Abstract
ARX algorithms are a class of symmetric-key algorithms constructed by Addition, Rotation, and XOR. To evaluate the resistance of an ARX cipher against differential and impossible-differential cryptanalysis, the recent automated methods employ constraint satisfaction solvers to search for optimal characteristics or impossible differentials. The main difficulty in formulating this search is finding the differential models of the non-linear operations. While an efficient bit-vector differential model was obtained for the modular addition with two variable inputs, no differential model for the modular addition by a constant has been proposed so far, preventing ARX ciphers including this operation from being evaluated with automated methods. In this paper, we present the first bit-vector differential model for the n-bit modular addition by a constant input. Our model contains basic bit-vector constraints and describes the binary logarithm of the differential probability. We describe an SMT-based automated method that includes our model to search for differential characteristics of ARX ciphers including constant additions. We also introduce a new automated method for obtaining impossible differentials where we do not search over a small pre-defined set of differences, such as low-weight differences, but let the SMT solver search through the space of differences. Moreover, we implement both methods in our open-source tool ArxPy to find characteristics and impossible differentials of ARX ciphers with constant additions in a fully automated way. As some examples, we provide related-key impossible differentials and differential characteristics of TEA, XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2, which achieve better results compared to previous works.
Keywords: Modular addition, ARX, SMT, Automated tool, Differential cryptanalysis, Impossible differential
Introduction
Low-end devices such as RFID tags, sensor networks, and the Internet of Things (IoT) are becoming ubiquitous. In 2018, Gartner, Inc. forecasted that there would be more than 25 billion connected devices forming the IoT by 2021 [24], and following the COVID-19 lockdowns Gartner also revealed that the unprecedented event led IoT implementers to increase IoT investments to reduce costs [25]. Traditional cryptographic algorithms are not suitable for these resource-constrained devices, and several lightweight cryptographic algorithms have been recently proposed to meet this growing demand. In this regard, the National Institute of Standards and Technology (NIST) has started a process to evaluate and standardize lightweight cryptographic algorithms [59].
ARX primitives, composed exclusively of modular Additions, cyclic Rotations, and XORs, are a promising class of lightweight cryptographic algorithms with the most efficient software implementations on low-end microcontrollers [17]. There are many noteworthy ARX algorithms, such as the hash function BLAKE [1], the stream cipher Salsa20 [7], the MAC algorithm Chaskey [58] and notable block ciphers like HIGHT [31], LEA [32], SPECK [6], SPARX [16] or CHAM [41]. Usually, ciphers that are exclusively composed of ARX operations and other common bit-vector operations (e.g., modular multiplication or logical shifts) are also considered in the class of ARX ciphers, such as IDEA [43], TEA [73], or XTEA [60].
The security of ARX ciphers is evaluated by analysing their robustness against various attacks. Some of the most successful attacks applied to ARX algorithms are differential cryptanalysis and their variants, such as boomerang or related-key differential attacks [32, 41]. These attacks exploit differences in the inputs that propagate through the cipher with high probability. Another powerful attack based on non-random propagation of differences is impossible-differential cryptanalysis [8, 37], which exploits input differences propagating to differences in the outputs with zero probability.
The standard approach to show an ARX cipher is secure against differential and impossible-differential attacks is by finding the optimal characteristics (i.e., trails of differences with the highest probabilities) and the longest impossible differentials and checking that no high-probability characteristic and no impossible differential cover most rounds of the cipher [31, 32]. When the best attack in the design stage is a differential or an impossible-differential attack, the number of rounds of the cipher is determined by the longest observed high-probability characteristic or impossible differential. Thus, searching for optimal characteristics and impossible differentials is a crucial step in the design and security analysis of a cipher.
Two main techniques have been applied to search for optimal characteristics of ARX algorithms: branch-and-bound algorithms [11, 13] based on Matsui’s algorithm [54], and the recent automated methods based on Constraint Satisfaction Problems (CSP), such as SMT (Satisfiability Modulo Theories) or MILP (Mixed Integer Linear Programming) problems [21, 57]. CSP-based methods have also been recently applied to find impossible differentials [14, 65, 66]. These automated methods formulate the characteristic or impossible-differential search problem as a CSP and delegate the solving task to one of the powerful off-the-shelf CSP solvers available nowadays [5, 49]. While some CSP-based open-source tools automate the search of ARX characteristics (e.g., CryptoSMT [38]), no CSP-based open-source tool has been published to search for impossible differentials of ARX ciphers.
The main difficulty in formulating a CSP-based search problem lies in the differential models of the non-linear operations, that is, the constraints describing the differential probability of the non-linear operations of the cipher. ARX ciphers can be efficiently described using the bit-vector theory of SMT, and several bit-vector differential models have been proposed so far [39, 47, 48]. For the modular addition with two n-bit operands, the foremost non-linear operation in ARX primitives, Lipmaa and Moriai found a bit-vector algorithm for computing the differential probability with complexity [47]. This algorithm can be straightforwardly translated to a bit-vector differential model, and it has been used in several SMT-based methods to search for characteristics [48, 57, 68] and impossible differentials [65] of ARX ciphers.
However, no CSP-based differential model has been proposed for the modular addition with a constant input, preventing from searching for characteristics or impossible differentials of ARX ciphers that contain constant additions. Lipmaa’s algorithm is restricted to the modular addition with two operands, and it cannot be applied when one of the inputs is fixed to a constant, as we will discuss later. Machado proposed an algorithm to compute the differential probability of the constant addition [53], but it cannot be translated to an efficient bit-vector differential model due to its recursive nature and the use of floating-point arithmetic.
Contributions
We propose an efficient bit-vector differential model for the modular addition by an n-bit constant. Our model contains basic bit-vector constraints and it is composed of a bit-vector formula that determines whether a differential over the constant addition has non-zero probability, and a bit-vector function that computes the binary logarithm of the differential probability. Our bit-vector model exploits the properties of the carry chain of the modular addition and relies on efficient well-known bit-vector functions, such as the Hamming weight or the bit-reversal, and new bit-vector functions that we have developed for the binary logarithm.
Furthermore, we describe an SMT-based automated method to search for characteristics of ARX ciphers, including constant additions. Our method is composed of an iterated search of optimal characteristics of round-reduced versions of the cipher and an automated encoding technique that formulates the SMT problems from the cipher’s Single Static Assignment (SSA) form. Moreover, we describe a new automated method to search for impossible differentials of ARX ciphers which does not depend on any pre-defined sets of input and output differences.
We have implemented our methods in an SMT-based open-source tool ArxPy,1 which fully automated the search of ARX characteristics and impossible differentials. ArxPy is the first open-source tool that can search for the characteristics of ARX ciphers with constant additions, and it is also the first CSP-based open-source tool that automates the search of ARX impossible differentials. ArxPy offers a simple interface to represent any ARX cipher, different types of characteristics and impossible differentials to search, and a complete documentation.
We have applied our characteristic and impossible-differential search methods to several ARX ciphers containing constant additions to provide some examples. In particular, we have searched for different types of related-key characteristics alongside related-key impossible differentials of TEA, XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2. With our automated approach, we have revisited results previously found with manual and ad-hoc techniques. We have obtained better characteristics in terms of probability and number of rounds, and longer impossible differentials.
With our bit-vector model for the constant addition, the SMT-based automated methods, and our open-source tool ArxPy, we provide cipher designers with the resources to design ARX ciphers, including constant additions that are secure against differential and impossible-differential attacks. Thus, cipher designers can choose the best constants for the modular additions and optimize the number of rounds to balance security and efficiency.
Differences to the conference version
This paper is an extended full version of the conference paper [3]. Thus, the content of the conference paper is included in this paper, namely the bit-vector differential model for the constant addition, the SMT-based method and tool to search for ARX differential characteristics and the related-key differential characteristics found for TEA, XTEA, HIGHT, and LEA. Apart from this content, the rest of this paper is new material. This new content includes the SMT-based method to search for impossible differentials of ARX ciphers, the tool to search for ARX impossible differentials, the related-key differential characteristics found for SHACAL-1 and SHACAL-2 and the related-key impossible differentials found for TEA, XTEA, HIGHT, LEA, SHACAL-1 and SHACAL-2. Furthermore, this paper enhances the description of the bit-vector differential model of the constant addition with improved proofs and new examples.
Outline
The notations and preliminaries are introduced in Sect. 2, and the bit-vector model for the modular addition by a constant is described in Sect. 3. Section 4 illustrates the formulation of the search of characteristics and impossible differentials as sequences of SMT problems. Section 5 presents the characteristics and impossible differentials found for TEA, XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2 using our automated approaches. Finally, Sect. 6 concludes the paper and addresses future works.
Preliminaries
Notations
Let x be an integer such that its n-bit vector representation when is , where x[0] and denote respectively the least and the most significant bit. For ease of notation, we define when and the symbol stands for an undetermined bit. The usual integer operations are denoted by and the basic bit-vector operations are gathered in Table 1.
Table 1.
Basic bit-vector operations for n-bit vectors
| x[i, j] | The bit-vector , |
| Bit-wise NOT of x | |
| Concatenation of x and y | |
| Bit-wise AND of x and y | |
| Bit-wise OR of x and y | |
| Bit-wise XOR of x and y | |
| (Logical) left shift of x by i bits | |
| Right shift of x by i bits | |
| Left cyclic rotation of x by i bits | |
| Right cyclic rotation of x by i bits | |
| Modular addition of x and y | |
| Modular subtraction of x and y | |
| Bit-vector equality of x and y, returning True | |
| If x and y are the same, otherwise False |
A mathematical expression only involving bit-vector variables and basic bit-vector operations is called a bit-vector expression. A bit-vector formula is a bit-vector expression returning or , such as , whereas an n-bit vector function is a bit-vector expression returning an n-bit vector. In order to measure the complexity of the bit-vector differential model that we propose in this paper, we define the bit-vector complexity of a bit-vector expression as the number of basic bit-vector operations that the expression is composed of.
In the literature of the bit-vector theory, the set of basic bit-vector operations usually includes the operations gathered in Table 1 and few additional operations, such as modular multiplication or modular division [42]. However, modular multiplication and modular division are much more costly than the other operations in practice, and we have excluded them from our set of basic bit-vector operations, which resembles the unit-cost RAM model used in [47].
Apart from the basic bit-vector operations listed in Table 1, we will also employ the following well-known bit-vector functions: and . The carry function returns the n-bit carry chain of the n-bit modular addition . It is defined iteratively as and for . Note that the carry has bit-vector complexity O(1), since . The carry function is an efficient function that allows propagating information from the least significant bits to the most significant bits, a property that we will exploit for our bit-vector differential model.
The bit-reversal function reverses the order of bits of x, i.e., . This function can be computed using a divide and conquer method with bit-vector complexity [29, Fig. 7-1]. We will use this function to define the reverse carry, , which allows to propagate information from right to left and also has bit-vector complexity .
The Hamming weight returns an n-bit vector denoting the number of non-zero bits of the n-bit input x. Similar to the bit-reversal, the Hamming weight can be computed using a divide and conquer approach with bit-vector complexity [29, Fig. 5-2]. The Hamming weight will be one of the main building blocks to obtain an efficient bit-vector representation of the binary logarithm.
The last bit-vector function we will consider is the leading zeros function . This function marks the leading zeros of an n-bit input x, that is, for , . This function is used as a subroutine for the well-known function to compute the number of leading zeros. Similar to the previous bit-vector functions, can be computed with bit-vector complexity [29, Fig. 5-16].
Differential and impossible-differential cryptanalysis
A block cipher is a family of permutations parametrized by a -bit key k, mapping n-bit plaintexts p to n-bit ciphertexts c. Most block ciphers consist of a key scheduling algorithm , which derives round keys from the master key k, and an encryption algorithm , which processes the plaintext by iterating a round function f and injecting a round key at each round, i.e., .
Block ciphers are shown to be secure by analysing their resistance against all known attacks. One of the most potent attacks, especially to ARX primitives, is differential cryptanalysis [10]. It exploits the non-random propagation of differences in the input to recover the secret key.
Let F be an n-bit to n-bit function and be the XOR of a pair of inputs and their corresponding outputs , i.e., and . The pair is called a differential and its probability is defined as
A differential is valid if it has non-zero probability. In this case, its weight is defined as
The differential has probability 1 for any function F, and a differential with non-zero input difference over a random n-bit permutation has probability . Differential cryptanalysis [10] exploits a differential over the n-bit block cipher with probability to recover the secret key with roughly encryption calls.
Related-key differential cryptanalysis [34] extends differential cryptanalysis by considering key differences. A related-key differential is given by a pair of differentials over the key schedule and the encryption function respectively,
where the ciphertext difference is computed using the related round-key pairs,
The probability of a related-key differential is the product of the probability of key schedule differential and the probability of encryption differential .
A related-key attack exploits a related-key differential with and to recover the secret key with complexity . The attacker takes about key pairs to find one key, on average, that satisfies the key schedule differential. Next and for each key pair, the attacker runs a differential attack over the encryption using encryption calls.
Related-key differential cryptanalysis requires a very powerful attacker that can query the encryption function for many keys . In fact, if an adversary can query for key differences , any block cipher is vulnerable to a related-key attack with complexity [74]. Thus, we distinguish between weak related-key differentials (i.e., ) and strong related-key differentials (i.e., ), which can be exploited in practice with a single related-key pair. Furthermore, we define equivalent keys as pairs of related keys such that , for some . Note that a related-key differential with leads to pairs of equivalent keys.
Lastly, we consider (related-key) impossible differentials. A differential over a function F is called impossible if its probability is zero, and a related-key differential over a block cipher is called impossible if its probability is zero for all keys. Impossible-differential cryptanalysis [8] is an attack on block ciphers that exploits an impossible differential over the block cipher holding for every key. Related-key impossible-differential cryptanalysis is a combination of impossible-differential cryptanalysis and related-key cryptanalysis. Using the known difference of the key pairs and the input and the output of the impossible differential, the attacker discards the wrong keys to obtain the correct key.
Searching for characteristics and impossible differentials.
The most challenging step to launch a differential attack is finding a differential with high probability. The main approach is to analyse how differences traverse through the round function and search for a characteristic, that is, a trail of differences
Similar to differentials, a characteristic is valid if it has non-zero probability and its weight is defined as . Furthermore, we denote a related-key characteristic by a pair of characteristics , where is the key schedule characteristic containing the trail of differences from the master key to the round keys and is the encryption characteristic containing the trail of differences through the encryption.
Obtaining the exact probability of a characteristic is computationally infeasible. Thus, two assumptions are commonly made. First, it is assumed that the differential probabilities over each round are independent, which allows computing the weight of a characteristic by summing the round weights, i.e.,
Second, it is assumed that the probability of a characteristic does not strongly depend on the choice of the secret key, also known as the hypothesis of stochastic equivalence [44], which allows computing the weight of a characteristic by averaging over all keys.
On top of that, designers also assume that the probability of a differential is close to the probability of the best characteristic , and they prove a cipher is secure against differential cryptanalysis by showing that characteristics with high probability cannot cover most rounds of the cipher. While these assumptions do not always hold, currently this is the best systematic approach to argue security against differential cryptanalysis, and this heuristic approach is widely used for ARX ciphers in practice [21, 39, 57, 68–70].
Searching for characteristics is usually dependent on some assumptions, as mentioned earlier. In contrast, the process of obtaining an impossible differential typically results in a sound proof, guaranteeing that the probability of the achieved differential is equal to zero. Therefore, most of the impossible-differential search methods are sound but not complete. In other words, any differential found by these methods is assuredly impossible, yet there may be many impossible differentials that the search methods cannot detect.
SMT solvers
A recent approach to search for characteristics and impossible differentials of ARX ciphers is by formulating the search problem as an SMT problem in the bit-vector theory [2, 39, 48, 57, 65, 68]. Satisfiability Modulo Theories (SMT) refers to the problem of determining whether a first order formula is satisfiable with respect to some logical theory. SMT problems are a generalization of SAT problems; while the latter problems are expressed in propositional logic, SMT formulas can be expressed in richer logics, such as the theory of bit-vectors or the theory of integers.
SMT has grown in recent years into a very active research field, and several off-the-shelf SMT solvers are available nowadays [5]. Most SMT solvers can determine the satisfiability of a problem and obtain an assignment of the variables that satisfies the problem. This feature allows SMT solvers to be applied in search problems.
An SMT problem in the bit-vector theory is given by a set of bit-vector variables and a set of bit-vector formulas or constraints. The constraints can be defined with the usual logical operations (e.g., , etc.) and the usual bit-vector operations (e.g., , etc.).
For example, a bit-vector SMT problem to find an 8-bit preimage of , given the 8-bit image , is the following:
This problem is satisfiable and the only assignment that satisfies the problem is .
Differential models
To represent a characteristic in a constraint satisfaction problem, it is necessary to find a differential model of the round function f. For an SMT problem in the bit-vector theory, a differential model of a function is given by a bit-vector formula and a bit-vector function . The formula is True if and only if the differential over f is valid, and the function returns the weight of a valid differential .
Characteristics over ARX ciphers are usually defined by considering the difference after each ARX operation. The differential models of the XOR and the cyclic rotations are very simple since these operations propagate differences deterministically, that is,
For the modular addition with two n-bit inputs, , the algorithm by Lipmaa and Moriai [47] can be translated into the following differential model with bit-vector complexity .
Theorem 1
Let be a differential over the modular addition and denote and . Then, the differential is valid if and only if the bit-vector formula
is True. In this case, the differential weight is given by the bit-vector function
For the modular addition with a constant input , Machado [53] obtained the following algorithm to compute the differential probability [53].
Theorem 2
Let (u, v) be a differential over the n-bit constant addition . Then, the differential probability is given by
where depends on the and , each one defined for by
For , and are defined by and .
Unfortunately, the algorithm illustrated in Theorem 2 is not suitable for constraint satisfaction problems due to its recursive nature and the use of floating-point arithmetic.
Some authors [46, Corollary 2] [4] have adapted the differential model of the 2-input addition (i.e., the modular addition with two independent inputs) for the constant addition by setting the difference of the second operand to zero, that is,
| 1 |
The approximation given by Eq. (1) models the differential by averaging over all a. While this approach can be used to model the constant addition by a round key, since the characteristic probability is also computed by averaging over all keys, for a fixed constant this approach is rather inaccurate.
Surprisingly, the differential properties of the 2-input addition and the constant addition are very different. The 2-input addition was shown to be CCZ-equivalent to a quadratic function [67], that is, the differential properties of the 2-input addition are the same as some quadratic functions. In particular, the set of inputs satisfying a differential over the 2-input addition forms a subspace of , which allows to describe its differential model using few basic operations.
On the other hand, the constant addition is not CCZ-equivalent to a quadratic function, since the set of inputs satisfying a differential over does not form a subspace for many a. In other words, the probability of a differential over the constant addition is not necessarily of the form for a positive integer , and finding a differential model for the constant input addition is a much harder problem.
We experimentally checked the accuracy of the approximation given by Eq. (1) for 8-bit constants a. For most values of a, validity formulas differ roughly in out of all differentials. For those differentials where they did not differ, the difference between their weights was significantly high on average.
Consequently, no differential model of the constant addition suitable for constraint satisfaction problems has been proposed so far. In the next section, we present the first differential model of the constant addition for SMT problems in the bit-vector theory.
Bit-vector differential model of the constant addition
We present a bit-vector differential model of the constant addition, composed of a bit-vector formula to determine whether a given differential is valid and a bit-vector function that computes the weight of the valid differential. Our model takes benefit from Theorem 2 [53]; however, we avoid bit iterations, floating-point arithmetic, multiplications and look-up tables, in order to obtain efficient bit-vector constraints to be used in bit-vector SMT problems.
Before we illustrate our model, we remark an essential property of Theorem 2. When the state is not or , the probability of the step i, , depends exclusively on ; otherwise, depends on and . When , and for the first three cases, is equal to . However, considering the forth case, i.e., , depends on and this dependency will proceed until we obtain a state for some positive integer . Thus, has the following expression when ,
| 2 |
Therefore, when , also depends on the previous states , which motivates the following definition.
Definition 1
Let . The chain is defined as the smallest set of previous states that completely determine , and the positive integer is called the length of .
Given a chain , note that and the remaining states in the chain (if any) are all equal to .
In the next example, we illustrate how to calculate the differential probability using the iterative method of Theorem 2 and we learn more about the intermediate variables used for obtaining the probability.
Example 1
Consider the differential over the modular addition by the 10-bit constant . According to Theorem 2, the differential probability of (u, v) is given by
Table 2 displays the variables we need to compute to obtain the differential probability. As we mentioned earlier, if , each can be computed in a straightforward way without any further dependencies of previous states.
Table 2.
The intermediate variables for finding the differential probability of Example 1
| i | 9 | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| a[i] | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 1 | 1 | 0 | 0 |
| u[i] | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 1 | 1 | 0 | 0 |
| v[i] | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 0 | 0 |
| 0 | 0 | 1 | 1 | 0 | 0 | 0 | |||||
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
For the remaining states equal to or , we first obtain their associated chains as
Then, we compute the associated using Eq. (2), and finally we obtain from the values of and the computed .
Multiplying each listed in Table 2 leads to the differential probability,
Validity
Let (u, v) be a differential over , the modular addition by n-bit constant a. According to Theorem 2, the differential probability of (u, v) can be expressed as . Thus, (u, v) is a valid differential, i.e., with non-zero probability, if and only if all are non-zero. If , note that must be or . While always implies , the other two cases require an extra condition to result in , as shown in the next lemma.
Lemma 1
Let the state be , for . Then, is equal to 0 if and only if
Proof
Having , if and only if . Let be the chain length of . The case for is trivial, since . To achieve when , the non-negative rational number must be equal to 0 or 1. Since is a monotonically increasing function of regarding Eq. (2), reaches its extrema in and , that is,
Thus, .
The next lemma provides a bit-vector expression to check Lemma 1 by exploiting the fact that the carry chain allows a bit to affect the bits to its left.
Lemma 2
Consider the following n-bit values,
Then, for all states , we have if and only if .
Proof
Let with chain length . Note that and that (resp. ) if and only if (resp. ).
The first operand of g[i], i.e., , is equal to one if and only if . For it is easy to see that ; therefore, the second operand of g[i] is 1, and by Lemma 1 if and only if .
When , and the second major operand of g[i] reduces to c. In particular, the two major operands of the function of c are given by
Thus, and ; otherwise, for we will obtain which does not conform to . By unrolling the recursive definition of c[i], we see that . In other words, if and only if . Together with the condition for , we have that exactly when , regarding Lemma 1.
Lemma 2 provides a bit-vector variable g that detects the states leading to invalidity. The next theorem presents the final bit-vector formula for the validity by taking into account the states as well.
Theorem 3
Let (u, v) be a differential over the n-bit constant addition . Consider the n-bit value g defined in Lemma 2 and the following n-bit values
Then, the bit-vector formula is True if and only if the differential (u, v) is valid.
Proof
By the definition of and , (respectively ) if and only if (respectively ). Moreover, exactly when , or when and (Lemma 2). Thus, if and only if .
Since the number of basic bit-vector operations of our bit-vector validity formula is independent of the bit-size of the inputs, the bit-vector complexity of is O(1).
Example 2
Consider the valid differential of Example 1, i.e. , , and . Previously, we showed that its differential probability is non-zero and equal to 5/16. In this example, we will illustrate our bit-vector validity formula step by step.
Table 3 provides some of the essential bit-vector values used in Theorem 3. Since there is no state equal to , is the all-zero bit-vector. As we have shown in Example 1, there are three states equal to , and the associated bit of is equal to one in the corresponding bits. In this example, no state leads to invalidity, and g is equal to the all-zero bit-vector. Thus, for all i, and our validity formula
evaluates to True.
Table 3.
The intermediate variables for evaluating the bit-vector validity formula of Example 2
| i | 9 | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
|---|---|---|---|---|---|---|---|---|---|---|
| a[i] | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 1 | 1 | 0 |
| u[i] | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 1 | 1 | 0 |
| v[i] | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 0 |
| g[i] | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 0 | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Weight of a valid differential
In this section, we propose a bit-vector function that computes the weight of a valid differential over the constant addition. Working with differential weights has the advantage that multiple differential weights can be combined by adding them up, while probabilities need to be multiplied, a very costly operation in a bit-vector SMT problem.
The weight of a valid differential over the constant addition is an irrational value in general, and it cannot be represented as a fixed-sized bit-vector. Thus, our bit-vector function computes a close approximation of the weight, and we provide almost tight bounds for the approximation error.
Through the rest of the section, let (u, v) be a valid differential over the n-bit constant addition . According to Theorem 2, the weight can be obtained by
| 3 |
Let denote the set of indices corresponding to the states with chain length bigger than one, i.e., . For , the probability only depends on the current state and is either 1 or 1/2. Based on the aforementioned fact, we show how to acquire the summation of all when using bit-vector expressions.
Lemma 3
Let . Then,
Proof
To prove the lemma, we divide the set into two parts as and . For each state , there are two possible cases. If is equal to , the corresponding step probability is . Otherwise, and we obtain . Considering these two cases leads to
Since the second case occurs when , we can use to compute the number of times this case happens.
Now for when , we know that . Since the probability is not equal to zero, we obtain . Thus we get
By and large, the sum of when is
Lemma 3 describes the sum of when as a bit-vector expression with complexity . To describe the logarithmic summation when as a bit-vector, we will first show how to split as the quotient of two integers.
Lemma 4
Let and let be the positive integer defined by
where is the chain length of the state . Then, .
Proof
Considering the definition of when ,
and following the definition of given by Eq. (2),
we obtain that . Moreover, having and results in . Thus, is always a positive integer.
Due to Lemma 4, we can decompose the logarithmic summation over as
The next lemma shows how to describe the summation involving the chain lengths with basic bit-vector operations.
Lemma 5
Consider the n-bit vector . Then,
Proof
Recall that there are exactly states in each chain such that
Therefore, we have When , the next state will be a member of the set . As a result, it is easy to see that for an arbitrary j, if is equal to , then either is included in some chain , or belongs to the set defined by
for some , where . Concerning Definition 1, one can observe that is not a chain. Therefore, .
Since we are assuming that the differential is valid, there are no states , and if and only if . On the other hand, the function can be used to detect the states from the set . In particular, is equal to if and only if . Therefore, we obtain
Representing the sum of by a bit-vector expression is the most complex and challenging part of our differential model. Thus, we will proceed in several steps. First, we will show how to obtain a bit-vector w that contains all the as some sub-vectors.
Lemma 6
Consider the following n-bit values,
Then, for all states with , .
Proof
For each and , note that exactly when and , and (resp. ) if and only if (resp. ). Denoting , where and , when the sub-vectors
result in . In particular, and the equality holds when .
It is easy to see that when and q is zero elsewhere. Then, the sub-vectors are composed of repeated copies of when , as shown by the following sub-vectors
The only exception for the above equations is when , where the two least significant bits of the above sub-vectors will be equal to zero.
Let , where and . Regarding the acquired patterns for q and d, we prove the following inequalities for
which imply the identity .
The first inequality can be derived from the fact that . For the second inequality, consider the index set . Then, the second inequality holds since for and we can see that
We are now ready to evaluate when . If , then , reduces to 0, and
If , then , reduces to 0, and
Hence, for and regarding Lemma 4, we obtain that .
Recall that both and have bit-vector complexity . Therefore, w can be described with basic bit-vector operations.
Since is not always a power of two, cannot be represented by a fixed-sized bit-vector. Thus, we will use the following approximation for the binary logarithm of a positive integer x,
| 4 |
where and for an m-bit vector z is defined by
In other words, includes the integer part of the logarithm and takes the four bits right after the most significant one as the “fraction” bits. While can be generalized to consider more fraction bits, we will show later that four fraction bits are enough to minimize the bounds of our approximation error.
To describe with basic bit-vector operations, we will introduce in the next proposition two new bit-vector functions and . Given a bit-vector x with sub-vectors delimited by a bit-vector y, computes the sum of the integer part of the logarithm of the delimited sub-vectors, whereas calculates the sum of the four most significant bits of the delimited sub-vectors.
Proposition 1
Let x and y be n-bit vectors such that y has r sub-vectors
where , and y is equal to zero elsewhere.
We define the bit-vector functions and by
where .
- If for , then
- If at least bits are dedicated to , then
Proof
Case (a) Let and . Note that , since . For , we obtain the sub-vectors
In particular, has m bits set to one. If , and , which implies that there is no carry chain, i.e., . Therefore, in both cases .
Note that the reversed carry chain stops at , and . Therefore, the same argument can be applied for , obtaining
Finally, it is easy to see that , concluding the proof for this case.
Case (b) First note that for and , the variable is
Therefore, the Hamming weight of computes the following summation:
While we define as a bit-vector function returning an n-bit output given an n-bit input, bits are sufficient to represent the output of . Therefore, by representing each in a -bit variable , the bit-vector expression does not overflow, and we obtain
which concludes the proof.
Since both and have bit-vector complexities, so do the functions and . The next lemma applies and to provide a bit-vector expression of the sum of .
Lemma 7
Let r and f be the bit-vectors given by
If at least bits are dedicated to r and f, then
Proof
Regarding Lemma 6, represents the -bit vector of and conforms to the pattern for any . Therefore,
following Proposition 1. For the second case, let c be the n-bit vector given by . Denoting by and for a given , note that is the most significant active bit of and
Thus conforms to the pattern and Proposition 1 leads to
For any n-bit variables x and y, it is easy to see that . Thus, bits are sufficient to represent , and f can also be represented with the same number of bits following Proposition 1. Therefore, by representing and f in -bit variables, the bit-vector expression does not overflow.
Recall that the differential weight of constant addition can be decomposed as
If the binary logarithm of is replaced by our approximation of the binary logarithm , we obtain the following approximation of the weight,
| 5 |
Our weight approximation can be computed with the bit-vector function described in Algorithm 1, as shown in the lemma.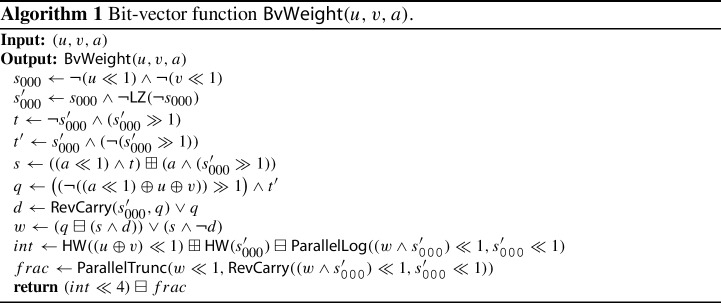
Lemma 8
If at least bits are dedicated to , then
Proof
Regarding Lemmas 3 and 5 and 7 we respectively obtain
All in all, we get the following identities,
Note that the four least significant bits of correspond to the fraction bits of the approximate weight. In other words, the output of represents the rational value
The bit-vector complexity of is dominated by the complexity of , , , , and . Since these operations can be computed with basic bit-vector operations, so does .
Theorem 4 shows that leads to a close approximation of the differential weight and provides explicit bounds for the approximation error.
Theorem 4
Let (u, v) be a valid differential over the n-bit constant addition , let be the differential weight of (u, v), and let be the bit-vector function defined by Algorithm 1. Then, the approximation error,
is bounded by
Section 3.3 is devoted to the proof of Theorem 4, where we will also analyse the error caused by our approximated binary logarithm. Before proving Theorem 4, we will describe an example to understand this theorem and Algorithm 1.
Example 3
Consider the same conditions as defined in Example 1, i.e., and the constant input . The weight for our differential is
Let’s find the approximate weight based on Algorithm 1. Table 4 presents some of the variables we obtain to compute the aforementioned approximate weight.
Table 4.
Intermediate variables for computing of Example 3
| i | 9 | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
|---|---|---|---|---|---|---|---|---|---|---|
| a[i] | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 1 | 1 | 0 |
| u[i] | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 1 | 1 | 0 |
| v[i] | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 0 | 1 | 0 |
| 1 | 0 | 1 | 1 | 1 | 0 | 0 | 0 | 1 | 1 | |
| 0 | 0 | 1 | 1 | 1 | 0 | 0 | 0 | 1 | 1 | |
| w[i] | 0 | 0 | 0 | 1 | 0 | 1 | 0 | 0 | 1 | 0 |
| 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 0 | 0 |
The set in this example is equal to . The variable int in Algorithm 1 consists of three parts. The first part of the variable int calculated in Algorithm 1 is
which is equal to .
The second part uses the variable which is the same as except that the leading one bits of are replaced in by zeros. In other words, but the remaining bits of these two bit-vectors are exactly equal. Computing the second part results in
and it is equal to .
For the third and last part of int, we compute w, obtaining . We remark that the bit-vector w for in fact includes as some subvectors, i.e.
Hence, the third part of int is computed as
which is equal to . Considering all three parts, the bit-vector int is obtained by
Moreover, the frac bit-vector in Algorithm 1 is calculated by
Considering the third major operand of int and the bit-vector frac, we can obtain the summation of all approximate logarithms
To summarize, the output of Algorithm 1 is
Therefore, the approximate weight will be equal to
The total error of our approximation is
which is a negative value and lower bounded by as suggested by Theorem 4.
Error analysis: proof of Theorem 4
In this subsection, we will prove Theorem 4 by gradually analysing the error produced by our approximation of the binary logarithm. As we can see from Eqs. (3) and (5), the gap between and is
Note that the integer part of is equal to the integer part of and the error is caused by the fraction part of the logarithm.
Given a positive integer x and the corresponding , we define as
The non-negative integer is called the precision of the fraction part. Note that is the generalization of , which considers bits for the fraction part. While Theorem 4 only focuses on , we will use in this section to additionally prove that our error bound also applies to .
The following lemma bounds the approximation error of when , with a similar proof as [56] for the sake of completeness. The main idea is that after extracting integer part of the logarithm in base 2, one can estimate by when .
Lemma 9
Consider a positive integer x and the binary logarithm approximation where . Then, the approximation error is bounded by , where B is given by
Proof
Let , where b is a non-negative integer such that . Therefore, and the error is given by
For , we obtain and . Note that e is a concave function of where if and only if . By deriving , one can see that is reached when .
The bound B is an almost tight bound, e.g., when , the obtained error is . The following example sheds more light on our binary logarithm approximation.
Example 4
Consider the positive integer . Note that and . In order to obtain the approximation defined in Proposition 9, we first find and omit the greatest "one" in binary representation of x, and we get . By interpreting the remaining bits as a binary fraction, we have . Therefore, the approximated binary logarithm of in binary representation is
which is equal to 4.8125. In addition, the corresponding error of such approximation is , which is a positive value and upper bounded by .
Finally, we can now prove Theorem 4, which basically states that if we dedicate 4 bits to the fraction precision , the approximation error E is bounded by . While Theorem 4 focuses on , we will show in the proof that we can also bound the error for . To this end, we generalize the approximated weight and the approximated weight error as follows
where is defined by Eq. (5) and is defined in Theorem 4.
Fig. 1.
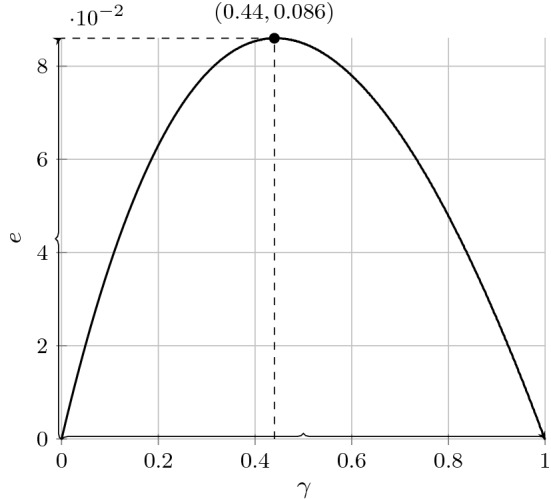
The error , over
Proof (Theorem 4)
First, we mention that is an integer number when or for we see . For these cases, and the approximation error is equal to zero.
Next, for each when , let such that and are two non-negative integers, and . If , we obtain and . Thus, the resulting error
is exactly the same as the error defined in Proposition 9, and .
On the other hand, for , i.e., , let , where and are two non-negative integers such that as well as . In this case, the approximated binary logarithm is . We now define a new error as
Due to the fact that , we can see that
Since and by reforming the error, we obtain the upper bound of
where and . Regarding Proposition 9, the new error is bounded by .
Note that for a valid differential (u, v) over the constant addition we can see that which for some belongs to the chain
Hence, we obtain
Similar to the proof of Lemma 4 we have
where is an integer. Therefore, by replacing with , the previous statements considering the error bounds of our approximation for the state and its new are still correct. We now define two bits and as
Finally, by defining the conditional index set we obtain
For , we can see that , resulting in
Since for , we have , the above inequalities hold for the approximation error E as well.
While dedicating bits as the fraction precision is enough to obtain the same error bounds as , considering creates a trade-off between the lower bound of the error and the complexity of Algorithm 1. As an example, choosing removes one call in Algorithm 1. However, by following the proof of Theorem 4 for , the error will be lower bounded by , which potentially is an acceptable trade-off.
The differential model of the constant addition as well as the approximation error will be used in the automated method that we will present in the next section to search for characteristics and impossible differentials of ARX ciphers.
SMT-based search of characteristics and impossible differentials
In this section, we describe how to formulate the search of optimal characteristics and impossible differentials as a sequence of SMT problems, which can be solved by an off-the-shelf SMT solver such as Boolector [62] or STP [22]. Our methods are inspired by the approach of Mouha and Preneel [57] to search for single-key characteristics of Salsa20 [57] and the approach by Sasaki and Todo to search for impossible differentials using Mixed Integer Linear Programming (MILP) [66].
Searching for characteristics
To search for characteristics up to probability , the probability space is decomposed into n intervals , where , and for each interval, the decision problem of whether there exists a characteristic with probability is encoded as an SMT problem. Note that a characteristic has probability if and only if its integer weight is equal to w. Section 4.2 describes the encoding process for an ARX cipher.
The SMT problems are provided to the SMT solver, which checks their satisfiability in increasing weight order. When the SMT solver finds the first satisfiable problem, an assignment of the variables that makes the problem satisfiable is obtained, and the search finishes. The assignment contains a characteristic with integer weight , and it is optimal in the sense that there are no characteristics with integer weight strictly smaller than . If the n SMT problems are found to be unsatisfiable, then it is proved there are no characteristics with probability higher than .
To speed up the search, we perform the search iteratively on round-reduced versions of the cipher. First, we search for an optimal characteristic for a small number of rounds r; let denote its integer weight. Then, we search for an optimal -round characteristic, but skipping the SMT problems with weight strictly less than . Since these SMT problems were found to be unsatisfiable for r rounds, they will also be unsatisfiable for rounds. This procedure is repeated until the total number of rounds is reached. Algorithm 2 describes in pseudo-code this search strategy. Our strategy prioritises SMT problems with low weight and small number of rounds, which are faster to solve. In addition, our search also finds optimal characteristics of round-reduced versions, which can be used in other differential-based attacks, such as rectangle or boomerang attacks [9, 71].
This automated method can be used to search for either single-key or related-key characteristics. Furthermore, additional SMT constraints can be added to the SMT problems in order to search for different types of characteristics. For related-key characteristics and by default, this method searches characteristics minimizing the total weight . Strong related-key characteristics can be searched by adding the constraint in the SMT problems. Similarly, equivalent keys can be found by adding the constraint .
Algorithm 2 returns the characteristic with the minimum SMT integer weight, obtained from the bit-vector differential models used within the SMT problems. When some of these models compute approximations of the intermediate weights, the SMT integer weight and the actual integer weight of the characteristic might differ, and the returned characteristic might not be optimal. However, if we have alternative models that compute the exact intermediate weights (that cannot be represented in the SMT problems) and a bound for the error of the SMT integer weight, Algorithm 2 can be adapted to obtain the optimal characteristic as follows. First, Algorithm 2 is used to obtain the characteristic with the minimum SMT integer weight . Then, one finds all2 characteristics with SMT integer weights , where is the absolute bound for the error of the SMT integer weight. Finally, the weights of the found characteristics are recomputed with the alternative models, and the characteristic with the minimum integer weight is returned. This adaptation can be used for ARX ciphers with constant additions, as the error bound can be computed from Theorem 4 and Machado’s algorithm [53] can be used to compute the exact weights of the constant additions.
This method only ensures optimality if the differential probabilities over each round are independent and the characteristic probability does not strongly depend on the choice of the secret key. When these assumptions do not hold for a cipher, we empirically compute the weight of each characteristic found by sampling many input pairs satisfying the input difference and counting those satisfying the difference trail. In this case, this method provides a practical heuristic to find characteristics with high probability, and it is one of the best systematic approaches for some families of ciphers, such as ARX.
Encoding the SMT problems
In this section, we explain how to formulate the decision problem of determining whether a characteristic exists with integer weight W of an ARX cipher as an SMT problem in the bit-vector theory.
First, the ARX cipher is represented in Static Single Assignment (SSA) form, that is, as an ordered list of instructions such that each variable is assigned exactly once and each instruction is a modular addition, a rotation, or an XOR.
For each variable x in the SSA representation, a bit-vector variable denoting the difference of x is defined in the SMT problem. Then, for every instruction , the weight and the differential model of f are added to the SMT problem as a bit-vector variable w and bit-vector constraints and , following Table 5.
Table 5.
Bit-vector differential models of ARX operations
Finally, the following bit-vector constraints are added to the SMT problem,
where denotes the input difference and denote the weight of each operation. The first constraint excludes the trivial characteristic with zero input difference, while the second constraint fixes the weight of the characteristic to the target weight. Note that the bit-size of the weights might need to be increased to prevent an overflow in the modular addition of the last constraint.
Example 5
Consider the keyed function with key k and input ,
This function can be written as a list of simple instructions (SSA form) as
where the output is the pair . Figure 2 depicts the function together with its intermediate variables.
Fig. 2.
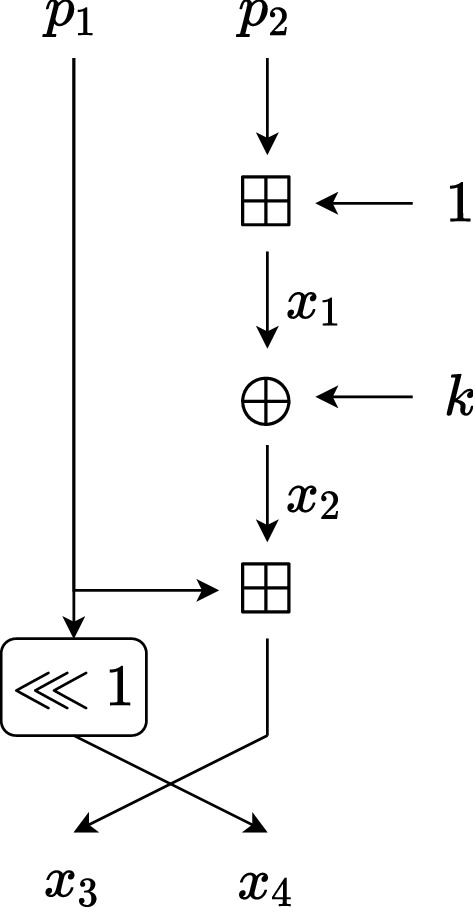
The function
An SMT problem in the bit-vector theory denoting whether has a characteristic with integer weight W is as follows:
The shifts in the last constraint are due to the fact that the last four bits of denote fraction bits. Furthermore, depending on the bit-size of , it might be necessary to extend the bit-size of the weights in order to prevent an overflow in the last modular additions.
Searching of impossible differentials
In [66], Sasaki and Todo [66] propose a MILP-based method to search for impossible differentials that employs the MILP problems used to search for characteristics. Since this method can also be adapted to SMT problems, we will explain the method within the SMT context.
The method’s main idea is that one can check whether a particular differential is impossible by querying a simple SMT problem. While it is infeasible to check all differentials, one can check those with a low number of active bits since most of the known impossible differentials have this property.
The subroutine to check whether a particular differential is impossible can be done as follows. First, the SMT problem of whether there exists a characteristic over the cipher is encoded as in Sect. 4.2. However, only the validity constraints are added; the weight constraints and the target weight W are ignored. Second, the constraints that fix the input and output differences to are added to the SMT problem, that is,
Then, the SMT solver checks the satisfiability of the SMT problem. If the problem is found to be unsatisfiable, the differential is impossible.
This method can be used to search for single-key and related-key impossible differentials. For the former case, the validity constraints of the key schedule are ignored, while for the latter case they are included in the SMT problems.
As opposed to the previous SMT-based characteristic search method, the impossible check subroutine is a sound method. In other words, a characteristic found by Algorithm 2 could be invalid due to the independence assumptions, but a differential found impossible by the check subroutine is always impossible. While the check subroutine is a sound method, it is not complete; there are some impossible differentials that cannot be detected by the check subroutine.
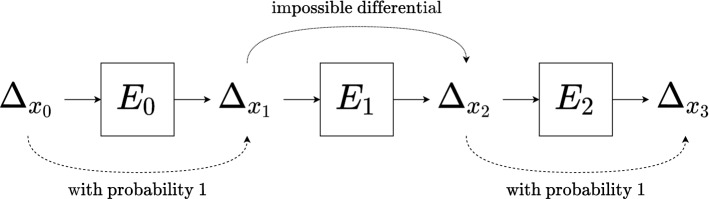
While the check subroutine is fast, checking all differentials is infeasible and only a small subset can be checked with the method by [66]. Thus, we propose a new automated method to search for impossible differentials that does not restrict the search over any pre-defined small subset and let the SMT solver efficiently search through the space of differentials. Our automated method proceeds as follows.
First, we split the cipher into three parts and . Let denote a partial characteristic over E, that is, any characteristic verifying
Note that no relation is imposed between and .
Then, we search for all partial characteristics using our SMT-based method from Sect. 4.1. For each partial characteristic , we apply the check subroutine to the differential over . If is found to be impossible over , then is an impossible differential over E, since and are differentials with probability one (see Fig. 3).
Fig. 3.
The partial characteristic over , alongside the condition that the inner part over is an impossible differential
Like the characteristic search method, we start searching for impossible differentials over a round-reduced version of the cipher and keep increasing the number of rounds iteratively. This procedure is described in Algorithm 3. While FindPartialCh in Algorithm 3 is responsible for finding partial characteristics, IsImpossible subroutine checks the corresponding inner differential to be impossible. Impossible differentials starting after a few rounds are useful in practice, and our method can easily be adapted by splitting the cipher into four parts, , where denotes the skipped rounds.
The main advantage of our method is that the subset of differentials to check does not need to be specified. Thus, it can find impossible differentials that other methods cannot. Moreover, the search of partial characteristics is quite fast, as for many operations f (including the modular addition and the constant addition) the constraint is much simpler than the constraint for the general case .
As opposed to the search of characteristics, the search of -round impossible differentials cannot reuse information obtained from the search of r-round impossible differentials. In other words, Algorithm 2 exploits the fact that if no r-round characteristics were found with weight w, then no -round characteristics can be found with the same weight. However, for some key schedules, Algorithm 2 might find -round impossible differentials even if no r-round impossible differentials were found.
Implementation
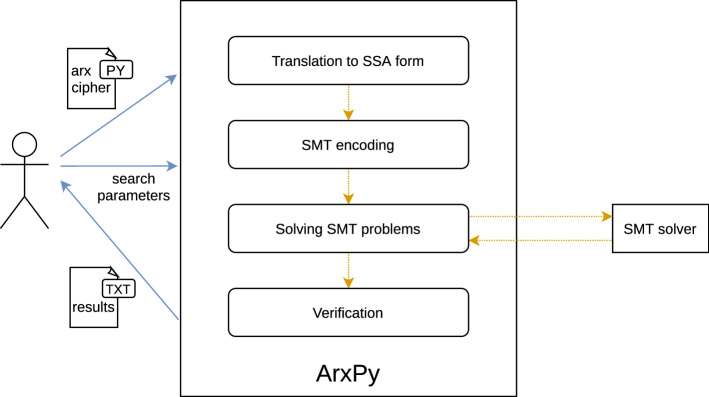
We have developed an open-source tool ArxPy3 to find characteristics and impossible differentials of ARX ciphers implementing the methods described earlier. Originally, ArxPy was a tool to search for rotational-XOR characteristics using SMT solvers [64]. However, we have extended it to support (related-key) differential characteristics and impossible differentials containing the constant addition. ArxPy provides high-level functions that automate the search, a simple interface to represent ARX ciphers, and complete documentation in HTML format, among other features.
ArxPy workflow is represented in Fig. 4. The user first defines the ARX cipher using the interface provided by ArxPy and chooses the parameters of the search (e.g., the type of the characteristic to search, the SMT solver to use, etc.). Then, ArxPy automatically translates the python implementation of the ARX cipher into SSA form, encodes the SMT problems associated to the type of search selected by the user, and solves the SMT problems by querying the SMT solver. When searching for characteristics, for each satisfiable SMT problem found, ArxPy reconstructs the characteristic from the assignment of the variables that satisfies the problem and empirically verifies the weight of the characteristic. Finally, ArxPy returns the results of the search to the user.
Fig. 4.
Workflow of ArxPy
Internally, ArxPy is implemented in Python 3 and uses the libraries SymPy [55] to obtain the SSA representation through symbolic execution and PySMT [23] for the communication with the SMT solvers. Thus, all the SMT solvers supported by PySMT can be directly used for ArxPy.
Experiments
We have applied our methods for finding characteristics and impossible differentials to some ARX ciphers that include constant additions. In particular, we have searched for related-key characteristics and related-key impossible differentials of TEA, XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2.
Due to the difficulty of searching for characteristics of ciphers with constant additions this far, cipher designers have avoided constant additions in the encryption functions so that they could search for single-key characteristics, the most threatening ones. Only a few ciphers include constant additions in the encryption function, and their ad-hoc structures make them more suitable to be analysed with other types of differences, such as additive differences in the case of TEA [11]. As a result, we have focused on searching related-key characteristics and impossible differentials of some well-known ciphers.
Regarding the search for characteristics, we used Algorithm 2 to find related-key characteristics starting from the first round of each cipher. For the case of impossible differentials, we applied Algorithm 3 to search for related-key impossible differentials but skipping the first rounds of the cipher. To this end, we repeatedly call Algorithm 3 while increasing the number of skipped rounds in each call.
For related-key characteristics, the usual assumptions (i.e., round independence and the hypothesis of stochastic equivalence) do not always hold. Thus, we empirically verify each characteristic and stopped each round-reduced search after the first valid characteristic is found.
To verify a related-key characteristic , we split in smaller characteristics with weight lower than 20, and empirically compute the probability of each differential by sampling a small multiple of input pairs for related-key pairs. After combining the probability of each differential, we obtain characteristic probabilities, one for each related-key pair. If the characteristic probability is non-zero for several key pairs, we consider the characteristic valid and we define its empirical probability (resp. weight) as the arithmetic mean of the characteristic probabilities (resp. weights), but excluding those key pairs with zero probability.
Thus, for each characteristic that we have found, i.e. strong related-key characteristic () and weak related-key characteristic (), Table 6 provides: (1) the theoretical key schedule and encryption weights , computed by summing the weight of each ARX operation; (2) the empirical key schedule and encryption weights , computed by sampling input pairs as explained before; and (3) the percentage of the valid key pairs that empirically lead to non-zero probability in the weight verification. In the appendix, we provide the round weights and the round differences for the characteristics covering the most rounds.
Table 6.
Best related-key differential characteristics of XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2
| Cipher | Ch. Type | Rounds | % valid keys | References | ||
|---|---|---|---|---|---|---|
| XTEA | Strong | 16 | 0 | 32 | – | [52] |
| 16 | (0,0) | (37, 32.02) | 46% | This paper | ||
| 18 | (0,0) | (57, 49.79) | 48% | This paper | ||
| Weak | 18 | 17 | 19 | – | [45, 52] | |
| 18 | (4.83, 3.15) | (16, 14.46) | 100% | This paper | ||
| 27 | (6.89, 5.74) | (40, 39.39) | 7% | This paper | ||
| HIGHT | Strong | 10 | 0 | 12 | – | [50] |
| 10 | (0, 0) | (12, 9.97) | 34% | This paper | ||
| 15 | (0, 0) | (45, 42.59) | 8% | This paper | ||
| Weak | 12 | 2 | 19 | – | [40] | |
| 12 | (2.48, 3.19) | (19, 17.65) | 40% | This paper | ||
| 14 | (13.09, 9.85) | (14, 11.46) | 17% | This paper | ||
| LEA | Weak | 11 | – | – | – | [32] |
| 6 | (1.56, 1.22) | (24, 22.50) | 100% | This paper | ||
| 7 | (2.56, 4.68) | (36, 34.35) | 100% | This paper | ||
| SHACAL-1 | Strong | 27 | 0 | 29 | – | [36] |
| 30 | (0, 0) | (63, 47.36) | 97% | This paper | ||
| Weak | 35 | 10 | 29 | – | [18, 72] | |
| 25 | (1, 0.87) | (22, 13.31) | 47% | This paper | ||
| SHACAL-2 | Strong | 24 | 0 | 38 | – | [51] |
| 23 | (0, 0) | (58, 48.06) | 100% | This paper | ||
| Weak | 24 | – | 52 | – | [12] | |
| 22 | (6.67, 2.38) | (29, 24.03) | 100% | This paper |
Imposes extra conditions on plaintext values or intermediate values
When searching for impossible differentials with skipped rounds, Algorithm 3 splits the cipher into four parts. More specifically, the cipher E is represented as , where denotes the skipped rounds, stands for the rounds of the inner impossible differential, and and respectively denote the backward and the forward rounds of the partial characteristics. In Table 7 we provide the number of rounds of each part for the best related-key impossible differentials that we found, and in Table 8 we provide the input and output differences of our longest impossible differentials.
Table 7.
Best related-key impossible differentials of XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2
Table 8.
Input, output, and key differences of our longest related-key impossible differentials
| Cipher | Differences | |
|---|---|---|
| XTEA | ||
| HIGHT | ||
| LEA | ||
| SHACAL-1 | ||
| SHACAL-2 | ||
Apart from all of the best-known impossible differentials that are indicated in Table 7, we also implemented and searched impossible differentials using the automated method of Sasaki and Todo [66] to compare the results with the ones observed by Algorithm 3. While for XTEA, LEA, and HIGHT, both methods find impossible differentials with the same number of rounds, for SHACAL-1 and SHACAL-2 Algorithm 3 achieves impossible differentials covering more rounds. For XTEA and HIGHT, the longest impossible differentials found by Algorithm 3 include a few active bits, and thus they could also be found by the other method. However, for SHACAL-1 and SHACAL-2, our algorithm found impossible differentials containing multiple active bits, which cannot be obtained by other methods that restrict to predefined differential subsets with a low number of active bits.
For the experiments, we have used ArxPy equipped with the SMT solver Boolector [62], winner of the SMT competition SMT-COMP 2019 in the bit-vector track [26]. We run the characteristic search for one week on a single core of an Intel Xeon 6244 at 3.60GHz. The search of impossible differentials was done on similar hardware during one week as well. Note that better characteristics and impossible differentials could be found if the round-reduced searches are not stopped after the first valid characteristic or if more time is employed.
TEA
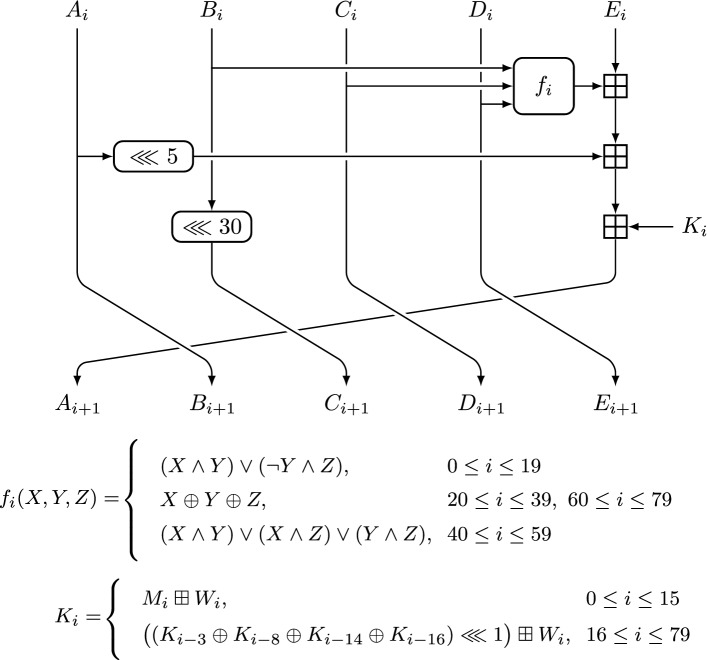
Designed by Wheeler and Needham, TEA [73] is a block cipher with 64-bit block size and 128-bit key size. It iterates 64 times an ARX round function, including constant additions and logical shifts, depicted in Fig. 5. Since the logical shifts propagate XOR differences deterministically, the encoding method presented in Sect. 4.2 can be easily extended to include these operations.
Fig. 5.
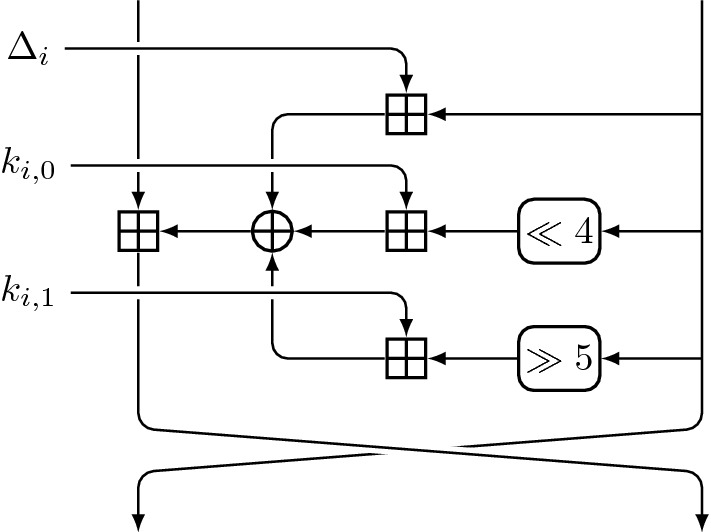
The i-th round of TEA, . The master key mk is split into four 32-bit words and the i-th round key is defined as if i is even and if i is odd. The i-th round constant is defined as , where
Kelsey et al. [35] presented the best related-key characteristics in [35]. They found a 2-round iterative strong related-key characteristic with weight , which they extended to a 60-round characteristic with weight (0, 30). They also discovered in [34] that each TEA key has three other equivalent keys.
Using ArxPy, we revisited the results by Kelsey et al. [34], but in a fully automated way. We found three related-key characteristics with weight zero over the full cipher, confirming that each key is equivalent to exactly three other keys. Excluding these three characteristics, we also obtained a 60-round strong related-key characteristic with weight (0, 30), and all the 60-round SMT problems with smaller weights were found to be unsatisfiable. Since a 60-round related-key characteristic is sufficient to mount the related-key differential cryptanalysis on full-round TEA [35], there is no need to search for characteristics containing more rounds of TEA, and we stop at 60 rounds.
There is also no need to search for related-key impossible differentials of TEA, as each of the three full-round zero-weight related-key characteristics induces roughly full-round related-key impossible differentials, simply by alternating either the plaintext or the ciphertext difference.
XTEA
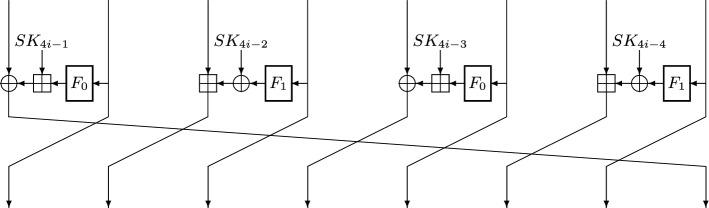
The block cipher XTEA [60] is designed by the same authors of TEA to fix the weakness of the former cipher (in the related-key setting). XTEA has a 64-bit block size and 128-bit key size, and it iterates 64 times the round function depicted in Fig. 6. Like TEA, the round function also includes logical shifts, but the constant additions are included in the key schedule.
Fig. 6.
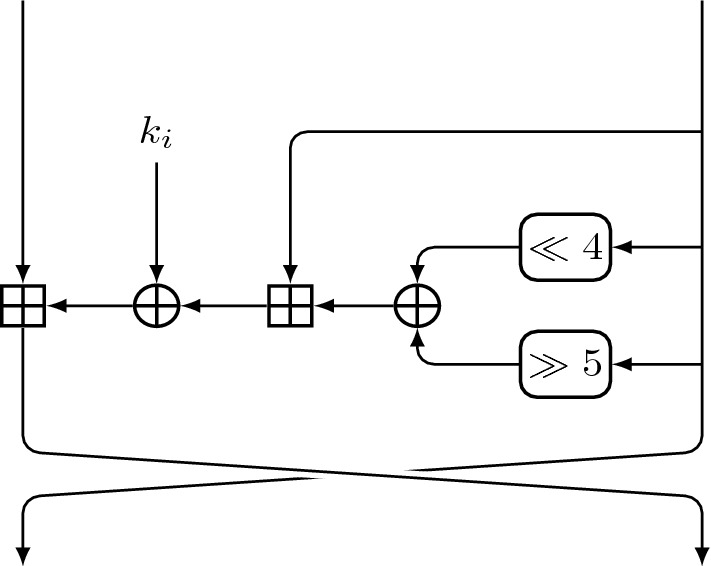
The i-th round of XTEA, . The master key mk is split into four 32-bit words and the i-th round key is defined as if i is even and if i is odd. The i-th constant is defined as , where
The longest related-key characteristics found so far are the 16-round strong related-key differential with weight 32, manually found by Lu in [52], and the 18-round weak related-key characteristic with weights , manually found by Lee et al. [45] but later improved to (17, 19) by Lu [52].
The results of our automated search for related-key characteristics are listed in Table 6. In the strong related-key search, we found an 18-round characteristic with weight 57; all the SMT problems for 19 rounds were found to be unsatisfiable. In the weak related-key search, we found characteristics up to 27 rounds, where the 27-round characteristic has total weight . No equivalent keys were found for XTEA.
In our automated search for related-key impossible differentials of XTEA, we observed impossible differentials spanning 25 rounds, similar to the best impossible differential found this far by Darbuka [15]. Denoting the cipher XTEA with 25 rounds by , our related-key impossible differential contains a 13-round inner impossible differential over , extended by a deterministic 7-round backward trail over and a deterministic 5-round forward trail over as depicted in Table 7. Our automated tool was also able to complete the search of related-key impossible differentials up to 31 rounds, but no impossible differentials spanning more than 25 rounds were found.
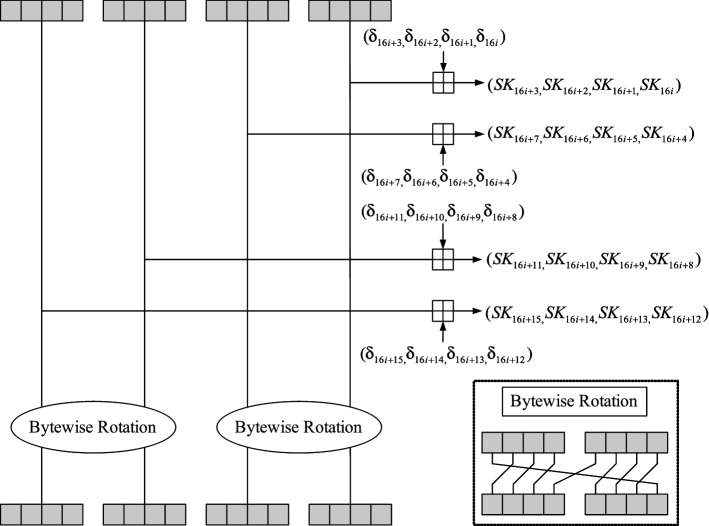
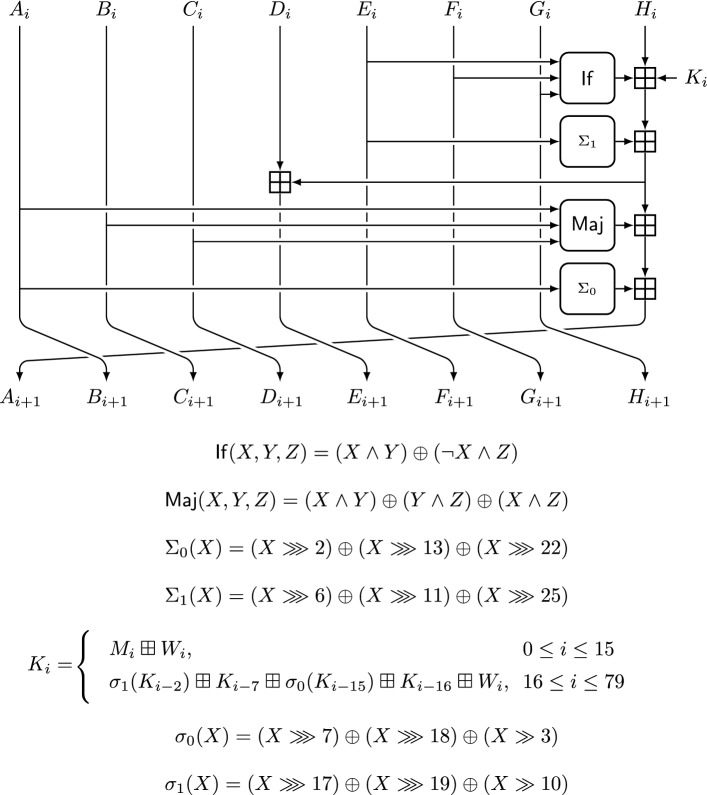
HIGHT
Adopted as an international standard by ISO/IEC [33], HIGHT [31] is a lightweight cipher with a block size of 64 bits and a key size of 128 bits. The encryption function performs initial and final key whitening transformations, and iterates 32 times a round function including XORs, 2-input additions and rotations; the constant additions are performed in the key schedule.
Fig. 7.
The i-th round function of HIGHT, [31]. The i-th round key is denoted by and the functions and are defined as and
Fig. 8.
The key schedule of HIGHT [31]. The round key words are denoted by and the key schedule constants are denoted by
The longest related-key characteristics found for HIGHT are a 10-round strong characteristic with weight 12 found by Lu [50], and a 12-round weak characteristic with weights found by Koo et al. [40]. In our automated search, we found related-key characteristics up to 15 rounds, listed in Table 6. The longest strong related-key characteristic we found covered 15 rounds with weights (0, 45), whereas the longest weak related-key characteristic covered 14 rounds with total weight .
Özen et al. introduced the best-known 22-round related-key impossible differential for HIGHT [63]. Using ArxPy, we found a new impossible differential covering the same number of rounds, as shown in Table 7. Our impossible differential consists of a 14-round inner impossible differential, extended by two zero-weight 4-round backward and forward related-key trails. The mentioned 22-round impossible differential is the longest related-key impossible differential that ArxPy could obtain in one week by checking up to 32 rounds of HIGHT.
LEA
Among the family of ARX ciphers LEA [32], we analysed LEA-128, the version with 128-bit block size, 24 rounds, and 128-bit key size. The encryption round function of LEA performs 2-input additions, rotations, and XORs, whereas the key schedule contains constant additions and rotations.
Fig. 9.
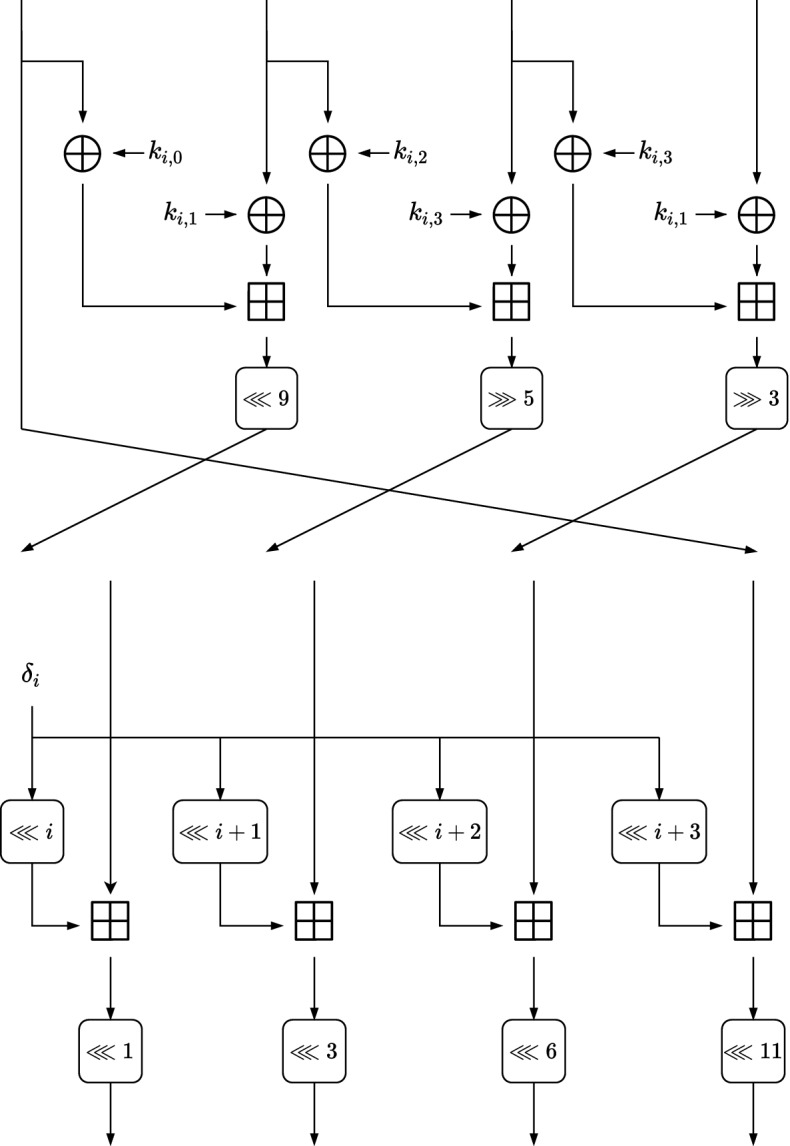
The i-th round function of the encryption (top) and the key schedule (bottom) of LEA-128, . The tuple denotes the i-th round key and denotes the i-th key schedule constant
The designers of LEA found related-key characteristics up to 11 rounds, but only specifying that the 11-round characteristics are valid for a small part of the key space and without providing the weights of such characteristics [32]. Excluding these characteristics, there are no others examples of related-key characteristics of LEA. Our automated search found weak related-key characteristics up to 7 rounds valid for the full key space, listed in Table 6. Strong characteristics with weight smaller than 128 were found up to 4 rounds, and all the strong related-key SMT problems for 5 rounds were found unsatisfiable. No equivalent keys were found for LEA.
We applied ArxPy on LEA to automatically search for related-key impossible differentials. While our method completed the search for a large number of rounds, only impossible differentials with non-zero key difference spanning up to four rounds were found. The lack of related-key impossible differentials, with low Hamming weight or with key schedule transitions with probability 1, seems to be due to the heavy and robust key schedule of LEA. By and large, ciphers with lightweight key schedule algorithms tend to have longer related-key impossible differentials in comparison to their single-key counterparts. However, the key schedule and the round function of LEA are of the same complexity. Thus, finding an impossible differential that covers more rounds in related-key setting instead of single-key setting seems infeasible. We confirmed this by applying our tool to LEA in the single-key setting, obtaining multiple 10-round single-key impossible differentials within a few hours.
SHACAL-1
Based on the compression function of the NIST standard hash function SHA-1 [19], the block cipher SHACAL-1 was initially suggested in [27] and submitted by Handschuh and Naccache to the NESSIE project [61]. SHACAL-1 uses 160-bit block size and 80 rounds, where its round function is similar to the SHA-1 compression function. The key size can be variable from 0 to 512 bits, although a minimum of 128-bit key size is required in [28] and we analysed SHACAL-1 for 512-bit keys.
There are some ad-hoc differential characteristics presented in [18, 30, 36]. However, Wang et al. [72] indicated that many of the previous characteristics are invalid. The longest valid XOR differential characteristic is a 35-round weak related-key characteristic that appeared in [18] and was later corrected in [72] to obtain the corrected weights . Moreover, the longest strong related-key XOR differential characteristic that is not found to be invalid by [72] spans 27 rounds of SHACAL-1 with the corresponding weights [36].
These characteristics do not necessarily start from the first round of SHACAL-1 since they are not used for a differential attack but rather for a rectangle attack [9]. Note that the round function of SHACAL-1 changes in different rounds (see Fig. 10), and these characteristics could take advantage of the variable definition of the round function. However, we are only looking for the characteristics starting from the first round and for the particular case of SHACAL-1 with variable round functions, we do not necessarily obtain the best possible characteristics.
Fig. 10.
The i-th round of SHACAL-1, . The 160-bit input is divided into five 32-bit words , , , , and . The function significantly changes regarding the round number. For a given 512-bit master key , the round keys are computed as described above, where is the round constant
Our automated tool ArxPy obtained a weak-key 25-round characteristic with . Moreover, the tool could also find a 30-round characteristic in the strong-key setting with the corresponding weights . In our search, a large amount of SHACAL-1 characteristics found by the SMT solver did not pass our empirical validation test, which significantly increased the running time for finding each valid characteristic. More specifically and in the weak-key setting, we found more than 100 empirically invalid characteristics until we detected a valid 25-round one; we also obtained multiple 26-round weak characteristics within a week, but they were found invalid by our empirical test. We discarded more than 900 empirically invalid characteristics for the strong-key setting before finding a valid 30-round characteristic, and none of the 31-round trails obtained in a week could pass the test.
One of the main reasons for the large number of empirically invalid characteristics is the 5-input modular addition within the round function of SHACAL-1. Since the differential model of the modular addition with three or more inputs is unknown, we had to approximate the differential model of the 5-input addition with a chain of 2-input addition models. In other words, to model the 5-input addition , we split it into four 2-input additions
and we model the four 2-input additions independently. Thus, we are approximating the differential probability of the 5-input addition
with the multiplication of the differential probabilities of the four 2-input additions
For many differentials, this approximation is not accurate, and this caused the appearance of many empirically invalid characteristics in our search.
As depicted in Table 7, our automated tool found the first known related-key impossible differential of SHACAL-1, extending to 30 rounds of the cipher from rounds 20 to 49. The backward and forward trails respectively traverse 2 and 12 rounds of SHACAL-1, delimiting the inner 16-round impossible differential. The search for 31-round impossible differentials did not finish after one week, and we stopped the search. Thus, we expect that dedicating more time to the search may result in obtaining longer impossible differentials.
Fig. 11.
The i-th round of SHACAL-2, . The 256-bit input is divided into eight 32-bit words , , , , , , , and . The special operators used in the round function of SHACAL-2 are , , , and that are defined as above. For a given 512-bit master key , the key schedule generates round keys as described in above, where is the round constant
SHACAL-2
Similar to SHACAL-1, the block cipher SHACAL-2 [28] was designed based on the compression function of the NIST standard hash function SHA-256 [20]. The cipher was submitted to the NESSIE project [61] and was approved as one of the NESSIE final selections. SHACAL-2 is a 256-bit block cipher, has 64 rounds, and supports a variable key size up to 512 bits. We analysed SHACAL-2 for 512-bit keys.
The longest ad-hoc related-key XOR differential characteristic in the strong-key setting is a 24-round characteristic presented in [51] with , which relies on some additional conditions on specific values alongside the differences to improve the weights. Moreover, in the weak-key setting, Biryukov et al. [12] provided two 24-round related-key XOR differential characteristics of SHACAL-2, each has encryption weight . However, they did not explicitly mention the key schedule weight for each characteristic.
Our automated search resulted in a 23-round characteristic in the strong-key setting with encryption weight and a 22-round characteristic in the weak-key setting with total weight . Like SHACAL-1, our automated search could not find longer characteristics of SHACAL-2 within a week due to the large number of empirically invalid characteristics found. The round function of SHACAL-2 also contains a modular addition with multiple inputs (i.e., seven operands), and modelling it with 2-input additions is one of the main reasons for the inaccurate differential behaviour for some special differences.
Table 7 lists the results of the best related-key impossible differentials of SHACAL-2. The 18-round impossible differential presented by Yang et al. in [75] has been the longest known related-key impossible differential for SHACAL-2 so far. Our automated tool ArxPy obtained a 24-round impossible differential, improving the previous best result by 6 rounds. This impossible differential includes a 12-round inner impossible differential, extended by two deterministic 1-round backward and 11-round forward trails. We checked up to 28-rounds of SHACAL-2 in one week, and the longest impossible differential we observed was the 24-round related-key impossible differential.
Conclusion
In this paper, we proposed the first bit-vector differential model of the n-bit modular addition with a constant. We described a bit-vector formula, with bit-vector complexity O(1), that determines whether a differential is valid and a bit-vector function, with complexity , that provides a close approximation of the differential weight. In this regard, we carefully studied our approximation error and obtained almost tight bounds. Moreover, we described two new SMT-based automated methods to search for characteristics and impossible differentials of ARX ciphers including constant additions, respectively.
Each of our methods formulates the search problem as a sequence of bit-vector SMT problems, encoded from the cipher’s SSA representation and the bit-vector differential models of each operation. We have implemented our methods in ArxPy, an open-source tool to find characteristics and impossible differentials of ARX ciphers in a fully automated way. To show some examples, we have applied our automated methods to search for equivalent keys, related-key characteristics, and related-key impossible differentials of TEA, XTEA, HIGHT, LEA, SHACAL-1, and SHACAL-2.
Regarding the characteristic results, for TEA we revisited previous results obtained in a manual approach. In contrast, for XTEA, HIGHT, and LEA, we improved the previous best-known related-key characteristics in both the strong-key and the weak-key settings. Our characteristic results of SHACAL-1 and SHACAL-2 did not outperform previous works in all settings due to the presence of modular additions with more than two inputs, for which no efficient differential model has been proposed yet.
Concerning the impossible differentials, our results for TEA, XTEA, and HIGHT are of the same length, compared to the best-known related-key impossible differentials. On the other hand, we obtained the longest related-key impossible differentials for LEA, SHACAL-1, and SHACAL-2.
Our differential model relies on a bit-vector-friendly approximation on the binary logarithm. Thus, future works could explore other approximations improving the bit-vector complexity or the approximation error, which could also be applied to other SMT problems involving the binary logarithm. While we have focused on the modular addition by a constant, there are other simple operations for which no differential model has been proposed so far, such as the modular multiplication, and the modular addition with more than two inputs. Obtaining differential models for more operations will allow designing ciphers with more flexibility, leading to new designs that potentially are more efficient.
Acknowledgements
Seyyed Arash Azimi and Mohammad Reza Aref were partially supported by Iran National Science Foundation (INSF) under Contract No. 96/53979. Adrián Ranea is supported by a PhD Fellowship from the Research Foundation - Flanders (FWO).
Appendix A: Characteristics
We describe the characteristics covering most rounds that we obtained in Sect. 5. For each characteristic, we provide the difference of the master key words , the difference of the plaintext words and the difference of the ciphertext words . Furthermore, for each round of the cipher, we provide the difference of the i-th round key words, the output difference of the i-th round function , the (cumulative) weight of the operations that compute the i-th round key words and the weight of the i-th round function . The differences are given in hexadecimal values.
Table 9.
The 60-round strong related-key characteristic of TEA
| i-th round | ||
|---|---|---|
| 0 | (0x00000000, 0x80000000) | 0 |
| 1 | (0x80000000, 0x00000000) | 1 |
| 2 | (0x00000000, 0x80000000) | 0 |
| 3 | (0x80000000, 0x00000000) | 1 |
| 4 | (0x00000000, 0x80000000) | 0 |
| 5 | (0x80000000, 0x00000000) | 1 |
| 6 | (0x00000000, 0x80000000) | 0 |
| 7 | (0x80000000, 0x00000000) | 1 |
| 8 | (0x00000000, 0x80000000) | 0 |
| 9 | (0x80000000, 0x00000000) | 1 |
| 10 | (0x00000000, 0x80000000) | 0 |
| 11 | (0x80000000, 0x00000000) | 1 |
| 12 | (0x00000000, 0x80000000) | 0 |
| 13 | (0x80000000, 0x00000000) | 1 |
| 14 | (0x00000000, 0x80000000) | 0 |
| 15 | (0x80000000, 0x00000000) | 1 |
| 16 | (0x00000000, 0x80000000) | 0 |
| 17 | (0x80000000, 0x00000000) | 1 |
| 18 | (0x00000000, 0x80000000) | 0 |
| 19 | (0x80000000, 0x00000000) | 1 |
| 20 | (0x00000000, 0x80000000) | 0 |
| 21 | (0x80000000, 0x00000000) | 1 |
| 22 | (0x00000000, 0x80000000) | 0 |
| 23 | (0x80000000, 0x00000000) | 1 |
| 24 | (0x00000000, 0x80000000) | 0 |
| 25 | (0x80000000, 0x00000000) | 1 |
| 26 | (0x00000000, 0x80000000) | 0 |
| 27 | (0x80000000, 0x00000000) | 1 |
| 28 | (0x00000000, 0x80000000) | 0 |
| 29 | (0x80000000, 0x00000000) | 1 |
| 30 | (0x00000000, 0x80000000) | 0 |
| 31 | (0x80000000, 0x00000000) | 1 |
| 32 | (0x00000000, 0x80000000) | 0 |
| 33 | (0x80000000, 0x00000000) | 1 |
| 34 | (0x00000000, 0x80000000) | 0 |
| 35 | (0x80000000, 0x00000000) | 1 |
| 36 | (0x00000000, 0x80000000) | 0 |
| 37 | (0x80000000, 0x00000000) | 1 |
| 38 | (0x00000000, 0x80000000) | 0 |
| 39 | (0x80000000, 0x00000000) | 1 |
| 40 | (0x00000000, 0x80000000) | 0 |
| 41 | (0x80000000, 0x00000000) | 1 |
| 42 | (0x00000000, 0x80000000) | 0 |
| 43 | (0x80000000, 0x00000000) | 1 |
| 44 | (0x00000000, 0x80000000) | 0 |
| 45 | (0x80000000, 0x00000000) | 1 |
| 46 | (0x00000000, 0x80000000) | 0 |
| 47 | (0x80000000, 0x00000000) | 1 |
| 48 | (0x00000000, 0x80000000) | 0 |
| 49 | (0x80000000, 0x00000000) | 1 |
| 50 | (0x00000000, 0x80000000) | 0 |
| 51 | (0x80000000, 0x00000000) | 1 |
| 52 | (0x00000000, 0x80000000) | 0 |
| 53 | (0x80000000, 0x00000000) | 1 |
| 54 | (0x00000000, 0x80000000) | 0 |
| 55 | (0x80000000, 0x00000000) | 1 |
| 56 | (0x00000000, 0x80000000) | 0 |
| 57 | (0x80000000, 0x00000000) | 1 |
| 58 | (0x00000000, 0x80000000) | 0 |
| 59 | (0x80000000, 0x00000000) | 1 |
| Total | 30 | |
| (0x80000000, 0x00000000) | ||
| (0x80000000, 0x00000000) | ||
| (0x00000000, 0x00000000, 0x00000000, 0x84000000) | ||
Table 10.
The three full-round related-key characteristics with total weight 0 of TEA
| (0x80000000, 0x80000000, 0x80000000, 0x80000000) | (0x00000000, 0x00000000) | (0x00000000, 0x00000000) |
| (0x00000000, 0x00000000, 0x80000000, 0x80000000) | (0x00000000, 0x00000000) | (0x00000000, 0x00000000) |
| (0x80000000, 0x80000000, 0x00000000, 0x00000000) | (0x00000000, 0x00000000) | (0x00000000, 0x00000000) |
Table 11.
The 18-round strong related-key characteristic of XTEA
| i-th round | ||||
|---|---|---|---|---|
| 0 | 0x00000000 | 0 | (0x00010000, 0x44200000) | 9 |
| 1 | 0x00000000 | 0 | (0x44200000, 0x04000000) | 6 |
| 2 | 0x00000000 | 0 | (0x04000000, 0x80000000) | 6 |
| 3 | 0x80000000 | 0 | (0x80000000, 0x00000000) | 2 |
| 4 | 0x80000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 5 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 6 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 7 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 8 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 9 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 10 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 11 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 12 | 0x80000000 | 0 | (0x00000000, 0x80000000) | 0 |
| 13 | 0x80000000 | 0 | (0x80000000, 0x04000000) | 2 |
| 14 | 0x00000000 | 0 | (0x04000000, 0x44200000) | 6 |
| 15 | 0x00000000 | 0 | (0x44200000, 0x00010000) | 6 |
| 16 | 0x00000000 | 0 | (0x00010000, 0xc4310800) | 9 |
| 17 | 0x00000000 | 0 | (0xc4310800, 0x01010040) | 11 |
| Total | 0 | 57 | ||
| (0xc4310800, 0x00010000) | ||||
| (0xc4310800, 0x01010040) | ||||
| (0x00000000, 0x00000000, 0x80000000, 0x00000000) | ||||
Table 12.
The 27-round weak related-key characteristic of XTEA
| i-th round | ||||
|---|---|---|---|---|
| 0 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 1 | 0x80000000 | 0 | (0x00000000, 0x80000000) | 0 |
| 2 | 0x80000000 | 0 | (0x80000000, 0x04000000) | 2 |
| 3 | 0x40200000 | 1.179 | (0x04000000, 0x04000000) | 4 |
| 4 | 0x40200000 | 0 | (0x04000000, 0x80000000) | 4 |
| 5 | 0x80000000 | 0 | (0x80000000, 0x00000000) | 2 |
| 6 | 0x80000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 7 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 8 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 9 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 10 | 0x80000000 | 0 | (0x00000000, 0x80000000) | 0 |
| 11 | 0x80000000 | 0 | (0x80000000, 0x04000000) | 2 |
| 12 | 0x40200000 | 1.006 | (0x04000000, 0x04000000) | 4 |
| 13 | 0x40200000 | 0.734 | (0x04000000, 0x80000000) | 4 |
| 14 | 0x80000000 | 0 | (0x80000000, 0x00000000) | 2 |
| 15 | 0x80000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 16 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 17 | 0x00000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 18 | 0x80000000 | 0 | (0x00000000, 0x80000000) | 0 |
| 19 | 0x00000000 | 0 | (0x80000000, 0x84000000) | 2 |
| 20 | 0x40600000 | 2.067 | (0x84000000, 0x80000000) | 4 |
| 21 | 0x80000000 | 0 | (0x80000000, 0x80000000) | 2 |
| 22 | 0x80000000 | 0 | (0x80000000, 0x84000000) | 2 |
| 23 | 0xc0600000 | 1.907 | (0x84000000, 0x80000000) | 4 |
| 24 | 0x00000000 | 0 | (0x80000000, 0x00000000) | 2 |
| 25 | 0x80000000 | 0 | (0x00000000, 0x00000000) | 0 |
| 26 | 0x80000000 | 0 | (0x00000000, 0x80000000) | 0 |
| Total | 6.893 | 40 | ||
| (0x00000000, 0x00000000) | ||||
| (0x80000000, 0x00000000) | ||||
| (0x00000000, 0x80000000, 0xc0200000, 0x80000000) | ||||
Table 13.
The 15-round strong related-key characteristic of HIGHT. The round -1 corresponds to the initial key whitening
| i-th round | ||||
|---|---|---|---|---|
| − 1 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x09, 0x20, 0xb8, 0xe9, 0x80, 0x00) | 1 |
| 0 | (0x00, 0x00, 0x80, 0x00) | 0 | (0x00, 0x00, 0x20, 0xb8, 0xe9, 0x80, 0x00, 0x00) | 3 |
| 1 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0xb8, 0x2c, 0x80, 0x00, 0x00, 0x00) | 6 |
| 2 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x2c, 0x80, 0x00, 0x00, 0x00, 0x00) | 3 |
| 3 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x80, 0x00, 0x00, 0x00, 0x00, 0x00) | 3 |
| 4 | (0x00, 0x80, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 5 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 6 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 7 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 8 | (0x80, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x80) | 0 |
| 9 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0xd4, 0x80, 0x00) | 5 |
| 10 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x90, 0xd4, 0x80, 0x00, 0x00) | 1 |
| 11 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0xe9, 0x90, 0x95, 0x80, 0x00, 0x00, 0x00) | 7 |
| 12 | (0x00, 0x00, 0x00, 0x00) | 0 | (0xe9, 0x00, 0x95, 0x80, 0x00, 0x00, 0x00, 0x80) | 1 |
| 13 | (0x00, 0x00, 0x00, 0x80) | 0 | (0x00, 0xe9, 0x80, 0x00, 0x00, 0xa4, 0x80, 0xe9) | 9 |
| 14 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x80, 0xe9, 0x80, 0x00, 0x89, 0xa4, 0x2b, 0xe9) | 6 |
| Total | 0 | 45 | ||
| (0x00, 0x00, 0x09, 0x20, 0xb8, 0xe9, 0x80, 0x00) | ||||
| (0x80, 0xe9, 0x80, 0x00, 0x89, 0xa4, 0x2b, 0xe9) | ||||
| (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x80, 0x00) | ||||
Table 14.
The 14-round weak related-key characteristic of HIGHT. The round -1 corresponds to the initial key whitening
| i-th round | ||||
|---|---|---|---|---|
| -1 | (0x00, 0x00, 0x00, 0x40) | 0 | (0x62, 0xc0, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 1 |
| 0 | (0x40, 0x00, 0x00, 0x00) | 0.791 | (0xc0, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 2 |
| 1 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0xc0) | 0 |
| 2 | (0x00, 0x00, 0x00, 0x3a) | 1.0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0xc0, 0x00) | 0 |
| 3 | (0x00, 0x00, 0x00, 0x40) | 0.752 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 1 |
| 4 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 5 | (0x00, 0x00, 0x00, 0x40) | 0.791 | (0x00, 0x00, 0x00, 0x00, 0x00, 0xc0, 0x00, 0x00) | 1 |
| 6 | (0x00, 0x00, 0x2e, 0x00) | 4.0 | (0x00, 0x00, 0x00, 0x00, 0xc0, 0x00, 0x00, 0x00) | 5 |
| 7 | (0x00, 0x00, 0x40, 0x00) | 1.093 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 1 |
| 8 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 9 | (0x00, 0x00, 0xc0, 0x00) | 0.046 | (0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00) | 1 |
| 10 | (0x00, 0x16, 0x00, 0x00) | 4.0 | (0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 11 | (0x00, 0x40, 0x00, 0x00) | 0.142 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 1 |
| 12 | (0x00, 0x00, 0x00, 0x00) | 0 | (0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00) | 0 |
| 13 | (0x00, 0x00, 0xc0, 0x00) | 0.476 | (0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00) | 1 |
| Total | 13.091 | 14 | ||
| (0x62, 0xc0, 0x00, 0x00, 0x00, 0x00, 0x00, 0x40) | ||||
| (0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00) | ||||
| (0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x7a, 0x00, 0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00) | ||||
Table 15.
The 7-round weak related-key characteristic of LEA
| i-th round | ||||
|---|---|---|---|---|
| 0 | (0x20000000, 0x00000000, 0x00000000, 0x00000000) | 0.408 | (0x80000000, 0x40000000, 0xc0000010, 0x4000000c) | 14 |
| 1 | (0x40000000, 0x00000000, 0x00000000, 0x00000000) | 0.462 | (0x00000000, 0x80000000, 0x80000000, 0x80000000) | 7 |
| 2 | (0x80000000, 0x00000000, 0x00000000, 0x00000000) | 0.695 | (0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 3 | (0x00000001, 0x00000000, 0x00000000, 0x00000000) | 0 | (0x00000200, 0x00000000, 0x00000000, 0x00000000) | 1 |
| 4 | (0x00000002, 0x00000000, 0x00000000, 0x00000000) | 0 | (0x00040400, 0x00000000, 0x00000000, 0x00000200) | 2 |
| 5 | (0x00000004, 0x00000000, 0x00000000, 0x00000000) | 0 | (0x08080800, 0x00000000, 0x00000040, 0x00040400) | 4 |
| 6 | (0x00000008, 0x00000000, 0x00000000, 0x00000000) | 1.0 | (0x10101010, 0x00000002, 0x00008088, 0x08080800) | 8 |
| Total | 2.565 | 36 | ||
| (0x4000000c, 0x2040000c, 0x20400004, 0x20400082) | ||||
| (0x10101010, 0x00000002, 0x00008088, 0x08080800) | ||||
| (0x10000000, 0x00000000, 0x00000000, 0x00000000) | ||||
Table 16.
The 30-round strong related-key characteristic of SHACAL-1
| i-th round | ||||
|---|---|---|---|---|
| 0 | 0x80000000 | 0 | (0x00000000, 0x00000002, 0x00000000, 0x80100008, 0x00008000) | 7 |
| 1 | 0x80000000 | 0 | (0x00008000, 0x00000000, 0x80000000, 0x00000000, 0x80100008) | 5 |
| 2 | 0x00000000 | 0 | (0x00000008, 0x00008000, 0x00000000, 0x80000000, 0x00000000) | 5 |
| 3 | 0x00000000 | 0 | (0x00000100, 0x00000008, 0x00002000, 0x00000000, 0x80000000) | 5 |
| 4 | 0x80000000 | 0 | (0x00000008, 0x00000100, 0x00000002, 0x00002000, 0x00000000) | 6 |
| 5 | 0x00000000 | 0 | (0x00000102, 0x00000008, 0x00000040, 0x00000002, 0x00002000) | 8 |
| 6 | 0x00000000 | 0 | (0x00000000, 0x00000102, 0x00000002, 0x00000040, 0x00000002) | 8 |
| 7 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x80000040, 0x00000002, 0x00000040) | 5 |
| 8 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x80000040, 0x00000002) | 5 |
| 9 | 0x00000000 | 0 | (0x00000002, 0x00000000, 0x00000000, 0x00000000, 0x80000040) | 3 |
| 10 | 0x80000000 | 0 | (0x00000000, 0x00000002, 0x00000000, 0x00000000, 0x00000000) | 3 |
| 11 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x80000000, 0x00000000, 0x00000000) | 1 |
| 12 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x80000000, 0x00000000) | 1 |
| 13 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x80000000) | 1 |
| 14 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 15 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 16 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 17 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 18 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 19 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 20 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 21 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 22 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 23 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 24 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 25 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 26 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 27 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 28 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 29 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| Total | 0 | 63 | ||
| (0x00000002, 0x00000000, 0x80100008, 0x00008000, 0x80000040) | ||||
| (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| (0x80000000, 0x80000000, 0x00000000, 0x00000000, | ||||
| 0x80000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x80000000, 0x00000000, 0x80000000, 0x00000000, | ||||
| 0x80000000, 0x00000000, 0x80000000, 0x00000000) | ||||
Table 17.
The 25-round weak related-key characteristic of SHACAL-1
| i-th round | ||||
|---|---|---|---|---|
| 0 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x80000040, 0x00000002, 0x80000000) | 3 |
| 1 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x80000040, 0x00000002) | 3 |
| 2 | 0x00000000 | 0 | (0x00000002, 0x00000000, 0x00000000, 0x00000000, 0x80000040) | 3 |
| 3 | 0x80000000 | 0 | (0x00000000, 0x00000002, 0x00000000, 0x00000000, 0x00000000) | 3 |
| 4 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x80000000, 0x00000000, 0x00000000) | 1 |
| 5 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x80000000, 0x00000000) | 1 |
| 6 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x80000000) | 1 |
| 7 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 8 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 9 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 10 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 11 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 12 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 13 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 14 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 15 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 16 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 17 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 18 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 19 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 20 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 21 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 22 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 0 |
| 23 | 0x00000003 | 1 | (0x00000001, 0x00000000, 0x00000000, 0x00000000, 0x00000000) | 4 |
| 24 | 0x00000000 | 0 | (0x00000020, 0x00000001, 0x00000000, 0x00000000, 0x00000000) | 3 |
| Total | 1 | 22 | ||
| (0x00000000, 0x00000102, 0x00000002, 0x80000000, 0x80000000) | ||||
| (0x00000020, 0x00000001, 0x00000000, 0x00000000, 0x00000000) | ||||
| (0x00000000, 0x80000000, 0x00000000, 0x80000000, | ||||
| 0x00000000, 0x80000000, 0x00000000, 0x80000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
Table 18.
The 23-round strong related-key characteristic of SHACAL-2
| i-th round | ||||
|---|---|---|---|---|
| 0 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x221c0240, 0x80000000, | 12 |
| 0x00000000, 0x00082200, 0x20040000, 0x80000000) | ||||
| 1 | 0x00000000 | 0 | (0x80000000, 0x00000000, 0x00000000, 0x221c0240, | 26 |
| 0x00000000, 0x00000000, 0x00082200, 0x20040000) | ||||
| 2 | 0x00000000 | 0 | (0x00000000, 0x80000000, 0x00000000, 0x00000000, | 7 |
| 0x02100040, 0x00000000, 0x00000000, 0x00082200) | ||||
| 3 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x80000000, 0x00000000, | 4 |
| 0x00000000, 0x02100040, 0x00000000, 0x00000000) | ||||
| 4 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x80000000, | 3 |
| 0x00000000, 0x00000000, 0x02100040, 0x00000000) | ||||
| 5 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 4 |
| 0x80000000, 0x00000000, 0x00000000, 0x02100040) | ||||
| 6 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 1 |
| 0x00000000, 0x80000000, 0x00000000, 0x00000000) | ||||
| 7 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 1 |
| 0x00000000, 0x00000000, 0x80000000, 0x00000000) | ||||
| 8 | 0x80000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x80000000) | ||||
| 9 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 10 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 3 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 11 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 12 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 13 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 14 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 15 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 16 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 17 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 18 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 19 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 20 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 21 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 22 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| Total | 0 | 58 | ||
| (0x00000000, 0x00000000, 0x221c0240, 0x80000000, | ||||
| 0x00000000, 0x00082200, 0x20040000, 0x80000000) | ||||
| (0x00000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| (0x00000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x80000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
Table 19.
The 22-round weak related-key characteristic of SHACAL-2
| i-th round | ||||
|---|---|---|---|---|
| 0 | 0x00000000 | 0 | (0x00000000, 0x00020000, 0x00000000, 0x00000000, | 6 |
| 0x01000840, 0x00000000, 0x00000000, 0x88000020) | ||||
| 1 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00020000, 0x00000000, | 4 |
| 0x00000000, 0x01000840, 0x00000000, 0x00000000) | ||||
| 2 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00020000, | 4 |
| 0x00000000, 0x00000000, 0x01000840, 0x00000000) | ||||
| 3 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 4 |
| 0x00020000, 0x00000000, 0x00000000, 0x01000840) | ||||
| 4 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 1 |
| 0x00000000, 0x00020000, 0x00000000, 0x00000000) | ||||
| 5 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 1 |
| 0x00000000, 0x00000000, 0x00020000, 0x00000000) | ||||
| 6 | 0x00020000 | 0.405 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 3 |
| 0x00000000, 0x00000000, 0x00000000, 0x00020000) | ||||
| 7 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 8 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 9 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 10 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 11 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 12 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 3 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 13 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 14 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 15 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 16 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 17 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 18 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 19 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 20 | 0x00000000 | 0 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 0 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| 21 | 0x80004400 | 6.262 | (0x00000000, 0x00000000, 0x00000000, 0x00000000, | 6 |
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
| Total | 6.67 | 29 | ||
| (0x00000000, 0x00020000, 0x00000000, 0x00000000, | ||||
| 0x01000840, 0x00000000, 0x00000000, 0x88000020) | ||||
| (0x80004400, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x80004400, 0x00000000, 0x00000000, 0x00000000) | ||||
| (0x00000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00020000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000, | ||||
| 0x00000000, 0x00000000, 0x00000000, 0x00000000) | ||||
Footnotes
It is possible to get another solution of an SMT problem by solving it again with an additional constraint that excludes the first solution. By repeating this process, one can find all the solutions.
Parts of this paper were presented at the Asiacrypt 2020 conference [3].
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Seyyed Arash Azimi, Email: arash_azimi@ee.sharif.edu.
Adrián Ranea, Email: adrian.ranea@esat.kuleuven.be.
Mahmoud Salmasizadeh, Email: salmasi@sharif.edu.
Javad Mohajeri, Email: mohajer@sharif.edu.
Mohammad Reza Aref, Email: aref@sharif.edu.
Vincent Rijmen, Email: vincent.rijmen@esat.kuleuven.be.
References
- 1.Aumasson JP, Henzen L, Meier W, Phan RCW. Sha-3 proposal blake. NIST (round 3) 2009;92:2008. [Google Scholar]
- 2.Aumasson J.P., Jovanovic P., Neves S.: Analysis of NORX: investigating differential and rotational properties. In: LATINCRYPT, volume 8895 of Lecture Notes in Computer Science. Springer, Cham (2014).
- 3.Azimi S.A., Ranea A., Salmasizadeh M., Mohajeri J., Aref M.R., Rijmen V.: A bit-vector differential model for the modular addition by a constant. In: International Conference on the Theory and Application of Cryptology and Information Security, pp. 385–414. Springer, Cham (2020).
- 4.Bagherzadeh E, Ahmadian Z. Milp-based automatic differential searches for LEA and HIGHT. IACR Cryptol. 2018;2018:948. [Google Scholar]
- 5.Barrett C, Tinelli C. Satisfiability modulo theories. In: Clarke EM, Henzinger TA, Veith H, Bloem R, editors. Handbook of Model Checking. Cham: Springer; 2018. pp. 305–343. [Google Scholar]
- 6.Beaulieu R, Shors D, Smith J, Treatman-Clark S, Weeks B, Wingers L. The SIMON and SPECK families of lightweight block ciphers. IACR Cryptol. 2013;2013:404. [Google Scholar]
- 7.Bernstein DJ. The salsa20 family of stream ciphers. New York: Springer; 2008. [Google Scholar]
- 8.Biham E., Biryukov A., Shamir A.: Cryptanalysis of skipjack reduced to 31 rounds using impossible differentials. In: EUROCRYPT, volume 1592 of Lecture Notes in Computer Science. Springer (1999).
- 9.Biham E., Dunkelman O., Keller N.: The rectangle attack-rectangling the serpent. In: Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Advances in Cryptology - EUROCRYPT 2001, Innsbruck, Austria, May 6–10, 2001 (2001).
- 10.Biham E, Shamir A. Differential cryptanalysis of des-like cryptosystems. J. Cryptol. 1991;4(1):3–72. doi: 10.1007/BF00630563. [DOI] [Google Scholar]
- 11.Biryukov A., Velichkov V.: Automatic search for differential trails in arx ciphers. In Cryptographers’ Track at the RSA Conference. Springer, Cham (2014)
- 12.Biryukov A., Lamberger M., Mendel F., Nikolić I.: Second-order differential collisions for reduced sha-256. In: International Conference on the Theory and Application of Cryptology and Information Security. Springer (2011)
- 13.Biryukov A., Velichkov V., Le Corre Y.: Automatic search for the best trails in arx: application to block cipher speck. In: International Conference on Fast Software Encryption, pp. 289–310. Springer (2016).
- 14.Cui T, Chen S, Fu K, Wang M, Jia K. New automatic tool for finding impossible differentials and zero-correlation linear approximations. Sci. China. 2021;64(2):129103. [Google Scholar]
- 15.Darbuka A.: Related-key attacks on block ciphers. Master’s thesis. Master’s thesis, Middle East Technical University (2009).
- 16.Dinu D., Perrin L., Udovenko A., Velichkov V., Großschädl J., Biryukov A.: Design strategies for ARX with provable bounds: Sparx and LAX. In: ASIACRYPT (1), volume 10031 of Lecture Notes in Computer Science (2016).
- 17.Dinu D, Corre YL, Khovratovich D, Perrin L, Großschädl J, Biryukov A. Triathlon of lightweight block ciphers for the internet of things. J. Cryptogr. Eng. 2019;9(3):283–302. doi: 10.1007/s13389-018-0193-x. [DOI] [Google Scholar]
- 18.Dunkelman O., Keller N., Kim J.: Related-key rectangle attack on the full shacal-1. In: International Workshop on Selected Areas in Cryptography. Springer (2006).
- 19.FIPS. Secure hash standard. Federal Information Processing Standards Publication 180-1. (1995).
- 20.FIPS. Secure hash standard. Federal Information Processing Standards Publication 180-4 (2015).
- 21.Fu K., Wang M., Guo Y., Sun S., Hu L.: Milp-based automatic search algorithms for differential and linear trails for speck. In: Fast Software Encryption—23rd International Conference, FSE 2016, Bochum, Germany, March 20–23, 2016 Revised Selected Papers (2016).
- 22.Ganesh V., Dill D.L.: A decision procedure for bit-vectors and arrays. In: CAV, volume 4590 of Lecture Notes in Computer Science. Springer (2007).
- 23.Gario M., Micheli A.: Pysmt: a solver-agnostic library for fast prototyping of smt-based algorithms. In: SMT Workshop 2015 (2015).
- 24.Gartner. Gartner identifies top 10 strategic IoT technologies and trends. https://www.gartner.com/en/newsroom/press-releases/2018-11-07-gartner-identifies-top-10-strategic-iot-technologies-and-trends (2018).
- 25.Gartner. Gartner survey reveals 47 percent of organizations will increase investments in IoT despite the impact of covid-19. https://www.gartner.com/en/newsroom/press-releases/2020-10-29-gartner-survey-reveals-47-percent-of-organizations-will-increase-investments-in-iot-despite-the-impact-of-covid-19- (2020).
- 26.Hadarean L., Hyvarinen A., Niemetz A., Reger G.: 14th international satisfiability modulo theories competition (smt-comp 2019). https://smt-comp.github.io/2019/ (2019).
- 27.Handschuh H., Knudsen L.R., Robshaw M.J.: Analysis of sha-1 in encryption mode. In: Track at the RSA Conference. Springer (2001)
- 28.Handschuh H., Naccache D.: Shacal: a family of block ciphers. Submission to the NESSIE project (2002).
- 29.Henry J, Warren S. Hacker’s delight. Boston: Addison-Wesley; 2003. [Google Scholar]
- 30.Hong S., Kim J., Lee S., Preneel B.: Related-key rectangle attacks on reduced versions of shacal-1 and aes-192. Springer, In International Workshop on Fast Software Encryption (2005).
- 31.Hong D., Sung J., Hong S., Lim J., Lee S., Koo B.S., Lee C., Chang D., Lee J., Jeong K., Kim H.: HIGHT: A new block cipher suitable for low-resource device. In: Cryptographic Hardware and Embedded Systems - CHES 2006, 8th International Workshop, Yokohama, Japan, October 10–13, 2006, Proceedings (2006).
- 32.Hong D., Lee J.K., Kim D.C., Kwon D., Ryu K.H., Lee D.G.: LEA: A 128-bit block cipher for fast encryption on common processors. In: WISA, volume 8267 of Lecture Notes in Computer Science. Springer (2013).
- 33.ISO/IEC 18033-3:2010. Information technology, Security techniques, Encryption algorithms, Part 3: Block ciphers. Standard, International Organization for Standardization (2010).
- 34.Kelsey J., Schneier B., Wagner D.A.: Key-schedule cryptanalysis of idea, g-des, gost, safer, and triple-des. In: CRYPTO, volume 1109 of Lecture Notes in Computer Science. Springer (1996).
- 35.Kelsey J., Schneier B., Wagner B.A.: Related-key cryptanalysis of 3-way, biham-des, cast, des-x, newdes, rc2, and TEA. In: ICICS, volume 1334 of Lecture Notes in Computer Science. Springer (1997).
- 36.Kim J., Kim G., Hong S., Lee S., Hong D.: The related-key rectangle attack, application to shacal-1. In: Australasian Conference on Information Security and Privacy. Springer (2004).
- 37.Knudsen L. Deal-a 128-bit block cipher. Complexity. 1998;258(2):216. [Google Scholar]
- 38.Kölbl S., Hadipour H.: Cryptosmt: An easy to use tool for cryptanalysis of symmetric primitives based on smt/sat solvers. https://github.com/kste/cryptosmt.
- 39.Kölbl S., Leander G., Tiessen T., Observations on the SIMON block cipher family. In Advances in Cryptology - CRYPTO 2015–35th Annual Cryptology Conference, Santa Barbara, CA, USA, August 16–20,: Proceedings. Part I, 2015 (2015).
- 40.Koo B., Hong D., Kwon D.: Related-key attack on the full HIGHT. In: Information Security and Cryptology - ICISC 2010 - 13th International Conference, Seoul, Korea, December 1–3, 2010, Revised Selected Papers (2010).
- 41.Koo B, Roh D, Kim H, Jung Y, Lee D, Kwon, D: CHAM: A family of lightweight block ciphers for resource-constrained devices. In: Information Security and Cryptology - ICISC 2017 - 20th International Conference, Seoul, South Korea, November 29–December 1, 2017, Revised Selected Papers (2017).
- 42.Kovásznai G, Fröhlich A, Biere A. Complexity of fixed-size bit-vector logics. Theory Comput. Syst. 2016;59(2):323. doi: 10.1007/s00224-015-9653-1. [DOI] [Google Scholar]
- 43.Lai X., Massey J.L.: A proposal for a new block encryption standard. In EUROCRYPT, volume 473 of Lecture Notes in Computer Science. Springer (1990).
- 44.Lai X., Massey J.L., Murphy S.: Markov ciphers and differential cryptanalysis. In: EUROCRYPT, volume 547 of Lecture Notes in Computer Science. Springer (1991).
- 45.Lee E., Hong D., Chang D., Hong S., Lim J.: A weak key class of XTEA for a related-key rectangle attack. In: VIETCRYPT, volume 4341 of Lecture Notes in Computer Science. Springer (2006).
- 46.Lipmaa H.: On differential properties of pseudo-hadamard transform and related mappings. In: A. Menezes, P. Sarkar (eds) Progress in Cryptology - INDOCRYPT 2002, Third International Conference on Cryptology in India, Hyderabad, India, December 16–18, 2002, vol. 2551 of Lecture Notes in Computer Science. Springer (2002).
- 47.Lipmaa H., Moriai S.: Efficient algorithms for computing differential properties of addition. In: Fast Software Encryption, 8th International Workshop, FSE 2001 Yokohama, Japan, April 2–4, 2001, Revised Papers (2001).
- 48.Liu Y, Witte GD, Ranea A, Ashur T. Rotational-xor cryptanalysis of reduced-round SPECK. IACR Trans. Symmetric Cryptol. 2017;3:2017. [Google Scholar]
- 49.Lodi A.: Mixed integer programming computation. In: 50 Years of Integer Programming. Springer (2010).
- 50.Lu J.: Cryptanalysis of reduced versions of the HIGHT block cipher from CHES 2006. In: Information Security and Cryptology - ICISC 2007, 10th International Conference, Seoul, Korea, November 29–30, 2007, Proceedings (2007).
- 51.Lu J., Kim J., Keller N., Dunkelman O.: Related-key rectangle attack on 42-round shacal-2. In: International Conference on Information Security. Springer (2006).
- 52.Lu J. Related-key rectangle attack on 36 rounds of the XTEA block cipher. Int. J. Inf. Sec. 2009;8(1):15. doi: 10.1007/s10207-008-0059-9. [DOI] [Google Scholar]
- 53.Machado AW. Differential probability of modular addition with a constant operand. IACR Cryptol. 2001;2001:52. [Google Scholar]
- 54.Matsui M.: On correlation between the order of s-boxes and the strength of des. Springer, In Workshop on the Theory and Application of of Cryptographic Techniques (1994).
- 55.Meurer A, Smith CP, Paprocki M, et al. Sympy: symbolic computing in python. PeerJ. 2017;3:e103. [Google Scholar]
- 56.Mitchell JN. Computer multiplication and division using binary logarithms. IRE Trans. Electron. Comput. 1962;4:512. doi: 10.1109/TEC.1962.5219391. [DOI] [Google Scholar]
- 57.Mouha N, Preneel B. Towards finding optimal differential characteristics for ARX: application to Salsa20. IACR Cryptol. 2013;2013:328. [Google Scholar]
- 58.Mouha N., Mennink B., Van Herrewege A., Watanabe D., Preneel B., Verbauwhede I.: Chaskey: an efficient mac algorithm for 32-bit microcontrollers. In International Conference on Selected Areas in Cryptography. Springer (2014).
- 59.National Institute of Standards and Technology. Lightweight cryptography project. https://csrc.nist.gov/Projects/Lightweight-Cryptography.
- 60.Needham R., Wheeler D.: Tea extensions. Technical report, Computer Laboratory, University of Cambridge (1997).
- 61.NESSIE. New european schemes for signatures, integrity and encryption. https://www.cosic.esat.kuleuven.be/nessie/index.html.
- 62.Niemetz A, Preiner M, Biere A. Boolector 2.0 system description. J. Satisf. Boolean Modeling Comput. 2015;9:53–58. doi: 10.3233/SAT190101. [DOI] [Google Scholar]
- 63.Özen O., Varıcı K., Tezcan C., Kocair C.: Lightweight block ciphers revisited: Cryptanalysis of reduced round present and height. In Australasian Conference on Information Security and Privacy. Springer (2009).
- 64.Ranea A, Liu Y, Ashur T. An easy-to-use tool for rotational-xor cryptanalysis of ARX block ciphers. Proc. Roman. Acad. Series A. 2017;18(3):1–8. [Google Scholar]
- 65.Ren J, Chen S. Cryptanalysis of reduced-round speck. IEEE Access. 2019;7:63045–63056. doi: 10.1109/ACCESS.2019.2917015. [DOI] [Google Scholar]
- 66.Sasaki Y., Todo Y.: New impossible differential search tool from design and cryptanalysis aspects - revealing structural properties of several ciphers. In EUROCRYPT (3), volume 10212 of Lecture Notes in Computer Science (2017).
- 67.Schulte-Geers E. On ccz-equivalence of addition mod $2^n$ Designs Codes Cryptogr. 2013;66(1–3):111–127. doi: 10.1007/s10623-012-9668-4. [DOI] [Google Scholar]
- 68.Song L., Huang Z., Yang Q.: Automatic differential analysis of ARX block ciphers with application to SPECK and LEA. In Information Security and Privacy - 21st Australasian Conference, ACISP: Melbourne, VIC, Australia, July 4–6, 2016, Proceedings. Part I, 2016 (2016).
- 69.Sun S., Hu L., Wang P., Qiao K., Ma X., Song L.: Automatic security evaluation and (related-key) differential characteristic search: Application to simon, present, lblock, DES(L) and other bit-oriented block ciphers. In Advances in Cryptology - ASIACRYPT 2014 - 20th International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, R.O.C., December 7–11, 2014. Proceedings, Part I (2014).
- 70.Sun S, Gerault D, Lafourcade P, Yang Q, Todo Y, Qiao K, Hu L. Analysis of aes, skinny, and others with constraint programming. IACR Trans. Symmetric Cryptol. 2017;1:2017. [Google Scholar]
- 71.Wagner DA. The boomerang attack. In Fast Software Encryption, 6th International Workshop, FSE ’99, Rome, Italy, March 24–26, 1999, Proceedings (1999).
- 72.Wang G., Keller N., Dunkelman O.: The delicate issues of addition with respect to xor differences. In: International Workshop on Selected Areas in Cryptography. Springer (2007).
- 73.Wheeler D.J., Needham R.M.: Tea, a tiny encryption algorithm. In FSE, volume 1008 of Lecture Notes in Computer Science. Springer (1994).
- 74.Winternitz RS, Hellman ME. Chosen-key attacks on a block cipher. Cryptologia. 1987;11(1):1–7. doi: 10.1080/0161-118791861749. [DOI] [Google Scholar]
- 75.Yang SP, Hu YP, Zhong MF. Related-key impossible differential attacks on 31-round shacal-2. J. Commun. 2006;28(11A):54–58. [Google Scholar]