, Art. no. 5678. [DOI] [PubMed] [Google Scholar]
- [31].Myers M. F., Rogers D. J., Cox J., Flahault, A. and Hay S. I., “Forecasting disease risk for increased epidemic preparedness in public health,” Adv. Parasitol., 47, pp. 309–330, 2000. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [32].Meng B., Wang J F., Liu J Y., and Wu J L., “Understanding the spatial diffusion process of SARS in Beijing,” Public Health, vol. 119, no. 12, pp. 1080–1087, Dec. 2005. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [33].Peeri N., et al. , “The SARS, MERS and novel coronavirus(COVID-19) epidemics, the newest and biggest global health threats: What lessons have we learned?,” Int. J. Epidemiol., vol. 49, no. 3, pp. 717–726, Jun. 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [34].Pluchino A., et al. , “A novel methodology for epidemic risk assessment: The case of COVID-19 outbreak in Italy,” 2020, arXiv: 2004.02739. [Google Scholar]
- [35].LT., “Importation and human-to-human transmission of a novel coronavirus in Vietnam,” New Engl. J. Med., vol. 382, pp. 872–874, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [36].Rothe C., et al. , “Transmission of 2019-nCoV infection from an asymptomatic contact in Germany,” N. Engl. J. Med., vol. 382, pp. 970–971, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [37].Roosa K., et al. , “Real-time forecasts of the COVID-19 epidemic in China from February 5th to February 24th, 2020,” Infect. Dis. Modell., vol. 5, pp. 256–263, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [38].Song Y., Jiang J., Wang X., Yang D., and Bai C., “Prospect and application of Internet of Things technology for prevention of SARIs,” Clin. Ehealth, Vol. [Google Scholar]
- [39].Sun P., et al. , “Clinical characteristics of hospitalized patients with SARS-CoV-2 infection: A single arm meta-analysis,” J. Med. Virol vol. 92, no. 6, pp. 612–617, 2020, doi: 10.1002/jmv.25735. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [40].Song Y., Jiang J., Wang X., Yang D., and Bai C., “Prospect and application of Internet of Things technology for prevention of SARIs,” Clin. ehealth vol. 3, pp. 1–4, 2020. [Online]. Available: https://doi.org/10.1016/j.ceh.2020.02.001 [Google Scholar]
- [41].Thomson M. C., et al. , “Malaria early warnings based on seasonal climate forecasts from multi-model ensembles,” Nature, vol. 439, pp. 576–579, 2006. [DOI] [PubMed] [Google Scholar]
- [42].Tian Z., Luo C., Qiu J., Du X., and Guizani M., “A, Distributed deep learning system for web attack detection on edge devices,” IEEE Trans. Ind. Informat., vol. 16, no. 3, pp. 1963–1971, Mar. 2020. [Google Scholar]
- [43].Tian Z., et al. , “Real time lateral movement detection based on evidence reasoning network for edge computing environment,” IEEE Trans. Ind. Inform., vol. 15, no. 7, pp. 4285–4294, Jul. 2019. [Google Scholar]
- [44].Tian Z., Gao X., Su S. and Qiu J., “Vcash: A novel reputation framework for identifying denial of traffic service in internet of connected vehicles,” IEEE Internet Things J., vol. 7, no. 5, pp. 3901–3909, May 2020. [Google Scholar]
- [45].Watts D. J., Muhamad R., Medina D. C., and Dodds P. S., “Multiscale, resurgent epidemics in a hierarchical metapopulation model,” Proc. Nat. Acad. USA, 2005, doi: 10.1073/pnas.0501226102. [DOI] [PMC free article] [PubMed]
- [46].Wang Y., Liu Y., Struthers J., and Lian M., “Spatiotemporal characteristics of COVID-19 epidemic in the United States,” Clin. Infect. Dis., 72, no. 4, pp. 643–651, Feb. 15 2021. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [47].WuLeung JT K., Leung GM., “Nowcasting and forecasting the potential domestic and international spread of the 2019-nCoV outbreak originating in Wuhan, China: A modeling study,” The Lancet, vol. 395, no. 10225, pp. 689–697, Feb. 29–Mar. 6 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [48].Zhou Y., Lau B. P. L., Yuen C., Tuncer B., and Wilhelm E., “Understand urban human mobility through crowdsensed data,” IEEE Commun. Mag., vol. 56, no. 11, pp. 52–59, Nov. 2018. [Google Scholar]
- [49].Zhou Y., Lau B. P. L., Koh Z., Yuen C., and Ng, B. K. K.“Understanding crowd behaviors in a social event by passive WiFi sensing and data mining,” IEEE Internet Things J., vol. 7, no. 5, pp. 4442–4454, May 2020. [Google Scholar]
- [50].Zhu N., et al. , “A novel coronavirus from patients with pneumonia in China, 2019,” New Engl J. Med., doi: 10.1056/NEJMoa2001017. [DOI] [PMC free article] [PubMed]