Abstract
Telecare Medicine Information System (TMIS) refers to a medical model that uses communication and information technology to realize multiple medical functions such as remote disease diagnosis, treatment, and health care. Because TMIS is carried out on an insecure public Internet, a large number of mutual authentication and key agreement protocols for TMIS have been proposed to protect the privacy of patients. Recently, Ostad-Sharif et al. proposed a novel anonymous authentication and key agreement scheme for TMIS. In this work, we will demonstrate that Ostad-Sharif et al.’s scheme exists the problems of strong authentication and inefficient password change, and it cannot resist the off-line password guessing attack. To overcome the weaknesses found in Ostad-Sharif et al.’s scheme, we propose a biometrics-based mutual authentication and key agreement protocol for TMIS, making full use of the advantages of one-way hash function and elliptic curve cryptosystem (ECC). The security of the proposed scheme is formally proved under the widely used random oracle model (ROM), and various known malicious attack resistances also are presented by the heuristic discussion. Compared with the existing related schemes, the computation cost and communication overhead of our scheme are reduced by 74.5% and 27.3% respectively.
Keywords: Authentication, Key agreement, Biometrics, TMIS, ROM
Introduction
Telecare Medicine Information System (TMIS) uses computer, communication, medical technology and equipment to realize face-to-face consultation between experts and patients, experts and medical staff through remote transmission of data, text, voice and image data [9]. It is not only a medical or clinical problem, but also a communication network, database and other aspects’ problem, and they need to be integrated into the network system.
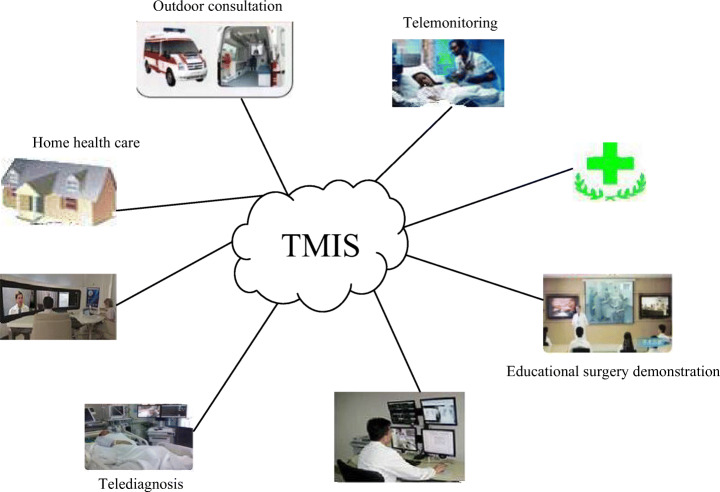
Driven by 5G technology, the application scenarios of TMIS have been expanded. The sudden COVID-19 has become an opportunity for the rapid growth of telemedicine. Telemedicine can prevent cross infection, reduce the burden of the hospital, and ensure the patients to obtain much-needed medical services. As shown in Fig. 1, the specific applications of TMIS include telediagnosis, remote consultation and nursing, educational surgery demonstration, remote surgery and treatment, telemonitoring, remote medical information service, etc.
Fig. 1.
Typical architecture of TMIS
TMIS is mainly composed of the following three parts: a) Providers of medical services. They are generally located in the medical centers of big cities and have rich medical resources and experience in diagnosis and treatment. b) Demanders of medical services. They may be local medical institutions that do not have sufficient medical capacity or conditions. Also, they may be patients in remote areas. c) The communication network and medical devices connecting provider and demander. The communication network includes ordinary telephone network, wireless communication network and communication satellite network; medical devices include computer software and hardware, diagnosis and treatment instruments, etc.
With the increasing maturity of technologies such as computers, sensors, and mobile Internet, as well as the continuous enhancement of national health awareness and the significant increase in demand for health services, TMIS shows strong application potential in the health and medical field [1, 13, 41]. It provides flexible and convenient electronic medical services for user, and gradually penetrates into people’s lives. More and more people begin to pay attention to the information security of TMIS. Since medical records are exposed to unsecured public network, they may be damaged, changed or leaked. This makes TMIS more vulnerable to various security threats and attacks. In order to protect the privacy security of users and medical data, efficient mutual authentication and key agreement schemes are urgently needed.
The authentication key agreement (AKA) protocol can realize mutual authentication between users and servers. While ensuring that only legitimate users can access the server, it can also resist server spoofing attacks. After user and server complete mutual authentication, the shared session key will be established to ensure the security of future communications. Moreover, the session key is negotiated by both parties, and they have the same contribution to the generation of the session key, which enhances the security of the session key.
In most secure communications, the communication system is required to provide confidentiality and authentication for the transmitted data [14, 33, 39]. Confidentiality means that the transmitted data can only be read by the designated receiver. Authentication means that the receiver can confirm that the received data is from the sender, and the data has never been tampered during transmission. In order to meet the requirement of secure communication, the communication participants need to share a one-time session key used to encrypt and authenticate messages. Therefore, participants need a key establishment protocol to generate and distribute the session key before communication. According to the existence of key generation center (KGC), key establishment protocols are generally divided into key transfer protocol and key agreement protocol. In the key transfer protocol, KGC will share a secret value with the user during the registration phase, and use this secret value to distribute the key. The key agreement protocol does not need the participation of KGC. Two or more participants exchange information and negotiate a common session key in an insecure channel controlled by the adversary, and nobody can determine the final session key value in advance. Key agreement protocol, encryption and digital signature are considered as the smallest three cryptographic primitives.
Related works
In order to ensure the communication security on the public channel, a large number of two-factor authentication schemes [3, 15, 21, 22, 37, 40] have been introduced in the past decades. However, researchers pointed out that these schemes were vulnerable to bypass attacks [27], and the secret parameters stored in the smart card may be exposed to the adversary. Later, researchers introduced biometrics into their authentication schemes [2, 7, 10, 17, 20, 23, 29], and the popular three-factor authentication scheme appeared. These schemes overcome the security weaknesses mentioned above.
In 2000, Hwang and Li [19] proposed a smart-card-based remote user authentication scheme using the ElGamal public key cryptosystem. Their scheme did not need to maintain a password table for verifying users’ legitimacy, and can withstand the replay attack. On the basis of Hwang and Li’s scheme, Sun [34] further proposed an efficient and practical remote user authentication scheme using smart cards. Their scheme not only provided the same advantages as Hwang and Li’s scheme, but also significantly reduced the communication and computation costs. Soon afterwards, Malasri and Wang [26] designed a novel two-tier scheme for verifying the authenticity of patient data, making full use of the advantages of ECC and symmetric encryption/decryption. And Boyen [6] pointed out that any protocol involving only two parties was vulnerable to dictionary attacks on the server. Later, Awasthi and Srivastava [4] proposed a new biometrics-based authentication scheme using the bitwise XOR operations and chaotic one-way hash function. However, Das and Goswami [11] discovered that their scheme failed to protect strong replay attack, establish a secret session key, provide the user anonymity and lacked rigorous formal security analysis. To withstand the security flaw, Das and Goswami proposed a novel and secure biometrics-based remote user authentication scheme.
In 2010, Li and Hwang [23] proposed an efficient biometrics-based remote user authentication scheme using smart cards, and its security was based on the smart card, biometrics verification and one-way hash function. However, Chang et al. [7] pointed out that applying only collision-resistant one-way hash functions would make users unable to be authenticated in Li and Hwang’s scheme, and the security of secret data cannot be ensured. Then they proposed a biometrics-based user authentication scheme to ensure uniqueness and anonymity at the same time. They claimed that only the legal user/patient himself/herself can access the remote server, and no one can trace him/her according to the transmitted data in their scheme. Their scheme is efficient due to the usage of one-way hash function and exclusive-or (XOR) operations. However, Das and Goswami [10] proved that Chang et al.’s scheme had design flaws in login and authentication phase and password change phase, failed to protect privileged insider attack, the man-in-the-middle attack, and did not provide proper authentication. Then they proposed an improved uniqueness-and-anonymity-preserving remote user authentication scheme.
In 2015, Amin et al. [2] demonstrated that Das and Goswami’s scheme lacked proper protection against several security attacks such as user anonymity, off-line password guessing attack, smart card theft attack, user impersonation attack, server impersonation attack, session key disclosure attack. To overcome these pitfalls, they proposed an anonymity preserving remote patient authentication scheme for e-health care systems. However, Ravanbakhsh and Nazari [29] proved that their scheme was vulnerable to privileged-insider attack, replay attack, session key disclosure attack, and did not provide patient untraceability and backward secrecy. Then they proposed an efficient remote mutual authentication scheme using ECC and Fuzzy Extractor. Also, Singh et al. [32] proposed an elliptic curve signcryption-based mutual authentication protocol. It greatly reduced the computing cost and communication overhead of smart card. And Shunmuganathan et al. [31] proposed a secure and efficient two factor authentication scheme for multi-server environment, and claimed that the advantage of this scheme was to protect the data stored in the smart card by increasing the dynamic attribute of identity and randomization of each session key. Experiments show that the scheme can resist various attacks, such as forgery attack, replay attack, smart card theft attack and so on. Chaudhry [8] conducted research on the multi-factor authentication and key agreement protocol for social multimedia, and at the same time verified the security of the proposed scheme with the well-known automatic security verification tool ProVerif, but the application field of the scheme is too narrow and the versatility is not strong.
In order to prevent information leakage, the secret high-entropy data can also be stored in the device (such as a smart card) carried by the user, which constitutes the Two-Factor AKA (2FAKA) protocol. For the 2FAKA protocol, the most basic security requirement is two-factor security, that is, the attacker cannot impersonate the legitimate user even if he obtains the user’s password or smart card. However, with the rapid development of the existing side-channel-attack technology, the secret information in the common smart card can be analyzed, and then the adversary can implement offline dictionary attack, which makes many schemes unable to provide two-factor security. For this, Wang et al. [38] proposed the idea of combining “fuzzy verification factor” with “honeywords” to solve the problem of offline dictionary attack caused by smart devices loss. The main function of “fuzzy verification factor” is to detect the user’s wrong input in time, which can effectively solve the delay and improve the user experience by reducing the computing and communication cost. “Honeywords” enables the protocol to identify the online guessing behavior of attackers in time, and achieve the security beyond the traditional upper limit while meeting the availability index. Moreover, the security of protocol is proved under the modified Random-Oracle-model (ROM).
In 2016, Tewari and Gupta [36] proposed an ultra-lightweight authentication protocol with very low computing and storage costs, and analysis shows that the protocol can meet most security requirements. Recently, Ostad-Sharif et al. [28] found that Ravanbakhsh and Nazari’s scheme [29] existed the problems of known session-specific temporary information attack and perfect forward secrecy. To overcome these deficiencies, they proposed a novel anonymous and unlinkable user authentication and key agreement scheme for TMIS based the elliptic curve cryptosystem (ECC). In this paper, we will point out that Ostad-Sharif et al.’s scheme still exists some problems, such as inefficient password change, off-line password guessing attack resistance, etc., then we give a new scheme. We combine elliptic curve cryptosystem with fuzzy extractor, and apply it to login and authentication phase, which solves the problem of password and biometric correctness detection. Moreover, it makes our protocol have strong authentication and password guessing attack resistance. Also, the ingenious combination of lightweight cryptographic primitives (such as hash, XOR and concatenation) further reduces the computational cost and communication overhead of the scheme.
Our contributions
The main contributions of this paper are as follows.
The recently-proposed Ostad-Sharif et al.’s enhanced mutual authentication and key-agreement protocol for TMIS is reviewed, and we find that their scheme exists the problems of strong authentication and inefficient password change, and it cannot resist the off-line password guessing attack.
To overcome the weaknesses in Ostad-Sharif et al.’s scheme, we propose a biometrics-based mutual authentication and key agreement protocol for TMIS.
The security of the proposed scheme is formally proved under the widely used ROM.
We demonstrate that the proposed scheme can provide all kinds of security by heuristic discussion.
Organization of the paper
The rest of our work is arranged as follows: Section 3 introduces some preliminaries. Section 4 reviews Ostad-Sharif et al.’s protocol. Section 5 points out the weaknesses of Ostad-Sharif et al.’s scheme. Our biometrics-based mutual authentication and key agreement protocol for TMIS is presented in Section 6. The security of the proposed scheme is formally proved under the widely used ROM in Section 7. We demonstrate that the proposed scheme can provide various security by heuristic discussion in Section 8. In Section 9, the performance of our scheme is compared with the related works. Finally, the conclusions are given in Section 10.
Preliminaries
This section introduces some basic knowledge that will be used in this paper, including some common symbols, elliptic curve defined in finite field, fuzzy extractor and so on.
Symbols guide
For simplicity, the notations and their descriptions used in the entire article are listed in Table 1.
Table 1.
Notations used in the paper
| Notation | Description |
|---|---|
| Fp | a finite field |
| E(Fp) | an elliptic curve defined on Fp |
| G | a based point with a big prime order q over the E(Fp) |
| the interval [1,q − 1] | |
| IDi | the identity of the patient |
| PWi | the password of the patient |
| σ | an extracted string |
| 𝜃 | a public auxiliary string |
| SK | the session key |
| s | the server’s long-term private key |
| Pubs | the server’s public key |
| SCi | the smart card issued to every specific patient |
| Ek(⋅)/Dk(⋅) | symmetric encryption/decryption with key k |
| h(⋅) | the one-way hash function |
| ⊕ | XOR operation |
| ∥ | the concatenation operation |
| adversary |
Elliptic curve over a prime finite field Fp
The elliptic curve equation defined on the prime finite field Fp is:
| 1 |
where a,b ∈ Fp and △ = 4a3 + 27b2 (mod p)≠ 0
The elliptic curve E(Fp) is defined as:
| 2 |
where is the infinity point.
The number of points on the elliptic curve E(Fp) is represented by ♯E(Fp), which is called the order of the elliptic curve.
Some operations on the elliptic curve are shown as follows:
1. If P = (x1,y1) ∈ E(Fp), and Q = (x2,y2) ∈ E(Fp), then P + Q = (x3,y3), where x3 = λ2 − x1 − x2 (mod p) and y3 = λ(x1 − x2) − y1 (mod p), where
2. Let P = (x,y) ∈ E(Fp), then the scalar multiplication in E(Fp) is defined as: tP = P + P + ⋯ + P(t − times).
Elliptic curve discrete logarithm problem (ECDLP): for the points P,Q ∈ E(Fp), variable α ∈ Fp, it is hard to calculate α meeting Q = α ⋅ P.
Elliptic curve computational Diffie-Hellman (ECDH) problem: for the points G,aG,bG ∈ E(Fp), it is computational impossible to calculate abG ∈ E(Fp).
Fuzzy extractor
In 2004, Dodis et al. [12] proposed the concept of fuzzy extractor. The fuzzy extractor Fe = (Gen,Rep) has two algorithms: the generation algorithm Gen and the regeneration algorithm Rep. The generation algorithm Gen outputs a string σ and a public auxiliary string 𝜃 for the input biometrics B (the first sampling of biometrics); The regeneration algorithm Rep outputs a string for the input biometrics (the second sampling of biometrics) and the public auxiliary string 𝜃. If the distance between the two samples B and is close enough, then . The fuzzy extractor can convert noisy biometrics into stable strings, and this good property enables the fuzzy extractor to be used in cryptographic systems.
Using fuzzy extractor, users can take their own biometrics as the input of Gen to obtain a public auxiliary string 𝜃 and an extracted random string σ. The random string σ can be used as the key of the cryptosystem; the public auxiliary string 𝜃 does not need to be kept secretly, as long as it is stored. After the cryptosystem runs, the key σ will be destroyed. When the cryptosystem needs to use the key again, the user takes his own biometrics and public auxiliary string 𝜃 as the input, and uses the regeneration algorithm Rep to reproduce the key σ. It can be seen that users do not need to store the key. When using the key, they only need to input their own biometrics, and the fuzzy extractor can recover the key safely and reliably.
Review of Ostad-Sharif et al.’s scheme
This section elaborates Ostad-Sharif et al.’s ECC-based anonymous user authentication and key agreement protocol for TMIS, which includes four phases: system setup, patient registration, login and authentication, and password change.
System setup phase
Firstly, the server selects an elliptic curve E(Fp) over a finite field Fp and a base point G with a large prime order q. Secondly, the server selects a random number as its private key. Finally, it publishes {E(Fp),G,p,q,hi(⋅)} and keeps s secretly, where hi(⋅)(i = 0,1,⋯ ,4) are one-way collision-resistant hash functions.
Patient registration phase
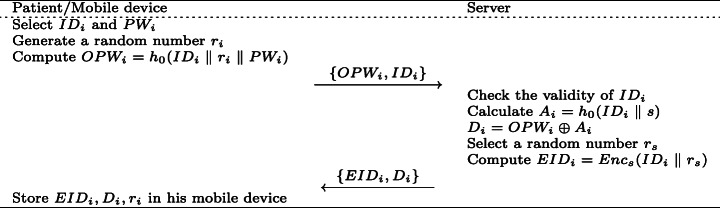
To access services from a medical server, a new user needs to register on the server through the following steps. This phase is shown in Fig. 2.
The patient selects an identity IDi, password PWi, generates a random number ri, computes OPWi = h0(IDi ∥ ri ∥ PWi), then sends a registration request {OPWi,IDi} to the server via a secure channel.
On receiving the request message {OPWi,IDi}, the server checks whether the IDi exists in his database, and if so, the server requests the patient to choose a different identity. Otherwise, the server computes Ai = h0(IDi ∥ s), Di = OPWi ⊕ Ai, selects a random number rs and computes EIDi = Encs(IDi ∥ rs). Finally, the server submits {EIDi,Di} to the patient.
Upon reception of the response message {EIDi,Di}, the patient stores {EIDi,Di,ri} into his mobile device.
Fig. 2.
Registration phase of Ostad-Sharif et al.’s scheme
Login and authentication phase
The login and authentication phase of Ostad-Sharif et al.’s scheme will be described in this subsection. When patient wants to access the service from server, he/she needs to do the following. As shown in Fig. 3.
The patient inputs his/her identity IDi, password PWi. Subsequently, the mobile device retrieves ri and Di from its memory, and computes OPWi = h0(IDi ∥ ri ∥ PWi), Ai = OPWi ⊕ Di. Then, the mobile device generates a random number , computes Xi = h1(IDi ∥ PWi ∥ xi)G, Vi = h2(IDi ∥ Ai ∥ Xi ∥ Ti), where Ti is its current time. Finally, the mobile device submits {EIDi,Xi,Vi,Ti} to the server via a public channel.
Upon reception of {EIDi,Xi,Vi,Ti}, the server checks the freshness of Ti, aborts if not; otherwise, the server computes (IDi ∥ rs) = Decs(EIDi), Ai = h0(IDi ∥ s), and verifies whether h2(IDi ∥ Ai ∥ Xi ∥ Ti)=?Vi. If the equation does not hold, the server aborts the session; otherwise, it generates a random number and computes Xs = h1(IDs ∥ s ∥ xs)G, K = h1(IDs ∥ s ∥ xs)Xi and SK = h3(IDi ∥ Ti ∥ K). Next, the server selects a random number , and computes , , . Finally, the server sends to the mobile device.
After receiving , the mobile device computes K = h1(IDi ∥ PWi ∥ xi)Xs, SK = h3(IDi ∥ Ti ∥ K), , verifies whether . If so, the mobile device substitutes EIDi with .
Fig. 3.
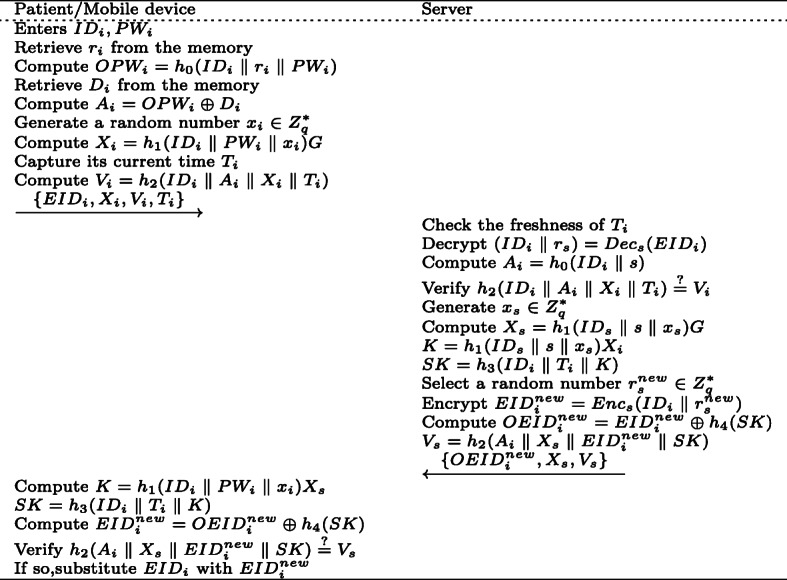
Login and authentication phase of Ostad-Sharif et al.’s scheme
Password change phase
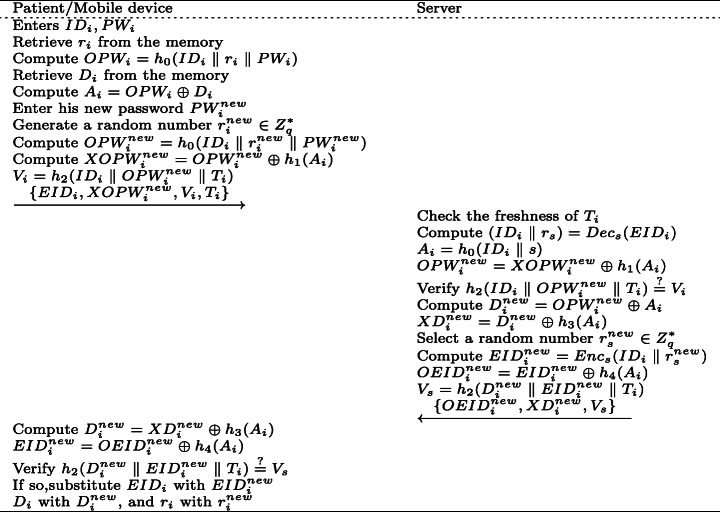
In practice, the user’s password is low entropy and easy to be leaked. At this stage, the user can change his/her password without repeating the registration process. The detailed steps are as follows. As shown in Fig. 4.
The patient inputs his/her identity IDi, password PWi, and computes OPWi = h0(IDi ∥ ri ∥ PWi), Ai = OPWi ⊕ Di. Then the mobile device asks the patient to input a new password.
The patient enters a new password , and the mobile device generates a new random number , computes , , . Then the mobile device sends to the server.
After receiving , the server checks Ti’s freshness. If it is fresh, the server computes (IDi ∥ rs) = Decs(EIDi), Ai = h0(IDi ∥ s), , and verifies whether . If not, the server aborts the session; otherwise, it computes and . Then, the server selects a random number and computes , , . Finally, the server submits to the patient.
On receiving , the mobile device computes , , and verifies whether . If true, the mobile device substitutes EIDi with , Di with , and ri with .
Fig. 4.
Password change phase of Ostad-Sharif et al.’s scheme
Weaknesses of Ostad-Sharif et al.’s protocol
In the section, we will point out that Ostad-Sharif et al.’s protocol exists the problems of strong authentication, inefficient password change and the off-line password guessing attack resistance. The detailed description is as follows.
Strong authentication
In the login and authentication phase of Ostad-Sharif et al.’s protocol, after the user enters his/her identity IDi and password PWi, the smart card does not check their correctness and proceeds to the next step.
Assuming that the patient inputs the wrong password instead of the correct password PWi. Then, the smart card computes , .
Smart card generates a random number , computes , , where Ti is its current time. Finally, the smart card submits to the server via a public channel.
Upon reception of , the server checks the freshness of Ti, aborts if not; otherwise, the server computes (IDi ∥ rs) = Decs(EIDi), Ai = h0(IDi ∥ s). Then the server verifies whether .
It is obviously that because . Therefore, the server considers the patient to be illegal, refuses him/her to log in and terminates the session.
Similarly, if the patient enters an incorrect identity IDi, the above problem will also occur during the login and authentication phase. This problem increases the communication and computing costs of the server.
Inefficient password change
In the password change phase of Ostad-Sharif et al.’s protocol, the old password is not verified for correctness, and we find some problems with the password change phase. The details are described as follows.
Assuming that the patient inputs the wrong password instead of the correct password PWi, and the smart card computes , . Then, the smart card asks the patient to input a new password.
The patient enters a new password , and then the patient and the server perform mutual authentication phase. After that, the server submits to the patient.
On receiving , the mobile device computes , , and verifies whether .
It is obviously that because . So the smart card refuses to update the password and terminates the session. This increases the burden on the server. If a malicious adversary sends a large number of password change requests to a specific server, it may cause the server to be paralyzed, and thus can not provide normal services for legitimate users.
Off-line password guessing attack
Messerges et al. [27] and He et al. [18] point out that all smart cards cannot resist the side channel attack and all data can be extracted from the smart cards. We assume an adversary has extracted the information {EIDi,Di,ri} from the smart card. In this subsection, we will prove that can obtain the patient’s password once he/she obtains the smart card of the patient in Ostad-Sharif et al.’s scheme. The details are as follows.
intercepts patient’s login information {EIDi,Xi,Vi,Ti} on public channel, and guesses patient’s identity and password from the user identity space Did and the password space Dpw respectively.
computes , , .
verifies whether or not. If true, gets the patient’s real identity IDi and password PWi. Otherwise, repeats (1) and (2) until he/she finds the correct identity and password.
Therefore, Ostad-Sharif et al.’s protocol cannot resist the off-line password guessing attack.
Our proposed scheme
To overcome the security weaknesses of Ostad-Sharif et al.’s protocol and enhance the security of protocol, we give a biometrics-based mutual authentication and key agreement protocol (BBAKA) for TMIS using elliptic curve cryptography. It consists of four phases: initialization phase, patient registration phase, login and authentication phase, password change phase. Fig. 5 shows the general flow of BBAKA protocol. Firstly, the key generation center (KGC) initializes system and generates public parameters. Secondly, the user and the server interact to complete mutual authentication and establish a common session key. The details are presented as follows.
Fig. 5.
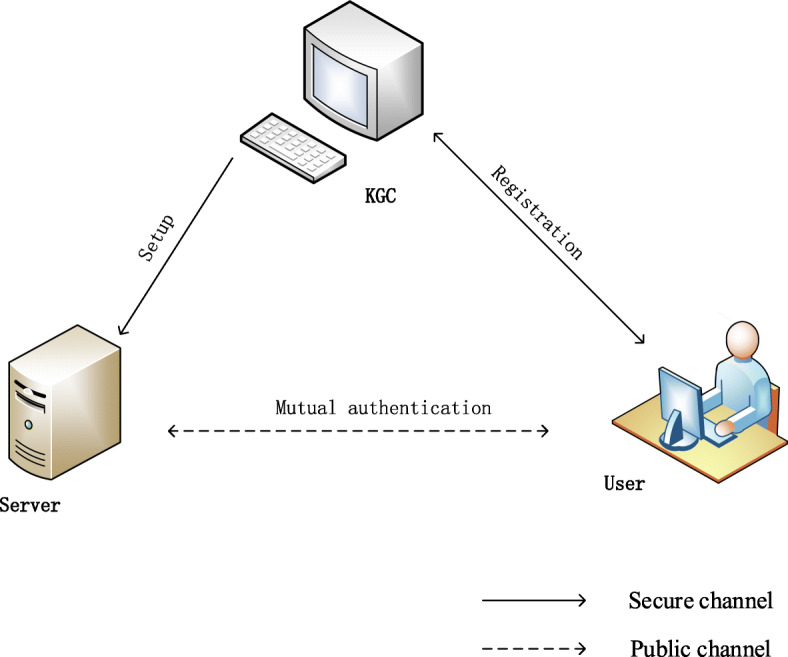
General flow of BBAKA protocol
Initialization phase
KGC initializes the system parameters as follows, then publicizes them.
The server chooses an elliptic curve E(Fp) and a base point G with large prime order q over E(Fp).
The server selects a secure one-way hash function: .
The server selects a random number as its long-term private key and calculates Pubs = s ⋅ G as its public key.
Server keeps s secretly and publishes the system parameters {E(Fp),G,Pubs,q,h(⋅)}.
Patient registration phase
If the patient needs to access the medical server, he/she should first register on KGC as the following steps. The details are shown in Fig. 6.
The patient selects an identity IDi, password PWi, imprints his/her biometrics Bi, generates a random number ri, computes (σi,𝜃i) = Gen(Bi), OPWi = h(IDi ∥ ri ∥ PWi). Then the patient sends a registration request {OPWi,IDi} to KGC via a secure channel.
Upon receiving the request message {OPWi,IDi}, KGC checks whether h(IDi) exists in its database. If so, KGC requests the patient to choose a different identity. Otherwise, it computes Ai = h(IDi ∥ s), Di = OPWi ⊕ Ai, selects a random number rs and computes EIDi = Encs(IDi ∥ rs), Ci = h(IDi ∥ Ai ∥ OPWi). Then KGC stores {EIDi,Di,Ci,h(⋅)} in a smart card SCi and submits SCi to the patient via a secure physical channel.
After receiving SCi, the patient computes yi = ri ⊕ h(σi) and stores yi,𝜃i in SCi.
Fig. 6.
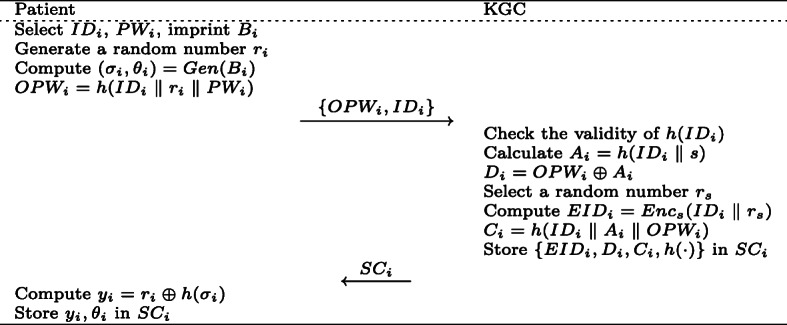
Registration phase of BBAKA protocol
Login and authentication phase
When the patient wants to login server, he and server need to authenticate each other’s legitimacy, and establish a shared session key to ensure the security of subsequent communication. The detailed description of this phase is shown in Fig. 7.
Patient inputs his identity IDi, password PWi, imprints Bi. Then the mobile device retrieves yi and Di from its memory, and computes σi = Rep(Bi,𝜃i), ri = yi ⊕ h(σi), OPWi = h(IDi ∥ ri ∥ PWi), Ai = OPWi ⊕ Di. Following, the mobile device verifies whether h(IDi ∥ Ai ∥ OPWi)=?Ci holds. If it does not hold, the mobile device terminates this session. Otherwise, the mobile device generates a random number , and computes Xi = α ⋅ G, Vi = h(IDi ∥ Ai ∥ Xi ∥ T1), where T1 is the current time. Finally, the mobile device submits {EIDi,Xi,Vi,T1} to server.
Upon reception of {EIDi,Xi,Vi,T1}, server checks the freshness of T1, aborts if not; otherwise, server computes (IDi ∥ rs) = Decs(EIDi), Ai = h(IDi ∥ s). Then server verifies whether h(IDi ∥ Ai ∥ Xi ∥ T1)=?Vi, if not, aborts the session; otherwise, it generates a random number and computes Xs = β ⋅ G, SK = h(IDi ∥ T1 ∥ Ai ∥ β ⋅ Xi). Next, server selects a new random number , computes , , and sends to the mobile device.
After receiving , the mobile device computes SK = h(IDi ∥ T1 ∥ Ai ∥ α ⋅ Xs), verifies whether . If so, it substitutes EIDi with .
Fig. 7.
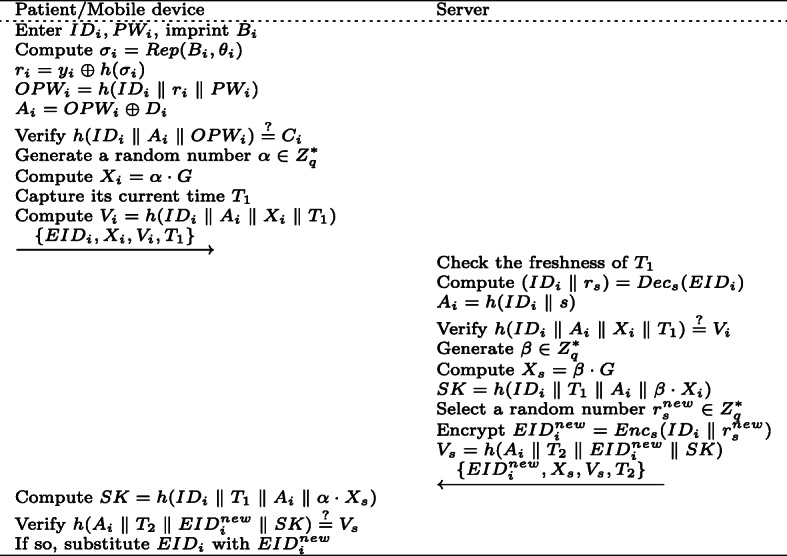
Login and authentication phase of BBAKA protocol
Password and biometrics change phase
At this stage, the patient can change his password and biometrics according to the following steps.
Patient inserts his smart card into the card reader and inputs his/her identity IDi, password PWi, imprints his/her biometrics Bi. Then smart card SCi computes σi = Rep(Bi,𝜃i), ri = yi ⊕ h(σi), OPWi = h(IDi ∥ ri ∥ PWi), Ai = OPWi ⊕ Di.
SCi checks h(IDi ∥ Ai ∥ OPWi)=?Ci. If not, SCi will reject the patient’s password and biometrics change request. Otherwise, patient is asked to enter a new password PWinew and biometrics Binew.
The patient enters a new password PWinew and imprints his/her new biometrics Binew.
On receiving PWinew and Binew, SCi generates a new random number rinew, and computes (σinew,𝜃inew) = Gen(Binew), OPWinew = h(IDi ∥ rinew ∥ PWinew), Dinew = OPWinew ⊕ Ai, Cinew = h(IDi ∥ Ai ∥ OPWinew), yinew = rinew ⊕ h(σinew). Finally, SCi updates {Di,Ci,yi,𝜃i} with {Dinew,Cinew,yinew,𝜃inew}.
Unlike Ostad-Sharif et al.’s protocol, our password and biometrics change phase does not require the participation of server, and patient can complete it locally. In this way, the computing and communication costs of server are reduced, which makes our protocol more efficient.
Formal security proof
In this section, we give the formal security proof of BBAKA protocol under the random oracle model (ROM) [5].
Security model
The BPR adversary model is widely used to prove the security of authentication scheme based password. U1 and U2 are protocol participants. The model allows each user to execute multiple protocols with other users. A user can execute a polynomial protocol instance in parallel. represents the t th instance of user Ui.
The security of the protocol depends on the capability of the adversary, which is simulated by a series of queries. It is assumed that the probability polynomial time (PPT) adversary completely controls the communication and can query any instance. can perform the following queries.
Execute(U1,U2): This query executes the protocol between users U1 and U2. The adversary gets all messages during the execution of the protocol.
: This query allows adversary to send a message M to instance , then executes the protocol π honestly and returns a response message to .
: This query returns the session key held by instance .
Corrupt(Ui): This query allows to get the long-term private key of Ui. But can’t get any intermediate data in the process of protocol execution.
: This query attempts to simulate the adversary’s ability to distinguish between session key and random key. Test oracle randomly selects a bit b. If b = 1, the session key is returned; If b = 0, random key is returned. Suppose that can only make one Test query.
Let be the session identifier of participant instance , which is a function of all messages received and sent by . Let be the partner identifier which is used to identify the participant who is exchanging keys with the instance .
Definition 1 (Partnership) Two instances and are partners if and only if: and .
Definition 2 (Freshness) Instance is fresh. If the status of this instance is accepted after receiving the last expected message, and neither nor its partners have been asked for Reveal query.
Definition 4 (Semantic Security) For any , is an event that makes one Test query on some fresh instances and correctly guesses the value of b. The advantage that attacks the protocol π is defined to be . The protocol π is called semantically secure if is negligible.
Security proof
First, we introduce the simulation of two oracles: Hash oracle and encryption/ decryption oracle.
Simulation of Hash Oracle Query
On receiving h(u) query, Hash returns v as follows.
v = h(u) is returned if (u,v) exists in list LH.
Otherwise, select a constant randomly and send it to , then add (u,v) into list LH.
Simulation of encryption/decryption Oracle Queries
When Ek(u) is queried, it returns v if the record (k,u,∗,v) exists in the list LC. Otherwise, it returns a random number and adds (k,u,E,v) into LC.
When Dk(v) is queried, it returns u if the record (k,u,∗,v) exists in the list LC. Otherwise, it returns a random number u and adds (k,u,D,v) into LC.
Next, we prove that the protocol is secure against the active adversary under ECDH assumption.
Theorem 1 Under ECDH assumption, BBAKA protocol can resist the attack of PPT adversary. The corresponding adversary advantage is
where qh,qc,qs and qe denote the number of Hash, encryption/decryption, Send and Execute oracle queries, respectively, denotes ’s probability of solving the ECDH problem successfully, lh is the output size of Hash oracle, lc is the output size of encryption/decryption oracle and lr is the string length of random numbers. |D| is the size of the password space, l is the length of σ, εb represents the probability that the biometric information of two different users satisfies the condition , which is obviously a negligible infinitesimal
Proof To prove that BBAKA protocol π is secure, we define five games Gi(0 ≤ i ≤ 4). Pr[Succi] denotes the probability which success in the game Gi.
GameG0: ’s query is responded as the real BBAKA protocol, so the probability that success in Game G0 is equal to ’s advantages in the original protocol. Then
| 3 |
Game G1: Hash oracle and encryption/decryption oracles are simulated as above, and other oracles are simulated as the original protocol. Then
| 4 |
Game G2: This game considers the hash result conflict and the random number conflict of all communication messages. In the transmitted messages {EIDi,Xi,Vi,T1} and , Xi and Xs contain random numbers α and β, respectively. According to the birthday paradox, the probability of collision in the Hash queries, encryption/decryption queries and transcripts are at most , and respectively. Thus
| 5 |
Game G3: In this game, instead of using hash oracle, tries to guess the correct hash value from other oracle queries. It is indistinguishable from G2 except that maybe guess Vi and Vs. Thus, we have
| 6 |
Game G4: In this terminating game, the session key is guessed without querying the hash oracle, so has no advantage to guess b. It has no advantage in distinguishing between the real session key and random session key. Then we have
| 7 |
G4 and G3 are indistinguishable unless queries Hash oracle on < IDi ∥ T1 ∥ Ai ∥ β ⋅ Xi >. Suppose can query Corrupt(Ui) in the following three ways.
Corrupt(Ui) returns Ui’s biometrics Bi to , and the probability is at most qs ⋅ εb.
Corrupt(Ui) returns Ui’s password PWi to , and the probability is at most ;
Corrupt(Ui) returns parameters stored in SCi to , and the probability is at most ;
The above three cases cannot occur at the same time, so the probability is at most . So
| 8 |
Then, we have
Finally, the theorem is proved according to formulas (3)-(8).
Other analysis
In this section, we analyze the important security features and various attack resistances of BBAKA protocol by heuristic discussion method. In addition, password guessing attack resistance has been proven in Section 7.2, so it is omitted here.
Mutual authentication and session key agreement
In the login and authentication phase of BBAKA protocol, server can authenticate the legitimacy of patient by comparing whether h(IDi ∥ Ai ∥ Xi ∥ T1)=?Vi, where Ai = h(IDi ∥ s), Xi = α ⋅ G, T1 is the current timestamp. has two ways to calculate Ai. The first one is that tries his best to get the user’s identity IDi and the system master key s; the second one is that calculates Ai by Ai = OPWi ⊕ Di, where OPWi = h(IDi ∥ ri ∥ PWi), ri = yi ⊕ h(σi). This requires to get the patient’s identity IDi, password PWi, biometrics Bi and the smart card. Clearly, both approaches are almost impossible for any adversary. In addition, since that only legitimate server can get these secret parameters IDi,SK,Xs and s, patients can authenticate server by checking , where SK = h(IDi ∥ T1 ∥ Ai ∥ α ⋅ Xs). After mutual authentication, patient and server establish a shared session key SK = h(IDi ∥ T1 ∥ Ai ∥ α ⋅ Xs). Therefore, our scheme can provide mutual authentication and session key agreement.
User anonymity and untraceability
User anonymity implies that adversary cannot get the user’s real identity IDi. In our protocol, the patient’s identity is sent with a fake name EIDi = Encs(IDi ∥ rs), where s is the server’s private key. To obtain the patient’s identity IDi, needs to get the values of s and the random number rs. For any adversary, this is almost impossible to accomplish. Furthermore, the patient’s pseudonym is updated at the end of each session without disclosing any information to the adversary. In addition, for the login request {EIDi,Xi,Vi,T1} and response message , they are all protected by the random numbers α, β and rs, and cannot get any useful information from these messages. Therefore, users is anonymity and can’t track users.
Perfect forward secrecy
In BBAKA protocol, the session key SK = h(IDi ∥ T1 ∥ Ai ∥ β ⋅ Xi), where Ai = h(IDi ∥ s) and Xi = α ⋅ G. It is protected by server’s private key s and random numbers α,β. Even if gets the master key s, he/she cannot get the value of β ⋅ Xi unless the ECDLP problem is solved. So the perfect forward secrecy is provided in our protocol.
User friendliness
Our protocol allows patients to freely choose and change their identities IDi, passwords PWi and biometrics Bi, which makes our protocol get a good user experience.
Resist the stolen-verifier attack
Our scheme does not require server to maintain a verification list to store secret parameters related to the user’s password and biometrics, and server’s database is not useful for to access patients’ other private information. Therefore, it can resist the stolen-verifier attack.
Resist the privileged insider attack
In the registration phase of BBAKA protocol, patient sends {OPWi,IDi} to server, where OPWi = h(IDi ∥ ri ∥ PWi). Because OPWi is protected by the random number ri, server cannot get the patient’s password PWi. In addition, patient does not send any biometrics information to server, so it is impossible for server to know the patient’s biometrics. Moreover, the use of random number ensures patient a different OPWi in every session. Therefore, our protocol can resist the privileged insider attack.
Resist the user impersonation attack
To impersonate a legitimate patient, must compute Vi = h(IDi ∥ Ai ∥ Xi ∥ T1), where Ai = h(IDi ∥ s), Xi = α ⋅ G. Obviously, cannot get Ai’s value without the system private key s. In addition, as described in the previous section, our protocol can provide user anonymity and untraceability, so also cannot get the user’s identity IDi. Thus, the user impersonation attack is powerless against our protocol.
Replay attack
Suppose the adversary intercepts a login message {EIDi,Xi,Vi,T1} and replays it to the server, the server can quickly detect this attack by checking the freshness of T1. Even if T1 is modified by the adversary, the server can also detect the replay attack by verifying h(IDi ∥ Ai ∥ Xi ∥ T1)=?Vi. Similarly, the patient can find the replay attack by checking the freshness of T2 and verifying . Thus, BBAKA protocol can resist the replay attack.
Man-in-the-middle attack
As discussed above, BBAKA protocol can provide mutual authentication and resist the impersonation attack. So it can successfully resist man-in-the-middle attack.
Resist the denial of service attack
In BBAKA protocol, patients can only send login requests after they are locally authenticated. The details are as follows: The patient inputs his/her identity IDi, password PWi, imprints Bi. Then the mobile device computes σi = Rep(Bi,𝜃i), ri = yi ⊕ h(σi), OPWi = h(IDi ∥ ri ∥ PWi), Ai = OPWi ⊕ Di, and verifies h(IDi ∥ Ai ∥ Xi ∥ T1)=?Vi. If it does not hold, the mobile device will end this session. Namely, only after the patient is authenticated by the mobile device, the login request is sent to the server. Thus, our protocol is secure against the denial of service attack.
Known session-specific temporary information attack
In our protocol, the patient and the server establish the session key SK = h(IDi ∥ T1 ∥ Ai ∥ β ⋅ Xi), where Ai = h(IDi ∥ s), Xi = α ⋅ G. Suppose that the temporary secrets α and β are leaked to the adversary, he still cannot calculate the session key unless he knows the system private key s. Also, only the legitimate server has the private key, is impossible to get s. So in any case, the adversary cannot calculate the session key.
Smart card loss attack
In our scheme, even if the patient’s smart card/mobile device is lost, he/she still can not be impersonated by a malicious adversary without his/her password. Furthermore, as mentioned above, BBAKA protocol can successfully resist the offline password guessing attack. Therefore, the smart card loss attack is powerless against BBAKA protocol.
Functionality and performance analysis
In this section, we carefully compares the functionality and performance of our protocol with the related works [24, 25, 28, 30, 35]. Comparison results are shown in Table 2.
Table 2.
Security comparison
| scheme | [28] | [24] | [25] | [35] | [30] | Our |
|---|---|---|---|---|---|---|
| Mutual authentication and key agreement | √ | √ | √ | √ | √ | √ |
| User anonymity | √ | √ | √ | × | √ | √ |
| User un-traceability | √ | × | × | √ | √ | √ |
| Perfect forward secrecy | √ | √ | √ | √ | × | √ |
| User friendliness | × | × | √ | √ | √ | √ |
| Resist stolen-verifier attack | × | × | √ | √ | × | √ |
| Resist off-line password guessing attack | × | √ | × | × | √ | √ |
| Resist privileged insider attack | √ | √ | √ | √ | √ | √ |
| Resist the user impersonation attack | √ | √ | √ | √ | √ | √ |
| Resist the replay attack | √ | × | × | √ | × | √ |
| Resist man-in-the-middle attack | √ | √ | √ | √ | √ | √ |
| Resist the denial of service attack | × | √ | × | × | √ | √ |
| Resist ephemeral secret leakage attack | √ | × | × | × | √ | √ |
| Resist smart card loss attack | √ | √ | × | √ | √ | √ |
Table 2 shows that [25, 28] and [35] cannot resist off-line password guessing attack and denial of service attack. Ostadsharif et al. [28] and [24] fail to provide the user friendliness. [24], [25] and [35] are powerless to resist the ephemeral secret leakage attack. Li et al. [24], [25] and [30] are vulnerable to the replay attack. Ostadsharif et al. [28], [24] and [30] can not resist the stolen-verifier attack. In addition, [30] and [25] exist the problems of perfect forward secrecy and smart card loss attack resistance respectively. However, our protocol can provide all these security features.
Next, we will compare the performance of BBAKA protocol with the recent existing authentication protocols [24, 25, 28, 30, 35]. We define the notations used for execution time in Table 3.
Table 3.
Notations of some operations
| Notation | Meaning | Execution time (s) |
|---|---|---|
| Tm | One elliptic curve point multiplication operation | 0.063075 |
| Ts | One symmetric encryption/decryption operation | 0.0087 |
| Th | One-way hash function | 0.0005 |
| Te | One modular exponentiation operation | 0.522 |
| Tchao | One chebyshev chaotic map | 0.066 |
| Tpk | One public key encryption/decryption | 0.522 |
According to He et al. [16], the executing time of elliptic curve point multiplication, symmetric encryption/decryption, one-way hash function, modular exponentiation, chebyshev chaotic map and public key encryption/decryption are 0.063075, 0.0087, 0.0005, 0.522, 0.066 and 0.522 second respectively. Since the executing time of concatenation and XOR operation are very short, we neglect them in all protocols. Furthermore, we assume that the size of random number, hash output, timestamp, chebyshev output and elliptic curve point are 64 bits, 160 bits, 32 bits, 320 bits and 320 bits respectively. In addition, the symmetric cryptographic algorithm used is AES-128 and the output size of public key encryption/decryption is 320 bits. The performance comparison results are shown in Table 4.
Table 4.
Performance comparison of our protocol with the related ones
| Scheme | Execution time of U | Execution time of S | Total execution time (second) | Communication cost |
|---|---|---|---|---|
| [28] | 7Th + 2Tm | 7Th + 2Tm + 2Ts | 14Th + 4Tm + 2Ts ≈ 0.2767 | 1184 bits |
| [24] | 11Th + 2Tchao | 8Th + 2Tchao | 19Th + 4Tchao ≈ 0.2735 | 1760 bits |
| [25] | 7Th + Tpk + Ts | 9Th + Tpk + 2Ts | 16Th + 2Tpk + 3Ts ≈ 1.0781 | 1344 bits |
| [35] | 10Th + 3Tchao | 3Th + 2Tchao | 13Th + 5Tchao ≈ 0.3365 | 1184 bits |
| [30] | 2Th + 3Tm | 2Th + 3Tm | 4Th + 6Tm ≈ 0.3805 | 1280 bits |
| Our | 6Th + 2Tm | 4Th + 2Tm + 2Ts | 10Th + 4Tm + 2Ts ≈ 0.2747 | 1280 bits |
In the login and authentication phase of BBAKA protocol, the mobile device executes six one-way hash function operations and two elliptic curve point multiplication operations. So the execution time of the mobile device is 6Th + 2Tm. The server executes four one-way hash function operations, two elliptic curve point multiplication operations and two symmetric encryption/decryption operations. So the execution time of the server is 4Th + 2Tm + 2Ts. Thus, the total execution time of BBAKA protocol is 10Th + 4Tm + 2Ts ≈ 10 × 0.0005 + 4 × 0.063075 + 2 × 0.0087 ≈ 0.2747 (second).
The mobile device sends request message {EIDi,Xi,Vi,T1} to the server, and then the server sends response message to the mobile device. So the communication cost of BBAKA protocol is 1280 bits.
According to Fig. 8, the total execution time of BBAKA protocol is obviously the least. Compared with protocols of Lwamo et al. [25] and Salem et al. [30], the total time-consuming of BBAKA protocol is reduced by about 74.5% and 27.8% respectively. In terms of communication cost, Fig. 9 shows that our protocol is significantly superior to the protocols [24] and [25], and almost equal to protocols [28, 35] and [30]. Also, our protocol can overcome four weaknesses of Ostad-Sharif et al.’s scheme [28] and Sureshkumar et al.’s scheme [35]. Compared with Li et al’s scheme [24], the communication overhead of BBAKA protocol is reduced by 27.3%. Although the communication cost of BBAKA protocol is slightly higher than Sureshkumar et al.’s protocol [35], it can overcome four weaknesses of their scheme. In summary, BBAKA protocol has great advantages in both execution time and communication cost.
Fig. 8.
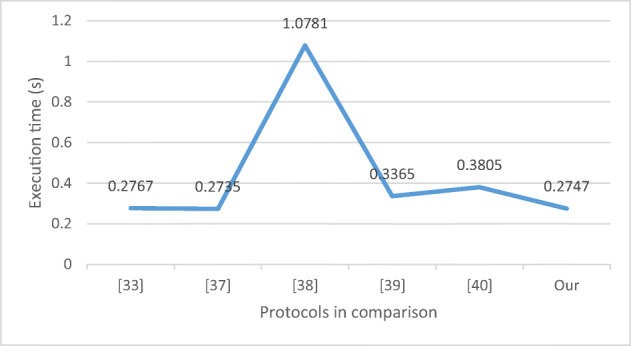
Execution time illustration of different protocols
Fig. 9.
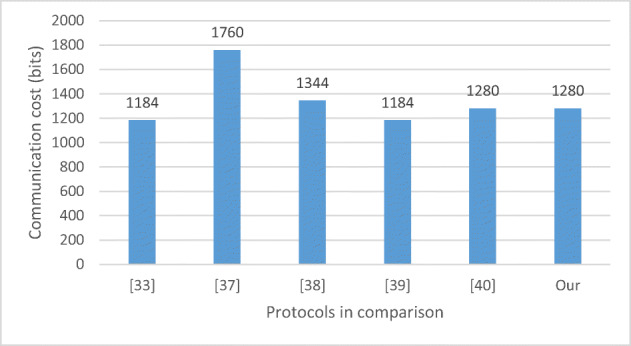
Communication cost illustration of different protocols
Conclusions
In this paper, Ostad-Sharif et al.’s scheme is reviewed, and then we point out that their scheme cannot provide the strong authentication and is vulnerable to off-line password guessing attack. Moreover, their scheme fails to update password correctly in the password change phase. To overcome these weaknesses, we propose a biometrics-based mutual authentication and key agreement protocol for TMIS. We take full advantage of lightweight cryptographic primitives such as ECC and hash functions, which makes our protocol more suitable for TMIS. Our protocol can provide not only the three security missing in Ostad-Sharif et al.’s protocol but also other security, such as user anonymity, un-traceability, perfect forward secrecy, etc. In addition, it can also resist all kinds of known attacks, such as stolen-verifier attack, privileged insider attack, replay attack, etc. Also, we prove the security of BBAKA protocol by formal method under ROM. Compared with related existing protocols, our protocol has less computation cost and communication overhead. In the future work, we will consider designing the key agreement protocol based on lattice cryptography to further improve the efficiency and security of the scheme.
Footnotes
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Yulei Chen, Email: ylchen.math@whu.edu.cn.
Jianhua Chen, Email: chenjh_ecc@163.com.
References
- 1.Alsmirat MA, Al-Alem F, Al-Ayyoub M, Jararweh Y, Gupta B. Impact of digital fingerprint image quality on the fingerprint recognition accuracy. Multimedia Tools and Applications. 2019;78(3):3649–3688. doi: 10.1007/s11042-017-5537-5. [DOI] [Google Scholar]
- 2.Amin R, Islam SH, Biswas GP, Khan MK, Li X. Cryptanalysis and enhancement of anonymity preserving remote user mutual authentication and session key agreement scheme for e-health care systems. J Med Syst. 2015;39(11):1–21. doi: 10.1007/s10916-015-0318-z. [DOI] [PubMed] [Google Scholar]
- 3.Awasthi AK, Lal SS. A remote user authentication scheme using smart cards with forward secrecy. IEEE Trans Consum Electron. 2003;49(4):1246–1248. doi: 10.1109/TCE.2003.1261225. [DOI] [Google Scholar]
- 4.Awasthi AK, Srivastava K. A biometric authentication scheme for telecare medicine information systems with nonce. J Med Syst. 2013;37(5):1–4. doi: 10.1007/s10916-013-9964-1. [DOI] [PubMed] [Google Scholar]
- 5.Bellare M, Pointcheval D, Rogaway P. Authenticated key exchange secure against dictionary attacks. theory and application of cryptographic techniques. 2000;1807:139–155. [Google Scholar]
- 6.Boyen X (2009) Hidden credential retrieval from a reusable password. In: ASIACCS’09: Proceedings of the 4th International Symposium on Information, Computer, and Communications Security, Sydney Australia, pp 228–238
- 7.Chang Y, Yu S, Shiao D. A uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J Med Syst. 2013;37(2):9902. doi: 10.1007/s10916-012-9902-7. [DOI] [PubMed] [Google Scholar]
- 8.Chaudhry SA. A secure biometric based multi-server authentication scheme for social multimedia networks. Multimedia Tools and Applications. 2016;75(20):12705–12725. doi: 10.1007/s11042-015-3194-0. [DOI] [Google Scholar]
- 9.Chaudhry SA, Mahmood K, Naqvi H, Khan MK. An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J Med Syst. 2015;39(11):1–12. doi: 10.1007/s10916-015-0335-y. [DOI] [PubMed] [Google Scholar]
- 10.Das AK, Goswami A. A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J Med Syst. 2013;37(3):9948. doi: 10.1007/s10916-013-9948-1. [DOI] [PubMed] [Google Scholar]
- 11.Das AK, Goswami A. An enhanced biometric authentication scheme for telecare medicine information systems with nonce using chaotic hash function. J Med Syst. 2014;38(6):1–19. doi: 10.1007/s10916-014-0027-z. [DOI] [PubMed] [Google Scholar]
- 12.Dodis Y, Reyzin L, Smith A (2004) Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. theory and application of cryptographic techniques, pp 523–540
- 13.Esposito C, Ficco M, Gupta BB. Blockchain-based authentication and authorization for smart city applications. Information Processing & Management. 2021;58(2):102468. doi: 10.1016/j.ipm.2020.102468. [DOI] [Google Scholar]
- 14.Gupta BB, Quamara M. An overview of internet of things (iot): architectural aspects, challenges, and protocols. Concurrency and Computation: Practice and Experience. 2020;32(21):e4946. doi: 10.1002/cpe.4946. [DOI] [Google Scholar]
- 15.He D, Kumar N, Chen J, Lee C, Chilamkurti N, Yeo S. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Systems. 2015;21(1):49–60. doi: 10.1007/s00530-013-0346-9. [DOI] [Google Scholar]
- 16.He D, Kumar N, Khan MK, Lee J. Anonymous two-factor authentication for consumer roaming service in global mobility networks. IEEE Trans Consum Electron. 2013;59(4):811–817. doi: 10.1109/TCE.2013.6689693. [DOI] [Google Scholar]
- 17.He D, Wang D. Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst J. 2015;9(3):816–823. doi: 10.1109/JSYST.2014.2301517. [DOI] [Google Scholar]
- 18.He D, Wu S. Security flaws in a smart card based authentication scheme for multi-server environment. Wirel Pers Commun. 2013;70(1):323–329. doi: 10.1007/s11277-012-0696-1. [DOI] [Google Scholar]
- 19.Hwang M, Li L. A new remote user authentication scheme using smart cards. IEEE Trans Consum Electron. 2000;46(1):28–30. doi: 10.1109/30.826377. [DOI] [Google Scholar]
- 20.Islam SKH, Vijayakumar P, Bhuiyan ZA, Amin R, Rajeev MV, Balusamy B. A provably secure three-factor session initiation protocol for multimedia big data communications. IEEE Internet Things J. 2018;5(5):3408–3418. doi: 10.1109/JIOT.2017.2739921. [DOI] [Google Scholar]
- 21.Kumari S, Khan MK. Cryptanalysis and improvement of ’a robust smart-card-based remote user password authentication scheme’. Int J Commun Syst. 2014;27(12):3939–3955. doi: 10.1002/dac.2590. [DOI] [Google Scholar]
- 22.Leu J, Hsieh W. Efficient and secure dynamic id-based remote user authentication scheme for distributed systems using smart cards. Iet Information Security. 2014;8(2):104–113. doi: 10.1049/iet-ifs.2012.0206. [DOI] [Google Scholar]
- 23.Li C, Hwang M. An efficient biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl. 2010;33(1):1–5. doi: 10.1016/j.jnca.2009.08.001. [DOI] [Google Scholar]
- 24.Li X, Wu F, Khan MK, Xu L, Shen J, Jo M. A secure chaotic map-based remote authentication scheme for telecare medicine information systems. Futur Gener Comput Syst. 2018;84:149–159. doi: 10.1016/j.future.2017.08.029. [DOI] [Google Scholar]
- 25.Lwamo NassoroMR, Zhu L, Xu C, Sharif K, Liu X, Zhang C. Suaa: a secure user authentication scheme with anonymity for the single & multi-server environments. Inf Sci. 2019;477:369–385. doi: 10.1016/j.ins.2018.10.037. [DOI] [Google Scholar]
- 26.Malasri K, Wang L. Design and implementation of a secure wireless mote-based medical sensor network. Sensors. 2009;9:6273–6297. doi: 10.3390/s90806273. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 27.Messerges TS, Dabbish EA, Sloan RH. Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput. 2002;51(5):541–552. doi: 10.1109/TC.2002.1004593. [DOI] [Google Scholar]
- 28.Ostadsharif A, Abbasinezhadmood D, Nikooghadam M. An enhanced anonymous and unlinkable user authentication and key agreement protocol for tmis by utilization of ecc. Int J Commun Syst. 2019;32(5):e3913. doi: 10.1002/dac.3913. [DOI] [Google Scholar]
- 29.Ravanbakhsh N, Nazari M. An efficient improvement remote user mutual authentication and session key agreement scheme for e-health care systems. Multimedia Tools and Applications. 2018;77(1):55–88. doi: 10.1007/s11042-016-4208-2. [DOI] [Google Scholar]
- 30.Salem FM, Amin R. A privacy-preserving rfid authentication protocol based on el-gamal cryptosystem for secure tmis. Inf Sci. 2020;527:382–393. doi: 10.1016/j.ins.2019.07.029. [DOI] [Google Scholar]
- 31.Shunmuganathan S, Saravanan RD, Palanichamy Y. Secure and efficient smart-card-based remote user authentication scheme for multiserver environment. Can J Electr Comput Eng. 2015;38(1):20–30. doi: 10.1109/CJECE.2014.2344447. [DOI] [Google Scholar]
- 32.Singh AK, Solanki A, Nayyar A, Qureshi B. Elliptic curve signcryption-based mutual authentication protocol for smart cards. Appl Sci. 2020;10(22):8291. doi: 10.3390/app10228291. [DOI] [Google Scholar]
- 33.Stergiou CL, Psannis KE, Gupta BB (2020) Iot-based big data secure management in the fog over a 6g wireless network. IEEE Internet Things J.
- 34.Sun H. An efficient user authentication scheme using smart cards. IEEE Trans Consum Electron. 2000;46(4):958–961. doi: 10.1109/30.920446. [DOI] [Google Scholar]
- 35.Sureshkumar V, Amin R, Obaidat MS, Karthikeyan I. An enhanced mutual authentication and key establishment protocol for tmis using chaotic map. Journal of Information Security and Applications. 2020;53:102539. doi: 10.1016/j.jisa.2020.102539. [DOI] [Google Scholar]
- 36.Tewari A, Gupta BB. Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for iot devices using rfid tags. The Journal of Supercomputing. 2017;73(3):1085–1102. doi: 10.1007/s11227-016-1849-x. [DOI] [Google Scholar]
- 37.Tsai J, Lo N, Wu T. Novel anonymous authentication scheme using smart cards. IEEE Transactions on Industrial Informatics. 2013;9(4):2004–2013. doi: 10.1109/TII.2012.2230639. [DOI] [Google Scholar]
- 38.Wang D, Wang P. Two birds with one stone: two-factor authentication with security beyond conventional bound. IEEE transactions on dependable and secure computing. 2016;15(4):708–722. [Google Scholar]
- 39.Wang H, Li Z, Li Y, Gupta BB, Choi C. Visual saliency guided complex image retrieval. Pattern Recogn Lett. 2020;130:64–72. doi: 10.1016/j.patrec.2018.08.010. [DOI] [Google Scholar]
- 40.Yang G, Wong DS, Wang H, Deng X. Two-factor mutual authentication based on smart cards and passwords. J Comput Syst Sci. 2008;74(7):1160–1172. doi: 10.1016/j.jcss.2008.04.002. [DOI] [Google Scholar]
- 41.Yu C, Li J, Li X, Ren X, Gupta BB. Four-image encryption scheme based on quaternion fresnel transform, chaos and computer generated hologram. Multimedia Tools and Applications. 2018;77(4):4585–4608. doi: 10.1007/s11042-017-4637-6. [DOI] [Google Scholar]