Abstract
Encryption makes information available only to those with the decoding key. We propose that microbes, living in a chemical environment, encrypt nutrients, thereby making them available only to those with the decoding enzymes, such as their kin. Examples of encrypted nutrients include cobamides, which are expensive to make and valuable for microbial fitness. Furthermore, we propose that hosts encrypt nutrients to encourage desirable colonizers. For instance, plant root exudates and breast milk oligosaccharides encourage beneficial microbes.
Introduction to the concept of encryption
Encryption is a way to restrict access to information or other valuable materials through the use of a code. Familiar examples include encryption of communications for privacy or bank transactions for security. In microbial communities, encryption commonly occurs with signaling molecules, whereby cells produce a diffusible chemical signal that is recognized only by recipient cells that possess a specific receptor for the signal – analogous to speakers and listeners of different languages. This allows members of a single species that share the genes for producing and sensing the molecule to have private conversations within a larger community (Figure 1A). In this forum, we suggest that not only is information encrypted but also valuable nutrients, including cobamides, are encrypted. We gradually build to this idea, first presenting quorum sensing as an example of information encryption, then moving on to siderophores as encrypting iron and cobamides as encrypted nutrients based on their variable lower ligand domain. Finally, we discuss how host organisms encrypt nutrients to restrict them from pathogens or make them available to select symbionts.
Figure 1. Nutrient encryption, decryption, and conversion in microbial communities.
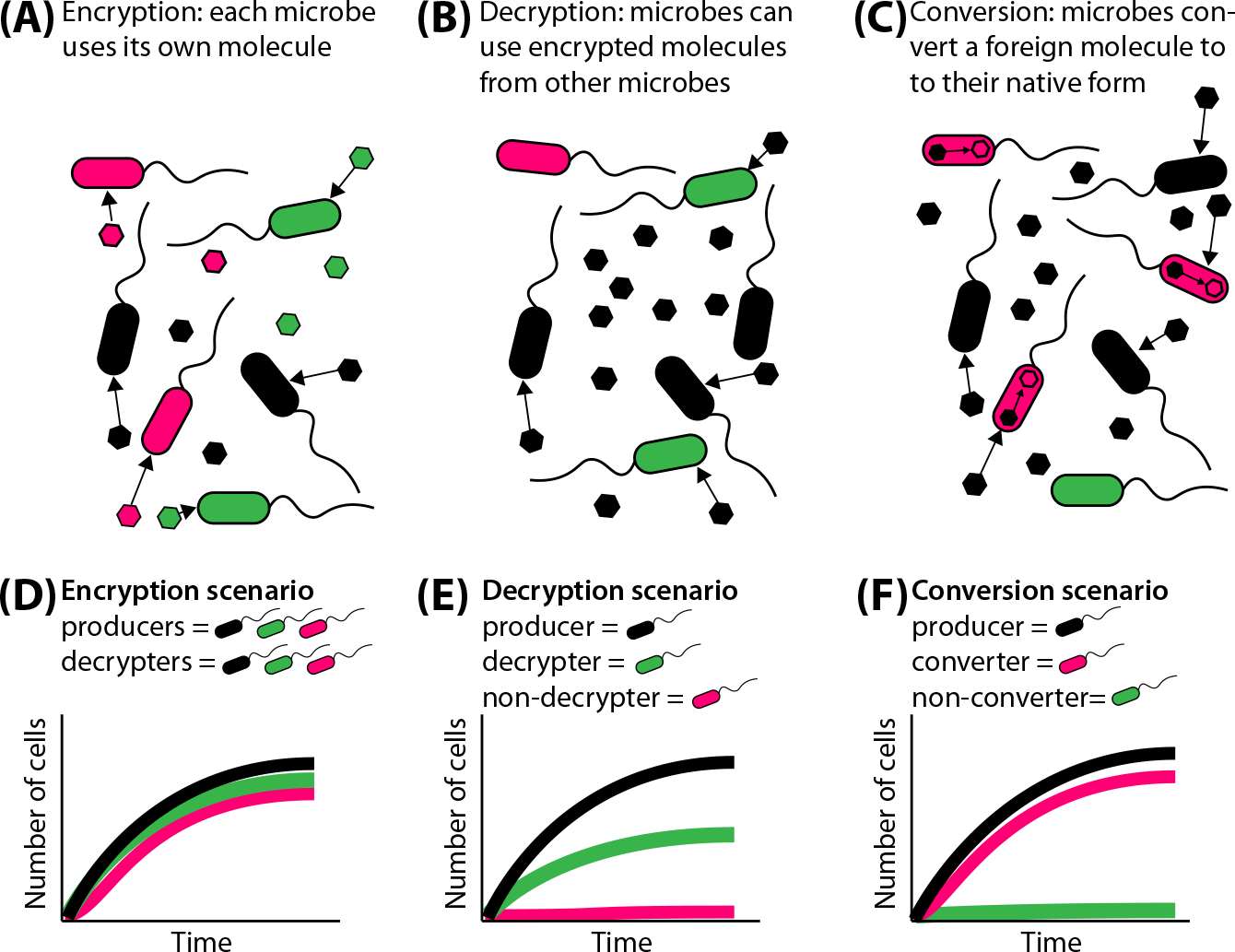
(A) Encryption allows each microbial strain to consume nutrients synthesized by its kin. (B) Decryption allows microbes to consume variants that were synthesized by other strains. (C) Conversion allows one strain to take up molecules from other bacterial species and chemically convert the foreign molecule to the native one. Different growth kinetics could result from (D) encryption, (E) decryption, and (F) conversion. (A–C) Black, green, and pink hexagons represent the nutrient molecule.
Examples of encryption in microbial communities
Acylhomoserine lactone (AHL) quorum sensing molecules encrypt information AHL quorum-sensing molecules are an example of informational encryption in signaling systems [1] (Figure 2A). Bacteria produce AHLs using a LuxI-type AHL synthase. AHL is sensed via binding to a LuxR-type receptor, and downstream genetic programs are activated when the AHL concentration exceeds a threshold level. Although AHL-based quorum sensing is widespread among Gram-negative bacteria, AHL signaling is phylogenetically encrypted: Differences in AHL structures allow communication to be restricted to the producer and closely related bacteria [1]. Each AHL contains an invariant homoserine lactone moiety and a variable acyl side chain. Specificity in AHL production is achieved by differences in substrate specificity in LuxI-type synthase homologs, resulting in species-specific production of different AHLs with distinct acyl side chains. Specificity in detection of AHLs is conferred by binding specificity in LuxR-type receptor homologs, which can discriminate among AHLs with different acyl side chains. Deploying and detecting species-specific AHLs is an example of chemical encryption that restricts access to communications in a microbial community. In some cases, however, multiple AHLs can be detected by a single receptor with the ability to bind multiple AHLs – an example of decryption (Figure 2B) [2]. Promiscuity in AHL detection can impact interspecies bacterial interactions as well as interactions between bacteria and hosts [2].
Figure 2. Encrypted molecules.

(A) The structures of acyl-homoserine lactones (AHLs), pyoverdine siderophores, and cobamides are shown with constant regions in black and variable regions labeled in pink boxes. (B) Variants of AHLs, pyoverdine siderophores, and cobamides with specific examples of the encryptions in pink.
Siderophores encrypt access to iron
Nutrients have been analogized to currency in microbial communities [3], and thus nutrient encryption can be thought of as analogous to bank transaction encryption. The clearest example of nutrient encryption is the secreted iron-scavenging molecules known as siderophores, which sequester iron so that only organisms that can recognize and import the siderophore can gain access to the iron (Figure 2). In this case, the siderophore serves as an encryption device for the nutrient, iron. As in AHLs, siderophores also have constant and variable regions. Siderophores are produced intracellularly and secreted into the environment, where they bind iron and are subsequently imported into cells [4]. Because they are costly to produce, a form of decryption has emerged in which bacteria have acquired siderophore receptors from other species, enabling them to use siderophores produced by different species without contributing to siderophore biosynthesis – known as siderophore piracy [5]. Piracy has been suggested to drive the evolution of diversification and specialization of siderophore structures in order to encrypt siderophores for strains’ private use [6]. For example, different Pseudomonad strains produce nearly 100 structural variants of pyoverdine siderophores, with variability in the peptide domain and side chain that are attached to an invariant hydroquinoline involved in iron binding (Figure 2B) [4]. Production and use of these different siderophores require compatibility between siderophore structure and the siderophore secretion proteins (cytoplasm to periplasm transporter) and outer membrane uptake system. Pyoverdine biosynthesis, secretion, and transport in Pseudomonas aeruginosa strains requires over 30 genes, which may explain why production is costly [4,6]. The cost of producing these molecules points to the value of encrypting them for use only by kin.
Cobamide diversity can be explained as nutrient encryption
Cobamides, the vitamin B12 family of cofactors, exhibit considerable structural diversity, nearly all of which is due to variation in the lower ligand domain [7] (Figure 2). The reasons for the diversity of cobamides are much less well-understood than the diversity of siderophores. We propose that the structural diversity in cobamides (Figure 2) may be due to evolutionary pressures similar to those that drive siderophore diversification.
Cobamides are costly to synthesize, requiring over 30 genes for de novo biosynthesis and thus are likely to be valuable nutrients. Cobamides serve as enzyme cofactors for various metabolic processes, including the synthesis of deoxynucleotides and methionine. Only a minority of prokaryotes produce cobamides; yet, the majority use them, and thus microbes compete for cobamides produced by a limited number of community members in their environment [7]. Like siderophores, cobamides include constant and variable regions, and different organisms have molecular specificity for the production and use of particular cobamides [7]. This is analogous to the molecular specificity in siderophore–receptor interactions. However, cobamides are different from siderophores in that cobamides themselves are nutrients, whereas siderophores simply provide access to a nutrient. Thus, in order to use a given cobamide, a cell must have transporters that can import the cobamide as well as enzymes that use it. Empirical evidence shows that bacteria are cobamide ‘decryptors’ – capable of using more than one cobamide – yet, growth can be substantially reduced on nonpreferred cobamides due to incompatibilities with the enzymes that use the cobamide as a cofactor [7] (Figure 1B,E).
In cobamide-dependent organisms and enzymes studied to date, there is a range in the level of specificity for cobamides. Some bacteria, such as Clostridioides difficile and Bacteroides thetaiotaomicron, can use a wide range of cobamides [8], entirely ‘decrypting’ the encrypted molecules via promiscuous enzymes (Figure 1B). By contrast, Dehalococcoides mccartyi dehalogenase activity is highly sensitive to the cobamide structure, suggesting that for it, the cobamides are encrypted [7]. Even within an enzyme class, different orthologs can evolve to prefer different cobamides. In a model cobamide-dependent enzyme, cobamide preferences have been traced to differences in enzyme-cobamide binding [7]. The variability in the range of cobamide promiscuity and the evolution of protein-ligand binding preferences has interesting parallels with the AHL quorum-sensing systems, where different LuxR homologs have varying levels of promiscuity in their response to AHLs [2]. Similarly, a range of specificity in siderophore recognition has also been observed [9]. Thus, gradations in the level of encryption are used to tune the range of organisms capable of accessing a nutrient.
Just as encrypted nutrients can be decrypted, encrypted nutrients can also be converted between encrypted forms via chemical modification (Figure 1C,F). An example of nutrient conversion is cobamide remodeling – the removal of the variable lower ligand moiety and replacement with a more favorable moiety. Microbes with the ability to remodel cobamides are able to make use of any cobamide in their environment, effectively canceling out their chemical encryption [10]. On the basis of all of these reasons, we propose that cobamides are encrypted nutrients.
Glycosylation can encrypt host information and resources for select microbes
Microbes encrypt molecules in the cases we have discussed thus far. However, multicellular hosts such as animals and plants also encrypt molecules, and these molecules can shape their interactions with bacteria based on the bacterial ability to decrypt the molecules. Glycosylated proteins such as mucus are a major site of microbe–host interactions. Proteins are glycosylated in the endoplasmic reticulum and Golgi body, where specialized enzymes append sugars onto nascent peptides. Glycosylation of proteins has long been described as a code because different glycans can imbue different functions in the body. For instance, glycosylation can traffic a protein to a particular site in the cell or to a particular tissue. Secreted mucus in the gut lumen is heavily glycosylated, and this glycosylation serves to form a hydrated layer that protects host cells from direct contact with bacteria.
Decryption mechanisms include targeted degradation by select bacteria in the gut that have evolved glycolytic enzymes to cleave glycans from mucus, allowing the bacteria to use the free sugars as carbon and nitrogen sources. Other bacteria that live in the gut but do not possess the appropriate glycolytic enzymes can consume the free sugars [11]. It has also been proposed that human breast milk, with over 200 different types of glycans, has this diversity in order to recruit and maintain specific types of Bifidobacteria and Lactobacillus that are crucial to early childhood development [12]. Similarly, plant root exudates, which are rich in glycans, cultivate specific bacterial and fungal species [13]. In these examples, the host is encrypting the nutrients, and select bacteria decrypt them, which allows the bacteria to occupy a privileged host space [11].
Host iron encryption by transferrin/lactoferrin can be subverted by microbial decryption
Competition for metals is also used as a host mechanism to prevent pathogen invasion. For instance, iron is a limiting nutrient for microbial growth. Mammalian hosts encrypt iron by secreting transferrin and lactoferrin, which sequester iron away from microbial cells. This strategy effectively prevents microbes from invading host tissues and allows the host to reclaim its own iron from the serum [14]. In this way, the host has encrypted iron transactions between host cells. However, pathogens have evolved decryption mechanisms. For instance, receptors for transferrin, lactoferrin, and heme allow pathogens to import the sequestered iron and access it. This decryption of host iron encryption allows these select organisms to subvert the host and claim the iron for themselves. Pathogens also use their own iron sequestration mechanisms, including siderophores, which compete with host sequestration molecules. Hosts in turn release siderocalin, which binds siderophores, effectively policing the decryptors. However, pathogens have evolved ‘stealth siderophores,’ which evade siderocalin, providing a second decryption strategy [14]. Thus, microbes and hosts may engage in encryption-decryption races for valuable resources.
Encryption-decryption requires a diversity of codes
The rise of transferrin and lactoferrin decryption mechanisms as well as the diversity of siderophores and cobamides can be explained by evolutionary selection pressures to protect valuable resources [6]. As soon as a new encoding is evolved, an evolutionary opportunity for a decoding mechanism is created. However, the core functional part of the molecule must remain unchanged, as can be seen in Figure 2. From an evolutionary perspective, the results of the selection pressures favoring the encoding of nutrients is evident in that the most diverse regions of siderophore operons are those that function in biosynthesis of the variable moieties (i.e., the peptide chain via NRPS), followed by the secretion and uptake systems. This diversity is consistent with coevolution of structural variability and function. These gene clusters show evidence of modularity, with gene shuffling and horizontal gene transfer corresponding to variations in siderophore structure [4]. Thus, the importance of encryption is apparent, based on the diversity of codes in bacterial genomes.
Perspective: what other types of molecules might be encrypted?
High-value nutrients and privileged spaces are costly to produce and maintain. Encryption is one mechanism to protect these valued resources, such as siderophores and cobamides. However, encryption itself is costly and does not make sense for every case. For example, amino acids are cheap to produce and often secreted, forming the basis of cross-feeding interactions with other bacteria. Amino acids are not encrypted, and the cost of encrypting them would likely make their production prohibitively expensive. We propose that this cost–benefit perspective can point the way to cases where encryption is a likely explanation for observed molecular complexity (e.g., [15]). One use of the encryption concept will be to predict the value of nutrients based on the complexity of their encryption mechanisms. Inversely, we may find new molecular encryptions if we examine valuable molecules. Cobamides, for instance, have nearly 20 discrete forms. We suggest that other metabolites may have similar diversity due to encryption. Molecular encryption could be harnessed to design targeted interactions in complex microbial communities. Thus, discovering new examples of encryption may enable new biotechnologies.
Acknowledgments
We thank Kent Kotaka, Angela Xu, Robert Scheffler, Josh Derrick, Zoila Alvarez-Aponte, Kenny Mok, Dennis Suazo, and Zachary Hallberg for helpful suggestions. Research in the Taga laboratory is supported by a National Institutes of Health (NIH) grant R35GM139633 and Department of Energy grant DE-SC0020155. Research in the Ludington laboratory is supported by National Science Foundation grants IOS 2032985 and IOS 2144342, NIH grant R01DK128454, a Scialog award from the Research Corporation for Science Advancement and the Allen Foundation, and the Carnegie Institution for Science Endowment.
Footnotes
Declaration of interests
No interests are declared.
References
- 1.Hawver LA et al. (2016) Specificity and complexity in bacterial quorum-sensing systems. FEMS Microbiol. Rev. 40, 738–752 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Wellington S and Greenberg EP (2019) Quorum sensing signal selectivity and the potential for interspecies cross talk. mBio 10, e00146–19 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 3.Morris JJ et al. (2012) The black queen hypothesis: Evolution of dependencies through adaptive gene loss. mBio 3, e00036–12 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Schalk IJ et al. (2020) An overview of siderophore biosynthesis among fluorescent Pseudomonads and new insights into their complex cellular organization. Environ. Microbiol. 22, 1447–1466 [DOI] [PubMed] [Google Scholar]
- 5.Traxler MF et al. (2012) Interspecies modulation of bacterial development through iron competition and siderophore piracy. Mol. Microbiol. 86, 628–644 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Niehus R et al. (2017) The evolution of siderophore production as a competitive trait. Evolution (N. Y.) 71, 1443–1455 [DOI] [PubMed] [Google Scholar]
- 7.Sokolovskaya OM et al. (2020) Sharing vitamins: cobamides unveil microbial interactions. Science 369, eaba0165. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 8.Shelton AN et al. (2020) Flexible cobamide metabolism in Clostridioides (Clostridium) difficile 630 erm. J. Bacteriol. 202, e00584–19 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Kramer J et al. (2020) Bacterial siderophores in community and host interactions. Nat. Rev. Microbiol. 18, 152–163 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Mok KC et al. (2020) Identification of a novel cobamide remodeling enzyme in the beneficial human gut bacterium Akkermansia muciniphila. mBio 11, e02507–20 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.Kashyap PC et al. (2013) Genetically dictated change in host mucus carbohydrate landscape exerts a diet-dependent effect on the gut microbiota. Proc. Natl. Acad. Sci. U. S. A. 110, 17059–17064 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Walsh C et al. (2020) Human milk oligosaccharides: Shaping the infant gut microbiota and supporting health. J. Funct. Foods 72, 104074. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 13.Xu L et al. (2018) Drought delays development of the sorghum root microbiome and enriches for monoderm bacteria. Proc. Natl. Acad. Sci. U. S. A. 115, E4284–E4293 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Skaar EP (2010) The battle for iron between bacterial pathogens and their vertebrate hosts. PLoS Pathog. 6, e1000949. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 15.Nguyen DD et al. (2013) MS/MS networking guided analysis of molecule and gene cluster families. Proc. Natl. Acad. Sci. U. S. A. 110, E2611–E2620 [DOI] [PMC free article] [PubMed] [Google Scholar]


