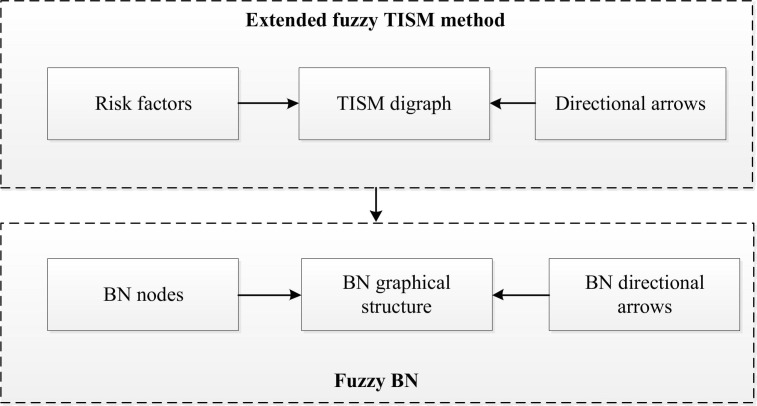
Abstract
With the amount of medical waste rapidly increasing since the corona virus disease 2019 (COVID-19) pandemic, medical waste treatment risk evaluation has become an important task. The transportation of medical waste is an essential process of medical waste treatment. This paper aims to develop an integrated model to evaluate COVID-19 medical waste transportation risk by integrating an extended type-2 fuzzy total interpretive structural model (TISM) with a Bayesian network (BN). First, an interval type-2 fuzzy based transportation risk rating scale is introduced to help experts express uncertain evaluation information, in which a new double alpha-cut method is developed for the defuzzification of the interval type-2 fuzzy numbers (IT2FNs). Second, TISM is combined with IT2FNs to construct a hierarchical structural model of COVID-19 medical waste transportation risk factors under a high uncertain environment; a new bidirectional extraction method is proposed to describe the hierarchy of risk factors more reasonably and accurately. Third, the BN is integrated with IT2FNs to make a comprehensive medical waste transportation risk evaluation, including identifying the sensitive factors and diagnosing the event's causation. Then, a case study of COVID-19 medical waste transportation is displayed to demonstrate the effectiveness of the proposed model. Further, a comparison of the proposed model with the traditional TISM and BN model is conducted to stress the advantages of the proposed model.
Keywords: Risk evaluation, Medical waste transportation, Interval type-2 fuzzy set, Total interpretive structural modeling, Bayesian network
1. Introduction
Medical waste, often known as health care waste, is created during a variety of medical procedures, including diagnosis, treatment, human or animal vaccination, and biological testing (Yong, et al., 2009). The corona virus disease 2019 (COVID-19) has produced a sharp rise in medical waste globally. Since corona virus has a high degree of spatial infectious, latent and viral, the tremendous increase in medical waste is a vital transmission medium for the virus and thus poses severe and new challenges to medical waste management (Chen et al., 2021, Zhao et al., 2022). Current research on COVID-19 medical waste mainly focuses on the selection of waste disposal techniques (Manupati, et al., 2021), sustainable production and waste management policies (Ahmad et al., 2021, Singh et al., 2022, Torkashvand et al., 2021), and the vehicle routing problem (Eren and Tuzkaya, 2021, Govindan et al., 2021). However, safe transportation within the medical waste treatment process is an essential problem in medical waste management (Kumar, et al., 2015). To our extent, no research considers the risks of COVID-19 medical waste transportation. The risks of medical waste transportation process will cause enormous loss of life and property, harm the environment and soil, and even affect social stability (Kumar, et al., 2015). For example, the rebound of the pandemic that broke out in Nanjing in July 2020 was caused by the improper handling of the protective clothing by airport staff after cleaning the cabin. Therefore, to avoid such incidents, identifying and evaluating the potential risk factors in the transportation process is a crucial issue that needs to be paid attention to.
Since the occurrence of COVID-19 is sudden and historical data is insufficient, the evaluation of risks requires the support of experts in related fields. Some researchers have used fuzzy set theory to deal with the inadequate data in the context of COVID-19 pandemic, indicating that the fuzzy set theory is effective and feasible (Karmaker et al., 2021, Mardani et al., 2020, Sharma et al., 2020). The fuzzy set theory proposed by L. A. Zadeh (1965) is an extensive used tool to handle ambiguous and confusing real-world problems, which can evaluate experts' subjective and inaccurate assessments. Type-1 fuzzy sets are used widely to model imprecise information in literature (Liu, 2011, Maniram Kumar et al., 2018, Sayyadi Tooranloo and Ayatollah, 2016). Nevertheless, uncertainties are inherent in handling words in a natural language, as the same words have various meanings for different persons (Boukezzoula and Coquin, 2020). To describe the different opinions about the same word, Zadeh (1975) proposed the type-2 fuzzy sets (T2FS). However, it has a relatively heavy computational burden in the actual application process (Xiaohong and Yingming, 2021). Thus, Mendel and John (2002) suggested the interval type-2 fuzzy sets (IT2FSs) as a reduced version of the T2FS. It's worth noting that the IT2FS is a particular instance of the T2FS, and its calculation is significantly easier than the T2FS. Therefore, it has been extensively utilized in many fields, such as maritime transportation (Celik and Akyuz, 2016, Pelin and Emre, 2021), green supplier selection (Wu, et al., 2019) and waste site selection (Hong, et al., 2021).
COVID-19 medical waste transportation process involves multiple risk factors since COVID-19 has a high degree of spatial infectious, latent and viral. Understanding the interactions between risk factors can help to control risks (Schulte, et al., 2012). Considering the interaction relationships between the risk factors related to COVID-19, total interpretative structural modeling (TISM) and decision making trial and evaluation laboratory (DEMATEL) are commonly used (Karmaker et al., 2021, Lakshmi Priyadarsini and Suresh, 2020, Sen et al., 2021). Sen, et al. (2021) applied DEMATEL to investigate the influential factors on COVID-19 related deaths and their effects on each other. Lakshmi Priyadarsini and Suresh (2020) introduced TISM to understand the interrelationship between and among the factors that affect the epidemiological characteristics of COVID-19. Karmaker, et al. (2021) used TISM to visualize the hierarchical structure of mutual relationships between/among the factors affecting supply chain sustainability in the context of COVID-19 pandemic. DEMATEL is a survey to help understand the complex relationship among selected factors, which is incapable of determining the hierarchical structure of complicated systems (Wang, et al., 2018). TISM is an enhanced version of interpretive structural modeling (ISM), proposed by Sushil (2012), which can identify the structural relationship between multiple factors and demonstrate direct and transitive relationships (Li, et al., 2019). Especially, Liao, et al. (2021) proposed a double alpha-cut-based consensus measurement method for HFLPRs, which has low computational complexity and high accuracy in handling fuzzy information. We refer to the idea and propose a new double alpha-cut method to convert the IT2FNs into numerical values of 0 or 1, by which we can establish a reachability matrix during the calculation of TISM under a high uncertain environment. After obtaining the reachability matrix, level extraction is used to determine the hierarchical relationships among risk factors. Two main widely used level extraction methods of TISM are up-type hierarchy method and down-type hierarchy method (Zhang, Huang et al., 2021), also known as result-first hierarchy extraction method and cause-first hierarchy extraction method. However, these two traditional extraction methods may have some inconsistencies in practice. So we propose a new hierarchical extraction method, called the bidirectional extraction method to help reflect the dialectical relationship between causes and results more realistic and effective.
As to quantify the risks of the COVID-19 medical waste transportation process, the Bayesian network (BN) provides a very important idea for the risk evaluation of systems composed of multiple risk factors. BN is popular to solve risk evaluation problems due to its ability to express dependencies among events, update probability based on new evidence and reasoning under uncertainty (Li, et al., 2018). Based on the hierarchical structure of risk factors obtained by TISM, BN is applied to describe uncertain and complex relationships among various factors quantitatively. Moreover, there has been a tendency in studies to combine fuzzy set theory with the BN considering the uncertain information during the evaluation process. For example, Ghasemi, et al. (2021) developed an approach for predicting human error probabilities of road tanker loading operation by using fuzzy set theory and BN. Yucesan, et al. (2021) use the fuzzy Bayesian network (FBN) to determine the occurrence probabilities of the failure modes and apply the model in an industrial kitchen equipment manufacturing facility. Guo, et al. (2020) combined the FBN with an improved similarity aggregation method to assess the storage tank accident risk, FBN is used to identify the critical events of the storage tank accident. Abbassinia, et al. (2020) developed a dynamic model of human error assessment in emergencies in the petrochemical industry based on FBN and fuzzy-AHP-TOPSIS method. Based on these studies, the BN based on the hierarchy of factors, is proposed to analyze risk factors and identify the sensitive factors for the medical waste transportation system. Moreover, the interval type-2 fuzzy numbers (IT2FNs) is used to calculate the prior probabilities of root nodes and the conditional probabilities of leaf nodes, which are the fuzzification of the linguistic expressions obtained from expert opinions.
Based on the abovementioned consideration, this paper proposes an extended fuzzy TISM method and maps the hierarchical structure model to BN. IT2FSs are applied to handle the subjective uncertainty of information when experts evaluate the COVID-19 medical waste transportation risk factors since the linguistic variables are more in line with the expression habits of experts. A double alpha-cut of IT2FNs and a new bidirectional extraction method are first combined with TISM method to construct the hierarchy diagram of risk factors under high uncertain environment. The BN is applied to model the objective uncertainties caused by probabilistic variations of risk factors and conduct a comprehensive risk analysis. It also provides a description of different risk factors and their interconnections through graphical representations. The contributions of this article are:
-
(i).
Experts evaluate the risk factors in the process of COVID-19 medical waste transportation by using IT2FNs, which has the capability of reflecting the subjectivity under uncertain environments.
-
(ii).
An extended fuzzy TISM method is proposed to analyze risk factors and interpret hierarchical relationships of risk factors in a complex and uncertain system.
-
(iii).
A new double alpha-cut is first combined with IT2FNs to convert IT2FNs into crisp numbers, which has low computational complexity and high accuracy in the calculation process.
-
(iv).
A new bidirectional extraction method is first proposed to construct the hierarchy diagram of risk factors in TISM, accurately reflecting the risk factors' levels.
-
(v).
The structural model of risk factors is transformed into a BN to quantitatively analyze the functions and interactions among risk factors. The IT2FSs are combined with BN to derive the prior probabilities and conditional probabilities of risk factors.
The rest of the paper is organized as follows. Section 2 briefly introduces some notions and properties about the IT2FS, TISM method and the BN. Section 3 describes the research methodology for the proposed risk evaluation framework. Section 4 introduces specific steps of the integrated model for COVID-19 medical waste transportation risk evaluation based on extended fuzzy TISM and fuzzy BN. Section 5 presents a case study in Nanjing concerning COVID-19 medical waste transportation process to emphasize the effectiveness of the proposed model. Section 6 conducts a comparison of our proposed model with traditional model. Section 7 provides a brief conclusion and future research directions.
2. Preliminaries
2.1. Interval type-2 fuzzy set
The interval type-2 fuzzy sets (IT2FSs) are used to express imprecise and uncertain evaluation information considering experts' psychological variables. A type-2 fuzzy set in the universe of discourse can be denoted by a type-2 membership function as follows:
| (1) |
In which, and for all admissible and. Furthermore, the type-2 fuzzy set can also be shown in the following form:
| (2) |
If all = 1, then is defined as an IT2FS. An IT2FS can be presented as a subset of type-2 fuzzy sets, which is defined as follows:
| (3) |
Among these various types of fuzzy numbers, the interval type-2 trapezoidal fuzzy number (IT2TrFN) is one of the most widely used for describing uncertainty information (Hendiani et al., 2020, Jin et al., 2020, Liu, 2011, Xie et al., 2017).
Let be an IT2TrFN, which can be denoted as Fig. 1 . Suppose that there are two IT2TrFNs as follows:
Fig. 1.
Interval type-2 trapezoidal fuzzy sets.
Mathematical operations between the IT2TrFNs are described as follows:
| (4) |
| (5) |
| (6) |
| (7) |
2.2. Total interpretive structural modeling
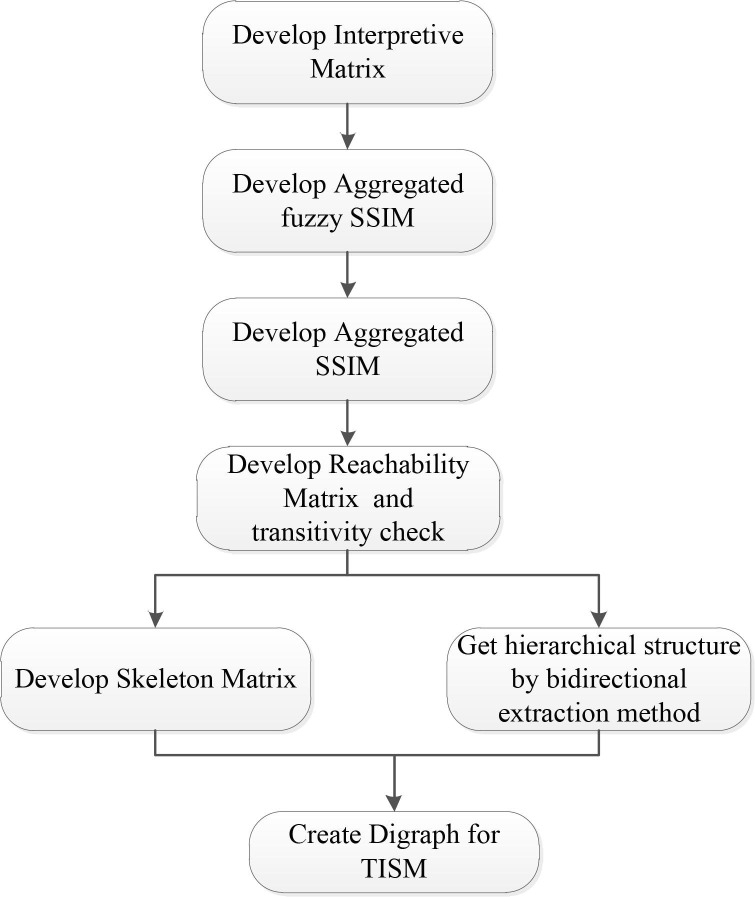
To explain the contextual direction and relationship between the elements in the pairwise comparison, Total Interpretive Structural Modeling (TISM) is proposed as an improved model of the ISM. TISM is used to model the factors for better comprehension of their interaction. Fig. 2 shows the flowchart and specific steps of TISM analysis:
Fig. 2.
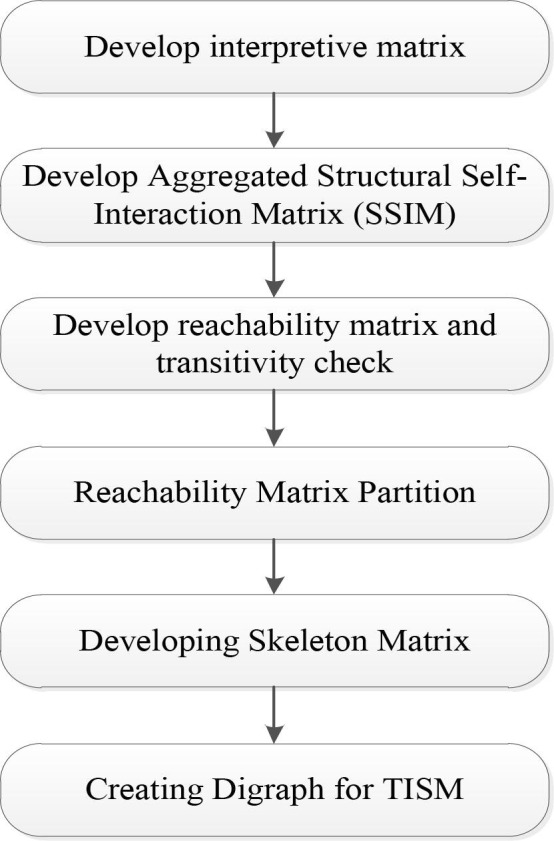
Specific steps of TISM.
Step 1: Developing Interpretive Matrix.
TISM (similar to ISM) starts with identifying the components and establishing their contextual relationships. Experts determine the connection between any two components depending on the context of each element.
Step 2: Develop Aggregated Structural Self-Interaction Matrix (SSIM).
V, A, X, and O are the four symbols that describe the relationships between any two elements under consideration. The aggregated SSIM is obtained by filling responses of a group of experts on the pairwise interaction matrix.
Step 3: Developing Reachability Matrix.
Convert the information in SSIM into 1 and 0 to construct the reachability matrix. Moreover, a transitivity check is required. The transitivity matrix is verified for the transitivity rule and modified as necessary until complete transitivity is achieved.
Step 4: Reachability Matrix Partition.
The next stage is to generate a digraph and extract a structural model when the transitivity check is completed. On sets and subsets of elements, relation partition and level partition may be used to partition the reachability matrix process (Warfield, 1974).
Step 5: Developing Skeleton Matrix.
After eliminating the transitivity, the reduction matrix is obtained by successfully removing the strongly connected elements in each level. Then the skeleton matrix is obtained by removing the leap-over binary relations among elements in the reduction matrix and the self-reaching binary relations.
Step 6: Creating Digraph for TISM.
The final TISM model shows all transitive and direct influential links according to the skeleton matrix. In addition, it is possible to analyze the proper justification behind the impact of one element on other elements.
2.3. Bayesian network
After obtaining the hierarchy diagram of risk factors, a Bayesian network (BN) is introduced to provide a flexible and robust graphical structure in a probabilistic approach, a directed acyclic graph composed of several nodes and the correlation between nodes (Bapin and Zarikas, 2019). The BN consists of two parts: one is the topological structure (which includes network nodes and directed links), and the other is the conditional probability table. The qualitative description element of the model is the topological structure, which consists of nodes displaying variables and directed arrows. A node from which a directed arrow is generated is called the parent node, while the other node to which the directed arrow is directed is called child node (Pristrom, et al., 2016). The Bayesian network's quantitative section concerns the probability tables of the system's variables. Probabilities, conditional probabilities, and their posterior probabilities are all included in the probability tables. Inference algorithms are based on the following equations (Mahadevan, et al., 2001):
The joint probability distribution of a set of variables is represented as:
| (8) |
where is the probability, represents number of nodes, represents the th node in the network, is the parent set of the variable. Then, the posterior (updated) probabilities can be calculated when new pieces of evidence on variables are given.
| (9) |
3. Research methodology
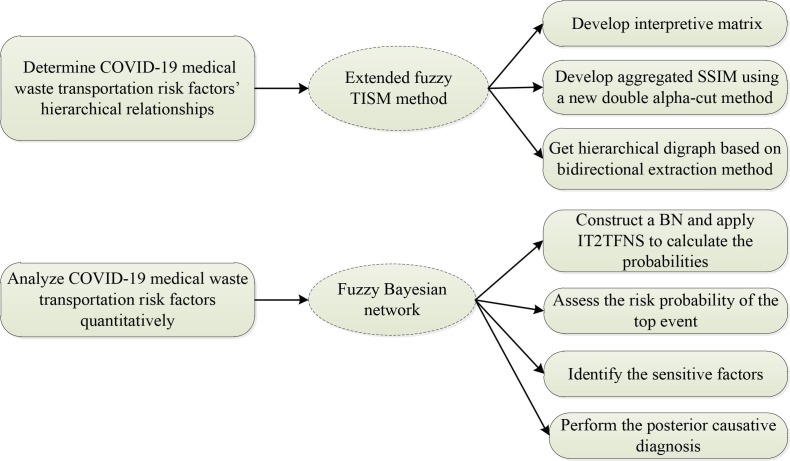
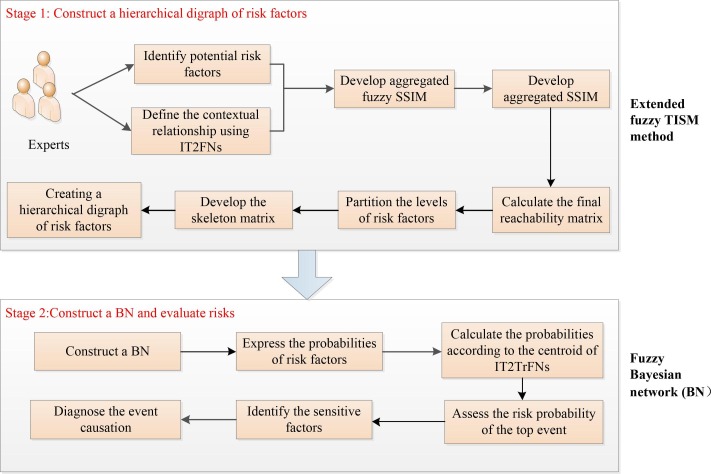
This section describes the research methodology for COVID-19 medical waste transportation risk evaluation from two aspects. First, COVID-19 medical waste is spatial infectious, latent and viral, which makes the transportation process contain multiple risk factors. An extended fuzzy TISM method is proposed to help understanding the interactions between/among risk factors and determine COVID-19 medical waste transportation risk factors’ hierarchical relationships. Second, considering the uncertainties caused by probabilistic variations of COVID-19 medical waste transportation risk factors, the probabilities of risk factors need to be quantified to control risk. The fuzzy BN is used to conduct a comprehensive risk analysis, including identifying the sensitive factors and diagnosing the event's causation. Fig. 3 is drawn to better presentation of the research methodology for COVID-19 medical waste transportation risk evaluation.
Fig. 3.
The framework of the research methodology.
3.1. Determination of risk factors' hierarchical relationships with extended fuzzy TISM method
To determine the COVID-19 medical waste transportation risk factors' hierarchical relationships, an extended fuzzy TISM method is proposed in this section. The traditional TISM is described in Section 2.2. During the TISM process, the double alpha-cut of IT2TrFNs is presented to convert the aggregated fuzzy SSIM into the aggregated SSIM. Moreover, a new bidirectional extraction method is also proposed to obtain a more reliable hierarchical structure. The detailed procedure for the extended fuzzy TISM is discussed as follows and the flow chart of TISM is drawn in Fig. 4 .
Fig. 4.
The flow chart of TISM.
3.1.1. Develop interpretive matrix
Let be the set of experts. Consider the risk factors, where is the th factor, in which. Traditional risk evaluation is based on probabilistic risk assessment methods, which require the support of accurate probability distribution information of risk factors. However, COVID-19 medical waste transportation is complicated and it is challenging to grasp sufficient information on related risk factors. Experts with knowledge and experience in relevant domains are needed to deal with the problem of inadequate data. Therefore, we introduce IT2TrFNs, one of the most often utilized forms of fuzzy numbers, to represent uncertainty and ambiguity. Table 1 adopts a five-level linguistic term to express experts' evaluation (Abdullah and Najib, 2014).
Table 1.
The linguistic terms of IT2TrFNs.
| Linguistic terms | IT2TrFNs |
|---|---|
| Very high influence(VH) | [(0.8,0.9,0.9,1.0;1),(0.85,0.9,0.9,0.95;0.9)] |
| High influence(H) | [(0.6,0.7,0.7,0.8;1),(0.65,0.7,0.7,0.75;0.9)] |
| Low influence (L) | [(0.4,0.5,0.5,0.6;1),(0.45,0.5,0.5,0.55;0.9)] |
| Very low influence (VL) | [(0.2,0.3,0.3,0.4;1),(0.25,0.3,0.3,0.35;0.9)] |
| No influence (No) | [(0,0.1,0.1,0.1;1),(0,0.1,0.1,0.05;0.9)] |
The risk factors are linked in such a way that they either influence or are influenced by one another. The following four symbols V, A, X, and O (Sayali Sandbhor 2019) are used to show the direction of the links between the two risk factors and.
-
(i).
V: To show a relationship from risk factor to risk factor but not vice versa; the relationship can be expressed as V followed by [Very high (VH), High (H), Low (L), Very low (VL)]. For example, V (VH) or V(H) or V(L) or V(VL).
-
(ii).
A: To show the relationship from risk factor to risk factor but not vice versa; the relationship can be expressed as A followed by [Very high (VH), High (H), Low (L), Very low (VL)].
-
(iii).
X: To show the relationship from risk factor to and risk factor to; the relationship can be expressed as X followed by [Very high (VH), High (H), Low (L), Very low (VL)].
-
(iv).
O: To show no existence of a relationship between two risk factors; the relationship can be represented as O followed by [No influence (No)].
3.1.2. Develop aggregated SSIM using a new double alpha-cut method
-
(i).
Develop aggregated fuzzy SSIM
The opinions of the experts on risk factors are collected. Then, the aggregated fuzzy SSIM is obtained according to Eq. (10).
| (10) |
-
(ii).
Develop aggregated fuzzy SSIM
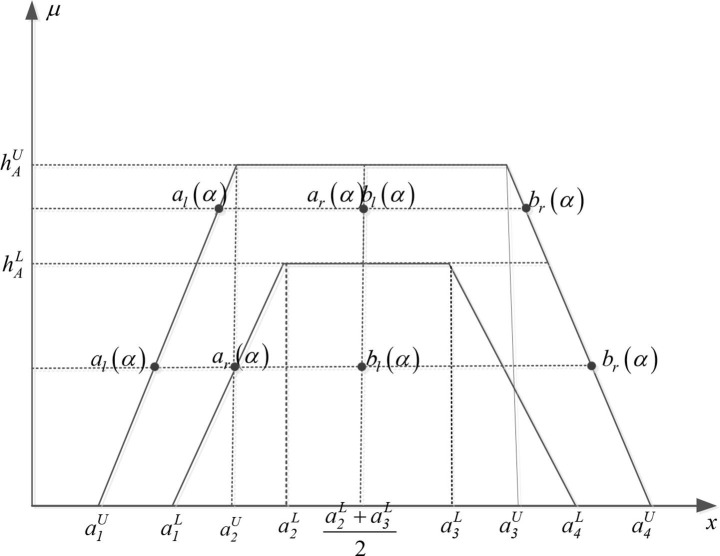
To establish an aggregated SSIM, the alpha-cut method is a method to deal with uncertainty, by which we can decompose the membership function of a fuzzy set into intervals (Rouhparvar and Panahi, 2015). The concept of alpha level sets of fuzzy sets was initiated by Nguyen (1978), regarded as a simple and effective way to convert fuzzy numbers into crisp values (Dymova et al., 2015, Liao et al., 2021, Yang et al., 2020). The most commonly used alpha-cuts of IT2FS are presented as Eq. (11) (Dymova, et al., 2015). Where and.
| (11) |
To avoid the overlap of the left and right intervals of the alpha-cuts of a IT2TrFN, Yang, et al. (2020) make a modification of and, which are defined as follows:
| (12) |
| (13) |
The lower and upper membership functions of IT2TrFNS are defined as follows:
| (14) |
| (15) |
The definition of the alpha-cuts of IT2TrFNs is depicted in Fig. 5 :
Fig. 5.
The alpha-cut of the IT2TrFNs.
A number of intermediate intervals could be obtained by cutting the membership functions by the alpha-cut. However, the widely used alpha-cuts of IT2TrFNs can only decompose the membership functions of a fuzzy set into intervals. As an important part of the TISM framework, the reachability matrix can help reflect the contextual relationships. To reach the reachability matrix with numerical values of 0 and 1, we refer to the idea of the double alpha-cut-based consensus measurement method in the study of Liao, et al. (2021) and propose a new double alpha-cut method to convert the IT2FNs in SSIM into crisp numbers. The specific steps are as follows:
The -cut set of IT2TrFN is defined as:
| (16) |
To demonstrate the characteristics of using double alpha-cut to deal with fuzzy information, a simple example is provided.
Example 1:Let an IT2TrFN. The membership functions, which have the domain,, of = 0.25, is.
As we can see from Example 1, the -cut set shows the distribution of the membership degrees corresponding to an IT2TrFN when is fixed as. Then, the second alpha-cut, -cut set is introduced as follows:
| (17) |
Example 2: In Example 1, is. Let be 0.1, 0.3 and 0.6 respectively. When = 0.1, both and are bigger than, so is 1. When = 0.3, although = 0.227 is smaller than 0.3, and is bigger than. Hence, is 1 as well. = 0.6, because both and are smaller than, is 0.
Based on the double alpha-cut proposed above, the IT2TrNs are defuzzified into 0 or 1. In this way, convert the information in into 1 and 0 to construct the aggregated SSIM.
| (18) |
3.1.3. Get hierarchical digraph based on bidirectional extraction method
-
(i).
Developing Reachability Matrix and transitivity check
Then, the aggregated SSIM matrix is turned into a reachability matrix. The final reachability is denoted as. A transitivity check among pairs of risk factors should be done simultaneously to avoid unnecessary iteration. 1* implies the transitivity between selected pairs of risk factors, which are changed from 0 to 1. Then, the final reachability matrix is obtained according to Eqs. (19), (20) (Warfield, 1974).
Let be a multiplying matrix which is defined as follows, where is an identity matrix:
| (19) |
| (20) |
-
(ii).
Reachability Matrix Partition—Bidirectional extraction
In this step, the final reachability matrix is partitioned at different levels. On the basis of the reachability matrix, a reachability set, an antecedent set and an intersection set are obtained, where. is the column set of the th row in the reachable matrix containing the element 1, is the set of rows with element 1 in the th column in the reachable matrix. The result-first hierarchy extraction rule is. The cause-first hierarchy extraction rule is. In a hierarchical diagram, the factors at the lowest level are the root causes and the factors at the top level are the output results. The factors at the middle level are the transition level, which are both causes and results. In order to keep all the root cause factors at the lowest level and the final result factors at the top level, this section defines a new bidirectional extraction method. The rotation extraction rule method is for the first iteration and for the second iteration; the rest should be deduced by analogy.
-
(iii).
Developing Skeleton Matrix
If there is a loop in the system, after the contraction processing is performed, all the forward edges of the contraction matrix obtained will be deleted. The resulting matrix is called the skeleton matrix. If the original matrix does not have loops, the skeleton matrix conforms to a simple algebraic formula.
| (21) |
-
(iv).
Creating Digraph for TISM
After determining the levels of risk factors, use the factors' serial number and the directional arrow to construct the relationships between the risk factors. The final TISM model shows all transitive links and direct influential links. Arrows point from lower-level factors to upper-level. It means that the lower-level factors have an influence on the upper-level factors.
3.2. The risk evaluation and analysis based on the fuzzy BN
The fuzzy BN is applied to analyze COVID-19 medical waste transportation risk factors quantitatively. IT2FNs is combined with BN to model the objective uncertainties caused by probabilistic variations of risk factors. The prior probabilities and the conditional probabilities are calculated according to the centroid of IT2FNs. BN is introduced to provide a description of risk factors and their interactions with graphical representations and evaluate the risk probability quantitatively.
3.2.1. Construct a BN and apply IT2TFNS to calculate the probabilities
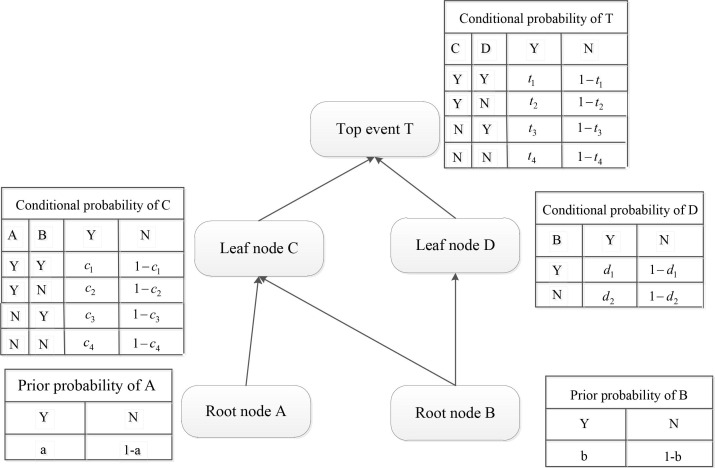
After obtaining the hierarchy diagram of risk factors, BN provides a graphical structure in a probabilistic approach based on the TISM digraph, including several nodes and the correlation between nodes. Netica software package, version 5.18, is utilized in this study to carry out the BN application, which is widely used in many studies (Fan et al., 2020, Fan et al., 2020, Sahin et al., 2019). Netica is practical software with an intuitive user interface that is great for BN applications. The most recent and quickest algorithms are utilized in conjunction with the networks to carry out various types of inference (Erkan, et al., 2021). The structure transformation of BN is shown in the Fig. 6 . The BN is composed of topological structure and conditional probability tables. Fig. 7 shows the particular example of BN with two root nodes, two leaf nodes and one top event.
Fig. 6.
Structure transformation of BN.
Fig. 7.
The particular example of BN.
To obtain the complete BN, experts are required to estimate the prior probabilities and conditional probabilities of nodes. In this paper, a five-level linguistic term is selected for expert expression, as shown in Table 1. To determine the probabilities of all nodes, the individual information of each expert should be aggregated firstly. For IT2FSs, a large variety of fuzzy power aggregation operators is suggested (Liu and Yu, 2014, Zhang, 2013). Among them, a traditional aggregation operator, named generalized weighted average (GWA) operator, is one of the most widely used operator for multiple attribute group decision making with fuzzy information (Chou and Cheng, 2012, Liu and Tang, 2016, Wang et al., 2016). It derives a group evaluation matrix based on the weights of each expert. The equation is shown below.
| (22) |
where represents the risk factors' probabilities evaluation provided by experts, represents the weights of the expert. Drawing the experience of the literature (Liu, 2011), take. The aggregation can be described as the following form:
| (23) |
where.
| (24) |
Next, the centroid of an IT2TrFN is applied to calculate the probabilities of the factors based on the aggregated evaluation information. Suppose the risk status of the risk factors are occurrence () and non-occurrence (), invite experts to give opinions on risk status according to Table 1.. The prior probabilities and conditional probabilities of risk factors are calculated according to the following equations. For an IT2TrFN, and can be derived according to the Eqs. (14), (15). The centroid of an IT2TrFN is the union of the centroids of all its embedded type-1 fuzzy sets. and represent the left and right endpoints of the centroid of an IT2TrFN.
| (25) |
Let represents the discretization of an IT2TrFN, the specific calculation formulas of and are defined as Eqs. (26), (27). The prior probabilities of root nodes and the conditional probabilities of leaf nodes can be calculated according to Eq. (28). Then, apply the probabilities to the Netica software.
| (26) |
| (27) |
| (28) |
3.2.2. Assess the risk probability of the top event.
BN provides a description of risk factors and their interconnections by graphical representations. Risk factor(s) at the top level (level I) should be called top event(s). The risk probability of the top event can be calculated by inputting the prior probabilities and the conditional probabilities of the antecedent set, as shown in Eq. (29).
| (29) |
where represents the probability of the top event, is the joint probability distribution of, which is an antecedent set of risk factors. is the conditional probability distribution.
3.2.3. Identify the sensitive factors
Sensitivity is used to measure the degree of influence of changes in the state of each risk factor on the change in the state of the top event. The sensitivity calculation can identify the risk factors that have a greater impact on the top event and should be controlled in the event development (Zhang, TerMaath, & Shields, et al., 2021). The equation is expressed as follows, where:
| (30) |
3.2.4. Perform the posterior causative diagnosis
According to Eq. (31), the posterior causative diagnosis is performed by backward inference of the BN, where . Suppose the top event is in the occurrence state, then calculate the posterior probability of each risk factor state (where is equal to or ). The higher the posterior probability at the state of risk factors, the higher the probability that these risk factors may cause the top event to be in the state. The posterior probability of each risk factor is ranked from largest to smallest. When the top event occurs, each risk factor is examined in turn.
| (31) |
4. The solution procedures for COVID-19 medical waste transportation risk
Based on the above research methodology for the medical waste transportation process, Section 4.1 presents the specific steps of the integrated risk evaluation model for COVID-19 medical waste transportation, which consists of three Stages as shown in Fig. 8 . Stage 1 is to identify risk factors and develop aggregated SSIM. Potential risk factors are identified and IT2FSs are applied to express the uncertainty in experts' evaluation. A new double alpha-cut of IT2FNs is first combined with TISM method to develop aggregated SSIM. Stage 2 is to construct a hierarchical digraph of risk factors. The type-2 fuzzy sets and a new bidirectional extraction method are combined with TISM method to construct the hierarchy diagram of risk factors. Stage 3 is to construct a BN and evaluate risks. The hierarchy diagram of risk factors is substituted into BN to describe the objective uncertainties caused by probabilistic variations of risk factors. The main characteristics of the integrated model are listed in Section 4.2.
Fig. 8.
The specific steps of the integrated risk evaluation model.
4.1. The specific steps of the integrated model
Stage 1: Identify risk factors and develop aggregated SSIM.
Step 1.1: Identify potential risk factors.
The first step is to recognize all potential risk factors of medical waste transportation. A set of risk factors is established as. represents experts who provide the evaluation of the risk factors' relationships.
Step 1.2: Define the contextual relationship between factors by IT2TFS.
The contextual relationship between factors is gathered from a group of experts. The direction of the relationship between the two factors and can be denoted by the following four symbols V, A, X and O and the linguistic terms of IT2TrFNs. The evaluation matrix can be expressed as.
Step 1.3: Develop aggregated fuzzy SSIM.
The aggregated fuzzy SSIM matrix is obtained according to Eq. (10).
Step 1.4: Develop aggregated SSIM using the double alpha-cut of IT2TrFNs.
Then, the aggregated SSIM with crisp numbers can be obtained based on the double alpha-cut of IT2TrFNs, using Eq. (18).
Step 1.5: Calculate the final reachability matrix.
The final reachability is calculated by using Eqs. (19), (20). Then, a transitivity check among pairs of factors should be done simultaneously to avoid unnecessary iteration.
Step 1.6: Partition the levels of risk factors.
Based on the reachability matrix, the levels of factors are determined according to the bidirectional extraction method; the rule is for the first iteration, for the second iteration and the rest be deduced by analogy.
Step 1.7: Develop the skeleton matrix.
If the original matrix does not have loops, the skeleton matrix can be obtained by using Eq. (21).
Step 1.8: Creating a hierarchical digraph of risk factors.
After determining the levels of risk factors, the final TISM uses a directional arrow to construct the relationship between the factors shown in the skeleton matrix. The hierarchical digraph of risk factors is created.
Stage2: Construct a BN and evaluate risks.
Step 2.1: Construct a BN.
After obtaining the hierarchy diagram of risk factors, the BN is constructed according to the transformation rules shown in Fig. 6.
Step 2.2: Express the probabilities of risk factors using IT2TrFNs.
After obtaining the hierarchical digraph, experts give evaluation opinions on the probabilities of risk factors by using the linguistic terms of IT2TrFNs shown in Table 1.
Step 2.3: Calculate the probabilities according to the centroid of IT2TrFNs.
The prior probabilities of root nodes and the conditional probabilities of leaf nodes are calculated according to the centroid of IT2TrFNs, using Eqs. (22), (23), (24), (25), (26), (27), (28).
Step 2.4: Assess the risk probability of the top event.
Based on the prior probabilities and conditional probabilities, the risk probability of the top event is obtained by using Eq. (29).
Step 2.5: Identify the sensitive factors.
Set the probability value of the node state for each risk factor to 1 and 0 respectively, represents the occurrence and non-occurrence of each risk factor, record the probability value of the top event. Then, calculate the sensitivity of each risk factor according to Eq.(30).
Step 2.6: Diagnose the event causation.
Set the probability of risk occurrence of the top event as 1, and obtain the posterior probability of each node to diagnose the event causation by using Eq. (31).
4.2. The main characteristics of the integrated model
The integrated model for COVID-19 medical waste transportation based on extended fuzzy TISM and fuzzy BN has been described above. This model can help analyze the risk factors in the medical waste transportation process under high uncertain environment, identify the sensitive factors and diagnose the event causation. The main characteristics are summarized below:
-
(i).
The COVID-19 pandemic is an emergency without sufficient historical data. The evaluation of COVID-19 medical waste transportation risk requires the support of experts in related fields. The proposed model considers the ambiguous evaluation information expressed by experts; introduces the linguistic terms and corresponding IT2FNs to avoid the omission and distortion of evaluation information under uncertain environments.
-
(ii).
Considering the interaction relationships between/among risk factors, TISM is combined with IT2FSs to analyze the contextual relationships of risk factors under uncertain environment. Moreover, a new double alpha-cut is proposed to defuzzificate the IT2FNs in the process of constructing the aggregated SSIM to help obtain a hierarchical digraph of risk factors.
-
(iii).
A new bidirectional extraction method is first developed to partition the levels of risk factors in the process of TISM. The bidirectional extraction method can reflect the dialectical relationship between causes and results more realistic and effective.
-
(iv).
After obtaining the hierarchical digraph of risk factors by using the extended fuzzy TISM method, the digraph is transformed into a BN to make a comprehensive risk evaluation. Moreover, the prior probabilities and conditional probabilities of risk factors are expressed by IT2FNs.
5. Case study
In this section, a case study of the COVID-19 medical waste transportation process at Lukou international airport in Nanjing is proposed to demonstrate the effectiveness and advantages of the proposed model. The detailed description and the calculation process of the case are shown as follows:
5.1. The detailed description of the case in Nanjing
On July 20, 2022, 9 samples were found to be positive in a routine nucleic acid test conducted at Lukou international airport in Jiangning District, Nanjing, all of which were airport cleaners. As of 24:00 on July 25, this round of Nanjing epidemic has affected 5 provinces and 9 cities. As of 24:00 on July 27, Nanjing has reported a total of 153 local confirmed cases and 2 local asymptomatic infections. The new cases are mainly concentrated in Lukou Airport and surrounding areas, and many cluster outbreaks have been found.in the reported cases. The initial COVID-19 virus in Nanjing was caused by the cleaner who cleaned the cabin of the CA910. The handling of the protective clothing after work was not standardized, which caused the individual infection and spread among the cleaners. Some other airport workers were infected by contact with cleaners or the polluted environment. Since corona virus has a high degree of spatial infectious, latent and viral, handling the protective clothing can also be regarded as part of the medical waste transportation process. Therefore, we take this Nanjing epidemic as the background to assess the risk of medical waste transportation.
5.2. The calculation process of the case study
Stage 1: Identify risk factors and develop aggregated SSIM.
Step 1.1: Identify potential risk factors.
Three relevant experts are invited to evaluate the risk factors' relationships. The three experts with different backgrounds and fields are selected to establish the expert group.
Table 2 shows the description of the three experts. Experts and are both from Zhongda Hospital Southeast University, is a doctor in the hospital's respiratory medicine department, is a supervisor of the hospital. Expert is a transportation worker responsible for the transportation of hospital medical waste. The three experts are suggested to give evaluation information in terms of linguistic terms, which is shown in Table 1.
Table 2.
The description of experts.
| Experts ID | Position | Age | Working experience |
|---|---|---|---|
| Doctor | 43 | 13 | |
| Supervisor | 37 | 9 | |
| Transportation worker | 35 | 10 |
COVID-19 medical waste must be transported by special employee and vehicles. Employee must take standard precautions as required, such as medical surgical masks, gloves and work clothes. Personnel entering the isolation ward to collect medical waste should take precautions according to the requirements of the employee entering the area. Therefore, possible risks are the risk of employee infection and the risk of inadequate personal protection of employee. At the same time, the storage of COVID-19 medical waste in the special area of medical institutions shall not be mixed with other medical waste and domestic waste, and should be marked with “highly infectious waste” identification signs and strict sealing measures should be adopted. Medical institutions should hand over the new crown medical waste to the medical waste disposal unit for disposal on the same day, specify the person responsible for management. According to the above transportation characteristics and the literature related to transportation risks, we can obtain 16 risk factors as shown in Table 3 .
Table 3.
The descriptions of risk factors.
| number | Risk factors | Literature support |
|---|---|---|
| Employee infection risk | (Akpieyi et al., 2015, Kumar et al., 2015) | |
| Low employee safety awareness | (Manupati, et al., 2021) | |
| Improper operation by employee | (Huang et al., 2020, Kumar et al., 2015, Manupati et al., 2021) | |
| Inadequate personal protection of employee | (Huang et al., 2020, Ouyang et al., 2021) | |
| Improper disinfection of transfer tools | (Akpieyi et al., 2015, Manupati et al., 2021) | |
| Unsafe handling equipment | (Huang et al., 2020, Kumar et al., 2015) | |
| Unreasonable collection and transportation of medical waste containers | (Ouyang, et al., 2021) | |
| Irregular construction of temporary storage sites for medical waste | (Taslimi, et al., 2020) | |
| Unreasonable location of storage location | (Kumar et al., 2015, Taslimi et al., 2020) | |
| Failure to conduct regular health checkups on relevant personnel | (Akpieyi et al., 2015, Manupati et al., 2021) | |
| Insufficient technical training | (Ouyang et al., 2021, Song et al., 2020) | |
| Lack of safety education | (Huang et al., 2020, Makan and Fadili, 2020) | |
| Insufficient accountability system | (Makan and Fadili, 2020, Song et al., 2020) | |
| Insufficient emergency response mechanism for safety management | (Huang et al., 2020, Makan and Fadili, 2020) | |
| Insufficient supervision of collection and disposal | (Makan and Fadili, 2020) | |
| Harsh processing environment | (Huang, et al., 2020) |
Step 1.2: Define the contextual relationship between factors by IT2TFS.
Define the contextual relationship between factors by IT2TFS.
The relationship between the factors is gathered from a group of three experts. The evaluation matrix represents the direction of the relationship between the two factors and given by the expert, which is shown in Table 4 .
Table 4.
The fuzzy SSIM matrix by expert.
| A(VL) | O(No) | A(H) | O(No) | O(No) | O(No) | A(H) | O(No) | A(L) | A(H) | A(VH) | A(VH) | A(VH) | A(L) | O(No) | |
| O(No) | O(No) | O(No) | A(H) | A(VH) | A(L) | V(H) | O(No) | O(No) | V(L) | O(No) | V(H) | V(VH) | V(L) | ||
| O(No) | O(No) | O(No) | A(H) | A(H) | A(H) | O(No) | A(H) | O(No) | V(L) | O(No) | V(H) | O(No) | |||
| O(No) | A(H) | O(No) | A(H) | A(VH) | A(L) | O(No) | O(No) | O(No) | O(No) | O(No) | O(No) | ||||
| O(No) | A(H) | O(No) | A(VH) | A(VH) | A(H) | O(No) | O(No) | O(No) | O(No) | O(No) | |||||
| O(No) | O(No) | O(No) | O(No) | O(No) | O(No) | O(No) | A(L) | A(L) | O(No) | ||||||
| O(No) | A(VH) | O(No) | A(VH) | A(H) | A(H) | O(No) | O(No) | O(No) | |||||||
| O(No) | O(No) | O(No) | A(L) | A(H) | O(No) | O(No) | O(No) | ||||||||
| O(No) | O(No) | O(No) | A(H) | A(H) | O(No) | O(No) | |||||||||
| O(No) | O(No) | O(No) | A(L) | A(VH) | O(No) | ||||||||||
| O(No) | O(No) | O(No) | O(No) | O(No) | |||||||||||
| V(L) | V(L) | V(H) | O(No) | ||||||||||||
| O(No) | A(H) | O(No) | |||||||||||||
| O(No) | O(No) | ||||||||||||||
| O(No) |
Step 1.3: Develop aggregated fuzzy SSIM.
The aggregated fuzzy SSIM matrix is obtained according to Eq. (10). Table A1 (see Appendix A) shows the detailed results.
Step 1.4: Develop aggregated SSIM using the double alpha-cut of IT2TrFNs.
The aggregated SSIM can be obtained based on the double alpha-cut of IT2TrFNs,using Eq. (18). Table A2 (see Appendix A) shows the detailed results.
Step 1.5: Calculate the final reachability matrix.
The final reachability is calculated by using Eqs. (19), (20). A transitivity check among pairs of factors should be done simultaneously to avoid unnecessary iteration. Table A3 (see Appendix A) presents the aggregated SSIM after transitivity check. Then, the final reachability is calculated by using Eqs. (19), (20) as shown in Table 5 .
Table 5.
The final reachability.
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 1 | 1 | 1 | 1 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | |
| 1 | 0 | 1 | 0 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Step 1.6: Partition the levels of factors.
The levels of factors are determined according to the bidirectional extraction method. Table 6 presents the calculation steps of the bidirectional extraction method.
Table 6.
The bidirectional extraction.
| Variables | Reachability set | Antecedent set | Intersection set | Level |
|---|---|---|---|---|
| (a):Iteration-1 | ||||
| 1 | 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16 | 1 | 1 | |
| 1,2,3,4,5,10 | 2,11,12,13,15 | 2 | ||
| 1,3,5 | 2,3,11,12,13,15,16 | 3 | ||
| 1,4 | 2,4,11,12,13,15 | 4 | ||
| 1,5 | 2,3,5,11,12,13,15,16 | 5 | ||
| 1,6 | 6,9,12,13,15,16 | 6 | ||
| 1,7 | 7,11,12,13,15 | 7 | ||
| 1,8 | 8,12,13,15 | 8 | ||
| 1,6,9 | 9,12,13,15 | 9 | ||
| 1,10 | 2,10,11,12,13,15 | 10 | ||
| 1,2,3,4,5,7,10,11 | 11 | 11 | ||
| 1,2,3,4,5,6,7,8,9,10,12,13,14,15,16 | 12 | 12 | ||
| 1,2,3,4,5,6,7,8,9,10,13 | 12,13 | 13 | ||
| 1,14 | 12,14 | 14 | ||
| 1,2,3,4,5,6,7,8,9,10,13,15 | 12,13,15 | 13,15 | ||
| 1,3,5,6,16 | 12,16 | 16 | ||
| (b):Iteration-2 | ||||
| 2,3,4,5,10 | 2,11,12,13,15,16 | 2 | ||
| 3,5 | 2,3,11,12,13,15,16 | 3 | ||
| 4 | 2,4,11,12,13,15 | 4 | ||
| 5 | 2,3,5,11,12,13,15,16 | 5 | ||
| 6 | 6,9,12,13,15,16 | 6 | ||
| 7 | 7,11,12,13,15 | 7 | ||
| 8 | 8,12,13,15 | 8 | ||
| 6,9 | 9,12,13,15 | 9 | ||
| 10 | 2,10,11,12,13,15 | 10 | ||
| 2,3,4,5,7,10,11 | 11 | 11 | II | |
| 2,3,4,5,6,7,8,9,10,12,13,14,15,16 | 12 | 12 | II | |
| 2,3,4,5,6,7,8,9,10,13 | 12,13 | 13 | ||
| 14 | 12,14 | 14 | ||
| 2,3,4,5,6,7,8,9,10,13,15 | 12,13,15 | 13,15 | ||
| 3,5,6,16 | 12,16 | 16 | ||
| (c):Iteration-3 | ||||
| 2,3,4,5,10 | 2, 13,15,16 | 2 | ||
| 3,5 | 2,3,13,15,16 | 3 | ||
| 4 | 2,4,,13,15 | 4 | III | |
| 5 | 2,3,5,13,15,16 | 5 | III | |
| 6 | 6,9,,13,15,16 | 6 | III | |
| 7 | 7,13,15 | 7 | III | |
| 8 | 8,13,15 | 8 | III | |
| 6,9 | 9,13,15 | 9 | ||
| 10 | 2,10,13,15 | 10 | III | |
| 2,3,4,5,6,7,8,9,10,13 | 13 | 13 | ||
| 14 | 14 | 14 | III | |
| 2,3,4,5,6,7,8,9,10,13 | 13,15 | 13 | ||
| 3,5,6,16 | 16 | 16 | ||
| (d):Iteration-4 | ||||
| 2,3, | 2,13,15,16 | 2 | ||
| 3, | 2,3,13,15,16 | 3 | ||
| 9 | 9,13,15 | 9 | ||
| 2,3,9,13 | 13 | 13 | IV | |
| 2,3,9,13,15 | 13,15 | 13,15 | IV | |
| 3, 16 | 16 | 16 | IV | |
| (e):Iteration-5 | ||||
| 2,3, | 2 | 2 | ||
| 3, | 2,3, | 3 | V | |
| 9 | 9, | 9 | V | |
| (f):Iteration-6 | ||||
| 2 | 2 | 2 | VI | |
Step 1.7: Develop the skeleton matrix.
If the original matrix does not have loops, the skeleton matrix in Table A4 (see Appendix A) is obtained according to Eq. (21).
Step 1.8: Creating a hierarchical digraph of risk factors.
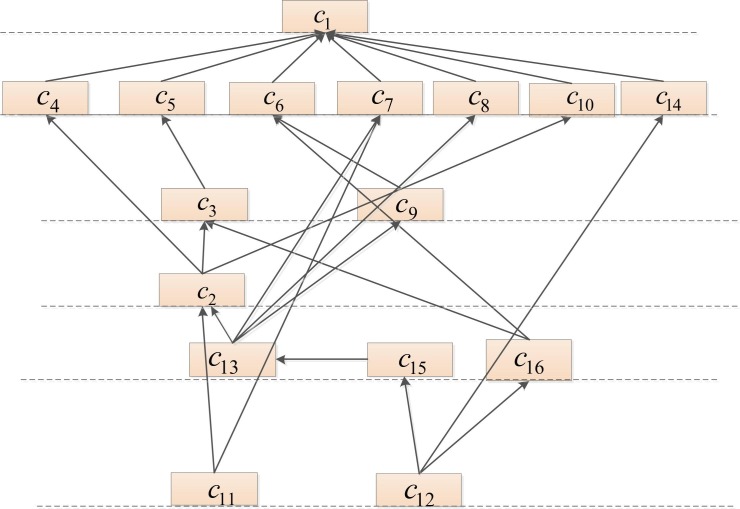
The level of each risk factor is determined through bidirectional extraction. Element 1 in the skeleton matrix determines where the arrow is pointing. Based on Table 6 and Table A4, the final TISM model is described in Fig. 9 .
Fig. 9.
The final TISM digraph.
Step 2: Construct a BN and evaluate risks.
Step 2.1: Construct a BN.
The BN structure is obtained based on the final TISM digraph.
Step 2.2: Express the probabilities of risk factors using IT2TrFNs.
The final TISM digraph is transformed into BN according to the corresponding relationship in Fig. 6. After obtaining the BN graphical structure, experts give evaluation opinions on the risk factors by using linguistic terms shown in Table 1. (Employee infection risk) is the top event.
Step 2.3: Calculate the probabilities according to the centroid of IT2TrFNs.
The prior probabilities and conditional probabilities for each sub-indicator in the BN are determined by experts' evaluation. The average probability of fuzzy occurrence for each factor is calculated according to the centrality calculation of IT2FNs. The and need to calculate the prior probabilities because the two nodes belong to root nodes, the results are shown in Table 7 and Table 8 . The risk status of the risk factors are occurrence () and non-occurrence (), three experts are invited to give evaluation opinions on the risk status of the root nodes and in the BN structure.
Table 7.
The evaluation of root nodes.
| Root nodes | |||
|---|---|---|---|
| VH | VH | H | |
| VH | H | H |
Table 8.
The aggregated evaluation matrix of root nodes.
| Root nodes | The aggregated evaluation |
|---|---|
| [(0.7333,0.8333,0.8333,0.9333;1.0),(0.7833,0.8333, 0.8333,0.8833;0.9)] | |
| [(0.6667,0.7667,0.7667,0.8667;1.0),(0.7167,0.7667,0.7667,0.8167;0.9)] |
Assuming that three experts are given the same weight, that is, is assigned 1/3 in Eq. (23). The aggregated evaluation matrix is shown in the table below.
Based on the aggregated evaluation matrix, the prior probabilities of and are calculated according to Eqs. (25), (26), (27), (28), respectively as below:
In the same way, the conditional probabilities of other leaf nodes are calculated based on the expert's linguistic variable evaluation value.
Step 2.4: Assess the risk probability of the top event.
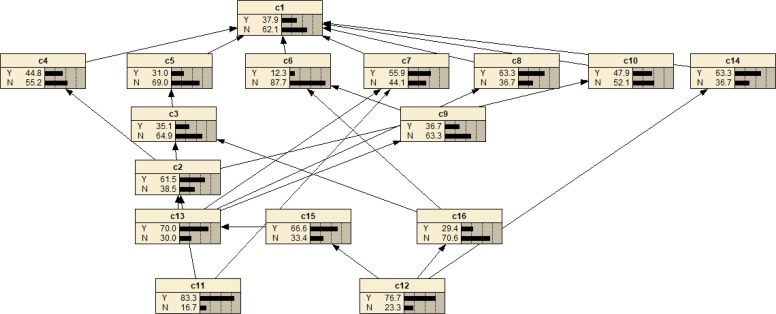
According to the prior probabilities of root nodes and conditional probabilities of leaf nodes, the BN is drawn on a visual interface in the Netica software. Through BN forward inference, the probability of occurrence for each risk factor is derived, and the calculation results are shown in Fig. 10 . The occurrence probability of the top event (medical waste transportation risk accident) is 0.379, which is relatively high. Therefore, it is necessary to study the causative factors leading to the top event to avoid the occurrence of larger accidents.
Fig. 10.
The occurrence probability of the top event.
Step 2.5: Identify the sensitive factors.
Based on the BN structure, risk factors can be expressed as an antecedent set of variables. In Netica software, the state of each risk factors in antecedent set is set to 1 and 0 respectively, record the probability value of the top event. The sensitivity of risk factors, which is the probability of top event when the factor occurs() minus the probability of when the factor does not occur (). The results are shown in Table 9 .
Table 9.
The sensitivity of risk factors.
| Risk factor | Rank | |||
|---|---|---|---|---|
| 0.452 | 0.267 | 0.185 | 3 | |
| 0.454 | 0.345 | 0.109 | 5 | |
| 0.548 | 0.242 | 0.306 | 1 | |
| 0.542 | 0.306 | 0.236 | 2 | |
| 0.488 | 0.364 | 0.124 | 4 | |
| 0.409 | 0.342 | 0.067 | 8 | |
| 0.386 | 0.368 | 0.018 | 11 | |
| 0.389 | 0.374 | 0.015 | 14 | |
| 0.4 | 0.356 | 0.044 | 10 | |
| 0.396 | 0.295 | 0.101 | 6 | |
| 0.383 | 0.367 | 0.016 | 13 | |
| 0.404 | 0.32 | 0.084 | 7 | |
| 0.385 | 0.369 | 0.016 | 12 | |
| 0.381 | 0.379 | 0.002 | 15 | |
| 0.416 | 0.364 | 0.052 | 9 |
In view of the findings, the top event (employee infection risk) increased obviously since the state of risk factors changed respectively. The sensitivity of risk factor is highest, which is 0.306. (Inadequate personal protection of employees) is the most sensitive factor, which means that is a crucial control risk factor in the transportation of medical waste. According to relevant news, the COVID-19 outbreak in Lukou international airport caused the employee infection by improper self-protection of the cleaning staff. Therefore, in the process of medical waste transportation and disposal, we should focus on controlling this risk factor, and minimize the possibility of this risk factor through control, to avoid the occurrence of employee infection.
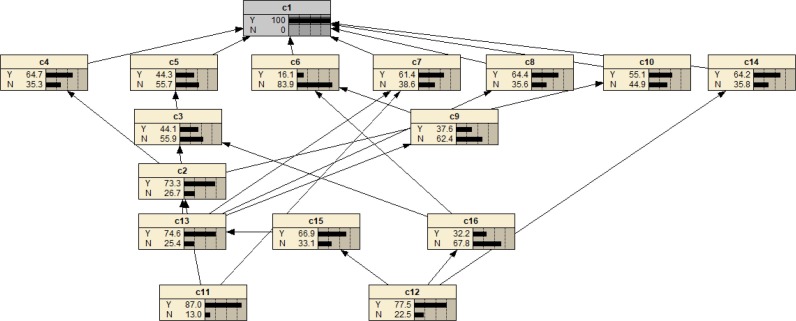
Step 2.6: Diagnose the event causation.
Set the occurrence probability of the top event as 1, and derive the posterior probability of each factor through BN backward inference, and the results are shown in Fig. 11 .
Fig. 11.
The event causation diagnosis.
It can be seen from Fig. 11 that the largest accident causal chains are (Lack of safety education → Insufficient supervision of collection and disposal → Insufficient accountability system → Low employee safety awareness → Inadequate personal protection of employees → Employee infection risk) and (Insufficient technical training → Low employee safety awareness → Inadequate personal protection of employees → Employee infection risk). The risk factors on the largest causal chains are important factors leading to the top event (Employee infection risk). Therefore, in the safety management of the medical waste transportation process, the above factors should be mainly controlled.
According to a report from Website of the Central Commission for Discipline Inspection and State Supervision Commission (https://www.ccdi.gov.cn/pln/202107/t20210728_142075.html), Lukou international airport had problems such as lack of supervision and unprofessional management; various measures for epidemic prevention and control have not been implemented in detail, resulting in the spread of the COVID-19 epidemic. Moreover, the airport had the problem of unprofessional management After the discovery of positive samples, the prevention and control management of relevant personnel at the airport was not in place, which led to the spread of the epidemic. The causal chains and critical factors identified by the proposed model are consistent with this report. Moreover, we also identified several other cause factors, such as lack of safety education and low employee safety awareness. The obtained results prove the feasibility and effectiveness of the proposed model and provide a reference for preventing the occurrence of similar accidents.
6. Comparisons analysis
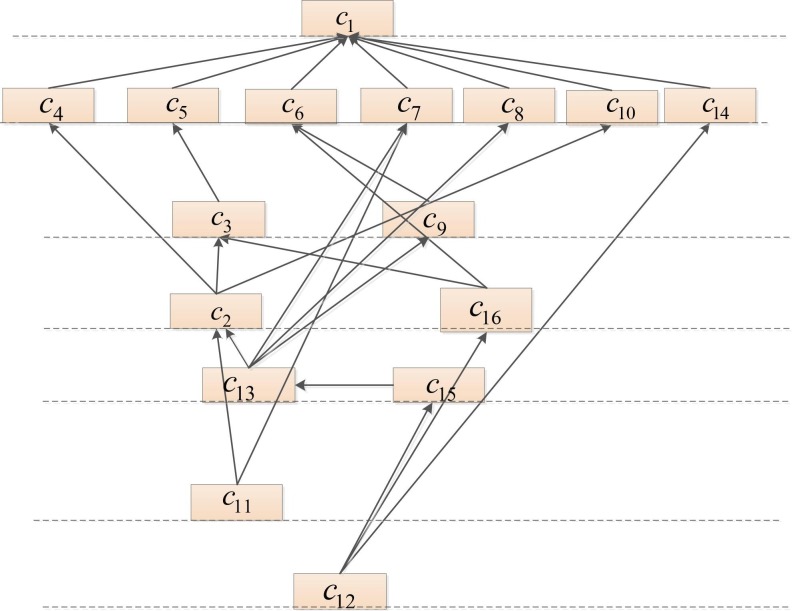
In this section, a comparison of our proposed model with traditional TISM and BN model is conducted. We substitute the data in the case study into the traditional TISM model. The level of each risk factor is determined through the result-first hierarchy extraction rule. The result-first hierarchy extraction rule is. Fig. 12 shows the digraph obtained from traditional TISM.
Fig. 12.
The digraph obtained from traditional TISM.
Then the TISM digraph is transformed into BN to make comprehensive risk analysis. Referring from the traditional BN (Wang, et al., 2022), the prior and conditional probabilities of risk factors are given by the experience of experts, represented by crisp numbers. Calculate the average of the probabilities given by the three experts. For example, the conditional probabilities of , the prior probabilities of are depicted in Table 10 and Table 11 .
Table 10.
The prior probabilities of.
| 0.7 | 0.6 | |
| 0.3 | 0.4 |
Table 11.
The conditional probabilities of.
| 0.767 | 0.233 | ||
| 0.483 | 0.517 | ||
| 0.35 | 0.65 | ||
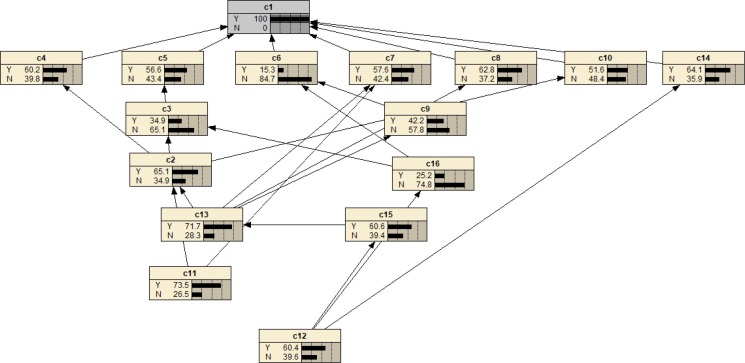
| 0.216 | 0.784 |
From Fig. 13 , we can conclude that the largest causal chains are (Lack of safety education → Insufficient emergency response mechanism for safety management → Employee infection risk). It can be seen that compared with the results obtained by the proposed model, many risk factors are lost in the accident causal chain obtained by the traditional BN model. The event causation diagnosis based on traditional BN is inconsistent with the mentioned factors in the report from Website of the Central Commission for Discipline Inspection and State Supervision Commission. The fuzzy BN proposed in this paper can provide a more complete and realistic accident causal chain because the IT2FNs can retain more uncertain information in the expert evaluation. At the same time, the hierarchical digraph obtained using traditional TISM has seven levels. and are both root factors, without being placed on the same level. It shows that the traditional hierarchical extraction method is not as effective as the bidirectional extraction method in reflecting the relationship between risk factors.
Fig. 13.
The event causation diagnosis based on traditional BN.
Therefore, the differences in results calculated by the traditional model and our proposed model are mainly in the following aspects. (i) In the practical BN application, the risk evaluation information is often uncertain and imprecise on account of the incomplete and inaccurate information, required knowledge and capability of experts. We combine the IT2FNs with TISM and BN, considering the uncertainty evaluation information, reflecting the relationship between/among risk factors more accurately. (ii) We propose a new hierarchical extraction method to conduct the hierarchy digraph. And the cause and effect elements are separated in the resulting hierarchy, making the hierarchical relationship between risk factors clearer. (iii) A new double alpha-cut is proposed to defuzzificate the IT2FNs in the process of constructing the aggregated SSIM to help obtain a hierarchical digraph of risk factors.
7. Conclusion
The risk identification and evaluation of COVID-19 medical waste transportation can effectively prevent potential infection accidents. IT2FNs are adopted to reflect the subjectivity under uncertain environments. The TISM is combined with IT2FNs to obtain a hierarchical digraph, which shows the relationships between risk factors, enhancing the understanding of complex accident systems and providing assistance in accident prevention. The hierarchical digraph obtained by fuzzy TISM is mapped to BN, assesses the occurrence probability of the top event using IT2TFS, identifies the sensitive factors and performs the posterior causative diagnosis. The feasibility of the integrated model is verified through the case study.
The case of COVID-19 medical waste transportation process in Nanjing selects 16 risk factors and constructs a hierarchical digraph based on the extended fuzzy TISM method. Then, the hierarchical digraph is transformed into BN, the prior probabilities of root nodes and conditional probabilities of leaf nodes are determined. The sensitive factors are identified by setting the occurrence probability of the risk factor to 1. The posterior probabilities of risk factors through BN backward inference is obtained by setting the occurrence probability of the top event as 1. The risk factor (0.306) is the most sensitive factor, also in the largest accident causal chains, which means (inadequate personal protection of employees) is a crucial control risk factor in medical waste transportation process. The results can provide a reference for preventing the occurrence of similar accidents.
The limitations of the proposed model mainly include two aspects. (i) The integrated model does not consider the significance of experts, which means that we have ignored the influences of the relative weights of experts on risk evaluation. (ii) The integrated model is failed to describe the dynamic situations when experts' opinions change. Further, the integrated model will be extended to cover some generalized aggregation operators to calculate the different weights of experts under uncertain environment. Henceforth, we will introduce some dynamic simulation techniques to fit dynamic situations in application better.
CRediT authorship contribution statement
Jing Tang: Conceptualization, Methodology, Validation, Formal analysis, Writing – original draft, Visualization. Xinwang Liu: Writing – review & editing, Supervision, Project administration, Funding acquisition. Weizhong Wang: Methodology, Validation, Data curation, Writing – original draft, Visualization.
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgment
This work was supported by the National Science Foundation of China (NSFC) (72071045, 71771051 and 72101004).
Appendix A.
In this appendix, we present detailed results about aggregated fuzzy SSIM matrix, aggregated SSIM, aggregated SSIM after transitivity check and the skeleton matrix of TISM method.
Table A1.
The aggregated fuzzy SSIM matrix.
| 0 | No | No | No | No | No | No | No | No | No | No | No | No | No | No | No | |
| No | 0 | L | VH | H | No | L | No | No | H | No | No | No | No | No | No | |
| L | No | 0 | No | H | No | L | No | No | No | No | No | No | No | No | No | |
| VH | No | No | 0 | No | No | No | No | No | No | No | No | No | No | No | No | |
| VH | No | No | No | 0 | No | No | No | No | No | No | No | No | No | No | No | |
| VH | No | No | No | No | 0 | No | No | No | No | No | No | No | No | No | No | |
| H | No | No | No | No | No | 0 | No | No | No | No | No | No | No | No | No | |
| L | No | No | No | No | L | No | 0 | No | No | No | No | No | No | No | No | |
| No | No | H | No | No | L | No | No | 0 | No | No | No | No | No | No | No | |
| H | No | No | No | No | No | No | No | No | 0 | No | No | No | No | No | No | |
| No | L | H | L | H | No | H | No | No | No | 0 | No | No | No | No | No | |
| No | VH | H | VH | VH | No | H | H | H | VH | No | 0 | No | H | L | L | |
| No | H | H | H | VH | No | VH | L | H | L | No | No | 0 | No | No | No | |
| H | No | No | No | No | No | No | No | No | No | No | No | No | 0 | No | No | |
| No | No | No | H | H | No | VH | No | No | No | No | No | H | No | 0 | No | |
| VL | No | H | No | No | L | No | No | No | No | No | No | No | No | No | 0 |
Table A2.
The aggregated SSIM.
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 1 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 1 | 1 | 1 | |
| 0 | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | |
| 0 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Table A3.
The aggregated SSIM after transitivity check.
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1* | 0 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1* | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1* | 1 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1* | 1 | 1 | 1 | 1 | 1* | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 1 | 1 | 1 | |
| 1* | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1* | 0 | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | |
| 1* | 0 | 1 | 0 | 1* | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Table A4.
The skeleton matrix.
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | |
| 0 | 1 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | |
| 0 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Data availability
Data will be made available on request.
References
- Abbassinia M., Kalatpour O., Motamedzade M., Soltanian A., Mohammadfam I. Dynamic Human Error Assessment in Emergency Using Fuzzy Bayesian CREAM. Journal of Research in Health Sciences. 2020;20:e00468. doi: 10.34172/jrhs.2020.03. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Abdullah L., Najib L. A new type-2 fuzzy set of linguistic variables for the fuzzy analytic hierarchy process. Expert Systems with Applications. 2014;41:3297–3305. [Google Scholar]
- Ahmad F., Ahmad S., Zaindin M. Sustainable production and waste management policies for COVID-19 medical equipment under uncertainty: A case study analysis. Computers & Industrial Engineering. 2021;157 doi: 10.1016/j.cie.2021.107381. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Akpieyi A., Tudor T.L., Dutra C. The utilisation of risk-based frameworks for managing healthcare waste: A case study of the National Health Service in London. Safety Science. 2015;72:127–132. [Google Scholar]
- Bapin Y., Zarikas V. Smart Building’s Elevator with Intelligent Control Algorithm based on Bayesian Networks. International Journal of Advanced Computer Science and Applications. 2019;10:16–24. [Google Scholar]
- Boukezzoula R., Coquin D. A decision-making computational methodology for a class of type-2 fuzzy intervals: An interval-based approach. Information Sciences. 2020;510:256–282. [Google Scholar]
- Celik E., Akyuz E. Application of interval type-2 fuzzy sets dematel methods in maritime transportation: The case of ship collision. International Journal of Maritime Engineering. 2016;158:A359–A371. [Google Scholar]
- Chen C., Chen J., Fang R., Ye F., Yang Z., Wang Z.…Tan W. What medical waste management system may cope With COVID-19 pandemic: Lessons from Wuhan. Resources, Conservation and Recycling. 2021;170 doi: 10.1016/j.resconrec.2021.105600. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Chou W.-C., Cheng Y.-P. A hybrid fuzzy MCDM approach for evaluating website quality of professional accounting firms. Expert Systems with Applications. 2012;39:2783–2793. [Google Scholar]
- Dymova L., Sevastjanov P., Tikhonenko A. An interval type-2 fuzzy extension of the TOPSIS method using alpha cuts. Knowledge-Based Systems. 2015;83:116–127. [Google Scholar]
- Eren E., Tuzkaya U.R. Safe distance-based vehicle routing problem: Medical waste collection case study in COVID-19 pandemic. Computers & Industrial Engineering. 2021;157 doi: 10.1016/j.cie.2021.107328. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Erkan C., Coskan S., Remzi F. An analysis of severity of oil spill caused by vessel accidents. Transportation Research Part D. 2021;90 [Google Scholar]
- Fan S., Blanco-Davis E., Yang Z., Zhang J., Yan X. Incorporation of human factors into maritime accident analysis using a data-driven Bayesian network. Reliability Engineering & System Safety. 2020;203 [Google Scholar]
- Fan S., Zhang J., Blanco-Davis E., Yang Z., Yan X. Maritime accident prevention strategy formulation from a human factor perspective using Bayesian Networks and TOPSIS. Ocean Engineering. 2020;210 [Google Scholar]
- Ghasemi F., Ghasemi A., Kalatpour O. Prediction of human error probability during the hydrocarbon road tanker loading operation using a hybrid technique of fuzzy sets, Bayesian network and CREAM. International Journal of Occupational Safety and Ergonomics. 2021:1–11. doi: 10.1080/10803548.2021.1889877. [DOI] [PubMed] [Google Scholar]
- Govindan K., Nasr A.K., Mostafazadeh P., Mina H. Medical waste management during coronavirus disease 2019 (COVID-19) outbreak: A mathematical programming model. Computers & Industrial Engineering. 2021;162 doi: 10.1016/j.cie.2021.107668. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Guo X., Jie J., Khan F., Ding L. Fuzzy bayesian network based on an improved similarity aggregation method for risk assessment of storage tank accident. Process Safety and Environmental Protection. 2020;144:242–252. [Google Scholar]
- Hendiani S., Jiang L.S., Sharifi E., Liao H.C. Multi-expert multi-criteria decision making based on the likelihoods of interval type-2 trapezoidal fuzzy preference relations. International Journal of Machine Learning and Cybernetics. 2020;11:2719–2741. [Google Scholar]
- Hong P.X., Ming W.Y., Sang C.K. A large-scale group decision-making method for site selection of waste to energy project under interval type-2 fuzzy environment. Sustainable Cities and Society. 2021;71 [Google Scholar]
- Huang W., Zhang Y., Kou X., Yin D., Mi R., Li L. Railway dangerous goods transportation system risk analysis: An Interpretive Structural Modeling and Bayesian Network combining approach. Reliability Engineering & System Safety. 2020;204 [Google Scholar]
- Jin F., Liu J., Chen H., Langari R. Interval Type-2 Trapezoidal Fuzzy Decision- Making Method With Consistency-Improving Algorithm and DEA Model. IEEE Access. 2020;8:120456–120472. [Google Scholar]
- Karmaker C.L., Ahmed T., Ahmed S., Ali S.M., Moktadir M.A., Kabir G. Improving supply chain sustainability in the context of COVID-19 pandemic in an emerging economy: Exploring drivers using an integrated model. Sustainable Production and Consumption. 2021;26:411–427. doi: 10.1016/j.spc.2020.09.019. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Kumar A., Duggal S., Gur R., Rongpharpi S.R., Sagar S., Rani M.…Khanijo C.M. Safe transportation of biomedical waste in a health care institution. Indian Journal of Medical Microbiology. 2015;33:383–386. doi: 10.4103/0255-0857.158559. [DOI] [PubMed] [Google Scholar]
- Lakshmi Priyadarsini S., Suresh M. Factors influencing the epidemiological characteristics of pandemic COVID 19: A TISM approach. International Journal of Healthcare Management. 2020;13:89–98. [Google Scholar]
- Li X., Chen G., Jiang S., He R., Xu C., Zhu H. Developing a dynamic model for risk analysis under uncertainty: Case of third-party damage on subsea pipelines. Journal of Loss Prevention in the Process Industries. 2018;54:289–302. [Google Scholar]
- Li F., Wang W., Dubljevic S., Khan F., Xu J., Yi J. Analysis on accident-causing factors of urban buried gas pipeline network by combining DEMATEL, ISM and BN methods. Journal of Loss Prevention in the Process Industries. 2019;61:49–57. [Google Scholar]
- Liao H., Jiang L., Fang R., Qin R. A consensus measure for group decision making with hesitant linguistic preference information based on double alpha-cut. Applied Soft Computing. 2021;98 [Google Scholar]
- Liu P. A weighted aggregation operators multi-attribute group decision-making method based on interval-valued trapezoidal fuzzy numbers. Expert Systems with Applications. 2011;38:1053–1060. [Google Scholar]
- Liu P., Tang G. Some power generalized aggregation operators based on the interval neutrosophic sets and their application to decision making. Journal of Intelligent & Fuzzy Systems. 2016;30:2517–2528. [Google Scholar]
- Liu P., Yu X. 2-Dimension uncertain linguistic power generalized weighted aggregation operator and its application in multiple attribute group decision making. Knowledge-Based Systems. 2014;57:69–80. [Google Scholar]
- Mahadevan S., Zhang R.X., Smith N. Bayesian networks for system reliability reassessment. Structural Safety. 2001;23:231–251. [Google Scholar]
- Makan A., Fadili A. Sustainability assessment of healthcare waste treatment systems using surrogate weights and PROMETHEE method. Waste Management & Research. 2020;39:73–82. doi: 10.1177/0734242X20947162. [DOI] [PubMed] [Google Scholar]
- Maniram Kumar A., Rajakarunakaran S., Pitchipoo P., Vimalesan R. Fuzzy based risk prioritisation in an auto LPG dispensing station. Safety Science. 2018;101:231–247. [Google Scholar]
- Manupati V.K., Ramkumar M., Baba V., Agarwal A. Selection of the best healthcare waste disposal techniques during and post COVID-19 pandemic era. Journal of Cleaner Production. 2021;281 doi: 10.1016/j.jclepro.2020.125175. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Mardani A., Saraji M.K., Mishra A.R., Rani P. A novel extended approach under hesitant fuzzy sets to design a framework for assessing the key challenges of digital health interventions adoption during the COVID-19 outbreak. Applied Soft Computing. 2020;96 doi: 10.1016/j.asoc.2020.106613. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Mendel J.M., John R.I.B. Type-2 fuzzy sets made simple. IEEE Transactions on Fuzzy Systems. 2002;10:117–127. [Google Scholar]
- Nguyen H.T. A note on the extension principle for fuzzy sets. Journal of Mathematical Analysis and Applications. 1978;64:369–380. [Google Scholar]
- Ouyang L., Zhu Y., Zheng W., Yan L. An information fusion FMEA method to assess the risk of healthcare waste. Journal of Management Science and Engineering. 2021;6:111–124. [Google Scholar]
- Pelin E., Emre A. An interval type-2 fuzzy SLIM approach to predict human error in maritime transportation. Ocean Engineering. 2021;232 [Google Scholar]
- Pristrom S., Yang Z., Wang J., Yan X. A novel flexible model for piracy and robbery assessment of merchant ship operations. Reliability Engineering & System Safety. 2016;155:196–211. [Google Scholar]
- Rouhparvar H., Panahi A. A new definition for defuzzification of generalized fuzzy numbers and its application. Applied Soft Computing. 2015;30:577–584. [Google Scholar]
- Sahin O., Stewart R.A., Faivre G., Ware D., Tomlinson R., Mackey B. Spatial Bayesian Network for predicting sea level rise induced coastal erosion in a small Pacific Island. Journal of Environmental Management. 2019;238:341–351. doi: 10.1016/j.jenvman.2019.03.008. [DOI] [PubMed] [Google Scholar]
- Sayali Sandbhor H.K. TISM Based Hierarchical Analysis of Factors Leading to Accidents on Indian Highways. Transportation Research Procedia. 2019;48:1166–1173. [Google Scholar]
- Sayyadi Tooranloo H., Ayatollah A.S. Pathology the Internet Banking Service Quality Using Failure Mode and Effect Analysis in Interval-Valued Intuitionistic Fuzzy Environment. International Journal of Fuzzy Systems. 2016;19:109–123. [Google Scholar]
- Schulte P.A., Pandalai S., Wulsin V., Chun H. Interaction of occupational and personal risk factors in workforce health and safety. American Journal of Public Health. 2012;102:434–448. doi: 10.2105/AJPH.2011.300249. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Sen G., Demirel E., Avci S., Aladag Z. Evaluation of effective risk factors in COVID-19 mortality rate with DEMATEL method. Journal of the Faculty of Engineering and Architecture of Gazi University. 2021;36:2151–2166. [Google Scholar]
- Sharma R., Shishodia A., Kamble S., Gunasekaran A., Belhadi A. Agriculture supply chain risks and COVID-19: Mitigation strategies and implications for the practitioners. International Journal of Logistics Research and Applications. 2020:1–27. [Google Scholar]
- Singh E., Kumar A., Mishra R., Kumar S. Solid waste management during COVID-19 pandemic: Recovery techniques and responses. Chemosphere. 2022;288 doi: 10.1016/j.chemosphere.2021.132451. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Song W., Li J., Li H., Ming X. Human factors risk assessment: An integrated method for improving safety in clinical use of medical devices. Applied Soft Computing. 2020;86 [Google Scholar]
- Sushil Interpreting the Interpretive Structural Model. Global Journal of Flexible Systems Management. 2012;13:87–106. [Google Scholar]
- Taslimi M., Batta R., Kwon C. Medical waste collection considering transportation and storage risk. Computers & Operations Research. 2020;120 [Google Scholar]
- Torkashvand J., Jonidi Jafari A., Godini K., Kazemi Z., Kazemi Z., Farzadkia M. Municipal solid waste management during COVID-19 pandemic: A comparison between the current activities and guidelines. Journal of Environmental Health Science and Engineering. 2021;19:173–179. doi: 10.1007/s40201-020-00591-9. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Wang L., Cao Q., Zhou L. Research on the influencing factors in coal mine production safety based on the combination of DEMATEL and ISM. Safety Science. 2018;103:51–61. [Google Scholar]
- Wang J., Peng Y., Lu J., Jiang Y. Analysis of risk factors affecting delay of high-speed railway in China based on Bayesian network modeling. Journal of Transportation Safety & Security. 2022;14:1022–1043. [Google Scholar]
- Wang M., Zheng H., Huang Z. Proceedings of the 2015 International Conference on Electrical and Information Technologies for Rail Transportation. Springer; 2016. Fault Prognosis of Track Circuit Based on GWA Fuzzy Neural Network; pp. 473–481. [Google Scholar]
- Warfield J.N. Toward interpretation of complex structural models. IEEE Transactions on Systems, Man, and Cybernetics. 1974:405–417. [Google Scholar]
- Wu Q., Zhou L., Chen Y., Chen H. An integrated approach to green supplier selection based on the interval type-2 fuzzy best-worst and extended VIKOR methods. Information Sciences. 2019;502:394–417. [Google Scholar]
- Xiaohong P., Yingming W. Evaluation of renewable energy sources in China using an interval type-2 fuzzy large-scale group risk evaluation method. Applied Soft Computing. 2021;108 [Google Scholar]
- Xie J., Zeng W., Li J., Yin Q. Similarity measures of generalized trapezoidal fuzzy numbers for fault diagnosis. Soft Computing. 2017;23:1999–2014. [Google Scholar]
- Yang Y.-Y., Liu X.-W., Liu F. Trapezoidal Interval Type-2 Fuzzy TOPSIS Using Alpha-Cuts. International Journal of Fuzzy Systems. 2020;22:293–309. [Google Scholar]
- Yong Z., Gang X., Guanxing W., Tao Z., Dawei J. Medical waste management in China: A case study of Nanjing. Waste Management. 2009;29:1376–1382. doi: 10.1016/j.wasman.2008.10.023. [DOI] [PubMed] [Google Scholar]
- Yucesan M., Gul M., Celik E. A holistic FMEA approach by fuzzy-based Bayesian network and best–worst method. Complex & Intelligent Systems. 2021;7:1547–1564. [Google Scholar]
- Zadeh L.A. Fuzzy sets. Information & Control. 1965;8:338–353. [Google Scholar]
- Zadeh L.A. The concept of a linguistic variable and its application to approximate reasoning—I. Information Sciences. 1975;8:199–249. [Google Scholar]
- Zhang Z. Hesitant fuzzy power aggregation operators and their application to multiple attribute group decision making. Information Sciences. 2013;234:150–181. [Google Scholar]
- Zhang Y., Huang Y., Zhao X., Li J., Yin F., Wang L. Research on the Influencing Factors of Kite Culture Inheritance Based on an Adversarial Interpretive Structure Modeling Method. IEEE Access. 2021;9:42140–42150. [Google Scholar]
- Zhang J., TerMaath S., Shields M.D. Imprecise global sensitivity analysis using bayesian multimodel inference and importance sampling. Mechanical Systems and Signal Processing. 2021;148 [Google Scholar]
- Zhao H., Liu H., Wei G., Zhang N., Qiao H., Gong Y.…Wu Y. A review on emergency disposal and management of medical waste during the COVID-19 pandemic in China. Science of the Total Environment. 2022;810 doi: 10.1016/j.scitotenv.2021.152302. [DOI] [PMC free article] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Data will be made available on request.