Abstract
Internet of things (IoT) application in e-health can play a vital role in countering rapidly spreading diseases that can effectively manage health emergency scenarios like pandemics. Efficient disease control also requires monitoring of Standard operating procedure (SOP) follow-up of the population in the disease-prone area with a cost-effective reporting and responding mechanism to register any violation. However, the IoT devices have limited resources and the application requires delay-sensitive data transmission. Named Data Networking (NDN) can significantly reduce content retrieval delays but inherits cache overflow and network congestion challenges. Therefore, we are motivated to present a novel smart COVID-19 pandemic-controlled eradication over NDN-IoT (SPICE-IT) mechanism. SPICE-IT introduces autonomous monitoring in indoor environments with efficient pull-based reporting mechanism that records violations at local servers and cloud server. Intelligent face mask detection and temperature monitoring mechanism examines every person. Cloud server controls the response action from the centre with an adaptive decision-making mechanism. Long short-term memory (LSTM) based caching mechanism reduces the cache overflow and overall network congestion problem.
Keywords: Health care, Named data networking of things, Content Caching, Internet of Things (IoT)
1. Introduction
Surrounded by countless microbes, bacteria and virus novel diseases are reported in every few months. Densely populated disease outbreak epicentres increase the spread of diseases especially airborne diseases and the diseases spread by direct and indirect human interaction [1]. Even if not being infected, humans can become carrier to vicious diseases and can spread them in an exponential rate wherever they travel. Once spread, a tremendous amount of loss in form of finances and lives can occur that can change the management and overall business structure of the whole world putting it to a halt for weeks and months with repercussions lasting for years. Prevalent in a region or population, disease widespread among population of people of a specific region is graded as an endemic [2]. Affecting many people at the same time, the disease eruption and spreading locally grades it to be an epidemic. Out of control disease spread among people of different regions and nationalities and reaching far borders of countries located in another corner of the world results as a pandemic such as Coronavirus Disease-19(COVID-19) [2]. With technological advancements, similar challenges require modern and efficient solutions that are practically deployable to detect and control the spread of diseases.
Smart sensing nodes in real-time collect and forward data over the network of things resulting in the internet of things (IoT) [3]. Providing cheap and feasible solutions with a wide range of utilities, IoT provide services with substantial security and efficient medical record exchange. In past few years, several IoT based platforms have been introduced that promise the provision of state of the art facilities in modern applications including but not limited to smart homes, smart cities, intelligent transportations system (ITS) and e-health care [4]. IoT communication protocols including CoAP, RPL and 6LoWPAN are particularly designed to enable secured communication over resource-constrained low powered IoT devices [5]. The network traffic requires content, information, and data without concerning about the source of the content. The IoT based applications also require broadcast nature of wireless multimedia unlike conventional unicast or multicast wireless transmissions associated with the internet protocol (IP) addresses of both sending node and destination node over heterogeneous networks.
To enable content-centric communication while substituting host-centric communication, named data networking (NDN) paradigm was recently introduced that deeply relies on the concept of information-centric networking (ICN) [6]. Future internet NDN paradigm retrieves content from the network with the application-specific naming scheme and flooding-based broadcast mechanism. Default in-network content caching reduces the end to end content retrieval delay providing efficient wireless communication required for the IoT applications. For the applications of smart homes, building monitoring systems and e-health, NDN-IoT platforms have also been proposed [7]. NDN based smart healthcare system to mitigate and control a pandemic with IoT technology also introduces some challenges. Widespread disease control and mitigation require monitoring and description of warning messages to and from the disaster control centres with confirmed message delivery mechanism with delay sensitivity. Besides, efficient caching is also required to cache the relevant content based on the available resources to mitigate cache overflow problem that can introduce additional delays in the communication.
In this paper, we extend NDN architecture in e-health care and introduce SPICE-IT: Smart COVID-19 Pandemic Controlled Eradication over NDN-IoT. The proposed system utilizes standard operation procedures (SOPs) functionalities in an indoor environment. We introduce novel data structures in NDN and their roles in COVID-19 report and response system. Moreover, the artificially intelligent system enables autonomous detection and reporting of possible COVID-19 suspected patients and violations of the SOPs in the closed spaces. Image processing-based face mask detection and warning generation mechanism is also introduced to monitor people personal habits. An intelligent caching mechanism is also introduced to keep the most relevant and important content in the cache based on the network traffic flow. The paper includes the following novelties and contributions:
-
•
An artificial intelligent face mask detection mechanism.
-
•
A hierarchical architecture is proposed in which the NDN-IoT communicates with local edge and central cloud to respond, monitor, and control pandemic spread with novel data structures.
-
•
An intelligent caching mechanism to enable traffic prediction based caching at local servers.
The rest of the paper is organized as follows. Section 2 discusses the related research works. Section 3 introduces the proposed system model. Face mask detection mechanism is introduced in Section 4. Section 5 introduces the proposed communication mechanism and the performance evaluation of the proposed system is included in Section 6. Section 7 concludes the paper.
2. Related work
With the advancement of IoT based applications in healthcare lead to the development of independent cloud-centric IoT based systems in mobile healthcare (m-health). In [8], an m-healthcare framework architecture is proposed for monitoring and diagnosing the diseases and updating with the level of their severity. The proposed solution has three phases. Phase first consists of biomedical sensors and devices to acquire health-related data of the patient. In phase second, the proposed medical diagnosis system decides the person’s health. Finally, in the third phase, an alert is generated and transmitted. The proposed framework is tested on a database from the web; however, it is not implemented in the real world to validate its performance in real-time critical scenarios.The concept of fog computing and Internet of Things (IoT) for an elderly e-health monitoring was introduced in [9]. The authors have proposed a 3-layer architecture where in the first layer data distribution is provided on the remote database for storage purposes, the second layer provides communication between the first and third layer and the third layer provides data management. The shortcoming in the system is that it does not include any emergency communication module for elderly which is an important and necessary feature. Moreover, the system can be enhanced to predict or diagnose basic diseases based on the symptoms by employing artificial intelligence in the system.
IoT based two-tier smart healthcare monitoring system proposed in [10]. The first tier monitors vital health information remotely in realtime using wireless sensors attached to each individual and the second tier relays the sensor data to the central. The proposed system architecture is not cost and energy efficient considering the sensors used. Moreover, for correlation, quantification and qualification of medical emergency events, better probability and deterministic algorithms are needed to be implemented. [11] also presents a smart healthcare system based on the concept of fog computing and smart e-health gateways. The proposed system architecture includes medical sensors and actuators network in which sensed data is transmitted with wired or wireless protocols to the smart gateways. The network of smart e-health gateways consisting of smart gateways forms a fog which is responsible for performing protocol conversion and providing services like data aggregation, filtering, and dimensionality reduction. Finally, a backend system made up of cloud computing platform for implementing broadcasting, data warehouse and data analytics in addition to GUI for visualization and feedback.
A secure healthcare data communication and monitoring framework which integrates the NDN-based IoT and edge cloud were proposed in [12]. In the proposed architecture IoT and edge cloud are integrated, and clusters are formed to overcome the resource limitations of IoT devices. The medical data in the proposed system is secured using the hash and encryption techniques for converting plaintext to ciphertext [13]. The proposed method however does not tackle the problematic case when cluster head fails to deliver data to edge devices. An NDN-based smart health IoT system named NHealthIoT was proposed in [7]. The proposed architecture comprises three phases where the data is collected from different sensors and processes the data at a local home server. In the data transmission phase, the healthcare data is transmitted to the cloud server using the publish–subscribe model of NDN. In the last phase of remote data processing, the cloud server is present that receives the healthcare data from the home server, analyzes it and supports visualization.
NDN-based smart healthcare IoT system or NDNoT was proposed in [14]. The proposed system supports both static and mobile users with four-layer architecture. The first layer deals with real time data collection. The second layer is collected data that is transmitted to healthcare centres. Networking services and database are provided in the third layer for recording, analysing, and visualizing the health data of the patient. The central control layer is the last layer which performs the function of routing the forwarding requests using NDN CRoS routing algorithm. The use of NDN based IoT systems is not only limited to smart healthcare systems but it also finds its applications in a similar domain of disaster management. An IoT Disaster Management System (DMS) architecture was proposed in [15] based on NDN, particularly for fire disaster. The authors have modified the legacy NDN functionality of producer and consumer and introduced a fire sensor and threshold level modules in the proposed architecture. The system is activated if the threshold level is exceeded indicating a fire situation.
The use of NDN based IoT systems in healthcare and disaster management systems is favourable. However, it is quite challenging to implement such systems due to the problems of NDN such as secure content retrieval, efficient caching and forwarding techniques, retrieval of fresh and valid data, caching overhead and cache replacement. Secure content retrieval using NDN caching technique is one of the major issues while using NDN based architectures. Moreover, the conventional authentication process for consumers in NDN results in high computation overhead and network delay. A collaborative data access control (CDAC) scheme for NDN was introduced in [16]. The producer in the scheme encrypts the data content and forwards it to the cache-enabled routers in the network. Then it acquires a decryption key for decoding the contents. The consumer destroys the sub-key after using which is computed locally using the decryption key.
Many routing strategies have been developed for efficient data retrieval in NDN. An active updating routing strategy in NDN for periodic data retrieval was proposed in [17]. The proposed method adds a period field in data packet’s MetaInfo for getting the periodic characteristic of data which indicates the periodic data generation. The table structure is also modified to store the periodic data. Furthermore, a cache control module is added in the router to support periodic data storage. Finally, a cache update algorithm is also proposed to determine the best active update time and number of requests as per user’s requirement in real-time. The proposed routing policy, however, is not widely applicable and the performance of the router is also not considered by authors to design an optimized algorithm. Enhanced network performance and efficient content availability and retrieval can be achieved using in-network caching of NDN. However, the security and privacy issues are one of the major concerns in this regard.
A reputation based blockchain scheme implemented over NDN for secure caching in a vehicular environment was introduced in [18] that establishes trust between consumer nodes and the content stores. A reputation value is assigned to each content store in the proposed scheme which is further increased/decreased according to the content served by it. The reputation value is increased by the consumer if the consumer is served with valid content. This way the content stores are aware of the trusted content and cache only the trusted content. A caching and forwarding scheme is proposed based on the rendezvous points (RP) [19] in which a detoured forwarding technique is proposed. Depending on the weights assigned request is detoured for a content name. To achieve faster packet forwarding, a route cache is also added to FIB design. Another caching technique in the IoT network is presented in [20] for NDN based IoT traffic which focuses on the freshness of the cached content. The work proposes a Least Fresh First (LFF) cache replacement policy. The proposed policy relies on the prediction of the time of the next event from the sensor for residual life estimation of particular retrieved content. For predicting the time value of the next event of the sensor, the authors have employed the Autoregressive Moving Average (ARMA) model [21]. When the new content arrives and it is to be cached and the cache is full, the proposed LFF algorithm evicts the least fresh content from the cache. The caching technique is useful in case of periodic IoT traffic, however, for OnOff IoT traffic it is not suitable.
The cache replacement in NDN is a critical task that requires an efficient replacement strategy to keep the popular data cached all the time to avoid extra delay and network overhead in re-fetching the data. An NDN cache replacement policy is proposed in [22] named as Named Data Networking Cache replacement approach based on Software Defined Networking (NC-SDN). The replacement strategy is based on the content popularity which is calculated by the switches in the Software Defined Network (SDN) architecture. The proposed approach uses a topological control system inspired by [23] to control the network in real-time. The cache replacement is performed based on three principles: (1) data popularity, (2) available topological information, and 3) collaboration of different nodes in the network. The data popularity is measured at each switch using a counter of Forwarding Interest Base (FIB) table which is incremented every time a content is retrieved from that switch. The content popularity is calculated based on Zipf law [24] The proposed method does not exploit the intelligent control of network resources in NDN. Moreover, the scope of proposed work is limited to single zone communication without exploring the communication between multiple zones.
With the development of machine learning techniques, the automated content caching is becoming popular. [25] implements the machine learning for behaviour of services’ data exchange. For each data item, the proposed system chooses a suitable caching strategy such as LRF or LFU, using deep learning. Recently, for sequential data prediction, recurrent neural networks (RNNs) have been proved as an efficient machine learning tool. Given the sequential nature of content requests, [26] proposes an LSTM based Encoder–Decoder model for predicting the content popularity considering it a seq2seq problem. A proposed caching policy then takes decisions based on the predicted information. Another content caching technique employing the machine learning tool is proposed in [27]. A deep reinforcement learning (DRL) based framework is proposed which employs Wolpertinger architecture for the content caching on the edge node. The system takes the content requests as an input and the DRL agent trains on the deep deterministic policy gradient (DDPG). The system claims to achieve short and long term cache hit rate. However, the system considers just one access point and same data size for all contents. [28] proposes edge caching based on machine learning for video content. The proposed scheme presents a content aware cache admission policy and online reinforcement learning algorithm is used for discovery of critical features from video feature space. The training is performed in two steps including, critical feature and admission decision.
Table 1.
Summary of Literature Review.
| Paper | Technologies used | Domain | Contributions | Limitations |
|---|---|---|---|---|
| [9] | VIoT, cloud | Smart healthcare | Monitoring and diagnosis of disease | No real-tie validation of scheme |
| [10] | Fog computing and IoT | Smart healthcare | Complete e-health system for elderly patients | No emergency communication module |
| [11] | IoT | Smart healthcare | Monitoring of health parameters | Not cost and energy efficient |
| [12] | Fog computing, cloud computing and IoT | Smart healthcare | Strategic positioning of smart gateways in e-health system in ioT | – |
| [13] | NDN based IoT, edge cloud, hashing | Smart healthcare | Healthcare data communication and monitoring + overcoming IoT resource limitations | No counters to cluster head failure problem |
| [8] | NDN, IoT, cloud | Smart healthcare | Monitoring of health parameters | – |
| [15] | NDN, IoT | Smart healthcare | Remote monitoring, storing, and communicating the patient’s health parameters | – |
| [16] | NDN, IoT, Wi-Fi | Disaster management | Fire disaster management system | System does not notify the nearby secure location; inefficient memory and broadcasting strategies used |
| [17] | NDN, IoT | Networking (NDN architecture) | Secure content retrieval and data access control in NDN | Not tested in real wireless IoT scenario |
| [18] | NDN | Networking (NDN architecture) | Routing strategy for periodic data retrieval | Not widely applicable; performance of router not considered in designing routing algorithm |
| [19] | NDN, blockchain | Vehicular Communication | Secure caching in vehicular environment | Not deployed on a real NDN testbed and cross-industry blockchain technologies |
| [20] | NDN | Networking (NDN architecture) | Caching and forwarding scheme for NDN | – |
| [21] | NDN, IoT | Networking (NDN based IoT) | Caching scheme for NDN based IoT traffic | Not suitable for OnOff IoT traffic |
| [22] | NDN, SDN | Networking (NDN architecture) | Cache replacement in NDN | Network resources are not intelligently controlled, suitable only for single zone communication |
| [25] | Machine learning | Content caching | Selection of suitable caching strategy using deep learning | – |
| [26] | Machine learning | Content caching | Predicting content popularity using long short-term memory (LSTM) | – |
| [27] | Machine learning, Edge caching | Content caching | Content caching | System considers just one access point and same data size for all contents |
| [28] | Machine learning, Edge caching | Video content caching | Discovery of critical features from video feature space using online reinforcement learning | – |
3. System model
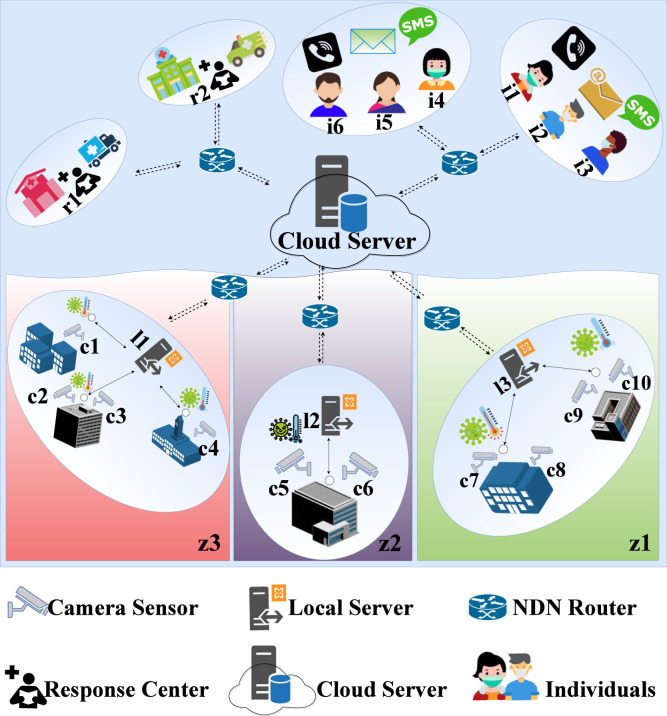
We introduced NDN-IoT based solution to monitor the SOPs of COVID-19 in the closed indoor environment. As illustrated in Fig. 1, the proposed architecture includes a set of installed cameras on buildings, a set of verified individuals that are people with or without masks, region based local servers1 , central cloud server and set of COVID response centres . Cities and resident areas are further divided into a set of different zones . The communication is supported with wired and wireless NDN based network backbone comprising of NDN relays and routers.
Fig. 1.
Proposed architecture.
The proposed architecture comprises of multiple hardware, processing, and communication elements. Cameras and thermal scanners mounted in the closed buildings to monitor individual-person health. Image processing mechanism is introduced to detect the proper face mask-wearing and is combined with the thermal scanning report to decide to generate which type of notification. Sensing a violation of SOP, interest is generated from the building cameras which first arrives at local servers and is further relayed towards the cloud server in multi-hop broadcasting. are assumed to be deployed at distract level although collects and responds to the requests forwarded from all local servers. Databases with the person by person habit and health record is maintained locally servers as well as on with periodic data synchronization. Policy-based decision-making mechanism controls the response of and central server . In response to the interest, takes actions in line with the intensity of the violation, previous record and central policy and generates action messages which act as a content packet.2 The virtual division of cities into zones helps to enforce smart lockdown in disease spread zones only instead of the whole city, province, or state shutdown.
End to end communication is supported with NDN based interest and content pull-based mechanism with novel data structures to provide the e-health service over NDN-IoT to ensure packet delivery. NDN introduces content caching over the relay nodes that participate in the content forwarding process. Considering continues data generation and communication over the network, we introduce long short-term memory (LSTM) based intelligent content caching mechanism that considers network traffic to cache content within the network while avoiding cache overflow problem. The intelligent content caching mechanism ensures that vital content is cached in the relay nodes while reducing the cache overflow problem while reducing the end to end delay.
4. Face mask detection
In this section, we introduce details of the face-mask detection mechanism used in the proposed system.
4.1. MobileNetV2
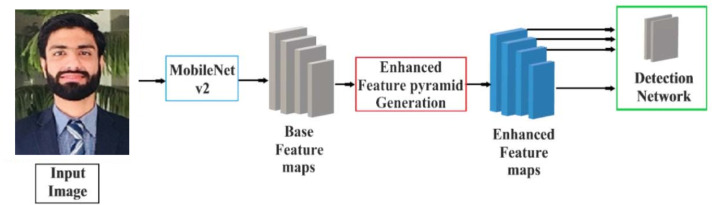
Fig. 2 shows the general architecture of the proposed method. The MobileNet v2 architecture first creates the basic convolution feature maps for fast object detection in low-end systems. An advanced pyramid production module is designed to create an enhanced pyramid, where each level of the pyramid can be used to identify objects of a different scale. Finally, a detection network, which is a fully convolutional network, connects to all feature levels in the extended functional pyramid to find objects. Furthermore, the focal loss function in the classification branch of the detection network is used to transfer class imbalance problems to single-phase object detectors. Details of each module are explained in the following sections.
Fig. 2.
The overall architecture of the proposed method.
4.1.1. Initial feature maps generation
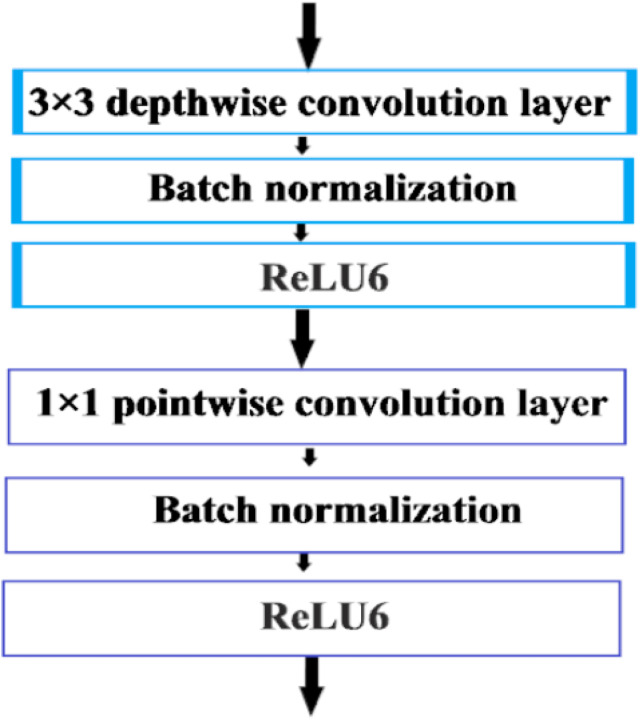
MobileNet is a neural network architecture introduced by Google that works very efficiently on mobile devices or with little processing effort. MobileNet was developed as a model that offers high precision and minimizes mathematical operations and parameters. The architecture of MobileNet v1 [29] replaces regular convolutional layers, which are essential for computer vision activities, but whose computation is quite costly, depthwise separable the 3 × 3 convolution layer that filters the input features. A 1 × 1 convolution layer, called a pointwise convolution layer, that combines these filter values to create new features. Fig. 3 shows a depthwise separable convolution block. Batch normalization and the ReLU6 layer follow each of the depthwise and pointwise convolution layers:
| (1) |
Fig. 3.
The architecture of a depthwise separable convolution block.
Together, the depthwise and pointwise convolution layers do almost the same as normal folding layers, but they are much faster. Suppose the size of the input image is 224 × 224 × 3, the entire architecture of MobileNet v1 is shown in Table 1. As shown in Table 1, MobileNet v1 includes a normal 3 × 3 convolution layer as the first layer, followed by 13 convolution blocks. There are no pooling layers between these depthwise separable blocks. Instead, some of the depthwise convolution layers have a step of 2 to reduce the spatial dimensions of the input feature map.
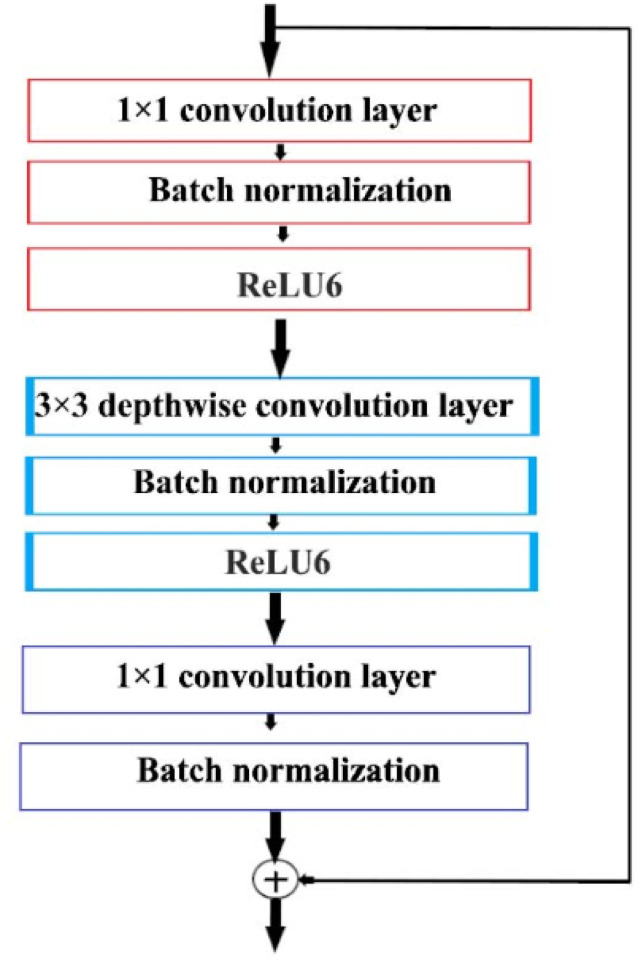
MobileNet v2 [30] is being advertised as an additional development of MobileNet v1, making it even more efficient and powerful. In the MobileNet v2 architecture, the depthwise separable convolution block is redesigned, as shown in Fig. 3. The new, detachable foldable block contains three depthwise separable convolution blocks. The first level is a 1 × 1 convolution layer that is used to expand the number of channels in the input function tab before entering the depthwise convolution layer. The intermediate is a 3 × 3 deep convolutional layer that filters the input features map as in MobileNet V1. The last layer is a 1 × 1 convolution layer. However, the last convolution layer is used to project multichannel data onto a tensor with a much smaller number of channels, thereby reducing the number of channels on the feature map. The last level is also known as the bottleneck layer, as it reduces the amount of data passing through the network.
Besides, the remaining connection in the MobileNet v2 architecture is adopted as in ResNet [31] to support gradients flow through the network. Each layer of the new depthwise separable convolution is followed by batch normalization and ReLU6 as the trigger function (except for the last bottleneck level, since the use of non-linearity was destroyed after this layer useful information was destroyed). The complete architecture of MobileNet v2 is shown in Table 2. As shown in Table 2, MobileNet v2 contains 17 of the new depthwise separable convolution blocks, followed by a custom 1 × 1 convolution layer. The first layer is a standard 3 × 3 convolution layer with 32 channels.
| values | 0 | > 0.00 & 0.50 | > 0.50 & 0.70 | > 0.70 & 1.00 |
| Action type () | Sync | Caution | Warning | Immediate action |
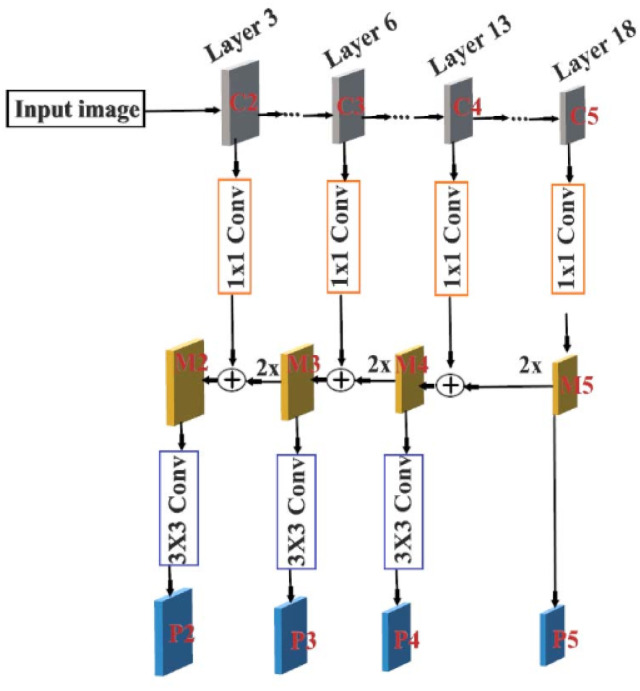
For fast object detection on low-end systems, this paper adopts MobileNet v2 architecture to generate initial feature maps. The feature maps generated after layer 18, layer 13, layer 6, and layer 3 are adopted to generate enhanced feature maps by feature pyramid generation module as explained in the next section.
For quick detection of objects on low-end systems, this article uses MobileNet v2 architecture to generate the feature maps. The feature maps produced at level 18, level 13, level 6, and level 3 are used to produce feature maps expanded by the resource pyramid production module, as explained in the next section.
4.2. Enhanced feature pyramid generation
In this article, the Functional Pyramid Network (FPN) is used to create the enhanced functional pyramid production module that produces improved feature maps in different resolutions. The FPN extends a standard convolution network with top-down pathway and lateral connections so that the network creates a large multi-scale feature pyramid with multiple input image ratings with a single resolution. Each level of the pyramid can be used to identify objects on a different scale. According to [20], this article develops FPN in MobileNetv2 architecture, as shown in Fig. 4. Let C5, C4, C3, C2 provide the feature map of levels 18, 13, 6 and 3. In this article, a 1 × 1 convolution layer is first applied to reduce the C5 channel depth to 256-d and create an M5. This functionality guide becomes the first level of the feature map, which is used to find objects in the detection network. This article follows the top-down path and analyzes the previous level by a factor of 2, using the algorithm to override the nearest neighbours. In the same branch, a 1 × 1 conviction level is applied to all corresponding feature map in the base network. The corresponding feature map is then combined using element-wise addition to unsampled feature map. A 3 × 3 conviction level is applied to all unified feature map to minimize the effect of aliasing when merging with the unsampled layer. This process is repeated until the best feature map is produced. The last set of feature maps is called P5, P4, P3, P2, corresponding to C5, C4, C3, C2, all with the same spatial dimensions. Since the above process uses the same classifier and regression table for each map of the output feature map, each map of the pyramidal features P5, P4, P3 and P2 have 256-d output channels.
Fig. 4.
The architecture of the depthwise separable convolution block used in MobileNet v2 architecture.
As with anchor boxes, the detection network with enhanced functionality crosses all sites at all levels of the feature pyramid, without the need for multiple anchor boxes to resize to a certain level. In this article, anchor boxes are assigned to a single ladder at each level of the enhanced pyramid, as in [9]. More specifically, this article defines anchor boxes with areas of 32 256 pixels at P2, P3, P4, P5 respectively. This article also uses anchor boxes with varying ratios 1:2, 1:1, 2:1 for the ratios at each level of the enhanced functional pyramid. Therefore, there are 15 anchor boxes at each point on the enhanced feature pyramid. In this article, the anchor boxes for training examples receive training labels according to their Intersection-over-Union (IoU) ratios with real site boundaries, as in [4]. In particular, an anchor box receives a positive label if it has the highest IoU for a given ground truth box or an IoU greater than 0.7 with a ground truth box and a negative label if it is an IoU less than 0.5 for each ground truth box.
4.3. Detection network
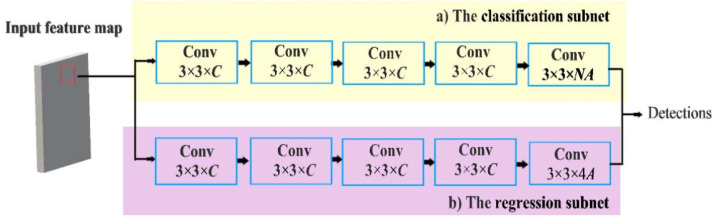
The detection network consists of a classification subnet and a regression subnet, as shown in Fig. 5 The distribution subnet predicts the probability that objects are present at any location and any level of the pyramid. The proposed distribution subnet is a small, fully convolutional network that maps to all feature levels in the expanded feature pyramid. The classification parameter is shared at each level of the pyramid. Fig. 6 (a) shows the architecture of the proposed distribution subnet. For each C-channel input characteristics map, four 3 × 3 C convolution levels are first applied, followed by ReLU activation. A 3 × 3 convolution level is then used with NA filters, where N is the number of object classes and A is the number of anchor boxes. Finally, sigmoidal activation is associated with generating NA binary predictions by spatial location. The regression subnet is used to roll back the displacement of each anchor box onto a real object on the adjacent ground. Fig. 6 (b) shows the architecture of the proposed regression subnet. As noted, the architecture of the cash regression sub-network is similar to that of the proposed distribution subnet. However, the regression subnet produces 4 A linear values per spatial location. For each of the anchor boxes A, based on their spatial position, these four outputs provide the relative offset between the anchor box and ground truth box. Although the Object Classification subnet and the Regression subnet share a common structure, they use separate parameters.
Fig. 5.
The architecture of the enhanced feature pyramid generation module.
Fig. 6.
The architecture of the detection network. (a) The classification subnet. (b) The box regression subnet.
4.4. Loss function
The Cross-Entropy (CE) loss function [4] is the common loss function used for object classification. The CE loss can reduce the imbalance between positive and negative samples. However, the CE loss is not good enough to train classifiers for distinguishing between easy and hard samples. In general object detection, because of complex backgrounds, the problem of balance between easy and hard samples becomes more significant. Focal loss function (FC) was originally introduced by Lin et al. [33] to dedicate the class imbalance problems for the one-stage object detectors. Inspired by the improvements of the FC loss, this paper proposes to use the focal loss function instead of the conventional CE loss. For better understanding, let us have a quick review of the CE loss function. The traditional CE loss for classification is formally defined as follow:
| (2) |
| (3) |
where p represents the predicted probability of given candidate having label represents the ground-truth label.
By adding a modulating factor to the CE loss, where represents the tunable focusing parameter. The loss function becomes the FL loss. Thus, the FL loss function is defined as follow:
| (4) |
With the FL loss function replacing the traditional CE loss function, the contribution of the easy examples is reduced while the ones from hard examples are enhanced during the training process. The output of the face mask detection is illustrated in Fig. 7(a,b).
Fig. 7.
Face mask detection.
5. SPICE-IT: Smart COVID-19 pandemic controlled eradication over NDN-IoT
In this section, the communication architecture of SPICE-IT is introduced.
5.1. NDN-IoT: Communication background
In NDN-IoT, content-centric communication is initiated with two types of packets: the Interest packet, sent by content requester with the name of the requested content. Each node propagating an interest is named as a consumer node and the nodes that relay the packets are named as forwarder nodes. Content provider nodes respond to an interest packet with the content data packet and become a producer node. NDN data structure includes content (CS) caching content, a pending interest table (PIT) that keeps a record of received and forwarded interest and forwarding information base (FIB) storing outgoing interfaces information (in NDN-IoT each sensing node is expected to be equipped to multiple interfaces including 802.11, WiMax, BLE, 5G etc.).
5.2. Proposed SPICE-IT system architecture
As illustrated in Fig. 1, SPICE-IT is sub categorized in multiple sub functional blocks. The communication is initiated by the cameras and thermal sensors mounted inside the closed buildings at various spots. As discussed in Section 2, the process of image processing-based face mask identification also calculates the percentage accuracy of result. While detecting the probability of face with mask on () and the probability of no face mask is also calculated as shown in (5).
| (5) |
is further labelled in to three categories as shown in (6).
| (6) |
Human body temperature is also classified into normal, pyrexia (fever) and hyperpyrexia [32] as shown in (7).
| (7) |
The parameter of observed temperature ratio () is calculated in Eq. (8).
| (8) |
where is the observed temperature, and are minimum and maximum temperatures respectively.
The sensing camera classifies the intensity of notifications as low critical, critical, and urgent notification types by calculating notification intensity factor () as shown in (9).
| (9) |
where is the sensor count parameter which is 2 in current application. Relationship between and notification type () is illustrated in Table 1.
| Values | 0 | > 0.00 & 0.50 | > 0.50 & 0.60 | > 0.60 & 1.00 |
| Type () | Sync | Low Critical | Critical | Urgent |
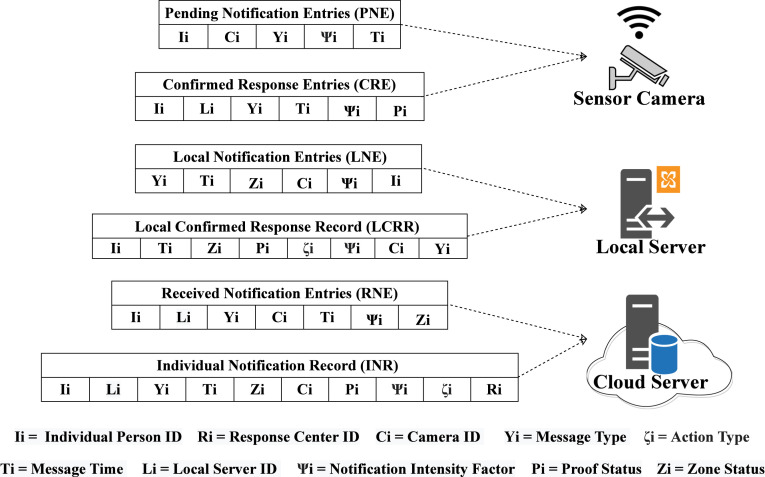
Once an SOP violation is observed, the notification is generated with an interest. We introduce novel NDN data structures in SPICE-IT as illustrated in Fig. 8. At the sensing camera, pending notification entries (PNE) stores the record of notification interest forwarded to the while still waiting for the confirmation of packet delivery. PNE stores information of individual(person) ID () of the person who violated the SOPs, camera ID () of the camera that recorded the event, notification intensity factor () of the event, notification message type () of the event and the time () when the event occurred. While confirmed response entries (CRE) stores the information regarding the events whose interest have been satisfied by the . CRE also stores the information of the local server ID () in addition to the other similar parameters stored in PNE.
Fig. 8.
SPICE-IT data structures.
Local servers () locally maintains the record of the individuals who violated the SOPs. SPICE-IT introduces data structures of local notification entries (RLNE) and individual local notification record (ILNR) to store and manage interest packets received from and content packets received from respectively (Fig. 8). The decision of content caching over is taken based on the LSTM mechanism is discussed in section V-C.
Cloud server plays a vital role in SPICE-IT. repeatedly synchronizes the individual SOP violation records with the . On receiving an interest packet from , decides to generate one of the following packets referring to the actions () taken by :
-
•
Generate Caution: Alert intensity of the packets are low. The broadcasted packets act twofold, act as interest packets to give caution on SOP violation and act as content packets for the action (content) requester.
-
•
Generate Warning: Alert intensity of the packets are medium. The broadcasted packets act as interest packets for the individual as a final warning. Similarly, the packets act as content packets for the action (content) requester.
-
•
Action Recommended: Alert intensity of the packets are high. The broadcasted packets act threefold, as interest packets for the individual informing him about that emergency centre is about to respond on the SOP violation, content packets for the action (content) requester and interests. Similarly, the packets act as content packets for the action (content), and as interest packets for the response team to take recommended actions.
SPICE-IT introduces data structures of received notification entries (RNE) and individual notification record (INR) at . Populated cities are virtually divided into multiple zones. Based on the rate of patient increase within a zone, can declare the zone as a safe, or unsafe zone. Officials then perform a smart lockdown to limit the disease spread by shutting down unsafe zones only. Value of is evaluated based on the values of individual previous SOP violation record factor (), safety factor of zone of notification (), and notification intensity factor () as shown in (10).
| Values | 0 | > 0.00 & 0.50 | > 0.50 & 0.70 | > 0.70 & 1.00 |
| () | No Violation | Few Violations | Repeated Violations | Serious Violations |
| () | Safe Zone | Critical Zone | Unsafe Zone | Emergency Zone |
| (10) |
Where value of is 3. Relationship between and action type () is illustrated in Table 2.
Emergency response centres () are the hospitals and medical centres that take actions recommended by the . Individuals receive the action notification from and can also request for the proof of the event of SOP violation accordingly.
5.3. Long Short-Term Memory (LSTM)
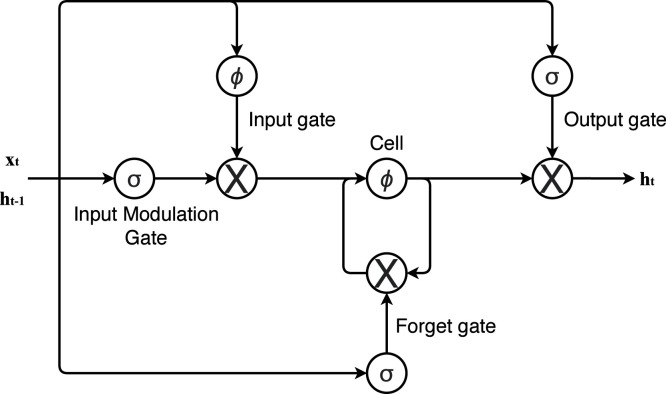
For intelligent caching and content retrieval we introduce long short-term memory network (LSTM) based mechanism that outstands the conventional recurrent neural networks (RNNs) with special units termed as memory. The memory cells temporarily store the state of the network. Special multiplicative units gates control the flow of information. The proposed training model predicts future network traffic at local servers which eventually leads to intelligent content caching withing the NDN-IoT reducing network congestion and cache overflow problems. Fig. 9 illustrates the structure of the LSTM cell.
Fig. 9.
LSTM cell.
The input sequence is the data-set containing NDN-IoT communication network traffic of entries, where represents th observation. The hidden states of memory cell is represented as and output of the cell is represented as . The computations are carried out as shown in Eqs. (11), (12). The memory cell contains information of t time stamp observed at each step. Several gates control the cell that decide either to keep or reset the values according to the state of the gate.
| (11) |
| (12) |
Four special gates control input reading (input gate ), to output new cell value (output gate ), to reset current cell value (forget gate ) and to modulate the input (input modulation gate ). Definitions of cell updates and input–outputs are shown in Eqs. (13)–(18).
| (13) |
| (14) |
| (15) |
| (16) |
| (17) |
| (18) |
Where is the network parameter matrix and denotes the product operations. The hyperbolic tangent and the sigmoid are the non-linearities with hidden states. The objective function is modelled in Eq. (19) as a function of mean squared error (MSE). The MSE is reduced using Adam optimizer based on stochastic gradient descent process.
| (19) |
where, represents the real value and represents the predicted value.
5.4. Example scenarios
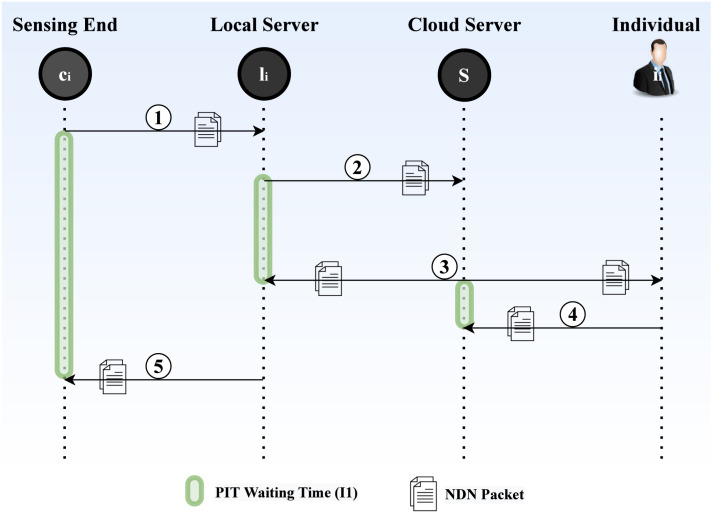
In Fig. 10, Fig. 11, Fig. 12, SPICE-IT example scenarios are illustrated. Considering in Fig. 10, an SOP violation by an individual is observed by the camera () in zone , an independent entry is created at PNE and the notification type of low criticality is broadcasted in the network which is received by the local server () (marked with 1) creaking an entry in LNE. Considering the network traffic intensity is high and low criticality further rebroadcasts the interest (marked as 2) that arrives at the cloud server and creates an entry in RNE. Assuming low , generates a caution message that acts as a content packet for and an interest packet for (marked as 3) with an entry marked at INR. responds to the interest with a content packet that acts as confirmation message which arrives at (marked as 4) and removes the PIT entry. further broadcasts the caution message which arrives at the (marked as5), PIT waiting time stops and the PIT entry is removed from .
Fig. 10.
SPICE-IT Example Scenario 1.
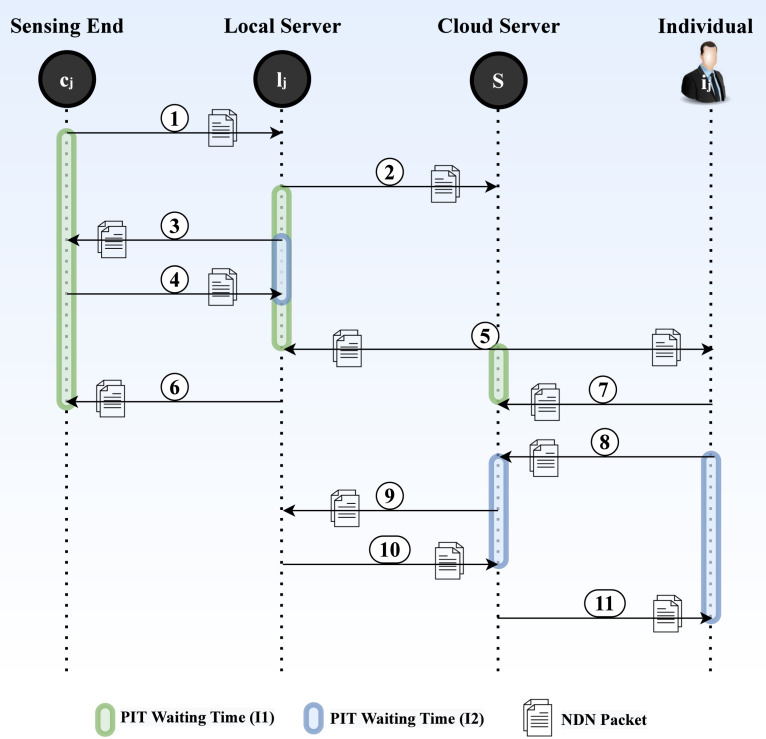
Fig. 11.
SPICE-IT Example Scenario 2.
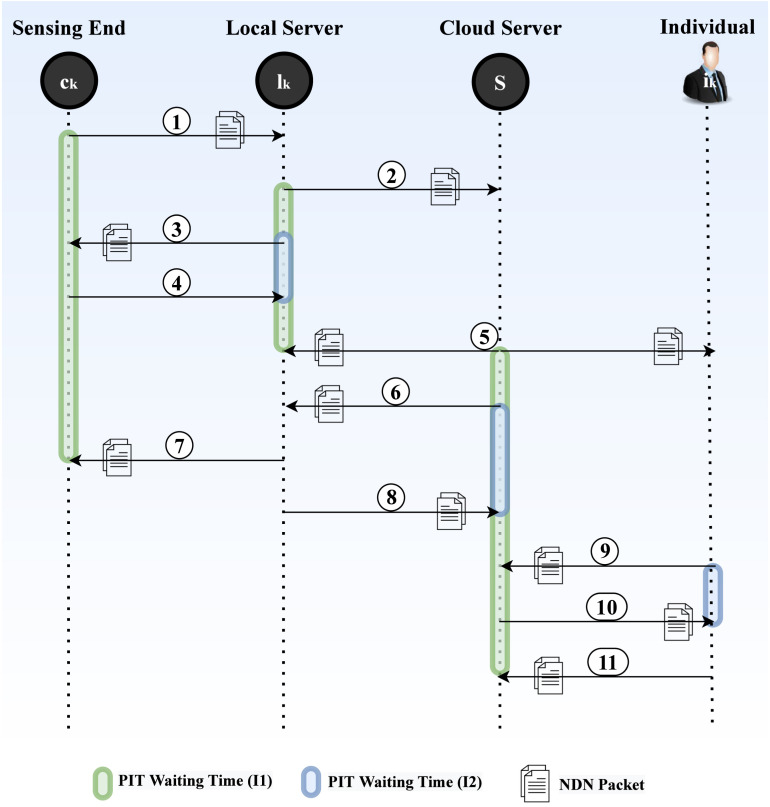
Fig. 12.
SPICE-IT Example Scenario 3.
Fig. 11 illustrates an event in zone was observed by sensing camera which is also a safe zone. Assuming that the network traffic was low and space in the cache of the was available using LSTM-based intelligent mechanism, evidence(video/picture) of the violation was requested from in form of an interest (marked as 3). In response to the interest, the evidence of a violation is provided in the data packet (marked as 4) removing the PIT entry for . Similarly, individual requests for the evidence of the violation in the form of an interest (marked as 8). The interest is rebroadcasted by (marked as 9). In response to the interest, the evidence of a violation is provided in the data packet (marked as 10 and 11) removing the PIT entry for from and respectively.
In Fig. 12, considering an event is recorded by the camera () in zone which is an unsafe zone. Considering the network traffic was low requests for the proof of the event in form of an interest (marked as 3) after forwarding the notification interest (marked as 2). The evidence of violation arrives as a data packet (marked as 4) that removes the PIT entry for . Assuming high , generates an action recommended message that notifies that response team is about to take an action on its violation (marked as 5). Same action packet is received at and acts as content packet for hence removing PIT entries for from and respectively (marled as 5 and 7). Considering the emergency scenario, also requests proof of the violation to be kept in the central database (marked as 6) which is provided by the (marked as 8) which was already cached at in advance. When an individual requests for the evidence of the violation in the form of an interest (marked as 9). The evidence of a violation is provided in the data packet (marked as 10) removing the PIT entry for from .
6. Performance evaluation
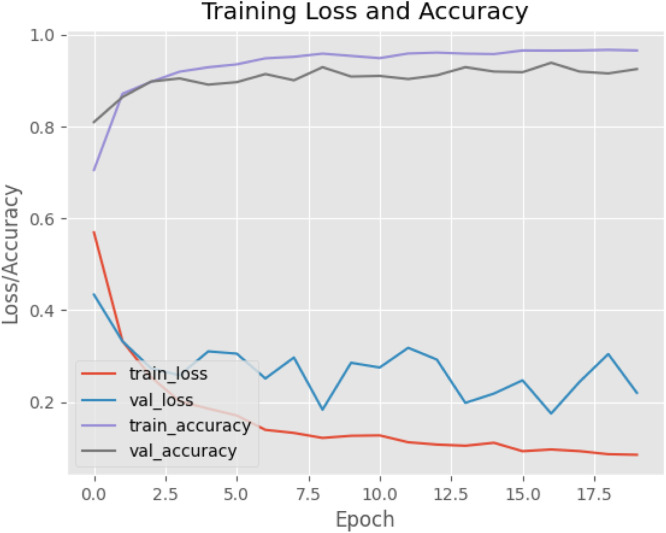
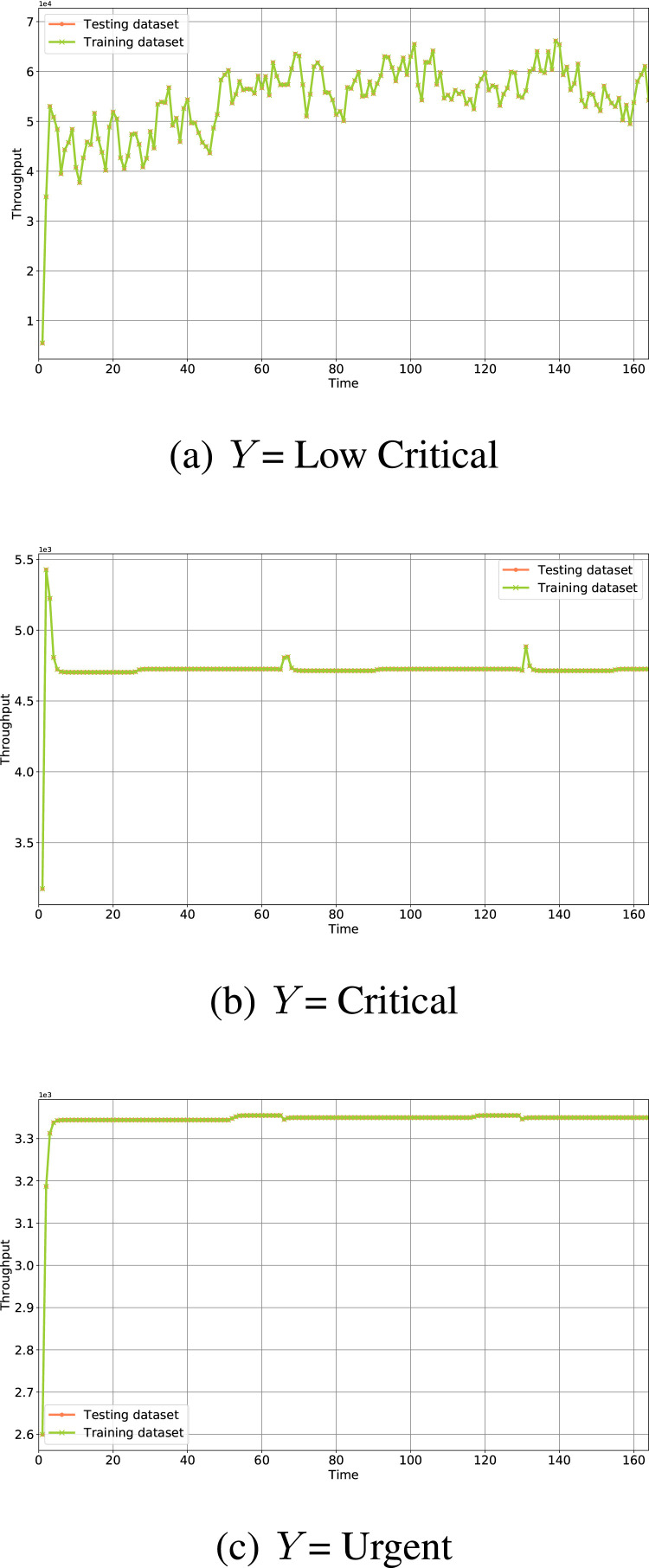
Two evaluate the performance of LSTM Enabled caching/requesting we simulated SPICE-IT over network consists of 20 sensing nodes (cameras), 1 local(edge) server, 22 intermediate routers as transit nodes and a central server. The local server is placed at 1–3 hop counts from thermal sensing cameras, whereas the central server is located at more than 20 hop counts. We consider the 20 thermal cameras which are located in buildings. These cameras detect the face mask and body temperature of the person within the building. These cameras act as the source that generates notifications () of types, as = Low Critical, = Critical and = Urgent, based on values as shown in Table 1. The mobile VNET2 framework is applied for the detection of face mask.3 The machine is learned for 20 epochs. Fig. 13 shows the loss and the accuracy curve for training the model. We simulated the network topology in ndnSIM [33], which is ns-3 based network simulator. The frequency of interest generation of = Low Critical, = Critical and = Urgent was kept high, medium and low respectively in all cases. For the prediction of network traffic, the dataset is collected for the training set and validating/testing set. Then LSTM is applied to the network traffic prediction at the local server. LSTM model consists of 5 stacked layers; the hyperparameters are shown in Table 3. The simulation was run on a Ubuntu server 18.04 installed on intel i7 processor with 8GB RAM. In our simulation, we use Keras and tensor flow at the backend for deep learning and pandas for data analysis. Fig. 14(a), Fig. 14(b) and Fig. 14(c) show the network traffic generated for the three types of notifications. Fig. 15 shows the traffic at respective transit links. After repeatedly fine-tuning the hyperparameters of the LSTM model, our model consists of one input layer, four hidden layers and one output layer with dropout layer as 20%.
Fig. 13.
Loss/accuracy curve.
Table 3.
LSTM hyper parameters.
| Number of layers | 5 |
| Neurons in each layer | 128 |
| Optimizer | ADAM |
| Dropout | 0.2 |
| Activation Layer | Softmax |
| Epoch | 300 |
| Batch size | 32 |
| Training data | 75% |
| Testing data | 25% |
Fig. 14.
Network Traffic Geenerated.
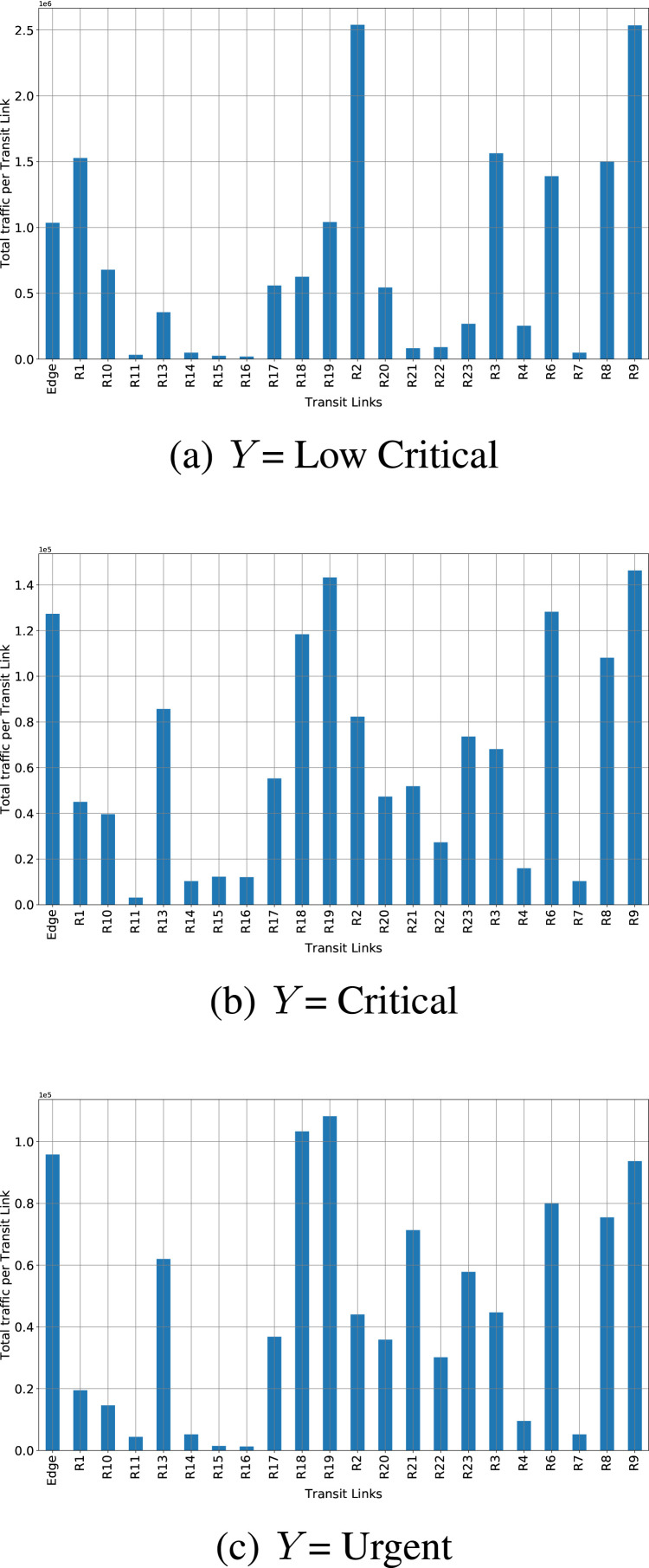
Fig. 15.
Network Traffic at Respective Transit Links.
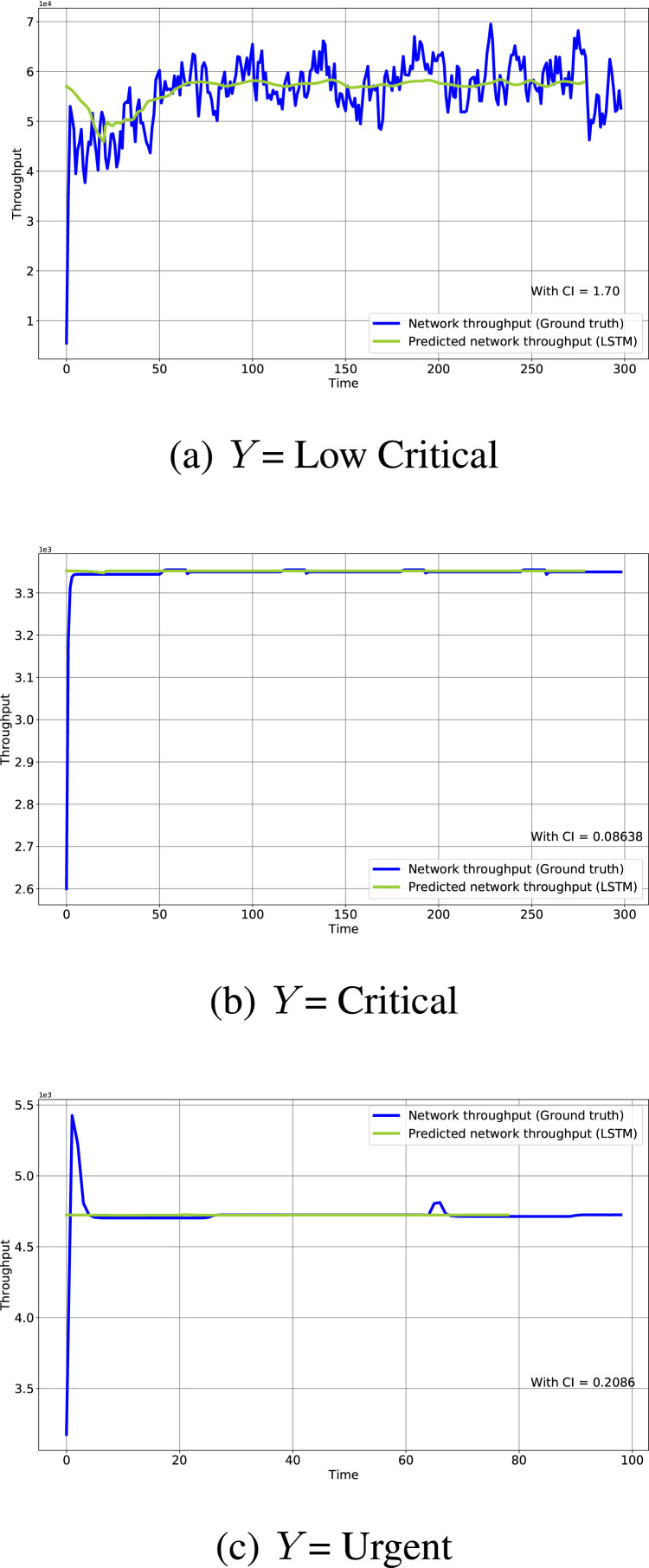
Fig. 16(a), Fig. 16(b) and Fig. 16(c) shows the predicted network traffic of the three types of notifications. Also the Confidential Interval (CI) has been shown. CI shows that predicted output can be varying with +/- CI. From Fig. 16(a), it is shown that transit traffic for interest type = Low Critical is high at links R1, R2, R3, R8. Fig. 16(b) shows for interest type = Critical, network traffic is high at Edge and transit links, R18, R19, R6, R8 and R9. Similarly Fig. 16(c) shows for interest type = Urgent, the network traffic is high at Edge and transit links R18, R19, R6, R8, R9.
Fig. 16.
Predicted Network Traffic.
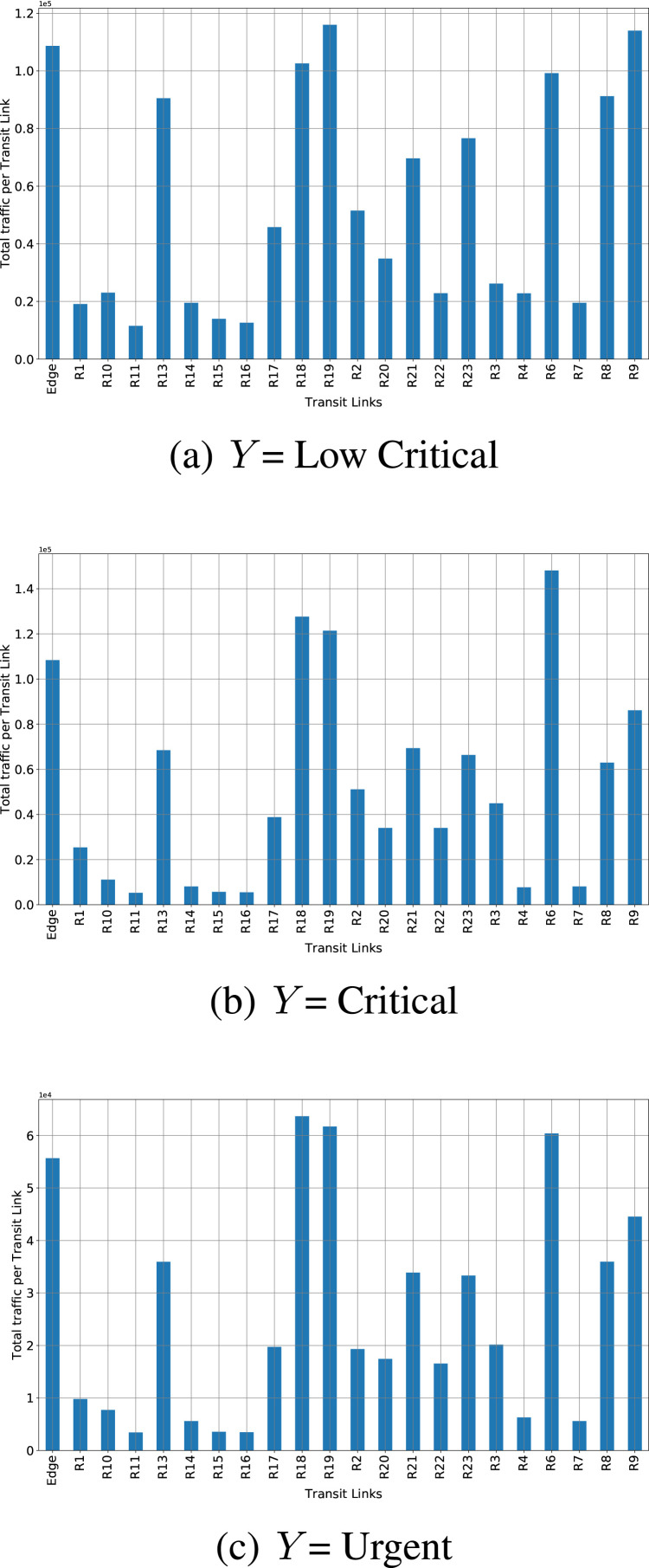
After predicting the network traffic at transit links, identifying the interest priority, the cache is enabled at local servers to reduce the network congestion. Fig. 17 show network traffic is reduced after enabling intelligent caching.
Fig. 17.
Network Traffic after Enabling Caching.
7. Conclusion
Considering the resource constraints of IoT devices and with the challenges inherited by NDN information-centric communication, SPICE-IT introduces an intelligent mechanism to monitor and counter COVID-19 pandemic spread in close indoor environments. The proposed mechanism works on different stages. In the first stage, monitoring is performed at IoT sensors that monitor SOP violations. In second stage NDN based content-centric communication enables the communication between IoT devices, local server, cloud server, individual persons and emergency response centres. An LSTM-based content requesting/caching mechanism is also introduced to request and store violation proof at the local server in advance to the cloud server request that reduces the content retrieval delay while avoiding network congestion problem. In the third stage, the cloud server communicates and takes an adaptive decision based on person previous record and disease spreading status in different geographical zones. In future, we will include testbed based testing of SPICE-IT and will make it more flexible to provide practical NDN-IoT based e-health service to counter the spread of COVID-19.
CRediT authorship contribution statement
Muhammad Toaha Raza Khan: Conception and design, or analysis, Interpretation of the data, Writing - original draft, Writing - review & editing. Malik Muhammad Saad: Conception and design, or analysis, Interpretation of the data, Writing - original draft, Writing - review & editing. Muhammad Ashar Tariq: Conception and design, or analysis, Interpretation of the data, Writing - original draft, Writing - review & editing. Junaid Akram: Conception and design, or analysis, Interpretation of the data, Writing - original draft, Writing - review & editing. Dongkyun Kim: Conception and design, or analysis, Interpretation of the data, Writing - original draft, Writing - review & editing.
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgement
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2016R1D1A3B01015510). All authors approved the version of the manuscript to be published.
Biographies

Muhammad Toaha Raza Khan (S15) is currently seeking the M.S. combined Ph.D degree in computer science and engineering with Kyungpook National University, South Korea, where he is also a member of the Wireless and Mobile Internet Laboratory (MoNet). His research interests include cognitive radio network communication, Flying Ad-hoc Networks (FANETs), and content-centric networks (CCNs). He also served as a Digital Content Editor of Crossroads (XRDS), the ACM magazine for students.

Malik Muhammad Saad received his B.S degree in Electrical Engineering from Institute of Space Technology, Islamabad in 2018. Currently he is pursuing Masters combined PhD degree in Computer Science and Engineering with Kyungpook National University, Daegu, Korea. He is also a member of Wireless and Mobile Internet Laboratory(MoNet). His research interests include, virtual networks, Software Defined Radios (SDRs), vehicular communication and Internet of Vehicles (IoV).

Muhammad Ashar Tariq has completed his BS degree in Electrical Engineering from Institute of Space Technology, Pakistan in 2018. He worked as a Graduate Research Assistant at the Institute of Space Technology for the year 2019. He is currently working as a Researcher at Mobile and Networking Technology Lab in School of Computer Science and Engineering, Kyungpook National University, Korea. His research interests include underwater wireless communication, V2V communication and the internet of underwater things (IoUT).

Junaid Akram Junaid Akram has done BS Computer Science from CUI Pakistan and his master’s degree from NUST which resulted in two publications. Mr. Akram has an evident track record in research including over 10 publications between 2018-2021. Previously, Mr Akram worked as a research assistant at NUST between 2017-2018 and as a research scientist /Team Lead at Blockchain lab, National Centre of Cyber Security NCCS, ITU Lahore. Currently, He is working as a Lecturer at The University of Lahore and is also admitted in PhD Computer Science at The University of Sydney . His research interests are Machine Learning, Data Science, AI for cybersecurity, and blockchain.

Dongkyun Kim received the B.S. degree from Kyungpook National University, Daegu, South Korea; and the M.S. and Ph.D. degrees from Seoul National University, Seoul, South Korea. He was a Visiting Researcher with Georgia Institute of Technology, Atlanta, GA, USA, in 1999. He also performed a post doctorate program with the Department of Computer Engineering, University of California, Santa Cruz, CA, USA, in 2002. From 2015 to 2016, he was a visiting faculty at CSC Research Group, Georgia Institute of Technology, Atlanta, USA. Currently, Prof. Kim is with the School of Computer Science and Engineering, Kyungpook National University. His current research interests include connected cars, vehicular ad hoc networks, the Internet of Things (machine-to-machine/device-to-device), Wi-Fi networks (including Wi-Fi Direct), wireless mesh networks, wireless sensor networks, and future Internet. Prof. Kim has been with the Organizing Committee or the Technical Program Committee for many conferences of the IEEE and the Association for Computing Machinery. He has been doing many editorial duties for several well-reputed international journals.
Footnotes
Edge servers and Local servers are replaceable terms.
Content packet and Data packet are replaceable terms.
This source code is publicly available at GitHub (https://github.com/maliksaad84/NDN-based-Framework-to-mitigate-COVID-19.git) released by us.
References
- 1.West J.S., Atkins S.D., Emberlin J., Fitt B.D. PCR To predict risk of airborne disease. Trends Microbiol. 2008;16(8):380–387. doi: 10.1016/j.tim.2008.05.004. [DOI] [PubMed] [Google Scholar]
- 2.Lackland D.T. Seminars in Nephrology. Vol. 25. Elsevier; 2005. Systemic hypertension: an endemic, epidemic, and a pandemic; pp. 194–197. [DOI] [PubMed] [Google Scholar]
- 3.Lee H.-C., Ke K.-H. Monitoring of large-area IoT sensors using a lora wireless mesh network system: Design and evaluation. IEEE Trans. Instrum. Meas. 2018;67(9):2177–2187. [Google Scholar]
- 4.Mathew P.S., Pillai A.S., Palade V. Cognitive Computing for Big Data Systems over IoT. Springer; 2018. Applications of IoT in healthcare; pp. 263–288. [Google Scholar]
- 5.Çorak B.H., Okay F.Y., Güzel M., Murt Ş., Ozdemir S. 2018 International Symposium on Networks, Computers and Communications (ISNCC) IEEE; 2018. Comparative analysis of IoT communication protocols; pp. 1–6. [Google Scholar]
- 6.Lei K., Zhong S., Zhu F., Xu K., Zhang H. An NDN IoT content distribution model with network coding enhanced forwarding strategy for 5G. IEEE Trans. Ind. Inf. 2017;14(6):2725–2735. [Google Scholar]
- 7.Saxena D., Raychoudhury V. Design and verification of an NDN-based safety-critical application: A case study with smart healthcare. IEEE Trans. Syst. Man Cybern. Syst. 2017;49(5):991–1005. [Google Scholar]
- 8.Verma P., Sood S.K. Cloud-centric IoT based disease diagnosis healthcare framework. J. Parallel Distrib. Comput. 2018;116:27–38. [Google Scholar]
- 9.Hassen H.B., Dghais W., Hamdi B. An E-health system for monitoring elderly health based on internet of things and fog computing. Health Inf. Sci. Syst. 2019;7(1):24. doi: 10.1007/s13755-019-0087-z. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Kulkarni N.J., Bakal J. 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA) IEEE; 2018. E-health: Iot based system and correlation of vital stats in identification of mass disaster event; pp. 1–6. [Google Scholar]
- 11.Rahmani A.M., Gia T.N., Negash B., Anzanpour A., Azimi I., Jiang M., Liljeberg P. Exploiting smart e-health gateways at the edge of healthcare internet-of-things: A fog computing approach. Future Gener. Comput. Syst. 2018;78:641–658. [Google Scholar]
- 12.Wang X., Cai S. Secure healthcare monitoring framework integrating NDN-based IoT with edge cloud. Future Gener. Comput. Syst. 2020 [Google Scholar]
- 13.He D., Kumar N., Zeadally S., Vinel A., Yang L.T. Efficient and privacy-preserving data aggregation scheme for smart grid against internal adversaries. IEEE Trans. Smart Grid. 2017;8(5):2411–2419. [Google Scholar]
- 14.Saxena D., Raychoudhury V., SriMahathi N. MobileHealth@ MobiHoc. 2015. Smarthealth-ndnot: Named data network of things for healthcare services. pp. 45–50. [Google Scholar]
- 15.Hannan A., Arshad S., Azam M.A., Loo J., Ahmed S.H., Majeed M.F., Shah S.C. Disaster management system aided by named data network of things: Architecture, design, and analysis. Sensors. 2018;18(8):2431. doi: 10.3390/s18082431. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Liu N., Gao S., Hou N. 2019 2nd International Conference on Hot Information-Centric Networking (HotICN) IEEE; 2019. Cdac: A collaborative data access control scheme in named data networking; pp. 44–49. [Google Scholar]
- 17.Wei H., Luo H., Obaidat M.S., Wu T.-Y. 2018 IEEE International Conference on Communications (ICC) IEEE; 2018. An active updating strategy for caching periodic data in the internet of things; pp. 1–6. [Google Scholar]
- 18.Khelifi H., Luo S., Nour B., Moungla H., Ahmed S.H. 2018 IEEE Conference on Standards for Communications and Networking (CSCN) IEEE; 2018. Reputation-based blockchain for secure NDN caching in vehicular networks; pp. 1–6. [Google Scholar]
- 19.Chen X., Zhang G., Gao Q., Cui H. Improving NDN forwarding engine performance by rendezvous-based caching and forwarding. Comput. Netw. 2018;145:232–242. [Google Scholar]
- 20.Meddeb M., Dhraief A., Belghith A., Monteil T., Drira K., Mathkour H. Least fresh first cache replacement policy for NDN-based IoT networks. Pervasive Mob. Comput. 2019;52:60–70. [Google Scholar]
- 21.Box G.E., Jenkins G.M., Reinsel G.C. John Wiley & Sons; 2011. Time Series Analysis: Forecasting and Control. [Google Scholar]
- 22.Kalghoum A., Gammar S.M., Saidane L.A. Towards a novel cache replacement strategy for named data networking based on software defined networking. Comput. Electr. Eng. 2018;66:98–113. [Google Scholar]
- 23.Fu Y., Bi J., Chen Z., Gao K., Zhang B., Chen G., Wu J. A hybrid hierarchical control plane for flow-based large-scale software-defined networks. IEEE Trans. Netw. Serv. Manag. 2015;12(2):117–131. doi: 10.1109/TNSM.2015.2434612. [DOI] [Google Scholar]
- 24.Breslau L., Pei Cao J., Li Fan Z., Phillips G., Shenker S. Proc. Eighteenth Annual Joint Conf. of the IEEE Computer and Communications Societies. the Future Is now (Cat. No.99CH36320) Conf. Computer Communications IEEE INFOCOM ’99. Vol. 1. 1999. Web caching and zipf-like distributions: evidence and implications; pp. 126–134. [DOI] [Google Scholar]
- 25.M. Pahl, S. Liebald, L. Wüstrich, Machine-learning based IoT data caching, in: Proc. IFIP/IEEE Symp. Integrated Network and Service Management (IM), 2019, pp. 9–12.
- 26.E.R.P.B. Arvind Narayanan, . Saurabh Verma, Z.-L. Zhang, Deepcache: A deep learning based framework for content caching, in: 2018 Workshop on Network Meets AI & ML, 2018.
- 27.Zhong C., Gursoy M.C., Velipasalar S. Proc. 52nd Annual Conf. Information Sciences and Systems (CISS) 2018. A deep reinforcement learning-based framework for content caching; pp. 1–6. [DOI] [Google Scholar]
- 28.X.Z. Yu Guan, Z. Guo, CACA: Learning-based content-aware cache admission for video content in edge caching, in: 27th ACM International Conference on Multimedia, 2019, pp. 456–464.
- 29.Howard A.G., Zhu M., Chen B., Kalenichenko D., Wang W., Weyand T., Andreetto M., Adam H. 2017. Mobilenets: Efficient convolutional neural networks for mobile vision applications. arXiv preprint arXiv:1704.04861. [Google Scholar]
- 30.M. Sandler, A. Howard, M. Zhu, A. Zhmoginov, L.-C. Chen, Mobilenetv2: Inverted residuals and linear bottlenecks, in: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), 2018.
- 31.Zhang K., Zuo W., Chen Y., Meng D., Zhang L. Beyond a gaussian denoiser: Residual learning of deep cnn for image denoising. IEEE Trans. Image Process. 2017;26(7):3142–3155. doi: 10.1109/TIP.2017.2662206. [DOI] [PubMed] [Google Scholar]
- 32.Walker H.K., Hall W.D., Hurst J.W. Butterworths; 1990. Peripheral Blood Smear–Clinical Methods: The History, Physical, and Laboratory Examinations. [PubMed] [Google Scholar]
- 33.Afanasyev A., Moiseenko I., Zhang L., et al. University of California, Los Angeles; 2012. ndnSIM: NDN simulator for NS-3: Tech. Rep. [Google Scholar]