Abstract
Contact tracing involves collecting people’s information to track the spread of COVID-19 and to warn people who have been in the proximity of infected individuals. This measure is important to public health and safety during the pandemic. However, customers’ concerns about the violation of their privacy might inhibit their cooperation in the contact tracing process, which poses a risk to public safety. This research investigates how to facilitate customers’ cooperative behavior in contact tracing based on cognitive trust and affective trust. The findings show that cognitive trust increases people’s willingness to disclose information and reduces their willingness to falsify it, whereas affective trust increases the willingness for both disclosure and falsification. This research contributes to the literature on customer data privacy by illuminating how cognitive and affective trust distinctly influence cooperative behavior, which has important implications for hospitality businesses.
Keywords: Contact tracing, Willingness to disclose, Hospitality, Trust, Data privacy, COVID-19
1. Introduction
Contact tracing is a measure for mitigating the transmission of infectious diseases, which is important to public health and safety during the COVID-19 pandemic (World Health Organization, 2020). It requires businesses to collect customers’ personal information (e.g., name, phone number, location, and travel history) in order to track the spread of the virus and to warn people who have been in the proximity of infected individuals (Servick, 2020). An increasing number of countries have implemented contact tracing in hospitality venues, such as restaurants, cafes, pubs, and clubs. For example, New Zealand’s largest online restaurant-booking website, Restaurant Hub, provides contact tracing instructions and QR codes for its registered venues (Restaurant Hub, 2020). Australia and the UK also require hospitality venues to collect customers’ contact details to support contact tracing (Government of NSW, 2020; The UK Government, 2020).
Contact tracing requires adequate customer cooperation to be effective (The New Daily, 2020). However, many customers of hospitality businesses have been reported to be reluctant to cooperate because of privacy concerns, posing a serious threat to public safety (The Conversation, 2020; Yahoo, 2020). Therefore, the present research draws on customer data privacy literature to investigate the main reasons behind customer reluctance to cooperate in contact tracing during the COVID-19 pandemic.
Drawing on the social exchange theory, extant literature on customer data privacy suggests that customers relinquish their personal information in exchange for products or services (Krishen et al., 2017; Lwin et al., 2007; Martin and Murphy, 2017; Schumann et al., 2014; White, 2004). Due to increasingly personalized advertisements and widely reported data scandals (e.g., the Facebook–Cambridge Analytica scandal), customers have become wary of the potential risk of disclosing their personal information (e.g., data access, breach, and misuse) and feel vulnerable in such exchanges (Kim et al., 2018; Krafft et al., 2017; Martin et al., 2017). Their perceived vulnerability triggers uncooperative behavioral intentions toward information requesters, including withholding and falsifying information (Martin et al., 2017).
Recent research on customer data privacy calls for examining interpersonal trust as a mechanism for promoting customers’ cooperative behavior (Bleier and Eisenbeiss, 2015; Jagadish, 2020; Martin and Murphy, 2017; Steinhoff et al., 2019; Waldman, 2018). Trust is a sensitive indicator of people’s willingness to accept vulnerability with positive expectations and beliefs about the other party in social exchanges (Kim et al., 2004). Concerning data privacy, customers are willing to accept being vulnerable in disclosing information with a business that they trust because they have positive expectations of it (Lwin et al., 2007; Waldman, 2018).
Despite the substantial role of trust in influencing customers’ cooperative behavior, research on customer data privacy has not yet considered the effects of different forms of trust. Grounded in social exchange theory, the trust literature has identified two forms of trust: cognitive trust and affective trust (e.g., McAllister, 1995). Cognitive trust refers to the rational evaluation of whether the other party to an exchange is trustworthy based on the knowledge and information regarding its ability, professionalism, and reliability (McAllister, 1995; Schaubroeck et al., 2011; Su and Mattila, 2020; Yang and Mossholder, 2010). Affective trust refers to the emotional bonds or connections with the party to the exchange that are grounded in the care and concern that it demonstrates (McAllister, 1995; Schaubroeck et al., 2011; Su and Mattila, 2020; Yang and Mossholder, 2010).
Past research has shown that these two forms of trust are driven by different antecedents and lead to different behavioral outcomes in leadership and organizational behavior (Nienaber et al., 2015; Schaubroeck et al., 2011). However, it is unclear how these two forms of trust evolve and distinctively influence customers’ cooperative behavior related to data privacy. To address this research gap and link to the COVID-19 pandemic, this research investigates the following questions: (1) How do cognitive trust and affective trust influence different cooperative behaviors toward contact tracing? (2) What are the antecedents for different forms of trust in contact tracing?
This research makes several theoretical contributions. First, it is among the first to apply cognitive and affective trust as psychological mechanisms to explicate different cooperative behaviors, namely, disclosure and falsification, related to data privacy, especially in the context of contract trancing. Our findings add theoretical nuance to the literature on customer data privacy (e.g., Janakiraman et al., 2018; Kashmiri et al., 2017; Martin et al., 2017) by showing that these two forms of trust have divergent effects. Second, this research identifies contact tracing-related perceptual factors and illuminates how they contribute to different forms of trust, thus adding to research on the antecedents of trust (Acquisti et al., 2015, 2012). Taken together, our findings have important implications for the hospitality industry and governments in facilitating customer cooperation in contact tracing.
The remainder of this paper is organized as follows: We review the relevant literature to develop our hypotheses regarding how cognitive trust and affective trust drive cooperative behaviors in contact tracing. We then conduct an exploratory qualitative study to identify the relevant perceptual antecedents and revert to the literature to conceptualize how they influence the two forms of trust. After establishing our conceptual model, we employ a survey study to test all hypotheses. Finally, we discuss the theoretical contributions and practical implications of our findings.
2. Conceptual development
Despite the benefit of contact tracing to public health and safety in the COVID-19 pandemic, it has been reported that many customers are reluctant to cooperate when they are asked to provide their personal information (The Conversation, 2020; Yahoo, 2020). Thus, it is important for us to understand the major obstacles to customer cooperative behaviors in contact tracing. To do so, we conducted a short survey of 240 participants from the US on Amazon Mechanic Turk (see Appendix A for more details). 74 % of the participants reported that they had been asked to provide contact information at hospitality venues. However, only 24 % of them reported having provided correct and complete information each time. Furthermore, among a range of plausible reasons, the most chosen reason for their reluctance to cooperate was their concern about privacy (for 68 % of the participants). These findings allow us to draw on customer data privacy literature to investigate cooperative behavior in contact tracing.
2.1. Contact tracing as social exchange
By drawing on social exchange theory (Blau, 1964), the literature on customer data privacy conceptualizes the provision of personal information as a form of social exchange in which customers relinquish their personal information in order to gain access to services or to obtain more relevant and better services from businesses (e.g., Martin and Murphy, 2017; Schumann et al., 2014; White, 2004). Whether to provide personal information or not depends on the customer’s evaluation of the expected benefit and cost of doing so. In this evaluation, the cost is largely associated with the perceived privacy vulnerability (Schumann et al., 2014). Privacy is defined as the customer’s control over the dissemination and use of their information (Jaap et al., 2021; Martin and Murphy, 2017). As customers have less control over their information after relinquishing it to a business, they become vulnerable to its potential misuse (Martin et al., 2017).
By applying this notion to the context of our research, contact tracing can be viewed as the exchange between customers and hospitality businesses where customers may feel that control has been taken over their information in exchange for services, leading consumers to feel vulnerable to privacy-related risks. Such vulnerability creates barriers for customers to cooperate in contact tracing.
2.2. Trust as the core mechanism of cooperation in contact tracing
Trust refers to an individual’s intention to accept vulnerability based upon positive expectations of the exchange party’s intentions or behavior (Kim et al., 2004). Trust acts as a core mechanism to facilitate people’s cooperation with the exchange party (Aguirre et al., 2015; Luo, 2002; Schaubroeck et al., 2011). When customers trust a business, they tend to accept their vulnerability because they believe that the business will handle their information appropriately (Martin et al., 2017). Hence, in terms of data privacy, trust generally increases customers’ cooperation with the business by disclosing information to it (Lwin et al., 2007; Martin et al., 2017; Wirtz and Lwin, 2009). Our literature review (Table 1 ) shows that prior research on trust and cooperative behavior related to data privacy has not considered different forms of trust and their effects on different cooperative behaviors such as willingness to disclose and falsify. The present research aims at addressing these research gaps.
Table 1.
Empirical studies on trust and customer cooperative behavior related to data privacy.
| Article | Context | Cooperative behavior (outcome variable) | Conceptualization of trust (explanatory variable) | Key findings | Examine both disclosure and falsification behaviors | Examine the effects of both affective and cognitive trust |
|---|---|---|---|---|---|---|
| Our research | Contact tracing (the hospitality and service industry) | Willingness to disclose, willingness to falsify | Cognitive trust and affective trust | Cognitive trust and affective trust have distinct effects on willingness to disclose and willingness to falsify. | Yes | Yes |
| Hospitality and tourism | ||||||
| Ioannou et al. (2020) | Travel (online) | Willingness to share information | Travelers’ trust. Trust is defined as “willingness to be vulnerable to the actions of another.” (p. 4) | Trust can reduce risk beliefs and encourages people to share their information. | No | No |
| Morosan and DeFranco (2015) | Mobile apps (hotel) | Willingness to disclose | Trust in organization and trust in system/app. Trust is viewed as “a social relationship where principals invest resources in agents in exchange for an uncertain future benefit.” (p. 123) | Consumer trust in hotel apps has a positive effect on willingness to disclose information. | No | No |
| Marketing | ||||||
| Aiken and Boush (2006) | Websites | Willingness to provide personal information | Signals of trust: a third-party certification, an objective-source rating, and an implication of investment in advertising. Perceived trustworthiness: cognitive, affective, and behavioral |
Trust signals can influence consumers’ perceived security and privacy, perceived firm trustworthiness, and willingness to provide personal information. | No | Yes |
| Bansal et al. (2016) | Online service context (financial websites) | Intention to disclose information | Trust in the website. Trust is defined as “the willingness to depend on another person or institution based on the belief in the integrity, ability, and benevolence of the other party.” (p.1) | Trust has an important impact on disclosure intention. This impact is influenced by customer personality and the sensitivity of the context. | No | No |
| Bart et al. (2005) | Websites | Behavioral intent (e.g., providing personal information, purchase intention, word of mouth) | Online trust. Trust is defined as “a psychological state comprising the intention to accept vulnerability based on positive expectations of the intentions or behaviors of Another.” (p.134) |
Online trust mediates the relationships between the characteristics of websites and consumers and consumer behavioral intent. | No | No |
| Cho (2006) | business-to-consumer (B2C) Internet exchange relationships | Self-disclosure and willingness to commit | Trust and distrust. Trust and distrust are considered as distinct entities. | Trust and distrust have different effects on customer behavioral intentions such as self-disclosure. | No | No |
| Grosso et al. (2020) | Retailing (online and offline) | Willingness to disclose | Micro- and micro-level trust: trust in a retail personnel, trust in a retailer, trust in a country | The interaction between three types of trust, privacy concerns, and information type influence consumers’ willingness to disclose. | No | No |
| Martin et al. (2017) | Retail, financial services, and technology | Falsifying information, negative word of mouth, switching behavior | Cognitive trust and feelings of violation. Cognitive trust is defined as “customer’s willingness to rely on a firm in which (s)he has confidence.” (p. 39) | Cognitive trust and feelings of violation mediate the relationships between data vulnerabilities and behavioral outcomes such as falsification. | No | No |
| Mothersbaugh et al. (2012) | Online service context (online TV program guide) | Willingness to disclose | Firm trust. It was measured based on whether a firm could be trusted, counted on, and relied on. | Firm trust is a key mechanism that mediates antecedents and disclosure intention. Specifically, firm trust can reduce perceived risk of disclosure. | No | No |
| White (2004) | Relationship marketing | Willingness to disclose | Relational depth (trust is considered as the underlying theoretical mechanism without being explicitly tested). | Deep relationship perceptions are associated with strong satisfaction and trust. Such perceptions can reduce risks in disclosing certain kinds of information but increase risks in disclosing embarrassing information. | No | No |
| Wirtz and Lwin (2009) | Online retailing | Relational behavior (provision and updating of customer information) | Trust in the website. Trust means that “customers have faith in the organization’s reliability and integrity and feel secure about sharing their personal information with the organization.” (p. 192) | Trust facilitates consumers’ relational behavior such as providing and updating their information on the website. | No | No |
| Information management | ||||||
| Anderson and Agarwal (2011) | Healthcare (digital) | Willingness to provide access to personal information, willingness to disclose | Trust in electronic medium. Trust is defined as “a multi-dimensional construct comprising of competence, reliability, and safety trusting beliefs; i.e., the individual’s belief that electronic storage provides a reliable and safe environment in which to store health information, and her belief that the electronic storage format provides the necessary components to facilitate electronic storage of health information.” (p. 474) |
Trust, intended purpose, and type of information have interaction effects on willingness to disclose and willingness to provide access. | No | No |
| Chai et al. (2011) | Blog | Knowledge sharing behaviors | Bloggers’ Trust. Trust is defined as “a user’s beliefs about the reliability, credibility, and accuracy of information gathered through the Web.” (p.318) | Bloggers’ trust, strength of social ties, and reciprocity all influence their knowledge sharing behavior positively. | No | No |
| Dinev and Hart (2006) | Online transactions | Willingness to provide personal information | Internet trust. Trust is defined as “beliefs reflecting confidence that personal information Internet websites will be handled competently.” (p. 64) | Internet trust has a positive effect on willingness to provide personal information to transact on the Internet. | No | No |
| Kehr et al. (2015) | Mobile application (driving behavior app) | Intention to disclose | Institutional trust. It is defined as “an individual's confidence that the data‐requesting medium will not misuse his or her data.” (p. 611) | Institutional trust influences consumers’ intention to disclose private information. | No | No |
| Malhotra et al. (2004) | E-commerce | Behavioral intention (intention to reveal personal information) | Trusting belief. It is defined as “the degree to which people believe a firm is dependable in protecting consumers’ personal information.” (p. 341) | Trusting beliefs negatively influence risk beliefs and positively influence intentions to reveal personal information. | No | No |
| Miltgen and Smith (2019) | Commercial websites | Withholding, falsification | Trust. It refers to “an individual’s trust in an entity that is requesting data.” (p. 706) | Trust reduces customers’ intentions to withhold and falsify their information. | No | No |
| Zimmer et al. (2010) | Websites | Intention to disclose | Trust in website. It refers to the “belief that the website is benevolent, competent, or honest in handling personal information.” (p. 117) | Trust can encourage people to disclose information because it reduces risk perceptions associated with disclosure. | No | No |
| Contact tracing | ||||||
| Guillon and Kergall (2020) | Digital contact tracing | Willingness to use a contact-tracing application (disclosing information to the application) | Trust in the government. It is defined as trust in the government to handle the health crisis. | Trust is significantly related to people’s willingness to use a contact-tracing application. | No | No |
| Hu et al. (2020) | COVID-19 safety measures (e.g., contact tracing) | Compliance with safety measures. | NA | Hospitality employees’ compliance with safety measures is driven by management practices and organizational crisis strategies. | No | No |
| Trang et al. (2020) | Digital contact tracing | Intention to install contact tracing app (disclosing information to the app) | NA | The benefit appeals, privacy designs, and convenience influence peoples’ intention to install contact tracing apps. | No | No |
Trust consists of two conceptually different forms—cognition-based and affect-based trust (Hon and Lu, 2010; Massey et al., 2019; McAllister, 1995; Tomlinson et al., 2020). Cognitive trust develops through knowledge and information that enables individuals to evaluate the other party’s competence and reliability, while affective trust is generated from positive feelings based on care and concern demonstrated by the other party (McAllister, 1995; Schaubroeck et al., 2011; Yang and Mossholder, 2010). We propose that these two forms of trust may influence customer cooperative behaviors differently due to their distinct characteristics. Specifically, we focus on disclosure and falsification as two specific behaviors.
Customers’ willingness to disclose represents their intention to cooperate publicly, and thus is an important behavioral outcome in the exchange of information between customers and businesses (Martin and Murphy, 2017). When customers disclose information, they can inconspicuously provide truthful information or offer false or incomplete information, which is called “falsification” (Lwin et al., 2007; Norberg and Horne, 2014). Falsification can complicate contact tracing efforts and put public health at risk (Queensland Government, 2020). Therefore, we conceptualize willingness to disclose and willingness to falsify as separate behaviors toward contact tracing and investigate how they are influenced by cognitive trust and affective trust.
Cognitive trust. Cognitive trust is individuals’ evaluation of the exchange party regarding whether it is competent, professional, and capable of handling the exchange (Johnson and Grayson, 2005; McAllister, 1995). In the context of contact tracing, customers who have cognitive trust in a business hold positive expectations that the business will implement an appropriate process in collecting, storing, and using their data (Martin et al., 2017). Such positive expectations of competence in data management increase customers’ willingness to accept their vulnerability in this exchange. Therefore, high cognitive trust in a business motivates customers to cooperate by disclosing truthful information that can support its purpose of contact tracing. In contrast, low cognitive trust in a business makes customers feel vulnerable to privacy-related risks such that they tend to exhibit behavioral reactance, such as withholding and falsification. Therefore, we propose the following:
H1
Customers’ cognitive trust in the business is positively related to their willingness to disclose (H1a) and negatively related to their willingness to falsify (H1b) in contact tracing conducted by this business.
Affective trust. Affective trust captures individuals’ positive feelings and emotions of the exchange party which are grounded in its demonstrated concern and care (Johnson and Grayson, 2005; McAllister, 1995). If individuals feel that the exchange party has concern and care for them, they tend to disclose broader and deeper information (Borg and Freytag, 2012; Park et al., 2011). This is because individuals reciprocate by providing their information to the exchange party in order to maintain a positive relationship (Moon, 2000; Park et al., 2011; White, 2004). In light of this notion, high affective trust associated with a business should increase customers’ willingness to disclose in contact tracing.
However, as positive feelings and emotions toward the business deepen, the associated motive to maintain this relationship can also become a pressure that leads to the invasion of people’s privacy (O’Malley et al., 1997; Song et al., 2016; Steinhoff et al., 2019). That is, individuals may feel obligated to comply with the request for disclosure from the exchange party without knowing if their privacy will be competently protected. To resolve this relationship maintenance–privacy risk dilemma, they can take a symbolic cooperative action—falsification—to maintain the relationship with the business without putting their privacy at risk. Therefore, affective trust can increase customers’ willingness to disclose but also increase their willingness to falsify. Formally, we propose:
H2
Customers’ affective trust in the business is positively related to their willingness to disclose (H2a) and their willingness to falsify (H2b) in contact tracing conducted by this business.
2.3. Perceptual antecedents of trust in the context of contact tracing
Past studies on customer data privacy show that customers’ trust and cooperative behaviors toward businesses are driven by various perceptual antecedents (Acquisti et al., 2015, 2012; Bansal et al., 2016; Su and Mattila, 2020; Yang et al., 2019). As hospitality businesses have only started adopting contact tracing since the COVID-19 pandemic, the perceptual antecedents of cognitive trust and affective trust in this context are unclear. Therefore, we conducted a pilot qualitative study to identify the most relevant perceptual antecedents. We followed protocols from Kvale (1996) to design semi-structured interviews and used convenience sampling to recruit 24 participants (including a pilot test with five participants) with experience and knowledge of contact tracing from Anglosphere countries, including Australia, New Zealand, the UK, the US, and Canada (see Appendix B for the participants’ profile). Our interview questions primarily focused on exploring participants’ experiences with contact tracing in hospitality venues (e.g., restaurants, cafes, and bars), the main reasons and drivers for their cooperative (or uncooperative) behavior, and their perceptions of the practices of hospitality businesses and governments (see Appendix C for interview questions).
We conducted thematic analysis (Braun and Clarke, 2006) and identified four key perceptual factors influencing cooperative behaviors in contact tracing: 1) perceived ethics of data collection, 2) perceived data protection policy, 3) perceived governmental regulation, and 4) perceived prevalence of participation, as shown in Table 2 (see Appendix D for detailed data analysis). We explain each of these perceptual antecedents in the following section. For each perceptual antecedent, we first illustrate its meanings and characteristics based on our qualitative findings, and then draw on the relevant literature to explain and predict how this antecedent influences the two forms of trust.
Table 2.
Summary of first-order codes, and second- and third-order themes (pilot study).
| First-order code | Second-order theme | Third-order theme |
|---|---|---|
| Data are collected to help stop the spread of COVID-19 | Perceived societal benefits | Perceived ethics of data collection |
| Data are collected to help hospitality businesses stay open and provide services for people | ||
| Hospitality businesses collect information because they want to protect customers | Perceived ethical consideration | |
| Hospitality businesses lack ethics because they collect customers’ data for targeted marketing | ||
| Collecting data for contact tracing is the businesses’ civic duty | Perceived social responsibility | |
| Every member of society has the obligation to support contact tracing | ||
|
| ||
| Only customers own their data, and they decide what information to share and with whom they share their information | Perceived data ownership | Perceived data protection policy |
| Customers are unaware of the ownership of their data | ||
| Customers give up the ownership of their data to businesses when they share information | ||
| Customers are concerned about hospitality staff’s unprofessional conduct | Perceived data protection in the collection process | |
| Hospitality businesses do not have adequate explanations for how they keep customer information confidential | ||
| Hospitality businesses do not provide information about customer data storage | Perceived data control | |
| The collected customer data should be used only by authorities, and only for contact tracing | ||
| The business controls the collected information and should be responsible for its safety | ||
|
| ||
| The uniform pattern of the QR codes and contact tracing app for businesses make me confident in the government | Confidence in regulators | Perceived governmental regulation |
| The government has made strong efforts to control the pandemic | ||
| The government wants to protect customers; so customers follow its regulations | ||
| Laws and regulations (including penalties) should supervise the use of customers’ data | Perceived sufficiency of regulations | |
| Government websites keep the public informed about data policy and regulation | ||
| The government encourages everyone to participate in contact tracing | Perceived regulation enforcement and policy support | |
| The tool of QR codes for businesses shows technological support from the authorities | ||
| The government should have provided stricter guidelines on how to collect store, and use data | ||
|
| ||
| Customers follow hospitality contact tracing because they see everyone uses/accepts it frequently |
Perceived prevalence |
Perceived prevalence/social norms for information disclosure |
| Contact tracing information frequently appears in the news and other media channels | ||
| Employers encourage people to participate in contact tracing | ||
| Contact tracing instructions are available at malls, parks, hotels, subways, etc. | ||
| The use of QR codes for contact tracing is a new normal |
Social norm | |
| All my family members, friends, and colleagues are okay with providing their information | ||
Perceived ethics of data collection. Our qualitative findings reveal that participants were willing to disclose their personal information if they perceived the following ethical characteristics of hospitality businesses: ethical considerations (e.g., the data were collected to protect other customers rather than to target customers for commercial purposes), societal benefits (e.g., data collection helps stop the spread of COVID-19, and helps businesses stay open and provide services for people), and social responsibility (e.g., businesses exercise responsibility in protecting their customers and honor their obligation to support contact tracing). For example, one participant (ID 01) emphasized that restaurants do not collect data for self-interest by stating: “They [restaurants] have collected information because they're looking after their customers. The information that they’ve collected is basically for the use of public health and for the benefit of customers … it’s to protect them …. I very much doubt that they [restaurants] would be misusing it.”
Many studies have shown that ethics are vital to the development of customer trust (Martínez and Del Bosque, 2013; Stanaland et al., 2011; Sung and Kim, 2010). Customers have positive expectations of an ethical business that exercises social responsibility and cares about public well-being (Fan, 2005; Singh et al., 2012). This expectation can be generalized to the customers’ belief that ethical businesses are also concerned with, and care about, their customers in implementing contact tracing. Therefore, customers feel less vulnerable and have higher trust in ethical businesses.
As businesses’ ethics reflect their motives and characteristics, such as altruism, benevolence, and sincerity, that generate positive feelings among customers and help form emotional bonds with them (Fan, 2005; Sung and Kim, 2010), such ethics contribute to affective trust. However, ethics do not convey any information about the competence and professionalism of the business in managing customers’ data. Therefore, we propose the following hypothesis:
H3
Customers’ perceived ethics of data collection conducted by the business is positively related to their affective trust in this business.
Perceived data protection policy. Our interview participants believed that their data should be handled safely by businesses to avoid data breaches and scandals. They stressed the importance of a business’s control of data (e.g., ability to control the flow of data, and management of data storage and data safety), protection of data (e.g., confidentiality of customer information and employees’ professionalism in data management), and ownership of data (e.g., who owns customer data, and customers’ own access to their data). These three themes can be merged and interpreted as perceived data protection policy. For example, one participant (ID 02) mentioned that data protection policy is an important driver for information disclosure: “Usually, when you enter your information on the Internet, they [websites] recommend that you read the privacy policy, which indicates how they're going to protect your information. But at restaurants, they do not indicate anything like this. I don't actually know how they're going to protect my information. I feel kind of insecure, and I don’t really want to give up my information.”
Data protection policy describes the way in which businesses exercise ownership of and power over customer data, and how they protect their use of customer data (Lwin et al., 2007; Martin and Murphy, 2017; Xu et al., 2012). Customers nowadays have become increasingly wary of the data protection policies of businesses (Kim et al., 2018; Wright and Xie, 2019). If customers perceive that a business implements adequate data protection, they believe that it has the competence and professionalism to manage their data properly, and are thus more willing to accept vulnerability (Lwin et al., 2007; Steinhoff et al., 2019). Therefore, businesses that integrate strong data protection policies into effective marketing communication can build the positive belief of competence, professionalism, and reliability among customers (Martin and Murphy, 2017; Trim and Lee, 2019), which in turn contributes to cognitive trust. However, data protection policy is limited in building emotional bonds through care and concern toward customers. Therefore, we hypothesize:
H4
Customers’ perceived data protection policy of the business is positively related to their cognitive trust in this business.
Perceived governmental regulation. Our interview participants attached importance to how governments regulate their businesses’ contact tracing practices. They emphasized the following characteristics of governmental regulation: confidence in regulators (e.g., positive beliefs about the government’s efforts to control the pandemic and protect their citizens), sufficiency of regulations (e.g., adequacy of data security laws and policy of contact tracing), and regulation enforcement and policy support (e.g., governments encouraging citizens to participate in contact tracing and providing advice to businesses on how to collect, store, and protect customer data). For example, one participant (ID 10) claimed that governments should guide restaurants to conduct contact tracing by providing the relevant policies. She explained: “There should be some level of government intervention, at least some regular check or some regular audit to make sure the hospitality venues are following the rules and guidelines properly.”
Customers expect governments to act as an external force to supervise the data practices of businesses through regulations and policies (Acquisti et al., 2015; Kashmiri et al., 2017; Lwin et al., 2007; Poortinga and Pidgeon, 2006; Xu et al., 2012). Well-developed governmental regulation deters business misconduct, such as the misuse of customer data, and provides detailed guidance and support for businesses to engage in appropriate data practices (Lwin et al., 2007; Xu et al., 2012). With more regulations, guidance, and support from governments, businesses can more knowledgeably, competently, and professionally collect and manage customer data, thus gaining cognitive trust from customers. However, complying with government regulations does not necessarily mean that the business cares for, and is concerned about, its customers, which limits its impact on affective trust. We thus propose the following hypothesis:
H5
Customers’ perceived governmental regulation is positively related to their cognitive trust in the business.
Perceived prevalence of information disclosure. Participants tended to observe how other people respond to contact tracing requests and used their immediate social circle as a reference to guide their own behavior. They paid attention to prevalence (e.g., the majority of the population, popular content in media channels, and employers’ emphasis on contact tracing) and social norms (e.g., popular use of QR codes, and family, friends, and colleagues respecting contact tracing in hospitality venues). For example, one participant (ID 08) claimed that she would participate in contact tracing at restaurants without too much concern if she saw this behavior becoming a norm followed by many other people. She said: “When you see people write in their names, you just follow that [behavior] without even thinking about it.”
Social and peer influence play an important role in how people perceive and respond to privacy (Acquisti et al., 2015, 2012). Customers’ perceived prevalence of information disclosure captures the extent to which others are engaging in information disclosure (Dootson et al., 2017). According to the “bandwagon effect,” customers tend to follow what the majority believes and does because other people’s actions serve as social proof (Van Herpen et al., 2009). This social proof is premised on the belief that if other people believe in something or follow something, it must be good. Applying this logic to contact tracing, if customers observe many other people disclosing information to a business, they infer that these people must trust the business (or that this business is trustworthy). It may not be straightforward or easy for customers to observe on which form the trust is developed, thus they can attribute such trust to either cognitive trust or affective trust. Therefore:
H6
Customers’ perceived prevalence of information disclosure is positively related to their cognitive trust (H6a) and affective trust (H6b).
2.4. The conceptual model
Based on our hypothesis development, we propose a perception–trust–behavior intention framework to capture the psychological process that drives the cooperative behaviors of customers in the context of contact tracing. The antecedents of trust include four perceptual factors, as identified in the qualitative pilot study. The two forms of trust, cognitive and affective, in turn, influence customers’ willingness to disclose and willingness to falsify. Fig. 1 summarizes the conceptual model and the predicted relationships.
Fig. 1.
The conceptual model.
3. Method
Our study used a survey to test the conceptual model and our hypotheses. We provided a brief to give participants the background information on contact tracing (see Appendix E). To ease participants into a concrete context of consumption, the survey instructed them to read that a restaurant chain “X” was adopting contact tracing and asked them questions related to this restaurant’s contact tracing. We purposefully kept the brief short and generic in order to elicit participants’ reactions based on their experiences and perceptions of contact tracing in the context of restaurants/eateries. We pre-tested the brief with 15 participants and sought feedback from them to ensure that it was easy to understand and had no ambiguity.
3.1. Sample and procedure
We collected data from US participants in June 2020, when contact tracing in restaurants had already begun in other Anglosphere countries, such as the UK, Australia, and New Zealand, and was on the horizon for restaurants in the US (American Council on Science and Health, 2020; Government of NSW, 2020; Restaurant Hub, 2020; The UK Government, 2020). The US was an ideal location to test our conceptual model because (1) it had the highest number of confirmed infection cases in the world by June 2020, and (2) US customers might have been aware of contact tracing but not yet used to the practice, which suggests variations in their cooperative behavior.
Participants residing in the US were recruited from Amazon Mechanic Turk. Upon giving their consent, they were instructed to read the brief and then complete a questionnaire. In total, 420 participants took part in the survey. After removing cases with incomplete responses (n = 12) and those that failed the attention check (n = 43) (Huang et al., 2015), we obtained 365 valid responses (29.9 % female, 82.5 % aged from 18 to 45 years, 84.9 % with university degrees, 44.1 % with an annual income from $45,000 to $90,000). The demographic details are presented in Table 3 .
Table 3.
Demographic profile of the participants.
| Characteristics | n | % | |
|---|---|---|---|
| Age | 18−30 | 142 | 38.9 |
| 31−45 | 159 | 43.6 | |
| 46 and above | 64 | 17.5 | |
| Gender | Male | 255 | 69.9 |
| Female | 109 | 29.9 | |
| Other | 1 | 0.3 | |
| Annual income (pretax) | Less than $45,000 | 174 | 47.7 |
| $45,000 to $90,000 | 161 | 44.1 | |
| More than $90,000 | 30 | 8.2 | |
| Education | High school or lower | 32 | 8.8 |
| Vocational school | 23 | 6.3 | |
| Four-year college | 245 | 67.1 | |
| Graduate school | 65 | 17.8 | |
| Political affiliation | Democrat | 169 | 46.3 |
| Republican | 114 | 31.2 | |
| Independent | 72 | 19.7 | |
| Other | 10 | 2.7 | |
| Ethnicity | European American | 177 | 48.5 |
| African American | 38 | 10.4 | |
| Latino American | 50 | 13.7 | |
| Asian American | 56 | 15.3 | |
| Other | 44 | 12.1 |
3.2. Measurements
All measurements were adapted from existing scales into our research context. The measurement items were subjected to a series of pre-tests (n = 15) to check for their relevance, readability, and comprehensiveness. In addition, to ensure the substantive validity of the measurements, a committee of five marketing researchers was asked to assess the items and assign them to the corresponding constructs according to how well they reflected their full contents. In response, minor revisions in terms of wordings were made to improve the quality of the questionnaire.
Specifically, we measured perceived ethics of data collection (ETH) based on items from Edinger‐Schons et al. (2018). Perceived data protection policy (POL) was measured with items devised by Lwin et al. (2007). We adapted items from the literature (Lwin et al., 2007; Poortinga and Pidgeon, 2006) to measure perceived governmental regulation (REG), and items from Dootson et al. (2017) to measure perceived prevalence of information disclosure (PRE). Regarding trust, we modified items from interpersonal trust research (Johnson and Grayson, 2005; McAllister, 1995) to measure cognitive trust (COT), and affective trust (AFT). Finally, willingness to disclose (DCL) and willingness to falsify (FAL) were measured by items adapted from Morosan (2018) and Martin et al. (2017), respectively. All items were measured on seven-point Likert scales (see Appendix F for the full item list).
3.3. Analysis and results
We carried out data analysis following a two-stage procedure of structural equation modeling (Anderson and Gerbing, 1988) with SmartPLS 3 (Ringle et al., 2015). In the first stage, the psychometric properties (reliability and validity) of the measurement model were examined. In the second stage, the structural model was estimated, and the hypotheses were tested using a partial least-squares structural equation model (PLS-SEM). Parameters in the model were estimated by a bootstrapping method with 5000 resamplings. The PLS-SEM approach was used because it is suitable for research that focuses on prediction and theory development (Reinartz et al., 2009), and it is appropriate for evaluating models with complex relationships (Chin, 1998).
3.3.1. Measurement model validation
The reliability of the measurement of each construct was assessed by composite reliability (CR) and Cronbach’s alpha (α) scores. As is shown in Table 4 , all construct measures achieved high internal consistency, with the values of CR and α exceeding the recommended threshold of 0.7 (Hair et al., 2016). Moreover, the average variance extracted (AVE) of each construct was greater than 0.5, and all factor loadings were higher than 0.7 and statistically significant (p < 0.001). This established the convergent validity of the measurement of the constructs (Hair et al., 2016).
Table 4.
Examination of reliability and convergent validity.
| Construct/Item | Cronbach's Alpha | Composite reliability | Average variance extracted | Loadings | Maximum cross-loading on other constructs | |
|---|---|---|---|---|---|---|
| Perceived ethics (ETH) | 0.891 | 0.917 | 0.647 | |||
| ETH1 | 0.806 | *** | 0.572 | |||
| ETH2 | 0.735 | *** | 0.478 | |||
| ETH3 | 0.807 | *** | 0.568 | |||
| ETH4 | 0.827 | *** | 0.627 | |||
| ETH5 | 0.811 | *** | 0.623 | |||
| ETH6 | 0.836 | *** | 0.611 | |||
| Perceived data protection policy (POL) | 0.892 | 0.925 | 0.755 | |||
| POL1 | 0.869 | *** | 0.611 | |||
| POL2 | 0.864 | *** | 0.560 | |||
| POL3 | 0.860 | *** | 0.594 | |||
| POL4 | 0.881 | *** | 0.677 | |||
| Perceived governmental regulation (REG) | 0.922 | 0.951 | 0.866 | |||
| REG1 | 0.937 | *** | 0.654 | |||
| REG2 | 0.918 | *** | 0.642 | |||
| REG3 | 0.936 | *** | 0.642 | |||
| Perceived prevalence of information disclosure (PRE) | 0.865 | 0.917 | 0.788 | |||
| PRE1 | 0.910 | *** | 0.605 | |||
| PRE2 | 0.866 | *** | 0.538 | |||
| PRE3 | 0.886 | *** | 0.620 | |||
| Cognitive trust (COT) | 0.859 | 0.899 | 0.640 | |||
| COT1 | 0.832 | *** | 0.658 | |||
| COT2 | 0.811 | *** | 0.602 | |||
| COT3 | 0.816 | *** | 0.614 | |||
| COT4 | 0.717 | *** | 0.520 | |||
| COT5 | 0.819 | *** | 0.686 | |||
| Affective trust (AFT) | 0.861 | 0.900 | 0.642 | |||
| AFT1 | 0.845 | *** | 0.698 | |||
| AFT2 | 0.821 | *** | 0.647 | |||
| AFT3 | 0.816 | *** | 0.672 | |||
| AFT4 | 0.784 | *** | 0.600 | |||
| AFT5 | 0.735 | *** | 0.559 | |||
| Willingness to disclose (DCL) | 0.927 | 0.954 | 0.872 | |||
| DCL1 | 0.939 | *** | 0.611 | |||
| DCL2 | 0.921 | *** | 0.630 | |||
| DCL3 | 0.941 | *** | 0.614 | |||
| Willingness to falsify (FAL) | 0.910 | 0.943 | 0.846 | |||
| FAL1 | 0.916 | *** | 0.339 | |||
| FAL2 | 0.935 | *** | 0.404 | |||
| FAL3 | 0.909 | *** | 0.335 | |||
Note: *** p < .001.
ETH = Perceived ethics of data collection. POL = Perceived data protection policy. REG = Perceived governmental regulation. PRE = Perceived prevalence of information disclosure. COT = Cognitive trust. AFT = Affective trust. DCL = Willingness to disclose. FAL = Willingness to falsify.
As is shown in Table 5 , in terms of discriminant validity, the measurement model passed the Fornell and Larcker criterion (i.e., the square root of the AVE of each construct was higher than its correlations with other constructs), and the heterotrait–monotrait ratio of correlations (HTMT) criterion (i.e., HTMT values were lower than 0.9 and statistically different from one) (Hair et al., 2017). The loading of each indicator on its corresponding construct was also greater than its cross-loadings on the other constructs (see Table 4). These tests confirmed the discriminant validity of the measurement of the constructs in the model.
Table 5.
Examination of discriminant validity.
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | |
|---|---|---|---|---|---|---|---|---|
| 1. Perceived ethics of data collection | 0.804 | 0.782 | 0.614 | 0.461 | 0.806 | 0.756 | 0.643 | 0.106 |
| 2. Perceived data protection policy | 0.704 | 0.869 | 0.755 | 0.547 | 0.726 | 0.700 | 0.718 | 0.080 |
| 3. Perceived governmental regulation | 0.562 | 0.688 | 0.930 | 0.742 | 0.638 | 0.711 | 0.710 | 0.347 |
| 4. Perceived prevalence of information disclosure | 0.408 | 0.483 | 0.664 | 0.887 | 0.542 | 0.590 | 0.689 | 0.440 |
| 5. Cognitive trust | 0.712 | 0.641 | 0.573 | 0.474 | 0.800 | 0.896 | 0.720 | 0.082 |
| 6. Affective trust | 0.670 | 0.626 | 0.651 | 0.521 | 0.774 | 0.801 | 0.697 | 0.171 |
| 7. Willingness to disclose | 0.587 | 0.655 | 0.658 | 0.618 | 0.646 | 0.634 | 0.934 | 0.133 |
| 8. Willingness to falsify | −0.033 | 0.073 | 0.322 | 0.393 | 0.066 | 0.169 | 0.125 | 0.920 |
Note: Values on the diagonal are square root of AVEs. Values below the diagonal are correlations. Values above the diagonal are HTMT ratios.
Because our data were collected in a cross-sectional survey with single informants, we used both ex- and post-ante remedies to minimize the threat of the common method bias (CMB) (Podsakoff et al. (2003). By way of ex-ante remedies, we tried to control for the CMB by obtaining feedback through a series of pre-tests while ensuring respondent anonymity, reducing the apprehension of evaluation, including attention checks, and organizing the order of questions to prevent item-priming effects (Podsakoff et al., 2003). Of the ex-post remedies, first, Harman’s single-factor test (Podsakoff and Organ, 1986) showed that the most variance explained by one factor met the criterion of less than 50 % (44.5 %). Second, a full collinearity test (Kock and Lynn, 2012) resulted in VIF values less than 3.33 (maximum VIF = 2.353), indicating no pathological collinearity (Kock, 2015). Third, the highest correlation between the constructs was lower than 0.9 (r = 0.77 between COT and AFT), indicating that there was no extremely high correlation (Pavlou et al., 2007). Fourth, the results of the common method factor approach, as suggested by Liang et al. (2007), showed that the variance of each item was mostly explained by its theoretical construct (average variance = 74.4 %), rather than by the common method factor (average variance = 1.3 %). Moreover, while all item loadings on the corresponding theoretical constructs were statistically significant (p < 0.001), several loadings on the method factor were insignificant (p > 0.05) (see Appendix G). Taken together, we conclude that CMB was not a serious issue in this study.
3.3.2. Structural model analysis
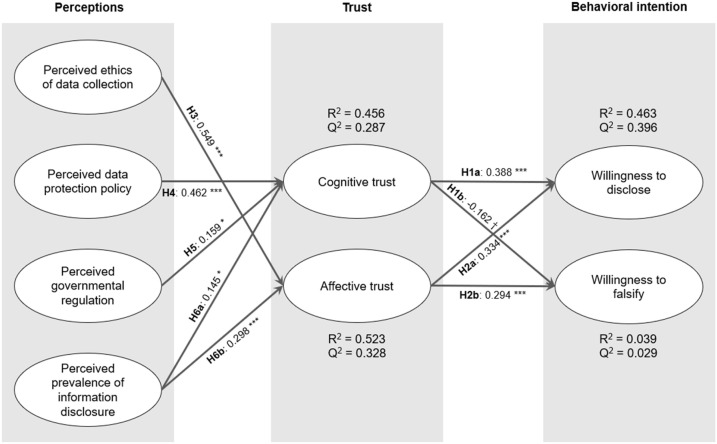
Fig. 2 shows the results of model estimation from the PLS-SEM in terms of path coefficients (β) and significance (p value) as well as the model’s explained variance (R2) and predictive relevance (Q2). More details of the PLS-SEM results are provided in Appendix H.
Fig. 2.
The results of the structural model.
Note: *** p < 0.001, ** p < 0.01, * p < 0.05, † p < 0.1.
We found that cognitive trust had a positive and significant effect on willingness to disclose (β = 0.388, t = 5.962, p < 0.001, f2 = 0.112), and a negative and significant effect on willingness to falsify (β = -0.162, t = 1.865, p = 0.062, f2 = 0.011), thus supporting H1a and H1b. In comparison, affective trust had a positive and significant effect on both willingness to disclose (β = 0.334, t = 5.307, p < 0.001, f2 = 0.083) and willingness to falsify (β = 0.294, t = 3.500, p < 0.001, f2 = 0.036), supporting H2a and H2b.
Perceived ethics of data collection had a significant effect on affective trust (β = 0.549, t = 10.914, p < 0.001, f2 = 0.526), thus supporting H3. Perceived data protection policy exerted a significant effect on cognitive trust (β = 0.462, t = 7.026, p < 0.001, f2 = 0.206), supporting H4. The path from perceived governmental regulation to cognitive trust was significant (β = 0.159, t = 2.270, p = 0.023, f2 = 0.018), supporting H5. In addition, perception of the prevalence of information disclosure had a significant effect on cognitive trust (β = 0.145, t = 2.500, p = 0.012, f2 = 0.022) and affective trust (β = 0.298, t = 6.180, p < 0.001, f2 = 0.155), thus supporting both H6a and H6b. Together, the constructs of perception explained 45.6 % and 52.3 % of the variance in cognitive trust and affective trust, respectively.
Overall, the structural model did not suffer from collinearity problems, as indicated by the low VIF values (< 3) of all sets of exogenous constructs (see Appendix G). It also had a moderate explanatory power or predictive accuracy (Hair et al., 2016), as the R2 values were within the acceptable range (>10 %, with the exception for the R2 of willingness to falsify) (Falk and Miller, 1992). All Q2 statistics obtained by a blindfolding procedure were greater than zero, indicating the predictive relevance of the endogenous constructs in the model (Hair et al., 2016).
We further analyzed the mediating roles of the two forms of trust on the relationships between perceptions and behavioral outcomes. Table 6 shows that cognitive trust significantly mediated the effect of perceived data protection policy, governmental regulation, and prevalence of information disclosure on customers’ willingness to disclose (p < 0.05), but did not significantly mediate the relationships between any perception and willingness to falsify (p > 0.05). By comparison, affective trust significantly mediated the influence of perceived ethics and the prevalence of information disclosure on willingness to disclose (p < 0.001), and was a significant mediator of the effects of perceived ethics and the prevalence of information disclosure on willingness to falsify (p < 0.01). These results provide further evidence of the distinct roles of cognitive trust and affective trust in our conceptual model.
Table 6.
Estimates of indirect effects in the model.
| Coefficient | t | p value | Lower limit of 95 % confidence interval | Upper limit of 95 % confidence interval | |
|---|---|---|---|---|---|
| Indirect effects on DCL | |||||
| ETH → AFT → DCL | 0.183 | 4.918 | 0.000 | 0.115 | 0.261 |
| POL → COT → DCL | 0.179 | 4.413 | 0.000 | 0.105 | 0.262 |
| REG → COT → DCL | 0.061 | 2.046 | 0.041 | 0.007 | 0.124 |
| PRE → COT → DCL | 0.056 | 2.252 | 0.024 | 0.012 | 0.110 |
| PRE → AFT → DCL | 0.099 | 3.724 | 0.000 | 0.052 | 0.156 |
| Indirect effects on FAL | |||||
| ETH → AFT → FAL | 0.161 | 3.421 | 0.001 | 0.071 | 0.257 |
| POL → COT → FAL | −0.075 | 1.692 | 0.091 | −0.168 | 0.006 |
| REG → COT → FAL | −0.026 | 1.486 | 0.137 | −0.064 | 0.004 |
| PRE → COT → FAL | −0.024 | 1.462 | 0.144 | −0.060 | 0.002 |
| PRE → AFT → FAL | 0.088 | 2.848 | 0.004 | 0.034 | 0.154 |
Note: ETH = Perceived ethics of data collection. POL = Perceived data protection policy. REG = Perceived governmental regulation. PRE = Perceived prevalence of information disclosure. COT = Cognitive trust. AFT = Affective trust. DCL = Willingness to disclose. FAL = Willingness to falsify.
4. Conclusions
Contact tracing is a safety practice for hospitality businesses to remain open in a safe environment during the COVID-19 pandemic. This research investigates customers’ cooperative behavior toward contact tracing based on cognitive trust and affective trust, and it examines perceptual antecedents of the two forms of trust. The findings show that cognitive trust facilitates willingness to disclose and reduces willingness to falsify, leading to actual cooperative behavior in contact tracing. By contrast, affective trust increases both the willingness toward disclosure and falsification, suggesting that it may encourage symbolic cooperative behavior. Such symbolic cooperation complicates contact tracing by creating barriers to quickly and precisely reach people who have been in proximal contact with infected individuals, and thus is detrimental to public safety.
Moreover, the findings demonstrate the relevant perceptual factors in contact tracing that influence cognitive trust and affective trust. Specifically, the antecedents of cognitive trust comprise perceived data protection policy, perceived governmental regulation, and perceived prevalence of information disclosure, while the antecedents of affective trust comprise perceived ethics of data collection and perceived prevalence of information disclosure. Theoretical and practical implications can be derived from our findings.
4.1. Theoretical implications
The primary contribution of this research is the demonstration of how different forms of trust influence cooperative behavior toward contact tracing in distinct ways. Although the literature on customer data privacy demonstrates has shown that trust is a key mechanism that promotes cooperative behavior, it overlooks the effects of different forms of trust (e.g., Aguirre et al., 2015; Jagadish, 2020; Martin and Murphy, 2017; Waldman, 2018). Our findings show that cognitive and affective trust differently influence two types of cooperative behaviors: the willingness toward disclosure and falsification. Cognitive trust encourages customers to disclose truthful information through positive evaluations of the competence, professionalism, and reliability of a business, which contribute to the confidence that private customer information will be handled appropriately. By comparison, affective trust can be a double-edged sword in facilitating customer cooperation in contact tracing. Customers tend to disclose information to a business with high affective trust because they have the motive to maintain a positive relationship with it. However, such a motive can pressure customers and trigger their intentions to provide false information, especially when they are unsure about how their data will be collected, managed, and used. Thus, our work here broadens and deepens the understanding of the role of trust in driving cooperative behavior related to data privacy.
Moreover, we add to the research on customer data privacy by identifying the antecedents of the two forms of trust and examining their effects. While past studies have suggested various antecedents of trust and consequent behaviors (Acquisti et al., 2015; Bansal et al., 2016; Su and Mattila, 2020; Yang et al., 2019), antecedents that specifically contribute to cognitive or affective trust are unclear. Our findings show that perceived protection policy reflects the competence, capability, and professionalism of the business in terms of ensuring the security of customer data, which is related to the attributes of cognitive trust. Similarly, perceived governmental regulation creates positive beliefs that the business has sufficient knowledge and skills to act competently and professionally in contact tracing, thus contributing to cognitive trust. Moreover, perceived business ethics conveys such business qualities as altruism, benevolence, and sincerity that create positive feelings and emotional connections, thus strengthening affective trust. Customers apply the prevalence of information disclosure as social proof to develop both cognitive and affective trust. The investigation of these perceptions deepens our understanding of the distinct characteristics of the two forms of trust, and it helps us establish a perception–trust–behavioral intention conceptual model to understand the psychological processes of customers in the context of contact tracing.
4.2. Practical implications
Our research has direct practical implications for hospitality businesses and governments in terms of effectively encouraging customers to cooperate in contact tracing. Hospitality businesses should prioritize the development of cognitive trust over that of affective trust to improve the effectiveness of contact tracing. Despite the clear benefit of affective trust in establishing and maintaining sustainable customer relationships, hospitality businesses should be cautious about the negative and costly effects of affective trust on customer cooperation that may even backfire. Therefore, for the sake of public health and safety in the COVID-19 pandemic, hospitality businesses should gain customer confidence in their capability of handling contact tracing competently and professionally before showing care and concern to develop relationships.
Hospitality businesses can gain cognitive trust by strengthening positive perceptions of data protection policy, the prevalence of information disclosure, and governmental regulation. First, businesses should offer fact-based information about their data protection policy to strengthen customers’ cognitive trust in them. For example, they can provide the relevant information on leaflets, posters, social media, and webpages to inform customers. Second, hospitality industry associations or influential platforms can collaborate with hospitality businesses to make contact tracing prevalent at a large scale through technological support and promotional activities. For example, the Restaurant Association of New Zealand has taken the lead in providing support for restaurants and cafes to conduct standardized contact tracing (Restaurant Association of New Zealand, 2020).
Finally, governments play an important role in helping hospitality businesses gain cognitive trust and facilitate contact tracing. Governments should enact sufficient regulatory mechanisms, such as administrative regulations, privacy standards, and supervision systems. Governments also need to strengthen the degree of regulatory enforcement on data practices in the hospitality industry. This regulatory enforcement is seen as an endorsement of the hospitality industry. For example, compared with Australia, where many electronic check-ins are outsourced to private companies with opaque privacy rules, the New Zealand government participates in designing and operating mobile applications for contact tracing for hospitality check-ins to balance the protection of personal privacy with protecting public health (ABC News, 2020). Such regulatory efforts send clear signals to customers that their privacy is respected. In this regard, hospitality businesses should lobby for, rather than resist, strong government regulation and intervention in contact tracing.
4.3. Limitations and future research directions
This research has limitations that offer directions for future studies. First, we measured customers’ behavioral intentions rather than their actual behaviors. Future research can collaborate with hospitality businesses to conduct field studies to better measure cooperative behavior. Second, our research was conducted in the Western context, where personal privacy and self-independence are highly valued. A fruitful area for future research will be to replicate our conceptual model in Eastern countries, such as South Korea and China, that have a strong culture of interdependence. How hospitality businesses and governments can facilitate cooperative behavior might need to be evaluated through a cultural lens. Finally, future research can extend the generalizability of our findings to other privacy-related contexts, such as customer registration, that require customers to disclose their information.
Funding
The authors gratefully acknowledge grants from Macquarie University for financial support.
Ethical approval
All procedures performed in studies involving human participants were in accordance with the ethical standards of the institutional and/or national research committee and with the 1964 Helsinki declaration and its later amendments or comparable ethical
standards.
Informed consent
Informed consent was obtained from all individual participants included in the research.
Declaration of Competing Interest
None.
Appendix A. A short survey
Table A1.
Demographic profile of the participants.
| Characteristics | n | % | |
|---|---|---|---|
| Age | 18−30 | 72 | 30.0 |
| 31−45 | 110 | 45.8 | |
| 46 and above | 58 | 24.2 | |
| Gender | Male | 154 | 64.2 |
| Female | 86 | 35.8 |
Table A2.
Summary of analyses results.
| 7-liker scale questions (1 = never, 7 = every time) | N | Mean | Std. Deviation | Std. Error Mean |
|---|---|---|---|---|
| Q1: During the pandemic, how often have you provided your contact information for contact tracing purpose when being asked to do so? | 238 | 4.15 | 2.162 | .140 |
| Q2: During the pandemic, how often have you provided 100 % correct and complete contact information for contact tracing purpose when being asked to do so? | 238 | 4.58 | 2.260 | .146 |
Table A3.
Summary of reasons for not disclosing and falsifying.
| Answers | Percentage |
|---|---|
| Concern for privacy | 67.5 % |
| Contact tracing is not necessary | 27.9 % |
| COVID-19 is not severe | 20.4 % |
| I am at low risk for COVID-19 | 19.2% |
| contact tracing is not helpful | 18.8 % |
| Too lazy to do so | 13.3 % |
| Other | 10.0 % |
Appendix B. Participants profile (pilot study)
| ID | Residence | Age | Gender | Profession |
|---|---|---|---|---|
| 01 | NZ | 52 | Female | Medical doctor |
| 02 | NZ | 35 | Female | Academic and former HR manager |
| 03 | NZ | 20 | Female | Colleague student |
| 04 | NZ | 28 | Male | Artist |
| 05 | NZ | 51 | Male | Health board staff / doctor |
| 06 | NZ | 49 | Female | Social worker |
| 07 | NZ | 27 | Female | University student |
| 08 | NZ | 30 | Female | Marketing administrator |
| 09 | NZ | 25 | Female | University student |
| 10 | NZ | 26 | Female | University support staff |
| 11 | Australia | 62 | Female | IT specialist |
| 12 | Australia | 36 | Male | Government employee |
| 13 | Australia | 31 | Female | Assistant accountant |
| 14 | Australia | 28 | Male | Academic |
| 15 | Australia | 22 | Male | Taxi driver |
| 16 | Australia | 20 | Female | Supermarket employee |
| 17 | Australia | 65 | Male | Retired resident |
| 18 | NZ | 38 | Male | COVID-19 response manager |
| 19 | Canada | 34 | Male | IT consultant |
| 20 | UK | 34 | Male | Academic |
| 21 | UK | 34 | Male | Retail manager |
| 22 | UK | 38 | Male | Community manager |
| 23 | USA | 33 | Male | Former HR administrator |
| 24 | USA | 30 | Male | Digital promotion broker |
Note: NZ = New Zealand, UK = United Kingdom, USA = United States of America.
Appendix C. Brief interview questions (pilot study)
-
1
Have you visited restaurants/cafes/bars during the COVID-19 pandemic? If yes, have you been requested to provide your personal information for contact tracing? Please share your experience.
-
2
Please tell us what personal information was requested from you and how your information was collected.
-
3
Did the restaurants/cafes/bars explain why they had collected your information?
-
4
Do you think you have a say in how your information was collected, stored, and used?
-
5
Did you provide incomplete information or 100 % accurate information? Did you have any concerns?
-
6
Please tell us what personal information you were not willing to share and explain why.
-
7
What can restaurants/cafes/bars do to encourage you to share your information for contact tracing?
-
8
What are the hospitality industry and governments doing to protect people’s privacy? What can they do to encourage customers to share their information for contact tracing?
Appendix D. Data analysis of qualitative interviews (pilot study)
Thematic analysis was applied to analyze our qualitative data (Braun and Clarke, 2006). We followed the process of making sense of and becoming familiar with the data, open coding, grouping codes with related meanings into themes, and an abstraction process to formulate the descriptions of the themes. We followed the guidelines from Sandberg (2005) to improve the validity (communicative) and reliability (interpretive awareness) of the findings. Communicative validity is an ongoing dialog throughout the research process where alternative knowledge claims are debated (Sandberg, 2005). We achieved communicative validity by ensuring the consistency of the findings through analyst triangulation by two independent analysts who interpreted the data simultaneously (Sandberg, 2005). This process generated initial categorical coding that was discussed rigorously by the authors until a consensus on the first-order codes had been achieved. The same process was repeated to generate the second- and third-order themes (see Table 1). Reliability as interpretive awareness acknowledges that researchers cannot escape from subjective interpretations and so must address this issue throughout the research process (Sandberg, 2005). During the interviews, reliability was achieved by asking open-ended questions and then following-up with probes. We further strengthened reliability through theoretical saturation (Corbin and Strauss, 1990). After the seventeenth interview, we achieved interpretive awareness as no new themes emerged from the data.
Appendix E. Survey brief (main study)
| The COVID-19 pandemic is one of the greatest challenges we face in decades. Government officials and health experts have been working together to contain the spread of the virus and help industries to recover from the crisis. |
| Many health experts suggest a contact tracing approach: tapping into personal information (e.g., name, phone number, location, travel history, health status) to track the spread of infection and warn people who have come into close proximity to a COVID-19 infected individual. Contact tracing has two purposes: 1) to figure out who a sick person caught an illness from, and 2) to find out who they’ve been in contact with while infectious. This contact tracing approach has been adopted by several countries, such as South Korea, Singapore, Australia, New Zealand, and some states in the U.S. |
| Restaurants, cafes, and bars have been hit hard by the pandemic. Their owners hope to reopen their businesses and allow customers to dine, and some of them have adopted the contact tracing approach for safety management. These restaurants require customers to provide contact details upon entry. For example, restaurants may require customers to provide information including names, contact information and visit times by filling a form, scanning a QR code or downloading a mobile App. |
| A major restaurant chain X in the U.S. (in order to avoid legal disputes, we use “X” to replace the real restaurant name) has adopted the contact tracing approach for safety management. This restaurant chain collects personal information including names and phone numbers from their customers. |
| Please answer the following questions based on your opinion about this restaurant chain X. |
Appendix F. Scales and items (main study)
| Construct | Item | Reference |
|---|---|---|
| Perceived ethics of data collection (ETH): a perception of the extent to which the business takes responsibility to look after public safety and wellbeing | Edinger‐Schons et al. (2018) | |
| ETH1 | The purpose for this restaurant chain to gather personal information during the COVID-19 pandemic is to fulfill responsibility for the society. | |
| ETH2 | The purpose for this restaurant chain to gather personal information during the COVID -19 pandemic is to support customers to live a healthy life. | |
| ETH3 | The purpose for this restaurant chain to gather personal information during the COVID -19 pandemic is to express their genuine feeling of responsibility. | |
| ETH4 | Given the act of collecting personal information during the COVID -19 pandemic, I believe this restaurant chain is genuinely concerned about being socially responsible. | |
| ETH5 | Given the act of collecting personal information during the COVID -19 pandemic, I believe this restaurant chain is committed to public welfare out of unselfish motives. | |
| ETH6 | Given the act of collecting personal information during the COVID -19 pandemic, I believe this restaurant chain’s commitment is based on the wish to do good. | |
| Perceived data protection policy (POL): a positive perception of the way the business exercises ownership, power, and protection over the use of customer data | Lwin et al. (2007) | |
| POL1 | This restaurant chain prevents customer information from being used for purposes other than those initially stated during the COVID -19 pandemic. | |
| POL2 | This restaurant chain prevents customer information from being shared with unauthorized external parties. | |
| POL3 | This restaurant chain’s databases containing customer information are protected from unauthorized access regardless of costs. | |
| POL4 | This restaurant chain keeps customer information secure. | |
| Perceived governmental regulation (REG): a perception regarding how well data practices and potential privacy risks are regulated and monitored by government authorities | Lwin et al. (2007); Poortinga and Pidgeon (2006) | |
| REG1 | The existing laws in the U.S. are sufficient to protect restaurant customers’ privacy when contact tracing is adopted during the COVID-19 pandemic. | |
| REG2 | There is stringent legal enforcement in the U.S to protect personal information of restaurant customers when contact tracing is adopted during the COVID-19 pandemic. | |
| REG3 | The U.S. government is doing enough to ensure that restaurant customers are protected against privacy violations when contact tracing is adopted during the COVID-19 pandemic. | |
| Perceived prevalence of information disclosure (PRE): a perception of the extent to which others are engaging in information disclosure | Dootson et al. (2017) | |
| PRE1 | During the COVID-19 pandemic, what proportion of restaurant customers in the U.S. do you think participate in sharing their personal information with restaurants? | |
| PRE2 | During the COVID-19 pandemic, what proportion of restaurant customers in the U.S. do you think accept the advice to share their personal information with restaurants? | |
| PRE3 | During the COVID-19 pandemic, what proportion of restaurant customers in the U.S. think sharing their personal information with restaurants is necessary? | |
| Cognitive trust (COT): a rational evaluation of whether the other exchange party is trustworthy or not based on its ability, professionalism, and reliability | Johnson and Grayson (2005); McAllister (1995) | |
| COT1 | I believe this restaurant chain does its business with professionalism and dedication during the COVID-19 pandemic. | |
| COT2 | Given the approach of this restaurant chain, I believe in its competence during the COVID-19 pandemic. | |
| COT3 | I can rely on this restaurant chain to serve me carefully during the COVID-19 pandemic. | |
| COT4 | I am confident about this restaurant chain’s ability to professionally operate its business during the COVID-19 pandemic. | |
| COT5 | I can confidently depend on this restaurant chain if I visit it during the COVID-19 pandemic. | |
| Affective trust (AFT): emotional bonds or connections with the exchange party that are grounded in its care and concern | Johnson and Grayson (2005); McAllister (1995) | |
| AFT1 | I would feel a sense of personal connection with this restaurant chain if I visit it during the COVID-19 pandemic. | |
| AFT2 | I feel that this restaurant chain will respond to me caringly as a customer during the COVID-19 pandemic. | |
| AFT3 | I feel that this restaurant chain will show a warm and caring attitude toward me during the COVID-19 pandemic. | |
| AFT4 | I feel that this restaurant chain will be concerned about me during the COVID-19 pandemic. | |
| AFT5 | I feel that this restaurant chain will care about maintaining a good relationship with me during the COVID-19 pandemic. | |
| Willingness to disclose (DCL): an intent to provide information to the business | Morosan (2018) | |
| DCL1 | How likely are you to disclose personal information to this restaurant chain during the COVID-19 pandemic? | |
| DCL2 | How willing are you to disclose personal information to this restaurant chain during the COVID-19 pandemic? | |
| DCL3 | How probable are you to disclose personal information to this restaurant chain during the COVID-19 pandemic? | |
| Willingness to falsify (FAL): an intent to provide false or incomplete information to the business | Martin et al. (2017) | |
| FAL1 | If this restaurant chain asks for my personal information when I visit it, I will give them false information. | |
| FAL2 | If this restaurant chain asks for my personal information when I visit it, I will purposely try to trick them when providing my information. | |
| FAL3 | If this restaurant chain asks for my personal information when I visit it, I think it is fine to give misleading answers on personal questions. | |
Appendix G. Common method bias analysis using the common method factor approach (main study)
| Item | Loading on theoretical construct (R1) | R12 | Loading on common method construct (R2) | R22 | ||
|---|---|---|---|---|---|---|
| ETH1 | 0.950 | *** | 0.902 | −0.162 | ** | 0.026 |
| ETH2 | 0.850 | *** | 0.722 | −0.131 | * | 0.017 |
| ETH3 | 0.831 | *** | 0.691 | −0.019 | ns | 0.000 |
| ETH4 | 0.772 | *** | 0.595 | 0.059 | ns | 0.004 |
| ETH5 | 0.660 | *** | 0.435 | 0.173 | ** | 0.030 |
| ETH6 | 0.776 | *** | 0.602 | 0.065 | ns | 0.004 |
| POL1 | 0.888 | *** | 0.789 | −0.021 | ns | 0.000 |
| POL2 | 0.977 | *** | 0.955 | −0.126 | * | 0.016 |
| POL3 | 0.900 | *** | 0.810 | −0.047 | ns | 0.002 |
| POL4 | 0.713 | *** | 0.509 | 0.190 | ** | 0.036 |
| REG1 | 0.915 | *** | 0.837 | 0.024 | ns | 0.001 |
| REG2 | 0.882 | *** | 0.778 | 0.041 | ns | 0.002 |
| REG3 | 0.994 | *** | 0.988 | −0.065 | * | 0.004 |
| PRE1 | 0.925 | *** | 0.856 | −0.019 | ns | 0.000 |
| PRE2 | 0.915 | *** | 0.838 | −0.061 | * | 0.004 |
| PRE3 | 0.823 | *** | 0.677 | 0.079 | * | 0.006 |
| COT1 | 0.715 | *** | 0.511 | 0.128 | * | 0.016 |
| COT2 | 0.883 | *** | 0.780 | −0.079 | ns | 0.006 |
| COT3 | 0.817 | *** | 0.667 | −0.003 | ns | 0.000 |
| COT4 | 0.872 | *** | 0.761 | −0.168 | ** | 0.028 |
| COT5 | 0.733 | *** | 0.537 | 0.096 | ns | 0.009 |
| AFT1 | 0.549 | *** | 0.301 | 0.322 | *** | 0.104 |
| AFT2 | 0.894 | *** | 0.799 | −0.081 | ns | 0.007 |
| AFT3 | 0.804 | *** | 0.647 | 0.017 | ns | 0.000 |
| AFT4 | 0.791 | *** | 0.626 | −0.010 | ns | 0.000 |
| AFT5 | 1.009 | *** | 1.018 | −0.295 | *** | 0.087 |
| DCL1 | 0.975 | *** | 0.951 | −0.041 | ns | 0.002 |
| DCL2 | 0.873 | *** | 0.762 | 0.056 | ns | 0.003 |
| DCL3 | 0.953 | *** | 0.909 | −0.014 | ns | 0.000 |
| FAL1 | 0.920 | *** | 0.846 | −0.028 | ns | 0.001 |
| FAL2 | 0.913 | *** | 0.833 | 0.066 | *** | 0.004 |
| FAL3 | 0.928 | *** | 0.862 | −0.040 | * | 0.002 |
| Average | 0.744 | 0.013 | ||||
Note: *** p < 0.001, ** p < 0.01, * p < 0.05, ns p ≥ 0.05.
Appendix H. Detailed PLS-SEM results (main study)
| Hypothesis | Direct paths | β | t | p value | f2 | VIF | Result |
|---|---|---|---|---|---|---|---|
| H1a | COT → DCL | 0.388 | 5.962 | 0.000 | 0.112 | 2.495 | Supported |
| H1b | COT → FAL | −0.162 | 1.865 | 0.062 | 0.011 | 2.495 | Weakly supported |
| H2a | AFT → DCL | 0.334 | 5.307 | 0.000 | 0.083 | 2.495 | Supported |
| H2b | AFT → FAL | 0.294 | 3.500 | 0.000 | 0.036 | 2.495 | Supported |
| H3 | ETH → AFT | 0.549 | 10.914 | 0.000 | 0.526 | 1.199 | Supported |
| H4 | POL → COT | 0.462 | 7.026 | 0.000 | 0.206 | 1.903 | Supported |
| H5 | REG → COT | 0.159 | 2.270 | 0.023 | 0.018 | 2.611 | Supported |
| H6a | PRE → COT | 0.145 | 2.500 | 0.012 | 0.022 | 1.794 | Supported |
| H6b | PRE → AFT | 0.298 | 6.180 | 0.000 | 0.155 | 1.199 | Supported |
| COT: | R2 = | 0.456 | Q2 = | 0.287 | |||
| AFT: | R2 = | 0.523 | Q2 = | 0.328 | |||
| DCL: | R2 = | 0.463 | Q2 = | 0.396 | |||
| FAL: | R2 = | 0.039 | Q2 = | 0.029 |
Note: ETH = Perceived ethics of data collection. POL = Perceived data protection policy. REG = Perceived governmental regulation. PRE = Perceived prevalence of information disclosure. COT = Cognitive trust. AFT = Affective trust. DCL = Willingness to disclose. FAL = Willingness to falsify.
References
- ABC News . 2020. The QR Code Has Turned COVID-19 Check-ins Into a Golden Opportunity for Marketing and Data Companies.https://www.abc.net.au/news/2020-10-31/covid-19-check-in-data-using-qr-codes-raises-privacy-concerns/12823432 [Google Scholar]
- Acquisti A., John L.K., Loewenstein G. The impact of relative standards on the propensity to disclose. J. Mark. Res. 2012;49(2):160–174. [Google Scholar]
- Acquisti A., Brandimarte L., Loewenstein G. Privacy and human behavior in the age of information. Science. 2015;347(6221):509–514. doi: 10.1126/science.aaa1465. [DOI] [PubMed] [Google Scholar]
- Aguirre E., Mahr D., Grewal D., de Ruyter K., Wetzels M. Unraveling the personalization paradox: the effect of information collection and trust-building strategies on online advertisement effectiveness. J. Retail. 2015;91(1):34–49. [Google Scholar]
- Aiken K.D., Boush D.M. Trustmarks, objective-source ratings, and implied investments in advertising: investigating online trust and the context-specific nature of internet signals. J. Acad. Mark. Sci. 2006;34(3):308–323. [Google Scholar]
- American Council on Science and Health . 2020. Coronavirus: Restaurant Customer Logs For Contact Tracing Are A Good Idea.https://www.acsh.org/news/2020/05/12/coronavirus-restaurant-customer-logs-contact-tracing-are-good-idea-14782 Accessed June 5 2020. [Google Scholar]
- Anderson C.L., Agarwal R. The digitization of healthcare: boundary risks, emotion, and consumer willingness to disclose personal health information. Inf. Syst. Res. 2011;22(3):469–490. [Google Scholar]
- Anderson J.C., Gerbing D.W. Structural equation modeling in practice: a review and recommended two-step approach. Psychol. Bull. 1988;103(3):411–423. [Google Scholar]
- Bansal G., Zahedi F.M., Gefen D. Do context and personality matter? Trust and privacy concerns in disclosing private information online. Inf. Manag. 2016;53(1):1–21. [Google Scholar]
- Bart Y., Shankar V., Sultan F., Urban G.L. Are the drivers and role of online trust the same for all web sites and consumers? A large-scale exploratory empirical study. J. Mark. 2005;69(4):133–152. [Google Scholar]
- Blau P.M. Wiley; New York: 1964. Exchange and Power in Social Life. [Google Scholar]
- Bleier A., Eisenbeiss M. The importance of trust for personalized online advertising. J. Retail. 2015;91(3):390–409. [Google Scholar]
- Borg S.W., Freytag P.V. Helicopter view: an interpersonal relationship sales process framework. J. Bus. Ind. Mark. 2012;27(7):564–571. [Google Scholar]
- Braun V., Clarke V. Using thematic analysis in psychology. Qual. Res. Psychol. 2006;3(2):77–101. [Google Scholar]
- Chai S., Das S., Rao H.R. Factors affecting bloggers’ knowledge sharing: an investigation across gender. J. Manag. Inf. Syst. 2011;28(3):309–342. [Google Scholar]
- Chin W.W. The partial least squares approach to structural equation modeling. Modern Methods for Business Research. 1998;295(2):295–336. [Google Scholar]
- Cho J. The mechanism of trust and distrust formation and their relational outcomes. J. Retail. 2006;82(1):25–35. [Google Scholar]
- Corbin J.M., Strauss A. Grounded theory research: procedures, canons, and evaluative criteria. Qual. Sociol. 1990;13(1):3–21. [Google Scholar]
- Dinev T., Hart P. An extended privacy calculus model for e-commerce transactions. Inf. Syst. Res. 2006;17(1):61–80. [Google Scholar]
- Dootson P., Lings I., Beatson A., Johnston K.A. Deterring deviant consumer behaviour: when ‘it’s wrong, don’t do it’doesn’t work. J. Mark. Manag. 2017;33(15–16):1355–1383. [Google Scholar]
- Edinger‐Schons L.M., Sipilä J., Sen S., Mende G., Wieseke J. Are two reasons better than one? The role of appeal type in consumer responses to sustainable products. J. Consum. Psychol. 2018;28(4):644–664. [Google Scholar]
- Falk R.F., Miller N.B. University of Akron Press; Akron: 1992. A Primer for Soft Modeling. [Google Scholar]
- Fan Y. Ethical branding and corporate reputation. Corp. Commun. Int. J. 2005;10(4):341–350. [Google Scholar]
- Government of NSW . 2020. COVID-19 Safety Plan.https://www.nsw.gov.au/sites/default/files/2020-06/covid-19-safety-plan-restaurants-and-cafes.pdf [Google Scholar]
- Grosso M., Castaldo S., Li H.A., Larivière B. What information do shoppers share? The effect of personnel-, retailer-, and country-trust on willingness to share information. J. Retail. 2020;96(4):524–547. [Google Scholar]
- Guillon M., Kergall P. Attitudes and opinions on quarantine and support for a contact-tracing application in France during the COVID-19 outbreak. Public Health. 2020;188:21–31. doi: 10.1016/j.puhe.2020.08.026. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hair J.F., Jr., Hult G.T.M., Ringle C., Sarstedt M. SAGE Publications; USA: 2016. A Primer on Partial Least Squares Structural Equation Modeling (PLS-SEM) [Google Scholar]
- Hon A.H., Lu L. The mediating role of trust between expatriate procedural justice and employee outcomes in Chinese hotel industry. Int. J. Hosp. Manag. 2010;29(4):669–676. [Google Scholar]
- Hu X., Yan H., Casey T., Wu C.-H. Creating a safe haven during the crisis: how organizations can achieve deep compliance with COVID-19 safety measures in the hospitality industry. Int. J. Hosp. Manag. 2020;92 doi: 10.1016/j.ijhm.2020.102662. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Huang J.L., Liu M., Bowling N.A. Insufficient effort responding: examining an insidious confound in survey data. J. Appl. Psychol. 2015;100(3):828–845. doi: 10.1037/a0038510. [DOI] [PubMed] [Google Scholar]
- Ioannou A., Tussyadiah I., Miller G. That’s private! Understanding travelers’ privacy concerns and online data disclosure. J. Travel. Res. 2020 doi: 10.1177/0047287520951642. [DOI] [Google Scholar]
- Jaap W., Xiao M., Thomas R., Hans R., Bernd S. Data analytics in a privacy-concerned world. J. Bus. Res. 2021;122:915–925. [Google Scholar]
- Jagadish H. Circles of privacy. J. Consum. Psychol. 2020;30(4):774–779. [Google Scholar]
- Janakiraman R., Lim J.H., Rishika R. The effect of a data breach announcement on customer behavior: evidence from a multichannel retailer. J. Mark. 2018;82(2):85–105. [Google Scholar]
- Johnson D., Grayson K. Cognitive and affective trust in service relationships. J. Bus. Res. 2005;58(4):500–507. [Google Scholar]
- Kashmiri S., Nicol C.D., Hsu L. Birds of a feather: intra-industry spillover of the Target customer data breach and the shielding role of IT, marketing, and CSR. J. Acad. Mark. Sci. 2017;45(2):208–228. [Google Scholar]
- Kehr F., Kowatsch T., Wentzel D., Fleisch E. Blissfully ignorant: the effects of general privacy concerns, general institutional trust, and affect in the privacy calculus. Inf. Syst. J. 2015;25(6):607–635. [Google Scholar]
- Kim P.H., Ferrin D.L., Cooper C.D., Dirks K.T. Removing the shadow of suspicion: the effects of apology versus denial for repairing competence-versus integrity-based trust violations. J. Appl. Psychol. 2004;89(1):104–118. doi: 10.1037/0021-9010.89.1.104. [DOI] [PubMed] [Google Scholar]
- Kim T., Barasz K., John L.K. Why am I seeing this ad? The effect of ad transparency on ad effectiveness. J. Consum. Res. 2018;45(5):906–932. [Google Scholar]
- Kock N. Common method bias in PLS-SEM: a full collinearity assessment approach. International Journal of e-Collaboration (ijec) 2015;11(4):1–10. [Google Scholar]
- Kock N., Lynn G. Lateral collinearity and misleading results in variance-based SEM: an illustration and recommendations. J. Assoc. Inf. Syst. 2012;13(7):546–580. [Google Scholar]
- Krafft M., Arden C.M., Verhoef P.C. Permission marketing and privacy concerns—Why do customers (not) grant permissions? J. Interact. Mark. 2017;39:39–54. [Google Scholar]
- Krishen A.S., Raschke R.L., Close A.G., Kachroo P. A power-responsibility equilibrium framework for fairness: understanding consumers’ implicit privacy concerns for location-based services. J. Bus. Res. 2017;73:20–29. [Google Scholar]
- Kvale S. SAGE Publications; USA: 1996. InterViews: An Introduction to Qualitative Research Interviewing. [Google Scholar]
- Liang H., Saraf N., Hu Q., Xue Y. Assimilation of enterprise systems: the effect of institutional pressures and the mediating role of top management. Mis Q. 2007:59–87. [Google Scholar]
- Luo X. Trust production and privacy concerns on the Internet: a framework based on relationship marketing and social exchange theory. Ind. Mark. Manag. 2002;31(2):111–118. [Google Scholar]
- Lwin M., Wirtz J., Williams J.D. Consumer online privacy concerns and responses: a power–responsibility equilibrium perspective. J. Acad. Mark. Sci. 2007;35(4):572–585. [Google Scholar]
- Malhotra N.K., Kim S.S., Agarwal J. Internet users’ information privacy concerns (IUIPC): the construct, the scale, and a causal model. Inf. Syst. Res. 2004;15(4):336–355. [Google Scholar]
- Martin K.D., Murphy P.E. The role of data privacy in marketing. J. Acad. Mark. Sci. 2017;45(2):135–155. [Google Scholar]
- Martin K.D., Borah A., Palmatier R.W. Data privacy: effects on customer and firm performance. J. Mark. 2017;81(1):36–58. [Google Scholar]
- Martínez P., Del Bosque I.R. CSR and customer loyalty: the roles of trust, customer identification with the company and satisfaction. Int. J. Hosp. Manag. 2013;35:89–99. [Google Scholar]
- Massey G.R., Wang P.Z., Kyngdon A.S. Conceptualizing and modeling interpersonal trust in exchange relationships: the effects of incomplete model specification. Ind. Mark. Manag. 2019;76:60–71. [Google Scholar]
- McAllister D.J. Affect-and cognition-based trust as foundations for interpersonal cooperation in organizations. Acad. Manag. J. 1995;38(1):24–59. [Google Scholar]
- Miltgen C.L., Smith H.J. Falsifying and withholding: exploring individuals’ contextual privacy-related decision-making. Inf. Manag. 2019;56(5):696–717. [Google Scholar]
- Moon Y. Intimate exchanges: using computers to elicit self-disclosure from consumers. J. Consum. Res. 2000;26(4):323–339. [Google Scholar]
- Morosan C. Information disclosure to biometric E-gates: the roles of perceived security, benefits, and emotions. J. Travel. Res. 2018;57(5):644–657. [Google Scholar]
- Mothersbaugh D.L., Foxx W.K., Beatty S.E., Wang S. Disclosure antecedents in an online service context: the role of sensitivity of information. J. Serv. Res. 2012;15(1):76–98. [Google Scholar]
- Nienaber A.-M., Hofeditz M., Romeike P.D. Vulnerability and trust in leader-follower relationships. Pers. Rev. 2015;44(4):567–591. [Google Scholar]
- Norberg P.A., Horne D.R. Coping with information requests in marketing exchanges: an examination of pre-post affective control and behavioral coping. J. Acad. Mark. Sci. 2014;42(4):415–429. [Google Scholar]
- O’Malley L., Patterson M., Evans M. Intimacy or intrusion? The privacy dilemma for relationship marketing in consumer markets. J. Mark. Manag. 1997;13(6):541–559. [Google Scholar]
- Park N., Jin B., Jin S.-A.A. Effects of self-disclosure on relational intimacy in Facebook. Comput. Human Behav. 2011;27(5):1974–1983. [Google Scholar]
- Pavlou P.A., Liang H., Xue Y. Understanding and mitigating uncertainty in online exchange relationships: a principal-agent perspective. Mis Q. 2007:105–136. [Google Scholar]
- Podsakoff P.M., Organ D.W. Self-reports in organizational research: problems and prospects. J. Manage. 1986;12(4):531–544. [Google Scholar]
- Podsakoff P.M., MacKenzie S.B., Lee J.-Y., Podsakoff N.P. Common method biases in behavioral research: a critical review of the literature and recommended remedies. J. Appl. Psychol. 2003;88(5):879–903. doi: 10.1037/0021-9010.88.5.879. [DOI] [PubMed] [Google Scholar]
- Poortinga W., Pidgeon N.F. Prior attitudes, salient value similarity, and dimensionality: toward an integrative model of trust in risk regulation. J. Appl. Soc. Psychol. 2006;36(7):1674–1700. [Google Scholar]
- Queensland Government . 2020. Fake Names and Numbers Putting Broader Community at Risk.https://www.health.qld.gov.au/news-events/doh-media-releases/releases/fake-names-and-numbers-putting-broader-community-at-risk-2020-07-13 [Google Scholar]
- Reinartz W., Haenlein M., Henseler J. An empirical comparison of the efficacy of covariance-based and variance-based SEM. Int. J. Res. Mark. 2009;26(4):332–344. [Google Scholar]
- Restaurant Association of New Zealand . 2020. Operating Your Business at Level 2: Guidelines for Hospitality Businesses.https://www.restaurantnz.co.nz/wp-content/uploads/2020/05/Level-2-Guidelines-for-operating-_PublicHealthOrder_v7_.pdf [Google Scholar]
- Restaurant Hub . 2020. Free Covid 19 Contact Tracing For Restaurateurs.https://www.restauranthub.co.nz/for-restaurants/covid-19-contact-tracing/ Accessed June 5 2020. [Google Scholar]
- Ringle C.M., Wende S., Becker J.-M. SmartPLS GmbH; Boenningstedt: 2015. SmartPLS 3. [Google Scholar]
- Sandberg J. How do we justify knowledge produced within interpretive approaches? Organ. Res. Methods. 2005;8(1):41–68. [Google Scholar]
- Schaubroeck J., Lam S.S., Peng A.C. Cognition-based and affect-based trust as mediators of leader behavior influences on team performance. J. Appl. Psychol. 2011;96(4):863–871. doi: 10.1037/a0022625. [DOI] [PubMed] [Google Scholar]
- Schumann J.H., von Wangenheim F., Groene N. Targeted online advertising: using reciprocity appeals to increase acceptance among users of free web services. J. Mark. 2014;78(1):59–75. [Google Scholar]
- Servick K. Cellphone tracking could help stem the spread of coronavirus. Is privacy the price. Science. 2020 doi: 10.1126/science.abb8296. [DOI] [Google Scholar]
- Singh J.J., Iglesias O., Batista-Foguet J.M. Does having an ethical brand matter? The influence of consumer perceived ethicality on trust, affect and loyalty. J. Bus. Ethics. 2012;111(4):541–549. [Google Scholar]
- Song J.H., Kim H.Y., Kim S., Lee S.W., Lee J.-H. Effects of personalized e-mail messages on privacy risk: moderating roles of control and intimacy. Mark. Lett. 2016;27(1):89–101. [Google Scholar]
- Stanaland A.J., Lwin M.O., Murphy P.E. Consumer perceptions of the antecedents and consequences of corporate social responsibility. J. Bus. Ethics. 2011;102(1):47–55. [Google Scholar]
- Steinhoff L., Arli D., Weaven S., Kozlenkova I.V. Online relationship marketing. J. Acad. Mark. Sci. 2019;47(3):369–393. [Google Scholar]
- Su N., Mattila A.S. Does gender bias exist? The impact of gender congruity on consumer’s Airbnb booking intention and the mediating role of trust. Int. J. Hosp. Manag. 2020 doi: 10.1016/j.ijhm.2019.102405. [DOI] [Google Scholar]
- Sung Y., Kim J. Effects of brand personality on brand trust and brand affect. Psychol. Mark. 2010;27(7):639–661. [Google Scholar]
- The Conversation . 2020. 70% Of People Surveyed Said They’d Download a Coronavirus App. Only 44% Did. Why the Gap?https://theconversation.com/70-of-people-surveyed-said-theyd-download-a-coronavirus-app-only-44-did-why-the-gap-138427 [Google Scholar]
- The New Daily . 2020. Millions More Must Download COVIDSafe Before Pubs Can Reopen, PM Suggests.https://thenewdaily.com.au/news/coronavirus/2020/05/02/coronavirus-covidsafe-pubs/ [Google Scholar]
- The UK Government . 2020. Guidance: Maintaining Records of Staff, Customers and Visitors to Support NHS Test and Trace.https://www.gov.uk/guidance/maintaining-records-of-staff-customers-and-visitors-to-support-nhs-test-and-trace [Google Scholar]
- Tomlinson E.C., Schnackenberg A., Dawley D., Ash S.R. Revisiting the trustworthiness‐Trust relationship: exploring the differential predictors of cognition‐and affect‐based trust. J. Organ. Behav. 2020;41(6):535–550. [Google Scholar]
- Trang S., Trenz M., Weiger W.H., Tarafdar M., Cheung C.M. One app to trace them all? Examining app specifications for mass acceptance of contact-tracing apps. Eur. J. Inf. Syst. 2020;29(4):415–428. [Google Scholar]
- Trim P.R., Lee Y.-I. The role of B2B marketers in increasing cyber security awareness and influencing behavioural change. Ind. Mark. Manag. 2019;83:224–238. [Google Scholar]
- Van Herpen E., Pieters R., Zeelenberg M. When demand accelerates demand: trailing the bandwagon. J. Consum. Psychol. 2009;19(3):302–312. [Google Scholar]
- Waldman A.E. Cambridge University Press; UK: 2018. Privacy As Trust: Information Privacy for an Information Age. [Google Scholar]
- White T.B. Consumer disclosure and disclosure avoidance: a motivational framework. J. Consum. Psychol. 2004;14(1–2):41–51. [Google Scholar]
- Wirtz J., Lwin M.O. Regulatory focus theory, trust, and privacy concern. J. Serv. Res. 2009;12(2):190–207. [Google Scholar]
- World Health Organization . 2020. Coronavirus Disease (COVID-19): Contact Tracing.https://www.who.int/news-room/q-a-detail/coronavirus-disease-covid-19-contact-tracing [Google Scholar]
- Wright S.A., Xie G.-X. Perceived privacy violation: exploring the malleability of privacy expectations. J. Bus. Ethics. 2019;156(1):123–140. [Google Scholar]
- Xu H., Teo H.-H., Tan B.C., Agarwal R. Research note—effects of individual self-protection, industry self-regulation, and government regulation on privacy concerns: a study of location-based services. Inf. Syst. Res. 2012;23(4):1342–1363. [Google Scholar]
- Yahoo . 2020. Why Large Group of Population Can’t Download the Coronavirus App.https://au.news.yahoo.com/why-large-group-of-population-cant-download-the-coronavirus-app-084122573.html [Google Scholar]
- Yang J., Mossholder K.W. Examining the effects of trust in leaders: a bases-and-foci approach. Leadersh. Q. 2010;21(1):50–63. [Google Scholar]
- Yang S.-B., Lee K., Lee H., Koo C. In Airbnb we trust: understanding consumers’ trust-attachment building mechanisms in the sharing economy. Int. J. Hosp. Manag. 2019;83:198–209. [Google Scholar]
- Zimmer J.C., Arsal R.E., Al-Marzouq M., Grover V. Investigating online information disclosure: effects of information relevance, trust and risk. Inf. Manag. 2010;47(2):115–123. [Google Scholar]