Abstract
In this study, an access control model for cooperative healthcare environments is presented. A work-based access control (WBAC) model is proposed by introducing the concept of team role classification based on Belbin team role theory and modifying the user-role assignment model from previous work. Roles are used in conjunction with team roles to handle access control in dynamic collaborative environments. To evaluate and analyze the security, efficiency, and practicality of the proposed model, we first formalize the model (events and policies), define the basic element set and relations in the WBAC model, present the WBAC authorization constraints, and define the WBAC access control decision function. Second, we evaluate the model’s security and manageability validity to ensure that the security and management requirements of our WBAC model are met. Finally, we evaluate the performance of the proposed model and compare it with relevant existing models. Verification indicates that WBAC is flexible, easy to manage and meets our expectation of allowing fine-grained access control, and it enhances the practicability of access control in dynamic collaboration environments.
Keywords: Electronic health records, Access control, Security, Privacy, Cooperative healthcare environments
Introduction
Electronic health records (EHRs) [14, 49] can be improved with a collaborative environment, through which medical providers such as physicians and specialists share information and work together as a team to solve particular medical cases. However, the collaborative environment might also leave users (e.g., patients) more susceptible to insider threats [22, 23, 53], a serious calamity that endangers the privacy and well-being of patients and medical personnel alike. Here, confidential information is improperly accessed and exploited by insiders. They are initially given permission to share information for purely benign purposes. In light of this, proper security mechanisms such as access control must be put in place to protect information residing on the health facility [2].
Access control is ideal for managing access to information and controlling the activities of legitimate users by mediating every attempt by a user to access a resource in the system [36]. Access control in distributed environments (e.g., inter-organization) has a different focus from centralized environments [39, 44, 51, 63, 65]. In centralized environments, access control policies can be defined in terms of role (job function), attributes, and privileges of users who are permitted to access resources according to their identities and associated privileges [28]. Role-based access control (RBAC) [31, 32, 55] and attribute-based access control (ABAC) [30, 37] are familiar examples of access control mechanisms. The access right decision to perform an action is made by analyzing the requester’s credentials (e.g., role and/or attributes) and his/her set of access rules/privileges. Due to the dynamic nature of collaboration and team work, it is important to understand to what extent and under what conditions other parties are granted with access rights [44, 65]. It is also necessary to employ access control policies to control the way in which information or services are shared between different parties [47, 54]. In distributed environments such as healthcare, different participants (individuals or organizations) can play several different roles at a given time (e.g., resource owner, agent or consumer) [5, 7]. Moreover, each participant manages his/her own resources and defines their own access control policies. Thus, participants collaborate with each other in various ways, which requires appropriate access control mechanisms in place to ensure that information is accessible only to those authorized to have access [59].
In our previous work [2–7], the work-based access control (WBAC) model was proposed by introducing the team role concept and modifying the team user-role assignment model from RBAC and ABAC. In [2], we proposed a team role classification based on Belbin team role theory [16]. The team is segregated into thought, action, and management based on contributions to the collaborative work. WBAC handles access control based on collaborative work and team role. Role is used in conjunction with team role to handle access control in dynamic collaborative environments. The team role determines the finer role and the extend of access of each team member. To the best of our knowledge, we are the first to use the team role theory with access control.
This study extends the work done in [7]. In this study, the general principles of the WBAC model are defined. We first formalize the model (events and policies), define the basic element set and relations in the WBAC model, present the WBAC authorization constraints, and define the WBAC access control decision function. Second, we evaluate the model’s security and manageability validity to ensure that the security and management requirements [4] are met. Finally, we evaluate the performance of the proposed model and compare it with RBAC and ABAC models.
The remaining part of this study is organized as follows. Section 2 presents a usage scenario of collaboration and sharing of healthcare data to better understand collaborations in the healthcare domain. In Section 3, a formal description and verification of the WBAC model is presented. Section 4 presents WBAC model security evaluation. In Section 5, WBAC model performance evaluation and comparing WBAC with the RBAC and ABAC models is given. Finally, discussion, future work, and conclusions are given in Section 6.
Collaboration and Secure Sharing of Healthcare Data
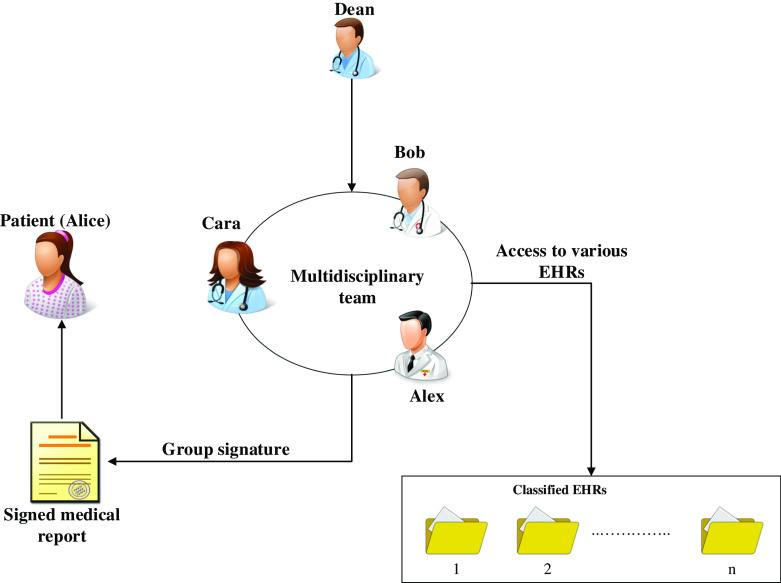
As shown in Fig. 1, a typical use case scenario adopted from [67] is presented. A patient named Alice is recently diagnosed with gastric cancer. Surgical removal of the stomach (gastrectomy) is the only curative treatment. For many patients, chemotherapy and radiation therapy are given after surgery to improve the chances of curing.
Fig. 1.
An example scenario of collaboration and sharing of healthcare data
Alice entered a cancer-treatment center at her chosen hospital (e.g., hospital A ). Alice has a primary care doctor (Dean) who she regularly visits. Upon entering the hospital, Alice also sees an attending doctor (Bob) from the hospital. Alice’s health condition has caused some complications, so her attending doctor would like to seek expert opinions and consultation regarding Alice’s treatment from different hospitals (e.g., hospital B), including Alice’s specific primary care doctor who is fully informed about Alice’s medical history. Note that the invited practitioners are specialized in different areas, where some are specialists and others are general practitioners. Also, the final medical report of Alice’s treatment should be signed by appropriate practitioners using digital signatures [18, 48]. Alice should be able to verify the authenticity of the consultation results through the practitioner’s digital signature [5, 6].
In such group consultation, also so-called multidisciplinary team consultation [19, 50, 62], it is noticeable that several healthcare professionals are involved in various roles to provide patient care. That involves many healthcare organizations and individuals, includes primary care doctors, general physicians and specialists. Every participant needs to obtain the medical records they request based on “minimum necessary”1 standard to uses and disclosures for treatment [13]. In this case, the act of managing the collaborative work must be clearly defined [5, 6]. By default, only the main practitioner should be aware of the patient’s personal information. The other medical practitioners with supporting roles are given information based on their contributing roles. For instance, if the supporting party is included solely for consultation purposes concerning the disease, only information essential for diagnosis is provided. It is not necessary to allow perusal of personal information related to the patient. Therefore, sharing and accessing healthcare records with efficient coordination between healthcare practitioners to perform collaborative work is a critical function in access control models [10]. The main concern is about losing control over the sensitive healthcare records while sharing them with multiple parties.
Insider abuse or misuse of privileges can be a threat to patient information and a liability for health care providers [2]. One of the main causes of insider threats is information leakage, which emerges when a supporting party is granted access beyond what is actually required. For instance, in treating a patient (Alice) case, the main practitioner Dean consults a specialist Cara from another department. In doing so, improper information access might occur if the Cara (Gastroenterologist) obtains more permissions than required. The key to solving this issue is to minimize the discrepancy between the granted access and the required access based on what is really needed. In this way, improper access to the patient’s sensitive information can be prevented [2].
Work-Based Access Control
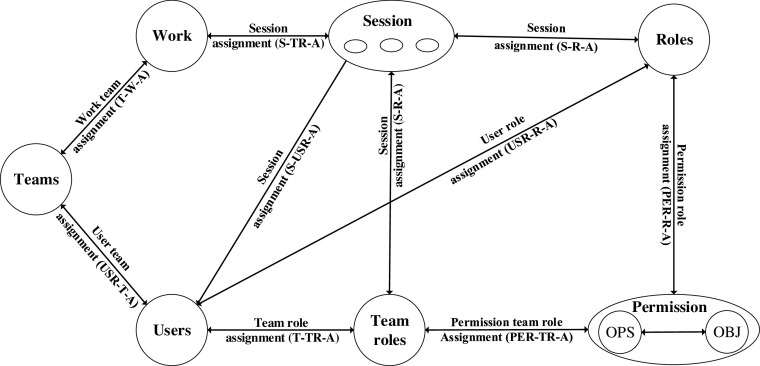
The basic element set and relations of WBAC model are defined in Fig. 2. The WBAC includes sets of data elements called sessions, users, roles, teams, team roles, works, permissions, operations, and objects. The WBAC model is fundamentally defined in terms of users being assigned to roles or teams, team members being assigned to team roles, work being assigned to teams, and permissions being associated with roles and team roles.
Fig. 2.
WBAC model
In the following, we formally express entities and relations for the proposed access control model (WBAC) and verify the main ideas for WBAC approach and policies.
WBAC Formal Description
WBAC policies consist of a number of access control rules. Each rule is a logical expression of the basic access control elements (i.e., users, roles/team roles, permissions, operations, and objects) and relations between these elements (e.g., user to role assignments, permission to role assignments, etc). We now define and explain the element sets and relationships between the elements presented in Fig. 2. The Core WBAC definitions OBJ, OPR, PER, R, TR, USR, T, W, and S are object, operation, permission, role, team role, user, team, work, and session, respectively.
Definition 1
An object is considered as any resource in the system that can be assigned with access rights. For example, records, files and/or devices such as patient medical devices (e.g., pacemakers, blood pressure device, etc.) [1, 29]. Access to an object potentially implies access to the information it contains [36]. The set of all objects is denoted by OBJ.
Formally: where . Objects covered by WBAC are classified into two sets of objects: O B J A and O B J B such that O B J = {O B J A ∪ O B J B}, listed in the permissions that are assigned to roles (Definition 4) and team roles (Definition 5) which will be accessed by a users (Definition 8).
P r i v a t e object denoted by O B J A. We assume that, O B J A contains resources related to personal information including names and addresses as well as resources that are not related to the current patient case such as family medical history, psychotherapy notes [35] and sexually transmitted diseases (STD) records, among others.
P r o t e c t e d object denoted by O B J B. We assume that this object contains resources related to current patient case. For example, consider scenario (Section 2), we could say that O B J B contains resources related to Alice’s current case such as past surgical history, date related to abdominal CT scan (computed tomography scan) and gastroscopy data, to name a few.
Definition 2
An operation is a term used to describe an action performed on resources (e.g., read, write, etc). The set of all operations is denoted by OPR.
Formally: where . Any operation that a user would perform on an object is defined entirely within the permission.
Definition 3
Permission specifies a special rights to perform some operation on resources for a subject (e.g., human users, machines, or processes). The set of all permissions are denoted by PER and it is a combination of object and operation.
Formally: P E R ⊆ O B J × O P R. Role and team role are associated with a set of permissions which are an approval to perform an operation on one or more objects.
Definition 4
A role is a collection of job functions within the context of a healthcare organization with some associated responsibility conferred on the user assigned to the role. Each role is authorized to perform one or more operations on objects.
In WBAC, we defined two types of roles. First is the main role (R), which represents the organizational role where the user has a common set of permissions to perform the job function associated with the role name. Formally, we have where r i ⊆ P E R. Second is the team role (TR), which is a collection of various roles assigned to different users contributing in several ways to a team with objective of accomplishing a specific work.
Definition 5
Team role (TR) is a set of roles defined within a team to restrict the roles memberships and also restrict access permissions to individuals who not only have the right organizational roles but also are associated to the task via team memberships.
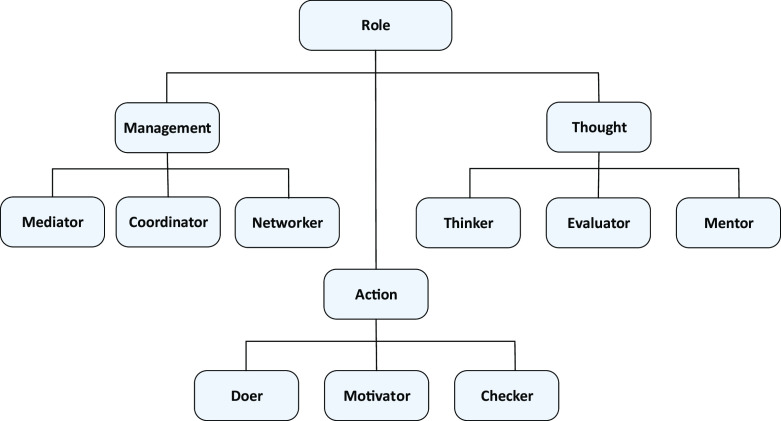
In [2], we proposed a team role classification based on Belbin team role theory [15, 16]. For the propose of this study, the nine different team roles that Belbin identified were rephrased and classified into thought, action, and management as illustrated in Fig. 3. Team member must be assigned to one team role (determined by their professional and/or technical knowledge) based on the goal, task, and contributes toward achieving the team’s objectives. The team role determines the finer role and the extend of access of each team member.
Fig. 3.
Taxonomy of team role [2]
Formally, we have T R = 〈t r t,t r a,t r m〉 where t r t is thought role, t r a is action role, t r m is management role and t r i ⊆ P E R where i ∈{t,a,m}.
Definition 6
Authorized role and authorized team role denoted by a u t h r(u s r), a u t h tr(u s r,t), respectively, are a subset of roles and team role that user is authorized to assume. We say that, a role r is authorized for a user if r is assigned to user. A u t h r(u s r) ⊆ R and a u t h tr(u s r,t) ⊂ T R, where usr is user (Definition 8) and t is a team (Definition 9).
Definition 7
An active role denoted by a c t r(u s r) is a subset of a u t h r(u s r) that user is currently performing. In other words, the active role of a user is a subset of his/her authorized roles. A c t r(u s r) ⊂ a u t h r(u s r). A user can execute a privilege only if the user has selected an active role.
Definition 8
A user is a term that is used to denote a subject. It is human users, machines, or processes that require access to system resources. The set of all users is denoted by USR.
Formally: where and u s r i = {s u,a u t h r(u s r i),t e a m member};t e a m member ∈ (T × T R)p where T is a team, s u ⊂ S is a session (Definition 11, is the number of teams which the u s r i is a member of and t e a m member = {t i,a u t h tr(u s r,t i)}i∈[0..p],t i ∈ T,a u t h tr(u s r,t) ∈ T R.
Definition 9
A team (t) encapsulates a collection of users in various roles and team role with the objective of accomplishing specific work. is a set of teams, where and t i ⊆ U S R.
In this study, we consider users as human beings (i.e., patients and healthcare providers), practically as an individual user or group of users that access the objects in the system to perform their jobs. For simplicity, we do not model the patient, but the data related to the patient (patient’ healthcare records) is modeled. The permissions available to the user are the union of permissions directly assigned to an active role or team role in a session (Definition 11).
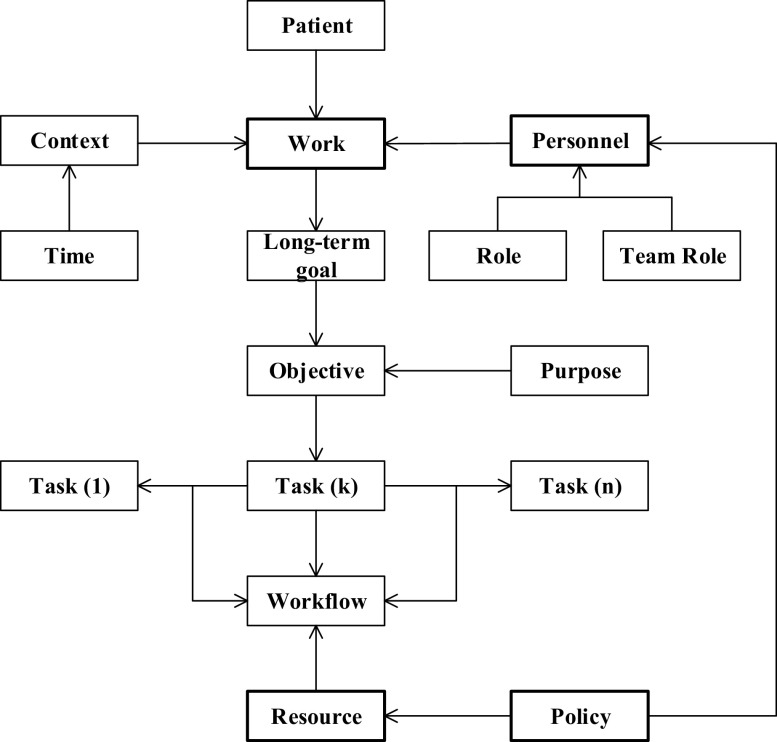
Definition 10
Work is an entity comprising a collection of elements named personnel, role, resource, context, and policy (Fig. 4) that interact with one another for a particular outcome to be achieved successfully. The set of all works are denoted by W . , where and w i = (t,o b j,s t a t e) where , , is the number of teams assigned to w i, is the number of objects assigned to work w i, and s t a t e ∈{0,1 }:
Fig. 4.
Work model for collaboration [2]
In WBAC, the treatment of Alice’s case (Section 2) is called a work. This work is performed by a group of personnel (healthcare providers) who play different roles in Alice’s treatment and also require access to different resources in different contexts. We consider patient’ healthcare records (patient’ EHRs) as objects which need to be accessed by healthcare providers.
A healthcare provider (who joins a team) can have various team roles whereby each of them is tied to a different collaborative work. TR restricts the role which each member of the team belongs to. Each team has a responsible person (head or manager) that decides who should join the team and who can perform what? For example, consider Alice’s case (Fig. 1), we have the primary doctor (Dean) as the team manager. Dean decides who would join the team and what team role each team member should have. A team member can perform what task in the collaboration is decided by what team role is assigned to him/her in the team. Moreover, the work is associated with a lifecycle (state) and only in active state, the team assigned to this work can perform their duties on it. Accessing resources and performing an operation related to work is controlled by WBAC authorization policies (Definition 12).
Definition 11
Session is an entity where user may activate a subset of role or team role he/she is assigned to. S denotes the set of sessions. Formally: where , s i = {a c t r(u s r),a u t h tr(u s r,t),a w}, where a w ⊆ W is an active work.
Each session is a mapping of one or many users to possible many roles and team roles. The permissions available to the user are the union of permissions from the activated role a c t r(u s r) or team role a u t h tr(u s r,t) in that session. Sessions include role and team role activation/deactivation, the enforcement of constraints on role and team role activation, and they are used for calculation of an access decision. Constraints such as separation of duty (SoD) [42] (discussed in Section 3.2) on sessions can limit the number of roles and team roles that a user can activate at the given time.
Definition 12
Authorization policy (AP) is a security statement of what is, and what is not allowed in the organization.
The goal of an authorization policy is to examine conditions in order to send an authorization result (permit or deny) for an authorized subject to access objects. It is possible to be an authorized user but not have access to a specific object. A policy may be presented mathematically or written on human language such as English to describes what a user and other entities (e.g., machines or process) on the system are allowed and/or disallowed to do. An example of policy in healthcare organization, only physicians, not nurses may prescribe a certain drug (e.g., antibiotics) to patients. To support a collaborative environment requirement [4], specially in the case where two or more different organizations cooperate and each of which might have its own resources’ policy based on the owner’s objectives and requirements, a dynamic policy with dual inclination is proposed in WBAC model [2], whereby the normal policy of enforcing access control is contained within the main policy. On the other hand, any policy that mediates resource sharing during collaborative work is covered by the collaboration policy.
Main policy ( M P ): The MP depends on the role (R). Therefore, it is only considered if the personnel (user) possesses a role.
Collaborative Policy ( C P ): CP depends on the team role (T R). In this respect, even if the personnel do not have the required personal roles, they can still gain access if they are invited into the collaboration. Team role (T R) provides a demarcation between the roles played by personnel within a collaboration work w.
Definition 13
Policy Set (P S ∈ A P) for a given system is the representation of the system’s access control mechanisms. In [4], we implemented two policy sets using XACML, where the first policy set is for MP and the second is for the CP.
Definition 14
Policy change is a sequence of modifying a policy set in the access control policies. Formally:
Let P be a policy that needs to be added or modified and PS is the policy set. Then,
If P ∈ P S, the change contains the activity of retracing P from PS and modifying it. Formally: P S ⊕{P,P ′} = (P S∖{P}∪ P ′) then, P S ′ = P S ⊕{P,P ′}.
Else if P∉P S, the change contains the activity of adding P ′ to PS. Formally: P S ′ = P S ∪ P ′.
Definition 15
Relation assignment is a many-to-many mapping of the defined data element to one another.
In the WBAC model, there is a number of assignment relations that are described as follows:
- User to role assignment: It is a many-to-many roles (R) to a users (USR) assignment relation. A user can have one or many roles and a role can be assigned to one or many users. For each user usr and role r, the Function (1) returns true if r is assigned to usr, false otherwise. Also, the set of roles assigned to user are updated in the a u t h r(u s r). Formally:
1 - User to team assignment: It is a many-to-many user to a team assignment relation. A team could have none or multiple users and a user could join one or multiple teams. The sets of users assigned to team t is defined in Function (2). Formally:
2 - Team member to team role assignment: It is a many-to-many team members to a team roles assignment relation. It defines a user that participates in a team should have one team role and a team role (tr) can be assigned to none or multiple users. Formally:
3 - Team to work assignment: It is a many-to-many relation assigning team t ′ to work w = {t,o b j,s t a t e}∈W. A work can have one or many teams and a team can be assigned to one or multiple works. Formally, we have:
4 - Permission to role assignment: It is many-to-many relation assignment defines a permission per which a role (r) can have. A role can have one or multiple permissions and a permission can be assigned to one or many roles. Formally:
5 - Permission to team role assignment: A many-to-many permissions (per) to a team role (tr) assignment relation. A team role can have one or multiple permissions and a permission can be assigned to one or many team roles. Formally:
6 - Session to user assignment: A many-to-many assignment relation of a session s i = {a c t r(u s r),a u t h tr(u s r,t),a w} to a user usr.
7 - Session to role assignment: A many-to-many assignment relation of a session s to an active role a c t r(u s r).
8 - Session to team role assignment: A many-to-many assignment relation a session s to a team role tr.
9
In the three relations (Functions (7), (8), and (9)), we assume the user can be assigned to one or multiple sessions and have one role and/or one team role in its participating team. To support the principle of least privilege, a user should be allowed to activate only those roles appropriate for a given occasion. But with constraints such as separation of duty (SoD), it may not be possible for a user to activate all his/her roles simultaneously.
WBAC Authorization Constraint Specification
Authorization constraint such as SoD [9, 42, 43, 60] and prerequisite constraints can be used to enforce conflict-of-interest polices that organizations may employ to prevent users from exceeding a reasonable level of authority for their roles. SoD is also used in multi-person control policies that show two or more different persons responsible to complete the task and set of related task. The purpose of this principle is to prevent one user from doing all parts of a task that requires two or more, in order to prevent collusion or fraud [43]. Two major types of SoD, static and dynamic, are presented in the literature [42]. Here, we discuss these two major types of SoD. Subsequently, we also define a variety of SoD and prerequisite constraints and their relationships in secure WBAC model.
Definition 16
Static separation of duty (SSoD) generally place restrictions on administrative operations that have the potential to undermine higher-level organizational SoD policies.
In other words, SSoD is used to enforce constraints on the assignment of users to set of roles or team roles to avoid a user from gaining authorization for permissions associated with conflicting roles. Examples of SSoD constraints are as follows:
Constraint 1 (C1)
Static-user-role-SoD: Two roles should never be assigned to the same user at a given time. Formally: Let mutual exclusion of role set be S S o D ⊆ R 2 ,
| 10 |
Constraint 2 (C2)
Static-user-team-role-SoD: Two team roles should never be assigned to the same user at one team. In other word, a user in one team can only be assigned to one team role at a given time.
Formally:
| 11 |
Constraint 3 (C3)
Object-based SSoD: Restricts that a user cannot perform an operation on a specific object. For example we have:
- Only a user ( usr) assigned with a team role ( t r a ) can access objects of O B J A . Formally we have:
12 - Only a user (usr) assigned with a team role(t r m)can access doctors’s information. Formally: Let o b j doctorInfo ∈ o b j b,
13
Definition 17
Dynamic separation of duty (DSoD) [42, 43] enforces constraints to limit the availability of the permissions over a user’s permission space by placing constraints on the roles and team roles that can be activated within or across sessions. Examples of DSoD constraints as follows:
Constraint 4 (C4)
Session-role DSoD : Session to role assignment disallows a user from activating two particular roles at the same time. Formally:
| 14 |
Where card(i.e., cardinality of a set) is the number of elements of the a c t r(u s r)set.
Constraint 5 (C5)
Session-team-role DSoD : Session to team role assignment disallows a user from activating two particular team roles at the same time. Formally:
| 15 |
Definition 18
Prerequisite constraint is based on competency and appropriateness, whereby a user can be assigned to role r i only if the user is already a member or not a member of specified roles, and similarly for permissions. Examples of prerequisite constraints can be presented as follows:
Constraint 6 (C6)
The number of authorized users for any team role does not exceed the cardinality of that role. Formally: Let n be the number of users a team role t r a should has. Then,
| 16 |
Constraint 7 (C7)
A collaborative work w has to be active, such that team members can work on it. Formally we have:
| 17 |
Definition 19
Delegation is referred to as a process in which one active entity (e.g., usr) in the system delegates its privileges to another entity (e.g., u s r ′) to carry out some function on behalf of the former user (usr) [61].
To fulfill a dynamic collaboration requirement [4], WBAC model supports delegation in which a user can delegate privileges to another user.
Constraint 8 (C8)
Delegation:
Let d e l e g a t e(u s r,u s r ′,r)be the role r which usr delegates to u s r ′ and r e v o k e(u s r,r)to revoke role,
| 18 |
¬U S R-R-A(u s r ′,r)is required because it is not useful to delegate a role (r) to user(u s r ′) whohas already been assigned to r. Also, usr should hold the role which he/she would delegateto u s r ′(USR-R-A(usr, r)). Moreover, constraints const(e.g., C1and C6) mustbe satisfied to enable the delegation.
Definition 20
Revocation is process of revoking the privileges that have been delegated. Often it is necessary to revoke privileges that have been delegated to a user [61] (e.g., when a healthcare provider returns back from holiday). Moreover, in WBAC, we have team revocation to revoke a team from a work (w), team membership revocation to revoke a user form team and active work should be revoked once the work is finished (more in Definition 27).
Constraint 9 (C9)
Revocation of delegated role:
| 19 |
Constraint 10 (C10)
Revocation of work: work should be revoked after it finishes. Let:
| 20 |
Definition 21
An access query (Q) is a tuple (u s r,o p r,o b j), where u s r ∈ U S R, o p r ∈ O P R and o b j ∈ O B J. A query q = (u s r,o p r,o b j) means that user (usr) requests to perform an operation (opr) on an object (obj).
Definition 22
Access state (Γ) is a particular model assignment to a given WBAC system. An access state γ ∈ Γ contains all the information necessary to make access control decisions for a given time. When a query q ∈ Q arises from an access request, γ ⊣ q means that the access request decision corresponding to q is permitted or denied in access state γ.
Definition 23
Access control decision function ( DF ) is defined as follows: if condition is evaluated as true, then there is decision d ∈{p e r m i t,d e n y}, according to the decision in the authorization policy.
Formally: Let U S R = {s u,a u t h r(u s r i),t e a m member}, and authorization policy A P = {a p i ∈ U S R × P E R}i∈[0...n] be a set of n permitted actions. Then,
| 21 |
| 22 |
WBAC Model Security Evaluation
Security evaluation answers questions such as whether an undesirable state is reachable and if every reachable state satisfies certain safety or availability properties [45]. Examples of undesirable states include states in which an untrusted user obtains access and states in which a user is entitled to access permission but does not get it. Security evaluation generalizes safety analysis as discussed in [33, 34, 41]. In this section, we evaluate the WBAC model based on the given scenario (Section 2).
Assumption 1
A patient, Alice, is a subject of medical records.
Assumption 2
Alice’s medical records include information about her health condition and treatments.
We assume that O B J A(Alice) = {F i l e 1,...,F i l e n}, where f i l e i is private information such as Alice’s personal data and other information not related to Alice’s current case, and O B J B(Alice) = {F i l e 1,...,F i l e n}, where f i l e i is information related to Alice’s current case, such as her old medical records (see Definition 1).
Assumption 3
Dean, Bob, Cara, and Alex are healthcare professionals who require access to Alice’s medical records while working on her treatment.
We assume Dean (head of the team) decides who should access what based on the required job. Table 1 presents the policy data used as input for our example proof.
Table 1.
Sample policy data
| Subject | Role | Object | Action | Permission |
|---|---|---|---|---|
| Dean | Primary doctor | O B J A(Alice), O B J B(Alice) | Read/write | Permit |
| Bob | General practitioner | O B J A(Alice), O B J B(Alice) | Read/write | Permit |
| Cara | Gastroenterologist | O B J B(Alice) | Read | Permit |
| Alex | Medical coordinator | O B J B(Alice) | Read | Permit |
Assumption 4
Role and team role assignment: If constraints C 1,...,C n are true, then role r and tr are assigned to users.
For the given system, the following access control policies are defined as follows:
- A private object can be accessed only by users with an associated action team role or a main role. Formally:
- A read operation can be performed on a protected object by any user with an associated team role. Formally:
Each user, object, or operation is associated with a set of attributes that may be used for access control decisions. For example, a user’s attributes may include the user’s role, team role, and ID. An object’s attributes may include the file type (private or protected) and file name. In our model, policy rules are specified that are applicable to multiple-attribute requests [4].
Example 1
Access state.
Consider Alice’s case. We assume that in the initial state denoted by γ 1 the formal model assignment is presented in Table 1 as follows:
where:
Security Analysis
Given access D F,Q,P S, and Γ, the security analysis takes the form (γ 1,q,p s,D F) where γ 1 ∈ Γ is the state, q ∈ Q is the access request, p s ∈ P S is the rule applicable to make a decision regarding an access request and D F ∈{0,1} is the decision function. Given a request q = {u s r,(o p r,o b j)}, if all rules (conditions) in PS are all evaluated as true, then the request is either permitted or denied according to the decision, as described in the access control decision function (Definition 23).
The proof of Example 1, let q = {C a r a,(w r i t e,o b j b)}. q is an access request from Cara who has been assigned t r t and wants to write in Alice’s file O B J B(Alice).
Proof 1
It is noted that the access request is mapped to 0 because Cara is not permitted to write Alice’s O B J B(Alice). With security analysis we can study safety properties, availability and mutual exclusion properties. Given access state γ 1 and S P ∈ A P, we can answer the questions concerning safety (is u s r ⊂{U S R} possible?) and availability (is u s r ⊂{U S R} necessary?) presented in [45] as follows:
Safety: Let usr be a presumably untrusted user. Is u s r ⊂{U S R} possible? In other words, is there a state in which user usr (presumably untrusted) could be included in the user set USR? A “no” answer means the system is safe. In our model, we assume that state γ 1 fully determines who can perform what on which object. Also, we assume that, in addition to administrative information, S P ∈ A P contains all the information about trusted users in user set (USR). In WBAC, users are considered as the healthcare providers who, on the one hand, are fully trusted and have the authority to (unintentionally) take the system to a state that violates the security requirements, but they are trusted not to do so. On the other hand, an insider who is trusted and included in the user set u s r ∈ U S R can intentionally take the system to a state that violates the security requirements.
Availability: Let usr be a presumably trusted user. Is u s r ⊂{U S R} necessary? In other words, in any state, should user usr be allowed to be included in user set USR? In WBAC, the answer should be “yes” because we want every healthcare provider to have access to resources when necessary. But we also want to ensure that every healthcare provider who has permission to access resources is included in user set USR.
Security analysis could ensure that the security requirements of our WBAC model are met, as long as the trusted users behave according to the defined policies. However, since we are dealing with insider issues, we could assume that a trusted user attempts to gain access to an object that is not associated with his/her privileges. The fact that access state γ 1 (Example 1) limits the user from accessing any object that is not associated with his/her privileges, it does not mean that the user (insider) cannot do it if he/she is motivated and has the capability to do so. However, it can be said that the security of the WBAC model is preserved as long as the trusted users are cooperating and behaving according to the defined policies.
Policy Management
Policy management forms the basis of access control. The security of any access control model is based on how the access control policies are defined and implemented in real situations. A policy should precisely capture the privileges and capabilities of users, and any action taken by users should be allowed by the policy [45]. To support dynamic environments such as healthcare, access policies need to be updated in a timely manner. A change or update in the access control system causes a state change from the current access state γ 1 (Definition 22) to a new access state (γ n). Examples of state changes are adding user, deleting user, adding roles, and/or deleting roles. Corresponding to a state change, there could be a policy change. For example, if a new role (r i) is added to the system, r i should have a new policy or update an existing policy for it.
Example 2 shows how to revise (if needed) the policy set when the access state of the WBAC system changes.
Example 2
Policy Revision.
Recall Alice’s treatment case and assume that the primary doctor (Dean) decides to consult another physician (gastroenterologist), and Cara cannot help to solve Alice’s case and she must be replaced. Lisa (gastroenterologist) is now joining Alice’s treatment team t 1 and she will be assigned the thought team role t r t. Then we have a new access state change γ 2 as underlined below.
where
Within the new access state γ 2, a new user called Lisa joins the team. She holds team role t r t. Similar to Cara, Lisa will get access (read only) to Alice’s O B J B resources in order to perform her task. Based on the state change here, it is unnecessary to modify the policy because Lisa was assigned with team role t r t and obtained all permissions associated with t r t.
Example 3
Policy Revision 2.
Continuing from Example 2, assume that Lisa wants to write in Alice’s O B J B. In this case, and based on our defined policy for t r t, Lisa does not have permission to write in Alice’s files. Currently, the system only allows the primary doctor Dean and healthcare providers who are assigned t r a to write to Alice’s objects. We do not want to assign Lisa to team role t r a because she is predominantly preoccupied with diagnosing the disease, and there is no urgent need for her to know Alice’s personal information and other information in O B J A.
To give Lisa permission to write in Alice’s O B J B, we assume a new team role “evaluator” (Fig. 3) would be added to the system. Evaluator is a sub-team role of thought [2]. Based on our team role classification, access to a collaborative resource can be tailored more specifically by harnessing the stipulated team roles.
Then, we have a new access state γ 3 where Lisa will be assigned a new team role. Let the new team role be t r evaluator, and we have (the complete γ 2 will not be repeated but the part that would be changed is shown):
Now, based on the state change, we need to modify our access policies by adding a policy for the new team role t r evaluator. In this case, it is only necessary to modify a policy in collaborative policy set CP (Definition 12) since the changes are done on the collaborative resources. In the new policy, a write operation can be performed on an object protected by any user with associated team role t r evaluator. Formally: .
In Example 3, the policy change (Definition 14) entails adding a new policy for the new team role t r evaluator. Therefore, it becomes P S ′ = P S ∪ P ′ in access state γ 3. The complexity of access control policy revision is dependent on a number of factors, such as the number of users, number of roles, and number of resources. Due to these factors, one important aspect is to guarantee policy completeness [57] and consistency [58].
Policy completeness means that the decisions the access control model should take are completely specified in the access policy. That is, there is no situation in which the system cannot reach the goal specified by the policy because it lacks an appropriate defined policy set for any access request [40]. For example, let P S = {p 1,p 2,...,p n} be a set of policies in PS for team roles and p 1 = t e a m r o l e(t r t) ∧ r e s o u r c e(O B J B) ∧ o p e r a t i o n(r e a d) → a l l o w. PS is said to be incomplete if there is no policy defined for every particular team role.
Detecting incompleteness in a large set of policies is very cumbersome. This challenge increases when the number of users, roles, resources, and environment conditions (e.g., time and location) are included in the policies [57]. The problem of incompleteness has been studied intensively in the access control community [57]. Therefore, automated mechanisms or tools are highly needed to assist policy administrators with detecting incompleteness and validating policy sets. However, policy incompleteness is out of the scope of this study. In our work [4], incompleteness is resolved by denying all access in unspecified cases.
Policy consistency means there are no contradictions or inconsistencies in a particular set of policies. Policies are said to be inconsistent for a specific situation when different incompatible policies are applicable [58]. Some researchers have attempted to solve the problem of inconsistency by adding special meta-rules to access control policies [56]. For example, XACML contains conflict resolution combining algorithms (e.g., deny-overrides algorithm, first-applicable algorithm, etc.) for combining rules and policies to solve a decision conflict between multiple policies [46].
Another important aspect of policy revision is the correctness of policy implementation. In our work [7], we apply modeling checking tool ACPT (access control policy testing) [38] to specify policy models and their properties during policy modeling to assure that WBAC policies satisfy the security properties intended by the model.
WBAC Model Performance Evaluation
In this section, we apply an evaluation framework adapted from [11, 12] to compare the performance of our model with the traditional RBAC and ABAC models. Since the WBAC model is based on RBAC and ABAC, here, we want to understand how WBAC model performance responds to changes in dynamic environments. The evaluation framework uses big O notation [17, 21] to describe the model’s functional capabilities. The framework supports a quantitative analysis based on the core function of access control as follows.
Definition 24
Authorization complexity is the process of evaluating the complexity of the access control decision function (Definition 23) to make an authorization decision (permit or deny) for an access request by a user to perform an operation on an object.
Definition 25
Permission modification is the process of modifying and updating the sets of permissions associated with roles and team roles to meet the authorization requirements of an organization. The following schema formally describes permission modification, where k is the number of roles or team roles represents changes.

Definition 26
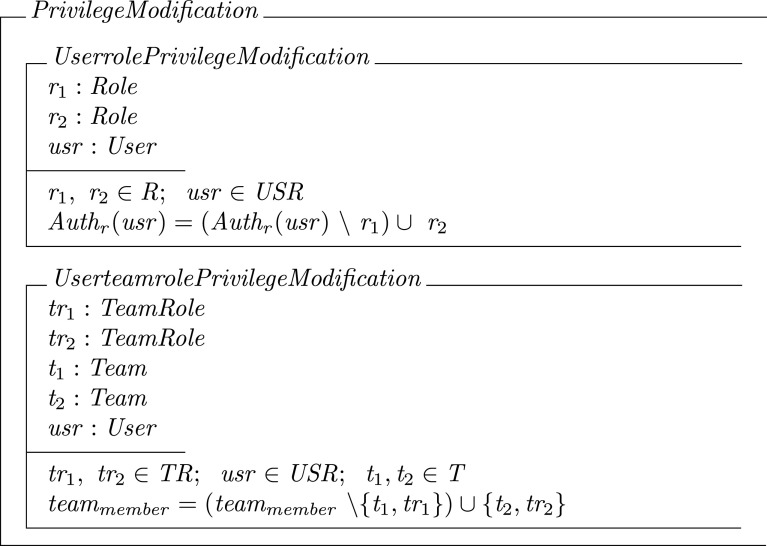
Privilege modification is the process of changing and modifying user membership into a role or team role (e.g., Example 2). Formally:
Definition 27
Revocation process is the process of revoking user membership in a role or team role. In WBAC, there are four types of membership revocation: (1) user revocation, where the user membership of a role is revoked; (2) team membership revocation, where the user is removed from the team by revoking his/her team role; (3) team revocation, where a complete team (t) is revoked from work (w); and (4) work revocation, the complete collaborative work is revoked. Formally:
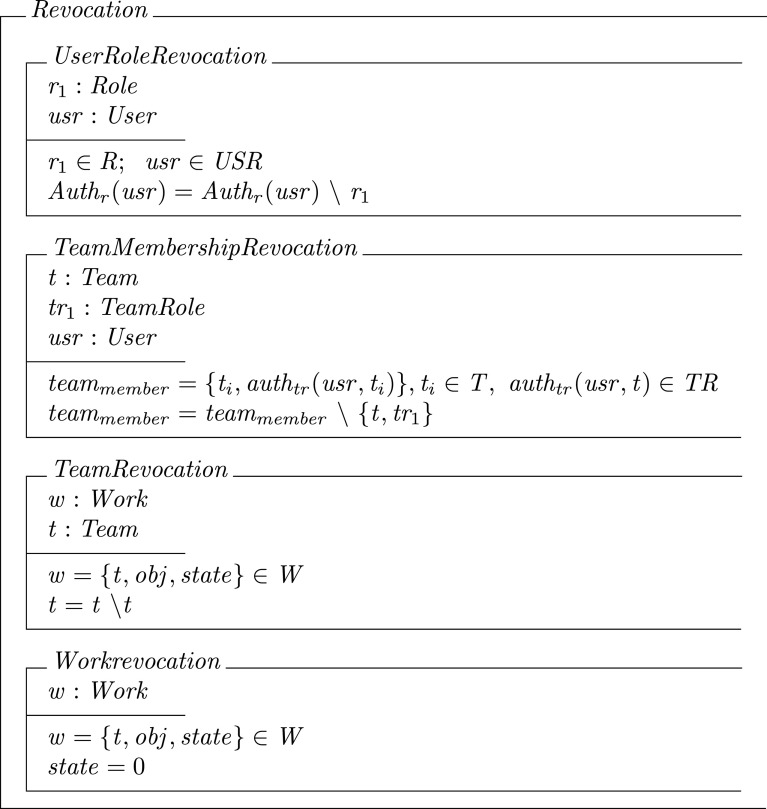
In the case of work revocation, the complete set of teams assigned to work is automatically revoked.
Definition 28
Permission review is the process of reviewing all available permissions (role and/or team role) assigned to a particular user. This can be done by checking the set of authorized role/team role (Definition 6) assigned to the user.
WBAC Performance Analysis
Authorization complexity: WBAC makes an access decision based on the role and team role assigned to a user as well as the permission associated with the role/team role. When a user requests an operation over an object, WBAC checks what role and/or team role is assigned to this user and the permission associated with the user’s active role or authorized team role, then returns with an access decision. The access control decision function (DF) (Definition 23) takes the access request (Q) (Definition 21) as an input and returns a Boolean value presenting the access control decision. The pre-condition for the success of DF is as shown in (21) and (22). In the worst case, the complexity of WBAC’s DF is O(c a r d(a c t r(u s r)) + (c a r d(w) × c a r d(t e a m member))).
Permission modification: In WBAC, permissions are modified by updating the permissions associated with roles and team roles in P E R-R-A(p e r,r) (5) and P E R-T R-A(p e r,t r) (6) without changing the privilege for each user. The permission modification function (Definition 25) takes p e r 1, p e r 2 ∈ P R E, and r ∈ R or t r ∈ T R as input. The function revokes p e r 1 if p e r 1 is mapped to r in P E R-R-A(p e r,r), and then grants r the new permission p e r 2. The case is similar to team role tr. In this case, the complexity of the WBAC permission modification function is , where k index of roles and team roles to be changed. In the worst case, it is assumed that the function would go through the complete set of R and TR to find the p e r 1 to be updated. However, in practice, the set of TR is very small. Therefore, the realistic complexity for team roles policy modification would be O(1).
-
Privilege modification: WBAC handles the change of user privilege by modifying user membership into role or team role relations ((1) and (3)). When a user permission changes, the user is revoked from the current a u t h r(u s r) and/or a u t h tr(u s r,t) (authorization constraint Section 3.2 must be true) and the new privilege is established based on the new access requirements.
The privilege modification function (Definition 26) takes r 1, r 2 ∈ R and u s r ∈ U S R as input, deletes the assignment of usr to r 1 and establishes a new assignment of usr to r 2. The function goes through the complete set of a u t h r(u s r) ∈ u s r to find the r to be updated. Therefore, the complexity of the WBAC privilege modification function is O(c a r d(a u t h r(u s r))). In case of team role, the privilege modification function takes t ∈ T, u s r ∈ U S R and t r a, t r t ∈ T R as input, deletes the assignments of usr to {t,t r a} and establishes a new assignment of usr to {t,t r t}. The difference between role r and tr is that, in tr the function goes through all teams to check the team membership and find the assignment of {t,t r a} to usr and update it accordingly. Therefore, the complexity of the WBAC privilege modification function in case of team role is O(c a r d(t e a m member)).
In the worst case, the privilege modification function goes through the complete set of a u t h r(u s r) ∈ u s r and t e a m member to find the assignment of role and team role to be updated. Thus, the complexity of the privilege modification function is O(c a r d(a u t h r(u s r)) + c a r d(t e a m member)).
- Revocation: WBAC handles four revocation functions as shown in Definition 20.
- The user role revocation function takes user u s r ∈ U S R as input and deletes all user assigned relations in U S R-R-A(u s r,r). The function goes through the complete set of a u t h r(u s r) to find all usr assignments to be deleted. In this case, the complexity of the WBAC user revocation function is O(c a r d(a u t h r(u s r))).
- The team membership revocation function takes t ∈ T, t r ∈ R T and u s r ∈ U S R as input and goes through the complete set of t e a m member to delete the user team membership by revoking his/her team role. In the worst case, the complexity of the team membership revocation function is O(c a r d(t e a m member)).
- The team revocation function takes w ∈ w and t ∈ T as input and revokes the complete team from the work. In the worst case, it is assumed to go through the whole set of W to find the assigned team to be revoked. Thus, the complexity of the team revocation function is O(c a r d(w)) + (c a r d(t))).
- The work revocation function takes w ∈ W as input and goes through the complete set of W to find the w to be revoked by changing the work state (Definition 10) to 0. Thus, the complexity of work revocation function is O(c a r d(W)).
Permission review: The permission review function (Definition 28) determines what permission (roles and/or team roles) a single user has. It takes usr as input and goes through the set of a u t h r(u s r) and t e a m member to find all permissions assigned to usr. The complexity of the permission review function is .
Comparing WBAC with the RBAC and ABAC Models
WBAC model was proposed to support the collaboration requirements and improve the manageability of access control. Here, we compare WBAC with RBAC and ABAC. Table 2 presents a comparison summary of the performance complexity of RBAC, ABAC and WBAC.
Table 2.
Comparison summary of the performance complexity of RBAC, ABAC, and WBAC
| Function | Access control model | ||
|---|---|---|---|
| RBAC | ABAC | WBAC | |
| Authorization complexity | O(c a r d(R)) | O(c a r d(P S) + c a r d(R U)) | O(c a r d(a c t r(u s r)) + (c a r d(w) × c a r d(t e a m member))) |
| Permission modification | O(c a r d(P S)) | ||
| Privilege modification | O(c a r d(U S R)) | O(1) | O(c a r d(a u t h r(u s r)) + O(c a r d(t e a m member))) |
| Revocation | O(c a r d(U S R)) | Undefined | O(c a r d(a u t h r(u s r)) + O(c a r d(t e a m member))) |
| Permission review | O(c a r d(U S R) × c a r d(R)) | O(c a r d(P S)) | |
RBAC makes authorization decisions based on a set of permissions associated with the roles. Therefore, when a user requests an operation over an object, RBAC checks the user’s role and if the requested permission is associated with the role, access is permitted; otherwise, it is denied. In the worst case, the authorization complexity of RBAC is O(c a r d(R)) (Table 2) [11]. ABAC makes authorization decisions based on a user’s attributes, object’s attributes, and operation’s attributes against the rules in the applicable policy sets (PS) [12]. ABAC takes the user’s attributes, object’s attributes, and the requested operation and checks them against the applicable policy. If the policy is satisfied with the requested attributes, access is permitted, otherwise the access is denied. In the worst case, the complexity of the ABAC authorization decision is O(c a r d(P S) + c a r d(R U)), where SP is the policy sets and RU is applicable rules.
To compare the authorization complexity of the access decision function of RBAC with WBAC, we assume the active role assigned to a user in RBAC is equal to the active role (a c t r(u s r)) assigned to the user in WBAC. However, the WBAC model was proposed to support the collaboration requirements and improve the manageability of access control during collaboration. Thus, WBAC adds insignificant time complexity when checking the collaboration policies (Definition 12). WBAC has to check the set of active work W and teams assigned to w i in order to make the authorization decision. RBAC denies an access request if a user does not have a role, while WBAC investigates further to check if the user is invited to the collaborative work. As we mentioned earlier, in most cases, especially in healthcare organizations, the invited user is an outsider who does not have an organization role [3]. Therefore, considering the collaboration requirements [4] and the granularity provider by WBAC based on the team role classification as well as object classification, the difference in time complexity added by T and TR is insignificant. Compared with WBAC, ABAC access evaluation depends on the process of finding the set of applicable policies in the complete policy set and the number of applicable rules that need to be evaluated.
Concerning the permission modification of WBAC and RBAC, WBAC performs similar to RBAC. RBAC makes the permission change by modifying and updating the permission sets associated with roles without changing the privileges for each user in the system. In the worst case, the permission modification of RBAC is , where it is assumed to go through the complete set of R to find the permission to be changed or updated. We believe the proposed team roles do not add much complexity to WBAC because there is only O(1) and WBAC performance can be improved by the way the data structures are used to store R and TR as well as what searching function or algorithm is used to find r ∈ R and t r ∈ T R to be updated for the changes. ABAC treats permission modification differently from RBAC and WBAC. It modifies the permission by updating or changing all the relevant attributes associated with the users. However, permission modification in RBAC is a very complex process. The complexity (O(c a r d(P S))) is dependent on the number of attributes used in the policy, namely 2n, where n is the number of attributes [11].
Considering the privilege modification of RBAC is O(c a r d(U S R)) as shown in Table 2, RBAC changes and updates the privilege by modifying the user membership into roles. WBAC handles user permission change similar to RBAC. Thus, the modification of user privilege in WBAC is as complex as in RBAC because in RBAC it is assumed that [11] the privilege modification function goes through the complete set of users to find the user role assignment that needs to be changed. In WBAC, the complexity is O(c a r d(a u t h r(u s r)) + O(c a r d(t e a m member))), in which it is assumed that set (c a r d(a u t h r(u s r,t)) ≤ (c a r d(R)) while set (c a r d(t e a m member) is also less than or equal to O(c a r d(U S R)) in RBAC. ABAC makes the privilege modification based on the user attribute and policy. The complexity of modifying user privilege is O(1). For example, if the user changes his/her position, only the position attribute needs to be changed. Moreover, all relevant policies associated with the old and new positions need to be updated to accommodate the current requirements.
The revocation process in WBAC is a little more complex compared to RBAC. Due to the use of work entity W to manage the collaborative work, WBAC adds four processes to the revocation process as shown in Definition 27. The user role revocation process in WBAC is similar to RBAC. WBAC and RBAC handle user role revocation by modifying the user membership in the U S R-R-A(u s r,r) assignment relation. The team membership revocation process in WBAC updates the user membership in the U S R-T-A(u s r,t) assignment relation. Its complexity is O(c a r d(t e a m member)), whereby the process must check the user memberships in all teams to find the team in which the user membership needs to be changed. Moreover, the team revocation process revokes the team assignment in relation T-W-A(t,w). Also, in WBAC, work w has to be revoked upon the completion of work (patient treatment). Once w is revoked, complete set of teams assigned to w will be revoked.
The permission review in RBAC is done by checking the set of permissions associated with the roles assigned to the user. The complexity is O(c a r d(U S R) × c a r d(R)) and WBAC handles this in a similar manner to RBAC. In WBAC, the system checks the set of a u t h r(u s r)) and the set of t e a m member for each user to determine all available permissions associated with a user’s authorized roles and authorized team roles. ABAC complicates the permission review because a large set of policies must be checked (O(c a r d(P S))) to determine the available permissions for every user.
Discussions, Future Work, and Conclusions
In this section, discussions, future works, and conclusions are presented.
Discussions
The healthcare environment is complex environment, where we have strong security and privacy requirements. The environment can be highly dynamical and the total number of objects and subject involved is potentially very high. That is, for the actual collaboration cases, only a fairly small subset of object and subjects will be involved, but we cannot know the participants in advance. One example of such a situation is explained in our case scenario (Section 2), which may not be predictable and it would be hard to express the condition of who should join the collaboration and when Dean necessitates collaborative support from other parties. Moreover, in deciding on the extent and limit of resource sharing, for instance, in the case of Alice’s treatment, which sensitive data should be disclosed to an assisting practitioner so collaboration can be effective, and which should be hidden to safeguard the patient’s privacy?
WBAC was proposed to address these concerns and support the security and collaboration requirements in access control [2, 4]. The major contributions of the WBAC model include ensuring that access rights are dynamically adapted to the actual needs of healthcare providers and providing fine-grained control of access rights with the least privilege principle, whereby healthcare providers are granted minimal access rights to carry out their duties. In our case scenario (Section 2), it was noted that primary doctor Dean could not solve Alice’s case alone. He invited a multidisciplinary team including Bob, Cara, and Alex to help. In this team, Dean is the core physician in the collaborative work and serves as the group manager. He is responsible for initiating the work (Alice’s treatment case) and choosing practitioners (group of doctors) who may be required to attend Alice’s consultation and treatment. This implies that Dean holds the main role. In other words, he owns the initiated collaborative work. Therefore, Dean is given a full access (based on his role as primary physician, Table 1) with regard to patient-related information. Bob, Cara and Alex are assigned to team roles based on the job function they will perform in Alice’s treatment.
The main advantage of WBAC is that it simplifies manageability in terms of modifying and updating the sets of permissions associated with roles and team roles, modifying and updating user-role and user-team role assignment, as well as reducing the complexity of permission reviews. Another advantage of WBAC is the least privilege and separation of duties (SoD) of team membership. Team roles define the least privilege and SoD that a user is required to perform on a particular object and also to restrict objects that are considered very sensitive (need-to-know principle). Users are assigned to classified team roles based on their required jobs during collaboration and no user should have more rights that can be misused. This minimizes potential damage due to unauthorized and improper access.
WBAC inherits the disadvantage of RBAC in the way that it requires very complex role engineering in terms of role predefining and role support. It necessitates intimate knowledge of the objects’ (i.e., healthcare records) classification and how permission (i.e., operation on an object) is granted to what role/team role. Healthcare records contain a wide range of information and healthcare record classification is also expensive as it requires skilled and knowledgeable people. Failure to achieve appropriate classification of healthcare records would render WBAC less secure. Other concerns with collaboration using WBAC are collaboration policy conflicts and permission constraints between collaborative parties. A collaboration pattern for information sharing is required to provide the set of rules regarding how the collaboration should be carried out. A control guideline is also required to secure collaboration between collaborative parties.
Although many challenges remain, WBAC seems to be a very promising candidate indeed. We are optimistic that WBAC can handle dynamic environments and scales well. This conclusion is based on case evaluations. While this allows for optimism about the suitability of WBAC for use within cooperative healthcare environments, final judgment must be reserved until field tests have been conducted.
Future Work
This research work can continue in the following directions.
Prototype the functionality to be implemented: develop and prototype the WBAC functionality to be implemented to understand the possible difficulties in managing the model during actual implementation; model performance validity could also be evaluated in terms of resource consumption, e.g., time and computational capability.
Cross-Border Healthcare Collaboration: European Union (EU) countries are seeking new ways to modernize and transform their healthcare systems by using information and communications technology in order to provide EU citizens (patients) with safe and high quality treatment in any EU country [20, 66] (EU directive 2011/24/EU framework on cross-border health care collaboration in the EU [25–27, 52]). Access to cross-border healthcare in the EU has undergone many developments in both academia and industries to meet EU healthcare domain needs. The eHealth Action Plan 2012–2020 [24] and the EU-funded project “UNIversal solutions in TELemedicine deployment for European HEALTH care” (United4health) [64] are among such developments. The aim of these projects is to provide solutions to improve healthcare quality, provide access to a high-quality healthcare system to all EU citizens around Europe, and support close cooperation between healthcare professionals and care providers from different organization. Therefore, in the future, the WBAC model can be further investigated in terms of cross-border healthcare collaboration. The plan is to evaluate the validity of the model to provide solutions to improve healthcare quality, provide access to a high-quality healthcare system to all EU citizens around Europe, and supporting secure cooperation between healthcare professionals and care providers from different organization.
Conclusions
According to the security and performance analysis of the proposed model, WBAC is suitable for collaborative healthcare systems in addressing information sharing and information security matters. It caters to the requirements of access control in collaborative environments and provides a flexible access control model without compromising the granularity of access rights. Moreover, this model is secure and easy to manage for supporting cooperative engagements that are best accomplished by organized, dynamic teams of healthcare practitioners within or among healthcare organizations whose objective is to achieve a specific work (patient treatment case). We believe WBAC meets our expectation of allowing fine-grained access control as well as enhances the practicability and manageability of access control in dynamic collaboration environments. Our conclusion is based on case evaluation. While this allows us to be optimistic about the suitability of WBAC for use within cooperative healthcare environments, we must reserve final judgment until field tests have been conducted.
Footnotes
Contributor Information
Mohamed Abomhara, Email: mohamed.abomhara@uia.no.
Huihui Yang, Email: huihui.yang@ccis.no.
Geir M. Køien, Email: geir.koien@uia.no
Mehdi Ben Lazreg, Email: mehdi.ben.lazreg@uia.no.
References
- 1.Abomhara M, Gerdes M, Køien GM. A stride-based threat model for telehealth systems. Norsk informasjonssikkerhetskonferanse (NISK) 2015;8(1):82–96. [Google Scholar]
- 2.Abomhara M, Køien GM (2016) Towards an access control model for collaborative healthcare systems. In: Proceedings of the 9th international joint conference on biomedical engineering systems and technologies (BIOSTEC 2016), vol 5, pp 213–222
- 3.Abomhara M, Lazrag MB (2016) Uml/ocl-based modeling of work-based access control policies for collaborative healthcare systems. In: IEEE 18th International conference on e-health networking, applications and services (Healthcom). IEEE, pp 1–6
- 4.Abomhara M, Nergaard H (2016) Modeling of work-based access control for cooperative healthcare systems with xacml. In: Proceedings of the Fifth international conference on global health challenges (GLOBAL HEALTH 2016 ), pp 14–21. ISBN:978-1-61208-511-1
- 5.Abomhara M, Yang H (2016) Attribute-based authenticated access for secure sharing of healthcare records in collaborative environments. In: Proceedings of the eighth international conference on ehealth, telemedicine, and social medicine (eTELEMED 2016), pp 138–144. ISBN: 978-1-61208-470-1
- 6.Abomhara M, Yang H. Collaborative and secure sharing of healthcare records using attribute-based authenticated access. Int J Adv Secur. 2016;9:3 & 4. [Google Scholar]
- 7.Abomhara M, Yang H, Køien GM (2016) Access control model for cooperative healthcare environments: modeling and verification. In: IEEE International conference on healthcare informatics (ICHI). IEEE, pp 46–54
- 8.Agris JL. Extending the minimum necessary standard to uses and disclosures for treatment: currents in contemporary bioethics. J Law Med Ethics. 2014;42(2):263–267. doi: 10.1111/jlme.12140. [DOI] [PubMed] [Google Scholar]
- 9.Ahn GJ, Sandhu R. Role-based authorization constraints specification. ACM Trans Inf Syst Secur (TISSEC) 2000;3(4):207–226. doi: 10.1145/382912.382913. [DOI] [Google Scholar]
- 10.Alotaiby FT, Chen JX (2004) A model for team-based access control (tmac 2004). In: International conference on information technology: coding and computing, 2004. Proceedings. ITCC 2004, vol 1. IEEE, pp 450–454
- 11.Alshehri S. Toward effective access control using attributes and pseudoroles. Ph.D. thesis: Rochester Institute of Technology; 2014. [Google Scholar]
- 12.Alshehri S, Raj RK (2013) Secure access control for health information sharing systems. In: 2013 IEEE International conference on healthcare informatics (ICHI). IEEE, pp 277–286
- 13.Annas GJ. Hipaa regulations–a new era of medical-record privacy? New England J Med. 2003;348(15):1486–90. doi: 10.1056/NEJMlim035027. [DOI] [PubMed] [Google Scholar]
- 14.Bain C. The implementation of the electronic medical records system in health care facilities. Procedia Manuf. 2015;3:4629–4634. doi: 10.1016/j.promfg.2015.07.547. [DOI] [Google Scholar]
- 15.Belbin M (1985) Management teams, why they succeed or fail. In: Bulletin of the British psychological society, vol 38. British Psychological Society, pp A1–A1
- 16.Belbin RM (2012) Team roles at work. Routledge
- 17.Black PE (2007) Big-o notation. Dict Algor Data Struct 2007
- 18.Boneh D, Shen E, Waters B (2006) Strongly unforgeable signatures based on computational diffie-hellman. In: International workshop on public key cryptography. Springer, pp 229–240
- 19.Borrill C, West M, Shapiro D, Rees A. Team working and effectiveness in health care. Br J Healthc Manag. 2000;6(8):364–371. doi: 10.12968/bjhc.2000.6.8.19300. [DOI] [Google Scholar]
- 20.Byrne D (2004) Enabling good health for all: a reflection process for a new EU health strategy. Commission of the European Communities. http://ec.europa.eu/health/ph_overview/Documents/pub_good_health_en.pdf
- 21.Chang SK (2003) Data structures and algorithms, vol 13 World Scientific
- 22.Chen Y, Nyemba S, Malin B. Detecting anomalous insiders in collaborative information systems. IEEE Trans Depend Secur Comput. 2012;9(3):332–344. doi: 10.1109/TDSC.2012.11. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Chen Y, Nyemba S, Zhang W, Malin B (2011) Leveraging social networks to detect anomalous insider actions in collaborative environments. In: 2011 IEEE International conference on intelligence and security informatics (ISI). IEEE, pp 119–124 [DOI] [PMC free article] [PubMed]
- 24.Commission E (2012) ehealth action plan 2012-2020 – innovative healthcare for the 21st century. European Commission staff working document for informative purposes. https://ec.europa.eu/digital-single-market/en/news/ehealth-action-plan-2012-2020-innovative-healthcare-21st-century
- 25.Commission E (2013) Overview of the national laws on electronic health records in the eu member states and their interaction with the provision of cross-border ehealth services. EU Health Programme (2008-2013). http://ec.europa.eu/health/ehealth/docs/laws_report_recommendations_en.pdf
- 26.Commission E (2015) Commission report on the operation of directive 2011/24/eu on the application of patients’ rights in cross-border healthcare. Report from the commission to the european parliament and the council (Brussels- 2015). http://ec.europa.eu/health/cross_border_care/policy/index_en.htm
- 27.Commission E (2015) Expert panel on effective ways of investing in health: Cross-border cooperation. http://ec.europa.eu/health/expert_panel/opinions/docs/009_crossborder_cooperation_en.pdf
- 28.Daiqin He D, Yang J. Authorization control in collaborative healthcare systems. J Theor Appl Electron Commerce Res. 2009;4(2):88–109. doi: 10.4067/S0718-18762009000200008. [DOI] [Google Scholar]
- 29.Denning T, Borning A, Friedman B, Gill BT, Kohno T, Maisel WH (2010) Patients, pacemakers, and implantable defibrillators: Human values and security for wireless implantable medical devices. In: Proceedings of the SIGCHI conference on human factors in computing systems. ACM, pp 917–926
- 30.Ferraiolo D, Chandramouli R, Hu V, Kuhn R (2016) A comparison of attribute based access control (abac) standards for data service applications:extensible access control markup language (xacml) and next generation access control (ngac). NIST Special Publication (800-178) 800(178). http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-178.pdf
- 31.Ferraiolo D, Kuhn DR, Chandramouli R (2003) Role-based access control. Artech House
- 32.Ferraiolo DF, Sandhu R, Gavrila S, Kuhn DR, Chandramouli R. Proposed nist standard for role-based access control. ACM Trans Inf Syst Secur (TISSEC) 2001;4(3):224–274. doi: 10.1145/501978.501980. [DOI] [Google Scholar]
- 33.Graham GS, Denning PJ (1972) Protection: principles and practice. InL Proceedings of the May 16-18, 1972, spring joint computer conference. ACM, pp 417–429
- 34.Harrison MA, Ruzzo WL, Ullman JD. Protection in operating systems. Commun ACM. 1976;19(8):461–471. doi: 10.1145/360303.360333. [DOI] [Google Scholar]
- 35.U.S. Department of Health & Human Services. Hipaa privacy rule and sharing information related to mental health. http://www.hhs.gov/hipaa/for-professionals/special-topics/mental-health/
- 36.Hu VC, Ferraiolo D, Kuhn DR (2006) Assessment of access control systems. US Department of Commerce National Institute of Standards and Technology
- 37.Hu VC, Ferraiolo D, Kuhn R, Schnitzer A, Sandlin K, Miller R, Scarfone K. Guide to attribute based access control (abac) definition and considerations. NIST Spec Publ. 2014;800:162. [Google Scholar]
- 38.Hwang J, Xie T, Hu V, Altunay M (2010) Acpt: a tool for modeling and verifying access control policies. In: 2010 IEEE International symposium on policies for distributed systems and networks (POLICY). IEEE, pp 40–43
- 39.Kang MH, Park JS, Froscher JN (2001) Access control mechanisms for inter-organizational workflow. In: Proceedings of the sixth ACM symposium on access control models and technologies. ACM, pp 66–74
- 40.Kikuchi S, Tsuchiya S, Adachi M, Katsuyama T (2007) Policy verification and validation framework based on model checking approach. In: Fourth international conference on autonomic computing (ICAC’07). IEEE, pp 1–1
- 41.Koch M, Mancini LV, Parisi-Presicce F (2002) Decidability of safety in graph-based models for access control. In: European symposium on research in computer security. Springer, pp 229–244
- 42.Kugblenu F, Asim M (2007) Separation of duty in role based access control system: a case study. Master’s thesis, School of Engineering Blekinge Institute of Technology
- 43.Kuhn DR (1997) Mutual exclusion of roles as a means of implementing separation of duty in role-based access control systems. In Proceedings of the second ACM workshop on Role-based access control. ACM, pp 23–30
- 44.Le XH, Doll T, Barbosu M, Luque A, Wang D. An enhancement of the role-based access control model to facilitate information access management in context of team collaboration and workflow. J Biomed Inf. 2012;45(6):1084–1107. doi: 10.1016/j.jbi.2012.06.001. [DOI] [PubMed] [Google Scholar]
- 45.Li N, Tripunitara MV. Security analysis in role-based access control. ACM Trans Inf Syst Secur (TISSEC) 2006;9(4):391–420. doi: 10.1145/1187441.1187442. [DOI] [Google Scholar]
- 46.Li N, Wang Q, Qardaji W, Bertino E, Rao P, Lobo J, Lin D (2009) Access control policy combining: theory meets practice. In: Proceedings of the 14th ACM symposium on access control models and technologies. ACM, pp 135–144
- 47.Li Q, Zhang X, Xu M, Wu J. Towards secure dynamic collaborations with group-based rbac model. Comput Secur. 2009;28(5):260–275. doi: 10.1016/j.cose.2008.12.004. [DOI] [Google Scholar]
- 48.Maji HK, Prabhakaran M, Rosulek M (2011) Attribute-based signatures. In: Cryptographers’ track at the RSA conference. Springer, pp 376–392
- 49.Menachemi N, Collum TH. Benefits and drawbacks of electronic health record systems. Risk Manag Healthc Policy. 2011;4:47–55. doi: 10.2147/RMHP.S12985. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 50.Mitchell P, Wynia M, Golden R, McNellis B, Okun S, Webb CE, Rohrbach V, Von Kohorn I (2012) Core principles & values of effective team-based health care. Washington DC: Institute of Medicine
- 51.Oh S, Park S. Task–role-based access control model. Inf Syst. 2003;28(6):533–562. doi: 10.1016/S0306-4379(02)00029-7. [DOI] [Google Scholar]
- 52.Passarani I (2013) Patient access to electronic health records. Report of the eHealth Stakeholder Group. http://ec.europa.eu/health/expert_panel/opinions/docs/009_crossborder_cooperation_en.pdf
- 53.Probst CW, Hunker J, Gollmann D, Bishop M (2010) Insider threats in cyber security, vol 49. Springer Science & Business Media
- 54.Rubio-Medrano CE, D’Souza C, Ahn GJ (2013) Supporting secure collaborations with attribute-based access control. In: 2013 9th International conference conference on collaborative computing: networking, applications and worksharing (collaboratecom). IEEE, pp 525–530
- 55.Sandhu RS, Coyne EJ, Feinstein HL, Youman CE. Role-based access control models. Computer. 1996;2:38–47. doi: 10.1109/2.485845. [DOI] [Google Scholar]
- 56.Shaikh RA, Adi K, Logrippo L (2016) A data classification method for inconsistency and incompleteness detection in access control policy sets. Int J Inf Secur 1–23
- 57.Shaikh RA, Adi K, Logrippo L, Mankovski S (2010) Detecting incompleteness in access control policies using data classification schemes. In: 2010 Fifth international conference on digital information management (ICDIM). IEEE, pp 417–422
- 58.Shaikh RA, Adi K, Logrippo L, Mankovski S (2010) Inconsistency detection method for access control policies. In: 2010 Sixth international conference on information assurance and security (IAS). IEEE, pp 204–209
- 59.Shen H, Dewan P (1992) Access control for collaborative environments. In: Proceedings of the 1992 ACM conference on Computer-supported cooperative work. ACM, pp 51–58
- 60.Sohr K, Ahn GJ, Gogolla M, Migge L (2005) Specification and validation of authorisation constraints using uml and ocl. In: Computer security–ESORICS 2005. Springer, pp 64–79
- 61.Sohr K, Drouineaud M, Ahn GJ, Gogolla M. Analyzing and managing role-based access control policies. IEEE Trans Knowl Data Eng. 2008;20(7):924–939. doi: 10.1109/TKDE.2008.28. [DOI] [Google Scholar]
- 62.Taylor C, Munro AJ, Glynne-Jones R, Griffith C, Trevatt P, Richards M, Ramirez AJ. Multidisciplinary team working in cancer: what is the evidence? BMJ. 2010;340:c951. doi: 10.1136/bmj.c951. [DOI] [PubMed] [Google Scholar]
- 63.Tolone W, Ahn GJ, Pai T, Hong SP. Access control in collaborative systems. ACM Comput Surv (CSUR) 2005;37(1):29–41. doi: 10.1145/1057977.1057979. [DOI] [Google Scholar]
- 64.United4Health: P7 eu project united4health 2013. Umbrella project: http://united4health.eu/
- 65.Wang W (1999) Team-and-role-based organizational context and access control for cooperative hypermedia environments. In: Proceedings of the tenth ACM conference on hypertext and hypermedia: returning to our diverse roots: returning to our diverse roots. ACM, pp 37–46
- 66.Wismar M, Palm W, Figueras J, Ernst K, Van Ginneken E, et al (2011) Cross-border health care in the european union: mapping and analysing practices and policies. World Health Organization
- 67.Zhang R, Liu L (2010) Security models and requirements for healthcare application clouds. In: IEEE 3rd International conference on cloud computing (CLOUD). IEEE, pp 268–275